|
|
[{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170985","id":1221724158,"node_id":"I_kwDOAEVQ_M5I0gf-","number":170985,"title":"Ncspot notifications not showing up in Dunst","user":{"login":"jrgiacone","id":71910145,"node_id":"MDQ6VXNlcjcxOTEwMTQ1","avatar_url":"https://avatars.githubusercontent.com/u/71910145?v=4","gravatar_id":"","url":"https://api.github.com/users/jrgiacone","html_url":"https://github.com/jrgiacone","followers_url":"https://api.github.com/users/jrgiacone/followers","following_url":"https://api.github.com/users/jrgiacone/following{/other_user}","gists_url":"https://api.github.com/users/jrgiacone/gists{/gist_id}","starred_url":"https://api.github.com/users/jrgiacone/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jrgiacone/subscriptions","organizations_url":"https://api.github.com/users/jrgiacone/orgs","repos_url":"https://api.github.com/users/jrgiacone/repos","events_url":"https://api.github.com/users/jrgiacone/events{/privacy}","received_events_url":"https://api.github.com/users/jrgiacone/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-30T04:44:05Z","updated_at":"2022-04-30T04:44:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nTrying to get dunst to show notifications for ncspot, currently no notifications show with the notifications enabled in the ncspot config file.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install ncspot\r\n2. install dunst and libnotify (to be safe)\r\n3. make sure to enable notifications in ncspot config file\r\n4. play some music and change the songs\r\n5. do the same with spotify to see expected notification banner\r\n\r\n### Expected behavior\r\nA notification should appear as it does with the spotify app, using the same settings as my other linux distributions.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\n@marsam @IvarWithoutBones @figsoda \r\n-->\r\n\r\n### Metadata\r\njrgiacone@nixos:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre372961.e10da1c7f54`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(jrgiacone): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170946","id":1221619936,"node_id":"I_kwDOAEVQ_M5I0HDg","number":170946,"title":"wineWowPackages.staging fails to build","user":{"login":"SFrijters","id":918365,"node_id":"MDQ6VXNlcjkxODM2NQ==","avatar_url":"https://avatars.githubusercontent.com/u/918365?v=4","gravatar_id":"","url":"https://api.github.com/users/SFrijters","html_url":"https://github.com/SFrijters","followers_url":"https://api.github.com/users/SFrijters/followers","following_url":"https://api.github.com/users/SFrijters/following{/other_user}","gists_url":"https://api.github.com/users/SFrijters/gists{/gist_id}","starred_url":"https://api.github.com/users/SFrijters/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SFrijters/subscriptions","organizations_url":"https://api.github.com/users/SFrijters/orgs","repos_url":"https://api.github.com/users/SFrijters/repos","events_url":"https://api.github.com/users/SFrijters/events{/privacy}","received_events_url":"https://api.github.com/users/SFrijters/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T22:06:41Z","updated_at":"2022-04-29T22:06:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhile trying to create https://github.com/NixOS/nixpkgs/pull/170943 I noticed that my buils were failing, but even rolling back to current master, wine won't build for me. This is on 57ba746ca7b.\r\n\r\n```\r\n$ nix-build -A wineWowPackages.staging --keep-failed --check\r\n[...]\r\nerror: builder for '/nix/store/x2j1290fkwyzh200fxikwx6i59jwpcif-wine-wow-7.4-staging.drv' failed with exit code 2;\r\n last 10 log lines:\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/kernelbase/libkernelbase.cross.a --export \\\r\n > /build/wine-7.4/dlls/kernelbase/kernelbase.spec\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/sechost/libsechost.cross.a --export \\\r\n > /build/wine-7.4/dlls/sechost/sechost.spec\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/setupapi/libsetupapi.cross.a --export \\\r\n > /build/wine-7.4/dlls/setupapi/setupapi.spec\r\n > /nix/store/6nsvi3ar932jjlslpgywas2fkzmvasg8-x86_64-w64-mingw32-binutils-2.38/bin/x86_64-w64-mingw32-dlltool: dlls/rpcrt4/librpcrt4.delay.a: error reading rpcrt4_dll_t.o: No such file or directory\r\n > winebuild: /nix/store/6nsvi3ar932jjlslpgywas2fkzmvasg8-x86_64-w64-mingw32-binutils-2.38/bin/x86_64-w64-mingw32-dlltool failed with status 1\r\n > make: *** [Makefile:171142: dlls/rpcrt4/librpcrt4.delay.a] Error 1\r\n > make: *** Waiting for unfinished jobs....\r\n For full logs, run 'nix log /nix/store/x2j1290fkwyzh200fxikwx6i59jwpcif-wine-wow-7.4-staging.drv'.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nOn master (57ba746ca7b):\r\n$ nix-build -A wineWowPackages.staging --keep-failed --check\r\n\r\n### Expected behavior\r\n\r\nWine staging builds successfully, as it did before.\r\n\r\n### Additional context\r\n\r\nI've tried to bisect this issue (I suspect that the gcc compiler or binutils bump that happened since the 7.4 update in nixpkgs may be causing the issue), but my machine has been chugging along for twelve hours on 52f8cf58a45 and I still haven't reached the actual wine build yet, so that is turning out to be impractical for me. Commit dd6c7096d629d9c6814c6980180254d3336a9a3b (which bumps the wine version to 7.4) works for me.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220426.cdb0887`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(frijters): `\"\"`\r\n - channels(root): `\"nixos, nixos-unstable-20.09pre225264.683c68232e9\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170944","id":1221576113,"node_id":"I_kwDOAEVQ_M5Iz8Wx","number":170944,"title":"nbb","user":{"login":"PlumpMath","id":1218365,"node_id":"MDQ6VXNlcjEyMTgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/1218365?v=4","gravatar_id":"","url":"https://api.github.com/users/PlumpMath","html_url":"https://github.com/PlumpMath","followers_url":"https://api.github.com/users/PlumpMath/followers","following_url":"https://api.github.com/users/PlumpMath/following{/other_user}","gists_url":"https://api.github.com/users/PlumpMath/gists{/gist_id}","starred_url":"https://api.github.com/users/PlumpMath/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PlumpMath/subscriptions","organizations_url":"https://api.github.com/users/PlumpMath/orgs","repos_url":"https://api.github.com/users/PlumpMath/repos","events_url":"https://api.github.com/users/PlumpMath/events{/privacy}","received_events_url":"https://api.github.com/users/PlumpMath/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T21:36:02Z","updated_at":"2022-04-29T21:36:02Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nNot [babashka](https://babashka.org/). Node.js babashka!?\r\nAd-hoc CLJS scripting on Node.js.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/babashka/nbb\r\n* source URL: https://github.com/babashka/nbb\r\n* license: EPL\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170911","id":1220827780,"node_id":"I_kwDOAEVQ_M5IxFqE","number":170911,"title":"Scala 3","user":{"login":"schlichtanders","id":4255480,"node_id":"MDQ6VXNlcjQyNTU0ODA=","avatar_url":"https://avatars.githubusercontent.com/u/4255480?v=4","gravatar_id":"","url":"https://api.github.com/users/schlichtanders","html_url":"https://github.com/schlichtanders","followers_url":"https://api.github.com/users/schlichtanders/followers","following_url":"https://api.github.com/users/schlichtanders/following{/other_user}","gists_url":"https://api.github.com/users/schlichtanders/gists{/gist_id}","starred_url":"https://api.github.com/users/schlichtanders/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schlichtanders/subscriptions","organizations_url":"https://api.github.com/users/schlichtanders/orgs","repos_url":"https://api.github.com/users/schlichtanders/repos","events_url":"https://api.github.com/users/schlichtanders/events{/privacy}","received_events_url":"https://api.github.com/users/schlichtanders/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-29T13:29:27Z","updated_at":"2022-04-30T07:15:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nScala 3 is more than a year old. It would be nice to have it packaged in nixpkgs as well.\r\n\r\nMaybe it is, but I couldn't find it under \"scala-3\" or respective versions.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://scala-lang.org/\r\n* source URL: https://github.com/lampepfl/dotty\r\n* license: Apache-2.0 License\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170902","id":1220715587,"node_id":"I_kwDOAEVQ_M5IwqRD","number":170902,"title":"mitmproxy: checks fail while building","user":{"login":"bouk","id":97820,"node_id":"MDQ6VXNlcjk3ODIw","avatar_url":"https://avatars.githubusercontent.com/u/97820?v=4","gravatar_id":"","url":"https://api.github.com/users/bouk","html_url":"https://github.com/bouk","followers_url":"https://api.github.com/users/bouk/followers","following_url":"https://api.github.com/users/bouk/following{/other_user}","gists_url":"https://api.github.com/users/bouk/gists{/gist_id}","starred_url":"https://api.github.com/users/bouk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bouk/subscriptions","organizations_url":"https://api.github.com/users/bouk/orgs","repos_url":"https://api.github.com/users/bouk/repos","events_url":"https://api.github.com/users/bouk/events{/privacy}","received_events_url":"https://api.github.com/users/bouk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T12:35:22Z","updated_at":"2022-04-29T12:35:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nmitmproxy tests fail while building\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior: `nix-shell -p mitmproxy`\r\n\r\n### Expected behavior\r\n\r\nI'm able to run `mitmproxy`\r\n\r\n### Screenshots\r\n\r\n<img width=\"1421\" alt=\"image\" src=\"https://user-images.githubusercontent.com/97820/165945159-f3628b8e-c535-4495-b943-cfa88b1cdd3a.png\">\r\n\r\n\r\n### Additional context\r\n\r\nFull build log can be found here: https://gist.github.com/bouk/cb7a8864fd6f224736f735b226b6e08a\r\n\r\nThe error in the failing tests seems to be `MemoryError: Cannot allocate write+execute memory for ffi.callback(). You might be running on a system that prevents this.`\r\n\r\n### Notify maintainers\r\n\r\n@fpletz @kamilchm\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(bouke): `\"darwin, nixpkgs\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/Users/bouke/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170897","id":1220629127,"node_id":"I_kwDOAEVQ_M5IwVKH","number":170897,"title":"Document how to work around dynamic linking problems caused by glibc updates","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null},{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-29T11:51:30Z","updated_at":"2022-04-29T15:25:16Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"With the recent update to glibc 2.34, a lot of people have been running into problems caused by nixpkgs and their non-NixOS distribution switching glibc version at a different pace (and the problem is probably also possible to run into on NixOS, albeit rarer). I've seen two different class of issues recently:\r\n\r\n* Missing internal glibc versions (of version `GLIBC_PRIVATE`): https://github.com/NixOS/nixpkgs/issues/169332\r\n* Missing versioned (up to date) public symbols, in this case `GLIBC_2.34` when an older version gets loaded by accident: https://github.com/NixOS/nixpkgs/issues/170550#issuecomment-1111002983, https://github.com/NixOS/nixpkgs/issues/169040, https://discourse.nixos.org/t/opening-links-in-brave-from-discord-is-broken-version-glibc-2-34-not-found/18764, https://discourse.nixos.org/t/glibc-2-33-vs-2-34-rust-madness/18909/3, …\r\n\r\nRelated discussion (on solving the technical problem):\r\n\r\n* https://discourse.nixos.org/t/could-we-robustly-protect-against-errors-version-glibc-2-33/18343\r\n* https://github.com/NixOS/nixpkgs/issues/31189\r\n\r\nI think a great help short of solving the problem altogether would be documenting it and how to work around it in a central place, i.e. the nixpkgs manual. Then it becomes easier to link to an answer to the recurring question. I lack the time and precise understanding of the problem at the moment, so it'd be great if someone could pick this up!","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170856","id":1219953046,"node_id":"I_kwDOAEVQ_M5ItwGW","number":170856,"title":"Nouveau segfault when launching X11 Display Manager","user":{"login":"vlinkz","id":20145996,"node_id":"MDQ6VXNlcjIwMTQ1OTk2","avatar_url":"https://avatars.githubusercontent.com/u/20145996?v=4","gravatar_id":"","url":"https://api.github.com/users/vlinkz","html_url":"https://github.com/vlinkz","followers_url":"https://api.github.com/users/vlinkz/followers","following_url":"https://api.github.com/users/vlinkz/following{/other_user}","gists_url":"https://api.github.com/users/vlinkz/gists{/gist_id}","starred_url":"https://api.github.com/users/vlinkz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vlinkz/subscriptions","organizations_url":"https://api.github.com/users/vlinkz/orgs","repos_url":"https://api.github.com/users/vlinkz/repos","events_url":"https://api.github.com/users/vlinkz/events{/privacy}","received_events_url":"https://api.github.com/users/vlinkz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-04-29T06:06:48Z","updated_at":"2022-04-30T05:08:26Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI have a Dell XPS 9550, which has both an Intel I7 and Nvidia 950M. When I do a fresh NixOS install (using NixOS-unstable), by default lightdm and sddm both cause a segmentation fault that seems to be related to nouveau. Disabling the nouveau driver with `modprobe -r nouveau` allows me to restart the display manager and launch a desktop environment. This happend with both SDDM and KDE Plasma, and Light with Pantheon. Log: https://gist.github.com/vlinkz/62e48c55793402d98746b92ad50ccea8\r\n```\r\n[ 9.341] (==) NOUVEAU(G0): Backing store enabled\r\n[ 9.341] (==) NOUVEAU(G0): Silken mouse enabled\r\n[ 9.341] (II) NOUVEAU(G0): [XvMC] Associated with Nouveau GeForce 8/9 Textured Video.\r\n[ 9.341] (II) NOUVEAU(G0): [XvMC] Extension initialized.\r\n[ 9.341] (==) NOUVEAU(G0): DPMS enabled\r\n[ 9.341] (EE) \r\n[ 9.341] (EE) Backtrace:\r\n[ 9.341] (EE) 0: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (OsSigHandler+0x25) [0x5b4065]\r\n[ 9.342] (EE) 1: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__sigaction+0x40) [0x7fad63270100]\r\n[ 9.342] (EE) 2: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (InitOutput+0x4e4) [0x487744]\r\n[ 9.342] (EE) 3: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (dix_main+0x194) [0x448694]\r\n[ 9.343] (EE) 4: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__libc_start_call_main+0x67) [0x7fad6325c1d7]\r\n[ 9.343] (EE) 5: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__libc_start_main+0x87) [0x7fad6325c297]\r\n[ 9.343] (EE) 6: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (_start+0x21) [0x431cd1]\r\n[ 9.343] (EE) \r\n[ 9.343] (EE) Segmentation fault at address 0x10\r\n[ 9.343] (EE) \r\nFatal server error:\r\n[ 9.343] (EE) Caught signal 11 (Segmentation fault). Server aborting\r\n[ 9.343] (EE) \r\n[ 9.343] (EE) \r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install NixOS unstable with all video driver options left at defaults\r\n2. Enable an X11 display manager such as lightdm\r\n3. Try to start display manager\r\n\r\n### Expected behavior\r\nDisplay manager starting\r\n\r\n### Additional context\r\n- Downgrading to NixOS 21.11 fixed the issue. Output log: https://gist.github.com/vlinkz/a7db75c7f0668f92369d0680669e747b\r\n- Adding `\"intel\"` to `xserver.videoDrivers` also works, but seemed to be disabled by default in https://github.com/NixOS/nixpkgs/issues/55520 and https://github.com/NixOS/nixpkgs/pull/55583\r\n- Setting `boot.kernelParams = [ \"nouveau.modeset=0\" ]` makes it work\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nNot sure who\r\n### Metadata\r\n22.05pre372961.e10da1c7f54 - Not working\r\n21.11.337266.feea25c5865 - Working\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170985","id":1221724158,"node_id":"I_kwDOAEVQ_M5I0gf-","number":170985,"title":"Ncspot notifications not showing up in Dunst","user":{"login":"jrgiacone","id":71910145,"node_id":"MDQ6VXNlcjcxOTEwMTQ1","avatar_url":"https://avatars.githubusercontent.com/u/71910145?v=4","gravatar_id":"","url":"https://api.github.com/users/jrgiacone","html_url":"https://github.com/jrgiacone","followers_url":"https://api.github.com/users/jrgiacone/followers","following_url":"https://api.github.com/users/jrgiacone/following{/other_user}","gists_url":"https://api.github.com/users/jrgiacone/gists{/gist_id}","starred_url":"https://api.github.com/users/jrgiacone/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jrgiacone/subscriptions","organizations_url":"https://api.github.com/users/jrgiacone/orgs","repos_url":"https://api.github.com/users/jrgiacone/repos","events_url":"https://api.github.com/users/jrgiacone/events{/privacy}","received_events_url":"https://api.github.com/users/jrgiacone/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-30T04:44:05Z","updated_at":"2022-04-30T04:44:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nTrying to get dunst to show notifications for ncspot, currently no notifications show with the notifications enabled in the ncspot config file.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install ncspot\r\n2. install dunst and libnotify (to be safe)\r\n3. make sure to enable notifications in ncspot config file\r\n4. play some music and change the songs\r\n5. do the same with spotify to see expected notification banner\r\n\r\n### Expected behavior\r\nA notification should appear as it does with the spotify app, using the same settings as my other linux distributions.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\n@marsam @IvarWithoutBones @figsoda \r\n-->\r\n\r\n### Metadata\r\njrgiacone@nixos:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre372961.e10da1c7f54`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(jrgiacone): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170985/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170946","id":1221619936,"node_id":"I_kwDOAEVQ_M5I0HDg","number":170946,"title":"wineWowPackages.staging fails to build","user":{"login":"SFrijters","id":918365,"node_id":"MDQ6VXNlcjkxODM2NQ==","avatar_url":"https://avatars.githubusercontent.com/u/918365?v=4","gravatar_id":"","url":"https://api.github.com/users/SFrijters","html_url":"https://github.com/SFrijters","followers_url":"https://api.github.com/users/SFrijters/followers","following_url":"https://api.github.com/users/SFrijters/following{/other_user}","gists_url":"https://api.github.com/users/SFrijters/gists{/gist_id}","starred_url":"https://api.github.com/users/SFrijters/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SFrijters/subscriptions","organizations_url":"https://api.github.com/users/SFrijters/orgs","repos_url":"https://api.github.com/users/SFrijters/repos","events_url":"https://api.github.com/users/SFrijters/events{/privacy}","received_events_url":"https://api.github.com/users/SFrijters/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T22:06:41Z","updated_at":"2022-04-29T22:06:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhile trying to create https://github.com/NixOS/nixpkgs/pull/170943 I noticed that my buils were failing, but even rolling back to current master, wine won't build for me. This is on 57ba746ca7b.\r\n\r\n```\r\n$ nix-build -A wineWowPackages.staging --keep-failed --check\r\n[...]\r\nerror: builder for '/nix/store/x2j1290fkwyzh200fxikwx6i59jwpcif-wine-wow-7.4-staging.drv' failed with exit code 2;\r\n last 10 log lines:\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/kernelbase/libkernelbase.cross.a --export \\\r\n > /build/wine-7.4/dlls/kernelbase/kernelbase.spec\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/sechost/libsechost.cross.a --export \\\r\n > /build/wine-7.4/dlls/sechost/sechost.spec\r\n > tools/winebuild/winebuild -b x86_64-w64-mingw32 -w --implib -o dlls/setupapi/libsetupapi.cross.a --export \\\r\n > /build/wine-7.4/dlls/setupapi/setupapi.spec\r\n > /nix/store/6nsvi3ar932jjlslpgywas2fkzmvasg8-x86_64-w64-mingw32-binutils-2.38/bin/x86_64-w64-mingw32-dlltool: dlls/rpcrt4/librpcrt4.delay.a: error reading rpcrt4_dll_t.o: No such file or directory\r\n > winebuild: /nix/store/6nsvi3ar932jjlslpgywas2fkzmvasg8-x86_64-w64-mingw32-binutils-2.38/bin/x86_64-w64-mingw32-dlltool failed with status 1\r\n > make: *** [Makefile:171142: dlls/rpcrt4/librpcrt4.delay.a] Error 1\r\n > make: *** Waiting for unfinished jobs....\r\n For full logs, run 'nix log /nix/store/x2j1290fkwyzh200fxikwx6i59jwpcif-wine-wow-7.4-staging.drv'.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nOn master (57ba746ca7b):\r\n$ nix-build -A wineWowPackages.staging --keep-failed --check\r\n\r\n### Expected behavior\r\n\r\nWine staging builds successfully, as it did before.\r\n\r\n### Additional context\r\n\r\nI've tried to bisect this issue (I suspect that the gcc compiler or binutils bump that happened since the 7.4 update in nixpkgs may be causing the issue), but my machine has been chugging along for twelve hours on 52f8cf58a45 and I still haven't reached the actual wine build yet, so that is turning out to be impractical for me. Commit dd6c7096d629d9c6814c6980180254d3336a9a3b (which bumps the wine version to 7.4) works for me.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220426.cdb0887`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(frijters): `\"\"`\r\n - channels(root): `\"nixos, nixos-unstable-20.09pre225264.683c68232e9\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170946/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170944","id":1221576113,"node_id":"I_kwDOAEVQ_M5Iz8Wx","number":170944,"title":"nbb","user":{"login":"PlumpMath","id":1218365,"node_id":"MDQ6VXNlcjEyMTgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/1218365?v=4","gravatar_id":"","url":"https://api.github.com/users/PlumpMath","html_url":"https://github.com/PlumpMath","followers_url":"https://api.github.com/users/PlumpMath/followers","following_url":"https://api.github.com/users/PlumpMath/following{/other_user}","gists_url":"https://api.github.com/users/PlumpMath/gists{/gist_id}","starred_url":"https://api.github.com/users/PlumpMath/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PlumpMath/subscriptions","organizations_url":"https://api.github.com/users/PlumpMath/orgs","repos_url":"https://api.github.com/users/PlumpMath/repos","events_url":"https://api.github.com/users/PlumpMath/events{/privacy}","received_events_url":"https://api.github.com/users/PlumpMath/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T21:36:02Z","updated_at":"2022-04-29T21:36:02Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nNot [babashka](https://babashka.org/). Node.js babashka!?\r\nAd-hoc CLJS scripting on Node.js.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/babashka/nbb\r\n* source URL: https://github.com/babashka/nbb\r\n* license: EPL\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170944/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170911","id":1220827780,"node_id":"I_kwDOAEVQ_M5IxFqE","number":170911,"title":"Scala 3","user":{"login":"schlichtanders","id":4255480,"node_id":"MDQ6VXNlcjQyNTU0ODA=","avatar_url":"https://avatars.githubusercontent.com/u/4255480?v=4","gravatar_id":"","url":"https://api.github.com/users/schlichtanders","html_url":"https://github.com/schlichtanders","followers_url":"https://api.github.com/users/schlichtanders/followers","following_url":"https://api.github.com/users/schlichtanders/following{/other_user}","gists_url":"https://api.github.com/users/schlichtanders/gists{/gist_id}","starred_url":"https://api.github.com/users/schlichtanders/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schlichtanders/subscriptions","organizations_url":"https://api.github.com/users/schlichtanders/orgs","repos_url":"https://api.github.com/users/schlichtanders/repos","events_url":"https://api.github.com/users/schlichtanders/events{/privacy}","received_events_url":"https://api.github.com/users/schlichtanders/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-29T13:29:27Z","updated_at":"2022-04-30T07:15:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nScala 3 is more than a year old. It would be nice to have it packaged in nixpkgs as well.\r\n\r\nMaybe it is, but I couldn't find it under \"scala-3\" or respective versions.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://scala-lang.org/\r\n* source URL: https://github.com/lampepfl/dotty\r\n* license: Apache-2.0 License\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170911/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170902","id":1220715587,"node_id":"I_kwDOAEVQ_M5IwqRD","number":170902,"title":"mitmproxy: checks fail while building","user":{"login":"bouk","id":97820,"node_id":"MDQ6VXNlcjk3ODIw","avatar_url":"https://avatars.githubusercontent.com/u/97820?v=4","gravatar_id":"","url":"https://api.github.com/users/bouk","html_url":"https://github.com/bouk","followers_url":"https://api.github.com/users/bouk/followers","following_url":"https://api.github.com/users/bouk/following{/other_user}","gists_url":"https://api.github.com/users/bouk/gists{/gist_id}","starred_url":"https://api.github.com/users/bouk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bouk/subscriptions","organizations_url":"https://api.github.com/users/bouk/orgs","repos_url":"https://api.github.com/users/bouk/repos","events_url":"https://api.github.com/users/bouk/events{/privacy}","received_events_url":"https://api.github.com/users/bouk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T12:35:22Z","updated_at":"2022-04-29T12:35:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nmitmproxy tests fail while building\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior: `nix-shell -p mitmproxy`\r\n\r\n### Expected behavior\r\n\r\nI'm able to run `mitmproxy`\r\n\r\n### Screenshots\r\n\r\n<img width=\"1421\" alt=\"image\" src=\"https://user-images.githubusercontent.com/97820/165945159-f3628b8e-c535-4495-b943-cfa88b1cdd3a.png\">\r\n\r\n\r\n### Additional context\r\n\r\nFull build log can be found here: https://gist.github.com/bouk/cb7a8864fd6f224736f735b226b6e08a\r\n\r\nThe error in the failing tests seems to be `MemoryError: Cannot allocate write+execute memory for ffi.callback(). You might be running on a system that prevents this.`\r\n\r\n### Notify maintainers\r\n\r\n@fpletz @kamilchm\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(bouke): `\"darwin, nixpkgs\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/Users/bouke/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170902/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170897","id":1220629127,"node_id":"I_kwDOAEVQ_M5IwVKH","number":170897,"title":"Document how to work around dynamic linking problems caused by glibc updates","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null},{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-29T11:51:30Z","updated_at":"2022-04-29T15:25:16Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"With the recent update to glibc 2.34, a lot of people have been running into problems caused by nixpkgs and their non-NixOS distribution switching glibc version at a different pace (and the problem is probably also possible to run into on NixOS, albeit rarer). I've seen two different class of issues recently:\r\n\r\n* Missing internal glibc versions (of version `GLIBC_PRIVATE`): https://github.com/NixOS/nixpkgs/issues/169332\r\n* Missing versioned (up to date) public symbols, in this case `GLIBC_2.34` when an older version gets loaded by accident: https://github.com/NixOS/nixpkgs/issues/170550#issuecomment-1111002983, https://github.com/NixOS/nixpkgs/issues/169040, https://discourse.nixos.org/t/opening-links-in-brave-from-discord-is-broken-version-glibc-2-34-not-found/18764, https://discourse.nixos.org/t/glibc-2-33-vs-2-34-rust-madness/18909/3, …\r\n\r\nRelated discussion (on solving the technical problem):\r\n\r\n* https://discourse.nixos.org/t/could-we-robustly-protect-against-errors-version-glibc-2-33/18343\r\n* https://github.com/NixOS/nixpkgs/issues/31189\r\n\r\nI think a great help short of solving the problem altogether would be documenting it and how to work around it in a central place, i.e. the nixpkgs manual. Then it becomes easier to link to an answer to the recurring question. I lack the time and precise understanding of the problem at the moment, so it'd be great if someone could pick this up!","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170897/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170856","id":1219953046,"node_id":"I_kwDOAEVQ_M5ItwGW","number":170856,"title":"Nouveau segfault when launching X11 Display Manager","user":{"login":"vlinkz","id":20145996,"node_id":"MDQ6VXNlcjIwMTQ1OTk2","avatar_url":"https://avatars.githubusercontent.com/u/20145996?v=4","gravatar_id":"","url":"https://api.github.com/users/vlinkz","html_url":"https://github.com/vlinkz","followers_url":"https://api.github.com/users/vlinkz/followers","following_url":"https://api.github.com/users/vlinkz/following{/other_user}","gists_url":"https://api.github.com/users/vlinkz/gists{/gist_id}","starred_url":"https://api.github.com/users/vlinkz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vlinkz/subscriptions","organizations_url":"https://api.github.com/users/vlinkz/orgs","repos_url":"https://api.github.com/users/vlinkz/repos","events_url":"https://api.github.com/users/vlinkz/events{/privacy}","received_events_url":"https://api.github.com/users/vlinkz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-04-29T06:06:48Z","updated_at":"2022-04-30T05:08:26Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI have a Dell XPS 9550, which has both an Intel I7 and Nvidia 950M. When I do a fresh NixOS install (using NixOS-unstable), by default lightdm and sddm both cause a segmentation fault that seems to be related to nouveau. Disabling the nouveau driver with `modprobe -r nouveau` allows me to restart the display manager and launch a desktop environment. This happend with both SDDM and KDE Plasma, and Light with Pantheon. Log: https://gist.github.com/vlinkz/62e48c55793402d98746b92ad50ccea8\r\n```\r\n[ 9.341] (==) NOUVEAU(G0): Backing store enabled\r\n[ 9.341] (==) NOUVEAU(G0): Silken mouse enabled\r\n[ 9.341] (II) NOUVEAU(G0): [XvMC] Associated with Nouveau GeForce 8/9 Textured Video.\r\n[ 9.341] (II) NOUVEAU(G0): [XvMC] Extension initialized.\r\n[ 9.341] (==) NOUVEAU(G0): DPMS enabled\r\n[ 9.341] (EE) \r\n[ 9.341] (EE) Backtrace:\r\n[ 9.341] (EE) 0: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (OsSigHandler+0x25) [0x5b4065]\r\n[ 9.342] (EE) 1: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__sigaction+0x40) [0x7fad63270100]\r\n[ 9.342] (EE) 2: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (InitOutput+0x4e4) [0x487744]\r\n[ 9.342] (EE) 3: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (dix_main+0x194) [0x448694]\r\n[ 9.343] (EE) 4: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__libc_start_call_main+0x67) [0x7fad6325c1d7]\r\n[ 9.343] (EE) 5: /nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6 (__libc_start_main+0x87) [0x7fad6325c297]\r\n[ 9.343] (EE) 6: /nix/store/bnic4bpn6x1jy2j3glnzdw54km94p9xa-xorg-server-21.1.3/bin/X (_start+0x21) [0x431cd1]\r\n[ 9.343] (EE) \r\n[ 9.343] (EE) Segmentation fault at address 0x10\r\n[ 9.343] (EE) \r\nFatal server error:\r\n[ 9.343] (EE) Caught signal 11 (Segmentation fault). Server aborting\r\n[ 9.343] (EE) \r\n[ 9.343] (EE) \r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install NixOS unstable with all video driver options left at defaults\r\n2. Enable an X11 display manager such as lightdm\r\n3. Try to start display manager\r\n\r\n### Expected behavior\r\nDisplay manager starting\r\n\r\n### Additional context\r\n- Downgrading to NixOS 21.11 fixed the issue. Output log: https://gist.github.com/vlinkz/a7db75c7f0668f92369d0680669e747b\r\n- Adding `\"intel\"` to `xserver.videoDrivers` also works, but seemed to be disabled by default in https://github.com/NixOS/nixpkgs/issues/55520 and https://github.com/NixOS/nixpkgs/pull/55583\r\n- Setting `boot.kernelParams = [ \"nouveau.modeset=0\" ]` makes it work\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nNot sure who\r\n### Metadata\r\n22.05pre372961.e10da1c7f54 - Not working\r\n21.11.337266.feea25c5865 - Working\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170856/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170847","id":1219819293,"node_id":"I_kwDOAEVQ_M5ItPcd","number":170847,"title":"lazarus package out of date","user":{"login":"laalsaas","id":43275254,"node_id":"MDQ6VXNlcjQzMjc1MjU0","avatar_url":"https://avatars.githubusercontent.com/u/43275254?v=4","gravatar_id":"","url":"https://api.github.com/users/laalsaas","html_url":"https://github.com/laalsaas","followers_url":"https://api.github.com/users/laalsaas/followers","following_url":"https://api.github.com/users/laalsaas/following{/other_user}","gists_url":"https://api.github.com/users/laalsaas/gists{/gist_id}","starred_url":"https://api.github.com/users/laalsaas/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/laalsaas/subscriptions","organizations_url":"https://api.github.com/users/laalsaas/orgs","repos_url":"https://api.github.com/users/laalsaas/repos","events_url":"https://api.github.com/users/laalsaas/events{/privacy}","received_events_url":"https://api.github.com/users/laalsaas/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-29T04:38:44Z","updated_at":"2022-04-29T04:38:44Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: legacyPackages.x86_64-linux.lazarus\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 2.0.12\r\ndesired version: 2.2.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @raskin \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170847/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170825","id":1219397022,"node_id":"I_kwDOAEVQ_M5IroWe","number":170825,"title":"Remove openjdk 12, 13, 14, 15, 16","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T22:39:19Z","updated_at":"2022-04-29T06:09:49Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"All of these are EOL and releases >=15 haven't received fixes for psychic signatures vulnerability.\r\n\r\nhttps://endoflife.date/java\r\n\r\n@edwtjo @asbachb ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170825/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170805","id":1219165229,"node_id":"I_kwDOAEVQ_M5Iqvwt","number":170805,"title":"pleroma: `pleroma_ctl instance gen` fails due to missing COOKIE file","user":{"login":"lambdadog","id":36526063,"node_id":"MDQ6VXNlcjM2NTI2MDYz","avatar_url":"https://avatars.githubusercontent.com/u/36526063?v=4","gravatar_id":"","url":"https://api.github.com/users/lambdadog","html_url":"https://github.com/lambdadog","followers_url":"https://api.github.com/users/lambdadog/followers","following_url":"https://api.github.com/users/lambdadog/following{/other_user}","gists_url":"https://api.github.com/users/lambdadog/gists{/gist_id}","starred_url":"https://api.github.com/users/lambdadog/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lambdadog/subscriptions","organizations_url":"https://api.github.com/users/lambdadog/orgs","repos_url":"https://api.github.com/users/lambdadog/repos","events_url":"https://api.github.com/users/lambdadog/events{/privacy}","received_events_url":"https://api.github.com/users/lambdadog/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-28T19:16:56Z","updated_at":"2022-04-29T01:58:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nPleroma fails to run due to missing cookie file. This causes no issues with the NixOS module as it overloads the pleroma derivation's `cookieFile` argument, but renders the default build unusable without explicitly setting `RELEASE_COOKIE`.\r\n\r\nThis is an issue due to `pleroma_ctl instance gen`, the intended way to generate a config for a fresh instance, [calling into pleroma](https://git.pleroma.social/pleroma/pleroma/-/blob/f3451e723bbc1adb879908532525d54dba1b601a/rel/files/bin/pleroma_ctl#L156) in order to run. It's worth noting using `pleroma_ctl instance gen` is the intended way to generate a config for the NixOS module and set up the postgresql database [as per the NixOS docs for the module](https://github.com/NixOS/nixpkgs/blob/a3d011eebcee9f70463a68c28b2252073336ed54/nixos/modules/services/networking/pleroma.xml#L9-L20).\r\n\r\n### Steps To Reproduce\r\nOn nixpkgs master:\r\n```console\r\n$ nix-shell -p pleroma\r\n$ cd $(mktemp -d)\r\n$ pleroma_ctl instance gen --output config.exs --output-psql setup.psql\r\ncat: /nix/store/lxxn1n18k959n8l41fizbi6gqz515xf4-pleroma-2.4.2/releases/COOKIE: No such file or directory\r\n```\r\n\r\n### Expected behavior\r\n`pleroma_ctl` running and generating the config.exs and setup.psql files.\r\n\r\n### Notify maintainers\r\n@petabyteboy\r\n@ninjatrappeur\r\n@yu-re-ka\r\n@kloenk\r\n\r\n### Metadata\r\n```console\r\n[lambdadog@taiga:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.33, NixOS, 22.05 (Quokka), 22.05pre368735.33772708c6d`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - channels(lambdadog): `\"nixpkgs-unstable\"`\r\n - channels(root): `\"musnix, nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nI did however explicitly use nixpkgs master for testing this, as so:\r\n```console\r\n[lambdadog@taiga:~]$ nix repl\r\nWelcome to Nix 2.8.0pre20220322_d5d4d98. Type :? for help.\r\n\r\nnix-repl> nixpkgs-pleroma = (fetchTarball https://github.com/NixOS/nixpkgs/archive/master.tar.gz)\r\n\r\nnix-repl> pkgs-pleroma = import nixpkgs-pleroma {} \r\n\r\nnix-repl> :u pkgs-pleroma.pleroma \r\nwarning: error: plugin-files set after plugins were loaded, you may need to move the flag before the subcommand\r\n\r\n[nix-shell:~]$ cd $(mktemp -d)\r\n\r\n[nix-shell:/run/user/1000/tmp.ZejW0ys6w5]$ pleroma_ctl instance gen --output config.exs --output-psql setup.psql\r\ncat: /nix/store/lxxn1n18k959n8l41fizbi6gqz515xf4-pleroma-2.4.2/releases/COOKIE: No such file or directory\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170805/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170803","id":1219136498,"node_id":"I_kwDOAEVQ_M5Iqovy","number":170803,"title":"nixos.tests.boot.biosUsb.x86_64-linux fails on hydra: \"cpage out of range (5)\"","user":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"},{"id":1674220329,"node_id":"MDU6TGFiZWwxNjc0MjIwMzI5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20channel%20blocker","name":"1.severity: channel blocker","color":"e11d21","default":false,"description":"Blocks a channel"},{"id":3536622080,"node_id":"LA_kwDOAEVQ_M7SzJIA","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20build%20failure","name":"0.kind: build failure","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-28T18:51:19Z","updated_at":"2022-04-30T08:22:18Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"https://hydra.nixos.org/build/174964149\r\n\r\n```\r\nmachine # Booting from Hard Disk...\r\nmachine # \r\nmachine # ISOLINUX 6.04 EHDD Copyright (C) 1994-2015 H. Peter Anvin et a\r\nmachine # ISOLINUX 6.04 Copyright (C) 1994-2015 H. Peter Anvin et al\r\nmachine # l\r\nmachine # e%@)0(B\u000elqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqkx\u000f NixOS \u000extqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu\u000f\u000ex\u000f NixOS 22.05pre-git Installer \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (nomodeset) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (copytoram) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (debug) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (serial console=ttyS0,115200n8) \u000ex\u000f\u000ex\u000f Memtest86+ \u000ex\u000f\u000emqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj\u000fPress [Tab] to edit optionsAutomatic boot in 10 seconds... Automatic boot in 9 seconds... Automatic boot in 8 seconds...Automatic boot in 7 seconds...Automatic boot in 6 seconds...Automatic boot in 5 seconds...Automatic boot in 4 seconds...Automatic boot in 3 seconds...Automatic boot in 2 seconds... Automatic boot in 1 second... \u000elqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqkx\u000f NixOS \u000extqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu\u000f\u000ex\u000f NixOS 22.05pre-git Installer \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (nomodeset) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (copytoram) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (debug) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (serial console=ttyS0,115200n8) \u000ex\u000f\u000ex\u000f Memtest86+ \u000ex\u000f\u000emqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj\u000fPress [Tab] to edit optionse%@)0(BLoading /boot/bzImage... cpage out of range (5)\r\nmachine # processing error - resetting ehci HC\r\nmachine # CHS: Error 0c00 reading sector 3058 (1/16/35)\r\nmachine # EDD: Error 0c00 reading sector 3058\r\nmachine # CHS: Error 0c00 reading sector 15543 (7/22/46)\r\nmachine # EDD: Error 0c00 reading sector 15543\r\nmachine # ok\r\nmachine # Loading /boot/initrd...CHS: Error 0c00 reading sector 70844 (35/4/33)\r\nmachine # EDD: Error 0c00 reading sector 70844\r\nmachine # CHS: Error 0c00 reading sector 96311 (47/24/48)\r\nmachine # EDD: Error 0c00 reading sector 96311\r\nmachine # ok\r\nmachine: connected to guest root shell\r\nmachine: (connecting took 1017.66 seconds)\r\n(finished: waiting for the VM to finish booting, in 1017.66 seconds)\r\ncleanup\r\n(finished: cleanup, in 0.00 seconds)\r\nTraceback (most recent call last):\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/bin/.nixos-test-driver-wrapped\", line 9, in <module>\r\n sys.exit(main())\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/__init__.py\", line 114, in main\r\n driver.run_tests()\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/driver.py\", line 146, in run_tests\r\n self.test_script()\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/driver.py\", line 142, in test_script\r\n exec(self.tests, symbols, None)\r\n File \"<string>\", line 9, in <module>\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 459, in wait_for_unit\r\n retry(check_active)\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 126, in retry\r\n if fn(False):\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 436, in check_active\r\n info = self.get_unit_info(unit, user)\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 462, in get_unit_info\r\n status, lines = self.systemctl('--no-pager show \"{}\"'.format(unit), user)\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 493, in systemctl\r\n return self.execute(\"systemctl {}\".format(q))\r\n File \"/nix/store/7m0m07v3yhj81l2p1sbj8krlzximmd21-nixos-test-driver-1.1/lib/python3.9/site-packages/test_driver/machine.py\", line 541, in execute\r\n self.shell.send(out_command.encode())\r\nBrokenPipeError: [Errno 32] Broken pipe\r\nmachine # cProbing EDD (edd=off to disable)... oc\r\n```\r\n\r\nSpecifically:\r\n\r\n```\r\nLoading /boot/bzImage... cpage out of range (5)\r\n```\r\n\r\n\r\nFor comparison, a successful run loads bzImage successfully:\r\n\r\n```\r\nmachine # ISOLINUX 6.04 EHDD Copyright (C) 1994-2015 H. Peter Anvin et a\r\nmachine # ISOLINUX 6.04 Copyright (C) 1994-2015 H. Peter Anvin et al\r\nmachine # l\r\nmachine # e%@)0(B\u000elqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqkx\u000f NixOS \u000extqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu\u000f\u000ex\u000f NixOS 22.05pre-git Installer \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (nomodeset) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (copytoram) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (debug) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (serial console=ttyS0,115200n8) \u000ex\u000f\u000ex\u000f Memtest86+ \u000ex\u000f\u000emqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj\u000fPress [Tab] to edit optionsAutomatic boot in 10 seconds... Automatic boot in 9 seconds... Automatic boot in 8 seconds...Automatic boot in 7 seconds...Automatic boot in 6 seconds...Automatic boot in 5 seconds...Automatic boot in 4 seconds...Automatic boot in 3 seconds...Automatic boot in 2 seconds... Automatic boot in 1 second... \u000elqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqkx\u000f NixOS \u000extqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqu\u000f\u000ex\u000f NixOS 22.05pre-git Installer \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (nomodeset) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (copytoram) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (debug) \u000ex\u000f\u000ex\u000f NixOS 22.05pre-git Installer (serial console=ttyS0,115200n8) \u000ex\u000f\u000ex\u000f Memtest86+ \u000ex\u000f\u000emqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqj\u000fPress [Tab] to edit optionse%@)0(BLoading /boot/bzImage... ok\r\nmachine # Loading /boot/initrd...ok\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170803/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170796","id":1219062787,"node_id":"I_kwDOAEVQ_M5IqWwD","number":170796,"title":"pycapnp broken on master (and hydra)","user":{"login":"dtzWill","id":817330,"node_id":"MDQ6VXNlcjgxNzMzMA==","avatar_url":"https://avatars.githubusercontent.com/u/817330?v=4","gravatar_id":"","url":"https://api.github.com/users/dtzWill","html_url":"https://github.com/dtzWill","followers_url":"https://api.github.com/users/dtzWill/followers","following_url":"https://api.github.com/users/dtzWill/following{/other_user}","gists_url":"https://api.github.com/users/dtzWill/gists{/gist_id}","starred_url":"https://api.github.com/users/dtzWill/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dtzWill/subscriptions","organizations_url":"https://api.github.com/users/dtzWill/orgs","repos_url":"https://api.github.com/users/dtzWill/repos","events_url":"https://api.github.com/users/dtzWill/events{/privacy}","received_events_url":"https://api.github.com/users/dtzWill/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-28T17:40:02Z","updated_at":"2022-04-30T03:33:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\npycapnp on latest master is now broken.\r\n\r\nApologies I'm short on time. Hydra shows the failure:\r\n\r\nhttps://hydra.nixos.org/job/nixos/trunk-combined/nixpkgs.python310Packages.pycapnp.x86_64-linux","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170796/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170791","id":1218930527,"node_id":"I_kwDOAEVQ_M5Ip2df","number":170791,"title":"Packaging request: remote / remote-exec","user":{"login":"pbsds","id":140964,"node_id":"MDQ6VXNlcjE0MDk2NA==","avatar_url":"https://avatars.githubusercontent.com/u/140964?v=4","gravatar_id":"","url":"https://api.github.com/users/pbsds","html_url":"https://github.com/pbsds","followers_url":"https://api.github.com/users/pbsds/followers","following_url":"https://api.github.com/users/pbsds/following{/other_user}","gists_url":"https://api.github.com/users/pbsds/gists{/gist_id}","starred_url":"https://api.github.com/users/pbsds/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pbsds/subscriptions","organizations_url":"https://api.github.com/users/pbsds/orgs","repos_url":"https://api.github.com/users/pbsds/repos","events_url":"https://api.github.com/users/pbsds/events{/privacy}","received_events_url":"https://api.github.com/users/pbsds/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T15:49:23Z","updated_at":"2022-04-28T15:49:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nThe `remote` CLI lets you execute long or computation-heavy tasks (e.g., compilation, integration tests, etc.) on a powerful remote host while you work on the source code locally. This process is known as remote execution and can enable remote build capabilities, among other things.\r\n\r\nWhen you execute `remote <cmd>`, it will first sync your local workspace to the remote host you selected using `rsync`. It will then execute the command `<cmd>` on this host using `ssh` and finally, bring all the created/modified files back to your local workspace. `remote` supports a host of configuration options to allow for complete customization of patterns for files and folders to include during the synchronization process in both directions.\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://pypi.org/project/remote-exec/\r\n* source URL: https://github.com/remote-cli/remote\r\n* license: bsd2\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170791/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170790","id":1218927591,"node_id":"I_kwDOAEVQ_M5Ip1vn","number":170790,"title":"Minizinc IDE cannot start due to Qt error","user":{"login":"volisoft","id":6010868,"node_id":"MDQ6VXNlcjYwMTA4Njg=","avatar_url":"https://avatars.githubusercontent.com/u/6010868?v=4","gravatar_id":"","url":"https://api.github.com/users/volisoft","html_url":"https://github.com/volisoft","followers_url":"https://api.github.com/users/volisoft/followers","following_url":"https://api.github.com/users/volisoft/following{/other_user}","gists_url":"https://api.github.com/users/volisoft/gists{/gist_id}","starred_url":"https://api.github.com/users/volisoft/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/volisoft/subscriptions","organizations_url":"https://api.github.com/users/volisoft/orgs","repos_url":"https://api.github.com/users/volisoft/repos","events_url":"https://api.github.com/users/volisoft/events{/privacy}","received_events_url":"https://api.github.com/users/volisoft/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T15:47:18Z","updated_at":"2022-04-28T16:40:56Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nMinizinc IDE could not be started throwing the following error:\r\n```console\r\n$ MiniZincIDE \r\nqt.qpa.plugin: Could not find the Qt platform plugin \"xcb\" in \"\"\r\nThis application failed to start because no Qt platform plugin could be initialized. Reinstalling the application may fix this problem.\r\n\r\nAborted (core dumped)\r\n```\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `MiniZincIDE` in terminal\r\n\r\n### Expected behavior\r\nAn application window is displayed.\r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@dtzWill @ttuegel \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - channels(root): `\"nixos-22.05pre338578.a2e281f5770\"`\r\n - channels(dev): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n\r\n```console\r\n$ echo $PATH\r\n/run/wrappers/bin:/home/dev/.nix-profile/bin:/etc/profiles/per-user/dev/bin:/nix/var/nix/profiles/default/bin:/run/current-system/sw/bin:/home/dev/.config/.emacs.d/bin\r\n$ echo $QT_PLUGIN_PATH \r\n/home/dev/.nix-profile/lib/qt4/plugins:/home/dev/.nix-profile/lib/kde4/plugins:/etc/profiles/per-user/dev/lib/qt4/plugins:/etc/profiles/per-user/dev/lib/kde4/plugins:/nix/var/nix/profiles/default/lib/qt4/plugins:/nix/var/nix/profiles/default/lib/kde4/plugins:/run/current-system/sw/lib/qt4/plugins:/run/current-system/sw/lib/kde4/plugins\r\n```\r\nDesktop manager: Xfce\r\nDisplay manager: lightdm\r\nWindow manager: i3","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170790/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170784","id":1218823445,"node_id":"I_kwDOAEVQ_M5IpcUV","number":170784,"title":"Firejail default whitelist .nix-profile","user":{"login":"onny","id":757752,"node_id":"MDQ6VXNlcjc1Nzc1Mg==","avatar_url":"https://avatars.githubusercontent.com/u/757752?v=4","gravatar_id":"","url":"https://api.github.com/users/onny","html_url":"https://github.com/onny","followers_url":"https://api.github.com/users/onny/followers","following_url":"https://api.github.com/users/onny/following{/other_user}","gists_url":"https://api.github.com/users/onny/gists{/gist_id}","starred_url":"https://api.github.com/users/onny/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/onny/subscriptions","organizations_url":"https://api.github.com/users/onny/orgs","repos_url":"https://api.github.com/users/onny/repos","events_url":"https://api.github.com/users/onny/events{/privacy}","received_events_url":"https://api.github.com/users/onny/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T14:32:22Z","updated_at":"2022-04-28T17:39:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nRunning a application with firejail should just work with `firejail chromium` but it doesn't on NixOS. It fails with:\r\n```\r\nError: no suitable chromium executable found\r\n```\r\n\r\nThis is because `chromium` is a symlink in \r\n```\r\n$ which chromium\r\n/home/onny/.nix-profile/bin/chromium\r\n```\r\n\r\nThis can be fixed by whitelisting this directory, so this command works:\r\n```\r\n$ firejail --whitelist=/home/onny/.nix-profile chromium\r\n``` \r\n\r\nIt is really not easy to figure this out. Would it be better to whitelist this directory by default?\r\n\r\n@raskin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170784/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170777","id":1218737217,"node_id":"I_kwDOAEVQ_M5IpHRB","number":170777,"title":"awscli2: Not building on unstable (x86_64)","user":{"login":"WolfangAukang","id":8378365,"node_id":"MDQ6VXNlcjgzNzgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/8378365?v=4","gravatar_id":"","url":"https://api.github.com/users/WolfangAukang","html_url":"https://github.com/WolfangAukang","followers_url":"https://api.github.com/users/WolfangAukang/followers","following_url":"https://api.github.com/users/WolfangAukang/following{/other_user}","gists_url":"https://api.github.com/users/WolfangAukang/gists{/gist_id}","starred_url":"https://api.github.com/users/WolfangAukang/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/WolfangAukang/subscriptions","organizations_url":"https://api.github.com/users/WolfangAukang/orgs","repos_url":"https://api.github.com/users/WolfangAukang/repos","events_url":"https://api.github.com/users/WolfangAukang/events{/privacy}","received_events_url":"https://api.github.com/users/WolfangAukang/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-28T13:32:36Z","updated_at":"2022-04-29T22:00:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTrying to build my configuration file. It contains `awscli2`. I'm getting the following issue:\r\n```\r\nerror: builder for '/nix/store/dkc8f19bwhawl042qr6ngpbf4kh8qdbj-python3.9-awscrt-0.12.4.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > super().run_command(command)\r\n > File \"/nix/store/xi8ha1k3mjpmnmmi5fp7fmq41f2wwghm-python3.9-setuptools-61.2.0/lib/python3.9/site-packages/setuptools/_distutils/dist.py\", line 986, in run_command\r\n > cmd_obj.run()\r\n > File \"setup.py\", line 208, in run\r\n > self._build_dependency(lib)\r\n > File \"setup.py\", line 201, in _build_dependency\r\n > subprocess.check_call(build_cmd)\r\n > File \"/nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/lib/python3.9/subprocess.py\", line 373, in check_call\r\n > raise CalledProcessError(retcode, cmd)\r\n > subprocess.CalledProcessError: Command '['/nix/store/28lglq8yh2d19dq3rfsksrzijc5yljrl-cmake-3.22.3/bin/cmake', '--build', './', '--config', 'RelWithDebInfo', '--target', 'install', '--parallel', '12']' returned non-zero exit status 2.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `nixos-rebuild` test\r\n\r\n### Expected behavior\r\nNo errors when building\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nUsing flakes and using nixos-unstable.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@bhipple @davegallant \r\n\r\n### Metadata\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"nixos-21.11, old-nixos-21.05\"`\r\n - channels(bjorn): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170777/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170773","id":1218669070,"node_id":"I_kwDOAEVQ_M5Io2oO","number":170773,"title":"Wavebox needs a version upgrade to 10.x from 4.x","user":{"login":"kciredor","id":1121650,"node_id":"MDQ6VXNlcjExMjE2NTA=","avatar_url":"https://avatars.githubusercontent.com/u/1121650?v=4","gravatar_id":"","url":"https://api.github.com/users/kciredor","html_url":"https://github.com/kciredor","followers_url":"https://api.github.com/users/kciredor/followers","following_url":"https://api.github.com/users/kciredor/following{/other_user}","gists_url":"https://api.github.com/users/kciredor/gists{/gist_id}","starred_url":"https://api.github.com/users/kciredor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kciredor/subscriptions","organizations_url":"https://api.github.com/users/kciredor/orgs","repos_url":"https://api.github.com/users/kciredor/repos","events_url":"https://api.github.com/users/kciredor/events{/privacy}","received_events_url":"https://api.github.com/users/kciredor/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T12:38:59Z","updated_at":"2022-04-28T12:38:59Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n###### Project name\r\n`nix search` name: wavebox\r\ncurrent version: 4.11.3\r\ndesired version: 10.101.9-2\r\n\r\n###### Notify maintainers\r\nmaintainers: @r-ryantm\r\n\r\n###### Note for maintainers\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170773/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170767","id":1218582247,"node_id":"I_kwDOAEVQ_M5Iohbn","number":170767,"title":"paperless-ngx 1.7.0","user":{"login":"alarsyo","id":15170378,"node_id":"MDQ6VXNlcjE1MTcwMzc4","avatar_url":"https://avatars.githubusercontent.com/u/15170378?v=4","gravatar_id":"","url":"https://api.github.com/users/alarsyo","html_url":"https://github.com/alarsyo","followers_url":"https://api.github.com/users/alarsyo/followers","following_url":"https://api.github.com/users/alarsyo/following{/other_user}","gists_url":"https://api.github.com/users/alarsyo/gists{/gist_id}","starred_url":"https://api.github.com/users/alarsyo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alarsyo/subscriptions","organizations_url":"https://api.github.com/users/alarsyo/orgs","repos_url":"https://api.github.com/users/alarsyo/repos","events_url":"https://api.github.com/users/alarsyo/events{/privacy}","received_events_url":"https://api.github.com/users/alarsyo/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-28T11:21:57Z","updated_at":"2022-04-28T13:54:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: `paperless-ngx`\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.6.0\r\ndesired version: 1.7.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @lukegb @erikarvstedt \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170767/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170761","id":1218523663,"node_id":"I_kwDOAEVQ_M5IoTIP","number":170761,"title":"Add support for Thaoma2d","user":{"login":"leiserfg","id":2947276,"node_id":"MDQ6VXNlcjI5NDcyNzY=","avatar_url":"https://avatars.githubusercontent.com/u/2947276?v=4","gravatar_id":"","url":"https://api.github.com/users/leiserfg","html_url":"https://github.com/leiserfg","followers_url":"https://api.github.com/users/leiserfg/followers","following_url":"https://api.github.com/users/leiserfg/following{/other_user}","gists_url":"https://api.github.com/users/leiserfg/gists{/gist_id}","starred_url":"https://api.github.com/users/leiserfg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/leiserfg/subscriptions","organizations_url":"https://api.github.com/users/leiserfg/orgs","repos_url":"https://api.github.com/users/leiserfg/repos","events_url":"https://api.github.com/users/leiserfg/events{/privacy}","received_events_url":"https://api.github.com/users/leiserfg/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T10:26:40Z","updated_at":"2022-04-28T10:26:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nThaoma2d is a fork of opentoonz\r\n**Metadata**\r\n\r\n* homepage URL: https://tahoma2d.org/\r\n* source URL: https://github.com/tahoma2d/tahoma2d\r\n* license: BSD 3-Clause\r\n* platforms: UNIX\r\n\r\nI'm tagging @chkno 'cause as the maintainer of opentooz, should be easier for him to do it.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170761/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170755","id":1218473106,"node_id":"I_kwDOAEVQ_M5IoGyS","number":170755,"title":"Packaging requests: pydeps","user":{"login":"pbsds","id":140964,"node_id":"MDQ6VXNlcjE0MDk2NA==","avatar_url":"https://avatars.githubusercontent.com/u/140964?v=4","gravatar_id":"","url":"https://api.github.com/users/pbsds","html_url":"https://github.com/pbsds","followers_url":"https://api.github.com/users/pbsds/followers","following_url":"https://api.github.com/users/pbsds/following{/other_user}","gists_url":"https://api.github.com/users/pbsds/gists{/gist_id}","starred_url":"https://api.github.com/users/pbsds/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pbsds/subscriptions","organizations_url":"https://api.github.com/users/pbsds/orgs","repos_url":"https://api.github.com/users/pbsds/repos","events_url":"https://api.github.com/users/pbsds/events{/privacy}","received_events_url":"https://api.github.com/users/pbsds/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-28T09:44:35Z","updated_at":"2022-04-28T16:38:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nPython module dependency visualization.\r\nGiven a python project it can produce a graph of the dependencies, exported in the graphviz dot language.\r\n\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/thebjorn/pydeps\r\n* source URL: https://github.com/thebjorn/pydeps\r\n* license: bsd2\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170755/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170747","id":1218374141,"node_id":"I_kwDOAEVQ_M5Inun9","number":170747,"title":"Please add jupyterlab as tool","user":{"login":"schlichtanders","id":4255480,"node_id":"MDQ6VXNlcjQyNTU0ODA=","avatar_url":"https://avatars.githubusercontent.com/u/4255480?v=4","gravatar_id":"","url":"https://api.github.com/users/schlichtanders","html_url":"https://github.com/schlichtanders","followers_url":"https://api.github.com/users/schlichtanders/followers","following_url":"https://api.github.com/users/schlichtanders/following{/other_user}","gists_url":"https://api.github.com/users/schlichtanders/gists{/gist_id}","starred_url":"https://api.github.com/users/schlichtanders/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schlichtanders/subscriptions","organizations_url":"https://api.github.com/users/schlichtanders/orgs","repos_url":"https://api.github.com/users/schlichtanders/repos","events_url":"https://api.github.com/users/schlichtanders/events{/privacy}","received_events_url":"https://api.github.com/users/schlichtanders/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-28T08:20:56Z","updated_at":"2022-04-28T17:08:01Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nWhile jupyterlab is available as a python package (`python39Packages.jupyterlab` and `python38Packages.jupyterlab` as of today), there is no respective app to be found in nixpkgs (like I would expect `jupyterlab`).\r\n\r\nWhat can be found is `jupyter`, which however seems to point to the notebook and not the lab.\r\n\r\nJupyterlab is a Web-Based development environment for interactive use for multiple languages. It is widespread, has probably millions of users and would be nice to have packaged in nixpks.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://jupyterlab.readthedocs.io/en/stable/\r\n* source URL: https://github.com/jupyterlab/jupyterlab\r\n* license: a revised bsd license\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170747/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170720","id":1218126838,"node_id":"I_kwDOAEVQ_M5ImyP2","number":170720,"title":"nextcloud: nextcloud-setup.service fails to enable enabled apps","user":{"login":"arnottcr","id":2526260,"node_id":"MDQ6VXNlcjI1MjYyNjA=","avatar_url":"https://avatars.githubusercontent.com/u/2526260?v=4","gravatar_id":"","url":"https://api.github.com/users/arnottcr","html_url":"https://github.com/arnottcr","followers_url":"https://api.github.com/users/arnottcr/followers","following_url":"https://api.github.com/users/arnottcr/following{/other_user}","gists_url":"https://api.github.com/users/arnottcr/gists{/gist_id}","starred_url":"https://api.github.com/users/arnottcr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/arnottcr/subscriptions","organizations_url":"https://api.github.com/users/arnottcr/orgs","repos_url":"https://api.github.com/users/arnottcr/repos","events_url":"https://api.github.com/users/arnottcr/events{/privacy}","received_events_url":"https://api.github.com/users/arnottcr/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-28T03:06:09Z","updated_at":"2022-04-30T03:46:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\nthe `nextcloud-setup.service` script is failing on [the second to last line](https://github.com/NixOS/nixpkgs/blob/a3917caedfead19f853aa5769de4c3ea4e4db584/nixos/modules/services/web-apps/nextcloud.nix#L766). it appears that despite [the comment](https://github.com/NixOS/nixpkgs/blob/a3917caedfead19f853aa5769de4c3ea4e4db584/nixos/modules/services/web-apps/nextcloud.nix#L765), we actually are \"fail[ing] when one of them cannot be enabled\".\r\n\r\n### Steps to reproduce\r\n\r\nhave `services.nextcloud.extraApps` configured, e.g.\r\n```nix\r\n{config, lib, pkgs, ...}: {\r\n services.nextcloud.extraApps.spreed = pkgs.fetchNextcloudApp {\r\n name = \"spreed\";\r\n sha256 = \"sha256-566oKMVRBjaZ69Ntg4zC7rjW01u0GF4RT4vJnzIl2Zk=\";\r\n url = \"https://github.com/nextcloud-releases/spreed/releases/download/v13.0.5/spreed-v13.0.5.tar.gz\";\r\n version = \"13.0.5\";\r\n };\r\n}\r\n```\r\nmake a change, like a new version, that triggers an upgrade [recte `nextcloud-setup.service`]. run `nixos-rebuild switch`, and see that the configuration change took place, but that the service run failed:\r\n```\r\nwarning: the following units failed: nextcloud-setup.service\r\n\r\n× nextcloud-setup.service\r\n Loaded: loaded (/etc/systemd/system/nextcloud-setup.service; enabled; vendor preset: enabled)\r\n Active: failed (Result: exit-code) since Thu 2022-04-28 01:47:19 UTC; 44ms ago\r\n Process: 453410 ExecStart=/nix/store/385yp1x94zykg4h0k6rzk8486aqqzmy3-unit-script-nextcloud-setup-start/bin/nextcloud-setup-start (code=exited, status=1/FAILURE)\r\n Main PID: 453410 (code=exited, status=1/FAILURE)\r\n IP: 0B in, 0B out\r\n CPU: 7.002s\r\n\r\nApr 28 01:47:19 localhost nextcloud-setup-start[453484]: spreed already enabled\r\nApr 28 01:47:19 localhost systemd[1]: nextcloud-setup.service: Main process exited, code=exited, status=1/FAILURE\r\nApr 28 01:47:19 localhost systemd[1]: nextcloud-setup.service: Failed with result 'exit-code'.\r\nApr 28 01:47:19 localhost systemd[1]: Failed to start nextcloud-setup.service.\r\nApr 28 01:47:19 localhost systemd[1]: nextcloud-setup.service: Consumed 7.002s CPU time, no IP traffic.\r\nwarning: error(s) occurred while switching to the new configuration\r\n```\r\n\r\n## Possible fixes\r\n\r\nIt seems like running `nextcloud-occ app:enable ... || true` or `nextcloud-occ app:enable --force ...`, such that we are actually ignoring the failures would resolve this, but I am unclear on the implications of the `--force` flag: \"enable the app regardless of the Nextcloud version requirement\".\r\n\r\n## Technical details\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.107, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170720/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170719","id":1218118251,"node_id":"I_kwDOAEVQ_M5ImwJr","number":170719,"title":"nextcloud: extraApps url file caching error","user":{"login":"arnottcr","id":2526260,"node_id":"MDQ6VXNlcjI1MjYyNjA=","avatar_url":"https://avatars.githubusercontent.com/u/2526260?v=4","gravatar_id":"","url":"https://api.github.com/users/arnottcr","html_url":"https://github.com/arnottcr","followers_url":"https://api.github.com/users/arnottcr/followers","following_url":"https://api.github.com/users/arnottcr/following{/other_user}","gists_url":"https://api.github.com/users/arnottcr/gists{/gist_id}","starred_url":"https://api.github.com/users/arnottcr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/arnottcr/subscriptions","organizations_url":"https://api.github.com/users/arnottcr/orgs","repos_url":"https://api.github.com/users/arnottcr/repos","events_url":"https://api.github.com/users/arnottcr/events{/privacy}","received_events_url":"https://api.github.com/users/arnottcr/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-28T02:53:56Z","updated_at":"2022-04-29T00:16:16Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\nwhen updating the version of several `services.nextcloud.extraApps` I changed `url` and `version`, but not `sha256`, and `nixos-rebuild switch`[0] actually worked, but used the old `.tar.gz` file.\r\n\r\nmy best guess is that because `https://github.com/nextcloud/polls/releases/download/v3.6.1/polls.tar.gz` and `https://github.com/nextcloud/polls/releases/download/v3.6.0/polls.tar.gz` both contain the same `polls.tar.gz` file, that some caching or validation is just looking at the file name? and because other apps use the version in the `url`, e.g. `https://github.com/nextcloud-releases/contacts/releases/download/v4.1.0/contacts-v4.1.0.tar.gz`, this only affects some apps.\r\n\r\n0] specifically `nixos-rebuild --verbose --target-host root@remotehost --flake './dir#thing' switch`\r\n\r\n\r\n### Steps to reproduce\r\n\r\nhave a `services.nextcloud.extraApps` entry that contains an app with a generic `.tar.gz` name, e.g.\r\n```nix\r\n{config, lib, pkgs, ...}: {\r\n services.nextcloud.extraApps.polls = pkgs.fetchNextcloudApp {\r\n name = \"polls\";\r\n sha256 = \"sha256-32w8kx2eS+TpsH4kjGym5JWDjG2h9kX3kEVpfOfUDjQ=\";\r\n url = \"https://github.com/nextcloud/polls/releases/download/v3.6.1/polls.tar.gz\";\r\n version = \"3.6.1\";\r\n };\r\n}\r\n```\r\nupgrade to the new version, say 3.6.2, and do not change the `sha256`, e.g.\r\n```nix\r\n{config, lib, pkgs, ...}: {\r\n services.nextcloud.extraApps.polls = pkgs.fetchNextcloudApp {\r\n name = \"polls\";\r\n sha256 = \"sha256-32w8kx2eS+TpsH4kjGym5JWDjG2h9kX3kEVpfOfUDjQ=\";\r\n url = \"https://github.com/nextcloud/polls/releases/download/v3.6.2/polls.tar.gz\";\r\n version = \"3.6.2\";\r\n };\r\n}\r\n```\r\nnow run `nixos-rebuild switch`. we would expect this to fail, with a `sha256` got/want error message, since `https://github.com/nextcloud/polls/releases/download/v3.6.1/polls.tar.gz` and `https://github.com/nextcloud/polls/releases/download/v3.6.2/polls.tar.gz` are not the same file, but it succeeds.\r\n\r\n## Technical details\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1-arch1-1, Arch Linux, noversion, rolling`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(user): `\"nixpkgs\"`\r\n - nixpkgs: `/home/user/.nix-defexpr/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170719/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170658","id":1217745702,"node_id":"I_kwDOAEVQ_M5IlVMm","number":170658,"title":"coccinelle 1.1.1","user":{"login":"armijnhemel","id":10587952,"node_id":"MDQ6VXNlcjEwNTg3OTUy","avatar_url":"https://avatars.githubusercontent.com/u/10587952?v=4","gravatar_id":"","url":"https://api.github.com/users/armijnhemel","html_url":"https://github.com/armijnhemel","followers_url":"https://api.github.com/users/armijnhemel/followers","following_url":"https://api.github.com/users/armijnhemel/following{/other_user}","gists_url":"https://api.github.com/users/armijnhemel/gists{/gist_id}","starred_url":"https://api.github.com/users/armijnhemel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armijnhemel/subscriptions","organizations_url":"https://api.github.com/users/armijnhemel/orgs","repos_url":"https://api.github.com/users/armijnhemel/repos","events_url":"https://api.github.com/users/armijnhemel/events{/privacy}","received_events_url":"https://api.github.com/users/armijnhemel/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T18:41:59Z","updated_at":"2022-04-27T18:41:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [X] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [X] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.1.0\r\ndesired version: 1.1.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers:\r\n\r\n@thoughtpolice \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\nThe version number displayed in `spatch --version` needs to be checked. In the current version I see this:\r\n\r\n```\r\n$ spatch --version\r\nspatch version 1.0.8-00205-gd3d29c86 compiled with OCaml version 4.13.1\r\nFlags passed to the configure script: --disable-dependency-tracking --prefix=/nix/store/5dp4a9070yvywskk7xqcxm3x45h6xigj-coccinelle-1.1.0\r\n```\r\nIt seems that `cvehound` uses this output to verify the version of `spatch` that it needs.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170658/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170656","id":1217726932,"node_id":"I_kwDOAEVQ_M5IlQnU","number":170656,"title":"cvehound","user":{"login":"armijnhemel","id":10587952,"node_id":"MDQ6VXNlcjEwNTg3OTUy","avatar_url":"https://avatars.githubusercontent.com/u/10587952?v=4","gravatar_id":"","url":"https://api.github.com/users/armijnhemel","html_url":"https://github.com/armijnhemel","followers_url":"https://api.github.com/users/armijnhemel/followers","following_url":"https://api.github.com/users/armijnhemel/following{/other_user}","gists_url":"https://api.github.com/users/armijnhemel/gists{/gist_id}","starred_url":"https://api.github.com/users/armijnhemel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armijnhemel/subscriptions","organizations_url":"https://api.github.com/users/armijnhemel/orgs","repos_url":"https://api.github.com/users/armijnhemel/repos","events_url":"https://api.github.com/users/armijnhemel/events{/privacy}","received_events_url":"https://api.github.com/users/armijnhemel/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T18:22:51Z","updated_at":"2022-04-27T18:22:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\ncvehound\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.0.4\r\ndesired version: 1.0.9\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers:\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170656/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170640","id":1217490988,"node_id":"I_kwDOAEVQ_M5IkXAs","number":170640,"title":"topgrade fails to build on darwin x86_64","user":{"login":"duckpuppy","id":19253,"node_id":"MDQ6VXNlcjE5MjUz","avatar_url":"https://avatars.githubusercontent.com/u/19253?v=4","gravatar_id":"","url":"https://api.github.com/users/duckpuppy","html_url":"https://github.com/duckpuppy","followers_url":"https://api.github.com/users/duckpuppy/followers","following_url":"https://api.github.com/users/duckpuppy/following{/other_user}","gists_url":"https://api.github.com/users/duckpuppy/gists{/gist_id}","starred_url":"https://api.github.com/users/duckpuppy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/duckpuppy/subscriptions","organizations_url":"https://api.github.com/users/duckpuppy/orgs","repos_url":"https://api.github.com/users/duckpuppy/repos","events_url":"https://api.github.com/users/duckpuppy/events{/privacy}","received_events_url":"https://api.github.com/users/duckpuppy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-04-27T15:05:16Z","updated_at":"2022-04-29T17:31:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nBuilding topgrade fails with an error on x86_64 darwin.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-build --attr topgrade\r\n\r\n### Expected behavior\r\ntopgrade builds successfully\r\n\r\n### Additional context\r\nBuild logs:\r\n\r\n```\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/667x95nwc4b9ldgkzjzpdkqqxzzjaxjn-source\r\nsource root is source\r\nExecuting cargoSetupPostUnpackHook\r\nunpacking source archive /nix/store/bjifswgnd6w1w3ap03v7aw0fgg07kk8v-topgrade-8.3.0-vendor.tar.gz\r\nFinished cargoSetupPostUnpackHook\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\nExecuting cargoSetupPostPatchHook\r\nValidating consistency between /private/tmp/nix-build-topgrade-8.3.0.drv-0/source//Cargo.lock and /private/tmp/nix-build-topgrade-8.3.0.drv-0/topgrade-8.3.0-vendor.tar.gz/Cargo.lock\r\nFinished cargoSetupPostPatchHook\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nExecuting cargoBuildHook\r\n++ env CC_x86_64-apple-darwin=/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc CXX_x86_64-apple-darwin=/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/c++ CC_x86_64-apple-darwin=/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc CXX_x86_64-apple-darwin=/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/c++ cargo build -j 12 --target x86_64-apple-darwin --frozen --release\r\n Compiling libc v0.2.121\r\n Compiling proc-macro2 v1.0.36\r\n Compiling unicode-xid v0.2.2\r\n Compiling syn v1.0.89\r\n Compiling cfg-if v1.0.0\r\n Compiling autocfg v1.1.0\r\n Compiling memchr v2.4.1\r\n Compiling cc v1.0.73\r\n Compiling version_check v0.9.4\r\n Compiling futures-core v0.3.21\r\n Compiling log v0.4.16\r\n Compiling futures-task v0.3.21\r\n Compiling unicode-segmentation v1.9.0\r\n Compiling futures-channel v0.3.21\r\n Compiling serde_derive v1.0.136\r\n Compiling unicode-width v0.1.9\r\n Compiling rustversion v1.0.6\r\n Compiling futures-util v0.3.21\r\n Compiling regex-syntax v0.6.25\r\n Compiling pin-project-lite v0.2.8\r\n Compiling futures-sink v0.3.21\r\n Compiling pin-utils v0.1.0\r\n Compiling block v0.1.6\r\n Compiling futures-io v0.3.21\r\n Compiling quick-error v1.2.3\r\n Compiling bitflags v1.3.2\r\n Compiling slab v0.4.5\r\n Compiling serde v1.0.136\r\n Compiling once_cell v1.10.0\r\n Compiling anyhow v1.0.56\r\n Compiling termcolor v1.1.3\r\n Compiling strsim v0.8.0\r\n Compiling ansi_term v0.12.1\r\n Compiling vec_map v0.8.2\r\n Compiling lazy_static v1.4.0\r\n Compiling topgrade v8.3.0 (/private/tmp/nix-build-topgrade-8.3.0.drv-0/source)\r\n Compiling bytes v1.1.0\r\n Compiling same-file v1.0.6\r\n Compiling either v1.6.1\r\n Compiling remove_dir_all v0.5.3\r\n Compiling fastrand v1.7.0\r\n Compiling glob v0.3.0\r\n Compiling proc-macro-error-attr v1.0.4\r\n Compiling proc-macro-error v1.0.4\r\n Compiling num-traits v0.2.14\r\n Compiling memoffset v0.6.5\r\n Compiling num-integer v0.1.44\r\n Compiling textwrap v0.11.0\r\n Compiling humantime v1.3.0\r\n Compiling heck v0.3.3\r\n Compiling walkdir v2.3.2\r\n Compiling sys-info v0.9.1\r\n Compiling mac-notification-sys v0.5.0\r\n Compiling aho-corasick v0.7.18\r\n Compiling quote v1.0.16\r\n Compiling regex v1.5.5\r\nThe following warnings were emitted during compilation:\r\n\r\nwarning: In file included from objc/notify.m:1:\r\nwarning: objc/notify.h:1:9: fatal error: 'Cocoa/Cocoa.h' file not found\r\nwarning: #import <Cocoa/Cocoa.h>\r\nwarning: ^~~~~~~~~~~~~~~\r\nwarning: 1 error generated.\r\n\r\nerror: failed to run custom build command for `mac-notification-sys v0.5.0`\r\n\r\nCaused by:\r\n process didn't exit successfully: `/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/release/build/mac-notification-sys-f385fad53602caf5/build-script-build` (exit status: 1)\r\n --- stdout\r\n TARGET = Some(\"x86_64-apple-darwin\")\r\n OPT_LEVEL = Some(\"3\")\r\n HOST = Some(\"x86_64-apple-darwin\")\r\n CC_x86_64-apple-darwin = Some(\"/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc\")\r\n CFLAGS_x86_64-apple-darwin = None\r\n CFLAGS_x86_64_apple_darwin = None\r\n HOST_CFLAGS = None\r\n CFLAGS = None\r\n CRATE_CC_NO_DEFAULTS = None\r\n DEBUG = Some(\"false\")\r\n CARGO_CFG_TARGET_FEATURE = Some(\"fxsr,sse,sse2,sse3,ssse3\")\r\n running: \"/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc\" \"-O3\" \"-ffunction-sections\" \"-fdata-sections\" \"-fPIC\" \"-m64\" \"-arch\" \"x86_64\" \"-fmodules\" \"-o\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/build/mac-notification-sys-25faa2b2f656e3c3/out/objc/notify.o\" \"-c\" \"objc/notify.m\"\r\n cargo:warning=In file included from objc/notify.m:1:\r\n cargo:warning=objc/notify.h:1:9: fatal error: 'Cocoa/Cocoa.h' file not found\r\n cargo:warning=#import <Cocoa/Cocoa.h>\r\n cargo:warning= ^~~~~~~~~~~~~~~\r\n cargo:warning=1 error generated.\r\n exit status: 1\r\n\r\n --- stderr\r\n\r\n\r\n error occurred: Command \"/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc\" \"-O3\" \"-ffunction-sections\" \"-fdata-sections\" \"-fPIC\" \"-m64\" \"-arch\" \"x86_64\" \"-fmodules\" \"-o\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/build/mac-notification-sys-25faa2b2f656e3c3/out/objc/notify.o\" \"-c\" \"objc/notify.m\" with args \"cc\" did not execute successfully (status code exit status: 1).\r\n\r\n\r\nwarning: build failed, waiting for other jobs to finish...\r\nerror: build failed\r\n```\r\n\r\nI did try to override the derivation using:\r\n```\r\n (self: super: {\r\n topgrade = super.topgrade.overrideAttrs\r\n (oldAttrs: {\r\n buildInputs = lib.optionals pkgs.stdenv.isDarwin\r\n (with pkgs.darwin.apple_sdk.frameworks; [ Foundation Cocoa ]);\r\n });\r\n })\r\n```\r\nThis allowed me to get past the error above (missing `Cocoa.h`), but then I ran into errors linking `libiconv`. I added `libiconvReal` to the `buildInputs` line, and got past that error - but that led to yet another error.\r\n\r\n```\r\nerror: linking with `/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc` failed: exit status: 1\r\n |\r\n = note: \"/nix/store/jnm93vsz7i25zby30d4z7wwrzqbsakdj-clang-wrapper-11.1.0/bin/cc\" \"-m64\" \"-arch\" \"x86_64\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/deps/topgrade-f02d26e18ee8917a.topgrade.ec14c5ea-cgu.7.rcgu.o\" \"-L\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/deps\" \"-L\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/release/deps\" \"-L\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/build/mac-notification-sys-25faa2b2f656e3c3/out\" \"-L\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/build/sys-info-ec3119b17d6c41e1/out\" \"-L\" \"/nix/store/wxg7gf0y8wgb6jmm18b7c5hfmx0gzi9n-rustc-1.60.0/lib/rustlib/x86_64-apple-darwin/lib\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/rustcj4vczc/libmac_notification_sys-5301132a40728390.rlib\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/rustcj4vczc/libsys_info-124ce347abda3c46.rlib\" \"/nix/store/wxg7gf0y8wgb6jmm18b7c5hfmx0gzi9n-rustc-1.60.0/lib/rustlib/x86_64-apple-darwin/lib/libcompiler_builtins-caab782057aac16e.rlib\" \"-framework\" \"Foundation\" \"-lSystem\" \"-lobjc\" \"-liconv\" \"-lSystem\" \"-lresolv\" \"-lc\" \"-lm\" \"-liconv\" \"-L\" \"/nix/store/wxg7gf0y8wgb6jmm18b7c5hfmx0gzi9n-rustc-1.60.0/lib/rustlib/x86_64-apple-darwin/lib\" \"-o\" \"/private/tmp/nix-build-topgrade-8.3.0.drv-0/source/target/x86_64-apple-darwin/release/deps/topgrade-f02d26e18ee8917a\" \"-Wl,-dead_strip\" \"-nodefaultlibs\"\r\n = note: Undefined symbols for architecture x86_64:\r\n \"_OBJC_CLASS_$_NSImage\", referenced from:\r\n objc-class-ref in libmac_notification_sys-5301132a40728390.rlib(notify.o)\r\n \"_LSCopyApplicationURLsForBundleIdentifier\", referenced from:\r\n _setApplication in libmac_notification_sys-5301132a40728390.rlib(notify.o)\r\n ld: symbol(s) not found for architecture x86_64\r\n clang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\n```\r\n\r\nAt this point, I'm at a loss on where to go to fix the build.\r\n\r\n### Notify maintainers\r\n@SuperSandro2000\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(paikens): `\"darwin, home-manager, nixpkgs-22.05pre372991.d9e593ed588, nur-duckpuppy, nur-gerschtli, nixos-21.05.4666.7bca80140fc, nixpkgs-master, unstable-22.05pre341453.ac169ec6371, nixpkgs-unstable-21.11pre299378.db6e089456c\"`\r\n - nixpkgs: `/Users/paikens/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170640/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170621","id":1217359804,"node_id":"I_kwDOAEVQ_M5Ij2-8","number":170621,"title":"emscriptenPackages.zlib is broken","user":{"login":"arximboldi","id":4521138,"node_id":"MDQ6VXNlcjQ1MjExMzg=","avatar_url":"https://avatars.githubusercontent.com/u/4521138?v=4","gravatar_id":"","url":"https://api.github.com/users/arximboldi","html_url":"https://github.com/arximboldi","followers_url":"https://api.github.com/users/arximboldi/followers","following_url":"https://api.github.com/users/arximboldi/following{/other_user}","gists_url":"https://api.github.com/users/arximboldi/gists{/gist_id}","starred_url":"https://api.github.com/users/arximboldi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/arximboldi/subscriptions","organizations_url":"https://api.github.com/users/arximboldi/orgs","repos_url":"https://api.github.com/users/arximboldi/repos","events_url":"https://api.github.com/users/arximboldi/events{/privacy}","received_events_url":"https://api.github.com/users/arximboldi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T13:26:11Z","updated_at":"2022-04-27T13:26:38Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nIt seems like since the upgrade to Emscripten 3, this has broken.\r\n\r\n### Steps To Reproduce\r\nTry use `emscriptenPackages.zlib`, you get error:\r\n```\r\ncache:INFO: generating system library: sysroot/lib/wasm32-emscripten/libstubs.a... (this will be cached in \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/cache/sysroot/lib/wasm32-emscripten/libstubs.a\" for subsequent builds)\r\nTraceback (most recent call last):\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/emcc.py\", line 3863, in <module>\r\n sys.exit(main(sys.argv))\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/emcc.py\", line 3856, in main\r\n ret = run(args)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/emcc.py\", line 1114, in run\r\n phase_calculate_system_libraries(state, linker_arguments, linker_inputs, newargs)\r\n File \"/nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/lib/python3.9/contextlib.py\", line 79, in inner\r\n return func(*args, **kwds)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/emcc.py\", line 2570, in phase_calculate_system_libraries\r\n extra_files_to_link += system_libs.calculate([f for _, f in sorted(linker_inputs)] + extra_files_to_link, forced=state.forced_stdlibs)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/system_libs.py\", line 1721, in calculate\r\n add_library('libstubs')\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/system_libs.py\", line 1681, in add_library\r\n libs_to_link.append((lib.get_link_flag(), need_whole_archive))\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/system_libs.py\", line 320, in get_link_flag\r\n fullpath = self.get_path()\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/system_libs.py\", line 312, in get_path\r\n return shared.Cache.get_lib(self.get_filename(), self.build)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/cache.py\", line 139, in get_lib\r\n return self.get(name, *args, **kwargs)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/cache.py\", line 167, in get\r\n creator(cachename)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/system_libs.py\", line 391, in build\r\n utils.safe_ensure_dirs(build_dir)\r\n File \"/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/tools/utils.py\", line 28, in safe_ensure_dirs\r\n os.makedirs(dirname, exist_ok=True)\r\n File \"/nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/lib/python3.9/os.py\", line 225, in makedirs\r\n mkdir(name, mode)\r\nPermissionError: [Errno 13] Permission denied: '/nix/store/lb30znn7ahijz2mhb5449bj40g80v1ya-emscripten-3.0.0/share/emscripten/cache/build/libstubs'\r\n```\r\n\r\n### Expected behavior\r\nThe derivation should be built or reused from the caches properly.\r\n\r\n### Notify maintainers\r\n@qknight @matthewbauer \r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.94, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d, nixos-18.03-18.03.133402.cb0e20d6db9, nixos-18.09-18.09.2574.a7e559a5504, nixos-19.03-19.03.173691.34c7eb7545d, nixos-19.09-19.09.2522.75f4ba05c63, nixos-20.03-20.03.3330.1db42b7fe38, nixos-20.09-20.09.4407.1c1f5649bb9, nixos-unstable-22.05pre350017.efeefb2af14\"`\r\n - channels(raskolnikov): `\"nixgl, nixpkgs-22.05pre335173.56cbe42f166\"`\r\n - nixpkgs: `/home/raskolnikov/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170621/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170609","id":1217209580,"node_id":"I_kwDOAEVQ_M5IjSTs","number":170609,"title":"glibc conflict between libzip and zlib","user":{"login":"dev-null-undefined","id":50732964,"node_id":"MDQ6VXNlcjUwNzMyOTY0","avatar_url":"https://avatars.githubusercontent.com/u/50732964?v=4","gravatar_id":"","url":"https://api.github.com/users/dev-null-undefined","html_url":"https://github.com/dev-null-undefined","followers_url":"https://api.github.com/users/dev-null-undefined/followers","following_url":"https://api.github.com/users/dev-null-undefined/following{/other_user}","gists_url":"https://api.github.com/users/dev-null-undefined/gists{/gist_id}","starred_url":"https://api.github.com/users/dev-null-undefined/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dev-null-undefined/subscriptions","organizations_url":"https://api.github.com/users/dev-null-undefined/orgs","repos_url":"https://api.github.com/users/dev-null-undefined/repos","events_url":"https://api.github.com/users/dev-null-undefined/events{/privacy}","received_events_url":"https://api.github.com/users/dev-null-undefined/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-27T11:19:51Z","updated_at":"2022-04-28T19:35:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThere seems to be a conflict between libzip and zlib which results into glibc \"not working\"\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```bash\r\n#!/bin/sh\r\nFHS=$(cat << EOF | bash\r\nnix-build --no-out-link -E 'with import <nixpkgs> {};\r\n buildFHSUserEnv {\r\n name = \"fhs\";\r\n targetPkgs = p: with p; [ libzip zlib bash ];\r\n runScript = \"bash\";\r\n }\r\n'\r\nEOF\r\n)\r\n\"$FHS/bin/fhs\"\r\n```\r\nI have tested a few packages and all had the same error message for example running `curl` will result into \r\n```\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by curl)\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/a66ajxprir5fby8qk1q4ghk6kcssj2pi-curl-7.82.0/lib/libcurl.so.4)\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/v8vpzh3slc5hm4d9id5bim4dsb4d2ndh-openssl-1.1.1n/lib/libcrypto.so.1.1)\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/vi108c0aja73igb6ls7sn1dhlakyq0rp-zstd-1.5.2/lib/libzstd.so.1)\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/08knm638413jpx9bmvdb4f510wpwhayf-libkrb5-1.19.2/lib/libkrb5.so.3)\r\ncurl: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/08knm638413jpx9bmvdb4f510wpwhayf-libkrb5-1.19.2/lib/libkrb5support.so.0)\r\n```\r\n\r\n### Expected behavior\r\nfhs environment with all packages working\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5`\r\n - channels(root): `\"nixos, nixos-hardware, nixos-stable-21.05\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170609/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170577","id":1216889362,"node_id":"I_kwDOAEVQ_M5IiEIS","number":170577,"title":"Python: build wheels in separate derivation","user":{"login":"FRidh","id":2129135,"node_id":"MDQ6VXNlcjIxMjkxMzU=","avatar_url":"https://avatars.githubusercontent.com/u/2129135?v=4","gravatar_id":"","url":"https://api.github.com/users/FRidh","html_url":"https://github.com/FRidh","followers_url":"https://api.github.com/users/FRidh/followers","following_url":"https://api.github.com/users/FRidh/following{/other_user}","gists_url":"https://api.github.com/users/FRidh/gists{/gist_id}","starred_url":"https://api.github.com/users/FRidh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FRidh/subscriptions","organizations_url":"https://api.github.com/users/FRidh/orgs","repos_url":"https://api.github.com/users/FRidh/repos","events_url":"https://api.github.com/users/FRidh/events{/privacy}","received_events_url":"https://api.github.com/users/FRidh/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-27T06:59:40Z","updated_at":"2022-04-28T15:14:22Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nPerform wheel building and wheel installing in two separate derivations.\r\n\r\n### Additional context\r\nBuilds of Python wheels typically have only very few dependencies. When installing the wheel, wrapping needs to be done and propagated build inputs are added to the store resulting in a much larger closure.\r\n\r\nBy putting the building in a separate derivation, we can avoid rebuilds which is especially interesting for larger builds.\r\n\r\nRelated issue for tests #26400","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577/reactions","total_count":5,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":4,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170577/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170574","id":1216834647,"node_id":"I_kwDOAEVQ_M5Ih2xX","number":170574,"title":"pylsp-rope","user":{"login":"epigramengineer","id":62736302,"node_id":"MDQ6VXNlcjYyNzM2MzAy","avatar_url":"https://avatars.githubusercontent.com/u/62736302?v=4","gravatar_id":"","url":"https://api.github.com/users/epigramengineer","html_url":"https://github.com/epigramengineer","followers_url":"https://api.github.com/users/epigramengineer/followers","following_url":"https://api.github.com/users/epigramengineer/following{/other_user}","gists_url":"https://api.github.com/users/epigramengineer/gists{/gist_id}","starred_url":"https://api.github.com/users/epigramengineer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/epigramengineer/subscriptions","organizations_url":"https://api.github.com/users/epigramengineer/orgs","repos_url":"https://api.github.com/users/epigramengineer/repos","events_url":"https://api.github.com/users/epigramengineer/events{/privacy}","received_events_url":"https://api.github.com/users/epigramengineer/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T05:55:40Z","updated_at":"2022-04-27T05:55:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nExtended refactoring capabilities for Python LSP Server using [Rope](https://github.com/python-rope/rope).\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/python-rope/pylsp-rope\r\n* source URL: https://github.com/python-rope/pylsp-rope\r\n* license: mit\r\n* platforms: unix, linux, darwin","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170574/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170573","id":1216821604,"node_id":"I_kwDOAEVQ_M5Ihzlk","number":170573,"title":"NixOS: Bluetooth not working (seems to be a bluez issue)","user":{"login":"graysonhead","id":6179496,"node_id":"MDQ6VXNlcjYxNzk0OTY=","avatar_url":"https://avatars.githubusercontent.com/u/6179496?v=4","gravatar_id":"","url":"https://api.github.com/users/graysonhead","html_url":"https://github.com/graysonhead","followers_url":"https://api.github.com/users/graysonhead/followers","following_url":"https://api.github.com/users/graysonhead/following{/other_user}","gists_url":"https://api.github.com/users/graysonhead/gists{/gist_id}","starred_url":"https://api.github.com/users/graysonhead/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/graysonhead/subscriptions","organizations_url":"https://api.github.com/users/graysonhead/orgs","repos_url":"https://api.github.com/users/graysonhead/repos","events_url":"https://api.github.com/users/graysonhead/events{/privacy}","received_events_url":"https://api.github.com/users/graysonhead/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-27T05:36:02Z","updated_at":"2022-04-28T16:16:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI just recently set up my laptop using nixos-unstable. When I set `hardware.bluetooth.enable = true;` and run `nixos-rebuild`, I get the following error.\r\n\r\n```\r\nApr 27 00:05:37 deckchair systemd[1]: Starting Bluetooth service...\r\nApr 27 00:05:37 deckchair systemd[161067]: bluetooth.service: Failed to set up mount namespacing: /run/systemd/unit-root/var/lib/bluetooth: No such file or directory\r\nApr 27 00:05:37 deckchair systemd[161067]: bluetooth.service: Failed at step NAMESPACE spawning /nix/store/cpswxwgcbxfbqydiya4xkcdwx3ndawyr-bluez-5.64/libexec/bluetooth/bluetoothd: No such file or directory\r\nApr 27 00:05:37 deckchair systemd[1]: bluetooth.service: Main process exited, code=exited, status=226/NAMESPACE\r\nApr 27 00:05:37 deckchair systemd[1]: bluetooth.service: Failed with result 'exit-code'.\r\nApr 27 00:05:37 deckchair systemd[1]: Failed to start Bluetooth service.\r\n```\r\n\r\nIt looks like when my system built the bluez derivation, `bluetoothd` is missing.\r\n\r\nI did find a similar [issue](https://github.com/NixOS/nixpkgs/issues/39937), in the bluez project, but it seems unrelated to this specific issue, although strikingly similar.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Nixos\r\n2. Set `hardware.bluetooth.enable = true;`\r\n3. Run `nixos-rebuild switch` \r\n\r\n### Expected behavior\r\nBluetooth service starts and bluetooth devices are usable.\r\n\r\n### Notify maintainers\r\n@ryantm (I didn't see any maintainers for Bluez in the metadata and your bot was the last to touch bluez)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[grayson@deckchair:~/nixos-configs]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.00 MiB download, 0.00 MiB unpacked):\r\n /nix/store/lqslhy9ywfxkhipy28sm9qprlmb7dlm8-nix-info\r\ncopying path '/nix/store/lqslhy9ywfxkhipy28sm9qprlmb7dlm8-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170573/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170572","id":1216817238,"node_id":"I_kwDOAEVQ_M5IhyhW","number":170572,"title":"`pkgs.dwarf-fortress-packages.dwarf-fortress-full` does not build on unstable","user":{"login":"l0b0","id":168301,"node_id":"MDQ6VXNlcjE2ODMwMQ==","avatar_url":"https://avatars.githubusercontent.com/u/168301?v=4","gravatar_id":"","url":"https://api.github.com/users/l0b0","html_url":"https://github.com/l0b0","followers_url":"https://api.github.com/users/l0b0/followers","following_url":"https://api.github.com/users/l0b0/following{/other_user}","gists_url":"https://api.github.com/users/l0b0/gists{/gist_id}","starred_url":"https://api.github.com/users/l0b0/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/l0b0/subscriptions","organizations_url":"https://api.github.com/users/l0b0/orgs","repos_url":"https://api.github.com/users/l0b0/repos","events_url":"https://api.github.com/users/l0b0/events{/privacy}","received_events_url":"https://api.github.com/users/l0b0/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T05:30:01Z","updated_at":"2022-04-27T05:36:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nSee log below.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `sudo nixos-rebuild switch --upgrade-all`\r\n\r\n### Expected behavior\r\nShould build.\r\n\r\n### Additional context\r\n\r\nLog:\r\n\r\n```console\r\nmake[2]: *** [plugins/CMakeFiles/autogems.dir/build.make:76: plugins/CMakeFiles/autogems.dir/autogems.cpp.o] Error 1\r\nmake[1]: *** [CMakeFiles/Makefile2:1686: plugins/CMakeFiles/autogems.dir/all] Error 2\r\nIn file included from /build/source/plugins/buildingplan-planner.cpp:16:\r\n/build/source/plugins/uicommon.h: In function 'std::string int_to_string(int)':\r\n/build/source/plugins/uicommon.h:163:59: error: taking address of rvalue [8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-fpermissive-fpermissive8;;]\r\n 163 | return static_cast<ostringstream*>( &(ostringstream() << n) )->str();\r\n | ~~~~~~~~~~~~~~~~~^~~~~\r\n[…]\r\nerror: builder for '/nix/store/dick2v6psqpryw4a8qz625q6jzjad4wm-dfhack-base-0.47.05-r1.drv' failed with exit code 2\r\nerror: 1 dependencies of derivation '/nix/store/r3n2a4hidrxh6qn8y4lx15fackxiyqbx-dfhack-0.47.05-r1.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/f3cx1qn99azh7lkk9j35md44n5hcn6dv-dwarf-fortress-env-0.47.05.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/c5a58xfzhkcyd8y0xa7yyb274gnz7088-dwarf-fortress-init.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/w36lv1yygs67bc3ylkyyii91hvsdd180-dwarf-fortress-0.47.05.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/z0fdqhsl9yv4wr8y0xqlkjgrlbl1w9wl-dwarf-fortress-full.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/gpmp9wqr008lgvg8i5w1ld5f5c54s7m8-user-environment.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/851dcij9q1mdshq8s1rdv2f7vacwg2jv-etc.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/7af7qy0igyk0fybvmgrbhbfc02a22ws1-nixos-system-big-22.05pre372658.6a323903ad0.drv' failed to build\r\n```\r\n\r\n### Notify maintainers\r\n@Baughn @numinit\r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369988.1ffba9f2f68`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-22.05pre372658.6a323903ad0\"`\r\n - channels(victor): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n ```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170572/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170543","id":1216636856,"node_id":"I_kwDOAEVQ_M5IhGe4","number":170543,"title":"radicle-cli","user":{"login":"khaled","id":11412,"node_id":"MDQ6VXNlcjExNDEy","avatar_url":"https://avatars.githubusercontent.com/u/11412?v=4","gravatar_id":"","url":"https://api.github.com/users/khaled","html_url":"https://github.com/khaled","followers_url":"https://api.github.com/users/khaled/followers","following_url":"https://api.github.com/users/khaled/following{/other_user}","gists_url":"https://api.github.com/users/khaled/gists{/gist_id}","starred_url":"https://api.github.com/users/khaled/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/khaled/subscriptions","organizations_url":"https://api.github.com/users/khaled/orgs","repos_url":"https://api.github.com/users/khaled/repos","events_url":"https://api.github.com/users/khaled/events{/privacy}","received_events_url":"https://api.github.com/users/khaled/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-27T00:43:56Z","updated_at":"2022-04-27T00:43:56Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nCommand-line tooling for Radicle. Radicle enables developers to securely collaborate on software over a peer-to-peer network built on Git. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://radicle.xyz/\r\n* source URL: https://github.com/radicle-dev/radicle-cli\r\n* license: gpl\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170543/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170539","id":1216592800,"node_id":"I_kwDOAEVQ_M5Ig7ug","number":170539,"title":"keycloak: CRC errors on keycloak 17.0.1","user":{"login":"RaitoBezarius","id":314564,"node_id":"MDQ6VXNlcjMxNDU2NA==","avatar_url":"https://avatars.githubusercontent.com/u/314564?v=4","gravatar_id":"","url":"https://api.github.com/users/RaitoBezarius","html_url":"https://github.com/RaitoBezarius","followers_url":"https://api.github.com/users/RaitoBezarius/followers","following_url":"https://api.github.com/users/RaitoBezarius/following{/other_user}","gists_url":"https://api.github.com/users/RaitoBezarius/gists{/gist_id}","starred_url":"https://api.github.com/users/RaitoBezarius/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/RaitoBezarius/subscriptions","organizations_url":"https://api.github.com/users/RaitoBezarius/orgs","repos_url":"https://api.github.com/users/RaitoBezarius/repos","events_url":"https://api.github.com/users/RaitoBezarius/events{/privacy}","received_events_url":"https://api.github.com/users/RaitoBezarius/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-26T23:26:30Z","updated_at":"2022-04-28T16:15:29Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nIt is impossible to enable Keycloak ≥ 17.0.1 at the moment with the NixOS module, as the `confFile` seems to introduce CRC errors after Quarkus augmentation process.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `services.keycloak.enable = true;`\r\n2. `nixos-rebuild switch`\r\n3. failure.\r\n\r\n### Expected behavior\r\n\r\nBuilding Keycloak with the configuration file should not introduce CRC errors.\r\n\r\n### Screenshots\r\n```\r\n2022-04-26 23:22:29,709 INFO [io.quarkus.deployment.QuarkusAugmentor] (main) Quarkus augmentation completed in 41351ms\r\nbuilding '/nix/store/g4ly72sp0qrh72g0f0vk1mwwnxdfz311-stage-2-init.sh.drv'...\r\nERROR: Failed to run 'build' command.\r\nERROR: Failed to update server configuration.\r\nERROR: Failed to load persisted properties from /build/source/bin/../lib/quarkus/generated-bytecode.jar\r\nERROR: invalid entry CRC (expected 0x6480a055 but got 0xda0e3380)\r\nFor more details run the same command passing the '--verbose' option. Also you can use '--help' to see the details about the usage of the particular command.\r\nerror: builder for '/nix/store/h0fc0f8b2hh1xmwbv5d30si2lx5f71a3-keycloak-17.0.1.drv' failed with exit code 1\r\nerror: 1 dependencies of derivation '/nix/store/zrzjbw3agf1vy9193wrmlv7qjsmw6nql-system-path.drv' failed to build\r\nerror (ignored): error: cannot unlink '/tmp/nix-build-acme-dns-0.8.drv-3/go-build3786141733': Directory not empty\r\nerror: 1 dependencies of derivation '/nix/store/h5sc8gg3i90vi047zcwlmj7mk69h1x7s-unit-keycloak.service.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/wjgjk18p8i5cg4i2hmj4n2ydrf8d6g0q-nixos-system-core-services-01-22.05.git.7f4a8f37d46.drv' failed to build\r\n```\r\n\r\nis quite precise.\r\n\r\n\r\n### Additional context\r\n\r\nThis might be related to some JRE runtimes issues with some precise Java versions, I'm trying the \"default\" one on nixpkgs-unstable-small and adoptjdk-open-jre (v11), and will try more in the future.\r\n\r\n### Notify maintainers\r\n\r\n@talyz\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369756.75ad56bdc92`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"home-manager, nixos, sops-nix\"`\r\n - channels(raito): `\"home-manager, nixgl, nixpkgs-21.11pre319254.b5182c214fa\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\nNot relevant to this problem as this is on a target server, the right nixpkgs revision is: `7f4a8f37d4621b27fc0c4eeb3880ecf1cb055371`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170539/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170489","id":1216450109,"node_id":"I_kwDOAEVQ_M5IgY49","number":170489,"title":"mate: touchpad not working correctly","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T20:35:10Z","updated_at":"2022-04-26T20:35:10Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nthe touchpad space is mapped 1:1 to the screen, but the edge is missing, so you can't reach menus\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. have computer with touchpad\r\n2. install nixos with mate desktop\r\n3. try to use touchpad\r\n\r\n### Expected behavior\r\nworking touchpad\r\n\r\n### Additional context\r\n\r\nThis is fixed with:\r\n\r\n`services.xserver.libinput.enable = true;`\r\n\r\nplease add it to https://github.com/NixOS/nixpkgs/blob/5db92536331da585eafa2aa55ce232ac900c9e9d/nixos/modules/services/x11/desktop-managers/mate.nix\r\n\r\nlike the other desktops do\r\n\r\nwe should also check if it's missing for other desktops too and see if it's needed\r\n\r\n### Notify maintainers\r\n@romildo \r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170489/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170486","id":1216437347,"node_id":"I_kwDOAEVQ_M5IgVxj","number":170486,"title":"okteta, yakuake and pygtk leak dev packages in runtime","user":{"login":"ilya-fedin","id":17829319,"node_id":"MDQ6VXNlcjE3ODI5MzE5","avatar_url":"https://avatars.githubusercontent.com/u/17829319?v=4","gravatar_id":"","url":"https://api.github.com/users/ilya-fedin","html_url":"https://github.com/ilya-fedin","followers_url":"https://api.github.com/users/ilya-fedin/followers","following_url":"https://api.github.com/users/ilya-fedin/following{/other_user}","gists_url":"https://api.github.com/users/ilya-fedin/gists{/gist_id}","starred_url":"https://api.github.com/users/ilya-fedin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ilya-fedin/subscriptions","organizations_url":"https://api.github.com/users/ilya-fedin/orgs","repos_url":"https://api.github.com/users/ilya-fedin/repos","events_url":"https://api.github.com/users/ilya-fedin/events{/privacy}","received_events_url":"https://api.github.com/users/ilya-fedin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-26T20:23:03Z","updated_at":"2022-04-27T14:52:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI see a lot of dev packages on my system:\r\n```\r\n nix-store -qR /run/current-system | grep '\\-dev'\r\n/nix/store/1s6ql728gwf3vcph00a6yzvz80cgkawm-harfbuzz-3.3.2-dev\r\n/nix/store/66rvnvvwp6dmbb4i1nkpsgav09klshi7-zlib-1.2.12-dev\r\n/nix/store/ysw3g2vspx2v5mj4jlsjkhgsk5zjsrdi-libxml2-2.9.13-dev\r\n/nix/store/1vn4zwyynaiw1x8vgdj9vi2fhfkvvsbx-libxslt-1.1.35-dev\r\n/nix/store/9vlb5aghn32wdg036c5nd8qbnh3xg2vs-libffi-3.4.2-dev\r\n/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev\r\n/nix/store/1wanxv8w19caz474w35yjzvcscap055c-atk-2.36.0-dev\r\n/nix/store/29ci2j5c12188a3akbfb0ggw2glmjka3-icu4c-70.1-dev\r\n/nix/store/gja3fdcl7bnzg2cjdapgp6d6g0wiqscj-libpng-apng-1.6.37-dev\r\n/nix/store/kqs3q7kbf1svxz4r3lvkipckl086hc6z-libjpeg-turbo-2.1.3-dev\r\n/nix/store/v4b48a7014m94m3a6g5j916vj2k9d30q-xz-5.2.5-dev\r\n/nix/store/nx1xnnrja5568cyp9r8kc9jfdflf5s2c-libtiff-4.3.0-dev\r\n/nix/store/2d98gnn5sz17cb9zvkw58ci2bwn6qh8d-gdk-pixbuf-2.42.8-dev\r\n/nix/store/yrp7hnh8rclhvlfxpm9ppxadbpbk76gm-libxcb-1.14-dev\r\n/nix/store/38hkqa73k3gcpgxk8c736s4rqj6n3kkg-libX11-1.7.2-dev\r\n/nix/store/4lr57pcibz4v7yzcywjjbrk5k7jiil1h-xcb-util-wm-0.4.1-dev\r\n/nix/store/ark29cfi77v8j5hisgrmpd3ayhin994a-bzip2-1.0.6.0.2-dev\r\n/nix/store/jxwjj3ak8n9wgmyfkr3j68jzqqffl6hf-freetype-2.12.0-dev\r\n/nix/store/9lhfj42dxf9grrwqk2v375bb733bh3jf-fontconfig-2.13.94-dev\r\n/nix/store/bsz8v048dx4v8a4ky27bw30qv5hm3rql-libXau-1.0.9-dev\r\n/nix/store/ghf6lc2sd7p9kzwhyi8c9raahsrzann4-libXext-1.3.4-dev\r\n/nix/store/imzql59xpa0k8sh6akab6n733znjzhq2-xcb-util-0.4.0-dev\r\n/nix/store/kzj38ssh2qdbpd6dmzqgjbf5r5y2y6g7-libXrender-0.9.10-dev\r\n/nix/store/77wicbhvcz8g94zjd28vrw3rq6ndb9lp-libglvnd-1.4.0-dev\r\n/nix/store/l97ffy2wia7k3039cq1g24hi4kn5jvin-libGL-1.4.0-dev\r\n/nix/store/q6ci7kwgccla2c8kpv7rqj23k8578b9a-expat-2.4.7-dev\r\n/nix/store/bhgkpp2p3wg192c96hq669wizc1xpwva-cairo-1.16.0-dev\r\n/nix/store/qwnd82izrxqh0s3mw064mx7xsx1kynv2-libXft-2.3.4-dev\r\n/nix/store/5nyv2il4nfr3nplpiagdxwr75mwm2vjv-pango-1.50.6-dev\r\n/nix/store/5s5ki2vsmgsrl72fy3n583p4g8ina92i-libXfixes-6.0.0-dev\r\n/nix/store/7yi3rz6qf7gzp5zpp0b0cb6pg7p3adzp-libXi-1.8-dev\r\n/nix/store/8l8cfgxafnl8hb1z6w2z64pg15w7qg0k-openssl-1.1.1n-dev\r\n/nix/store/srg2bim63yrh90yfgs6g4rqj4wm1a7sc-gmp-with-cxx-6.2.1-dev\r\n/nix/store/984d0p92vig60621advhb37pdr2kgv9b-cups-2.4.1-dev\r\n/nix/store/9r4kh9n63jkck2nw36vwh6lnwlkmzy43-xcb-util-renderutil-0.3.9-dev\r\n/nix/store/ai35s2cvy25qbnb3xd6p959psynpsvpz-xcb-util-keysyms-0.4.0-dev\r\n/nix/store/d2nm8bfnnz8nafbm9rdkvlp8ifxr815d-libdrm-2.4.110-dev\r\n/nix/store/802s62hd9hqvrq8v0nmjv9m3vy1iym8f-libXrandr-1.5.2-dev\r\n/nix/store/f2f3mmxq1690wjzzrmfx0kg1g4phaqqp-libICE-1.0.10-dev\r\n/nix/store/hmajb49fq2f0fvp853y33ypsvkq35j66-wayland-1.20.0-dev\r\n/nix/store/i2c33539zgwy48343n829zmkyqq7lbfp-libXcursor-1.2.0-dev\r\n/nix/store/kqwwcb8hhyfwz86mifqhixi6vrg7bhv1-libXinerama-1.1.4-dev\r\n/nix/store/mka5pfgkkx4mp0hj7jhxwm9rmkcrx43n-libXcomposite-0.4.5-dev\r\n/nix/store/s4hrnmc41nn9n0bycvd7ssfpbm62zbcf-libSM-1.2.3-dev\r\n/nix/store/dsvwivybx5xnw4rhf3k3kgr5g35ylgn1-gtk+3-3.24.33-dev\r\n/nix/store/igz51dvincwvf96ilsvpjhswkzigsivf-dbus-1.12.20-dev\r\n/nix/store/i0612v7kc416h0pvzq0kq0z5cks2vpp0-at-spi2-core-2.44.0-dev\r\n/nix/store/lh9rayfvdhvvz08ifv1kqchk3m7vs63s-pcre2-10.39-dev\r\n/nix/store/mjkhmhd1x22zk2w5hycyv9jrwyjnr93b-libxkbcommon-1.4.0-dev\r\n/nix/store/nrbm90mfg67iwj98h50ikc33bj9m1kbp-xcb-util-image-0.4.0-dev\r\n/nix/store/x6sgybml42ng9k9hfjyk9j14qplk9f80-sqlite-3.38.2-dev\r\n/nix/store/yfwkpmddsfzl8nkam6q4xr5njhd253h7-systemd-250.4-dev\r\n/nix/store/byyibx4ql3r5w7x5pdbgfbvkc5hzwcdc-qtbase-5.15.3-dev\r\n/nix/store/2kjcikca67n24rwrlydd5zfjc5zam867-kdbusaddons-5.93.0-dev\r\n/nix/store/6x5x45q14g9jwgwf8ffx7yd32v5dbvw7-ki18n-5.93.0-dev\r\n/nix/store/jwanrq2ipb5gfs1y1spi5rgaz586z6i7-karchive-5.93.0-dev\r\n/nix/store/3jcmicn09nnq875q7szdzg11c7vzxjch-kdoctools-5.93.0-dev\r\n/nix/store/5r2d5grlhhzyifd199g372ill76b9i9f-kcoreaddons-5.93.0-dev\r\n/nix/store/63mcnbhiaaajkdpwp7d0vq9v2hskna43-kitemviews-5.93.0-dev\r\n/nix/store/7gfj68bmwiqqp1x7g29bw50nsvm45n1f-sonnet-5.93.0-dev\r\n/nix/store/dagm6fz21nrw2b5hfvkk5ww3v50yj154-kconfig-5.93.0-dev\r\n/nix/store/mk0gq51m1vzcmv91y67sgpkz337vky0q-kwindowsystem-5.93.0-dev\r\n/nix/store/g6vkfi5g1daf043daixz0raq1lr9j6cr-kcrash-5.93.0-dev\r\n/nix/store/81wjc5s5zcjm6mhnbrnnyvx95hlfvs7k-kservice-5.93.0-dev\r\n/nix/store/ah98qp2z4larf0s85c7mvqcgqjassgqq-kguiaddons-5.93.0-dev\r\n/nix/store/nwxqp90yqrxg1bks0q1wh6x89v8x8qrg-qtsvg-5.15.3-dev\r\n/nix/store/yg71h4572iyhzxr8scik9qxghhlkcb2x-qtdeclarative-5.15.3-dev\r\n/nix/store/jkgl47z7gxyibsw6yzr4ws12hgsvx0df-qttools-5.15.3-dev\r\n/nix/store/wkkch35m7gpjiy4lgy0x0cnvf7sz1lwz-kauth-5.93.0-dev\r\n/nix/store/zkky9j5l9xhmrx5lzkfsg6sjkgzm36fa-kwidgetsaddons-5.93.0-dev\r\n/nix/store/zvrzcsnqxj1nh5z2lpxh0rzbqqjsi3zi-kcodecs-5.93.0-dev\r\n/nix/store/mdlw33nfn8s7p9lgm89mpkkb14fgn22n-kconfigwidgets-5.93.0-dev\r\n/nix/store/8ydgcrnchxz0jygsxb5xb8ddyh9b0c8f-kiconthemes-5.93.0-dev\r\n/nix/store/l3g5cvj1lqjjfh3i4y944s3kvzr2l1ai-kcompletion-5.93.0-dev\r\n/nix/store/05cxk8vn9l2p4cii13rra52vgsvr2y2c-ktextwidgets-5.93.0-dev\r\n/nix/store/n278lhr1yagddwdkbal6w5wl7k4si933-systemd-minimal-250.4-dev\r\n/nix/store/5my22f291i6zyrnz345msdic3ccpgmji-libusb-1.0.25-dev\r\n/nix/store/k8fgn28n88z67c78ads052l8mgf5lkd1-qtquickcontrols-5.15.3-dev\r\n/nix/store/3z8afdb9y6hpyig17hfry0pmagghz1kf-gtk+-2.24.33-dev\r\n/nix/store/kfkl0xg02x0rb130a690sm3ynkrjvs8v-python3.9-pygobject-3.42.0-dev\r\n/nix/store/2zhksr9v2yhly31bvlfamf28hdn3bbzk-libaccounts-glib-1.24-dev\r\n/nix/store/4cj86i9lvn2wic5376wril53jpydnfnc-kjobwidgets-5.93.0-dev\r\n/nix/store/gv7q8kkxald4qbnqrlmmq32nyw21rl0k-attica-5.93.0-dev\r\n/nix/store/j723ilhainch506nlnvjrvv2vj7i1wdb-kglobalaccel-5.93.0-dev\r\n/nix/store/lghmkkzanz8r0560dfyzis3ca0x38q3g-kxmlgui-5.93.0-dev\r\n/nix/store/airl7yli0v4cqi4izmyamax13f8lz2ld-kbookmarks-5.93.0-dev\r\n/nix/store/ch6p3rd7r5ijm7s29npbgnlk30lwrgvy-kded-5.93.0-dev\r\n/nix/store/fd8w8f44g9a2qjx6smcj0apmdfylp679-solid-5.93.0-dev\r\n/nix/store/z74g6bswkan4d1y0iwbai13hab20v9bq-knotifications-5.93.0-dev\r\n/nix/store/z9s0559cp7319kxcqargyxbfhjk6maai-kwallet-5.93.0-dev\r\n/nix/store/c66am37518f24jvv3n57gbwimzz96an1-kio-5.93.0-dev\r\n/nix/store/4bkpp2jpkvj90qk2kxas601lmyr2fh73-kinit-5.93.0-dev\r\n/nix/store/12d28nw0w2d9gw8cm94yfs5529mkhi06-syndication-5.93.0-dev\r\n/nix/store/16fv8dazigxfzj8c7x445z8k0f8xvxn4-kpackage-5.93.0-dev\r\n/nix/store/a46bmiw58v3b7mkyfbfl4bs7gqzw1pag-kirigami2-5.93.0-dev\r\n/nix/store/hix9hpwp1zqm0zxg73vhf68jfvyqzlvd-knewstuff-5.93.0-dev\r\n/nix/store/51apyva0jgvfj349jxidzld3mzd10dgc-kdeclarative-5.93.0-dev\r\n/nix/store/v61mssd82m0ykp6knbm5jl14d8s4bdah-kcmutils-5.93.0-dev\r\n/nix/store/z88f3x21a6cc8zlxkhrvs938nrpwsm9z-kparts-5.93.0-dev\r\n/nix/store/jq2ybvjjzymn8cfhwdhqnxb52c0mw1ig-pipewire-0.3.49-dev\r\n/nix/store/k5f3aq38czp3wbqnp2c40q2lgqlpzd3i-knotifyconfig-5.93.0-dev\r\n```\r\nIt seems, most of them are pulled by okteta and yakuake while dev package of gtk2 is pulled by pygtk2 (that is pulled by gimp on my system)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install those packages via environment.systemPackages\r\n\r\n### Expected behavior\r\nI don't think those packages are required for these applications and pygtk to work, so I expect they don't pull them :)\r\n\r\n### Notify maintainers\r\n@peterhoeg @bkchr @fridh\r\n(is pygtk unmaintained?)\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.2-zen3, NixOS, 22.05 (Quokka), 22.05.20220423.bc41b01`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - nixpkgs: `/etc/static/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170486/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170481","id":1216429979,"node_id":"I_kwDOAEVQ_M5IgT-b","number":170481,"title":"Clean up hardware-configuration.nix","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":6314755,"node_id":"MDU6TGFiZWw2MzE0NzU1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wontfix","name":"2.status: wontfix","color":"e6e6e6","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-26T20:15:12Z","updated_at":"2022-04-26T22:16:29Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThis is the created config:\r\n\r\n```\r\n# Do not modify this file! It was generated by ‘nixos-generate-config’\r\n# and may be overwritten by future invocations. Please make changes\r\n# to /etc/nixos/configuration.nix instead.\r\n{ config, lib, pkgs, modulesPath, ... }:\r\n\r\n{\r\n imports =\r\n [ (modulesPath + \"/installer/scan/not-detected.nix\")\r\n ];\r\n\r\n boot.initrd.availableKernelModules = [ \"uhci_hcd\" \"ehci_pci\" \"ahci\" \"usbhid\" \"ums_realtek\" \"usb_storage\" \"sd_mod\" \"sr_mod\" ];\r\n boot.initrd.kernelModules = [ ];\r\n boot.kernelModules = [ \"wl\" ];\r\n boot.extraModulePackages = [ config.boot.kernelPackages.broadcom_sta ];\r\n\r\n fileSystems.\"/\" =\r\n { device = \"/dev/disk/by-uuid/5fc95d4a-ead1-4851-8fe3-f430ada41292\";\r\n fsType = \"ext4\";\r\n };\r\n\r\n swapDevices =\r\n [ { device = \"/dev/disk/by-uuid/6fa3a32d-ffef-49b2-b662-05f3e2cf7e4e\"; }\r\n ];\r\n\r\n # The global useDHCP flag is deprecated, therefore explicitly set to false here.\r\n # Per-interface useDHCP will be mandatory in the future, so this generated config\r\n # replicates the default behaviour.\r\n networking.useDHCP = lib.mkDefault false;\r\n networking.interfaces.enp9s0.useDHCP = lib.mkDefault true;\r\n\r\n hardware.cpu.intel.updateMicrocode = lib.mkDefault config.hardware.enableRedistributableFirmware;\r\n}\r\n```\r\n\r\nProblems:\r\n\r\n` boot.extraModulePackages = [ config.boot.kernelPackages.broadcom_sta ];`\r\n\r\nstrange way to refer to a package. should be `boot.extraModulePackages = with pkgs; [ kernelPackages.broadcom_sta ];` i guess\r\n\r\n` hardware.cpu.intel.updateMicrocode = lib.mkDefault config.hardware.enableRedistributableFirmware;`\r\n\r\ntechnically that should work, but it's not easy to debug. use IF enableRedistributableFirmware then TRUE or something\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\n\r\n`hardware-configuration.nix` should follow best practices in nix syntax and be easy to understand to (new) users\r\n\r\n### Additional context\r\n\r\nMaybe something of that came from the new graphical installer? @vlinkz\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170481/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170475","id":1216417936,"node_id":"I_kwDOAEVQ_M5IgRCQ","number":170475,"title":"ledger-live-desktop bubblewrapping is ... aggressive? Seems to break the application","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-26T20:02:43Z","updated_at":"2022-04-26T20:12:35Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen I launch Ledger Live Desktop, it just plainly acts like it can't see my data folder in `~/.local/share`.\r\n\r\nDid something change wrt to it recently?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170475/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170470","id":1216395287,"node_id":"I_kwDOAEVQ_M5IgLgX","number":170470,"title":"godot-export-templates: Linux exports are huge","user":{"login":"pacien","id":1449319,"node_id":"MDQ6VXNlcjE0NDkzMTk=","avatar_url":"https://avatars.githubusercontent.com/u/1449319?v=4","gravatar_id":"","url":"https://api.github.com/users/pacien","html_url":"https://github.com/pacien","followers_url":"https://api.github.com/users/pacien/followers","following_url":"https://api.github.com/users/pacien/following{/other_user}","gists_url":"https://api.github.com/users/pacien/gists{/gist_id}","starred_url":"https://api.github.com/users/pacien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pacien/subscriptions","organizations_url":"https://api.github.com/users/pacien/orgs","repos_url":"https://api.github.com/users/pacien/repos","events_url":"https://api.github.com/users/pacien/events{/privacy}","received_events_url":"https://api.github.com/users/pacien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"pacien","id":1449319,"node_id":"MDQ6VXNlcjE0NDkzMTk=","avatar_url":"https://avatars.githubusercontent.com/u/1449319?v=4","gravatar_id":"","url":"https://api.github.com/users/pacien","html_url":"https://github.com/pacien","followers_url":"https://api.github.com/users/pacien/followers","following_url":"https://api.github.com/users/pacien/following{/other_user}","gists_url":"https://api.github.com/users/pacien/gists{/gist_id}","starred_url":"https://api.github.com/users/pacien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pacien/subscriptions","organizations_url":"https://api.github.com/users/pacien/orgs","repos_url":"https://api.github.com/users/pacien/repos","events_url":"https://api.github.com/users/pacien/events{/privacy}","received_events_url":"https://api.github.com/users/pacien/received_events","type":"User","site_admin":false},"assignees":[{"login":"pacien","id":1449319,"node_id":"MDQ6VXNlcjE0NDkzMTk=","avatar_url":"https://avatars.githubusercontent.com/u/1449319?v=4","gravatar_id":"","url":"https://api.github.com/users/pacien","html_url":"https://github.com/pacien","followers_url":"https://api.github.com/users/pacien/followers","following_url":"https://api.github.com/users/pacien/following{/other_user}","gists_url":"https://api.github.com/users/pacien/gists{/gist_id}","starred_url":"https://api.github.com/users/pacien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pacien/subscriptions","organizations_url":"https://api.github.com/users/pacien/orgs","repos_url":"https://api.github.com/users/pacien/repos","events_url":"https://api.github.com/users/pacien/events{/privacy}","received_events_url":"https://api.github.com/users/pacien/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-04-26T19:37:04Z","updated_at":"2022-04-26T19:37:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe nixpkgs Godot export template for Linux is huge (about 500MB) and causes\r\nall game exports to be at least as heavy.\r\n\r\n### Expected behavior\r\n\r\nThe export template and exported games should have the reasonable base size\r\nbelow 50MB, like when generated with the pre-compiled binary templates\r\ndownloaded directly from the Godot website.\r\n\r\n### Additional context\r\n\r\nStripping the export templates may help, as suggested in the upstream\r\ndocumentation:\r\nhttps://docs.godotengine.org/en/stable/development/compiling/optimizing_for_size.html\r\n\r\nNot sure of why it's not done automatically.\r\n\r\n### Notify maintainers\r\n\r\nCC: @Twey @jojosch\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170470/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170469","id":1216395052,"node_id":"I_kwDOAEVQ_M5IgLcs","number":170469,"title":"godot-export-templates: missing templates for targets other than Linux","user":{"login":"pacien","id":1449319,"node_id":"MDQ6VXNlcjE0NDkzMTk=","avatar_url":"https://avatars.githubusercontent.com/u/1449319?v=4","gravatar_id":"","url":"https://api.github.com/users/pacien","html_url":"https://github.com/pacien","followers_url":"https://api.github.com/users/pacien/followers","following_url":"https://api.github.com/users/pacien/following{/other_user}","gists_url":"https://api.github.com/users/pacien/gists{/gist_id}","starred_url":"https://api.github.com/users/pacien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pacien/subscriptions","organizations_url":"https://api.github.com/users/pacien/orgs","repos_url":"https://api.github.com/users/pacien/repos","events_url":"https://api.github.com/users/pacien/events{/privacy}","received_events_url":"https://api.github.com/users/pacien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T19:36:48Z","updated_at":"2022-04-26T19:36:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the issue\r\n\r\n`pkgs.godot-export-templates` only has contains a template for Linux/X11\r\nx86_64, whereas the pre-built binary archive on the official website has\r\ntemplates for:\r\n\r\n- Android\r\n- iPhone\r\n- Linux/X11 (i386, x86_64)\r\n- OS X\r\n- WebAssembly\r\n- Windows UWP (ARM, x86, x64)\r\n- Windows (32, 64bits)\r\n\r\n### Expected behavior\r\n\r\nWe should have those export templates as well?\r\n\r\n### Additional context\r\n\r\nSome of the missing templates (WebAssembly) can probably be cross-built with\r\nlittle modifications. Other platforms might be more tricky.\r\n\r\n### Notify maintainers\r\n\r\nCC: @Twey @jojosch\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170469/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170468","id":1216394010,"node_id":"I_kwDOAEVQ_M5IgLMa","number":170468,"title":"godot: godot-export-templates not detected","user":{"login":"pacien","id":1449319,"node_id":"MDQ6VXNlcjE0NDkzMTk=","avatar_url":"https://avatars.githubusercontent.com/u/1449319?v=4","gravatar_id":"","url":"https://api.github.com/users/pacien","html_url":"https://github.com/pacien","followers_url":"https://api.github.com/users/pacien/followers","following_url":"https://api.github.com/users/pacien/following{/other_user}","gists_url":"https://api.github.com/users/pacien/gists{/gist_id}","starred_url":"https://api.github.com/users/pacien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pacien/subscriptions","organizations_url":"https://api.github.com/users/pacien/orgs","repos_url":"https://api.github.com/users/pacien/repos","events_url":"https://api.github.com/users/pacien/events{/privacy}","received_events_url":"https://api.github.com/users/pacien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T19:35:42Z","updated_at":"2022-04-26T19:35:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe Godot IDE (`pkgs.godot`) does not automatically find the templates provided\r\nby `pkgs.godot-export-templates`, even when added to the environment.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n\r\n1. Run `nix shell nixpkgs#godot nixpkgs#godot-export-templates`\r\n2. Run `godot --editor`\r\n3. In Godot's menu: `Editor` -> `Manage Export Template...`\r\n4. \"Export templates are missing. Download them or install from a file.\"\r\n\r\n### Expected behavior\r\n\r\nGodot should detect the location of the export templates provided by the\r\npackage `pkgs.godot-export-templates`.\r\n\r\n### Additional context\r\n\r\nAccording to the manual page [godot(6)], the program is looking for those files\r\nto be placed in `$XDG_DATA_HOME/godot/templates` or\r\n`~/.local/share/godot/templates`.\r\n\r\n[godot(6)]: https://github.com/godotengine/godot/blob/922348f/misc/dist/linux/godot.6#L160\r\n\r\n`pkgs.godot` could perhaps include the templates from\r\n`pkgs.godot-export-templates` by default and be patched or wrapped to register\r\nthe templates' path?\r\n\r\n### Notify maintainers\r\n\r\nCC: @Twey\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170468/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170465","id":1216352062,"node_id":"I_kwDOAEVQ_M5IgA8-","number":170465,"title":"nix run disabled by default on NixOS 22.05","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":207327249,"node_id":"MDU6TGFiZWwyMDczMjcyNDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20changelog","name":"9.needs: changelog","color":"eb6420","default":false,"description":null},{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-04-26T18:53:27Z","updated_at":"2022-04-27T13:59:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOn a fresh install of NixOS:\r\n\r\n```\r\n[x@nixos:~]$ nix run nixpkgs.geekbench\r\nerror: experimental Nix feature 'nix-command' is disabled; use '--extra-experimental-features nix-command' to override\r\n```\r\n\r\nThis works on NixOS 21.11, so it's a regression.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nNix should work by default on NixOS.\r\n\r\n### Additional context\r\nDoes also apply to other nix commands like nix shell.\r\n\r\n### Notify maintainers\r\n@eelco @lovesegfault @artturin\r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170465/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170463","id":1216340759,"node_id":"I_kwDOAEVQ_M5If-MX","number":170463,"title":"nix-shell does not work with unfree packages (even when they are allowed)","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-26T18:40:49Z","updated_at":"2022-04-27T03:01:26Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```\r\n[x@nixos:~]$ nix-shell -p geekbench\r\nerror: Package ‘geekbench-5.4.4’ in /nix/var/nix/profiles/per-user/root/channels/nixos/pkgs/tools/misc/geekbench/default.nix:35 has an unfree license (‘unfree’), refusing to evaluate.\r\n\r\n a) To temporarily allow unfree packages, you can use an environment variable\r\n for a single invocation of the nix tools.\r\n\r\n $ export NIXPKGS_ALLOW_UNFREE=1\r\n\r\n Note: For `nix shell`, `nix build`, `nix develop` or any other Nix 2.4+\r\n (Flake) command, `--impure` must be passed in order to read this\r\n environment variable.\r\n\r\n b) For `nixos-rebuild` you can set\r\n { nixpkgs.config.allowUnfree = true; }\r\n in configuration.nix to override this.\r\n\r\n Alternatively you can configure a predicate to allow specific packages:\r\n { nixpkgs.config.allowUnfreePredicate = pkg: builtins.elem (lib.getName pkg) [\r\n \"geekbench\"\r\n ];\r\n }\r\n\r\n c) For `nix-env`, `nix-build`, `nix-shell` or any other Nix command you can add\r\n { allowUnfree = true; }\r\n to ~/.config/nixpkgs/config.nix.\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\n\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. have `nixpkgs.config.allowUnfree = true;` in `configuration.nix`\r\n2. `nix-shell -p geekbench`\r\n3. error: has an unfree license\r\n\r\n### Expected behavior\r\nno errors\r\n\r\n### Additional context\r\nMaybe related to https://github.com/NixOS/nixpkgs/issues/166220\r\nhttps://github.com/NixOS/nixpkgs/issues/116340\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170463/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170461","id":1216338623,"node_id":"I_kwDOAEVQ_M5If9q_","number":170461,"title":"Pantheon: user accounts settings are missing from system settings","user":{"login":"alexeymuranov","id":712698,"node_id":"MDQ6VXNlcjcxMjY5OA==","avatar_url":"https://avatars.githubusercontent.com/u/712698?v=4","gravatar_id":"","url":"https://api.github.com/users/alexeymuranov","html_url":"https://github.com/alexeymuranov","followers_url":"https://api.github.com/users/alexeymuranov/followers","following_url":"https://api.github.com/users/alexeymuranov/following{/other_user}","gists_url":"https://api.github.com/users/alexeymuranov/gists{/gist_id}","starred_url":"https://api.github.com/users/alexeymuranov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alexeymuranov/subscriptions","organizations_url":"https://api.github.com/users/alexeymuranov/orgs","repos_url":"https://api.github.com/users/alexeymuranov/repos","events_url":"https://api.github.com/users/alexeymuranov/events{/privacy}","received_events_url":"https://api.github.com/users/alexeymuranov/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1207068537,"node_id":"MDU6TGFiZWwxMjA3MDY4NTM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20pantheon","name":"6.topic: pantheon","color":"fef2c0","default":false,"description":"The Pantheon desktop environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-26T18:38:26Z","updated_at":"2022-04-27T07:29:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI cannot find user accounts settings in Pantheon. That is, clicking on \"User Accounts Settings...\" in user/session applet (in the top right corner) opens System Settings, but there are no User Accounts Settings. In particular, i cannot change user profile picture.\r\n\r\n### Steps To Reproduce\r\n1. Activate Pantheon desktop.\r\n2. Log in with Pantheon desktop.\r\n3. Click on \"User Accounts Settings...\" in session menu (top right corner).\r\n\r\n### Expected behavior\r\nShould be able to access user accounts settings.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\n\r\n### Notify maintainers\r\n@bobby285271 \r\n@davidak \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.111, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.337209.c254b8c915a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170461/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170429","id":1216035137,"node_id":"I_kwDOAEVQ_M5IezlB","number":170429,"title":"amdgpu: black screen after resume from suspend","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T14:21:23Z","updated_at":"2022-04-26T18:28:39Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\ni was able to connect via ssh to get the dmesg... now not even htop starts. the kernel seem to have problems\r\n\r\ndmesg: https://gist.github.com/davidak/a98e70b4de9d20af153177a6867038d3\r\n\r\nissue happened at 16:00, i resumed and suspended successfully before\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. suspend\r\n2. resume\r\n3. login\r\n4. black screen\r\n\r\n### Expected behavior\r\nusable computer\r\n\r\n### Screenshots\r\nimagine a complete black image\r\n\r\n### Additional context\r\nit seem that the problem might be caused by too many chrome tabs\r\n\r\nmaybe related to https://github.com/NixOS/nixpkgs/issues/119843\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369988.1ffba9f2f68`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"home-manager-21.11, nixos-22.05pre369988.1ffba9f2f68, nixos-hardware, nixos-unstable-22.05pre369988.1ffba9f2f68\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\nHardware:\r\n\r\nIntel Core i9 9900K\r\nAMD Radeon RX 6600 XT\r\nGigabyte Z390 UD Mainboard","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170429/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170419","id":1215966762,"node_id":"I_kwDOAEVQ_M5Iei4q","number":170419,"title":"github-desktop: Cannot connect github account","user":{"login":"MichaelAkvo","id":91939214,"node_id":"U_kgDOBXrhjg","avatar_url":"https://avatars.githubusercontent.com/u/91939214?v=4","gravatar_id":"","url":"https://api.github.com/users/MichaelAkvo","html_url":"https://github.com/MichaelAkvo","followers_url":"https://api.github.com/users/MichaelAkvo/followers","following_url":"https://api.github.com/users/MichaelAkvo/following{/other_user}","gists_url":"https://api.github.com/users/MichaelAkvo/gists{/gist_id}","starred_url":"https://api.github.com/users/MichaelAkvo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MichaelAkvo/subscriptions","organizations_url":"https://api.github.com/users/MichaelAkvo/orgs","repos_url":"https://api.github.com/users/MichaelAkvo/repos","events_url":"https://api.github.com/users/MichaelAkvo/events{/privacy}","received_events_url":"https://api.github.com/users/MichaelAkvo/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-26T13:32:36Z","updated_at":"2022-04-28T08:07:56Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTrying to connect a github account will open a browser, request access, and finally fail to send the access token to the application as it can't be opened.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. File > Settings\r\n2. Sign in to Github \r\n\r\n\r\n3. Login and give access\r\n\r\n### Expected behavior\r\n\r\nThe github desktop app should be opened after the token has been given access\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n\r\n### Additional context\r\n\r\nIt's trying to call `x-github-desktop-dev-auth://oauth?code=CODE&state=STATE`\r\n\r\n### Notify maintainers\r\n\r\n@dan4ik605743\r\n\r\n### Metadata\r\n\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.111, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.337100.7b38b03d76a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170419/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170395","id":1215687740,"node_id":"I_kwDOAEVQ_M5Idew8","number":170395,"title":"nixos.tests.lxd.aarch64-linux fails on hydra","user":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"},{"id":3536622080,"node_id":"LA_kwDOAEVQ_M7SzJIA","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20build%20failure","name":"0.kind: build failure","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"assignees":[{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false}],"milestone":null,"comments":3,"created_at":"2022-04-26T09:42:03Z","updated_at":"2022-04-26T18:28:22Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"For example https://hydra.nixos.org/build/174728144\r\n\r\nThis test has always been failing: https://hydra.nixos.org/job/nixos/trunk-combined/nixos.tests.lxd.aarch64-linux/all\r\n\r\nFrom the logs:\r\n\r\n```\r\nmachine: must succeed: lxc image import /nix/store/cafixfv42cfn63g8bbg592rxkrhnsmp9-lxd.tar.xz /nix/store/z3inz6kkrwj5nzn7d46av7iyfp7j926h-rootfs.tar.xz --alias alpine\r\nmachine # To start your first container, try: lxc launch ubuntu:20.04\r\nmachine # Or for a virtual machine: lxc launch ubuntu:20.04 --vm\r\nmachine # \r\n(finished: must succeed: lxc image import /nix/store/cafixfv42cfn63g8bbg592rxkrhnsmp9-lxd.tar.xz /nix/store/z3inz6kkrwj5nzn7d46av7iyfp7j926h-rootfs.tar.xz --alias alpine, in 2.94 seconds)\r\nsubtest: Containers can be launched and destroyed\r\nmachine: must succeed: lxc launch alpine test\r\nmachine # Error: Failed creating instance record: Requested architecture isn't supported by this host\r\nmachine: output: Creating test\r\n\r\nTest \"Containers can be launched and destroyed\" failed with error: \"command `lxc launch alpine test` failed (exit code 1)\"\r\n```\r\n\r\n/cc @patryk27","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170395/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170389","id":1215608062,"node_id":"I_kwDOAEVQ_M5IdLT-","number":170389,"title":"Update rtl-sdr to 0.8.0","user":{"login":"QuantMint","id":24614168,"node_id":"MDQ6VXNlcjI0NjE0MTY4","avatar_url":"https://avatars.githubusercontent.com/u/24614168?v=4","gravatar_id":"","url":"https://api.github.com/users/QuantMint","html_url":"https://github.com/QuantMint","followers_url":"https://api.github.com/users/QuantMint/followers","following_url":"https://api.github.com/users/QuantMint/following{/other_user}","gists_url":"https://api.github.com/users/QuantMint/gists{/gist_id}","starred_url":"https://api.github.com/users/QuantMint/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/QuantMint/subscriptions","organizations_url":"https://api.github.com/users/QuantMint/orgs","repos_url":"https://api.github.com/users/QuantMint/repos","events_url":"https://api.github.com/users/QuantMint/events{/privacy}","received_events_url":"https://api.github.com/users/QuantMint/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"markuskowa","id":26470037,"node_id":"MDQ6VXNlcjI2NDcwMDM3","avatar_url":"https://avatars.githubusercontent.com/u/26470037?v=4","gravatar_id":"","url":"https://api.github.com/users/markuskowa","html_url":"https://github.com/markuskowa","followers_url":"https://api.github.com/users/markuskowa/followers","following_url":"https://api.github.com/users/markuskowa/following{/other_user}","gists_url":"https://api.github.com/users/markuskowa/gists{/gist_id}","starred_url":"https://api.github.com/users/markuskowa/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/markuskowa/subscriptions","organizations_url":"https://api.github.com/users/markuskowa/orgs","repos_url":"https://api.github.com/users/markuskowa/repos","events_url":"https://api.github.com/users/markuskowa/events{/privacy}","received_events_url":"https://api.github.com/users/markuskowa/received_events","type":"User","site_admin":false},"assignees":[{"login":"markuskowa","id":26470037,"node_id":"MDQ6VXNlcjI2NDcwMDM3","avatar_url":"https://avatars.githubusercontent.com/u/26470037?v=4","gravatar_id":"","url":"https://api.github.com/users/markuskowa","html_url":"https://github.com/markuskowa","followers_url":"https://api.github.com/users/markuskowa/followers","following_url":"https://api.github.com/users/markuskowa/following{/other_user}","gists_url":"https://api.github.com/users/markuskowa/gists{/gist_id}","starred_url":"https://api.github.com/users/markuskowa/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/markuskowa/subscriptions","organizations_url":"https://api.github.com/users/markuskowa/orgs","repos_url":"https://api.github.com/users/markuskowa/repos","events_url":"https://api.github.com/users/markuskowa/events{/privacy}","received_events_url":"https://api.github.com/users/markuskowa/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-04-26T08:39:10Z","updated_at":"2022-04-26T11:36:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: rtl-sdr\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.6.0\r\ndesired version: 0.8.0\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @bjornfor \r\n\r\n###### Note for maintainers\r\n\r\nThis package is currenty using git://git.osmocom.org/rtl-sdr.git but it should probably switch to https://github.com/librtlsdr/librtlsdr\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170389/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170373","id":1215368997,"node_id":"I_kwDOAEVQ_M5IcQ8l","number":170373,"title":"Enabling services.hardware.xow breaks","user":{"login":"lasers","id":852504,"node_id":"MDQ6VXNlcjg1MjUwNA==","avatar_url":"https://avatars.githubusercontent.com/u/852504?v=4","gravatar_id":"","url":"https://api.github.com/users/lasers","html_url":"https://github.com/lasers","followers_url":"https://api.github.com/users/lasers/followers","following_url":"https://api.github.com/users/lasers/following{/other_user}","gists_url":"https://api.github.com/users/lasers/gists{/gist_id}","starred_url":"https://api.github.com/users/lasers/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lasers/subscriptions","organizations_url":"https://api.github.com/users/lasers/orgs","repos_url":"https://api.github.com/users/lasers/repos","events_url":"https://api.github.com/users/lasers/events{/privacy}","received_events_url":"https://api.github.com/users/lasers/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-26T04:21:20Z","updated_at":"2022-04-27T14:48:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nEnabling services.hardware.`xow` (as a systemd service) breaks.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add `services.hardware.xow.enable = true;`\r\n2. `sudo nixos-rebuild switch --upgrade`\r\n3. An error about `git: command not found` and several other errors like \"has not been declared\", \"does not name a type\", etc.\r\n\r\n### Expected behavior\r\n\r\nTo rebuild xow and everything else without any issues.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@jansol \r\n\r\n### Metadata\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre372388.87d34a6b898`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(chris): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170373/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170372","id":1215367162,"node_id":"I_kwDOAEVQ_M5IcQf6","number":170372,"title":"Unicode Sinhala font by Lanka Linux User Group\"","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T04:18:32Z","updated_at":"2022-04-26T04:18:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\n_describe the project a little_\r\n\r\n**Metadata**\r\n\r\n* homepage URL: http://www.lug.lk/fonts/lklug\r\n* source URL: http://archive.ubuntu.com/ubuntu/pool/main/f/fonts-lklug-sinhala/fonts-lklug-sinhala_0.6.orig.tar.xz\r\n* license: gpl2Plus\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170372/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170369","id":1215350515,"node_id":"I_kwDOAEVQ_M5IcMbz","number":170369,"title":"SIL Padauk - Burmese Unicode 6 TrueType font","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T03:50:58Z","updated_at":"2022-04-26T03:50:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAdd SIL Padauk - Burmese Unicode 6 TrueType font.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://software.sil.org/padauk\r\n* source URL: http://archive.ubuntu.com/ubuntu/pool/main/f/fonts-sil-padauk/fonts-sil-padauk_3.003.orig.tar.xz\r\n* license: ofl\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170369/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170361","id":1215284395,"node_id":"I_kwDOAEVQ_M5Ib8Sr","number":170361,"title":"Update Pantheon to version 7","user":{"login":"bobby285271","id":20080233,"node_id":"MDQ6VXNlcjIwMDgwMjMz","avatar_url":"https://avatars.githubusercontent.com/u/20080233?v=4","gravatar_id":"","url":"https://api.github.com/users/bobby285271","html_url":"https://github.com/bobby285271","followers_url":"https://api.github.com/users/bobby285271/followers","following_url":"https://api.github.com/users/bobby285271/following{/other_user}","gists_url":"https://api.github.com/users/bobby285271/gists{/gist_id}","starred_url":"https://api.github.com/users/bobby285271/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bobby285271/subscriptions","organizations_url":"https://api.github.com/users/bobby285271/orgs","repos_url":"https://api.github.com/users/bobby285271/repos","events_url":"https://api.github.com/users/bobby285271/events{/privacy}","received_events_url":"https://api.github.com/users/bobby285271/received_events","type":"User","site_admin":false},"labels":[{"id":1207068537,"node_id":"MDU6TGFiZWwxMjA3MDY4NTM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20pantheon","name":"6.topic: pantheon","color":"fef2c0","default":false,"description":"The Pantheon desktop environment"}],"state":"open","locked":false,"assignee":{"login":"bobby285271","id":20080233,"node_id":"MDQ6VXNlcjIwMDgwMjMz","avatar_url":"https://avatars.githubusercontent.com/u/20080233?v=4","gravatar_id":"","url":"https://api.github.com/users/bobby285271","html_url":"https://github.com/bobby285271","followers_url":"https://api.github.com/users/bobby285271/followers","following_url":"https://api.github.com/users/bobby285271/following{/other_user}","gists_url":"https://api.github.com/users/bobby285271/gists{/gist_id}","starred_url":"https://api.github.com/users/bobby285271/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bobby285271/subscriptions","organizations_url":"https://api.github.com/users/bobby285271/orgs","repos_url":"https://api.github.com/users/bobby285271/repos","events_url":"https://api.github.com/users/bobby285271/events{/privacy}","received_events_url":"https://api.github.com/users/bobby285271/received_events","type":"User","site_admin":false},"assignees":[{"login":"bobby285271","id":20080233,"node_id":"MDQ6VXNlcjIwMDgwMjMz","avatar_url":"https://avatars.githubusercontent.com/u/20080233?v=4","gravatar_id":"","url":"https://api.github.com/users/bobby285271","html_url":"https://github.com/bobby285271","followers_url":"https://api.github.com/users/bobby285271/followers","following_url":"https://api.github.com/users/bobby285271/following{/other_user}","gists_url":"https://api.github.com/users/bobby285271/gists{/gist_id}","starred_url":"https://api.github.com/users/bobby285271/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bobby285271/subscriptions","organizations_url":"https://api.github.com/users/bobby285271/orgs","repos_url":"https://api.github.com/users/bobby285271/repos","events_url":"https://api.github.com/users/bobby285271/events{/privacy}","received_events_url":"https://api.github.com/users/bobby285271/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-04-26T02:38:02Z","updated_at":"2022-04-26T04:06:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Tracking issue for Pantheon 7 (see #121847 for Pantheon 6).\r\n\r\nVisit [the project board](https://github.com/NixOS/nixpkgs/projects/21) for lists of random notes that needs attention and [this page](https://bobby285271.github.io/what-changed/) for lists of upstream updates that needs review.\r\n\r\ncc @NixOS/pantheon\r\n\r\n#### FAQ\r\n\r\n> Feel free to add more if you can edit this issue.\r\n\r\n##### Can we have Pantheon 7 in NixOS 22.05 / 22.11?\r\n\r\nProbably, it depends on upstream release schedule. But this shouldn't become a blocker for NixOS 22.05 / 22.11.\r\n\r\n##### Merge time for #130380 sounds too long for me, can updates happen faster?\r\n\r\nSome updates need to be addressed together ([see the project board](https://github.com/NixOS/nixpkgs/projects/21)), I try to split updates into small PRs when the update harmonize with existing parts well. We always merge things when it is ready.\r\n\r\n##### How to test a Pantheon update?\r\n\r\nFor flake users, you can try https://github.com/bobby285271/test-pantheon.\r\n\r\nFor non-flake users, use:\r\n\r\n```\r\n$ env NIX_PATH=nixpkgs=/path/to/nixpkgs:nixos-config=/path/to/configuration.nix nixos-rebuild build-vm\r\n```\r\n\r\nDo not forget to adjust the path to the nixpkgs checkout `/path/to/nixpkgs` and the configuration `/path/to/configuration.nix`.\r\n\r\n##### Why don't handle the following error for me?\r\n\r\n```\r\nFailed assertions:\r\n- You have set services.power-profiles-daemon.enable = true;\r\nwhich conflicts with services.tlp.enable = true;\r\n```\r\n\r\nI am following what is done in GNOME. We have no way of knowing which way a user wants to resolve the conflict.\r\n\r\nTo disable tlp: `services.tlp.enable = false;`.\r\nTo disable power-profiles-daemon: `services.power-profiles-daemon.enable = false;`.\r\n\r\n##### Why granite 7 is packaged as a separate package?\r\n\r\nIn short, granite 6 is for GTK3 apps and granite 7 is for GTK4 apps. I don't really have the time and knowledge to port the world to GTK4.\r\n\r\n##### Why latest mutter and gsd?\r\n\r\nCurrent latest is 42, which is shipped in ubuntu 22.04 and elementary OS 7.\r\n\r\nBy using the latest we can prevent duplicate work in mutter & gsd maintenance. I will explicitly pin them to 42 a few weeks before GNOME 43 happens. I plan to stick with 42 before elementary OS 8 is out due to all of those weird issues when using 3.38 on Pantheon 6.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170361/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170353","id":1215240442,"node_id":"I_kwDOAEVQ_M5Ibxj6","number":170353,"title":"Add SIL Abyssinica font","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T01:38:28Z","updated_at":"2022-04-26T01:38:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nIt'a a Unicode font for Ethiopian and Erythrean scripts.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: http://scripts.sil.org/AbyssinicaSIL\r\n* source URL: http://archive.ubuntu.com/ubuntu/pool/main/f/fonts-sil-abyssinica/fonts-sil-abyssinica_1.500.orig.tar.xz\r\n* license: ofl\r\n* platforms: all","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170353/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170352","id":1215236950,"node_id":"I_kwDOAEVQ_M5IbwtW","number":170352,"title":"kalendar: Icon theme \"breeze\" not found.","user":{"login":"anthr76","id":25143877,"node_id":"MDQ6VXNlcjI1MTQzODc3","avatar_url":"https://avatars.githubusercontent.com/u/25143877?v=4","gravatar_id":"","url":"https://api.github.com/users/anthr76","html_url":"https://github.com/anthr76","followers_url":"https://api.github.com/users/anthr76/followers","following_url":"https://api.github.com/users/anthr76/following{/other_user}","gists_url":"https://api.github.com/users/anthr76/gists{/gist_id}","starred_url":"https://api.github.com/users/anthr76/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/anthr76/subscriptions","organizations_url":"https://api.github.com/users/anthr76/orgs","repos_url":"https://api.github.com/users/anthr76/repos","events_url":"https://api.github.com/users/anthr76/events{/privacy}","received_events_url":"https://api.github.com/users/anthr76/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-26T01:34:19Z","updated_at":"2022-04-26T18:27:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nkalendar fails to launch.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p kalendar` on unstable\r\n\r\n\r\n### Expected behavior\r\nThe application starts\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\n\r\n```\r\nQML debugging is enabled. Only use this in a safe environment.\r\nIcon theme \"breeze\" not found.\r\nIcon theme \"breeze\" not found.\r\nfish: Job 1, 'kalendar' terminated by signal SIGSEGV (Address boundary error)\r\n```\r\n\r\nAlso do we really need QML debugging?\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@SuperSandro2000 \r\n@hqurve \r\n@chuangzhu\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n~~> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(anthonyjrabbito): `\"latest-22.05pre369988.1ffba9f2f68, nixos-21.11.337114.9887f024766\"`\r\n - nixpkgs: `/nix/store/vixwi1vkcmhfj2lcc1x5mjf70jdsgrgk-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170352/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170350","id":1215229485,"node_id":"I_kwDOAEVQ_M5Ibu4t","number":170350,"title":"warn/prevent version bumps without hash updates","user":{"login":"a-m-joseph","id":54836058,"node_id":"MDQ6VXNlcjU0ODM2MDU4","avatar_url":"https://avatars.githubusercontent.com/u/54836058?v=4","gravatar_id":"","url":"https://api.github.com/users/a-m-joseph","html_url":"https://github.com/a-m-joseph","followers_url":"https://api.github.com/users/a-m-joseph/followers","following_url":"https://api.github.com/users/a-m-joseph/following{/other_user}","gists_url":"https://api.github.com/users/a-m-joseph/gists{/gist_id}","starred_url":"https://api.github.com/users/a-m-joseph/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a-m-joseph/subscriptions","organizations_url":"https://api.github.com/users/a-m-joseph/orgs","repos_url":"https://api.github.com/users/a-m-joseph/repos","events_url":"https://api.github.com/users/a-m-joseph/events{/privacy}","received_events_url":"https://api.github.com/users/a-m-joseph/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-26T01:25:18Z","updated_at":"2022-04-26T01:26:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI build all my own packages (`--option trusted-substituters \"\"`), \"nixtoo\" style. Most of the time I don't even use cachix for FODs (`--option substituters \"\"`). I wish more people did this, clearly I don't have much company.\r\n\r\nI've been running into a surprising number of hash mismatches, like #170349.\r\n\r\nMost of these are due to version-bump commits that change the version but don't update the hash. Since everybody else is pulling from cachix, and cachix already has the old source code with the old hash, and is happy to serve it to people asking for the new source code with the old hash, I'm the only one that notices.\r\n\r\nEverybody else is actually running old versions of software when they think they're running new versions!\r\n\r\nThis is pretty crazy. We really need a way to catch this kind of mistake automatically. It's far more prevalent than you think.\r\n\r\nHere's one idea: require that if an FOD has the same output-hash as an FOD already in the store (or drawn from a substituter), then they must have the same `${pname}-${version}`; else abort with an error message. There's probably a better way to do this. But it is a problem that needs to get fixed.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170347","id":1215190798,"node_id":"I_kwDOAEVQ_M5IblcO","number":170347,"title":"Btrfs not compressing nix/store where zfs does","user":{"login":"jrgiacone","id":71910145,"node_id":"MDQ6VXNlcjcxOTEwMTQ1","avatar_url":"https://avatars.githubusercontent.com/u/71910145?v=4","gravatar_id":"","url":"https://api.github.com/users/jrgiacone","html_url":"https://github.com/jrgiacone","followers_url":"https://api.github.com/users/jrgiacone/followers","following_url":"https://api.github.com/users/jrgiacone/following{/other_user}","gists_url":"https://api.github.com/users/jrgiacone/gists{/gist_id}","starred_url":"https://api.github.com/users/jrgiacone/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jrgiacone/subscriptions","organizations_url":"https://api.github.com/users/jrgiacone/orgs","repos_url":"https://api.github.com/users/jrgiacone/repos","events_url":"https://api.github.com/users/jrgiacone/events{/privacy}","received_events_url":"https://api.github.com/users/jrgiacone/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-26T00:34:36Z","updated_at":"2022-04-26T18:25:04Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen building the system in a vm to test out which file system I will use I noticed btrfs taking up much more space than zfs at default settings. The only difference was the nix/store was on btrfs not compressing all my files such as ghc.\r\n\r\nBoth Files have the same configuration with the corresponding file system adds.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. create two separate vm using zstd with a zfs pool and btrfs forced-compression=zstd (note for btrfs you will have to edit the hardware-config file and manually add options as these do not get run on their own)\r\n2. Build xmonad which will pull ghc 9.0.2 (using untable)\r\n\r\n### Expected behavior\r\nWith the same compression levels and zstd, I expect the compression to be equivalent.\r\n\r\nncdu for Btrfs:\r\n\r\n\r\nncdu for Zfs:\r\n\r\n\r\n\r\n\r\n### Notify maintainers\r\nI'm sorry I could not find a btrfs\r\n\r\n### Metadata\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170347/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170279","id":1214701512,"node_id":"I_kwDOAEVQ_M5IZt_I","number":170279,"title":"Nodejs inside docker image using dockerTools.buildImage cannot start in NixOS (but starts in Ubuntu)","user":{"login":"CMCDragonkai","id":640797,"node_id":"MDQ6VXNlcjY0MDc5Nw==","avatar_url":"https://avatars.githubusercontent.com/u/640797?v=4","gravatar_id":"","url":"https://api.github.com/users/CMCDragonkai","html_url":"https://github.com/CMCDragonkai","followers_url":"https://api.github.com/users/CMCDragonkai/followers","following_url":"https://api.github.com/users/CMCDragonkai/following{/other_user}","gists_url":"https://api.github.com/users/CMCDragonkai/gists{/gist_id}","starred_url":"https://api.github.com/users/CMCDragonkai/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/CMCDragonkai/subscriptions","organizations_url":"https://api.github.com/users/CMCDragonkai/orgs","repos_url":"https://api.github.com/users/CMCDragonkai/repos","events_url":"https://api.github.com/users/CMCDragonkai/events{/privacy}","received_events_url":"https://api.github.com/users/CMCDragonkai/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""},{"id":2484660663,"node_id":"MDU6TGFiZWwyNDg0NjYwNjYz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.%20topic:%20docker%20tools","name":"6. topic: docker tools","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-25T15:39:39Z","updated_at":"2022-04-26T20:40:35Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using `dockerTools.buildImage` with just `nodejs` as the only contents, it is not possible to run the `/bin/node` inside the container **in NixOS**. But it does work in Ubuntu 22.04.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n\r\n```nix\r\n dockerTools.buildImage {\r\n name = \"nodejs\";\r\n contents = [ nodejs ];\r\n keepContentsDirlinks = true;\r\n extraCommands = ''\r\n mkdir -m 1777 tmp\r\n '';\r\n };\r\n```\r\n\r\nBuild that with `nix-build` or `nix repl`, and then load it and run:\r\n\r\n```\r\nloaded=\"$(docker load --input \"$(nix-build ./default.nix)\")\"\r\nimage=\"$(cut -d' ' -f3 <<< \"$loaded\")\"\r\ndocker run -it \"$image\" /bin/node\r\n```\r\n\r\nResults in:\r\n\r\n```\r\n/bin/node[1]: ../src/node_platform.cc:61:std::unique_ptr<long unsigned int> node::WorkerThreadsTaskRunner::DelayedTaskScheduler::Start(): Assertion `(0) == (uv_thread_create(t.get(), start_thread, this))' failed.\r\n 1: 0xa64dd8 node::Abort() [/bin/node]\r\n 2: 0xa64e67 [/bin/node]\r\n 3: 0xae5f75 node::WorkerThreadsTaskRunner::WorkerThreadsTaskRunner(int) [/bin/node]\r\n 4: 0xae60a2 node::NodePlatform::NodePlatform(int, v8::TracingController*) [/bin/node]\r\n 5: 0xa24d2f node::V8Platform::Initialize(int) [/bin/node]\r\n 6: 0xa2304b node::InitializeOncePerProcess(int, char**, node::InitializationSettingsFlags, node::ProcessFlags::Flags) [/bin/node]\r\n 7: 0xa231d9 node::InitializeOncePerProcess(int, char**) [/bin/node]\r\n 8: 0xa23238 node::Start(int, char**) [/bin/node]\r\n 9: 0x7f1c2eaf91d7 [/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6]\r\n10: 0x7f1c2eaf9297 __libc_start_main [/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/libc.so.6]\r\n11: 0x989ce1 _start [/bin/node]\r\n```\r\n\r\n### Expected behavior\r\n\r\nIt should just run the node repl.\r\n\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Metadata\r\n\r\nI'm pinned on a5774e76bb8c3145eac524be62375c937143b80c as the nixpkgs commit revision.\r\n\r\nRunning on NixOS\r\n\r\n```\r\n»» ~\r\n ♖ nix-shell -p nix-info --run \"nix-info -m\" pts/3 1:41:14\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, Matrix Vostro 5402 1, noversion`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n\r\nAnd my NixOS nixpkgs revision is d89f18a17e51532ed5f4d45297b0ddf11e46b9c8","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170279/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170254","id":1214545769,"node_id":"I_kwDOAEVQ_M5IZH9p","number":170254,"title":"spacedrive: Packaging request","user":{"login":"khrj","id":44947946,"node_id":"MDQ6VXNlcjQ0OTQ3OTQ2","avatar_url":"https://avatars.githubusercontent.com/u/44947946?v=4","gravatar_id":"","url":"https://api.github.com/users/khrj","html_url":"https://github.com/khrj","followers_url":"https://api.github.com/users/khrj/followers","following_url":"https://api.github.com/users/khrj/following{/other_user}","gists_url":"https://api.github.com/users/khrj/gists{/gist_id}","starred_url":"https://api.github.com/users/khrj/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/khrj/subscriptions","organizations_url":"https://api.github.com/users/khrj/orgs","repos_url":"https://api.github.com/users/khrj/repos","events_url":"https://api.github.com/users/khrj/events{/privacy}","received_events_url":"https://api.github.com/users/khrj/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-25T13:50:02Z","updated_at":"2022-04-25T15:51:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nCross platform file manager supporting cloud providers\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.spacedrive.app/\r\n* source URL: https://github.com/spacedriveapp/spacedrive\r\n* license: GPL-3.0\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170254/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170203","id":1214026966,"node_id":"I_kwDOAEVQ_M5IXJTW","number":170203,"title":"GoTrue","user":{"login":"J0","id":8011761,"node_id":"MDQ6VXNlcjgwMTE3NjE=","avatar_url":"https://avatars.githubusercontent.com/u/8011761?v=4","gravatar_id":"","url":"https://api.github.com/users/J0","html_url":"https://github.com/J0","followers_url":"https://api.github.com/users/J0/followers","following_url":"https://api.github.com/users/J0/following{/other_user}","gists_url":"https://api.github.com/users/J0/gists{/gist_id}","starred_url":"https://api.github.com/users/J0/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/J0/subscriptions","organizations_url":"https://api.github.com/users/J0/orgs","repos_url":"https://api.github.com/users/J0/repos","events_url":"https://api.github.com/users/J0/events{/privacy}","received_events_url":"https://api.github.com/users/J0/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-25T06:19:32Z","updated_at":"2022-04-25T06:19:32Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nHoping to package GoTrue: https://github.com/supabase/gotrue\r\n\r\nWill do it if there's no one else who's keen to take it up\r\n\r\nRelates to #159878\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/supabase/gotrue\r\n* source URL: https://github.com/supabase/gotrue\r\n* license: Apache2\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170203/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170186","id":1213905153,"node_id":"I_kwDOAEVQ_M5IWrkB","number":170186,"title":"`gstreamermm` fails to build","user":{"login":"austinbutler","id":354741,"node_id":"MDQ6VXNlcjM1NDc0MQ==","avatar_url":"https://avatars.githubusercontent.com/u/354741?v=4","gravatar_id":"","url":"https://api.github.com/users/austinbutler","html_url":"https://github.com/austinbutler","followers_url":"https://api.github.com/users/austinbutler/followers","following_url":"https://api.github.com/users/austinbutler/following{/other_user}","gists_url":"https://api.github.com/users/austinbutler/gists{/gist_id}","starred_url":"https://api.github.com/users/austinbutler/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/austinbutler/subscriptions","organizations_url":"https://api.github.com/users/austinbutler/orgs","repos_url":"https://api.github.com/users/austinbutler/repos","events_url":"https://api.github.com/users/austinbutler/events{/privacy}","received_events_url":"https://api.github.com/users/austinbutler/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-25T03:17:03Z","updated_at":"2022-04-26T16:29:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`gstreamermm` fails to build. Seems to be [due to GCC 11 upgrade](https://gitlab.gnome.org/GNOME/gstreamermm/-/issues/11). A [fix has been merged upstream](https://gitlab.gnome.org/GNOME/gstreamermm/-/merge_requests/4). That said, the project is mostly abandoned. The last release was 4 years ago, and they recommend building from a release since building from source is much harder. I can confirm, as I am unable to make it build from source (but then again for me autotools is like discovering ancient tablets in the sand with hieroglyphs on them).\r\n\r\nThere are only a few packages that depend on `gstreamermm`. If it's too much hassle to get working may just want to retire these.\r\n\r\n- [obs-gstreamer](https://search.nixos.org/packages?channel=unstable&from=0&size=50&sort=relevance&type=packages&query=obs-gstreamer)\r\n- [subtitleeditor](https://search.nixos.org/packages?channel=unstable&from=0&size=50&sort=relevance&type=packages&query=subtitleeditor)\r\n- [mapmap](https://search.nixos.org/packages?channel=unstable&from=0&size=50&sort=relevance&type=packages&query=mapmap)\r\n\r\n### Steps To Reproduce\r\n\r\n1. `nix-build -A gst_all_1.gstreamermm`\r\n\r\n### Expected behavior\r\n\r\nBuild works.\r\n\r\n### Additional context\r\n\r\nEnd of log from building on current `master`:\r\n\r\n```\r\nmake[2]: Leaving directory '/build/gstreamermm-1.10.0/gstreamer/gstreamermm'\r\nMaking all in tests\r\nmake[2]: Entering directory '/build/gstreamermm-1.10.0/tests'\r\nmake[2]: Nothing to be done for 'all'.\r\nmake[2]: Leaving directory '/build/gstreamermm-1.10.0/tests'\r\nMaking all in examples\r\nmake[2]: Entering directory '/build/gstreamermm-1.10.0/examples'\r\n CXX audio_video_muxer/main.o\r\n CXX all_media_player/main.o\r\n CXX dynamic_changing_source/main.o\r\nIn file included from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gasyncqueue.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib.h:32,\r\n from /nix/store/x5balm62kwx33v3psj33q558z5aclg6b-glibmm-2.66.2-dev/include/glibmm-2.4/glibmm/threads.h:30,\r\n from ../gstreamer/gstreamermm/check.h:11,\r\n from ../gstreamer/gstreamermm.h:63,\r\n from audio_video_muxer/main.cc:8:\r\n../gstreamer/gstreamermm/register.h: In function 'GType Gst::register_mm_type(const gchar*)':\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gatomic.h:113:19: error: argument 2 of '__atomic_load' must not be a pointer to a 'volatile' type\r\n 113 | __atomic_load (gapg_temp_atomic, &gapg_temp_newval, __ATOMIC_SEQ_CST); \\\r\n | ~~~~~~~~~~~~~~^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:260:7: note: in expansion of macro 'g_atomic_pointer_get'\r\n 260 | (!g_atomic_pointer_get (location) && \\\r\n | ^~~~~~~~~~~~~~~~~~~~\r\n../gstreamer/gstreamermm/register.h:114:9: note: in expansion of macro 'g_once_init_enter'\r\n 114 | if (g_once_init_enter (&gonce_data)) {\r\n | ^~~~~~~~~~~~~~~~~\r\nIn file included from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gasyncqueue.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib.h:32,\r\n from /nix/store/x5balm62kwx33v3psj33q558z5aclg6b-glibmm-2.66.2-dev/include/glibmm-2.4/glibmm/threads.h:30,\r\n from ../gstreamer/gstreamermm/check.h:11,\r\n from ../gstreamer/gstreamermm.h:63,\r\n from all_media_player/main.cc:8:\r\n../gstreamer/gstreamermm/register.h: In function 'GType Gst::register_mm_type(const gchar*)':\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gatomic.h:113:19: error: argument 2 of '__atomic_load' must not be a pointer to a 'volatile' type\r\n 113 | __atomic_load (gapg_temp_atomic, &gapg_temp_newval, __ATOMIC_SEQ_CST); \\\r\n | ~~~~~~~~~~~~~~^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:260:7: note: in expansion of macro 'g_atomic_pointer_get'\r\n 260 | (!g_atomic_pointer_get (location) && \\\r\n | ^~~~~~~~~~~~~~~~~~~~\r\n../gstreamer/gstreamermm/register.h:114:9: note: in expansion of macro 'g_once_init_enter'\r\n 114 | if (g_once_init_enter (&gonce_data)) {\r\n | ^~~~~~~~~~~~~~~~~\r\nmake[2]: *** [Makefile:829: audio_video_muxer/main.o] Error 1\r\nmake[2]: *** Waiting for unfinished jobs....\r\nmake[2]: *** [Makefile:829: all_media_player/main.o] Error 1\r\nIn file included from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gasyncqueue.h:32,\r\n from /nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib.h:32,\r\n from /nix/store/x5balm62kwx33v3psj33q558z5aclg6b-glibmm-2.66.2-dev/include/glibmm-2.4/glibmm/threads.h:30,\r\n from ../gstreamer/gstreamermm/check.h:11,\r\n from ../gstreamer/gstreamermm.h:63,\r\n from dynamic_changing_source/main.cc:7:\r\n../gstreamer/gstreamermm/register.h: In function 'GType Gst::register_mm_type(const gchar*)':\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gatomic.h:113:19: error: argument 2 of '__atomic_load' must not be a pointer to a 'volatile' type\r\n 113 | __atomic_load (gapg_temp_atomic, &gapg_temp_newval, __ATOMIC_SEQ_CST); \\\r\n | ~~~~~~~~~~~~~~^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/nix/store/ajl4sxhfgqzch5cnwq9rlsk19wxkq13n-glib-2.72.0-dev/include/glib-2.0/glib/gthread.h:260:7: note: in expansion of macro 'g_atomic_pointer_get'\r\n 260 | (!g_atomic_pointer_get (location) && \\\r\n | ^~~~~~~~~~~~~~~~~~~~\r\n../gstreamer/gstreamermm/register.h:114:9: note: in expansion of macro 'g_once_init_enter'\r\n 114 | if (g_once_init_enter (&gonce_data)) {\r\n | ^~~~~~~~~~~~~~~~~\r\nmake[2]: *** [Makefile:829: dynamic_changing_source/main.o] Error 1\r\nmake[2]: Leaving directory '/build/gstreamermm-1.10.0/examples'\r\nmake[1]: *** [Makefile:607: all-recursive] Error 1\r\nmake[1]: Leaving directory '/build/gstreamermm-1.10.0'\r\nmake: *** [Makefile:461: all] Error 2\r\nerror: builder for '/nix/store/h3xignaxqd14g4aniv3ajfx7mcihw3l3-gstreamermm-1.10.0.drv' failed with exit code 2;\r\n```\r\n\r\nEnd of log trying to build from source:\r\n\r\n```\r\nmake all-recursive\r\nmake[1]: Entering directory '/home/austin/Documents/gstreamermm'\r\nMaking all in tools\r\nmake[2]: Entering directory '/home/austin/Documents/gstreamermm/tools'\r\n CXX extra_defs_gen/generate_defs_gst.o\r\n CXXLD extra_defs_gen/generate_defs_gst\r\n CXX extra_defs_gen/generate_plugin_module_defs_gst.o\r\n CXXLD extra_defs_gen/generate_plugin_module_defs_gst\r\n CXX extra_defs_gen/generate_plugin_gmmproc_file.o\r\nextra_defs_gen/generate_plugin_gmmproc_file.cc:386:13: warning: Deprecated pre-processor symbol: replace with \"(g_array_get_type ())\"\r\n 386 | returnGType != G_TYPE_VALUE_ARRAY &&\r\n | ^ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n CXXLD extra_defs_gen/generate_plugin_gmmproc_file\r\nmake[2]: Leaving directory '/home/austin/Documents/gstreamermm/tools'\r\nMaking all in gstreamer/gstreamermm\r\nmake[2]: Entering directory '/home/austin/Documents/gstreamermm/gstreamer/gstreamermm'\r\nmake[2]: *** No rule to make target 'allocator.cc', needed by 'allocator.lo'. Stop.\r\nmake[2]: Leaving directory '/home/austin/Documents/gstreamermm/gstreamer/gstreamermm'\r\nmake[1]: *** [Makefile:610: all-recursive] Error 1\r\nmake[1]: Leaving directory '/home/austin/Documents/gstreamermm'\r\nmake: *** [Makefile:464: all] Error 2\r\n```\r\n\r\n\r\n### Notify maintainers\r\n\r\n@alesya-h @plcplc @erictapen @romildo \r\n\r\n### Metadata\r\n\r\n```yaml\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre372012.bc41b01dd7a`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"home-manager, nixos\"`\r\n - channels(austin): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170186/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170167","id":1213819092,"node_id":"I_kwDOAEVQ_M5IWWjU","number":170167,"title":"Thunar segfault after a background process finishes","user":{"login":"lucasew","id":15693688,"node_id":"MDQ6VXNlcjE1NjkzNjg4","avatar_url":"https://avatars.githubusercontent.com/u/15693688?v=4","gravatar_id":"","url":"https://api.github.com/users/lucasew","html_url":"https://github.com/lucasew","followers_url":"https://api.github.com/users/lucasew/followers","following_url":"https://api.github.com/users/lucasew/following{/other_user}","gists_url":"https://api.github.com/users/lucasew/gists{/gist_id}","starred_url":"https://api.github.com/users/lucasew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lucasew/subscriptions","organizations_url":"https://api.github.com/users/lucasew/orgs","repos_url":"https://api.github.com/users/lucasew/repos","events_url":"https://api.github.com/users/lucasew/events{/privacy}","received_events_url":"https://api.github.com/users/lucasew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-25T00:41:02Z","updated_at":"2022-04-26T13:32:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nSimple operations happen fine without problem but if an operation spawns a progress bar like a copy of a lot of files or a big file then after the process complete thunar just quits and segfaults.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `dd if=/dev/zero of=somefile.img bs=1M count=10000 status=progress`\r\n2. Browse to where you created that img file using thunar\r\n3. Ctrl+C Ctrl+V -- Just copy and paste the file, can be anywhere.\r\n4. The process will happen nicely with a progress bar but right after it's done thunar will just commit die\r\n\r\n### Expected behavior\r\nThunar keeps working after a long (not trivial) operation\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nSegfault information obtained via `journalctl -f` while the tests were happening.\r\n\r\n```\r\nabr 24 21:27:40 acer-nix kernel: traps: .thunar-wrapped[409861] general protection fault ip:7f724268b023 sp:7ffd325238c0 error:0 in libgtk-3.so.0.2404.29[7f7242316000+379000]\r\nabr 24 21:27:40 acer-nix systemd[1]: Started Process Core Dump (PID 411723/UID 0).\r\nabr 24 21:27:40 acer-nix dhcpcd[2266]: enp2s0f1: requesting DHCPv6 information\r\nabr 24 21:27:42 acer-nix systemd-coredump[411724]: [🡕] Process 409861 (.thunar-wrapped) of user 1000 dumped core.\r\n \r\n Module linux-vdso.so.1 with build-id d91820235c8ef3c8490cfd1b8717b77385bf8b90\r\n Module thunar-wallpaper-plugin.so without build-id.\r\n Module thunar-archive-plugin.so without build-id.\r\n Module librsvg-2.so.2 without build-id.\r\n Module libpixbufloader-svg.so without build-id.\r\n Module libgioremote-volume-monitor.so without build-id.\r\n Module libxfce4kbd-private-3.so.0 without build-id.\r\n Module thunar-uca.so without build-id.\r\n Module libgvfscommon.so without build-id.\r\n Module libgvfsdbus.so without build-id.\r\n Module libxfconfgsettingsbackend.so without build-id.\r\n Module libgpg-error.so.0 without build-id.\r\n Module libgcrypt.so.20 without build-id.\r\n Module libcap.so.2 without build-id.\r\n Module liblz4.so.1 without build-id.\r\n Module libzstd.so.1 without build-id.\r\n Module liblzma.so.5 without build-id.\r\n Module libgcc_s.so.1 without build-id.\r\n Module libstdc++.so.6 without build-id.\r\n Module libicudata.so.70 without build-id.\r\n Module libsystemd.so.0 without build-id.\r\n Module libblkid.so.1 with build-id 61b22bf07a841dc9ed49f9765bc91e0e71267f7e\r\n Module libdatrie.so.1 without build-id.\r\n Module libGLX.so.0 without build-id.\r\n Module libXdmcp.so.6 without build-id.\r\n Module libXau.so.6 without build-id.\r\n Module libGLdispatch.so.0 without build-id.\r\n Module libxml2.so.2 without build-id.\r\n Module libjson-glib-1.0.so.0 without build-id.\r\n Module libsqlite3.so.0 with build-id 6ad9ac43fd4fcec64b7b6dfebe021eef03f898ca\r\n Module libicui18n.so.70 without build-id.\r\n Module libicuuc.so.70 without build-id.\r\n Module libatspi.so.0 without build-id.\r\n Module libdbus-1.so.3 without build-id.\r\n Module libexpat.so.1 without build-id.\r\n Module libbz2.so.1 without build-id.\r\n Module libX11-xcb.so.1 without build-id.\r\n Module libxcb-util.so.1 without build-id.\r\n Module libgraphite2.so.3 without build-id.\r\n Module ld-linux-x86-64.so.2 with build-id 30c57076927b082f79b8e0307c2ade477e78866b\r\n Module libpcre.so.1 without build-id.\r\n Module libffi.so.8 without build-id.\r\n Module libselinux.so.1 without build-id.\r\n Module libmount.so.1 with build-id f09895bf7359bf6b31be1dd2d8b7f0cc54a78ed7\r\n Module libthai.so.0 without build-id.\r\n Module libgthread-2.0.so.0 with build-id b4f5c65b985bccbd6328480e35fb1b525c4168fd\r\n Module libjpeg.so.62 without build-id.\r\n Module libpthread.so.0 with build-id 7e1bb32908f70cf0fc00d66c983160c7b115f188\r\n Module librt.so.1 with build-id f610c78fef64474570c8ba2b5c00427c340d1e84\r\n Module libGL.so.1 without build-id.\r\n Module libXrender.so.1 without build-id.\r\n Module libxcb-render.so.0 without build-id.\r\n Module libxcb.so.1 without build-id.\r\n Module libxcb-shm.so.0 without build-id.\r\n Module libpng16.so.16 without build-id.\r\n Module libdl.so.2 with build-id c06f3da244980c9a6e8e2a1e4d8990a085103471\r\n Module libEGL.so.1 without build-id.\r\n Module libfreetype.so.6 without build-id.\r\n Module libpixman-1.so.0 with build-id e543e4db693226a37e0c1af6b6ee9224c1b47b63\r\n Module libXinerama.so.1 without build-id.\r\n Module libXrandr.so.2 without build-id.\r\n Module libXcomposite.so.1 without build-id.\r\n Module libXcursor.so.1 without build-id.\r\n Module libXext.so.6 without build-id.\r\n Module libwayland-egl.so.1 with build-id a13b79b32a09a96f5df69cc5acadbfda6a509b0f\r\n Module libwayland-cursor.so.0 with build-id 524fd5133c3a6674f347e2c4aa584acc511fcbde\r\n Module libwayland-client.so.0 with build-id 45e2076feb37f91b15990758f811e5e0338a2fb3\r\n Module libxkbcommon.so.0 without build-id.\r\n Module libXfixes.so.3 without build-id.\r\n Module libtracker-sparql-3.0.so.0 without build-id.\r\n Module libatk-bridge-2.0.so.0 without build-id.\r\n Module libXi.so.6 without build-id.\r\n Module libepoxy.so.0 without build-id.\r\n Module libfribidi.so.0 without build-id.\r\n Module libfontconfig.so.1 without build-id.\r\n Module libpangoft2-1.0.so.0 without build-id.\r\n Module libstartup-notification-1.so.0 without build-id.\r\n Module libuuid.so.1 with build-id 5e3c36f16c9a47e9311eb52ca3becf4a885cda3c\r\n Module libudev.so.1 without build-id.\r\n Module libm.so.6 with build-id bb1ad44ec0afbc9acf56402168c25a629dfd7adb\r\n Module libX11.so.6 without build-id.\r\n Module libcairo-gobject.so.2 with build-id 05c4ef277157c7284df9fef6c182cea2d364822a\r\n Module libharfbuzz.so.0 without build-id.\r\n Module libpangocairo-1.0.so.0 without build-id.\r\n Module libz.so.1 without build-id.\r\n Module libgmodule-2.0.so.0 with build-id 4080e7e72c752ae8ab4331f44f085a685a744094\r\n Module libc.so.6 with build-id b2073195a02092e5988e0c88ddbe22da749f69ac\r\n Module libglib-2.0.so.0 with build-id 24d88f2adb3db24c34f9ad621f772b856c7d4a11\r\n Module libgobject-2.0.so.0 with build-id 00e12bb4b861118cda92b66a299d308a69360f3b\r\n Module libgio-2.0.so.0 with build-id a68fb56a72583f7f51403d6ef1e485a4a72a7ced\r\n Module libpango-1.0.so.0 without build-id.\r\n Module libxfconf-0.so.3 without build-id.\r\n Module libxfce4util.so.7 without build-id.\r\n Module libgdk_pixbuf-2.0.so.0 with build-id 2479465a0d6b9071753c6883b013ed7283db85e8\r\n Module libcairo.so.2 with build-id c2905b7a90de8e2d0df5cf44e3efead78eb4e607\r\n Module libatk-1.0.so.0 without build-id.\r\n Module libgdk-3.so.0 with build-id aec011cbef7b06ae5e37135e4742f9f0ae4285ed\r\n Module libgtk-3.so.0 with build-id 0af3db8336812ba0d6360bad8de517c02a49d1b8\r\n Module libxfce4ui-2.so.0 without build-id.\r\n Module libICE.so.6 without build-id.\r\n Module libSM.so.6 without build-id.\r\n Module libnotify.so.4 without build-id.\r\n Module libgudev-1.0.so.0 without build-id.\r\n Module libexo-2.so.0 without build-id.\r\n Module libthunarx-3.so.0 without build-id.\r\n Module .thunar-wrapped without build-id.\r\n Stack trace of thread 409861:\r\n #0 0x00007f724268b023 gtk_tray_icon_manager_filter (libgtk-3.so.0 + 0x408023)\r\n #1 0x00007f724220e11f gdk_event_apply_filters (libgdk-3.so.0 + 0x9511f)\r\n #2 0x00007f724220e452 _gdk_x11_display_queue_events (libgdk-3.so.0 + 0x95452)\r\n #3 0x00007f72421b2660 gdk_display_get_event (libgdk-3.so.0 + 0x39660)\r\n #4 0x00007f724220e1b2 gdk_event_source_dispatch (libgdk-3.so.0 + 0x951b2)\r\n #5 0x00007f7241c26e3b g_main_context_dispatch (libglib-2.0.so.0 + 0x56e3b)\r\n #6 0x00007f7241c270e8 g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x570e8)\r\n #7 0x00007f7241c2719f g_main_context_iteration (libglib-2.0.so.0 + 0x5719f)\r\n #8 0x00007f7241e4a605 g_application_run (libgio-2.0.so.0 + 0xe2605)\r\n #9 0x0000000000423932 main (.thunar-wrapped + 0x23932)\r\n #10 0x00007f72419fe1d7 __libc_start_call_main (libc.so.6 + 0x2d1d7)\r\n #11 0x00007f72419fe297 __libc_start_main@@GLIBC_2.34 (libc.so.6 + 0x2d297)\r\n #12 0x00000000004239c1 _start (.thunar-wrapped + 0x239c1)\r\n \r\n Stack trace of thread 411363:\r\n #0 0x00007f7241ad5cb9 syscall (libc.so.6 + 0x104cb9)\r\n #1 0x00007f7241c7af42 g_cond_wait_until (libglib-2.0.so.0 + 0xaaf42)\r\n #2 0x00007f7241bf5761 g_async_queue_pop_intern_unlocked (libglib-2.0.so.0 + 0x25761)\r\n #3 0x00007f7241c51dea g_thread_pool_thread_proxy (libglib-2.0.so.0 + 0x81dea)\r\n #4 0x00007f7241c513cd g_thread_proxy (libglib-2.0.so.0 + 0x813cd)\r\n #5 0x00007f7241a5aeb2 start_thread (libc.so.6 + 0x89eb2)\r\n #6 0x00007f7241add31c __clone3 (libc.so.6 + 0x10c31c)\r\n \r\n Stack trace of thread 409862:\r\n #0 0x00007f7241ad0f89 __poll (libc.so.6 + 0xfff89)\r\n #1 0x00007f7241c2707e g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x5707e)\r\n #2 0x00007f7241c2719f g_main_context_iteration (libglib-2.0.so.0 + 0x5719f)\r\n #3 0x00007f7241c271f1 glib_worker_main (libglib-2.0.so.0 + 0x571f1)\r\n #4 0x00007f7241c513cd g_thread_proxy (libglib-2.0.so.0 + 0x813cd)\r\n #5 0x00007f7241a5aeb2 start_thread (libc.so.6 + 0x89eb2)\r\n #6 0x00007f7241add31c __clone3 (libc.so.6 + 0x10c31c)\r\n \r\n Stack trace of thread 409863:\r\n #0 0x00007f7241ad0f89 __poll (libc.so.6 + 0xfff89)\r\n #1 0x00007f7241c2707e g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x5707e)\r\n #2 0x00007f7241c273d3 g_main_loop_run (libglib-2.0.so.0 + 0x573d3)\r\n #3 0x00007f7241e861c6 gdbus_shared_thread_func (libgio-2.0.so.0 + 0x11e1c6)\r\n #4 0x00007f7241c513cd g_thread_proxy (libglib-2.0.so.0 + 0x813cd)\r\n #5 0x00007f7241a5aeb2 start_thread (libc.so.6 + 0x89eb2)\r\n #6 0x00007f7241add31c __clone3 (libc.so.6 + 0x10c31c)\r\n \r\n Stack trace of thread 411722:\r\n #0 0x00007f7241ad5cb9 syscall (libc.so.6 + 0x104cb9)\r\n #1 0x00007f7241c7ae1f g_cond_wait (libglib-2.0.so.0 + 0xaae1f)\r\n #2 0x00007f7241deb92b g_io_scheduler_job_send_to_mainloop (libgio-2.0.so.0 + 0x8392b)\r\n #3 0x00007f7242acadd8 exo_job_emit (libexo-2.so.0 + 0x15dd8)\r\n #4 0x0000000000454c75 thunar_job_files_ready (.thunar-wrapped + 0x54c75)\r\n #5 0x0000000000451da2 _thunar_io_jobs_ls (.thunar-wrapped + 0x51da2)\r\n #6 0x000000000047fd93 thunar_simple_job_execute (.thunar-wrapped + 0x7fd93)\r\n #7 0x00007f7242acaa4f exo_job_scheduler_job_func (libexo-2.so.0 + 0x15a4f)\r\n #8 0x00007f7241deb566 io_job_thread (libgio-2.0.so.0 + 0x83566)\r\n #9 0x00007f7241e1d6ae g_task_thread_pool_thread (libgio-2.0.so.0 + 0xb56ae)\r\n #10 0x00007f7241c51c94 g_thread_pool_thread_proxy (libglib-2.0.so.0 + 0x81c94)\r\n #11 0x00007f7241c513cd g_thread_proxy (libglib-2.0.so.0 + 0x813cd)\r\n #12 0x00007f7241a5aeb2 start_thread (libc.so.6 + 0x89eb2)\r\n #13 0x00007f7241add31c __clone3 (libc.so.6 + 0x10c31c)\r\n ELF object binary architecture: AMD x86-64\r\nabr 24 21:27:42 acer-nix systemd[1]: systemd-coredump@5-411723-0.service: Deactivated successfully.\r\n\r\n```\r\n\r\nCurrent commit of my configuration: https://github.com/lucasew/nixcfg/tree/8d7462e0539e122dba52eb7e2b3117bbb3de5898\r\n- Reproduced on `acer-nix`, my only node running NixOS with some gui\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@romildo @worldofpeace @siraben @andresilva \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nlucasew@acer-nix /tmp 0$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/store/j4n45y0r4ybms9vz64wisbffq7hbf78q-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170167/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170147","id":1213776683,"node_id":"I_kwDOAEVQ_M5IWMMr","number":170147,"title":"RetroFE has moved","user":{"login":"armeenm","id":29145250,"node_id":"MDQ6VXNlcjI5MTQ1MjUw","avatar_url":"https://avatars.githubusercontent.com/u/29145250?v=4","gravatar_id":"","url":"https://api.github.com/users/armeenm","html_url":"https://github.com/armeenm","followers_url":"https://api.github.com/users/armeenm/followers","following_url":"https://api.github.com/users/armeenm/following{/other_user}","gists_url":"https://api.github.com/users/armeenm/gists{/gist_id}","starred_url":"https://api.github.com/users/armeenm/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armeenm/subscriptions","organizations_url":"https://api.github.com/users/armeenm/orgs","repos_url":"https://api.github.com/users/armeenm/repos","events_url":"https://api.github.com/users/armeenm/events{/privacy}","received_events_url":"https://api.github.com/users/armeenm/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-24T21:40:29Z","updated_at":"2022-04-24T21:40:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\nLooks like it lives [here](https://github.com/phulshof/RetroFE) and [here](http://retrofe.nl/) now. `retrofe` in nixpkgs hasn't been touched in 6 years.\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.6.169\r\ndesired version: ?\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @hrdinka \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170147/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170143","id":1213771298,"node_id":"I_kwDOAEVQ_M5IWK4i","number":170143,"title":"scipy doesn't build on Darwin","user":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-24T21:16:15Z","updated_at":"2022-04-29T13:21:47Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nscipy doesn't build on Darwin right now (trunk).\r\nHydra: https://hydra.nixos.org/build/173999765\r\n\r\nThe error in Hydra seems to be some builder failure and not actually related to the issue.\r\nIt however fails as well when I try to build on my Mac. We should get rid of both issues.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Try to build `python39Packages.scipy`\r\n\r\n### Expected behavior\r\n\r\nIt builds\r\n\r\n### Additional context\r\n\r\nI don't need this Python module myself but a lot of other packages depend on it.\r\nThis is currently the package with the most dependants (322) that fails so it'd be nice to have this cleaned up before ZHF starts.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@NixOS/darwin-maintainers ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170143/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170125","id":1213745220,"node_id":"I_kwDOAEVQ_M5IWEhE","number":170125,"title":"Support all cmdline options in systemd stage 1","user":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-24T19:25:29Z","updated_at":"2022-04-24T22:41:58Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"These are parsed by stage-1-init.sh:\r\n- [x] console= probably not necessary since systemd handles this\r\n- [x] init= just works\r\n- [ ] boot.persistence=\r\n- [ ] boot.persistence.opt=\r\n- [x] boot.trace `systemd.log_level=debug`\r\n- [x] debugtrace `systemd.log_level=debug`\r\n- [ ] boot.shell_on_fail\r\n- [ ] boot.debug1\r\n- [ ] debug1\r\n- [ ] boot.debug1devices\r\n- [ ] boot.debug1mounts\r\n- [ ] boot.panic_on_fail\r\n- [ ] stage1panic=1\r\n- [x] root= handled by systemd\r\n- [ ] copytoram\r\n- [ ] findiso=\r\n\r\nWe don't need to support them all, just figure out if some of them have no alternative with systemd","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170125/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170095","id":1213660347,"node_id":"I_kwDOAEVQ_M5IVvy7","number":170095,"title":"libclc should be packaged as llvmPackages*.libclc","user":{"login":"primeos","id":7537109,"node_id":"MDQ6VXNlcjc1MzcxMDk=","avatar_url":"https://avatars.githubusercontent.com/u/7537109?v=4","gravatar_id":"","url":"https://api.github.com/users/primeos","html_url":"https://github.com/primeos","followers_url":"https://api.github.com/users/primeos/followers","following_url":"https://api.github.com/users/primeos/following{/other_user}","gists_url":"https://api.github.com/users/primeos/gists{/gist_id}","starred_url":"https://api.github.com/users/primeos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/primeos/subscriptions","organizations_url":"https://api.github.com/users/primeos/orgs","repos_url":"https://api.github.com/users/primeos/repos","events_url":"https://api.github.com/users/primeos/events{/privacy}","received_events_url":"https://api.github.com/users/primeos/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-24T13:49:02Z","updated_at":"2022-04-24T13:49:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"In case someone has time and motivation.\r\n\r\nPrior discussions:\r\n- https://github.com/NixOS/nixpkgs/pull/136402#discussion_r702472564","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170095/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170083","id":1213625529,"node_id":"I_kwDOAEVQ_M5IVnS5","number":170083,"title":"Grafana Mimir","user":{"login":"bryanhonof","id":5932804,"node_id":"MDQ6VXNlcjU5MzI4MDQ=","avatar_url":"https://avatars.githubusercontent.com/u/5932804?v=4","gravatar_id":"","url":"https://api.github.com/users/bryanhonof","html_url":"https://github.com/bryanhonof","followers_url":"https://api.github.com/users/bryanhonof/followers","following_url":"https://api.github.com/users/bryanhonof/following{/other_user}","gists_url":"https://api.github.com/users/bryanhonof/gists{/gist_id}","starred_url":"https://api.github.com/users/bryanhonof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bryanhonof/subscriptions","organizations_url":"https://api.github.com/users/bryanhonof/orgs","repos_url":"https://api.github.com/users/bryanhonof/repos","events_url":"https://api.github.com/users/bryanhonof/events{/privacy}","received_events_url":"https://api.github.com/users/bryanhonof/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-24T11:20:12Z","updated_at":"2022-04-24T18:48:34Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\n[Grafana Mimir](https://github.com/grafana/mimir) provides horizontally scalable, highly available, multi-tenant, long-term storage for Prometheus. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://grafana.com/oss/mimir/\r\n* source URL: https://github.com/grafana/mimir\r\n* license: AGPL-3.0\r\n* platforms: unix\r\n\r\nI'll be using this issue to track my progress.\r\n\r\n- [x] Package Mimir\r\n- [ ] Write a NixOS module to run Mimir in [monolithic mode](https://grafana.com/docs/mimir/latest/operators-guide/architecture/deployment-modes/#monolithic-mode)\r\n- [ ] Write NixOS modules for the multiple components of Mimir to run in [microservices mode](https://grafana.com/docs/mimir/latest/operators-guide/architecture/deployment-modes/#microservices-mode)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170083/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170080","id":1213615380,"node_id":"I_kwDOAEVQ_M5IVk0U","number":170080,"title":"many python builds failing due to DeprecationWarning","user":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-24T10:35:21Z","updated_at":"2022-04-25T00:12:58Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"https://gist.github.com/samuela/f4dad8455762fe70ef44044140081814\r\n\r\nWhy is deprecation warning an error instead of an warning?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170080/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170074","id":1213605278,"node_id":"I_kwDOAEVQ_M5IViWe","number":170074,"title":"`python310Packages.jupyter_server` fails to build due to DeprecationWarning","user":{"login":"oati","id":79354991,"node_id":"MDQ6VXNlcjc5MzU0OTkx","avatar_url":"https://avatars.githubusercontent.com/u/79354991?v=4","gravatar_id":"","url":"https://api.github.com/users/oati","html_url":"https://github.com/oati","followers_url":"https://api.github.com/users/oati/followers","following_url":"https://api.github.com/users/oati/following{/other_user}","gists_url":"https://api.github.com/users/oati/gists{/gist_id}","starred_url":"https://api.github.com/users/oati/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/oati/subscriptions","organizations_url":"https://api.github.com/users/oati/orgs","repos_url":"https://api.github.com/users/oati/repos","events_url":"https://api.github.com/users/oati/events{/privacy}","received_events_url":"https://api.github.com/users/oati/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-24T09:52:33Z","updated_at":"2022-04-24T22:40:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Output\r\n```\r\nerror: builder for '/nix/store/qdlp99232d45idldfxpvp9v21r53jk9f-python3.10-jupyterlab_server-2.12.0.drv' failed with exit code 5;\r\n last 10 log lines:\r\n > jupyterlab_server/translation_utils.py:48\r\n > /build/jupyterlab_server-2.12.0/jupyterlab_server/translation_utils.py:48: DeprecationWarning: invalid escape sequence '\\.'\r\n > \"jupyter\\.lab\\.toolbars/.*/label\": \"toolbar\",\r\n >\r\n > jupyterlab_server/app.py:31\r\n > /build/jupyterlab_server-2.12.0/jupyterlab_server/app.py:31: DeprecationWarning: metadata {'default': '2.12.0'} was set from the constructor. With traitlets 4.1, metadata should be set using the .tag() method, e.g., Int().tag(key1='value1', key2='value2')\r\n > app_version = Unicode('', help='The version of the application.',\r\n >\r\n > -- Docs: https://docs.pytest.org/en/stable/how-to/capture-warnings.html\r\n > ============================= 6 warnings in 2.23s ==============================\r\n For full logs, run 'nix log /nix/store/qdlp99232d45idldfxpvp9v21r53jk9f-python3.10-jupyterlab_server-2.12.0.drv'.\r\n```\r\n\r\n### Full Logs\r\nhttps://gist.github.com/oati/e1487741dc2f8aa55a0c15244cf17787\r\n\r\n### Notify maintainers\r\n@elohmeier ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170074/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170055","id":1213543652,"node_id":"I_kwDOAEVQ_M5IVTTk","number":170055,"title":"libstdcxx5, gcc throws a segmentation fault on compilation. ","user":{"login":"crimsonalucard","id":1806857,"node_id":"MDQ6VXNlcjE4MDY4NTc=","avatar_url":"https://avatars.githubusercontent.com/u/1806857?v=4","gravatar_id":"","url":"https://api.github.com/users/crimsonalucard","html_url":"https://github.com/crimsonalucard","followers_url":"https://api.github.com/users/crimsonalucard/followers","following_url":"https://api.github.com/users/crimsonalucard/following{/other_user}","gists_url":"https://api.github.com/users/crimsonalucard/gists{/gist_id}","starred_url":"https://api.github.com/users/crimsonalucard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/crimsonalucard/subscriptions","organizations_url":"https://api.github.com/users/crimsonalucard/orgs","repos_url":"https://api.github.com/users/crimsonalucard/repos","events_url":"https://api.github.com/users/crimsonalucard/events{/privacy}","received_events_url":"https://api.github.com/users/crimsonalucard/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-04-24T05:25:00Z","updated_at":"2022-04-24T18:55:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nlibstdcxx5 throws segmentation fault on installation. \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. run `nix-env -iA nixpkgs.libstdcxx5 `\r\n2. watch failure\r\n3. ...\r\n\r\n### Expected behavior\r\nsuccess\r\n\r\n### Screenshots\r\nno screenshots will post log\r\n\r\n### Additional context\r\nlog:\r\n```warning: name collision in input Nix expressions, skipping '/home/brian/.nix-defexpr/channels_root/unstable'\r\nreplacing old 'libstdc++5-3.3.6'\r\ninstalling 'libstdc++5-3.3.6'\r\nthis derivation will be built:\r\n /nix/store/2q71g0wvsa00ik66kprqldv5iyc2lfdy-libstdc++5-3.3.6.drv\r\nbuilding '/nix/store/2q71g0wvsa00ik66kprqldv5iyc2lfdy-libstdc++5-3.3.6.drv'...\r\nunpacking sources\r\nunpacking source archive /nix/store/x8bl1fmzzhm7fkhhgk56m5pdb3sf4wby-gcc-core-3.3.6.tar.bz2\r\nunpacking source archive /nix/store/5ykqhz8yflwfad51ayp0bjzp55kyajxs-gcc-g++-3.3.6.tar.bz2\r\nsource root is gcc-3.3.6\r\nsetting SOURCE_DATE_EPOCH to timestamp 1115126617 of file gcc-3.3.6/.brik\r\npatching sources\r\napplying patch /nix/store/3dagnp0z7nflgsdzgzgmjfw63j3k052q-no-sys-dirs.patch\r\npatching file gcc/cppdefault.c\r\npatching file gcc/gcc.c\r\npatching file gcc/Makefile.in\r\napplying patch /nix/store/jbilvhq21cp18za211ich1vjsy4xp0ki-siginfo.patch\r\npatching file gcc/config/i386/linux.h\r\napplying patch /nix/store/r7p5mwzspp8qaky2g6lyrsswdzps0yq7-gcc-3.4.3-no_multilib_amd64.patch\r\npatching file gcc/config/i386/t-linux64\r\napplying patch /nix/store/bimxmanbwfmp6ksj7nlv1a3dcwzcrzrb-struct-ucontext.patch\r\npatching file gcc/config/alpha/linux.h\r\npatching file gcc/config/i386/linux.h\r\npatching file gcc/config/i386/linux64.h\r\npatching file gcc/config/rs6000/linux.h\r\nconfiguring\r\nconfigure flags: --prefix=/nix/store/jf7wynjq7sdqxjvnv8h73b9i5aji23p3-libstdc++5-3.3.6 --disable-multilib --enable-__cxa-atexit --enable-threads=posix --enable-languages=c++ --enable-clocale=gnu\r\nConfiguring for a x86_64-unknown-linux-gnu host.\r\nCreated \"Makefile\" in /build/build using \"mt-frag\"\r\nConfiguring libiberty...\r\ncreating cache ../config.cache\r\nchecking whether to enable maintainer-specific portions of Makefiles... no\r\nchecking for makeinfo... no\r\nchecking for perl... no\r\nchecking host system type... x86_64-unknown-linux-gnu\r\nchecking build system type... x86_64-unknown-linux-gnu\r\nchecking for ar... ar\r\nchecking for ranlib... ranlib\r\nchecking for gcc... gcc\r\nchecking whether we are using GNU C... yes\r\nchecking whether gcc accepts -g... yes\r\nchecking whether gcc and cc understand -c and -o together... yes\r\nchecking for POSIXized ISC... no\r\nchecking for working const... yes\r\nchecking for inline... inline\r\nchecking for a BSD compatible install... /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/install -c\r\nchecking how to run the C preprocessor... gcc -E\r\nchecking for sys/file.h... yes\r\nchecking for sys/param.h... yes\r\nchecking for limits.h... yes\r\nchecking for stdlib.h... yes\r\nchecking for malloc.h... yes\r\nchecking for string.h... yes\r\nchecking for unistd.h... yes\r\nchecking for strings.h... yes\r\nchecking for sys/time.h... yes\r\nchecking for time.h... yes\r\nchecking for sys/resource.h... yes\r\nchecking for sys/stat.h... yes\r\nchecking for sys/mman.h... yes\r\nchecking for fcntl.h... yes\r\nchecking for alloca.h... yes\r\nchecking for sys/pstat.h... no\r\nchecking for sys/sysmp.h... no\r\nchecking for sys/sysinfo.h... yes\r\nchecking for machine/hal_sysinfo.h... no\r\nchecking for sys/table.h... no\r\nchecking for sys/sysctl.h... no\r\nchecking for sys/systemcfg.h... no\r\nchecking for sys/wait.h that is POSIX.1 compatible... yes\r\nchecking whether time.h and sys/time.h may both be included... yes\r\nchecking whether errno must be declared... no\r\nchecking for ANSI C header files... yes\r\nchecking for uintptr_t... no\r\nchecking for pid_t... yes\r\nchecking whether the C compiler (gcc -g -O2 ) works... yes\r\nchecking whether the C compiler (gcc -g -O2 ) is a cross-compiler... no\r\nchecking for asprintf... yes\r\nchecking for atexit... yes\r\nchecking for basename... yes\r\nchecking for bcmp... yes\r\nchecking for bcopy... yes\r\nchecking for bsearch... yes\r\nchecking for bzero... yes\r\nchecking for calloc... yes\r\nchecking for clock... yes\r\nchecking for ffs... yes\r\nchecking for getcwd... yes\r\nchecking for getpagesize... yes\r\nchecking for index... yes\r\nchecking for insque... yes\r\nchecking for memchr... yes\r\nchecking for memcmp... yes\r\nchecking for memcpy... yes\r\nchecking for memmove... yes\r\nchecking for memset... yes\r\nchecking for mkstemps... yes\r\nchecking for putenv... yes\r\nchecking for random... yes\r\nchecking for rename... yes\r\nchecking for rindex... yes\r\nchecking for setenv... yes\r\nchecking for sigsetmask... yes\r\nchecking for strcasecmp... yes\r\nchecking for strchr... yes\r\nchecking for strdup... yes\r\nchecking for strncasecmp... yes\r\nchecking for strrchr... yes\r\nchecking for strstr... yes\r\nchecking for strtod... yes\r\nchecking for strtol... yes\r\nchecking for strtoul... yes\r\nchecking for tmpnam... yes\r\nchecking for vasprintf... yes\r\nchecking for vfprintf... yes\r\nchecking for vprintf... yes\r\nchecking for vsprintf... yes\r\nchecking for waitpid... yes\r\nchecking whether alloca needs Cray hooks... no\r\nchecking stack direction for C alloca... -1\r\nchecking for vfork.h... no\r\nchecking for working vfork... yes\r\nchecking for _doprnt... no\r\nchecking for sys_errlist... no\r\nchecking for sys_nerr... no\r\nchecking for sys_siglist... no\r\nchecking for external symbol _system_configuration... no\r\nchecking whether canonicalize_file_name must be declared... yes\r\nchecking for getrusage... yes\r\nchecking for on_exit... yes\r\nchecking for psignal... yes\r\nchecking for strerror... yes\r\nchecking for strsignal... yes\r\nchecking for sysconf... yes\r\nchecking for times... yes\r\nchecking for sbrk... yes\r\nchecking for gettimeofday... yes\r\nchecking for realpath... yes\r\nchecking for canonicalize_file_name... yes\r\nchecking for pstat_getstatic... no\r\nchecking for pstat_getdynamic... no\r\nchecking for sysmp... no\r\nchecking for getsysinfo... no\r\nchecking for table... no\r\nchecking for sysctl... no\r\nchecking for unistd.h... (cached) yes\r\nchecking for getpagesize... (cached) yes\r\nchecking for working mmap... yes\r\nchecking for working strncmp... yes\r\nupdating cache ../config.cache\r\ncreating ./config.status\r\ncreating Makefile\r\ncreating testsuite/Makefile\r\ncreating config.h\r\nConfiguring gcc...\r\nloading cache ../config.cache\r\nchecking LIBRARY_PATH variable... ok\r\nchecking GCC_EXEC_PREFIX variable... ok\r\nchecking host system type... x86_64-unknown-linux-gnu\r\nchecking target system type... x86_64-unknown-linux-gnu\r\nchecking build system type... x86_64-unknown-linux-gnu\r\nchecking for gcc... (cached) gcc\r\nchecking whether the C compiler (gcc -g -O2 ) works... yes\r\nchecking whether the C compiler (gcc -g -O2 ) is a cross-compiler... no\r\nchecking whether we are using GNU C... (cached) yes\r\nchecking whether gcc accepts -g... (cached) yes\r\nchecking whether gcc and cc understand -c and -o together... (cached) yes\r\nchecking for gnatbind... no\r\nchecking for compiler driver that understands Ada... no\r\nchecking whether gcc accepts -Wno-long-long... yes\r\nchecking how to run the C preprocessor... (cached) gcc -E\r\nchecking for inline... (cached) inline\r\nchecking for volatile... yes\r\nchecking for long double... yes\r\nchecking for long long int... yes\r\nchecking for __int64... no\r\nchecking for built-in _Bool... yes\r\nchecking size of short... 2\r\nchecking size of int... 4\r\nchecking size of long... 8\r\nchecking size of long long... 8\r\nchecking execution character set... ASCII\r\nchecking whether make sets ${MAKE}... yes\r\nchecking whether a default assembler was specified... no\r\nchecking whether a default linker was specified... no\r\nchecking for GNU C library... yes\r\nchecking for mawk... no\r\nchecking for gawk... gawk\r\nchecking whether ln works... yes\r\nchecking whether ln -s works... yes\r\nchecking for ranlib... (cached) ranlib\r\nchecking for a BSD compatible install... (cached) /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/install -c\r\nchecking for ANSI C header files... (cached) yes\r\nchecking whether time.h and sys/time.h may both be included... (cached) yes\r\nchecking for working stdbool.h... yes\r\nchecking whether string.h and strings.h may both be included... yes\r\nchecking for sys/wait.h that is POSIX.1 compatible... (cached) yes\r\nchecking for limits.h... (cached) yes\r\nchecking for stddef.h... yes\r\nchecking for string.h... (cached) yes\r\nchecking for strings.h... (cached) yes\r\nchecking for stdlib.h... (cached) yes\r\nchecking for time.h... (cached) yes\r\nchecking for fcntl.h... (cached) yes\r\nchecking for unistd.h... (cached) yes\r\nchecking for sys/file.h... (cached) yes\r\nchecking for sys/time.h... (cached) yes\r\nchecking for sys/mman.h... (cached) yes\r\nchecking for sys/resource.h... (cached) yes\r\nchecking for sys/param.h... (cached) yes\r\nchecking for sys/times.h... yes\r\nchecking for sys/stat.h... (cached) yes\r\nchecking for direct.h... no\r\nchecking for malloc.h... (cached) yes\r\nchecking for langinfo.h... yes\r\nchecking for thread.h... no\r\nchecking for pthread.h... yes\r\nchecking for CHAR_BIT... yes\r\nchecking byte ordering... little-endian\r\nchecking floating point format... IEEE (little-endian)\r\nchecking for mktemp... yes\r\nchecking for makeinfo... no\r\nconfigure: warning: \r\n*** Makeinfo is missing or too old.\r\n*** Info documentation will not be built.\r\nchecking for recent Pod::Man... no\r\nchecking for flex... flex\r\nchecking for bison... bison\r\nchecking for collect2 libraries... none required\r\nchecking for library containing exc_resume... no\r\nchecking for library containing ldexp... none required\r\nchecking for preprocessor stringizing operator... yes\r\nchecking for inttypes.h... yes\r\nchecking for times... (cached) yes\r\nchecking for clock... (cached) yes\r\nchecking for dup2... yes\r\nchecking for kill... yes\r\nchecking for getrlimit... yes\r\nchecking for setrlimit... yes\r\nchecking for atoll... yes\r\nchecking for atoq... no\r\nchecking for sysconf... (cached) yes\r\nchecking for strsignal... (cached) yes\r\nchecking for putc_unlocked... yes\r\nchecking for fputc_unlocked... yes\r\nchecking for fputs_unlocked... yes\r\nchecking for fwrite_unlocked... yes\r\nchecking for fprintf_unlocked... no\r\nchecking for getrusage... (cached) yes\r\nchecking for nl_langinfo... yes\r\nchecking for lstat... yes\r\nchecking for scandir... yes\r\nchecking for alphasort... yes\r\nchecking for gettimeofday... (cached) yes\r\nchecking for mmap... yes\r\nchecking for ssize_t... yes\r\nchecking for uid_t in sys/types.h... yes\r\nchecking type of array argument to getgroups... gid_t\r\nchecking whether the printf functions support %p... yes\r\nchecking whether read-only mmap of a plain file works... yes\r\nchecking whether mmap from /dev/zero works... yes\r\nchecking for MAP_ANON(YMOUS)... yes\r\nchecking whether mmap with MAP_ANON(YMOUS) works... yes\r\nchecking for pid_t... (cached) yes\r\nchecking for vfork.h... (cached) no\r\nchecking for working vfork... (cached) yes\r\nchecking for iconv... yes\r\nchecking for iconv declaration... \r\n extern size_t iconv (iconv_t cd, char * *inbuf, size_t *inbytesleft, char * *outbuf, size_t *outbytesleft);\r\nchecking whether getenv is declared... yes\r\nchecking whether atol is declared... yes\r\nchecking whether sbrk is declared... yes\r\nchecking whether abort is declared... yes\r\nchecking whether atof is declared... yes\r\nchecking whether getcwd is declared... yes\r\nchecking whether getwd is declared... yes\r\nchecking whether strsignal is declared... yes\r\nchecking whether putc_unlocked is declared... yes\r\nchecking whether fputs_unlocked is declared... yes\r\nchecking whether fwrite_unlocked is declared... yes\r\nchecking whether fprintf_unlocked is declared... no\r\nchecking whether strstr is declared... yes\r\nchecking whether errno is declared... yes\r\nchecking whether vasprintf is declared... yes\r\nchecking whether malloc is declared... yes\r\nchecking whether realloc is declared... yes\r\nchecking whether calloc is declared... yes\r\nchecking whether free is declared... yes\r\nchecking whether basename is declared... yes\r\nchecking whether getopt is declared... yes\r\nchecking whether clock is declared... yes\r\nchecking whether getrlimit is declared... yes\r\nchecking whether setrlimit is declared... yes\r\nchecking whether getrusage is declared... yes\r\nchecking whether times is declared... yes\r\nchecking for struct tms... yes\r\nchecking for clock_t... yes\r\nchecking for uchar... \r\nchecking for .preinit_array/.init_array/.fini_array support... yes\r\nchecking if mkdir takes one argument... no\r\nchecking for main in -lunwind... no\r\nUsing `../../gcc-3.3.6/gcc/config/i386/i386.c' for machine-specific logic.\r\nUsing `../../gcc-3.3.6/gcc/config/i386/i386.md' as machine description file.\r\nUsing the following target machine macro files:\r\n ../../gcc-3.3.6/gcc/config/i386/biarch64.h\r\n ../../gcc-3.3.6/gcc/config/i386/i386.h\r\n ../../gcc-3.3.6/gcc/config/i386/unix.h\r\n ../../gcc-3.3.6/gcc/config/i386/att.h\r\n ../../gcc-3.3.6/gcc/config/dbxelf.h\r\n ../../gcc-3.3.6/gcc/config/elfos.h\r\n ../../gcc-3.3.6/gcc/config/svr4.h\r\n ../../gcc-3.3.6/gcc/config/linux.h\r\n ../../gcc-3.3.6/gcc/config/i386/x86-64.h\r\n ../../gcc-3.3.6/gcc/config/i386/linux64.h\r\nchecking for library containing strerror... none required\r\nchecking for working const... (cached) yes\r\nchecking for off_t... yes\r\nchecking for size_t... yes\r\nchecking for working alloca.h... (cached) yes\r\nchecking for alloca... yes\r\nchecking whether we are using the GNU C Library 2.1 or newer... yes\r\nchecking for argz.h... yes\r\nchecking for limits.h... (cached) yes\r\nchecking for locale.h... yes\r\nchecking for nl_types.h... yes\r\nchecking for malloc.h... (cached) yes\r\nchecking for stddef.h... (cached) yes\r\nchecking for stdlib.h... (cached) yes\r\nchecking for string.h... (cached) yes\r\nchecking for unistd.h... (cached) yes\r\nchecking for sys/param.h... (cached) yes\r\nchecking for feof_unlocked... yes\r\nchecking for fgets_unlocked... yes\r\nchecking for getcwd... (cached) yes\r\nchecking for getegid... yes\r\nchecking for geteuid... yes\r\nchecking for getgid... yes\r\nchecking for getuid... yes\r\nchecking for mempcpy... yes\r\nchecking for munmap... yes\r\nchecking for putenv... (cached) yes\r\nchecking for setenv... (cached) yes\r\nchecking for setlocale... yes\r\nchecking for stpcpy... yes\r\nchecking for strchr... (cached) yes\r\nchecking for strcasecmp... (cached) yes\r\nchecking for strdup... (cached) yes\r\nchecking for strtoul... (cached) yes\r\nchecking for tsearch... yes\r\nchecking for __argz_count... yes\r\nchecking for __argz_stringify... yes\r\nchecking for __argz_next... yes\r\nchecking for iconv... (cached) yes\r\nchecking for iconv declaration... (cached) \r\n extern size_t iconv (iconv_t cd, char * *inbuf, size_t *inbytesleft, char * *outbuf, size_t *outbytesleft);\r\nchecking for nl_langinfo and CODESET... yes\r\nchecking for LC_MESSAGES... yes\r\nchecking whether NLS is requested... yes\r\nchecking whether included gettext is requested... no\r\nchecking for libintl.h... yes\r\nchecking for GNU gettext in libc... yes\r\nchecking for dcgettext... yes\r\nchecking for msgfmt... no\r\nchecking for gmsgfmt... :\r\nchecking for xgettext... no\r\nchecking for bison... bison\r\nchecking version of bison... 3.8.2, ok\r\nchecking for catalogs to be installed... be ca da de el es fr ja nl rw sv tr be ca da de el es fr ja nl rw sv tr\r\nchecking what assembler to use... as\r\nchecking what linker to use... ld\r\nchecking what nm to use... nm\r\nchecking what objdump to use... objdump\r\nchecking assembler alignment features... .p2align including maximum skip\r\nchecking assembler subsection support... working .subsection -1\r\nchecking assembler weak support... yes\r\nchecking assembler hidden support... yes\r\nchecking assembler leb128 support... ../../gcc-3.3.6/gcc/configure: line 7351: test: too many arguments\r\nyes\r\nchecking assembler eh_frame optimization... yes\r\nchecking assembler section merging support... yes\r\nchecking assembler thread-local storage support... yes\r\nchecking assembler instructions... filds fists \r\nchecking cmov syntax... no\r\nchecking assembler GOTOFF in data directives... no\r\nchecking assembler dwarf2 debug_line support... yes\r\nchecking assembler --gdwarf2 support... yes\r\nchecking assembler --gstabs support... yes\r\nchecking linker read-only and read-write section mixing... read-write\r\nchecking linker PT_GNU_EH_FRAME support... yes\r\nchecking linker --as-needed support... yes\r\nUsing ggc-page for garbage collection.\r\nchecking whether to enable maintainer-specific portions of Makefiles... no\r\nLinks are now set up to build a native compiler for x86_64-unknown-linux-gnu\r\nupdating cache ../config.cache\r\ncreating ./config.status\r\ncreating Makefile\r\ncreating intl/Makefile\r\ncreating fixinc/Makefile\r\ncreating gccbug\r\ncreating mklibgcc\r\ncreating mkheaders\r\ncreating auto-host.h\r\nbuilding\r\ncat: /nix/store/dgic5ks4yixhh0havidjwd02rskmqlgp-binutils-wrapper-2.38/nix-support/libc-ldflags-before: No such file or directory\r\nbuild flags: SHELL=/nix/store/fcd0m68c331j7nkdxvnnpb8ggwsaiqac-bash-5.1-p16/bin/bash NATIVE_SYSTEM_HEADER_DIR=/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include SYSTEM_HEADER_DIR=/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include CFLAGS_FOR_BUILD=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib CFLAGS_FOR_TARGET=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib CXXFLAGS_FOR_BUILD=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib CXXFLAGS_FOR_TARGET=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib FLAGS_FOR_TARGET=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib LDFLAGS_FOR_BUILD=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib LDFLAGS_FOR_TARGET=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib BOOT_CFLAGS=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib BOOT_LDFLAGS=-I/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -B/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib/\\ \\ -idirafter\\ /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include\\ -idirafter\\ /nix/store/19xbyxc31snlk60cil7cx6l4xw126ids-gcc-11.2.0/lib/gcc/x86_64-unknown-linux-gnu/11.2.0/include-fixed\\ \\ -O2\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-rpath\\ -Wl\\,/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\\ -Wl\\,-L/nix/store/ayrsyv7npr0lcbann4k9lxr19x813f0z-glibc-2.34-115/lib\r\nmake[1]: Entering directory '/build/build/libiberty'\r\nif [ x\"\" != x ] && [ ! -d pic ]; then \\\r\n mkdir pic; \\\r\nelse true; fi\r\ntouch stamp-picdir\r\nif [ x\"\" != x ]; then \\\r\n gcc -c -DHAVE_CONFIG_H -g -O2 -I. -I../../gcc-3.3.6/libiberty/../include -W -Wall -Wtraditional -pedantic ../../gcc-3.3.6/libiberty/regex.c -o pic/regex.o; \\\r\nelse true; fi\r\ngcc -c -DHAVE_CONFIG_H -g -O2 -I. -I../../gcc-3.3.6/libiberty/../include -W -Wall -Wtraditional -pedantic ../../gcc-3.3.6/libiberty/regex.c -o regex.o\r\nIn file included from /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include/features.h:488,\r\n from /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include/bits/libc-header-start.h:33,\r\n from /nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include/stdlib.h:25,\r\n from ../../gcc-3.3.6/libiberty/regex.c:130:\r\n/nix/store/pvn23vycg674bj6nypjcfyhqbr85rqxa-glibc-2.34-115-dev/include/sys/cdefs.h:1: internal compiler error: Segmentation fault\r\n 1 | /* Copyright (C) 1992-2021 Free Software Foundation, Inc.\r\n | \r\n0x15f6767 internal_error(char const*, ...)\r\n ???:0\r\n0x16238d4 cpp_sys_macro_p(cpp_reader*)\r\n ???:0\r\n0x161391d cpp_classify_number(cpp_reader*, cpp_token const*, char const**, unsigned int)\r\n ???:0\r\n0x161554a _cpp_parse_expr\r\n ???:0\r\n0x160fe88 _cpp_handle_directive\r\n ???:0\r\n0x161ea48 _cpp_lex_token\r\n ???:0\r\n0x746a0e c_lex_with_flags(tree_node**, unsigned int*, unsigned char*, int)\r\n ???:0\r\n0x70087c c_parse_file()\r\n ???:0\r\n0x74f21d c_common_parse_file()\r\n ???:0\r\nPlease submit a full bug report,\r\nwith preprocessed source if appropriate.\r\nPlease include the complete backtrace with any bug report.\r\nSee <https://gcc.gnu.org/bugs/> for instructions.\r\nmake[1]: *** [Makefile:126: regex.o] Error 1\r\nmake[1]: Leaving directory '/build/build/libiberty'\r\nmake: *** [Makefile:1293: all-libiberty] Error 2\r\nerror: builder for '/nix/store/2q71g0wvsa00ik66kprqldv5iyc2lfdy-libstdc++5-3.3.6.drv' failed with exit code 2;\r\n last 10 log lines:\r\n > ???:0\r\n > 0x74f21d c_common_parse_file()\r\n > ???:0\r\n > Please submit a full bug report,\r\n > with preprocessed source if appropriate.\r\n > Please include the complete backtrace with any bug report.\r\n > See <https://gcc.gnu.org/bugs/> for instructions.\r\n > make[1]: *** [Makefile:126: regex.o] Error 1\r\n > make[1]: Leaving directory '/build/build/libiberty'\r\n > make: *** [Makefile:1293: all-libiberty] Error 2\r\n For full logs, run 'nix log /nix/store/2q71g0wvsa00ik66kprqldv5iyc2lfdy-libstdc++5-3.3.6.drv'.\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170055/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170026","id":1213474192,"node_id":"I_kwDOAEVQ_M5IVCWQ","number":170026,"title":"haruna: segmentation fault on exit","user":{"login":"klemensn","id":91517496,"node_id":"U_kgDOBXRyOA","avatar_url":"https://avatars.githubusercontent.com/u/91517496?v=4","gravatar_id":"","url":"https://api.github.com/users/klemensn","html_url":"https://github.com/klemensn","followers_url":"https://api.github.com/users/klemensn/followers","following_url":"https://api.github.com/users/klemensn/following{/other_user}","gists_url":"https://api.github.com/users/klemensn/gists{/gist_id}","starred_url":"https://api.github.com/users/klemensn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/klemensn/subscriptions","organizations_url":"https://api.github.com/users/klemensn/orgs","repos_url":"https://api.github.com/users/klemensn/repos","events_url":"https://api.github.com/users/klemensn/events{/privacy}","received_events_url":"https://api.github.com/users/klemensn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-23T23:05:35Z","updated_at":"2022-04-23T23:05:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\n`haruna` crashes due to `SIGSEGV` upon exit if and only if closed graphically,\ni.e. starting it in the shell and using `^C` causes it to exit cleanly.\n\nOther graphical programs in the KDE/Plasma suite do not crash like this.\n\n### Steps To Reproduce\n1. `$ nix shell -p haruna`\n2. `$ haruna`\n3. close the window graphically.\n\n### Expected behavior\nClear exit without crashing (and possibly dumping core).\n\n### Additional context\n```console\n$ haruna\nunknown() : qrc:/qml/main.qml:105:5: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\n\nunknown() : qrc:/qml/HProgressBar.qml:209:5: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\n\nunknown() : qrc:/qml/MpvVideo.qml:308:5: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\n\nunknown() : qrc:/qml/Menus/AudioMenu.qml:34:9: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\n\nunknown() : qrc:/qml/Menus/AudioMenu.qml:34:9: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\n\nCannot load libcuda.so.1\n\nSegmentation fault (core dumped)\n```\n```console\n$ coredumpctl debug -A '-q -batch -ex bt'\n\n PID: 21320 (.haruna-wrapped)\n UID: 1000 (kn)\n GID: 100 (users)\n Signal: 11 (SEGV)\n Timestamp: Sun 2022-04-24 00:51:08 EET (8min ago)\n Command Line: /run/current-system/sw/bin/haruna\n Executable: /nix/store/7fgyqycl6nq6f383bmbrp6hgwj8rzf8m-haruna-0.7.3/bin/.haruna-wrapped\n Control Group: /user.slice/user-1000.slice/user@1000.service/app.slice/app-org.kde.konsole-67982889e83241a2a3c711bc1707691b.scope\n Unit: user@1000.service\n User Unit: app-org.kde.konsole-67982889e83241a2a3c711bc1707691b.scope\n Slice: user-1000.slice\n Owner UID: 1000 (kn)\n Boot ID: <redacted>\n Machine ID: <redacted>\n Hostname: <redacted>\n Storage: /var/lib/systemd/coredump/core.\\x2eharuna-wrapped.1000.b129b782e4504185a59a5e4acf89a2a6.21320.1650754268000000 (present)\n Disk Size: 126.4M\n Message: Process 21320 (.haruna-wrapped) of user 1000 dumped core.\n \n Module linux-vdso.so.1 with build-id a1fd594851d4fab6351cb7deca8610d7679d4f9c\n Module libqjpeg.so without build-id.\n Module libqico.so without build-id.\n Module libqgif.so without build-id.\n Module libqsvg.so without build-id.\n Module kimg_xcf.so without build-id.\n Module kimg_tga.so without build-id.\n Module kimg_rgb.so without build-id.\n Module kimg_ras.so without build-id.\n Module kimg_psd.so without build-id.\n Module kimg_pic.so without build-id.\n Module kimg_pcx.so without build-id.\n Module kimg_ora.so without build-id.\n Module kimg_kra.so without build-id.\n Module kimg_hdr.so without build-id.\n Module libIexMath-2_5.so.25 without build-id.\n Module libIlmThread-2_5.so.25 without build-id.\n Module libImath-2_5.so.25 without build-id.\n Module libIex-2_5.so.25 without build-id.\n Module libHalf-2_5.so.25 without build-id.\n Module libIlmImf-2_5.so.25 without build-id.\n Module kimg_exr.so without build-id.\n Module kimg_eps.so without build-id.\n Module libavif.so.13 without build-id.\n Module kimg_avif.so without build-id.\n Module kimg_ani.so without build-id.\n Module libxdg-shell.so without build-id.\n Module libaspell.so.15 without build-id.\n Module sonnet_aspell.so without build-id.\n Module org.kde.desktop.so without build-id.\n Module libdrm_nouveau.so.2 without build-id.\n Module libdrm_amdgpu.so.1 without build-id.\n Module libelf.so.0 without build-id.\n Module libdrm_radeon.so.1 without build-id.\n Module libLLVM-13.so with build-id b0d994d4c8011ca12e535b02eed5526ab4329ea1\n Module iris_dri.so with build-id 1f573fbfec1d4cd944644cdd2cb97d6beffed5be\n Module libxshmfence.so.1 without build-id.\n Module libxcb-sync.so.1 without build-id.\n Module libxcb-present.so.0 without build-id.\n Module libxcb-dri3.so.0 without build-id.\n Module libxcb-dri2.so.0 without build-id.\n Module libX11-xcb.so.1 without build-id.\n Module libglapi.so.0 without build-id.\n Module libEGL_mesa.so.0 without build-id.\n Module libqt-plugin-wayland-egl.so without build-id.\n Module libQt5QuickShapes.so.5 without build-id.\n Module libqmlshapesplugin.so without build-id.\n Module libKF5SonnetCore.so.5 without build-id.\n Module libsonnetquickplugin.so without build-id.\n Module libmodelsplugin.so without build-id.\n Module libqtgraphicaleffectsprivate.so without build-id.\n Module libqqc2desktopstyleplugin.so without build-id.\n Module libqtquicktemplates2plugin.so without build-id.\n Module libKirigamiPlugin.so without build-id.\n Module libqmlplugin.so without build-id.\n Module libqtlabsplatformplugin.so without build-id.\n Module libqtgraphicaleffectsplugin.so without build-id.\n Module libqquicklayoutsplugin.so without build-id.\n Module libwindowplugin.so without build-id.\n Module libqtquickcontrols2fusionstyleplugin.so without build-id.\n Module libqtquickcontrols2plugin.so without build-id.\n Module libQt5QmlWorkerScript.so.5 without build-id.\n Module libqtquick2plugin.so without build-id.\n Module libpulse-mainloop-glib.so.0 without build-id.\n Module libdbusmenu-qt5.so.2 without build-id.\n Module libphonon4qt5.so.4 without build-id.\n Module libKF5WaylandClient.so.5 without build-id.\n Module libKF5Notifications.so.5 without build-id.\n Module KDEPlasmaPlatformTheme.so without build-id.\n Module libcomposeplatforminputcontextplugin.so without build-id.\n Module libqwayland-generic.so without build-id.\n Module libjansson.so.4 without build-id.\n Module libMESSAGING-SEND-samba4.so without build-id.\n Module libwinbind-client-samba4.so without build-id.\n Module libgpg-error.so.0 without build-id.\n Module libdatrie.so.1 without build-id.\n Module libflag-mapping-samba4.so without build-id.\n Module libclidns-samba4.so without build-id.\n Module libcli-ldap-common-samba4.so without build-id.\n Module libhcrypto-samba4.so.5 without build-id.\n Module libhx509-samba4.so.5 without build-id.\n Module libheimbase-samba4.so.1 without build-id.\n Module libroken-samba4.so.19 without build-id.\n Module libwind-samba4.so.0 without build-id.\n Module libmsghdr-samba4.so without build-id.\n Module libndr-krb5pac.so.0 without build-id.\n Module libasn1-samba4.so.8 without build-id.\n Module libcommon-auth-samba4.so without build-id.\n Module libsamba-modules-samba4.so without build-id.\n Module libwbclient.so.0 without build-id.\n Module libsamdb.so.0 without build-id.\n Module libgcrypt.so.20 without build-id.\n Module liblz4.so.1 without build-id.\n Module libthai.so.0 without build-id.\n Module libselinux.so.1 without build-id.\n Module libgmodule-2.0.so.0 with build-id 4080e7e72c752ae8ab4331f44f085a685a744094\n Module libmd.so.0 without build-id.\n Module libldb.so.2 without build-id.\n Module libldbsamba-samba4.so without build-id.\n Module libsamdb-common-samba4.so without build-id.\n Module libcli-nbt-samba4.so without build-id.\n Module libauthkrb5-samba4.so without build-id.\n Module libaddns-samba4.so without build-id.\n Module libgssapi-samba4.so.2 without build-id.\n Module libcli-cldap-samba4.so without build-id.\n Module libkrb5-samba4.so.26 without build-id.\n Module libndr-nbt.so.0 without build-id.\n Module libtdb.so.1 without build-id.\n Module libtdb-wrap-samba4.so without build-id.\n Module libutil-setid-samba4.so without build-id.\n Module libserver-role-samba4.so without build-id.\n Module libserver-id-db-samba4.so without build-id.\n Module libtalloc-report-printf-samba4.so without build-id.\n Module libsmbd-shim-samba4.so without build-id.\n Module libinterfaces-samba4.so without build-id.\n Module libiov-buf-samba4.so without build-id.\n Module libutil-reg-samba4.so without build-id.\n Module libmessages-util-samba4.so without build-id.\n Module libmessages-dgm-samba4.so without build-id.\n Module libsamba-cluster-support-samba4.so without build-id.\n Module libunwind-x86_64.so.8 without build-id.\n Module libtime-basic-samba4.so without build-id.\n Module libsys-rw-samba4.so without build-id.\n Module libsocket-blocking-samba4.so without build-id.\n Module libdbwrap-samba4.so without build-id.\n Module libndr-samba-samba4.so without build-id.\n Module libutil-tdb-samba4.so without build-id.\n Module libdcerpc-binding.so.0 without build-id.\n Module libndr-samba4.so without build-id.\n Module libsamba-sockets-samba4.so without build-id.\n Module libsmb-transport-samba4.so without build-id.\n Module libcom_err-samba4.so.0 without build-id.\n Module libasn1util-samba4.so without build-id.\n Module libkrb5samba-samba4.so without build-id.\n Module libCHARSET3-samba4.so without build-id.\n Module libcliauth-samba4.so without build-id.\n Module libgensec-samba4.so without build-id.\n Module libgenrand-samba4.so without build-id.\n Module libFLAC.so.8 without build-id.\n Module libgraphite2.so.3 without build-id.\n Module libresolv.so.2 with build-id 847b86d7c620ae7d08e842f302f10127790a9660\n Module libkeyutils.so.1 without build-id.\n Module libkrb5support.so.0 without build-id.\n Module libcom_err.so.3 without build-id.\n Module libk5crypto.so.3 without build-id.\n Module libkrb5.so.3 without build-id.\n Module libsystemd.so.0 without build-id.\n Module libGLX.so.0 without build-id.\n Module libXdmcp.so.6 without build-id.\n Module libXau.so.6 without build-id.\n Module libblkid.so.1 with build-id 9459fab4838321b9f3e8515f33f474b2584cdc22\n Module libnuma.so.1 without build-id.\n Module libmvec.so.1 with build-id 7c827e5796833344caad512799f83613f41171ef\n Module libogg.so.0 without build-id.\n Module libxcb-render.so.0 without build-id.\n Module libpixman-1.so.0 with build-id e543e4db693226a37e0c1af6b6ee9224c1b47b63\n Module libpcre.so.1 without build-id.\n Module libpango-1.0.so.0 without build-id.\n Module libpangoft2-1.0.so.0 without build-id.\n Module libpangocairo-1.0.so.0 without build-id.\n Module libgio-2.0.so.0 with build-id a68fb56a72583f7f51403d6ef1e485a4a72a7ced\n Module libgdk_pixbuf-2.0.so.0 with build-id 2479465a0d6b9071753c6883b013ed7283db85e8\n Module libcairo-gobject.so.2 with build-id 05c4ef277157c7284df9fef6c182cea2d364822a\n Module libbsd.so.0 without build-id.\n Module libsecrets3-samba4.so without build-id.\n Module libsamba-debug-samba4.so without build-id.\n Module libsamba3-util-samba4.so without build-id.\n Module libndr-standard.so.0 without build-id.\n Module libsamba-credentials.so.1 without build-id.\n Module libsamba-hostconfig.so.0 without build-id.\n Module libgse-samba4.so without build-id.\n Module libcli-smb-common-samba4.so without build-id.\n Module libdcerpc-samba-samba4.so without build-id.\n Module libtevent.so.0 without build-id.\n Module libsamba-errors.so.1 without build-id.\n Module libtevent-util.so.0 without build-id.\n Module libsamba-security-samba4.so without build-id.\n Module libsmbconf.so.0 without build-id.\n Module libreplace-samba4.so without build-id.\n Module libsamba-util.so.0 without build-id.\n Module libmsrpc3-samba4.so without build-id.\n Module liblibsmb-samba4.so without build-id.\n Module liblibcli-lsa3-samba4.so without build-id.\n Module libndr.so.2 without build-id.\n Module libtalloc.so.2 without build-id.\n Module libgmp.so.10 without build-id.\n Module libhogweed.so.6 without build-id.\n Module libnettle.so.8 without build-id.\n Module libtasn1.so.6 without build-id.\n Module libunistring.so.2 without build-id.\n Module libidn2.so.0 without build-id.\n Module libp11-kit.so.0 without build-id.\n Module libubsan.so.1 without build-id.\n Module libsodium.so.23 with build-id 3aa7ee4592a79c9c863b8688768dc44bff830782\n Module libgomp.so.1 without build-id.\n Module libXrender.so.1 without build-id.\n Module libdecor-0.so.0 without build-id.\n Module libXxf86vm.so.1 without build-id.\n Module libXi.so.6 without build-id.\n Module libXcursor.so.1 without build-id.\n Module libfftw3.so.3 without build-id.\n Module libsamplerate.so.0 without build-id.\n Module libcap.so.2 without build-id.\n Module libsndfile.so.1 without build-id.\n Module libpulsecommon-14.2.so without build-id.\n Module libatomic.so.1 without build-id.\n Module libreadline.so.6 without build-id.\n Module libepoxy.so.0 without build-id.\n Module libunwind.so.8 without build-id.\n Module libxcb-xfixes.so.0 without build-id.\n Module libxcb-shape.so.0 without build-id.\n Module libxcb-shm.so.0 without build-id.\n Module libffi.so.8 without build-id.\n Module libexpat.so.1 without build-id.\n Module libwayland-server.so.0 with build-id 611748fd13b52d47ec0537600e836dc3414879f5\n Module libsoxr.so.0 without build-id.\n Module libGLdispatch.so.0 without build-id.\n Module libdvdcss.so.2 without build-id.\n Module libncursesw.so.6 without build-id.\n Module libQt5WaylandClient.so.5 without build-id.\n Module libgthread-2.0.so.0 with build-id b4f5c65b985bccbd6328480e35fb1b525c4168fd\n Module libzstd.so.1 without build-id.\n Module libpcre2-16.so.0 without build-id.\n Module libicudata.so.70 without build-id.\n Module libicuuc.so.70 without build-id.\n Module libicui18n.so.70 without build-id.\n Module libharfbuzz.so.0 without build-id.\n Module libpng16.so.16 without build-id.\n Module libcrypto.so.1.1 with build-id 045c7bcdb176312d33bff1324d3a567655b4da20\n Module libssl.so.1.1 with build-id 0ef22347eec4807957f0b133dc07634b1f68555c\n Module libgssapi_krb5.so.2 without build-id.\n Module libQt5QuickTemplates2.so.5 without build-id.\n Module libdbus-1.so.3 without build-id.\n Module libdl.so.2 with build-id c06f3da244980c9a6e8e2a1e4d8990a085103471\n Module libudev.so.1 without build-id.\n Module libGL.so.1 without build-id.\n Module libQt5Svg.so.5 without build-id.\n Module libQt5PrintSupport.so.5 without build-id.\n Module libKF5GlobalAccel.so.5 without build-id.\n Module libxcb-keysyms.so.1 without build-id.\n Module libXfixes.so.3 without build-id.\n Module libxcb.so.1 without build-id.\n Module libQt5X11Extras.so.5 without build-id.\n Module libmount.so.1 with build-id cd0ad49160143a594d579b9a6d293517055994a3\n Module libKF5DBusAddons.so.5 without build-id.\n Module libKF5Crash.so.5 without build-id.\n Module ld-linux-x86-64.so.2 with build-id 30c57076927b082f79b8e0307c2ade477e78866b\n Module libopenh264.so.6 without build-id.\n Module libxvidcore.so.4 without build-id.\n Module libxavs.so.1 without build-id.\n Module libx265.so.199 without build-id.\n Module libx264.so.163 without build-id.\n Module libvorbisenc.so.2 without build-id.\n Module libvorbis.so.0 without build-id.\n Module libvo-amrwbenc.so.0 without build-id.\n Module libtheoradec.so.1 without build-id.\n Module libtheoraenc.so.1 without build-id.\n Module libSvtAv1Enc.so.0 without build-id.\n Module libspeex.so.1 without build-id.\n Module libopus.so.0 without build-id.\n Module libopenjp2.so.7 without build-id.\n Module libopencore-amrnb.so.0 without build-id.\n Module libmp3lame.so.0 without build-id.\n Module libgsm.so without build-id.\n Module libaom.so.3 without build-id.\n Module libcairo.so.2 with build-id c2905b7a90de8e2d0df5cf44e3efead78eb4e607\n Module libglib-2.0.so.0 with build-id 24d88f2adb3db24c34f9ad621f772b856c7d4a11\n Module libgobject-2.0.so.0 with build-id 00e12bb4b861118cda92b66a299d308a69360f3b\n Module librsvg-2.so.2 without build-id.\n Module libdav1d.so.6 without build-id.\n Module libcelt0.so.2 without build-id.\n Module liblzma.so.5 without build-id.\n Module libwebp.so.7 without build-id.\n Module libwebpmux.so.3 without build-id.\n Module libvpx.so.7 without build-id.\n Module libsmbclient.so.0 without build-id.\n Module libssh.so.4 without build-id.\n Module libsrt.so.1.4 without build-id.\n Module libgnutls.so.30 without build-id.\n Module libmodplug.so.1 without build-id.\n Module libgme.so.0 without build-id.\n Module libbz2.so.1 without build-id.\n Module libfreetype.so.6 without build-id.\n Module libfontconfig.so.1 without build-id.\n Module libzmq.so.5 without build-id.\n Module libvidstab.so.1.1 without build-id.\n Module libvmaf.so.1 without build-id.\n Module libfribidi.so.0 without build-id.\n Module libmysofa.so.1 without build-id.\n Module libbs2b.so.0 without build-id.\n Module libpostproc.so.55 without build-id.\n Module libmfx.so.1 without build-id.\n Module libz.so.1 without build-id.\n Module libzimg.so.2 without build-id.\n Module libXv.so.1 without build-id.\n Module libXrandr.so.2 without build-id.\n Module libXinerama.so.1 without build-id.\n Module libXext.so.6 without build-id.\n Module libXss.so.1 without build-id.\n Module libxkbcommon.so.0 without build-id.\n Module libwayland-cursor.so.0 with build-id 524fd5133c3a6674f347e2c4aa584acc511fcbde\n Module libvulkan.so.1 without build-id.\n Module libvdpau.so.1 without build-id.\n Module libva-x11.so.2 without build-id.\n Module libva-wayland.so.2 without build-id.\n Module libva-drm.so.2 without build-id.\n Module libva.so.2 without build-id.\n Module libuchardet.so.0 without build-id.\n Module libshaderc_shared.so.1 without build-id.\n Module libSDL2-2.0.so.0 without build-id.\n Module librubberband.so.2 without build-id.\n Module libpulse.so.0 without build-id.\n Module libopenal.so.1 without build-id.\n Module liblua.so.5.2 without build-id.\n Module librt.so.1 with build-id f610c78fef64474570c8ba2b5c00427c340d1e84\n Module libplacebo.so.192 without build-id.\n Module libbluray.so.2 without build-id.\n Module libavdevice.so.58 without build-id.\n Module libass.so.9 without build-id.\n Module libarchive.so.13 without build-id.\n Module liblcms2.so.2 without build-id.\n Module libjpeg.so.62 without build-id.\n Module libwayland-client.so.0 with build-id 45e2076feb37f91b15990758f811e5e0338a2fb3\n Module libwayland-egl.so.1 with build-id a13b79b32a09a96f5df69cc5acadbfda6a509b0f\n Module libgbm.so.1 without build-id.\n Module libswresample.so.3 without build-id.\n Module libEGL.so.1 without build-id.\n Module libdvdread.so.8 without build-id.\n Module libpthread.so.0 with build-id 7e1bb32908f70cf0fc00d66c983160c7b115f188\n Module libdvdnav.so.4 without build-id.\n Module libdrm.so.2 without build-id.\n Module libcaca.so.0 without build-id.\n Module libasound.so.2 without build-id.\n Module libattr.so.1 without build-id.\n Module libacl.so.1 without build-id.\n Module libKF5GuiAddons.so.5 without build-id.\n Module libKF5Archive.so.5 without build-id.\n Module libexslt.so.0 without build-id.\n Module libxslt.so.1 without build-id.\n Module libxml2.so.2 without build-id.\n Module libc.so.6 with build-id b2073195a02092e5988e0c88ddbe22da749f69ac\n Module libgcc_s.so.1 without build-id.\n Module libm.so.6 with build-id bb1ad44ec0afbc9acf56402168c25a629dfd7adb\n Module libstdc++.so.6 without build-id.\n Module libQt5Core.so.5 without build-id.\n Module libQt5Gui.so.5 without build-id.\n Module libQt5Network.so.5 without build-id.\n Module libQt5Qml.so.5 without build-id.\n Module libQt5QmlModels.so.5 without build-id.\n Module libQt5Quick.so.5 without build-id.\n Module libQt5QuickControls2.so.5 without build-id.\n Module libQt5DBus.so.5 without build-id.\n Module libKF5CoreAddons.so.5 without build-id.\n Module libQt5Xml.so.5 without build-id.\n Module libKF5Solid.so.5 without build-id.\n Module libQt5Widgets.so.5 without build-id.\n Module libKF5ItemViews.so.5 without build-id.\n Module libKF5Codecs.so.5 without build-id.\n Module libKF5AuthCore.so.5 without build-id.\n Module libKF5Auth.so.5 without build-id.\n Module libKF5WidgetsAddons.so.5 without build-id.\n Module libKF5I18n.so.5 without build-id.\n Module libKF5ConfigCore.so.5 without build-id.\n Module libKF5ConfigGui.so.5 without build-id.\n Module libKF5ConfigWidgets.so.5 without build-id.\n Module libKF5IconThemes.so.5 without build-id.\n Module libKF5XmlGui.so.5 without build-id.\n Module libKF5Bookmarks.so.5 without build-id.\n Module libX11.so.6 without build-id.\n Module libKF5WindowSystem.so.5 without build-id.\n Module libKF5Completion.so.5 without build-id.\n Module libKF5JobWidgets.so.5 without build-id.\n Module libKF5Service.so.5 without build-id.\n Module libQt5Concurrent.so.5 without build-id.\n Module libKF5KIOCore.so.5 without build-id.\n Module libKF5KIOGui.so.5 without build-id.\n Module libswscale.so.5 without build-id.\n Module libavcodec.so.58 without build-id.\n Module libavformat.so.58 without build-id.\n Module libavfilter.so.7 without build-id.\n Module libavutil.so.56 without build-id.\n Module libmpv.so.1 without build-id.\n Module libKF5Kirigami2.so.5 without build-id.\n Module libKF5KIONTLM.so.5 without build-id.\n Module libKF5KIOWidgets.so.5 without build-id.\n Module libKF5KIOFileWidgets.so.5 without build-id.\n Module libKF5FileMetaData.so.3 without build-id.\n Module libKF5DocTools.so.5 without build-id.\n Module .haruna-wrapped without build-id.\n Stack trace of thread 21323:\n #0 0x00007f82e80a8c4c _ZN7QObject10disconnectEPKS_PKcS1_S3_ (libQt5Core.so.5 + 0x2f8c4c)\n #1 0x00007f82e9655cd0 n/a (libQt5DBus.so.5 + 0x27cd0)\n #2 0x00007f82e96476c5 n/a (libQt5DBus.so.5 + 0x196c5)\n #3 0x00007f82e7e86441 n/a (libQt5Core.so.5 + 0xd6441)\n #4 0x00007f82e7972eb2 start_thread (libc.so.6 + 0x89eb2)\n #5 0x00007f82e79f531c __clone3 (libc.so.6 + 0x10c31c)\n \n Stack trace of thread 21321:\n #0 0x00007f82e796fc05 __futex_abstimed_wait_common (libc.so.6 + 0x86c05)\n #1 0x00007f82e79723b2 pthread_cond_wait@@GLIBC_2.3.2 (libc.so.6 + 0x893b2)\n #2 0x00007f82e7e8c61b _ZN14QWaitCondition4waitEP6QMutex14QDeadlineTimer (libQt5Core.so.5 + 0xdc61b)\n #3 0x00007f82de360901 n/a (libQt5WaylandClient.so.5 + 0x7c901)\n #4 0x00007f82e7e86441 n/a (libQt5Core.so.5 + 0xd6441)\n #5 0x00007f82e7972eb2 start_thread (libc.so.6 + 0x89eb2)\n #6 0x00007f82e79f531c __clone3 (libc.so.6 + 0x10c31c)\n \n Stack trace of thread 21322:\n #0 0x00007f82e79e8f89 __poll (libc.so.6 + 0xfff89)\n #1 0x00007f82de36095b n/a (libQt5WaylandClient.so.5 + 0x7c95b)\n #2 0x00007f82e7e86441 n/a (libQt5Core.so.5 + 0xd6441)\n #3 0x00007f82e7972eb2 start_thread (libc.so.6 + 0x89eb2)\n #4 0x00007f82e79f531c __clone3 (libc.so.6 + 0x10c31c)\n \n Stack trace of thread 21324:\n #0 0x00007f82e79e8f89 __poll (libc.so.6 + 0xfff89)\n #1 0x00007f82e3e7407e g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x5707e)\n #2 0x00007f82e3e7419f g_main_context_iteration (libglib-2.0.so.0 + 0x5719f)\n #3 0x00007f82e80d16c0 _ZN20QEventDispatcherGlib13processEventsE6QFlagsIN10QEventLoop17ProcessEventsFlagEE (libQt5Core.so.5 + 0x3216c0)\n #4 0x00007f82e807803b _ZN10QEventLoop4execE6QFlagsINS_17ProcessEventsFlagEE (libQt5Core.so.5 + 0x2c803b)\n #5 0x00007f82e7e8512b _ZN7QThread4execEv (libQt5Core.so.5 + 0xd512b)\n #6 0x00007f82e7e86441 n/a (libQt5Core.so.5 + 0xd6441)\n #7 0x00007f82e7972eb2 start_thread (libc.so.6 + 0x89eb2)\n #8 0x00007f82e79f531c __clone3 (libc.so.6 + 0x10c31c)\n \n Stack trace of thread 21320:\n #0 0x00007f82e796fc05 __futex_abstimed_wait_common (libc.so.6 + 0x86c05)\n #1 0x00007f82e79723b2 pthread_cond_wait@@GLIBC_2.3.2 (libc.so.6 + 0x893b2)\n #2 0x00007f82e7e8c61b _ZN14QWaitCondition4waitEP6QMutex14QDeadlineTimer (libQt5Core.so.5 + 0xdc61b)\n #3 0x00007f82e7e86121 _ZN7QThread4waitE14QDeadlineTimer (libQt5Core.so.5 + 0xd6121)\n #4 0x00007f82e96474d3 n/a (libQt5DBus.so.5 + 0x194d3)\n #5 0x00007f82e9647569 n/a (libQt5DBus.so.5 + 0x19569)\n #6 0x00007f82e792c225 __run_exit_handlers (libc.so.6 + 0x43225)\n #7 0x00007f82e792c3aa exit (libc.so.6 + 0x433aa)\n #8 0x00007f82e79161de __libc_start_call_main (libc.so.6 + 0x2d1de)\n #9 0x00007f82e7916297 __libc_start_main@@GLIBC_2.34 (libc.so.6 + 0x2d297)\n #10 0x000000000041b231 _start (.haruna-wrapped + 0x1b231)\n ELF object binary architecture: AMD x86-64\n\n\nwarning: Can't open file /memfd:wayland-cursor (deleted) during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file /memfd:unknown-usage:QtQml (deleted) during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n\nwarning: Can't open file /run/nscd/db639n2z (deleted) during file-backed mapping note processing\n\nwarning: Can't open file anon_inode:i915.gem which was expanded to anon_inode:i915.gem during file-backed mapping note processing\n[New LWP 21323]\n[New LWP 21321]\n[New LWP 21322]\n[New LWP 21324]\n[New LWP 21320]\n[Thread debugging using libthread_db enabled]\nUsing host libthread_db library \"/nix/store/6w8g7njm4mck5dmjxws0z1xnrxvl81xa-glibc-2.34-115/lib/libthread_db.so.1\".\nCore was generated by `/run/current-system/sw/bin/haruna'.\nProgram terminated with signal SIGSEGV, Segmentation fault.\n#0 0x00007f82e80a8c4c in QObject::disconnect(QObject const*, char const*, QObject const*, char const*) () from /nix/store/q89pzz0r5f7kz1ng3dnacmayznv54nr3-qtbase-5.15.3/lib/libQt5Core.so.5\n[Current thread is 1 (Thread 0x7f82c7fff640 (LWP 21323))]\n#0 0x00007f82e80a8c4c in QObject::disconnect(QObject const*, char const*, QObject const*, char const*) () from /nix/store/q89pzz0r5f7kz1ng3dnacmayznv54nr3-qtbase-5.15.3/lib/libQt5Core.so.5\n#1 0x00007f82e9655cd0 in ?? () from /nix/store/q89pzz0r5f7kz1ng3dnacmayznv54nr3-qtbase-5.15.3/lib/libQt5DBus.so.5\n#2 0x00007f82e96476c5 in ?? () from /nix/store/q89pzz0r5f7kz1ng3dnacmayznv54nr3-qtbase-5.15.3/lib/libQt5DBus.so.5\n#3 0x00007f82e7e86441 in ?? () from /nix/store/q89pzz0r5f7kz1ng3dnacmayznv54nr3-qtbase-5.15.3/lib/libQt5Core.so.5\n#4 0x00007f82e7972eb2 in start_thread () from /nix/store/6w8g7njm4mck5dmjxws0z1xnrxvl81xa-glibc-2.34-115/lib/libc.so.6\n#5 0x00007f82e79f531c in clone3 () from /nix/store/6w8g7njm4mck5dmjxws0z1xnrxvl81xa-glibc-2.34-115/lib/libc.so.6\n```\n\n\n### Notify maintainers\n@jojosh\n\n### Metadata\n```console\n - system: `\"x86_64-linux\"`\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369988.1ffba9f2f68`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - channels(kn): `\"nixos\"`\n - channels(root): `\"home-manager, nixos\"`\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170026/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170024","id":1213471584,"node_id":"I_kwDOAEVQ_M5IVBtg","number":170024,"title":"libretro dosbox fails to build on unstable","user":{"login":"x10an14","id":710608,"node_id":"MDQ6VXNlcjcxMDYwOA==","avatar_url":"https://avatars.githubusercontent.com/u/710608?v=4","gravatar_id":"","url":"https://api.github.com/users/x10an14","html_url":"https://github.com/x10an14","followers_url":"https://api.github.com/users/x10an14/followers","following_url":"https://api.github.com/users/x10an14/following{/other_user}","gists_url":"https://api.github.com/users/x10an14/gists{/gist_id}","starred_url":"https://api.github.com/users/x10an14/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/x10an14/subscriptions","organizations_url":"https://api.github.com/users/x10an14/orgs","repos_url":"https://api.github.com/users/x10an14/repos","events_url":"https://api.github.com/users/x10an14/events{/privacy}","received_events_url":"https://api.github.com/users/x10an14/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-23T22:48:36Z","updated_at":"2022-04-24T09:10:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Be on nixpkgs git sha `875b41570c41386017d787caefedc008ddb6e31b` (I've not bisected it more closely)\r\n2. Have this config in your nixos config somewhere:\r\n ```nix\r\n environment.systemPackages = with pkgs; [retroarchFull]\r\n ```\r\n3. `nixos-rebuild build`\r\n\r\n### Expected behavior\r\nFor the build to be successful.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\n`nix log /nix/store/arskaab9sggpqc5jfh5jvwinm0znhhag-libretro-dosbox-unstable-2022-04-08.drv`:\r\nhttps://paste.sr.ht/~x10an14/451f1df94f5fc9a63d6412e14cfe48916002b9f6\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@thiagokokada @kolbycrouch\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.14, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170024/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000/events","html_url":"https://github.com/NixOS/nixpkgs/issues/170000","id":1213439860,"node_id":"I_kwDOAEVQ_M5IU590","number":170000,"title":"nixos-rebuild test leaves around result link with a flake configuration","user":{"login":"2xsaiko","id":3987560,"node_id":"MDQ6VXNlcjM5ODc1NjA=","avatar_url":"https://avatars.githubusercontent.com/u/3987560?v=4","gravatar_id":"","url":"https://api.github.com/users/2xsaiko","html_url":"https://github.com/2xsaiko","followers_url":"https://api.github.com/users/2xsaiko/followers","following_url":"https://api.github.com/users/2xsaiko/following{/other_user}","gists_url":"https://api.github.com/users/2xsaiko/gists{/gist_id}","starred_url":"https://api.github.com/users/2xsaiko/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/2xsaiko/subscriptions","organizations_url":"https://api.github.com/users/2xsaiko/orgs","repos_url":"https://api.github.com/users/2xsaiko/repos","events_url":"https://api.github.com/users/2xsaiko/events{/privacy}","received_events_url":"https://api.github.com/users/2xsaiko/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-23T19:47:04Z","updated_at":"2022-04-24T22:39:41Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nRunning `nixos-rebuild test` leaves a result symlink in the current directory. According to the man page, this is only supposed to happen with `nixos-rebuild build` and `build-vm`. However, it looks like for the flake builder, it only [doesn't place the result link into the current directory for nixos-rebuild switch and boot](https://github.com/NixOS/nixpkgs/blob/204366af6ddce48b873ad5b293fc61285e29a065/pkgs/os-specific/linux/nixos-rebuild/nixos-rebuild.sh#L255).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have a flake system configuration\r\n2. Run `nixos-rebuild test`\r\n3. See result symlink in current directory\r\n\r\n### Expected behavior\r\nNo result symlink is left around in the current directory.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@thiagokokada \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.111, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - nixpkgs: `/etc/nix/inputs/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/170000/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169996","id":1213420453,"node_id":"I_kwDOAEVQ_M5IU1Ol","number":169996,"title":"libsForQt514.qt5.qtwebengine fails to build on master","user":{"login":"gador","id":1883533,"node_id":"MDQ6VXNlcjE4ODM1MzM=","avatar_url":"https://avatars.githubusercontent.com/u/1883533?v=4","gravatar_id":"","url":"https://api.github.com/users/gador","html_url":"https://github.com/gador","followers_url":"https://api.github.com/users/gador/followers","following_url":"https://api.github.com/users/gador/following{/other_user}","gists_url":"https://api.github.com/users/gador/gists{/gist_id}","starred_url":"https://api.github.com/users/gador/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/gador/subscriptions","organizations_url":"https://api.github.com/users/gador/orgs","repos_url":"https://api.github.com/users/gador/repos","events_url":"https://api.github.com/users/gador/events{/privacy}","received_events_url":"https://api.github.com/users/gador/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null},{"id":3536622080,"node_id":"LA_kwDOAEVQ_M7SzJIA","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20build%20failure","name":"0.kind: build failure","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-23T18:53:53Z","updated_at":"2022-04-24T22:39:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nlibsForQt514.qt5.qtwebengine currently fails to build locally and on [hydra](https://hydra.nixos.org/build/174137848). \r\n[Build log on hydra](https://hydra.nixos.org/build/174137848/nixlog/3)\r\n\r\nThe interessting line seems to be:\r\n```\r\n/nix/store/m2vh2ny7bqpwij1gpmvl5gxj7y4dgr4f-binutils-2.38/bin/ld: /nix/store/ggj5c9a57qs8i83rxwv34hiz7jgm8hml-x265-3.5/lib/libx265.so.199: undefined reference to `std::__throw_bad_array_new_length()@GLIBCXX_3.4.29'\r\ncollect2: error: ld returned 1 exit status\r\n```\r\nThe last successful build on hydra was linked to e1118817a12dba39081d9e70ae52dd38aa184c2e. After that it seems to fail (starting with ba88a5afa6fff7710c17b5423ff9d721386c4164)\r\n\r\nBisecting takes forever. I would hazard a guess that it has to do with 95af2245a32f8e1310ad4e3bf50b76d86ddbbc0a and PR #168737 which broke some other packages as well.\r\n\r\nEDIT:\r\n```\r\n# git bisect --first-parent\r\n95af2245a32f8e1310ad4e3bf50b76d86ddbbc0a is the first bad commit\r\ncommit 95af2245a32f8e1310ad4e3bf50b76d86ddbbc0a\r\nMerge: 212dde2609b 70d726c2a51\r\nAuthor: Martin Weinelt <mweinelt@users.noreply.github.com>\r\nDate: Sun Apr 17 20:38:16 2022 +0200\r\n```\r\n\r\nEDIT2:\r\nThe error seems to stem from the c++ upgrade. The error message is referenced e.g. here https://github.com/JuliaLang/julia/issues/40703.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. checkout nixpkgs master\r\n2. nix-build -A libsForQt514.qt5.qtwebengine .\r\n\r\n### Expected behavior\r\n\r\nBuild should succeed. \r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@matthewbauer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05.20220417.862c63f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos, nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169996/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169995","id":1213419822,"node_id":"I_kwDOAEVQ_M5IU1Eu","number":169995,"title":"mono: LLVM backend","user":{"login":"armeenm","id":29145250,"node_id":"MDQ6VXNlcjI5MTQ1MjUw","avatar_url":"https://avatars.githubusercontent.com/u/29145250?v=4","gravatar_id":"","url":"https://api.github.com/users/armeenm","html_url":"https://github.com/armeenm","followers_url":"https://api.github.com/users/armeenm/followers","following_url":"https://api.github.com/users/armeenm/following{/other_user}","gists_url":"https://api.github.com/users/armeenm/gists{/gist_id}","starred_url":"https://api.github.com/users/armeenm/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armeenm/subscriptions","organizations_url":"https://api.github.com/users/armeenm/orgs","repos_url":"https://api.github.com/users/armeenm/repos","events_url":"https://api.github.com/users/armeenm/events{/privacy}","received_events_url":"https://api.github.com/users/armeenm/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-23T18:51:06Z","updated_at":"2022-04-23T18:51:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\nThe LLVM backend for Mono [looks like it could be bumped](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/compilers/mono/llvm.nix).\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: mono\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 2017-02-15\r\ndesired version: [2022-04-18](https://github.com/dotnet/llvm-project/commits/release/11.x)\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @thoughtpolice \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169995/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169980","id":1213369024,"node_id":"I_kwDOAEVQ_M5IUorA","number":169980,"title":"Swiftshader not building","user":{"login":"AtilaSaraiva","id":29521461,"node_id":"MDQ6VXNlcjI5NTIxNDYx","avatar_url":"https://avatars.githubusercontent.com/u/29521461?v=4","gravatar_id":"","url":"https://api.github.com/users/AtilaSaraiva","html_url":"https://github.com/AtilaSaraiva","followers_url":"https://api.github.com/users/AtilaSaraiva/followers","following_url":"https://api.github.com/users/AtilaSaraiva/following{/other_user}","gists_url":"https://api.github.com/users/AtilaSaraiva/gists{/gist_id}","starred_url":"https://api.github.com/users/AtilaSaraiva/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AtilaSaraiva/subscriptions","organizations_url":"https://api.github.com/users/AtilaSaraiva/orgs","repos_url":"https://api.github.com/users/AtilaSaraiva/repos","events_url":"https://api.github.com/users/AtilaSaraiva/events{/privacy}","received_events_url":"https://api.github.com/users/AtilaSaraiva/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-23T17:31:55Z","updated_at":"2022-04-23T17:31:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe swiftshader derivation is not properly building.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...clone the nixpkgs repository master branch\r\n2. ...nix-build -A swiftshader\r\n\r\n### Expected behavior\r\nThe expected behaviour is for the derivation to build, but it doesn't giving:\r\n```\r\n[...]\r\n[ 15%] \u001b[32mBuilding CXX object third_party/SPIRV-Tools/source/CMakeFiles/SPIRV-Tools-shared.dir/val/basic_block.cpp.o\u001b[0m\r\nIn file included from \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:15\u001b[m\u001b[K:\r\nIn member function '\u001b[01m\u001b[Ksw::RGB9E5::operator unsigned int() const\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentSparse_Test::TestBody()\u001b[m\u001b[K' at \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:91:42\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/src/System/../System/Half.hpp:115:68:\u001b[m\u001b[K \u001b[01;31m\u001b[Kerror: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' is used uninitialized [\u001b[01;31m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wuninitialized\u0007-Werror=uninitialized\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 115 | return *reinterpret_cast<const unsigned int *>(this\u001b[01;31m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;31m\u001b[K^\u001b[m\u001b[K\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:\u001b[m\u001b[K In member function '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentSparse_Test::TestBody()\u001b[m\u001b[K':\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:91:56:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' declared here\r\n 91 | unsigned int val = RGB9E5(f, 0.0f, 0.0f\u001b[01;36m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;36m\u001b[K^\u001b[m\u001b[K\r\nIn file included from \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:15\u001b[m\u001b[K:\r\nIn member function '\u001b[01m\u001b[Ksw::RGB9E5::operator unsigned int() const\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentRandom_Test::TestBody()\u001b[m\u001b[K' at \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:112:36\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/src/System/../System/Half.hpp:115:68:\u001b[m\u001b[K \u001b[01;31m\u001b[Kerror: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' is used uninitialized [\u001b[01;31m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wuninitialized\u0007-Werror=uninitialized\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 115 | return *reinterpret_cast<const unsigned int *>(this\u001b[01;31m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;31m\u001b[K^\u001b[m\u001b[K\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:\u001b[m\u001b[K In member function '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentRandom_Test::TestBody()\u001b[m\u001b[K':\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:112:50:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' declared here\r\n 112 | unsigned int val = RGB9E5(r, g, b\u001b[01;36m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;36m\u001b[K^\u001b[m\u001b[K\r\nIn file included from \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:15\u001b[m\u001b[K:\r\nIn member function '\u001b[01m\u001b[Ksw::RGB9E5::operator unsigned int() const\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentExhaustive_Test::TestBody()\u001b[m\u001b[K' at \u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:129:42\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/src/System/../System/Half.hpp:115:68:\u001b[m\u001b[K \u001b[01;31m\u001b[Kerror: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' is used uninitialized [\u001b[01;31m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wuninitialized\u0007-Werror=uninitialized\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 115 | return *reinterpret_cast<const unsigned int *>(this\u001b[01;31m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;31m\u001b[K^\u001b[m\u001b[K\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:\u001b[m\u001b[K In member function '\u001b[01m\u001b[Kvirtual void MathTest_SharedExponentExhaustive_Test::TestBody()\u001b[m\u001b[K':\r\n\u001b[01m\u001b[K/build/SwiftShader-4ed9d34/tests/MathUnitTests/unittests.cpp:129:56:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[K'\u001b[01m\u001b[K<anonymous>\u001b[m\u001b[K' declared here\r\n 129 | unsigned int val = RGB9E5(f, 0.0f, 0.0f\u001b[01;36m\u001b[K)\u001b[m\u001b[K;\r\n | \u001b[01;36m\u001b[K^\u001b[m\u001b[K\r\ncc1plus: all warnings being treated as errors\r\nmake[2]: *** [tests/MathUnitTests/CMakeFiles/math-unittests.dir/build.make:90: tests/MathUnitTests/CMakeFiles/math-unittests.dir/unittests.cpp.o] Error 1\r\nmake[1]: *** [CMakeFiles/Makefile2:2537: tests/MathUnitTests/CMakeFiles/math-unittests.dir/all] Error 2\r\nmake[1]: *** Waiting for unfinished jobs....\r\n[ 15%] \u001b[32mBuilding CXX object third_party/SPIRV-Tools/source/CMakeFiles/SPIRV-Tools-shared.dir/val/construct.cpp.o\u001b[0m\r\n[...]\r\n```\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@expipiplus1 \r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169980/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169970","id":1213359266,"node_id":"I_kwDOAEVQ_M5IUmSi","number":169970,"title":"haruna: request update 0.7.3 -> 0.8.0","user":{"login":"SuperSamus","id":40663462,"node_id":"MDQ6VXNlcjQwNjYzNDYy","avatar_url":"https://avatars.githubusercontent.com/u/40663462?v=4","gravatar_id":"","url":"https://api.github.com/users/SuperSamus","html_url":"https://github.com/SuperSamus","followers_url":"https://api.github.com/users/SuperSamus/followers","following_url":"https://api.github.com/users/SuperSamus/following{/other_user}","gists_url":"https://api.github.com/users/SuperSamus/gists{/gist_id}","starred_url":"https://api.github.com/users/SuperSamus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SuperSamus/subscriptions","organizations_url":"https://api.github.com/users/SuperSamus/orgs","repos_url":"https://api.github.com/users/SuperSamus/repos","events_url":"https://api.github.com/users/SuperSamus/events{/privacy}","received_events_url":"https://api.github.com/users/SuperSamus/received_events","type":"User","site_admin":false},"labels":[{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-23T16:46:22Z","updated_at":"2022-04-24T00:28:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: haruna\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.7.3\r\ndesired version: 0.8.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @jojosch \r\n\r\n###### Note for maintainers\r\n\r\nI tried to update it myself, but when trying to open the result I get either:\r\n```\r\nfish: Job 1, '/nix/store/qjwn854dkqnbbx6pc6aw…' terminated by signal SIGSEGV (Address boundary error)\r\n```\r\nor:\r\n```\r\nunknown() : QQmlApplicationEngine failed to load component\r\n\r\nunknown() : qrc:/qml/main.qml:78:5: SettingsEditor is not a type\r\n```\r\n\r\nSome dependencies could be moved to `nativeBuildInputs`, since they are build time only.\r\n\r\nThe project supports `yt-dlp` other than `youtube-dl`. Since `mpv` uses the former, maybe switching could be considered.\r\n\r\nThe homepage is outdated. It's now \"https://invent.kde.org/multimedia/haruna\".\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169970/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169956","id":1213334084,"node_id":"I_kwDOAEVQ_M5IUgJE","number":169956,"title":"rabbitmq-server doesn't build on x86_64-darwin","user":{"login":"turion","id":303489,"node_id":"MDQ6VXNlcjMwMzQ4OQ==","avatar_url":"https://avatars.githubusercontent.com/u/303489?v=4","gravatar_id":"","url":"https://api.github.com/users/turion","html_url":"https://github.com/turion","followers_url":"https://api.github.com/users/turion/followers","following_url":"https://api.github.com/users/turion/following{/other_user}","gists_url":"https://api.github.com/users/turion/gists{/gist_id}","starred_url":"https://api.github.com/users/turion/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/turion/subscriptions","organizations_url":"https://api.github.com/users/turion/orgs","repos_url":"https://api.github.com/users/turion/repos","events_url":"https://api.github.com/users/turion/events{/privacy}","received_events_url":"https://api.github.com/users/turion/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":355392299,"node_id":"MDU6TGFiZWwzNTUzOTIyOTk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20erlang","name":"6.topic: erlang","color":"fef2c0","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-23T14:52:33Z","updated_at":"2022-04-25T11:02:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"In https://github.com/NixOS/nixpkgs/pull/169684 we noticed that `rabbitmq-server` doesn't build on `x86_64-darwin` anymore despite no changes relevant to this.\r\n\r\nThis is probably due to a cross-compilation issue in erlang on darwin. @reckenrode did some valuable research on this: https://github.com/NixOS/nixpkgs/pull/169684#issuecomment-1107470733\r\n\r\nProbably, `elixir` and `erlang` need to go to `depsBuildBuild`, but this doesn't fix the problem entirely.\r\n\r\nCC @armeenm @NixOS/darwin-maintainers ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169956/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169949","id":1213302297,"node_id":"I_kwDOAEVQ_M5IUYYZ","number":169949,"title":"Performance regression in Gnome 41.1 on kernel >=5.16.10 with AMDGPU driven Navi 14 based cards","user":{"login":"icodeforyou-dot-net","id":61844926,"node_id":"MDQ6VXNlcjYxODQ0OTI2","avatar_url":"https://avatars.githubusercontent.com/u/61844926?v=4","gravatar_id":"","url":"https://api.github.com/users/icodeforyou-dot-net","html_url":"https://github.com/icodeforyou-dot-net","followers_url":"https://api.github.com/users/icodeforyou-dot-net/followers","following_url":"https://api.github.com/users/icodeforyou-dot-net/following{/other_user}","gists_url":"https://api.github.com/users/icodeforyou-dot-net/gists{/gist_id}","starred_url":"https://api.github.com/users/icodeforyou-dot-net/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/icodeforyou-dot-net/subscriptions","organizations_url":"https://api.github.com/users/icodeforyou-dot-net/orgs","repos_url":"https://api.github.com/users/icodeforyou-dot-net/repos","events_url":"https://api.github.com/users/icodeforyou-dot-net/events{/privacy}","received_events_url":"https://api.github.com/users/icodeforyou-dot-net/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-23T13:41:25Z","updated_at":"2022-04-23T17:20:50Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nUpdating from kernel 5.16.9 to 5.16.10 and above (tested on 5.17.4) leads to performance degradation in Gnome 41.1 on AMDGPU driven Navi 14 based card in animations such as moving between workspaces, opening applications menu and moving of desktop windows.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n1. Update Linux kernel from 5.16.9 to 5.16.10 or above\r\n2. Run Gnome 41.1 with AMDGPU driver and AMD 5500XT Navi 14 based card on 4k@60Hz\r\n3. Move larger windows around with mouse, open app menu or switch between workspaces\r\n4. Enjoy sluggish animations!\r\n\r\n### Expected behavior\r\n\r\nSmooth animations on 4k@60hz as on kernel 5.16.9\r\n\r\n### Additional context\r\n\r\nI assume that the bug is due to some change in the Linux kernel from 5.16.9 to 5.16.10. Changelog for kernel 5.16.10 included several changes to AMDGPU drivers. Any help on how to go after the problem on my own are appreciated.\r\n\r\n### Notify maintainers\r\n@TredwellGit @Ma27 @NeQuissimus @alyssais @thoughtpolice\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169949/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169943","id":1213293086,"node_id":"I_kwDOAEVQ_M5IUWIe","number":169943,"title":"Olaris Server","user":{"login":"mrsetna","id":104261145,"node_id":"U_kgDOBjbmGQ","avatar_url":"https://avatars.githubusercontent.com/u/104261145?v=4","gravatar_id":"","url":"https://api.github.com/users/mrsetna","html_url":"https://github.com/mrsetna","followers_url":"https://api.github.com/users/mrsetna/followers","following_url":"https://api.github.com/users/mrsetna/following{/other_user}","gists_url":"https://api.github.com/users/mrsetna/gists{/gist_id}","starred_url":"https://api.github.com/users/mrsetna/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mrsetna/subscriptions","organizations_url":"https://api.github.com/users/mrsetna/orgs","repos_url":"https://api.github.com/users/mrsetna/repos","events_url":"https://api.github.com/users/mrsetna/events{/privacy}","received_events_url":"https://api.github.com/users/mrsetna/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-23T12:54:09Z","updated_at":"2022-04-23T12:54:09Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nOlaris is an open-source, community driven, media manager and transcoding server. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: [https://blog.olaris.tv](https://blog.olaris.tv)\r\n* source URL: [https://gitlab.com/olaris/olaris-server](https://gitlab.com/olaris/olaris-server)\r\n* license: GNU GENERAL PUBLIC LICENSE Version 3, 29 June 2007\r\n* platform: Linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169943/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169901","id":1213209311,"node_id":"I_kwDOAEVQ_M5IUBrf","number":169901,"title":"DaVinci Resolve Studio 18 Beta","user":{"login":"valwithoutfriends","id":100195058,"node_id":"U_kgDOBfja8g","avatar_url":"https://avatars.githubusercontent.com/u/100195058?v=4","gravatar_id":"","url":"https://api.github.com/users/valwithoutfriends","html_url":"https://github.com/valwithoutfriends","followers_url":"https://api.github.com/users/valwithoutfriends/followers","following_url":"https://api.github.com/users/valwithoutfriends/following{/other_user}","gists_url":"https://api.github.com/users/valwithoutfriends/gists{/gist_id}","starred_url":"https://api.github.com/users/valwithoutfriends/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/valwithoutfriends/subscriptions","organizations_url":"https://api.github.com/users/valwithoutfriends/orgs","repos_url":"https://api.github.com/users/valwithoutfriends/repos","events_url":"https://api.github.com/users/valwithoutfriends/events{/privacy}","received_events_url":"https://api.github.com/users/valwithoutfriends/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-23T05:53:01Z","updated_at":"2022-04-23T18:49:11Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"I wanna use NixOS my only daily drive. There is a lot of Resolve users around. Studio and free version is needed. :)\r\n\r\nhomepage URL: https://www.blackmagicdesign.com/fi/products/davinciresolve/\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169901/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169820","id":1212562026,"node_id":"I_kwDOAEVQ_M5IRjpq","number":169820,"title":"switch-to-configuration assertions","user":{"login":"kirelagin","id":451835,"node_id":"MDQ6VXNlcjQ1MTgzNQ==","avatar_url":"https://avatars.githubusercontent.com/u/451835?v=4","gravatar_id":"","url":"https://api.github.com/users/kirelagin","html_url":"https://github.com/kirelagin","followers_url":"https://api.github.com/users/kirelagin/followers","following_url":"https://api.github.com/users/kirelagin/following{/other_user}","gists_url":"https://api.github.com/users/kirelagin/gists{/gist_id}","starred_url":"https://api.github.com/users/kirelagin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kirelagin/subscriptions","organizations_url":"https://api.github.com/users/kirelagin/orgs","repos_url":"https://api.github.com/users/kirelagin/repos","events_url":"https://api.github.com/users/kirelagin/events{/privacy}","received_events_url":"https://api.github.com/users/kirelagin/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-22T16:33:57Z","updated_at":"2022-04-26T20:49:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I am looking for a way to implement assertions for `nixos-rebuild switch`, that is, something that will allow me to test a condition at activation time and, if it is not satisfied, print an error and cancel activation entirely.\r\n\r\nMy current approach is to write a custom activation script, however, as far as I can tell, errors from activation snippets are ignored (only a message is printed). I can also do `exit 1`, but, while it will terminate the activation script (i.e. no more snippets will be executed), all other steps (e.g. restarting units) will still happen.\r\n\r\nI was actually surprised by the facts that an error in an activation script does not cancel the activation, I would actually expect everything to fail in this case. However, I am not sure that changing this behaviour at this point is reasonable. But what about having something like an `$out/assertions` script that `switch-to-configuration.pl` will execute at the very beginning and cancel everything if it fails?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169820/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169812","id":1212503361,"node_id":"I_kwDOAEVQ_M5IRVVB","number":169812,"title":"github-runner impure environment","user":{"login":"aanderse","id":7755101,"node_id":"MDQ6VXNlcjc3NTUxMDE=","avatar_url":"https://avatars.githubusercontent.com/u/7755101?v=4","gravatar_id":"","url":"https://api.github.com/users/aanderse","html_url":"https://github.com/aanderse","followers_url":"https://api.github.com/users/aanderse/followers","following_url":"https://api.github.com/users/aanderse/following{/other_user}","gists_url":"https://api.github.com/users/aanderse/gists{/gist_id}","starred_url":"https://api.github.com/users/aanderse/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/aanderse/subscriptions","organizations_url":"https://api.github.com/users/aanderse/orgs","repos_url":"https://api.github.com/users/aanderse/repos","events_url":"https://api.github.com/users/aanderse/events{/privacy}","received_events_url":"https://api.github.com/users/aanderse/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-22T15:30:15Z","updated_at":"2022-04-29T16:29:33Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nour `github-runner` package is failing some very basic tasks because `LD_LIBRARY_PATH` is injected into the environment\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n1. deploy `github-runner` on NixOS\r\n```nix\r\n{\r\n services.github-runner.enable = true;\r\n services.github-runner.url = \"https://github.com/ORG_NAME\";\r\n services.github-runner.tokenFile = config.sops.secrets.\"github-runner/token\".path;\r\n services.github-runner.extraPackages = with pkgs; [ config.virtualisation.docker.package ];\r\n\r\n virtualisation.docker.enable = true;\r\n\r\n systemd.services.github-runner.serviceConfig.SupplementaryGroups = [ \"docker\" ];\r\n}\r\n```\r\n2. add this to your repo under `.github/workflows/self-hosted-runner-bug.yml`:\r\n```yaml\r\nname: \"LD_LIBRARY_PATH issue with github-runner package\"\r\non: [push, pull_request]\r\njobs:\r\n cargo-version:\r\n runs-on: self-hosted\r\n steps:\r\n - name: demonstrate cargo failing because of mismatched libc version\r\n run: nix run nixpkgs#cargo -- --version\r\n```\r\n3. push to your repo and watch the failure\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\ni don't want `LD_LIBRARY_PATH` from our `github-runner` package pushed down to the execution environment\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n\r\n\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/41929bd53f24b0758ffc33f70d3bd1ef109e4f6c/pkgs/development/tools/continuous-integration/github-runner/default.nix#L275-L279\r\n\r\ni'm fairly certain the use of `makeWrapper` and `LD_LIBRARY_PATH` is the problem here, specifically `cargo` specifies `curl` as a `buildInput` in its derivation, but `github-runner` pushes a `LD_LIBRARY_PATH` with a different `curl` into all execution environments\r\n\r\nshouldn't we be pushing `patchelf` instead of `makeWrapper` for [these lines](https://github.com/NixOS/nixpkgs/blob/41929bd53f24b0758ffc33f70d3bd1ef109e4f6c/pkgs/development/tools/continuous-integration/github-runner/default.nix#L285-L291)?\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\nping @veehaitch @newAM\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n\r\nversion of nix used on the machine running `github-runner`: 491ad20776074706da6befe0cb8334f2df23fc00","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169812/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169792","id":1212372460,"node_id":"I_kwDOAEVQ_M5IQ1Xs","number":169792,"title":"Unable to get EGL working with Intel integrated graphics","user":{"login":"PAI5REECHO","id":96688573,"node_id":"U_kgDOBcNZvQ","avatar_url":"https://avatars.githubusercontent.com/u/96688573?v=4","gravatar_id":"","url":"https://api.github.com/users/PAI5REECHO","html_url":"https://github.com/PAI5REECHO","followers_url":"https://api.github.com/users/PAI5REECHO/followers","following_url":"https://api.github.com/users/PAI5REECHO/following{/other_user}","gists_url":"https://api.github.com/users/PAI5REECHO/gists{/gist_id}","starred_url":"https://api.github.com/users/PAI5REECHO/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PAI5REECHO/subscriptions","organizations_url":"https://api.github.com/users/PAI5REECHO/orgs","repos_url":"https://api.github.com/users/PAI5REECHO/repos","events_url":"https://api.github.com/users/PAI5REECHO/events{/privacy}","received_events_url":"https://api.github.com/users/PAI5REECHO/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-22T13:36:03Z","updated_at":"2022-04-23T17:21:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'm not really sure what's wrong with my system configuration but I'm unable to get EGL working under Wayland or Xorg when it was previously working some days ago. I'm on unstable so maybe I updated something that broke it?\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Configure a system with Intel HD 4000 graphics using the following:\r\n```nix\r\n{ ... }: {\r\n environment = {\r\n variables = {\r\n MESA_GL_VERSION_OVERRIDE = \"4.3\";\r\n };\r\n };\r\n\r\n hardware = {\r\n opengl = {\r\n enable = true;\r\n driSupport = true;\r\n driSupport32Bit = true;\r\n extraPackages = with pkgs; [\r\n vaapiIntel\r\n vaapiVdpau\r\n libvdpau-va-gl\r\n ];\r\n };\r\n };\r\n}\r\n```\r\n2. Run `eglinfo` in SwayWM:\r\n```console\r\n$ echo $DISPLAY $MESA_GL_VERSION_OVERRIDE $WAYLAND_DISPLAY\r\n:0 4.3 wayland-1\r\n$ eglinfo\r\n...\r\n\r\nDevice platform:\r\neglinfo: eglInitialize failed\r\n```\r\n\r\n### Expected behavior\r\nEGL should initialize\r\n\r\n### Additional context\r\nNormal OpenGL applications work (`glxinfo` reports fine and `glxgears` works)\r\n\r\n### Notify maintainers\r\nNot sure who'd be best to ping here since the OpenGL module & `vaapiIntel` package list no maintainers.\r\n@primeos\r\n@colemickens\r\n@Synthetica9\r\n@Ma27 \r\n@abbradar\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.9.0pre20220420_9345b4e`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169792/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169775","id":1212299211,"node_id":"I_kwDOAEVQ_M5IQjfL","number":169775,"title":"Even more minimal JRE","user":{"login":"regiskuckaertz","id":629976,"node_id":"MDQ6VXNlcjYyOTk3Ng==","avatar_url":"https://avatars.githubusercontent.com/u/629976?v=4","gravatar_id":"","url":"https://api.github.com/users/regiskuckaertz","html_url":"https://github.com/regiskuckaertz","followers_url":"https://api.github.com/users/regiskuckaertz/followers","following_url":"https://api.github.com/users/regiskuckaertz/following{/other_user}","gists_url":"https://api.github.com/users/regiskuckaertz/gists{/gist_id}","starred_url":"https://api.github.com/users/regiskuckaertz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/regiskuckaertz/subscriptions","organizations_url":"https://api.github.com/users/regiskuckaertz/orgs","repos_url":"https://api.github.com/users/regiskuckaertz/repos","events_url":"https://api.github.com/users/regiskuckaertz/events{/privacy}","received_events_url":"https://api.github.com/users/regiskuckaertz/received_events","type":"User","site_admin":false},"labels":[{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-22T12:26:01Z","updated_at":"2022-04-30T07:52:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"https://github.com/NixOS/nixpkgs/blob/c542baa0c894796c92a8173dead027f3b952c22e/pkgs/development/compilers/openjdk/jre.nix#L24\r\n\r\nHow would you feel about adding these options:\r\n```\r\n--no-header-files\r\n Excludes header files.\r\n--no-man-pages\r\n Excludes man pages.\r\n--compress=2\r\n Enable ZIP compression of resources\r\n```\r\n\r\nWith jdk17_headless and the sole `java.base` module, it drops from 80 to 32MB.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169775/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169733","id":1212023486,"node_id":"I_kwDOAEVQ_M5IPgK-","number":169733,"title":"nextcloud: config is seemingly garbage-collected","user":{"login":"rien","id":3226995,"node_id":"MDQ6VXNlcjMyMjY5OTU=","avatar_url":"https://avatars.githubusercontent.com/u/3226995?v=4","gravatar_id":"","url":"https://api.github.com/users/rien","html_url":"https://github.com/rien","followers_url":"https://api.github.com/users/rien/followers","following_url":"https://api.github.com/users/rien/following{/other_user}","gists_url":"https://api.github.com/users/rien/gists{/gist_id}","starred_url":"https://api.github.com/users/rien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rien/subscriptions","organizations_url":"https://api.github.com/users/rien/orgs","repos_url":"https://api.github.com/users/rien/repos","events_url":"https://api.github.com/users/rien/events{/privacy}","received_events_url":"https://api.github.com/users/rien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-22T08:39:29Z","updated_at":"2022-04-26T21:05:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nToday, pas midnight (00:00) my nextcloud instance broke. It was giving the following error:\r\n\r\n```\r\nInternal Server Error\r\n\r\nThe server encountered an internal error and was unable to complete your request.\r\nPlease contact the server administrator if this error reappears multiple times, please include the technical details below in your report.\r\nMore details can be found in the webserver log.\r\n<br />\r\n<b>Fatal error</b>: Uncaught TypeError: flock(): Argument #1 ($stream) must be of type resource, bool given in /nix/store/y6hqghw0ax0ybxdiaalbn1zk3s4qk5bz-nextcloud-23.0.3/lib/private/Config.php:215\r\n```\r\n\r\nIn the corresponding php file, it seems like the actual config file is unreadable or doesn't exist.\r\n\r\nI tried restarting `nginx` and `php-fpm-nextcloud`, but the error persisted.\r\n\r\nLooking at the log file, a few moments before these error messages occurred, an automatic `nix-gc` happened, containing among the listing of deleted files the following log line:\r\n```\r\nApr 22 00:00:02 space nix-gc-start[1148255]: deleting '/nix/store/hrz874jjb96mrwxf2n4sycqfswfci6a0-nextcloud-config.php'\r\n```\r\n\r\n**The crash was fixed by rebuilding the system.** This seems to suggest that the config was actually still being referenced somewhere, as restarting the relevant services wasn't doing anything. \r\n\r\nI _think_ it could be caused by the following line:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/821a81dcc4e872bf2836ac18b12938e7de6c0f49/nixos/modules/services/web-apps/nextcloud.nix#L776\r\n\r\nWhere the `overrideConfig` is garbage collected. But that seems weird, because the current config should reference this file somehow.\r\n\r\n\r\n### Steps To Reproduce\r\n\r\nUnfortunately I could not reproduce this by performing a `nix-collect-garbage -d` manually. By rebuilding and garbage collecting my system, I think I also removed all evidence required to troubleshoot this issue unfortunately.\r\n\r\n### Expected behavior\r\n\r\nNextcloud shouldn't stop working after a garbage collect.\r\n\r\n### Additional context\r\n\r\nMy system configuration is a NixOS flake over at [rien/nixos-config#580efa35](https://github.com/rien/nixos-config/tree/580efa35cb057682397f4227b4770ad25c02cb03). There are multiple machines configured, the server experiencing the crash was [space](https://github.com/rien/nixos-config/blob/580efa35cb057682397f4227b4770ad25c02cb03/machines/space/default.nix) and it was using [this custom module to configure nextcould](https://github.com/rien/nixos-config/blob/580efa35cb057682397f4227b4770ad25c02cb03/modules/nextcloud.nix). All links reference the commit that was currently deployed to the server.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@schneefux @bachp @globin @fpletz @ma27\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 22.05 (Quokka), 22.05.20220413.ff9efb0`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-20.09.1721.896270d629e\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169733/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169729","id":1212008331,"node_id":"I_kwDOAEVQ_M5IPceL","number":169729,"title":"intel-graphics-compiler is not being fetched from the cache and the compilation fails","user":{"login":"leiserfg","id":2947276,"node_id":"MDQ6VXNlcjI5NDcyNzY=","avatar_url":"https://avatars.githubusercontent.com/u/2947276?v=4","gravatar_id":"","url":"https://api.github.com/users/leiserfg","html_url":"https://github.com/leiserfg","followers_url":"https://api.github.com/users/leiserfg/followers","following_url":"https://api.github.com/users/leiserfg/following{/other_user}","gists_url":"https://api.github.com/users/leiserfg/gists{/gist_id}","starred_url":"https://api.github.com/users/leiserfg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/leiserfg/subscriptions","organizations_url":"https://api.github.com/users/leiserfg/orgs","repos_url":"https://api.github.com/users/leiserfg/repos","events_url":"https://api.github.com/users/leiserfg/events{/privacy}","received_events_url":"https://api.github.com/users/leiserfg/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-22T08:25:11Z","updated_at":"2022-04-28T17:23:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI use intel-compute-runtime to provide opencl to darktable and it's not being fetched from the cache since today 2022-04-22\r\nAlso, compiling intel-graphics-compiler (which is a dependency) fails so I had to remove it altogether.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n`nix-env -i intel-compute-runtime`\r\n\r\n### Expected behavior\r\nGet's installed from cache\r\n\r\n### Notify maintainers\r\n@gloaming \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nnix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32-1-MANJARO, Manjaro Linux, noversion, rolling`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(leiserfg): `\"home-manager, nixpkgs\"`\r\n - nixpkgs: `/home/leiserfg/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169729/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169697","id":1211845071,"node_id":"I_kwDOAEVQ_M5IO0nP","number":169697,"title":"Add Korean Nanum fonts","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-22T05:37:22Z","updated_at":"2022-04-22T05:37:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAdd Korean Nanum fonts: \r\n\r\n- Nanum Gothic\r\n- Nanum Barun Gothic\r\n- Nanum Barunpen\r\n- Nanum Brush\r\n- Nanum Myengjo\r\n- Nanum Pen\r\n- Nanum Square\r\n- Nanum Square Round\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://hangeul.naver.com/font\r\n* source URL: http://archive.ubuntu.com/ubuntu/pool/universe/f/fonts-nanum/fonts-nanum_20170925.orig.tar.xz\r\n* license: ofl\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169697/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169693","id":1211832966,"node_id":"I_kwDOAEVQ_M5IOxqG","number":169693,"title":"systemd-boot: nixos-rebuild switch fails with non-zero exit status","user":{"login":"volisoft","id":6010868,"node_id":"MDQ6VXNlcjYwMTA4Njg=","avatar_url":"https://avatars.githubusercontent.com/u/6010868?v=4","gravatar_id":"","url":"https://api.github.com/users/volisoft","html_url":"https://github.com/volisoft","followers_url":"https://api.github.com/users/volisoft/followers","following_url":"https://api.github.com/users/volisoft/following{/other_user}","gists_url":"https://api.github.com/users/volisoft/gists{/gist_id}","starred_url":"https://api.github.com/users/volisoft/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/volisoft/subscriptions","organizations_url":"https://api.github.com/users/volisoft/orgs","repos_url":"https://api.github.com/users/volisoft/repos","events_url":"https://api.github.com/users/volisoft/events{/privacy}","received_events_url":"https://api.github.com/users/volisoft/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":23,"created_at":"2022-04-22T05:16:16Z","updated_at":"2022-04-27T11:50:02Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nAfter updating to the latest nixos-unstable `nixos-rebuild switch` fails with error. \r\n```console\r\nbuilding the system configuration...\r\nwarning: Git tree '/home/dev/x/my/prj/nix' is dirty\r\nupdating systemd-boot from (249.7) to (250.4)\r\nSource file \"/nix/store/h5k31zlk8j216523prxwwqxn8bdlakpl-systemd-250.4/lib/systemd/boot/efi/systemd-bootaa64.efi\" does not carry version information!\r\nSource file \"/nix/store/h5k31zlk8j216523prxwwqxn8bdlakpl-systemd-250.4/lib/systemd/boot/efi/systemd-bootaa64.efi\" does not carry version information!\r\nTraceback (most recent call last):\r\n File \"/nix/store/53c7jabsxd2wizryywviz4n8jk9cyb9y-systemd-boot\", line 316, in <module>\r\n main()\r\n File \"/nix/store/53c7jabsxd2wizryywviz4n8jk9cyb9y-systemd-boot\", line 267, in main\r\n subprocess.check_call([\"/nix/store/h5k31zlk8j216523prxwwqxn8bdlakpl-systemd-250.4/bin/bootctl\", \"--path=/boot\", \"update\"])\r\n File \"/nix/store/9zncdsgdwz3h7hnmfqnc0ya0c27hwfi7-python3-3.9.12/lib/python3.9/subprocess.py\", line 373, in check_call\r\n raise CalledProcessError(retcode, cmd)\r\nsubprocess.CalledProcessError: Command '['/nix/store/h5k31zlk8j216523prxwwqxn8bdlakpl-systemd-250.4/bin/bootctl', '--path=/boot', 'update']' returned non-zero exit status 1.\r\nwarning: error(s) occurred while switching to the new configuration\r\n\r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. run `sudo nixos-rebuild switch --flake '.#dev-system`\r\n\r\n### Expected behavior\r\nThe system should be updated without an error.\r\n\r\n### Screenshots\r\nN/A\r\n### Additional context\r\nThe system is built using nix flakes\r\n### Notify maintainers\r\n\r\n@flokli @Kloenk @Mic92 @trofi \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/vxi9xxfb59slzql57hbvrkvrac8khmkj-bash-interactive-5.1-p12-dev\r\ncopying path '/nix/store/vxi9xxfb59slzql57hbvrkvrac8khmkj-bash-interactive-5.1-p12-dev' from 'https://cache.nixos.org'...\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.15.13, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre338578.a2e281f5770\"`\r\n - channels(dev): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n\r\n```console\r\n[user@system:~]$ sudo nixos-rebuild boot\r\nbuilding Nix...\r\nbuilding the system configuration...\r\nupdating systemd-boot from (249.7) to (249.5)\r\nSkipping \"/boot/EFI/systemd/systemd-bootaa64.efi\", since a newer boot loader version exists already.\r\nSkipping \"/boot/EFI/BOOT/BOOTAA64.EFI\", since a newer boot loader version exists already.\r\nTraceback (most recent call last):\r\n File \"/nix/store/s03ypdz6dwlgx97p74hqlx428rvwi6kn-systemd-boot\", line 314, in <module>\r\n main()\r\n File \"/nix/store/s03ypdz6dwlgx97p74hqlx428rvwi6kn-systemd-boot\", line 267, in main\r\n subprocess.check_call([\"/nix/store/f4sblwaj2d09kgr3k1imw3mq8cxq3gk9-systemd-249.5/bin/bootctl\", \"--path=/boot\", \"update\"])\r\n File \"/nix/store/aa9jdd3ijz3icvpahyl87z2dk0hlbw10-python3-3.9.6/lib/python3.9/subprocess.py\", line 373, in check_call\r\n raise CalledProcessError(retcode, cmd)\r\nsubprocess.CalledProcessError: Command '['/nix/store/f4sblwaj2d09kgr3k1imw3mq8cxq3gk9-systemd-249.5/bin/bootctl', '--path=/boot', 'update']' returned non-zero exit status 1.\r\nwarning: error(s) occurred while switching to the new configuration\r\ndev@devbox:~/x/my/prj/nix$ bootctl --path /boot status; echo $?\r\nFailed to read \"/boot/EFI/systemd\": Permission denied\r\nFailed to open \"/boot/loader/loader.conf\": Permission denied\r\nSystem:\r\n Firmware: UEFI 2.70 (EDK II 1.00)\r\n Secure Boot: disabled\r\n Setup Mode: user\r\n TPM2 Support: no\r\n Boot into FW: supported\r\n\r\nCurrent Boot Loader:\r\n Product: systemd-boot 249.7\r\n Features: ✓ Boot counting\r\n ✓ Menu timeout control\r\n ✓ One-shot menu timeout control\r\n ✓ Default entry control\r\n ✓ One-shot entry control\r\n ✓ Support for XBOOTLDR partition\r\n ✓ Support for passing random seed to OS\r\n ✓ Boot loader sets ESP information\r\n ESP: /dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753\r\n File: └─/EFI/systemd/systemd-bootaa64.efi\r\n\r\nRandom Seed:\r\n Passed to OS: no\r\n System Token: not set\r\n Exists: no\r\n\r\nAvailable Boot Loaders on ESP:\r\n ESP: /boot (/dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753)\r\n\r\nBoot Loaders Listed in EFI Variables:\r\n Title: Linux Boot Manager\r\n ID: 0x0004\r\n Status: active, boot-order\r\n Partition: /dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753\r\n File: └─/EFI/systemd/systemd-bootaa64.efi\r\n\r\nBoot Loader Entries:\r\n $BOOT: /boot (/dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753)\r\n\r\n1\r\n[user@system:~]$ bootctl status --no-variables\r\nFailed to read \"/boot/EFI/systemd\": Permission denied\r\nFailed to open \"/boot/loader/loader.conf\": Permission denied\r\nSystem:\r\n Firmware: UEFI 2.70 (EDK II 1.00)\r\n Secure Boot: disabled\r\n Setup Mode: user\r\n TPM2 Support: no\r\n Boot into FW: supported\r\n\r\nCurrent Boot Loader:\r\n Product: systemd-boot 249.7\r\n Features: ✓ Boot counting\r\n ✓ Menu timeout control\r\n ✓ One-shot menu timeout control\r\n ✓ Default entry control\r\n ✓ One-shot entry control\r\n ✓ Support for XBOOTLDR partition\r\n ✓ Support for passing random seed to OS\r\n ✓ Boot loader sets ESP information\r\n ESP: /dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753\r\n File: └─/EFI/systemd/systemd-bootaa64.efi\r\n\r\nRandom Seed:\r\n Passed to OS: no\r\n System Token: not set\r\n Exists: no\r\n\r\nAvailable Boot Loaders on ESP:\r\n ESP: /boot (/dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753)\r\n\r\nBoot Loaders Listed in EFI Variables:\r\n Title: Linux Boot Manager\r\n ID: 0x0004\r\n Status: active, boot-order\r\n Partition: /dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753\r\n File: └─/EFI/systemd/systemd-bootaa64.efi\r\n\r\nBoot Loader Entries:\r\n $BOOT: /boot (/dev/disk/by-partuuid/bdd476a4-8770-4e2f-8ec3-913e47fdf753)\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169693/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169677","id":1211741666,"node_id":"I_kwDOAEVQ_M5IObXi","number":169677,"title":"xrootd: xrdcp \"Could not load authentication handler\", libXrdSec-5.so isn't found","user":{"login":"ShamrockLee","id":44064051,"node_id":"MDQ6VXNlcjQ0MDY0MDUx","avatar_url":"https://avatars.githubusercontent.com/u/44064051?v=4","gravatar_id":"","url":"https://api.github.com/users/ShamrockLee","html_url":"https://github.com/ShamrockLee","followers_url":"https://api.github.com/users/ShamrockLee/followers","following_url":"https://api.github.com/users/ShamrockLee/following{/other_user}","gists_url":"https://api.github.com/users/ShamrockLee/gists{/gist_id}","starred_url":"https://api.github.com/users/ShamrockLee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ShamrockLee/subscriptions","organizations_url":"https://api.github.com/users/ShamrockLee/orgs","repos_url":"https://api.github.com/users/ShamrockLee/repos","events_url":"https://api.github.com/users/ShamrockLee/events{/privacy}","received_events_url":"https://api.github.com/users/ShamrockLee/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-22T02:31:19Z","updated_at":"2022-04-22T02:31:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nXRootD failed to access the files following the `root://` URL, complaining that `libXrdSec.so` isn't found and the authentication handler couldn't be loaded.\r\n\r\nHowever, `libXrdSec.so` does present in the output directory.\r\n\r\n```console\r\n$ nix shell .#xrootd --command xrdcp -v -d 3 root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root /dev/shm/\r\n...\r\n[2022-04-22 09:42:38.329696 +0800][Error ][XRootDTransport ] Unable to get the security framework: Plugin No such file or directory loading seclib libXrdSec-5.so\r\n...\r\nRun: [FATAL] Auth failed: Could not load authentication handler. (source)\r\n...\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enter the top directory of Nixpkgs\r\n2. `nix shell .#xrootd --command xrdcp root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR`\r\n3. See\r\n ```\r\n [0B/0B][100%][==================================================][0B/s]\r\n Run: [FATAL] Auth failed: Could not load authentication handler. (source)\r\n ```\r\n4. Run `nix shell .#xrootd --command xrdcp -v -d 3 root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR`\r\n5. See the detailed output\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nTerminal output during execution:\r\nShort:\r\n```\r\n$ nix shell .#xrootd --command xrdcp root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root /dev/shm/\r\n[0B/0B][100%][==================================================][0B/s]\r\nRun: [FATAL] Auth failed: Could not load authentication handler. (source)\r\n\r\n```\r\n\r\nLong:\r\n```console\r\n$ nix shell .#xrootd --command xrdcp -v -d 3 root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root /dev/shm/\r\n[2022-04-22 09:42:36.282010 +0800][Dump ][App ] Chunk size: 8388608, parallel chunks 4, streams: 1\r\n[2022-04-22 09:42:36.282048 +0800][Dump ][App ] Processing source entry: root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, type xroot, target file: file:///dev/shm/\r\n[2022-04-22 09:42:36.282083 +0800][Dump ][Utility ] Adding job with properties: 'checkSumMode' = 'none', 'checkSumPreset' = '', 'checkSumType' = '', 'chunkSize' = '8388608', 'coerce' = '0', 'continue' = '0', 'cpTimeout' = '0', 'delegate' = '0', 'dynamicSource' = '0', 'force' = '0', 'initTimeout' = '600', 'makeDir' = '0', 'parallelChunks' = '4', 'posc' = '0', 'preserveXAttr' = '0', 'rmOnBadCksum' = '0', 'source' = 'root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root', 'target' = 'file:///dev/shm/', 'targetIsDir' = '1', 'thirdParty' = 'none', 'tpcTimeout' = '1800', 'xcp' = '0', 'xcpBlockSize' = '134217728', 'xrate' = '0', 'xrateThreashold' = '0', 'zipAppend' = '0', 'zipArchive' = '0'\r\n[2022-04-22 09:42:36.282094 +0800][Debug ][Utility ] CopyProcess: 2 jobs to prepare\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282104 +0800][Dump ][Utility ] Path: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] URL: file:///dev/shm/\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] Protocol: file\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] Host Name: localhost\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282118 +0800][Dump ][Utility ] Path: /dev/shm\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282135 +0800][Dump ][Utility ] Path: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] URL: file://localhost/dev/shm/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] Protocol: file\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] Host Name: localhost\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282146 +0800][Dump ][Utility ] Path: /dev/shm/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282152 +0800][Debug ][Utility ] Creating a classic copy job, from root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root to file://localhost/dev/shm/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282159 +0800][Debug ][Utility ] Monitor library name not set. No monitoring\r\n[2022-04-22 09:42:36.282179 +0800][Debug ][Utility ] Env: trying to get a non-existent string entry: pollerpreference\r\n[2022-04-22 09:42:36.282184 +0800][Debug ][Poller ] Available pollers: built-in\r\n[2022-04-22 09:42:36.282186 +0800][Debug ][Poller ] Attempting to create a poller according to preference: built-in\r\n[2022-04-22 09:42:36.282188 +0800][Debug ][Poller ] Creating poller: built-in\r\n[2022-04-22 09:42:36.282191 +0800][Debug ][Poller ] Creating and starting the built-in poller...\r\n[2022-04-22 09:42:36.282312 +0800][Debug ][Poller ] Using 1 poller threads\r\n[2022-04-22 09:42:36.282323 +0800][Debug ][TaskMgr ] Starting the task manager...\r\n[2022-04-22 09:42:36.282356 +0800][Debug ][TaskMgr ] Task manager started\r\n[2022-04-22 09:42:36.282362 +0800][Debug ][JobMgr ] Starting the job manager...\r\n[2022-04-22 09:42:36.282400 +0800][Debug ][JobMgr ] Job manager started, 3 workers\r\n[2022-04-22 09:42:36.282405 +0800][Debug ][TaskMgr ] Registering task: \"FileTimer task\" to be run at: [2022-04-22 09:42:36 +0800]\r\n[2022-04-22 09:42:36.282409 +0800][Debug ][Utility ] Opening root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root for reading\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282421 +0800][Dump ][Utility ] Path: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282435 +0800][Dump ][Utility ] Path: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282445 +0800][Dump ][Utility ] Path: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root\r\n[2022-04-22 09:42:36.282461 +0800][Debug ][File ] [0xd3cf10@root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root?xrdcl.requuid=486fcf91-14cc-4617-85cb-cf284e63621f] Sending an open command\r\n[2022-04-22 09:42:36.282470 +0800][Dump ][XRootD ] [eospublic.cern.ch:1094] Sending message kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat )\r\n[2022-04-22 09:42:36.282480 +0800][Debug ][ExDbgMsg ] [eospublic.cern.ch:1094] MsgHandler created: 0xd424f0 (message: kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ) ).\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] URL: eospublic.cern.ch:1094\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282494 +0800][Dump ][Utility ] Path:\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] URL: root://eospublic.cern.ch:1094\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] Protocol: root\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] User Name:\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] Password:\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] Host Name: eospublic.cern.ch\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] Port: 1094\r\n[2022-04-22 09:42:36.282503 +0800][Dump ][Utility ] Path:\r\n[2022-04-22 09:42:36.282511 +0800][Debug ][PostMaster ] Creating new channel to: root://eospublic.cern.ch:1094\r\n[2022-04-22 09:42:36.282520 +0800][Debug ][PostMaster ] [eospublic.cern.ch:1094] Stream parameters: Network Stack: IPAuto, Connection Window: 120, ConnectionRetry: 5, Stream Error Window: 1800\r\n[2022-04-22 09:42:36.282527 +0800][Debug ][TaskMgr ] Registering task: \"TickGeneratorTask for: root://eospublic.cern.ch:1094\" to be run at: [2022-04-22 09:42:51 +0800]\r\n[2022-04-22 09:42:36.282534 +0800][Dump ][PostMaster ] [eospublic.cern.ch:1094] Sending message kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ) (0xd3d600) through substream 0 expecting answer at 0\r\n[2022-04-22 09:42:37.282505 +0800][Dump ][TaskMgr ] Running task: \"FileTimer task\"\r\n[2022-04-22 09:42:37.282539 +0800][Dump ][TaskMgr ] Will rerun task \"FileTimer task\" at [2022-04-22 09:42:52 +0800]\r\n[2022-04-22 09:42:37.305170 +0800][Debug ][PostMaster ] [eospublic.cern.ch:1094] Found 2 address(es): [::ffff:128.142.160.145]:1094, [2001:1458:301:17::100:e]:1094\r\n[2022-04-22 09:42:37.305205 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Attempting connection to [2001:1458:301:17::100:e]:1094\r\n[2022-04-22 09:42:37.305237 +0800][Debug ][Poller ] Adding socket 0xd3dbd0 to the poller\r\n[2022-04-22 09:42:37.614083 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Async connection call returned\r\n[2022-04-22 09:42:37.614196 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending out the initial hand shake + kXR_protocol\r\n[2022-04-22 09:42:37.614263 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Wrote a message: (0xec001430), 44 bytes\r\n[2022-04-22 09:42:37.919823 +0800][Dump ][XRootDTransport ] [msg: 0xec001690] Expecting 8 bytes of message body\r\n[2022-04-22 09:42:37.919898 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:37.919916 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 16 bytes\r\n[2022-04-22 09:42:37.919933 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Got the server hand shake response (type: manager [], protocol version 400)\r\n[2022-04-22 09:42:37.919962 +0800][Dump ][XRootDTransport ] [msg: 0xec001690] Expecting 8 bytes of message body\r\n[2022-04-22 09:42:37.919978 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:37.919993 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 16 bytes\r\n[2022-04-22 09:42:37.920015 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] kXR_protocol successful (type: manager [], protocol version 400)\r\n[2022-04-22 09:42:37.920386 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending out kXR_login request, username: shamrock, cgi: ?xrd.cc=us&xrd.tz=8&xrd.appname=xrdcp&xrd.info=&xrd.hostname=nixos-202104&xrd.rn=unknown, dual-stack: true, private IPv4: true, private IPv6: true\r\n[2022-04-22 09:42:37.920454 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Wrote a message: (0xec001840), 112 bytes\r\n[2022-04-22 09:42:38.329306 +0800][Dump ][XRootDTransport ] [msg: 0xec001430] Expecting 135 bytes of message body\r\n[2022-04-22 09:42:38.329376 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:38.329398 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 143 bytes\r\n[2022-04-22 09:42:38.329420 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Logged in, session: 58bd960721730000220f000064759707\r\n[2022-04-22 09:42:38.329435 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Authentication is required: &P=krb5,xrootd/eospublic.cern.ch@CERN.CH&P=gsi,v:10400,c:ssl,ca:5168735f.0|4339b4bc.0&P=sss,0.13:/etc/eos.keytab&P=unix\r\n[2022-04-22 09:42:38.329452 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending authentication data\r\n[2022-04-22 09:42:38.329696 +0800][Error ][XRootDTransport ] Unable to get the security framework: Plugin No such file or directory loading seclib libXrdSec-5.so\r\n[2022-04-22 09:42:38.332027 +0800][Error ][AsyncSock ] [eospublic.cern.ch:1094.0] Socket error while handshaking: [FATAL] Auth failed\r\n[2022-04-22 09:42:38.332054 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Closing the socket\r\n[2022-04-22 09:42:38.332069 +0800][Debug ][Poller ] <[2401:e180:8861:273:d771:cbef:4aba:163e]:49708><--><[2001:1458:301:17::100:e]:1094> Removing socket from the poller\r\n[2022-04-22 09:42:38.332158 +0800][Error ][PostMaster ] [eospublic.cern.ch:1094] elapsed = 1, pConnectionWindow = 120 seconds.\r\n[2022-04-22 09:42:38.332223 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Attempting connection to [::ffff:128.142.160.145]:1094\r\n[2022-04-22 09:42:38.332309 +0800][Debug ][Poller ] Adding socket 0xd3dbd0 to the poller\r\n[2022-04-22 09:42:38.665893 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Async connection call returned\r\n[2022-04-22 09:42:38.665998 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending out the initial hand shake + kXR_protocol\r\n[2022-04-22 09:42:38.666094 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Wrote a message: (0xd44180), 44 bytes\r\n[2022-04-22 09:42:39.046270 +0800][Dump ][XRootDTransport ] [msg: 0xec001430] Expecting 8 bytes of message body\r\n[2022-04-22 09:42:39.046344 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:39.046361 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 16 bytes\r\n[2022-04-22 09:42:39.046377 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Got the server hand shake response (type: manager [], protocol version 400)\r\n[2022-04-22 09:42:39.046405 +0800][Dump ][XRootDTransport ] [msg: 0xec001430] Expecting 8 bytes of message body\r\n[2022-04-22 09:42:39.046419 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:39.046432 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 16 bytes\r\n[2022-04-22 09:42:39.046452 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] kXR_protocol successful (type: manager [], protocol version 400)\r\n[2022-04-22 09:42:39.046852 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending out kXR_login request, username: shamrock, cgi: ?xrd.cc=us&xrd.tz=8&xrd.appname=xrdcp&xrd.info=&xrd.hostname=nixos-202104&xrd.rn=unknown, dual-stack: true, private IPv4: true, private IPv6: true\r\n[2022-04-22 09:42:39.046931 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Wrote a message: (0xec001690), 112 bytes\r\n[2022-04-22 09:42:39.455691 +0800][Dump ][XRootDTransport ] [msg: 0xd44180] Expecting 135 bytes of message body\r\n[2022-04-22 09:42:39.455785 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received message header, size: 8\r\n[2022-04-22 09:42:39.455811 +0800][Dump ][AsyncSock ] [eospublic.cern.ch:1094.0] Received a message of 143 bytes\r\n[2022-04-22 09:42:39.455842 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Logged in, session: 72bd9607217300007a0d000080759707\r\n[2022-04-22 09:42:39.455858 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Authentication is required: &P=krb5,xrootd/eospublic.cern.ch@CERN.CH&P=gsi,v:10400,c:ssl,ca:5168735f.0|4339b4bc.0&P=sss,0.13:/etc/eos.keytab&P=unix\r\n[2022-04-22 09:42:39.455872 +0800][Debug ][XRootDTransport ] [eospublic.cern.ch:1094.0] Sending authentication data\r\n[2022-04-22 09:42:39.455998 +0800][Error ][XRootDTransport ] Unable to get the security framework: Plugin No such file or directory loading seclib libXrdSec-5.so\r\n[2022-04-22 09:42:39.456046 +0800][Error ][AsyncSock ] [eospublic.cern.ch:1094.0] Socket error while handshaking: [FATAL] Auth failed\r\n[2022-04-22 09:42:39.456067 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Closing the socket\r\n[2022-04-22 09:42:39.456092 +0800][Debug ][Poller ] <[::ffff:192.168.190.108]:51900><--><[::ffff:128.142.160.145]:1094> Removing socket from the poller\r\n[2022-04-22 09:42:39.456204 +0800][Error ][PostMaster ] [eospublic.cern.ch:1094] elapsed = 1, pConnectionWindow = 120 seconds.\r\n[2022-04-22 09:42:39.456242 +0800][Error ][PostMaster ] [eospublic.cern.ch:1094] Unable to recover: [FATAL] Auth failed.\r\n[2022-04-22 09:42:39.456288 +0800][Error ][XRootD ] [eospublic.cern.ch:1094] Impossible to send message kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ). Trying to recover.\r\n[2022-04-22 09:42:39.456323 +0800][Debug ][XRootD ] [eospublic.cern.ch:1094] Handling error while processing kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ): [FATAL] Auth failed.\r\n[2022-04-22 09:42:39.456353 +0800][Debug ][ExDbgMsg ] [eospublic.cern.ch:1094] Passing to the thread-pool MsgHandler: 0xd424f0 (message: kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ) ).\r\n[2022-04-22 09:42:39.456521 +0800][Debug ][ExDbgMsg ] [eospublic.cern.ch:1094] Calling MsgHandler: 0xd424f0 (message: kXR_open (file: /eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root, mode: 00, flags: kXR_open_read kXR_async kXR_retstat ) ) with status: [FATAL] Auth failed.\r\n[2022-04-22 09:42:39.456638 +0800][Debug ][File ] [0xd3cf10@root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root?xrdcl.requuid=486fcf91-14cc-4617-85cb-cf284e63621f] Open has returned with status [FATAL] Auth failed: Could not load authentication handler.\r\n[2022-04-22 09:42:39.456677 +0800][Debug ][File ] [0xd3cf10@root://eospublic.cern.ch:1094//eos/opendata/cms/MonteCarloCASTOR/MinBias_TuneZ2_7TeV_pythia6_cff_py_GEN_SIM_START311_V2_Dec11_v2/MinBias_TuneZ2_7TeV_pythia6_cff_py_Step3_START42_V11_Dec11_v2/86bcdbe9c73956c342e477ba771c41c7/STEP2_RAW2DIGI_L1Reco_RECO_7TeV_10_1_s8p.root?xrdcl.requuid=486fcf91-14cc-4617-85cb-cf284e63621f] Error while opening at eospublic.cern.ch:1094: [FATAL] Auth failed: Could not load authentication handler.\r\n[2022-04-22 09:42:39.456711 +0800][Debug ][ExDbgMsg ] [eospublic.cern.ch:1094] Destroying MsgHandler: 0xd424f0.\r\n[0B/0B][100%][==================================================][0B/s]\r\nRun: [FATAL] Auth failed: Could not load authentication handler. (source)\r\n[2022-04-22 09:42:39.457436 +0800][Debug ][JobMgr ] Stopping the job manager...\r\n[2022-04-22 09:42:39.457472 +0800][Dump ][JobMgr ] Stopping worker #0...\r\n[2022-04-22 09:42:39.457763 +0800][Dump ][JobMgr ] Worker #0 stopped\r\n[2022-04-22 09:42:39.457817 +0800][Dump ][JobMgr ] Stopping worker #1...\r\n[2022-04-22 09:42:39.458029 +0800][Dump ][JobMgr ] Worker #1 stopped\r\n[2022-04-22 09:42:39.458084 +0800][Dump ][JobMgr ] Stopping worker #2...\r\n[2022-04-22 09:42:39.458276 +0800][Dump ][JobMgr ] Worker #2 stopped\r\n[2022-04-22 09:42:39.458329 +0800][Debug ][JobMgr ] Job manager stopped\r\n[2022-04-22 09:42:39.458344 +0800][Debug ][TaskMgr ] Stopping the task manager...\r\n[2022-04-22 09:42:39.458679 +0800][Debug ][TaskMgr ] Task manager stopped\r\n[2022-04-22 09:42:39.458753 +0800][Debug ][Poller ] Stopping the poller...\r\n[2022-04-22 09:42:39.458936 +0800][Debug ][TaskMgr ] Requesting unregistration of: \"TickGeneratorTask for: root://eospublic.cern.ch:1094\"\r\n[2022-04-22 09:42:39.459006 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Closing the socket\r\n[2022-04-22 09:42:39.459024 +0800][Debug ][PostMaster ] [eospublic.cern.ch:1094] Destroying stream\r\n[2022-04-22 09:42:39.459036 +0800][Debug ][AsyncSock ] [eospublic.cern.ch:1094.0] Closing the socket\r\n\r\n```\r\n\r\n### Notify maintainers\r\n\r\n`xrootd` is packaged by myself, but I haven't found the solution. Suggestions and helps are more than welcom.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - nixpkgs: `/nix/store/9dmig1pv9njj5kswvs8yvw3qp6b81zkd-source`\r\n\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169677/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169674","id":1211737075,"node_id":"I_kwDOAEVQ_M5IOaPz","number":169674,"title":"Add Japanese Takao fonts","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-22T02:23:03Z","updated_at":"2022-04-22T02:23:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAdd Japanese Takao Gothic, Mincho, P Gothic, and P Mincho fonts.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://launchpad.net/takao-fonts\r\n* source URL: http://deb.debian.org/debian/pool/main/f/fonts-takao/fonts-takao_00303.01.orig.tar.gz\r\n* license: ipa\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169674/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169667","id":1211711900,"node_id":"I_kwDOAEVQ_M5IOUGc","number":169667,"title":"Add Tibetan Machine OpenType font","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-22T01:31:19Z","updated_at":"2022-04-22T01:31:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAdd Tibetan Machine OpenType font for Tibetan, Dzongkha, and Ladakhi languages.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://collab.its.virginia.edu/wiki/tibetan-script/Tibetan%20Machine%20Uni.html\r\n* source URL: mirror://debian/pool/main/f/fonts-tibetan-machine/fonts-tibetan-machine_1.901b.orig.tar.bz2\r\n* license: gpl2+\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169667/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169652","id":1211655943,"node_id":"I_kwDOAEVQ_M5IOGcH","number":169652,"title":"Add Khmeros TrueType font for Khmer language","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-21T23:47:00Z","updated_at":"2022-04-21T23:47:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAdd Khmeros TrueType font for Khmer language. Also, see\r\n\r\n- https://github.com/NixOS/nixpkgs/issues/167130\r\n- https://github.com/NixOS/nixpkgs/issues/166735\r\n\r\nAll issues have attached PRs.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://khmeros.info/\r\n* source URL: mirror://debian/pool/main/f/fonts-khmeros/fonts-khmeros_5.0.orig.tar.xz\r\n* license: gpl2+\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169652/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169644","id":1211621174,"node_id":"I_kwDOAEVQ_M5IN982","number":169644,"title":"rabbitmq-java-client: out of date","user":{"login":"armeenm","id":29145250,"node_id":"MDQ6VXNlcjI5MTQ1MjUw","avatar_url":"https://avatars.githubusercontent.com/u/29145250?v=4","gravatar_id":"","url":"https://api.github.com/users/armeenm","html_url":"https://github.com/armeenm","followers_url":"https://api.github.com/users/armeenm/followers","following_url":"https://api.github.com/users/armeenm/following{/other_user}","gists_url":"https://api.github.com/users/armeenm/gists{/gist_id}","starred_url":"https://api.github.com/users/armeenm/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armeenm/subscriptions","organizations_url":"https://api.github.com/users/armeenm/orgs","repos_url":"https://api.github.com/users/armeenm/repos","events_url":"https://api.github.com/users/armeenm/events{/privacy}","received_events_url":"https://api.github.com/users/armeenm/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-21T22:41:02Z","updated_at":"2022-04-23T17:23:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Lives [here](https://github.com/rabbitmq/rabbitmq-java-client) now. Out of date and depends on python2. Last touched [July 2014](https://github.com/NixOS/nixpkgs/commit/30431e71608576baf880567b2894ad2a542f8d5e).\r\n\r\n###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 3.3.4\r\ndesired version: 5.14.2\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: NONE!\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169644/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169634","id":1211546975,"node_id":"I_kwDOAEVQ_M5INr1f","number":169634,"title":"Android: SDK Tools is deprecated. Switch to cmdline-tools instead","user":{"login":"kjeremy","id":4325700,"node_id":"MDQ6VXNlcjQzMjU3MDA=","avatar_url":"https://avatars.githubusercontent.com/u/4325700?v=4","gravatar_id":"","url":"https://api.github.com/users/kjeremy","html_url":"https://github.com/kjeremy","followers_url":"https://api.github.com/users/kjeremy/followers","following_url":"https://api.github.com/users/kjeremy/following{/other_user}","gists_url":"https://api.github.com/users/kjeremy/gists{/gist_id}","starred_url":"https://api.github.com/users/kjeremy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kjeremy/subscriptions","organizations_url":"https://api.github.com/users/kjeremy/orgs","repos_url":"https://api.github.com/users/kjeremy/repos","events_url":"https://api.github.com/users/kjeremy/events{/privacy}","received_events_url":"https://api.github.com/users/kjeremy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-21T20:59:43Z","updated_at":"2022-04-22T02:54:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Android SDK Tools have been deprecated for a while: https://developer.android.com/studio/releases/sdk-tools\r\n\r\n`androidEnv.composeAndroidPackages` should migrate to using the `cmdline-tools` package for the latest in Android development. This should also fix `flutter doctor` not finding the Android tools.\r\n\r\n@miallo\r\n@SuperSandro2000\r\n@numinit","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169634/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169633","id":1211535140,"node_id":"I_kwDOAEVQ_M5INo8k","number":169633,"title":"openjdk: Java vulnerable to CVE-2022-21449; Patch available","user":{"login":"gregod","id":4532398,"node_id":"MDQ6VXNlcjQ1MzIzOTg=","avatar_url":"https://avatars.githubusercontent.com/u/4532398?v=4","gravatar_id":"","url":"https://api.github.com/users/gregod","html_url":"https://github.com/gregod","followers_url":"https://api.github.com/users/gregod/followers","following_url":"https://api.github.com/users/gregod/following{/other_user}","gists_url":"https://api.github.com/users/gregod/gists{/gist_id}","starred_url":"https://api.github.com/users/gregod/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/gregod/subscriptions","organizations_url":"https://api.github.com/users/gregod/orgs","repos_url":"https://api.github.com/users/gregod/repos","events_url":"https://api.github.com/users/gregod/events{/privacy}","received_events_url":"https://api.github.com/users/gregod/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-21T20:45:48Z","updated_at":"2022-04-25T11:39:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nThe openjdk / jdk versions from version 15 onward are vulnerable to high severity [CVE-2022-21449](https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21449)\r\n\r\nI have verified that this is the case for the versions included in nixpkgs using the following POC using openjdk 17.\r\n\r\n```\r\nimport java.security.*;\r\nclass POC { \r\n public static void main(String args[]) throws Exception { \r\n KeyPair keyPair = KeyPairGenerator.getInstance(\"EC\").generateKeyPair();\r\n byte[] blankSignature = new byte[64];\r\n Signature sig = Signature.getInstance(\"SHA256WithECDSAInP1363Format\");\r\n sig.initVerify(keyPair.getPublic());\r\n sig.update(\"Hello, world!\".getBytes());\r\n boolean validSig = sig.verify(blankSignature);\r\n if (validSig) {\r\n System.out.println(\"Vulnerable to CVE-2022-21449: Blank signature accepted\"); \r\n } else {\r\n System.out.println(\"Not vulnerable\"); \r\n }\r\n } \r\n} \r\n// adapted from https://connect2id.com/blog/cve-2022-21449\r\n```\r\n\r\n\r\n## Suggested Solutions\r\n\r\nVersions containing a fix have been released (for jdk17 in 17.0.3, nixpkgs master is at 17.0.1 )\r\n\r\nAlternatively, the necessary patch (https://github.com/openjdk/jdk/commit/e2f8ce9c3ff4518e070960bafa70ba780746aa5c), is very small and could be backported via fetchpatch to all versions >15. \r\n\r\n## Notify maintainers\r\n@edwtjo \r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169633/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169627","id":1211470404,"node_id":"I_kwDOAEVQ_M5INZJE","number":169627,"title":"composeAndroidPackages does not allow the user to specify the cmdline-tools package","user":{"login":"kjeremy","id":4325700,"node_id":"MDQ6VXNlcjQzMjU3MDA=","avatar_url":"https://avatars.githubusercontent.com/u/4325700?v=4","gravatar_id":"","url":"https://api.github.com/users/kjeremy","html_url":"https://github.com/kjeremy","followers_url":"https://api.github.com/users/kjeremy/followers","following_url":"https://api.github.com/users/kjeremy/following{/other_user}","gists_url":"https://api.github.com/users/kjeremy/gists{/gist_id}","starred_url":"https://api.github.com/users/kjeremy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kjeremy/subscriptions","organizations_url":"https://api.github.com/users/kjeremy/orgs","repos_url":"https://api.github.com/users/kjeremy/repos","events_url":"https://api.github.com/users/kjeremy/events{/privacy}","received_events_url":"https://api.github.com/users/kjeremy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-21T19:34:30Z","updated_at":"2022-04-25T01:53:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`pkgs.androidenv.composeandroidPackages` does not allow us to specify `cmdline-tools` in `includeExtras` or anywhere else that I can find. `flutter doctor` complains that it cannot find the cmdline-tools.\r\n\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@miallo \r\n@SuperSandro2000 \r\n@numinit \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"nixos\"`\r\n - channels(jkolb): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169627/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169602","id":1211232218,"node_id":"I_kwDOAEVQ_M5IMe_a","number":169602,"title":"Issues with Markdown.pl (perlPackage.TextMarkdown)","user":{"login":"WolfangAukang","id":8378365,"node_id":"MDQ6VXNlcjgzNzgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/8378365?v=4","gravatar_id":"","url":"https://api.github.com/users/WolfangAukang","html_url":"https://github.com/WolfangAukang","followers_url":"https://api.github.com/users/WolfangAukang/followers","following_url":"https://api.github.com/users/WolfangAukang/following{/other_user}","gists_url":"https://api.github.com/users/WolfangAukang/gists{/gist_id}","starred_url":"https://api.github.com/users/WolfangAukang/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/WolfangAukang/subscriptions","organizations_url":"https://api.github.com/users/WolfangAukang/orgs","repos_url":"https://api.github.com/users/WolfangAukang/repos","events_url":"https://api.github.com/users/WolfangAukang/events{/privacy}","received_events_url":"https://api.github.com/users/WolfangAukang/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-21T15:51:28Z","updated_at":"2022-04-21T22:19:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nNeed to use the `Markdown.pl` from `perlPackage.TextMarkdown` for a program I'm building, but when using it, I'm getting an error message on it. Not sure if I'm using it the correct way or not.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `nix-build -A perlPackage.TextMarkdown`\r\n2. Run `./result/bin/Markdown.pl test.md > test.html`\r\n\r\n### Expected behavior\r\nNo output on the console\r\n\r\n### Screenshots\r\n```\r\n·> ./result/bin/Markdown.pl\r\n/nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/env: ‘perl -I/nix/store/xvacdngzsxn6hwnymncs8iv752aal4j0-perl-5.34.1/lib/perl5/site_perl -I/nix/store/l71nrkaw7w7na5k8fryg9mr09x01qviz-perl5.34.1-List-MoreUtils-0.430/lib/perl5/site_perl -I/nix’: No such file or directory\r\n/nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/env: use -[v]S to pass options in shebang lines\r\n·> echo $?\r\n127\r\n```\r\n\r\n### Additional context\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\n·> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"nixos-21.11.334247.573095944e7\"`\r\n - channels(bjorn): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169602/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169593","id":1211162242,"node_id":"I_kwDOAEVQ_M5IMN6C","number":169593,"title":"Unable to start Waydroid session (loop mountpoint busy)","user":{"login":"PAI5REECHO","id":96688573,"node_id":"U_kgDOBcNZvQ","avatar_url":"https://avatars.githubusercontent.com/u/96688573?v=4","gravatar_id":"","url":"https://api.github.com/users/PAI5REECHO","html_url":"https://github.com/PAI5REECHO","followers_url":"https://api.github.com/users/PAI5REECHO/followers","following_url":"https://api.github.com/users/PAI5REECHO/following{/other_user}","gists_url":"https://api.github.com/users/PAI5REECHO/gists{/gist_id}","starred_url":"https://api.github.com/users/PAI5REECHO/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PAI5REECHO/subscriptions","organizations_url":"https://api.github.com/users/PAI5REECHO/orgs","repos_url":"https://api.github.com/users/PAI5REECHO/repos","events_url":"https://api.github.com/users/PAI5REECHO/events{/privacy}","received_events_url":"https://api.github.com/users/PAI5REECHO/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-21T14:56:34Z","updated_at":"2022-04-22T06:50:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'm unable to start a Waydroid session because of a mount command error\r\n\r\n### Steps To Reproduce\r\n[Per the instructions on how to manually start waydroid](https://docs.waydro.id/usage/install-on-desktops#manually-starting-waydroid=):\r\n1. `sudo waydroid init`\r\n2. `sudo systemctl restart waydroid-container`\r\n3. `sudo waydroid container start`\r\n4. `waydroid session start` (`WARNING: Service manager /dev/binder has died`)\r\n\r\nMy `/var/lib/waydroid/waydroid.log` log file content is:\r\n```\r\n(875887) [10:45:58] % tail -n 60 -F /var/lib/waydroid/waydroid.log\r\n(875887) [10:45:58] *** output passed to waydroid stdout, not to this log ***\r\n(875903) [10:46:01] % chmod 666 -R /dev/binder\r\n(875903) [10:46:01] % chmod 666 -R /dev/vndbinder\r\n(875903) [10:46:01] % chmod 666 -R /dev/hwbinder\r\n(875903) [10:46:01] Container manager is waiting for session to load\r\n(875956) [10:46:07] % chmod 666 -R /dev/binder\r\n(875956) [10:46:07] % chmod 666 -R /dev/vndbinder\r\n(875956) [10:46:07] % chmod 666 -R /dev/hwbinder\r\n(875956) [10:46:07] Container manager is waiting for session to load\r\n(875967) [10:46:08] Save session config: /var/lib/waydroid/session.cfg\r\n(875967) [10:46:08] UserMonitor service is not even started\r\n(875967) [10:46:08] Clipboard service is not even started\r\n(875956) [10:46:09] % /nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/data/scripts/waydroid-net.sh start\r\n(875956) [10:46:09] % mount /var/lib/waydroid/images/system.img /var/lib/waydroid/rootfs\r\n(875956) [10:46:09] % mount -o remount,ro /var/lib/waydroid/images/system.img /var/lib/waydroid/rootfs\r\n(875956) [10:46:09] % mount /var/lib/waydroid/images/vendor.img /var/lib/waydroid/rootfs/vendor\r\n(875956) [10:46:09] % mount -o remount,ro /var/lib/waydroid/images/vendor.img /var/lib/waydroid/rootfs/vendor\r\n(875956) [10:46:09] % mount -o bind /var/lib/waydroid/waydroid.prop /var/lib/waydroid/rootfs/vendor/waydroid.prop\r\n(875956) [10:46:09] % mount -o bind /home/me/.local/share/waydroid/data /var/lib/waydroid/data\r\n(875956) [10:46:09] % umount -l /sys/fs/cgroup/schedtune\r\numount: /sys/fs/cgroup/schedtune: no mount point specified.\r\n(875956) [10:46:09] % chmod 777 -R /dev/ashmem\r\n(875956) [10:46:09] % chmod 777 -R /dev/dri\r\n(875956) [10:46:09] % chmod 777 -R /dev/fb0\r\n(875956) [10:46:09] % chmod 777 -R /dev/video0\r\n(875956) [10:46:09] % lxc-start -P /var/lib/waydroid/lxc -F -n waydroid -- /init\r\n(875956) [10:46:09] New background process: pid=876019, output=background\r\n(875956) [10:46:09] Save session config: /var/lib/waydroid/session.cfg\r\n(875903) [10:46:09] % /nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/data/scripts/waydroid-net.sh start\r\nwaydroid-net is already running\r\n(875903) [10:46:09] % umount /var/lib/waydroid/rootfs/vendor/waydroid.prop\r\n(875903) [10:46:09] % umount /var/lib/waydroid/rootfs/vendor\r\n(875903) [10:46:09] % umount /var/lib/waydroid/rootfs\r\n(875903) [10:46:09] % mount /var/lib/waydroid/images/system.img /var/lib/waydroid/rootfs\r\nmount: /var/lib/waydroid/rootfs: /dev/loop0 already mounted or mount point busy.\r\n(875903) [10:46:09] ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^\r\n(875903) [10:46:09] NOTE: The failed command's output is above the ^^^ line in the log file: /var/lib/waydroid/waydroid.log\r\n(875903) [10:46:09] ERROR: Command failed: % mount /var/lib/waydroid/images/system.img /var/lib/waydroid/rootfs\r\n(875903) [10:46:09] See also: <https://github.com/waydroid>\r\n(875903) [10:46:09] Traceback (most recent call last):\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/__init__.py\", line 69, in main\r\n actions.container_manager.start(args)\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/actions/container_manager.py\", line 132, in start\r\n helpers.images.mount_rootfs(args, cfg[\"waydroid\"][\"images_path\"])\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/helpers/images.py\", line 90, in mount_rootfs\r\n helpers.mount.mount(args, images_dir + \"/system.img\",\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/helpers/mount.py\", line 131, in mount\r\n tools.helpers.run.user(args, [\"mount\", source, destination])\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/helpers/run.py\", line 58, in user\r\n return tools.helpers.run_core.core(args, msg, cmd, working_dir, output,\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/helpers/run_core.py\", line 343, in core\r\n check_return_code(args, code, log_message)\r\n File \"/nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/tools/helpers/run_core.py\", line 219, in check_return_code\r\n raise RuntimeError(\"Command failed: \" + log_message)\r\nRuntimeError: Command failed: % mount /var/lib/waydroid/images/system.img /var/lib/waydroid/rootfs\r\n\r\n(876087) [10:46:09] UserMonitor service is not even started\r\n(876087) [10:46:09] Clipboard service is not even started\r\n(875956) [10:46:10] session manager stopped, stopping container and waiting...\r\n(875956) [10:46:10] % lxc-stop -P /var/lib/waydroid/lxc -n waydroid -k\r\nlxc-start: waydroid: conf.c: run_buffer: 321 Script exited with status 126\r\nlxc-start: waydroid: start.c: lxc_end: 988 Failed to run lxc.hook.post-stop for container \"waydroid\"\r\n(875956) [10:46:10] % /nix/store/ygl038g51jp8qh2jgmff7dw5g0hvgnd6-waydroid-1.2.0/lib/python3.9/site-packages/data/scripts/waydroid-net.sh stop\r\n(875956) [10:46:10] % umount /var/lib/waydroid/data\r\n(875956) [10:46:10] % chmod 666 -R /dev/binder\r\n(875956) [10:46:10] % chmod 666 -R /dev/vndbinder\r\n(875956) [10:46:10] % chmod 666 -R /dev/hwbinder\r\n(875956) [10:46:10] Container manager is waiting for session to load\r\n```\r\n\r\n### Expected behavior\r\nShould be able to start Waydroid session so I begin using the UI\r\n\r\n### Additional context\r\nhttps://github.com/waydroid/waydroid/issues/99 may be related\r\n\r\n### Notify maintainers\r\n@mcaju\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.9.0pre20220420_9345b4e`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169593/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169572","id":1210905543,"node_id":"I_kwDOAEVQ_M5ILPPH","number":169572,"title":"Howdy: pam Face auth","user":{"login":"peterromfeldhk","id":5515707,"node_id":"MDQ6VXNlcjU1MTU3MDc=","avatar_url":"https://avatars.githubusercontent.com/u/5515707?v=4","gravatar_id":"","url":"https://api.github.com/users/peterromfeldhk","html_url":"https://github.com/peterromfeldhk","followers_url":"https://api.github.com/users/peterromfeldhk/followers","following_url":"https://api.github.com/users/peterromfeldhk/following{/other_user}","gists_url":"https://api.github.com/users/peterromfeldhk/gists{/gist_id}","starred_url":"https://api.github.com/users/peterromfeldhk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterromfeldhk/subscriptions","organizations_url":"https://api.github.com/users/peterromfeldhk/orgs","repos_url":"https://api.github.com/users/peterromfeldhk/repos","events_url":"https://api.github.com/users/peterromfeldhk/events{/privacy}","received_events_url":"https://api.github.com/users/peterromfeldhk/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-21T11:33:21Z","updated_at":"2022-04-21T11:33:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nWindows Hello™ style authentication for Linux.\r\nFace ID pam\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/boltgolt/howdy\r\n* source URL: https://github.com/boltgolt/howdy\r\n* license: mit\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169572/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169570","id":1210846738,"node_id":"I_kwDOAEVQ_M5ILA4S","number":169570,"title":"How to maintain helper script documentation?","user":{"login":"fricklerhandwerk","id":6599296,"node_id":"MDQ6VXNlcjY1OTkyOTY=","avatar_url":"https://avatars.githubusercontent.com/u/6599296?v=4","gravatar_id":"","url":"https://api.github.com/users/fricklerhandwerk","html_url":"https://github.com/fricklerhandwerk","followers_url":"https://api.github.com/users/fricklerhandwerk/followers","following_url":"https://api.github.com/users/fricklerhandwerk/following{/other_user}","gists_url":"https://api.github.com/users/fricklerhandwerk/gists{/gist_id}","starred_url":"https://api.github.com/users/fricklerhandwerk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fricklerhandwerk/subscriptions","organizations_url":"https://api.github.com/users/fricklerhandwerk/orgs","repos_url":"https://api.github.com/users/fricklerhandwerk/repos","events_url":"https://api.github.com/users/fricklerhandwerk/events{/privacy}","received_events_url":"https://api.github.com/users/fricklerhandwerk/received_events","type":"User","site_admin":false},"labels":[{"id":1540529485,"node_id":"MDU6TGFiZWwxNTQwNTI5NDg1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20documentation%20source","name":"6.topic: documentation source","color":"fef2c0","default":false,"description":"Meta-discussion about documentation and its workflow"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-21T10:40:35Z","updated_at":"2022-04-23T17:25:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nImproving documentation should be easy. But changing comments in core dependencies such as `patch-shebangs.sh` causes [mass rebuilds](https://github.com/NixOS/nixpkgs/pull/121015#discussion_r854986018). That way it is not practical to maintain the manual and keep it in sync with the scripts it is documenting.\r\n\r\n### Expected behavior\r\nDesirable properties:\r\n- script documentation visible in the manual\r\n- script documentation available in place\r\n- single source of truth\r\n\r\nCompromises:\r\n- provide means of bidirectional navigation\r\n #121015 already adds links to the source. How would one reference a manual section from a shell script comment? Links may break, section names may change and would have to be found manually.\r\n- maintain double book keeping\r\n This may work for a while, but requires creation and strict observation of contributing guidelines not to lose track, and does not scale.\r\n - add mechanism to extract script documentation into the manuals\r\n This satisfies all requirements, but adds significant complexity and yet more code to maintain.\r\n\r\n@roberth you brought this up https://github.com/NixOS/nixpkgs/issues/129741#issuecomment-1011217958 https://github.com/NixOS/nixpkgs/pull/121015#discussion_r854986018\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169570/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169559","id":1210725095,"node_id":"I_kwDOAEVQ_M5IKjLn","number":169559,"title":"python3.pkgs.gplearn (Genetic Programming in Python): package","user":{"login":"EvilMav","id":6803717,"node_id":"MDQ6VXNlcjY4MDM3MTc=","avatar_url":"https://avatars.githubusercontent.com/u/6803717?v=4","gravatar_id":"","url":"https://api.github.com/users/EvilMav","html_url":"https://github.com/EvilMav","followers_url":"https://api.github.com/users/EvilMav/followers","following_url":"https://api.github.com/users/EvilMav/following{/other_user}","gists_url":"https://api.github.com/users/EvilMav/gists{/gist_id}","starred_url":"https://api.github.com/users/EvilMav/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/EvilMav/subscriptions","organizations_url":"https://api.github.com/users/EvilMav/orgs","repos_url":"https://api.github.com/users/EvilMav/repos","events_url":"https://api.github.com/users/EvilMav/events{/privacy}","received_events_url":"https://api.github.com/users/EvilMav/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-21T08:56:06Z","updated_at":"2022-04-23T17:26:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nProvides symbolic regression functionality.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://gplearn.readthedocs.io/\r\n* source URL: https://pypi.org/project/gplearn/\r\n* license: New BSD\r\n* platforms: python3\r\n\r\nI'm happy to package, but it might need a long-therm maintainer. Although it does not seem to be updated too frequently.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169559/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169546","id":1210622310,"node_id":"I_kwDOAEVQ_M5IKKFm","number":169546,"title":"Package request: zotero / dataserver ","user":{"login":"a-kenji","id":65275785,"node_id":"MDQ6VXNlcjY1Mjc1Nzg1","avatar_url":"https://avatars.githubusercontent.com/u/65275785?v=4","gravatar_id":"","url":"https://api.github.com/users/a-kenji","html_url":"https://github.com/a-kenji","followers_url":"https://api.github.com/users/a-kenji/followers","following_url":"https://api.github.com/users/a-kenji/following{/other_user}","gists_url":"https://api.github.com/users/a-kenji/gists{/gist_id}","starred_url":"https://api.github.com/users/a-kenji/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a-kenji/subscriptions","organizations_url":"https://api.github.com/users/a-kenji/orgs","repos_url":"https://api.github.com/users/a-kenji/repos","events_url":"https://api.github.com/users/a-kenji/events{/privacy}","received_events_url":"https://api.github.com/users/a-kenji/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-21T07:36:46Z","updated_at":"2022-04-21T07:36:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nThe backend of https://github.com/zotero/zotero.\r\nWhich allows synchronization of bibliographies,\r\nwith different zotero instances.\r\n\r\nA module, that can be configured with the database and services would be a goal of this package request.\r\n\r\nI expect this to be quite an effort to package up\r\nand support, so here is some prior work to possibly get people started: \r\n- https://github.com/ZotPrime/zotprime\r\n- https://github.com/nextlevelshit/zotero-dataserver-docker\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.zotero.org/\r\n* source URL: https://github.com/zotero/dataserver\r\n* license: AGPLv3\r\n* platforms: unix, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169546/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169478","id":1210130371,"node_id":"I_kwDOAEVQ_M5IIR_D","number":169478,"title":"hugo 0.96.0 build breaks under darwin x86","user":{"login":"lockejan","id":25434434,"node_id":"MDQ6VXNlcjI1NDM0NDM0","avatar_url":"https://avatars.githubusercontent.com/u/25434434?v=4","gravatar_id":"","url":"https://api.github.com/users/lockejan","html_url":"https://github.com/lockejan","followers_url":"https://api.github.com/users/lockejan/followers","following_url":"https://api.github.com/users/lockejan/following{/other_user}","gists_url":"https://api.github.com/users/lockejan/gists{/gist_id}","starred_url":"https://api.github.com/users/lockejan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lockejan/subscriptions","organizations_url":"https://api.github.com/users/lockejan/orgs","repos_url":"https://api.github.com/users/lockejan/repos","events_url":"https://api.github.com/users/lockejan/events{/privacy}","received_events_url":"https://api.github.com/users/lockejan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-20T19:37:55Z","updated_at":"2022-04-20T19:59:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nInstalling hugo 0.96.0 under darwin results in an error.\r\nThe last version wasn't broken.\r\n\r\n```\r\nerror: builder for '/nix/store/kdkfj0l9pc17yy876xdr1lqkn6sprlja-hugo-0.96.0.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > github.com/gohugoio/hugo\r\n > # github.com/gohugoio/hugo\r\n > /nix/store/ska85j344wk3a1mbabsr104085lwl0ri-go-1.18.1/share/go/pkg/tool/darwin_amd64/link: running clang++ failed: exit status 1\r\n > Undefined symbols for architecture x86_64:\r\n > \"_SecTrustEvaluateWithError\", referenced from:\r\n > _crypto/x509/internal/macos.x509_SecTrustEvaluateWithError_trampoline.abi0 in go.o\r\n > \"_utimensat\", referenced from:\r\n > _syscall.libc_utimensat_trampoline.abi0 in go.o\r\n > ld: symbol(s) not found for architecture x86_64\r\n > clang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\n For full logs, run 'nix log /nix/store/kdkfj0l9pc17yy876xdr1lqkn6sprlja-hugo-0.96.0.drv'.\r\nerror: 1 dependencies of derivation '/nix/store/y74ryb2b2nvsw9y3llbw3d1q7czqkfpc-nix-shell-env.drv' failed to build\r\n\r\n```\r\n\r\ntry: nix-env -iA nixpkgs.hugo\r\n\r\n### Additional context\r\nFull log\r\n```\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/gxnpywgvgzvyzmfw4dp3vrdp3kla5kvn-source\r\nsource root is source\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nBuilding subPackage ./.\r\ngo: downloading github.com/fsnotify/fsnotify v1.5.1\r\ngo: downloading github.com/bep/debounce v1.2.0\r\ngo: downloading github.com/alecthomas/chroma v0.10.0\r\n\r\n...\r\n\r\ngithub.com/gohugoio/hugo/commands\r\ngithub.com/gohugoio/hugo\r\n# github.com/gohugoio/hugo\r\n/nix/store/ska85j344wk3a1mbabsr104085lwl0ri-go-1.18.1/share/go/pkg/tool/darwin_amd64/link: running clang++ failed: exit status 1\r\nUndefined symbols for architecture x86_64:\r\n \"_SecTrustEvaluateWithError\", referenced from:\r\n _crypto/x509/internal/macos.x509_SecTrustEvaluateWithError_trampoline.abi0 in go.o\r\n \"_utimensat\", referenced from:\r\n _syscall.libc_utimensat_trampoline.abi0 in go.o\r\nld: symbol(s) not found for architecture x86_64\r\nclang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\n\r\n```\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nThe last PR https://github.com/NixOS/nixpkgs/pull/168184 seems to introduce the breaking changes @DeeUnderscore\r\n@schneefux @Br1ght0ne @Frostman\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(lockejan): `\"home-manager, nixpkgs\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/Users/lockejan/.nix-defexpr/channels/nixpkgs\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169478/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169473","id":1210111805,"node_id":"I_kwDOAEVQ_M5IINc9","number":169473,"title":"rpl 1.10: ModuleNotFoundError: No module named 'chardet'","user":{"login":"rkoe","id":2507744,"node_id":"MDQ6VXNlcjI1MDc3NDQ=","avatar_url":"https://avatars.githubusercontent.com/u/2507744?v=4","gravatar_id":"","url":"https://api.github.com/users/rkoe","html_url":"https://github.com/rkoe","followers_url":"https://api.github.com/users/rkoe/followers","following_url":"https://api.github.com/users/rkoe/following{/other_user}","gists_url":"https://api.github.com/users/rkoe/gists{/gist_id}","starred_url":"https://api.github.com/users/rkoe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rkoe/subscriptions","organizations_url":"https://api.github.com/users/rkoe/orgs","repos_url":"https://api.github.com/users/rkoe/repos","events_url":"https://api.github.com/users/rkoe/events{/privacy}","received_events_url":"https://api.github.com/users/rkoe/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-20T19:18:14Z","updated_at":"2022-04-23T17:27:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe rpl-package broke recently:\r\n\r\n```\r\n$ rpl\r\nTraceback (most recent call last):\r\n File \"/nix/store/6s8s9w0nmbmh8a40ima1w275z7zfchxs-rpl-1.10/bin/.rpl-wrapped\", line 30, in <module>\r\n from chardet.universaldetector import UniversalDetector\r\nModuleNotFoundError: No module named 'chardet'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. $ nix-env -iA nixos.rpl\r\n2. $ rpl\r\n\r\n### Notify maintainers\r\n@teto \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336847.e387bb3a4d0\"`\r\n - channels(user): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169473/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169466","id":1210030756,"node_id":"I_kwDOAEVQ_M5IH5qk","number":169466,"title":"android-platform-tools 33.0.1, aarch64-darwin support","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-20T18:07:15Z","updated_at":"2022-04-23T17:27:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 31.0.3\r\ndesired version: 33.0.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers:\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169466/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169465","id":1210025818,"node_id":"I_kwDOAEVQ_M5IH4da","number":169465,"title":"nextcloud: overzealous hsts header usage","user":{"login":"arnottcr","id":2526260,"node_id":"MDQ6VXNlcjI1MjYyNjA=","avatar_url":"https://avatars.githubusercontent.com/u/2526260?v=4","gravatar_id":"","url":"https://api.github.com/users/arnottcr","html_url":"https://github.com/arnottcr","followers_url":"https://api.github.com/users/arnottcr/followers","following_url":"https://api.github.com/users/arnottcr/following{/other_user}","gists_url":"https://api.github.com/users/arnottcr/gists{/gist_id}","starred_url":"https://api.github.com/users/arnottcr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/arnottcr/subscriptions","organizations_url":"https://api.github.com/users/arnottcr/orgs","repos_url":"https://api.github.com/users/arnottcr/repos","events_url":"https://api.github.com/users/arnottcr/events{/privacy}","received_events_url":"https://api.github.com/users/arnottcr/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-20T18:02:26Z","updated_at":"2022-04-24T02:23:59Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"The `Strict-Transport-Security` header should only be added if [services.nextcloud.https](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/nixos/modules/services/web-apps/nextcloud.nix#L148) is enabled, right?\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/147b03fa8ebf9d5d5f6784f87dc61f0e7beee911/nixos/modules/services/web-apps/nextcloud.nix#L910","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169465/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169464","id":1210018701,"node_id":"I_kwDOAEVQ_M5IH2uN","number":169464,"title":"vscode-fhs run from nix develop cannot launch terminal or extensions with binaries","user":{"login":"kjeremy","id":4325700,"node_id":"MDQ6VXNlcjQzMjU3MDA=","avatar_url":"https://avatars.githubusercontent.com/u/4325700?v=4","gravatar_id":"","url":"https://api.github.com/users/kjeremy","html_url":"https://github.com/kjeremy","followers_url":"https://api.github.com/users/kjeremy/followers","following_url":"https://api.github.com/users/kjeremy/following{/other_user}","gists_url":"https://api.github.com/users/kjeremy/gists{/gist_id}","starred_url":"https://api.github.com/users/kjeremy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kjeremy/subscriptions","organizations_url":"https://api.github.com/users/kjeremy/orgs","repos_url":"https://api.github.com/users/kjeremy/repos","events_url":"https://api.github.com/users/kjeremy/events{/privacy}","received_events_url":"https://api.github.com/users/kjeremy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-20T17:55:20Z","updated_at":"2022-04-29T14:11:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nvscode-fhs fails to launch the terminal process (and other extension issues) if launched from within a `nix develop` session.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add vscode-fhs to your configuration.nix\r\n2. Run `git clone https://github.com/breakds/flake-example-hello-repeater`\r\n3. Run `nix develop`\r\n4. Run `code .`\r\n5. Go to the Terminal Menu and select New Terminal\r\n\r\n### Expected behavior\r\nA Terminal window should pop up. Instead the bash process dies.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n\r\n\r\n### Additional context\r\nThis also impacts cmake from the CMake Tools extension. The same problem manifests in the Nix Env Selector extension as missing symbols from `nix-shell`.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@eadwu @Synthetica9 @maxeaubrey @bobby285271 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese 4 paths will be fetched (0.03 MiB download, 0.15 MiB unpacked):\r\n /nix/store/4ybkncn05qbhgbdxg9sxdgpm1jpdx76w-gcc-wrapper-10.3.0\r\n /nix/store/83l8wwrx7xs3mh9sbbj6whmyx8y4cz36-stdenv-linux\r\n /nix/store/c4k3fcsp5cqg9v0rpac9qbqmbkm6a7pk-binutils-wrapper-2.35.2\r\n /nix/store/wsjfqi1r5f6r9jvxm8kji8q0cdahfjpl-expand-response-params\r\ncopying path '/nix/store/wsjfqi1r5f6r9jvxm8kji8q0cdahfjpl-expand-response-params' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/c4k3fcsp5cqg9v0rpac9qbqmbkm6a7pk-binutils-wrapper-2.35.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4ybkncn05qbhgbdxg9sxdgpm1jpdx76w-gcc-wrapper-10.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/83l8wwrx7xs3mh9sbbj6whmyx8y4cz36-stdenv-linux' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(root): `\"nixos\"`\r\n - channels(jkolb): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169464/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169461","id":1209998680,"node_id":"I_kwDOAEVQ_M5IHx1Y","number":169461,"title":"ncdu_2: CPU features impurity","user":{"login":"lourkeur","id":15657735,"node_id":"MDQ6VXNlcjE1NjU3NzM1","avatar_url":"https://avatars.githubusercontent.com/u/15657735?v=4","gravatar_id":"","url":"https://api.github.com/users/lourkeur","html_url":"https://github.com/lourkeur","followers_url":"https://api.github.com/users/lourkeur/followers","following_url":"https://api.github.com/users/lourkeur/following{/other_user}","gists_url":"https://api.github.com/users/lourkeur/gists{/gist_id}","starred_url":"https://api.github.com/users/lourkeur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lourkeur/subscriptions","organizations_url":"https://api.github.com/users/lourkeur/orgs","repos_url":"https://api.github.com/users/lourkeur/repos","events_url":"https://api.github.com/users/lourkeur/events{/privacy}","received_events_url":"https://api.github.com/users/lourkeur/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-20T17:35:07Z","updated_at":"2022-04-21T00:11:01Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nThe output will include recent vector instructions if and only if the builder supports them. This break reproducibility.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Get on an Intel Sandy Bridge machine\r\n2. Run a derivation from a substituter. This results in a `SIGILL` due to a `vmovups xmm0 xmmword ptr` instruction\r\n3. Build locally and run. No `SIGILL`\r\n\r\n### Expected behavior\r\nBoth derivations should be identical.\r\n\r\n### Screenshots\r\nThis is the segfault inside an assembly debugger\r\n\r\n### Additional context\r\nThis might affect `zig` projects in general. @andrewrk @AndersonTorres\r\n\r\nThis is both an impurity and a usability problem because I cannot use certain derivations on some of my older computers.\r\n\r\n### Notify maintainers\r\n@pSub @SuperSandro2000 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/etc/nix/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169461/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169458","id":1209937891,"node_id":"I_kwDOAEVQ_M5IHi_j","number":169458,"title":"postgresql: add listenAddress","user":{"login":"arnottcr","id":2526260,"node_id":"MDQ6VXNlcjI1MjYyNjA=","avatar_url":"https://avatars.githubusercontent.com/u/2526260?v=4","gravatar_id":"","url":"https://api.github.com/users/arnottcr","html_url":"https://github.com/arnottcr","followers_url":"https://api.github.com/users/arnottcr/followers","following_url":"https://api.github.com/users/arnottcr/following{/other_user}","gists_url":"https://api.github.com/users/arnottcr/gists{/gist_id}","starred_url":"https://api.github.com/users/arnottcr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/arnottcr/subscriptions","organizations_url":"https://api.github.com/users/arnottcr/orgs","repos_url":"https://api.github.com/users/arnottcr/repos","events_url":"https://api.github.com/users/arnottcr/events{/privacy}","received_events_url":"https://api.github.com/users/arnottcr/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-20T16:39:29Z","updated_at":"2022-04-23T17:28:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"`enableTCPIP` is incorrectly defined, as currently you are only disabling binding to all [recte external] interfaces. To actually disable TCP/IP, you want `listen_addresses = ''`. I am unclear on how exactly compatibility would work for this issue, since the desired behaviour is incompatible with the current set.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/147b03fa8ebf9d5d5f6784f87dc61f0e7beee911/nixos/modules/services/databases/postgresql.nix#L288","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169458/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169457","id":1209918891,"node_id":"I_kwDOAEVQ_M5IHeWr","number":169457,"title":"Using ZFS on desktop with stock kernel is bad experience","user":{"login":"poelzi","id":66107,"node_id":"MDQ6VXNlcjY2MTA3","avatar_url":"https://avatars.githubusercontent.com/u/66107?v=4","gravatar_id":"","url":"https://api.github.com/users/poelzi","html_url":"https://github.com/poelzi","followers_url":"https://api.github.com/users/poelzi/followers","following_url":"https://api.github.com/users/poelzi/following{/other_user}","gists_url":"https://api.github.com/users/poelzi/gists{/gist_id}","starred_url":"https://api.github.com/users/poelzi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/poelzi/subscriptions","organizations_url":"https://api.github.com/users/poelzi/orgs","repos_url":"https://api.github.com/users/poelzi/repos","events_url":"https://api.github.com/users/poelzi/events{/privacy}","received_events_url":"https://api.github.com/users/poelzi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-04-20T16:22:36Z","updated_at":"2022-04-26T16:05:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nZFS on a desktop system with default kernel which is compiled with PREEMTIVE_VOLUNTARY causes a system with terrible lagg, short hangs and very bad realtime behaviour. This is easily so see with jackd and mixxx for example.\r\n\r\nIf the kernel is compiled with these changes, the system behaves much better:\r\n```\r\nboot.kernelPatches = [ {\r\n name = \"enable RT_FULL\";\r\n patch = null;\r\n extraConfig = ''\r\n PREEMPT y\r\n PREEMPT_BUILD y\r\n PREEMPT_VOLUNTARY n\r\n PREEMPT_COUNT y\r\n PREEMPTION y\r\n '';\r\n } ];\r\n```\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Do any ZFS file io\r\n2. Run mixxx + jackd for example\r\n3. Observe the stuttering and underuns\r\n\r\n### Expected behavior\r\nMore behaviour similar to other filesystems\r\n\r\n### Additional context\r\n\r\nUpstream ticket: https://github.com/openzfs/zfs/issues/13128\r\n\r\n\r\n### Notify maintainers\r\n\r\n@wizeman @hmenke @jcumming @jonringer @fpletz @globin \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.20, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(poelzi): `\"home-manager-21.11, nixos-21.05.4726.530a53dcbc9\"`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169457/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169443","id":1209725233,"node_id":"I_kwDOAEVQ_M5IGvEx","number":169443,"title":"X11 fails to start with AMD card (on NixOS 21.11)","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-20T13:53:30Z","updated_at":"2022-04-21T15:48:34Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```\r\n...\r\n[ 5.668] (II) AMDGPU: Driver for AMD Radeon:\r\n\tAll GPUs supported by the amdgpu kernel driver\r\n[ 5.671] (II) AMDGPU(0): [KMS] Kernel modesetting enabled.\r\n[ 5.671] (EE) AMDGPU(0): [drm] Failed to open DRM device for pci:0000:03:00.0: No such file or directory\r\n[ 5.671] (EE) Screen 0 deleted because of no matching config section.\r\n[ 5.671] (II) UnloadModule: \"amdgpu\"\r\n[ 5.671] (EE) Device(s) detected, but none match those in the config file.\r\n[ 5.671] (EE) \r\nFatal server error:\r\n[ 5.671] (EE) no screens found(EE) \r\n```\r\n\r\nX.0.log: https://gist.github.com/davidak/6704cc4a980745f54e614ee30520dc0a\r\n\r\nEven without `services.xserver.videoDrivers = [ \"amdgpu\" ];`: https://gist.github.com/davidak/23d128e318e80bef32112baaef21d466\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. i have rolled back from unstable where it works (not sure if X has state that might cause such issues)\r\n2. have system with amd gpu\r\n3. use pantheon desktop (which uses X11)\r\n\r\n### Expected behavior\r\nX11 starting\r\n\r\n### Additional context\r\nSame error message as in https://github.com/NixOS/nixpkgs/issues/167909 (same system)\r\n\r\nIt worked before on NixOS stable before i updated to unstable! I don't have the generation anymore.\r\n\r\n### Notify maintainers\r\n\r\nmaybe @corngood ?\r\n\r\n### Metadata\r\n\r\nNixOS 21.11.337107.147b03fa8eb\r\n\r\nAlso reproducible with\r\n\r\n- 21.11pre335443.e84444b14cc\r\n- 21.11pre337040.a62ce97f92b\r\n\r\n(pretty sure it worked there before i upgraded).","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169443/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169442","id":1209707609,"node_id":"I_kwDOAEVQ_M5IGqxZ","number":169442,"title":"NSD DNSSec broken after BIND 9.18.0","user":{"login":"hexchen","id":41522204,"node_id":"MDQ6VXNlcjQxNTIyMjA0","avatar_url":"https://avatars.githubusercontent.com/u/41522204?v=4","gravatar_id":"","url":"https://api.github.com/users/hexchen","html_url":"https://github.com/hexchen","followers_url":"https://api.github.com/users/hexchen/followers","following_url":"https://api.github.com/users/hexchen/following{/other_user}","gists_url":"https://api.github.com/users/hexchen/gists{/gist_id}","starred_url":"https://api.github.com/users/hexchen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hexchen/subscriptions","organizations_url":"https://api.github.com/users/hexchen/orgs","repos_url":"https://api.github.com/users/hexchen/repos","events_url":"https://api.github.com/users/hexchen/events{/privacy}","received_events_url":"https://api.github.com/users/hexchen/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-20T13:40:27Z","updated_at":"2022-04-20T15:06:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nBIND 9.18.0 removed the python-based dnssec-keymgr, leading to failures in the nsd-dnssec unit.\r\n```\r\nApr 20 12:41:12 koryaksky nsd-dnssec-start[4182876]: /nix/store/0rm8aws5rfxj4crab61yzffqldvc6xg2-unit-script-nsd-dnssec-start/bin/nsd-dnssec-start: line 7: /nix/store/57knpqw2siwi6saz3vws91hq33pvsg51-bind-9.18.1/bin/dnssec-keymgr: No such \r\nfile or directory\r\n```\r\n\r\n### Steps To Reproduce\r\nEnable dnssec handling via `services.nsd.zones.<name>.dnssec`\r\n\r\n### Expected behavior\r\ndnssec is properly handled\r\n\r\n### Additional context\r\nThe deprecation of the dnssec-keymgr tool is documented here: https://downloads.isc.org/isc/bind9/9.18.2/doc/arm/html/notes.html#removed-features\r\n\r\nPotential fix: package up https://gitlab.isc.org/isc-projects/dnssec-keymgr and use it instead of the no-longer included tools.\r\n\r\n### Notify maintainers\r\n@hrdinka \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/etc/src/nixpkgs`\r\n```\r\ncurrent nixpkgs hash: 1ffba9f2f683063c2b14c9f4d12c55ad5f4ed887\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169442/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169427","id":1209549041,"node_id":"I_kwDOAEVQ_M5IGEDx","number":169427,"title":"Dotnet license","user":{"login":"linsui","id":36977733,"node_id":"MDQ6VXNlcjM2OTc3NzMz","avatar_url":"https://avatars.githubusercontent.com/u/36977733?v=4","gravatar_id":"","url":"https://api.github.com/users/linsui","html_url":"https://github.com/linsui","followers_url":"https://api.github.com/users/linsui/followers","following_url":"https://api.github.com/users/linsui/following{/other_user}","gists_url":"https://api.github.com/users/linsui/gists{/gist_id}","starred_url":"https://api.github.com/users/linsui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/linsui/subscriptions","organizations_url":"https://api.github.com/users/linsui/orgs","repos_url":"https://api.github.com/users/linsui/repos","events_url":"https://api.github.com/users/linsui/events{/privacy}","received_events_url":"https://api.github.com/users/linsui/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-04-20T11:24:32Z","updated_at":"2022-04-20T16:25:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAccording to https://github.com/dotnet/installer#license, the pre-built dotnot binaries are not licensed under MIT but https://dotnet.microsoft.com/en-us/dotnet_library_license.htm. According to the EULA it seems the binary can't be redistributed. See https://devblogs.microsoft.com/premier-developer/net-core-overview/ also.\r\n\r\n> Licensing model: Source (MIT), Binary (Microsoft EULA)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@tonyhoglund @IvarWithoutBones @prusnak\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169427/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169387","id":1209087738,"node_id":"I_kwDOAEVQ_M5IETb6","number":169387,"title":"virt-manager can't use zpool for storage(cant refresh volume list)","user":{"login":"ghost","id":10137,"node_id":"MDQ6VXNlcjEwMTM3","avatar_url":"https://avatars.githubusercontent.com/u/10137?v=4","gravatar_id":"","url":"https://api.github.com/users/ghost","html_url":"https://github.com/ghost","followers_url":"https://api.github.com/users/ghost/followers","following_url":"https://api.github.com/users/ghost/following{/other_user}","gists_url":"https://api.github.com/users/ghost/gists{/gist_id}","starred_url":"https://api.github.com/users/ghost/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ghost/subscriptions","organizations_url":"https://api.github.com/users/ghost/orgs","repos_url":"https://api.github.com/users/ghost/repos","events_url":"https://api.github.com/users/ghost/events{/privacy}","received_events_url":"https://api.github.com/users/ghost/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-20T02:34:54Z","updated_at":"2022-04-22T05:49:16Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nvirt-manager can't use zpool for storage(cant refresh volume list)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n `sudo zfs create -V 50G tank/<name>`\r\n\r\n### Expected behavior\r\n\r\n\r\n\r\n```console\r\n$ zfs list\r\nNAME USED AVAIL REFER MOUNTPOINT\r\ntank 57.4G 404G 192K none\r\ntank/home 1.74G 404G 1.74G legacy\r\ntank/<name> 51.6G 455G 88K -\r\ntank/nix 4.14G 404G 4.14G legacy\r\n$ ls /dev/zvol/tank/\r\nlrwxrwxrwx 9 root 20 Apr 10:20 mac -> ../../zd0\r\n```\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@globin \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220419.c10c891`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169387/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169358","id":1208805873,"node_id":"I_kwDOAEVQ_M5IDOnx","number":169358,"title":"youtube-dl : youtube_dl.utils.RegexNotFoundError: Unable to extract Initial JS player n function name","user":{"login":"kevung","id":12058649,"node_id":"MDQ6VXNlcjEyMDU4NjQ5","avatar_url":"https://avatars.githubusercontent.com/u/12058649?v=4","gravatar_id":"","url":"https://api.github.com/users/kevung","html_url":"https://github.com/kevung","followers_url":"https://api.github.com/users/kevung/followers","following_url":"https://api.github.com/users/kevung/following{/other_user}","gists_url":"https://api.github.com/users/kevung/gists{/gist_id}","starred_url":"https://api.github.com/users/kevung/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kevung/subscriptions","organizations_url":"https://api.github.com/users/kevung/orgs","repos_url":"https://api.github.com/users/kevung/repos","events_url":"https://api.github.com/users/kevung/events{/privacy}","received_events_url":"https://api.github.com/users/kevung/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-19T20:03:31Z","updated_at":"2022-04-20T22:54:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nyoutube-dl does not download videos from a youtube playlist link.\r\n\r\n```\r\n[unger@unger tmp]$ youtube-dl https://youtube.com/playlist?list=OLAK5uy_n9bV6G3_wAm1SOcRR79jUCYET5Wrk63cE --verbose\r\n[debug] System config: []\r\n[debug] User config: []\r\n[debug] Custom config: []\r\n[debug] Command-line args: ['https://youtube.com/playlist?list=OLAK5uy_n9bV6G3_wAm1SOcRR79jUCYET5Wrk63cE', '--verbose']\r\n[debug] Encodings: locale UTF-8, fs utf-8, out utf-8, pref UTF-8\r\n[debug] youtube-dl version 2021.12.17\r\n[debug] Lazy loading extractors enabled\r\n[debug] Python version 3.9.11 (CPython) - Linux-5.10.109-x86_64-with-glibc2.33\r\n[debug] exe versions: ffmpeg 4.4.1, ffprobe 4.4.1, rtmpdump 2.4\r\n[debug] Proxy map: {}\r\n[youtube:tab] OLAK5uy_n9bV6G3_wAm1SOcRR79jUCYET5Wrk63cE: Downloading webpage\r\n[download] Downloading playlist: Sympathique\r\n[youtube:tab] playlist Sympathique: Downloading 11 videos\r\n[download] Downloading video 1 of 11\r\n[youtube] l3AVD7NavZ4: Downloading webpage\r\n[youtube] l3AVD7NavZ4: Downloading player 19eb72e4\r\nERROR: l3AVD7NavZ4: Traceback (most recent call last):\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1442, in _n_descramble\r\n self._player_cache[player_id] = self._extract_n_function(video_id, player_url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1415, in _extract_n_function\r\n funcname = self._extract_n_function_name(jscode)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1396, in _extract_n_function_name\r\n nfunc_and_idx = self._search_regex(\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/common.py\", line 1012, in _search_regex\r\n raise RegexNotFoundError('Unable to extract %s' % _name)\r\nyoutube_dl.utils.RegexNotFoundError: Unable to extract Initial JS player n function name; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\n (caused by RegexNotFoundError('Unable to extract \\x1b[0;34mInitial JS player n function name\\x1b[0m; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.')); please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\nTraceback (most recent call last):\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1442, in _n_descramble\r\n self._player_cache[player_id] = self._extract_n_function(video_id, player_url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1415, in _extract_n_function\r\n funcname = self._extract_n_function_name(jscode)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1396, in _extract_n_function_name\r\n nfunc_and_idx = self._search_regex(\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/common.py\", line 1012, in _search_regex\r\n raise RegexNotFoundError('Unable to extract %s' % _name)\r\nyoutube_dl.utils.RegexNotFoundError: Unable to extract Initial JS player n function name; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\nTraceback (most recent call last):\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1442, in _n_descramble\r\n self._player_cache[player_id] = self._extract_n_function(video_id, player_url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1415, in _extract_n_function\r\n funcname = self._extract_n_function_name(jscode)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1396, in _extract_n_function_name\r\n nfunc_and_idx = self._search_regex(\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/common.py\", line 1012, in _search_regex\r\n raise RegexNotFoundError('Unable to extract %s' % _name)\r\nyoutube_dl.utils.RegexNotFoundError: Unable to extract Initial JS player n function name; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\n\r\nDuring handling of the above exception, another exception occurred:\r\n\r\nTraceback (most recent call last):\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/YoutubeDL.py\", line 815, in wrapper\r\n return func(self, *args, **kwargs)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/YoutubeDL.py\", line 836, in __extract_info\r\n ie_result = ie.extract(url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/common.py\", line 534, in extract\r\n ie_result = self._real_extract(url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1874, in _real_extract\r\n self._unthrottle_format_urls(video_id, player_url, formats)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1459, in _unthrottle_format_urls\r\n n_response = self._n_descramble(n_param, player_url, video_id)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1449, in _n_descramble\r\n raise ExtractorError(traceback.format_exc(), cause=e, video_id=video_id)\r\nyoutube_dl.utils.ExtractorError: l3AVD7NavZ4: Traceback (most recent call last):\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1442, in _n_descramble\r\n self._player_cache[player_id] = self._extract_n_function(video_id, player_url)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1415, in _extract_n_function\r\n funcname = self._extract_n_function_name(jscode)\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/youtube.py\", line 1396, in _extract_n_function_name\r\n nfunc_and_idx = self._search_regex(\r\n File \"/nix/store/a9xxgb1cm5dn9qf2cy44bfghmfizdasx-python3.9-youtube-dl-2021.12.17/lib/python3.9/site-packages/youtube_dl/extractor/common.py\", line 1012, in _search_regex\r\n raise RegexNotFoundError('Unable to extract %s' % _name)\r\nyoutube_dl.utils.RegexNotFoundError: Unable to extract Initial JS player n function name; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\n (caused by RegexNotFoundError('Unable to extract \\x1b[0;34mInitial JS player n function name\\x1b[0m; please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.')); please report this issue on https://yt-dl.org/bug . Make sure you are using the latest version; see https://yt-dl.org/update on how to update. Be sure to call youtube-dl with the --verbose flag and include its complete output.\r\n\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install youtube-dl (in configuration.nix)\r\n2. `youtube-dl https://youtube.com/playlist?list=OLAK5uy_n9bV6G3_wAm1SOcRR79jUCYET5Wrk63cE`\r\n\r\n### Expected behavior\r\n\r\nThe videos from the playlist should be downloaded\r\n\r\n### Notify maintainers\r\n\r\n@bluescreen303 @fpletz @Ma27 @rycee @asymmetric @peti @AndersonTorres \r\n\r\n### Metadata\r\n\r\n```[unger@unger ~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.109, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.337100.7b38b03d76a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169358/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169350","id":1208680971,"node_id":"I_kwDOAEVQ_M5ICwIL","number":169350,"title":"Kamailio SIP Server","user":{"login":"mawis","id":2042030,"node_id":"MDQ6VXNlcjIwNDIwMzA=","avatar_url":"https://avatars.githubusercontent.com/u/2042030?v=4","gravatar_id":"","url":"https://api.github.com/users/mawis","html_url":"https://github.com/mawis","followers_url":"https://api.github.com/users/mawis/followers","following_url":"https://api.github.com/users/mawis/following{/other_user}","gists_url":"https://api.github.com/users/mawis/gists{/gist_id}","starred_url":"https://api.github.com/users/mawis/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mawis/subscriptions","organizations_url":"https://api.github.com/users/mawis/orgs","repos_url":"https://api.github.com/users/mawis/repos","events_url":"https://api.github.com/users/mawis/events{/privacy}","received_events_url":"https://api.github.com/users/mawis/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-19T18:01:27Z","updated_at":"2022-04-19T18:01:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nKamailio® (successor of former OpenSER and SER) is an Open Source SIP Server released under GPLv2+, able to handle thousands of call setups per second. Kamailio can be used to build large platforms for VoIP and realtime communications – presence, WebRTC, Instant messaging and other applications. Moreover, it can be easily used for scaling up SIP-to-PSTN gateways, PBX systems or media servers like Asterisk™, FreeSWITCH™ or SEMS.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.kamailio.org/\r\n* source URL: https://www.kamailio.org/w/download/\r\n* repository URL: https://github.com/kamailio/kamailio\r\n* license: gpl2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169339","id":1208487697,"node_id":"I_kwDOAEVQ_M5ICA8R","number":169339,"title":"Gnome web (epiphany) on gtk4 from source build fails","user":{"login":"Millrocious","id":79750098,"node_id":"MDQ6VXNlcjc5NzUwMDk4","avatar_url":"https://avatars.githubusercontent.com/u/79750098?v=4","gravatar_id":"","url":"https://api.github.com/users/Millrocious","html_url":"https://github.com/Millrocious","followers_url":"https://api.github.com/users/Millrocious/followers","following_url":"https://api.github.com/users/Millrocious/following{/other_user}","gists_url":"https://api.github.com/users/Millrocious/gists{/gist_id}","starred_url":"https://api.github.com/users/Millrocious/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Millrocious/subscriptions","organizations_url":"https://api.github.com/users/Millrocious/orgs","repos_url":"https://api.github.com/users/Millrocious/repos","events_url":"https://api.github.com/users/Millrocious/events{/privacy}","received_events_url":"https://api.github.com/users/Millrocious/received_events","type":"User","site_admin":false},"labels":[{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-19T14:57:06Z","updated_at":"2022-04-20T20:38:38Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Gnome web (epiphany) on gtk4 from source build fails\r\n\r\noutput:\r\n```\r\nthis derivation will be built:\r\n /nix/store/9mbdhad6rafirnmh65fjkp8vjn9z38q5-epiphany-43.drv\r\nbuilding '/nix/store/9mbdhad6rafirnmh65fjkp8vjn9z38q5-epiphany-43.drv'...\r\nunpacking sources\r\nunpacking source archive /nix/store/8vdj6lbkrnw0xakxzjifq2khk8bk066s-epiphany-wip-exalm-gtk4.tar.gz\r\nsource root is epiphany-wip-exalm-gtk4\r\nsetting SOURCE_DATE_EPOCH to timestamp 1649764684 of file epiphany-wip-exalm-gtk4/third-party/readability/reader.css\r\npatching sources\r\npatching script interpreter paths in post_install.py\r\npost_install.py: interpreter directive changed from \"#!/usr/bin/env python3\" to \"/nix/store/kwp97hvzh4dff613a4vhpbl6yblavshb-python3-3.9.11/bin/python3\"\r\nconfiguring\r\nmeson flags: --buildtype=plain --libdir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/lib --libexecdir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/libexec --bindir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/bin --sbindir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/sbin --includedir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/include --mandir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/share/man --infodir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/share/info --localedir=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43/share/locale -Dauto_features=enabled -Dwrap_mode=nodownload --prefix=/nix/store/b9033231xbmvxx0hz9gkl2ni0fn3aywl-epiphany-43 -Dunit_tests=disabled \r\nThe Meson build system\r\nVersion: 0.57.1\r\nSource dir: /build/epiphany-wip-exalm-gtk4\r\nBuild dir: /build/epiphany-wip-exalm-gtk4/build\r\nBuild type: native build\r\nProject name: epiphany\r\nProject version: 42.beta\r\nC compiler for the host machine: gcc (gcc 10.3.0 \"gcc (GCC) 10.3.0\")\r\nC linker for the host machine: gcc ld.bfd 2.35.2\r\nHost machine cpu family: x86_64\r\nHost machine cpu: x86_64\r\nFound pkg-config: /nix/store/00ipmxm9k10lqjklrb2rbsjgkg1bsx7c-pkg-config-wrapper-0.29.2/bin/pkg-config (0.29.2)\r\nRun-time dependency iso-codes found: YES 4.6.0\r\nRun-time dependency cairo found: YES 1.16.0\r\nFound CMake: /nix/store/ilykjpp6m7brss45clmp2dxmlknvb2m4-cmake-3.21.2/bin/cmake (3.21.2)\r\nRun-time dependency gcr-4-gtk4 found: NO (tried pkgconfig and cmake)\r\n\r\nmeson.build:81:0: ERROR: Dependency \"gcr-4-gtk4\" not found, tried pkgconfig and cmake\r\n\r\nA full log can be found at /build/epiphany-wip-exalm-gtk4/build/meson-logs/meson-log.txt\r\nerror: builder for '/nix/store/9mbdhad6rafirnmh65fjkp8vjn9z38q5-epiphany-43.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > Host machine cpu: x86_64\r\n > Found pkg-config: /nix/store/00ipmxm9k10lqjklrb2rbsjgkg1bsx7c-pkg-config-wrapper-0.29.2/bin/pkg-config (0.29.2)\r\n > Run-time dependency iso-codes found: YES 4.6.0\r\n > Run-time dependency cairo found: YES 1.16.0\r\n > Found CMake: /nix/store/ilykjpp6m7brss45clmp2dxmlknvb2m4-cmake-3.21.2/bin/cmake (3.21.2)\r\n > Run-time dependency gcr-4-gtk4 found: NO (tried pkgconfig and cmake)\r\n >\r\n > meson.build:81:0: ERROR: Dependency \"gcr-4-gtk4\" not found, tried pkgconfig and cmake\r\n >\r\n > A full log can be found at /build/epiphany-wip-exalm-gtk4/build/meson-logs/meson-log.txt\r\n For full logs, run 'nix log /nix/store/9mbdhad6rafirnmh65fjkp8vjn9z38q5-epiphany-43.drv'.\r\n\r\n```\r\n## The package.nix:\r\n```\r\n{ lib\r\n, stdenv\r\n, meson\r\n, ninja\r\n, gettext\r\n, fetchurl\r\n, fetchpatch\r\n, pkg-config\r\n, gtk4\r\n, glib\r\n, icu\r\n, cmake\r\n, wrapGAppsHook\r\n, gnome\r\n, libxml2\r\n, libxslt\r\n, itstool\r\n, webkitgtk\r\n, libsoup\r\n, glib-networking\r\n, libsecret\r\n, libnotify\r\n, libarchive\r\n, p11-kit\r\n, sqlite\r\n, gcr\r\n, isocodes\r\n, desktop-file-utils\r\n, python3\r\n, nettle\r\n, gdk-pixbuf\r\n, gst_all_1\r\n, json-glib\r\n, libdazzle\r\n, libhandy\r\n, buildPackages\r\n, withPantheon ? false\r\n}:\r\n\r\nstdenv.mkDerivation rec {\r\n pname = \"epiphany\";\r\n version = \"43\";\r\n\r\n src = fetchurl {\r\n url = \"https://gitlab.gnome.org/GNOME/epiphany/-/archive/wip/exalm/gtk4/epiphany-wip-exalm-gtk4.tar.gz\";\r\n sha256 = \"sha256-VFj/G6f91HWJl2vLSKsJX5hS1ukXPLrTVID94q1WBbM=\";\r\n };\r\n\r\n patches = lib.optionals withPantheon [\r\n # Pantheon specific patches for epiphany\r\n # https://github.com/elementary/browser\r\n #\r\n # Patch to unlink nav buttons\r\n # https://github.com/elementary/browser/pull/18\r\n (fetchpatch {\r\n url = \"https://raw.githubusercontent.com/elementary/browser/cc17559a7ac6effe593712b4f3d0bbefde6e3b62/navigation-buttons.patch\";\r\n sha256 = \"sha256-G1/JUjn/8DyO9sgL/5Kq205KbTOs4EMi4Vf3cJ8FHXU=\";\r\n })\r\n ];\r\n\r\n nativeBuildInputs = [\r\n desktop-file-utils\r\n gettext\r\n itstool\r\n libxslt\r\n gcr\r\n meson\r\n cmake\r\n ninja\r\n pkg-config\r\n python3\r\n wrapGAppsHook\r\n buildPackages.glib\r\n buildPackages.gtk3\r\n ];\r\n\r\n buildInputs = [\r\n gdk-pixbuf\r\n glib\r\n gst_all_1.gst-libav\r\n gst_all_1.gst-plugins-bad\r\n gst_all_1.gst-plugins-base\r\n gst_all_1.gst-plugins-good\r\n gst_all_1.gst-plugins-ugly\r\n gst_all_1.gstreamer\r\n gtk4\r\n icu\r\n isocodes\r\n json-glib\r\n libdazzle\r\n libhandy\r\n libnotify\r\n libarchive\r\n libsecret\r\n libsoup\r\n libxml2\r\n nettle\r\n p11-kit\r\n sqlite\r\n webkitgtk\r\n ];\r\n\r\n # Tests need an X display\r\n mesonFlags = [\r\n \"-Dunit_tests=disabled\"\r\n ];\r\n\r\n postPatch = ''\r\n chmod +x post_install.py # patchShebangs requires executable file\r\n patchShebangs post_install.py\r\n '';\r\n\r\n passthru = {\r\n updateScript = gnome.updateScript {\r\n packageName = pname;\r\n };\r\n };\r\n\r\n meta = with lib; {\r\n homepage = \"https://wiki.gnome.org/Apps/Epiphany\";\r\n description = \"WebKit based web browser for GNOME\";\r\n maintainers = teams.gnome.members ++ teams.pantheon.members;\r\n license = licenses.gpl3Plus;\r\n platforms = platforms.linux;\r\n };\r\n}\r\n\r\n```\r\n\r\n## Technical details\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.2, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169339/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169322","id":1208338655,"node_id":"I_kwDOAEVQ_M5IBcjf","number":169322,"title":"can't launch pgadmin4 on master","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-19T12:59:41Z","updated_at":"2022-04-19T22:57:28Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\non master b07f020d2f1c83a9b8f01e188ef503e63c0953cc, trying to run pgadmin4 fails:\r\n\r\n```\r\n❯ nix shell .#pgadmin\r\nnixpkgs2 on master \r\n➜ pgadmin\r\npgadmin: command not found\r\nnixpkgs2 on master \r\n❯ pgadmin4\r\nTraceback (most recent call last):\r\n File \"/nix/store/4cbmq2dxcfrb5yfbpdv92fq8qk9zg483-pgadmin-6.7/bin/.pgadmin4-wrapped\", line 6, in <module>\r\n from pgadmin4.pgAdmin4 import main\r\n File \"/nix/store/4cbmq2dxcfrb5yfbpdv92fq8qk9zg483-pgadmin-6.7/lib/python3.9/site-packages/pgadmin4/pgAdmin4.py\", line 98, in <module>\r\n app = create_app()\r\n File \"/nix/store/4cbmq2dxcfrb5yfbpdv92fq8qk9zg483-pgadmin-6.7/lib/python3.9/site-packages/pgadmin4/pgadmin/__init__.py\", line 233, in create_app\r\n app.jinja_env.trim_blocks = True\r\n File \"/nix/store/q07dwn6b7rl574ka43xq5f8d7j17apzd-python3.9-Flask-2.1.1/lib/python3.9/site-packages/flask/helpers.py\", line 752, in __get__\r\n return super().__get__(obj, type=type)\r\n File \"/nix/store/0gyvjdji4rwslg7gmib2x7i1gnm4vbw3-python3.9-werkzeug-2.1.0/lib/python3.9/site-packages/werkzeug/utils.py\", line 107, in __get__\r\n value = self.fget(obj) # type: ignore\r\n File \"/nix/store/q07dwn6b7rl574ka43xq5f8d7j17apzd-python3.9-Flask-2.1.1/lib/python3.9/site-packages/flask/app.py\", line 602, in jinja_env\r\n return self.create_jinja_environment()\r\n File \"/nix/store/q07dwn6b7rl574ka43xq5f8d7j17apzd-python3.9-Flask-2.1.1/lib/python3.9/site-packages/flask/app.py\", line 694, in create_jinja_environment\r\n rv = self.jinja_environment(self, **options)\r\n File \"/nix/store/q07dwn6b7rl574ka43xq5f8d7j17apzd-python3.9-Flask-2.1.1/lib/python3.9/site-packages/flask/templating.py\", line 42, in __init__\r\n BaseEnvironment.__init__(self, **options)\r\n File \"/nix/store/4yicnl0ycpjqb5z3np5c53y619p5zv3s-python3.9-Jinja2-3.1.1/lib/python3.9/site-packages/jinja2/environment.py\", line 363, in __init__\r\n self.extensions = load_extensions(self, extensions)\r\n File \"/nix/store/4yicnl0ycpjqb5z3np5c53y619p5zv3s-python3.9-Jinja2-3.1.1/lib/python3.9/site-packages/jinja2/environment.py\", line 117, in load_extensions\r\n extension = t.cast(t.Type[\"Extension\"], import_string(extension))\r\n File \"/nix/store/4yicnl0ycpjqb5z3np5c53y619p5zv3s-python3.9-Jinja2-3.1.1/lib/python3.9/site-packages/jinja2/utils.py\", line 149, in import_string\r\n return getattr(__import__(module, None, None, [obj]), obj)\r\nAttributeError: module 'jinja2.ext' has no attribute 'autoescape'\r\n\r\n```\r\nanother issue is that nix run .#pgadmin wont work, we could set mainProgram.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169322/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169321","id":1208319193,"node_id":"I_kwDOAEVQ_M5IBXzZ","number":169321,"title":"frei0r: Not all plugins are installed","user":{"login":"harrisonthorne","id":33523827,"node_id":"MDQ6VXNlcjMzNTIzODI3","avatar_url":"https://avatars.githubusercontent.com/u/33523827?v=4","gravatar_id":"","url":"https://api.github.com/users/harrisonthorne","html_url":"https://github.com/harrisonthorne","followers_url":"https://api.github.com/users/harrisonthorne/followers","following_url":"https://api.github.com/users/harrisonthorne/following{/other_user}","gists_url":"https://api.github.com/users/harrisonthorne/gists{/gist_id}","starred_url":"https://api.github.com/users/harrisonthorne/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/harrisonthorne/subscriptions","organizations_url":"https://api.github.com/users/harrisonthorne/orgs","repos_url":"https://api.github.com/users/harrisonthorne/repos","events_url":"https://api.github.com/users/harrisonthorne/events{/privacy}","received_events_url":"https://api.github.com/users/harrisonthorne/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-19T12:48:29Z","updated_at":"2022-04-23T21:39:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSome frei0r plugins that appear in the archive from the [dyne site](https://files.dyne.org/frei0r/releases/) do not appear when installed with nix.\r\n\r\n(Also, frei0r is out of date; 1.8.0 is available! :))\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n\r\n1. Install `frei0r` via `environment.systemPackages` or home-manager `home.packages`\r\n2. For reference, download and extract the 1.7.0 archive from the [site](https://files.dyne.org/frei0r/releases/) mentioned above\r\n3. Observe that some plugins, such as `scale0tilt.so`, are missing from `$out/lib/frei0r-1/` (e.g. `~/.nix-profile/lib/frei0r-1/`)\r\n\r\n### Expected behavior\r\n\r\nI expect to see `scale0tilt.so` in frei0r's lib folder and to be able to use it in Kdenlive.\r\n\r\n### Additional context\r\n\r\nI'm trying to use these plugins with Kdenlive. Included in the logs of Kdenlive's startup are these lines:\r\n\r\n```\r\n...\r\nplugin not available: \"frei0r.baltan\"\r\nplugin not available: \"frei0r.bgsubtract0r\"\r\nplugin not available: \"frei0r.bigsh0t_eq_mask\"\r\nplugin not available: \"frei0r.bigsh0t_eq_to_rect\"\r\nplugin not available: \"frei0r.bigsh0t_hemi_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_rect_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_stabilize_360\"\r\nplugin not available: \"frei0r.bigsh0t_transform_360\"\r\nplugin not available: \"frei0r.delay0r\"\r\nplugin not available: \"frei0r.delaygrab\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.rgbparade\"\r\nplugin not available: \"frei0r.scale0tilt\"\r\nplugin not available: \"frei0r.vectorscope\"\r\n...\r\n```\r\n\r\n...along with a lot of other missing plugins from `avfilter` and a missing `opencv.tracker` plugin, too.\r\n\r\n<details>\r\n<summary>Full Kdenlive logs</summary>\r\n\r\n```\r\n=== /// CANNOT ACCESS SPEECH DICTIONARIES FOLDER\r\nNo LADSPA plugins were found!\r\n\r\nCheck your LADSPA_PATH environment variable.\r\nprofilePath from KdenliveSetting::mltPath: \"/nix/store/parkimd4avly3ahwsyy869yba9pibp1k-mlt-7.0.1/share/mlt/profiles\"\r\nprofilePath from appDir/../share: \"/nix/store/vgmzfj236aqm6fppzz7kghzr8ws3szw2-kdenlive-21.12.3/share/mlt-7/profiles\"\r\nprofilePath from build-time MLT_DATADIR: \"/nix/store/parkimd4avly3ahwsyy869yba9pibp1k-mlt-7.0.1/share/mlt-7/profiles\"\r\nmeltPath from KdenliveSetting::rendererPath: \"/nix/store/parkimd4avly3ahwsyy869yba9pibp1k-mlt-7.0.1/share/mlt-7/profiles\"\r\nInvalid metadata for \"audiochannels\"\r\nFailed to parse \"audiochannels\"\r\nInvalid metadata for \"audioconvert\"\r\nFailed to parse \"audioconvert\"\r\nInvalid metadata for \"imageconvert\"\r\nFailed to parse \"imageconvert\"\r\nInvalid metadata for \"telecide\"\r\nFailed to parse \"telecide\"\r\nInvalid metadata for \"jack\"\r\nFailed to parse \"jack\"\r\nInvalid metadata for \"deinterlace\"\r\nFailed to parse \"deinterlace\"\r\nInvalid metadata for \"glsl.manager\"\r\nFailed to parse \"glsl.manager\"\r\nInvalid metadata for \"movit.convert\"\r\nFailed to parse \"movit.convert\"\r\nInvalid metadata for \"movit.crop\"\r\nFailed to parse \"movit.crop\"\r\nInvalid metadata for \"movit.resample\"\r\nFailed to parse \"movit.resample\"\r\nInvalid metadata for \"movit.resize\"\r\nFailed to parse \"movit.resize\"\r\nInvalid metadata for \"avcolour_space\"\r\nFailed to parse \"avcolour_space\"\r\nInvalid metadata for \"avcolor_space\"\r\nFailed to parse \"avcolor_space\"\r\nInvalid metadata for \"avdeinterlace\"\r\nFailed to parse \"avdeinterlace\"\r\nInvalid metadata for \"swscale\"\r\nFailed to parse \"swscale\"\r\nInvalid metadata for \"swresample\"\r\nFailed to parse \"swresample\"\r\nplugin not available: \"avfilter.acompressor\"\r\nplugin not available: \"avfilter.aecho\"\r\nplugin not available: \"avfilter.agate\"\r\nplugin not available: \"audiolevelgraph\"\r\nplugin not available: \"avfilter.atadenoise\"\r\nplugin not available: \"avfilter.bs2b\"\r\nplugin not available: \"avfilter.bwdif\"\r\nplugin not available: \"avfilter.deblock\"\r\nplugin not available: \"avfilter.dedot\"\r\nplugin not available: \"avfilter.deflate\"\r\nplugin not available: \"avfilter.derain\"\r\nplugin not available: \"avfilter.doubleweave\"\r\nplugin not available: \"avfilter.field\"\r\nplugin not available: \"avfilter.framestep\"\r\nplugin not available: \"avfilter.fspp\"\r\nplugin not available: \"avfilter.graphmonitor\"\r\nplugin not available: \"avfilter.hqdn3d\"\r\nplugin not available: \"avfilter.inflate\"\r\nplugin not available: \"avfilter.lagfun\"\r\nplugin not available: \"avfilter.loudnorm\"\r\nplugin not available: \"avfilter.random\"\r\nplugin not available: \"avfilter.removegrain\"\r\nplugin not available: \"avfilter.separatefields\"\r\nplugin not available: \"avfilter.shuffleplanes\"\r\nplugin not available: \"avfilter.sofalizer\"\r\nplugin not available: \"avfilter.sr\"\r\nplugin not available: \"avfilter.tmix\"\r\nplugin not available: \"avfilter.w3fdif\"\r\nplugin not available: \"avfilter.weave\"\r\nplugin not available: \"avfilter.yadif\"\r\nplugin not available: \"frei0r.baltan\"\r\nplugin not available: \"frei0r.bgsubtract0r\"\r\nplugin not available: \"frei0r.bigsh0t_eq_mask\"\r\nplugin not available: \"frei0r.bigsh0t_eq_to_rect\"\r\nplugin not available: \"frei0r.bigsh0t_hemi_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_rect_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_stabilize_360\"\r\nplugin not available: \"frei0r.bigsh0t_transform_360\"\r\nplugin not available: \"frei0r.delay0r\"\r\nplugin not available: \"frei0r.delaygrab\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.rgbparade\"\r\nplugin not available: \"frei0r.scale0tilt\"\r\nplugin not available: \"frei0r.vectorscope\"\r\nplugin not available: \"gpstext\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa.9354877\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"movit.unsharp_mask\"\r\nplugin not available: \"rbpitch\"\r\nplugin not available: \"rbpitch\"\r\nplugin not available: \"region\"\r\nplugin not available: \"timewarp\"\r\nplugin not available: \"opencv.tracker\"\r\nplugin not available: \"avfilter.acompressor\"\r\nplugin not available: \"avfilter.aecho\"\r\nplugin not available: \"avfilter.agate\"\r\nplugin not available: \"audiolevelgraph\"\r\nplugin not available: \"avfilter.atadenoise\"\r\nplugin not available: \"avfilter.bs2b\"\r\nplugin not available: \"avfilter.bwdif\"\r\nplugin not available: \"avfilter.deblock\"\r\nplugin not available: \"avfilter.dedot\"\r\nplugin not available: \"avfilter.deflate\"\r\nplugin not available: \"avfilter.derain\"\r\nplugin not available: \"avfilter.doubleweave\"\r\nplugin not available: \"avfilter.field\"\r\nplugin not available: \"avfilter.framestep\"\r\nplugin not available: \"avfilter.fspp\"\r\nplugin not available: \"avfilter.graphmonitor\"\r\nplugin not available: \"avfilter.hqdn3d\"\r\nplugin not available: \"avfilter.inflate\"\r\nplugin not available: \"avfilter.lagfun\"\r\nplugin not available: \"avfilter.loudnorm\"\r\nplugin not available: \"avfilter.random\"\r\nplugin not available: \"avfilter.removegrain\"\r\nplugin not available: \"avfilter.separatefields\"\r\nplugin not available: \"avfilter.shuffleplanes\"\r\nplugin not available: \"avfilter.sofalizer\"\r\nplugin not available: \"avfilter.sr\"\r\nplugin not available: \"avfilter.tmix\"\r\nplugin not available: \"avfilter.w3fdif\"\r\nplugin not available: \"avfilter.weave\"\r\nplugin not available: \"avfilter.yadif\"\r\nplugin not available: \"frei0r.baltan\"\r\nplugin not available: \"frei0r.bgsubtract0r\"\r\nplugin not available: \"frei0r.bigsh0t_eq_mask\"\r\nplugin not available: \"frei0r.bigsh0t_eq_to_rect\"\r\nplugin not available: \"frei0r.bigsh0t_hemi_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_rect_to_eq\"\r\nplugin not available: \"frei0r.bigsh0t_stabilize_360\"\r\nplugin not available: \"frei0r.bigsh0t_transform_360\"\r\nplugin not available: \"frei0r.delay0r\"\r\nplugin not available: \"frei0r.delaygrab\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.lightgraffiti\"\r\nplugin not available: \"frei0r.rgbparade\"\r\nplugin not available: \"frei0r.scale0tilt\"\r\nplugin not available: \"frei0r.vectorscope\"\r\nplugin not available: \"gpstext\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa.9354877\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"ladspa\"\r\nplugin not available: \"movit.unsharp_mask\"\r\nplugin not available: \"rbpitch\"\r\nplugin not available: \"rbpitch\"\r\nplugin not available: \"region\"\r\nplugin not available: \"timewarp\"\r\nplugin not available: \"opencv.tracker\"\r\nplugin not available: \"region\"\r\nplugin not available: \"region\"\r\nQObject::disconnect: Unexpected nullptr parameter\r\nQObject::disconnect: Unexpected nullptr parameter\r\nQObject::disconnect: Unexpected nullptr parameter\r\nqrc:/qml/timeline.qml:2022:5: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }\r\n```\r\n</details>\r\n\r\n[My system](https://codeberg.org/harrisonthorne/nixos-config) and [HM configuration](https://codeberg.org/harrisonthorne/dotfiles/) both use flakes.\r\n\r\n### Notify maintainers\r\n\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@cillianderoiste \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.33, NixOS, 22.05 (Quokka), 22.05.20220413.ff9efb0`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(harrison): `\"home-manager, nixos\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169321/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169293","id":1207964631,"node_id":"I_kwDOAEVQ_M5IABPX","number":169293,"title":"enable tests for vimPlugins.sqlite-lua ","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null},{"id":1249449681,"node_id":"MDU6TGFiZWwxMjQ5NDQ5Njgx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20lua","name":"6.topic: lua","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-19T08:22:06Z","updated_at":"2022-04-19T08:22:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nSince my update to unstable 1ffba9f2f683063c2b14c9f4d12c55ad5f4ed887, I get this kind of output\r\n\r\n```\r\nE5108: Error executing lua ...r/pack/home-manager/start/sqlite.lua/lua/sqlite/defs.lua:29: /nix/store/4s21k8k7p1mfik0b33r2spq5hq7774k1-glibc-2.33-108/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/gqllzy0vrkkgxxawvqrdysbzm0dvrig4-sqlite-3.38.2/lib/libsqlite3.so) \r\nstack traceback: \r\n [builtin#203]: at 0x7f2e8b7ade70 \r\n ...r/pack/home-manager/start/sqlite.lua/lua/sqlite/defs.lua:29: in main chunk \r\n [C]: in function 'require' \r\n .../pack/home-manager/start/sqlite.lua/lua/sqlite/utils.lua:252: in function '__index' \r\n ...dir/pack/home-manager/start/sqlite.lua/lua/sqlite/db.lua:153: in function 'open' \r\n ....nvim/lua/telescope/_extensions/frecency/sql_wrapper.lua:46: in function 'bootstrap' \r\n ...cy.nvim/lua/telescope/_extensions/frecency/db_client.lua:92: in function 'init' \r\n ...ope-frecency.nvim/lua/telescope/_extensions/frecency.lua:285: in function 'setup' \r\n .../start/telescope.nvim/lua/telescope/_extensions/init.lua:64: in function 'load_extension' \r\n /home/teto/.config/nvim/lua/init-manual.lua:1188: in main chunk \r\n [C]: in function 'require' \r\n /home/teto/.config/nvim/lua/init-home-manager.lua:6: in main chunk \r\n [C]: in function 'require' \r\n ```\r\n\r\nseems like we hit a bug here https://github.com/tami5/sqlite.lua/blob/9ccd2a6538d8a201d1ea08784bd866950e1b4130/lua/sqlite/defs.lua#L7 . Not sure how to best fix it yet but in any case to prevent regressions we should enable tests for this package.\r\n\r\n`nix-build -A vimPlugins.sqlite-lua `\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169293/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169278","id":1207758095,"node_id":"I_kwDOAEVQ_M5H_O0P","number":169278,"title":"RISC-V linux cross compilation failing since staging-next merge","user":{"login":"Madouura","id":93990818,"node_id":"U_kgDOBZovog","avatar_url":"https://avatars.githubusercontent.com/u/93990818?v=4","gravatar_id":"","url":"https://api.github.com/users/Madouura","html_url":"https://github.com/Madouura","followers_url":"https://api.github.com/users/Madouura/followers","following_url":"https://api.github.com/users/Madouura/following{/other_user}","gists_url":"https://api.github.com/users/Madouura/gists{/gist_id}","starred_url":"https://api.github.com/users/Madouura/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Madouura/subscriptions","organizations_url":"https://api.github.com/users/Madouura/orgs","repos_url":"https://api.github.com/users/Madouura/repos","events_url":"https://api.github.com/users/Madouura/events{/privacy}","received_events_url":"https://api.github.com/users/Madouura/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-19T05:16:00Z","updated_at":"2022-04-22T14:34:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAt least since #168737 was merged into master, #168826 has failed to compile.\r\nI suspect a GCC change causing this issue.\r\n\r\n```console\r\nriscv64-linux-gcc -DHAVE_CONFIG_H -I. -I../.. -DLOCALEDIR=\\\"/nix/store/84q2jjw95gh7qy3iqvqb45jn2zbhvj88-xz-riscv64-linux-5.2.5/share/locale\\\" -I../../src/common -I../../src/liblzma/api -I../../lib -pthread -fvisibility=hidden -Wall -Wextra -Wvla -Wformat=2 -Winit-self -Wmissing-include-dirs -Wstrict-aliasing -Wfloat-equal -Wundef -Wshadow -Wpointer-arith -Wbad-function-cast -Wwrite-strings -Wlogical-op -Waggregate-return -Wstrict-prototypes -Wold-style-definition -Wmissing-prototypes -Wmissing-declarations -Wmissing-noreturn -Wredundant-decls -g -O2 -c -o xz-tuklib_mbstr_width.o `test -f '../common/tuklib_mbstr_width.c' || echo './'`../common/tuklib_mbstr_width.c\r\n riscv64-linux-g++ ... servls.cpp\r\n CC setlocale_null.o\r\nchecking for pthread_join in -lpthread... yes\r\nchecking for isblank... yes\r\nriscv64-linux-gcc -I. -DHAVE_CONFIG_H -g -O2 -ggdb3 -Wall -W -Wno-sign-compare -Wmissing-prototypes -Wmissing-declarations -Wstrict-prototypes -Wpointer-arith -Wbad-function-cast -Wnested-externs -fpic -c rsa-sec-compute-root.c \\\r\n&& true\r\n../arch/riscv/include/asm/vdso/gettimeofday.h: Assembler messages:\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a4,0xc01'\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a5,0xc01'\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a4,0xc01'\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a5,0xc01'\r\nmake[2]: *** [../scripts/Makefile.build:288: arch/riscv/kernel/vdso/vgettimeofday.o] Error 1\r\n/nix/store/fcd0m68c331j7nkdxvnnpb8ggwsaiqac-bash-5.1-p16/bin/bash ./libtool --tag=CC --mode=compile riscv64-linux-gcc -DHAVE_CONFIG_H -I. -g -O2 -c -o mips/mips_init.lo mips/mips_init.c\r\nEnabled Schematron support\r\nmake[1]: *** [../arch/riscv/Makefile:120: vdso_prepare] Error 2\r\nmake[1]: Leaving directory '/build/source/build'\r\nmake: *** [Makefile:219: __sub-make] Error 2\r\n/nix/store/fcd0m68c331j7nkdxvnnpb8ggwsaiqac-bash-5.1-p16/bin/bash ../libtool --tag=CC --mode=compile riscv64-linux-gcc -DHAVE_CONFIG_H -I. -I.. -I/nix/store/agic7qa5l02cfy2vyq2nabpg2dq6px1v-libgpg-error-riscv64-linux-1.42-dev/include -g -O2 -fvisibility=hidden -fno-delete-null-pointer-checks -Wall -c -o libgcrypt_la-global.lo `test -f 'global.c' || echo './'`global.c\r\nriscv64-linux-gcc -DHAVE_CONFIG_H -I. -I../.. -DLOCALEDIR=\\\"/nix/store/84q2jjw95gh7qy3iqvqb45jn2zbhvj88-xz-riscv64-linux-5.2.5/share/locale\\\" -I../../src/common -I../../src/liblzma/api -I../../lib -pthread -fvisibility=hidden -Wall -Wextra -Wvla -Wformat=2 -Winit-self -Wmissing-include-dirs -Wstrict-aliasing -Wfloat-equal -Wundef -Wshadow -Wpointer-arith -Wbad-function-cast -Wwrite-strings -Wlogical-op -Waggregate-return -Wstrict-prototypes -Wold-style-definition -Wmissing-prototypes -Wmissing-declarations -Wmissing-noreturn -Wredundant-decls -g -O2 -c -o xz-tuklib_mbstr_fw.o `test -f '../common/tuklib_mbstr_fw.c' || echo './'`../common/tuklib_mbstr_fw.c\r\nbuilder for '/nix/store/qbplv2xrhm7vykirys4p4fdpvs5l6vdz-linux-riscv64-linux-5.17.1-visionfive.drv' failed with exit code 2\r\ncannot build derivation '/nix/store/5ncfqz7m4nqhawfwdcib850dccd59p3b-nixos-system-nixos-22.05pre-git.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/ykl76jhdjahkhx22zk00pk26a7jrhg88-ext4-fs.img.zst-riscv64-linux.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/9b2w7mdbh54n82g3xy2xnfgzlij0m3mr-nixos-sd-image-22.05pre-git-riscv64-linux-visionfive.img-riscv64-linux.drv': 1 dependencies couldn't be built\r\nerror: build of '/nix/store/9b2w7mdbh54n82g3xy2xnfgzlij0m3mr-nixos-sd-image-22.05pre-git-riscv64-linux-visionfive.img-riscv64-linux.drv' failed\r\n```\r\n\r\nSame issue with linux-5.15.34 with no changes.\r\n```console\r\n LINK resolve_btfids\r\n LDS arch/riscv/kernel/vdso/vdso.lds\r\n AS arch/riscv/kernel/vdso/rt_sigreturn.o\r\n CC arch/riscv/kernel/vdso/vgettimeofday.o\r\n../arch/riscv/include/asm/vdso/gettimeofday.h: Assembler messages:\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a4,0xc01'\r\n../arch/riscv/include/asm/vdso/gettimeofday.h:71: Error: unrecognized opcode `csrr a4,0xc01'\r\nmake[2]: *** [../scripts/Makefile.build:277: arch/riscv/kernel/vdso/vgettimeofday.o] Error 1\r\nmake[1]: *** [../arch/riscv/Makefile:121: vdso_prepare] Error 2\r\nmake[1]: Leaving directory '/build/linux-5.15.34/build'\r\nmake: *** [Makefile:219: __sub-make] Error 2\r\nbuilder for '/nix/store/nbmmmcbrnrhr6c8hcznw0ybjzn55sj5b-linux-riscv64-unknown-linux-gnu-5.15.34.drv' failed with exit code 2\r\nerror: build of '/nix/store/nbmmmcbrnrhr6c8hcznw0ybjzn55sj5b-linux-riscv64-unknown-linux-gnu-5.15.34.drv' failed\r\n```\r\n\r\n### Expected behavior\r\nSuccessful (starfive variant) linux kernel cross compilation from x86_64 to risc64.\r\n\r\n### Additional context\r\nAttempting to build #168826\r\n\r\n### Notify maintainers\r\n@fabianhjr @mweinelt (https://github.com/NixOS/nixpkgs/pull/168737#issuecomment-1100713869)\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.20, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11, home-manager-21.11\"`\r\n - channels(mado): `\"home-manager-21.11, nixos-21.11.337100.7b38b03d76a, nixos-unstable-22.05pre369988.1ffba9f2f68\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169278/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169245","id":1207584921,"node_id":"I_kwDOAEVQ_M5H-kiZ","number":169245,"title":"nvidia-vaapi-driver requires kernel modesetting","user":{"login":"jessestricker","id":978183,"node_id":"MDQ6VXNlcjk3ODE4Mw==","avatar_url":"https://avatars.githubusercontent.com/u/978183?v=4","gravatar_id":"","url":"https://api.github.com/users/jessestricker","html_url":"https://github.com/jessestricker","followers_url":"https://api.github.com/users/jessestricker/followers","following_url":"https://api.github.com/users/jessestricker/following{/other_user}","gists_url":"https://api.github.com/users/jessestricker/gists{/gist_id}","starred_url":"https://api.github.com/users/jessestricker/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jessestricker/subscriptions","organizations_url":"https://api.github.com/users/jessestricker/orgs","repos_url":"https://api.github.com/users/jessestricker/repos","events_url":"https://api.github.com/users/jessestricker/events{/privacy}","received_events_url":"https://api.github.com/users/jessestricker/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-19T00:35:49Z","updated_at":"2022-04-20T14:56:45Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCommit 0326d67a58f58ddf6756f3df673bba5d2c9870da introduced support for VAAPI, \r\nbut when I tried to test this using `vainfo` from `libva-utils`, it failed.\r\n\r\n### Steps To Reproduce\r\n\r\n```\r\n$ NVD_LOG=1 nix shell nixpkgs#libva-utils -c vainfo\r\nlibva info: VA-API version 1.14.0\r\nlibva info: Trying to open /run/opengl-driver/lib/dri/nvidia_drv_video.so\r\nlibva info: Found init function __vaDriverInit_1_0\r\n[16546-16546] ../src/vabackend.c:1634 __vaDriverInit_1_0 Initialising NVIDIA VA-API Driver: 0xb29ee0\r\n[16546-16546] ../src/export-buf.c: 171 findCudaDisplay Found 3 EGL devices\r\n[16546-16546] ../src/export-buf.c: 175 findCudaDisplay Got EGL_CUDA_DEVICE_NV value '0' from device 0\r\n[16546-16546] ../src/export-buf.c: 135 checkModesetParameter Checking device file: /dev/dri/renderD128\r\n[16546-16546] ../src/export-buf.c: 145 checkModesetParameter ERROR: This driver requires the nvidia_drm.modeset kernel module parameter set to 1\r\nlibva error: /run/opengl-driver/lib/dri/nvidia_drv_video.so init failed\r\nlibva info: va_openDriver() returns 1\r\nvaInitialize failed with error code 1 (operation failed),exit\r\n```\r\n\r\n### Expected behavior\r\n\r\nAs this is a hard dependency, I expected *one* of the following:\r\n- `hardware.nvidia.modesetting.enable = true` should be set by default.\r\n- `hardware.opengl.extraPackages` does not contain `nvidia-vaapi-driver`\r\n\r\nA less satisfactory option is to merely document this somewhere, maybe in the [GPU](https://nixos.org/manual/nixos/stable/index.html#sec-gpu-accel) section of the manual\r\n\r\n### Notify maintainers\r\n@jonringer \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220417.1ffba9f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(jesse): `\"\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\nedit: second paragraph in *Expected behavior*","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169245/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169231","id":1207441172,"node_id":"I_kwDOAEVQ_M5H-BcU","number":169231,"title":"RFP: filestash - web-based file manager","user":{"login":"phaer","id":101753,"node_id":"MDQ6VXNlcjEwMTc1Mw==","avatar_url":"https://avatars.githubusercontent.com/u/101753?v=4","gravatar_id":"","url":"https://api.github.com/users/phaer","html_url":"https://github.com/phaer","followers_url":"https://api.github.com/users/phaer/followers","following_url":"https://api.github.com/users/phaer/following{/other_user}","gists_url":"https://api.github.com/users/phaer/gists{/gist_id}","starred_url":"https://api.github.com/users/phaer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/phaer/subscriptions","organizations_url":"https://api.github.com/users/phaer/orgs","repos_url":"https://api.github.com/users/phaer/repos","events_url":"https://api.github.com/users/phaer/events{/privacy}","received_events_url":"https://api.github.com/users/phaer/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-18T20:50:43Z","updated_at":"2022-04-18T20:50:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nDropbox-like file manager that let you manage your data anywhere it is located:\r\n[FTP](https://www.filestash.app/ftp-client.html) • FTPS • [SFTP](https://www.filestash.app/ssh-file-transfer.html) • [WebDAV](https://www.filestash.app/webdav-client.html) • Git • [S3](https://www.filestash.app/s3-browser.html) • [LDAP](https://www.filestash.app/ldap-browser.html) • Mysql\r\nCardDAV • CalDAV • Backblaze B2 • [Minio](https://www.filestash.app/s3-browser.html)\r\nDropbox • Google Drive\r\n\r\nTechnically it's a go-app with an nodejs/webpack/react-based frontend and quite a few external dependencies. See dockerfile at https://github.com/mickael-kerjean/filestash/blob/master/docker/Dockerfile\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.filestash.app/\r\n* source URL: https://github.com/mickael-kerjean/filestash\r\n* license: AGPLv3\r\n* platforms: unix, linux, darwin,\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169231/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169229","id":1207379622,"node_id":"I_kwDOAEVQ_M5H9yam","number":169229,"title":"harmonize lua wrapping across nixpkgs","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":1249449681,"node_id":"MDU6TGFiZWwxMjQ5NDQ5Njgx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20lua","name":"6.topic: lua","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"assignees":[{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-04-18T19:38:23Z","updated_at":"2022-04-18T19:38:24Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nOne problem is that handling of LUA_PATH across nixpkgs is very heterogeneous, and so it makes harder to make some global changes. I think it's heterogeneous partly because lua utilities are broken. For instance the LUA_PATH generation hook removes the defaults from the lua interpreter (\";;\"). Many modules hardcode the different lua paths instead of using e.g. wrapLuaProgram, luaPathList from pkgs/development/lua-modules/lib.nix . I believe wrapLuaProgram is broken so let's first fix this and add some tests. any help welcome.\r\n\r\n### Steps to reproduce\r\n\r\n\r\n\r\n## Technical details\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169229/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169227","id":1207369578,"node_id":"I_kwDOAEVQ_M5H9v9q","number":169227,"title":"xcodebuild segmentation fault on aarch64-darwin","user":{"login":"Congee","id":2083950,"node_id":"MDQ6VXNlcjIwODM5NTA=","avatar_url":"https://avatars.githubusercontent.com/u/2083950?v=4","gravatar_id":"","url":"https://api.github.com/users/Congee","html_url":"https://github.com/Congee","followers_url":"https://api.github.com/users/Congee/followers","following_url":"https://api.github.com/users/Congee/following{/other_user}","gists_url":"https://api.github.com/users/Congee/gists{/gist_id}","starred_url":"https://api.github.com/users/Congee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Congee/subscriptions","organizations_url":"https://api.github.com/users/Congee/orgs","repos_url":"https://api.github.com/users/Congee/repos","events_url":"https://api.github.com/users/Congee/events{/privacy}","received_events_url":"https://api.github.com/users/Congee/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-18T19:26:24Z","updated_at":"2022-04-20T14:55:18Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`xcodebuild` crashes outright with a xcode project. Can anyone provide some pointers for debugging?\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `git clone https://github.com/exelban/stats`\r\n2. `nix-shell -p xcodebuild`\r\n3. `xcodebuild`\r\n\r\n### Expected behavior\r\nIt should not ... crash\r\n\r\n### Screenshots\r\n<img width=\"754\" alt=\"image\" src=\"https://user-images.githubusercontent.com/2083950/163863408-6ab76d94-3e80-4058-9629-9ded80dfbd6c.png\">\r\n\r\n### Additional context\r\nIt fails for other projects. Stack trace is included. And, I don't have a native XCode.app installed, if this helps.\r\n\r\n<details><summary>crash log</summary>\r\n\r\n```\r\n-------------------------------------\r\nTranslated Report (Full Report Below)\r\n-------------------------------------\r\n\r\nProcess: xcbuild [50470]\r\nPath: /Volumes/VOLUME/*/xcbuild\r\nIdentifier: xcbuild\r\nVersion: ???\r\nCode Type: ARM-64 (Native)\r\nParent Process: zsh [50068]\r\nUser ID: 501\r\n\r\nDate/Time: 2022-04-18 15:06:13.0430 -0400\r\nOS Version: macOS 12.3.1 (21E258)\r\nReport Version: 12\r\nAnonymous UUID: 7BB02881-AEEA-5C75-7E0C-9FF7C4F633DC\r\n\r\nSleep/Wake UUID: 7FDC912A-6EB1-4331-836C-56098A7B579D\r\n\r\nTime Awake Since Boot: 330000 seconds\r\nTime Since Wake: 49482 seconds\r\n\r\nSystem Integrity Protection: enabled\r\n\r\nCrashed Thread: 0 Dispatch queue: com.apple.main-thread\r\n\r\nException Type: EXC_BAD_ACCESS (SIGSEGV)\r\nException Codes: KERN_INVALID_ADDRESS at 0x0000000000000038\r\nException Codes: 0x0000000000000001, 0x0000000000000038\r\nException Note: EXC_CORPSE_NOTIFY\r\n\r\nTermination Reason: Namespace SIGNAL, Code 11 Segmentation fault: 11\r\nTerminating Process: exc handler [50470]\r\n\r\nVM Region Info: 0x38 is not in any region. Bytes before following region: 4296294344\r\n REGION TYPE START - END [ VSIZE] PRT/MAX SHRMOD REGION DETAIL\r\n UNUSED SPACE AT START\r\n---> \r\n __TEXT 100144000-100150000 [ 48K] r-x/r-x SM=COW ...UME/*/xcbuild\r\n\r\nThread 0 Crashed:: Dispatch queue: com.apple.main-thread\r\n0 ??? \t 0x1004dba3c AddDependencies(DependenciesContext const&, std::__1::shared_ptr<pbxproj::PBX::Target> const&) + 192\r\n1 ??? \t 0x1004dbfd0 pbxbuild::Build::DependencyResolver::resolveLegacyDependencies(pbxbuild::Build::Context const&, bool, ext::optional<std::__1::vector<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> >, std::__1::allocator<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> > > > > const&) const + 240\r\n2 ??? \t 0x1004dbfd0 pbxbuild::Build::DependencyResolver::resolveLegacyDependencies(pbxbuild::Build::Context const&, bool, ext::optional<std::__1::vector<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> >, std::__1::allocator<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> > > > > const&) const + 240\r\n3 ??? \t 0x1003c7c74 xcexecution::Parameters::resolveDependencies(pbxbuild::Build::Environment const&, pbxbuild::Build::Context const&) const + 124\r\n4 ??? \t 0x1003caa74 xcexecution::SimpleExecutor::build(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*, pbxbuild::Build::Environment const&, xcexecution::Parameters const&) + 236\r\n5 ??? \t 0x10036d048 xcdriver::BuildAction::Run(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*, xcdriver::Options const&) + 1428\r\n6 ??? \t 0x10036a720 xcdriver::Driver::Run(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*) + 276\r\n7 ??? \t 0x10014fe94 main + 92\r\n8 dyld \t 0x100285088 start + 516\r\n\r\n\r\nThread 0 crashed with ARM Thread State (64-bit):\r\n x0: 0x000000016fcb77c8 x1: 0x000060000178a240 x2: 0x0000000000000000 x3: 0x00000001c2448ff8\r\n x4: 0x0000000000001200 x5: 0x0000000000000020 x6: 0x0000000000000000 x7: 0x000000016fcb8248\r\n x8: 0x00006000030ad458 x9: 0x0000000000000000 x10: 0x000060000178a580 x11: 0x00000000000007fd\r\n x12: 0x0000000000000035 x13: 0x00000000dc7f003a x14: 0x00000000dc9f0800 x15: 0x00000000000003e1\r\n x16: 0x0000000080000000 x17: 0x000000005c800000 x18: 0x0000000000000000 x19: 0x000060000178a240\r\n x20: 0x000000016fcb77c8 x21: 0x000060000178ff40 x22: 0x000000016fcb8768 x23: 0x000000016fcb7918\r\n x24: 0x0000600002cadc90 x25: 0x0000000000000000 x26: 0xffffffffffffffff x27: 0x0000000000000001\r\n x28: 0x000060000178ff00 fp: 0x000000016fcb77a0 lr: 0x00000001004dbfd0\r\n sp: 0x000000016fcb76e0 pc: 0x00000001004dba3c cpsr: 0x80001000\r\n far: 0x0000000000000038 esr: 0x92000006 (Data Abort) byte read Translation fault\r\n\r\nBinary Images:\r\n 0x0 - 0xffffffffffffffff ??? (*) <00000000-0000-0000-0000-000000000000> ???\r\n 0x100280000 - 0x1002dffff dyld (*) <fbb89662-e6f2-3434-b542-f75185ac5e74> /usr/lib/dyld\r\n\r\nExternal Modification Summary:\r\n Calls made by other processes targeting this process:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n Calls made by this process:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n Calls made by all processes on this machine:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n\r\nVM Region Summary:\r\nReadOnly portion of Libraries: Total=667.2M resident=0K(0%) swapped_out_or_unallocated=667.2M(100%)\r\nWritable regions: Total=804.4M written=0K(0%) resident=0K(0%) swapped_out=0K(0%) unallocated=804.4M(100%)\r\n\r\n VIRTUAL REGION \r\nREGION TYPE SIZE COUNT (non-coalesced) \r\n=========== ======= ======= \r\nActivity Tracing 256K 1 \r\nKernel Alloc Once 32K 1 \r\nMALLOC 172.2M 18 \r\nMALLOC guard page 96K 5 \r\nMALLOC_MEDIUM (reserved) 240.0M 2 reserved VM address space (unallocated)\r\nMALLOC_NANO (reserved) 384.0M 1 reserved VM address space (unallocated)\r\nSTACK GUARD 56.0M 1 \r\nStack 8176K 1 \r\n__AUTH 220K 44 \r\n__AUTH_CONST 2887K 122 \r\n__DATA 1291K 140 \r\n__DATA_CONST 4016K 147 \r\n__DATA_DIRTY 233K 50 \r\n__LINKEDIT 585.4M 27 \r\n__OBJC_CONST 260K 29 \r\n__OBJC_RO 82.9M 1 \r\n__OBJC_RW 3152K 1 \r\n__TEXT 81.8M 154 \r\n__UNICODE 592K 1 \r\ndyld private memory 1024K 1 \r\nshared memory 32K 2 \r\n=========== ======= ======= \r\nTOTAL 1.6G 749 \r\nTOTAL, minus reserved VM space 1000.0M 749 \r\n\r\n\r\n\r\n-----------\r\nFull Report\r\n-----------\r\n\r\n{\"app_name\":\"xcbuild\",\"timestamp\":\"2022-04-18 15:06:13.00 -0400\",\"app_version\":\"\",\"slice_uuid\":\"00000000-0000-0000-0000-000000000000\",\"build_version\":\"\",\"platform\":1,\"share_with_app_devs\":1,\"is_first_party\":1,\"bug_type\":\"309\",\"os_version\":\"macOS 12.3.1 (21E258)\",\"incident_id\":\"7A010F52-09D5-4E25-8479-979ACDE0914E\",\"name\":\"xcbuild\"}\r\n{\r\n \"uptime\" : 330000,\r\n \"procLaunch\" : \"2022-04-18 15:06:12.9970 -0400\",\r\n \"procRole\" : \"Unspecified\",\r\n \"version\" : 2,\r\n \"userID\" : 501,\r\n \"deployVersion\" : 210,\r\n \"modelCode\" : \"MacBookPro18,4\",\r\n \"procStartAbsTime\" : 7938146094408,\r\n \"coalitionID\" : 576,\r\n \"osVersion\" : {\r\n \"train\" : \"macOS 12.3.1\",\r\n \"build\" : \"21E258\",\r\n \"releaseType\" : \"User\"\r\n },\r\n \"captureTime\" : \"2022-04-18 15:06:13.0430 -0400\",\r\n \"incident\" : \"7A010F52-09D5-4E25-8479-979ACDE0914E\",\r\n \"bug_type\" : \"309\",\r\n \"pid\" : 50470,\r\n \"procExitAbsTime\" : 7938147186585,\r\n \"translated\" : false,\r\n \"cpuType\" : \"ARM-64\",\r\n \"procName\" : \"xcbuild\",\r\n \"procPath\" : \"\\/Volumes\\/VOLUME\\/*\\/xcbuild\",\r\n \"parentProc\" : \"zsh\",\r\n \"parentPid\" : 50068,\r\n \"coalitionName\" : \"net.kovidgoyal.kitty\",\r\n \"crashReporterKey\" : \"7BB02881-AEEA-5C75-7E0C-9FF7C4F633DC\",\r\n \"responsiblePid\" : 1392,\r\n \"wakeTime\" : 49482,\r\n \"sleepWakeUUID\" : \"7FDC912A-6EB1-4331-836C-56098A7B579D\",\r\n \"sip\" : \"enabled\",\r\n \"vmRegionInfo\" : \"0x38 is not in any region. Bytes before following region: 4296294344\\n REGION TYPE START - END [ VSIZE] PRT\\/MAX SHRMOD REGION DETAIL\\n UNUSED SPACE AT START\\n---> \\n __TEXT 100144000-100150000 [ 48K] r-x\\/r-x SM=COW ...UME\\/*\\/xcbuild\",\r\n \"isCorpse\" : 1,\r\n \"exception\" : {\"codes\":\"0x0000000000000001, 0x0000000000000038\",\"rawCodes\":[1,56],\"type\":\"EXC_BAD_ACCESS\",\"signal\":\"SIGSEGV\",\"subtype\":\"KERN_INVALID_ADDRESS at 0x0000000000000038\"},\r\n \"termination\" : {\"flags\":0,\"code\":11,\"namespace\":\"SIGNAL\",\"indicator\":\"Segmentation fault: 11\",\"byProc\":\"exc handler\",\"byPid\":50470},\r\n \"vmregioninfo\" : \"0x38 is not in any region. Bytes before following region: 4296294344\\n REGION TYPE START - END [ VSIZE] PRT\\/MAX SHRMOD REGION DETAIL\\n UNUSED SPACE AT START\\n---> \\n __TEXT 100144000-100150000 [ 48K] r-x\\/r-x SM=COW ...UME\\/*\\/xcbuild\",\r\n \"extMods\" : {\"caller\":{\"thread_create\":0,\"thread_set_state\":0,\"task_for_pid\":0},\"system\":{\"thread_create\":0,\"thread_set_state\":0,\"task_for_pid\":0},\"targeted\":{\"thread_create\":0,\"thread_set_state\":0,\"task_for_pid\":0},\"warnings\":0},\r\n \"faultingThread\" : 0,\r\n \"threads\" : [{\"triggered\":true,\"id\":4349594,\"threadState\":{\"x\":[{\"value\":6170572744},{\"value\":105553140949568},{\"value\":0},{\"value\":7554240504,\"symbolLocation\":0,\"symbol\":\"nanov2_free_definite_size\"},{\"value\":4608},{\"value\":32},{\"value\":0},{\"value\":6170575432},{\"value\":105553167307864},{\"value\":0},{\"value\":105553140950400},{\"value\":2045},{\"value\":53},{\"value\":3699310650},{\"value\":3701409792},{\"value\":993},{\"value\":2147483648},{\"value\":1551892480},{\"value\":0},{\"value\":105553140949568},{\"value\":6170572744},{\"value\":105553140973376},{\"value\":6170576744},{\"value\":6170573080},{\"value\":105553163115664},{\"value\":0},{\"value\":18446744073709551615},{\"value\":1},{\"value\":105553140973312}],\"flavor\":\"ARM_THREAD_STATE64\",\"lr\":{\"value\":4300062672},\"cpsr\":{\"value\":2147487744},\"fp\":{\"value\":6170572704},\"sp\":{\"value\":6170572512},\"esr\":{\"value\":2449473542,\"description\":\"(Data Abort) byte read Translation fault\"},\"pc\":{\"value\":4300061244,\"matchesCrashFrame\":1},\"far\":{\"value\":56}},\"queue\":\"com.apple.main-thread\",\"frames\":[{\"imageOffset\":4300061244,\"symbol\":\"AddDependencies(DependenciesContext const&, std::__1::shared_ptr<pbxproj::PBX::Target> const&)\",\"symbolLocation\":192,\"imageIndex\":0},{\"imageOffset\":4300062672,\"symbol\":\"pbxbuild::Build::DependencyResolver::resolveLegacyDependencies(pbxbuild::Build::Context const&, bool, ext::optional<std::__1::vector<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> >, std::__1::allocator<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> > > > > const&) const\",\"symbolLocation\":240,\"imageIndex\":0},{\"imageOffset\":4300062672,\"symbol\":\"pbxbuild::Build::DependencyResolver::resolveLegacyDependencies(pbxbuild::Build::Context const&, bool, ext::optional<std::__1::vector<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> >, std::__1::allocator<std::__1::basic_string<char, std::__1::char_traits<char>, std::__1::allocator<char> > > > > const&) const\",\"symbolLocation\":240,\"imageIndex\":0},{\"imageOffset\":4298931316,\"symbol\":\"xcexecution::Parameters::resolveDependencies(pbxbuild::Build::Environment const&, pbxbuild::Build::Context const&) const\",\"symbolLocation\":124,\"imageIndex\":0},{\"imageOffset\":4298943092,\"symbol\":\"xcexecution::SimpleExecutor::build(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*, pbxbuild::Build::Environment const&, xcexecution::Parameters const&)\",\"symbolLocation\":236,\"imageIndex\":0},{\"imageOffset\":4298559560,\"symbol\":\"xcdriver::BuildAction::Run(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*, xcdriver::Options const&)\",\"symbolLocation\":1428,\"imageIndex\":0},{\"imageOffset\":4298549024,\"symbol\":\"xcdriver::Driver::Run(process::User const*, process::Context const*, process::Launcher*, libutil::Filesystem*)\",\"symbolLocation\":276,\"imageIndex\":0},{\"imageOffset\":4296343188,\"symbol\":\"main\",\"symbolLocation\":92,\"imageIndex\":0},{\"imageOffset\":20616,\"symbol\":\"start\",\"symbolLocation\":516,\"imageIndex\":1}]}],\r\n \"usedImages\" : [\r\n {\r\n \"size\" : 0,\r\n \"source\" : \"A\",\r\n \"base\" : 0,\r\n \"uuid\" : \"00000000-0000-0000-0000-000000000000\"\r\n },\r\n {\r\n \"source\" : \"P\",\r\n \"arch\" : \"arm64e\",\r\n \"base\" : 4297588736,\r\n \"size\" : 393216,\r\n \"uuid\" : \"fbb89662-e6f2-3434-b542-f75185ac5e74\",\r\n \"path\" : \"\\/usr\\/lib\\/dyld\",\r\n \"name\" : \"dyld\"\r\n }\r\n],\r\n \"sharedCache\" : {\r\n \"base\" : 7552958464,\r\n \"size\" : 3136438272,\r\n \"uuid\" : \"1df3dfc1-141a-35d0-a4e5-f1e113894c6e\"\r\n},\r\n \"vmSummary\" : \"ReadOnly portion of Libraries: Total=667.2M resident=0K(0%) swapped_out_or_unallocated=667.2M(100%)\\nWritable regions: Total=804.4M written=0K(0%) resident=0K(0%) swapped_out=0K(0%) unallocated=804.4M(100%)\\n\\n VIRTUAL REGION \\nREGION TYPE SIZE COUNT (non-coalesced) \\n=========== ======= ======= \\nActivity Tracing 256K 1 \\nKernel Alloc Once 32K 1 \\nMALLOC 172.2M 18 \\nMALLOC guard page 96K 5 \\nMALLOC_MEDIUM (reserved) 240.0M 2 reserved VM address space (unallocated)\\nMALLOC_NANO (reserved) 384.0M 1 reserved VM address space (unallocated)\\nSTACK GUARD 56.0M 1 \\nStack 8176K 1 \\n__AUTH 220K 44 \\n__AUTH_CONST 2887K 122 \\n__DATA 1291K 140 \\n__DATA_CONST 4016K 147 \\n__DATA_DIRTY 233K 50 \\n__LINKEDIT 585.4M 27 \\n__OBJC_CONST 260K 29 \\n__OBJC_RO 82.9M 1 \\n__OBJC_RW 3152K 1 \\n__TEXT 81.8M 154 \\n__UNICODE 592K 1 \\ndyld private memory 1024K 1 \\nshared memory 32K 2 \\n=========== ======= ======= \\nTOTAL 1.6G 749 \\nTOTAL, minus reserved VM space 1000.0M 749 \\n\",\r\n \"legacyInfo\" : {\r\n \"threadTriggered\" : {\r\n \"queue\" : \"com.apple.main-thread\"\r\n }\r\n},\r\n \"trialInfo\" : {\r\n \"rollouts\" : [\r\n {\r\n \"rolloutId\" : \"60356660bbe37970735c5624\",\r\n \"factorPackIds\" : {\r\n\r\n },\r\n \"deploymentId\" : 240000027\r\n },\r\n {\r\n \"rolloutId\" : \"5fc94383418129005b4e9ae0\",\r\n \"factorPackIds\" : {\r\n\r\n },\r\n \"deploymentId\" : 240000334\r\n }\r\n ],\r\n \"experiments\" : [\r\n\r\n ]\r\n}\r\n}\r\n```\r\n</details>\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@copumpkin \r\n@matthewbauer \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 12.3.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(cwu): `\"\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169227/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169201","id":1207060965,"node_id":"I_kwDOAEVQ_M5H8knl","number":169201,"title":"GNOME 42: gnome-online-accounts fails to load any webkit view after upgrade","user":{"login":"hyphenrf","id":26802762,"node_id":"MDQ6VXNlcjI2ODAyNzYy","avatar_url":"https://avatars.githubusercontent.com/u/26802762?v=4","gravatar_id":"","url":"https://api.github.com/users/hyphenrf","html_url":"https://github.com/hyphenrf","followers_url":"https://api.github.com/users/hyphenrf/followers","following_url":"https://api.github.com/users/hyphenrf/following{/other_user}","gists_url":"https://api.github.com/users/hyphenrf/gists{/gist_id}","starred_url":"https://api.github.com/users/hyphenrf/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hyphenrf/subscriptions","organizations_url":"https://api.github.com/users/hyphenrf/orgs","repos_url":"https://api.github.com/users/hyphenrf/repos","events_url":"https://api.github.com/users/hyphenrf/events{/privacy}","received_events_url":"https://api.github.com/users/hyphenrf/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":13,"created_at":"2022-04-18T13:39:24Z","updated_at":"2022-04-25T06:03:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\ngoa will expire google account access tokens and not allow me to re-login after upgrading to 42.\r\nI've tried clearing everything goa-related from config and cache user dirs, to no avail. It keeps loading infinitely.\r\nRunning `gnome-control-center online-accounts` from the commandline and then picking the google account outputs this `error: bwrap: Can't mkdir parents for /run/current-system/sw/share/fonts: No such file or directory`\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. login to google via goa on 21.11\r\n2. change channel from 21.11 to unstable\r\n3. rebuild --upgrade\r\n\r\n### Screenshots\r\nThis is how it looks now when I click on google:\r\n\r\n\r\n\r\n### Additional context\r\ngnome-shell is running on wayland by default\r\nSince this seems to be touching fonts, here's my fonts config\r\n```nix\r\n{\r\n # ...\r\n fonts = {\r\n fonts = with pkgs; [ jetbrains-mono ];\r\n fontconfig.defaultFonts = {\r\n monospace = [ \"JetBrains Mono\" ];\r\n };\r\n };\r\n #...\r\n}\r\n```\r\n\r\n### Notify maintainers\r\n@bobby285271\r\n@hedning\r\n@jtojnar\r\n@dasj19\r\n@maxeaubrey\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369756.75ad56bdc92`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169201/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169193","id":1207001702,"node_id":"I_kwDOAEVQ_M5H8WJm","number":169193,"title":"git 2.35.2 breaks nixos-rebuild with flake repo owned by non-root user","user":{"login":"NickCao","id":15247171,"node_id":"MDQ6VXNlcjE1MjQ3MTcx","avatar_url":"https://avatars.githubusercontent.com/u/15247171?v=4","gravatar_id":"","url":"https://api.github.com/users/NickCao","html_url":"https://github.com/NickCao","followers_url":"https://api.github.com/users/NickCao/followers","following_url":"https://api.github.com/users/NickCao/following{/other_user}","gists_url":"https://api.github.com/users/NickCao/gists{/gist_id}","starred_url":"https://api.github.com/users/NickCao/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NickCao/subscriptions","organizations_url":"https://api.github.com/users/NickCao/orgs","repos_url":"https://api.github.com/users/NickCao/repos","events_url":"https://api.github.com/users/NickCao/events{/privacy}","received_events_url":"https://api.github.com/users/NickCao/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":20,"created_at":"2022-04-18T12:28:38Z","updated_at":"2022-04-29T11:17:07Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nAfter upgrading to git 2.35.2 (which is the version currently in nixos-unstable-small), running `sudo nixos-rebuild switch` with a flake repo owned by non-root user would result in a cryptic error message saying\r\n```\r\nwarning: Not a git repository. Use --no-index to compare two paths outside a working tree\r\nusage: git diff --no-index [<options>] <path> <path>\r\n...... (the full git diff help)\r\nerror: program 'git' failed with exit code 129\r\n(use '--show-trace' to show detailed location information)\r\n```\r\nThe underlying reason is that due to the fix for [CVE-2022-24765](https://github.blog/2022-04-12-git-security-vulnerability-announced/), git now effectively treats any directory not owned by the calling user as not a git repo. A temporary workaround would be to add the repo to `safe.directory` entry of the root user's git config. A possible long term fix is to only use `sudo` or others means for privilege elevation when absolutely required in `nixos-rebuild`.\r\n\r\n### Notify maintainers\r\n@Profpatsch \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220418.f26866c`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - nixpkgs: `/nix/store/xy6wkddgna3rsmqkb53120x8lpf1pbvr-source`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193/reactions","total_count":42,"+1":42,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169193/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169182","id":1206868123,"node_id":"I_kwDOAEVQ_M5H71ib","number":169182,"title":"SickGear is missing some \"optional\" dependencies","user":{"login":"joepie91","id":1663259,"node_id":"MDQ6VXNlcjE2NjMyNTk=","avatar_url":"https://avatars.githubusercontent.com/u/1663259?v=4","gravatar_id":"","url":"https://api.github.com/users/joepie91","html_url":"https://github.com/joepie91","followers_url":"https://api.github.com/users/joepie91/followers","following_url":"https://api.github.com/users/joepie91/following{/other_user}","gists_url":"https://api.github.com/users/joepie91/gists{/gist_id}","starred_url":"https://api.github.com/users/joepie91/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/joepie91/subscriptions","organizations_url":"https://api.github.com/users/joepie91/orgs","repos_url":"https://api.github.com/users/joepie91/repos","events_url":"https://api.github.com/users/joepie91/events{/privacy}","received_events_url":"https://api.github.com/users/joepie91/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-18T09:35:48Z","updated_at":"2022-04-18T09:35:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nA number of dependencies which are *technically* optional (but without which some features don't work) appear to be missing from the SickRage package:\r\n\r\n```\r\n2022-04-18 11:28:01 WARNING SUBLIMINAL :: Service tvsubtitles not available: none of available features could be used. One of ['lxml'] required\r\n2022-04-18 11:28:01 WARNING SUBLIMINAL :: Service addic7ed not available: none of available features could be used. One of ['lxml'] required\r\n```\r\n\r\n(Presumably this requires some Python `lxml` package?)\r\n\r\n```\r\n2022-04-17 03:47:13 SHOWUPDATER :: Failed to unpack archive: /var/lib/sickbeard/cache/alts/tmp/alt.rar with error: Cannot find working tool\r\n2022-04-17 03:47:13 SHOWUPDATER :: Failed to unpack json data: /var/lib/sickbeard/cache/alts/tmp/alt.rar with error: [Errno 2] No such file or directory: '/var/lib/sickbeard/cache/alts/alt.json'\r\n```\r\n\r\n(Presumably this requires `unrar`?)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install SickGear from nixpkgs\r\n2. Enable subtitle fetching\r\n3. Add a show with subtitles enabled\r\n4. Look at regular logs (for the subtitle warning) and error logs (for the rar error)\r\n\r\nI'm not entirely sure when or why SickGear fetches the `.rar` file, but I *think* the subtitle fetch is attempted when a show episode is being searched for.\r\n\r\n### Expected behavior\r\nFeatures should work out of the box.\r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\nN/A\r\n\r\n### Notify maintainers\r\n@rembo10 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.110, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(sven): `\"\"`\r\n - channels(root): `\"nixos-21.11.337090.0a862f558d4\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nNote: SickGear is installed from `unstable`, even though I am running stable.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169182/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169178","id":1206813048,"node_id":"I_kwDOAEVQ_M5H7oF4","number":169178,"title":"Print Screen not working in cinnamon desktop ","user":{"login":"kamalsomani","id":1288306,"node_id":"MDQ6VXNlcjEyODgzMDY=","avatar_url":"https://avatars.githubusercontent.com/u/1288306?v=4","gravatar_id":"","url":"https://api.github.com/users/kamalsomani","html_url":"https://github.com/kamalsomani","followers_url":"https://api.github.com/users/kamalsomani/followers","following_url":"https://api.github.com/users/kamalsomani/following{/other_user}","gists_url":"https://api.github.com/users/kamalsomani/gists{/gist_id}","starred_url":"https://api.github.com/users/kamalsomani/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kamalsomani/subscriptions","organizations_url":"https://api.github.com/users/kamalsomani/orgs","repos_url":"https://api.github.com/users/kamalsomani/repos","events_url":"https://api.github.com/users/kamalsomani/events{/privacy}","received_events_url":"https://api.github.com/users/kamalsomani/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1803518571,"node_id":"MDU6TGFiZWwxODAzNTE4NTcx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cinnamon","name":"6.topic: cinnamon","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-18T08:26:35Z","updated_at":"2022-04-20T18:49:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI am new to nixos...\r\nWhen I try to use printScr Key on keyboard. it not responding.\r\nnon of the printScreen optins working..\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ... press Key PrintScr\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nShould take a screen shot\r\nask for location to save to.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/6iw7yxcpsn4p7q2lf93n021gjzji8lbl-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/6iw7yxcpsn4p7q2lf93n021gjzji8lbl-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169178/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169150","id":1206582253,"node_id":"I_kwDOAEVQ_M5H6vvt","number":169150,"title":"Package request: curl-impersonate","user":{"login":"ivan","id":4458,"node_id":"MDQ6VXNlcjQ0NTg=","avatar_url":"https://avatars.githubusercontent.com/u/4458?v=4","gravatar_id":"","url":"https://api.github.com/users/ivan","html_url":"https://github.com/ivan","followers_url":"https://api.github.com/users/ivan/followers","following_url":"https://api.github.com/users/ivan/following{/other_user}","gists_url":"https://api.github.com/users/ivan/gists{/gist_id}","starred_url":"https://api.github.com/users/ivan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ivan/subscriptions","organizations_url":"https://api.github.com/users/ivan/orgs","repos_url":"https://api.github.com/users/ivan/repos","events_url":"https://api.github.com/users/ivan/events{/privacy}","received_events_url":"https://api.github.com/users/ivan/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-18T02:20:33Z","updated_at":"2022-04-18T02:22:38Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\nhttps://github.com/lwthiker/curl-impersonate is like curl, but doesn't get you blocked by cloudflare and other WAPs that insist you have the TLS fingerprint of a web browser.\r\n\r\n> A special compilation of [curl](https://github.com/curl/curl)[](https://github.com/lwthiker/curl-impersonate#why) that makes it impersonate real browsers. It can impersonate the four major browsers: Chrome, Edge, Safari & Firefox. This curl binary is able to perform a TLS handshake that is identical to that of a real browser.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/lwthiker/curl-impersonate\r\n* source URL: https://github.com/lwthiker/curl-impersonate\r\n* license: MIT\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169150/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169143","id":1206553130,"node_id":"I_kwDOAEVQ_M5H6ooq","number":169143,"title":"graphical-session.target does not start when running wayland sessions","user":{"login":"nrdxp","id":34083928,"node_id":"MDQ6VXNlcjM0MDgzOTI4","avatar_url":"https://avatars.githubusercontent.com/u/34083928?v=4","gravatar_id":"","url":"https://api.github.com/users/nrdxp","html_url":"https://github.com/nrdxp","followers_url":"https://api.github.com/users/nrdxp/followers","following_url":"https://api.github.com/users/nrdxp/following{/other_user}","gists_url":"https://api.github.com/users/nrdxp/gists{/gist_id}","starred_url":"https://api.github.com/users/nrdxp/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nrdxp/subscriptions","organizations_url":"https://api.github.com/users/nrdxp/orgs","repos_url":"https://api.github.com/users/nrdxp/repos","events_url":"https://api.github.com/users/nrdxp/events{/privacy}","received_events_url":"https://api.github.com/users/nrdxp/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-18T01:24:13Z","updated_at":"2022-04-20T14:53:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe graphical-session.target systemd user target doesn't seem to get started when running a session from a display manager (in my case GDM), if that session is wayland based. Looks like the reason is that this is usually started from the [xsession wrapper script](https://github.com/NixOS/nixpkgs/blob/fd609f92336b4c1677697b09202cfc1439f35aec/nixos/modules/services/x11/display-managers/default.nix#L90), which obviously doesn't play a role in wayland sessions.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\nEasiest way to reproduce might be enable GDM and Sway and start a session. Then just confirm with `systemctl --user status graphical-session.target`.\r\n\r\n### Expected behavior\r\nShould work the same way as in an X session, that is `graphical-session.target` is started on a new session and stopped on session exit, allow user units which are wanted by the graphical-session to also start and stop as expected on session starts and restarts.\r\n\r\n### Additional Context\r\nAt least according to the [docs for GDM](https://help.gnome.org/admin/gdm/stable/configuration.html.en), there are PreSession and PostSession script facilities which sound like they might be just what we need. It would be much better, however, to able to implement this in a display manager agnostic way. Still, if we have to implement it as a GDM only feature initially, that's much better than nothing imho.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169143/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169128","id":1206516376,"node_id":"I_kwDOAEVQ_M5H6fqY","number":169128,"title":"wireguard: peer endpoints are set after the opportunities to set DNS configuration","user":{"login":"nagisa","id":679122,"node_id":"MDQ6VXNlcjY3OTEyMg==","avatar_url":"https://avatars.githubusercontent.com/u/679122?v=4","gravatar_id":"","url":"https://api.github.com/users/nagisa","html_url":"https://github.com/nagisa","followers_url":"https://api.github.com/users/nagisa/followers","following_url":"https://api.github.com/users/nagisa/following{/other_user}","gists_url":"https://api.github.com/users/nagisa/gists{/gist_id}","starred_url":"https://api.github.com/users/nagisa/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nagisa/subscriptions","organizations_url":"https://api.github.com/users/nagisa/orgs","repos_url":"https://api.github.com/users/nagisa/repos","events_url":"https://api.github.com/users/nagisa/events{/privacy}","received_events_url":"https://api.github.com/users/nagisa/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-17T23:57:10Z","updated_at":"2022-04-20T14:53:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe units generated by the `networking.wireguard` set-up disallow using DNS service provided by the peer and connecting to peers using a domain address, rather than an IP.\r\n\r\nA typical attempt to achieve this might look like this:\r\n\r\n```nix\r\n{\r\n networking.wireguard = {\r\n enable = true;\r\n interfaces.wg0 = {\r\n postSetup = ''echo \"nameserver 192.168.2.1\" | ${pkgs.openresolv}/bin/resolvconf -x -m 0 -a wg0'';\r\n postShutdown = \"${pkgs.openresolv}/bin/resolvconf -f -d wg0\";\r\n peers = [{\r\n endpoint = \"wg.example.com:12345\";\r\n allowedIPs = [\"0.0.0.0/0\"];\r\n }];\r\n };\r\n };\r\n}\r\n```\r\n\r\nHowever here the sequence of operations will be:\r\n\r\n1. `ip link add dev wg0 type wireguard`\r\n2. Set up the nameserver\r\n3. `wg set wg0 peer \"...\" endpoint \"wg.example.com:12345\"`\r\n\r\nHere resolving the wg.example.com will naturally fail, since it cannot be resolved anymore.\r\n\r\nInstead the setup should provide an (easy) way to tie some setup to a specific peer – and it needs to work with the `dynamicEndpointRefreshSeconds` functionality too. For initial set-up I'd imagine the flow needs to look like this (this is also what wg-quick does)\r\n\r\n1. `ip link add dev wg0 type wireguard`\r\n2. `wg set wg0 peer \"...\" endpoint \"wg.example.com:12345\"`\r\n3. Set up the nameserver.\r\n\r\nand for the refreshes it might make sense to first try resolving with the DNS server that has been set-up and failing that recreate the peer from scratch (which would involve removing the peer, unsetting the DNS settings tied to it, and recreating it.)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169128/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169126","id":1206513305,"node_id":"I_kwDOAEVQ_M5H6e6Z","number":169126,"title":"Ability to intermix impurely installed VSCode extensions with vscode-with-extensions/vscode-extensions.* packages","user":{"login":"PAI5REECHO","id":96688573,"node_id":"U_kgDOBcNZvQ","avatar_url":"https://avatars.githubusercontent.com/u/96688573?v=4","gravatar_id":"","url":"https://api.github.com/users/PAI5REECHO","html_url":"https://github.com/PAI5REECHO","followers_url":"https://api.github.com/users/PAI5REECHO/followers","following_url":"https://api.github.com/users/PAI5REECHO/following{/other_user}","gists_url":"https://api.github.com/users/PAI5REECHO/gists{/gist_id}","starred_url":"https://api.github.com/users/PAI5REECHO/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PAI5REECHO/subscriptions","organizations_url":"https://api.github.com/users/PAI5REECHO/orgs","repos_url":"https://api.github.com/users/PAI5REECHO/repos","events_url":"https://api.github.com/users/PAI5REECHO/events{/privacy}","received_events_url":"https://api.github.com/users/PAI5REECHO/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-17T23:38:08Z","updated_at":"2022-04-20T15:39:22Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'd like to be able to install [Live Share](https://marketplace.visualstudio.com/items?itemName=MS-vsliveshare.vsliveshare) without having to use `vscode-with-extensions` to explicitly declare all extensions the I use. Using `vscode-with-extensions` is extremely annoying, I don't want to have to restart my VSCode every time I install or remove an extensions. I prefer the impure way when they just work already. It'd be nice if I could just grab extensions that require fixes to work (like live share) from the `vscode-extensions.*` packages and use them in my current installation. For now I'm just getting the output path of the Live Share extension from Nixpkgs and symlinking it to my home folder:\r\n```console\r\n$ env NIXPKGS_ALLOW_UNFREE=1 nix show-derivation --impure nixpkgs#vscode-extensions.ms-vsliveshare.vsliveshare | jq -r '.[].outputs.out.path'\r\n/nix/store/gdj9l1pxgfy8zb9vycghijm5ahhpj1kz-vscode-extension-ms-vsliveshare-vsliveshare-1.0.5043\r\n$ trash ~/.vscode/extensions/ms-vsliveshare.vsliveshare-*\r\n$ ln -s /nix/store/gdj9l1pxgfy8zb9vycghijm5ahhpj1kz-vscode-extension-ms-vsliveshare-vsliveshare-1.0.5043/share/vscode/extensions/ms-vsliveshare.vsliveshare/ ~/.vscode/extensions/ms-vsliveshare.vsliveshare-1.0.5527\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install [Live Share](https://marketplace.visualstudio.com/items?itemName=MS-vsliveshare.vsliveshare)\r\n2. Join collaboration session\r\n3. Observe error when running extension\r\n\r\n### Expected behavior\r\nShould be able to use `vscode-with-extensions` in addition to plugins installed impurely\r\n\r\n### Notify maintainers\r\n@jraygauthier @deviant @eadwu @synthetica @maxeaubrey @bobby285271\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220330.710fed5`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220401_bf48959`\r\n - channels(root): `\"nixos\"`\r\n - channels(somebody): `\"hm-21.05.tar.gz, home-manager-21.05.tar.gz, nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169126/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169118","id":1206502520,"node_id":"I_kwDOAEVQ_M5H6cR4","number":169118,"title":"nixpkgs podman and qemu on darwin don't play well together","user":{"login":"zaphar","id":40631,"node_id":"MDQ6VXNlcjQwNjMx","avatar_url":"https://avatars.githubusercontent.com/u/40631?v=4","gravatar_id":"","url":"https://api.github.com/users/zaphar","html_url":"https://github.com/zaphar","followers_url":"https://api.github.com/users/zaphar/followers","following_url":"https://api.github.com/users/zaphar/following{/other_user}","gists_url":"https://api.github.com/users/zaphar/gists{/gist_id}","starred_url":"https://api.github.com/users/zaphar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zaphar/subscriptions","organizations_url":"https://api.github.com/users/zaphar/orgs","repos_url":"https://api.github.com/users/zaphar/repos","events_url":"https://api.github.com/users/zaphar/events{/privacy}","received_events_url":"https://api.github.com/users/zaphar/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-17T22:37:26Z","updated_at":"2022-04-20T14:52:52Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nOn darwin `podman machine` requires qemu to be installed. It also assumes that qemu has either been installed from source or via brew. This results in error messages where podman can't find the edk2 file.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install both podman and qemu using nix.\r\n2. run `podman machine init test`\r\n3. run `podman machine start test`\r\n\r\n### Expected behavior\r\nTo see a successfully started virtual machine. Instead you will see the following:\r\n\r\n```sh\r\n$> podman machine init test ~\r\nExtracting compressed file\r\nImage resized.\r\nMachine init complete\r\nTo start your machine run:\r\n\r\n\tpodman machine start test\r\n$> podman machine start test ~\r\nStarting machine \"test\"\r\nINFO[0000] waiting for clients...\r\nINFO[0000] new connection from to /var/folders/z4/0zhrndk13bxd8jdrz_51h75c0000gn/T/podman/qemu_test.sock\r\nWaiting for VM ...\r\nqemu-system-aarch64: -drive file=edk2-aarch64-code.fd,if=pflash,format=raw,readonly=on: Could not open 'edk2-aarch64-code.fd': No such file or directory\r\nError: dial unix /var/folders/z4/0zhrndk13bxd8jdrz_51h75c0000gn/T/podman/test_ready.sock: connect: connection refused\r\nERRO[0003] cannot receive packets from , disconnecting: cannot read size from socket: EOF\r\n```\r\n\r\n\r\n### Additional context\r\n\r\nFor context the issue in podman appears to be this: https://github.com/containers/podman/blob/main/pkg/machine/qemu/options_darwin_arm64.go#L47 . It would be possible to work around this by modifying by modifying the appropriate machine configuration in `~/.config/containers/podman/machine/qemu/${name}.json` but that would require there to be a known good location for the edk2 file to live and right now it's only in the store path for qemu and that can change over time. Ideally the quemu `share` path would be put in the profile and podman would be patched to search the current nixos profile path for qemu instead.\r\n\r\nAs it is if you want to use podman and qemu on darwin then qemu can't be installed via nix it would have to installed via brew intead.\r\n\r\n### Notify maintainers\r\n@zowoq @marsam \r\n\r\n### Metadata\r\n```sh\r\nnix-shell -p nix-info --run \"nix-info -m\" ~\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixpkgs\"`\r\n - channels(zaphar): `\"darwin\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n ```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169118/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169115","id":1206495829,"node_id":"I_kwDOAEVQ_M5H6apV","number":169115,"title":"github-cli writes absoloute executable store path to gitconfig","user":{"login":"klemensn","id":91517496,"node_id":"U_kgDOBXRyOA","avatar_url":"https://avatars.githubusercontent.com/u/91517496?v=4","gravatar_id":"","url":"https://api.github.com/users/klemensn","html_url":"https://github.com/klemensn","followers_url":"https://api.github.com/users/klemensn/followers","following_url":"https://api.github.com/users/klemensn/following{/other_user}","gists_url":"https://api.github.com/users/klemensn/gists{/gist_id}","starred_url":"https://api.github.com/users/klemensn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/klemensn/subscriptions","organizations_url":"https://api.github.com/users/klemensn/orgs","repos_url":"https://api.github.com/users/klemensn/repos","events_url":"https://api.github.com/users/klemensn/events{/privacy}","received_events_url":"https://api.github.com/users/klemensn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-04-17T22:01:08Z","updated_at":"2022-04-18T19:32:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\nUsing `gh` to authenticate and pull via HTTPS installs credential helpers\ncontaining absoloute `/nix/store/.../bin/gh` in my `~/.gitconfig`:\n```console\n[credential \"https://github.com\"]\n\thelper = \n\thelper = !/nix/store/0zbc2qcqiy332bd25y2cmj3mwv0gzdhv-gh-2.6.0/bin/gh auth git-credential\n[credential \"https://gist.github.com\"]\n\thelper = \n\thelper = !/nix/store/0zbc2qcqiy332bd25y2cmj3mwv0gzdhv-gh-2.6.0/bin/gh auth git-credential\n```\n\nThis will work until I garbage collect version 2.6.0.\n```console\n(set -x; readlink `which gh`)\n++ which gh\n+ readlink /run/current-system/sw/bin/gh\n/nix/store/ib0k4ghxrxrrb34wfxxwinp3rzp3z175-gh-2.7.0/bin/gh\n```\n\n### Steps To Reproduce\n1. Run `$ gh auth login` and successfully login (via HTTPS)\n\n### Expected behavior\nStore paths must not be used, instead `PATH` lookup or perhaps some \"constant\"\nabsoloute path should be used.\n\n### Notify maintainers\n@zowoq\n\n### Metadata\n```console\n - system: `\"x86_64-linux\"`\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05pre368234.fd364d26885`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - channels(root): `\"nixos\"`\n - channels(kn): `\"nixos\"`\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169115/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169073","id":1206422846,"node_id":"I_kwDOAEVQ_M5H6I0-","number":169073,"title":"Pipenv: No module named 'jnius'","user":{"login":"ifurther","id":55025025,"node_id":"MDQ6VXNlcjU1MDI1MDI1","avatar_url":"https://avatars.githubusercontent.com/u/55025025?v=4","gravatar_id":"","url":"https://api.github.com/users/ifurther","html_url":"https://github.com/ifurther","followers_url":"https://api.github.com/users/ifurther/followers","following_url":"https://api.github.com/users/ifurther/following{/other_user}","gists_url":"https://api.github.com/users/ifurther/gists{/gist_id}","starred_url":"https://api.github.com/users/ifurther/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ifurther/subscriptions","organizations_url":"https://api.github.com/users/ifurther/orgs","repos_url":"https://api.github.com/users/ifurther/repos","events_url":"https://api.github.com/users/ifurther/events{/privacy}","received_events_url":"https://api.github.com/users/ifurther/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-17T16:26:39Z","updated_at":"2022-04-20T14:52:29Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\n`Traceback (most recent call last):\n File \"/nix/store/z4sd700l05shq1z72g21w0fav2xs955d-pipenv-2022.1.8/lib/python3.9/site-packages/pipenv/vendor/platformdirs/android.py\", line 83, in _android_folder\n from jnius import autoclass # noqa: SC200\nModuleNotFoundError: No module named 'jnius'`\n\n### Expected behavior\nThe error is belong in pipenv using jnius on Android. \n\n\n### Notify maintainers\n<!--\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\nIf in doubt, check `git blame` for whoever last touched something.\n-->\n\n### Metadata\n - system: `\"aarch64-linux\"`\n - host os: `Linux 3.10.84-perf-g39a29a8`\n - multi-user?: `no`\n - sandbox: `no`\n - version: `nix-env (Nix) 2.3.16`\n - channels(nix-on-droid): `\"home-manager-21.11, nix-on-droid-21.11, nixpkgs-21.11.337090.0a862f558d4\"`\n - nixpkgs: `/data/data/com.termux.nix/files/home/.nix-defexpr/channels/nixpkgs`\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169073/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169070","id":1206419299,"node_id":"I_kwDOAEVQ_M5H6H9j","number":169070,"title":"unable to build devicetree overlays","user":{"login":"flokli","id":183879,"node_id":"MDQ6VXNlcjE4Mzg3OQ==","avatar_url":"https://avatars.githubusercontent.com/u/183879?v=4","gravatar_id":"","url":"https://api.github.com/users/flokli","html_url":"https://github.com/flokli","followers_url":"https://api.github.com/users/flokli/followers","following_url":"https://api.github.com/users/flokli/following{/other_user}","gists_url":"https://api.github.com/users/flokli/gists{/gist_id}","starred_url":"https://api.github.com/users/flokli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/flokli/subscriptions","organizations_url":"https://api.github.com/users/flokli/orgs","repos_url":"https://api.github.com/users/flokli/repos","events_url":"https://api.github.com/users/flokli/events{/privacy}","received_events_url":"https://api.github.com/users/flokli/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-17T16:10:20Z","updated_at":"2022-04-20T14:52:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"I'm not sure if it never worked with the in-nixpkgs tooling, or if it recently regressed - but I'm unable to build a closure with the following device tree overlay:\r\n\r\n```nix\r\n hardware.deviceTree.overlays = [{\r\n name = \"onboard-wifi\";\r\n dtsText = ''\r\n /dts-v1/;\r\n /plugin/;\r\n\r\n / {\r\n compatible = \"pine64,pine64-plus\", \"allwinner,sun50i-a64\";\r\n\r\n fragment@0 {\r\n target = <&mmc1>;\r\n __overlay__ {\r\n pinctrl-names = \"default\";\r\n pinctrl-0 = <&mmc1_pins>;\r\n vmmc-supply = <®_dldo4>;\r\n vqmmc-supply = <®_eldo1>;\r\n mmc-pwrseq = <&wifi_pwrseq>;\r\n non-removable;\r\n bus-width = <4>;\r\n status = \"okay\";\r\n };\r\n };\r\n\r\n wifi_pwrseq: wifi_pwrseq {\r\n compatible = \"mmc-pwrseq-simple\";\r\n reset-gpios = <&r_pio 0 2 1>; /* PL2 */\r\n //^ GPIO_ACTIVE_LOW\r\n };\r\n };\r\n '';\r\n }];\r\n```\r\n\r\nThe derivation fails to build with the following error message:\r\n\r\n```\r\nError at 'compatible': FDT_ERR_NOTFOUND\r\nerror: build of '/nix/store/9kxhd9z88q5fi991x49fc2lskrbcysid-device-tree-overlays.drv' on 'ssh://flokli@aarch64.nixos.community' failed: error: builder for '/nix/store/9kxhd9z88q5fi991x49fc2lskrbcysid-device-tree-overlays.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > './hisilicon/hi6220-hikey.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./hisilicon/hi6220-hikey.dtb'\r\n > './hisilicon/hip05-d02.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./hisilicon/hip05-d02.dtb'\r\n > ./socionext -> /nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext\r\n > './socionext/uniphier-ld20-global.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-ld20-global.dtb'\r\n > './socionext/uniphier-ld11-global.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-ld11-global.dtb'\r\n > './socionext/uniphier-ld20-ref.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-ld20-ref.dtb'\r\n > './socionext/uniphier-pxs3-ref.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-pxs3-ref.dtb'\r\n > './socionext/uniphier-ld20-akebi96.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-ld20-akebi96.dtb'\r\n > './socionext/uniphier-ld11-ref.dtb' -> '/nix/store/zspkrzkfvbp66m48p1r7nnb0sdqi78jz-device-tree-overlays/./socionext/uniphier-ld11-ref.dtb'\r\n > Error at 'compatible': FDT_ERR_NOTFOUND\r\n For full logs, run 'nix log /nix/store/9kxhd9z88q5fi991x49fc2lskrbcysid-device-tree-overlays.drv'.\r\n```\r\n\r\nRelated: https://github.com/NixOS/nixpkgs/pull/79370\r\n\r\ncc @leifhelm @sorki @kwohlfahrt @samueldr ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169070/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169056","id":1206392668,"node_id":"I_kwDOAEVQ_M5H6Bdc","number":169056,"title":"Apparmor tools are broken (aa-genprof, aa-logprof, ...)","user":{"login":"wyndon","id":72203260,"node_id":"MDQ6VXNlcjcyMjAzMjYw","avatar_url":"https://avatars.githubusercontent.com/u/72203260?v=4","gravatar_id":"","url":"https://api.github.com/users/wyndon","html_url":"https://github.com/wyndon","followers_url":"https://api.github.com/users/wyndon/followers","following_url":"https://api.github.com/users/wyndon/following{/other_user}","gists_url":"https://api.github.com/users/wyndon/gists{/gist_id}","starred_url":"https://api.github.com/users/wyndon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wyndon/subscriptions","organizations_url":"https://api.github.com/users/wyndon/orgs","repos_url":"https://api.github.com/users/wyndon/repos","events_url":"https://api.github.com/users/wyndon/events{/privacy}","received_events_url":"https://api.github.com/users/wyndon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-17T14:38:38Z","updated_at":"2022-04-17T14:38:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA lot of apparmor tools doesn't work because they can't find a python module.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `security.apparmor.enable = true;`\r\n2. `aa-genprof`\r\n\r\n### Expected behavior\r\nThey should work.\r\n\r\n### Additional context\r\n```console\r\n[user@system:~]$ aa-genprof\r\nTraceback (most recent call last):\r\n File \"/nix/store/37a49x53whgrnw3552cg7qik9wnj9mjp-apparmor-utils-3.0.4/bin/.aa-genprof-wrapped\", line 22, in <module>\r\n import apparmor.aa as apparmor\r\nModuleNotFoundError: No module named 'apparmor'\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@joachifm @julm @thoughtpolice\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.27-xanmod1-tt, NixOS, 22.05 (Quokka), 22.05.20220416.75ad56b`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/store/ps3i3zj8c9swr3a39kybnsv7ys0pw1p3-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169056/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169044","id":1206355174,"node_id":"I_kwDOAEVQ_M5H54Tm","number":169044,"title":"`rescursiveUpdateUntil` tries to merge non-set types","user":{"login":"DavHau","id":42246742,"node_id":"MDQ6VXNlcjQyMjQ2NzQy","avatar_url":"https://avatars.githubusercontent.com/u/42246742?v=4","gravatar_id":"","url":"https://api.github.com/users/DavHau","html_url":"https://github.com/DavHau","followers_url":"https://api.github.com/users/DavHau/followers","following_url":"https://api.github.com/users/DavHau/following{/other_user}","gists_url":"https://api.github.com/users/DavHau/gists{/gist_id}","starred_url":"https://api.github.com/users/DavHau/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/DavHau/subscriptions","organizations_url":"https://api.github.com/users/DavHau/orgs","repos_url":"https://api.github.com/users/DavHau/repos","events_url":"https://api.github.com/users/DavHau/events{/privacy}","received_events_url":"https://api.github.com/users/DavHau/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-17T11:52:08Z","updated_at":"2022-04-19T22:55:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`recursiveUpdateUntil` seems to naively merge values which are not sets and therefore fails.\r\n\r\n### Steps To Reproduce\r\n```\r\nnix-repl> :lf nixpkgs\r\nnix-repl> lib.recursiveUpdateUntil (path: l: r: false) {foo = 1;} {foo = 2;}\r\nerror: value is an integer while a set was expected\r\n```\r\n\r\n### Expected behavior\r\n```\r\nnix-repl> :lf nixpkgs\r\nnix-repl> lib.recursiveUpdateUntil (path: l: r: false) {foo = 1;} {foo = 2;}\r\n{foo = 1;}\r\n```\r\n\r\n### Additional context\r\n`recursiveUpdate` (without `Until`), does not have that problem and stops the recursion if something is not a set.\r\n\r\nI propse that either:\r\n - the documentation of `recusiveUpdateUntil` should be updated to clearly state that the user needs to take care of stopping the recursion in any case\r\n - or `recursiveUpdateUntil` is updated to stop recursion when encountering anything else than an attrset, so it will behave similar to `recursiveUpdate`.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@nbp @infinisil\r\n### Metadata\r\n\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.110, NixOS, 21.11 (Porcupine), 21.11.20220413.a62ce97`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220318_963b8aa`\r\n - channels(root): `\"nixos-22.05pre353535.48d63e924a2\"`\r\n - nixpkgs: `/nix/store/ps3i3zj8c9swr3a39kybnsv7ys0pw1p3-source`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169044/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169040","id":1206340385,"node_id":"I_kwDOAEVQ_M5H50sh","number":169040,"title":"Teamviewer panic on Steam Deck and Ubuntu","user":{"login":"vegabook","id":3780883,"node_id":"MDQ6VXNlcjM3ODA4ODM=","avatar_url":"https://avatars.githubusercontent.com/u/3780883?v=4","gravatar_id":"","url":"https://api.github.com/users/vegabook","html_url":"https://github.com/vegabook","followers_url":"https://api.github.com/users/vegabook/followers","following_url":"https://api.github.com/users/vegabook/following{/other_user}","gists_url":"https://api.github.com/users/vegabook/gists{/gist_id}","starred_url":"https://api.github.com/users/vegabook/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vegabook/subscriptions","organizations_url":"https://api.github.com/users/vegabook/orgs","repos_url":"https://api.github.com/users/vegabook/repos","events_url":"https://api.github.com/users/vegabook/events{/privacy}","received_events_url":"https://api.github.com/users/vegabook/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-17T10:36:28Z","updated_at":"2022-04-22T12:31:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nTeamviewer core dump when trying to start it up\r\n\r\n\r\n### Steps to reproduce\r\n```\r\n(134)(deck@steamdeck etc)$ nix-env --version\r\nnix-env (Nix) 2.7.0\r\n```\r\n\r\n```\r\n(deck@steamdeck etc)$ env | grep NIX\r\nNIXPKGS_ALLOW_UNFREE=1\r\nNIX_PROFILES=/nix/var/nix/profiles/default /home/deck/.nix-profile\r\nNIX_SSL_CERT_FILE=/etc/ssl/certs/ca-certificates.crt\r\n```\r\n\r\n```\r\n(deck@steamdeck etc)$ nix-env -iA nixpkgs.teamviewer\r\ninstalling 'teamviewer-15.26.4'\r\nbuilding '/nix/store/nsci1hpb9r1crx8a2hj3iw3ijzg9fsfa-user-environment.drv'...\r\n\r\n\r\n(deck@steamdeck etc)$ teamviewer\r\n\r\nInit...\r\nxprop: /usr/lib/libc.so.6: version `GLIBC_2.34' not found (required by /nix/store/0np4qysvv5v05w49bs3ii123gckd4n0b-libX11-1.7.2/lib/libX11.so.6)\r\nCheckCPU: SSE2 support: yes\r\nChecking setup...\r\nLaunching TeamViewer ...\r\nStarting network process (no daemon)\r\nNetwork process already started (or error)\r\nLaunching TeamViewer GUI ...\r\nAborted (core dumped)\r\n\r\n```\r\n\r\nJust FYI:\r\n\r\n```\r\n(deck@steamdeck etc)$ pacman -Qi glibc | grep Version\r\nVersion : 2.33-5\r\n```\r\n\r\n\r\n## Technical details\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n```\r\n(1)(deck@steamdeck etc)$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.13.0-valve10.1-1-neptune-02144-g7fffaf925dfb, SteamOS, noversion, 20220227.3`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(deck): `\"nixpkgs\"`\r\n - nixpkgs: `/home/deck/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n\r\n## EDIT: same problem on Ubuntu 22.04\r\n\r\n```\r\ntbrowne@nd2204:~$ teamviewer\r\n\r\nInit...\r\nCheckCPU: SSE2 support: yes\r\nChecking setup...\r\nLaunching TeamViewer ...\r\nStarting network process (no daemon)\r\nNetwork process already started (or error)\r\nLaunching TeamViewer GUI ...\r\nAborted (core dumped)\r\n\r\n\r\ntbrowne@nd2204:~$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese 5 paths will be fetched (0.55 MiB download, 2.68 MiB unpacked):\r\n /nix/store/7j34mspj2frysf64igawwai4lbpsi9wq-bash-interactive-5.1-p16-info\r\n /nix/store/cj898w82i3kbd2k8djs5ziyzlgpnvrdb-bash-interactive-5.1-p16-man\r\n /nix/store/jx971k1cp21nfb842jwy4camssl3k6l6-nix-info\r\n /nix/store/rpd8ps4hv6q9vdj4w0p4v9nhiva63vp5-bash-interactive-5.1-p16-doc\r\n /nix/store/vkv057i6d4h2sw3ym8m76j193d54vi5d-bash-interactive-5.1-p16-dev\r\ncopying path '/nix/store/rpd8ps4hv6q9vdj4w0p4v9nhiva63vp5-bash-interactive-5.1-p16-doc' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vkv057i6d4h2sw3ym8m76j193d54vi5d-bash-interactive-5.1-p16-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7j34mspj2frysf64igawwai4lbpsi9wq-bash-interactive-5.1-p16-info' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/cj898w82i3kbd2k8djs5ziyzlgpnvrdb-bash-interactive-5.1-p16-man' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/jx971k1cp21nfb842jwy4camssl3k6l6-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.0-25-generic, Ubuntu, 22.04 (Jammy Jellyfish), nobuild`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(tbrowne): `\"nixpkgs\"`\r\n - nixpkgs: `/home/tbrowne/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169040/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169034","id":1206334181,"node_id":"I_kwDOAEVQ_M5H5zLl","number":169034,"title":"libstrangle: symbol lookup error","user":{"login":"rapenne-s","id":248016,"node_id":"MDQ6VXNlcjI0ODAxNg==","avatar_url":"https://avatars.githubusercontent.com/u/248016?v=4","gravatar_id":"","url":"https://api.github.com/users/rapenne-s","html_url":"https://github.com/rapenne-s","followers_url":"https://api.github.com/users/rapenne-s/followers","following_url":"https://api.github.com/users/rapenne-s/following{/other_user}","gists_url":"https://api.github.com/users/rapenne-s/gists{/gist_id}","starred_url":"https://api.github.com/users/rapenne-s/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rapenne-s/subscriptions","organizations_url":"https://api.github.com/users/rapenne-s/orgs","repos_url":"https://api.github.com/users/rapenne-s/repos","events_url":"https://api.github.com/users/rapenne-s/events{/privacy}","received_events_url":"https://api.github.com/users/rapenne-s/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-17T10:04:46Z","updated_at":"2022-04-17T10:31:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nlibstrangle doesn't work anymore, we have the same issue reported in https://gitlab.com/torkel104/libstrangle/-/issues/47 , this prevent at least lutris to work because it's used as a dependency\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p glxinfo libstrangle`\r\n2. `strangle -f 10 glxgears`\r\n3. result: `glxgears: symbol lookup error: /nix/store/mwq0w8yjawm2hs19d39hykbw3s2i9dxp-libstrangle-0.1.1/lib/libstrangle/lib64/libstrangle.so: undefined symbol: __libc_dlsym`\r\n\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\nglxgears is shown and limited to 10 fps\r\n\r\n### Notify maintainers\r\n@aske \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220416.75ad56b`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169034/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169031","id":1206326622,"node_id":"I_kwDOAEVQ_M5H5xVe","number":169031,"title":"exaile fails to start: \"python3: not found\"","user":{"login":"aidalgol","id":2313201,"node_id":"MDQ6VXNlcjIzMTMyMDE=","avatar_url":"https://avatars.githubusercontent.com/u/2313201?v=4","gravatar_id":"","url":"https://api.github.com/users/aidalgol","html_url":"https://github.com/aidalgol","followers_url":"https://api.github.com/users/aidalgol/followers","following_url":"https://api.github.com/users/aidalgol/following{/other_user}","gists_url":"https://api.github.com/users/aidalgol/gists{/gist_id}","starred_url":"https://api.github.com/users/aidalgol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/aidalgol/subscriptions","organizations_url":"https://api.github.com/users/aidalgol/orgs","repos_url":"https://api.github.com/users/aidalgol/repos","events_url":"https://api.github.com/users/aidalgol/events{/privacy}","received_events_url":"https://api.github.com/users/aidalgol/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-17T09:24:36Z","updated_at":"2022-04-20T14:50:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe program `exaile` does not launch, because it cannot find python.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set the user channel `nixpkgs` to `https://nixos.org/channels/nixpkgs-unstable`\r\n2. Run `nix-shell -p exaile --run exaile`\r\n\r\nThis will output,\r\n```console\r\n/nix/store/aaaa....-exaile-4.1.1/bin/..exaile-wrapped-wrapped: line 14: exec: python3: not found\r\n````\r\n\r\n### Expected behavior\r\nFor the GUI application Exaile to launch.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@ryneeverett\r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.111, NixOS, 21.11 (Porcupine), 21.11.20220415.278ecd2`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(aidan): `\"home-manager, nixpkgs-22.05pre369575.0b43a436fbb\"`\r\n - channels(root): `\"nixos-21.11.336755.efea022d6fe, home-manager-21.11.tar.gz\"`\r\n - nixpkgs: `/home/aidan/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169031/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002/events","html_url":"https://github.com/NixOS/nixpkgs/issues/169002","id":1206265200,"node_id":"I_kwDOAEVQ_M5H5iVw","number":169002,"title":"A bug in mutter is causing issues with window previews in some extensions","user":{"login":"Krutonium","id":3945538,"node_id":"MDQ6VXNlcjM5NDU1Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/3945538?v=4","gravatar_id":"","url":"https://api.github.com/users/Krutonium","html_url":"https://github.com/Krutonium","followers_url":"https://api.github.com/users/Krutonium/followers","following_url":"https://api.github.com/users/Krutonium/following{/other_user}","gists_url":"https://api.github.com/users/Krutonium/gists{/gist_id}","starred_url":"https://api.github.com/users/Krutonium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Krutonium/subscriptions","organizations_url":"https://api.github.com/users/Krutonium/orgs","repos_url":"https://api.github.com/users/Krutonium/repos","events_url":"https://api.github.com/users/Krutonium/events{/privacy}","received_events_url":"https://api.github.com/users/Krutonium/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-17T02:51:07Z","updated_at":"2022-04-20T14:50:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'm running my system on Unstable right now as one does on occasion, and I've run into a bug with an extension that I use called dash to panel. I tracked down the [bug on their tracker](https://github.com/home-sweet-gnome/dash-to-panel/issues/1620), and found that it's a bug in Mutter itself, that was fixed in [these two commits](https://gitlab.gnome.org/GNOME/mutter/-/merge_requests/2321/commits).\r\n\r\nI am writing to request that these two commits be added to mutter, basically, and I'll admit I'm not even sure this is the place to do it, or the way to do it. If it's not, point me where to/how to, please and thank you!\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use Gnome 42\r\n2. Install Dash to Dock\r\n3. Window Previews don't close due to a bug in Mutter\r\n\r\n### Expected behavior\r\nWindow Previews should close\r\n\r\n### Additional context\r\nMore information can be found at the issue I linked previously\r\n\r\n### Notify maintainers\r\n\r\nBasically the @gnome group which [appears to be made up of](https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix#L245-L252)\r\n @bobby285271\r\n @hedning\r\n @jtojnar\r\n @dasj19\r\n @maxeaubrey\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.2-zen3, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(krutonium): `\"\"`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d, nixos-hardware\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/169002/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168987","id":1206244824,"node_id":"I_kwDOAEVQ_M5H5dXY","number":168987,"title":"bcachefs module for custom kernel","user":{"login":"shadowrylander","id":12785394,"node_id":"MDQ6VXNlcjEyNzg1Mzk0","avatar_url":"https://avatars.githubusercontent.com/u/12785394?v=4","gravatar_id":"","url":"https://api.github.com/users/shadowrylander","html_url":"https://github.com/shadowrylander","followers_url":"https://api.github.com/users/shadowrylander/followers","following_url":"https://api.github.com/users/shadowrylander/following{/other_user}","gists_url":"https://api.github.com/users/shadowrylander/gists{/gist_id}","starred_url":"https://api.github.com/users/shadowrylander/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/shadowrylander/subscriptions","organizations_url":"https://api.github.com/users/shadowrylander/orgs","repos_url":"https://api.github.com/users/shadowrylander/repos","events_url":"https://api.github.com/users/shadowrylander/events{/privacy}","received_events_url":"https://api.github.com/users/shadowrylander/received_events","type":"User","site_admin":false},"labels":[{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-17T00:20:25Z","updated_at":"2022-04-20T14:50:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Hello!\r\n\r\nWith the following `configuration.nix`:\r\n\r\n```\r\n{ config, lib, pkgs, ... }: with builtins; with lib;\r\n\r\nlet\r\n nixos-hardware = builtins.fetchGit { url = \"https://github.com/nixos/nixos-hardware.git\"; ref = \"master\"; };\r\nin {\r\n imports =\r\n [ # Include the results of the hardware scan.\r\n ./hardware-configuration.nix\r\n \"${nixos-hardware}/microsoft/surface\"\r\n ];\r\n\r\n ...\r\n\r\n boot = {\r\n loader = {\r\n systemd-boot.enable = true;\r\n efi = {\r\n canTouchEfiVariables = true;\r\n efiSysMountPoint = \"/boot/efi\";\r\n };\r\n grub.copyKernels = true;\r\n };\r\n zfs = {\r\n enableUnstable = true;\r\n devNodes = \"/dev/\";\r\n };\r\n kernelParams = [ \"nohibernate\" ];\r\n initrd.supportedFilesystems = [ \"zfs\" \"bcachefs\" ];\r\n supportedFilesystems = config.boot.initrd.supportedFilesystems;\r\n };\r\n\r\n ...\r\n\r\n nix = {\r\n useSandbox = false;\r\n package = pkgs.nixUnstable;\r\n };\r\n\r\n hardware.enableRedistributableFirmware = lib.mkDefault true;\r\n\r\n ...\r\n\r\n system.stateVersion = \"21.11\";\r\n\r\n boot.kernelPatches = [ {\r\n name = \"bcachefs-6ddf061e68560a2bb263b126af7e894a6c1afb5f\";\r\n\r\n patch = fetchpatch {\r\n name = \"bcachefs-6ddf061e68560a2bb263b126af7e894a6c1afb5f.diff\";\r\n url = \"https://evilpiepirate.org/git/bcachefs.git/rawdiff/?id=6ddf061e68560a2bb263b126af7e894a6c1afb5f&id2=v5.16\";\r\n sha256 = \"1nkrr1cxavw0rqxlyiz7pf9igvqay0d5kk7194v9ph3fcp9rz5kc\";\r\n };\r\n\r\n extraConfig = \"BCACHEFS_FS m\";\r\n } ];\r\n}\r\n```\r\n\r\nAnd the following `bcachefs.nix`, in a forked repo of `nixpkgs`:\r\n\r\n```\r\n{ config, lib, pkgs, utils, ... }:\r\n\r\nwith lib;\r\n\r\nlet\r\n\r\n bootFs = filterAttrs (n: fs: (fs.fsType == \"bcachefs\") && (utils.fsNeededForBoot fs)) config.fileSystems;\r\n\r\n commonFunctions = ''\r\n prompt() {\r\n local name=\"$1\"\r\n printf \"enter passphrase for $name: \"\r\n }\r\n tryUnlock() {\r\n local name=\"$1\"\r\n local path=\"$2\"\r\n if bcachefs unlock -c $path > /dev/null 2> /dev/null; then # test for encryption\r\n prompt $name\r\n until bcachefs unlock $path 2> /dev/null; do # repeat until sucessfully unlocked\r\n printf \"unlocking failed!\\n\"\r\n prompt $name\r\n done\r\n printf \"unlocking successful.\\n\"\r\n fi\r\n }\r\n '';\r\n\r\n openCommand = name: fs:\r\n let\r\n # we need only unlock one device manually, and cannot pass multiple at once\r\n # remove this adaptation when bcachefs implements mounting by filesystem uuid\r\n # also, implement automatic waiting for the constituent devices when that happens\r\n # bcachefs does not support mounting devices with colons in the path, ergo we don't (see #49671)\r\n firstDevice = head (splitString \":\" fs.device);\r\n in\r\n ''\r\n tryUnlock ${name} ${firstDevice}\r\n '';\r\n\r\nin\r\n\r\n{\r\n config = mkIf (elem \"bcachefs\" config.boot.supportedFilesystems) (mkMerge [\r\n {\r\n system.fsPackages = [ pkgs.bcachefs-tools ];\r\n\r\n # use kernel package with bcachefs support until it's in mainline\r\n # boot.kernelPackages = pkgs.linuxPackages_testing_bcachefs;\r\n }\r\n\r\n (mkIf ((elem \"bcachefs\" config.boot.initrd.supportedFilesystems) || (bootFs != {})) {\r\n # chacha20 and poly1305 are required only for decryption attempts\r\n boot.initrd.availableKernelModules = [ \"bcachefs\" \"sha256\" \"chacha20\" \"poly1305\" ];\r\n\r\n boot.initrd.extraUtilsCommands = ''\r\n copy_bin_and_libs ${pkgs.bcachefs-tools}/bin/bcachefs\r\n '';\r\n boot.initrd.extraUtilsCommandsTest = ''\r\n $out/bin/bcachefs version\r\n '';\r\n\r\n boot.initrd.postDeviceCommands = commonFunctions + concatStrings (mapAttrsToList openCommand bootFs);\r\n })\r\n ]);\r\n}\r\n```\r\n\r\nI'm getting the following error:\r\n\r\n```\r\nbuilding Nix...\r\nbuilding the system configuration...\r\nthese 4 derivations will be built:\r\n /nix/store/9f0b1iwk44pj2czf94vl95r4csxyb0rp-linux-5.16.11-modules-shrunk.drv\r\n /nix/store/vdlbc5gly53xabn3n0dk4j0xr8spknhn-stage-1-init.sh.drv\r\n /nix/store/c3cdcix05adv5imm82pzgvrz46slnx8i-initrd-linux-5.16.11.drv\r\n /nix/store/qvnqqmvpbaibky8q1bscdb7vm0hcnzzy-nixos-system-sandshrew-22.05.git.cf37c07a41bM.drv\r\nbuilding '/nix/store/9f0b1iwk44pj2czf94vl95r4csxyb0rp-linux-5.16.11-modules-shrunk.drv'...\r\nkernel version is 5.16.11\r\nroot module: xhci_pci\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/common/usb-common.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/core/usbcore.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/host/xhci-hcd.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/host/xhci-pci-renesas.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/host/xhci-pci.ko.xz\r\nroot module: nvme\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/arch/x86/crypto/crct10dif-pclmul.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_generic.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/lib/crc-t10dif.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/block/t10-pi.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/nvme/host/nvme-core.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/nvme/host/nvme.ko.xz\r\nroot module: uas\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/common/usb-common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/core/usbcore.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/scsi/scsi_common.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/scsi/scsi_mod.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/storage/usb-storage.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/usb/storage/uas.ko.xz\r\nroot module: sd_mod\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/arch/x86/crypto/crct10dif-pclmul.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crct10dif_generic.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/lib/crc-t10dif.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/scsi/scsi_common.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/scsi/scsi_mod.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/block/t10-pi.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/scsi/sd_mod.ko.xz\r\nroot module: hyperv_keyboard\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/hv/hv_vmbus.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/input/serio/serio.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/input/serio/hyperv-keyboard.ko.xz\r\nroot module: md_mod\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/md-mod.ko.xz\r\nroot module: raid0\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/md-mod.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/raid0.ko.xz\r\nroot module: raid1\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/md-mod.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/raid1.ko.xz\r\nroot module: raid10\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/md-mod.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/raid10.ko.xz\r\nroot module: raid456\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/arch/x86/crypto/crc32c-intel.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crc32c_generic.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/lib/libcrc32c.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/lib/raid6/raid6_pq.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/xor.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/md-mod.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/async_tx/async_tx.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/async_tx/async_xor.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/async_tx/async_pq.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/async_tx/async_memcpy.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/async_tx/async_raid6_recov.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/drivers/md/raid456.ko.xz\r\nroot module: ext2\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/fs/mbcache.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/fs/ext2/ext2.ko.xz\r\nroot module: ext4\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/fs/jbd2/jbd2.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/fs/mbcache.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/lib/crc16.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/arch/x86/crypto/crc32c-intel.ko.xz\r\n dependency already copied: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/crypto/crc32c_generic.ko.xz\r\n copying dependency: /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11/kernel/fs/ext4/ext4.ko.xz\r\nroot module: bcachefs\r\nmodprobe: FATAL: Module bcachefs not found in directory /nix/store/ibx3n5f2af7l645n6a5v909si6b2xl2z-linux-5.16.11-modules/lib/modules/5.16.11\r\nerror: builder for '/nix/store/9f0b1iwk44pj2czf94vl95r4csxyb0rp-linux-5.16.11-modules-shrunk.drv' failed with exit code 1\r\nerror: 1 dependencies of derivation '/nix/store/vdlbc5gly53xabn3n0dk4j0xr8spknhn-stage-1-init.sh.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/c3cdcix05adv5imm82pzgvrz46slnx8i-initrd-linux-5.16.11.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/qvnqqmvpbaibky8q1bscdb7vm0hcnzzy-nixos-system-sandshrew-22.05.git.cf37c07a41bM.drv' failed to build\r\n```\r\n\r\nAs far as I can tell, this is more or less how the `bcachefs` test kernel is built as well; why isn't the `bcachefs` module being found for this `surface` kernel, as built from `${nixos-hardware}/microsoft/surface`?\r\n\r\nIn addition, I do apologize if this isn't the place to ask for help, but I've asked on the Discourse and Reddit, but didn't get much of a response, and I don't know how to access the IRC.\r\n\r\nThank you kindly for the help!\r\n\r\n## Technical details\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(shadowrylander): `\"j\"`\r\n - channels(root): `\"j, nixos-21.11.336282.ed02c2ba038\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168987/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168984","id":1206237794,"node_id":"I_kwDOAEVQ_M5H5bpi","number":168984,"title":"golangci-lint does not build on darwin-x86_64 - undefined symbols","user":{"login":"wlcx","id":3065381,"node_id":"MDQ6VXNlcjMwNjUzODE=","avatar_url":"https://avatars.githubusercontent.com/u/3065381?v=4","gravatar_id":"","url":"https://api.github.com/users/wlcx","html_url":"https://github.com/wlcx","followers_url":"https://api.github.com/users/wlcx/followers","following_url":"https://api.github.com/users/wlcx/following{/other_user}","gists_url":"https://api.github.com/users/wlcx/gists{/gist_id}","starred_url":"https://api.github.com/users/wlcx/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wlcx/subscriptions","organizations_url":"https://api.github.com/users/wlcx/orgs","repos_url":"https://api.github.com/users/wlcx/repos","events_url":"https://api.github.com/users/wlcx/events{/privacy}","received_events_url":"https://api.github.com/users/wlcx/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":337081580,"node_id":"MDU6TGFiZWwzMzcwODE1ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20golang","name":"6.topic: golang","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-16T23:33:26Z","updated_at":"2022-04-26T09:38:21Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"golangci-lint on unstable does not build on darwin-x86_64. This seems to have been caused by #166801 which switched the go version from 1.17 to 1.18 (to fix another (runtime) bug!)\r\n\r\nSee hydra: https://hydra.nixos.org/job/nixpkgs/trunk/golangci-lint.x86_64-darwin\r\n\r\n```\r\n/nix/store/gynxiihx8rd89nid1ma8pmj9b3nd3kzz-go-1.18.1/share/go/pkg/tool/darwin_amd64/link: running clang failed: exit status 1\r\nUndefined symbols for architecture x86_64:\r\n \"_SecTrustEvaluateWithError\", referenced from:\r\n _crypto/x509/internal/macos.x509_SecTrustEvaluateWithError_trampoline.abi0 in go.o\r\n \"_utimensat\", referenced from:\r\n _syscall.libc_utimensat_trampoline.abi0 in go.o\r\nld: symbol(s) not found for architecture x86_64\r\nclang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\n```\r\n\r\nFYI (sorry to ping but not really sure who else I would ask)\r\n@Arriven @siraben - author/merger of #166801\r\n@Mic92 - arbitrary maintainer\r\n\r\n\r\n```console\r\n❯ nix run nixpkgs#nix-info -- -m\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixpkgs-22.05pre344086.568e0bc498e\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168984/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168982","id":1206236870,"node_id":"I_kwDOAEVQ_M5H5bbG","number":168982,"title":"networkmanager-pptp","user":{"login":"neumantm","id":27770422,"node_id":"MDQ6VXNlcjI3NzcwNDIy","avatar_url":"https://avatars.githubusercontent.com/u/27770422?v=4","gravatar_id":"","url":"https://api.github.com/users/neumantm","html_url":"https://github.com/neumantm","followers_url":"https://api.github.com/users/neumantm/followers","following_url":"https://api.github.com/users/neumantm/following{/other_user}","gists_url":"https://api.github.com/users/neumantm/gists{/gist_id}","starred_url":"https://api.github.com/users/neumantm/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/neumantm/subscriptions","organizations_url":"https://api.github.com/users/neumantm/orgs","repos_url":"https://api.github.com/users/neumantm/repos","events_url":"https://api.github.com/users/neumantm/events{/privacy}","received_events_url":"https://api.github.com/users/neumantm/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-16T23:26:33Z","updated_at":"2022-04-16T23:26:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nPlugin for network manager adding support for pptp vpns\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/NetworkManager/NetworkManager-pptp\r\n* source URL: https://github.com/NetworkManager/NetworkManager-pptp\r\n* license: gpl2\r\n* platforms: linux, ?\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168982/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168960","id":1206204180,"node_id":"I_kwDOAEVQ_M5H5TcU","number":168960,"title":"Prometheus: Federation scrape configuration leads to invalid param lookup","user":{"login":"Shawn8901","id":12239057,"node_id":"MDQ6VXNlcjEyMjM5MDU3","avatar_url":"https://avatars.githubusercontent.com/u/12239057?v=4","gravatar_id":"","url":"https://api.github.com/users/Shawn8901","html_url":"https://github.com/Shawn8901","followers_url":"https://api.github.com/users/Shawn8901/followers","following_url":"https://api.github.com/users/Shawn8901/following{/other_user}","gists_url":"https://api.github.com/users/Shawn8901/gists{/gist_id}","starred_url":"https://api.github.com/users/Shawn8901/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Shawn8901/subscriptions","organizations_url":"https://api.github.com/users/Shawn8901/orgs","repos_url":"https://api.github.com/users/Shawn8901/repos","events_url":"https://api.github.com/users/Shawn8901/events{/privacy}","received_events_url":"https://api.github.com/users/Shawn8901/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-16T19:58:40Z","updated_at":"2022-04-18T16:49:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI am currently struggling with the ability to configure a valid federation between two Prometheus instances.\r\nInstance A is my Prometheus master and import all scraped values from Instance B with a specific label.\r\nThe current module implementation does not result in a valid federation configuration (or i dont get it how to properly escape it).\r\n\r\nA minimal setup for a federation is\r\n\r\n```\r\nservices.prometheus = {\r\n enable = true;\r\n port = 9001;\r\n retentionTime = \"30d\";\r\n scrapeConfigs = [\r\n {\r\n job_name = \"myJob\";\r\n honor_labels = true;\r\n metrics_path = \"/federate\";\r\n params = {\r\n \"match[]\" = [ \"{myLabel='LabelValue'}\" ];\r\n };\r\n static_configs = [\r\n {\r\n targets = [ \"other_host:9001\" ];\r\n }\r\n ];\r\n }\r\n ];\r\n};\r\n```\r\n\r\nThe problematic part is here the `params` field.\r\nFrom[ documentation of Prometheus](https://prometheus.io/docs/prometheus/latest/federation/) the match Params has to contain a line like ` - '{job=\"prometheus\"}'`. The specific params from [our module](https://github.com/NixOS/nixpkgs/blob/9c3048dfdbe157c0a96d603f98ce12b0b0b289ff/nixos/modules/services/monitoring/prometheus/default.nix#L315) does define the type as a attribute list of strings, so my example should result in the desired result.\r\n\r\nPlease notice that the quotes around the LabelValue are important in that case otherwise it does not result in a valid request to a federation instance.\r\n\r\n\r\n \r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use example code form above\r\n2. Check generated configuration file for missing quotes.\r\n3. (Optional) Have another Prometheus instance set up and data available to be loaded and verity that no values can be imported\r\n\r\nThe generated config from aboves example is \r\n\r\n```\r\n{\r\n \"alerting\": {\r\n \"alertmanagers\": []\r\n },\r\n \"global\": {},\r\n \"remote_read\": [],\r\n \"remote_write\": [],\r\n \"rule_files\": [\r\n \"/nix/store/flb9r5zzcbja5l5v7zc6kqpbmy847kwv-rules-checkrules-checked\"\r\n ],\r\n \"scrape_configs\": [\r\n {\r\n \"honor_labels\": true,\r\n \"job_name\": \"myJob\",\r\n \"metrics_path\": \"/federate\",\r\n \"params\": {\r\n \"match[]\": [\r\n \"{myLabel=LabelValue}\"\r\n ]\r\n },\r\n \"static_configs\": [\r\n {\r\n \"labels\": {},\r\n \"targets\": [\r\n \"other_host:9001\"\r\n ]\r\n }\r\n ]\r\n }\r\n ]\r\n}\r\n```\r\nWhich is missing the quotes, which are required to be a valid configuration.\r\n\r\nThe actual error the server may get on loading the data could be something like that\r\n```\r\n1:10: parse error: unexpected identifier \"LabelValue\" in label matching, expected string\r\n```\r\n(I did just fill in the params as GET like the documentation of Prometheus explains how the federation values are loaded)\r\n\r\n### Expected behavior\r\nA user is able to configure a federation via declarative scrapeConfig attribute.\r\n\r\nThe expected configuration for above's example is \r\n```\r\n{\r\n \"alerting\": {\r\n \"alertmanagers\": []\r\n },\r\n \"global\": {},\r\n \"remote_read\": [],\r\n \"remote_write\": [],\r\n \"rule_files\": [\r\n \"/nix/store/flb9r5zzcbja5l5v7zc6kqpbmy847kwv-rules-checkrules-checked\"\r\n ],\r\n \"scrape_configs\": [\r\n {\r\n \"honor_labels\": true,\r\n \"job_name\": \"myJob\",\r\n \"metrics_path\": \"/federate\",\r\n \"params\": {\r\n \"match[]\": [\r\n \"{myLabel='LabelValue'}\"\r\n ]\r\n },\r\n \"static_configs\": [\r\n {\r\n \"labels\": {},\r\n \"targets\": [\r\n \"other_host:9001\"\r\n ]\r\n }\r\n ]\r\n }\r\n ]\r\n}\r\n\r\n```\r\n\r\n\r\n### Additional context\r\nI also tried other combinations like \r\n\r\n```\r\nparams = {\r\n \"match[]\" = [ ''{myLabel=\"LabelValue\"}'' ];\r\n};\r\n```\r\nresulting in an escaped value `\"{myLabel=\\\"LabelValue\\\"}\"`, which is also obvious wrong.\r\n\r\nI already tried to analyze the issue to some point.\r\nAt https://github.com/NixOS/nixpkgs/blob/9c3048dfdbe157c0a96d603f98ce12b0b0b289ff/nixos/modules/services/monitoring/prometheus/default.nix#L38 is the actual writing of the file.\r\n\r\nWhen i do something like with my flake (tank is the hostname of the Prometheus master)\r\n```\r\n:lf .#\r\npkgs = nixosConfigurations.tank.pkgs\r\nwritePrettyJSON = name: x: \r\n pkgs.runCommandLocal name { } ''\r\n echo '${builtins.toJSON x}' | ${pkgs.jq}/bin/jq . > $out\r\n ''\r\na = nixosConfigurations.tank.config.services.prometheus.scrapeConfigs\r\nwritePrettyJSON \"test\" a \r\n```\r\n\r\nThat should be the minimal part of the config writing without the prior validation logic and results in the expected result `{\\\"match[]\\\":[\\\"{myLabel='LabelValue'}\\\"]}`\r\nSo my assumption is that it gets somewhere on validation broken and that is here:\r\nhttps://github.com/NixOS/nixpkgs/blob/9c3048dfdbe157c0a96d603f98ce12b0b0b289ff/nixos/modules/services/monitoring/prometheus/default.nix#L51\r\n\r\nSadly i am a newbie on nix language and not able to bring that to a nix repl to play around.\r\n\r\nBut as the plain write operation does result in a valid configuration i am at least optimistic that i do not do things wrong.\r\n\r\n\r\nAs workaround i can use configText attribute to bring in again the fixed generated config.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@basvandijk @yrd @amarshall \r\n\r\n(I have @ the last editor of the file and the persons which edited the section i assume may causes the issue, as the module has no meta tag)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nshawn•~» nix-shell -p nix-info --run \"nix-info -m\" [21:44:35]\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05.20220415.5181d59`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/etc/nix/inputs/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168960/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168943","id":1206160281,"node_id":"I_kwDOAEVQ_M5H5IuZ","number":168943,"title":"Some Octave packages fail to build ever since 7.1.0","user":{"login":"doronbehar","id":10998835,"node_id":"MDQ6VXNlcjEwOTk4ODM1","avatar_url":"https://avatars.githubusercontent.com/u/10998835?v=4","gravatar_id":"","url":"https://api.github.com/users/doronbehar","html_url":"https://github.com/doronbehar","followers_url":"https://api.github.com/users/doronbehar/followers","following_url":"https://api.github.com/users/doronbehar/following{/other_user}","gists_url":"https://api.github.com/users/doronbehar/gists{/gist_id}","starred_url":"https://api.github.com/users/doronbehar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/doronbehar/subscriptions","organizations_url":"https://api.github.com/users/doronbehar/orgs","repos_url":"https://api.github.com/users/doronbehar/repos","events_url":"https://api.github.com/users/doronbehar/events{/privacy}","received_events_url":"https://api.github.com/users/doronbehar/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-16T16:38:08Z","updated_at":"2022-04-16T16:38:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"For example:\r\n\r\n```\r\n$ nix build -Lf. octave.pkgs.io\r\noctave> Sourcing write-required-octave-packages-hook.sh\r\noctave> Using writeRequiredOctavePackagesPhase\r\noctave> unpacking sources\r\noctave> unpacking source archive /nix/store/zh1w2v3fh79hrkx0cx37a1a48hvwhjiy-io-2.6.3.tar.gz\r\noctave> source root is io-2.6.3\r\noctave> setting SOURCE_DATE_EPOCH to timestamp 1604255252 of file io-2.6.3/src/octave_4_2_co\r\noctave> patching sources\r\noctave> building\r\noctave> error: unlink: operation failed: No such file or directory\r\noctave> error: called from\r\noctave> build at line 80 column 7\r\noctave> pkg at line 720 column 7\r\n```\r\n\r\n`octave.pkgs.signal` fails similarly. The line that causes the failure according to my testing is:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/7392416a539344c3b3d19c7e6cb7f4e6f49f72aa/pkgs/development/interpreters/octave/build-octave-package.nix#L115\r\n\r\nA list of some packages that didn't break:\r\n\r\n1. `octave.pkgs.netcdf`\r\n2. `octave.pkgs.symbolic`\r\n3. `octave.pkgs.control`\r\n\r\nCould be this is an upstream issue.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168943/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168939","id":1206155031,"node_id":"I_kwDOAEVQ_M5H5HcX","number":168939,"title":"Evolution crashes when closing the message compose window","user":{"login":"NetaliDev","id":15304894,"node_id":"MDQ6VXNlcjE1MzA0ODk0","avatar_url":"https://avatars.githubusercontent.com/u/15304894?v=4","gravatar_id":"","url":"https://api.github.com/users/NetaliDev","html_url":"https://github.com/NetaliDev","followers_url":"https://api.github.com/users/NetaliDev/followers","following_url":"https://api.github.com/users/NetaliDev/following{/other_user}","gists_url":"https://api.github.com/users/NetaliDev/gists{/gist_id}","starred_url":"https://api.github.com/users/NetaliDev/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NetaliDev/subscriptions","organizations_url":"https://api.github.com/users/NetaliDev/orgs","repos_url":"https://api.github.com/users/NetaliDev/repos","events_url":"https://api.github.com/users/NetaliDev/events{/privacy}","received_events_url":"https://api.github.com/users/NetaliDev/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-16T16:19:10Z","updated_at":"2022-04-20T14:48:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nEvolution crashes with a segmentation fault when I try to close the message compose window. This happens when I try to close it with the Ctrl+W shortcut or when I try to close it over my window manager. Therefore, it is currently not possible to cancel composing a message without Evolution crashing.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start Evolution\r\n2. Start composing a message (e.g. by composing a new mail message or by creating a reply to a mail message)\r\n3. Close the compose message window\r\n4. Evolution crashes with a segmentation fault\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@jtojnar \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[netali@erza:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.34, NixOS, 22.05 (Quokka), 22.05pre369524.5181d5945ed`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168939/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168928","id":1206126498,"node_id":"I_kwDOAEVQ_M5H5Aei","number":168928,"title":"vimPlugins.coq_nvim needs aditional handling","user":{"login":"lucasew","id":15693688,"node_id":"MDQ6VXNlcjE1NjkzNjg4","avatar_url":"https://avatars.githubusercontent.com/u/15693688?v=4","gravatar_id":"","url":"https://api.github.com/users/lucasew","html_url":"https://github.com/lucasew","followers_url":"https://api.github.com/users/lucasew/followers","following_url":"https://api.github.com/users/lucasew/following{/other_user}","gists_url":"https://api.github.com/users/lucasew/gists{/gist_id}","starred_url":"https://api.github.com/users/lucasew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lucasew/subscriptions","organizations_url":"https://api.github.com/users/lucasew/orgs","repos_url":"https://api.github.com/users/lucasew/repos","events_url":"https://api.github.com/users/lucasew/events{/privacy}","received_events_url":"https://api.github.com/users/lucasew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null},{"id":1072455660,"node_id":"MDU6TGFiZWwxMDcyNDU1NjYw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20coq","name":"6.topic: coq","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-16T14:36:08Z","updated_at":"2022-04-26T09:41:47Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe plugin definition is generated by a script but the way it works requires some extra handling.\r\n\r\nIt depends on some other python libs and requires patching to write state outside of the nix store.\r\n\r\nI got it working on [my config](https://github.com/lucasew/nixcfg/tree/master/packages/custom/neovim). \r\n\r\nI would like to upstream those alternative techniques to benefit more people but I don't know what file to change and how to pass extra python packages to the target neovim. \r\n\r\nAnother discussion that would help is where to store the files that would be stored otherwise in the .var folder.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Just add coq_nvim to your neovim configuration and run `:COQnow` and you will see the problem\r\n\r\n### Expected behavior\r\nPlugin working out of the box from the nixpkgs build\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\n- [My neovim config with the fixes](https://github.com/lucasew/nixcfg/tree/master/packages/custom/neovim)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@teto @TomHotston \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nlucasew@acer-nix ~ 0$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.3, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/store/j4n45y0r4ybms9vz64wisbffq7hbf78q-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168928/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168924","id":1206117950,"node_id":"I_kwDOAEVQ_M5H4-Y-","number":168924,"title":"Cinnamon desktop: cannot install or update user-installed applets, desklets, extensions, ...","user":{"login":"alexeymuranov","id":712698,"node_id":"MDQ6VXNlcjcxMjY5OA==","avatar_url":"https://avatars.githubusercontent.com/u/712698?v=4","gravatar_id":"","url":"https://api.github.com/users/alexeymuranov","html_url":"https://github.com/alexeymuranov","followers_url":"https://api.github.com/users/alexeymuranov/followers","following_url":"https://api.github.com/users/alexeymuranov/following{/other_user}","gists_url":"https://api.github.com/users/alexeymuranov/gists{/gist_id}","starred_url":"https://api.github.com/users/alexeymuranov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alexeymuranov/subscriptions","organizations_url":"https://api.github.com/users/alexeymuranov/orgs","repos_url":"https://api.github.com/users/alexeymuranov/repos","events_url":"https://api.github.com/users/alexeymuranov/events{/privacy}","received_events_url":"https://api.github.com/users/alexeymuranov/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1803518571,"node_id":"MDU6TGFiZWwxODAzNTE4NTcx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cinnamon","name":"6.topic: cinnamon","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-16T13:56:48Z","updated_at":"2022-04-20T14:48:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI have user-installed Cinnamon applets, desklets, extensions, themes, which have been installed in the home folder by a different OS (as far as i remember). Many of them work under NixOS (some do not: #129963). However, i cannot update them. When i try, i get the message:\r\n\r\n> No such file or directory: 'msgfmt'\r\n\r\nThe same happens if i try to install a new applet.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set up Cinnamon desktop on NixOS and log in.\r\n2. Try to install an applet.\r\n\r\n### Expected behavior\r\nShould be able to install and update user-installed applets, desklets, extensions, themes.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nI am just beginning to switch over to Cinnamon from GNOME 3 (having been fed up with GNOME, especially under NixOS).\r\n\r\n### Notify maintainers\r\n@mkg20001 \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.110, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(alexey): `\"\"`\r\n - channels(root): `\"nixos-21.11.337053.2f06b87f64b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168924/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168901","id":1206082495,"node_id":"I_kwDOAEVQ_M5H41u_","number":168901,"title":"coreutils 9.1","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"assignees":[{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false}],"milestone":null,"comments":1,"created_at":"2022-04-16T10:44:09Z","updated_at":"2022-04-20T14:48:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: coreutils\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 9.0\r\ndesired version: 9.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @dasJ \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168901/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168861","id":1205985084,"node_id":"I_kwDOAEVQ_M5H4d88","number":168861,"title":"btrfs-progs: doesn't cross compile to `armv6l-linux` (from `x86_64-linux`)","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-16T02:17:38Z","updated_at":"2022-04-20T14:47:13Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTry to build `btrfs-progs` for `raspberryPi`.\r\n\r\nNote, I'm trying staging because #168734 is necessary.\r\n\r\n`nix build github:nixos/nixpkgs/staging#pkgsCross.raspberryPi.btrfs-progs` fails:\r\n\r\n```\r\ngot build log for 'github:nixos/nixpkgs/staging#pkgsCross.raspberryPi.btrfs-progs' from 'daemon'\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/3brya9ik47l5qw6cndf7pf8cgjpymaaz-btrfs-progs-v5.16.2.tar.xz\r\nsource root is btrfs-progs-v5.16.2\r\nsetting SOURCE_DATE_EPOCH to timestamp 1645050425 of file btrfs-progs-v5.16.2/configure\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\n@nix { \"action\": \"setPhase\", \"phase\": \"updateAutotoolsGnuConfigScriptsPhase\" }\r\nupdateAutotoolsGnuConfigScriptsPhase\r\nUpdating Autotools / GNU config script to a newer upstream version: ./config/config.sub\r\nUpdating Autotools / GNU config script to a newer upstream version: ./config/config.guess\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\nconfigure flags: --disable-static --prefix=/nix/store/3zngz0dnlg3l31wgan0x83ndjicc5075-btrfs-progs-armv6l-unknown-linux-gnueabihf-5.16.2 --build=x86_64-unknown-linux-gnu --host=armv6l-unknown-linux-gnueabihf\r\nchecking for armv6l-unknown-linux-gnueabihf-gcc... armv6l-unknown-linux-gnueabihf-gcc\r\nchecking whether the C compiler works... yes\r\nchecking for C compiler default output file name... a.out\r\nchecking for suffix of executables... \r\nchecking whether we are cross compiling... yes\r\nchecking for suffix of object files... o\r\nchecking whether we are using the GNU C compiler... yes\r\nchecking whether armv6l-unknown-linux-gnueabihf-gcc accepts -g... yes\r\nchecking for armv6l-unknown-linux-gnueabihf-gcc option to accept ISO C89... none needed\r\nchecking how to run the C preprocessor... armv6l-unknown-linux-gnueabihf-gcc -E\r\nchecking for grep that handles long lines and -e... /nix/store/bqkx3pi50phcglv0l551jhp96bq8njl0-gnugrep-3.7/bin/grep\r\nchecking for egrep... /nix/store/bqkx3pi50phcglv0l551jhp96bq8njl0-gnugrep-3.7/bin/grep -E\r\nchecking for ANSI C header files... yes\r\nchecking for sys/types.h... yes\r\nchecking for sys/stat.h... yes\r\nchecking for stdlib.h... yes\r\nchecking for string.h... yes\r\nchecking for memory.h... yes\r\nchecking for strings.h... yes\r\nchecking for inttypes.h... yes\r\nchecking for stdint.h... yes\r\nchecking for unistd.h... yes\r\nchecking minix/config.h usability... no\r\nchecking minix/config.h presence... no\r\nchecking for minix/config.h... no\r\nchecking whether it is safe to define __EXTENSIONS__... yes\r\nchecking for armv6l-unknown-linux-gnueabihf-gcc... (cached) armv6l-unknown-linux-gnueabihf-gcc\r\nchecking whether we are using the GNU C compiler... (cached) yes\r\nchecking whether armv6l-unknown-linux-gnueabihf-gcc accepts -g... (cached) yes\r\nchecking for armv6l-unknown-linux-gnueabihf-gcc option to accept ISO C89... (cached) none needed\r\nchecking whether C compiler accepts -std=gnu90... yes\r\nchecking build system type... x86_64-unknown-linux-gnu\r\nchecking host system type... armv6l-unknown-linux-gnueabihf\r\nchecking for an ANSI C-conforming const... yes\r\nchecking for working volatile... yes\r\nchecking whether byte ordering is bigendian... no\r\nchecking for special C compiler options needed for large files... no\r\nchecking for _FILE_OFFSET_BITS value needed for large files... 64\r\nchecking for a BSD-compatible install... /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/install -c\r\nchecking whether ln -s works... yes\r\nchecking for armv6l-unknown-linux-gnueabihf-ar... armv6l-unknown-linux-gnueabihf-ar\r\nchecking for rm... /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/rm\r\nchecking for rmdir... /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/rmdir\r\nchecking for openat... yes\r\nchecking for reallocarray... yes\r\nchecking for clock_gettime... yes\r\nchecking linux/perf_event.h usability... yes\r\nchecking linux/perf_event.h presence... yes\r\nchecking for linux/perf_event.h... yes\r\nchecking linux/hw_breakpoint.h usability... yes\r\nchecking linux/hw_breakpoint.h presence... yes\r\nchecking for linux/hw_breakpoint.h... yes\r\nchecking pkg-config is at least version 0.9.0... yes\r\nchecking execinfo.h usability... yes\r\nchecking execinfo.h presence... yes\r\nchecking for execinfo.h... yes\r\nchecking for backtrace... yes\r\nchecking for backtrace_symbols_fd... yes\r\nchecking for xmlto... /nix/store/aj13vfq0jp61an12dhz71alcb8py2wnw-xmlto-0.0.28/bin/xmlto\r\nchecking for mv... /nix/store/hgl0ydlkgs6y6hx9h7k209shw3v7z77j-coreutils-9.0/bin/mv\r\nchecking for a sed that does not truncate output... /nix/store/1442kn5q9ah0bhhqm99f8nr76diczqgm-gnused-4.8/bin/sed\r\nchecking for asciidoc... /nix/store/1hp17i8mcnwx537a0g1mfwxyf902pgy3-asciidoc-9.1.0/bin/asciidoc\r\nchecking for asciidoctor... no\r\nchecking for EXT2FS... yes\r\nchecking for COM_ERR... yes\r\nchecking for REISERFS... no\r\nchecking for FIEMAP_EXTENT_SHARED defined in linux/fiemap.h... yes\r\nchecking for EXT4_EPOCH_MASK defined in ext2fs/ext2_fs.h... yes\r\nchecking linux/blkzoned.h usability... yes\r\nchecking linux/blkzoned.h presence... yes\r\nchecking for linux/blkzoned.h... yes\r\nchecking for struct blk_zone.capacity... yes\r\nchecking for BLKGETZONESZ defined in linux/blkzoned.h... yes\r\nchecking for BLKID... yes\r\nchecking for UUID... yes\r\nchecking for ZLIB... yes\r\nchecking for ZSTD... yes\r\nchecking for LIBUDEV... yes\r\nchecking for a Python interpreter with version >= 3.4... python\r\nchecking for python... /nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/bin/python\r\nchecking for python version... 3.9\r\nchecking for python platform... linux\r\nchecking for GNU default python prefix... ${prefix}\r\nchecking for GNU default python exec_prefix... ${exec_prefix}\r\nchecking for python script directory (pythondir)... ${PYTHON_PREFIX}/lib/python3.9/site-packages\r\nchecking for python extension module directory (pyexecdir)... ${PYTHON_EXEC_PREFIX}/lib/python3.9/site-packages\r\nchecking for PYTHON... yes\r\nchecking for lzo_version in -llzo2... yes\r\nconfigure: creating ./config.status\r\nconfig.status: creating Makefile.inc\r\nconfig.status: creating Documentation/Makefile\r\nconfig.status: creating version.h\r\nconfig.status: creating libbtrfsutil/libbtrfsutil.pc\r\nconfig.status: creating config.h\r\n\r\n\tbtrfs-progs: v5.16.2 \r\n\tlibbtrfs: 0.1.2 (deprecated)\r\n\tlibbtrfsutil: 1.2.0\r\n\r\n\tprefix: /nix/store/3zngz0dnlg3l31wgan0x83ndjicc5075-btrfs-progs-armv6l-unknown-linux-gnueabihf-5.16.2\r\n\texec prefix: ${prefix}\r\n\r\n\tbindir: ${exec_prefix}/bin\r\n\tlibdir: ${exec_prefix}/lib\r\n\tincludedir: ${prefix}/include\r\n\tpkgconfigdir: ${libdir}/pkgconfig\r\n\r\n\tcompiler: armv6l-unknown-linux-gnueabihf-gcc\r\n\tCFLAGS: -g -O2 -Wall -D_FORTIFY_SOURCE=2\r\n\tLDFLAGS: \r\n\r\n\tprograms: yes\r\n\tshared libraries: yes\r\n\tstatic libraries: no\r\n\tdocumentation: yes\r\n\tdoc generator: asciidoc\r\n\tbacktrace support: yes\r\n\tbtrfs-convert: yes (ext2)\r\n\tbtrfs-restore zstd: yes\r\n\tPython bindings: yes\r\n\tPython interpreter: /nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/bin/python\r\n\tcrypto provider: builtin \r\n\tlibudev: yes\r\n\tzoned device: yes\r\n\t\r\n\tType 'make' to compile.\r\n\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nbuild flags: -j12 -l12 SHELL=/nix/store/fcd0m68c331j7nkdxvnnpb8ggwsaiqac-bash-5.1-p16/bin/bash udevruledir=\\$\\(out\\)/lib/udev/rules.d\r\n [CC] btrfs.o\r\n [CC] kernel-lib/list_sort.o\r\n [CC] kernel-lib/radix-tree.o\r\n [CC] kernel-lib/raid56.o\r\n [CC] kernel-lib/rbtree.o\r\n [CC] kernel-lib/tables.o\r\n [CC] kernel-shared/backref.o\r\n [CC] kernel-shared/extent_io.o\r\n [CC] kernel-shared/file-item.o\r\n [CC] kernel-shared/file.o\r\n [CC] kernel-shared/free-space-cache.o\r\n [CC] kernel-shared/free-space-tree.o\r\n [CC] kernel-shared/inode-item.o\r\n [CC] kernel-shared/inode.o\r\n [CC] kernel-shared/print-tree.o\r\n [CC] kernel-shared/root-tree.o\r\n [CC] kernel-shared/extent-tree.o\r\n [CC] kernel-shared/disk-io.o\r\n [CC] kernel-shared/dir-item.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/string.h:519\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[K./kerncompat.h:30\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kkernel-shared/print-tree.c:23\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kstrncpy\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kbg_flags_to_str\u001b[m\u001b[K' at \u001b[01m\u001b[Kkernel-shared/print-tree.c:197:4\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/string_fortified.h:95:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K__builtin_strncpy\u001b[m\u001b[K' specified bound 64 equals destination size [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wstringop-truncation\u0007-Wstringop-truncation\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 95 | return \u001b[01;35m\u001b[K__builtin___strncpy_chk (__dest, __src, __len,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 96 | \u001b[01;35m\u001b[K __glibc_objsize (__dest))\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] kernel-shared/delayed-ref.o\r\n [CC] kernel-shared/ulist.o\r\n [CC] kernel-shared/uuid-tree.o\r\n [CC] kernel-shared/transaction.o\r\n [CC] kernel-shared/zoned.o\r\n [CC] common/device-scan.o\r\n [CC] common/device-utils.o\r\n [CC] common/extent-cache.o\r\n [CC] common/format-output.o\r\n [CC] common/parse-utils.o\r\n [CC] common/open-utils.o\r\n [CC] common/path-utils.o\r\n [CC] common/rbtree-utils.o\r\n [CC] common/repair.o\r\n [CC] common/send-stream.o\r\n [CC] common/send-utils.o\r\n [CC] common/string-table.o\r\n [CC] common/task-utils.o\r\n [CC] common/units.o\r\n [CC] common/utils.o\r\n [CC] common/messages.o\r\n [CC] cmds/receive-dump.o\r\n [CC] check/qgroup-verify.o\r\n [CC] common/help.o\r\n [CC] crypto/xxhash.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/stdio.h:888\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kcommon/help.c:17\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kfprintf\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kusage_command_internal\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:257:3\u001b[m\u001b[K,\r\n inlined from '\u001b[01m\u001b[Kusage_command_usagestr\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:271:8\u001b[m\u001b[K,\r\n inlined from '\u001b[01m\u001b[Kusage\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:331:2\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/stdio2.h:105:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K%s\u001b[m\u001b[K' directive argument is null [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wformat-overflow=\u0007-Wformat-overflow=\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 105 | return \u001b[01;35m\u001b[K__fprintf_chk (__stream, __USE_FORTIFY_LEVEL - 1, __fmt,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 106 | \u001b[01;35m\u001b[K __va_arg_pack ())\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\nIn function '\u001b[01m\u001b[Kfprintf\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kusage_command_internal\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:254:3\u001b[m\u001b[K,\r\n inlined from '\u001b[01m\u001b[Kusage_command_usagestr\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:271:8\u001b[m\u001b[K,\r\n inlined from '\u001b[01m\u001b[Kusage\u001b[m\u001b[K' at \u001b[01m\u001b[Kcommon/help.c:331:2\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/stdio2.h:105:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K%s\u001b[m\u001b[K' directive argument is null [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wformat-overflow=\u0007-Wformat-overflow=\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 105 | return \u001b[01;35m\u001b[K__fprintf_chk (__stream, __USE_FORTIFY_LEVEL - 1, __fmt,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 106 | \u001b[01;35m\u001b[K __va_arg_pack ())\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] crypto/sha224-256.o\r\n [CC] crypto/hash.o\r\n [CC] libbtrfsutil/stubs.o\r\n [CC] libbtrfsutil/subvolume.o\r\n [CC] cmds/subvolume.o\r\n [CC] cmds/subvolume-list.o\r\n [CC] cmds/filesystem.o\r\n [CC] cmds/device.o\r\n [CC] cmds/scrub.o\r\n [CC] cmds/inspect.o\r\n [CC] cmds/balance.o\r\n [CC] cmds/send.o\r\n [CC] cmds/receive.o\r\n\u001b[01m\u001b[Kcmds/inspect.c:\u001b[m\u001b[K In function '\u001b[01m\u001b[K__ino_to_path_fd\u001b[m\u001b[K':\r\n\u001b[01m\u001b[Kcmds/inspect.c:70:21:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[Karray subscript '\u001b[01m\u001b[Ki\u001b[m\u001b[K' is outside the bounds of an interior zero-length array '\u001b[01m\u001b[K__u64[0]\u001b[m\u001b[K' {aka '\u001b[01m\u001b[Klong long unsigned int[]\u001b[m\u001b[K'} [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wzero-length-bounds\u0007-Wzero-length-bounds\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 70 | ptr += \u001b[01;35m\u001b[Kfspath->val[i]\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~^~~\u001b[m\u001b[K\r\nIn file included from \u001b[01m\u001b[Kcmds/inspect.c:27\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K./ioctl.h:500:8:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[Kwhile referencing '\u001b[01m\u001b[Kval\u001b[m\u001b[K'\r\n 500 | __u64 \u001b[01;36m\u001b[Kval\u001b[m\u001b[K[0]; /* out */\r\n | \u001b[01;36m\u001b[K^~~\u001b[m\u001b[K\r\n\u001b[01m\u001b[Kcmds/inspect.c:\u001b[m\u001b[K In function '\u001b[01m\u001b[Kcmd_inspect_logical_resolve\u001b[m\u001b[K':\r\n\u001b[01m\u001b[Kcmds/inspect.c:247:13:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[Karray subscript -1 is outside array bounds of '\u001b[01m\u001b[Kchar[4096]\u001b[m\u001b[K' [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Warray-bounds\u0007-Warray-bounds\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 247 | \u001b[01;35m\u001b[Kpath_ptr[-1]\u001b[m\u001b[K = '\\0';\r\n | \u001b[01;35m\u001b[K~~~~~~~~^~~~\u001b[m\u001b[K\r\n\u001b[01m\u001b[Kcmds/inspect.c:156:7:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[Kwhile referencing '\u001b[01m\u001b[Kfull_path\u001b[m\u001b[K'\r\n 156 | char \u001b[01;36m\u001b[Kfull_path\u001b[m\u001b[K[PATH_MAX];\r\n | \u001b[01;36m\u001b[K^~~~~~~~~\u001b[m\u001b[K\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/string.h:519\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[K./kerncompat.h:30\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kcmds/inspect.c:26\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kstrncpy\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kcmd_inspect_logical_resolve\u001b[m\u001b[K' at \u001b[01m\u001b[Kcmds/inspect.c:282:5\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/string_fortified.h:95:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K__builtin_strncpy\u001b[m\u001b[K' specified bound 4096 equals destination size [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wstringop-truncation\u0007-Wstringop-truncation\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 95 | return \u001b[01;35m\u001b[K__builtin___strncpy_chk (__dest, __src, __len,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 96 | \u001b[01;35m\u001b[K __glibc_objsize (__dest))\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] cmds/quota.o\r\n [CC] crypto/blake2b-ref.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/string.h:519\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[K./kerncompat.h:30\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kcmds/scrub.c:19\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kstrncpy\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kscrub_start\u001b[m\u001b[K' at \u001b[01m\u001b[Kcmds/scrub.c:1363:3\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/string_fortified.h:95:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K__builtin_strncpy\u001b[m\u001b[K' output may be truncated copying 107 bytes from a string of length 4095 [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wstringop-truncation\u0007-Wstringop-truncation\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 95 | return \u001b[01;35m\u001b[K__builtin___strncpy_chk (__dest, __src, __len,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 96 | \u001b[01;35m\u001b[K __glibc_objsize (__dest))\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] cmds/replace.o\r\n [CC] cmds/rescue.o\r\n [CC] cmds/rescue-chunk-recover.o\r\n [CC] cmds/rescue-super-recover.o\r\n [CC] cmds/property.o\r\n [CC] cmds/filesystem-usage.o\r\n [CC] cmds/inspect-dump-tree.o\r\n [CC] cmds/restore.o\r\n [CC] cmds/inspect-dump-super.o\r\n [CC] cmds/inspect-tree-stats.o\r\n [CC] check/main.o\r\n [CC] mkfs/common.o\r\n [CC] check/mode-common.o\r\n [CC] check/mode-lowmem.o\r\n [CC] libbtrfsutil/errors.o\r\n [CC] libbtrfsutil/filesystem.o\r\n [CC] libbtrfsutil/qgroup.o\r\n [CC] cmds/filesystem-du.o\r\n [CC] mkfs/rootdir.o\r\n [CC] btrfs-map-logical.o\r\n [CC] image/main.o\r\n [CC] image/sanitize.o\r\n [CC] convert/common.o\r\n [CC] convert/source-fs.o\r\n [CC] convert/source-ext2.o\r\n [CC] convert/source-reiserfs.o\r\n [CC] btrfs-corrupt-block.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/string.h:519\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kkerncompat.h:30\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kbtrfs-corrupt-block.c:26\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kstrncpy\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kmain\u001b[m\u001b[K' at \u001b[01m\u001b[Kbtrfs-corrupt-block.c:1318:5\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/string_fortified.h:95:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K__builtin_strncpy\u001b[m\u001b[K' specified bound 80 equals destination size [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wstringop-truncation\u0007-Wstringop-truncation\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 95 | return \u001b[01;35m\u001b[K__builtin___strncpy_chk (__dest, __src, __len,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 96 | \u001b[01;35m\u001b[K __glibc_objsize (__dest))\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] libbtrfs/send-stream.o\r\n [CC] libbtrfs/send-utils.o\r\n [LD] libbtrfsutil.so.1.2.0\r\nMaking all in Documentation\r\n [ASCII] btrfs-ioctl.xml\r\n [ASCII] btrfs-man5.xml\r\n [XMLTO] btrfs-ioctl.3\r\n [XMLTO] btrfs-man5.5\r\nrm btrfs-man5.xml btrfs-ioctl.xml\r\n [AR] libbtrfsutil.a\r\n [CC] convert/main.o\r\n [CC] btrfs-select-super.o\r\n [LN] libbtrfsutil.so.1\r\n [LN] libbtrfsutil.so\r\n [CC] btrfstune.o\r\n [PY] libbtrfsutil\r\n [CC] btrfs-find-root.o\r\n [CC] mkfs/main.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/string.h:519\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[K./kerncompat.h:30\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kconvert/main.c:83\u001b[m\u001b[K:\r\nIn function '\u001b[01m\u001b[Kstrncpy\u001b[m\u001b[K',\r\n inlined from '\u001b[01m\u001b[Kmain\u001b[m\u001b[K' at \u001b[01m\u001b[Kconvert/main.c:1940:6\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/35pjnvb806b8q94kvjngqh2crav07294-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-10.3.0/armv6l-unknown-linux-gnueabihf/sys-include/bits/string_fortified.h:95:10:\u001b[m\u001b[K \u001b[01;35m\u001b[Kwarning: \u001b[m\u001b[K'\u001b[01m\u001b[K__builtin_strncpy\u001b[m\u001b[K' specified bound 37 equals destination size [\u001b[01;35m\u001b[K\u001b]8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wstringop-truncation\u0007-Wstringop-truncation\u001b]8;;\u0007\u001b[m\u001b[K]\r\n 95 | return \u001b[01;35m\u001b[K__builtin___strncpy_chk (__dest, __src, __len,\u001b[m\u001b[K\r\n | \u001b[01;35m\u001b[K^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n 96 | \u001b[01;35m\u001b[K __glibc_objsize (__dest))\u001b[m\u001b[K;\r\n | \u001b[01;35m\u001b[K~~~~~~~~~~~~~~~~~~~~~~~~~\u001b[m\u001b[K\r\n [CC] cmds/qgroup.o\r\nIn file included from \u001b[01m\u001b[K/nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/include/python3.9/Python.h:50\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kbtrfsutilpy.h:27\u001b[m\u001b[K,\r\n from \u001b[01m\u001b[Kerror.c:20\u001b[m\u001b[K:\r\n\u001b[01m\u001b[K/nix/store/hym1n0ygqp9wcm7pxn4sfrql3fg7xa09-python3-3.9.12/include/python3.9/pyport.h:741:2:\u001b[m\u001b[K \u001b[01;31m\u001b[Kerror: \u001b[m\u001b[K#error \"LONG_BIT definition appears wrong for platform (bad gcc/glibc config?).\"\r\n 741 | #\u001b[01;31m\u001b[Kerror\u001b[m\u001b[K \"LONG_BIT definition appears wrong for platform (bad gcc/glibc config?).\"\r\n | \u001b[01;31m\u001b[K^~~~~\u001b[m\u001b[K\r\nerror: command '/nix/store/lxmy4hfcpg59knmh5iw37kmwx6f45ps2-armv6l-unknown-linux-gnueabihf-stage-final-gcc-debug-wrapper-10.3.0/bin/armv6l-unknown-linux-gnueabihf-gcc' failed with exit code 1\r\n [CC] crypto/crc32c.o\r\nmake: *** [Makefile:562: libbtrfsutil_python] Error 1\r\nmake: *** Waiting for unfinished jobs....\r\n\r\n```\r\n\r\nstaging is at : 9bdcee8f0451a95ad846eb064a29179467969b64","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168861/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168847","id":1205970631,"node_id":"I_kwDOAEVQ_M5H4abH","number":168847,"title":"nixos-help fails to detect browsers/opens in LibreOffice instead","user":{"login":"klemensn","id":91517496,"node_id":"U_kgDOBXRyOA","avatar_url":"https://avatars.githubusercontent.com/u/91517496?v=4","gravatar_id":"","url":"https://api.github.com/users/klemensn","html_url":"https://github.com/klemensn","followers_url":"https://api.github.com/users/klemensn/followers","following_url":"https://api.github.com/users/klemensn/following{/other_user}","gists_url":"https://api.github.com/users/klemensn/gists{/gist_id}","starred_url":"https://api.github.com/users/klemensn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/klemensn/subscriptions","organizations_url":"https://api.github.com/users/klemensn/orgs","repos_url":"https://api.github.com/users/klemensn/repos","events_url":"https://api.github.com/users/klemensn/events{/privacy}","received_events_url":"https://api.github.com/users/klemensn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-16T01:00:47Z","updated_at":"2022-04-20T14:46:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\n`nixos-help` always shows documentation in LibreOffice for me despite having\ninstalled three different browsers.\n\n### Steps To Reproduce\n1. install browsers either through `environment.systemPackage` or nix-shell:\n `$ nix-shell -p firefox -p chromium -p w3m`\n2. `$ nixos-help`\n```console\nkf.service.services: KApplicationTrader: mimeType \"x-scheme-handler/file\" not found\nkf.service.services: KApplicationTrader: mimeType \"x-scheme-handler/file\" not found\n\n```\n[... LibreOffice opens...]\n\n### Expected behavior\nOpening the HTML pages in any of the three installed browsers.\n\n### Additional context\nLooking at the sources, I wonder how it is supposed to work in the first place:\n```console\n$ cat $(which nixos-help)\n#!/nix/store/ld19k12mf0pa42ff43qs3sizamp09f03-bash-5.1-p16/bin/bash\n# Finds first executable browser in a colon-separated list.\n# (see how xdg-open defines BROWSER)\nbrowser=\"$(\n IFS=: ; for b in $BROWSER; do\n [ -n \"$(type -P \"$b\" || true)\" ] && echo \"$b\" && break\n done\n)\"\nif [ -z \"$browser\" ]; then\n browser=\"$(type -P xdg-open || true)\"\n if [ -z \"$browser\" ]; then\n browser=\"/nix/store/844ypdf9zlwnzrhh2f9h3x60p5lpysnd-w3m-0.5.3+git20190105/bin/w3m\"\n fi\nfi\nexec \"$browser\" /nix/store/g1gr02i6j8z4n3acjpcqfdbaxjs38i7n-nixos-manual-html/share/doc/nixos/index.html\n```\n\n`$BROWSER` is used but not defined anywhere in nixpkgs, so xdg-open(1) looks at\nthe file which is\n```console\nhtml=/nix/store/g1gr02i6j8z4n3acjpcqfdbaxjs38i7n-nixos-manual-html/share/doc/nixos/index.html\n$ file -b $html\nXML 1.0 document, Unicode text, UTF-8 text, with very long lines (9227)\n$ head -n2 $html\n<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"no\"?>\n<!DOCTYPE html PUBLIC \"-//W3C//DTD XHTML 1.0 Transitional//EN\" \"http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd\"><html xmlns=\"http://www.w3.org/1999/xhtml\"><head><meta http-equiv=\"Content-Type\" content=\"text/html; charset=UTF-8\" /><title>NixOS Manual</title><link rel=\"stylesheet\" type=\"text/css\" href=\"style.css\" /><link rel=\"stylesheet\" type=\"text/css\" href=\"overrides.css\" /><link rel=\"stylesheet\" type=\"text/css\" href=\"highlightjs/mono-blue.css\" /><script src=\"./highlightjs/highlight.pack.js\" type=\"text/javascript\"></script><script src=\"./highlightjs/loader.js\" type=\"text/javascript\"></script><meta name=\"generator\" content=\"DocBook XSL Stylesheets V1.79.2\" /><link rel=\"home\" href=\"index.html\" title=\"NixOS Manual\" /><link rel=\"next\" href=\"options.html\" title=\"Appendix A. Configuration Options\" /></head><body><div class=\"navheader\"><table width=\"100%\" summary=\"Navigation header\"><tr><th colspan=\"3\" align=\"center\">NixOS Manual</th></tr><tr><td width=\"20%\" align=\"left\"> </td><th width=\"60%\" align=\"center\"> </th><td width=\"20%\" align=\"right\"> <a accesskey=\"n\" href=\"options.html\">Next</a></td></tr></table><hr /></div><div class=\"book\"><div class=\"titlepage\"><div><div><h1 class=\"title\"><a id=\"book-nixos-manual\"></a>NixOS Manual</h1></div><div><h2 class=\"subtitle\">Version 22.05\n```\n\nNo surprise xdg-open(1) picks a non-browser tool for it.\n\n`BROWSER=firefox nixos-help` works around this does not help the \"NixOS Manual\"\n.desktop entry.\n\n### Metadata\n```console\n - system: `\"x86_64-linux\"`\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05pre368234.fd364d26885`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - channels(root): `\"nixos\"`\n - channels(kn): `\"nixos\"`\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168847/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168843","id":1205957751,"node_id":"I_kwDOAEVQ_M5H4XR3","number":168843,"title":"libxfs in environment.systemPackages does not provide mkfs.xfs(1) in PATH","user":{"login":"klemensn","id":91517496,"node_id":"U_kgDOBXRyOA","avatar_url":"https://avatars.githubusercontent.com/u/91517496?v=4","gravatar_id":"","url":"https://api.github.com/users/klemensn","html_url":"https://github.com/klemensn","followers_url":"https://api.github.com/users/klemensn/followers","following_url":"https://api.github.com/users/klemensn/following{/other_user}","gists_url":"https://api.github.com/users/klemensn/gists{/gist_id}","starred_url":"https://api.github.com/users/klemensn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/klemensn/subscriptions","organizations_url":"https://api.github.com/users/klemensn/orgs","repos_url":"https://api.github.com/users/klemensn/repos","events_url":"https://api.github.com/users/klemensn/events{/privacy}","received_events_url":"https://api.github.com/users/klemensn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-16T00:03:33Z","updated_at":"2022-04-16T11:37:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\nMerely installing `libxfs` aka. `xfsprogs.dev` as opposed to the full `xfsprogs`\npackage does not make mkfs.xfs(1) reachable via `PATH` lookup.\n\nConsider creating a new XFS filesytem from scratch without having any XFS\ntooling installed:\n\n```console\n$ mkfs.xfs -h\nThe program 'mkfs.xfs' is not in your PATH. You can make it available in an\nephemeral shell by typing:\n nix-shell -p libxfs\n$ nix-shell -p libxfs\n[... download...]\n[... do the work...]\n$ exit\n# nixos-rebuild edit\n[... add libxfs to environment.systemPackages...]\n# nixos-rebuild switch\n$ mkfs.xfs\nThe program 'mkfs.xfs' is not in your PATH. You can make it available in an\nephemeral shell by typing:\n nix-shell -p libxfs\n```\n\nnix-shell(1) does the trick and installing libxfs does install it, but\nmkfs.xfs(1) remains unreachable unless explicitly spawn a shell each time.\n\nInstalling \"xfsprogs\" rather than \"libxfs\" system wide sucessfully makes\nmkfs.xfs(1) available without nix-shell(1), but it also pulls in undesired\nall the other XFS tools.\n\n### Steps To Reproduce\n1. `# nixos-rebuild edit`\n2. [... add \"libxfs\" to `environment.systemPackages`...]\n3. `# nixos-rebuild switch`\n4. `$ mkfs.xfs -h`\n\n### Expected behavior\nInstalling \"libxfs\" system wide should make mkfs.xfs(1) available.\n\n### Notify maintainers\n@dezgeg @ajs124\n\n### Metadata\n```console\n - system: `\"x86_64-linux\"`\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05pre368234.fd364d26885`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - channels(root): `\"nixos\"`\n - channels(kn): `\"nixos\"`\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168843/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168842","id":1205954260,"node_id":"I_kwDOAEVQ_M5H4WbU","number":168842,"title":"Giara fails to start: RuntimeError: could not create new GType: giara+giara_clamp+GiaraClamp (subclass of AdwClamp)","user":{"login":"klemensn","id":91517496,"node_id":"U_kgDOBXRyOA","avatar_url":"https://avatars.githubusercontent.com/u/91517496?v=4","gravatar_id":"","url":"https://api.github.com/users/klemensn","html_url":"https://github.com/klemensn","followers_url":"https://api.github.com/users/klemensn/followers","following_url":"https://api.github.com/users/klemensn/following{/other_user}","gists_url":"https://api.github.com/users/klemensn/gists{/gist_id}","starred_url":"https://api.github.com/users/klemensn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/klemensn/subscriptions","organizations_url":"https://api.github.com/users/klemensn/orgs","repos_url":"https://api.github.com/users/klemensn/repos","events_url":"https://api.github.com/users/klemensn/events{/privacy}","received_events_url":"https://api.github.com/users/klemensn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-15T23:48:53Z","updated_at":"2022-04-15T23:48:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\ngiara fails to start but merely prints a python backtrace.\n\n### Steps To Reproduce\nSteps to reproduce the behavior:\n1. $ `nix-shell -p giara` or add \"pkgs.giara\" to `environment.systemPackages`\n and rebuild the system\n2. $ giara\n\n```console\n/nix/store/dixynjprqk0fzbhkryv6j049svkx6b98-python3.9-pygobject-3.42.0/lib/python3.9/site-packages/gi/types.py:217: Warning: cannot derive 'giara+giara_clamp+GiaraClamp' from final parent type 'AdwClamp'\n _gi.type_register(cls, namespace.get('__gtype_name__'))\nTraceback (most recent call last):\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/bin/..giara-wrapped-wrapped\", line 68, in <module>\n from giara import __main__\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/__main__.py\", line 8, in <module>\n from giara.app_window import AppWindow\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/app_window.py\", line 4, in <module>\n from giara.main_ui import MainUI\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/main_ui.py\", line 4, in <module>\n from giara.main_deck import MainDeck\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/main_deck.py\", line 2, in <module>\n from giara.left_stack import LeftStack\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/left_stack.py\", line 3, in <module>\n from giara.sections import PostListSection\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/sections.py\", line 2, in <module>\n from giara.post_preview_listview import PostPreviewListView\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/post_preview_listview.py\", line 5, in <module>\n from giara.giara_clamp import GiaraClampScrollable\n File \"/nix/store/aqji0xafsdyzsd7yc7jiy33ylckbcc12-giara-1.0/lib/python3.9/site-packages/giara/giara_clamp.py\", line 4, in <module>\n class GiaraClamp(Adw.Clamp):\n File \"/nix/store/dixynjprqk0fzbhkryv6j049svkx6b98-python3.9-pygobject-3.42.0/lib/python3.9/site-packages/gi/types.py\", line 226, in __init__\n super(GObjectMeta, cls).__init__(name, bases, dict_)\n File \"/nix/store/dixynjprqk0fzbhkryv6j049svkx6b98-python3.9-pygobject-3.42.0/lib/python3.9/site-packages/gi/types.py\", line 205, in __init__\n cls._type_register(cls.__dict__)\n File \"/nix/store/dixynjprqk0fzbhkryv6j049svkx6b98-python3.9-pygobject-3.42.0/lib/python3.9/site-packages/gi/types.py\", line 217, in _type_register\n _gi.type_register(cls, namespace.get('__gtype_name__'))\nRuntimeError: could not create new GType: giara+giara_clamp+GiaraClamp (subclass of AdwClamp)\n```\n\n### Expected behavior\nStart up the graphical reddit client.\n\n### Additional context\nAdd any other context about the problem here.\n\n### Notify maintainers\n@dasj19\n\n### Metadata\n```console\n - system: `\"x86_64-linux\"`\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05pre368234.fd364d26885`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - channels(root): `\"nixos\"`\n - channels(kn): `\"nixos\"`\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168842/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168829","id":1205877855,"node_id":"I_kwDOAEVQ_M5H4Dxf","number":168829,"title":"logrotate fails to finalize on riscv64 build","user":{"login":"Madouura","id":93990818,"node_id":"U_kgDOBZovog","avatar_url":"https://avatars.githubusercontent.com/u/93990818?v=4","gravatar_id":"","url":"https://api.github.com/users/Madouura","html_url":"https://github.com/Madouura","followers_url":"https://api.github.com/users/Madouura/followers","following_url":"https://api.github.com/users/Madouura/following{/other_user}","gists_url":"https://api.github.com/users/Madouura/gists{/gist_id}","starred_url":"https://api.github.com/users/Madouura/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Madouura/subscriptions","organizations_url":"https://api.github.com/users/Madouura/orgs","repos_url":"https://api.github.com/users/Madouura/repos","events_url":"https://api.github.com/users/Madouura/events{/privacy}","received_events_url":"https://api.github.com/users/Madouura/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-15T20:46:24Z","updated_at":"2022-04-22T00:28:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAs the title states, it does not finish (cross) compiling to riscv64.\r\n\r\n```bash\r\npost-installation fixup\r\nshrinking RPATHs of ELF executables and libraries in /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0\r\nshrinking /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0/sbin/logrotate\r\ngzipping man pages under /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0/share/man/\r\nriscv64-unknown-linux-gnu-strip is /nix/store/pmbl1qd8iqk4b44sdrj3advh8s9gcfbq-riscv64-unknown-linux-gnu-stage-final-gcc-debug-wrapper-10.3.0/bin/riscv64-unknown-linux-gnu-strip\r\nstripping (with command riscv64-unknown-linux-gnu-strip and flags -S) in /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0/sbin\r\npatching script interpreter paths in /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0\r\nchecking for references to /build/ in /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0...\r\nmoving /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0/sbin/* to /nix/store/yl7lljq9mcqci0k7wlbns4xm8fjz6321-logrotate-riscv64-unknown-linux-gnu-3.19.0/bin\r\nbuilding '/nix/store/n3nq3d79cvsf98b5pw1z88jn74xp43fv-logrotate.conf.drv'...\r\n/build/.attr-0: line 14: /nix/store/76ry6fv0c7n31ah9jg0jm3mqci2n5knb-coreutils-riscv64-unknown-linux-gnu-9.0/bin/id: cannot execute binary file: Exec format error\r\nbuilder for '/nix/store/n3nq3d79cvsf98b5pw1z88jn74xp43fv-logrotate.conf.drv' failed with exit code 126\r\ncannot build derivation '/nix/store/a02x84vy2bak2b78m5vasdik8sd3nbf8-unit-logrotate-checkconf.service.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/cjzi5xqb95swyk490c3fv5jy0p4fwzw5-unit-logrotate.service.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/vacc5bn1szk99p3pyb2q220xphyl6srj-system-units.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/wh3v282827cxpa4zfmlp5j7mrgxrjhk0-etc.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/x24y87d0lpdz6ql2yfv3gfhkyfmabr6x-nixos-system-nixos-22.05pre-git.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/wp1h969krwbwlfdcqnrf106cgx062x8m-ext4-fs.img.zst-riscv64-unknown-linux-gnu.drv': 1 dependencies couldn't be built\r\ncannot build derivation '/nix/store/7rv1nz4ksch76g316s6wqpcghqzxklxl-nixos-sd-image-22.05pre-git-riscv64-linux-visionfive.img-riscv64-unknown-linux-gnu.drv': 1 dependencies couldn't be built\r\nerror: build of '/nix/store/7rv1nz4ksch76g316s6wqpcghqzxklxl-nixos-sd-image-22.05pre-git-riscv64-linux-visionfive.img-riscv64-unknown-linux-gnu.drv' failed\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set up cross compilation either in nix-build or in your system.\r\n2. Attempt to finalize logrotate build\r\n3. ???\r\n4. It's borked!\r\n\r\n### Expected behavior\r\nIt should have compiled.\r\n\r\n### Additional context\r\nCurrently attempting a cross-compile for VisionFive.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@viric \r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.19, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11, home-manager-21.11\"`\r\n - channels(mado): `\"home-manager-21.11, nixos-21.11.337053.2f06b87f64b, nixos-unstable-22.05pre369117.ff9efb0724d\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168829/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168821","id":1205844329,"node_id":"I_kwDOAEVQ_M5H37lp","number":168821,"title":"libvirt VMs being stopped on system upgrade?","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-15T19:43:53Z","updated_at":"2022-04-20T14:45:00Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nFiling this so I can test and revisit. I'm pretty sure I lost some libvirt guests due to a system upgrade...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168821/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168809","id":1205756017,"node_id":"I_kwDOAEVQ_M5H3mBx","number":168809,"title":"SteamVR does not work","user":{"login":"wizardwatch","id":48140117,"node_id":"MDQ6VXNlcjQ4MTQwMTE3","avatar_url":"https://avatars.githubusercontent.com/u/48140117?v=4","gravatar_id":"","url":"https://api.github.com/users/wizardwatch","html_url":"https://github.com/wizardwatch","followers_url":"https://api.github.com/users/wizardwatch/followers","following_url":"https://api.github.com/users/wizardwatch/following{/other_user}","gists_url":"https://api.github.com/users/wizardwatch/gists{/gist_id}","starred_url":"https://api.github.com/users/wizardwatch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wizardwatch/subscriptions","organizations_url":"https://api.github.com/users/wizardwatch/orgs","repos_url":"https://api.github.com/users/wizardwatch/repos","events_url":"https://api.github.com/users/wizardwatch/events{/privacy}","received_events_url":"https://api.github.com/users/wizardwatch/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-15T17:43:22Z","updated_at":"2022-04-17T17:05:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nOn recent builds of NixOS unstable, SteamVR fails with the error \"A key component of SteamVR isn't working properly.\" and the error code 307. Reverting back to an old build with Kernel 5.10 works, so it may be related to the kernel version. I tried updating to the latest kernel, both zen and vanilla based on https://gitlab.freedesktop.org/drm/amd/-/issues/1856, but this did not resolve the issue. I use an amd 5700xt for my GPU.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Steam from latest unstable\r\n2. Launch SteamVR with valve index\r\n\r\n### Expected behavior\r\nSteamVR works without issue.\r\n\r\n\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.2, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220411_f7276bc`\r\n - channels(wyatt): `\"nixos-21.05pre281538.9e377a6ce42\"`\r\n - channels(root): `\"nixos-21.05pre290427.673aea9f84c\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168809/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168769","id":1205431574,"node_id":"I_kwDOAEVQ_M5H2W0W","number":168769,"title":"Neovide failes in mixed glibc configuration","user":{"login":"ck3d","id":25088352,"node_id":"MDQ6VXNlcjI1MDg4MzUy","avatar_url":"https://avatars.githubusercontent.com/u/25088352?v=4","gravatar_id":"","url":"https://api.github.com/users/ck3d","html_url":"https://github.com/ck3d","followers_url":"https://api.github.com/users/ck3d/followers","following_url":"https://api.github.com/users/ck3d/following{/other_user}","gists_url":"https://api.github.com/users/ck3d/gists{/gist_id}","starred_url":"https://api.github.com/users/ck3d/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ck3d/subscriptions","organizations_url":"https://api.github.com/users/ck3d/orgs","repos_url":"https://api.github.com/users/ck3d/repos","events_url":"https://api.github.com/users/ck3d/events{/privacy}","received_events_url":"https://api.github.com/users/ck3d/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":333381548,"node_id":"MDU6TGFiZWwzMzMzODE1NDg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20rust","name":"6.topic: rust","color":"fef2c0","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-15T09:30:57Z","updated_at":"2022-04-20T14:44:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nIf you run NixOS 21.11 which uses glibc version 2.33 and want to run neovide from nixon-unstabled which is compiled with glibc version 2.34, then neovide failes to start.\r\n\r\nGlibc 2.34 was introduced with https://github.com/NixOS/nixpkgs/pull/133431\r\n\r\n### Steps To Reproduce\r\n\r\n```\r\n$ neovide --nofork\r\nthread 'main' panicked at 'called `Result::unwrap()` on an `Err` value: CreationErrors([OsError(\"Could not create EGL display object\"), OsError(\"`glXQueryExtensionsString` found no glX extensions\")])', src/window/mod.rs:331:10\r\n```\r\n\r\n### Expected behavior\r\n\r\nThe application starts.\r\n\r\n### Notify maintainers\r\n\r\nI am the maintainer.\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.2-xanmod1-tt, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/l5lbpfccaxn6scvkaawj5hhi13if8d6q-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168769/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168767","id":1205410946,"node_id":"I_kwDOAEVQ_M5H2RyC","number":168767,"title":"Weird extendModules behaviour when used inside a submodule","user":{"login":"minijackson","id":1200507,"node_id":"MDQ6VXNlcjEyMDA1MDc=","avatar_url":"https://avatars.githubusercontent.com/u/1200507?v=4","gravatar_id":"","url":"https://api.github.com/users/minijackson","html_url":"https://github.com/minijackson","followers_url":"https://api.github.com/users/minijackson/followers","following_url":"https://api.github.com/users/minijackson/following{/other_user}","gists_url":"https://api.github.com/users/minijackson/gists{/gist_id}","starred_url":"https://api.github.com/users/minijackson/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/minijackson/subscriptions","organizations_url":"https://api.github.com/users/minijackson/orgs","repos_url":"https://api.github.com/users/minijackson/repos","events_url":"https://api.github.com/users/minijackson/events{/privacy}","received_events_url":"https://api.github.com/users/minijackson/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":126506370,"node_id":"MDU6TGFiZWwxMjY1MDYzNzA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20work-in-progress","name":"2.status: work-in-progress","color":"e6e6e6","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-15T09:02:38Z","updated_at":"2022-04-26T21:12:53Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen `extendModules` is used inside a submodule, strange collisions / \"not defined\" errors can happen\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. From this flake:\r\n\r\n```nix\r\n{\r\n inputs.nixpkgs.url = \"github:NixOS/nixpkgs\";\r\n outputs = {\r\n self,\r\n nixpkgs,\r\n }:\r\n with nixpkgs.lib; {\r\n lib.thing = evalModules {\r\n modules = [\r\n ({\r\n lib,\r\n extendModules,\r\n ...\r\n }: {\r\n options.sub = mkOption {\r\n default = {};\r\n type = types.submodule ({\r\n config,\r\n extendModules,\r\n ...\r\n }: {\r\n options.value = mkOption {\r\n type = types.int;\r\n };\r\n\r\n options.specialisation = mkOption {\r\n default = {};\r\n inherit\r\n (extendModules {\r\n modules = [{specialisation = mkOverride 0 {};}];\r\n })\r\n type\r\n ;\r\n };\r\n });\r\n };\r\n })\r\n {config.sub.value = 1;}\r\n ];\r\n };\r\n };\r\n}\r\n\r\n```\r\n\r\n2. If we do `nix eval '.#lib.thing.config.sub.specialisation.value'`, we get:\r\n\r\n```\r\nerror: The option `sub.specialisation.value' is used but not defined.\r\n```\r\n\r\n3. But if we add `{config.sub.specialisation.value = mkDefault 2;}` to the modules of `evalModules`, we get:\r\n\r\n```\r\n1\r\n```\r\n\r\nSo from my understanding it wrongly assumes that the option isn't defined since it's not defined at the local level, but if defined locally still gets the global value afterwards.\r\n\r\n4. Weirdly enough, if we add `{config.sub.specialisation.value = 2;}` instead (without the `mkDefault`), we get:\r\n\r\n```\r\nerror: The option `sub.specialisation.value' has conflicting definition values:\r\n - In `<unknown-file>': 1\r\n - In `<unknown-file>': 2\r\n```\r\n\r\nBut doing it in the same module as the setting of `config.sub.value` doesn't yield this error, and correctly reports back 2.\r\n\r\n### Expected behavior\r\n\r\n- Just setting `config.sub.value = 1` should be enough for `sub.specialisation.value == 1`.\r\n- Also setting `config.sub.specialisation.value = 2` either in the same module or in another one should set the specialised value to 2.\r\n\r\n### Additional context\r\n\r\nThe usecase I have for this is that I'm developing a deployment tool. At the top-level we define an attrset of nodes, whose configurations are submodules. I would like to have specialisation support at the node level, and came across `extendModules` by reading how NixOS does it.\r\n\r\n### Notify maintainers\r\n\r\n@roberth as the creator of `extendModules` (thank you a lot for that, by the way!)\r\n\r\n### Metadata\r\n\r\nN/A","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168767/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168694","id":1204844266,"node_id":"I_kwDOAEVQ_M5H0Hbq","number":168694,"title":"Vulnerability roundup 113: xerces-c-3.2.3: 1 advisory [8.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:19:12Z","updated_at":"2022-04-24T12:16:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=xerces-c&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=xerces-c+in%3Apath&type=Code)\n\n* [ ] [CVE-2018-1311](https://nvd.nist.gov/vuln/detail/CVE-2018-1311) CVSSv3=8.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2018-1311\n\nThe Apache Xerces-C 3.0.0 to 3.2.3 XML parser contains a use-after-free error triggered during the scanning of external DTDs. This flaw has not been addressed in the maintained version of the library and has no current mitigation other than to disable DTD processing. This can be accomplished via the DOM using a standard parser feature, or via SAX using the XERCES_DISABLE_DTD environment variable.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168694/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168692","id":1204844189,"node_id":"I_kwDOAEVQ_M5H0Had","number":168692,"title":"Vulnerability roundup 113: vyper-0.3.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:19:08Z","updated_at":"2022-04-24T12:24:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=vyper&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=vyper+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24787](https://nvd.nist.gov/vuln/detail/CVE-2022-24787) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-24787\n\nVyper is a Pythonic Smart Contract Language for the Ethereum Virtual Machine. In version 0.3.1 and prior, bytestrings can have dirty bytes in them, resulting in the word-for-word comparisons giving incorrect results. Even without dirty nonzero bytes, two bytestrings can compare to equal if one ends with `\"\\x00\"` because there is no comparison of the length. A patch is available and expected to be part of the 0.3.2 release. There are currently no known workarounds.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @siraben\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168692/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168691","id":1204844164,"node_id":"I_kwDOAEVQ_M5H0HaE","number":168691,"title":"Vulnerability roundup 113: vyper-0.3.0: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:19:05Z","updated_at":"2022-04-24T12:24:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=vyper&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=vyper+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24787](https://nvd.nist.gov/vuln/detail/CVE-2022-24787) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24787\n\nVyper is a Pythonic Smart Contract Language for the Ethereum Virtual Machine. In version 0.3.1 and prior, bytestrings can have dirty bytes in them, resulting in the word-for-word comparisons giving incorrect results. Even without dirty nonzero bytes, two bytestrings can compare to equal if one ends with `\"\\x00\"` because there is no comparison of the length. A patch is available and expected to be part of the 0.3.2 release. There are currently no known workarounds.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @siraben\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168691/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168690","id":1204844118,"node_id":"I_kwDOAEVQ_M5H0HZW","number":168690,"title":"Vulnerability roundup 113: vim-8.2.4350: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506370,"node_id":"MDU6TGFiZWwxMjY1MDYzNzA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20work-in-progress","name":"2.status: work-in-progress","color":"e6e6e6","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-14T18:19:02Z","updated_at":"2022-04-24T12:40:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=vim&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=vim+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1154](https://nvd.nist.gov/vuln/detail/CVE-2022-1154) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2022-1160](https://nvd.nist.gov/vuln/detail/CVE-2022-1160) CVSSv3=7.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-1154\n\nUse after free in utf_ptr2char in GitHub repository vim/vim prior to 8.2.4646.\n\n### CVE-2022-1160\n\nheap buffer overflow in get_one_sourceline in GitHub repository vim/vim prior to 8.2.4647.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @equirosa\nCc @lovek323\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168690/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168685","id":1204843959,"node_id":"I_kwDOAEVQ_M5H0HW3","number":168685,"title":"Vulnerability roundup 113: radare2-5.6.2: 3 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:18:49Z","updated_at":"2022-04-14T18:18:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=radare2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=radare2+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1061](https://nvd.nist.gov/vuln/detail/CVE-2022-1061) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-1207](https://nvd.nist.gov/vuln/detail/CVE-2022-1207) CVSSv3=6.6 (nixos-21.11)\n* [ ] [CVE-2022-1052](https://nvd.nist.gov/vuln/detail/CVE-2022-1052) CVSSv3=5.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-1061\n\nHeap Buffer Overflow in parseDragons in GitHub repository radareorg/radare2 prior to 5.6.8.\n\n### CVE-2022-1207\n\nOut-of-bounds read in GitHub repository radareorg/radare2 prior to 5.6.8. This vulnerability allows attackers to read sensitive information from outside the allocated buffer boundary.\n\n### CVE-2022-1052\n\nHeap Buffer Overflow in iterate_chained_fixups in GitHub repository radareorg/radare2 prior to 5.6.6.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @7c6f434c\nCc @arkivm\nCc @makefu\nCc @mic92\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168685/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168683","id":1204839132,"node_id":"I_kwDOAEVQ_M5H0GLc","number":168683,"title":"Vulnerability roundup 113: qemu-6.2.0: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:13:45Z","updated_at":"2022-04-29T22:47:15Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=qemu&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=qemu+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1050](https://nvd.nist.gov/vuln/detail/CVE-2022-1050) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-1050\n\nGuest driver might execute HW commands when shared buffers are not yet allocated, potentially leading to a use-after-free condition.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @alyssais\nCc @edolstra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168683/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168682","id":1204839091,"node_id":"I_kwDOAEVQ_M5H0GKz","number":168682,"title":"Vulnerability roundup 113: qemu-6.1.1: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:13:42Z","updated_at":"2022-04-14T18:13:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=qemu&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=qemu+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1050](https://nvd.nist.gov/vuln/detail/CVE-2022-1050) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-1050\n\nGuest driver might execute HW commands when shared buffers are not yet allocated, potentially leading to a use-after-free condition.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @alyssais\nCc @edolstra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168682/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168680","id":1204839031,"node_id":"I_kwDOAEVQ_M5H0GJ3","number":168680,"title":"Vulnerability roundup 113: podman-3.4.3: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:13:38Z","updated_at":"2022-04-14T18:13:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=podman&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=podman+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-27649](https://nvd.nist.gov/vuln/detail/CVE-2022-27649) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-27649\n\nA flaw was found in Podman, where containers were started incorrectly with non-empty default permissions. A vulnerability was found in Moby (Docker Engine), where containers were started incorrectly with non-empty inheritable Linux process capabilities. This flaw allows an attacker with access to programs with inheritable file capabilities to elevate those capabilities to the permitted set when execve(2) runs.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @adisbladis\nCc @kalbasit\nCc @marsam\nCc @saschagrunert\nCc @vdemeester\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168680/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168679","id":1204838977,"node_id":"I_kwDOAEVQ_M5H0GJB","number":168679,"title":"Vulnerability roundup 113: pjsip-2.12: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:13:35Z","updated_at":"2022-04-14T18:13:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=pjsip&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=pjsip+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24786](https://nvd.nist.gov/vuln/detail/CVE-2022-24786) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-24763](https://nvd.nist.gov/vuln/detail/CVE-2022-24763) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-24786\n\nPJSIP is a free and open source multimedia communication library written in C. PJSIP versions 2.12 and prior do not parse incoming RTCP feedback RPSI (Reference Picture Selection Indication) packet, but any app that directly uses pjmedia_rtcp_fb_parse_rpsi() will be affected. A patch is available in the `master` branch of the `pjsip/pjproject` GitHub repository. There are currently no known workarounds.\n\n### CVE-2022-24763\n\nPJSIP is a free and open source multimedia communication library written in the C language. Versions 2.12 and prior contain a denial-of-service vulnerability that affects PJSIP users that consume PJSIP's XML parsing in their apps. Users are advised to update. There are no known workarounds.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @olynch\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168679/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168678","id":1204838936,"node_id":"I_kwDOAEVQ_M5H0GIY","number":168678,"title":"Vulnerability roundup 113: openjpeg-2.4.0: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:13:32Z","updated_at":"2022-04-14T18:13:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=openjpeg&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=openjpeg+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1122](https://nvd.nist.gov/vuln/detail/CVE-2022-1122) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-1122\n\nA flaw was found in the opj2_decompress program in openjpeg2 2.4.0 in the way it handles an input directory with a large number of files. When it fails to allocate a buffer to store the filenames of the input directory, it calls free() on an uninitialized pointer, leading to a segmentation fault and a denial of service.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @codyopel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168678/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168677","id":1204838915,"node_id":"I_kwDOAEVQ_M5H0GID","number":168677,"title":"Vulnerability roundup 113: nginx-1.20.2: 1 advisory [7.4]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:13:30Z","updated_at":"2022-04-14T18:13:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=nginx&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=nginx+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-3618](https://nvd.nist.gov/vuln/detail/CVE-2021-3618) CVSSv3=7.4 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-3618\n\nALPACA is an application layer protocol content confusion attack, exploiting TLS servers implementing different protocols but using compatible certificates, such as multi-domain or wildcard certificates. A MiTM attacker having access to victim's traffic at the TCP/IP layer can redirect traffic from one subdomain to another, resulting in a valid TLS session. This breaks the authentication of TLS and cross-protocol attacks may be possible where the behavior of one protocol service may compromise the other at the application layer.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @7c6f434c\nCc @ajs124\nCc @fpletz\nCc @globin\nCc @thoughtpolice\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168677/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168675","id":1204838828,"node_id":"I_kwDOAEVQ_M5H0GGs","number":168675,"title":"Vulnerability roundup 113: mediawiki-1.36.4: 6 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:13:25Z","updated_at":"2022-04-14T18:13:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mediawiki&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mediawiki+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-28205](https://nvd.nist.gov/vuln/detail/CVE-2022-28205) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2022-28206](https://nvd.nist.gov/vuln/detail/CVE-2022-28206) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2022-28209](https://nvd.nist.gov/vuln/detail/CVE-2022-28209) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2021-45472](https://nvd.nist.gov/vuln/detail/CVE-2021-45472) CVSSv3=6.1 (nixos-21.11)\n* [ ] [CVE-2021-45474](https://nvd.nist.gov/vuln/detail/CVE-2021-45474) CVSSv3=6.1 (nixos-21.11)\n* [ ] [CVE-2021-45471](https://nvd.nist.gov/vuln/detail/CVE-2021-45471) CVSSv3=5.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-28205\n\nAn issue was discovered in MediaWiki through 1.37.1. The CentralAuth extension mishandles a ttl issue for groups expiring in the future.\n\n### CVE-2022-28206\n\nAn issue was discovered in MediaWiki through 1.37.1. ImportPlanValidator.php in the FileImporter extension mishandles the check for edit rights.\n\n### CVE-2022-28209\n\nAn issue was discovered in Mediawiki through 1.37.1. The check for the override-antispoof permission in the AntiSpoof extension is incorrect.\n\n### CVE-2021-45472\n\nIn MediaWiki through 1.37, XSS can occur in Wikibase because an external identifier property can have a URL format that includes a $1 formatter substitution marker, and the javascript: URL scheme (among others) can be used.\n\n### CVE-2021-45474\n\nIn MediaWiki through 1.37, the Special:ImportFile URI (aka FileImporter) allows XSS, as demonstrated by the clientUrl parameter.\n\n### CVE-2021-45471\n\nIn MediaWiki through 1.37, blocked IP addresses are allowed to edit EntitySchema items.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @redvers\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168675/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168674","id":1204838799,"node_id":"I_kwDOAEVQ_M5H0GGP","number":168674,"title":"Vulnerability roundup 113: lua-5.4.3: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:13:22Z","updated_at":"2022-04-14T18:13:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=lua&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=lua+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-44647](https://nvd.nist.gov/vuln/detail/CVE-2021-44647) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-44647\n\nLua 5.4.4 and 5.4.2 are affected by SEGV by type confusion in funcnamefromcode function in ldebug.c which can cause a local denial of service.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168674/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168673","id":1204838716,"node_id":"I_kwDOAEVQ_M5H0GE8","number":168673,"title":"Vulnerability roundup 113: libtiff-4.3.0: 2 advisories [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-14T18:13:17Z","updated_at":"2022-04-23T22:53:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=libtiff&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=libtiff+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1210](https://nvd.nist.gov/vuln/detail/CVE-2022-1210) CVSSv3=6.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-1056](https://nvd.nist.gov/vuln/detail/CVE-2022-1056) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-1210\n\nA vulnerability classified as problematic was found in LibTIFF 4.3.0. Affected by this vulnerability is the TIFF File Handler of tiff2ps. Opening a malicious file leads to a denial of service. The attack can be launched remotely but requires user interaction. The exploit has been disclosed to the public and may be used.\n\n### CVE-2022-1056\n\nOut-of-bounds Read error in tiffcrop in libtiff 4.3.0 allows attackers to cause a denial-of-service via a crafted tiff file. For users that compile libtiff from sources, the fix is available with commit 46dc8fcd.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @alyssais\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168673/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168671","id":1204838656,"node_id":"I_kwDOAEVQ_M5H0GEA","number":168671,"title":"Vulnerability roundup 113: jenkins-2.332.2: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:13:13Z","updated_at":"2022-04-14T18:13:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=jenkins&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=jenkins+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0538](https://nvd.nist.gov/vuln/detail/CVE-2022-0538) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0538\n\nJenkins 2.333 and earlier, LTS 2.319.2 and earlier defines custom XStream converters that have not been updated to apply the protections for the vulnerability CVE-2021-43859 and allow unconstrained resource usage.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @coreyoconnor\nCc @earldouglas\nCc @fpletz\nCc @nequissimus\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168671/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168668","id":1204833110,"node_id":"I_kwDOAEVQ_M5H0EtW","number":168668,"title":"Vulnerability roundup 113: htmldoc-1.9.14: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:08:09Z","updated_at":"2022-04-14T18:08:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=htmldoc&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=htmldoc+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24191](https://nvd.nist.gov/vuln/detail/CVE-2022-24191) CVSSv3=5.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24191\n\nIn HTMLDOC 1.9.14, an infinite loop in the gif_read_lzw function can lead to a pointer arbitrarily pointing to heap memory and resulting in a buffer overflow.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @shanemikel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168668/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168667","id":1204833048,"node_id":"I_kwDOAEVQ_M5H0EsY","number":168667,"title":"Vulnerability roundup 113: gradle-7.4.2: 1 advisory [8.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:08:07Z","updated_at":"2022-04-17T15:57:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25364](https://nvd.nist.gov/vuln/detail/CVE-2022-25364) CVSSv3=8.1 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-25364\n\nIn Gradle Enterprise before 2021.4.2, the default built-in build cache configuration allowed anonymous write access. If this was not manually changed, a malicious actor with network access to the build cache could potentially populate it with manipulated entries that execute malicious code as part of a build. As of 2021.4.2, the built-in build cache is inaccessible-by-default, requiring explicit configuration of its access-control settings before it can be used. (Remote build cache nodes are unaffected as they are inaccessible-by-default.)\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @liff\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168667/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168666","id":1204832980,"node_id":"I_kwDOAEVQ_M5H0ErU","number":168666,"title":"Vulnerability roundup 113: gpac-2.0.0: 1 advisory [5.0]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:08:05Z","updated_at":"2022-04-14T18:08:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gpac&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gpac+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1172](https://nvd.nist.gov/vuln/detail/CVE-2022-1172) CVSSv3=5.0 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-1172\n\nNull Pointer Dereference Caused Segmentation Fault in GitHub repository gpac/gpac prior to 2.1.0-DEV.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @bluescreen303\nCc @mgdelacroix\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168666/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168665","id":1204832869,"node_id":"I_kwDOAEVQ_M5H0Epl","number":168665,"title":"Vulnerability roundup 113: gpac-1.0.1: 2 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:08:01Z","updated_at":"2022-04-14T18:08:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gpac&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gpac+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-1222](https://nvd.nist.gov/vuln/detail/CVE-2022-1222) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-1172](https://nvd.nist.gov/vuln/detail/CVE-2022-1172) CVSSv3=5.0 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-1222\n\nInf loop in GitHub repository gpac/gpac prior to 2.1.0-DEV.\n\n### CVE-2022-1172\n\nNull Pointer Dereference Caused Segmentation Fault in GitHub repository gpac/gpac prior to 2.1.0-DEV.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @bluescreen303\nCc @mgdelacroix\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168665/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168664","id":1204832803,"node_id":"I_kwDOAEVQ_M5H0Eoj","number":168664,"title":"Vulnerability roundup 113: gogs-0.12.6: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:07:59Z","updated_at":"2022-04-14T18:08:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gogs&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gogs+in%3Apath&type=Code)\n\n* [ ] [CVE-2019-10348](https://nvd.nist.gov/vuln/detail/CVE-2019-10348) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2019-10348\n\nJenkins Gogs Plugin stored credentials unencrypted in job config.xml files on the Jenkins master where they can be viewed by users with Extended Read permission, or access to the master file system.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @kalbasit\nCc @schneefux\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168664/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168662","id":1204832679,"node_id":"I_kwDOAEVQ_M5H0Emn","number":168662,"title":"Vulnerability roundup 113: ffmpeg-5.0.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:07:55Z","updated_at":"2022-04-14T18:07:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=ffmpeg&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=ffmpeg+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-38291](https://nvd.nist.gov/vuln/detail/CVE-2021-38291) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-38291\n\nFFmpeg version (git commit de8e6e67e7523e48bb27ac224a0b446df05e1640) suffers from a an assertion failure at src/libavutil/mathematics.c.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @codyopel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168662/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168658","id":1204832443,"node_id":"I_kwDOAEVQ_M5H0Ei7","number":168658,"title":"Vulnerability roundup 113: calibre-web-0.6.17: 2 advisories [9.9]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:07:47Z","updated_at":"2022-04-14T18:07:47Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=calibre-web&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=calibre-web+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0939](https://nvd.nist.gov/vuln/detail/CVE-2022-0939) CVSSv3=9.9 (nixos-unstable)\n* [ ] [CVE-2022-0990](https://nvd.nist.gov/vuln/detail/CVE-2022-0990) CVSSv3=9.1 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0939\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.18.\n\n### CVE-2022-0990\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.18.\n\n-----\nScanned versions: nixos-unstable: ff9efb0724d.\n\nCc @pborzenkov\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168658/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168657","id":1204832347,"node_id":"I_kwDOAEVQ_M5H0Ehb","number":168657,"title":"Vulnerability roundup 113: calibre-web-0.6.13: 4 advisories [9.9]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:07:44Z","updated_at":"2022-04-14T18:07:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=calibre-web&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=calibre-web+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0939](https://nvd.nist.gov/vuln/detail/CVE-2022-0939) CVSSv3=9.9 (nixos-21.11)\n* [ ] [CVE-2022-0990](https://nvd.nist.gov/vuln/detail/CVE-2022-0990) CVSSv3=9.1 (nixos-21.11)\n* [ ] [CVE-2022-0405](https://nvd.nist.gov/vuln/detail/CVE-2022-0405) CVSSv3=4.3 (nixos-21.11)\n* [ ] [CVE-2022-0406](https://nvd.nist.gov/vuln/detail/CVE-2022-0406) CVSSv3=4.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0939\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.18.\n\n### CVE-2022-0990\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.18.\n\n### CVE-2022-0405\n\nImproper Access Control in GitHub repository janeczku/calibre-web prior to 0.6.16.\n\n### CVE-2022-0406\n\nImproper Authorization in GitHub repository janeczku/calibre-web prior to 0.6.16.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @pborzenkov\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168657/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168656","id":1204832289,"node_id":"I_kwDOAEVQ_M5H0Egh","number":168656,"title":"Vulnerability roundup 113: busybox-1.34.1: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T18:07:41Z","updated_at":"2022-04-18T12:41:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=busybox&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=busybox+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-28391](https://nvd.nist.gov/vuln/detail/CVE-2022-28391) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-28391\n\nBusyBox through 1.35.0 allows remote attackers to execute arbitrary code if netstat is used to print a DNS PTR record's value to a VT compatible terminal. Alternatively, the attacker could choose to change the terminal's colors.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @TethysSvensson\nCc @alyssais\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168656/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168655","id":1204832192,"node_id":"I_kwDOAEVQ_M5H0EfA","number":168655,"title":"Vulnerability roundup 113: buildah-1.23.1: 1 advisory [6.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:07:39Z","updated_at":"2022-04-14T18:07:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=buildah&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=buildah+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-27651](https://nvd.nist.gov/vuln/detail/CVE-2022-27651) CVSSv3=6.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-27651\n\nA flaw was found in buildah where containers were incorrectly started with non-empty default permissions. A bug was found in Moby (Docker Engine) where containers were incorrectly started with non-empty inheritable Linux process capabilities, enabling an attacker with access to programs with inheritable file capabilities to elevate those capabilities to the permitted set when execve(2) runs. This has the potential to impact confidentiality and integrity.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b.\n\nCc @Profpatsch\nCc @adisbladis\nCc @kalbasit\nCc @saschagrunert\nCc @vdemeester\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168655/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168654","id":1204832107,"node_id":"I_kwDOAEVQ_M5H0Edr","number":168654,"title":"Vulnerability roundup 113: advancecomp-2.1: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T18:07:37Z","updated_at":"2022-04-14T18:07:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=advancecomp&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=advancecomp+in%3Apath&type=Code)\n\n* [ ] [CVE-2019-8383](https://nvd.nist.gov/vuln/detail/CVE-2019-8383) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2019-8383\n\nAn issue was discovered in AdvanceCOMP through 2.1. An invalid memory address occurs in the function adv_png_unfilter_8 in lib/png.c. It can be triggered by sending a crafted file to a binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact when a victim opens a specially crafted file.\n\n-----\nScanned versions: nixos-21.11: a62ce97f92b; nixos-unstable: ff9efb0724d.\n\nCc @7c6f434c\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168654/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168651","id":1204793824,"node_id":"I_kwDOAEVQ_M5Hz7Hg","number":168651,"title":"Nautilus : Extensions broken ?","user":{"login":"wyndon","id":72203260,"node_id":"MDQ6VXNlcjcyMjAzMjYw","avatar_url":"https://avatars.githubusercontent.com/u/72203260?v=4","gravatar_id":"","url":"https://api.github.com/users/wyndon","html_url":"https://github.com/wyndon","followers_url":"https://api.github.com/users/wyndon/followers","following_url":"https://api.github.com/users/wyndon/following{/other_user}","gists_url":"https://api.github.com/users/wyndon/gists{/gist_id}","starred_url":"https://api.github.com/users/wyndon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wyndon/subscriptions","organizations_url":"https://api.github.com/users/wyndon/orgs","repos_url":"https://api.github.com/users/wyndon/repos","events_url":"https://api.github.com/users/wyndon/events{/privacy}","received_events_url":"https://api.github.com/users/wyndon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T17:25:59Z","updated_at":"2022-04-17T15:57:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIt seems that many extensions are not working on Nautilus right now. In the right-click menu, I don't have a \"Share\" option, \"Send to\" is also missing, `mat2` integration is not there either, `nautilus-open-any-terminal` same thing.\r\n\r\nI started a Pop_OS! virtual machine, which was running GNOME 40, and I could see the \"Share\" and \"Send to\" options, I did not test the rest though.\r\n\r\nThen, I started a Fedora virtual machine, which was running GNOME 42, and encountered the same problems as above (at least with Share and Send to), so I assume this is a problem with recent versions of GNOME/Nautilus. Opening for tracking.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Launch Nautilus and see if you have the \"Share\" and \"Send To\" options when you right-click on a file/folder.\r\n\r\n### Expected behavior\r\nExtensions should work.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.27-xanmod1-tt, NixOS, 22.05 (Quokka), 22.05.20220413.ff9efb0`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/store/1mq6ivn9y8zkjljiy66d4xjjhlhq0h3r-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168651/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168644","id":1204683437,"node_id":"I_kwDOAEVQ_M5HzgKt","number":168644,"title":"why3: withProvers doesn't configure correctly","user":{"login":"bouk","id":97820,"node_id":"MDQ6VXNlcjk3ODIw","avatar_url":"https://avatars.githubusercontent.com/u/97820?v=4","gravatar_id":"","url":"https://api.github.com/users/bouk","html_url":"https://github.com/bouk","followers_url":"https://api.github.com/users/bouk/followers","following_url":"https://api.github.com/users/bouk/following{/other_user}","gists_url":"https://api.github.com/users/bouk/gists{/gist_id}","starred_url":"https://api.github.com/users/bouk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bouk/subscriptions","organizations_url":"https://api.github.com/users/bouk/orgs","repos_url":"https://api.github.com/users/bouk/repos","events_url":"https://api.github.com/users/bouk/events{/privacy}","received_events_url":"https://api.github.com/users/bouk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-14T15:33:02Z","updated_at":"2022-04-19T08:26:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using `why3.withProvers [ z3 alt-ergo ]` I'd expect `why3 --list` to show Z3 and Alt-Ergo.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n\r\n(make sure https://github.com/NixOS/nixpkgs/pull/168643 is merged or check out my branch)\r\n\r\n1. `rm -f ~/.why3.conf`\r\n2. `nix build --impure --expr 'with import <nixpkgs> {}; why3.withProvers [ z3 alt-ergo ]'`\r\n3. `result/bin/why3 --list-provers`\r\n```\r\nKnown provers:\r\n```\r\n\r\n### Expected behavior\r\n\r\nI'd expect `Z3` and `Alt-Ergo` to be listed.\r\n\r\n### Solution\r\n\r\nThe `withProvers` derivation does `--extra-config`: https://github.com/NixOS/nixpkgs/blob/cb80b946a4eecc7f3ed59c3cceb5ef6cb23c7d86/pkgs/applications/science/logic/why3/with-provers.nix#L30\r\n\r\nIt should do `--config` instead to overwrite the config completely. \r\n\r\n### Notify maintainers\r\n\r\n@thoughtpolice @vbgl \r\n\r\n\r\n### Metadata\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(bouke): `\"darwin, nixpkgs\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/Users/bouke/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168644/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168605","id":1204276417,"node_id":"I_kwDOAEVQ_M5Hx8zB","number":168605,"title":"radicle-upstream is out-of-date","user":{"login":"suhr","id":65870,"node_id":"MDQ6VXNlcjY1ODcw","avatar_url":"https://avatars.githubusercontent.com/u/65870?v=4","gravatar_id":"","url":"https://api.github.com/users/suhr","html_url":"https://github.com/suhr","followers_url":"https://api.github.com/users/suhr/followers","following_url":"https://api.github.com/users/suhr/following{/other_user}","gists_url":"https://api.github.com/users/suhr/gists{/gist_id}","starred_url":"https://api.github.com/users/suhr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/suhr/subscriptions","organizations_url":"https://api.github.com/users/suhr/orgs","repos_url":"https://api.github.com/users/suhr/repos","events_url":"https://api.github.com/users/suhr/events{/privacy}","received_events_url":"https://api.github.com/users/suhr/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-14T09:25:56Z","updated_at":"2022-04-14T09:25:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: `legacyPackages.x86_64-linux.radicle-upstream`\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.2.12\r\ndesired version: 0.2.14\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @d-xo \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168605/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168534","id":1203739287,"node_id":"I_kwDOAEVQ_M5Hv5qX","number":168534,"title":"Upgrade to go 1.18 by default for 22.05","user":{"login":"Mic92","id":96200,"node_id":"MDQ6VXNlcjk2MjAw","avatar_url":"https://avatars.githubusercontent.com/u/96200?v=4","gravatar_id":"","url":"https://api.github.com/users/Mic92","html_url":"https://github.com/Mic92","followers_url":"https://api.github.com/users/Mic92/followers","following_url":"https://api.github.com/users/Mic92/following{/other_user}","gists_url":"https://api.github.com/users/Mic92/gists{/gist_id}","starred_url":"https://api.github.com/users/Mic92/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Mic92/subscriptions","organizations_url":"https://api.github.com/users/Mic92/orgs","repos_url":"https://api.github.com/users/Mic92/repos","events_url":"https://api.github.com/users/Mic92/events{/privacy}","received_events_url":"https://api.github.com/users/Mic92/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":337081580,"node_id":"MDU6TGFiZWwzMzcwODE1ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20golang","name":"6.topic: golang","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-13T20:09:29Z","updated_at":"2022-04-17T15:57:10Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOnly the last two go releases will receive security updates. Therefore we should at least the latest release to not have an unsupported go version before the next nixos release: https://go.dev/doc/devel/release","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168534/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168532","id":1203716401,"node_id":"I_kwDOAEVQ_M5Hv0Ex","number":168532,"title":"Feedback wanted: Desktops maturity","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null},{"id":465618943,"node_id":"MDU6TGFiZWw0NjU2MTg5NDM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20community%20feedback","name":"9.needs: community feedback","color":"eb6420","default":false,"description":null},{"id":782188183,"node_id":"MDU6TGFiZWw3ODIxODgxODM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20xfce","name":"6.topic: xfce","color":"fef2c0","default":false,"description":"The Xfce Desktop Environment"},{"id":1207068537,"node_id":"MDU6TGFiZWwxMjA3MDY4NTM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20pantheon","name":"6.topic: pantheon","color":"fef2c0","default":false,"description":"The Pantheon desktop environment"},{"id":1754115667,"node_id":"MDU6TGFiZWwxNzU0MTE1NjY3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20maintainer%20feedback","name":"9.needs: maintainer feedback","color":"eb6420","default":false,"description":""},{"id":1803518571,"node_id":"MDU6TGFiZWwxODAzNTE4NTcx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cinnamon","name":"6.topic: cinnamon","color":"fef2c0","default":false,"description":""},{"id":3656735196,"node_id":"LA_kwDOAEVQ_M7Z9Vnc","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20LXQt","name":"6.topic: LXQt","color":"fef2c0","default":false,"description":"The Lightweight Qt Desktop Environment"},{"id":3689348382,"node_id":"LA_kwDOAEVQ_M7b5v0e","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20Lumina%20DE","name":"6.topic: Lumina DE","color":"fef2c0","default":false,"description":"The Lumina Desktop Environment"},{"id":3693998097,"node_id":"LA_kwDOAEVQ_M7cLfAR","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20Enlightenment%20DE","name":"6.topic: Enlightenment DE","color":"FEF2C0","default":false,"description":"The Enlightenment Desktop Environment"},{"id":4034771318,"node_id":"LA_kwDOAEVQ_M7wfbl2","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20mate","name":"6.topic: mate","color":"fef2c0","default":false,"description":"The MATE Desktop Environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":26,"created_at":"2022-04-13T19:48:37Z","updated_at":"2022-04-29T03:17:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"This issue is to collect information about the maturity of our desktops.\r\n\r\nWe want to provide an easy install of desktops for users with a graphical installer (https://github.com/NixOS/nixpkgs/pull/161788). It uses X11 except GNOME.\r\n\r\nThe provided desktops should be **ready for daily use** and **stable**.\r\n\r\nI'm asking the **maintainers**, but feedback from **users** of these desktops are also apprectiated!\r\n\r\nJust rate the desktops with :+1: or :-1: on the comment. For more detailed feedback, write a comment.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532/reactions","total_count":9,"+1":9,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168532/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168529","id":1203706802,"node_id":"I_kwDOAEVQ_M5Hvxuy","number":168529,"title":"Create lumina team","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-13T19:39:18Z","updated_at":"2022-04-13T19:39:18Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/634141959076a8ab69ca2cca0f266852256d79ee/pkgs/desktops/lumina/lumina/default.nix#L111\r\n\r\ncreate team in https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix and github for easier communication\r\n\r\ncc @romildo ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168529/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168527","id":1203704633,"node_id":"I_kwDOAEVQ_M5HvxM5","number":168527,"title":"Create LXQt team","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-13T19:36:41Z","updated_at":"2022-04-13T19:36:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\ndoes not even have maintainer set right now\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/634141959076a8ab69ca2cca0f266852256d79ee/pkgs/desktops/lxqt/default.nix\r\n\r\ncreate team in https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix and github for easier communication\r\n\r\n@romildo \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168527/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168526","id":1203702549,"node_id":"I_kwDOAEVQ_M5HvwsV","number":168526,"title":"Create Enlightenment team","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-13T19:34:36Z","updated_at":"2022-04-13T19:34:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nhas no team, makes it hard to contact https://github.com/NixOS/nixpkgs/blob/634141959076a8ab69ca2cca0f266852256d79ee/pkgs/desktops/enlightenment/enlightenment/default.nix#L78\r\n\r\ncreate team in https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix and github\r\n\r\ncc @romildo","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168526/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168525","id":1203700251,"node_id":"I_kwDOAEVQ_M5HvwIb","number":168525,"title":"Create mate github team","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-13T19:31:56Z","updated_at":"2022-04-14T14:46:52Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\n@NixOS/mate missing\r\n\r\nexists in https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix#L356-L363\r\n\r\ncc @romildo","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168525/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168523","id":1203698312,"node_id":"I_kwDOAEVQ_M5HvvqI","number":168523,"title":"Create Cinnamon desktop github team","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-13T19:29:44Z","updated_at":"2022-04-13T19:29:44Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\n@NixOS/cinnamon missing\r\n\r\nexists in https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix#L94-L101\r\n\r\ncc @mkg20001","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523/reactions","total_count":4,"+1":2,"-1":0,"laugh":0,"hooray":2,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168523/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168513","id":1203611961,"node_id":"I_kwDOAEVQ_M5Hvak5","number":168513,"title":"Provide consistent user experience (style)","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-13T17:54:48Z","updated_at":"2022-04-17T15:55:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nWe should provide a consistent user experience when it comes to design. In this issue i focus on graphical design.\r\n\r\nRight now it's a total mess.\r\n\r\n### Desktop background\r\n\r\nSome desktops use their default background (GNOME, Plasma5, Xfce, MATE, Enlightenment, LXQt, Lumina). Others use a NixOS background (Pantheon, Cinnamon).\r\n\r\nThere is a PR for GNOME to use a NixOS background, but it's a different background: https://github.com/NixOS/nixpkgs/pull/166096\r\n\r\nIt would be great to have a simple background (logo in middle, color background, optionally with gradient) and a more complex (like https://github.com/NixOS/nixos-artwork/blob/master/bootloader/isolinux/bios-boot.png). In light and dark mode.\r\n\r\n### NixOS Logo\r\n\r\nThere are many versions of the NixOS logo used all over the place. We should stick to official logos and use them consistently.\r\n\r\nHave clear rules when to use which version and follow them.\r\n\r\nWe need color and monochrome version, for bright and dark background.\r\n\r\nThis is a start, but i think it needs improvement: https://github.com/NixOS/nixos-artwork/tree/master/logo\r\n\r\n### Theme / Style\r\n\r\nThere are many different styles used.\r\n\r\nFor example in boot screens. GRUB, systemd-boot, isolinux look completely different. I think they should look the same when technical possible.\r\n\r\nRelated: https://github.com/NixOS/nixpkgs/issues/168434\r\n\r\nThe style should be in line with website, documentation, videos, twitter profile picture, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168513/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168485","id":1203270121,"node_id":"I_kwDOAEVQ_M5HuHHp","number":168485,"title":"GTK3 ignore theme change using gsettings","user":{"login":"uningan","id":810075,"node_id":"MDQ6VXNlcjgxMDA3NQ==","avatar_url":"https://avatars.githubusercontent.com/u/810075?v=4","gravatar_id":"","url":"https://api.github.com/users/uningan","html_url":"https://github.com/uningan","followers_url":"https://api.github.com/users/uningan/followers","following_url":"https://api.github.com/users/uningan/following{/other_user}","gists_url":"https://api.github.com/users/uningan/gists{/gist_id}","starred_url":"https://api.github.com/users/uningan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/uningan/subscriptions","organizations_url":"https://api.github.com/users/uningan/orgs","repos_url":"https://api.github.com/users/uningan/repos","events_url":"https://api.github.com/users/uningan/events{/privacy}","received_events_url":"https://api.github.com/users/uningan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-13T13:01:21Z","updated_at":"2022-04-17T21:41:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIm running sway WM from 21.11 channel, when I change theme using `gsettings` CLI tool I expect GTK3 on-fly changing theme. Test GTK4 using `gtk4-demo` and works well.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Launch `gtk3-demo` and `gtk4-demo` (ie: `nix-shell -p gtk4.dev --run gtk4-demo`)\r\n2. Run `gsettings set org.gnome.desktop.interface gtk-theme Adwaita-dark`\r\n\r\n### Expected behavior\r\nBoth GTK3 and GTK4 apps change their theme.\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-21.11beta333771.8e6b3914626, unstable-21.11pre299378.db6e089456c\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168485/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168484","id":1203263554,"node_id":"I_kwDOAEVQ_M5HuFhC","number":168484,"title":"qutebrowser crashes on file dialog","user":{"login":"ivan-pop","id":45109448,"node_id":"MDQ6VXNlcjQ1MTA5NDQ4","avatar_url":"https://avatars.githubusercontent.com/u/45109448?v=4","gravatar_id":"","url":"https://api.github.com/users/ivan-pop","html_url":"https://github.com/ivan-pop","followers_url":"https://api.github.com/users/ivan-pop/followers","following_url":"https://api.github.com/users/ivan-pop/following{/other_user}","gists_url":"https://api.github.com/users/ivan-pop/gists{/gist_id}","starred_url":"https://api.github.com/users/ivan-pop/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ivan-pop/subscriptions","organizations_url":"https://api.github.com/users/ivan-pop/orgs","repos_url":"https://api.github.com/users/ivan-pop/repos","events_url":"https://api.github.com/users/ivan-pop/events{/privacy}","received_events_url":"https://api.github.com/users/ivan-pop/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-13T12:55:35Z","updated_at":"2022-04-14T09:38:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nOpening file picker in qutebrowser crashes it with\r\n```console\r\n(python3.9:237842): GLib-GIO-ERROR **: 15:44:11.748: No GSettings schemas are installed on the system\r\n``` \r\n### Steps To Reproduce\r\n1. `qutebrowser -T`\r\n2. `:open https://viljamis.com/filetest/`\r\n3. Click on `Choose file`\r\n\r\n### Expected behavior\r\nqutebrowser should not crash and show GTK file picker.\r\n\r\n### Additional context\r\nThis appears to be similar to #161399, but trying to do the same fix I tried in #162089 does not seem to solve this issue.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@jagajaga @rnhmjoj @ebzzry @dotlambda\r\n\r\n### Metadata\r\n\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0-zen1, NixOS, 22.05 (Quokka), 22.05.20220406.b6966d9`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/store/gyzqxklnmyzl773qpqylnfvhg6gimyad-source`\r\n```\r\n```console\r\n> qutebrowser -T --version\r\n ______ ,,\r\n ,.-\"` | ,-` |\r\n .^ || |\r\n / ,-*^| || |\r\n; / | || ;-*```^*.\r\n; ; | |;,-*` \\\r\n| | | ,-*` ,-\"\"\"\\ \\\r\n| \\ ,-\"` ,-^`| \\ |\r\n \\ `^^ ,-;| | ; |\r\n *; ,-*` || | / ;;\r\n `^^`` | || | ,^ /\r\n | || `^^` ,^\r\n | _,\"| _,-\"\r\n -*` ****\"\"\"``\r\n\r\nqutebrowser v2.5.0\r\nGit commit: \r\nBackend: QtWebEngine 5.15.8, based on Chromium 87.0.4280.144\r\nQt: 5.15.3\r\n\r\nCPython: 3.9.11\r\nPyQt: 5.15.4\r\n\r\nsip: 6.5.1\r\ncolorama: no\r\njinja2: 3.0.3\r\npygments: 2.11.2\r\nyaml: 6.0\r\nadblock: 0.5.2\r\nPyQt5.QtWebEngineWidgets: yes\r\nPyQt5.QtWebEngine: 5.15.4\r\nPyQt5.QtWebKitWidgets: no\r\npdf.js: 2.8.335 (/nix/store/z5n6n43w80lh2p2pfp694q38chlrmnl0-pdfjs-2.8.335/build/pdf.js)\r\nsqlite: 3.38.1\r\nQtNetwork SSL: OpenSSL 1.1.1n 15 Mar 2022\r\n\r\nStyle: Adwaita::Style\r\nPlatform plugin: xcb\r\nOpenGL: Intel, 4.6 (Compatibility Profile) Mesa 21.3.8\r\nPlatform: Linux-5.17.0-zen1-x86_64-with-glibc2.34, 64bit\r\nLinux distribution: NixOS 22.05 (Quokka) (nixos)\r\nFrozen: False\r\nImported from /nix/store/n6igivhh4ly81khcmldpglph8vpq5lff-qutebrowser-2.5.0/lib/python3.9/site-packages/qutebrowser\r\nUsing Python from /nix/store/9px00aaqzb6n5p03i9wd8rx3msg95y9r-python3-3.9.11/bin/python3.9\r\nQt library executable path: /nix/store/p1aapf3rsdw6xvj557as4694l78zd1hc-qtbase-5.15.3/libexec, data path: /nix/store/p1aapf3rsdw6xvj557as4694l78zd1hc-qtbase-5.15.3\r\n\r\nPaths:\r\ncache: /tmp/qutebrowser-basedir-25nfm2h_/cache\r\nconfig: /tmp/qutebrowser-basedir-25nfm2h_/config\r\ndata: /tmp/qutebrowser-basedir-25nfm2h_/data\r\nruntime: /tmp/qutebrowser-basedir-25nfm2h_/runtime\r\n\r\nAutoconfig loaded: yes\r\nConfig.py: no config.py was loaded\r\nUptime: 0:00:00\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168484/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168434","id":1202642073,"node_id":"I_kwDOAEVQ_M5HrtyZ","number":168434,"title":"nixos logo stretched on isolinux splash screen","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-13T01:34:42Z","updated_at":"2022-04-17T15:54:42Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Boot Installer on BIOS system\r\n\r\n### Expected behavior\r\nLogo should have the correct proportions.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nThis was always an issue and it annoys me every time i boot the installer. There might be already an issue, but i have not found it.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168434/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168431","id":1202637306,"node_id":"I_kwDOAEVQ_M5Hrsn6","number":168431,"title":"vscode-fhs and vscodium-fhs crash on execution for non-NixOS","user":{"login":"ramesh45345","id":6318224,"node_id":"MDQ6VXNlcjYzMTgyMjQ=","avatar_url":"https://avatars.githubusercontent.com/u/6318224?v=4","gravatar_id":"","url":"https://api.github.com/users/ramesh45345","html_url":"https://github.com/ramesh45345","followers_url":"https://api.github.com/users/ramesh45345/followers","following_url":"https://api.github.com/users/ramesh45345/following{/other_user}","gists_url":"https://api.github.com/users/ramesh45345/gists{/gist_id}","starred_url":"https://api.github.com/users/ramesh45345/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ramesh45345/subscriptions","organizations_url":"https://api.github.com/users/ramesh45345/orgs","repos_url":"https://api.github.com/users/ramesh45345/repos","events_url":"https://api.github.com/users/ramesh45345/events{/privacy}","received_events_url":"https://api.github.com/users/ramesh45345/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-13T01:25:09Z","updated_at":"2022-04-13T21:12:24Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nBoth the `vscode-fhs` and `vscodium-fhs` packages crash on execution when run on a non-NixOS operating system. Behavior was observed on Arch Linux (libvirt/qemu VM), Fedora Kinoite 35 (VM, and host with nVidia driver), and Ubuntu 21.10 (VM), all x86_64-linux.\r\n\r\nOn all machines, home-manager with a stock config (none or one additional packages installed), along with an up-to-date nix (2.7.0). Nix was installed using single user mode.\r\n\r\nBoth of these packages do execute correctly when tested on NixOS, the problem is only observed when using Nix on a non-NixOS platform.\r\n\r\nThe following log is observed for `vscodium-fhs` (which does not show useful information):\r\n```\r\n$ nix-shell -p vscodium-fhs --command \"codium --version\"\r\n1.65.2\r\nc722ca6c7eed3d7987c0d5c3df5c45f6b15e77d1\r\nx64\r\n$ nix-shell -p vscodium-fhs --command \"codium --verbose --log=trace\"\r\nGtk-Message: 21:03:17.439: Failed to load module \"canberra-gtk-module\"\r\nGtk-Message: 21:03:17.470: Failed to load module \"colorreload-gtk-module\"\r\nGtk-Message: 21:03:17.471: Failed to load module \"window-decorations-gtk-module\"\r\n```\r\n\r\nThe following log is observed for `vscode-fhs` (not very interesting either):\r\n```\r\n$ nix-shell -p vscode-fhs --command \"code --version\"\r\n1.65.2\r\nc722ca6c7eed3d7987c0d5c3df5c45f6b15e77d1\r\nx64\r\n$ nix-shell -p vscode-fhs --command \"code --verbose --log=trace\"\r\nGtk-Message: 21:05:08.773: Failed to load module \"canberra-gtk-module\"\r\nGtk-Message: 21:05:08.808: Failed to load module \"colorreload-gtk-module\"\r\nGtk-Message: 21:05:08.808: Failed to load module \"window-decorations-gtk-module\"\r\n[53:0412/210508.849696:ERROR:angle_platform_impl.cc(44)] Display.cpp:840 (initialize): ANGLE Display::initialize error 12289: glXQueryExtensionsString returned NULL\r\n[53:0412/210508.850074:ERROR:gl_surface_egl.cc(780)] EGL Driver message (Critical) eglInitialize: glXQueryExtensionsString returned NULL\r\n[53:0412/210508.850336:ERROR:gl_surface_egl.cc(1373)] eglInitialize OpenGL failed with error EGL_NOT_INITIALIZED, trying next display type\r\n[53:0412/210508.850722:ERROR:angle_platform_impl.cc(44)] Display.cpp:840 (initialize): ANGLE Display::initialize error 12289: glXQueryExtensionsString returned NULL\r\n[53:0412/210508.850904:ERROR:gl_surface_egl.cc(780)] EGL Driver message (Critical) eglInitialize: glXQueryExtensionsString returned NULL\r\n[53:0412/210508.851119:ERROR:gl_surface_egl.cc(1373)] eglInitialize OpenGLES failed with error EGL_NOT_INITIALIZED\r\n[53:0412/210508.851332:ERROR:gl_initializer_linux_x11.cc(178)] GLSurfaceEGL::InitializeOneOff failed.\r\n[53:0412/210508.852404:ERROR:viz_main_impl.cc(160)] Exiting GPU process due to errors during initialization\r\n[64:0412/210508.880678:ERROR:gpu_init.cc(440)] Passthrough is not supported, GL is swiftshader\r\n[main 2022-04-13T01:05:08.965Z] [File Watcher (node.js)] Request to start watching: /home/user/.config/Code/User (excludes: <none>),/home/user/.config/Code/User/settings.json (excludes: <none>)\r\n[main 2022-04-13T01:05:08.982Z] Starting VS Code\r\n[main 2022-04-13T01:05:08.982Z] from: /nix/store/57xhiklf9hvrlk8y0n73xppai2sz2wx3-vscode-1.65.2/lib/vscode/resources/app\r\n[main 2022-04-13T01:05:08.982Z] args: {\r\n _: [],\r\n diff: false,\r\n add: false,\r\n goto: false,\r\n 'new-window': false,\r\n 'reuse-window': false,\r\n wait: false,\r\n help: false,\r\n 'list-extensions': false,\r\n 'show-versions': false,\r\n 'pre-release': false,\r\n version: false,\r\n verbose: true,\r\n log: 'trace',\r\n status: false,\r\n 'prof-startup': false,\r\n 'no-cached-data': false,\r\n 'prof-v8-extensions': false,\r\n 'disable-extensions': false,\r\n 'disable-gpu': false,\r\n 'ms-enable-electron-run-as-node': false,\r\n telemetry: false,\r\n debugRenderer: false,\r\n logExtensionHostCommunication: false,\r\n 'skip-release-notes': false,\r\n 'skip-welcome': false,\r\n 'disable-telemetry': false,\r\n 'disable-updates': false,\r\n 'disable-keytar': false,\r\n 'disable-workspace-trust': false,\r\n 'disable-crash-reporter': false,\r\n 'skip-add-to-recently-opened': false,\r\n 'unity-launch': false,\r\n 'open-url': false,\r\n 'file-write': false,\r\n 'file-chmod': false,\r\n 'driver-verbose': false,\r\n force: false,\r\n 'do-not-sync': false,\r\n trace: false,\r\n 'force-user-env': false,\r\n 'force-disable-user-env': false,\r\n 'open-devtools': false,\r\n __sandbox: false,\r\n 'no-proxy-server': false,\r\n 'no-sandbox': false,\r\n nolazy: false,\r\n 'force-renderer-accessibility': false,\r\n 'ignore-certificate-errors': false,\r\n 'allow-insecure-localhost': false,\r\n 'disable-dev-shm-usage': false,\r\n logsPath: '/home/user/.config/Code/logs/20220412T210508'\r\n}\r\n[main 2022-04-13T01:05:08.984Z] Resolving machine identifier...\r\n[main 2022-04-13T01:05:08.985Z] Resolved machine identifier: 743a96d627a885f58f870320cc80e748ca8792b94b37a67bbdb69e2ac8b42295\r\n[main 2022-04-13T01:05:08.986Z] Main->SharedProcess#connect\r\n[main 2022-04-13T01:05:08.996Z] [File Watcher (node.js)] Started watching: '/home/user/.config/Code/User'\r\n[main 2022-04-13T01:05:08.997Z] [File Watcher (node.js)] Error: ENOENT: no such file or directory, stat '/home/user/.config/Code/User/settings.json'\r\n[main 2022-04-13T01:05:09.014Z] StorageMainService: creating global storage\r\n[main 2022-04-13T01:05:09.034Z] lifecycle (main): phase changed (value: 2)\r\n[main 2022-04-13T01:05:09.036Z] windowsManager#open\r\n[main 2022-04-13T01:05:09.037Z] windowsManager#open pathsToOpen [ [Object: null prototype] {} ]\r\n[main 2022-04-13T01:05:09.038Z] windowsManager#doOpenEmpty {\r\n restore: false,\r\n remoteAuthority: undefined,\r\n filesToOpen: undefined,\r\n forceNewWindow: false\r\n}\r\n[main 2022-04-13T01:05:09.039Z] IPC Object URL: Registered new channel vscode:625266b3-2e5d-4226-b320-ffa1435aec28.\r\n[main 2022-04-13T01:05:09.040Z] window#validateWindowState: validating window state on 1 display(s) {\r\n width: 1024,\r\n height: 768,\r\n mode: 1,\r\n x: 128,\r\n y: 260,\r\n hasDefaultState: true\r\n}\r\n[main 2022-04-13T01:05:09.040Z] window#validateWindowState: 1 monitor working area { x: 0, y: 28, width: 1280, height: 1235 }\r\n[main 2022-04-13T01:05:09.040Z] window#ctor: using window state {\r\n width: 1024,\r\n height: 768,\r\n mode: 1,\r\n x: 128,\r\n y: 260,\r\n hasDefaultState: true\r\n}\r\n```\r\n\r\n### Steps To Reproduce\r\n1. Ensure that vscode and vscodium configuration (in .config, and root of home folder) have been removed to ensure a clean run.\r\n2. On a non-NixOS operating system, with Nix installed in single user mode, run `nix-shell -p vscodium-fhs --command \"codium --verbose --log=trace\"`\r\n3. Observe that the program does not run. Note that there is no trace in the console when executing.\r\n4. On a non-NixOS operating system, with Nix installed in single user mode, run `nix-shell -p vscodium --command \"codium --verbose --log=trace\"`\r\n5. Observe that the program executes and loads the editor.\r\n\r\n### Expected behavior\r\nIt is expected that the program loads successfully.\r\n\r\n### Additional context\r\nAs stated above, `vscode-fhs` and `vscodium-fhs` work properly on NixOS, but not on other Linux OSes.\r\n\r\nIs it normal for fhs packages to not work in non-NixOS? Is it possible I have a configuration issue?\r\n\r\n### Notify maintainers\r\n@Synthetica9 @turion @bobby285271 @eadwu @maxeaubrey \r\n\r\n### Metadata\r\n```\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1-arch1-1, Arch Linux, noversion, rolling`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(user): `\"home-manager, nixpkgs\"`\r\n - nixpkgs: `/home/user/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168431/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168392","id":1202161949,"node_id":"I_kwDOAEVQ_M5Hp4kd","number":168392,"title":"Hyprland compositor / wayland window manager","user":{"login":"Ashe","id":8940077,"node_id":"MDQ6VXNlcjg5NDAwNzc=","avatar_url":"https://avatars.githubusercontent.com/u/8940077?v=4","gravatar_id":"","url":"https://api.github.com/users/Ashe","html_url":"https://github.com/Ashe","followers_url":"https://api.github.com/users/Ashe/followers","following_url":"https://api.github.com/users/Ashe/following{/other_user}","gists_url":"https://api.github.com/users/Ashe/gists{/gist_id}","starred_url":"https://api.github.com/users/Ashe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Ashe/subscriptions","organizations_url":"https://api.github.com/users/Ashe/orgs","repos_url":"https://api.github.com/users/Ashe/repos","events_url":"https://api.github.com/users/Ashe/events{/privacy}","received_events_url":"https://api.github.com/users/Ashe/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-04-12T17:22:01Z","updated_at":"2022-04-23T13:49:44Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n> Hyprland is a Dynamic Tiling Wayland Compositor in early development stages. \r\n\r\nIt recently received a lot of attention on [reddit](https://www.reddit.com/r/unixporn/comments/u1fq8j/hyprland_to_that_one_guy_who_asked_me_to_keep/) as a fresh window manager for wayland (video can be found [here](https://www.reddit.com/r/unixporn/comments/u1fq8j/hyprland_to_that_one_guy_who_asked_me_to_keep/?utm_source=share&utm_medium=web2x&context=3)).\r\n\r\nIt would be quite nice to have it as a package so that we can experience it's development and provide feedback!\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/vaxerski/Hyprland\r\n* source URL: https://github.com/vaxerski/Hyprland\r\n* license: [BSD-3-Clause License](https://github.com/vaxerski/Hyprland/blob/main/LICENSE)\r\n* platforms: linux (wayland)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168392/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168384","id":1202020049,"node_id":"I_kwDOAEVQ_M5HpV7R","number":168384,"title":"Package request: Frame","user":{"login":"suhr","id":65870,"node_id":"MDQ6VXNlcjY1ODcw","avatar_url":"https://avatars.githubusercontent.com/u/65870?v=4","gravatar_id":"","url":"https://api.github.com/users/suhr","html_url":"https://github.com/suhr","followers_url":"https://api.github.com/users/suhr/followers","following_url":"https://api.github.com/users/suhr/following{/other_user}","gists_url":"https://api.github.com/users/suhr/gists{/gist_id}","starred_url":"https://api.github.com/users/suhr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/suhr/subscriptions","organizations_url":"https://api.github.com/users/suhr/orgs","repos_url":"https://api.github.com/users/suhr/repos","events_url":"https://api.github.com/users/suhr/events{/privacy}","received_events_url":"https://api.github.com/users/suhr/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-12T15:29:58Z","updated_at":"2022-04-12T15:29:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nA privacy focused Ethereum wallet that runs natively on macOS, Windows and Linux\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://frame.sh/\r\n* source URL: https://github.com/floating/frame\r\n* license: gpl3\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168384/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168381","id":1201988679,"node_id":"I_kwDOAEVQ_M5HpORH","number":168381,"title":"astroid mail sending is broken","user":{"login":"ehmry","id":537775,"node_id":"MDQ6VXNlcjUzNzc3NQ==","avatar_url":"https://avatars.githubusercontent.com/u/537775?v=4","gravatar_id":"","url":"https://api.github.com/users/ehmry","html_url":"https://github.com/ehmry","followers_url":"https://api.github.com/users/ehmry/followers","following_url":"https://api.github.com/users/ehmry/following{/other_user}","gists_url":"https://api.github.com/users/ehmry/gists{/gist_id}","starred_url":"https://api.github.com/users/ehmry/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ehmry/subscriptions","organizations_url":"https://api.github.com/users/ehmry/orgs","repos_url":"https://api.github.com/users/ehmry/repos","events_url":"https://api.github.com/users/ehmry/events{/privacy}","received_events_url":"https://api.github.com/users/ehmry/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-12T15:05:49Z","updated_at":"2022-04-25T19:46:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe astroid mail client is no longer able to send mail.\r\n\r\nAstroid from `release-21.11` still works and its version has not been updated since then, so I assume this is caused by some sort of Gnome/GTK bloatcancer.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Edit `.config/astroid/config` and set `accounts: …: sendmail:` to something like a script that can be verified if its been invoked.\r\n2. Open astroid and send a mail\r\n\r\n### Expected behavior\r\nThe sendmail command is invoked.\r\n\r\n```\r\n[10:00:00] [0x00007fa076142b40] [M] [info] mw: yes-no: got yes!\r\n[10:00:00] [0x00007fa076142b40] [M] [info] em: sending message..\r\n[10:00:00] [0x00007fa076142b40] [M] [info] msg: loading message from file (mid supplied): /home/cache/astroid/1649775597.ytgm3jlhd3.astroid@zuni.none\r\n[10:00:00] [0x00007fa076142b40] [M] [warning] charset: not defined.\r\n[10:00:00] [0x00007fa076142b40] [M] [info] cm: sending (threaded)..\r\n[10:00:02] [0x00007f9ff61ff640] [M] [warning] cm: sending message from account: ########\r\n[10:00:02] [0x00007f9ff61ff640] [M] [warning] cm: message sent successfully!\r\n```\r\n\r\n### Actual behavior\r\n```\r\n[09:44:45] [0x00007fe68dc33b40] [M] [info] mw: Really send message?\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] mw: yes-no: got yes!\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] em: sending message..\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] msg: loading message from file (mid supplied): /home/cache/astroid/1649774680.10ybmgdaux.astroid@zuni.none\r\n[09:44:46] [0x00007fe68dc33b40] [M] [warning] charset: not defined.\r\n\r\n** (astroid:44115): CRITICAL **: 09:44:46.095: \r\nunhandled exception (type Glib::Error) in signal handler:\r\ndomain: gtk-icon-theme-error-quark\r\ncode : 0\r\nwhat : Icon 'mail-send' not present in theme Adwaita\r\n\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] mw: yes-no: got yes!\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] em: sending message..\r\n[09:44:46] [0x00007fe68dc33b40] [M] [info] msg: loading message from file (mid supplied): /home/cache/astroid/1649774680.10ybmgdaux.astroid@zuni.none\r\n[09:44:46] [0x00007fe68dc33b40] [M] [warning] charset: not defined.\r\n\r\n** (astroid:44115): CRITICAL **: 09:44:46.099: \r\nunhandled exception (type Glib::Error) in signal handler:\r\ndomain: gtk-icon-theme-error-quark\r\ncode : 0\r\nwhat : Icon 'mail-send' not present in theme Adwaita\r\n\r\n```\r\n\r\n### Notify maintainers\r\n @bdimcheff @SuprDewd \r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220313_7abce04`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168381/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168362","id":1201144962,"node_id":"I_kwDOAEVQ_M5HmASC","number":168362,"title":"initrd secrets not present on kexec","user":{"login":"nrdxp","id":34083928,"node_id":"MDQ6VXNlcjM0MDgzOTI4","avatar_url":"https://avatars.githubusercontent.com/u/34083928?v=4","gravatar_id":"","url":"https://api.github.com/users/nrdxp","html_url":"https://github.com/nrdxp","followers_url":"https://api.github.com/users/nrdxp/followers","following_url":"https://api.github.com/users/nrdxp/following{/other_user}","gists_url":"https://api.github.com/users/nrdxp/gists{/gist_id}","starred_url":"https://api.github.com/users/nrdxp/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nrdxp/subscriptions","organizations_url":"https://api.github.com/users/nrdxp/orgs","repos_url":"https://api.github.com/users/nrdxp/repos","events_url":"https://api.github.com/users/nrdxp/events{/privacy}","received_events_url":"https://api.github.com/users/nrdxp/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-12T06:02:01Z","updated_at":"2022-04-17T15:52:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nUsing grub2 to unlock my luks encrypted volume, I also use a keyfile placed inside the initrd to avoid having to type the password twice on boot. However, when running a cycling the machine with kexec, the kernel cannot find the keyfile and falls back to password.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. setup a keyfile for your luks encrypted volume and include in in the initrd like so: `boot.initrd.secrets.\"keyfile.bin\" = \"/path/to/keyfile.bin\";`\r\n2. ensure boot works properly with this keyfile in place with: `boot.initrd.luks.devices.<your-device>.keyfile = \"keyfile.bin\";`\r\n3. run a test boot to ensure this is working as expected\r\n4. now from a live system, run `systemctl start prepare-kexec`, and then `systemctl kexec`\r\n5. Notice how the kernel can not now find the keyfile and will either fail completely or fall back to password depending on how it is configured\r\n\r\n### Expected behavior\r\nSince kexec should presumably load the same initrd as the bootloader, I'm a bit surprised by this behavior and I'd expect the secrets to be present in either case\r\n\r\n### Metadata\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n/cc based on git-blame of kexec module: \r\n@shlevy @lheckemann ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168362/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168358","id":1201018515,"node_id":"I_kwDOAEVQ_M5HlhaT","number":168358,"title":"prusa-slicer: Simple STL file crashes PrusaSlicer","user":{"login":"Moredread","id":100848,"node_id":"MDQ6VXNlcjEwMDg0OA==","avatar_url":"https://avatars.githubusercontent.com/u/100848?v=4","gravatar_id":"","url":"https://api.github.com/users/Moredread","html_url":"https://github.com/Moredread","followers_url":"https://api.github.com/users/Moredread/followers","following_url":"https://api.github.com/users/Moredread/following{/other_user}","gists_url":"https://api.github.com/users/Moredread/gists{/gist_id}","starred_url":"https://api.github.com/users/Moredread/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Moredread/subscriptions","organizations_url":"https://api.github.com/users/Moredread/orgs","repos_url":"https://api.github.com/users/Moredread/repos","events_url":"https://api.github.com/users/Moredread/events{/privacy}","received_events_url":"https://api.github.com/users/Moredread/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-12T04:30:06Z","updated_at":"2022-04-12T21:00:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nprusa-slicer crashes, maybe related to our wxWidgets version.\r\n\r\nSee https://github.com/prusa3d/PrusaSlicer/issues/8168 for now.\r\n\r\ncc @anna328p\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168358/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168322","id":1200512698,"node_id":"I_kwDOAEVQ_M5Hjl66","number":168322,"title":"nixos-rebuild overrides ssh ControlPath","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-11T20:43:13Z","updated_at":"2022-04-17T15:48:46Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI wanted to run `nixos-rebuild switch --flake '.#runner' --target-host example.com`\r\nI do this from a nix-shell which makes the control socket a tad long, deployment fails with:\r\n```\r\nunix_listener: path \"/tmp/nix-shell.ALygQn/nixos-rebuild.Xf5hWG/ssh-example.com.I9XWzKh3xOHIhaDg\" too long for Unix domain socket\r\n```\r\n\r\nIf I exit the nix-shell it succeeds. I then spent several minutes trying to understand why `export NIX_SSHOPTS=\"-xvvvv -F ssh_config \"` (with ssh_config overriding the ssh ControlPath ) was ignoring my ControlPath change. Directly setting the config would work though, i.e., ` export NIX_SSHOPTS=\"-vvvv -F ssh_config -o ControlPath=./%C\"` works.\r\n\r\nTurns out the option is overriden in https://github.com/NixOS/nixpkgs/blob/b1cdb609b053db6414e088fe0479c374203df841/pkgs/os-specific/linux/nixos-rebuild/nixos-rebuild.sh#L421 . It looks used just in case of cleanup https://github.com/NixOS/nixpkgs/blob/b1cdb609b053db6414e088fe0479c374203df841/pkgs/os-specific/linux/nixos-rebuild/nixos-rebuild.sh#L376\r\n\r\nI wonder if changing the line to \r\n`SSHOPTS=\"${NIX_SSHOPTS:- -o ControlMaster=auto -o ControlPath=$tmpDir/ssh-%n -o ControlPersist=60}\"`\r\nwouldn't be better ?\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168322/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168320","id":1200507119,"node_id":"I_kwDOAEVQ_M5Hjkjv","number":168320,"title":"plasma: Doesn't install packages needed for Info Center","user":{"login":"SuperSamus","id":40663462,"node_id":"MDQ6VXNlcjQwNjYzNDYy","avatar_url":"https://avatars.githubusercontent.com/u/40663462?v=4","gravatar_id":"","url":"https://api.github.com/users/SuperSamus","html_url":"https://github.com/SuperSamus","followers_url":"https://api.github.com/users/SuperSamus/followers","following_url":"https://api.github.com/users/SuperSamus/following{/other_user}","gists_url":"https://api.github.com/users/SuperSamus/gists{/gist_id}","starred_url":"https://api.github.com/users/SuperSamus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SuperSamus/subscriptions","organizations_url":"https://api.github.com/users/SuperSamus/orgs","repos_url":"https://api.github.com/users/SuperSamus/repos","events_url":"https://api.github.com/users/SuperSamus/events{/privacy}","received_events_url":"https://api.github.com/users/SuperSamus/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-11T20:37:33Z","updated_at":"2022-04-17T15:48:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nPlasma's Info Center requires some tools to display some types of information, which aren't installed by `services.xserver.desktopManager.plasma5.enable`. These are:\r\n\r\n- `lspci` (Devices->PCI)\r\n- `eglinfo` (Graphics->OpenGL (EGL))\r\n- `glxinfo` (Graphics->OpenGL (GLX))\r\n- `vulkaninfo` (Graphics->Vulkan)\r\n- `xdpyinfo` (Graphics->X-Server)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Plasma with `services.xserver.desktopManager.plasma5.enable`;\r\n2. On Plasma, open Info Center;\r\n3. Open one of the menus above (the ones in \"Describe the bug\");\r\n4. Info Center will complain that executable needed to show the information could not be found in $PATH (because it's not installed).\r\n\r\n### Expected behavior\r\nThe tools are installed, and Info Center will show the information.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168320/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168315","id":1200466195,"node_id":"I_kwDOAEVQ_M5HjakT","number":168315,"title":"Jellyfin exits to homescreen won't play back","user":{"login":"mkiljan","id":88359964,"node_id":"MDQ6VXNlcjg4MzU5OTY0","avatar_url":"https://avatars.githubusercontent.com/u/88359964?v=4","gravatar_id":"","url":"https://api.github.com/users/mkiljan","html_url":"https://github.com/mkiljan","followers_url":"https://api.github.com/users/mkiljan/followers","following_url":"https://api.github.com/users/mkiljan/following{/other_user}","gists_url":"https://api.github.com/users/mkiljan/gists{/gist_id}","starred_url":"https://api.github.com/users/mkiljan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mkiljan/subscriptions","organizations_url":"https://api.github.com/users/mkiljan/orgs","repos_url":"https://api.github.com/users/mkiljan/repos","events_url":"https://api.github.com/users/mkiljan/events{/privacy}","received_events_url":"https://api.github.com/users/mkiljan/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-11T19:58:18Z","updated_at":"2022-04-14T12:11:46Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nHi - I have Jellyfin and have everything on it and stream it from my apple laptop to my roku on two tv's with a mesh wifi system and an extra wifi adapter to the older 2012 macbook.\r\nEverytime I get on to either tv- jellyfin will show up, but when I attempt to play anything, it will only play for a few minutes and then exit right back to the homescreen- happens with movies and tv shows- with everything\r\n\r\n### Steps to reproduce\r\nTurn tv on. Turn roku on. or vice versa- always on- click on jellyfin and then choose show, then stops working\r\n\r\n## Technical details\r\nI know this isn't the most technical question, but I can't resolve it and cannot find a way to fix it anywhere on the net. Thank you.\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168315/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168296","id":1200290727,"node_id":"I_kwDOAEVQ_M5Hivun","number":168296,"title":"Packaging request: Konsave","user":{"login":"zendo","id":348013,"node_id":"MDQ6VXNlcjM0ODAxMw==","avatar_url":"https://avatars.githubusercontent.com/u/348013?v=4","gravatar_id":"","url":"https://api.github.com/users/zendo","html_url":"https://github.com/zendo","followers_url":"https://api.github.com/users/zendo/followers","following_url":"https://api.github.com/users/zendo/following{/other_user}","gists_url":"https://api.github.com/users/zendo/gists{/gist_id}","starred_url":"https://api.github.com/users/zendo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zendo/subscriptions","organizations_url":"https://api.github.com/users/zendo/orgs","repos_url":"https://api.github.com/users/zendo/repos","events_url":"https://api.github.com/users/zendo/events{/privacy}","received_events_url":"https://api.github.com/users/zendo/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-11T17:24:52Z","updated_at":"2022-04-11T17:24:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nA CLI program that will let you save and apply your Linux customizations with just one command! \r\nIt officially supports KDE Plasma but it can be used on all other desktop environments too!\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://pypi.org/project/Konsave/\r\n* source URL: https://github.com/Prayag2/konsave\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168296/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168277","id":1200021994,"node_id":"I_kwDOAEVQ_M5HhuHq","number":168277,"title":"LDtk - 2D level editor","user":{"login":"Ashe","id":8940077,"node_id":"MDQ6VXNlcjg5NDAwNzc=","avatar_url":"https://avatars.githubusercontent.com/u/8940077?v=4","gravatar_id":"","url":"https://api.github.com/users/Ashe","html_url":"https://github.com/Ashe","followers_url":"https://api.github.com/users/Ashe/followers","following_url":"https://api.github.com/users/Ashe/following{/other_user}","gists_url":"https://api.github.com/users/Ashe/gists{/gist_id}","starred_url":"https://api.github.com/users/Ashe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Ashe/subscriptions","organizations_url":"https://api.github.com/users/Ashe/orgs","repos_url":"https://api.github.com/users/Ashe/repos","events_url":"https://api.github.com/users/Ashe/events{/privacy}","received_events_url":"https://api.github.com/users/Ashe/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-11T14:01:14Z","updated_at":"2022-04-11T14:01:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nLDtk is an open source level editor that's used to make video games such as Dead Cells. It's just reached a big milestone and recently hit 1.0.0 release (now on 1.1.1).\r\n\r\nI apologise to the people of nixpkgs for requesting for so many new packages today!\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://ldtk.io/\r\n* source URL: https://github.com/deepnight/ldtk\r\n* license: mit\r\n* platforms: linux, mac, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168277/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168272","id":1199927521,"node_id":"I_kwDOAEVQ_M5HhXDh","number":168272,"title":"broken GNOME Authenticator","user":{"login":"nesnera","id":1737463,"node_id":"MDQ6VXNlcjE3Mzc0NjM=","avatar_url":"https://avatars.githubusercontent.com/u/1737463?v=4","gravatar_id":"","url":"https://api.github.com/users/nesnera","html_url":"https://github.com/nesnera","followers_url":"https://api.github.com/users/nesnera/followers","following_url":"https://api.github.com/users/nesnera/following{/other_user}","gists_url":"https://api.github.com/users/nesnera/gists{/gist_id}","starred_url":"https://api.github.com/users/nesnera/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nesnera/subscriptions","organizations_url":"https://api.github.com/users/nesnera/orgs","repos_url":"https://api.github.com/users/nesnera/repos","events_url":"https://api.github.com/users/nesnera/events{/privacy}","received_events_url":"https://api.github.com/users/nesnera/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-11T12:51:29Z","updated_at":"2022-04-25T13:38:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nPackage ‘authenticator-4.0.3’ in /nix/store/a9y4fzm81l0pv0kp7dkrzp22c94wjkcm-nixos-21.11.335677.ceaca998029/nixos/pkgs/applications/misc/authenticator/default.nix:95 is marked as broken, refusing to evaluate.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. # nix-env -iA nixos.authenticator\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@dotlambda \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.3, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335677.ceaca998029\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168272/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168256","id":1199710419,"node_id":"I_kwDOAEVQ_M5HgiDT","number":168256,"title":"jl: build failure due to ghc 9","user":{"login":"schuelermine","id":48802534,"node_id":"MDQ6VXNlcjQ4ODAyNTM0","avatar_url":"https://avatars.githubusercontent.com/u/48802534?v=4","gravatar_id":"","url":"https://api.github.com/users/schuelermine","html_url":"https://github.com/schuelermine","followers_url":"https://api.github.com/users/schuelermine/followers","following_url":"https://api.github.com/users/schuelermine/following{/other_user}","gists_url":"https://api.github.com/users/schuelermine/gists{/gist_id}","starred_url":"https://api.github.com/users/schuelermine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schuelermine/subscriptions","organizations_url":"https://api.github.com/users/schuelermine/orgs","repos_url":"https://api.github.com/users/schuelermine/repos","events_url":"https://api.github.com/users/schuelermine/events{/privacy}","received_events_url":"https://api.github.com/users/schuelermine/received_events","type":"User","site_admin":false},"labels":[{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""},{"id":3536622080,"node_id":"LA_kwDOAEVQ_M7SzJIA","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20build%20failure","name":"0.kind: build failure","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-11T09:52:30Z","updated_at":"2022-04-21T01:42:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n```\r\nbuilder for '/nix/store/rhspfhlw8414pfy394l77v9mp7fyqahv-jl-0.0.5.drv' failed with exit code 1;\r\nlast 10 log lines:\r\n> | ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^\r\n> [7 of 9] Compiling JL.Inferer ( src/JL/Inferer.hs, dist/build/JL/Inferer.o, dist/build/JL/Inferer.dyn_o )\r\n>\r\n> src/JL/Inferer.hs:12:1: warning: [-Wunused-imports]\r\n> The import of ‘Control.Monad.Writer’ is redundant\r\n> except perhaps to import instances from ‘Control.Monad.Writer’\r\n> To import instances alone, use: import Control.Monad.Writer()\r\n> |\r\n> 12 | import Control.Monad.Writer\r\n> | ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^\r\nFor full logs, run 'nix log /nix/store/rhspfhlw8414pfy394l77v9mp7fyqahv-jl-0.0.5.drv'.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Build `pkgs.jl`\r\n\r\n### Notify maintainers\r\n@fgaz \r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220403.bc4b9ee`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - channels(root): `\"nixos, nixpkgs\"`\r\n - channels(anselmschueler): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168256/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168248","id":1199622864,"node_id":"I_kwDOAEVQ_M5HgMrQ","number":168248,"title":"Hashlink - virtual machine for Haxe development","user":{"login":"Ashe","id":8940077,"node_id":"MDQ6VXNlcjg5NDAwNzc=","avatar_url":"https://avatars.githubusercontent.com/u/8940077?v=4","gravatar_id":"","url":"https://api.github.com/users/Ashe","html_url":"https://github.com/Ashe","followers_url":"https://api.github.com/users/Ashe/followers","following_url":"https://api.github.com/users/Ashe/following{/other_user}","gists_url":"https://api.github.com/users/Ashe/gists{/gist_id}","starred_url":"https://api.github.com/users/Ashe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Ashe/subscriptions","organizations_url":"https://api.github.com/users/Ashe/orgs","repos_url":"https://api.github.com/users/Ashe/repos","events_url":"https://api.github.com/users/Ashe/events{/privacy}","received_events_url":"https://api.github.com/users/Ashe/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-11T08:42:20Z","updated_at":"2022-04-24T10:44:22Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nHashlink is a virtual machine used in Haxe/Heaps game projects. This is the same stack that shiro games and motion twin uses to make things like Dead Cells and Northgard. The full steps for installing heaps (which goes through dependencies) can be found [here](https://heaps.io/documentation/installation.html), and one of the steps is to download hashlink and put it on the path.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://hashlink.haxe.org/\r\n* source URL: https://github.com/HaxeFoundation/hashlink/releases\r\n* license: mit \r\n* platforms: linux, mac, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168248/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168231","id":1199416716,"node_id":"I_kwDOAEVQ_M5HfaWM","number":168231,"title":"binwalk doesn't build on macOS because of permissions","user":{"login":"ethnt","id":137037,"node_id":"MDQ6VXNlcjEzNzAzNw==","avatar_url":"https://avatars.githubusercontent.com/u/137037?v=4","gravatar_id":"","url":"https://api.github.com/users/ethnt","html_url":"https://github.com/ethnt","followers_url":"https://api.github.com/users/ethnt/followers","following_url":"https://api.github.com/users/ethnt/following{/other_user}","gists_url":"https://api.github.com/users/ethnt/gists{/gist_id}","starred_url":"https://api.github.com/users/ethnt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ethnt/subscriptions","organizations_url":"https://api.github.com/users/ethnt/orgs","repos_url":"https://api.github.com/users/ethnt/repos","events_url":"https://api.github.com/users/ethnt/events{/privacy}","received_events_url":"https://api.github.com/users/ethnt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-11T05:30:58Z","updated_at":"2022-04-17T15:42:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI'm getting permission errors when building `binwalk` on macOS:\r\n\r\n```\r\nSignature Exception: [Errno 1] Operation not permitted: '/private/tmp/nix-build-python3.9-binwalk-2.3.3.drv-0/source/testing/tests/input-vectors/_dirtraversal.tar.extracted'\r\n----------------------------------------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/core/module.py\", line 595, in main\r\n retval = self.run()\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/modules/signature.py\", line 192, in run\r\n self.scan_file(fp)\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/modules/signature.py\", line 171, in scan_file\r\n self.result(r=r)\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/core/module.py\", line 489, in result\r\n getattr(self, dependency.attribute).callback(r)\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/modules/extractor.py\", line 256, in callback\r\n (extraction_directory, dd_file, scan_extracted_files, extraction_utility) = self.extract(r.offset,\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/modules/extractor.py\", line 628, in extract\r\n output_directory = self.build_output_directory(file_name)\r\n File \"/nix/store/ym1ds0c4dzwmp3xl66ng9zy3zd7lb72j-python3.9-binwalk-2.3.3/lib/python3.9/site-packages/binwalk/modules/extractor.py\", line 580, in build_output_directory\r\n os.chown(output_directory, self.runas_uid, self.runas_gid)\r\nPermissionError: [Errno 1] Operation not permitted: '/private/tmp/nix-build-python3.9-binwalk-2.3.3.drv-0/source/testing/tests/input-vectors/_dirtraversal.tar.extracted'\r\n----------------------------------------------------------------------------------------------------\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-env -iA nixpkgs.binwalk` or `nix-env -iA nixpkgs.python39Packages.binwalk`\r\n\r\n### Expected behavior\r\n\r\nbinwalk to be installed successfully.\r\n\r\n### Notify maintainers\r\n\r\n@mweinelt\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixpkgs\"`\r\n - channels(ethan): `\"nixpkgs, darwin\"`\r\n - nixpkgs: `/Users/ethan/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168231/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168223","id":1199362710,"node_id":"I_kwDOAEVQ_M5HfNKW","number":168223,"title":"Package/ module request : JustSayIt","user":{"login":"dit7ya","id":14034137,"node_id":"MDQ6VXNlcjE0MDM0MTM3","avatar_url":"https://avatars.githubusercontent.com/u/14034137?v=4","gravatar_id":"","url":"https://api.github.com/users/dit7ya","html_url":"https://github.com/dit7ya","followers_url":"https://api.github.com/users/dit7ya/followers","following_url":"https://api.github.com/users/dit7ya/following{/other_user}","gists_url":"https://api.github.com/users/dit7ya/gists{/gist_id}","starred_url":"https://api.github.com/users/dit7ya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dit7ya/subscriptions","organizations_url":"https://api.github.com/users/dit7ya/orgs","repos_url":"https://api.github.com/users/dit7ya/repos","events_url":"https://api.github.com/users/dit7ya/events{/privacy}","received_events_url":"https://api.github.com/users/dit7ya/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-11T04:14:06Z","updated_at":"2022-04-11T04:14:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nOffline, low latency, highly accurate and secure speech to command translation software and API.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/omlins/JustSayIt.jl\r\n* source URL: https://github.com/omlins/JustSayIt.jl\r\n* license: mit\r\n* platforms: linux, darwin","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168223/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168205","id":1199286879,"node_id":"I_kwDOAEVQ_M5He6pf","number":168205,"title":"gnucash needs dconf","user":{"login":"PhilippWoelfel","id":19400064,"node_id":"MDQ6VXNlcjE5NDAwMDY0","avatar_url":"https://avatars.githubusercontent.com/u/19400064?v=4","gravatar_id":"","url":"https://api.github.com/users/PhilippWoelfel","html_url":"https://github.com/PhilippWoelfel","followers_url":"https://api.github.com/users/PhilippWoelfel/followers","following_url":"https://api.github.com/users/PhilippWoelfel/following{/other_user}","gists_url":"https://api.github.com/users/PhilippWoelfel/gists{/gist_id}","starred_url":"https://api.github.com/users/PhilippWoelfel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PhilippWoelfel/subscriptions","organizations_url":"https://api.github.com/users/PhilippWoelfel/orgs","repos_url":"https://api.github.com/users/PhilippWoelfel/repos","events_url":"https://api.github.com/users/PhilippWoelfel/events{/privacy}","received_events_url":"https://api.github.com/users/PhilippWoelfel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-11T01:58:44Z","updated_at":"2022-04-24T20:42:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nGnucash needs `dconf`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install package `gnucash` using `configuration.nix`: `environment.systemPackages = with pkgs; [ gnucash ];`\r\n2. Run gnucash from terminal, click on `Edit->Preferences`. Try to change any setting. \r\n3. The settings do not change, and the terminal shows repeated error messages: `failed to commit changes to dconf: GDBus.Error:org.freedesktop.DBus.Error.ServiceUnknown: The name ca.desrt.dconf was not provided by any .service files`\r\n\r\n### Expected behavior\r\nCan change Gnucash settings\r\n\r\n### Additional context\r\nThe problem can be fixed by adding `programs.dconf.enable = true;` to the configuration.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05pre367991.42948b30067`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"home-manager, nixos\"`\r\n - channels(philipp): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168205/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168161","id":1199126487,"node_id":"I_kwDOAEVQ_M5HeTfX","number":168161,"title":"Make stage 1 systemd options visible","user":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"assignees":[{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false}],"milestone":null,"comments":2,"created_at":"2022-04-10T17:58:20Z","updated_at":"2022-04-18T18:47:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Issue to track where we have options that are currently invisible because the initrd is not stable yet:\r\n- [ ] nixos/modules/services/hardware/udev.nix\r\n- [ ] nixos/modules/system/boot/systemd/initrd.nix\r\n- [ ] nixos/modules/tasks/swraid.nix\r\n- [ ] nixos/modules/tasks/lvm.nix\r\n\r\nWarnings to emit:\r\n\r\n- [ ] hibernation needs to be explicitly enabled\r\n- [ ] LVM2 needs to be explicitly enabled\r\n- [ ] swraid needs to be explicitly enabled","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168161/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168147","id":1199065188,"node_id":"I_kwDOAEVQ_M5HeEhk","number":168147,"title":"nix-prefetch-git is (slightly) broken","user":{"login":"seppeljordan","id":4805746,"node_id":"MDQ6VXNlcjQ4MDU3NDY=","avatar_url":"https://avatars.githubusercontent.com/u/4805746?v=4","gravatar_id":"","url":"https://api.github.com/users/seppeljordan","html_url":"https://github.com/seppeljordan","followers_url":"https://api.github.com/users/seppeljordan/followers","following_url":"https://api.github.com/users/seppeljordan/following{/other_user}","gists_url":"https://api.github.com/users/seppeljordan/gists{/gist_id}","starred_url":"https://api.github.com/users/seppeljordan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/seppeljordan/subscriptions","organizations_url":"https://api.github.com/users/seppeljordan/orgs","repos_url":"https://api.github.com/users/seppeljordan/repos","events_url":"https://api.github.com/users/seppeljordan/events{/privacy}","received_events_url":"https://api.github.com/users/seppeljordan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-10T15:02:01Z","updated_at":"2022-04-10T15:02:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI tried to use nix-prefetch-git to check out `nixpkgs` while using the `--deepClone` options. The resulting sha256 hash is not the correct one to use with `nixpkgs.fetchgit`.\r\n\r\n### Steps To Reproduce\r\n\r\nI wrote a bash script that produces the issue on my machine.\r\n```\r\n#!/usr/bin/env sh\r\n\r\nset -x\r\n\r\nURL='https://github.com/NixOS/nixpkgs.git'\r\nOUTPUT_FROM_PREFETCH=$(nix-prefetch-git --deepClone \"${URL}\")\r\nSHA256_AS_CALCULATED_BY_PREFETCH=$(echo \"${OUTPUT_FROM_PREFETCH}\" | jq -r '.sha256')\r\nREVISION=$(echo \"${OUTPUT_FROM_PREFETCH}\" | jq -r '.rev')\r\nHASH_IN_SRI_FORMAT=$(nix hash to-sri sha256:${SHA256_AS_CALCULATED_BY_PREFETCH} | sed -e 's/^sha256\\-//')\r\nnix-build --no-out-link --expr \"with import <nixpkgs> {}; \r\nfetchgit \r\n{ url = \\\"${URL}\\\"; rev = \\\"${REVISION}\\\"; sha256 = \\\"${HASH_IN_SRI_FORMAT}\\\"; deepClone = true;}\r\n\"\r\n```\r\n\r\nWhen run this on my machine the following output is produced:\r\n\r\n```console\r\n$ sh test-prefetch-git.sh \r\n+ URL=https://github.com/NixOS/nixpkgs.git\r\n++ nix-prefetch-git --deepClone https://github.com/NixOS/nixpkgs.git\r\nInitialized empty Git repository in /tmp/nix-shell.zYwbSx/git-checkout-tmp-eYcwHIbd/nixpkgs/.git/\r\nremote: Enumerating objects: 49668, done.\r\nremote: Counting objects: 100% (49668/49668), done.\r\nremote: Compressing objects: 100% (32180/32180), done.\r\nremote: Total 49668 (delta 1794), reused 38869 (delta 1372), pack-reused 0\r\nReceiving objects: 100% (49668/49668), 33.85 MiB | 7.76 MiB/s, done.\r\nResolving deltas: 100% (1794/1794), done.\r\nFrom https://github.com/NixOS/nixpkgs\r\n * branch 164e44e62faf175771a3ea905876945529259ee6 -> FETCH_HEAD\r\nUpdating files: 100% (30098/30098), done.\r\nSwitched to a new branch 'fetchgit'\r\nremoving `.git'...\r\nwarning: unknown setting 'experimental-features'\r\n\r\ngit revision is 164e44e62faf175771a3ea905876945529259ee6\r\npath is /nix/store/m5gny1r98spjwqpcc2abnamdxa3g2wql-nixpkgs\r\ngit human-readable version is -- none --\r\nCommit date is 2022-04-10 09:33:57 -0500\r\nhash is 0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\r\n+ OUTPUT_FROM_PREFETCH='{\r\n \"url\": \"https://github.com/NixOS/nixpkgs.git\",\r\n \"rev\": \"164e44e62faf175771a3ea905876945529259ee6\",\r\n \"date\": \"2022-04-10T09:33:57-05:00\",\r\n \"path\": \"/nix/store/m5gny1r98spjwqpcc2abnamdxa3g2wql-nixpkgs\",\r\n \"sha256\": \"0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\",\r\n \"fetchLFS\": false,\r\n \"fetchSubmodules\": false,\r\n \"deepClone\": true,\r\n \"leaveDotGit\": false\r\n}'\r\n++ echo '{\r\n \"url\": \"https://github.com/NixOS/nixpkgs.git\",\r\n \"rev\": \"164e44e62faf175771a3ea905876945529259ee6\",\r\n \"date\": \"2022-04-10T09:33:57-05:00\",\r\n \"path\": \"/nix/store/m5gny1r98spjwqpcc2abnamdxa3g2wql-nixpkgs\",\r\n \"sha256\": \"0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\",\r\n \"fetchLFS\": false,\r\n \"fetchSubmodules\": false,\r\n \"deepClone\": true,\r\n \"leaveDotGit\": false\r\n}'\r\n++ jq -r .sha256\r\n+ SHA256_AS_CALCULATED_BY_PREFETCH=0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\r\n++ echo '{\r\n \"url\": \"https://github.com/NixOS/nixpkgs.git\",\r\n \"rev\": \"164e44e62faf175771a3ea905876945529259ee6\",\r\n \"date\": \"2022-04-10T09:33:57-05:00\",\r\n \"path\": \"/nix/store/m5gny1r98spjwqpcc2abnamdxa3g2wql-nixpkgs\",\r\n \"sha256\": \"0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\",\r\n \"fetchLFS\": false,\r\n \"fetchSubmodules\": false,\r\n \"deepClone\": true,\r\n \"leaveDotGit\": false\r\n}'\r\n++ jq -r .rev\r\n+ REVISION=164e44e62faf175771a3ea905876945529259ee6\r\n++ nix hash to-sri sha256:0mlbkq3q9yppw6dm7wsk8kvvwwvxrxcrv69nqy167dgypy4zq0hs\r\n++ sed -e 's/^sha256\\-//'\r\n+ HASH_IN_SRI_FORMAT=GgL8ib/+tWOCxzaZnVnPfXO+90RT81Ob4ff6hAeei1Y=\r\n+ nix-build --no-out-link --expr 'with import <nixpkgs> {}; \r\nfetchgit \r\n{ url = \"https://github.com/NixOS/nixpkgs.git\"; rev = \"164e44e62faf175771a3ea905876945529259ee6\"; sha256 = \"GgL8ib/+tWOCxzaZnVnPfXO+90RT81Ob4ff6hAeei1Y=\"; deepClone = true;}\r\n'\r\nthis derivation will be built:\r\n /nix/store/gkgsanlrsicgasmn2b8fkwpzax82sln7-nixpkgs-164e44e.drv\r\nbuilding '/nix/store/gkgsanlrsicgasmn2b8fkwpzax82sln7-nixpkgs-164e44e.drv'...\r\nexporting https://github.com/NixOS/nixpkgs.git (rev 164e44e62faf175771a3ea905876945529259ee6) into /nix/store/hls8xpfghx84bih44480hlx00in4g36v-nixpkgs-164e44e\r\nInitialized empty Git repository in /nix/store/hls8xpfghx84bih44480hlx00in4g36v-nixpkgs-164e44e/.git/\r\nremote: Enumerating objects: 49668, done.\r\nremote: Counting objects: 100% (49668/49668), done.\r\nremote: Compressing objects: 100% (32131/32131), done.\r\nremote: Total 49668 (delta 1841), reused 38936 (delta 1421), pack-reused 0\r\nReceiving objects: 100% (49668/49668), 33.83 MiB | 597.00 KiB/s, done.\r\nResolving deltas: 100% (1841/1841), done.\r\nFrom https://github.com/NixOS/nixpkgs\r\n * branch 164e44e62faf175771a3ea905876945529259ee6 -> FETCH_HEAD\r\nUpdating files: 100% (30098/30098), done.\r\nSwitched to a new branch 'fetchgit'\r\nEnumerating objects: 49668, done.\r\nCounting objects: 100% (49668/49668), done.\r\nCompressing objects: 100% (33552/33552), done.\r\nWriting objects: 100% (49668/49668), done.\r\nTotal 49668 (delta 1015), reused 47661 (delta 0), pack-reused 0\r\nEnumerating objects: 49668, done.\r\nNothing new to pack.\r\nerror: hash mismatch in fixed-output derivation '/nix/store/gkgsanlrsicgasmn2b8fkwpzax82sln7-nixpkgs-164e44e.drv':\r\n specified: sha256-GgL8ib/+tWOCxzaZnVnPfXO+90RT81Ob4ff6hAeei1Y=\r\n got: sha256-TImVBL7mn+eFshu6vodRxL+jSHgT5g6RHk/ohm3HDPI=\r\n```\r\n\r\n### Expected behavior\r\nI would expect that using the hash given by `nix-prefetch-git --deepClone` would work for `fetchgit { deepClone=true; ...}`.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\nI have no idea who the maintainer of this is. Sorry. If community members know who is responsible for this code, feel free to add them.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(me): `\"\"`\r\n - channels(root): `\"nixos-22.05pre345234.b2737d4980a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168147/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168100","id":1198900910,"node_id":"I_kwDOAEVQ_M5Hdcau","number":168100,"title":"Package Request: obs-vkcapture","user":{"login":"YellowOnion","id":364160,"node_id":"MDQ6VXNlcjM2NDE2MA==","avatar_url":"https://avatars.githubusercontent.com/u/364160?v=4","gravatar_id":"","url":"https://api.github.com/users/YellowOnion","html_url":"https://github.com/YellowOnion","followers_url":"https://api.github.com/users/YellowOnion/followers","following_url":"https://api.github.com/users/YellowOnion/following{/other_user}","gists_url":"https://api.github.com/users/YellowOnion/gists{/gist_id}","starred_url":"https://api.github.com/users/YellowOnion/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/YellowOnion/subscriptions","organizations_url":"https://api.github.com/users/YellowOnion/orgs","repos_url":"https://api.github.com/users/YellowOnion/repos","events_url":"https://api.github.com/users/YellowOnion/events{/privacy}","received_events_url":"https://api.github.com/users/YellowOnion/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-10T06:20:24Z","updated_at":"2022-04-12T10:49:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nVulkan/OpenGL plugin for OBS.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/nowrep/obs-vkcapture\r\n* source URL: https://github.com/nowrep/obs-vkcapture\r\n* license: gpl2\r\n* platforms: linux\r\n\r\n@jb55 @MP2E @V \r\n\r\nI quickly threw together this:\r\n\r\n```nix\r\n{ config, lib, pkgs, stdenv, fetchFromGitHub, vulkan-headers, ... }:\r\nlet info = lib.importJSON ./version.json;\r\nin\r\n with pkgs;\r\n stdenv.mkDerivation {\r\n pname = \"obs-vkcapture\";\r\n name = \"obs-vkcapture\";\r\n src = fetchFromGitHub {inherit (info) owner repo rev sha256;};\r\n\r\n nativeBuildInputs = [ cmake gcc vulkan-headers libGL obs-studio vulkan-loader pkg-config];\r\n }\r\n```\r\n\r\n\r\nEdit: Took me a we while to get it working locally,\r\n\r\nlooks like upstream mentions some issues with 32bit games:\r\n\r\nhttps://github.com/nowrep/obs-vkcapture/issues/36","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168100/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168067","id":1198793392,"node_id":"I_kwDOAEVQ_M5HdCKw","number":168067,"title":"filebeat: missing modules","user":{"login":"bbenno","id":32938211,"node_id":"MDQ6VXNlcjMyOTM4MjEx","avatar_url":"https://avatars.githubusercontent.com/u/32938211?v=4","gravatar_id":"","url":"https://api.github.com/users/bbenno","html_url":"https://github.com/bbenno","followers_url":"https://api.github.com/users/bbenno/followers","following_url":"https://api.github.com/users/bbenno/following{/other_user}","gists_url":"https://api.github.com/users/bbenno/gists{/gist_id}","starred_url":"https://api.github.com/users/bbenno/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bbenno/subscriptions","organizations_url":"https://api.github.com/users/bbenno/orgs","repos_url":"https://api.github.com/users/bbenno/repos","events_url":"https://api.github.com/users/bbenno/events{/privacy}","received_events_url":"https://api.github.com/users/bbenno/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-09T22:41:21Z","updated_at":"2022-04-15T22:00:17Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nEnabling the nginx module in the filebeat service results in the service crashing because it cannot find and load the module.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n1. Conigure filebeat with [appropriate module configuration](https://www.elastic.co/guide/en/beats/filebeat/7.16/filebeat-module-nginx.html)\r\n```nix\r\n{ config, pkgs, lib, ... }:\r\n{\r\n services.nginx.enable = true;\r\n # [...]\r\n services.filebeat = {\r\n enable = true;\r\n package = pkgs.filebeat7;\r\n modules.nginx = let nginxLogPath = \"/var/log/nginx/\";\r\n in {\r\n access = {\r\n enabled = true;\r\n var.paths = map (x: nginxLogPath + x) [ \"access.log*\" ];\r\n };\r\n error = {\r\n enabled = true;\r\n var.paths = map (x: nginxLogPath + x) [ \"error.log*\" ];\r\n };\r\n };\r\n };\r\n}\r\n```\r\n2. `nixos-rebuild`\r\n3. `systemctl status filebeat` → Failed to start Filebeat log shipper.\r\n\r\n```console\r\n> journalctl -eu filebeat\r\n[...]\r\nINFO instance/beat.go:328 Setup Beat: filebeat; Version: 7.16.1\r\nINFO [index-management] idxmgmt/std.go:184 Set output.elasticsearch.index to 'filebeat-7.16.1' as ILM is enabled.\r\nINFO [esclientleg] eslegclient/connection.go:102 elasticsearch url: https://[...].aws.cloud.es.io:443\r\nINFO [publisher] pipeline/module.go:113 Beat name: [...]\r\nERROR [modules] fileset/modules.go:142 Not loading modules. Module directory not found: /nix/store/x2nzjy32zlh47pbbblcx6mk7nldm27ig-filebeat-7.16.1/bin/module\r\nINFO instance/beat.go:461 filebeat stopped.\r\nERROR instance/beat.go:1015 Exiting: no modules or inputs enabled and configuration reloading disabled. What files do you want me to watch?\r\nExiting: no modules or inputs enabled and configuration reloading disabled. What files do you want me to watch?\r\nfilebeat.service: Main process exited, code=exited, status=1/FAILURE\r\n[...]\r\n```\r\n\r\n### Expected behavior\r\n\r\nThe `filebeat.service` starts and runs without issues.\r\n\r\n### Additional context\r\n\r\nfilebeat expects modules files within the non-existent `/nix/store/...-filebeat-7.16.1/bin/module` folder.\r\nThe `/nix/store/...-filebeat-7.16.1/bin` only contains the `filebeat` executable.\r\n\r\n### Notify maintainers\r\n\r\n@fadenb @basvandijk\r\n\r\n### Metadata\r\n\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.108, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336755.efea022d6fe, home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168067/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168064","id":1198788694,"node_id":"I_kwDOAEVQ_M5HdBBW","number":168064,"title":"Some plugins for haskell-language-server 8.10.7 are missing","user":{"login":"samhh","id":6402443,"node_id":"MDQ6VXNlcjY0MDI0NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6402443?v=4","gravatar_id":"","url":"https://api.github.com/users/samhh","html_url":"https://github.com/samhh","followers_url":"https://api.github.com/users/samhh/followers","following_url":"https://api.github.com/users/samhh/following{/other_user}","gists_url":"https://api.github.com/users/samhh/gists{/gist_id}","starred_url":"https://api.github.com/users/samhh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samhh/subscriptions","organizations_url":"https://api.github.com/users/samhh/orgs","repos_url":"https://api.github.com/users/samhh/repos","events_url":"https://api.github.com/users/samhh/events{/privacy}","received_events_url":"https://api.github.com/users/samhh/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-09T22:20:13Z","updated_at":"2022-04-14T12:50:08Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe core of haskell-language-server works, and it finds Cabal and GHC in a Nix shell, however HLint and other plugins like formatting providers don't work. I _think_ I'm using the correct HLS package per this [user guide](https://haskell4nix.readthedocs.io/nixpkgs-users-guide.html#how-to-install-haskell-language-server).\r\n\r\n### Steps To Reproduce\r\n\r\nMy nixpkgs everywhere that follows is recent \"unstable\".\r\n\r\nSteps to reproduce the behavior:\r\n1. Install `pkgs.haskell-language-server` globally or via Home Manager. Hook up a LSP-capable editor.\r\n2. Go into a Haskell project and enter this Nix shell:\r\n```nix\r\n{ pkgs ? import <nixpkgs> {} }:\r\n\r\npkgs.mkShell {\r\n buildInputs = with pkgs; [\r\n cabal-install\r\n haskell.compiler.ghc8107\r\n ];\r\n}\r\n```\r\n3. With the project building, add the following code:\r\n```hs\r\nfoo = (\"bar\")\r\n```\r\n\r\n### Expected behavior\r\n\r\nHLS should report a HLint warning, like it does if you run `hlint <file>`:\r\n\r\n```\r\n<file>: Warning: Redundant bracket\r\nFound:\r\n (\"bar\")\r\nPerhaps:\r\n \"bar\"\r\n\r\n1 hint\r\n```\r\n\r\n### Additional context\r\n\r\nWith a formatting provider configured such as stylish-haskell, HLS reports:\r\n\r\n```\r\nhls: -32600: No plugin enabled for STextDocumentFormatting, available: []\r\n```\r\n\r\nHLS seems able to find stuff in the Nix shell environment:\r\n\r\n```console\r\n$ haskell-language-server --probe-tools\r\nhaskell-language-server version: 1.6.1.1 (GHC: 9.0.2) (PATH: /nix/store/hagqp70hxxrf5kwjsksfm74h7i0s29im-haskell-language-server-1.6.1.1/bin/haskell-language-server)\r\nTool versions found on the $PATH\r\ncabal:\t\t3.6.2.0\r\nstack:\t\tNot found\r\nghc:\t\t8.10.7\r\n```\r\n\r\nI've recently migrated from Arch to NixOS with the same editor (Neovim) config. On Arch with GHCup both HLint and stylish-haskell worked. I'm convinced this isn't an editor issue because HLint previously worked without any reference to it in my editor config.\r\n\r\n### Notify maintainers\r\n\r\nBest guess based upon recent `hackage-packages.nix` activity: @maralorn @sternenseemann @gebner \r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220406.b6966d9`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(sam): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168064/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168050","id":1198769239,"node_id":"I_kwDOAEVQ_M5Hc8RX","number":168050,"title":"mediathekview not working on arm","user":{"login":"irishrain","id":74204581,"node_id":"MDQ6VXNlcjc0MjA0NTgx","avatar_url":"https://avatars.githubusercontent.com/u/74204581?v=4","gravatar_id":"","url":"https://api.github.com/users/irishrain","html_url":"https://github.com/irishrain","followers_url":"https://api.github.com/users/irishrain/followers","following_url":"https://api.github.com/users/irishrain/following{/other_user}","gists_url":"https://api.github.com/users/irishrain/gists{/gist_id}","starred_url":"https://api.github.com/users/irishrain/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/irishrain/subscriptions","organizations_url":"https://api.github.com/users/irishrain/orgs","repos_url":"https://api.github.com/users/irishrain/repos","events_url":"https://api.github.com/users/irishrain/events{/privacy}","received_events_url":"https://api.github.com/users/irishrain/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-09T20:58:47Z","updated_at":"2022-04-09T20:58:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nThe mediathekview package downloads MediathekView-${version}-linux.tar.gz. This contains the binaries for amd64 architecture, and therefore does not work on arm. The package should use MediathekView-${version}-linux-armhf.tar.gz on arm architecture.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install NixOS on arm\r\n2. Install mediathekview package\r\n3. start \"mediathek\"\r\n4. There will be an error message about the wrong architecture\r\n\r\n### Expected behavior\r\nMediathekview should work on arm\r\n\r\n### Notify maintainers\r\n@moredread\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168050/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168019","id":1198718349,"node_id":"I_kwDOAEVQ_M5Hcv2N","number":168019,"title":"Can we package opencl-amdgpu-pro-icd?","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-09T17:16:35Z","updated_at":"2022-04-09T17:16:35Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\nCan we use OpenCL from amdgpu-pro together with amdgpu?\r\n\r\nArch has such a package: https://aur.archlinux.org/packages/opencl-amd\r\n\r\nSome links:\r\n\r\n- https://github.com/Diolinux/amd-opencl-pro-linux-resolve/blob/main/install-opencl-amd.sh\r\n- https://math.dartmouth.edu/~sarunas/amdgpu.html\r\n- https://linuxconfig.org/install-opencl-for-the-amdgpu-open-source-drivers-on-debian-and-ubuntu\r\n- https://devtalk.blender.org/t/guide-install-amd-opencl-on-pop-os-some-ubuntu-derivates-linux-amdgpu-amdgpu-pro-rocm-rocr/13458\r\n\r\nI hope to be able to use davinci-resolve with amd gpu with this and still use the open source driver.\r\n\r\n@corngood\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://amdgpu-install.readthedocs.io/en/latest/install-overview.html#stack-use-cases\r\n* source URL: http://repo.radeon.com/amdgpu-install/latest/\r\n* license: unfree\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":1,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168019/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018/events","html_url":"https://github.com/NixOS/nixpkgs/issues/168018","id":1198714256,"node_id":"I_kwDOAEVQ_M5Hcu2Q","number":168018,"title":"Update ethminer to use addOpenGLRunpath","user":{"login":"SomeoneSerge","id":9720532,"node_id":"MDQ6VXNlcjk3MjA1MzI=","avatar_url":"https://avatars.githubusercontent.com/u/9720532?v=4","gravatar_id":"","url":"https://api.github.com/users/SomeoneSerge","html_url":"https://github.com/SomeoneSerge","followers_url":"https://api.github.com/users/SomeoneSerge/followers","following_url":"https://api.github.com/users/SomeoneSerge/following{/other_user}","gists_url":"https://api.github.com/users/SomeoneSerge/gists{/gist_id}","starred_url":"https://api.github.com/users/SomeoneSerge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SomeoneSerge/subscriptions","organizations_url":"https://api.github.com/users/SomeoneSerge/orgs","repos_url":"https://api.github.com/users/SomeoneSerge/repos","events_url":"https://api.github.com/users/SomeoneSerge/events{/privacy}","received_events_url":"https://api.github.com/users/SomeoneSerge/received_events","type":"User","site_admin":false},"labels":[{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-09T17:00:20Z","updated_at":"2022-04-09T17:01:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nCurrently `ethminer` uses `wrapProgram` instead of patchelf:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/7689f188c97dfd95e2cd2b78522aaab7207d74ab/pkgs/tools/misc/ethminer/default.nix#L84\r\n\r\nAfter which the NixOS module performs another, redundant, modification to the `LD_LIBRARY_PATH`:\r\n\r\nhttps://github.com/NixOS/nixpkgs/pull/167209\r\n\r\n\r\n### Solution\r\n\r\n- [ ] `ethminer` should switch to `addOpenGLRunpath`, conditionally on `cudaSupport`\r\n- [ ] The NixOS module shouldn't touch `LD_LIBRARY_PATH`, but should check that `hardware.opengl.enable` is `true`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/168018/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167994","id":1198601936,"node_id":"I_kwDOAEVQ_M5HcTbQ","number":167994,"title":"systemd-cryptsetup is broken when used with tpm2","user":{"login":"ymatsiuk","id":24990891,"node_id":"MDQ6VXNlcjI0OTkwODkx","avatar_url":"https://avatars.githubusercontent.com/u/24990891?v=4","gravatar_id":"","url":"https://api.github.com/users/ymatsiuk","html_url":"https://github.com/ymatsiuk","followers_url":"https://api.github.com/users/ymatsiuk/followers","following_url":"https://api.github.com/users/ymatsiuk/following{/other_user}","gists_url":"https://api.github.com/users/ymatsiuk/gists{/gist_id}","starred_url":"https://api.github.com/users/ymatsiuk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ymatsiuk/subscriptions","organizations_url":"https://api.github.com/users/ymatsiuk/orgs","repos_url":"https://api.github.com/users/ymatsiuk/repos","events_url":"https://api.github.com/users/ymatsiuk/events{/privacy}","received_events_url":"https://api.github.com/users/ymatsiuk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-04-09T13:27:24Z","updated_at":"2022-04-21T23:23:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nPlugins built with `systemd` are not available in `cryptsetup`\r\n```\r\nmachine # [ 5.839874] systemd-cryptsetup[455]: Token 0 unusable for segment 0 with desired keyslot priority 2.\r\nmachine # [ 5.840623] systemd-cryptsetup[455]: Trying to load /nix/store/l6y9kks5z6ywsxivnld12hh326lbx2yc-cryptsetup-2.4.3/lib/cryptsetup/libcryptsetup-token-systemd-tpm2.so.\r\nmachine # [ 5.841665] systemd-cryptsetup[455]: /nix/store/l6y9kks5z6ywsxivnld12hh326lbx2yc-cryptsetup-2.4.3/lib/cryptsetup/libcryptsetup-token-systemd-tpm2.so: cannot open shared object file: No such file or directory\r\nmachine # [ 5.842962] systemd-cryptsetup[455]: No TPM2 metadata enrolled in LUKS2 header or TPM2 support not available, falling back to traditional unlocking.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n#### Local with TPM2\r\n```bash\r\nsystemd-cryptenroll --tpm2-device=list\r\ndd if=/dev/zero of=encrypted.img bs=1 count=0 seek=1G\r\necho -n lukspass | cryptsetup luksFormat -q encrypted.img -\r\n\r\n# confirm it works with cryptsetup and password\r\nsudo cryptsetup luksOpen encrypted.img foo\r\n# enter password: lukspass\r\nsudo cryptsetup luksClose foo\r\n\r\n# enroll tpm2\r\nsudo PASSWORD=lukspass systemd-cryptenroll --tpm2-device=auto --tpm2-pcrs=7 encrypted.img\r\nsudo ${pkgs.systemd}/lib/systemd/systemd-cryptsetup attach luks encrypted.img - tpm2-device=auto\r\n```\r\nPassword prompt appears:\r\n```bash\r\nSet cipher aes, mode xts-plain64, key size 512 bits for device encrypted.img.\r\n🔐 Please enter passphrase for disk foo: (press TAB for no echo)\r\n```\r\n\r\n```bash\r\n#cleanup\r\nsudo systemd-cryptenroll --wipe-slot=tpm2 encrypted.img\r\n```\r\n\r\n#### Using tests with `swtpm`\r\n1. enable debug in systemd `boot.kernelParams = [ \"systemd.log_level=debug\" \"systemd.log_target=console\" \"console=ttyS0,38400\" \"console=tty1\" ];`\r\n2. run the test `nix build .#nixosTests.systemd-cryptenroll` (give it a minute since it spits out lots of debug statement)\r\n3. inspect the log `nix log .#nixosTests.systemd-cryptenroll`\r\n\r\n### Expected behavior\r\nPassword prompt should not appear\r\n\r\n### Additional context\r\nhttps://github.com/NixOS/nixpkgs/pull/139864 should've been caught this issue\r\n\r\n`strace` suggests that the new [systemd feature](https://github.com/systemd/systemd/blob/928c6c00c37cc01860a0a6fec30e8188bb52929b/NEWS#L647-L649) is to blame:\r\n```\r\n1933590 openat(AT_FDCWD, \"/nix/store/l6y9kks5z6ywsxivnld12hh326lbx2yc-cryptsetup-2.4.3/lib/cryptsetup/libcryptsetup-token-systemd-tpm2.so\", O_RDONLY|O_CLOEXEC) = -1 ENOENT (No such file or directory)\r\n```\r\n\r\nIt seems like `cryptsetup` expects the [library](https://gitlab.com/cryptsetup/cryptsetup/-/blob/main/lib/luks2/luks2_token.c#L154) to be present under `${cryptsetup}/lib/cryptsetup` but it's present under `${systemd}/lib/cryptsetup`\r\nNo matter what I do I get into dependency loop 🤷🏻 \r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@flokli @kloenk @mic92\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - channels(ymatsiuk): `\"\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167994/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167982","id":1198542423,"node_id":"I_kwDOAEVQ_M5HcE5X","number":167982,"title":"Touchpad doesn't work on Lenovo Yoga Slim 7 (NixOS)","user":{"login":"Wonderful-guy","id":67173663,"node_id":"MDQ6VXNlcjY3MTczNjYz","avatar_url":"https://avatars.githubusercontent.com/u/67173663?v=4","gravatar_id":"","url":"https://api.github.com/users/Wonderful-guy","html_url":"https://github.com/Wonderful-guy","followers_url":"https://api.github.com/users/Wonderful-guy/followers","following_url":"https://api.github.com/users/Wonderful-guy/following{/other_user}","gists_url":"https://api.github.com/users/Wonderful-guy/gists{/gist_id}","starred_url":"https://api.github.com/users/Wonderful-guy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Wonderful-guy/subscriptions","organizations_url":"https://api.github.com/users/Wonderful-guy/orgs","repos_url":"https://api.github.com/users/Wonderful-guy/repos","events_url":"https://api.github.com/users/Wonderful-guy/events{/privacy}","received_events_url":"https://api.github.com/users/Wonderful-guy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-09T11:35:03Z","updated_at":"2022-04-15T16:47:17Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nTouchpad doesn't work on laptop Lenovo Yoga Slim 7 14ITL05.\r\n```\r\nnix --version: \r\nnix (Nix) 2.3.16\r\n```\r\nconfiguration.nix: system.stateVersion = \"22.05\"; \r\n\r\n### Expected behavior\r\nI expect the touchpad working.\r\n\r\n### Additional context\r\n```\r\nxinput list\r\n⎡ Virtual core pointer id=2 [master pointer (3)]\r\n⎜ ↳ Virtual core XTEST pointer id=4 [slave pointer (2)]\r\n⎜ ↳ USB Optical Mouse id=10 [slave pointer (2)]\r\n⎣ Virtual core keyboard id=3 [master keyboard (2)]\r\n ↳ Virtual core XTEST keyboard id=5 [slave keyboard (3)]\r\n ↳ Power Button id=6 [slave keyboard (3)]\r\n ↳ Video Bus id=7 [slave keyboard (3)]\r\n ↳ Power Button id=8 [slave keyboard (3)]\r\n ↳ Sleep Button id=9 [slave keyboard (3)]\r\n ↳ Integrated Camera: Integrated C id=11 [slave keyboard (3)]\r\n ↳ Integrated Camera: Integrated I id=12 [slave keyboard (3)]\r\n ↳ Ideapad extra buttons id=13 [slave keyboard (3)]\r\n ↳ Intel HID events id=14 [slave keyboard (3)]\r\n ↳ AT Translated Set 2 keyboard id=15 [slave keyboard (3)]\r\n```\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(gur): `\"\"`\r\n - channels(root): `\"nixos-21.11.336847.e387bb3a4d0\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167982/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167972","id":1198456477,"node_id":"I_kwDOAEVQ_M5Hbv6d","number":167972,"title":"`pycrypto-2.6.1-13.1` fails to build","user":{"login":"dschrempf","id":5596239,"node_id":"MDQ6VXNlcjU1OTYyMzk=","avatar_url":"https://avatars.githubusercontent.com/u/5596239?v=4","gravatar_id":"","url":"https://api.github.com/users/dschrempf","html_url":"https://github.com/dschrempf","followers_url":"https://api.github.com/users/dschrempf/followers","following_url":"https://api.github.com/users/dschrempf/following{/other_user}","gists_url":"https://api.github.com/users/dschrempf/gists{/gist_id}","starred_url":"https://api.github.com/users/dschrempf/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dschrempf/subscriptions","organizations_url":"https://api.github.com/users/dschrempf/orgs","repos_url":"https://api.github.com/users/dschrempf/repos","events_url":"https://api.github.com/users/dschrempf/events{/privacy}","received_events_url":"https://api.github.com/users/dschrempf/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"oxzi","id":8402811,"node_id":"MDQ6VXNlcjg0MDI4MTE=","avatar_url":"https://avatars.githubusercontent.com/u/8402811?v=4","gravatar_id":"","url":"https://api.github.com/users/oxzi","html_url":"https://github.com/oxzi","followers_url":"https://api.github.com/users/oxzi/followers","following_url":"https://api.github.com/users/oxzi/following{/other_user}","gists_url":"https://api.github.com/users/oxzi/gists{/gist_id}","starred_url":"https://api.github.com/users/oxzi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/oxzi/subscriptions","organizations_url":"https://api.github.com/users/oxzi/orgs","repos_url":"https://api.github.com/users/oxzi/repos","events_url":"https://api.github.com/users/oxzi/events{/privacy}","received_events_url":"https://api.github.com/users/oxzi/received_events","type":"User","site_admin":false},"assignees":[{"login":"oxzi","id":8402811,"node_id":"MDQ6VXNlcjg0MDI4MTE=","avatar_url":"https://avatars.githubusercontent.com/u/8402811?v=4","gravatar_id":"","url":"https://api.github.com/users/oxzi","html_url":"https://github.com/oxzi","followers_url":"https://api.github.com/users/oxzi/followers","following_url":"https://api.github.com/users/oxzi/following{/other_user}","gists_url":"https://api.github.com/users/oxzi/gists{/gist_id}","starred_url":"https://api.github.com/users/oxzi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/oxzi/subscriptions","organizations_url":"https://api.github.com/users/oxzi/orgs","repos_url":"https://api.github.com/users/oxzi/repos","events_url":"https://api.github.com/users/oxzi/events{/privacy}","received_events_url":"https://api.github.com/users/oxzi/received_events","type":"User","site_admin":false}],"milestone":null,"comments":1,"created_at":"2022-04-09T09:22:33Z","updated_at":"2022-04-09T11:08:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen building `weechat` with scripts on latest `nixpgks-unstable-small`:\r\n\r\n```\r\n weechat = super.weechat.override {\r\n configure = { availablePlugins, ... }: {\r\n scripts = with super.weechatScripts; [\r\n buffer_autoset\r\n colorize_nicks\r\n highmon\r\n wee-slack\r\n weechat-autosort\r\n weechat-go\r\n weechat-matrix\r\n weechat-notify-send\r\n weechat-otr\r\n ];\r\n };\r\n };\r\n```\r\n\r\nI get the following error:\r\n\r\n```\r\nerror: builder for '/nix/store/0s29dz0lw0yr0r6k4w6iyqa1sng78x9i-python3.9-pycrypto-2.6.1-13.1.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > dist.run_commands()\r\n > File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/dist.py\", line 967, in run_commands\r\n > self.run_command(cmd)\r\n > File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/dist.py\", line 986, in run_command\r\n > cmd_obj.run()\r\n > File \"setup.py\", line 316, in run\r\n > from Crypto import SelfTest\r\n > File \"/build/python-crypto/build/lib.linux-x86_64-3.9/Crypto/SelfTest/__init__.py\", line 35, in <module>\r\n > from StringIO import StringIO\r\n > ModuleNotFoundError: No module named 'StringIO'\r\n For full logs, run 'nix log /nix/store/0s29dz0lw0yr0r6k4w6iyqa1sng78x9i-python3.9-pycrypto-2.6.1-13.1.drv'.\r\nerror: 1 dependencies of derivation '/nix/store/vmzwc5376fd7hgxpj27qabr3g3j3b00j-weechat-otr-env.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/43r0bkzrmgmhwyz2gi8q2pv0xbivpzlz-libpath.patch.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/drk6n0j55zn8zgrg96wqwd69rd77mq4s-weechat-otr-1.9.2.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/4z2lnxd75p9yn2avxpv0zaj0f7dxfji7-weechat-headless.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/cxh6pjkhm5d2z3p5ysll3ac10g26g3yc-weechat-bin-env-3.4.1.drv' failed to build\r\nerror (ignored): error: cannot unlink '/tmp/nix-build-deploy-rs-0.1.0.drv-0/xdb4am9sh2aakxilgrmb4851xc114lr5-source/target/x86_64-unknown-linux-gnu/release/deps': Directory not empty\r\nerror: 1 dependencies of derivation '/nix/store/m5a2h0ka6yr64m5013rcxdayhhayvb5b-home-manager-path.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/rsq7406lgj7ikssa3n5qr5bv8fri1vnl-home-manager-generation.drv' failed to build\r\nerror: error: 1 dependencies of derivation '/nix/store/99lhxj5avp3b27h34hbbr9ax3ka5x5s1-activatable-home-manager-generation.drv' failed to build\r\n```\r\n\r\nThe error is caused by `pycrypto`, the last lines of the logs are:\r\n\r\n```\r\nrunning test\r\n/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/command/install.py:34: SetuptoolsDeprecationWarning: setup.py install is deprecated. Use build and pi>\r\n warnings.warn(\r\nTraceback (most recent call last):\r\n File \"/build/python-crypto/nix_run_setup\", line 8, in <module>\r\n exec(compile(getattr(tokenize, 'open', open)(__file__).read().replace('\\\\r\\\\n', '\\\\n'), __file__, 'exec'))\r\n File \"setup.py\", line 451, in <module>\r\n core.setup(**kw)\r\n File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/core.py\", line 148, in setup\r\n return run_commands(dist)\r\n File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/core.py\", line 163, in run_commands\r\n dist.run_commands()\r\n File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/dist.py\", line 967, in run_commands\r\n self.run_command(cmd)\r\n File \"/nix/store/cc6n0h7n7db2gc1x4a3vh0z6aks7gand-python3.9-setuptools-60.8.2/lib/python3.9/site-packages/setuptools/_distutils/dist.py\", line 986, in run_command\r\n cmd_obj.run()\r\n File \"setup.py\", line 316, in run\r\n from Crypto import SelfTest\r\n File \"/build/python-crypto/build/lib.linux-x86_64-3.9/Crypto/SelfTest/__init__.py\", line 35, in <module>\r\n from StringIO import StringIO\r\nModuleNotFoundError: No module named 'StringIO'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Build `weechat` using the provided override.\r\n\r\n### Additional context\r\nBuilding `python3Packages.pycrypto` using `nix shell nixpkgs-unstable#python3Packages.pycrypto` works. I don't exactly know why (maybe the tests are deactivated?).\r\n\r\n### Notify maintainers\r\nNo maintainers in `pycrpto/default.nix`.\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka), 22.05.20220408.e10e367`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - nixpkgs: `/nix/store/040yq8hrrylcby60md5lsipc7mz19bik-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167972/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167967","id":1198395572,"node_id":"I_kwDOAEVQ_M5HbhC0","number":167967,"title":"logseq 0.6.5 error with auto git commit","user":{"login":"Eliot00","id":18375468,"node_id":"MDQ6VXNlcjE4Mzc1NDY4","avatar_url":"https://avatars.githubusercontent.com/u/18375468?v=4","gravatar_id":"","url":"https://api.github.com/users/Eliot00","html_url":"https://github.com/Eliot00","followers_url":"https://api.github.com/users/Eliot00/followers","following_url":"https://api.github.com/users/Eliot00/following{/other_user}","gists_url":"https://api.github.com/users/Eliot00/gists{/gist_id}","starred_url":"https://api.github.com/users/Eliot00/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Eliot00/subscriptions","organizations_url":"https://api.github.com/users/Eliot00/orgs","repos_url":"https://api.github.com/users/Eliot00/repos","events_url":"https://api.github.com/users/Eliot00/events{/privacy}","received_events_url":"https://api.github.com/users/Eliot00/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-09T07:27:53Z","updated_at":"2022-04-09T07:27:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nEnabled logseq's Git auto commit feature, it show an error:\r\n\r\n```log\r\n/nix/store/yynafzpallyyx5rc5cy3a8gkxm54v22x-logseq-0.6.5/share/logseq/resources/app/node_modules/dugite/git/bin/git: /nix/store/ilfqlmd6npxh3zaszdj7dj7zy6w96gmi-zlib-1.2.12/lib/libz.so.1: no version information available (required by /nix/store/yynafzpallyyx5rc5cy3a8gkxm54v22x-logseq-0.6.5/share/logseq/resources/app/node_modules/dugite/git/bin/git)\r\n\r\nIf you don't want to see those errors or don't need git, you can disable the \"Git auto commit\" feature on Settings > Version control.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\n\r\nno error\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.32, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(elliot): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167967/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167931","id":1197886232,"node_id":"I_kwDOAEVQ_M5HZksY","number":167931,"title":"xgboost: checkPhase demands GPUs when built with cudaSupport","user":{"login":"SomeoneSerge","id":9720532,"node_id":"MDQ6VXNlcjk3MjA1MzI=","avatar_url":"https://avatars.githubusercontent.com/u/9720532?v=4","gravatar_id":"","url":"https://api.github.com/users/SomeoneSerge","html_url":"https://github.com/SomeoneSerge","followers_url":"https://api.github.com/users/SomeoneSerge/followers","following_url":"https://api.github.com/users/SomeoneSerge/following{/other_user}","gists_url":"https://api.github.com/users/SomeoneSerge/gists{/gist_id}","starred_url":"https://api.github.com/users/SomeoneSerge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SomeoneSerge/subscriptions","organizations_url":"https://api.github.com/users/SomeoneSerge/orgs","repos_url":"https://api.github.com/users/SomeoneSerge/repos","events_url":"https://api.github.com/users/SomeoneSerge/events{/privacy}","received_events_url":"https://api.github.com/users/SomeoneSerge/received_events","type":"User","site_admin":false},"labels":[{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-08T22:03:18Z","updated_at":"2022-04-15T20:03:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"The failing build: [[233]](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F0la8zlmdr0r6z700w8nc2dny3ji47fn3-xgboost-1.5.2.drv/log?via-job=bb35aaa9-52f1-4846-ba13-22a8f90c0ea3).\r\n\r\nCC @NixOS/cuda-maintainers @abbradar\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167931/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167913","id":1197691121,"node_id":"I_kwDOAEVQ_M5HY1Dx","number":167913,"title":"Apache beam GCP would be awesome to have","user":{"login":"blackgnezdo","id":8768818,"node_id":"MDQ6VXNlcjg3Njg4MTg=","avatar_url":"https://avatars.githubusercontent.com/u/8768818?v=4","gravatar_id":"","url":"https://api.github.com/users/blackgnezdo","html_url":"https://github.com/blackgnezdo","followers_url":"https://api.github.com/users/blackgnezdo/followers","following_url":"https://api.github.com/users/blackgnezdo/following{/other_user}","gists_url":"https://api.github.com/users/blackgnezdo/gists{/gist_id}","starred_url":"https://api.github.com/users/blackgnezdo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/blackgnezdo/subscriptions","organizations_url":"https://api.github.com/users/blackgnezdo/orgs","repos_url":"https://api.github.com/users/blackgnezdo/repos","events_url":"https://api.github.com/users/blackgnezdo/events{/privacy}","received_events_url":"https://api.github.com/users/blackgnezdo/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T19:00:54Z","updated_at":"2022-04-08T19:02:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nI was happy to find that [apache beam is already packaged](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/python-modules/apache-beam/default.nix). Sadly, trying to run an example quickly resulted in a missing runtime dependency:\r\n```\r\n ❯ nix-channel --add https://nixos.org/channels/nixpkgs-unstable unstable\r\n ❯ nix-channel --update\r\n ❯ nix-shell -p '(import <unstable> {}).python39Packages.apache-beam'\r\n \r\n[nix-shell:~]$ python3 ~/beam/examples/wordcount.py --output /tmp/x\r\n\r\n/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/__init__.py:79: UserWarning: This version of Apache Beam has not been sufficiently tested on Python 3.9. You may encounter bugs or missing features.\r\n warnings.warn(\r\nINFO:root:Missing pipeline option (runner). Executing pipeline using the default runner: DirectRunner.\r\nTraceback (most recent call last):\r\n File \"/home/gnezdo/beam/examples/wordcount.py\", line 94, in <module>\r\n run()\r\n File \"/home/gnezdo/beam/examples/wordcount.py\", line 73, in run\r\n lines = p | 'Read' >> ReadFromText(known_args.input)\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/textio.py\", line 666, in __init__\r\n self._source = self._source_class(\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/textio.py\", line 128, in __init__\r\n super().__init__(\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/filebasedsource.py\", line 124, in __init__\r\n self._validate()\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/options/value_provider.py\", line 193, in _f\r\n return fnc(self, *args, **kwargs)\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/filebasedsource.py\", line 185, in _validate\r\n match_result = FileSystems.match([pattern], limits=[1])[0]\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/filesystems.py\", line 203, in match\r\n filesystem = FileSystems.get_filesystem(patterns[0])\r\n File \"/nix/store/v264lg3apzdj0zpc4xb6zg29a17mcxnw-python3.9-apache-beam-2.35.0/lib/python3.9/site-packages/apache_beam/io/filesystems.py\", line 103, in get_filesystem\r\n raise ValueError(\r\nValueError: Unable to get filesystem from specified path, please use the correct path or ensure the required dependency is installed, e.g., pip install apache-beam[gcp]. Path specified: gs://dataflow-samples/shakespeare/kinglear.txt\r\n```\r\n\r\nSome place else `pip install apache-beam[gcp]` would suffice, but this is clearly not a Nix way.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://beam.apache.org/\r\n* source URL:\r\n* license: apache\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167913/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167909","id":1197653958,"node_id":"I_kwDOAEVQ_M5HYr_G","number":167909,"title":"Pantheon with amdgpu-pro driver: xorg fails to start","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-08T18:20:31Z","updated_at":"2022-04-20T15:28:23Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `services.xserver.desktopManager.pantheon.enable = true;`\r\n2. `services.xserver.videoDrivers = [ \"amdgpu-pro\" ];`\r\n3. Fatal server error\r\n\r\nFull Xorg log: https://gist.github.com/davidak/fc9fcbc2b23c0b67a678443b79f30ded\r\n\r\n### Expected behavior\r\nSame as with amdgpu driver.\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Additional context\r\nIt works perfectly with amdgpu driver.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@corngood asked for log in https://github.com/NixOS/nixpkgs/pull/151019#issuecomment-1001810016.\r\n\r\nCan you have a look?\r\n\r\n### Metadata\r\n\r\nBuild from unstable: 22.05pre367572.b6966d911da\r\n\r\nStill reproducible with 22.05pre369524.5181d5945ed","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167909/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167896","id":1197492757,"node_id":"I_kwDOAEVQ_M5HYEoV","number":167896,"title":"Package/ Module Request: Firezone","user":{"login":"dit7ya","id":14034137,"node_id":"MDQ6VXNlcjE0MDM0MTM3","avatar_url":"https://avatars.githubusercontent.com/u/14034137?v=4","gravatar_id":"","url":"https://api.github.com/users/dit7ya","html_url":"https://github.com/dit7ya","followers_url":"https://api.github.com/users/dit7ya/followers","following_url":"https://api.github.com/users/dit7ya/following{/other_user}","gists_url":"https://api.github.com/users/dit7ya/gists{/gist_id}","starred_url":"https://api.github.com/users/dit7ya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dit7ya/subscriptions","organizations_url":"https://api.github.com/users/dit7ya/orgs","repos_url":"https://api.github.com/users/dit7ya/repos","events_url":"https://api.github.com/users/dit7ya/events{/privacy}","received_events_url":"https://api.github.com/users/dit7ya/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T15:50:36Z","updated_at":"2022-04-08T15:50:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nFirezone is a self-managed WireGuard®-based VPN server and Linux firewall designed for simplicity and security.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.firez.one/\r\n* source URL: https://github.com/firezone/firezone\r\n* license: Apache-2.0\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167896/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167893","id":1197467843,"node_id":"I_kwDOAEVQ_M5HX-jD","number":167893,"title":"Unhelpful error message: error: attribute 'name' missing","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T15:26:47Z","updated_at":"2022-04-08T19:37:47Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`nixos-rebuild switch --show-trace` shows this error message and i have no idea what the issue is and how to fix it.\r\n\r\n```\r\nerror: attribute 'name' missing\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/servers/x11/xorg/overrides.nix:628:69:\r\n\r\n 627| meta.platforms = lib.platforms.unix;\r\n 628| } else throw \"unsupported xorg abiCompat ${abiCompat} for ${attrs_passed.name}\";\r\n | ^\r\n 629|\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/servers/x11/xorg/overrides.nix:594:59:\r\n\r\n 593|\r\n 594| xorgserver = with self; super.xorgserver.overrideAttrs (attrs_passed:\r\n | ^\r\n 595| # exchange attrs if abiCompat is set\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:381:56:\r\n\r\n 380| ({\r\n 381| overrideAttrs = f: stdenv.mkDerivation (attrs // (f attrs));\r\n | ^\r\n 382|\r\n\r\n … while evaluating 'overrideAttrs'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:381:22:\r\n\r\n 380| ({\r\n 381| overrideAttrs = f: stdenv.mkDerivation (attrs // (f attrs));\r\n | ^\r\n 382|\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:86:32:\r\n\r\n 85| ${if result ? overrideAttrs then \"overrideAttrs\" else null} = fdrv:\r\n 86| overrideResult (x: x.overrideAttrs fdrv);\r\n | ^\r\n 87| }\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:86:29:\r\n\r\n 85| ${if result ? overrideAttrs then \"overrideAttrs\" else null} = fdrv:\r\n 86| overrideResult (x: x.overrideAttrs fdrv);\r\n | ^\r\n 87| }\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:79:60:\r\n\r\n 78| # Change the result of the function call by applying g to it\r\n 79| overrideResult = g: makeOverridable (copyArgs (args: g (f args))) origArgs;\r\n | ^\r\n 80| in\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:79:54:\r\n\r\n 78| # Change the result of the function call by applying g to it\r\n 79| overrideResult = g: makeOverridable (copyArgs (args: g (f args))) origArgs;\r\n | ^\r\n 80| in\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:69:16:\r\n\r\n 68| let\r\n 69| result = f origArgs;\r\n | ^\r\n 70|\r\n\r\n … while evaluating 'makeOverridable'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:67:24:\r\n\r\n 66| */\r\n 67| makeOverridable = f: origArgs:\r\n | ^\r\n 68| let\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:79:27:\r\n\r\n 78| # Change the result of the function call by applying g to it\r\n 79| overrideResult = g: makeOverridable (copyArgs (args: g (f args))) origArgs;\r\n | ^\r\n 80| in\r\n\r\n … while evaluating 'overrideResult'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:79:24:\r\n\r\n 78| # Change the result of the function call by applying g to it\r\n 79| overrideResult = g: makeOverridable (copyArgs (args: g (f args))) origArgs;\r\n | ^\r\n 80| in\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:86:13:\r\n\r\n 85| ${if result ? overrideAttrs then \"overrideAttrs\" else null} = fdrv:\r\n 86| overrideResult (x: x.overrideAttrs fdrv);\r\n | ^\r\n 87| }\r\n\r\n … while evaluating 'overrideAttrs'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/customisation.nix:85:73:\r\n\r\n 84| overrideDerivation = fdrv: overrideResult (x: overrideDerivation x fdrv);\r\n 85| ${if result ? overrideAttrs then \"overrideAttrs\" else null} = fdrv:\r\n | ^\r\n 86| overrideResult (x: x.overrideAttrs fdrv);\r\n\r\n … from call site\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/servers/x11/xorg/overrides.nix:594:27:\r\n\r\n 593|\r\n 594| xorgserver = with self; super.xorgserver.overrideAttrs (attrs_passed:\r\n | ^\r\n 595| # exchange attrs if abiCompat is set\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:156:13:\r\n\r\n 155| (map (drv: drv.__spliced.hostHost or drv) depsHostHost)\r\n 156| (map (drv: drv.crossDrv or drv) buildInputs)\r\n | ^\r\n 157| ]\r\n\r\n … from call site\r\n\r\n … while evaluating 'getOutput'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/lib/attrsets.nix:489:23:\r\n\r\n 488| */\r\n 489| getOutput = output: pkg:\r\n | ^\r\n 490| if ! pkg ? outputSpecified || ! pkg.outputSpecified\r\n\r\n … from call site\r\n\r\n … while evaluating the attribute 'buildInputs' of the derivation 'xf86-input-evdev-2.10.6'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\n\r\n 204| // (lib.optionalAttrs (attrs ? name || (attrs ? pname && attrs ? version)) {\r\n 205| name =\r\n | ^\r\n 206| let\r\n\r\n … while evaluating the attribute 'value'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:452:44:\r\n\r\n 451| defnsByName' = byName \"config\" (module: value:\r\n 452| [{ inherit (module) file; inherit value; }]\r\n | ^\r\n 453| ) configs;\r\n\r\n … while evaluating 'dischargeProperties'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:669:25:\r\n\r\n 668| */\r\n 669| dischargeProperties = def:\r\n | ^\r\n 670| if def._type or \"\" == \"merge\" then\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:598:137:\r\n\r\n 597| defs' = concatMap (m:\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n | ^\r\n 599| ) defs;\r\n\r\n … while evaluating definitions from `/nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/services/x11/xserver.nix':\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:597:28:\r\n\r\n 596| # Process mkMerge and mkIf properties.\r\n 597| defs' = concatMap (m:\r\n | ^\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:597:17:\r\n\r\n 596| # Process mkMerge and mkIf properties.\r\n 597| defs' = concatMap (m:\r\n | ^\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n\r\n … while evaluating the attribute 'values'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:710:7:\r\n\r\n 709| in {\r\n 710| values = concatMap (def: if getPrio def == highestPrio then [(strip def)] else []) defs;\r\n | ^\r\n 711| inherit highestPrio;\r\n\r\n … while evaluating the attribute 'values'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:611:9:\r\n\r\n 610| in {\r\n 611| values = defs''';\r\n | ^\r\n 612| inherit (defs'') highestPrio;\r\n\r\n … while evaluating the attribute 'mergedValue'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:617:5:\r\n\r\n 616| # Type-check the remaining definitions, and merge them. Or throw if no definitions.\r\n 617| mergedValue =\r\n | ^\r\n 618| if isDefined then\r\n\r\n … while evaluating the option `environment.etc./X11/xorg.conf.d/10-evdev.conf.source':\r\n\r\n … while evaluating the attribute 'value'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:585:9:\r\n\r\n 584| in warnDeprecation opt //\r\n 585| { value = builtins.addErrorContext \"while evaluating the option `${showOption loc}':\" value;\r\n | ^\r\n 586| inherit (res.defsFinal') highestPrio;\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:171:72:\r\n\r\n 170| # For definitions that have an associated option\r\n 171| declaredConfig = mapAttrsRecursiveCond (v: ! isOption v) (_: v: v.value) options;\r\n | ^\r\n 172|\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/attrsets.nix:304:20:\r\n\r\n 303| then recurse (path ++ [name]) value\r\n 304| else f (path ++ [name]) value;\r\n | ^\r\n 305| in mapAttrs g set;\r\n\r\n … while evaluating 'g'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/attrsets.nix:301:19:\r\n\r\n 300| g =\r\n 301| name: value:\r\n | ^\r\n 302| if isAttrs value && cond value\r\n\r\n … from call site\r\n\r\n … while evaluating 'escapeShellArg'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/strings.nix:318:20:\r\n\r\n 317| */\r\n 318| escapeShellArg = arg: \"'${replaceStrings [\"'\"] [\"'\\\\''\"] (toString arg)}'\";\r\n | ^\r\n 319|\r\n\r\n … from call site\r\n\r\n … while evaluating 'concatMapStringsSep'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/strings.nix:110:5:\r\n\r\n 109| # List of input strings\r\n 110| list: concatStringsSep sep (map f list);\r\n | ^\r\n 111|\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/etc/etc.nix:54:43:\r\n\r\n 53| mkdir -p \"$out/etc\"\r\n 54| ${concatMapStringsSep \"\\n\" (etcEntry: escapeShellArgs [\r\n | ^\r\n 55| \"makeEtcEntry\"\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/etc/etc.nix:54:33:\r\n\r\n 53| mkdir -p \"$out/etc\"\r\n 54| ${concatMapStringsSep \"\\n\" (etcEntry: escapeShellArgs [\r\n | ^\r\n 55| \"makeEtcEntry\"\r\n\r\n … from call site\r\n\r\n … while evaluating 'concatMapStringsSep'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/strings.nix:110:5:\r\n\r\n 109| # List of input strings\r\n 110| list: concatStringsSep sep (map f list);\r\n | ^\r\n 111|\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/etc/etc.nix:54:7:\r\n\r\n 53| mkdir -p \"$out/etc\"\r\n 54| ${concatMapStringsSep \"\\n\" (etcEntry: escapeShellArgs [\r\n | ^\r\n 55| \"makeEtcEntry\"\r\n\r\n … while evaluating the attribute 'buildCommand' of the derivation 'etc'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\n\r\n 204| // (lib.optionalAttrs (attrs ? name || (attrs ? pname && attrs ? version)) {\r\n 205| name =\r\n | ^\r\n 206| let\r\n\r\n … while evaluating the attribute 'value'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:452:44:\r\n\r\n 451| defnsByName' = byName \"config\" (module: value:\r\n 452| [{ inherit (module) file; inherit value; }]\r\n | ^\r\n 453| ) configs;\r\n\r\n … while evaluating 'dischargeProperties'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:669:25:\r\n\r\n 668| */\r\n 669| dischargeProperties = def:\r\n | ^\r\n 670| if def._type or \"\" == \"merge\" then\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:598:137:\r\n\r\n 597| defs' = concatMap (m:\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n | ^\r\n 599| ) defs;\r\n\r\n … while evaluating definitions from `/nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/etc/etc.nix':\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:597:28:\r\n\r\n 596| # Process mkMerge and mkIf properties.\r\n 597| defs' = concatMap (m:\r\n | ^\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:597:17:\r\n\r\n 596| # Process mkMerge and mkIf properties.\r\n 597| defs' = concatMap (m:\r\n | ^\r\n 598| map (value: { inherit (m) file; inherit value; }) (builtins.addErrorContext \"while evaluating definitions from `${m.file}':\" (dischargeProperties m.value))\r\n\r\n … while evaluating the attribute 'values'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:710:7:\r\n\r\n 709| in {\r\n 710| values = concatMap (def: if getPrio def == highestPrio then [(strip def)] else []) defs;\r\n | ^\r\n 711| inherit highestPrio;\r\n\r\n … while evaluating the attribute 'values'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:611:9:\r\n\r\n 610| in {\r\n 611| values = defs''';\r\n | ^\r\n 612| inherit (defs'') highestPrio;\r\n\r\n … while evaluating the attribute 'mergedValue'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:617:5:\r\n\r\n 616| # Type-check the remaining definitions, and merge them. Or throw if no definitions.\r\n 617| mergedValue =\r\n | ^\r\n 618| if isDefined then\r\n\r\n … while evaluating the option `system.activationScripts.etc.text':\r\n\r\n … while evaluating the attribute 'value'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:585:9:\r\n\r\n 584| in warnDeprecation opt //\r\n 585| { value = builtins.addErrorContext \"while evaluating the option `${showOption loc}':\" value;\r\n | ^\r\n 586| inherit (res.defsFinal') highestPrio;\r\n\r\n … while evaluating anonymous lambda\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/modules.nix:171:72:\r\n\r\n 170| # For definitions that have an associated option\r\n 171| declaredConfig = mapAttrsRecursiveCond (v: ! isOption v) (_: v: v.value) options;\r\n | ^\r\n 172|\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/attrsets.nix:304:20:\r\n\r\n 303| then recurse (path ++ [name]) value\r\n 304| else f (path ++ [name]) value;\r\n | ^\r\n 305| in mapAttrs g set;\r\n\r\n … while evaluating 'g'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/attrsets.nix:301:19:\r\n\r\n 300| g =\r\n 301| name: value:\r\n | ^\r\n 302| if isAttrs value && cond value\r\n\r\n … from call site\r\n\r\n … while evaluating the attribute 'text'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/activation/activation-script.nix:9:5:\r\n\r\n 8| addAttributeName = mapAttrs (a: v: v // {\r\n 9| text = ''\r\n | ^\r\n 10| #### Activation script snippet ${a}:\r\n\r\n … while evaluating 'id'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/trivial.nix:14:5:\r\n\r\n 13| # The value to return\r\n 14| x: x;\r\n | ^\r\n 15|\r\n\r\n … from call site\r\n\r\n … while evaluating 'textClosureMap'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/lib/strings-with-deps.nix:75:35:\r\n\r\n 74|\r\n 75| textClosureMap = f: predefined: names:\r\n | ^\r\n 76| concatStringsSep \"\\n\" (map f (textClosureList predefined names));\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/activation/activation-script.nix:49:9:\r\n\r\n 48|\r\n 49| ${textClosureMap id (withDrySnippets) (attrNames withDrySnippets)}\r\n | ^\r\n 50|\r\n\r\n … while evaluating 'systemActivationScript'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/activation/activation-script.nix:20:33:\r\n\r\n 19|\r\n 20| systemActivationScript = set: onlyDry: let\r\n | ^\r\n 21| set' = mapAttrs (_: v: if isString v then (noDepEntry v) // { supportsDryActivation = false; } else v) set;\r\n\r\n … from call site\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/activation/activation-script.nix:136:18:\r\n\r\n 135| apply = set: set // {\r\n 136| script = systemActivationScript set false;\r\n | ^\r\n 137| };\r\n\r\n … while evaluating the attribute 'system.activationScripts.script'\r\n\r\n at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/system/activation/activation-script.nix:136:9:\r\n\r\n 135| apply = set: set // {\r\n 136| script = systemActivationScript set false;\r\n | ^\r\n 137| };\r\n\r\n … while evaluating the attribute 'activationScript' of the derivation 'nixos-system-gaming-21.11.336824.ccb90fb9e11'\r\n\r\n at /nix/store/rifmrf8ma50p8hjz60xysvsw0cpg9nf3-nixos-21.11.336824.ccb90fb9e11/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\n\r\n 204| // (lib.optionalAttrs (attrs ? name || (attrs ? pname && attrs ? version)) {\r\n 205| name =\r\n | ^\r\n 206| let\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n```\r\n # use proprietary gpu driver\r\n services.xserver.videoDrivers = [ \"amdgpu-pro\" ];\r\n boot.initrd.kernelModules = [ \"amdgpu-pro\" ];\r\n```\r\n\r\nThe issue is that `amdgpu-pro` is still broken on stable (https://github.com/NixOS/nixpkgs/issues/78031).\r\n\r\n### Expected behavior\r\nHelpful error messages.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.336824.ccb90fb9e11, nixos-hardware, nixos-unstable-22.05pre366144.bc4b9eef3ce\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167893/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167872","id":1197319036,"node_id":"I_kwDOAEVQ_M5HXaN8","number":167872,"title":"Packaging request: fcitx5-skk","user":{"login":"zer0-star","id":32029533,"node_id":"MDQ6VXNlcjMyMDI5NTMz","avatar_url":"https://avatars.githubusercontent.com/u/32029533?v=4","gravatar_id":"","url":"https://api.github.com/users/zer0-star","html_url":"https://github.com/zer0-star","followers_url":"https://api.github.com/users/zer0-star/followers","following_url":"https://api.github.com/users/zer0-star/following{/other_user}","gists_url":"https://api.github.com/users/zer0-star/gists{/gist_id}","starred_url":"https://api.github.com/users/zer0-star/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zer0-star/subscriptions","organizations_url":"https://api.github.com/users/zer0-star/orgs","repos_url":"https://api.github.com/users/zer0-star/repos","events_url":"https://api.github.com/users/zer0-star/events{/privacy}","received_events_url":"https://api.github.com/users/zer0-star/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-08T13:27:17Z","updated_at":"2022-04-08T15:16:34Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nfcitx5-skk is an input method engine for Fcitx5, which uses libskk as its backend.\r\n\r\nIt seems some of the fcitx5 engines (including fcitx5-skk) are missing. Probably the other engines also need to be added.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/fcitx/fcitx5-skk\r\n* source URL: https://github.com/fcitx/fcitx5-skk\r\n* license: gpl3+\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167872/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167869","id":1197294140,"node_id":"I_kwDOAEVQ_M5HXUI8","number":167869,"title":"openmoji has started taking forever to build.","user":{"login":"kevincox","id":494012,"node_id":"MDQ6VXNlcjQ5NDAxMg==","avatar_url":"https://avatars.githubusercontent.com/u/494012?v=4","gravatar_id":"","url":"https://api.github.com/users/kevincox","html_url":"https://github.com/kevincox","followers_url":"https://api.github.com/users/kevincox/followers","following_url":"https://api.github.com/users/kevincox/following{/other_user}","gists_url":"https://api.github.com/users/kevincox/gists{/gist_id}","starred_url":"https://api.github.com/users/kevincox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kevincox/subscriptions","organizations_url":"https://api.github.com/users/kevincox/orgs","repos_url":"https://api.github.com/users/kevincox/repos","events_url":"https://api.github.com/users/kevincox/events{/privacy}","received_events_url":"https://api.github.com/users/kevincox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-04-08T13:05:00Z","updated_at":"2022-04-14T19:49:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nopenmoji-color and openmoji-black now both take >12h to build. They are timing out on hydra https://hydra.nixos.org/job/nixos/trunk-combined/nixpkgs.openmoji-color.x86_64-linux.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-build -A openmoji-color\r\n\r\n### Notify maintainers\r\n@fgaz","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167869/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167865","id":1197274018,"node_id":"I_kwDOAEVQ_M5HXPOi","number":167865,"title":"depreciate python3.guestfs in favour of libguestfs python bindings (which are currently not built)","user":{"login":"armijnhemel","id":10587952,"node_id":"MDQ6VXNlcjEwNTg3OTUy","avatar_url":"https://avatars.githubusercontent.com/u/10587952?v=4","gravatar_id":"","url":"https://api.github.com/users/armijnhemel","html_url":"https://github.com/armijnhemel","followers_url":"https://api.github.com/users/armijnhemel/followers","following_url":"https://api.github.com/users/armijnhemel/following{/other_user}","gists_url":"https://api.github.com/users/armijnhemel/gists{/gist_id}","starred_url":"https://api.github.com/users/armijnhemel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armijnhemel/subscriptions","organizations_url":"https://api.github.com/users/armijnhemel/orgs","repos_url":"https://api.github.com/users/armijnhemel/repos","events_url":"https://api.github.com/users/armijnhemel/events{/privacy}","received_events_url":"https://api.github.com/users/armijnhemel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T12:44:51Z","updated_at":"2022-04-08T12:44:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n(note: I have added the bug report here, as it didn't seem to fit any of the other categories. Please move it to the right categery if that is a better fit).\r\n\r\nThe current package version of the `guestfs` Python package is 1.40.2 (although nixpkgs ships 1.40.1) and it doesn't seem to be actively updated anymore. Other distributions, such as Fedora, seem to instead use the Python bindings shipped in the default `libguestfs` source. These bindings are currently not built in nixpkgs.\r\n\r\nThis would possibly affect `diffoscope` which is (as far as I can see) the only package in nixpkgs that is currently using the Python bindings.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. none\r\n\r\n### Expected behavior\r\n\r\nNone\r\n\r\n### Screenshots\r\n\r\nnone\r\n\r\n### Additional context\r\n\r\nNone\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@grahamc @offlinehacker \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167865/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167864","id":1197258602,"node_id":"I_kwDOAEVQ_M5HXLdq","number":167864,"title":"radiotray-ng not working on nixos-unstable","user":{"login":"boogewooge","id":56923667,"node_id":"MDQ6VXNlcjU2OTIzNjY3","avatar_url":"https://avatars.githubusercontent.com/u/56923667?v=4","gravatar_id":"","url":"https://api.github.com/users/boogewooge","html_url":"https://github.com/boogewooge","followers_url":"https://api.github.com/users/boogewooge/followers","following_url":"https://api.github.com/users/boogewooge/following{/other_user}","gists_url":"https://api.github.com/users/boogewooge/gists{/gist_id}","starred_url":"https://api.github.com/users/boogewooge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/boogewooge/subscriptions","organizations_url":"https://api.github.com/users/boogewooge/orgs","repos_url":"https://api.github.com/users/boogewooge/repos","events_url":"https://api.github.com/users/boogewooge/events{/privacy}","received_events_url":"https://api.github.com/users/boogewooge/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T12:28:21Z","updated_at":"2022-04-08T12:28:21Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`radiotray-ng` installs fine, but doesn't work anymore on nixos-unstable. It shows greyed out in the tray. Menus work, but playing a station fails.\r\n\r\nTested on basic gnome and i3 setups.\r\n\r\nSee the log:\r\n```\r\n[2022-04-08 14:20:46.344050] [0x00007f1b80dc2fc0] [info ] (main.cpp:262) - radiotray-ng (v0.2.8-unknown) starting up\r\n[2022-04-08 14:20:46.344121] [0x00007f1b80dc2fc0] [info ] (main.cpp:264) - radiotray-ng/0.2.8 (Linux x86_64; n/a/n/a (n/a))\r\n[2022-04-08 14:20:46.344128] [0x00007f1b80dc2fc0] [info ] (main.cpp:91) - debug logging enabled\r\n[2022-04-08 14:20:46.344139] [0x00007f1b80dc2fc0] [info ] (player.cpp:26) - starting gstreamer\r\n[2022-04-08 14:20:46.358049] [0x00007f1b80dc2fc0] [error] (player.cpp:427) - could not create souphttpsrc element\r\n[2022-04-08 14:20:46.359375] [0x00007f1b80dc2fc0] [debug] (bookmarks.cpp:31) - loading: /home/boogie/.config/radiotray-ng/bookmarks.json\r\n[2022-04-08 14:20:46.359711] [0x00007f1b80dc2fc0] [debug] (file_monitor.hpp:108) - monitoring: /home/boogie/.config/radiotray-ng/bookmarks.json\r\n[2022-04-08 14:20:46.360763] [0x00007f1b80dc2fc0] [debug] (media_keys.cpp:198) - starting media keys\r\n[2022-04-08 14:21:23.264277] [0x00007f1b80dc2fc0] [info ] (radiotray_ng.cpp:499) - downloading: SomaFM, Groove Salad, https://somafm.com/groovesalad256.pls\r\n[2022-04-08 14:21:23.264331] [0x00007f1b80dc2fc0] [debug] (notification.cpp:63) - notify: Connecting, Radiotray-NG, radiotray-ng-notification\r\n[2022-04-08 14:21:23.273186] [0x00007f1b80dc2fc0] [debug] (playlist_downloader.cpp:140) - http-timeout=15\r\n[2022-04-08 14:21:25.957687] [0x00007f1b80dc2fc0] [debug] (playlist_downloader.cpp:174) - [REDACTED - useless playlist info]\r\n[2022-04-08 14:21:25.958568] [0x00007f1b80dc2fc0] [info ] (playlist_downloader.cpp:96) - decoder: PLS, audio/x-scpls\r\n[2022-04-08 14:21:25.958865] [0x00007f1b80dc2fc0] [error] (player.cpp:88) - gstreamer not ready\r\n[2022-04-08 14:21:25.958873] [0x00007f1b80dc2fc0] [error] (radiotray_ng.cpp:533) - failed to download playlist: https://somafm.com/groovesalad256.pls\r\n[2022-04-08 14:21:25.958994] [0x00007f1b80dc2fc0] [debug] (notification.cpp:63) - notify: Error, Failed to download playlist, radiotray-ng-notification\r\n```\r\n\r\nInternet connection is working completely fine and so is the targeted radio stream, so the failed downloads are not due to any external issues.\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@dtzWill\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0-zen1, NixOS, 22.05 (Quokka), 22.05pre367572.b6966d911da`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(boogie): `\"unstable\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167864/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167859","id":1197205551,"node_id":"I_kwDOAEVQ_M5HW-gv","number":167859,"title":"aeson 1.5 tracking issue","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":131612005,"node_id":"MDU6TGFiZWwxMzE2MTIwMDU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20sprintable","name":"3.skill: sprintable","color":"f7c6c7","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-08T11:32:25Z","updated_at":"2022-04-26T07:45:52Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"We are still building some packages with `aeson` 1.5 which is a slight annoyance, so let's make a list and migrate them to 2.0 one by one!\r\n\r\nPackages still using `aeson` 1.5:\r\n\r\n* [x] `niv`\r\n* [ ] `nix-linter`\r\n* [ ] `vaultenv`\r\n* [ ] `stack`\r\n* [ ] `descriptive`\r\n* [ ] `mattermost-api`, `matterhorn`\r\n* [ ] `elmPackages`\r\n* [ ] `spago`, `bower-json`\r\n\r\nPackages that are failing because they don't support `aeson` 2.0 (but also haven't been overridden to use 1.5):\r\n\r\n* [x] `ghcjs` #166553\r\n* [ ] `jl`\r\n* [ ] `hasura-graphql-engine` (because of `haskellPackages.graphql-parser`)\r\n\r\ncc @NixOS/haskell ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167859/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167847","id":1197143741,"node_id":"I_kwDOAEVQ_M5HWva9","number":167847,"title":"Packaging request: MikTeX","user":{"login":"linsui","id":36977733,"node_id":"MDQ6VXNlcjM2OTc3NzMz","avatar_url":"https://avatars.githubusercontent.com/u/36977733?v=4","gravatar_id":"","url":"https://api.github.com/users/linsui","html_url":"https://github.com/linsui","followers_url":"https://api.github.com/users/linsui/followers","following_url":"https://api.github.com/users/linsui/following{/other_user}","gists_url":"https://api.github.com/users/linsui/gists{/gist_id}","starred_url":"https://api.github.com/users/linsui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/linsui/subscriptions","organizations_url":"https://api.github.com/users/linsui/orgs","repos_url":"https://api.github.com/users/linsui/repos","events_url":"https://api.github.com/users/linsui/events{/privacy}","received_events_url":"https://api.github.com/users/linsui/received_events","type":"User","site_admin":false},"labels":[{"id":1236941869,"node_id":"MDU6TGFiZWwxMjM2OTQxODY5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20TeX","name":"6.topic: TeX","color":"fef2c0","default":false,"description":"Issues regarding texlive and TeX in general"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-08T10:29:30Z","updated_at":"2022-04-08T19:36:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nMiKTeX is a modern C/C++ implementation of TeX & Friends for Windows, macOS and Linux.\r\n\r\nI partly build it. But the binaries doesn't work for me.\r\n\r\n```nix\r\n{ lib\r\n, stdenv\r\n, fetchFromGitHub\r\n, wrapQtAppsHook\r\n, bison\r\n, cmake\r\n, flex\r\n, fop\r\n, git\r\n, gnused\r\n, libxslt\r\n, pkg-config\r\n, qttools\r\n, apr\r\n, aprutil\r\n, boost\r\n, bzip2\r\n, cairo\r\n, expat\r\n, fontconfig\r\n, freetype\r\n, fribidi\r\n, gd\r\n, gmp\r\n, graphite2\r\n, harfbuzzFull\r\n, hunspell\r\n, icu\r\n, libjpeg\r\n, log4cxx\r\n, lzma\r\n, mpfr\r\n, libmspack\r\n, libressl\r\n, pixman\r\n, libpng\r\n, poppler\r\n, popt\r\n, potrace\r\n, qtdeclarative\r\n, qtscript\r\n, uriparser\r\n, zziplib\r\n, libsForQt5\r\n}:\r\n\r\nstdenv.mkDerivation rec {\r\n pname = \"miktex\";\r\n version = \"22.3\";\r\n\r\n src = fetchFromGitHub {\r\n owner = pname;\r\n repo = pname;\r\n rev = version;\r\n sha256 = \"sha256-IvXlFEM7fp0EYSmQmt1KKAAMQM4bTZL0vPfdFpXJKhQ=\";\r\n };\r\n\r\n postPatch = ''\r\n substituteInPlace Programs/TeXAndFriends/omega/otps/source/outocp.c \\\r\n --replace 'fprintf(stderr, s);' 'fprintf(stderr, \"%s\", s);'\r\n '';\r\n\r\n nativeBuildInputs = [\r\n wrapQtAppsHook\r\n bison\r\n cmake\r\n flex\r\n fop\r\n git\r\n gnused\r\n libxslt\r\n pkg-config\r\n qttools\r\n ];\r\n\r\n buildInputs = [\r\n apr\r\n aprutil\r\n boost\r\n bzip2\r\n cairo\r\n expat\r\n fontconfig\r\n freetype\r\n fribidi\r\n gd\r\n gmp\r\n graphite2\r\n harfbuzzFull\r\n hunspell\r\n icu\r\n libjpeg\r\n log4cxx\r\n lzma\r\n mpfr\r\n libmspack\r\n libressl\r\n pixman\r\n libpng\r\n poppler\r\n popt\r\n potrace\r\n qtdeclarative\r\n qtscript\r\n uriparser\r\n zziplib\r\n libsForQt5.poppler\r\n ];\r\n\r\n cmakeFlags = [\r\n \"-DWITH_BOOTSTRAPPING=FALSE\"\r\n \"-DUSE_SYSTEM_POPPLER=TRUE\"\r\n \"-DUSE_SYSTEM_POPPLER_QT5=TRUE\"\r\n \"-DWITH_MAN_PAGES=FALSE\"\r\n ];\r\n\r\n preBuild = ''\r\n export HOME=$TMPDIR\r\n export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:$(pwd)/sandbox/miktex/bin/linux-x86_64\r\n '';\r\n\r\n meta = with lib; {\r\n description = \"A modern TeX distribution\";\r\n homepage = \"https://miktex.org\";\r\n platforms = platforms.unix;\r\n license = licenses.bsd3;\r\n };\r\n}\r\n```\r\n\r\nI had to disable the man pages however it builds fine with pure nix-shell.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167847/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167806","id":1196758068,"node_id":"I_kwDOAEVQ_M5HVRQ0","number":167806,"title":"plasma-workspaces won't evaluate: shows up as missing","user":{"login":"td5038","id":93895804,"node_id":"U_kgDOBZi8fA","avatar_url":"https://avatars.githubusercontent.com/u/93895804?v=4","gravatar_id":"","url":"https://api.github.com/users/td5038","html_url":"https://github.com/td5038","followers_url":"https://api.github.com/users/td5038/followers","following_url":"https://api.github.com/users/td5038/following{/other_user}","gists_url":"https://api.github.com/users/td5038/gists{/gist_id}","starred_url":"https://api.github.com/users/td5038/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/td5038/subscriptions","organizations_url":"https://api.github.com/users/td5038/orgs","repos_url":"https://api.github.com/users/td5038/repos","events_url":"https://api.github.com/users/td5038/events{/privacy}","received_events_url":"https://api.github.com/users/td5038/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-08T02:33:56Z","updated_at":"2022-04-08T11:00:55Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nplasma-workspaces is not getting evaluated during a rebuild of NixOS.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use a complete KDE Plasma\r\n2. Implement the ksysguard alias workaround\r\n3. Wait, and watch nixos-rebuild fail\r\n\r\n### Expected behavior\r\nI expected to have a new NixOS configuration\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@ttuegel @nyanloutre \r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.108, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336824.ccb90fb9e11\"`\r\n - channels(zjcadmin): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167806/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167765","id":1196488204,"node_id":"I_kwDOAEVQ_M5HUPYM","number":167765,"title":"anki-bin: blank main window","user":{"login":"dnaq","id":1299717,"node_id":"MDQ6VXNlcjEyOTk3MTc=","avatar_url":"https://avatars.githubusercontent.com/u/1299717?v=4","gravatar_id":"","url":"https://api.github.com/users/dnaq","html_url":"https://github.com/dnaq","followers_url":"https://api.github.com/users/dnaq/followers","following_url":"https://api.github.com/users/dnaq/following{/other_user}","gists_url":"https://api.github.com/users/dnaq/gists{/gist_id}","starred_url":"https://api.github.com/users/dnaq/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dnaq/subscriptions","organizations_url":"https://api.github.com/users/dnaq/orgs","repos_url":"https://api.github.com/users/dnaq/repos","events_url":"https://api.github.com/users/dnaq/events{/privacy}","received_events_url":"https://api.github.com/users/dnaq/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-07T19:37:32Z","updated_at":"2022-04-11T20:43:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nAfter upgrading to the current version of nixpgs (nixos-unstable) anki starts up to a blank main window. According to the documentation (https://docs.ankiweb.net/platform/linux/blank-window.html) that is because of the system glibc having changed to a version not compatible with anki. Their suggested fix is that users move to using the beta package instead.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-shell -p `anki-bin`\r\n2. anki\r\n\r\n### Expected behavior\r\nAnki working as usual\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@Atemu \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05.20220406.b6966d9`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - channels(root): `\"\"`\r\n - channels(user): `\"\"`\r\n - nixpkgs: `/nix/store/gyzqxklnmyzl773qpqylnfvhg6gimyad-source`\r\noutput here\r\n```\r\n\r\nExcerpt from flake.lock:\r\n\r\n```nix\r\n\"nixpkgs\": {\r\n \"locked\": {\r\n \"lastModified\": 1646497237,\r\n \"narHash\": \"sha256-Ccpot1h/rV8MgcngDp5OrdmLTMaUTbStZTR5/sI7zW0=\",\r\n \"owner\": \"nixos\",\r\n \"repo\": \"nixpkgs\",\r\n \"rev\": \"062a0c5437b68f950b081bbfc8a699d57a4ee026\",\r\n \"type\": \"github\"\r\n },\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765/reactions","total_count":5,"+1":5,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167765/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167735","id":1196307647,"node_id":"I_kwDOAEVQ_M5HTjS_","number":167735,"title":"flutter 2.10.1 : non functioning `flutter devices`","user":{"login":"msackman","id":389910,"node_id":"MDQ6VXNlcjM4OTkxMA==","avatar_url":"https://avatars.githubusercontent.com/u/389910?v=4","gravatar_id":"","url":"https://api.github.com/users/msackman","html_url":"https://github.com/msackman","followers_url":"https://api.github.com/users/msackman/followers","following_url":"https://api.github.com/users/msackman/following{/other_user}","gists_url":"https://api.github.com/users/msackman/gists{/gist_id}","starred_url":"https://api.github.com/users/msackman/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/msackman/subscriptions","organizations_url":"https://api.github.com/users/msackman/orgs","repos_url":"https://api.github.com/users/msackman/repos","events_url":"https://api.github.com/users/msackman/events{/privacy}","received_events_url":"https://api.github.com/users/msackman/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-07T16:41:13Z","updated_at":"2022-04-14T22:14:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`flutter devices` no longer works.\r\n\r\n### Steps To Reproduce\r\n```console\r\n# flutter -v devices\r\n[ +69 ms] executing: uname -m\r\n[ +35 ms] Exit code 0 from: uname -m\r\n[ ] x86_64\r\n[ +6 ms] executing: [/nix/store/w34kvrzcn95zsvx2dii4b321rnrc60lh-flutter-2.10.1-unwrapped/] git -c log.showSignature=false log -n 1 --pretty=format:%H\r\n[ +6 ms] Exit code 0 from: git -c log.showSignature=false log -n 1 --pretty=format:%H\r\n[ ] db747aa1331bd95bc9b3874c842261ca2d302cd5\r\n[ ] executing: [/nix/store/w34kvrzcn95zsvx2dii4b321rnrc60lh-flutter-2.10.1-unwrapped/] git tag --points-at db747aa1331bd95bc9b3874c842261ca2d302cd5\r\n[ +21 ms] Exit code 0 from: git tag --points-at db747aa1331bd95bc9b3874c842261ca2d302cd5\r\n[ ] 2.10.1\r\n[ +13 ms] executing: [/nix/store/w34kvrzcn95zsvx2dii4b321rnrc60lh-flutter-2.10.1-unwrapped/] git rev-parse --abbrev-ref --symbolic @{u}\r\n[ +7 ms] Exit code 0 from: git rev-parse --abbrev-ref --symbolic @{u}\r\n[ ] origin/stable\r\n[ ] executing: [/nix/store/w34kvrzcn95zsvx2dii4b321rnrc60lh-flutter-2.10.1-unwrapped/] git ls-remote --get-url origin\r\n[ +6 ms] Exit code 0 from: git ls-remote --get-url origin\r\n[ ] https://github.com/flutter/flutter.git\r\n[ +83 ms] executing: [/nix/store/w34kvrzcn95zsvx2dii4b321rnrc60lh-flutter-2.10.1-unwrapped/] git rev-parse --abbrev-ref HEAD\r\n[ +8 ms] Exit code 0 from: git rev-parse --abbrev-ref HEAD\r\n[ ] stable\r\n[ +66 ms] Artifact Instance of 'AndroidGenSnapshotArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'AndroidInternalBuildArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IOSEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterWebSdk' is not required, skipping update.\r\n[ +4 ms] Artifact Instance of 'WindowsEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'WindowsUwpEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'MacOSEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'LinuxEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'LinuxFuchsiaSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'MacOSFuchsiaSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterRunnerSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterRunnerDebugSymbols' is not required, skipping update.\r\n[ +61 ms] Artifact Instance of 'MaterialFonts' is not required, skipping update.\r\n[ ] Artifact Instance of 'GradleWrapper' is not required, skipping update.\r\n[ ] Artifact Instance of 'AndroidGenSnapshotArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'AndroidInternalBuildArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IOSEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterWebSdk' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterSdk' is not required, skipping update.\r\n[ ] Artifact Instance of 'WindowsEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'WindowsUwpEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'MacOSEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'LinuxEngineArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'LinuxFuchsiaSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'MacOSFuchsiaSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterRunnerSDKArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FlutterRunnerDebugSymbols' is not required, skipping update.\r\n[ ] Artifact Instance of 'IosUsbArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IosUsbArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IosUsbArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IosUsbArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'IosUsbArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'FontSubsetArtifacts' is not required, skipping update.\r\n[ ] Artifact Instance of 'PubDependencies' is not required, skipping update.\r\n[ +41 ms] executing: /nix/store/yq4mcr5ykjdbgn1wnbhn2darrzhaba26-android-sdk-env/share/android-sdk/platform-tools/adb devices -l\r\n[ +53 ms] /nix/store/yq4mcr5ykjdbgn1wnbhn2darrzhaba26-android-sdk-env/share/android-sdk/platform-tools/adb: symbol lookup error: /usr/lib/libc.so.6: undefined symbol: __nptl_change_stack_perm, version GLIBC_PRIVATE\r\n[ +16 ms] \"flutter devices\" took 196ms.\r\n[ +6 ms] Unable to run \"adb\", check your Android SDK installation and ANDROID_SDK_ROOT environment variable: /nix/store/yq4mcr5ykjdbgn1wnbhn2darrzhaba26-android-sdk-env/share/android-sdk/platform-tools/adb\r\n[ +5 ms]\r\n#0 throwToolExit (package:flutter_tools/src/base/common.dart:10:3)\r\n#1 AndroidDevices.pollingGetDevices (package:flutter_tools/src/android/android_device_discovery.dart:75:7)\r\n<asynchronous suspension>\r\n#2 PollingDeviceDiscovery._populateDevices (package:flutter_tools/src/device.dart:413:54)\r\n<asynchronous suspension>\r\n#3 Future.wait.<anonymous closure> (dart:async/future.dart:473:21)\r\n<asynchronous suspension>\r\n#4 DeviceManager.refreshAllConnectedDevices (package:flutter_tools/src/device.dart:180:40)\r\n<asynchronous suspension>\r\n#5 DevicesCommand.runCommand (package:flutter_tools/src/commands/devices.dart:65:34)\r\n<asynchronous suspension>\r\n#6 FlutterCommand.run.<anonymous closure> (package:flutter_tools/src/runner/flutter_command.dart:1161:27)\r\n<asynchronous suspension>\r\n#7 AppContext.run.<anonymous closure> (package:flutter_tools/src/base/context.dart:150:19)\r\n<asynchronous suspension>\r\n#8 CommandRunner.runCommand (package:args/command_runner.dart:209:13)\r\n<asynchronous suspension>\r\n#9 FlutterCommandRunner.runCommand.<anonymous closure> (package:flutter_tools/src/runner/flutter_command_runner.dart:276:9)\r\n<asynchronous suspension>\r\n#10 AppContext.run.<anonymous closure> (package:flutter_tools/src/base/context.dart:150:19)\r\n<asynchronous suspension>\r\n#11 FlutterCommandRunner.runCommand (package:flutter_tools/src/runner/flutter_command_runner.dart:229:5)\r\n<asynchronous suspension>\r\n#12 run.<anonymous closure>.<anonymous closure> (package:flutter_tools/runner.dart:62:9)\r\n<asynchronous suspension>\r\n#13 AppContext.run.<anonymous closure> (package:flutter_tools/src/base/context.dart:150:19)\r\n<asynchronous suspension>\r\n#14 main (package:flutter_tools/executable.dart:94:3)\r\n<asynchronous suspension>\r\n\r\n\r\n[ +3 ms] Running shutdown hooks\r\n[ ] Shutdown hooks complete\r\n[ +1 ms] exiting with code 1\r\n```\r\n\r\n### Expected behavior\r\n```console\r\n# /nix/store/yq4mcr5ykjdbgn1wnbhn2darrzhaba26-android-sdk-env/share/android-sdk/platform-tools/adb devices -l\r\nList of devices attached\r\n\r\n```\r\n\r\n### Additional context\r\nIt looks like it's a packaging issue with flutter because when I run adb manually it works just fine, as shown above in \"Expected behaviour\"\r\n\r\n### Notify maintainers\r\n@ericdallo \r\n@babariviere \r\n@mkg20001 \r\n\r\n### Metadata\r\n```console\r\n# nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.16.18, NixOS, 21.11 (Porcupine)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.3.16`\r\n- channels(root): `\"home-manager-21.11, nixos-21.11.336824.ccb90fb9e11, nixos-unstable-22.05pre367572.b6966d911da\"`\r\n- channels(matthew): `\"android-nixpkgs\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167735/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167707","id":1196037609,"node_id":"I_kwDOAEVQ_M5HShXp","number":167707,"title":"Peazip","user":{"login":"CMCDragonkai","id":640797,"node_id":"MDQ6VXNlcjY0MDc5Nw==","avatar_url":"https://avatars.githubusercontent.com/u/640797?v=4","gravatar_id":"","url":"https://api.github.com/users/CMCDragonkai","html_url":"https://github.com/CMCDragonkai","followers_url":"https://api.github.com/users/CMCDragonkai/followers","following_url":"https://api.github.com/users/CMCDragonkai/following{/other_user}","gists_url":"https://api.github.com/users/CMCDragonkai/gists{/gist_id}","starred_url":"https://api.github.com/users/CMCDragonkai/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/CMCDragonkai/subscriptions","organizations_url":"https://api.github.com/users/CMCDragonkai/orgs","repos_url":"https://api.github.com/users/CMCDragonkai/repos","events_url":"https://api.github.com/users/CMCDragonkai/events{/privacy}","received_events_url":"https://api.github.com/users/CMCDragonkai/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-07T13:18:46Z","updated_at":"2022-04-23T16:53:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\nPeazip is a GUI archive manager for Linux, MacOS, Windows. It's open source. I think nixpkgs is missing a GUI archive manager.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://peazip.github.io/peazip-linux.html\r\n* source URL: https://github.com/peazip/PeaZip\r\n* license: lgplv3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167707/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167683","id":1195871350,"node_id":"I_kwDOAEVQ_M5HR4x2","number":167683,"title":"`xnu` not building on aarch64-darwin","user":{"login":"kubukoz","id":894884,"node_id":"MDQ6VXNlcjg5NDg4NA==","avatar_url":"https://avatars.githubusercontent.com/u/894884?v=4","gravatar_id":"","url":"https://api.github.com/users/kubukoz","html_url":"https://github.com/kubukoz","followers_url":"https://api.github.com/users/kubukoz/followers","following_url":"https://api.github.com/users/kubukoz/following{/other_user}","gists_url":"https://api.github.com/users/kubukoz/gists{/gist_id}","starred_url":"https://api.github.com/users/kubukoz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kubukoz/subscriptions","organizations_url":"https://api.github.com/users/kubukoz/orgs","repos_url":"https://api.github.com/users/kubukoz/repos","events_url":"https://api.github.com/users/kubukoz/events{/privacy}","received_events_url":"https://api.github.com/users/kubukoz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-07T10:52:58Z","updated_at":"2022-04-26T18:04:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe xnu package, which is a dependency of openconnect via network_cmds, doesn't build on aarch64-darwin (M1 macs).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Clone current master\r\n2. `nix-build -A xnu`\r\n3. See failure\r\n\r\n### Expected behavior\r\nBuild succeeds\r\n\r\n### Additional context\r\n\r\nThis might be related to #150880.\r\n\r\nFailing build: https://hydra.nixos.org/build/172392835\r\n\r\n```\r\nclang-11: error: cannot use 'cpp-output' output with multiple -arch options\r\nmig: fatal: \"<no name yet>\", line -1: no SubSystem declaration\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@NixOS/darwin-maintainers \r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n\r\n- system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 12.3`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(kubukoz): `\"nixpkgs\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167683/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167666","id":1195759162,"node_id":"I_kwDOAEVQ_M5HRdY6","number":167666,"title":"Error start nginx unit with use jemalloc memory allocator and glibc 2.34","user":{"login":"Izorkin","id":26877687,"node_id":"MDQ6VXNlcjI2ODc3Njg3","avatar_url":"https://avatars.githubusercontent.com/u/26877687?v=4","gravatar_id":"","url":"https://api.github.com/users/Izorkin","html_url":"https://github.com/Izorkin","followers_url":"https://api.github.com/users/Izorkin/followers","following_url":"https://api.github.com/users/Izorkin/following{/other_user}","gists_url":"https://api.github.com/users/Izorkin/gists{/gist_id}","starred_url":"https://api.github.com/users/Izorkin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Izorkin/subscriptions","organizations_url":"https://api.github.com/users/Izorkin/orgs","repos_url":"https://api.github.com/users/Izorkin/repos","events_url":"https://api.github.com/users/Izorkin/events{/privacy}","received_events_url":"https://api.github.com/users/Izorkin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-07T09:19:02Z","updated_at":"2022-04-07T09:19:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nError start nginx unit with use jemalloc memory allocator and glibc 2.34\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Apply patch:\r\n```diff\r\ndiff --git a/nixos/tests/web-servers/unit-php.nix b/nixos/tests/web-servers/unit-php.nix\r\nindex 5bef7fab3ef..db28b7ef86b 100644\r\n--- a/nixos/tests/web-servers/unit-php.nix\r\n+++ b/nixos/tests/web-servers/unit-php.nix\r\n@@ -7,6 +7,7 @@ in {\r\n meta.maintainers = with pkgs.lib.maintainers; [ izorkin ];\r\n\r\n nodes.machine = { config, lib, pkgs, ... }: {\r\n+ systemd.services.unit.environment = { LD_PRELOAD = \"${pkgs.jemalloc}/lib/libjemalloc.so\"; };\r\n services.unit = {\r\n enable = true;\r\n config = pkgs.lib.strings.toJSON {\r\n\r\n```\r\n2. Run `nix-build nixos/tests/web-servers/unit-php.nix`\r\n\r\nError:\r\n```\r\n{\r\n \"error\": \"Failed to apply new configuration.\"\r\n}\r\n```\r\nDebug log:\r\n```\r\n[debug] 71678#71678 \"php-74-info\" prototype setup\r\n[debug] 71678#71678 setproctitle: \"unit: \"php-74-info\" prototype\"\r\n[debug] 71678#71678 epoll 3 free\r\n[debug] 71678#71678 free(618738078000)\r\n[debug] 71678#71678 free(618738073000)\r\n[debug] 71678#71678 malloc(2048): 618738073000\r\n[debug] 71678#71678 malloc(384): 618738078000\r\n[debug] 71678#71678 epoll_create(): 3\r\n[debug] 71678#71678 signalfd(): 4\r\n[debug] 71678#71678 eventfd(): 5\r\n[debug] 71678#71678 malloc(232): 61873807B000\r\n[debug] 71678#71678 socket close(8)\r\n[debug] 71678#71678 pthread_mutex_lock(61873805C078) enter\r\n[debug] 71678#71678 process 71678 added\r\n[debug] 71678#71678 pthread_mutex_unlock(61873805C078) exit\r\n[debug] 71678#71678 epoll 3 set event: fd:10 op:1 ev:80002001\r\n[debug] 71678#71678 application language module: 7.4.28 \"/nix/store/84gi28nnmwrsgnf5yggzqc4cgw5x6shk-unit-1.26.1/modules/php74.unit.so\"\r\n[debug] 71678#71678 malloc(20): 6187380252C0\r\nfree(): invalid pointer\r\n[debug] 71125#71125 epoll_wait(3): 1\r\n[debug] 71125#71125 epoll: fd:4 ev:0001 d:61873803C6A8 rd:0 wr:0\r\n[debug] 71125#71125 timer expire minimum: 127507165:41107558\r\n[debug] 71125#71125 work queue: fast\r\n[debug] 71125#71125 signalfd handler\r\n[debug] 71125#71125 read signalfd(4): 128\r\n[debug] 71125#71125 signalfd(4) signo:17\r\n[debug] 71125#71125 sigchld handler signo:17 (SIGCHLD)\r\n[debug] 71125#71125 waitpid(): 71678\r\n[alert] 71125#71125 process 71678 exited on signal 6 (core dumped)\r\n```\r\n\r\n\r\n### Notify maintainers\r\ncc @Ma27 @jonringer\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167666/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167599","id":1195241930,"node_id":"I_kwDOAEVQ_M5HPfHK","number":167599,"title":"elmerfem 8.4: nglib-based imports do not work","user":{"login":"grindhold","id":2592640,"node_id":"MDQ6VXNlcjI1OTI2NDA=","avatar_url":"https://avatars.githubusercontent.com/u/2592640?v=4","gravatar_id":"","url":"https://api.github.com/users/grindhold","html_url":"https://github.com/grindhold","followers_url":"https://api.github.com/users/grindhold/followers","following_url":"https://api.github.com/users/grindhold/following{/other_user}","gists_url":"https://api.github.com/users/grindhold/gists{/gist_id}","starred_url":"https://api.github.com/users/grindhold/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/grindhold/subscriptions","organizations_url":"https://api.github.com/users/grindhold/orgs","repos_url":"https://api.github.com/users/grindhold/repos","events_url":"https://api.github.com/users/grindhold/events{/privacy}","received_events_url":"https://api.github.com/users/grindhold/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T22:20:11Z","updated_at":"2022-04-06T22:20:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nOpening STEP-files does not work in nixos' build of ElmerGUI 8.4\r\nApparently all import formats that are provided by the mesh generator `nglib`dont work. Combined with the error message \"no [...] mesh generator\" leads me to assume there is some build-flag or dependency missing.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n1. Open the executable `ElmerGUI`\r\n2. When the UI shows up after the splash screen, click the leftmost \"Open\" Button in the toolbar\r\n3. Navigate to and open `~/.nix-profile/share/ElmerGUI/samples/step/pump_carter_sup.stp` [This is a well-known-to-work file that's being referenced by official tutorials of the application] \r\n4. ElmerGUI will put out \"unable to (re)mesh: no input data or mesh generator [...]\" in the status bar.\r\n\r\n### Expected behavior\r\nThe content of the file should show up in the 3D-view of the applilcation\r\n\r\n### Notify maintainers\r\n@Wulfsta @markuskowa \r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167599/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167528","id":1194569046,"node_id":"I_kwDOAEVQ_M5HM61W","number":167528,"title":"OpenAL gives wrong include and libs path with pkg-config","user":{"login":"necessarily-equal","id":59283660,"node_id":"MDQ6VXNlcjU5MjgzNjYw","avatar_url":"https://avatars.githubusercontent.com/u/59283660?v=4","gravatar_id":"","url":"https://api.github.com/users/necessarily-equal","html_url":"https://github.com/necessarily-equal","followers_url":"https://api.github.com/users/necessarily-equal/followers","following_url":"https://api.github.com/users/necessarily-equal/following{/other_user}","gists_url":"https://api.github.com/users/necessarily-equal/gists{/gist_id}","starred_url":"https://api.github.com/users/necessarily-equal/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/necessarily-equal/subscriptions","organizations_url":"https://api.github.com/users/necessarily-equal/orgs","repos_url":"https://api.github.com/users/necessarily-equal/repos","events_url":"https://api.github.com/users/necessarily-equal/events{/privacy}","received_events_url":"https://api.github.com/users/necessarily-equal/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-06T12:49:10Z","updated_at":"2022-04-13T05:29:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe pkg-config file for OpenAL is unusable.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. open a devshell with pkg-config and openal (works both with the stable and unstable release of nixpkgs)\r\n2. `pkg-config --cflags`\r\n3. notice that the flags are not correct: « `-I/nix/store/iccwkh7yacv40zyqnj1mah73616mid5s-openal-soft-1.21.1//nix/store/iccwkh7yacv40zyqnj1mah73616mid5s-openal-soft-1.21.1/include -I/nix/store/iccwkh7yacv40zyqnj1mah73616mid5s-openal-soft-1.21.1//nix/store/iccwkh7yacv40zyqnj1mah73616mid5s-openal-soft-1.21.1/include/AL` »\r\n\r\nin a single command, `nix-shell -E 'with (import <nixpkgs> {}); stdenv.mkDerivation{name=\"foo\"; buildInputs=[pkg-config openal];}' --run 'pkg-config --cflags openal'`\r\n\r\nhere is the result on unstable: `-I/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1//nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include -I/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1//nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include/AL`\r\n\r\n### Expected behavior\r\nInclude path is\r\n* `/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include`\r\n* `/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include/AL`\r\ninstead of\r\n* `/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1//nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include`\r\n* `/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1//nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/include/AL`\r\n\r\nLikewise for `--libs`, `-L/nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1//nix/store/dvb8l321pvzdyb2c2ljpc9wvrfzs335w-openal-soft-1.21.1/lib` should not contain the path twice.\r\n\r\n### Notify maintainers\r\n@ftrvxmtrx\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11.336340.2ebb6c1e5ae, nixpkgs-git\"`\r\n - channels(afontain): `\"nixos-20.09-20.09.4407.1c1f5649bb9, nixpkgs-unstable-22.05pre342949.28d58b97925, nixpkgs-20.09-20.09.4407.1c1f5649bb9\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167528/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167527","id":1194555760,"node_id":"I_kwDOAEVQ_M5HM3lw","number":167527,"title":"Meshcentral agent","user":{"login":"Jonasmadsen","id":36917429,"node_id":"MDQ6VXNlcjM2OTE3NDI5","avatar_url":"https://avatars.githubusercontent.com/u/36917429?v=4","gravatar_id":"","url":"https://api.github.com/users/Jonasmadsen","html_url":"https://github.com/Jonasmadsen","followers_url":"https://api.github.com/users/Jonasmadsen/followers","following_url":"https://api.github.com/users/Jonasmadsen/following{/other_user}","gists_url":"https://api.github.com/users/Jonasmadsen/gists{/gist_id}","starred_url":"https://api.github.com/users/Jonasmadsen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Jonasmadsen/subscriptions","organizations_url":"https://api.github.com/users/Jonasmadsen/orgs","repos_url":"https://api.github.com/users/Jonasmadsen/repos","events_url":"https://api.github.com/users/Jonasmadsen/events{/privacy}","received_events_url":"https://api.github.com/users/Jonasmadsen/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T12:37:17Z","updated_at":"2022-04-06T12:38:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nMeshcentral is a remote administration tool similar to teamviewer but self hosted.\r\nMeshcentral server exists in nixpkgs, but the agent (client) doesn't. It would be very cool to control nixos remotely using meshcentral.\r\nYou could deploy and control a fleet using declarative nixos configurations only with an open source self hosted solution.\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.meshcommander.com/meshcentral2\r\n* source URL: https://github.com/Ylianst/MeshAgent\r\n* license: [Apache 2.0](https://www.apache.org/licenses/LICENSE-2.0)\r\n* platforms: unix, linux, darwin, ... all of them appears to be supported\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167527/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167525","id":1194537452,"node_id":"I_kwDOAEVQ_M5HMzHs","number":167525,"title":"How to check signatures in `updateScript`? Standard solution?","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T12:22:52Z","updated_at":"2022-04-06T12:22:52Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I wrote this\r\nhttps://github.com/NixOS/nixpkgs/pull/161528/files#diff-682a8009a63076efa39b138a1091b2c69d7da595c6f8eaaffb15611a08ac50b6R40-R46\r\n\r\n```\r\n curl \"https://downloads.apache.org/$path\" >$tmp/src.tar.gz\r\n curl \"https://downloads.apache.org/$path.asc\" >$tmp/src.tar.gz.asc\r\n # See https://downloads.apache.org/cassandra/KEYS\r\n # Make sure that any new key corresponds to someone on the project\r\n for key in A4C465FEA0C552561A392A61E91335D77E3E87CB; do\r\n gpg --trustdb-name \"$tmp/trust.db\" --batch --recv-keys \"$key\"\r\n echo \"$key:5:\" | gpg --trustdb-name \"$tmp/trust.db\" --batch --import-ownertrust\r\n done\r\n gpg --trustdb-name \"$tmp/trust.db\" --batch --verify --trust-model direct $tmp/src.tar.gz.asc $tmp/src.tar.gz\r\n```\r\n\r\nbecause I figured trusting all apache KEYS is too susceptible to attack, as it is basically the same as trusting `https://downloads.apache.org`. The point is to have more than one root of trust, right?\r\n\r\nWe should standardize a solution, validate it and document it in the manual.\r\n - [ ] turn this logic into a reusable script (package?)\r\n - [ ] validate it by attacking it, preferably in tests\r\n - [ ] describe it in the manual\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167525/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167510","id":1194334700,"node_id":"I_kwDOAEVQ_M5HMBns","number":167510,"title":"roogle 1.4.0 doesn't exist anymore","user":{"login":"06kellyjac","id":9866621,"node_id":"MDQ6VXNlcjk4NjY2MjE=","avatar_url":"https://avatars.githubusercontent.com/u/9866621?v=4","gravatar_id":"","url":"https://api.github.com/users/06kellyjac","html_url":"https://github.com/06kellyjac","followers_url":"https://api.github.com/users/06kellyjac/followers","following_url":"https://api.github.com/users/06kellyjac/following{/other_user}","gists_url":"https://api.github.com/users/06kellyjac/gists{/gist_id}","starred_url":"https://api.github.com/users/06kellyjac/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/06kellyjac/subscriptions","organizations_url":"https://api.github.com/users/06kellyjac/orgs","repos_url":"https://api.github.com/users/06kellyjac/repos","events_url":"https://api.github.com/users/06kellyjac/events{/privacy}","received_events_url":"https://api.github.com/users/06kellyjac/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T09:29:06Z","updated_at":"2022-04-07T20:39:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nNeither https://github.com/hkmatsumoto/roogle or https://github.com/roogle-rs/roogle have a tag `1.4.0` :eyes:\r\n\r\nhydra seems happy but that's just because it's riding off it's old cached copy that doesn't exist anymore.\r\n\r\nI'd raise an issue on the `hkmatsumoto` repo but it doesn't take issues. I'm going to write out some context here and maybe ask on the original `roogle-rs` repo linking here\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. invalidate the cached source\r\n2. `nix-build -A roogle`\r\n3. Error\r\n\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@figsoda \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167510/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167506","id":1194301289,"node_id":"I_kwDOAEVQ_M5HL5dp","number":167506,"title":"Radarr fails to handle Gzip encoded requests","user":{"login":"janstenpickle","id":1926225,"node_id":"MDQ6VXNlcjE5MjYyMjU=","avatar_url":"https://avatars.githubusercontent.com/u/1926225?v=4","gravatar_id":"","url":"https://api.github.com/users/janstenpickle","html_url":"https://github.com/janstenpickle","followers_url":"https://api.github.com/users/janstenpickle/followers","following_url":"https://api.github.com/users/janstenpickle/following{/other_user}","gists_url":"https://api.github.com/users/janstenpickle/gists{/gist_id}","starred_url":"https://api.github.com/users/janstenpickle/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/janstenpickle/subscriptions","organizations_url":"https://api.github.com/users/janstenpickle/orgs","repos_url":"https://api.github.com/users/janstenpickle/repos","events_url":"https://api.github.com/users/janstenpickle/events{/privacy}","received_events_url":"https://api.github.com/users/janstenpickle/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":12,"created_at":"2022-04-06T09:03:17Z","updated_at":"2022-04-08T19:53:34Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOn Nixos, the current version of Radarr (`4.0.5.5981`) fails to accept or make HTTP requests due to a missing (I think) Dotnet dependency (`liblibSystem.IO.Compression.Native`).\r\n\r\nMaking requests without compression enabled does work, however search inside of Radarr doesn't as the Dotnet HTTP seems to also depend on Zlib.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set up Radarr with with `services.radar...` options\r\n2. Ensure `services.radar.openFirewall` is set to `true`\r\n3. Rebuild the system\r\n4. Browse to `<hostname>:7878`\r\n6. See error in systemd journal for `radarr.service`\r\n\r\n### Expected behavior\r\n\r\nRadarr should be able to respond to and make HTTP requests with zlib compression enabled.\r\n\r\n### Screenshots\r\n\r\nTechnically not a screenshot, but a stacktrace\r\n\r\n```\r\n[v3.2.2.5080] System.IO.Compression.ZLibException: The underlying compression routine could not be loaded correctly.\r\n ---> System.DllNotFoundException: Unable to load shared library 'libSystem.IO.Compression.Native' or one of its dependencies. In order to help diagnose loading problems, consider setting the LD_DEBUG environment variable: liblibSystem.IO.Compression.Native: cannot open shared object file: No such file or directory\r\n at Interop.zlib.DeflateInit2_(ZStream& stream, CompressionLevel level, CompressionMethod method, Int32 windowBits, Int32 memLevel, CompressionStrategy strategy)\r\n at System.IO.Compression.ZLibNative.ZLibStreamHandle.DeflateInit2_(CompressionLevel level, Int32 windowBits, Int32 memLevel, CompressionStrategy strategy)\r\n at System.IO.Compression.Deflater..ctor(CompressionLevel compressionLevel, Int32 windowBits)\r\n --- End of inner exception stack trace ---\r\n at System.IO.Compression.Deflater..ctor(CompressionLevel compressionLevel, Int32 windowBits)\r\n at System.IO.Compression.DeflateStream.InitializeDeflater(Stream stream, Boolean leaveOpen, Int32 windowBits, CompressionLevel compressionLevel)\r\n at System.IO.Compression.DeflateStream..ctor(Stream stream, CompressionMode mode, Boolean leaveOpen, Int32 windowBits, Int64 uncompressedSize)\r\n at System.IO.Compression.GZipStream..ctor(Stream stream, CompressionMode mode, Boolean leaveOpen)\r\n at Radarr.Http.Extensions.Pipelines.GzipCompressionPipeline.WriteGZipStream(Action`1 innerContent, Stream targetStream) in D:\\a\\1\\s\\src\\Radarr.Http\\Extensions\\Pipelines\\GZipPipeline.cs:line 73\r\n at Radarr.Http.Extensions.Pipelines.GzipCompressionPipeline.<>c__DisplayClass6_0.<CompressResponse>b__1(Stream responseStream) in D:\\a\\1\\s\\src\\Radarr.Http\\Extensions\\Pipelines\\GZipPipeline.cs:line 51\r\n at Nancy.Owin.NancyMiddleware.RequestComplete(NancyContext context, IDictionary`2 environment, Func`2 performPassThrough, Func`2 next)\r\n at Nancy.Owin.NancyMiddleware.<>c__DisplayClass2_1.<<UseNancy>b__1>d.MoveNext()\r\n--- End of stack trace from previous location ---\r\n at Microsoft.AspNetCore.Owin.WebSocketAcceptAdapter.<>c__DisplayClass6_0.<<AdaptWebSockets>b__0>d.MoveNext()\r\n--- End of stack trace from previous location ---\r\n at Radarr.Host.Middleware.SignalRMiddleware.<Attach>b__7_0(HttpContext context, Func`1 next) in D:\\a\\1\\s\\src\\NzbDrone.Host\\WebHost\\Middleware\\SignalRMiddleware.cs:line 51\r\n at Microsoft.AspNetCore.Server.Kestrel.Core.Internal.Http.HttpProtocol.ProcessRequests[TContext](IHttpApplication`1 application)\r\n```\r\n\r\n### Additional context\r\nI tried both inside and outside of a Nix container, which yielded the same result.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(chris): `\"\"`\r\n - channels(root): `\"nixos-21.11.336824.ccb90fb9e11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167506/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167495","id":1194233414,"node_id":"I_kwDOAEVQ_M5HLo5G","number":167495,"title":"Can't create basic electron app, either using node2js, npm or yarn. Error spawn ENOENT","user":{"login":"tobiasBora","id":2164118,"node_id":"MDQ6VXNlcjIxNjQxMTg=","avatar_url":"https://avatars.githubusercontent.com/u/2164118?v=4","gravatar_id":"","url":"https://api.github.com/users/tobiasBora","html_url":"https://github.com/tobiasBora","followers_url":"https://api.github.com/users/tobiasBora/followers","following_url":"https://api.github.com/users/tobiasBora/following{/other_user}","gists_url":"https://api.github.com/users/tobiasBora/gists{/gist_id}","starred_url":"https://api.github.com/users/tobiasBora/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tobiasBora/subscriptions","organizations_url":"https://api.github.com/users/tobiasBora/orgs","repos_url":"https://api.github.com/users/tobiasBora/repos","events_url":"https://api.github.com/users/tobiasBora/events{/privacy}","received_events_url":"https://api.github.com/users/tobiasBora/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T08:08:46Z","updated_at":"2022-04-06T08:09:26Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI need to use both electron and some node libraries (easymidi). If I install directly the electron package, I can start directly the project, but then I can't install/use node libraries (or at least I don't know how). If I use npm, yarn or node2nix to install electron, then I get errors (as I reported [here](https://discourse.nixos.org/t/cant-setup-development-with-electron-error-spawn-enoent/18497)), given in the steps to reproduce.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```\r\n$ nix-shell -p yarn\r\n$ git clone https://github.com/electron/electron-quick-start\r\n$ cd electron-quick-start/\r\n$ yarn install\r\n$ yarn start\r\nyarn run v1.22.15\r\n $ electron .\r\nevents.js:377\r\n throw er; // Unhandled 'error' event\r\n ^\r\n\r\nError: spawn /tmp/c/electron-quick-start/node_modules/electron/dist/electron ENOENT\r\n at Process.ChildProcess._handle.onexit (internal/child_process.js:274:19)\r\n at onErrorNT (internal/child_process.js:469:16)\r\n at processTicksAndRejections (internal/process/task_queues.js:82:21)\r\nEmitted 'error' event on ChildProcess instance at:\r\n at Process.ChildProcess._handle.onexit (internal/child_process.js:280:12)\r\n at onErrorNT (internal/child_process.js:469:16)\r\n at processTicksAndRejections (internal/process/task_queues.js:82:21) {\r\n errno: -2,\r\n code: 'ENOENT',\r\n syscall: 'spawn /tmp/c/electron-quick-start/node_modules/electron/dist/electron',\r\n path: '/tmp/c/electron-quick-start/node_modules/electron/dist/electron',\r\n spawnargs: [ '.' ]\r\n}\r\nerror Command failed with exit code 1.\r\ninfo Visit https://yarnpkg.com/en/docs/cli/run for documentation about this command.\r\n```\r\n\r\nHere are the detailled log (produced with a different run with the same error, using npm here):\r\n```\r\n0 info it worked if it ends with ok\r\n1 verbose cli [\r\n1 verbose cli '/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/bin/node',\r\n1 verbose cli '/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/bin/npm',\r\n1 verbose cli 'start'\r\n1 verbose cli ]\r\n2 info using npm@6.14.15\r\n3 info using node@v14.18.0\r\n4 verbose run-script [ 'prestart', 'start', 'poststart' ]\r\n5 info lifecycle electron-quick-start@1.0.0~prestart: electron-quick-start@1.0.0\r\n6 info lifecycle electron-quick-start@1.0.0~start: electron-quick-start@1.0.0\r\n7 verbose lifecycle electron-quick-start@1.0.0~start: unsafe-perm in lifecycle true\r\n8 verbose lifecycle electron-quick-start@1.0.0~start: PATH: /nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/lib/node_modules/npm/node_modules/npm-lifecycle/node-gyp-bin:/tmp/d/electron-quick-start/no\r\nde_modules/.bin:/nix/store/yx24h6ywbkg7rm5x7lrm8mx8ypcf4ywi-bash-interactive-5.1-p8/bin:/nix/store/fj3ywsx22xvjd4mly4323ikjcavyv91v-patchelf-0.13/bin:/nix/store/s5hkav7whndbfz0szshpb46h4idqdq9a-gcc-wrapper-10.3\r\n.0/bin:/nix/store/a2w3l1m75908yd05a0h40vnrzvxfd0gd-gcc-10.3.0/bin:/nix/store/mfz26azl9561jgd5n73nkszzp6qhsaal-glibc-2.33-50-bin/bin:/nix/store/xyn0240zrpprnspg3n0fi8c8aw5bq0mr-coreutils-8.32/bin:/nix/store/5d5j\r\n1z9bg01wqxahihy2x5n22ykc32w8-binutils-wrapper-2.35.1/bin:/nix/store/a4mmjm3bblxwp8h53bcfx3dly80ib0ba-binutils-2.35.1/bin:/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/bin:/nix/store/xyn0240zrpprnsp\r\ng3n0fi8c8aw5bq0mr-coreutils-8.32/bin:/nix/store/1nq62klcc9n2jv2ixaf77makkzdcghrh-findutils-4.8.0/bin:/nix/store/xwkxkx4bk005q35hsdhqbkbdv7g28cz5-diffutils-3.8/bin:/nix/store/dy4ylp9439la4lq35ah2mj80fi87pk4w-gnu\r\nsed-4.8/bin:/nix/store/xxgddhdi57bbgd1yxza44plq6krjmiz1-gnugrep-3.6/bin:/nix/store/31pkw5yi08fj4l0glzvpf1cp4ywkxh86-gawk-5.1.0/bin:/nix/store/nwg8in201f7y6vdm787v3j84jjrn0ayw-gnutar-1.34/bin:/nix/store/ygzg6wzh\r\ngxf51ianb4zjvrzq4ilx9jd7-gzip-1.10/bin:/nix/store/gakfgapj20lv13vkcz6c38j8i9vz4ypi-bzip2-1.0.6.0.2-bin/bin:/nix/store/xgp0bgw4rpnbc3vr2qdsdbixp3zy4v1l-gnumake-4.3/bin:/nix/store/wadmyilr414n7bimxysbny876i2vlm5r\r\n-bash-5.1-p8/bin:/nix/store/347zp4r9a7gm5gk0gwijqw294nnyypcs-patch-2.7.6/bin:/nix/store/f2x98vk07px8916b9xid7jq6ky86sfmi-xz-5.2.5-bin/bin\r\n9 verbose lifecycle electron-quick-start@1.0.0~start: CWD: /tmp/d/electron-quick-start\r\n10 silly lifecycle electron-quick-start@1.0.0~start: Args: [ '-c', 'electron .' ]\r\n11 silly lifecycle electron-quick-start@1.0.0~start: Returned: code: 1 signal: null\r\n12 info lifecycle electron-quick-start@1.0.0~start: Failed to exec start script\r\n13 verbose stack Error: electron-quick-start@1.0.0 start: `electron .`\r\n13 verbose stack Exit status 1\r\n13 verbose stack at EventEmitter.<anonymous> (/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/lib/node_modules/npm/node_modules/npm-lifecycle/index.js:332:16)\r\n13 verbose stack at EventEmitter.emit (events.js:400:28)\r\n13 verbose stack at ChildProcess.<anonymous> (/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/lib/node_modules/npm/node_modules/npm-lifecycle/lib/spawn.js:55:14)\r\n13 verbose stack at ChildProcess.emit (events.js:400:28)\r\n13 verbose stack at maybeClose (internal/child_process.js:1058:16)\r\n13 verbose stack at Process.ChildProcess._handle.onexit (internal/child_process.js:293:5)\r\n14 verbose pkgid electron-quick-start@1.0.0\r\n15 verbose cwd /tmp/d/electron-quick-start\r\n16 verbose Linux 5.10.75\r\n17 verbose argv \"/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/bin/node\" \"/nix/store/06680csx89n416lvsy2yljmw6rvibj8y-nodejs-14.18.0/bin/npm\" \"start\"\r\n18 verbose node v14.18.0\r\n19 verbose npm v6.14.15\r\n20 error code ELIFECYCLE\r\n21 error errno 1\r\n22 error electron-quick-start@1.0.0 start: `electron .`\r\n22 error Exit status 1\r\n23 error Failed at the electron-quick-start@1.0.0 start script.\r\n23 error This is probably not a problem with npm. There is likely additional logging output above.\r\n24 verbose exit [ 1, true ]\r\n```\r\n\r\nIf I try to use `node2nix` (after removing the `node_modules` as it gives errors), I can't even install the libraries:\r\n```\r\n$ nix-shell -I nixpkgs=local-nixos-unstable -A shell\r\n[...]\r\n\r\n> electron@18.0.2 postinstall /nix/store/rz9jlhkzwgy1xv0ky35ww1zdqb28f0zx-node-dependencies-electron-quick-start-1.0.0/electron-quick-start/node_modules/electron\r\n> node install.js\r\n\r\nRequestError: getaddrinfo ENOTFOUND github.com\r\n at ClientRequest.<anonymous> (/nix/store/rz9jlhkzwgy1xv0ky35ww1zdqb28f0zx-node-dependencies-electron-quick-start-1.0.0/electron-quick-start/node_modules/got/source/request-as-event-emitter.js:178:14)\r\n at Object.onceWrapper (events.js:421:26)\r\n at ClientRequest.emit (events.js:326:22)\r\n at ClientRequest.origin.emit (/nix/store/rz9jlhkzwgy1xv0ky35ww1zdqb28f0zx-node-dependencies-electron-quick-start-1.0.0/electron-quick-start/node_modules/@szmarczak/http-timer/source/index.js:37:11)\r\n at TLSSocket.socketErrorListener (_http_client.js:427:9)\r\n at TLSSocket.emit (events.js:314:20)\r\n at emitErrorNT (internal/streams/destroy.js:92:8)\r\n at emitErrorAndCloseNT (internal/streams/destroy.js:60:3)\r\n at processTicksAndRejections (internal/process/task_queues.js:84:21)\r\nnpm ERR! code ELIFECYCLE\r\nnpm ERR! errno 1\r\nnpm ERR! electron@18.0.2 postinstall: `node install.js`\r\nnpm ERR! Exit status 1\r\nnpm ERR! \r\nnpm ERR! Failed at the electron@18.0.2 postinstall script.\r\nnpm ERR! This is probably not a problem with npm. There is likely additional logging output above.\r\n\r\nnpm ERR! A complete log of this run can be found in:\r\nnpm ERR! /build/.npm/_logs/2022-04-06T08_02_33_311Z-debug.log\r\n\r\nerror: builder for '/nix/store/xzifn0013kxmv2kdck7n5m8422ppad78-node-dependencies-electron-quick-start-1.0.0.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > npm ERR! errno 1\r\n > npm ERR! electron@18.0.2 postinstall: `node install.js`\r\n > npm ERR! Exit status 1\r\n > npm ERR!\r\n > npm ERR! Failed at the electron@18.0.2 postinstall script.\r\n > npm ERR! This is probably not a problem with npm. There is likely additional logging output above.\r\n > \r\n > npm ERR! A complete log of this run can be found in:\r\n > npm ERR! /build/.npm/_logs/2022-04-06T08_02_33_311Z-debug.log\r\n > \r\n For full logs, run 'nix log /nix/store/xzifn0013kxmv2kdck7n5m8422ppad78-node-dependencies-electron-quick-start-1.0.0.drv'.\r\n\r\n```\r\n\r\nThe closer issue I can find is this one https://github.com/electron-userland/electron-builder/issues/6069 but the solution does not seem to work for me.\r\n\r\n### Expected behavior\r\n\r\nI expect to be able to develop electron apps using yarn, npm or node2nix.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@svanderburg @goibhniu @gilligan @cko @marsam @travisbhartwell @manveru @prusnak\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.75, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5pre20211007_844dd90`\r\n - channels(leo): `\"local-nixos-unstable-22.05pre366144.bc4b9eef3ce, nixos-unstable-22.05pre362644.1ec61dd4167, home-manager, local-nixpkgs-unstable-21.11pre304920.dd98b100651, nixos-20-03-20.03.3328.6d1a044fc9f, test\"`\r\n - channels(root): `\"nixos-21.11pre325514.a4bf4434570\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\nNote that to ensure I was running the latest version, I also tried to use `nix-shell -I nixpkgs=local-nixos-unstable` instead of `nix-shell`, with the same errors.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167495/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167452","id":1193881737,"node_id":"I_kwDOAEVQ_M5HKTCJ","number":167452,"title":"pyside2: ERROR: Could not find a version that satisfies the requirement pyside2","user":{"login":"milahu","id":12958815,"node_id":"MDQ6VXNlcjEyOTU4ODE1","avatar_url":"https://avatars.githubusercontent.com/u/12958815?v=4","gravatar_id":"","url":"https://api.github.com/users/milahu","html_url":"https://github.com/milahu","followers_url":"https://api.github.com/users/milahu/followers","following_url":"https://api.github.com/users/milahu/following{/other_user}","gists_url":"https://api.github.com/users/milahu/gists{/gist_id}","starred_url":"https://api.github.com/users/milahu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/milahu/subscriptions","organizations_url":"https://api.github.com/users/milahu/orgs","repos_url":"https://api.github.com/users/milahu/repos","events_url":"https://api.github.com/users/milahu/events{/privacy}","received_events_url":"https://api.github.com/users/milahu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T00:58:48Z","updated_at":"2022-04-06T00:59:26Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"pip cannot find pyside2\r\n\r\n* low priority (few packages depend on pyside2)\r\n* easy to fix (but compiling may take a while)\r\n\r\n### Steps To Reproduce\r\n\r\nbuild `PySimpleGUIQt` which depends on `pyside2`\r\n\r\n<details>\r\n\r\n```nix\r\n{ lib\r\n, buildPythonPackage\r\n, fetchPypi\r\n, python\r\n, pyside2\r\n}:\r\n\r\nbuildPythonPackage rec {\r\n pname = \"PySimpleGUIQt\";\r\n version = \"0.35.0\";\r\n src = fetchPypi {\r\n inherit pname version;\r\n sha256 = \"sha256-LBjqJhVUI1os2u525hbQrcFIUB6Jv0ESp5jyppvzyLU=\";\r\n };\r\n pythonImportsCheck = [ \"PySimpleGUIQt\" ];\r\n propagatedBuildInputs = [\r\n pyside2\r\n # FIXME\r\n # ERROR: Could not find a version that satisfies the requirement pyside2 (from pysimpleguiqt) (from versions: none)\r\n ];\r\n checkPhase = ''\r\n runHook preCheck\r\n ${python.interpreter} -m unittest\r\n runHook postCheck\r\n '';\r\n meta = with lib; {\r\n homepage = \"https://github.com/PySimpleGUI/PySimpleGUI\";\r\n description = \"Python GUIs for Humans. Qt backend\";\r\n license = licenses.lgpl3Plus;\r\n };\r\n}\r\n```\r\n\r\n</details>\r\n\r\n### Expected behavior\r\n\r\npip should find pyside2\r\n\r\n### Possible solution\r\n\r\nwe had the same problem with pyside6 in https://github.com/NixOS/nixpkgs/pull/141883#discussion_r800094696\r\n\r\nworking nix file for pyside6 https://github.com/milahu/nixpkgs/blob/qt-6-init/pkgs/development/python-modules/pyside6/default.nix#L68\r\nworking pkgbuild file for pyside6 https://github.com/archlinux/svntogit-packages/blob/e1fe2063534324b8d978bb3a5e0b687f6e07f8ea/trunk/PKGBUILD#L34\r\n\r\nbroken nix file for pyside2 https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/python-modules/pyside2/default.nix\r\n\r\n### Notify maintainers\r\n\r\n@gebner\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167452/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167449","id":1193861822,"node_id":"I_kwDOAEVQ_M5HKOK-","number":167449,"title":"dockutil 2.0.5 -> 3.0.2","user":{"login":"JayRovacsek","id":29395089,"node_id":"MDQ6VXNlcjI5Mzk1MDg5","avatar_url":"https://avatars.githubusercontent.com/u/29395089?v=4","gravatar_id":"","url":"https://api.github.com/users/JayRovacsek","html_url":"https://github.com/JayRovacsek","followers_url":"https://api.github.com/users/JayRovacsek/followers","following_url":"https://api.github.com/users/JayRovacsek/following{/other_user}","gists_url":"https://api.github.com/users/JayRovacsek/gists{/gist_id}","starred_url":"https://api.github.com/users/JayRovacsek/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/JayRovacsek/subscriptions","organizations_url":"https://api.github.com/users/JayRovacsek/orgs","repos_url":"https://api.github.com/users/JayRovacsek/repos","events_url":"https://api.github.com/users/JayRovacsek/events{/privacy}","received_events_url":"https://api.github.com/users/JayRovacsek/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-06T00:18:39Z","updated_at":"2022-04-06T06:43:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: dockutil\r\n\r\ncurrent version: 2.0.5\r\ndesired version: 3.0.2\r\n\r\n###### Notify maintainers\r\n\r\nmaintainers: @tboerger \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167449/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167389","id":1193602501,"node_id":"I_kwDOAEVQ_M5HJO3F","number":167389,"title":"davinci-resolve: Blackmagic Mini Panel hardware support not working","user":{"login":"lukego","id":13791,"node_id":"MDQ6VXNlcjEzNzkx","avatar_url":"https://avatars.githubusercontent.com/u/13791?v=4","gravatar_id":"","url":"https://api.github.com/users/lukego","html_url":"https://github.com/lukego","followers_url":"https://api.github.com/users/lukego/followers","following_url":"https://api.github.com/users/lukego/following{/other_user}","gists_url":"https://api.github.com/users/lukego/gists{/gist_id}","starred_url":"https://api.github.com/users/lukego/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lukego/subscriptions","organizations_url":"https://api.github.com/users/lukego/orgs","repos_url":"https://api.github.com/users/lukego/repos","events_url":"https://api.github.com/users/lukego/events{/privacy}","received_events_url":"https://api.github.com/users/lukego/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-04-05T19:07:13Z","updated_at":"2022-04-07T19:09:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe Blackmagic Mini Panel hardware device is not working with the davinci-resolve in nixpkgs.\r\n\r\nI am troubleshooting this myself but I create this issue for sharing and visibility.\r\n\r\n### Steps To Reproduce\r\n\r\nMethod A:\r\n\r\n1. Connect the panel via USB and enable in `DaVinci Resolve -> Preferences -> Control Panels`.\r\n2. Restart DaVinci Resolve.\r\n3. Panel does not connect to resolve and log contains the error below:\r\n\r\n```\r\n$ cat ~/.local/share/DaVinciResolve/logs/panel.log\r\nopened log file\r\nOpening communication to resolve..\r\nFailed to create listener\r\nUnsupported DaVinci Panel API Version (0.0), please update\r\nResolve discovery\r\nResolve discovery\r\n```\r\n\r\nMethod B:\r\n\r\n1. Connect the panel via Ethernet and enable in `DaVinci Resolve -> Preferences -> Control Panels`.\r\n2. Restart DaVinci Resolve.\r\n3. Panel does not connect and log contains a similar (but not identical) message:\r\n\r\n```\r\n$ cat ~/.local/share/DaVinciResolve/logs/panel.log\r\nopened log file\r\nOpening communication to resolve..\r\nFailed to create listener\r\nUnsupported DaVinci Panel API Version (0.0), please update\r\n```\r\n\r\nIn both cases the display on the panel says \"No Connection to DaVinci Resolve: Please go to DaVinci Resolve Preferences menu to select this panel.\" (This is the same behavior as powering on the panel with DaVinci Resolve is not running anywhere.)\r\n\r\n### Expected behavior\r\n\r\nThe panel should connect either via USB or via Ethernet.\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Additional context\r\n\r\nThe same panel works out of the box with Resolve on macOS.\r\n\r\n### Notify maintainers\r\n\r\n@jshcmpbll\r\n\r\n### Metadata\r\n\r\n```\r\n[luke@snowy:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.15, NixOS, 22.05 (Quokka), 22.05.git.19d4f7dc485`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/home/luke/git/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167389/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167368","id":1193424035,"node_id":"I_kwDOAEVQ_M5HIjSj","number":167368,"title":"Cassandra 4.0","user":{"login":"turion","id":303489,"node_id":"MDQ6VXNlcjMwMzQ4OQ==","avatar_url":"https://avatars.githubusercontent.com/u/303489?v=4","gravatar_id":"","url":"https://api.github.com/users/turion","html_url":"https://github.com/turion","followers_url":"https://api.github.com/users/turion/followers","following_url":"https://api.github.com/users/turion/following{/other_user}","gists_url":"https://api.github.com/users/turion/gists{/gist_id}","starred_url":"https://api.github.com/users/turion/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/turion/subscriptions","organizations_url":"https://api.github.com/users/turion/orgs","repos_url":"https://api.github.com/users/turion/repos","events_url":"https://api.github.com/users/turion/events{/privacy}","received_events_url":"https://api.github.com/users/turion/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-05T16:20:01Z","updated_at":"2022-04-06T11:08:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Cassandra 4.0 has been released. It would be great if we could supply it as `cassandra_4_0` initially, and eventually move to it as a default. See https://cassandra.apache.org/_/download.html\r\n\r\n###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n\r\n\r\n`nix search` name: `cassandra`\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 3.11.12\r\ndesired version: 4.0.3\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @roberth\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167368/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167350","id":1193189064,"node_id":"I_kwDOAEVQ_M5HHp7I","number":167350,"title":"diffoscope: runtime dependency on ghc","user":{"login":"FRidh","id":2129135,"node_id":"MDQ6VXNlcjIxMjkxMzU=","avatar_url":"https://avatars.githubusercontent.com/u/2129135?v=4","gravatar_id":"","url":"https://api.github.com/users/FRidh","html_url":"https://github.com/FRidh","followers_url":"https://api.github.com/users/FRidh/followers","following_url":"https://api.github.com/users/FRidh/following{/other_user}","gists_url":"https://api.github.com/users/FRidh/gists{/gist_id}","starred_url":"https://api.github.com/users/FRidh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FRidh/subscriptions","organizations_url":"https://api.github.com/users/FRidh/orgs","repos_url":"https://api.github.com/users/FRidh/repos","events_url":"https://api.github.com/users/FRidh/events{/privacy}","received_events_url":"https://api.github.com/users/FRidh/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"FRidh","id":2129135,"node_id":"MDQ6VXNlcjIxMjkxMzU=","avatar_url":"https://avatars.githubusercontent.com/u/2129135?v=4","gravatar_id":"","url":"https://api.github.com/users/FRidh","html_url":"https://github.com/FRidh","followers_url":"https://api.github.com/users/FRidh/followers","following_url":"https://api.github.com/users/FRidh/following{/other_user}","gists_url":"https://api.github.com/users/FRidh/gists{/gist_id}","starred_url":"https://api.github.com/users/FRidh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FRidh/subscriptions","organizations_url":"https://api.github.com/users/FRidh/orgs","repos_url":"https://api.github.com/users/FRidh/repos","events_url":"https://api.github.com/users/FRidh/events{/privacy}","received_events_url":"https://api.github.com/users/FRidh/received_events","type":"User","site_admin":false},"assignees":[{"login":"FRidh","id":2129135,"node_id":"MDQ6VXNlcjIxMjkxMzU=","avatar_url":"https://avatars.githubusercontent.com/u/2129135?v=4","gravatar_id":"","url":"https://api.github.com/users/FRidh","html_url":"https://github.com/FRidh","followers_url":"https://api.github.com/users/FRidh/followers","following_url":"https://api.github.com/users/FRidh/following{/other_user}","gists_url":"https://api.github.com/users/FRidh/gists{/gist_id}","starred_url":"https://api.github.com/users/FRidh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FRidh/subscriptions","organizations_url":"https://api.github.com/users/FRidh/orgs","repos_url":"https://api.github.com/users/FRidh/repos","events_url":"https://api.github.com/users/FRidh/events{/privacy}","received_events_url":"https://api.github.com/users/FRidh/received_events","type":"User","site_admin":false}],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":3,"created_at":"2022-04-05T13:57:06Z","updated_at":"2022-04-21T12:51:43Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nMassive dependency.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167343","id":1193081612,"node_id":"I_kwDOAEVQ_M5HHPsM","number":167343,"title":"android-studio cannot launch the Android emulator","user":{"login":"mawis","id":2042030,"node_id":"MDQ6VXNlcjIwNDIwMzA=","avatar_url":"https://avatars.githubusercontent.com/u/2042030?v=4","gravatar_id":"","url":"https://api.github.com/users/mawis","html_url":"https://github.com/mawis","followers_url":"https://api.github.com/users/mawis/followers","following_url":"https://api.github.com/users/mawis/following{/other_user}","gists_url":"https://api.github.com/users/mawis/gists{/gist_id}","starred_url":"https://api.github.com/users/mawis/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mawis/subscriptions","organizations_url":"https://api.github.com/users/mawis/orgs","repos_url":"https://api.github.com/users/mawis/repos","events_url":"https://api.github.com/users/mawis/events{/privacy}","received_events_url":"https://api.github.com/users/mawis/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-05T12:28:31Z","updated_at":"2022-04-05T12:28:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI tried on 21.11 and unstable to use android-studio with the Android emulator. This worked some weeks ago, but currently I cannot open the emulator. I get the following output on the terminal:\r\n\r\n```\r\n2022-04-05 12:07:01,583 [ 83661] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:07:01,587 [ 83665] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:07:02,314 [ 84392] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:07:02,385 [ 84463] WARN - #com.android.ddmlib - * daemon started successfully \r\n2022-04-05 12:07:05,380 [ 87458] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:07:05,381 [ 87459] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:07:07,310 [ 89388] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:07:07,379 [ 89457] WARN - #com.android.ddmlib - * daemon started successfully \r\n2022-04-05 12:07:14,344 [ 96422] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:07:14,345 [ 96423] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:07:14,811 [ 96889] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:07:14,881 [ 96959] WARN - #com.android.ddmlib - * daemon started successfully \r\n2022-04-05 12:09:09,818 [ 211896] WARN - n.process.BaseOSProcessHandler - Process hasn't generated any output for a long time.\r\nIf it's a long-running mostly idle daemon process, consider overriding OSProcessHandler#readerOptions with 'BaseOutputReader.Options.forMostlySilentProcess()' to reduce CPU usage.\r\nCommand line: /home/matthias/Android/Sdk/emulator/emulator -netdelay none -netspeed full -avd Pixel_XL_API_31 -qt-hide-window -grpc-use-token -idle-grpc-timeout 300 \r\njava.lang.Throwable: Process creation:\r\n\tat com.intellij.execution.process.BaseOSProcessHandler.<init>(BaseOSProcessHandler.java:33)\r\n\tat com.android.tools.idea.avdmanager.EmulatorProcessHandler.<init>(EmulatorProcessHandler.java:36)\r\n\tat com.android.tools.idea.avdmanager.EmulatorRunner.start(EmulatorRunner.java:66)\r\n\tat com.android.tools.idea.avdmanager.AvdManagerConnection.continueToStartAvd(AvdManagerConnection.java:572)\r\n\tat com.android.tools.idea.avdmanager.AvdManagerConnection.continueToStartAvdIfAccelerationErrorIsNotBlocking(AvdManagerConnection.java:507)\r\n\tat com.android.tools.idea.avdmanager.AvdManagerConnection.lambda$startAvd$4(AvdManagerConnection.java:497)\r\n\tat com.google.common.util.concurrent.AbstractTransformFuture$AsyncTransformFuture.doTransform(AbstractTransformFuture.java:213)\r\n\tat com.google.common.util.concurrent.AbstractTransformFuture$AsyncTransformFuture.doTransform(AbstractTransformFuture.java:202)\r\n\tat com.google.common.util.concurrent.AbstractTransformFuture.run(AbstractTransformFuture.java:118)\r\n\tat com.google.common.util.concurrent.DirectExecutor.execute(DirectExecutor.java:30)\r\n\tat com.google.common.util.concurrent.AbstractFuture.executeListener(AbstractFuture.java:1213)\r\n\tat com.google.common.util.concurrent.AbstractFuture.complete(AbstractFuture.java:983)\r\n\tat com.google.common.util.concurrent.AbstractFuture.set(AbstractFuture.java:746)\r\n\tat com.google.common.util.concurrent.TrustedListenableFutureTask$TrustedFutureInterruptibleTask.afterRanInterruptibly(TrustedListenableFutureTask.java:131)\r\n\tat com.google.common.util.concurrent.InterruptibleTask.run(InterruptibleTask.java:133)\r\n\tat com.google.common.util.concurrent.TrustedListenableFutureTask.run(TrustedListenableFutureTask.java:78)\r\n\tat java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)\r\n\tat java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)\r\n\tat java.base/java.util.concurrent.Executors$PrivilegedThreadFactory$1$1.run(Executors.java:668)\r\n\tat java.base/java.util.concurrent.Executors$PrivilegedThreadFactory$1$1.run(Executors.java:665)\r\n\tat java.base/java.security.AccessController.doPrivileged(Native Method)\r\n\tat java.base/java.util.concurrent.Executors$PrivilegedThreadFactory$1.run(Executors.java:665)\r\n\tat java.base/java.lang.Thread.run(Thread.java:829)\r\n2022-04-05 12:10:41,088 [ 303166] WARN - dea.sdk.SystemInfoStatsMonitor - CpuInfoFlags.fromExitCode(): unknown flag values '0x80' \r\n2022-04-05 12:12:06,361 [ 388439] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:12:06,362 [ 388440] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:12:07,342 [ 389420] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:12:07,412 [ 389490] WARN - #com.android.ddmlib - * daemon started successfully \r\n2022-04-05 12:12:09,615 [ 391693] WARN - ger.EmulatorConnectionListener - Timed out after 300seconds waiting for emulator to come online. \r\n2022-04-05 12:12:10,033 [ 392111] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:12:10,034 [ 392112] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:12:20,044 [ 402122] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:12:20,112 [ 402190] WARN - #com.android.ddmlib - * daemon started successfully \r\n2022-04-05 12:12:27,917 [ 409995] WARN - #com.android.ddmlib - Adb connection Error:EOF \r\n2022-04-05 12:12:27,918 [ 409996] WARN - #com.android.ddmlib - Cannot reach ADB server, attempting to reconnect. \r\n2022-04-05 12:12:37,926 [ 420004] WARN - #com.android.ddmlib - * daemon not running; starting now at tcp:5037 \r\n2022-04-05 12:12:37,995 [ 420073] WARN - #com.android.ddmlib - * daemon started successfully \r\n```\r\n\r\nAnd after some time the following notification is shown:\r\n\r\n\r\n\r\nBut it seems something is running:\r\n\r\n```console\r\n[matthias@tejo ~ ]$ ps ax|grep emu\r\n 641229 pts/0 Sl+ 0:02 /home/matthias/Android/Sdk/emulator/qemu/linux-x86_64/qemu-system-x86_64 -netdelay none -netspeed full -avd Pixel_XL_API_31 -qt-hide-window -grpc-use-token -idle-grpc-timeout 300\r\n 641234 pts/0 Sl+ 0:00 /home/matthias/Android/Sdk/emulator/emulator64-crash-service -pipe 5 -ppid 1048 -data-dir /tmp/android-matthias/5bb3dd90-07b4-4924-ab9b-44d7d095bb1a\r\n 642127 pts/1 S+ 0:00 grep --color=auto --exclude-dir=.bzr --exclude-dir=CVS --exclude-dir=.git --exclude-dir=.hg --exclude-dir=.svn --exclude-dir=.idea --exclude-dir=.tox emu\r\n[matthias@tejo ~ ]$ \r\n```\r\n\r\nRunning `ldd /home/matthias/Android/Sdk/emulator/qemu/linux-x86_64/qemu-system-x86_64` on a normal terminal results in:\r\n\r\n```console\r\n\tlinux-vdso.so.1 (0x00007fff3b191000)\r\n\tlibtcmalloc_minimal.so.4 => not found\r\n\tlibutil.so.1 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libutil.so.1 (0x00007f18ef7f4000)\r\n\tlibc++.so.1 => not found\r\n\tlibdl.so.2 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libdl.so.2 (0x00007f18ef7ef000)\r\n\tlibrt.so.1 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/librt.so.1 (0x00007f18ef7e4000)\r\n\tlibm.so.6 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libm.so.6 (0x00007f18ef6a1000)\r\n\tlibpthread.so.0 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libpthread.so.0 (0x00007f18ef681000)\r\n\tlibQt5WebEngineWidgetsAndroidEmu.so.5 => not found\r\n\tlibQt5WebChannelAndroidEmu.so.5 => not found\r\n\tlibQt5NetworkAndroidEmu.so.5 => not found\r\n\tlibQt5QmlAndroidEmu.so.5 => not found\r\n\tlibQt5WebSocketsAndroidEmu.so.5 => not found\r\n\tlibQt5CoreAndroidEmu.so.5 => not found\r\n\tlibQt5GuiAndroidEmu.so.5 => not found\r\n\tlibQt5WidgetsAndroidEmu.so.5 => not found\r\n\tlibQt5SvgAndroidEmu.so.5 => not found\r\n\tlibX11.so.6 => not found\r\n\tlibpulse.so.0 => not found\r\n\tlibgcc_s.so.1 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libgcc_s.so.1 (0x00007f18ef663000)\r\n\tlibc.so.6 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib/libc.so.6 (0x00007f18ef48e000)\r\n\t/lib64/ld-linux-x86-64.so.2 => /nix/store/rxjh6jxg7ksisbcxl0cjwcff5iprpdfz-glibc-2.33-123/lib64/ld-linux-x86-64.so.2 (0x00007f18ef7fb000)\r\n```\r\n\r\nBut I don't know whether android-studio runs the emulator in a different environmetn.\r\n\r\nI already deleted /home/matthias/Android completely and reinstalled the SDK using android-studio.\r\n\r\n\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\n1. open `android-studio`\r\n2. create new project\r\n3. create new device\r\n4. run the emulated device\r\n\r\n### Expected behavior\r\nAndroid emulator shows up as a new GUI window\r\n\r\n### Screenshots\r\nsee above\r\n\r\n### Additional context\r\nI also tried this using `android-studio` from the unstable channel as well as `androidStudioPackages.dev` from unstable with the same results\r\n\r\n### Notify maintainers\r\n@fabianhjr\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[matthias@tejo ~ ]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.07 MiB download, 0.34 MiB unpacked):\r\n /nix/store/h8lf018lfkq58qr6fdjabnwln8bi8m5k-stdenv-linux\r\n /nix/store/jr1ywzriqw9labw6flr8j9b78w0in11d-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/jr1ywzriqw9labw6flr8j9b78w0in11d-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/h8lf018lfkq58qr6fdjabnwln8bi8m5k-stdenv-linux' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.108, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336820.af0a9bc0e53, unstable-22.05pre366144.bc4b9eef3ce\"`\r\n - channels(matthias): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167343/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167245","id":1192383498,"node_id":"I_kwDOAEVQ_M5HElQK","number":167245,"title":"whoogle-search","user":{"login":"seberm","id":212597,"node_id":"MDQ6VXNlcjIxMjU5Nw==","avatar_url":"https://avatars.githubusercontent.com/u/212597?v=4","gravatar_id":"","url":"https://api.github.com/users/seberm","html_url":"https://github.com/seberm","followers_url":"https://api.github.com/users/seberm/followers","following_url":"https://api.github.com/users/seberm/following{/other_user}","gists_url":"https://api.github.com/users/seberm/gists{/gist_id}","starred_url":"https://api.github.com/users/seberm/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/seberm/subscriptions","organizations_url":"https://api.github.com/users/seberm/orgs","repos_url":"https://api.github.com/users/seberm/repos","events_url":"https://api.github.com/users/seberm/events{/privacy}","received_events_url":"https://api.github.com/users/seberm/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-04T22:33:01Z","updated_at":"2022-04-04T22:33:01Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nA self-hosted, ad-free, privacy-respecting metasearch engine.\r\n\r\n**Metadata**\r\n* homepage URL: https://github.com/benbusby/whoogle-search\r\n* source URL: https://github.com/benbusby/whoogle-search\r\n* license: mit\r\n* platforms: unix, linux, ... maybe more\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167245/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167226","id":1192249588,"node_id":"I_kwDOAEVQ_M5HEEj0","number":167226,"title":"texlive: cannot handle cyclic dependencies","user":{"login":"xworld21","id":1962985,"node_id":"MDQ6VXNlcjE5NjI5ODU=","avatar_url":"https://avatars.githubusercontent.com/u/1962985?v=4","gravatar_id":"","url":"https://api.github.com/users/xworld21","html_url":"https://github.com/xworld21","followers_url":"https://api.github.com/users/xworld21/followers","following_url":"https://api.github.com/users/xworld21/following{/other_user}","gists_url":"https://api.github.com/users/xworld21/gists{/gist_id}","starred_url":"https://api.github.com/users/xworld21/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/xworld21/subscriptions","organizations_url":"https://api.github.com/users/xworld21/orgs","repos_url":"https://api.github.com/users/xworld21/repos","events_url":"https://api.github.com/users/xworld21/events{/privacy}","received_events_url":"https://api.github.com/users/xworld21/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1236941869,"node_id":"MDU6TGFiZWwxMjM2OTQxODY5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20TeX","name":"6.topic: TeX","color":"fef2c0","default":false,"description":"Issues regarding texlive and TeX in general"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-04T20:00:55Z","updated_at":"2022-04-04T20:04:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe latest TeX Live has a cyclic dependency between two packages (`ctex` and `xecjk`). The current `texlive` cannot handle it and ends up in an infinite recursion. The code should be made more robust to deal with this cases (and we might as well make it more efficient).\r\n\r\n### Additional context\r\nWhy the circular dependency exists: https://tug.org/pipermail/tex-live/2022-January/047648.html\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@veprbl \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167226/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167214","id":1192140505,"node_id":"I_kwDOAEVQ_M5HDp7Z","number":167214,"title":"Packaging request: melange vimPlugin","user":{"login":"Zaechus","id":19353212,"node_id":"MDQ6VXNlcjE5MzUzMjEy","avatar_url":"https://avatars.githubusercontent.com/u/19353212?v=4","gravatar_id":"","url":"https://api.github.com/users/Zaechus","html_url":"https://github.com/Zaechus","followers_url":"https://api.github.com/users/Zaechus/followers","following_url":"https://api.github.com/users/Zaechus/following{/other_user}","gists_url":"https://api.github.com/users/Zaechus/gists{/gist_id}","starred_url":"https://api.github.com/users/Zaechus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Zaechus/subscriptions","organizations_url":"https://api.github.com/users/Zaechus/orgs","repos_url":"https://api.github.com/users/Zaechus/repos","events_url":"https://api.github.com/users/Zaechus/events{/privacy}","received_events_url":"https://api.github.com/users/Zaechus/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-04T18:12:47Z","updated_at":"2022-04-04T18:12:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nWarm color scheme for Neovim and beyond\r\n\r\n**Metadata**\r\n\r\n* homepage URL: [melange](https://github.com/savq/melange)\r\n* source URL: [github.com/savq/melange](https://github.com/savq/melange)\r\n* license: mit\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167214/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167180","id":1191798095,"node_id":"I_kwDOAEVQ_M5HCWVP","number":167180,"title":"NVIDIA Proprietary driver missing nvidia-bug-report.sh script","user":{"login":"starcraft66","id":1858154,"node_id":"MDQ6VXNlcjE4NTgxNTQ=","avatar_url":"https://avatars.githubusercontent.com/u/1858154?v=4","gravatar_id":"","url":"https://api.github.com/users/starcraft66","html_url":"https://github.com/starcraft66","followers_url":"https://api.github.com/users/starcraft66/followers","following_url":"https://api.github.com/users/starcraft66/following{/other_user}","gists_url":"https://api.github.com/users/starcraft66/gists{/gist_id}","starred_url":"https://api.github.com/users/starcraft66/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/starcraft66/subscriptions","organizations_url":"https://api.github.com/users/starcraft66/orgs","repos_url":"https://api.github.com/users/starcraft66/repos","events_url":"https://api.github.com/users/starcraft66/events{/privacy}","received_events_url":"https://api.github.com/users/starcraft66/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-04T13:31:25Z","updated_at":"2022-04-04T18:55:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI want to report an NVIDIA driver bug to nvidia's forums and they require users to submit a log file generated by a script called `nvidia-bug-report.sh` included in their proprietary driver package, however the nix derviation for the drivers doesn't seem to include this script.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable nvidia proprietary driver\r\n2. Try running `nvidia-bug-report.sh`\r\n\r\n### Expected behavior\r\nA log file is created\r\n\r\n### Notify maintainers\r\n@jonringer \r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.18, NixOS, 22.05 (Quokka), 22.05.20220403.1ddbc47`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"\"`\r\n - channels(tristan): `\"\"`\r\n - nixpkgs: `/nix/store/8qg31y2v1pn81305kmcqadna7rp6g22w-6lqy3gmi8ajsmljbhsvgx4gbk55152zk-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167180/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167179","id":1191793920,"node_id":"I_kwDOAEVQ_M5HCVUA","number":167179,"title":"bottles: creating a non-custom bottle gets stuck on \"Setting Windows version…\"","user":{"login":"piousdeer","id":31318219,"node_id":"MDQ6VXNlcjMxMzE4MjE5","avatar_url":"https://avatars.githubusercontent.com/u/31318219?v=4","gravatar_id":"","url":"https://api.github.com/users/piousdeer","html_url":"https://github.com/piousdeer","followers_url":"https://api.github.com/users/piousdeer/followers","following_url":"https://api.github.com/users/piousdeer/following{/other_user}","gists_url":"https://api.github.com/users/piousdeer/gists{/gist_id}","starred_url":"https://api.github.com/users/piousdeer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piousdeer/subscriptions","organizations_url":"https://api.github.com/users/piousdeer/orgs","repos_url":"https://api.github.com/users/piousdeer/repos","events_url":"https://api.github.com/users/piousdeer/events{/privacy}","received_events_url":"https://api.github.com/users/piousdeer/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-04T13:28:30Z","updated_at":"2022-04-04T15:29:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCreating a \"gaming\" or an \"application\" bottle gets stuck on \"Setting Windows version…\"\r\n\r\nWhat Bottles shows:\r\n```\r\nGenerating bottle configuration…\r\nThe WINE config is being updated…\r\nWINE config updated!\r\nRunning as Flatpak, sandboxing userdir…\r\nSandboxing userdir…\r\nSetting Windows version…\r\n```\r\nCommand line log:\r\n```\r\n(14:26:53) INFO Performing Bottles checks... \r\n(14:26:53) INFO Dxvks found:\r\n\t - dxvk-1.10.1\r\n \r\n(14:26:53) INFO Vkd3ds found:\r\n\t - vkd3d-proton-2.6\r\n \r\n(14:26:53) INFO Nvapis found:\r\n\t - dxvk-nvapi-v0.5.3\r\n \r\n(14:26:53) INFO Latencyflexs found:\r\n\t - latencyflex-v0.1.0\r\n \r\n(14:26:53) INFO Runners found:\r\n\t - sys-wine-7.0\r\n\t - caffe-7.5\r\n \r\n(14:26:54) INFO Bottles Started! \r\n(14:27:08) INFO Generating bottle configuration… \r\n(14:27:08) INFO Using WINE Runtime tool -- send_status(-i) \r\nwineserver: using server-side synchronization.\r\nwine: could not load kernel32.dll, status c0000135\r\n(14:27:09) INFO Setting Windows version… \r\n(14:27:09) INFO Removing Value: [HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion] from Key: [SubVersionNumber] in games registry \r\n(14:27:09) INFO Using WINE Registry CLI -- remove\r\n0078:err:environ:run_wineboot boot event wait timed out\r\nwine: could not load kernel32.dll, status c0000135\r\n(14:32:09) INFO \r\n(14:32:09) INFO Removing Value: [HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion] from Key: [VersionNumber] in games registry \r\n(14:32:10) INFO Using WINE Registry CLI -- remove\r\n```\r\nThe last 5 lines repeat every 5 minutes.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Bottles via home-manager\r\n2. Try to create a \"gaming\" or an \"application\" bottle\r\n\r\n### Additional context\r\nThis issue is not present in the Flatpak version. After restarting Bottles, the bottle shows up as damaged. Attempting to repair it will make it show up as a \"custom\" bottle and also generate 2 more damaged bottles named \"dosdevices\" and \"drive_c\".\r\n\r\n### Notify maintainers\r\n@bloomvdomino\r\n@psydvl\r\n@SCOTT-HAMILTON\r\n\r\n### Metadata\r\n\r\n```console\r\nv@leginix ~> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 22.05 (Quokka), 22.05pre365028.710fed5a248`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(v): `\"home-manager-21.11.tar.gz\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167179/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167177","id":1191772687,"node_id":"I_kwDOAEVQ_M5HCQIP","number":167177,"title":"azure-cli: No module named 'azure.keyvault.keys'","user":{"login":"peterromfeldhk","id":5515707,"node_id":"MDQ6VXNlcjU1MTU3MDc=","avatar_url":"https://avatars.githubusercontent.com/u/5515707?v=4","gravatar_id":"","url":"https://api.github.com/users/peterromfeldhk","html_url":"https://github.com/peterromfeldhk","followers_url":"https://api.github.com/users/peterromfeldhk/followers","following_url":"https://api.github.com/users/peterromfeldhk/following{/other_user}","gists_url":"https://api.github.com/users/peterromfeldhk/gists{/gist_id}","starred_url":"https://api.github.com/users/peterromfeldhk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterromfeldhk/subscriptions","organizations_url":"https://api.github.com/users/peterromfeldhk/orgs","repos_url":"https://api.github.com/users/peterromfeldhk/repos","events_url":"https://api.github.com/users/peterromfeldhk/events{/privacy}","received_events_url":"https://api.github.com/users/peterromfeldhk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-04T13:14:13Z","updated_at":"2022-04-04T15:27:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n```console\r\n$ az keyvault key show --name my-vault-key --vault-name my-vault\r\nThe command failed with an unexpected error. Here is the traceback:\r\nNo module named 'azure.keyvault.keys'\r\nTraceback (most recent call last):\r\n File \"/nix/store/67nbrn8qn0d9xph46dqr8z9mv0k6vlrx-python3.9-knack-0.8.2/lib/python3.9/site-packages/knack/cli.py\", line 231, in invoke\r\n cmd_result = self.invocation.execute(args)\r\n File \"/nix/store/wg5mcdzvnwp1nr9wma44lydc9hyznlm4-python3.9-azure-cli-core-2.30.0/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 556, in execute\r\n self.commands_loader.load_arguments(command)\r\n File \"/nix/store/wg5mcdzvnwp1nr9wma44lydc9hyznlm4-python3.9-azure-cli-core-2.30.0/lib/python3.9/site-packages/azure/cli/core/__init__.py\", line 517, in load_arguments\r\n self.command_table[command].load_arguments() # this loads the arguments via reflection\r\n File \"/nix/store/wg5mcdzvnwp1nr9wma44lydc9hyznlm4-python3.9-azure-cli-core-2.30.0/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 313, in load_arguments\r\n super(AzCliCommand, self).load_arguments()\r\n File \"/nix/store/67nbrn8qn0d9xph46dqr8z9mv0k6vlrx-python3.9-knack-0.8.2/lib/python3.9/site-packages/knack/commands.py\", line 104, in load_arguments\r\n cmd_args = self.arguments_loader()\r\n File \"/nix/store/gcgvpdybnsim7i8kka4ndc4f71qhbcqs-python3.9-azure-cli-2.30.0/lib/python3.9/site-packages/azure/cli/command_modules/keyvault/_command_type.py\", line 75, in keyvault_arguments_loader\r\n op = get_op_handler()\r\n File \"/nix/store/gcgvpdybnsim7i8kka4ndc4f71qhbcqs-python3.9-azure-cli-2.30.0/lib/python3.9/site-packages/azure/cli/command_modules/keyvault/_command_type.py\", line 72, in get_op_handler\r\n return self.command_loader.get_op_handler(operations_tmpl.format(method_name))\r\n File \"/nix/store/wg5mcdzvnwp1nr9wma44lydc9hyznlm4-python3.9-azure-cli-core-2.30.0/lib/python3.9/site-packages/azure/cli/core/__init__.py\", line 894, in get_op_handler\r\n op = import_module(mod_to_import)\r\n File \"/nix/store/ghkj7bcqraixj20qafwcpj0jwx56awda-python3-3.9.6/lib/python3.9/importlib/__init__.py\", line 127, in import_module\r\n return _bootstrap._gcd_import(name[level:], package, level)\r\n File \"<frozen importlib._bootstrap>\", line 1030, in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 1007, in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 972, in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 228, in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap>\", line 1030, in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 1007, in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 984, in _find_and_load_unlocked\r\nModuleNotFoundError: No module named 'azure.keyvault.keys'\r\n```\r\n\r\n### Steps To Reproduce\r\nthe simplest way to reproduce is to add \"azure.keyvault.keys\" to `pythonImportsCheck` in `default.nix`\r\n\r\n### Expected behavior\r\nNo exception\r\n\r\n### Additional context\r\ni was able to get it to work by adding \"azure.keyvault\" to `pythonNamespaces` for `azure-keyvault` in `python-packages.nix`\r\nbut then other commands stopped working:\r\n```console\r\n$ az keyvault key list -n my-vault -otable\r\nThe command failed with an unexpected error. Here is the traceback:\r\ncannot import name 'KeyVaultAuthentication' from 'azure.keyvault' (unknown location)\r\nTraceback (most recent call last):\r\n File \"/nix/store/h2r8lj1s2igzhmxzlqi3gxc0z6m0hfsn-python3.9-knack-0.9.0/lib/python3.9/site-packages/knack/cli.py\", line 231, in invoke\r\n cmd_result = self.invocation.execute(args)\r\n File \"/nix/store/7k9q5rmbxib90f4ncip5ckgjgcyfx05d-python3.9-azure-cli-core-2.34.1/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 658, in execute\r\n raise ex\r\n File \"/nix/store/7k9q5rmbxib90f4ncip5ckgjgcyfx05d-python3.9-azure-cli-core-2.34.1/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 721, in _run_jobs_serially\r\n results.append(self._run_job(expanded_arg, cmd_copy))\r\n File \"/nix/store/7k9q5rmbxib90f4ncip5ckgjgcyfx05d-python3.9-azure-cli-core-2.34.1/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 692, in _run_job\r\n result = cmd_copy(params)\r\n File \"/nix/store/7k9q5rmbxib90f4ncip5ckgjgcyfx05d-python3.9-azure-cli-core-2.34.1/lib/python3.9/site-packages/azure/cli/core/commands/__init__.py\", line 328, in __call__\r\n return self.handler(*args, **kwargs)\r\n File \"/nix/store/j0p1n4aq2d7swpmchk7rjn7nh5y9yzn6-python3.9-azure-cli-2.34.1/lib/python3.9/site-packages/azure/cli/command_modules/keyvault/_command_type.py\", line 100, in keyvault_command_handler\r\n client = client_factory(command_args['cmd'].cli_ctx, command_args)\r\n File \"/nix/store/j0p1n4aq2d7swpmchk7rjn7nh5y9yzn6-python3.9-azure-cli-2.34.1/lib/python3.9/site-packages/azure/cli/command_modules/keyvault/_client_factory.py\", line 147, in keyvault_data_plane_factory\r\n from azure.keyvault import KeyVaultAuthentication, KeyVaultClient\r\nImportError: cannot import name 'KeyVaultAuthentication' from 'azure.keyvault' (unknown location)\r\n```\r\n\r\n### Notify maintainers\r\n@jonringer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager, nixos-21.11.336811.0aac710801a\"`\r\n - channels(peter): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167177/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167130","id":1191260666,"node_id":"I_kwDOAEVQ_M5HATH6","number":167130,"title":"Add TrueType font for Lao language","user":{"login":"serge-belov","id":38824235,"node_id":"MDQ6VXNlcjM4ODI0MjM1","avatar_url":"https://avatars.githubusercontent.com/u/38824235?v=4","gravatar_id":"","url":"https://api.github.com/users/serge-belov","html_url":"https://github.com/serge-belov","followers_url":"https://api.github.com/users/serge-belov/followers","following_url":"https://api.github.com/users/serge-belov/following{/other_user}","gists_url":"https://api.github.com/users/serge-belov/gists{/gist_id}","starred_url":"https://api.github.com/users/serge-belov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/serge-belov/subscriptions","organizations_url":"https://api.github.com/users/serge-belov/orgs","repos_url":"https://api.github.com/users/serge-belov/repos","events_url":"https://api.github.com/users/serge-belov/events{/privacy}","received_events_url":"https://api.github.com/users/serge-belov/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-04T05:07:21Z","updated_at":"2022-04-04T05:07:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nThe package contains TrueType fonts for Lao language.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: http://prdownloads.sourceforge.net/laofoss/\r\n* source URL: http://deb.debian.org/debian/pool/main/f/fonts-lao/fonts-lao_0.0.20060226.orig.tar.xz\r\n* license: gpl2+\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167130/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167091","id":1191058002,"node_id":"I_kwDOAEVQ_M5G_hpS","number":167091,"title":"LightDM not following default shell","user":{"login":"Narice","id":31109099,"node_id":"MDQ6VXNlcjMxMTA5MDk5","avatar_url":"https://avatars.githubusercontent.com/u/31109099?v=4","gravatar_id":"","url":"https://api.github.com/users/Narice","html_url":"https://github.com/Narice","followers_url":"https://api.github.com/users/Narice/followers","following_url":"https://api.github.com/users/Narice/following{/other_user}","gists_url":"https://api.github.com/users/Narice/gists{/gist_id}","starred_url":"https://api.github.com/users/Narice/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Narice/subscriptions","organizations_url":"https://api.github.com/users/Narice/orgs","repos_url":"https://api.github.com/users/Narice/repos","events_url":"https://api.github.com/users/Narice/events{/privacy}","received_events_url":"https://api.github.com/users/Narice/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1207068537,"node_id":"MDU6TGFiZWwxMjA3MDY4NTM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20pantheon","name":"6.topic: pantheon","color":"fef2c0","default":false,"description":"The Pantheon desktop environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-04-03T22:00:38Z","updated_at":"2022-04-05T03:16:05Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nLightDM is not following the default shell that is set in the nixos configuration.\r\nThe login shell is hardcoded as `bash` instead of using the default user shell of the first shell in `environment.shells`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. use lightdm\r\n2. start a session\r\n3. check with htop the login shell that was used: bash\r\n4. an alternative is to check the `/etc/passwd` file to see the user's assigned shell\r\n\r\n### Expected behavior\r\nLightDM should follow the default user shell or the first shell in `environment.shells` to avoid confusion for the user.\r\nThe user should not have to search through the source code to find out that he has to manually set `lightdm` user's shell to `pkgs.zsh`.\r\nFurthermore, the user must use `lib.mkForce` to not use conflict.\r\nHere is the relevant line (311):\r\nhttps://github.com/NixOS/nixpkgs/blob/0aac710801aec4ba545527cf41a5706028fe6271/nixos/modules/services/x11/display-managers/lightdm.nix#L307-L312\r\n\r\n### Additional context\r\nit stems from a change that needed to be reverted after a pantheon upgrade:\r\nhttps://github.com/NixOS/nixpkgs/commit/c134f6443a6a595b665f749fb79df8cd2519c029\r\n\r\n### Notify maintainers\r\n@davidak\r\nI won't ping worldofpeace as if I remember correctly, he left the project :sparkles: :stuck_out_tongue_winking_eye: \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - nixpkgs: `/nix/store/d9wpzgyjlpw1424kw2lyilah6690fnk3-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167091/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167068","id":1191017754,"node_id":"I_kwDOAEVQ_M5G_X0a","number":167068,"title":"CUDA in 22.05","user":{"login":"SomeoneSerge","id":9720532,"node_id":"MDQ6VXNlcjk3MjA1MzI=","avatar_url":"https://avatars.githubusercontent.com/u/9720532?v=4","gravatar_id":"","url":"https://api.github.com/users/SomeoneSerge","html_url":"https://github.com/SomeoneSerge","followers_url":"https://api.github.com/users/SomeoneSerge/followers","following_url":"https://api.github.com/users/SomeoneSerge/following{/other_user}","gists_url":"https://api.github.com/users/SomeoneSerge/gists{/gist_id}","starred_url":"https://api.github.com/users/SomeoneSerge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SomeoneSerge/subscriptions","organizations_url":"https://api.github.com/users/SomeoneSerge/orgs","repos_url":"https://api.github.com/users/SomeoneSerge/repos","events_url":"https://api.github.com/users/SomeoneSerge/events{/privacy}","received_events_url":"https://api.github.com/users/SomeoneSerge/received_events","type":"User","site_admin":false},"labels":[{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":1,"created_at":"2022-04-03T19:09:13Z","updated_at":"2022-04-18T18:56:26Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nThis is a aggregate issue to track (the selected subset of) that state of CUDA in master before the 22-05 release.\r\nIt's concern is the world evaluated with `{ config.cudaSupport = true; config.allowUnfree = true; }` \r\n\r\n- The release will see the following changes that affect how we package and use cuda:\r\n - [x] The new scope-based interface for consuming cuda-related packages, introduced together with the redistributable cuda packages in https://github.com/NixOS/nixpkgs/pull/167016/\r\n - [ ] cudnn drops its `propagatedBuildInputs` which used to include `cudatoolkit` and cause a lot of obscure errors. Happens in: https://github.com/NixOS/nixpkgs/pull/168748\r\n- We currently have the following failures (we might not fix them before the release, but back-port later) \r\n \r\n - [ ] As of (at least) 2022-04-11 jax is failing on master, cf. [jax: tests/test_sparse.py](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F53190dyjcf00cl0rja4ficaghlxn8ab9-python3.9-jax-0.3.5.drv/log?via-job=f167030f-e041-4191-95b7-74c71afd5aad)\r\n - [ ] `test_sparse.py` has been fixed upstream, but blocked in nixpkgs because of: https://github.com/NixOS/nixpkgs/issues/169148\r\n \r\n - [ ] [catboost](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2Flj1np2w0gmwnr45aq20lbf7dwjqmg3va-python3.10-catboost-0.24.4.drv/log?via-job=f167030f-e041-4191-95b7-74c71afd5aad)\r\n \r\n - [ ] As of (at least) 2022-04-11, [tensorflow-datasets is failing](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2Fsw770kmi645jczmwi21x5h9k16ara6nd-python3.9-tensorflow-datasets-4.5.2.drv/log?via-job=f167030f-e041-4191-95b7-74c71afd5aad), cf. https://github.com/NixOS/nixpkgs/issues/167445\r\n \r\n - [ ] [`xgboost`](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F87l72vpbkaxh1zixmrzd56lw4a6j9m80-xgboost-1.5.2.drv/log?via-job=ab473808-fd27-43d3-aa86-1e82235718e0)\r\n \r\n ```\r\n CMake Error at CMakeLists.txt:140 (message):\r\n `BUILD_WITH_CUDA_CUB` should be set to `ON` for CUDA >= 11.4\r\n ```\r\n \r\n ...and now it's https://github.com/NixOS/nixpkgs/issues/167931\r\n \r\n - [ ] `python39Packages.mxnet`\r\n CMake configurePhase [fails](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F6l39w83hvhr4y78dhv1v50y5ixjvk2vd-mxnet-1.8.0.drv/log?via-job=930fc1c2-1577-48e1-b532-c9252621fe60)\r\n \r\n Likely will be fixed in: https://github.com/NixOS/nixpkgs/pull/167250\r\n - [ ] `cholmod-extra`\r\n \r\n Tests [fail](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F46nw0nv4gr1q747rxpgkf2nhyc6lvxjf-cholmod-extra-1.2.0.drv/log?via-job=930fc1c2-1577-48e1-b532-c9252621fe60): too large residuals\r\n \r\n - [ ] `python3*Packages.chainer`\r\n \r\n Complains about [cupy version](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2Fgwfj4vnzag4lqrggg033pdggzyai1737-python3.9-chainer-7.8.1.drv/log?via-job=8db14681-ab92-465d-8355-575c55c32e12)\r\n \r\n Marked as broken in: https://github.com/NixOS/nixpkgs/pull/167250\r\n - [ ] `python310Packages.caffe`\r\n \r\n CMake configurePhase [fails](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F27crqg6g0z173cr380qcid5c8mrv0m87-caffe-1.0.drv/log?via-job=8db14681-ab92-465d-8355-575c55c32e12)\r\n - [x] `python39Packages.caffe`\r\n \r\n Fixed by: https://github.com/NixOS/nixpkgs/pull/166784/\r\n \r\n - [x] `blender`: failing dependency (opensubdiv)\r\n \r\n - [x] `opensubdiv`: [fails at cmake configurePhase](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F6q4a99a0ww0vzll8q6212xzrsbipp76z-opensubdiv-3.4.4.drv/log?via-job=930fc1c2-1577-48e1-b532-c9252621fe60)\r\n \r\n Likely will be fixed in: https://github.com/NixOS/nixpkgs/pull/167250\r\n \r\n - [x] Pytorch\r\n \r\n Cmake error: https://github.com/NixOS/nixpkgs/issues/166403\r\n Build error: https://github.com/NixOS/nixpkgs/issues/161843\r\n Fixed by: https://github.com/NixOS/nixpkgs/pull/166784/\r\n\r\n\r\ncc @NixOS/cuda-maintainers ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":1,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167068/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167065","id":1191014545,"node_id":"I_kwDOAEVQ_M5G_XCR","number":167065,"title":"Librewolf should support pgo","user":{"login":"squalus","id":36899624,"node_id":"MDQ6VXNlcjM2ODk5NjI0","avatar_url":"https://avatars.githubusercontent.com/u/36899624?v=4","gravatar_id":"","url":"https://api.github.com/users/squalus","html_url":"https://github.com/squalus","followers_url":"https://api.github.com/users/squalus/followers","following_url":"https://api.github.com/users/squalus/following{/other_user}","gists_url":"https://api.github.com/users/squalus/gists{/gist_id}","starred_url":"https://api.github.com/users/squalus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/squalus/subscriptions","organizations_url":"https://api.github.com/users/squalus/orgs","repos_url":"https://api.github.com/users/squalus/repos","events_url":"https://api.github.com/users/squalus/events{/privacy}","received_events_url":"https://api.github.com/users/squalus/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-03T18:56:24Z","updated_at":"2022-04-03T18:56:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Profile guided optimization was added for Firefox in #164646. It's disabled for Librewolf because it hung during the profiling step.\r\n\r\nI ran some tests to see what was causing this. If `remove-internal-plugin-certs.patch` is omitted, the hang doesn't happen. Not sure why.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167065/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167044","id":1190960703,"node_id":"I_kwDOAEVQ_M5G_J4_","number":167044,"title":"Get crystal 1.4.x in before 22.05 is frozen","user":{"login":"peterhoeg","id":722550,"node_id":"MDQ6VXNlcjcyMjU1MA==","avatar_url":"https://avatars.githubusercontent.com/u/722550?v=4","gravatar_id":"","url":"https://api.github.com/users/peterhoeg","html_url":"https://github.com/peterhoeg","followers_url":"https://api.github.com/users/peterhoeg/followers","following_url":"https://api.github.com/users/peterhoeg/following{/other_user}","gists_url":"https://api.github.com/users/peterhoeg/gists{/gist_id}","starred_url":"https://api.github.com/users/peterhoeg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterhoeg/subscriptions","organizations_url":"https://api.github.com/users/peterhoeg/orgs","repos_url":"https://api.github.com/users/peterhoeg/repos","events_url":"https://api.github.com/users/peterhoeg/events{/privacy}","received_events_url":"https://api.github.com/users/peterhoeg/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"peterhoeg","id":722550,"node_id":"MDQ6VXNlcjcyMjU1MA==","avatar_url":"https://avatars.githubusercontent.com/u/722550?v=4","gravatar_id":"","url":"https://api.github.com/users/peterhoeg","html_url":"https://github.com/peterhoeg","followers_url":"https://api.github.com/users/peterhoeg/followers","following_url":"https://api.github.com/users/peterhoeg/following{/other_user}","gists_url":"https://api.github.com/users/peterhoeg/gists{/gist_id}","starred_url":"https://api.github.com/users/peterhoeg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterhoeg/subscriptions","organizations_url":"https://api.github.com/users/peterhoeg/orgs","repos_url":"https://api.github.com/users/peterhoeg/repos","events_url":"https://api.github.com/users/peterhoeg/events{/privacy}","received_events_url":"https://api.github.com/users/peterhoeg/received_events","type":"User","site_admin":false},"assignees":[{"login":"peterhoeg","id":722550,"node_id":"MDQ6VXNlcjcyMjU1MA==","avatar_url":"https://avatars.githubusercontent.com/u/722550?v=4","gravatar_id":"","url":"https://api.github.com/users/peterhoeg","html_url":"https://github.com/peterhoeg","followers_url":"https://api.github.com/users/peterhoeg/followers","following_url":"https://api.github.com/users/peterhoeg/following{/other_user}","gists_url":"https://api.github.com/users/peterhoeg/gists{/gist_id}","starred_url":"https://api.github.com/users/peterhoeg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterhoeg/subscriptions","organizations_url":"https://api.github.com/users/peterhoeg/orgs","repos_url":"https://api.github.com/users/peterhoeg/repos","events_url":"https://api.github.com/users/peterhoeg/events{/privacy}","received_events_url":"https://api.github.com/users/peterhoeg/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-04-03T15:22:08Z","updated_at":"2022-04-10T12:14:51Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Cc @NixOS/crystal-lang ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167044/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167034","id":1190920389,"node_id":"I_kwDOAEVQ_M5G_ADF","number":167034,"title":"gitit module: repair or drop","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":290122996,"node_id":"MDU6TGFiZWwyOTAxMjI5OTY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20clean-up","name":"9.needs: clean-up","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-04-03T12:42:34Z","updated_at":"2022-04-13T09:56:14Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"This is essentially a repost of [this discourse topic](https://discourse.nixos.org/t/gitit-module-keep-or-ditch/3921): We have a NixOS module for gitit in nixpkgs which [was deactivated](https://github.com/nixos/nixpkgs/commit/122d5e497e6d) due to its impact on evaluation performance. It continued to be shipped, so that one could include it manually, but it has bitrotted since then. One thing I noticed is that it makes an incorrect assumption where gitit's data files would be located, but there may be more issues.\r\n\r\nIt would be great if we could either find someone willing to fix the module up or drop it altogether.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167034/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025/events","html_url":"https://github.com/NixOS/nixpkgs/issues/167025","id":1190903472,"node_id":"I_kwDOAEVQ_M5G-76w","number":167025,"title":"22.05 Feature Freeze","user":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"labels":[{"id":2392802829,"node_id":"MDU6TGFiZWwyMzkyODAyODI5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20release%20process","name":"6.topic: release process","color":"4cd3ba","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"Mic92","id":96200,"node_id":"MDQ6VXNlcjk2MjAw","avatar_url":"https://avatars.githubusercontent.com/u/96200?v=4","gravatar_id":"","url":"https://api.github.com/users/Mic92","html_url":"https://github.com/Mic92","followers_url":"https://api.github.com/users/Mic92/followers","following_url":"https://api.github.com/users/Mic92/following{/other_user}","gists_url":"https://api.github.com/users/Mic92/gists{/gist_id}","starred_url":"https://api.github.com/users/Mic92/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Mic92/subscriptions","organizations_url":"https://api.github.com/users/Mic92/orgs","repos_url":"https://api.github.com/users/Mic92/repos","events_url":"https://api.github.com/users/Mic92/events{/privacy}","received_events_url":"https://api.github.com/users/Mic92/received_events","type":"User","site_admin":false},"assignees":[{"login":"Mic92","id":96200,"node_id":"MDQ6VXNlcjk2MjAw","avatar_url":"https://avatars.githubusercontent.com/u/96200?v=4","gravatar_id":"","url":"https://api.github.com/users/Mic92","html_url":"https://github.com/Mic92","followers_url":"https://api.github.com/users/Mic92/followers","following_url":"https://api.github.com/users/Mic92/following{/other_user}","gists_url":"https://api.github.com/users/Mic92/gists{/gist_id}","starred_url":"https://api.github.com/users/Mic92/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Mic92/subscriptions","organizations_url":"https://api.github.com/users/Mic92/orgs","repos_url":"https://api.github.com/users/Mic92/repos","events_url":"https://api.github.com/users/Mic92/events{/privacy}","received_events_url":"https://api.github.com/users/Mic92/received_events","type":"User","site_admin":false},{"login":"tomberek","id":178444,"node_id":"MDQ6VXNlcjE3ODQ0NA==","avatar_url":"https://avatars.githubusercontent.com/u/178444?v=4","gravatar_id":"","url":"https://api.github.com/users/tomberek","html_url":"https://github.com/tomberek","followers_url":"https://api.github.com/users/tomberek/followers","following_url":"https://api.github.com/users/tomberek/following{/other_user}","gists_url":"https://api.github.com/users/tomberek/gists{/gist_id}","starred_url":"https://api.github.com/users/tomberek/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tomberek/subscriptions","organizations_url":"https://api.github.com/users/tomberek/orgs","repos_url":"https://api.github.com/users/tomberek/repos","events_url":"https://api.github.com/users/tomberek/events{/privacy}","received_events_url":"https://api.github.com/users/tomberek/received_events","type":"User","site_admin":false},{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false}],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":45,"created_at":"2022-04-03T11:33:05Z","updated_at":"2022-04-29T14:19:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"It's time for another feature freeze!\r\n\r\nLet's clarify any blocking concerns for the 22.05 release in this thread, which will go live on May 30th.\r\nFeature Freeze issue of th previous release: #140168\r\nRelease Schedule: #165792\r\n\r\n**Edit**: I have crossed out subsystems that have responded that there are no blockers\r\n\r\nNix/nix-cli ecosystem: @Profpatsch @edolstra @grahamc @nbp\r\nMobile: @samueldr\r\n~~NixOS Modules / internals: @ericson2314 @infinisil @alyssais @roberth~~\r\n~~NixOS tests: @tfc~~\r\nMarketing: @garbas @tomberek\r\n~~Docs: @ryantm~~\r\nRelease: @NixOS/nixos-release-managers\r\nDarwin: @NixOS/darwin-maintainers\r\n\r\n~~BEAM: @NixOS/beam @minijackson~~\r\nC: @matthewbauer @mic92\r\nCoq: @CohenCyril @Zimmi48 @siraben @vbgl\r\n~~Dhall: @Gabriel439 @ehmry~~\r\n~~Emacs: @adisbladis~~\r\n~~Vim/Neovim: @jonringer @softinio @teto~~\r\nGo: @c00w @cstrahan @Frostman @kalbasit @mic92 @orivej @rvolosatovs @zowoq\r\nHaskell: @NixOS/haskell\r\n~~Python: @fridh @mweinelt @jonringer~~\r\nPerl: @stigtsp\r\n~~PHP: @NixOS/php @ma27~~\r\nRuby: @marsam\r\nRust: @andir @lnl7 @mic92 @zowoq\r\n~~R: @bcdarwin @jbedo~~\r\n\r\nBazel: @mboes @marsam @uri-canva @avdv @olebedev @groodt @aherrmann @ylecornec\r\nBlockchains: @mmahut @RaghavSood\r\nCinnamon: @mkg20001\r\n~~DockerTools: @roberth @utdemir~~\r\nGNOME: @NixOS/gnome @bobby285271 @dasj19 @maxeaubrey\r\n~~Pantheon: @NixOS/pantheon~~\r\nPodman: @NixOS/podman\r\nPostgreSQL: @thoughtpolice\r\nQt / KDE: @NixOS/qt-kde\r\nsystemd: @NixOS/systemd\r\n\r\nEveryone else: @NixOS/nixpkgs-committers @NixOS/release-engineers\r\n\r\nIf you think some subsystem/person/GitHub team should be added or removed for the next release, you can modify the list [here](https://github.com/NixOS/nixpkgs/blob/master/maintainers/team-list.nix#L17).\r\n\r\nNo issue is too big or too small, but let's remember that we are all working on the project voluntarily in our free time here, so let's focus on the issues that can be realistically addressed by release time. Thanks everyone!","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025/reactions","total_count":32,"+1":0,"-1":0,"laugh":0,"hooray":16,"confused":0,"heart":0,"rocket":11,"eyes":5},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/167025/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166953","id":1190701465,"node_id":"I_kwDOAEVQ_M5G-KmZ","number":166953,"title":"Noto-fonts: switch to variable fonts","user":{"login":"Mathnerd314","id":322214,"node_id":"MDQ6VXNlcjMyMjIxNA==","avatar_url":"https://avatars.githubusercontent.com/u/322214?v=4","gravatar_id":"","url":"https://api.github.com/users/Mathnerd314","html_url":"https://github.com/Mathnerd314","followers_url":"https://api.github.com/users/Mathnerd314/followers","following_url":"https://api.github.com/users/Mathnerd314/following{/other_user}","gists_url":"https://api.github.com/users/Mathnerd314/gists{/gist_id}","starred_url":"https://api.github.com/users/Mathnerd314/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Mathnerd314/subscriptions","organizations_url":"https://api.github.com/users/Mathnerd314/orgs","repos_url":"https://api.github.com/users/Mathnerd314/repos","events_url":"https://api.github.com/users/Mathnerd314/events{/privacy}","received_events_url":"https://api.github.com/users/Mathnerd314/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-04-02T18:06:38Z","updated_at":"2022-04-26T01:51:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThis is a follow up to https://github.com/NixOS/nixpkgs/pull/166600 and the comment in https://github.com/NixOS/nixpkgs/blob/a0a77f1c738384eb82560b9d359e27afb35c4dfc/pkgs/data/fonts/noto-fonts/default.nix#L34\r\n\r\nAFAICT, just like the variable fonts are best for CJK, they are the best version to use for all the other Noto fonts too. This is what [Fedora thinks](https://fedoraproject.org/wiki/Changes/VariableNotoFonts#Benefit_to_Fedora). The variable fonts save a lot of disk space (10.94MiB vs 1.02MiB for Sinhala) and provide all variations, as well as enabling custom font variations in software that supports them.\r\n\r\nI was wondering about hinting but it seems that all that's [happening](https://github.com/googlefonts/noto-source/blob/main/scripts/notobuilder.py#L46) is [ttfautohint](https://github.com/googlefonts/gftools/blob/0ede0eb58feeb0b44ad9ef9fb0ea7987a9b2b3ef/Lib/gftools/builder/autohint.py#L97). ttfautohint is built into FreeType so I think it gets run on Linux regardless for TTF fonts.\r\n\r\nNow, the Adobe CFF renderer for OTF is better than the TTF renderer, and ideally we would get OTF variable fonts like with CJK. But those aren't available at the moment.\r\n\r\nunhinted/slim-variable-ttf is a variable font with only 400 (Regular) through 700 (Bold) on the weight axis, prepared for Android system UI use ([script](https://github.com/googlefonts/noto-source/blob/main/misc_scripts/slimmer-vfs.sh#L20), [doc note](https://github.com/notofonts/noto-docs/issues/3)), it's smaller at 353 KB vs 1.03MB. Since we ship Light (300) in the main noto-fonts package I think we want the full range. Although Fedora [chose](https://src.fedoraproject.org/rpms/google-noto-fonts/blob/rawhide/f/google-noto-fonts.spec#_940) the slim, the savings from removing weights seems small IMO.\r\n\r\nI'm opening this now but I think we should wait a week or two before switching over the fonts, in case there is more fallout from the variable CJK switch.\r\n\r\n### Notify maintainers\r\ncc @midchildan since you've been writing all the patches recently","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166953/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166925","id":1190621608,"node_id":"I_kwDOAEVQ_M5G93Go","number":166925,"title":"xdg-desktop-portal: copy flatpak interfaces in and remove the libflatpak dep","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-02T12:41:17Z","updated_at":"2022-04-02T12:41:17Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI'm watching a bunch of ostree/flatpak stuff build and noticed it was xdp pulling it in.\r\n\r\nhttps://github.com/flatpak/xdg-desktop-portal/issues/296\r\n\r\nhttps://github.com/flatpak/xdg-desktop-portal/blob/9e00c2f7ed922128c344914b8670abc67cf55608/configure.ac#L52=\r\n\r\nIt seems like we could copy the interfaces from flatpak to xdp and then not have to depend on libflatpak as a buildInput directly.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166925/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166913","id":1190567035,"node_id":"I_kwDOAEVQ_M5G9px7","number":166913,"title":"Gnome language & locale settings are not applied","user":{"login":"demokritos","id":3399860,"node_id":"MDQ6VXNlcjMzOTk4NjA=","avatar_url":"https://avatars.githubusercontent.com/u/3399860?v=4","gravatar_id":"","url":"https://api.github.com/users/demokritos","html_url":"https://github.com/demokritos","followers_url":"https://api.github.com/users/demokritos/followers","following_url":"https://api.github.com/users/demokritos/following{/other_user}","gists_url":"https://api.github.com/users/demokritos/gists{/gist_id}","starred_url":"https://api.github.com/users/demokritos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/demokritos/subscriptions","organizations_url":"https://api.github.com/users/demokritos/orgs","repos_url":"https://api.github.com/users/demokritos/repos","events_url":"https://api.github.com/users/demokritos/events{/privacy}","received_events_url":"https://api.github.com/users/demokritos/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-02T09:01:20Z","updated_at":"2022-04-07T20:37:48Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI changed gnome language settings and re-logged in, but language and locale didn't change.\r\nIt seems that locale keeps to `i18n.defaultLocale`. `locale` command in a terminal prints only with that default locale.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. set `i18n.supportedLocales` to an array of multiple locales in `/etc/nixos/configuration.nix`\r\n2. nixos-rebuild switch\r\n3. change language to one of the supported locales in gnome settings\r\n4. re-log in\r\n\r\n### Expected behavior\r\nInterface language should be changed\r\n\r\n### Screenshots\r\n\r\nLanguage setting is English, but the actual interface is in Korean. \r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0-zen1, NixOS, 22.05 (Quokka), 22.05pre365028.710fed5a248`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(esrevinu): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166913/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166912","id":1190565589,"node_id":"I_kwDOAEVQ_M5G9pbV","number":166912,"title":"python39Packages.twisted fails to build on darwin","user":{"login":"polachok","id":94035,"node_id":"MDQ6VXNlcjk0MDM1","avatar_url":"https://avatars.githubusercontent.com/u/94035?v=4","gravatar_id":"","url":"https://api.github.com/users/polachok","html_url":"https://github.com/polachok","followers_url":"https://api.github.com/users/polachok/followers","following_url":"https://api.github.com/users/polachok/following{/other_user}","gists_url":"https://api.github.com/users/polachok/gists{/gist_id}","starred_url":"https://api.github.com/users/polachok/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/polachok/subscriptions","organizations_url":"https://api.github.com/users/polachok/orgs","repos_url":"https://api.github.com/users/polachok/repos","events_url":"https://api.github.com/users/polachok/events{/privacy}","received_events_url":"https://api.github.com/users/polachok/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-04-02T08:56:34Z","updated_at":"2022-04-07T20:37:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\npython39Packages.twisted fails to build on darwin\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n`nix-env -iA nixpkgs.python39Packages.twisted`\r\n\r\n### Expected behavior\r\ninstall succeeds\r\n\r\n### Additional context\r\n```\r\nnix-env -iA nixpkgs.python39Packages.twisted\r\ninstalling 'python3.9-Twisted-21.7.0'\r\nthis derivation will be built:\r\n /nix/store/8mjr8ynaz4i6a8vz1qlmj1qzvl4ccwsd-python3.9-Twisted-21.7.0.drv\r\nbuilding '/nix/store/8mjr8ynaz4i6a8vz1qlmj1qzvl4ccwsd-python3.9-Twisted-21.7.0.drv'...\r\nSourcing python-remove-tests-dir-hook\r\nSourcing python-catch-conflicts-hook.sh\r\nSourcing python-remove-bin-bytecode-hook.sh\r\nSourcing setuptools-build-hook\r\nUsing setuptoolsBuildPhase\r\nUsing setuptoolsShellHook\r\nSourcing pip-install-hook\r\nUsing pipInstallPhase\r\nSourcing python-imports-check-hook.sh\r\nUsing pythonImportsCheckPhase\r\nSourcing python-namespaces-hook\r\nunpacking sources\r\nunpacking source archive /nix/store/vjxb8j9kpcmzvlm9crrfc38vzzsxcn3k-Twisted-21.7.0.tar.gz\r\nsource root is Twisted-21.7.0\r\nsetting SOURCE_DATE_EPOCH to timestamp 1627461731 of file Twisted-21.7.0/setup.cfg\r\npatching sources\r\napplying patch /nix/store/4fscdq7nf4mzb07gc2h9c9sf3z6a8w8l-CVE-2022-21712.patch\r\npatching file src/twisted/web/client.py\r\nHunk #1 FAILED at 10.\r\nHunk #2 FAILED at 25.\r\nHunk #3 succeeded at 2109 (offset -1 lines).\r\nHunk #4 succeeded at 2132 (offset -1 lines).\r\nHunk #5 succeeded at 2154 (offset -1 lines).\r\nHunk #6 succeeded at 2207 (offset -1 lines).\r\n2 out of 6 hunks FAILED -- saving rejects to file src/twisted/web/client.py.rej\r\npatching file src/twisted/web/client.py\r\nHunk #1 FAILED at 10.\r\nHunk #2 FAILED at 24.\r\nHunk #3 succeeded at 2110 (offset 10 lines).\r\nHunk #4 succeeded at 2165 (offset 10 lines).\r\n2 out of 4 hunks FAILED -- saving rejects to file src/twisted/web/client.py.rej\r\npatching file src/twisted/web/iweb.py\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 FAILED at 5.\r\nHunk #2 FAILED at 32.\r\nHunk #3 FAILED at 52.\r\nHunk #4 succeeded at 2580 (offset -7 lines).\r\nHunk #5 succeeded at 2622 (offset -7 lines).\r\nHunk #6 succeeded at 2676 (offset -7 lines).\r\nHunk #7 succeeded at 2686 (offset -7 lines).\r\nHunk #8 succeeded at 2713 (offset -7 lines).\r\n3 out of 8 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 succeeded at 2749 (offset -9 lines).\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 succeeded at 2627 (offset -9 lines).\r\nHunk #2 succeeded at 2657 (offset -9 lines).\r\nHunk #3 succeeded at 2719 (offset -9 lines).\r\nHunk #4 succeeded at 2730 (offset -9 lines).\r\nHunk #5 succeeded at 2750 (offset -9 lines).\r\nHunk #6 succeeded at 2999 (offset -9 lines).\r\nHunk #7 succeeded at 3037 (offset -9 lines).\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 FAILED at 5.\r\nHunk #2 FAILED at 38.\r\nHunk #3 FAILED at 50.\r\nHunk #4 succeeded at 2665 (offset -9 lines).\r\nHunk #5 succeeded at 2717 (offset -9 lines).\r\nHunk #6 succeeded at 2767 (offset -9 lines).\r\n3 out of 6 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 FAILED at 5.\r\nHunk #2 FAILED at 33.\r\nHunk #3 succeeded at 102 (offset -8 lines).\r\nHunk #4 succeeded at 2588 (offset -9 lines).\r\nHunk #5 succeeded at 2624 (offset -9 lines).\r\nHunk #6 succeeded at 2713 (offset -9 lines).\r\nHunk #7 succeeded at 2986 (offset -9 lines).\r\nHunk #8 succeeded at 3023 (offset -9 lines).\r\n2 out of 8 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 FAILED at 5.\r\nHunk #2 FAILED at 29.\r\nHunk #3 succeeded at 2986 (offset 20 lines).\r\nHunk #4 succeeded at 3026 (offset 20 lines).\r\n2 out of 4 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\npatching file src/twisted/web/test/test_agent.py\r\nHunk #1 FAILED at 8.\r\nHunk #2 FAILED at 70.\r\n2 out of 2 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\npatching file src/twisted/topfiles/10294.bugfix\r\nerror: builder for '/nix/store/8mjr8ynaz4i6a8vz1qlmj1qzvl4ccwsd-python3.9-Twisted-21.7.0.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > Hunk #1 FAILED at 5.\r\n > Hunk #2 FAILED at 29.\r\n > Hunk #3 succeeded at 2986 (offset 20 lines).\r\n > Hunk #4 succeeded at 3026 (offset 20 lines).\r\n > 2 out of 4 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\n > patching file src/twisted/web/test/test_agent.py\r\n > Hunk #1 FAILED at 8.\r\n > Hunk #2 FAILED at 70.\r\n > 2 out of 2 hunks FAILED -- saving rejects to file src/twisted/web/test/test_agent.py.rej\r\n > patching file src/twisted/topfiles/10294.bugfix\r\n For full logs, run 'nix log /nix/store/8mjr8ynaz4i6a8vz1qlmj1qzvl4ccwsd-python3.9-Twisted-21.7.0.drv'.\r\n```\r\n\r\n### Notify maintainers\r\n@mweinelt \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 12.3`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"home-manager-21.11, nixpkgs-21.11.336755.efea022d6fe, nixpkgs-unstable-22.05pre363562.30d3d79b7d3\"`\r\n - channels(plhk): `\"home-manager-21.11, nixpkgs-21.11.336755.efea022d6fe, nixpkgs-unstable-22.05pre363562.30d3d79b7d3\"`\r\n - nixpkgs: `/Users/plhk/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166912/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166911","id":1190564798,"node_id":"I_kwDOAEVQ_M5G9pO-","number":166911,"title":"cabal repl with `-fobject-code` on M1 broken","user":{"login":"zwilias","id":1038427,"node_id":"MDQ6VXNlcjEwMzg0Mjc=","avatar_url":"https://avatars.githubusercontent.com/u/1038427?v=4","gravatar_id":"","url":"https://api.github.com/users/zwilias","html_url":"https://github.com/zwilias","followers_url":"https://api.github.com/users/zwilias/followers","following_url":"https://api.github.com/users/zwilias/following{/other_user}","gists_url":"https://api.github.com/users/zwilias/gists{/gist_id}","starred_url":"https://api.github.com/users/zwilias/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zwilias/subscriptions","organizations_url":"https://api.github.com/users/zwilias/orgs","repos_url":"https://api.github.com/users/zwilias/repos","events_url":"https://api.github.com/users/zwilias/events{/privacy}","received_events_url":"https://api.github.com/users/zwilias/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-02T08:53:08Z","updated_at":"2022-04-07T20:37:29Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nRunning `cabal repl` with `-fobject-code` and running any code leads to strange \"missing file: [..]/lib/settings\" error, but only on aarch64-darwin.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Clone https://github.com/zwilias/cabal-repl-m1-repro\r\n2. `direnv allow`\r\n3. `cabal repl --repl-options='-fobject-code'`\r\n4. `Main.main`\r\n\r\n```\r\nMissing file: /nix/store/cvcqjx3pdslvw4p21p9nf4pij2m60gw4-ghc-8.10.7/lib/ghc-8.10.7/lib/settings\r\n*** Exception: ExitFailure 1\r\n```\r\n\r\n### Expected behavior\r\n\r\n`\"Hello, Haskell!\"`\r\n\r\n### Additional context\r\n\r\n- This does work on other architectures\r\n- GHC version doesn't seem to matter, same issue occurs with 9.2.1\r\n- The actual error seems a bit funny, as if `-B` wasn't set properly\r\n- Setting the super secret `_GHC_TOP_DIR` variable manually results in... a different error:\r\n```\r\n$ _GHC_TOP_DIR=/nix/store/cvcqjx3pdslvw4p21p9nf4pij2m60gw4-ghc-8.10.7/lib/ghc-8.10.7 cabal repl --repl-options='-fobject-code'\r\n> Main.main\r\n<interactive>: no input files\r\nUsage: For basic information, try the `--help' option.\r\n*** Exception: ExitFailure 1\r\n```\r\n\r\n### Notify maintainers\r\n@peti \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 12.3`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"\"`\r\n - channels(ilias): `\"\"`\r\n - nixpkgs: `/nix/store/zlcqhgq592ffj2k145q7k5vbg51vm106-v5ijr9q40jny9fr6i8q9859qsdagh0s5-source\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166911/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166902","id":1190474755,"node_id":"I_kwDOAEVQ_M5G9TQD","number":166902,"title":"davinci-resolve: package studio version","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-04-02T02:59:32Z","updated_at":"2022-04-23T06:51:13Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Create package \"davinci-resolve-studio\".\r\n\r\nMight need some changes to support license: https://github.com/NixOS/nixpkgs/pull/152113#issuecomment-1075642604\r\n\r\nCheck out other derivations like [nvidia](https://github.com/NixOS/nixpkgs/blob/634141959076a8ab69ca2cca0f266852256d79ee/pkgs/os-specific/linux/nvidia-x11/default.nix) to prevent duplication of code. Have one file for general package build and another one for specific versions. (not sure what the best practices are now)\r\n\r\nYou can add the beta versions too.\r\n\r\nFollow up to https://github.com/NixOS/nixpkgs/pull/152113.\r\n\r\n@jshcmpbll ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902/reactions","total_count":4,"+1":2,"-1":0,"laugh":0,"hooray":1,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166902/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166900","id":1190472681,"node_id":"I_kwDOAEVQ_M5G9Svp","number":166900,"title":"davinci-resolve: .desktop file missing","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-02T02:50:03Z","updated_at":"2022-04-15T14:23:31Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nFollow up to https://github.com/NixOS/nixpkgs/pull/152113.\r\n\r\nThis might help: https://github.com/NixOS/nixpkgs/pull/152113#discussion_r795106901\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\n\r\n### Additional context\r\n\r\n### Notify maintainers\r\n@jshcmpbll\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166900/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166887","id":1190400623,"node_id":"I_kwDOAEVQ_M5G9BJv","number":166887,"title":"Allow setting `gnome-keyring` components","user":{"login":"fufexan","id":36706276,"node_id":"MDQ6VXNlcjM2NzA2Mjc2","avatar_url":"https://avatars.githubusercontent.com/u/36706276?v=4","gravatar_id":"","url":"https://api.github.com/users/fufexan","html_url":"https://github.com/fufexan","followers_url":"https://api.github.com/users/fufexan/followers","following_url":"https://api.github.com/users/fufexan/following{/other_user}","gists_url":"https://api.github.com/users/fufexan/gists{/gist_id}","starred_url":"https://api.github.com/users/fufexan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fufexan/subscriptions","organizations_url":"https://api.github.com/users/fufexan/orgs","repos_url":"https://api.github.com/users/fufexan/repos","events_url":"https://api.github.com/users/fufexan/events{/privacy}","received_events_url":"https://api.github.com/users/fufexan/received_events","type":"User","site_admin":false},"labels":[{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-01T23:58:06Z","updated_at":"2022-04-07T20:37:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\nCurrently GNOME Keyring is started with all components by its systemd service (included with the package), with no way for the user to change it.\r\n\r\nIf a user wants to use a separate SSH agent, they're blocked by `gnome-keyring-daemon` which will set `SSH_AUTH_SOCK` even if if was set before.\r\n\r\nAn ideal fix would be to have an option like Home Manager: https://nix-community.github.io/home-manager/options.html#opt-services.gnome-keyring.components. That way, users could set the components based on their needs.\r\n\r\nI'm not entirely sure, but it should be possible to override the service included in the package, just like in [gdm's case](https://github.com/NixOS/nixpkgs/blob/nixos-unstable/nixos/modules/services/x11/display-managers/gdm.nix#L175).\r\n\r\n## Technical details\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166887/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166797","id":1189551209,"node_id":"I_kwDOAEVQ_M5G5xxp","number":166797,"title":"vscode-extensions.ms-vscode.cpptools: not work","user":{"login":"dan4ik605743","id":86075850,"node_id":"MDQ6VXNlcjg2MDc1ODUw","avatar_url":"https://avatars.githubusercontent.com/u/86075850?v=4","gravatar_id":"","url":"https://api.github.com/users/dan4ik605743","html_url":"https://github.com/dan4ik605743","followers_url":"https://api.github.com/users/dan4ik605743/followers","following_url":"https://api.github.com/users/dan4ik605743/following{/other_user}","gists_url":"https://api.github.com/users/dan4ik605743/gists{/gist_id}","starred_url":"https://api.github.com/users/dan4ik605743/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dan4ik605743/subscriptions","organizations_url":"https://api.github.com/users/dan4ik605743/orgs","repos_url":"https://api.github.com/users/dan4ik605743/repos","events_url":"https://api.github.com/users/dan4ik605743/events{/privacy}","received_events_url":"https://api.github.com/users/dan4ik605743/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-01T10:00:56Z","updated_at":"2022-04-01T12:38:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nOpenDebug does not work.\r\n\r\n### Steps To Reproduce\r\n1. install vscode-cpptools\r\n2. check working opendebug\r\n3. -> not work\r\n\r\n### Screenshots\r\n\r\n\r\n### Notify maintainers\r\n@jraygauthier\r\n\r\n### Metadata\r\n```console\r\nλ ~ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.27-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/store/f71alr07xb2swc37fiqjr5h416qcs6wr-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166797/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166750","id":1189154450,"node_id":"I_kwDOAEVQ_M5G4Q6S","number":166750,"title":"Icons do not render in GNOME applications","user":{"login":"hello-smile6","id":73048226,"node_id":"MDQ6VXNlcjczMDQ4MjI2","avatar_url":"https://avatars.githubusercontent.com/u/73048226?v=4","gravatar_id":"","url":"https://api.github.com/users/hello-smile6","html_url":"https://github.com/hello-smile6","followers_url":"https://api.github.com/users/hello-smile6/followers","following_url":"https://api.github.com/users/hello-smile6/following{/other_user}","gists_url":"https://api.github.com/users/hello-smile6/gists{/gist_id}","starred_url":"https://api.github.com/users/hello-smile6/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hello-smile6/subscriptions","organizations_url":"https://api.github.com/users/hello-smile6/orgs","repos_url":"https://api.github.com/users/hello-smile6/repos","events_url":"https://api.github.com/users/hello-smile6/events{/privacy}","received_events_url":"https://api.github.com/users/hello-smile6/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-04-01T02:55:17Z","updated_at":"2022-04-07T20:37:17Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nIcons won't render in GNOME applications, even though the icons are installed.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install `nixpkgs.elementary`.\r\n2. Execute `io.elementary.calendar` and observe the absence of icons.\r\n\r\n### Expected behavior\r\nI was expecting for apps to use the installed icon library.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n b4fa72a8bfe0% ls -a .config/plank \r\n. ..\r\nb4fa72a8bfe0% nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.13.0-1021-gcp, Ubuntu, 20.04.2 LTS (Focal Fossa)`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(runner): `\"nixpkgs, nixpkgs-stable-21_11-21.11.tar.gz, nixpkgs-unstable\"`\r\n - nixpkgs: `/home/runner/.nix-defexpr/channels/nixpkgs`\r\n\r\nb4fa72a8bfe0% b4fa72a8bfe0% ls -a .config/plank \r\n. ..\r\nb4fa72a8bfe0% nix-shell -p nix-info --run \"nix-info -m\"\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166750/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166742","id":1189114667,"node_id":"I_kwDOAEVQ_M5G4HMr","number":166742,"title":"minetest on Darwin aarch64 fails to run with Killed: 9","user":{"login":"3noch","id":882455,"node_id":"MDQ6VXNlcjg4MjQ1NQ==","avatar_url":"https://avatars.githubusercontent.com/u/882455?v=4","gravatar_id":"","url":"https://api.github.com/users/3noch","html_url":"https://github.com/3noch","followers_url":"https://api.github.com/users/3noch/followers","following_url":"https://api.github.com/users/3noch/following{/other_user}","gists_url":"https://api.github.com/users/3noch/gists{/gist_id}","starred_url":"https://api.github.com/users/3noch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/3noch/subscriptions","organizations_url":"https://api.github.com/users/3noch/orgs","repos_url":"https://api.github.com/users/3noch/repos","events_url":"https://api.github.com/users/3noch/events{/privacy}","received_events_url":"https://api.github.com/users/3noch/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-04-01T01:50:37Z","updated_at":"2022-04-07T20:37:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nminetest fails to run and reports Killed: 9\r\n\r\n### Steps To Reproduce\r\nbuild minetest and run on macos aarch64 (I can't confirm if x86 is also broken).\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166742/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166741","id":1189111293,"node_id":"I_kwDOAEVQ_M5G4GX9","number":166741,"title":"glib package directory needs to have dbus uuid","user":{"login":"hello-smile6","id":73048226,"node_id":"MDQ6VXNlcjczMDQ4MjI2","avatar_url":"https://avatars.githubusercontent.com/u/73048226?v=4","gravatar_id":"","url":"https://api.github.com/users/hello-smile6","html_url":"https://github.com/hello-smile6","followers_url":"https://api.github.com/users/hello-smile6/followers","following_url":"https://api.github.com/users/hello-smile6/following{/other_user}","gists_url":"https://api.github.com/users/hello-smile6/gists{/gist_id}","starred_url":"https://api.github.com/users/hello-smile6/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hello-smile6/subscriptions","organizations_url":"https://api.github.com/users/hello-smile6/orgs","repos_url":"https://api.github.com/users/hello-smile6/repos","events_url":"https://api.github.com/users/hello-smile6/events{/privacy}","received_events_url":"https://api.github.com/users/hello-smile6/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-04-01T01:44:21Z","updated_at":"2022-04-04T08:18:09Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nFor some reason, many programs look for the dbus uuid in the glib package directory. However, it is never there.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-env -iA nixpkgs.pantheon`\r\n2. `io.elementary.wingpanel`\r\n3. Look at the command-line output.\r\n\r\n### Expected behavior\r\nI expected dbus to work without configuration.\r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\nI have a NoVNC server running, feel free to use [the NoVNC server](https://vnc-gnome.9pfs.repl.co/vnc.html) to get more information. \r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nrunner@7aede57d0f27:~/vnc-gnome$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.13.0-1021-gcp, Ubuntu, 20.04.2 LTS (Focal Fossa)`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(runner): `\"nixpkgs, nixpkgs-stable-21_11-21.11.tar.gz, nixpkgs-unstable\"`\r\n - nixpkgs: `/home/runner/.nix-defexpr/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166741/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166719","id":1188874484,"node_id":"I_kwDOAEVQ_M5G3Mj0","number":166719,"title":"tiktok-scraper","user":{"login":"kiyayo","id":37314590,"node_id":"MDQ6VXNlcjM3MzE0NTkw","avatar_url":"https://avatars.githubusercontent.com/u/37314590?v=4","gravatar_id":"","url":"https://api.github.com/users/kiyayo","html_url":"https://github.com/kiyayo","followers_url":"https://api.github.com/users/kiyayo/followers","following_url":"https://api.github.com/users/kiyayo/following{/other_user}","gists_url":"https://api.github.com/users/kiyayo/gists{/gist_id}","starred_url":"https://api.github.com/users/kiyayo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kiyayo/subscriptions","organizations_url":"https://api.github.com/users/kiyayo/orgs","repos_url":"https://api.github.com/users/kiyayo/repos","events_url":"https://api.github.com/users/kiyayo/events{/privacy}","received_events_url":"https://api.github.com/users/kiyayo/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T22:01:05Z","updated_at":"2022-03-31T22:01:05Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\ncommandline application to scrape and download useful information from TikTok.\r\n\r\n**Metadata**\r\n\r\n\r\n* source URL: https://github.com/drawrowfly/tiktok-scraper\r\n* license: mit\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166719/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166710","id":1188673396,"node_id":"I_kwDOAEVQ_M5G2bd0","number":166710,"title":"Vulnerability roundup 112: zsh-5.8: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:13:31Z","updated_at":"2022-03-31T20:13:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=zsh&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=zsh+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45444](https://nvd.nist.gov/vuln/detail/CVE-2021-45444) CVSSv3=7.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-45444\n\nIn zsh before 5.8.1, an attacker can achieve code execution if they control a command output inside the prompt, as demonstrated by a %F argument. This occurs because of recursive PROMPT_SUBST expansion.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @pSub\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166710/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166706","id":1188672064,"node_id":"I_kwDOAEVQ_M5G2bJA","number":166706,"title":"Vulnerability roundup 112: wavpack-5.4.0: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:12:50Z","updated_at":"2022-03-31T20:12:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=wavpack&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=wavpack+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-44269](https://nvd.nist.gov/vuln/detail/CVE-2021-44269) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-44269\n\nAn out of bounds read was found in Wavpack 5.4.0 in processing *.WAV files. This issue triggered in function WavpackPackSamples of file src/pack_utils.c, tainted variable cnt is too large, that makes pointer sptr read beyond heap bound.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @codyopel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166706/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166705","id":1188671962,"node_id":"I_kwDOAEVQ_M5G2bHa","number":166705,"title":"Vulnerability roundup 112: wasmtime-0.21.0: 1 advisory [8.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:12:47Z","updated_at":"2022-03-31T20:12:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=wasmtime&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=wasmtime+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23636](https://nvd.nist.gov/vuln/detail/CVE-2022-23636) CVSSv3=8.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23636\n\nWasmtime is an open source runtime for WebAssembly & WASI. Prior to versions 0.34.1 and 0.33.1, there exists a bug in the pooling instance allocator in Wasmtime's runtime where a failure to instantiate an instance for a module that defines an `externref` global will result in an invalid drop of a `VMExternRef` via an uninitialized pointer. A number of conditions listed in the GitHub Security Advisory must be true in order for an instance to be vulnerable to this issue. Maintainers believe that the effective impact of this bug is relatively small because the usage of `externref` is still uncommon and without a resource limiter configured on the `Store`, which is not the default configuration, it is only possible to trigger the bug from an error returned by `mprotect` or `VirtualAlloc`. Note that on Linux with the `uffd` feature enabled, it is only possible to trigger the bug from a resource limiter as the call to `mprotect` is skipped. The bug has been fixed in 0.34.1 and 0.33.1 and users are encouraged to upgrade as soon as possible. If it is not possible to upgrade to version 0.34.1 or 0.33.1 of the `wasmtime` crate, it is recommend that support for the reference types proposal be disabled by passing `false` to `Config::wasm_reference_types`. Doing so will prevent modules that use `externref` from being loaded entirely.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @matthewbauer\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166705/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166702","id":1188671747,"node_id":"I_kwDOAEVQ_M5G2bED","number":166702,"title":"Vulnerability roundup 112: vault-1.8.6: 2 advisories [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:12:41Z","updated_at":"2022-03-31T20:12:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=vault&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=vault+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25243](https://nvd.nist.gov/vuln/detail/CVE-2022-25243) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-25244](https://nvd.nist.gov/vuln/detail/CVE-2022-25244) CVSSv3=6.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-25243\n\n\"Vault and Vault Enterprise 1.8.0 through 1.8.8, and 1.9.3 allowed the PKI secrets engine under certain configurations to issue wildcard certificates to authorized users for a specified domain, even if the PKI role policy attribute allow_subdomains is set to false. Fixed in Vault Enterprise 1.8.9 and 1.9.4.\n\n### CVE-2022-25244\n\nVault Enterprise clusters using the tokenization transform feature can expose the tokenization key through the tokenization key configuration endpoint to authorized operators with `read` permissions on this endpoint. Fixed in Vault Enterprise 1.9.4, 1.8.9 and 1.7.10.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @Chili-Man\nCc @kalbasit\nCc @lnl7\nCc @offlinehacker\nCc @pradeepchhetri\nCc @rushmorem\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166702/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166701","id":1188671681,"node_id":"I_kwDOAEVQ_M5G2bDB","number":166701,"title":"Vulnerability roundup 112: usbguard-1.0.0: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:12:39Z","updated_at":"2022-03-31T20:54:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=usbguard&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=usbguard+in%3Apath&type=Code)\n\n* [ ] [CVE-2019-25058](https://nvd.nist.gov/vuln/detail/CVE-2019-25058) CVSSv3=7.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2019-25058\n\nAn issue was discovered in USBGuard before 1.1.0. On systems with the usbguard-dbus daemon running, an unprivileged user could make USBGuard allow all USB devices to be connected in the future.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @tnias\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166701/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166699","id":1188671618,"node_id":"I_kwDOAEVQ_M5G2bCC","number":166699,"title":"Vulnerability roundup 112: trytond-6.2.3: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:12:37Z","updated_at":"2022-03-31T20:12:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=trytond&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=trytond+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-26662](https://nvd.nist.gov/vuln/detail/CVE-2022-26662) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2022-26661](https://nvd.nist.gov/vuln/detail/CVE-2022-26661) CVSSv3=6.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-26662\n\nAn XML Entity Expansion (XEE) issue was discovered in Tryton Application Platform (Server) 5.x through 5.0.45, 6.x through 6.0.15, and 6.1.x and 6.2.x through 6.2.5, and Tryton Application Platform (Command Line Client (proteus)) 5.x through 5.0.11, 6.x through 6.0.4, and 6.1.x and 6.2.x through 6.2.1. An unauthenticated user can send a crafted XML-RPC message to consume all the resources of the server.\n\n### CVE-2022-26661\n\nAn XXE issue was discovered in Tryton Application Platform (Server) 5.x through 5.0.45, 6.x through 6.0.15, and 6.1.x and 6.2.x through 6.2.5, and Tryton Application Platform (Command Line Client (proteus)) 5.x through 5.0.11, 6.x through 6.0.4, and 6.1.x and 6.2.x through 6.2.1. An authenticated user can make the server parse a crafted XML SEPA file to access arbitrary files on the system.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @johbo\nCc @udono\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166699/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166698","id":1188671549,"node_id":"I_kwDOAEVQ_M5G2bA9","number":166698,"title":"Vulnerability roundup 112: trytond-6.2.0: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:12:34Z","updated_at":"2022-03-31T20:12:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=trytond&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=trytond+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-26662](https://nvd.nist.gov/vuln/detail/CVE-2022-26662) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-26661](https://nvd.nist.gov/vuln/detail/CVE-2022-26661) CVSSv3=6.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-26662\n\nAn XML Entity Expansion (XEE) issue was discovered in Tryton Application Platform (Server) 5.x through 5.0.45, 6.x through 6.0.15, and 6.1.x and 6.2.x through 6.2.5, and Tryton Application Platform (Command Line Client (proteus)) 5.x through 5.0.11, 6.x through 6.0.4, and 6.1.x and 6.2.x through 6.2.1. An unauthenticated user can send a crafted XML-RPC message to consume all the resources of the server.\n\n### CVE-2022-26661\n\nAn XXE issue was discovered in Tryton Application Platform (Server) 5.x through 5.0.45, 6.x through 6.0.15, and 6.1.x and 6.2.x through 6.2.5, and Tryton Application Platform (Command Line Client (proteus)) 5.x through 5.0.11, 6.x through 6.0.4, and 6.1.x and 6.2.x through 6.2.1. An authenticated user can make the server parse a crafted XML SEPA file to access arbitrary files on the system.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @johbo\nCc @udono\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166698/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166697","id":1188671483,"node_id":"I_kwDOAEVQ_M5G2a_7","number":166697,"title":"Vulnerability roundup 112: traefik-2.5.3: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:12:32Z","updated_at":"2022-03-31T20:12:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=traefik&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=traefik+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23632](https://nvd.nist.gov/vuln/detail/CVE-2022-23632) CVSSv3=9.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23632\n\nTraefik is an HTTP reverse proxy and load balancer. Prior to version 2.6.1, Traefik skips the router transport layer security (TLS) configuration when the host header is a fully qualified domain name (FQDN). For a request, the TLS configuration choice can be different than the router choice, which implies the use of a wrong TLS configuration. When sending a request using FQDN handled by a router configured with a dedicated TLS configuration, the TLS configuration falls back to the default configuration that might not correspond to the configured one. If the CNAME flattening is enabled, the selected TLS configuration is the SNI one and the routing uses the CNAME value, so this can skip the expected TLS configuration. Version 2.6.1 contains a patch for this issue. As a workaround, one may add the FDQN to the host rule. However, there is no workaround if the CNAME flattening is enabled.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @kalbasit\nCc @vdemeester\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166697/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166695","id":1188671348,"node_id":"I_kwDOAEVQ_M5G2a90","number":166695,"title":"Vulnerability roundup 112: tcpreplay-4.4.1: 5 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:12:28Z","updated_at":"2022-04-24T16:23:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=tcpreplay&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=tcpreplay+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-27940](https://nvd.nist.gov/vuln/detail/CVE-2022-27940) CVSSv3=7.8 (nixos-unstable)\n* [ ] [CVE-2022-27941](https://nvd.nist.gov/vuln/detail/CVE-2022-27941) CVSSv3=7.8 (nixos-unstable)\n* [ ] [CVE-2022-27942](https://nvd.nist.gov/vuln/detail/CVE-2022-27942) CVSSv3=7.8 (nixos-unstable)\n* [ ] [CVE-2022-25484](https://nvd.nist.gov/vuln/detail/CVE-2022-25484) CVSSv3=5.5 (nixos-unstable)\n* [ ] [CVE-2022-27939](https://nvd.nist.gov/vuln/detail/CVE-2022-27939) CVSSv3=5.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-27940\n\ntcprewrite in Tcpreplay 4.4.1 has a heap-based buffer over-read in get_ipv6_next in common/get.c.\n\n### CVE-2022-27941\n\ntcprewrite in Tcpreplay 4.4.1 has a heap-based buffer over-read in get_l2len_protocol in common/get.c.\n\n### CVE-2022-27942\n\ntcpprep in Tcpreplay 4.4.1 has a heap-based buffer over-read in parse_mpls in common/get.c.\n\n### CVE-2022-25484\n\ntcpprep v4.4.1 has a reachable assertion (assert(l2len > 0)) in packet2tree() at tree.c in tcpprep v4.4.1.\n\n### CVE-2022-27939\n\ntcprewrite in Tcpreplay 4.4.1 has a reachable assertion in get_layer4_v6 in common/get.c.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @proteansec\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166695/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166691","id":1188661358,"node_id":"I_kwDOAEVQ_M5G2Yhu","number":166691,"title":"Vulnerability roundup 112: rtl_433-21.12: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:07:19Z","updated_at":"2022-03-31T20:07:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=rtl_433&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=rtl_433+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25051](https://nvd.nist.gov/vuln/detail/CVE-2022-25051) CVSSv3=5.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-25051\n\nAn Off-by-one Error occurs in cmr113_decode of rtl_433 21.12 when decoding a crafted file.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @earldouglas\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166691/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166689","id":1188661213,"node_id":"I_kwDOAEVQ_M5G2Yfd","number":166689,"title":"Vulnerability roundup 112: radare2-5.6.2: 7 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:07:15Z","updated_at":"2022-03-31T20:07:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=radare2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=radare2+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0676](https://nvd.nist.gov/vuln/detail/CVE-2022-0676) CVSSv3=7.8 (nixos-21.11)\n* [ ] [CVE-2022-1031](https://nvd.nist.gov/vuln/detail/CVE-2022-1031) CVSSv3=7.8 (nixos-21.11)\n* [ ] [CVE-2022-0713](https://nvd.nist.gov/vuln/detail/CVE-2022-0713) CVSSv3=7.1 (nixos-21.11)\n* [ ] [CVE-2022-0476](https://nvd.nist.gov/vuln/detail/CVE-2022-0476) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-0695](https://nvd.nist.gov/vuln/detail/CVE-2022-0695) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-0712](https://nvd.nist.gov/vuln/detail/CVE-2022-0712) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-0849](https://nvd.nist.gov/vuln/detail/CVE-2022-0849) CVSSv3=5.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0676\n\nHeap-based Buffer Overflow in GitHub repository radareorg/radare2 prior to 5.6.4.\n\n### CVE-2022-1031\n\nUse After Free in op_is_set_bp in GitHub repository radareorg/radare2 prior to 5.6.6.\n\n### CVE-2022-0713\n\nHeap-based Buffer Overflow in GitHub repository radareorg/radare2 prior to 5.6.4.\n\n### CVE-2022-0476\n\nDenial of Service in GitHub repository radareorg/radare2 prior to 5.6.4.\n\n### CVE-2022-0695\n\nDenial of Service in GitHub repository radareorg/radare2 prior to 5.6.4.\n\n### CVE-2022-0712\n\nNULL Pointer Dereference in GitHub repository radareorg/radare2 prior to 5.6.4.\n\n### CVE-2022-0849\n\nUse After Free in r_reg_get_name_idx in GitHub repository radareorg/radare2 prior to 5.6.6.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @7c6f434c\nCc @arkivm\nCc @makefu\nCc @mic92\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166689/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166688","id":1188661112,"node_id":"I_kwDOAEVQ_M5G2Yd4","number":166688,"title":"Vulnerability roundup 112: qt-4.8.7: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:07:12Z","updated_at":"2022-03-31T20:07:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=qt&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=qt+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25634](https://nvd.nist.gov/vuln/detail/CVE-2022-25634) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-25634\n\nQt through 5.15.8 and 6.x through 6.2.3 can load system library files from an unintended working directory.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @lovek323\nCc @orivej\nCc @phreedom\nCc @svanderburg\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166688/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166686","id":1188660960,"node_id":"I_kwDOAEVQ_M5G2Ybg","number":166686,"title":"Vulnerability roundup 112: qemu-6.1.1: 4 advisories [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-31T20:07:07Z","updated_at":"2022-04-24T17:51:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=qemu&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=qemu+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-3748](https://nvd.nist.gov/vuln/detail/CVE-2021-3748) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2021-3930](https://nvd.nist.gov/vuln/detail/CVE-2021-3930) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2021-20257](https://nvd.nist.gov/vuln/detail/CVE-2021-20257) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-26354](https://nvd.nist.gov/vuln/detail/CVE-2022-26354) CVSSv3=3.2 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-3748\n\nA use-after-free vulnerability was found in the virtio-net device of QEMU. It could occur when the descriptor's address belongs to the non direct access region, due to num_buffers being set after the virtqueue elem has been unmapped. A malicious guest could use this flaw to crash QEMU, resulting in a denial of service condition, or potentially execute code on the host with the privileges of the QEMU process.\n\n### CVE-2021-3930\n\nAn off-by-one error was found in the SCSI device emulation in QEMU. It could occur while processing MODE SELECT commands in mode_sense_page() if the 'page' argument was set to MODE_PAGE_ALLS (0x3f). A malicious guest could use this flaw to potentially crash QEMU, resulting in a denial of service condition.\n\n### CVE-2021-20257\n\nAn infinite loop flaw was found in the e1000 NIC emulator of the QEMU. This issue occurs while processing transmits (tx) descriptors in process_tx_desc if various descriptor fields are initialized with invalid values. This flaw allows a guest to consume CPU cycles on the host, resulting in a denial of service. The highest threat from this vulnerability is to system availability.\n\n### CVE-2022-26354\n\nA flaw was found in the vhost-vsock device of QEMU. In case of error, an invalid element was not detached from the virtqueue before freeing its memory, leading to memory leakage and other unexpected results. Affected QEMU versions <= 6.2.0.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @alyssais\nCc @edolstra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166686/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166685","id":1188660901,"node_id":"I_kwDOAEVQ_M5G2Yal","number":166685,"title":"Vulnerability roundup 112: postgresql-10.20: 2 advisories [7.2]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:07:05Z","updated_at":"2022-03-31T20:07:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=postgresql&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=postgresql+in%3Apath&type=Code)\n\n* [ ] [CVE-2019-9193](https://nvd.nist.gov/vuln/detail/CVE-2019-9193) CVSSv3=7.2 (nixos-unstable)\n* [ ] [CVE-2021-3393](https://nvd.nist.gov/vuln/detail/CVE-2021-3393) CVSSv3=4.3 (nixos-unstable)\n\n## CVE details\n\n### CVE-2019-9193\n\n** DISPUTED ** In PostgreSQL 9.3 through 11.2, the \"COPY TO/FROM PROGRAM\" function allows superusers and users in the 'pg_execute_server_program' group to execute arbitrary code in the context of the database's operating system user. This functionality is enabled by default and can be abused to run arbitrary operating system commands on Windows, Linux, and macOS. NOTE: Third parties claim/state this is not an issue because PostgreSQL functionality for ‘COPY TO/FROM PROGRAM’ is acting as intended. References state that in PostgreSQL, a superuser can execute commands as the server user without using the ‘COPY FROM PROGRAM’.\n\n### CVE-2021-3393\n\nAn information leak was discovered in postgresql in versions before 13.2, before 12.6 and before 11.11. A user having UPDATE permission but not SELECT permission to a particular column could craft queries which, under some circumstances, might disclose values from that column in error messages. An attacker could use this flaw to obtain information stored in a column they are allowed to write but not read.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @danbst\nCc @globin\nCc @ivan\nCc @marsam\nCc @thoughtpolice\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166685/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166684","id":1188660837,"node_id":"I_kwDOAEVQ_M5G2YZl","number":166684,"title":"Vulnerability roundup 112: pjsip-2.12: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:07:03Z","updated_at":"2022-03-31T20:07:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=pjsip&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=pjsip+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24754](https://nvd.nist.gov/vuln/detail/CVE-2022-24754) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-24764](https://nvd.nist.gov/vuln/detail/CVE-2022-24764) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-24754\n\nPJSIP is a free and open source multimedia communication library written in C language. In versions prior to and including 2.12 PJSIP there is a stack-buffer overflow vulnerability which only impacts PJSIP users who accept hashed digest credentials (credentials with data_type `PJSIP_CRED_DATA_DIGEST`). This issue has been patched in the master branch of the PJSIP repository and will be included with the next release. Users unable to upgrade need to check that the hashed digest data length must be equal to `PJSIP_MD5STRLEN` before passing to PJSIP.\n\n### CVE-2022-24764\n\nPJSIP is a free and open source multimedia communication library written in C. Versions 2.12 and prior contain a stack buffer overflow vulnerability that affects PJSUA2 users or users that call the API `pjmedia_sdp_print(), pjmedia_sdp_media_print()`. Applications that do not use PJSUA2 and do not directly call `pjmedia_sdp_print()` or `pjmedia_sdp_media_print()` should not be affected. A patch is available on the `master` branch of the `pjsip/pjproject` GitHub repository. There are currently no known workarounds.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @olynch\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166684/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166682","id":1188660695,"node_id":"I_kwDOAEVQ_M5G2YXX","number":166682,"title":"Vulnerability roundup 112: openssh-8.8p1: 1 advisory [3.7]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-31T20:06:59Z","updated_at":"2022-04-04T08:18:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=openssh&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=openssh+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-36368](https://nvd.nist.gov/vuln/detail/CVE-2021-36368) CVSSv3=3.7 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-36368\n\n** DISPUTED ** An issue was discovered in OpenSSH before 8.9. If a client is using public-key authentication with agent forwarding but without -oLogLevel=verbose, and an attacker has silently modified the server to support the None authentication option, then the user cannot determine whether FIDO authentication is going to confirm that the user wishes to connect to that server, or that the user wishes to allow that server to connect to a different server on the user's behalf. NOTE: the vendor's position is \"this is not an authentication bypass, since nothing is being bypassed.\"\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @dasJ\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166682/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166681","id":1188660593,"node_id":"I_kwDOAEVQ_M5G2YVx","number":166681,"title":"Vulnerability roundup 112: openjpeg-2.4.0: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-31T20:06:56Z","updated_at":"2022-04-27T08:39:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=openjpeg&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=openjpeg+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-3575](https://nvd.nist.gov/vuln/detail/CVE-2021-3575) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-3575\n\nA heap-based buffer overflow was found in openjpeg in color.c:379:42 in sycc420_to_rgb when decompressing a crafted .j2k file. An attacker could use this to execute arbitrary code with the permissions of the application compiled against openjpeg.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @codyopel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166681/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166680","id":1188660525,"node_id":"I_kwDOAEVQ_M5G2YUt","number":166680,"title":"Vulnerability roundup 112: ocrfeeder-0.8.3: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:06:54Z","updated_at":"2022-04-01T06:19:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=ocrfeeder&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=ocrfeeder+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-27811](https://nvd.nist.gov/vuln/detail/CVE-2022-27811) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-27811\n\nGNOME OCRFeeder before 0.8.4 allows OS command injection via shell metacharacters in a PDF or image filename.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @doronbehar\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166680/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166673","id":1188650456,"node_id":"I_kwDOAEVQ_M5G2V3Y","number":166673,"title":"Vulnerability roundup 112: moodle-3.11.5: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:38Z","updated_at":"2022-03-31T20:01:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=moodle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=moodle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0983](https://nvd.nist.gov/vuln/detail/CVE-2022-0983) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0983\n\nAn SQL injection risk was identified in Badges code relating to configuring criteria. Access to the relevant capability was limited to teachers and managers by default.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @freezeboy\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166673/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166672","id":1188650371,"node_id":"I_kwDOAEVQ_M5G2V2D","number":166672,"title":"Vulnerability roundup 112: moodle-3.11.4: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:01:35Z","updated_at":"2022-03-31T20:01:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=moodle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=moodle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0983](https://nvd.nist.gov/vuln/detail/CVE-2022-0983) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0983\n\nAn SQL injection risk was identified in Badges code relating to configuring criteria. Access to the relevant capability was limited to teachers and managers by default.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @freezeboy\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166672/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166671","id":1188650291,"node_id":"I_kwDOAEVQ_M5G2V0z","number":166671,"title":"Vulnerability roundup 112: mitmproxy-7.0.4: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:33Z","updated_at":"2022-03-31T20:01:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mitmproxy&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mitmproxy+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24766](https://nvd.nist.gov/vuln/detail/CVE-2022-24766) CVSSv3=9.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24766\n\nmitmproxy is an interactive, SSL/TLS-capable intercepting proxy. In mitmproxy 7.0.4 and below, a malicious client or server is able to perform HTTP request smuggling attacks through mitmproxy. This means that a malicious client/server could smuggle a request/response through mitmproxy as part of another request/response's HTTP message body. While mitmproxy would only see one request, the target server would see multiple requests. A smuggled request is still captured as part of another request's body, but it does not appear in the request list and does not go through the usual mitmproxy event hooks, where users may have implemented custom access control checks or input sanitization. Unless mitmproxy is used to protect an HTTP/1 service, no action is required. The vulnerability has been fixed in mitmproxy 8.0.0 and above. There are currently no known workarounds.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @fpletz\nCc @kamilchm\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166671/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166670","id":1188650177,"node_id":"I_kwDOAEVQ_M5G2VzB","number":166670,"title":"Vulnerability roundup 112: mattermost-5.37.5: 3 advisories [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:01:29Z","updated_at":"2022-03-31T20:01:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mattermost&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mattermost+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0708](https://nvd.nist.gov/vuln/detail/CVE-2022-0708) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-1002](https://nvd.nist.gov/vuln/detail/CVE-2022-1002) CVSSv3=5.4 (nixos-21.11)\n* [ ] [CVE-2022-1003](https://nvd.nist.gov/vuln/detail/CVE-2022-1003) CVSSv3=4.9 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0708\n\nMattermost 6.3.0 and earlier fails to protect email addresses of the creator of the team via one of the APIs, which allows authenticated team members to access this information resulting in sensitive & private information disclosure.\n\n### CVE-2022-1002\n\nMattermost 6.3.0 and earlier fails to properly sanitize the HTML content in the email invitation sent to guest users, which allows registered users with special permissions to invite guest users to inject unescaped HTML content in the email invitations.\n\n### CVE-2022-1003\n\nOne of the API in Mattermost version 6.3.0 and earlier fails to properly protect the permissions, which allows the system administrators to combine the two distinct privileges/capabilities in a way that allows them to override certain restricted configurations like EnableUploads.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @fpletz\nCc @ryantm\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166670/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166668","id":1188650030,"node_id":"I_kwDOAEVQ_M5G2Vwu","number":166668,"title":"Vulnerability roundup 112: maddy-0.5.2: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:25Z","updated_at":"2022-03-31T20:01:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=maddy&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=maddy+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24732](https://nvd.nist.gov/vuln/detail/CVE-2022-24732) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24732\n\nMaddy Mail Server is an open source SMTP compatible email server. Versions of maddy prior to 0.5.4 do not implement password expiry or account expiry checking when authenticating using PAM. Users are advised to upgrade. Users unable to upgrade should manually remove expired accounts via existing filtering mechanisms.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @NickCao\nCc @kalbasit\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166668/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166667","id":1188649910,"node_id":"I_kwDOAEVQ_M5G2Vu2","number":166667,"title":"Vulnerability roundup 112: lua-5.4.3: 1 advisory [6.3]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":1249449681,"node_id":"MDU6TGFiZWwxMjQ5NDQ5Njgx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20lua","name":"6.topic: lua","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T20:01:21Z","updated_at":"2022-04-07T20:35:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=lua&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=lua+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-44964](https://nvd.nist.gov/vuln/detail/CVE-2021-44964) CVSSv3=6.3 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-44964\n\nUse after free in garbage collector and finalizer of lgc.c in Lua interpreter 5.4.0~5.4.3 allows attackers to perform Sandbox Escape via a crafted script file.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166667/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166666","id":1188649825,"node_id":"I_kwDOAEVQ_M5G2Vth","number":166666,"title":"Vulnerability roundup 112: liquibase-4.4.3: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:19Z","updated_at":"2022-03-31T20:01:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=liquibase&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=liquibase+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0839](https://nvd.nist.gov/vuln/detail/CVE-2022-0839) CVSSv3=9.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0839\n\nImproper Restriction of XML External Entity Reference in GitHub repository liquibase/liquibase prior to 4.8.0.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166666/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166665","id":1188649733,"node_id":"I_kwDOAEVQ_M5G2VsF","number":166665,"title":"Vulnerability roundup 112: libxml2-2.9.12: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:16Z","updated_at":"2022-03-31T20:01:17Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=libxml2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=libxml2+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23308](https://nvd.nist.gov/vuln/detail/CVE-2022-23308) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23308\n\nvalid.c in libxml2 before 2.9.13 has a use-after-free of ID and IDREF attributes.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @edolstra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166665/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166663","id":1188649564,"node_id":"I_kwDOAEVQ_M5G2Vpc","number":166663,"title":"Vulnerability roundup 112: libpano13-2.9.20: 1 advisory [9.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:12Z","updated_at":"2022-03-31T20:01:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=libpano13&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=libpano13+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-33293](https://nvd.nist.gov/vuln/detail/CVE-2021-33293) CVSSv3=9.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-33293\n\nPanorama Tools libpano13 v2.9.20 was discovered to contain an out-of-bounds read in the function panoParserFindOLine() in parser.c.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166663/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166662","id":1188649497,"node_id":"I_kwDOAEVQ_M5G2VoZ","number":166662,"title":"Vulnerability roundup 112: liblouis-3.21.0: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T20:01:10Z","updated_at":"2022-03-31T20:01:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=liblouis&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=liblouis+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-26981](https://nvd.nist.gov/vuln/detail/CVE-2022-26981) CVSSv3=7.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-26981\n\nLiblouis through 3.21.0 has a buffer overflow in compilePassOpcode in compileTranslationTable.c (called, indirectly, by tools/lou_checktable.c).\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @jtojnar\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166662/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166660","id":1188639938,"node_id":"I_kwDOAEVQ_M5G2TTC","number":166660,"title":"Vulnerability roundup 112: liblouis-3.19.0: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:56:07Z","updated_at":"2022-03-31T19:56:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=liblouis&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=liblouis+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-26981](https://nvd.nist.gov/vuln/detail/CVE-2022-26981) CVSSv3=7.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-26981\n\nLiblouis through 3.21.0 has a buffer overflow in compilePassOpcode in compileTranslationTable.c (called, indirectly, by tools/lou_checktable.c).\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166660/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166658","id":1188639802,"node_id":"I_kwDOAEVQ_M5G2TQ6","number":166658,"title":"Vulnerability roundup 112: keycloak-16.1.0: 1 advisory [6.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:56:03Z","updated_at":"2022-03-31T19:56:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=keycloak&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=keycloak+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-20323](https://nvd.nist.gov/vuln/detail/CVE-2021-20323) CVSSv3=6.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-20323\n\nA POST based reflected Cross Site Scripting vulnerability on has been identified in Keycloak.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @ngerstle\nCc @talyz\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166658/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166656","id":1188639668,"node_id":"I_kwDOAEVQ_M5G2TO0","number":166656,"title":"Vulnerability roundup 112: jenkins-2.332.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:55:59Z","updated_at":"2022-04-01T15:05:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=jenkins&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=jenkins+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0538](https://nvd.nist.gov/vuln/detail/CVE-2022-0538) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0538\n\nJenkins 2.333 and earlier, LTS 2.319.2 and earlier defines custom XStream converters that have not been updated to apply the protections for the vulnerability CVE-2021-43859 and allow unconstrained resource usage.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @coreyoconnor\nCc @earldouglas\nCc @fpletz\nCc @nequissimus\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166656/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166655","id":1188639610,"node_id":"I_kwDOAEVQ_M5G2TN6","number":166655,"title":"Vulnerability roundup 112: invoiceplane-1.5.11: 3 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:57Z","updated_at":"2022-03-31T19:55:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=invoiceplane&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=invoiceplane+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-29024](https://nvd.nist.gov/vuln/detail/CVE-2021-29024) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2021-29022](https://nvd.nist.gov/vuln/detail/CVE-2021-29022) CVSSv3=5.3 (nixos-unstable)\n* [ ] [CVE-2021-29023](https://nvd.nist.gov/vuln/detail/CVE-2021-29023) CVSSv3=5.3 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-29024\n\nIn InvoicePlane 1.5.11 a misconfigured web server allows unauthenticated directory listing and file download. Allowing an attacker to directory traversal and download files suppose to be private without authentication.\n\n### CVE-2021-29022\n\nIn InvoicePlane 1.5.11, the upload feature discloses the full path of the file upload directory.\n\n### CVE-2021-29023\n\nInvoicePlane 1.5.11 doesn't have any rate-limiting for password reset and the reset token is generated using a weak mechanism that is predictable.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @onny\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166655/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166654","id":1188639514,"node_id":"I_kwDOAEVQ_M5G2TMa","number":166654,"title":"Vulnerability roundup 112: imagemagick-6.9.12-26: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:55:54Z","updated_at":"2022-03-31T19:55:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=imagemagick&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=imagemagick+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-3610](https://nvd.nist.gov/vuln/detail/CVE-2021-3610) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-3596](https://nvd.nist.gov/vuln/detail/CVE-2021-3596) CVSSv3=6.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-3610\n\nA heap-based buffer overflow vulnerability was found in ImageMagick in versions prior to 7.0.11-14 in ReadTIFFImage() in coders/tiff.c. This issue is due to an incorrect setting of the pixel array size, which can lead to a crash and segmentation fault.\n\n### CVE-2021-3596\n\nA NULL pointer dereference flaw was found in ImageMagick in versions prior to 7.0.10-31 in ReadSVGImage() in coders/svg.c. This issue is due to not checking the return value from libxml2's xmlCreatePushParserCtxt() and uses the value directly, which leads to a crash and segmentation fault.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @erictapen\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166654/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166653","id":1188639442,"node_id":"I_kwDOAEVQ_M5G2TLS","number":166653,"title":"Vulnerability roundup 112: httpie-2.6.0: 2 advisories [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:55:52Z","updated_at":"2022-04-11T10:22:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=httpie&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=httpie+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24737](https://nvd.nist.gov/vuln/detail/CVE-2022-24737) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-0430](https://nvd.nist.gov/vuln/detail/CVE-2022-0430) CVSSv3=5.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24737\n\nHTTPie is a command-line HTTP client. HTTPie has the practical concept of sessions, which help users to persistently store some of the state that belongs to the outgoing requests and incoming responses on the disk for further usage. Before 3.1.0, HTTPie didn‘t distinguish between cookies and hosts they belonged. This behavior resulted in the exposure of some cookies when there are redirects originating from the actual host to a third party website. Users are advised to upgrade. There are no known workarounds.\n\n### CVE-2022-0430\n\nExposure of Sensitive Information to an Unauthorized Actor in GitHub repository httpie/httpie prior to 3.1.0.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @SuperSandro2000\nCc @antono\nCc @relrod\nCc @schneefux\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166653/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166652","id":1188639361,"node_id":"I_kwDOAEVQ_M5G2TKB","number":166652,"title":"Vulnerability roundup 112: htmldoc-1.9.15: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:50Z","updated_at":"2022-03-31T19:55:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=htmldoc&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=htmldoc+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0534](https://nvd.nist.gov/vuln/detail/CVE-2022-0534) CVSSv3=5.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0534\n\nA vulnerability was found in htmldoc version 1.9.15 where the stack out-of-bounds read takes place in gif_get_code() and occurs when opening a malicious GIF file, which can result in a crash (segmentation fault).\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @shanemikel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166652/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166651","id":1188639317,"node_id":"I_kwDOAEVQ_M5G2TJV","number":166651,"title":"Vulnerability roundup 112: haproxy-2.3.14: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:48Z","updated_at":"2022-03-31T19:55:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=haproxy&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=haproxy+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0711](https://nvd.nist.gov/vuln/detail/CVE-2022-0711) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0711\n\nA flaw was found in the way HAProxy processed HTTP responses containing the \"Set-Cookie2\" header. This flaw could allow an attacker to send crafted HTTP response packets which lead to an infinite loop, eventually resulting in a denial of service condition. The highest threat from this vulnerability is availability.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166651/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166650","id":1188639252,"node_id":"I_kwDOAEVQ_M5G2TIU","number":166650,"title":"Vulnerability roundup 112: guake-3.6.3: 1 advisory [8.0]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:46Z","updated_at":"2022-03-31T19:55:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=guake&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=guake+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-23556](https://nvd.nist.gov/vuln/detail/CVE-2021-23556) CVSSv3=8.0 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-23556\n\nThe package guake before 3.8.5 are vulnerable to Exposed Dangerous Method or Function due to the exposure of execute_command and execute_command_by_uuid methods via the d-bus interface, which makes it possible for a malicious user to run an arbitrary command via the d-bus method. **Note:** Exploitation requires the user to have installed another malicious program that will be able to send dbus signals or run terminal commands.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @msteen\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166650/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166649","id":1188639155,"node_id":"I_kwDOAEVQ_M5G2TGz","number":166649,"title":"Vulnerability roundup 112: gradle-5.6.4: 1 advisory [8.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:55:43Z","updated_at":"2022-03-31T19:55:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25364](https://nvd.nist.gov/vuln/detail/CVE-2022-25364) CVSSv3=8.1 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-25364\n\nIn Gradle Enterprise before 2021.4.2, the default built-in build cache configuration allowed anonymous write access. If this was not manually changed, a malicious actor with network access to the build cache could potentially populate it with manipulated entries that execute malicious code as part of a build. As of 2021.4.2, the built-in build cache is inaccessible-by-default, requiring explicit configuration of its access-control settings before it can be used. (Remote build cache nodes are unaffected as they are inaccessible-by-default.)\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @liff\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166649/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166648","id":1188639087,"node_id":"I_kwDOAEVQ_M5G2TFv","number":166648,"title":"Vulnerability roundup 112: gogs-0.12.5: 2 advisories [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:41Z","updated_at":"2022-03-31T19:55:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gogs&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gogs+in%3Apath&type=Code)\n\n* [ ] [CVE-2019-10348](https://nvd.nist.gov/vuln/detail/CVE-2019-10348) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-0415](https://nvd.nist.gov/vuln/detail/CVE-2022-0415) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2019-10348\n\nJenkins Gogs Plugin stored credentials unencrypted in job config.xml files on the Jenkins master where they can be viewed by users with Extended Read permission, or access to the master file system.\n\n### CVE-2022-0415\n\nRemote Command Execution in uploading repository file in GitHub repository gogs/gogs prior to 0.12.6.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @kalbasit\nCc @schneefux\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166648/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166647","id":1188639018,"node_id":"I_kwDOAEVQ_M5G2TEq","number":166647,"title":"Vulnerability roundup 112: gogs-0.12.3: 3 advisories [9.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:55:39Z","updated_at":"2022-03-31T19:55:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gogs&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gogs+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0871](https://nvd.nist.gov/vuln/detail/CVE-2022-0871) CVSSv3=9.1 (nixos-21.11)\n* [ ] [CVE-2022-0415](https://nvd.nist.gov/vuln/detail/CVE-2022-0415) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-0870](https://nvd.nist.gov/vuln/detail/CVE-2022-0870) CVSSv3=5.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0871\n\nImproper Authorization in GitHub repository gogs/gogs prior to 0.12.5.\n\n### CVE-2022-0415\n\nRemote Command Execution in uploading repository file in GitHub repository gogs/gogs prior to 0.12.6.\n\n### CVE-2022-0870\n\nServer-Side Request Forgery (SSRF) in GitHub repository gogs/gogs prior to 0.12.5.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @kalbasit\nCc @schneefux\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166647/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166646","id":1188638923,"node_id":"I_kwDOAEVQ_M5G2TDL","number":166646,"title":"Vulnerability roundup 112: go-ethereum-1.10.8: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:55:36Z","updated_at":"2022-03-31T19:55:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go-ethereum&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go-ethereum+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23327](https://nvd.nist.gov/vuln/detail/CVE-2022-23327) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23327\n\nA design flaw in Go-Ethereum 1.10.12 and older versions allows an attacker node to send 5120 future transactions with a high gas price in one message, which can purge all of pending transactions in a victim node's memory pool, causing a denial of service (DoS).\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @RaghavSood\nCc @adisbladis\nCc @kalbasit\nCc @lionello\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166646/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166644","id":1188629775,"node_id":"I_kwDOAEVQ_M5G2Q0P","number":166644,"title":"Vulnerability roundup 112: go-1.17.5: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:50:30Z","updated_at":"2022-03-31T19:50:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24921](https://nvd.nist.gov/vuln/detail/CVE-2022-24921) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-27191](https://nvd.nist.gov/vuln/detail/CVE-2022-27191) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24921\n\nregexp.Compile in Go before 1.16.15 and 1.17.x before 1.17.8 allows stack exhaustion via a deeply nested expression.\n\n### CVE-2022-27191\n\ngolang.org/x/crypto/ssh before 0.0.0-20220314234659-1baeb1ce4c0b in Go through 1.16.15 and 1.17.x through 1.17.8 allows an attacker to crash a server in certain circumstances involving AddHostKey.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @Frostman\nCc @c00w\nCc @cstrahan\nCc @kalbasit\nCc @mdlayher\nCc @mic92\nCc @orivej\nCc @rvolosatovs\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166644/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166643","id":1188629677,"node_id":"I_kwDOAEVQ_M5G2Qyt","number":166643,"title":"Vulnerability roundup 112: go-1.16.13: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:50:27Z","updated_at":"2022-03-31T19:50:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24921](https://nvd.nist.gov/vuln/detail/CVE-2022-24921) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-27191](https://nvd.nist.gov/vuln/detail/CVE-2022-27191) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24921\n\nregexp.Compile in Go before 1.16.15 and 1.17.x before 1.17.8 allows stack exhaustion via a deeply nested expression.\n\n### CVE-2022-27191\n\ngolang.org/x/crypto/ssh before 0.0.0-20220314234659-1baeb1ce4c0b in Go through 1.16.15 and 1.17.x through 1.17.8 allows an attacker to crash a server in certain circumstances involving AddHostKey.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @Frostman\nCc @c00w\nCc @cstrahan\nCc @kalbasit\nCc @mdlayher\nCc @mic92\nCc @orivej\nCc @rvolosatovs\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166643/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166641","id":1188629507,"node_id":"I_kwDOAEVQ_M5G2QwD","number":166641,"title":"Vulnerability roundup 112: glibc-2.33-117: 3 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:50:22Z","updated_at":"2022-03-31T19:50:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=glibc&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=glibc+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23218](https://nvd.nist.gov/vuln/detail/CVE-2022-23218) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2022-23219](https://nvd.nist.gov/vuln/detail/CVE-2022-23219) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-38604](https://nvd.nist.gov/vuln/detail/CVE-2021-38604) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23218\n\nThe deprecated compatibility function svcunix_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its path argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n### CVE-2022-23219\n\nThe deprecated compatibility function clnt_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its hostname argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n### CVE-2021-38604\n\nIn librt in the GNU C Library (aka glibc) through 2.34, sysdeps/unix/sysv/linux/mq_notify.c mishandles certain NOTIFY_REMOVED data, leading to a NULL pointer dereference. NOTE: this vulnerability was introduced as a side effect of the CVE-2021-33574 fix.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @edolstra\nCc @ma27\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166641/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166640","id":1188629441,"node_id":"I_kwDOAEVQ_M5G2QvB","number":166640,"title":"Vulnerability roundup 112: gitea-1.15.11: 2 advisories [7.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:50:20Z","updated_at":"2022-03-31T19:50:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gitea&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gitea+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0905](https://nvd.nist.gov/vuln/detail/CVE-2022-0905) CVSSv3=7.1 (nixos-21.11)\n* [ ] [CVE-2022-1058](https://nvd.nist.gov/vuln/detail/CVE-2022-1058) CVSSv3=6.1 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0905\n\nImproper Authorization in GitHub repository go-gitea/gitea prior to 1.16.4.\n\n### CVE-2022-1058\n\nOpen Redirect on login in GitHub repository go-gitea/gitea prior to 1.16.5.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @disassembler\nCc @kolaente\nCc @ma27\nCc @techknowlogick\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166640/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166635","id":1188629054,"node_id":"I_kwDOAEVQ_M5G2Qo-","number":166635,"title":"Vulnerability roundup 112: envoy-1.17.3: 7 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T19:50:08Z","updated_at":"2022-03-31T19:50:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=envoy&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=envoy+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21654](https://nvd.nist.gov/vuln/detail/CVE-2022-21654) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2021-43824](https://nvd.nist.gov/vuln/detail/CVE-2021-43824) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2021-43825](https://nvd.nist.gov/vuln/detail/CVE-2021-43825) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2021-43826](https://nvd.nist.gov/vuln/detail/CVE-2021-43826) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-21655](https://nvd.nist.gov/vuln/detail/CVE-2022-21655) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-21657](https://nvd.nist.gov/vuln/detail/CVE-2022-21657) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21656](https://nvd.nist.gov/vuln/detail/CVE-2022-21656) CVSSv3=5.9 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-21654\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. Envoy's tls allows re-use when some cert validation settings have changed from their default configuration. The only workaround for this issue is to ensure that default tls settings are used. Users are advised to upgrade.\n\n### CVE-2021-43824\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. In affected versions a crafted request crashes Envoy when a CONNECT request is sent to JWT filter configured with regex match. This provides a denial of service attack vector. The only workaround is to not use regex in the JWT filter. Users are advised to upgrade.\n\n### CVE-2021-43825\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. Sending a locally generated response must stop further processing of request or response data. Envoy tracks the amount of buffered request and response data and aborts the request if the amount of buffered data is over the limit by sending 413 or 500 responses. However when the buffer overflows while response is processed by the filter chain the operation may not be aborted correctly and result in accessing a freed memory block. If this happens Envoy will crash resulting in a denial of service.\n\n### CVE-2021-43826\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. In affected versions of Envoy a crash occurs when configured for :ref:`upstream tunneling <envoy_v3_api_field_extensions.filters.network.tcp_proxy.v3.TcpProxy.tunneling_config>` and the downstream connection disconnects while the the upstream connection or http/2 stream is still being established. There are no workarounds for this issue. Users are advised to upgrade.\n\n### CVE-2022-21655\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. The envoy common router will segfault if an internal redirect selects a route configured with direct response or redirect actions. This will result in a denial of service. As a workaround turn off internal redirects if direct response entries are configured on the same listener.\n\n### CVE-2022-21657\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. In affected versions Envoy does not restrict the set of certificates it accepts from the peer, either as a TLS client or a TLS server, to only those certificates that contain the necessary extendedKeyUsage (id-kp-serverAuth and id-kp-clientAuth, respectively). This means that a peer may present an e-mail certificate (e.g. id-kp-emailProtection), either as a leaf certificate or as a CA in the chain, and it will be accepted for TLS. This is particularly bad when combined with the issue described in pull request #630, in that it allows a Web PKI CA that is intended only for use with S/MIME, and thus exempted from audit or supervision, to issue TLS certificates that will be accepted by Envoy. As a result Envoy will trust upstream certificates that should not be trusted. There are no known workarounds to this issue. Users are advised to upgrade.\n\n### CVE-2022-21656\n\nEnvoy is an open source edge and service proxy, designed for cloud-native applications. The default_validator.cc implementation used to implement the default certificate validation routines has a \"type confusion\" bug when processing subjectAltNames. This processing allows, for example, an rfc822Name or uniformResourceIndicator to be authenticated as a domain name. This confusion allows for the bypassing of nameConstraints, as processed by the underlying OpenSSL/BoringSSL implementation, exposing the possibility of impersonation of arbitrary servers. As a result Envoy will trust upstream certificates that should not be trusted.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @lukegb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166635/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166634","id":1188628980,"node_id":"I_kwDOAEVQ_M5G2Qn0","number":166634,"title":"Vulnerability roundup 112: edk2-202202: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:50:06Z","updated_at":"2022-03-31T19:50:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=edk2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=edk2+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-38578](https://nvd.nist.gov/vuln/detail/CVE-2021-38578) CVSSv3=9.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-38578\n\nExisting CommBuffer checks in SmmEntryPoint will not catch underflow when computing BufferSize.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166634/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166633","id":1188628906,"node_id":"I_kwDOAEVQ_M5G2Qmq","number":166633,"title":"Vulnerability roundup 112: edk2-202108: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:50:03Z","updated_at":"2022-03-31T19:50:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=edk2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=edk2+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-38578](https://nvd.nist.gov/vuln/detail/CVE-2021-38578) CVSSv3=9.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-38578\n\nExisting CommBuffer checks in SmmEntryPoint will not catch underflow when computing BufferSize.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166633/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166632","id":1188628835,"node_id":"I_kwDOAEVQ_M5G2Qlj","number":166632,"title":"Vulnerability roundup 112: drogon-1.7.4: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:50:01Z","updated_at":"2022-03-31T19:50:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=drogon&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=drogon+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-25297](https://nvd.nist.gov/vuln/detail/CVE-2022-25297) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-25297\n\nThis affects the package drogonframework/drogon before 1.7.5. The unsafe handling of file names during upload using HttpFile::save() method may enable attackers to write files to arbitrary locations outside the designated target folder.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @urlordjames\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166632/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166631","id":1188628767,"node_id":"I_kwDOAEVQ_M5G2Qkf","number":166631,"title":"Vulnerability roundup 112: drill-0.7.2: 1 advisory [5.4]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:49:59Z","updated_at":"2022-03-31T19:50:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=drill&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=drill+in%3Apath&type=Code)\n\n* [ ] [CVE-2017-12630](https://nvd.nist.gov/vuln/detail/CVE-2017-12630) CVSSv3=5.4 (nixos-unstable)\n\n## CVE details\n\n### CVE-2017-12630\n\nIn Apache Drill 1.11.0 and earlier when submitting form from Query page users are able to pass arbitrary script or HTML which will take effect on Profile page afterwards. Example: after submitting special script that returns cookie information from Query page, malicious user may obtain this information from Profile page afterwards.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @Br1ght0ne\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166631/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166629","id":1188617492,"node_id":"I_kwDOAEVQ_M5G2N0U","number":166629,"title":"Vulnerability roundup 112: discourse-2.9.0.beta1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:33Z","updated_at":"2022-03-31T19:44:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=discourse&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=discourse+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-41082](https://nvd.nist.gov/vuln/detail/CVE-2021-41082) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-41082\n\nDiscourse is a platform for community discussion. In affected versions any private message that includes a group had its title and participating user exposed to users that do not have access to the private messages. However, access control for the private messages was not compromised as users were not able to view the posts in the leaked private message despite seeing it in their inbox. The problematic commit was reverted around 32 minutes after it was made. Users are encouraged to upgrade to the latest commit if they are running Discourse against the `tests-passed` branch.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @talyz\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166629/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166627","id":1188617257,"node_id":"I_kwDOAEVQ_M5G2Nwp","number":166627,"title":"Vulnerability roundup 112: cri-o-1.22.1: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:27Z","updated_at":"2022-03-31T19:44:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=cri-o&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=cri-o+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0811](https://nvd.nist.gov/vuln/detail/CVE-2022-0811) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0811\n\nA flaw was found in CRI-O in the way it set kernel options for a pod. This issue allows anyone with rights to deploy a pod on a Kubernetes cluster that uses the CRI-O runtime to achieve a container escape and arbitrary code execution as root on the cluster node, where the malicious pod was deployed.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @adisbladis\nCc @kalbasit\nCc @saschagrunert\nCc @vdemeester\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166627/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166625","id":1188617123,"node_id":"I_kwDOAEVQ_M5G2Nuj","number":166625,"title":"Vulnerability roundup 112: containerd-1.5.9: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:23Z","updated_at":"2022-03-31T19:44:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=containerd&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=containerd+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23648](https://nvd.nist.gov/vuln/detail/CVE-2022-23648) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23648\n\ncontainerd is a container runtime available as a daemon for Linux and Windows. A bug was found in containerd prior to versions 1.6.1, 1.5.10, and 1.14.12 where containers launched through containerd’s CRI implementation on Linux with a specially-crafted image configuration could gain access to read-only copies of arbitrary files and directories on the host. This may bypass any policy-based enforcement on container setup (including a Kubernetes Pod Security Policy) and expose potentially sensitive information. Kubernetes and crictl can both be configured to use containerd’s CRI implementation. This bug has been fixed in containerd 1.6.1, 1.5.10, and 1.4.12. Users should update to these versions to resolve the issue.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @endocrimes\nCc @kalbasit\nCc @offlinehacker\nCc @vdemeester\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166625/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166624","id":1188617066,"node_id":"I_kwDOAEVQ_M5G2Ntq","number":166624,"title":"Vulnerability roundup 112: containerd-1.4.11: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:21Z","updated_at":"2022-04-21T10:18:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=containerd&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=containerd+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23648](https://nvd.nist.gov/vuln/detail/CVE-2022-23648) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23648\n\ncontainerd is a container runtime available as a daemon for Linux and Windows. A bug was found in containerd prior to versions 1.6.1, 1.5.10, and 1.14.12 where containers launched through containerd’s CRI implementation on Linux with a specially-crafted image configuration could gain access to read-only copies of arbitrary files and directories on the host. This may bypass any policy-based enforcement on container setup (including a Kubernetes Pod Security Policy) and expose potentially sensitive information. Kubernetes and crictl can both be configured to use containerd’s CRI implementation. This bug has been fixed in containerd 1.6.1, 1.5.10, and 1.4.12. Users should update to these versions to resolve the issue.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166624/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166623","id":1188616998,"node_id":"I_kwDOAEVQ_M5G2Nsm","number":166623,"title":"Vulnerability roundup 112: consul-1.10.3: 1 advisory [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:19Z","updated_at":"2022-03-31T19:44:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=consul&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=consul+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24687](https://nvd.nist.gov/vuln/detail/CVE-2022-24687) CVSSv3=6.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-24687\n\nHashiCorp Consul and Consul Enterprise 1.8.0 through 1.9.14, 1.10.7, and 1.11.2 has Uncontrolled Resource Consumption.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @kalbasit\nCc @nh2\nCc @pradeepchhetri\nCc @vdemeester\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166623/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166622","id":1188616924,"node_id":"I_kwDOAEVQ_M5G2Nrc","number":166622,"title":"Vulnerability roundup 112: clickhouse-21.8.8.29: 7 advisories [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:16Z","updated_at":"2022-03-31T19:44:17Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=clickhouse&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=clickhouse+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-43304](https://nvd.nist.gov/vuln/detail/CVE-2021-43304) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2021-43305](https://nvd.nist.gov/vuln/detail/CVE-2021-43305) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2021-42387](https://nvd.nist.gov/vuln/detail/CVE-2021-42387) CVSSv3=8.1 (nixos-21.11)\n* [ ] [CVE-2021-42388](https://nvd.nist.gov/vuln/detail/CVE-2021-42388) CVSSv3=8.1 (nixos-21.11)\n* [ ] [CVE-2021-42389](https://nvd.nist.gov/vuln/detail/CVE-2021-42389) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2021-42390](https://nvd.nist.gov/vuln/detail/CVE-2021-42390) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2021-42391](https://nvd.nist.gov/vuln/detail/CVE-2021-42391) CVSSv3=6.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-43304\n\nHeap buffer overflow in Clickhouse's LZ4 compression codec when parsing a malicious query. There is no verification that the copy operations in the LZ4::decompressImpl loop and especially the arbitrary copy operation wildCopy<copy_amount>(op, ip, copy_end), don’t exceed the destination buffer’s limits.\n\n### CVE-2021-43305\n\nHeap buffer overflow in Clickhouse's LZ4 compression codec when parsing a malicious query. There is no verification that the copy operations in the LZ4::decompressImpl loop and especially the arbitrary copy operation wildCopy<copy_amount>(op, ip, copy_end), don’t exceed the destination buffer’s limits. This issue is very similar to CVE-2021-43304, but the vulnerable copy operation is in a different wildCopy call.\n\n### CVE-2021-42387\n\nHeap out-of-bounds read in Clickhouse's LZ4 compression codec when parsing a malicious query. As part of the LZ4::decompressImpl() loop, a 16-bit unsigned user-supplied value ('offset') is read from the compressed data. The offset is later used in the length of a copy operation, without checking the upper bounds of the source of the copy operation.\n\n### CVE-2021-42388\n\nHeap out-of-bounds read in Clickhouse's LZ4 compression codec when parsing a malicious query. As part of the LZ4::decompressImpl() loop, a 16-bit unsigned user-supplied value ('offset') is read from the compressed data. The offset is later used in the length of a copy operation, without checking the lower bounds of the source of the copy operation.\n\n### CVE-2021-42389\n\nDivide-by-zero in Clickhouse's Delta compression codec when parsing a malicious query. The first byte of the compressed buffer is used in a modulo operation without being checked for 0.\n\n### CVE-2021-42390\n\nDivide-by-zero in Clickhouse's DeltaDouble compression codec when parsing a malicious query. The first byte of the compressed buffer is used in a modulo operation without being checked for 0.\n\n### CVE-2021-42391\n\nDivide-by-zero in Clickhouse's Gorilla compression codec when parsing a malicious query. The first byte of the compressed buffer is used in a modulo operation without being checked for 0.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @orivej\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166622/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166621","id":1188616860,"node_id":"I_kwDOAEVQ_M5G2Nqc","number":166621,"title":"Vulnerability roundup 112: calibre-web-0.6.16: 2 advisories [9.9]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:14Z","updated_at":"2022-03-31T19:44:15Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=calibre-web&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=calibre-web+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0767](https://nvd.nist.gov/vuln/detail/CVE-2022-0767) CVSSv3=9.9 (nixos-unstable)\n* [ ] [CVE-2022-0766](https://nvd.nist.gov/vuln/detail/CVE-2022-0766) CVSSv3=9.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0767\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.17.\n\n### CVE-2022-0766\n\nServer-Side Request Forgery (SSRF) in GitHub repository janeczku/calibre-web prior to 0.6.17.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @pborzenkov\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166621/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166618","id":1188616622,"node_id":"I_kwDOAEVQ_M5G2Nmu","number":166618,"title":"Vulnerability roundup 112: blender-2.93.5: 2 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:07Z","updated_at":"2022-03-31T19:44:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=blender&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=blender+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0545](https://nvd.nist.gov/vuln/detail/CVE-2022-0545) CVSSv3=7.8 (nixos-21.11)\n* [ ] [CVE-2022-0544](https://nvd.nist.gov/vuln/detail/CVE-2022-0544) CVSSv3=5.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0545\n\nAn integer overflow in the processing of loaded 2D images leads to a write-what-where vulnerability and an out-of-bounds read vulnerability, allowing an attacker to leak sensitive information or achieve code execution in the context of the Blender process when a specially crafted image file is loaded. This flaw affects Blender versions prior to 2.83.19, 2.93.8 and 3.1.\n\n### CVE-2022-0544\n\nAn integer underflow in the DDS loader of Blender leads to an out-of-bounds read, possibly allowing an attacker to read sensitive data using a crafted DDS image file. This flaw affects Blender versions prior to 2.83.19, 2.93.8 and 3.1.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @cillianderoiste\nCc @veprbl\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166618/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166617","id":1188616550,"node_id":"I_kwDOAEVQ_M5G2Nlm","number":166617,"title":"Vulnerability roundup 112: bento4-1.6.0-639: 1 advisory [8.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:05Z","updated_at":"2022-03-31T19:44:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=bento4&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=bento4+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-27607](https://nvd.nist.gov/vuln/detail/CVE-2022-27607) CVSSv3=8.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-27607\n\nBento4 1.6.0-639 has a heap-based buffer over-read in the AP4_HvccAtom class, a different issue than CVE-2018-14531.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe; nixos-unstable: 710fed5a248.\n\nCc @makefu\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166617/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166616","id":1188616487,"node_id":"I_kwDOAEVQ_M5G2Nkn","number":166616,"title":"Vulnerability roundup 112: archivy-1.4.0: 1 advisory [6.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:03Z","updated_at":"2022-03-31T19:44:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=archivy&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=archivy+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0697](https://nvd.nist.gov/vuln/detail/CVE-2022-0697) CVSSv3=6.1 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0697\n\nOpen Redirect in GitHub repository archivy/archivy prior to 1.7.0.\n\n-----\nScanned versions: nixos-21.11: efea022d6fe.\n\nCc @siraben\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166616/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166615","id":1188616417,"node_id":"I_kwDOAEVQ_M5G2Njh","number":166615,"title":"Vulnerability roundup 112: archisteamfarm-5.2.2.4: 1 advisory [6.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T19:44:01Z","updated_at":"2022-03-31T19:44:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=archisteamfarm&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=archisteamfarm+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23627](https://nvd.nist.gov/vuln/detail/CVE-2022-23627) CVSSv3=6.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23627\n\nArchiSteamFarm (ASF) is a C# application with primary purpose of idling Steam cards from multiple accounts simultaneously. Due to a bug in ASF code, introduced in version V5.2.2.2, the program didn't adequately verify effective access of the user sending proxy (i.e. `[Bots]`) commands. In particular, a proxy-like command sent to bot `A` targeting bot `B` has incorrectly verified user's access against bot `A` - instead of bot `B`, to which the command was originally designated. This in result allowed access to resources beyond those configured, being a security threat affecting confidentiality of other bot instances. A successful attack exploiting this bug requires a significant access granted explicitly by original owner of the ASF process prior to that, as attacker has to control at least a single bot in the process to make use of this inadequate access verification loophole. The issue is patched in ASF V5.2.2.5, V5.2.3.2 and future versions. Users are advised to update as soon as possible.\n\n-----\nScanned versions: nixos-unstable: 710fed5a248.\n\nCc @SuperSandro2000\nCc @legendofmiracles\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166615/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166604","id":1188459817,"node_id":"I_kwDOAEVQ_M5G1nUp","number":166604,"title":"llvmPackages_14.lldb: broken, \"ModuleNotFoundError: No module named 'lldb'\"","user":{"login":"dtzWill","id":817330,"node_id":"MDQ6VXNlcjgxNzMzMA==","avatar_url":"https://avatars.githubusercontent.com/u/817330?v=4","gravatar_id":"","url":"https://api.github.com/users/dtzWill","html_url":"https://github.com/dtzWill","followers_url":"https://api.github.com/users/dtzWill/followers","following_url":"https://api.github.com/users/dtzWill/following{/other_user}","gists_url":"https://api.github.com/users/dtzWill/gists{/gist_id}","starred_url":"https://api.github.com/users/dtzWill/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dtzWill/subscriptions","organizations_url":"https://api.github.com/users/dtzWill/orgs","repos_url":"https://api.github.com/users/dtzWill/repos","events_url":"https://api.github.com/users/dtzWill/events{/privacy}","received_events_url":"https://api.github.com/users/dtzWill/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-31T18:18:05Z","updated_at":"2022-04-01T21:24:27Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`lldb` from `llvmPackages_14.lldb` seems to be broken, reporting:\r\n\r\n```console\r\n$ lldb --version\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nModuleNotFoundError: No module named 'lldb'\r\nlldb version 14.0.0\r\n```\r\n\r\nThis error is present in all invocations of `lldb` I've tried: with no arguments, pointed at an executable, and debugging a coredump (`SYSTEMD_DEBUGGER=lldb` for `coredumpctl debug`(/gdb), FWIW).\r\n\r\nCoredump usage is worse, with something like:\r\n\r\n```\r\n$ coredump debug\r\n...<<snip>>...\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nModuleNotFoundError: No module named 'lldb'\r\n(lldb) target create \"<<redacted>>\" --core \"/var/tmp/coredump-VXmhXt\"\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nNameError: name 'run_one_line' is not defined\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nNameError: name 'run_one_line' is not defined\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nNameError: name 'run_one_line' is not defined\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nNameError: name 'run_one_line' is not defined\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nNameError: name 'run_one_line' is not defined\r\n\r\nCore file '/var/tmp/coredump-VXmhXt' (x86_64) was loaded.\r\n(lldb)\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `lldb --version` or other `lldb` invocations, until this is fixed this works: `nix run nixpkgs#llvmPackages_14.lldb -- --version`.\r\n2. Note the messages as described above\r\n\r\n### Expected behavior\r\n\r\nLLDB doesn't show this error, and presumably whatever functionality triggering this isn't working properly but I haven't tried using it after the error(s) are printed.\r\n\r\n### Additional context\r\n\r\nAnother LLVM14 package to fix before this is ready for use:\r\n\r\ncc https://github.com/NixOS/nixpkgs/pull/165701\r\n\r\n### Notify maintainers\r\n\r\n@lovek323 @7c6f434c @dtzWill @primeos \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka), 22.05pre364898.00e27c78d3d`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220330_2252272`\r\n - channels(will): `\"\"`\r\n - channels(root): `\"home-manager, nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166604/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166553","id":1187929681,"node_id":"I_kwDOAEVQ_M5Gzl5R","number":166553,"title":"haskell.compiler.ghcjs has a broken dependency","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":436938058,"node_id":"MDU6TGFiZWw0MzY5MzgwNTg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20regression","name":"0.kind: regression","color":"84b6eb","default":false,"description":"Something that worked before working no longer"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-31T11:23:00Z","updated_at":"2022-04-02T15:00:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nAs a fallout of the migration to GHC 9.0.2 `webdriver` got marked as broken, as it failed to build with GHC 9.0.2 and the\r\nStackage LTS 19 package set we now have. It would be necessary to investigate if `ghcjs` survived this (i.e. if it still\r\nbuilds) and if not to get it to work again.\r\n\r\n```\r\nnix-instantiate -A haskell.compiler.ghcjs\r\nerror: Package ‘webdriver-0.9.0.1’ in /home/lukas/src/nix/nixpkgs/pkgs/development/haskell-modules/hackage-packages.nix:292014 is marked as broken, refusing to evaluate.\r\n\r\na) To temporarily allow broken packages, you can use an environment variable\r\n for a single invocation of the nix tools.\r\n\r\n $ export NIXPKGS_ALLOW_BROKEN=1\r\n \r\n Note: For `nix shell`, `nix build`, `nix develop` or any other Nix 2.4+\r\n (Flake) command, `--impure` must be passed in order to read this\r\n environment variable.\r\n \r\nb) For `nixos-rebuild` you can set\r\n { nixpkgs.config.allowBroken = true; }\r\nin configuration.nix to override this.\r\n\r\nc) For `nix-env`, `nix-build`, `nix-shell` or any other Nix command you can add\r\n { allowBroken = true; }\r\nto ~/.config/nixpkgs/config.nix.\r\n\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\ncc @dfordivam @obsidian-systems-maintenance","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166553/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166545","id":1187789319,"node_id":"I_kwDOAEVQ_M5GzDoH","number":166545,"title":"Tuist","user":{"login":"nagra-gs","id":101186170,"node_id":"U_kgDOBgf6eg","avatar_url":"https://avatars.githubusercontent.com/u/101186170?v=4","gravatar_id":"","url":"https://api.github.com/users/nagra-gs","html_url":"https://github.com/nagra-gs","followers_url":"https://api.github.com/users/nagra-gs/followers","following_url":"https://api.github.com/users/nagra-gs/following{/other_user}","gists_url":"https://api.github.com/users/nagra-gs/gists{/gist_id}","starred_url":"https://api.github.com/users/nagra-gs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nagra-gs/subscriptions","organizations_url":"https://api.github.com/users/nagra-gs/orgs","repos_url":"https://api.github.com/users/nagra-gs/repos","events_url":"https://api.github.com/users/nagra-gs/events{/privacy}","received_events_url":"https://api.github.com/users/nagra-gs/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T09:32:59Z","updated_at":"2022-04-07T20:29:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nTuist helps manage the structure and dependencies of a Xcode project.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://tuist.io/\r\n* source URL: https://github.com/tuist/tuist/archive/refs/tags/3.1.0.zip\r\n* license: mit\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166545/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166542","id":1187736244,"node_id":"I_kwDOAEVQ_M5Gy2q0","number":166542,"title":"Jami daemon as a service","user":{"login":"Munksgaard","id":230613,"node_id":"MDQ6VXNlcjIzMDYxMw==","avatar_url":"https://avatars.githubusercontent.com/u/230613?v=4","gravatar_id":"","url":"https://api.github.com/users/Munksgaard","html_url":"https://github.com/Munksgaard","followers_url":"https://api.github.com/users/Munksgaard/followers","following_url":"https://api.github.com/users/Munksgaard/following{/other_user}","gists_url":"https://api.github.com/users/Munksgaard/gists{/gist_id}","starred_url":"https://api.github.com/users/Munksgaard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Munksgaard/subscriptions","organizations_url":"https://api.github.com/users/Munksgaard/orgs","repos_url":"https://api.github.com/users/Munksgaard/repos","events_url":"https://api.github.com/users/Munksgaard/events{/privacy}","received_events_url":"https://api.github.com/users/Munksgaard/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T08:56:47Z","updated_at":"2022-03-31T08:56:47Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Jami daemon as a service**\r\n\r\nIn addition to various clients, we currently package jami-daemon, although it's not really usable in it's current form. For one, it doesn't output the binary in the `bin` folder as you'd expect, meaning that `jamid` is not correctly brought into scope. Instead the binary resides in `libexec`. Apart from fixing this, though, jami-daemon would be much more usable if it was a service you could enable.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://jami.net/\r\n* source URL: https://github.com/NixOS/nixpkgs/blob/nixos-unstable/pkgs/applications/networking/instant-messengers/jami/daemon.nix#L133\r\n* license: [](https://spdx.org/licenses)GNU General Public License v3.0 or later\r\n* platforms: unix, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166542/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166517","id":1187404121,"node_id":"I_kwDOAEVQ_M5GxllZ","number":166517,"title":"Package Request: EnvKey (E2EE Configuration & Secrets Manager)","user":{"login":"byrongibson","id":275081,"node_id":"MDQ6VXNlcjI3NTA4MQ==","avatar_url":"https://avatars.githubusercontent.com/u/275081?v=4","gravatar_id":"","url":"https://api.github.com/users/byrongibson","html_url":"https://github.com/byrongibson","followers_url":"https://api.github.com/users/byrongibson/followers","following_url":"https://api.github.com/users/byrongibson/following{/other_user}","gists_url":"https://api.github.com/users/byrongibson/gists{/gist_id}","starred_url":"https://api.github.com/users/byrongibson/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/byrongibson/subscriptions","organizations_url":"https://api.github.com/users/byrongibson/orgs","repos_url":"https://api.github.com/users/byrongibson/repos","events_url":"https://api.github.com/users/byrongibson/events{/privacy}","received_events_url":"https://api.github.com/users/byrongibson/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-31T02:21:27Z","updated_at":"2022-03-31T02:23:11Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nEnvKey is an end-to-end encrypted configuration and secrets manager. It protects your organization's API keys, encryption keys, credentials, and other secrets, and makes it easy to run servers, scripts, tests, and everything else with the latest config. It also helps you avoid duplication in your configuration, react to environment updates in real-time, resolve conflicts smoothly, and a lot more.\r\n\r\nYou get an intuitive, spreadsheet-like UI for managing environments, along with a developer-friendly CLI that does almost anything the UI can. Run any program in any language with the latest environment variables.\r\n\r\nSecurely manage both configuration and secrets across environments, servers, and development machines all in one place.\r\nUse a cross-platform UI and developer-friendly CLI to set environment variables, manage access, revert to previous versions, review audit logs, prevent duplication, build automations, and more.\r\n\r\nEnvKey's client-side end-to-end encryption is built with the NaCl crypto library. Whether you use EnvKey Cloud or host EnvKey yourself, no configuration or secrets are ever sent to the host running EnvKey in plaintext. Public keys are verified by a web of trust. Invitations are verified out-of-band. Secrets are never accessed through a web browser. More details on security and encryption can be found here: https://docs-v2.envkey.com/docs/security\r\n\r\nAdditional examples and discussion: https://news.ycombinator.com/item?id=30855879\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://envkey.com/\r\n* source URL: https://github.com/envkey/envkey\r\n* license: mit\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166517/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166499","id":1187194545,"node_id":"I_kwDOAEVQ_M5Gwyax","number":166499,"title":"nixos-rebuild fails cross-build a flake","user":{"login":"wentasah","id":140542,"node_id":"MDQ6VXNlcjE0MDU0Mg==","avatar_url":"https://avatars.githubusercontent.com/u/140542?v=4","gravatar_id":"","url":"https://api.github.com/users/wentasah","html_url":"https://github.com/wentasah","followers_url":"https://api.github.com/users/wentasah/followers","following_url":"https://api.github.com/users/wentasah/following{/other_user}","gists_url":"https://api.github.com/users/wentasah/gists{/gist_id}","starred_url":"https://api.github.com/users/wentasah/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wentasah/subscriptions","organizations_url":"https://api.github.com/users/wentasah/orgs","repos_url":"https://api.github.com/users/wentasah/repos","events_url":"https://api.github.com/users/wentasah/events{/privacy}","received_events_url":"https://api.github.com/users/wentasah/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-30T23:57:35Z","updated_at":"2022-04-07T20:28:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`nixos-rebuild` does not work when when building a flake and the host and target systems are not the same.\r\n\r\nThe problem was originally posted by @chvp in https://github.com/NixOS/nixpkgs/issues/153981#issuecomment-1083128534.\r\n\r\n### Steps To Reproduce\r\n\r\n1. On a Darwin system run: `darwin# nixos-rebuild switch --flake ... --build-host linuxhost --target-host linuxhost --config ...`\r\n2. Observe this error: `error: a 'x86_64-linux' with features {} is required to build '/nix/store/yq1xkqyhb6qh9z4j1bw7b9kdfb0qai2z-nixos-rebuild.drv', but I am a 'aarch64-darwin' with features {benchmark, big-parallel, nixos-test}` \r\n\r\n(@chvp, please correct the above if it's not what you are doing. I don't have a darwin system to test that.)\r\n\r\n### Expected behavior\r\nNo error is produced as was the case before #153981.\r\n\r\n### Additional context\r\n\r\nRecently, `nixos-rebuild` [gained a feature](https://github.com/NixOS/nixpkgs/pull/153981) to reexecute a new version of itself, before building a flake system. This is the same thing that's being done for non-flake systems. The TODO comment requesting addition of the same thing for flakes [was added here](https://github.com/NixOS/nixpkgs/commit/22cc7ab78c3e45ebbb1ec66be6c5b9c7f47f780d#diff-4efef885a98a7c3dcdc7c4cb4fcaa10480fdc0da3627afaa8f5513edc068ab35R240).\r\n\r\nOne way of resolving the issue could be to disable reexecution if the host and target systems are different. However, I'm not sure whether it's a good thing to have different behavior between cross and native builds. I think that it's generally not possible to build a host version of `nixos-rebuild` to reexecute itself, because the flake being built for the target host might not have any configuration for the host system, just a configuration for the target. Maybe, I'm missing something. Any suggestions?\r\n\r\n### Notify maintainers\r\n\r\n@Profpatsch (@Enzime @Infinisil)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166499/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166467","id":1186956539,"node_id":"I_kwDOAEVQ_M5Gv4T7","number":166467,"title":"Cannot execute dotnet generated binary files on NixOS ","user":{"login":"SDAChess","id":44714756,"node_id":"MDQ6VXNlcjQ0NzE0NzU2","avatar_url":"https://avatars.githubusercontent.com/u/44714756?v=4","gravatar_id":"","url":"https://api.github.com/users/SDAChess","html_url":"https://github.com/SDAChess","followers_url":"https://api.github.com/users/SDAChess/followers","following_url":"https://api.github.com/users/SDAChess/following{/other_user}","gists_url":"https://api.github.com/users/SDAChess/gists{/gist_id}","starred_url":"https://api.github.com/users/SDAChess/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SDAChess/subscriptions","organizations_url":"https://api.github.com/users/SDAChess/orgs","repos_url":"https://api.github.com/users/SDAChess/repos","events_url":"https://api.github.com/users/SDAChess/events{/privacy}","received_events_url":"https://api.github.com/users/SDAChess/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-30T20:32:39Z","updated_at":"2022-03-30T20:39:06Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen trying to execute dotnet generated binaries, the dotnet linker fails to find the root of the dotnet installation (DOTNET_ROOT).\r\n\r\n### Steps To Reproduce\r\n\r\nCreate the following files:\r\nTest.csproj\r\n```xml\r\n<Project Sdk=\"Microsoft.NET.Sdk\">\r\n\r\n <PropertyGroup>\r\n <OutputType>Exe</OutputType>\r\n <TargetFramework>net5.0</TargetFramework>\r\n </PropertyGroup>\r\n\r\n</Project>\r\n```\r\nProgram.cs\r\n```csharp\r\nusing System;\r\n\r\nclass TestClass\r\n{\r\n static void Main(string[] args)\r\n {\r\n Console.WriteLine(args.Length);\r\n }\r\n}\r\n```\r\nExecute ```dotnet build``` to compile the \"project\".\r\n\r\nExecuting ``dotnet run`` works fine but ``./bin/Debug/net5.0/Test`` crashes with the following error:\r\n```\r\nA fatal error occurred. The required library libhostfxr.so could not be found.\r\nIf this is a self-contained application, that library should exist in [/tmp/test/bin/Debug/net5.0/].\r\nIf this is a framework-dependent application, install the runtime in the global location [/usr/share/dotnet] or use the DOTNET_ROOT environment variable to specify the runtime location or register the runtime location in [/etc/dotnet/install_location].\r\n\r\nThe .NET runtime can be found at:\r\n - https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=nixos.21.11-x64&apphost_version=5.0.12\r\n```\r\nSetting the ``DOTNET_ROOT`` environment variable to the path given by ``whereis dotnet`` fixes the issue.\r\n\r\n### Additional context\r\nI tested this on ``dotnet-sdk_5`` and ``dotnet-sdk_6`` packages and both have the same issue.\r\n\r\n### Notify maintainers\r\n\r\nHello, @kuznero :wave: \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166467/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166459","id":1186898854,"node_id":"I_kwDOAEVQ_M5GvqOm","number":166459,"title":"automatic checks of the neovim config","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-30T19:33:04Z","updated_at":"2022-04-07T20:28:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nwhen building the neovim wrapper, we should make sure that the generated config can be started fine. \r\nI sometimes have to rebuild my system because I forgot a comma in the config, kinda annoying.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166459/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166440","id":1186731340,"node_id":"I_kwDOAEVQ_M5GvBVM","number":166440,"title":"NodeJS 12 EOL","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-30T16:48:59Z","updated_at":"2022-04-07T20:27:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"The NodeJS 12 release goes end-of-life on 2022-04-30, which needs handling before the next release.\r\n\r\nhttps://nodejs.org/en/about/releases/\r\n\r\nWorst case we update `knownVulnerabilities` like in f0b48706406b.\r\n\r\n@marsam @cko @gilligan @cillianderoiste ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166440/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166438","id":1186714041,"node_id":"I_kwDOAEVQ_M5Gu9G5","number":166438,"title":"Gnome Screen Autorotate not working after a recent upgrade","user":{"login":"astrojhgu","id":2651231,"node_id":"MDQ6VXNlcjI2NTEyMzE=","avatar_url":"https://avatars.githubusercontent.com/u/2651231?v=4","gravatar_id":"","url":"https://api.github.com/users/astrojhgu","html_url":"https://github.com/astrojhgu","followers_url":"https://api.github.com/users/astrojhgu/followers","following_url":"https://api.github.com/users/astrojhgu/following{/other_user}","gists_url":"https://api.github.com/users/astrojhgu/gists{/gist_id}","starred_url":"https://api.github.com/users/astrojhgu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/astrojhgu/subscriptions","organizations_url":"https://api.github.com/users/astrojhgu/orgs","repos_url":"https://api.github.com/users/astrojhgu/repos","events_url":"https://api.github.com/users/astrojhgu/events{/privacy}","received_events_url":"https://api.github.com/users/astrojhgu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-30T16:33:12Z","updated_at":"2022-04-07T20:27:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\nGnome Screen Autorotate not work.\r\nby using `journalctl -f`, some error message can be seen (see below)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install and enable `nixos.gnomeExtensions.screen-autorotate`\r\n2. rotate laptop in real world\r\n3. The screen does not rotate accordingly.\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nThe screen should be auto rotated according to the orientation of the laptop in the real world.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\nFollowing is a piece of message related, shown by `journalctl -f`\r\n```\r\nMar 31 00:29:42 x1yoga .gnome-shell-wr[1753]: Rotate screen to left-up\r\nMar 31 00:29:42 x1yoga gjs[126321]: cannot register existing type 'GCancellable'\r\nMar 31 00:29:42 x1yoga gjs[126321]: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\nMar 31 00:29:42 x1yoga gjs[126321]: g_once_init_leave: assertion 'result != 0' failed\r\nMar 31 00:29:44 x1yoga .gnome-shell-wr[1753]: Rotate screen to normal\r\nMar 31 00:29:44 x1yoga gjs[126335]: cannot register existing type 'GCancellable'\r\nMar 31 00:29:44 x1yoga gjs[126335]: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\nMar 31 00:29:44 x1yoga gjs[126335]: g_once_init_leave: assertion 'result != 0' failed\r\nMar 31 00:29:46 x1yoga .gnome-shell-wr[1753]: Rotate screen to right-up\r\nMar 31 00:29:46 x1yoga gjs[126349]: cannot register existing type 'GCancellable'\r\nMar 31 00:29:46 x1yoga gjs[126349]: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\nMar 31 00:29:46 x1yoga gjs[126349]: g_once_init_leave: assertion 'result != 0' failed\r\nMar 31 00:29:48 x1yoga .gnome-shell-wr[1753]: Rotate screen to normal\r\nMar 31 00:29:48 x1yoga gjs[126362]: cannot register existing type 'GCancellable'\r\nMar 31 00:29:48 x1yoga gjs[126362]: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\nMar 31 00:29:48 x1yoga gjs[126362]: g_once_init_leave: assertion 'result != 0' failed\r\n```\r\n\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\nThis abnormal condition happens since the latest upgrade.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@piegamesde \r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.29, NixOS, 22.05 (Quokka), 22.05pre364329.ce8cbe3c01f`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166438/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166416","id":1186419038,"node_id":"I_kwDOAEVQ_M5Gt1Fe","number":166416,"title":"Cross compiling v4l-utils for aarch64 fails","user":{"login":"cyber-murmel","id":30078229,"node_id":"MDQ6VXNlcjMwMDc4MjI5","avatar_url":"https://avatars.githubusercontent.com/u/30078229?v=4","gravatar_id":"","url":"https://api.github.com/users/cyber-murmel","html_url":"https://github.com/cyber-murmel","followers_url":"https://api.github.com/users/cyber-murmel/followers","following_url":"https://api.github.com/users/cyber-murmel/following{/other_user}","gists_url":"https://api.github.com/users/cyber-murmel/gists{/gist_id}","starred_url":"https://api.github.com/users/cyber-murmel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cyber-murmel/subscriptions","organizations_url":"https://api.github.com/users/cyber-murmel/orgs","repos_url":"https://api.github.com/users/cyber-murmel/repos","events_url":"https://api.github.com/users/cyber-murmel/events{/privacy}","received_events_url":"https://api.github.com/users/cyber-murmel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-30T12:55:03Z","updated_at":"2022-04-19T18:15:33Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCross compiling v4l-utils for aarch64 fails with\r\n```\r\nerror: attribute 'runtimeShell' missing, at /nix/store/pzl7yl8kf47lqnnqns8mzr22a3m8w7b8-ce8cbe3.tar.gz/pkgs/top-level/all-packages.nix:745:17\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```shell\r\n$ nix-build https://github.com/NixOS/nixpkgs/archive/ce8cbe3.tar.gz \\ # nixos-unstable Wed, 30 Mar 2022 12:48:45 +0000\r\n -A pkgsCross.aarch64-multiplatform.v4l-utils\r\n```\r\n\r\n### Expected behavior\r\nI expect a `result` symlink to v4l-utils.\r\n\r\n### Screenshots\r\nCross compilation on an x86 computer:\r\n\r\n\r\nNative build on aarch64 machine:\r\n\r\n\r\n### Notify maintainers\r\n@pSub\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(marble): `\"nixos-unstable-22.05pre356180.d5f23787297\"`\r\n - channels(root): `\"nixos-21.11.336673.d89f18a17e5\"`\r\n - channels(work): `\"nixos-unstable-21.11pre328987.c935f5e0add\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.15.29, NixOS, 22.05 (Quokka), 22.05pre-git`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(nixos): `\"\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166416/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166410","id":1186390493,"node_id":"I_kwDOAEVQ_M5GtuHd","number":166410,"title":"nvidia-x11-495.44-5.17 failed to build in latest update","user":{"login":"mudrii","id":220262,"node_id":"MDQ6VXNlcjIyMDI2Mg==","avatar_url":"https://avatars.githubusercontent.com/u/220262?v=4","gravatar_id":"","url":"https://api.github.com/users/mudrii","html_url":"https://github.com/mudrii","followers_url":"https://api.github.com/users/mudrii/followers","following_url":"https://api.github.com/users/mudrii/following{/other_user}","gists_url":"https://api.github.com/users/mudrii/gists{/gist_id}","starred_url":"https://api.github.com/users/mudrii/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mudrii/subscriptions","organizations_url":"https://api.github.com/users/mudrii/orgs","repos_url":"https://api.github.com/users/mudrii/repos","events_url":"https://api.github.com/users/mudrii/events{/privacy}","received_events_url":"https://api.github.com/users/mudrii/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null},{"id":436938058,"node_id":"MDU6TGFiZWw0MzY5MzgwNTg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20regression","name":"0.kind: regression","color":"84b6eb","default":false,"description":"Something that worked before working no longer"},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-30T12:31:54Z","updated_at":"2022-04-07T20:27:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nSystem update failed due to Nvidia driver build failure for nvidia-x11-495.44-5.17\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. update nixos nixos-rebuild switch\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\nInstall latest nvidia drivers for linux kernel linux-5.17\r\n\r\n### Screenshots\r\nError\r\n```\r\n CC [M] /build/kernel/nvidia/os-interface.o\r\n CC [M] /build/kernel/nvidia/os-mlock.o\r\n CC [M] /build/kernel/nvidia/os-pci.o\r\n/build/kernel/nvidia/nv-mmap.c: In function 'nv_encode_caching':\r\n/build/kernel/nvidia/nv-mmap.c:334:16: warning: this statement may fall through [8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wimplicit-fallthrough=-Wimplicit-fallthrough=8;;]\r\n 334 | if (NV_ALLOW_CACHING(memory_type))\r\n | ^\r\n/build/kernel/nvidia/nv-mmap.c:337:9: note: here\r\n 337 | default:\r\n | ^~~~~~~\r\n/build/kernel/nvidia/nv-dma.c:976: warning: \"IMPORT_SGT_STUBS_NEEDED\" redefined\r\n 976 | #define IMPORT_SGT_STUBS_NEEDED 0\r\n | \r\n/build/kernel/nvidia/nv-dma.c:970: note: this is the location of the previous definition\r\n 970 | #define IMPORT_SGT_STUBS_NEEDED 1\r\n | \r\nIn file included from /build/kernel/common/inc/nv-procfs.h:26,\r\n from /build/kernel/nvidia/nv-procfs.c:31:\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_gpu_info':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:29: error: implicit declaration of function 'PDE' [8;;https://gcc.gnu.org/onlinedocs/gcc/Warning-Options.html#index-Wimplicit-function-declaration-Werror=implicit-function-declaration8;;]\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:192:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 192 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(gpu_info);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:192:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 192 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(gpu_info);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_power':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:244:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 244 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(power);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_version':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:258:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 258 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(version);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_file':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/nvidia/nv-procfs.c:303:16: note: in expansion of macro 'NV_PDE_DATA'\r\n 303 | nvpp->nv = NV_PDE_DATA(inode);\r\n | ^~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_params':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:469:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 469 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(params);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c: In function 'nv_procfs_open_text_file':\r\n/build/kernel/common/inc/nv-procfs-utils.h:104:39: error: invalid type argument of '->' (have 'int')\r\n 104 | # define NV_PDE_DATA(inode) PDE(inode)->data\r\n | ^~\r\n/build/kernel/common/inc/nv-procfs-utils.h:126:27: note: in expansion of macro 'NV_PDE_DATA'\r\n 126 | NV_PDE_DATA(inode)); \\\r\n | ^~~~~~~~~~~\r\n/build/kernel/common/inc/nv-procfs-utils.h:150:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_HELPER'\r\n 150 | NV_DEFINE_SINGLE_PROCFS_FILE_HELPER(name, open_callback, close_callback)\\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:38:5: note: in expansion of macro 'NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY'\r\n 38 | NV_DEFINE_SINGLE_PROCFS_FILE_READ_ONLY(name, \\\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\n/build/kernel/nvidia/nv-procfs.c:1304:1: note: in expansion of macro 'NV_DEFINE_SINGLE_NVRM_PROCFS_FILE'\r\n 1304 | NV_DEFINE_SINGLE_NVRM_PROCFS_FILE(text_file);\r\n | ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\ncc1: some warnings being treated as errors\r\nmake[3]: *** [/nix/store/k0v44aqabwi50a9c1rcanfllgcxynrvj-linux-5.17-dev/lib/modules/5.17.0/source/scripts/Makefile.build:288: /build/kernel/nvidia/nv-procfs.o] Error 1\r\nmake[3]: *** Waiting for unfinished jobs....\r\nmake[2]: *** [/nix/store/k0v44aqabwi50a9c1rcanfllgcxynrvj-linux-5.17-dev/lib/modules/5.17.0/source/Makefile:1831: /build/kernel] Error 2\r\nmake[2]: Leaving directory '/nix/store/k0v44aqabwi50a9c1rcanfllgcxynrvj-linux-5.17-dev/lib/modules/5.17.0/build'\r\nmake[1]: *** [Makefile:219: __sub-make] Error 2\r\nmake[1]: Leaving directory '/nix/store/k0v44aqabwi50a9c1rcanfllgcxynrvj-linux-5.17-dev/lib/modules/5.17.0/source'\r\nmake: *** [Makefile:80: modules] Error 2\r\nerror: builder for '/nix/store/q0rjqmdfx1sh8d4qs7xdvawl1qwv5zwc-nvidia-x11-495.44-5.17.drv' failed with exit code 2\r\nerror: 1 dependencies of derivation '/nix/store/hrl7anrqbn8ppds4adk3rpfyvraphd0b-etc.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/fpigj45a8528yjscqbqg6j0j6z7g9ngd-linux-5.17-modules.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/5b7r63lbkkdzjg0yjrrpj3asy9fzzgpg-system-path.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/rz4qvnhqzm6b6dsp406c2lpz5cqf5bn9-nixos-system-p53-nixos-21.11.336735.9b168e5e624.drv' failed to build\r\n```\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n ~ nix-shell -p nix-info --run \"nix-info -m\" 171ms\r\nthis path will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/n32py8bgkgi73llcc57kffrnwnaf0vm4-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/n32py8bgkgi73llcc57kffrnwnaf0vm4-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.16, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"home-manage-21.11, home-manager-21.11, nixos-21.11.336735.9b168e5e624, unstable-22.05pre364329.ce8cbe3c01f\"`\r\n - channels(mudrii): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166410/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166405","id":1186295302,"node_id":"I_kwDOAEVQ_M5GtW4G","number":166405,"title":"opensubdiv: cmake configure fails with cuda11","user":{"login":"SomeoneSerge","id":9720532,"node_id":"MDQ6VXNlcjk3MjA1MzI=","avatar_url":"https://avatars.githubusercontent.com/u/9720532?v=4","gravatar_id":"","url":"https://api.github.com/users/SomeoneSerge","html_url":"https://github.com/SomeoneSerge","followers_url":"https://api.github.com/users/SomeoneSerge/followers","following_url":"https://api.github.com/users/SomeoneSerge/following{/other_user}","gists_url":"https://api.github.com/users/SomeoneSerge/gists{/gist_id}","starred_url":"https://api.github.com/users/SomeoneSerge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SomeoneSerge/subscriptions","organizations_url":"https://api.github.com/users/SomeoneSerge/orgs","repos_url":"https://api.github.com/users/SomeoneSerge/repos","events_url":"https://api.github.com/users/SomeoneSerge/events{/privacy}","received_events_url":"https://api.github.com/users/SomeoneSerge/received_events","type":"User","site_admin":false},"labels":[{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-30T11:09:42Z","updated_at":"2022-03-30T11:44:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nThe opensubdiv fails to configure when calling with `cudatoolkit_11`\r\nThe package is required for building blender with cuda support.\r\nThis issue probably supersedes https://github.com/NixOS/nixpkgs/issues/31426 where opensubdiv seems to have reached the build phase. \r\nBuild log: [/nix/store/73615l3kilb23l2497qj8lgsjffbgdwn-opensubdiv-3.4.4.drv](https://hercules-ci.com/accounts/github/SomeoneSerge/derivations/%2Fnix%2Fstore%2F73615l3kilb23l2497qj8lgsjffbgdwn-opensubdiv-3.4.4.drv/log?via-job=f5fc6166-1af1-4d2f-ae08-ad09efb62b6b)\r\nThe overlay: https://github.com/SomeoneSerge/nixpkgs-unfree/blob/2a18afff5689f8df6c481da95484e93dea70f491/configs.nix#L16\r\n\r\n### Steps to reproduce\r\n\r\n```nix\r\nwith (import ./. {\r\n config.allowUnfree = true;\r\n config.cudaSupport = true;\r\n overlays = [(final: prev: {\r\n cudatoolkit = final.cudatoolkit_11; # cf. https://github.com/SomeoneSerge/nixpkgs-unfree/blob/2a18afff5689f8df6c481da95484e93dea70f491/configs.nix#L16\r\n })];\r\n});\r\n\r\nmkShell {\r\n buildInputs = [\r\n blender\r\n ];\r\n}\r\n```\r\n\r\n## Notify maintainers\r\n\r\n- [cuda-maintainers](https://github.com/orgs/NixOS/teams/cuda-maintainers)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166405/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166404","id":1186291847,"node_id":"I_kwDOAEVQ_M5GtWCH","number":166404,"title":"xwayland apps on plasma wayland don't do layout switching while pressing caps_lock","user":{"login":"NANASHI0X74","id":17546398,"node_id":"MDQ6VXNlcjE3NTQ2Mzk4","avatar_url":"https://avatars.githubusercontent.com/u/17546398?v=4","gravatar_id":"","url":"https://api.github.com/users/NANASHI0X74","html_url":"https://github.com/NANASHI0X74","followers_url":"https://api.github.com/users/NANASHI0X74/followers","following_url":"https://api.github.com/users/NANASHI0X74/following{/other_user}","gists_url":"https://api.github.com/users/NANASHI0X74/gists{/gist_id}","starred_url":"https://api.github.com/users/NANASHI0X74/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NANASHI0X74/subscriptions","organizations_url":"https://api.github.com/users/NANASHI0X74/orgs","repos_url":"https://api.github.com/users/NANASHI0X74/repos","events_url":"https://api.github.com/users/NANASHI0X74/events{/privacy}","received_events_url":"https://api.github.com/users/NANASHI0X74/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-30T11:06:38Z","updated_at":"2022-03-30T11:15:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI've configured to switch keyboard layouts in plasma's settings with \"Caps Lock (while pressed), Alt+Caps Lock for the original Caps Lock action\". This has been working well with x11, but since switching to using plasma on wayland I've noticed that now this behavior is broken for xwayland apps. If I switch the layout manually, that'll work for xwayland apps and if I'm using a native wayland app, the caps lock behavior works there. \r\n\r\n### Steps To Reproduce\r\n1. Configure at least two different keyboard layouts to use. In my case, this is set via: \r\n```\r\nservices.xserver = {\r\n enable = true;\r\n layout = \"gb,de\";\r\n displayManager.sddm.enable = true;\r\n desktopManager.plasma5.enable = true;\r\n};\r\n```\r\n2. Set [Hardware] Input Devices -> Keyboard -> advanced -> configure keyboard options and switching to another layout -> Caps Lock (while pressed)[...]\r\n3. open an xwayland app, such as slack\r\n4. type for example `Caps+;`\r\n\r\n### Expected behavior\r\nwith my configured layouts, this should type `ö`, but it actually types `;`\r\n\r\n### Additional context\r\nthis works correctly with native wayland applications, as I mentioned.\r\nAlso, I just realized that until a second ago I also had `services.xserver.xkbOptions = \"eurosign:e,grp:caps_switch\";` in my system configuration, but this didn't seem to apply anyway when using a wayland session, as confirmed with `setxkbmap -print -verbose 10`\r\n\r\n### Notify maintainers\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.30, NixOS, 22.05 (Quokka), 22.05.20220327.ce8cbe3`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-21.11pre323790.5f0194220f2\"`\r\n - nixpkgs: `/nix/store/g1562lf0ibiwj5d2ahz2prxy6dsxim7r-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166404/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166401","id":1186263356,"node_id":"I_kwDOAEVQ_M5GtPE8","number":166401,"title":"apple-m1 compiler optimisations for aarch64-darwin?","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-30T10:40:46Z","updated_at":"2022-03-30T12:32:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/dd697d414853a99d0d5f05ee23430923c6da1176/lib/systems/platforms.nix#L393-L398\r\n\r\nadds inappropriate `arch` args for apple-m1. According to Apple clang, `arch = \"armv8.5a+fp-armv8+neon+crc+crypto+dotprod+fp16fml+ras+lse+rdm+rcpc+zcm+zcz+fullfp16+sm4+sha3+sha2+aes\";`.\r\n\r\n(The string isn't even correct for `apple-13` AFAICT, it's `armv8.4a`.)\r\n\r\nIs there any reason against setting `arch` to the string above?\r\n\r\nSecondly, is there any reason against setting `cpu = \"apple-m1\";` once llvm12 is default? llvm11 doesn't support that cpu type; what would happen if a package's llvm was overridden to be llvm11?\r\n\r\ncc @thefloweringash @NixOS/darwin-maintainers ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166401/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166348","id":1185735622,"node_id":"I_kwDOAEVQ_M5GrOPG","number":166348,"title":"yubikey-manager broken on macOS","user":{"login":"tusing","id":1077203,"node_id":"MDQ6VXNlcjEwNzcyMDM=","avatar_url":"https://avatars.githubusercontent.com/u/1077203?v=4","gravatar_id":"","url":"https://api.github.com/users/tusing","html_url":"https://github.com/tusing","followers_url":"https://api.github.com/users/tusing/followers","following_url":"https://api.github.com/users/tusing/following{/other_user}","gists_url":"https://api.github.com/users/tusing/gists{/gist_id}","starred_url":"https://api.github.com/users/tusing/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tusing/subscriptions","organizations_url":"https://api.github.com/users/tusing/orgs","repos_url":"https://api.github.com/users/tusing/repos","events_url":"https://api.github.com/users/tusing/events{/privacy}","received_events_url":"https://api.github.com/users/tusing/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-30T02:05:17Z","updated_at":"2022-03-30T12:32:11Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"`procps` on macOS can not include `pkill` (#141157), but it is used in the `yubikey-manager` derivation:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/57a54d6e57a0e6cd460e0a44ff784c4287df69f3/pkgs/tools/misc/yubikey-manager/default.nix#L19\r\n\r\nThis results in errors like this:\r\n\r\n```\r\nTraceback (most recent call last):\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/bin/.ykman-wrapped\", line 9, in <module>\r\n sys.exit(main())\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 378, in main\r\n cli(obj={})\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1128, in __call__\r\n return self.main(*args, **kwargs)\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1053, in main\r\n rv = self.invoke(ctx)\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1659, in invoke\r\n return _process_result(sub_ctx.command.invoke(sub_ctx))\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1659, in invoke\r\n return _process_result(sub_ctx.command.invoke(sub_ctx))\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1659, in invoke\r\n return _process_result(sub_ctx.command.invoke(sub_ctx))\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 1395, in invoke\r\n return ctx.invoke(self.callback, **ctx.params)\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/core.py\", line 754, in invoke\r\n return __callback(*args, **kwargs)\r\n File \"/nix/store/8rjqb6knk07xgbqdspibq5pq3sbjgb4d-python3.9-click-8.0.3/lib/python3.9/site-packages/click/decorators.py\", line 26, in new_func\r\n return f(get_current_context(), *args, **kwargs)\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/openpgp.py\", line 156, in set_pin_retries\r\n controller = ctx.obj[\"controller\"]\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/util.py\", line 164, in __getitem__\r\n self.resolve()\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/util.py\", line 161, in resolve\r\n self._objects[k] = f()\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 306, in <lambda>\r\n ctx.obj.add_resolver(\"conn\", lambda: resolve()[0])\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 301, in resolve\r\n items = _run_cmd_for_single(ctx, subcmd.name, connections, reader)\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 197, in _run_cmd_for_single\r\n return retrying_connect(None, connections, state=state)\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 107, in retrying_connect\r\n raise e\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/cli/__main__.py\", line 97, in retrying_connect\r\n return connect_to_device(serial, connections)\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/device.py\", line 216, in connect_to_device\r\n conn = dev.open_connection(connection_type)\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/pcsc/__init__.py\", line 87, in open_connection\r\n return self._open_smartcard_connection()\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/pcsc/__init__.py\", line 97, in _open_smartcard_connection\r\n if kill_scdaemon():\r\n File \"/nix/store/gy3890h1qvmsk341ypavpida4f47dziz-python3.9-yubikey-manager-4.0.8/lib/python3.9/site-packages/ykman/pcsc/__init__.py\", line 142, in kill_scdaemon\r\n return_code = subprocess.call([\"/nix/store/22p96jcqi0f6zgazpk6kbzy1fyrjyxis-procps-1003.1-2008/bin/pkill\", \"-9\", \"scdaemon\"]) # nosec\r\n File \"/nix/store/3j4k5ja8zpr7v5xiyfgjwjb8qnl4iycv-python3-3.9.10/lib/python3.9/subprocess.py\", line 349, in call\r\n with Popen(*popenargs, **kwargs) as p:\r\n File \"/nix/store/3j4k5ja8zpr7v5xiyfgjwjb8qnl4iycv-python3-3.9.10/lib/python3.9/subprocess.py\", line 951, in __init__\r\n self._execute_child(args, executable, preexec_fn, close_fds,\r\n File \"/nix/store/3j4k5ja8zpr7v5xiyfgjwjb8qnl4iycv-python3-3.9.10/lib/python3.9/subprocess.py\", line 1821, in _execute_child\r\n raise child_exception_type(errno_num, err_msg, err_filename)\r\nFileNotFoundError: [Errno 2] No such file or directory: '/nix/store/22p96jcqi0f6zgazpk6kbzy1fyrjyxis-procps-1003.1-2008/bin/pkill'\r\n```\r\n\r\nIs it possible to use `/usr/bin/pkill` on Darwin and `${procps}/bin/pkill` elsewhere?\r\n\r\n(@mweinelt)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166348/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166312","id":1185373484,"node_id":"I_kwDOAEVQ_M5Gp10s","number":166312,"title":"option description mentions mautrix-telegram instead of mautrix-facebook","user":{"login":"f0x52","id":23422690,"node_id":"MDQ6VXNlcjIzNDIyNjkw","avatar_url":"https://avatars.githubusercontent.com/u/23422690?v=4","gravatar_id":"","url":"https://api.github.com/users/f0x52","html_url":"https://github.com/f0x52","followers_url":"https://api.github.com/users/f0x52/followers","following_url":"https://api.github.com/users/f0x52/following{/other_user}","gists_url":"https://api.github.com/users/f0x52/gists{/gist_id}","starred_url":"https://api.github.com/users/f0x52/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/f0x52/subscriptions","organizations_url":"https://api.github.com/users/f0x52/orgs","repos_url":"https://api.github.com/users/f0x52/repos","events_url":"https://api.github.com/users/f0x52/events{/privacy}","received_events_url":"https://api.github.com/users/f0x52/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T20:25:56Z","updated_at":"2022-03-30T12:31:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"When copying this to make a mautrix-twitter module, I realised that this line mentions mautrix-telegram instead of mautrix-facebook..\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/ce8cbe3c01fd8ee2de526ccd84bbf9b82397a510/nixos/modules/services/misc/mautrix-facebook.nix#L95\r\n\r\nAlso since all these bridges use basically/exactly? the same module anyways, maybe they could be combined somehow?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166312/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166311","id":1185365914,"node_id":"I_kwDOAEVQ_M5Gpz-a","number":166311,"title":"Zulipchat SSL Error","user":{"login":"abbec","id":455022,"node_id":"MDQ6VXNlcjQ1NTAyMg==","avatar_url":"https://avatars.githubusercontent.com/u/455022?v=4","gravatar_id":"","url":"https://api.github.com/users/abbec","html_url":"https://github.com/abbec","followers_url":"https://api.github.com/users/abbec/followers","following_url":"https://api.github.com/users/abbec/following{/other_user}","gists_url":"https://api.github.com/users/abbec/gists{/gist_id}","starred_url":"https://api.github.com/users/abbec/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/abbec/subscriptions","organizations_url":"https://api.github.com/users/abbec/orgs","repos_url":"https://api.github.com/users/abbec/repos","events_url":"https://api.github.com/users/abbec/events{/privacy}","received_events_url":"https://api.github.com/users/abbec/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T20:17:56Z","updated_at":"2022-03-29T20:18:52Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCannot connect to the Rust org on zulipchat.com because Zulip throws an SSL error.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p zulip --run \"zulip\"`\r\n\r\n### Expected behavior\r\nZulip can connect to https://rust-lang.zulipchat.com. It works fine when using the official AppImage directly.\r\n\r\n### Screenshots\r\n\r\n\r\n### Notify maintainers\r\n@andersk @jonafato \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.16-200.fc35.x86_64, Fedora Linux, 35 (Workstation Edition)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(abbe): `\"home-manager, nixgl, toolbelt\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166311/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166241","id":1184817564,"node_id":"I_kwDOAEVQ_M5GnuGc","number":166241,"title":"File roller can't unzip rar files correctly","user":{"login":"linsui","id":36977733,"node_id":"MDQ6VXNlcjM2OTc3NzMz","avatar_url":"https://avatars.githubusercontent.com/u/36977733?v=4","gravatar_id":"","url":"https://api.github.com/users/linsui","html_url":"https://github.com/linsui","followers_url":"https://api.github.com/users/linsui/followers","following_url":"https://api.github.com/users/linsui/following{/other_user}","gists_url":"https://api.github.com/users/linsui/gists{/gist_id}","starred_url":"https://api.github.com/users/linsui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/linsui/subscriptions","organizations_url":"https://api.github.com/users/linsui/orgs","repos_url":"https://api.github.com/users/linsui/repos","events_url":"https://api.github.com/users/linsui/events{/privacy}","received_events_url":"https://api.github.com/users/linsui/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-29T12:49:33Z","updated_at":"2022-03-30T02:42:26Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nFile roller can't unzip rar files correctly. The extracted files are very large (more that 900M with a 12K file). I also reported upstream but the developer can't reproduce this problem. See https://gitlab.gnome.org/GNOME/file-roller/-/issues/153\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open an rar file created by winrar. \r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nThe file should be extracked correctly. Since bsdtar works well there are some problems in file roller..\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nA test file. \r\n[This is a test file.zip](https://github.com/NixOS/nixpkgs/files/8371508/This.is.a.test.file.zip)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@NixOS/gnome \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.26-hardened1, NixOS, 22.05 (Quokka), 22.05pre364329.ce8cbe3c01f`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166241/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166229","id":1184708380,"node_id":"I_kwDOAEVQ_M5GnTcc","number":166229,"title":"Elixir and Erlang RELEASE_COOKIE: let's reach consensus on what to do to fix the current mess","user":{"login":"NinjaTrappeur","id":1219785,"node_id":"MDQ6VXNlcjEyMTk3ODU=","avatar_url":"https://avatars.githubusercontent.com/u/1219785?v=4","gravatar_id":"","url":"https://api.github.com/users/NinjaTrappeur","html_url":"https://github.com/NinjaTrappeur","followers_url":"https://api.github.com/users/NinjaTrappeur/followers","following_url":"https://api.github.com/users/NinjaTrappeur/following{/other_user}","gists_url":"https://api.github.com/users/NinjaTrappeur/gists{/gist_id}","starred_url":"https://api.github.com/users/NinjaTrappeur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NinjaTrappeur/subscriptions","organizations_url":"https://api.github.com/users/NinjaTrappeur/orgs","repos_url":"https://api.github.com/users/NinjaTrappeur/repos","events_url":"https://api.github.com/users/NinjaTrappeur/events{/privacy}","received_events_url":"https://api.github.com/users/NinjaTrappeur/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null},{"id":355392299,"node_id":"MDU6TGFiZWwzNTUzOTIyOTk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20erlang","name":"6.topic: erlang","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-03-29T11:19:57Z","updated_at":"2022-04-28T22:43:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"# Some Context\r\n\r\nSince Elixir 1.13, the absence of a release cookie at startup leads to a failure in the `mix-release`-generated start script. We've been hit pretty badly by this issue for the Pleroma package\r\n\r\nFirst, @Kloenk approched this by injecting a random cookie to the service start script in https://github.com/NixOS/nixpkgs/pull/149368 via a systemd-provided env variable.\r\n\r\nWhile it did fix the Pleroma service startup, it did not fix the situation for the interactive binaries such as `pleroma_ctl`. Trying to fix that issue, I opened https://github.com/NixOS/nixpkgs/pull/164398, which wraps all the `$out/bin` binaries with the previously mentioned release cookie env variable containing a dummy release-cookie.\r\n\r\nSadly, this PR broke some existing setups which led @yu-re-ka to open https://github.com/NixOS/nixpkgs/pull/164965 .\r\n\r\nAt this point, @yu-re-ka, @Kloenk and me started to discuss how to fix this once and for all on Matrix. During this discussion, we realized that most of the single-node beam packages are likely to suffer from the same issue. We agreed the proper fix shouldn't live in the `pleroma` derivation but rather in the `mix-release` routine in charge of generating the startup scripts.\r\n\r\n# Status Quo\r\n\r\nHow could we solve this unfortunate situation?\r\n\r\nI personally can see 3 options:\r\n\r\n1. Leave everything as it is and assume the leaf package to correctly set `RELEASE_COOKIE`. In that case, we probably should write some documentation about it and streamline the wrapper introduced at https://github.com/NixOS/nixpkgs/pull/149368.\r\n1. Patch the [`mix-release` script generator](https://sourcegraph.com/github.com/elixir-lang/elixir/-/blob/lib/mix/lib/mix/tasks/release.init.ex?L102) to use a static cookie. We'd first generate a static release cookie in the Nix store and then patch the script generator to set `RELEASE_COOKIE` to this static value. In practice, it would mean we'd stop deleting the statically generated release cookie in the [`mix-release` `postFixup` script](https://github.com/NixOS/nixpkgs/blob/e705e589507d0d8fb225613e0d45d1a5bba223fe/pkgs/development/beam-modules/mix-release.nix#L103). This would solve this release cookie issue **for the single node deployments**. Of course, we'd provide a way to override this and set a custom cookie in case of a multi-node deployment.\r\n1. Patch the [`mix-release` script generator](https://sourcegraph.com/github.com/elixir-lang/elixir/-/blob/lib/mix/lib/mix/tasks/release.init.ex?L102) to use a cookie situated at runtime's `$(PWD)/cookie` instead of something located in the `$RELEASE_ROOT`, ie. in the release Nix store path.\r\n\r\n\r\n\r\nI'd be personally in favor of moving forward [^1] with the solution 2. I'd assume that if a user is advanced-enough to setup a multi-node Erlang cluster, they are advanced enough to override the static dummy cookie in their Nix config to something sensible.\r\n\r\nI don't like the idea of leaving things as they are (ie. solution 1): we'll know for sure that any binary produced by `beamPackages.mixRelease` will fail at startup **unless** it gets patched.\r\n\r\nDear @NixOS/beam maintainers, what do you think? Do you see any option besides the ones listed above? Which one do you personally favor? Why?\r\n\r\nCc: @yu-re-ka @Kloenk @happysalada @NixOS/beam \r\n\r\n[^1]: Meaning: I'm up to implement that if we all agree it's the way to go.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166229/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166228","id":1184699524,"node_id":"I_kwDOAEVQ_M5GnRSE","number":166228,"title":"Packaging request: normcap","user":{"login":"pbsds","id":140964,"node_id":"MDQ6VXNlcjE0MDk2NA==","avatar_url":"https://avatars.githubusercontent.com/u/140964?v=4","gravatar_id":"","url":"https://api.github.com/users/pbsds","html_url":"https://github.com/pbsds","followers_url":"https://api.github.com/users/pbsds/followers","following_url":"https://api.github.com/users/pbsds/following{/other_user}","gists_url":"https://api.github.com/users/pbsds/gists{/gist_id}","starred_url":"https://api.github.com/users/pbsds/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pbsds/subscriptions","organizations_url":"https://api.github.com/users/pbsds/orgs","repos_url":"https://api.github.com/users/pbsds/repos","events_url":"https://api.github.com/users/pbsds/events{/privacy}","received_events_url":"https://api.github.com/users/pbsds/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T11:12:26Z","updated_at":"2022-03-29T11:12:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nOCR-powered screenshot tool to capture text instead of images. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://dynobo.github.io/normcap/\r\n* source URL: https://github.com/dynobo/normcap\r\n* license: GPL3\r\n* platforms: unix\r\n* example package: [AUR](https://aur.archlinux.org/packages/normcap) ([PKGBUILD](https://aur.archlinux.org/cgit/aur.git/tree/PKGBUILD?h=normcap))\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166228/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166220","id":1184648673,"node_id":"I_kwDOAEVQ_M5GnE3h","number":166220,"title":"Allow unfree packages with `nix shell`","user":{"login":"GuillaumeDesforges","id":1882000,"node_id":"MDQ6VXNlcjE4ODIwMDA=","avatar_url":"https://avatars.githubusercontent.com/u/1882000?v=4","gravatar_id":"","url":"https://api.github.com/users/GuillaumeDesforges","html_url":"https://github.com/GuillaumeDesforges","followers_url":"https://api.github.com/users/GuillaumeDesforges/followers","following_url":"https://api.github.com/users/GuillaumeDesforges/following{/other_user}","gists_url":"https://api.github.com/users/GuillaumeDesforges/gists{/gist_id}","starred_url":"https://api.github.com/users/GuillaumeDesforges/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/GuillaumeDesforges/subscriptions","organizations_url":"https://api.github.com/users/GuillaumeDesforges/orgs","repos_url":"https://api.github.com/users/GuillaumeDesforges/repos","events_url":"https://api.github.com/users/GuillaumeDesforges/events{/privacy}","received_events_url":"https://api.github.com/users/GuillaumeDesforges/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T10:27:14Z","updated_at":"2022-03-29T10:27:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nCurrently, it's not possible to use unfree packages with `nix shell`\r\n\r\ne.g.\r\n\r\n```\r\nnix shell nixpkgs#python3Packages.cupy\r\n```\r\n\r\na current workaround is to use `--impure`, but one can want both unfree and not impure.\r\n\r\n### Possible fix\r\n\r\nMy guess is that the `legacyPackages` is loaded with inherited `system`.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/c618329a61cd39c2b1d34bdd6e5d7127b1d14e3a/flake.nix#L43\r\n\r\nThere is no way to provide an argument to flakes (see https://github.com/NixOS/nix/issues/3843#issuecomment-661710951) and pass it to the instanciation, and most likely won't ever be.\r\n\r\nTherefore, a suggestion would be to add\r\n\r\n```nix\r\nlegacyPackages.withUnfree = forAllSystems (system: import ./. { inherit system; config.allowUnfree = true; });\r\n```\r\n\r\nThe downside is that we get all packages twice, e.g. in commands such as `nix search`.\r\n\r\n### Note\r\n\r\nWe could think of being able to pass an argument such as `--allow-unfree` to the Nix command, but in my opinion it is too focused on nixpkgs and most likely to be rejected.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166220/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166208","id":1184524971,"node_id":"I_kwDOAEVQ_M5Gmmqr","number":166208,"title":"Liquibase should use `LiquibaseCommandLine` rather than `Main`","user":{"login":"sir4ur0n","id":1204125,"node_id":"MDQ6VXNlcjEyMDQxMjU=","avatar_url":"https://avatars.githubusercontent.com/u/1204125?v=4","gravatar_id":"","url":"https://api.github.com/users/sir4ur0n","html_url":"https://github.com/sir4ur0n","followers_url":"https://api.github.com/users/sir4ur0n/followers","following_url":"https://api.github.com/users/sir4ur0n/following{/other_user}","gists_url":"https://api.github.com/users/sir4ur0n/gists{/gist_id}","starred_url":"https://api.github.com/users/sir4ur0n/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sir4ur0n/subscriptions","organizations_url":"https://api.github.com/users/sir4ur0n/orgs","repos_url":"https://api.github.com/users/sir4ur0n/repos","events_url":"https://api.github.com/users/sir4ur0n/events{/privacy}","received_events_url":"https://api.github.com/users/sir4ur0n/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T08:47:24Z","updated_at":"2022-03-30T12:30:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`Main` was deprecated in favor of `LiquibaseCommandLine`, so we should update the Nix package accordingly.\r\nUntil then, Liquibase does not provide any help in CLI.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. The Liquibase Nix package calls `Main`: https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/tools/database/liquibase/default.nix#L54\r\n2. `Main` was deprecated in favor of `LiquibaseCommandLine`, cf https://www.javadoc.io/doc/org.liquibase/liquibase-core/4.8.0/liquibase/integration/commandline/Main.html\r\n3. When running `liquibase` or `liquibase --help` from the CLI with the current Nixpkgs Liquibase package, the only output is about this deprecation, and no help is provided to the user:\r\n```shell\r\n$ nix-shell -p liquibase\r\n> liquibase --version\r\n####################################################\r\n## _ _ _ _ ##\r\n## | | (_) (_) | ##\r\n## | | _ __ _ _ _ _| |__ __ _ ___ ___ ##\r\n## | | | |/ _` | | | | | '_ \\ / _` / __|/ _ \\ ##\r\n## | |___| | (_| | |_| | | |_) | (_| \\__ \\ __/ ##\r\n## \\_____/_|\\__, |\\__,_|_|_.__/ \\__,_|___/\\___| ##\r\n## | | ##\r\n## |_| ##\r\n## ##\r\n## Get documentation at docs.liquibase.com ##\r\n## Get certified courses at learn.liquibase.com ##\r\n## Free schema change activity reports at ##\r\n## https://hub.liquibase.com ##\r\n## ##\r\n####################################################\r\nStarting Liquibase at 10:38:15 (version 4.8.0 #1581 built at 2022-02-18 21:43+0000)\r\nLiquibase Version: 4.8.0\r\nLiquibase Community 4.8.0 by Liquibase\r\nRunning Java under /nix/store/f7fbh6afmvf8spkg8h30c1s0ddi7kqc5-openjdk-17.0.1+12/lib/openjdk (Version 17.0.1)\r\n> liquibase\r\nHelp not available when running liquibase.integration.commandline.Main directly. Use liquibase.integration.commandline.LiquibaseCommandLine\r\n> liquibase --help\r\nHelp not available when running liquibase.integration.commandline.Main directly. Use liquibase.integration.commandline.LiquibaseCommandLine\r\n```\r\n\r\n### Additional context\r\nI think this \"Not displaying any useful help\" was changed after version 4.4.3 (either 4.7.1 or 4.8.0), i.e. only recent Nixpkgs version (after commit 64e7f299d0a5e7240226ae788cee1c70938b951c from February 12) have this problem.\r\n\r\n### Notify maintainers\r\n@r-ryantm (not tagged as `maintaner` per se, but you are the closest to a maintainer based on Git history :sweat_smile: )\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-22.05pre338278.b0bf5f888d3\"`\r\n - channels(sir4ur0n): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\nBut the Nix channel is not relevant as I reproduced using a fresh Nix flake.\r\n\r\n`flake.nix`:\r\n```nix\r\n{\r\n description = \"Liquibase\";\r\n\r\n inputs = { nixpkgs.url = \"github:NixOS/nixpkgs/nixpkgs-unstable\"; };\r\n\r\n outputs = { self, nixpkgs }:\r\n let\r\n system = \"x86_64-linux\";\r\n pkgs = nixpkgs.legacyPackages.${system};\r\n in\r\n {\r\n devShell.${system} = pkgs.mkShell {\r\n buildInputs =\r\n [ pkgs.liquibase ];\r\n };\r\n\r\n };\r\n}\r\n```\r\n\r\n`flake.lock`:\r\n```json\r\n{\r\n \"nodes\": {\r\n \"nixpkgs\": {\r\n \"locked\": {\r\n \"lastModified\": 1648219316,\r\n \"narHash\": \"sha256-Ctij+dOi0ZZIfX5eMhgwugfvB+WZSrvVNAyAuANOsnQ=\",\r\n \"owner\": \"NixOS\",\r\n \"repo\": \"nixpkgs\",\r\n \"rev\": \"30d3d79b7d3607d56546dd2a6b49e156ba0ec634\",\r\n \"type\": \"github\"\r\n },\r\n \"original\": {\r\n \"owner\": \"NixOS\",\r\n \"ref\": \"nixpkgs-unstable\",\r\n \"repo\": \"nixpkgs\",\r\n \"type\": \"github\"\r\n }\r\n },\r\n \"root\": {\r\n \"inputs\": {\r\n \"nixpkgs\": \"nixpkgs\"\r\n }\r\n }\r\n },\r\n \"root\": \"root\",\r\n \"version\": 7\r\n}\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166208/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166205","id":1184508931,"node_id":"I_kwDOAEVQ_M5GmiwD","number":166205,"title":"Some `libc++abi` symbols are missing with LLVM12+'s `stdenv` on Darwin","user":{"login":"rrbutani","id":7833358,"node_id":"MDQ6VXNlcjc4MzMzNTg=","avatar_url":"https://avatars.githubusercontent.com/u/7833358?v=4","gravatar_id":"","url":"https://api.github.com/users/rrbutani","html_url":"https://github.com/rrbutani","followers_url":"https://api.github.com/users/rrbutani/followers","following_url":"https://api.github.com/users/rrbutani/following{/other_user}","gists_url":"https://api.github.com/users/rrbutani/gists{/gist_id}","starred_url":"https://api.github.com/users/rrbutani/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rrbutani/subscriptions","organizations_url":"https://api.github.com/users/rrbutani/orgs","repos_url":"https://api.github.com/users/rrbutani/repos","events_url":"https://api.github.com/users/rrbutani/events{/privacy}","received_events_url":"https://api.github.com/users/rrbutani/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T08:34:48Z","updated_at":"2022-03-30T12:29:08Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Problem\r\n\r\nWhen using `stdenv`s (or even just `libc++` versions, really) from `llvmPackages` corresponding to LLVM 12 and newer on macOS, symbols related to exceptions (such as `__cxa_allocate_exception`) are not found by the linker.\r\n\r\nThis can be reproduced by compiling and linking any C++ program that makes use of exceptions, i.e.:\r\n```bash\r\nclang++ -xc++ - <<<\"int main() { throw 0; return 5; }\" -o /tmp/foo\r\n```\r\n\r\nResults in:\r\n```\r\nUndefined symbols for architecture arm64:\r\n \"___cxa_allocate_exception\", referenced from:\r\n _main in --bbc70b.o\r\n \"___cxa_throw\", referenced from:\r\n _main in --bbc70b.o\r\nld: symbol(s) not found for architecture arm64\r\nclang-13: error: linker command failed with exit code 1 (use -v to see invocation)\r\n```\r\n\r\nComparing the `libc++` dylibs used by the wrapped `clang++` in the LLVM 12 and 13 `stdenv`s (i.e. `llvmPackages_12.libcxxStdenv`) to that used in the LLVM 11 `stdenv` reveals that while LLVM 11's `libc++.dylib` [reexports](https://stackoverflow.com/questions/49308950/indirect-symbols-in-mach-o-files) such symbols, newer `libc++.dylib`s do _not_.\r\n\r\nWhen run through `llvm-nm -C` and grepped for `__cxa_allocate_exception`, here is the output for LLVM 11's `libc++` dylib:\r\n```\r\n U ___cxa_allocate_exception\r\n I ___cxa_allocate_exception (indirect for ___cxa_allocate_exception)\r\n```\r\n\r\nAnd LLVM 13's:\r\n```\r\n U ___cxa_allocate_exception\r\n```\r\n\r\nBoth of these `libc++` dylibs have a dynamic dependency on `libc++abi` which actually provides a definition for this symbol (this can be observed with `otool -L <dylib path>` which shows the `libc++abi.dylib` dep and then `llvm-nm -C <libc++abi.dylib path>` which shows that the symbol is defined in the `libc++abi` dylib) however only `libc++` versions prior to LLVM 12's reexport the symbol.\r\n\r\nThis is consistent with the `libc++` source code. [These symbols](https://github.com/llvm/llvm-project/commit/ecf313c01ddefb8191d87e516586c37f84862837#diff-47f1b1f4b47562cb331e16fd9e443d5ef1dab41102412a8c34dcf336686426cf) were [initially removed from the main list of symbols reexported and gated on `libc++` exception support](https://github.com/llvm/llvm-project/commit/ecf313c01ddefb8191d87e516586c37f84862837#diff-20b3eeb706b19c7998c7dd44ac45c72752750df57dd43da9e46f2ff0782bbd75R214-R221). However later [this logic and the special list of symbols was removed](https://github.com/llvm/llvm-project/commit/4f13b999297140486b2faa1b5d8d7c768fb40dfb#diff-20b3eeb706b19c7998c7dd44ac45c72752750df57dd43da9e46f2ff0782bbd75L215-L226).\r\n\r\n## Open Questions\r\n\r\nI am not certain I understand the changes in the commit linked above; it's not clear to me why `libcxxabi` was changed to [_reexport_ these symbols](https://github.com/llvm/llvm-project/commit/4f13b999297140486b2faa1b5d8d7c768fb40dfb#diff-b91bcd42277b0ed3b1b885639f5486f1995b4fc65ea4dc8ce53bce3399c01e1fL207-R227).\r\n\r\nThis seems like an ABI break but there is no mention of this being potentially problematic [on the CL](https://reviews.llvm.org/D88623) and the comments added to the changelog in this commit seem to insist that it only _adds_ some reexports to `libc++`.\r\n\r\n## Potential Solutions\r\n\r\nI am not sure what the \"right\" solution is but anecdotally it [seems](https://github.com/grailbio/bazel-toolchain/blob/b84d6720b061f0b986dce811795dfcf1023831f8/toolchain/cc_toolchain_config.bzl#L189-L192) like [it's common](https://reviews.llvm.org/D96070#2543334) to pass in `-lc++abi` as a linkopt on macOS.\r\n\r\n`cc-wrapper` [already does this on Linux](https://github.com/NixOS/nixpkgs/blob/a785ec661fadba2ded58467f951b51c34631c269/pkgs/build-support/cc-wrapper/default.nix#L382).\r\n\r\n## To Reproduce\r\n\r\nHere's a flake:\r\n```nix\r\n{\r\n inputs = {\r\n # nixpkgs.url = github:nixos/nixpkgs?ref=1a8754caf8eb8831b904daaf34b2ee737053b383; # commit for the 13.0.1 LLVM bump\r\n nixpkgs.url = github:nixos/nixpkgs/nixpkgs-unstable; # LLVM 13 is broken on Darwin on 21.11; using < instead of ^ so we get caching\r\n flake-utils.url = github:numtide/flake-utils;\r\n };\r\n\r\n # The issue only affects Darwin. Both because symbol rexport is only a thing\r\n # on mach-o platforms\r\n # (https://github.com/llvm/llvm-project/blob/4f13b999297140486b2faa1b5d8d7c768fb40dfb/libcxx/src/CMakeLists.txt#L202-L215)\r\n # and because `-lc++abi` is always added to the cc wrapper for Linux:\r\n # https://github.com/NixOS/nixpkgs/blob/a785ec661fadba2ded58467f951b51c34631c269/pkgs/build-support/cc-wrapper/default.nix#L382\r\n outputs = { self, nixpkgs, flake-utils }: flake-utils.lib.eachSystem [ \"aarch64-darwin\" \"x86_64-darwin\" ] (system:\r\n let\r\n normal = import nixpkgs { inherit system; };\r\n imp = func: import nixpkgs { inherit system; config.replaceStdenv = { pkgs }: (func pkgs).libcxxStdenv; };\r\n l_11 = imp (n: n.llvmPackages_11);\r\n l_12 = imp (n: n.llvmPackages_12);\r\n l_13 = imp (n: n.llvmPackages_13);\r\n l_13' = import nixpkgs {\r\n inherit system;\r\n # config.replaceStdenv = { pkgs }: pkgs.llvmPackages_13.libcxxStdenv.overrideAttrs (old: {\r\n # postFixup = old.postFixup + ''\r\n # echo \"-lc++abi\" >> $out/nix-support/libcxx-ldflags\r\n # '';\r\n # });\r\n config.replaceStdenv = { pkgs }:\r\n let\r\n clang' = pkgs.llvmPackages_13.libcxxClang.overrideAttrs (old: {\r\n # We _should_ use an overlay or something similar here but they allegedly don't interact well with `replaceStdenv`.\r\n #\r\n # We're essentially adding this: https://github.com/NixOS/nixpkgs/blob/3491c5ea290bca5437845b6348919fcb23950af9/pkgs/build-support/cc-wrapper/default.nix#L382\r\n postFixup = old.postFixup + ''\r\n echo \"-lc++abi\" >> $out/nix-support/libcxx-ldflags\r\n '';\r\n });\r\n\r\n # https://github.com/NixOS/nixpkgs/blob/904ed45698338365f086c22ab5af167adf8bee9a/pkgs/development/compilers/llvm/13/default.nix#L241\r\n stdenv' = pkgs.overrideCC pkgs.stdenv clang';\r\n in\r\n stdenv';\r\n };\r\n\r\n cmd = ''clang++ -xc++ - <<<\"int main() { throw 4; return 0; }\" -v'';\r\n test = np: np.runCommandCC \"test-cxx\" {} ''\r\n ${cmd} -o $out\r\n '';\r\n hook = ''\r\n cd \"$(mktemp -d)\"\r\n libcxx_dir=\"$(${cmd} -o out -Wl,-v |& tee /dev/stderr | grep -P '\\t/nix/store/.*-libcxx-.*/lib' | tail -1)\"\r\n libcxx=$(echo \"$libcxx_dir/libc++.dylib\" | xargs)\r\n\r\n echo -e \"\\nlibcxx: $libcxx\"\r\n echo \"contains:\"\r\n ${normal.llvmPackages.llvm}/bin/llvm-nm -C \"$libcxx\" | grep __cxa_allocate_exception\r\n '';\r\n in {\r\n\r\n # `nix flake check` shows the error\r\n checks.l11 = test l_11; # Works fine\r\n checks.l12 = test l_12; # Fails\r\n checks.l13 = test l_13; # Fails\r\n checks.l13' = test l_13'; # A workaround\r\n\r\n devShells = {\r\n llvm11 = l_11.mkShell { shellHook = hook; };\r\n llvm12 = l_12.mkShell { shellHook = hook; };\r\n llvm13 = l_13.mkShell { shellHook = hook; };\r\n };\r\n });\r\n}\r\n```\r\n\r\nRunning `nix flake check` shows the error when compiling with the LLVM 12 and 13 `stdenv`s; entering the dev shells with `nix develop` prints the path of the `libc++` dylib that's used and greps it for `__cxa_allocate_exception` (one of the missing symbols).\r\n\r\nThe above also contains an example of a workaround that adds `-lc++abi` to the wrapper used in the LLVM 13 `stdenv`.\r\n\r\nI think this is reproducible with any nixpkgs version after the LLVM 12.0.0 package was added but just in case, here's my flake.lock file:\r\n\r\n<details><summary>Click to expand</summary>\r\n\r\n```json\r\n{\r\n \"nodes\": {\r\n \"flake-utils\": {\r\n \"locked\": {\r\n \"lastModified\": 1648297722,\r\n \"narHash\": \"sha256-W+qlPsiZd8F3XkzXOzAoR+mpFqzm3ekQkJNa+PIh1BQ=\",\r\n \"owner\": \"numtide\",\r\n \"repo\": \"flake-utils\",\r\n \"rev\": \"0f8662f1319ad6abf89b3380dd2722369fc51ade\",\r\n \"type\": \"github\"\r\n },\r\n \"original\": {\r\n \"owner\": \"numtide\",\r\n \"repo\": \"flake-utils\",\r\n \"type\": \"github\"\r\n }\r\n },\r\n \"nixpkgs\": {\r\n \"locked\": {\r\n \"lastModified\": 1648219316,\r\n \"narHash\": \"sha256-Ctij+dOi0ZZIfX5eMhgwugfvB+WZSrvVNAyAuANOsnQ=\",\r\n \"owner\": \"nixos\",\r\n \"repo\": \"nixpkgs\",\r\n \"rev\": \"30d3d79b7d3607d56546dd2a6b49e156ba0ec634\",\r\n \"type\": \"github\"\r\n },\r\n \"original\": {\r\n \"owner\": \"nixos\",\r\n \"ref\": \"nixpkgs-unstable\",\r\n \"repo\": \"nixpkgs\",\r\n \"type\": \"github\"\r\n }\r\n },\r\n \"root\": {\r\n \"inputs\": {\r\n \"flake-utils\": \"flake-utils\",\r\n \"nixpkgs\": \"nixpkgs\"\r\n }\r\n }\r\n },\r\n \"root\": \"root\",\r\n \"version\": 7\r\n}\r\n```\r\n\r\n</details>","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166205/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166202","id":1184471533,"node_id":"I_kwDOAEVQ_M5GmZnt","number":166202,"title":"todoist-electron : App doesnt open browser while login","user":{"login":"wiredhikari","id":81508805,"node_id":"MDQ6VXNlcjgxNTA4ODA1","avatar_url":"https://avatars.githubusercontent.com/u/81508805?v=4","gravatar_id":"","url":"https://api.github.com/users/wiredhikari","html_url":"https://github.com/wiredhikari","followers_url":"https://api.github.com/users/wiredhikari/followers","following_url":"https://api.github.com/users/wiredhikari/following{/other_user}","gists_url":"https://api.github.com/users/wiredhikari/gists{/gist_id}","starred_url":"https://api.github.com/users/wiredhikari/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wiredhikari/subscriptions","organizations_url":"https://api.github.com/users/wiredhikari/orgs","repos_url":"https://api.github.com/users/wiredhikari/repos","events_url":"https://api.github.com/users/wiredhikari/events{/privacy}","received_events_url":"https://api.github.com/users/wiredhikari/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-29T08:03:36Z","updated_at":"2022-03-29T08:03:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\nBrowser doesn't pop up when clicked on \"Continue in Browser\" button \r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ... Open the App\r\n2. ...Try logging in\r\n3. ...\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166202/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166201","id":1184465582,"node_id":"I_kwDOAEVQ_M5GmYKu","number":166201,"title":"networking.wireguard...publicKey fails on newlines","user":{"login":"dbeecham","id":1388869,"node_id":"MDQ6VXNlcjEzODg4Njk=","avatar_url":"https://avatars.githubusercontent.com/u/1388869?v=4","gravatar_id":"","url":"https://api.github.com/users/dbeecham","html_url":"https://github.com/dbeecham","followers_url":"https://api.github.com/users/dbeecham/followers","following_url":"https://api.github.com/users/dbeecham/following{/other_user}","gists_url":"https://api.github.com/users/dbeecham/gists{/gist_id}","starred_url":"https://api.github.com/users/dbeecham/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dbeecham/subscriptions","organizations_url":"https://api.github.com/users/dbeecham/orgs","repos_url":"https://api.github.com/users/dbeecham/repos","events_url":"https://api.github.com/users/dbeecham/events{/privacy}","received_events_url":"https://api.github.com/users/dbeecham/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-29T07:58:16Z","updated_at":"2022-03-30T12:28:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIf a `networking.wireguard.interfaces.<name>.peers.<peer-index>.publicKey` contains newlines, e.g. when using `= builtins.readFile pubkey`, this bit of code\r\n\r\n```\r\n let\r\n keyToUnitName = replaceChars\r\n [ \"/\" \"-\" \" \" \"+\" \"=\" ]\r\n [ \"-\" \"\\\\x2d\" \"\\\\x20\" \"\\\\x2b\" \"\\\\x3d\" ];\r\n unitName = keyToUnitName publicKey;\r\n refreshSuffix = optionalString dynamicRefreshEnabled \"-refresh\";\r\n in\r\n \"wireguard-${interfaceName}-peer-${unitName}${refreshSuffix}\";\r\n```\r\n\r\nin nixos/modules/services/networking/wireguard.nix doesn't substitute the newline, and nix fails with an error like \"store path contains illegal character ' '\".\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `...publicKey = \"\\n\"`\r\n2. build\r\n\r\n### Expected behavior\r\nnewline is replaced with some useful character\r\n\r\n### Notify maintainers\r\n@grahamc maybe","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166201/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166132","id":1183927671,"node_id":"I_kwDOAEVQ_M5GkU13","number":166132,"title":"breitbandmessung runtime error due to unsupported OS","user":{"login":"felschr","id":3314323,"node_id":"MDQ6VXNlcjMzMTQzMjM=","avatar_url":"https://avatars.githubusercontent.com/u/3314323?v=4","gravatar_id":"","url":"https://api.github.com/users/felschr","html_url":"https://github.com/felschr","followers_url":"https://api.github.com/users/felschr/followers","following_url":"https://api.github.com/users/felschr/following{/other_user}","gists_url":"https://api.github.com/users/felschr/gists{/gist_id}","starred_url":"https://api.github.com/users/felschr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/felschr/subscriptions","organizations_url":"https://api.github.com/users/felschr/orgs","repos_url":"https://api.github.com/users/felschr/repos","events_url":"https://api.github.com/users/felschr/events{/privacy}","received_events_url":"https://api.github.com/users/felschr/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-28T20:06:20Z","updated_at":"2022-04-20T11:04:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nRunning `breitbandmessung` results in the following error message showing up:\r\n> Da ist etwas schiefgelaufen...\r\n> Ihr Betriebssystem wird von dieser Anwendung nicht unterstützt\r\n\r\nwhich roughly translates to:\r\n> Something went wrong...\r\n> Your operating system isn't supported by this application.\r\n\r\n### Steps To Reproduce\r\nRun `breitbandmessung`, e.g. via `nix run \"nixpkgs#breitbandmessung\"`.\r\n\r\n### Expected behavior\r\nApp should run without causing error that prevents usage.\r\n\r\n### Additional context\r\nSee previous issue #166086 & #166118.\r\n\r\nThe runtime error is probably related to:\r\nhttps://github.com/NixOS/nixpkgs/blob/e8ed7bf5202d9117a06f8f85844cc3b3c260fc78/pkgs/applications/networking/breitbandmessung/default.nix#L37-L48\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/e8ed7bf5202d9117a06f8f85844cc3b3c260fc78/pkgs/applications/networking/breitbandmessung/default.nix#L106-L107\r\n\r\n### Notify maintainers\r\n@B4dM4n\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka), 22.05.20220323.1d08ea2`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - nixpkgs: `/nix/store/hsff9pi1qinxljahr833z0xivr1apx27-source`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166132/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166112","id":1183717262,"node_id":"I_kwDOAEVQ_M5GjheO","number":166112,"title":"Unpack fails when there are two zip files in the srcs field of mkDerivation","user":{"login":"itsfarseen","id":40014472,"node_id":"MDQ6VXNlcjQwMDE0NDcy","avatar_url":"https://avatars.githubusercontent.com/u/40014472?v=4","gravatar_id":"","url":"https://api.github.com/users/itsfarseen","html_url":"https://github.com/itsfarseen","followers_url":"https://api.github.com/users/itsfarseen/followers","following_url":"https://api.github.com/users/itsfarseen/following{/other_user}","gists_url":"https://api.github.com/users/itsfarseen/gists{/gist_id}","starred_url":"https://api.github.com/users/itsfarseen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/itsfarseen/subscriptions","organizations_url":"https://api.github.com/users/itsfarseen/orgs","repos_url":"https://api.github.com/users/itsfarseen/repos","events_url":"https://api.github.com/users/itsfarseen/events{/privacy}","received_events_url":"https://api.github.com/users/itsfarseen/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T16:53:13Z","updated_at":"2022-03-28T16:53:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Describe the bug**\r\n\r\nI was trying to take two zip files and produce a single package.\r\nSpecifically, I was trying to build a package that includes https://github.com/solana-labs/solana and https://github.com/solana-labs/bpf-tools.\r\n\r\nEverything works fine when there is only one entry in the `srcs` field. As soon as I add two entries, unpack phase errors out.\r\n\r\n**Steps To Reproduce**\r\n\r\nMinimal repro: https://github.com/itsfarseen/repro-nix-multiple-src-zip\r\n\r\nError message:\r\n```\r\n$ nix build 13.854s 18:45\r\nerror: builder for '/nix/store/148aybzhywpnkh82p8fvdz3qd0n7k065-test.drv' failed with exit code 1;\r\n last 5 log lines:\r\n > unpacking sources\r\n > unpacking source archive /nix/store/9kyiq086c7hvyvyzlk7azc9s7saw6kbc-source\r\n > unpacking source archive /nix/store/zsahrfi6qpblxpi8v0i92n8v9rl2ihjd-source\r\n > cp: cannot create directory 'source/zsahrfi6qpblxpi8v0i92n8v9rl2ihjd-source': Permission denied\r\n > do not know how to unpack source archive /nix/store/zsahrfi6qpblxpi8v0i92n8v9rl2ihjd-source\r\n For full logs, run 'nix log /nix/store/148aybzhywpnkh82p8fvdz3qd0n7k065-test.drv'.\r\n```\r\n\r\nIn the error message, the following part doesn't make sense.\r\n> cp: cannot create directory 'source/zsahrfi6qpblxpi8v0i92n8v9rl2ihjd-source': Permission denied\r\n\r\nWhy is the path not absolute here? 🤔\r\n\r\n**Expected behavior**\r\n\r\nUnpack phase should complete successfully. \r\nIn the minimal repro, the other phases may fail because I haven't configured them.\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka), 22.05pre363214.1d08ea2bd83`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(farseen): `\"home-manager-21.11, nixos-21.11-21.11.336646.d2caa937753\"`\r\n - channels(root): `\"nixos-22.05pre363214.1d08ea2bd83, home-manager-21.11, nixos-unstable-22.05pre363214.1d08ea2bd83\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos````\r\n```\r\n\r\n**Additional context**\r\nNix flakes feature is enabled.\r\n\r\nWas originally reported at https://github.com/NixOS/nix/issues/6331 \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166112/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166110","id":1183712022,"node_id":"I_kwDOAEVQ_M5GjgMW","number":166110,"title":"remove libselinux from packages?","user":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"labels":[{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T16:48:04Z","updated_at":"2022-03-28T16:50:40Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"do we even need libselinux in nixpkgs?\r\n\r\narch doesn't even have it packaged","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166110/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166108","id":1183707570,"node_id":"I_kwDOAEVQ_M5GjfGy","number":166108,"title":"pakcs: 2.2.1 -> 3.4.2","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T16:44:03Z","updated_at":"2022-03-28T16:44:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: pakcs\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 2.2.1\r\ndesired version: 3.4.2\r\n\r\nWhen updating, it should also be checked if it builds with GHC 9.0 now.\r\n\r\n###### Notify maintainers\r\n\r\n`kkallio`, no GitHub username available.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166108/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166101","id":1183629571,"node_id":"I_kwDOAEVQ_M5GjMED","number":166101,"title":"Veloren Vulkan launch error","user":{"login":"papojari","id":81317317,"node_id":"MDQ6VXNlcjgxMzE3MzE3","avatar_url":"https://avatars.githubusercontent.com/u/81317317?v=4","gravatar_id":"","url":"https://api.github.com/users/papojari","html_url":"https://github.com/papojari","followers_url":"https://api.github.com/users/papojari/followers","following_url":"https://api.github.com/users/papojari/following{/other_user}","gists_url":"https://api.github.com/users/papojari/gists{/gist_id}","starred_url":"https://api.github.com/users/papojari/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/papojari/subscriptions","organizations_url":"https://api.github.com/users/papojari/orgs","repos_url":"https://api.github.com/users/papojari/repos","events_url":"https://api.github.com/users/papojari/events{/privacy}","received_events_url":"https://api.github.com/users/papojari/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"yusdacra","id":19897088,"node_id":"MDQ6VXNlcjE5ODk3MDg4","avatar_url":"https://avatars.githubusercontent.com/u/19897088?v=4","gravatar_id":"","url":"https://api.github.com/users/yusdacra","html_url":"https://github.com/yusdacra","followers_url":"https://api.github.com/users/yusdacra/followers","following_url":"https://api.github.com/users/yusdacra/following{/other_user}","gists_url":"https://api.github.com/users/yusdacra/gists{/gist_id}","starred_url":"https://api.github.com/users/yusdacra/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yusdacra/subscriptions","organizations_url":"https://api.github.com/users/yusdacra/orgs","repos_url":"https://api.github.com/users/yusdacra/repos","events_url":"https://api.github.com/users/yusdacra/events{/privacy}","received_events_url":"https://api.github.com/users/yusdacra/received_events","type":"User","site_admin":false},"assignees":[{"login":"yusdacra","id":19897088,"node_id":"MDQ6VXNlcjE5ODk3MDg4","avatar_url":"https://avatars.githubusercontent.com/u/19897088?v=4","gravatar_id":"","url":"https://api.github.com/users/yusdacra","html_url":"https://github.com/yusdacra","followers_url":"https://api.github.com/users/yusdacra/followers","following_url":"https://api.github.com/users/yusdacra/following{/other_user}","gists_url":"https://api.github.com/users/yusdacra/gists{/gist_id}","starred_url":"https://api.github.com/users/yusdacra/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yusdacra/subscriptions","organizations_url":"https://api.github.com/users/yusdacra/orgs","repos_url":"https://api.github.com/users/yusdacra/repos","events_url":"https://api.github.com/users/yusdacra/events{/privacy}","received_events_url":"https://api.github.com/users/yusdacra/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-03-28T15:43:21Z","updated_at":"2022-03-28T15:44:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI've installed Airshipper and all the Vulkan stuff to play Veloren. However when I click *Play* on Airshipper to launch Veloren it doesn't work. **vkcube does work though**. Here are the logs:\r\n```\r\n\u001b[2m2022-03-28T15:16:12.933326Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mveloren_common_frontend\u001b[0m\u001b[2m:\u001b[0m Setup terminal and file logging. \u001b[3mpath\u001b[0m\u001b[2m=\u001b[0m\"/home/papojari/.local/share/airshipper/profiles/default/userdata/voxygen/logs\" \u001b[3mfile\u001b[0m\u001b[2m=\u001b[0m\"2022-03-28_voxygen.log\"\r\n\u001b[2m2022-03-28T15:16:12.933336Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mveloren_voxygen\u001b[0m\u001b[2m:\u001b[0m Using userdata dir at: /home/papojari/.local/share/airshipper/profiles/default/userdata\r\n\u001b[2m2022-03-28T15:16:12.933338Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mveloren_voxygen\u001b[0m\u001b[2m:\u001b[0m Using config dir at: /home/papojari/.local/share/airshipper/profiles/default/userdata/voxygen\r\n\u001b[2m2022-03-28T15:16:12.955918Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mveloren_common_assets\u001b[0m\u001b[2m:\u001b[0m Assets found path=/home/papojari/.local/share/airshipper/profiles/default/assets\r\n\u001b[2m2022-03-28T15:16:12.989546Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mwinit::platform_impl::platform::x11::window\u001b[0m\u001b[2m:\u001b[0m Guessed window scale factor: 1 \r\n\u001b[2m2022-03-28T15:16:13.000075Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to find extension: VK_KHR_surface \r\n\u001b[2m2022-03-28T15:16:13.000081Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to find extension: VK_KHR_xlib_surface \r\n\u001b[2m2022-03-28T15:16:13.000084Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to find extension: VK_KHR_xcb_surface \r\n\u001b[2m2022-03-28T15:16:13.000086Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to find extension: VK_KHR_wayland_surface \r\n\u001b[2m2022-03-28T15:16:13.000088Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to find extension: VK_KHR_get_physical_device_properties2 \r\n\u001b[2m2022-03-28T15:16:13.002397Z\u001b[0m \u001b[33m WARN\u001b[0m \u001b[2mgfx_backend_vulkan\u001b[0m\u001b[2m:\u001b[0m Unable to create Vulkan instance: VkError(ERROR_INCOMPATIBLE_DRIVER) \r\n\u001b[2m2022-03-28T15:16:13.002489Z\u001b[0m \u001b[32m INFO\u001b[0m \u001b[2mwgpu_core::hub\u001b[0m\u001b[2m:\u001b[0m Dropping Global \r\n\u001b[2m2022-03-28T15:16:13.092676Z\u001b[0m \u001b[31mERROR\u001b[0m \u001b[2mveloren_voxygen\u001b[0m\u001b[2m:\u001b[0m VOXYGEN HAS PANICKED\r\n\r\nA critical error has occurred and Voxygen has been forced to terminate in an unusual manner. Details about the error can be found below.\r\n\r\n> What should I do?\r\n\r\nWe need your help to fix this! You can help by contacting us and reporting this problem. To do this, open an issue on the Veloren issue tracker:\r\n\r\nhttps://www.gitlab.com/veloren/veloren/issues/new\r\n\r\nIf you're on the Veloren community Discord server, we'd be grateful if you could also post a message in the #support channel.\r\n \r\n> What should I include?\r\n\r\nThe error information below will be useful in finding and fixing the problem. Please include as much information about your setup and the events that led up to the panic as possible.\r\n \r\nVoxygen has logged information about the problem (including this message) to the file /home/papojari/.local/share/airshipper/profiles/default/userdata/voxygen/logs/2022-03-28_voxygen.log. Please include the contents of this file in your bug report.\r\n \r\n> Error information\r\n\r\nThe information below is intended for developers and testers.\r\n\r\nPanic Payload: \"Failed to select a rendering backend! No compatible backends were found. We currently support vulkan, metal, dx12, and dx11. Installing or updating vulkan drivers may resolve this issue. If the issue persists, please include the operating system and GPU details in your bug report to help us identify the cause.\"\r\nPanicInfo: panicked at 'Failed to select a rendering backend! No compatible backends were found. We currently support vulkan, metal, dx12, and dx11. Installing or updating vulkan drivers may resolve this issue. If the issue persists, please include the operating system and GPU details in your bug report to help us identify the cause.', voxygen/src/main.rs:255:13\r\nGame version: c23e96f9 [2022-03-21]\r\n\r\nBacktrace:\r\n 0: veloren_voxygen::main::{{closure}}\r\n at /builds/veloren/veloren/voxygen/src/main.rs:136:13\r\n 1: std::panicking::rust_panic_with_hook\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/std/src/panicking.rs:610:17\r\n 2: std::panicking::begin_panic_handler::{{closure}}\r\n 3: std::sys_common::backtrace::__rust_end_short_backtrace\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/std/src/sys_common/backtrace.rs:139:18\r\n 4: rust_begin_unwind\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/std/src/panicking.rs:498:5\r\n 5: core::panicking::panic_fmt\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/core/src/panicking.rs:107:14\r\n 6: veloren_voxygen::main\r\n at /builds/veloren/veloren/voxygen/src/main.rs:255:13\r\n 7: core::ops::function::FnOnce::call_once\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/core/src/ops/function.rs:227:5\r\n std::sys_common::backtrace::__rust_begin_short_backtrace\r\n at /rustc/91a0600a5c22b9d159e3c57526af83e71d1120f8/library/std/src/sys_common/backtrace.rs:123:18\r\n 8: main\r\n 9: __libc_start_main\r\n 10: _start\r\n ```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Airshipper with Nix\r\n2. Start Airshipper\r\n3. Click on *Play*\r\n\r\n### Expected behavior\r\nAirshipper should launch Veloren.\r\n\r\n### Additional context\r\nMy system is running on a AMD R9 280X graphics card which doesn't use the amdgpu driver by default which has vulkan support, but instead uses the radeon driver which doesn't have vulkan support. My system is using the amdgpu driver though.\r\n\r\n### Notify maintainers\r\n@yusdacra \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[papojari@Mothership:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.103, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(papojari): `\"nixos-22.05pre360796.73ad5f9e147\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166101/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166098","id":1183619958,"node_id":"I_kwDOAEVQ_M5GjJt2","number":166098,"title":"Package Request: Ada Language Server & Related Tooling","user":{"login":"enderger","id":36283171,"node_id":"MDQ6VXNlcjM2MjgzMTcx","avatar_url":"https://avatars.githubusercontent.com/u/36283171?v=4","gravatar_id":"","url":"https://api.github.com/users/enderger","html_url":"https://github.com/enderger","followers_url":"https://api.github.com/users/enderger/followers","following_url":"https://api.github.com/users/enderger/following{/other_user}","gists_url":"https://api.github.com/users/enderger/gists{/gist_id}","starred_url":"https://api.github.com/users/enderger/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/enderger/subscriptions","organizations_url":"https://api.github.com/users/enderger/orgs","repos_url":"https://api.github.com/users/enderger/repos","events_url":"https://api.github.com/users/enderger/events{/privacy}","received_events_url":"https://api.github.com/users/enderger/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T15:35:15Z","updated_at":"2022-03-28T15:35:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nThe Ada programming language is severely lacking in packaging for Nix. A good early target is to get the Ada Language Server running, since it allows development in Ada on NixOS and provides a baseline set of things to package (Alire also needs to be packaged at some point, but that’s for a future issue).\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/AdaCore/ada_language_server\r\n* source URL: https://github.com/AdaCore/ada_language_server\r\n* license: GPL 3.0\r\n* platforms: unix/linux/darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166098/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166086","id":1183530697,"node_id":"I_kwDOAEVQ_M5Giz7J","number":166086,"title":"breitbandmessung build fails due to missing command: autoPatchelfFile","user":{"login":"felschr","id":3314323,"node_id":"MDQ6VXNlcjMzMTQzMjM=","avatar_url":"https://avatars.githubusercontent.com/u/3314323?v=4","gravatar_id":"","url":"https://api.github.com/users/felschr","html_url":"https://github.com/felschr","followers_url":"https://api.github.com/users/felschr/followers","following_url":"https://api.github.com/users/felschr/following{/other_user}","gists_url":"https://api.github.com/users/felschr/gists{/gist_id}","starred_url":"https://api.github.com/users/felschr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/felschr/subscriptions","organizations_url":"https://api.github.com/users/felschr/orgs","repos_url":"https://api.github.com/users/felschr/repos","events_url":"https://api.github.com/users/felschr/events{/privacy}","received_events_url":"https://api.github.com/users/felschr/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-03-28T14:29:23Z","updated_at":"2022-03-28T17:47:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nInstalling `breitbandmessung` fails due to missing command `autoPatchelfFile`:\r\n```\r\n$ sudo nixos-rebuild switch\r\nbuilding the system configuration...\r\nerror: builder for '/nix/store/bansdpcfz1p3yzrc2y2n61iklbc71z1h-breitbandmessung-3.1.0.drv' failed with exit code 127;\r\n last 8 log lines:\r\n > patching sources\r\n > configuring\r\n > no configure script, doing nothing\r\n > building\r\n > no Makefile, doing nothing\r\n > glibPreInstallPhase\r\n > installing\r\n > /nix/store/lkk0hf9h4x85mb4lrsf2sh25qm2i4n18-stdenv-linux/setup: line 1360: autoPatchelfFile: command not found\r\n For full logs, run 'nix log /nix/store/bansdpcfz1p3yzrc2y2n61iklbc71z1h-breitbandmessung-3.1.0.drv'.\r\nerror: 1 dependencies of derivation '/nix/store/gvkryrkd675vr27y7ypdh8y39gd6nsxq-home-manager-path.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/lmv2zm0nwpk2n28di81kpfqag9rk86cx-home-manager-generation.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/bk9nv989l6c7rbwzrcmfp9aha6691447-user-environment.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/z1y6yszbvwqbxn0j4j5alh20y71031hp-etc.drv' failed to build\r\nerror: error: 1 dependencies of derivation '/nix/store/91kzm0fr5kqjpfrfr3k02kgph4qh3x7a-nixos-system-home-pc-22.05.20220323.1d08ea2.drv' failed to build\r\n```\r\n\r\n### Steps To Reproduce\r\nInstall `breitbandmessung`, e.g. via `nix run \"nixpkgs#breitbandmessung\"`.\r\n\r\n### Expected behavior\r\nApp should build, install & run without errors.\r\n\r\n### Notify maintainers\r\n@B4dM4n\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka), 22.05.20220323.1d08ea2`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - nixpkgs: `/nix/store/hsff9pi1qinxljahr833z0xivr1apx27-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166086/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166076","id":1183443587,"node_id":"I_kwDOAEVQ_M5GieqD","number":166076,"title":"Make implications of `security.pam.yubico.enable` more obvious","user":{"login":"MalteT","id":11077981,"node_id":"MDQ6VXNlcjExMDc3OTgx","avatar_url":"https://avatars.githubusercontent.com/u/11077981?v=4","gravatar_id":"","url":"https://api.github.com/users/MalteT","html_url":"https://github.com/MalteT","followers_url":"https://api.github.com/users/MalteT/followers","following_url":"https://api.github.com/users/MalteT/following{/other_user}","gists_url":"https://api.github.com/users/MalteT/gists{/gist_id}","starred_url":"https://api.github.com/users/MalteT/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MalteT/subscriptions","organizations_url":"https://api.github.com/users/MalteT/orgs","repos_url":"https://api.github.com/users/MalteT/repos","events_url":"https://api.github.com/users/MalteT/events{/privacy}","received_events_url":"https://api.github.com/users/MalteT/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-28T13:27:41Z","updated_at":"2022-03-28T19:38:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nEnabling `security.pam.yubico.enable` will allow the yubikey to be used for **every** PAM service that is not overriden via `security.pam.services.<name>.yubicoAuth = false`. I was quite astonished to be able to `ssh` into my machine without having to enter any password, just because the Yubikey was plugged into the target host.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set `security.pam.yubico.enable = true` in your NixOS config and configure the challenge-response cipher. `security.pam.yubico.control = \"sufficient\"` is probably required aswell.\r\n2. Set `services.openssh.enable = true`.\r\n3. Plug your Yubikey into your computer.\r\n4. `ssh` into your machine from every other computer in your network.\r\n\r\n### Expected behavior\r\nThis should not be the \"default\" behaviour. The problematic part in the above configuration is `security.pam.yubico.enable`.\r\nIn my opinion (without much knowledge on the topic) the option should be deprecated. Less extreme options include:\r\n\r\n- Disabling `security.pam.services.sshd.yubicoAuth` by default.\r\n- Throwing a warning when setting `security.pam.yubico.enable`\r\n\r\nUser @lvkm:matrix.org has also [mentioned their concerns about](https://matrix.to/#/!KqkRjyTEzAGRiZFBYT:nixos.org/$0HSeisSC8Oj68grIg16klAUtZTsxhLCNoeoYURgQdpk?via=nixos.org&via=matrix.org&via=tchncs.de) https://github.com/NixOS/nixpkgs/blob/1d08ea2bd83abef174fb43cbfb8a856b8ef2ce26/nixos/modules/services/networking/ssh/sshd.nix#L512\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@dtzWill (sorry for putting you here, it's been a long time since you've worked on `security.pam`)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076/reactions","total_count":3,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":3},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166076/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166054","id":1183149893,"node_id":"I_kwDOAEVQ_M5GhW9F","number":166054,"title":"Unable to run ulauncher due too libgvfsdbus loading error ","user":{"login":"PAI5REECHO","id":96688573,"node_id":"U_kgDOBcNZvQ","avatar_url":"https://avatars.githubusercontent.com/u/96688573?v=4","gravatar_id":"","url":"https://api.github.com/users/PAI5REECHO","html_url":"https://github.com/PAI5REECHO","followers_url":"https://api.github.com/users/PAI5REECHO/followers","following_url":"https://api.github.com/users/PAI5REECHO/following{/other_user}","gists_url":"https://api.github.com/users/PAI5REECHO/gists{/gist_id}","starred_url":"https://api.github.com/users/PAI5REECHO/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PAI5REECHO/subscriptions","organizations_url":"https://api.github.com/users/PAI5REECHO/orgs","repos_url":"https://api.github.com/users/PAI5REECHO/repos","events_url":"https://api.github.com/users/PAI5REECHO/events{/privacy}","received_events_url":"https://api.github.com/users/PAI5REECHO/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T09:25:26Z","updated_at":"2022-03-28T09:25:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'm unable to launch `ulauncher` from the command-line\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install `ulauncher` into `home.packages` using `home-manager`\r\n2. Run `ulauncher` from the command-line\r\n```\r\n/nix/store/jsp3h3wpzc842j0rz61m5ly71ak6qgdn-glibc-2.32-54/lib/libc.so.6: version `GLIBC_2.33' not found (required by /nix/store/wshxmgpgrx9cmk0hrbmsxsdg47nmnkc7-gvfs-1.48.1/lib/gio/modules/libgvfsdbus.so)\r\nFailed to load module: /nix/store/wshxmgpgrx9cmk0hrbmsxsdg47nmnkc7-gvfs-1.48.1/lib/gio/modules/libgvfsdbus.so\r\n2022-03-28 09:17:06,011 | WARNING | ulauncher.utils.image_loader: load_image() | Could not load image /home/somebody/.nix-profile/share/ulauncher/media/gear.svg. E: gdk-pixbuf-error-quark: Unable to load image-loading module: /nix/store/jpkv8c5z9fyxbl8s587zjc6winicrj8r-librsvg-2.52.6/lib/gdk-pixbuf-2.0/2.10.0/loaders/libpixbufloader-svg.so: /nix/store/jsp3h3wpzc842j0rz61m5ly71ak6qgdn-glibc-2.32-54/lib/libc.so.6: version `GLIBC_2.33' not found (required by /nix/store/jpkv8c5z9fyxbl8s587zjc6winicrj8r-librsvg-2.52.6/lib/librsvg-2.so.2) (5)\r\n2022-03-28 09:17:06,011 | ERROR | ulauncher: except_hook() | Uncaught exception\r\nTraceback (most recent call last):\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/bin/..ulauncher-wrapped-wrapped\", line 29, in <module>\r\n main()\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/main.py\", line 128, in main\r\n window = UlauncherWindow.get_instance()\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/utils/decorator/singleton.py\", line 19, in wrapper\r\n instance = fn(*args, **kwargs)\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/ui/windows/UlauncherWindow.py\", line 55, in get_instance\r\n return cls()\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/ui/windows/UlauncherWindow.py\", line 65, in __new__\r\n new_object.finish_initializing(builder)\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/ui/windows/UlauncherWindow.py\", line 98, in finish_initializing\r\n self.init_theme()\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/ui/windows/UlauncherWindow.py\", line 237, in init_theme\r\n self._render_prefs_icon()\r\n File \"/nix/store/9y6q4kpg2jl2w9q29bjw9dzmvprxk4wb-ulauncher-5.9.0/lib/python3.8/site-packages/ulauncher/ui/windows/UlauncherWindow.py\", line 388, in _render_prefs_icon\r\n surface = Gdk.cairo_surface_create_from_pixbuf(prefs_pixbuf, scale_factor, self.get_window())\r\nTypeError: Argument 0 does not allow None as a value\r\n```\r\n\r\n### Expected behavior\r\n`ulauncher` to run\r\n\r\n### Notify maintainers\r\n@aaronjanse\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220318_8ad485e`\r\n - channels(root): `\"nixos-21.05.3948.d14d83a3691, home-manager-21.05, nixos-unstable-21.11pre320334.82155ff501c\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166054/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166053","id":1183138711,"node_id":"I_kwDOAEVQ_M5GhUOX","number":166053,"title":"Cross compiling Python2 `greenlet` fails for Raspberry Pi","user":{"login":"cyber-murmel","id":30078229,"node_id":"MDQ6VXNlcjMwMDc4MjI5","avatar_url":"https://avatars.githubusercontent.com/u/30078229?v=4","gravatar_id":"","url":"https://api.github.com/users/cyber-murmel","html_url":"https://github.com/cyber-murmel","followers_url":"https://api.github.com/users/cyber-murmel/followers","following_url":"https://api.github.com/users/cyber-murmel/following{/other_user}","gists_url":"https://api.github.com/users/cyber-murmel/gists{/gist_id}","starred_url":"https://api.github.com/users/cyber-murmel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cyber-murmel/subscriptions","organizations_url":"https://api.github.com/users/cyber-murmel/orgs","repos_url":"https://api.github.com/users/cyber-murmel/repos","events_url":"https://api.github.com/users/cyber-murmel/events{/privacy}","received_events_url":"https://api.github.com/users/cyber-murmel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-28T09:18:17Z","updated_at":"2022-03-28T14:52:09Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCross compiling Python2 `greenlet` (needed for klipper) for Raspberry Pi fails with\r\n```\r\narmv6l-unknown-linux-gnueabihf-gcc -fno-strict-aliasing -g -O2 -DNDEBUG -g -fwrapv -O3 -Wall -Wstrict-prototypes -fPIC -I/nix/store/zxrnf05y8h59s5pz5gsjwgr78lb6mm67-python-2.7.18/include/python2.7 -c src/greenlet/greenlet.c -o build/temp.linux-x86_64-2.7/src/greenlet/greenlet.o\r\nIn file included from /nix/store/zxrnf05y8h59s5pz5gsjwgr78lb6mm67-python-2.7.18/include/python2.7/Python.h:61,\r\n from src/greenlet/greenlet.h:8,\r\n from src/greenlet/greenlet.c:11:\r\n/nix/store/zxrnf05y8h59s5pz5gsjwgr78lb6mm67-python-2.7.18/include/python2.7/pyport.h:895:2: error: #error \"LONG_BIT definition appears wrong for platform (bad gcc/glibc config?).\"\r\n 895 | #error \"LONG_BIT definition appears wrong for platform (bad gcc/glibc config?).\"\r\n | ^~~~~\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```bash\r\n# build from current master (Mon Mar 28 08:55:41 AM UTC 2022)\r\nnix-build https://github.com/NixOS/nixpkgs/archive/e801b16.tar.gz -A pkgsCross.raspberryPi.python2Packages.greenlet\r\n```\r\n\r\n### Expected behavior\r\nA successful build of the package with.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\n```bash\r\n# same problem with 21.11\r\nnix-build https://github.com/NixOS/nixpkgs/archive/nixos-21.11.tar.gz -A pkgsCross.raspberryPi.python2Packages.greenlet\r\n```\r\n\r\n### Notify maintainers\r\n@wamserma\r\n@mweinelt\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(marble): `\"nixos-unstable-22.05pre356180.d5f23787297\"`\r\n - channels(root): `\"nixos-21.11.336646.d2caa937753\"`\r\n - channels(work): `\"nixos-unstable-21.11pre328987.c935f5e0add\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166053/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166049","id":1183114154,"node_id":"I_kwDOAEVQ_M5GhOOq","number":166049,"title":"Cross compiling Python `libgpiod` for Raspberry Pi fails","user":{"login":"cyber-murmel","id":30078229,"node_id":"MDQ6VXNlcjMwMDc4MjI5","avatar_url":"https://avatars.githubusercontent.com/u/30078229?v=4","gravatar_id":"","url":"https://api.github.com/users/cyber-murmel","html_url":"https://github.com/cyber-murmel","followers_url":"https://api.github.com/users/cyber-murmel/followers","following_url":"https://api.github.com/users/cyber-murmel/following{/other_user}","gists_url":"https://api.github.com/users/cyber-murmel/gists{/gist_id}","starred_url":"https://api.github.com/users/cyber-murmel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cyber-murmel/subscriptions","organizations_url":"https://api.github.com/users/cyber-murmel/orgs","repos_url":"https://api.github.com/users/cyber-murmel/repos","events_url":"https://api.github.com/users/cyber-murmel/events{/privacy}","received_events_url":"https://api.github.com/users/cyber-murmel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-28T08:58:59Z","updated_at":"2022-04-10T15:24:58Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCross compiling Python `libgpiod` for Raspberry Pi fails with\r\n```\r\nchecking for a Python interpreter with version >= 3.0... none\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```bash\r\n# build from current master (Mon Mar 28 08:55:41 AM UTC 2022)\r\nnix-build https://github.com/NixOS/nixpkgs/archive/e801b16.tar.gz -A pkgsCross.raspberryPi.python3Packages.libgpiod\r\n```\r\n\r\n### Expected behavior\r\nA successful build of the package with Python support.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\n```bash\r\n# same problem with 21.11\r\nnix-build https://github.com/NixOS/nixpkgs/archive/nixos-21.11.tar.gz -A pkgsCross.raspberryPi.python3Packages.libgpiod\r\n```\r\n\r\n### Notify maintainers\r\n@expipiplus1\r\n@ryantm\r\n@jonringer\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(marble): `\"nixos-unstable-22.05pre356180.d5f23787297\"`\r\n - channels(root): `\"nixos-21.11.336646.d2caa937753\"`\r\n - channels(work): `\"nixos-unstable-21.11pre328987.c935f5e0add\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166049/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005/events","html_url":"https://github.com/NixOS/nixpkgs/issues/166005","id":1182665975,"node_id":"I_kwDOAEVQ_M5Gfgz3","number":166005,"title":"Zecwallet Lite","user":{"login":"suhr","id":65870,"node_id":"MDQ6VXNlcjY1ODcw","avatar_url":"https://avatars.githubusercontent.com/u/65870?v=4","gravatar_id":"","url":"https://api.github.com/users/suhr","html_url":"https://github.com/suhr","followers_url":"https://api.github.com/users/suhr/followers","following_url":"https://api.github.com/users/suhr/following{/other_user}","gists_url":"https://api.github.com/users/suhr/gists{/gist_id}","starred_url":"https://api.github.com/users/suhr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/suhr/subscriptions","organizations_url":"https://api.github.com/users/suhr/orgs","repos_url":"https://api.github.com/users/suhr/repos","events_url":"https://api.github.com/users/suhr/events{/privacy}","received_events_url":"https://api.github.com/users/suhr/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-27T21:18:20Z","updated_at":"2022-03-27T21:18:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nZecwallet Lite is a fully featured shielded wallet for Zcash.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.zecwallet.co/\r\n* source URL: https://github.com/adityapk00/zecwallet-lite\r\n* license: mit\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/166005/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165987","id":1182629365,"node_id":"I_kwDOAEVQ_M5GfX31","number":165987,"title":"KDE Cannot Launch Orca Configuration","user":{"login":"Fidgetcetera","id":15249812,"node_id":"MDQ6VXNlcjE1MjQ5ODEy","avatar_url":"https://avatars.githubusercontent.com/u/15249812?v=4","gravatar_id":"","url":"https://api.github.com/users/Fidgetcetera","html_url":"https://github.com/Fidgetcetera","followers_url":"https://api.github.com/users/Fidgetcetera/followers","following_url":"https://api.github.com/users/Fidgetcetera/following{/other_user}","gists_url":"https://api.github.com/users/Fidgetcetera/gists{/gist_id}","starred_url":"https://api.github.com/users/Fidgetcetera/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Fidgetcetera/subscriptions","organizations_url":"https://api.github.com/users/Fidgetcetera/orgs","repos_url":"https://api.github.com/users/Fidgetcetera/repos","events_url":"https://api.github.com/users/Fidgetcetera/events{/privacy}","received_events_url":"https://api.github.com/users/Fidgetcetera/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-27T18:59:49Z","updated_at":"2022-03-28T14:51:07Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nKDE cannot launch the Orca screen reader's configuration options from the accessibility menu (even if `services.gnome.at-spi2-core.enable = true` is set and `orca` is in the system packages). The error given is \r\nCould not set gsettings for Orca: \"gsettings set org.gnome.desktop.a11y.applications screen-reader-enabled true\" failed.\r\n\r\nI've tried adding gsettings to my system packages, but gsettings hits:\r\n```\r\n(process:43355): dconf-WARNING **: 13:44:58.981: failed to commit changes to dconf: GDBus.Error:org.freedesktop.DBus.Error.ServiceUnknown: The name ca.desrt.dconf was not provided by any .service files\r\n```\r\nPresumably separately gsettings *also* is hitting a dependency issue here.\r\n\r\nThere should probably be a Services config option that enables orca and all the weird things you need enabled to make it work, perhaps even enabling it at startup. I'd lean \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have KDE without GNOME installed.\r\n2. Have Orca installed.\r\n3. Go to accessibility system settings.\r\n4. Click \"Launch Orca screen reader configuration.\"\r\n\r\n### Expected behavior\r\nThe button works and opens Orca's configuration.\r\n\r\n### Notify maintainers\r\n@berce @hedning @dasj19 @maxeaubrey \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nfidgetcetera@kuiper in ~ \r\ntook 22ms 🔋: 🔌 85% \r\n🐯🌺🌑💤🐲🍰😈|🔮 nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/n32py8bgkgi73llcc57kffrnwnaf0vm4-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/n32py8bgkgi73llcc57kffrnwnaf0vm4-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(fidgetcetera): `\"\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/nix/store/yqhznlsx7qj05d3nfahjgiwwxhpvk7a4-nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165987/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165958","id":1182562427,"node_id":"I_kwDOAEVQ_M5GfHh7","number":165958,"title":"21.11: git crashes on commits with SSH signatures","user":{"login":"sersorrel","id":9433472,"node_id":"MDQ6VXNlcjk0MzM0NzI=","avatar_url":"https://avatars.githubusercontent.com/u/9433472?v=4","gravatar_id":"","url":"https://api.github.com/users/sersorrel","html_url":"https://github.com/sersorrel","followers_url":"https://api.github.com/users/sersorrel/followers","following_url":"https://api.github.com/users/sersorrel/following{/other_user}","gists_url":"https://api.github.com/users/sersorrel/gists{/gist_id}","starred_url":"https://api.github.com/users/sersorrel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sersorrel/subscriptions","organizations_url":"https://api.github.com/users/sersorrel/orgs","repos_url":"https://api.github.com/users/sersorrel/repos","events_url":"https://api.github.com/users/sersorrel/events{/privacy}","received_events_url":"https://api.github.com/users/sersorrel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-27T15:13:26Z","updated_at":"2022-03-27T18:33:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\ngit pre-2.34 crashes when asked to show the signature of a commit signed with an ssh key:\r\n\r\n```console\r\n$ git show --show-signature 6d6dfc8fdf04b7b187128cea480aa467c80a2a08\r\nBUG: gpg-interface.c:284: bad signature '-----BEGIN SSH SIGNATURE-----\r\nU1NIU0lHAAAAAQAAAGgAAAATZWNkc2Etc2hhMi1uaXN0cDI1NgAAAAhuaXN0cDI1NgAAAE\r\nEEJjeiqwgYxvFNPcSGHiJXIhuubNfMpqxpSstx+FwHCEJqBDYzrKRb0U7orqAw//nFhkwL\r\nQvD/JyM3R95+EZRo0AAAAANnaXQAAAAAAAAABnNoYTUxMgAAAGQAAAATZWNkc2Etc2hhMi\r\n1uaXN0cDI1NgAAAEkAAAAhAMXlaJQLAlRENc62oGdJbSjPkTkRJ3qdo1X98xbf6oWyAAAA\r\nIH61bgYRswjrGJLzx/sJt9NcOONzQyr974E4hULdMUyK\r\n-----END SSH SIGNATURE-----\r\n'\r\nfish: Job 1, 'git show --show-signature 6d6df…' terminated by signal SIGABRT (Abort)\r\n```\r\n\r\nThis also happens if you e.g. have `%G?` in a `--pretty=format:` string to `git log`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. have git 2.33.1 installed\r\n2. in nixpkgs, `git show --show-signature 6d6dfc8fdf04b7b187128cea480aa467c80a2a08`\r\n3. ...\r\n\r\n### Expected behavior\r\nit would be nice if it were possible to browse nixpkgs with the current stable version of nixos :)\r\n\r\n### Additional context\r\nI guess it's a little late to do much about this at this point; there are already ssh-signed commits merged into nixpkgs. Updating 21.11 to git 2.34.1 would probably fix it, though that introduces a backwards-incompatible change ('The \"--preserve-merges\" option of \"git rebase\" has been removed.') and has the potential to introduce more bugs...\r\n\r\n(given 22.05 will release in at most two months, I am not particularly expecting this to get fixed, I just wanted to open an issue in the hope that anyone else running into this would be able to find some reference to it on google)\r\n\r\n### Notify maintainers\r\n@primeos @wmertens @globin\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.29, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(ash): `\"home-manager-21.11, nixos-unstable-22.05pre360796.73ad5f9e147\"`\r\n - channels(root): `\"nixos-21.11.336589.2c66a7a6e03\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165958/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165897","id":1182197670,"node_id":"I_kwDOAEVQ_M5Gduem","number":165897,"title":"libvirt: session-mode libvirt can't always find /run/libvirt/nix-helpers/qemu-bridge-helper","user":{"login":"alex-robbins","id":26225338,"node_id":"MDQ6VXNlcjI2MjI1MzM4","avatar_url":"https://avatars.githubusercontent.com/u/26225338?v=4","gravatar_id":"","url":"https://api.github.com/users/alex-robbins","html_url":"https://github.com/alex-robbins","followers_url":"https://api.github.com/users/alex-robbins/followers","following_url":"https://api.github.com/users/alex-robbins/following{/other_user}","gists_url":"https://api.github.com/users/alex-robbins/gists{/gist_id}","starred_url":"https://api.github.com/users/alex-robbins/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alex-robbins/subscriptions","organizations_url":"https://api.github.com/users/alex-robbins/orgs","repos_url":"https://api.github.com/users/alex-robbins/repos","events_url":"https://api.github.com/users/alex-robbins/events{/privacy}","received_events_url":"https://api.github.com/users/alex-robbins/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-27T00:18:51Z","updated_at":"2022-03-27T14:04:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI sometimes create a qemu VM in libvirt in \"session mode\", meaning that the libvirt daemon is running as my non-root user, and the system-wide libvirtd does not need to be running ([docs](https://libvirt.org/daemons.html#operating-modes)). This VM has a network bridge, which libvirt apparently creates by calling `/run/wrappers/bin/qemu-bridge-helper`, which in turn uses `/run/libvirt/nix-helpers/qemu-bridge-helper`. \r\n\r\nThe problem is that `/run/libvirt` doesn't get fully populated until the system libvirtd gets started. Previously, in nixpkgs 7f9b6e2ba (from February), this wasn't noticeable because libvirtd.service was WantedBy libvirt-guests.service (which is WantedBy multi-user.target), so libvirtd would always be started on boot to populate that directory. Now, with 1d08ea2b, this is no longer the case, and libvirtd.service does not get started (presumably, if libvirt-guests.service actually needed to start a VM, then libvirtd.service would be socket-activated, but for me this is not the case). As a result, `/run/libvirt` doesn't get populated and my session-mode libvirt can't find `/run/libvirt/nix-helpers/qemu-bridge-helper`. \r\n\r\n### Steps To Reproduce\r\n1. In python:\r\n ```python\r\n conn = libvirt.open('qemu:///session')\r\n dom = conn.createXML(Path('path/to/vm.xml').read_text())\r\n ```\r\n The VM's XML file defines a network bridge, which is why `qemu-bridge-helper` gets involved.\r\n3. Get the following output:\r\n ```\r\n libvirt: QEMU Driver error : internal error: /run/wrappers/bin/qemu-bridge-helper --use-vnet --br=virbr0 --fd=29: failed to communicate with bridge helper: Transport endpoint is not connected\r\n stderr=/run/wrappers/bin/qemu-bridge-helper: cannot run `/run/libvirt/nix-helpers/qemu-bridge-helper': No such file or directory\r\n ...\r\n libvirt.libvirtError: internal error: /run/wrappers/bin/qemu-bridge-helper --use-vnet --br=virbr0 --fd=29: failed to communicate with bridge helper: Transport endpoint is not connected\r\n stderr=/run/wrappers/bin/qemu-bridge-helper: cannot run `/run/libvirt/nix-helpers/qemu-bridge-helper': No such file or directory\r\n ```\r\n\r\n### Expected behavior\r\nThe libvirt user session should be usable without first starting the system-wide libvirtd.\r\n\r\n### Additional context\r\nIf you start (and optionally stop) the system libvirtd.service before following the steps to reproduce, everything works fine, because the `/run/libvirt` directory gets populated. \r\n\r\nProbably, `/run/libvirt/nix-helpers/qemu-bridge-helper` should be put somewhere else, where session-mode daemons can use it without needing to have previously started system-mode libvirtd. (The same may be true of other stuff in `/run/libvirt` too.)\r\n\r\n### Notify maintainers\r\nlibvirt maintainers: @lovesegfault, @fpletz, @globin \r\n\r\n### Metadata\r\n> Please run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\nOkay, but I'm using flakes and that channel looks old. See relevant commit hashes above.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.17.0, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220322_d5d4d98`\r\n - channels(root): `\"nixos-21.11pre333218.263ef4cc414, nixos-hardware\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165897/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165882","id":1182111050,"node_id":"I_kwDOAEVQ_M5GdZVK","number":165882,"title":"firewalld","user":{"login":"cawilliamson","id":1141769,"node_id":"MDQ6VXNlcjExNDE3Njk=","avatar_url":"https://avatars.githubusercontent.com/u/1141769?v=4","gravatar_id":"","url":"https://api.github.com/users/cawilliamson","html_url":"https://github.com/cawilliamson","followers_url":"https://api.github.com/users/cawilliamson/followers","following_url":"https://api.github.com/users/cawilliamson/following{/other_user}","gists_url":"https://api.github.com/users/cawilliamson/gists{/gist_id}","starred_url":"https://api.github.com/users/cawilliamson/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cawilliamson/subscriptions","organizations_url":"https://api.github.com/users/cawilliamson/orgs","repos_url":"https://api.github.com/users/cawilliamson/repos","events_url":"https://api.github.com/users/cawilliamson/events{/privacy}","received_events_url":"https://api.github.com/users/cawilliamson/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-26T21:55:34Z","updated_at":"2022-03-27T14:04:30Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nI'm really just wondering if there's any possibility NixOS will adopt firewalld as a native firewall option?\r\n\r\nIt seems odd that we have similar options like Shorewall packaged up but not firewalld.\r\n\r\nI see there was an effort to package this previously which was then reverted but haven't seen any lively discussion on the topic so thought I'd kick things off.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://firewalld.org/\r\n* source URL: https://github.com/firewalld/firewalld\r\n* license: gpl2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165882/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165881","id":1182109660,"node_id":"I_kwDOAEVQ_M5GdY_c","number":165881,"title":"Mediathekview version 13.8.0 -> 13.8.1 (official log4j)","user":{"login":"j-steinbach","id":69524139,"node_id":"MDQ6VXNlcjY5NTI0MTM5","avatar_url":"https://avatars.githubusercontent.com/u/69524139?v=4","gravatar_id":"","url":"https://api.github.com/users/j-steinbach","html_url":"https://github.com/j-steinbach","followers_url":"https://api.github.com/users/j-steinbach/followers","following_url":"https://api.github.com/users/j-steinbach/following{/other_user}","gists_url":"https://api.github.com/users/j-steinbach/gists{/gist_id}","starred_url":"https://api.github.com/users/j-steinbach/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/j-steinbach/subscriptions","organizations_url":"https://api.github.com/users/j-steinbach/orgs","repos_url":"https://api.github.com/users/j-steinbach/repos","events_url":"https://api.github.com/users/j-steinbach/events{/privacy}","received_events_url":"https://api.github.com/users/j-steinbach/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-26T21:53:25Z","updated_at":"2022-03-27T14:02:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [X] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [X] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: mediathekview\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 13.8.0\r\ndesired version: 13.8.1\r\n\r\nThis update contains the official log4j fix: [changelog](https://mediathekview.de/changelog/13-8-1/)\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @Moredread \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165881/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165858","id":1181917403,"node_id":"I_kwDOAEVQ_M5GcqDb","number":165858,"title":"No users.users.*.hashedPasswordFile option","user":{"login":"lheckemann","id":341954,"node_id":"MDQ6VXNlcjM0MTk1NA==","avatar_url":"https://avatars.githubusercontent.com/u/341954?v=4","gravatar_id":"","url":"https://api.github.com/users/lheckemann","html_url":"https://github.com/lheckemann","followers_url":"https://api.github.com/users/lheckemann/followers","following_url":"https://api.github.com/users/lheckemann/following{/other_user}","gists_url":"https://api.github.com/users/lheckemann/gists{/gist_id}","starred_url":"https://api.github.com/users/lheckemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lheckemann/subscriptions","organizations_url":"https://api.github.com/users/lheckemann/orgs","repos_url":"https://api.github.com/users/lheckemann/repos","events_url":"https://api.github.com/users/lheckemann/events{/privacy}","received_events_url":"https://api.github.com/users/lheckemann/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-26T17:15:40Z","updated_at":"2022-04-05T19:49:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Password hashes, while less sensitive than unhashed passwords, are secrets. We should therefore have a `hashedPasswordFile` option in `users.users` that avoids both placing the hashes in the store world-readable and storing the password unhashed.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165858/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165857","id":1181914044,"node_id":"I_kwDOAEVQ_M5GcpO8","number":165857,"title":"nodePackages.vercel: it's not using the system Go for Go cloud functions on vercel dev","user":{"login":"lucasew","id":15693688,"node_id":"MDQ6VXNlcjE1NjkzNjg4","avatar_url":"https://avatars.githubusercontent.com/u/15693688?v=4","gravatar_id":"","url":"https://api.github.com/users/lucasew","html_url":"https://github.com/lucasew","followers_url":"https://api.github.com/users/lucasew/followers","following_url":"https://api.github.com/users/lucasew/following{/other_user}","gists_url":"https://api.github.com/users/lucasew/gists{/gist_id}","starred_url":"https://api.github.com/users/lucasew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lucasew/subscriptions","organizations_url":"https://api.github.com/users/lucasew/orgs","repos_url":"https://api.github.com/users/lucasew/repos","events_url":"https://api.github.com/users/lucasew/events{/privacy}","received_events_url":"https://api.github.com/users/lucasew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":337081580,"node_id":"MDU6TGFiZWwzMzcwODE1ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20golang","name":"6.topic: golang","color":"fef2c0","default":false,"description":null},{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-26T17:11:01Z","updated_at":"2022-03-26T21:27:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI am doing a project and running it locally using vercel dev.\r\n\r\nThis project uses a Golang cloud function on the API folder\r\n\r\nInstead of using the system Go or reference it as a dependency it's using the provided go from `@vercel/go` so it triggers that problem when you run a binary that expects a FHS system but it's NixOS\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a simple project with an HTML file or something like this\r\n2. Add at least one cloud function (using the `api` folder using go\r\n3. `vercel dev`\r\n\r\n### Expected behavior\r\nvercel uses the system available Go, or the one declared as dependency\r\n\r\n### Screenshots\r\n```\r\n[nix-shell:~/WORKSPACE/irrigationProject]$ vercel dev [28/919]\r\nVercel CLI 24.0.0 \r\n> Running Dev Command “react-scripts start” \r\nℹ 「wds」: Project is running at http://192.168.1.10/ \r\nℹ 「wds」: webpack output is served from \r\nℹ 「wds」: Content not from webpack is served from /home/lucasew/WORKSPACE/irrigationProject/public\r\nℹ 「wds」: 404s will fallback to / \r\nStarting the development server... \r\n \r\n> Ready! Available at http://localhost:3000 \r\nError! Command failed: go build -ldflags -s -w -o /nix/store/wqmssw3p3khlf4sp4g14m73kfmqpjdpk-vercel-24.0.0/lib/node_modules/vercel/node_m\r\nodules/@vercel/go/dist/analyze /nix/store/wqmssw3p3khlf4sp4g14m73kfmqpjdpk-vercel-24.0.0/lib/node_modules/vercel/node_modules/@vercel/go/d\r\nist/analyze.go \r\n```\r\n### Additional context\r\n- Vercel 24.0.0\r\n- NixOS\r\n- nixpkgs: `github:NixOS/nixpkgs/73ad5f9e147c0d2a2061f1d4bd91e05078dc0b58` nixos-unstable\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@kidonng \r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.14, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - nixpkgs: `/nix/store/f71alr07xb2swc37fiqjr5h416qcs6wr-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165857/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165836","id":1181710600,"node_id":"I_kwDOAEVQ_M5Gb3kI","number":165836,"title":"Embedded target triplets (system, config) are used and interpreted incorrectly","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"},{"id":2476856759,"node_id":"MDU6TGFiZWwyNDc2ODU2NzU5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20exotic","name":"6.topic: exotic","color":"fef2c0","default":false,"description":"Exotic hardware or software platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-26T12:09:34Z","updated_at":"2022-03-26T12:09:34Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe following writeup assumes that autotools is our source of truth with regards to target triplets. This is the case in nixpkgs and also implicit for Nix use in general, since its configure system is autoconf-based and produces the `system` strings in the first place.\r\n\r\nWhen fighting binutils' autoconf to accept Solo5's new and custom `aarch64-solo5-none` triplet, I noticed a curious discrepancy between nixpkgs' `lib` and autotools:\r\n\r\n```console\r\n> nix-instantiate --eval -E 'with import <nixpkgs> {}; (lib.systems.elaborate \"riscv64-none-elf\").config'\r\n\"riscv64-unknown-none-elf\"\r\n> $(nix-build '<nixpkgs>' -A gnu-config)/config.sub riscv64-none-elf\r\nriscv64-none-elf\r\n> $(nix-build '<nixpkgs>' -A gnu-config)/config.sub riscv64-unknown-none-elf\r\nInvalid configuration `riscv64-unknown-none-elf': Kernel `none' not known to work with OS `elf'.\r\n```\r\n\r\nThe discrepancy can be boiled down to — after digging through the depths of `config.sub` for a bit — that autotools considers `none` a valid vendor, whereas for nixpkgs `none` can never be a vendor and will always be interpreted as a kernel.\r\n\r\nWhen using `lib.systems.examples`, the problem is more subtle, since an explicit `config` argument is never elaborated:\r\n\r\n```console\r\n> nix-instantiate --eval -E 'with import <nixpkgs> {}; (lib.systems.elaborate lib.systems.examples.riscv64-embedded).config' # correct\r\n\"riscv64-none-elf\"\r\n> nix-instantiate --eval -E 'with import <nixpkgs> {}; (lib.systems.elaborate lib.systems.examples.riscv64-embedded).parsed.vendor' # autotools believes this should be `none`\r\n{ _type = \"vendor\"; name = \"unknown\"; }\r\n```\r\n\r\nSo in conclusion, the following discrepancies between nixpkgs and autotools exists:\r\n\r\n* nixpkgs considers `none` only a valid kernel, whereas for autotools, it can both be a vendor and an OS\r\n* nixpkgs considers `none-elf` as a valid kernel-abi pairing; autotools does operate differently here:\r\n * It uses Kernel-OS, so in `linux-musl` and `linux-gnu` `gnu` and `musl` are considered OS, curiously.\r\n * If instead of the Kernel-OS pairing it receives a single string, it'll consider that as the OS, whereas\r\n nixpkgs would interpret it as the kernel always. This is somewhat important, since autotools *prefixes*\r\n the OS with a modifier (the kernel) if it is given, whereas nixpkgs will *postfix* the kernel with a modifier\r\n (the ABI). This is probably the biggest divergence I could make out philosophically, although in practice\r\n I don't know of any cases where it produces problematic results.\r\n\r\nThe biggest problem I ran into was `none-elf`:\r\n\r\n* nixpkgs thinks this is Kernel `none` and ABI `elf`\r\n* autotools won't accept this `elf` is not an OS that works with Kernel `none` to their knowledge.\r\n\r\nIn the case of all example triplets, this problem is obscured by the fact that nixpkgs and autotools interpret the triplet differently, with autotools taking `none` for the vendor. When trying to force a certain vendor for `aarch64-solo5-none`, things fell apart:\r\n\r\n* `aarch64-solo5-none` would be accepted and parsed correctly by both, except that we would need to use `aarch64-solo5-none-elf` to make nixpkgs understand the exec format correctly\r\n* `aarch64-solo5-none-elf` will break autotools as described.\r\n\r\nI think we were bound to run into some kind of problem at some point; The big problem with autotools is that (unless the triplet is in its most canonical form, i.e. of four components) you have to know what the possible values for each component are to expand the triplet correctly. Additionally, `config.sub` handles a couple of extra edge cases and backwards compatibility, resulting in a very intricate logic that's hard to replicate.\r\n\r\nAnother aspect is surely that we don't have a concept of multiple platform identifier systems, so all `config`s we use need to work with LLVM as well, since we have no concept of “convert this into an LLVM triple”. I need to research LLVM triples still, but possibly this could be a tamer system for us to use *if* we can figure out how to convert the triples to autotools target triplets correctly.\r\n\r\nFor the matter of the incorrect autotools triplets for the embedded platforms, I'm not sure how to proceed, actually. I think the first step would be to figure out where these triplets came from and what their correct autotools variant or interpretation would be:\r\n\r\n* `riscv64-none-elf`\r\n* `riscv32-none-elf`\r\n* `aarch64-none-elf`\r\n* `aarch64_be-none-elf`\r\n* `arm-none-eabi{,hf}`, `powerpc{,le}-none-eabi` (appear to be correct, i.e. autotools accepts `arm-unknown-none-eabi` which is the nixpkgs interpretation)\r\n\r\ncc @alyssais @Ericson2314 @jaykru (added riscv* embedded) @matthewbauer @vincrusher (added embedded platforms)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165836/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165828","id":1181647894,"node_id":"I_kwDOAEVQ_M5GboQW","number":165828,"title":"nixos-rebuild --flake <remote-flake-url> doesn't seem to work","user":{"login":"eliasnaur","id":524812,"node_id":"MDQ6VXNlcjUyNDgxMg==","avatar_url":"https://avatars.githubusercontent.com/u/524812?v=4","gravatar_id":"","url":"https://api.github.com/users/eliasnaur","html_url":"https://github.com/eliasnaur","followers_url":"https://api.github.com/users/eliasnaur/followers","following_url":"https://api.github.com/users/eliasnaur/following{/other_user}","gists_url":"https://api.github.com/users/eliasnaur/gists{/gist_id}","starred_url":"https://api.github.com/users/eliasnaur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/eliasnaur/subscriptions","organizations_url":"https://api.github.com/users/eliasnaur/orgs","repos_url":"https://api.github.com/users/eliasnaur/repos","events_url":"https://api.github.com/users/eliasnaur/events{/privacy}","received_events_url":"https://api.github.com/users/eliasnaur/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-26T10:19:15Z","updated_at":"2022-03-27T12:37:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Steps To Reproduce\r\n```\r\n$ nixos-rebuild switch --flake sourcehut:~eliasnaur/cattle\r\nbuilding the system configuration...\r\nerror: input 'sourcehut:~eliasnaur/cattle#nixosConfigurations.\"themachine\".config.system.build.toplevel' is unsupported\r\n```\r\n\r\nHowever,\r\n\r\n```\r\n$ nix flake show sourcehut:~eliasnaur/cattle\r\nsourcehut:~eliasnaur/cattle/b173e2913820ee767d8cd959bdd82d9275a2dce4\r\n├───nix: unknown\r\n└───nixosConfigurations\r\n └───themachine: NixOS configuration\r\n```\r\n\r\nand `nixos-rebuild switch` on a local checkout does work:\r\n\r\n```\r\n$ nixos-rebuild switch --flake ~e/proj/cattle\r\nbuilding the system configuration...\r\nactivating the configuration...\r\nsetting up /etc...\r\nreloading user units for e...\r\nsetting up tmpfiles\r\n```\r\n\r\n### Expected behavior\r\nI expected all flake URLs to work when passed to `nixos-rebuild switch`. It appears to only work for local flakes.\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.106, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-21.11.336646.d2caa937753, nixos-unstable-22.05pre362644.1ec61dd4167\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165828/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165817","id":1181583199,"node_id":"I_kwDOAEVQ_M5GbYdf","number":165817,"title":"Packaging request: Oversteer","user":{"login":"mightyiam","id":635591,"node_id":"MDQ6VXNlcjYzNTU5MQ==","avatar_url":"https://avatars.githubusercontent.com/u/635591?v=4","gravatar_id":"","url":"https://api.github.com/users/mightyiam","html_url":"https://github.com/mightyiam","followers_url":"https://api.github.com/users/mightyiam/followers","following_url":"https://api.github.com/users/mightyiam/following{/other_user}","gists_url":"https://api.github.com/users/mightyiam/gists{/gist_id}","starred_url":"https://api.github.com/users/mightyiam/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mightyiam/subscriptions","organizations_url":"https://api.github.com/users/mightyiam/orgs","repos_url":"https://api.github.com/users/mightyiam/repos","events_url":"https://api.github.com/users/mightyiam/events{/privacy}","received_events_url":"https://api.github.com/users/mightyiam/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"AndersonTorres","id":5954806,"node_id":"MDQ6VXNlcjU5NTQ4MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5954806?v=4","gravatar_id":"","url":"https://api.github.com/users/AndersonTorres","html_url":"https://github.com/AndersonTorres","followers_url":"https://api.github.com/users/AndersonTorres/followers","following_url":"https://api.github.com/users/AndersonTorres/following{/other_user}","gists_url":"https://api.github.com/users/AndersonTorres/gists{/gist_id}","starred_url":"https://api.github.com/users/AndersonTorres/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AndersonTorres/subscriptions","organizations_url":"https://api.github.com/users/AndersonTorres/orgs","repos_url":"https://api.github.com/users/AndersonTorres/repos","events_url":"https://api.github.com/users/AndersonTorres/events{/privacy}","received_events_url":"https://api.github.com/users/AndersonTorres/received_events","type":"User","site_admin":false},"assignees":[{"login":"AndersonTorres","id":5954806,"node_id":"MDQ6VXNlcjU5NTQ4MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5954806?v=4","gravatar_id":"","url":"https://api.github.com/users/AndersonTorres","html_url":"https://github.com/AndersonTorres","followers_url":"https://api.github.com/users/AndersonTorres/followers","following_url":"https://api.github.com/users/AndersonTorres/following{/other_user}","gists_url":"https://api.github.com/users/AndersonTorres/gists{/gist_id}","starred_url":"https://api.github.com/users/AndersonTorres/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AndersonTorres/subscriptions","organizations_url":"https://api.github.com/users/AndersonTorres/orgs","repos_url":"https://api.github.com/users/AndersonTorres/repos","events_url":"https://api.github.com/users/AndersonTorres/events{/privacy}","received_events_url":"https://api.github.com/users/AndersonTorres/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-03-26T08:03:49Z","updated_at":"2022-03-27T19:02:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n Steering Wheel Manager for GNU/Linux \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/berarma/oversteer\r\n* source URL: https://github.com/berarma/oversteer\r\n* license: [GPL-3.0](https://github.com/berarma/oversteer/blob/master/LICENSE)\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165817/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165794","id":1181315785,"node_id":"I_kwDOAEVQ_M5GaXLJ","number":165794,"title":"kotlin-native: attempts to fetch dependencies from the network","user":{"login":"brecert","id":11599528,"node_id":"MDQ6VXNlcjExNTk5NTI4","avatar_url":"https://avatars.githubusercontent.com/u/11599528?v=4","gravatar_id":"","url":"https://api.github.com/users/brecert","html_url":"https://github.com/brecert","followers_url":"https://api.github.com/users/brecert/followers","following_url":"https://api.github.com/users/brecert/following{/other_user}","gists_url":"https://api.github.com/users/brecert/gists{/gist_id}","starred_url":"https://api.github.com/users/brecert/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/brecert/subscriptions","organizations_url":"https://api.github.com/users/brecert/orgs","repos_url":"https://api.github.com/users/brecert/repos","events_url":"https://api.github.com/users/brecert/events{/privacy}","received_events_url":"https://api.github.com/users/brecert/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-25T22:10:07Z","updated_at":"2022-04-21T18:19:44Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`kotlin-native` attempts to fetch prebuilt binaries for its first run, this fails due to nix's restrictions on network access in derivations.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. create a derivation that looks something like\r\n```nix\r\n{\r\n nativeBuildInputs = [ pkgs.kotlin-native ];\r\n buildPhase = ''\r\n kotlinc-native ./example.kt\r\n '';\r\n}\r\n```\r\n2. attempt to build the derivation\r\n\r\n### Log\r\n```console\r\n❯ nix log /nix/store/3bb44kbb6wh9f2samqp08mckbn17r28z-question-kotlin.drv\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/yckqrqrl0vv7843rg5idaasna89xhizd-question-kotlin\r\nsource root is question-kotlin\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\nno configure script, doing nothing\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nDownloading native dependencies (LLVM, sysroot etc). This is a one-time action performed only on the first run of the compiler.\r\nCannot download a dependency: java.net.UnknownHostException: download.jetbrains.com\r\nWaiting 3.0 sec and trying again (attempt: 2/10).\r\nCannot download a dependency: java.net.UnknownHostException: download.jetbrains.com\r\nWaiting 6.0 sec and trying again (attempt: 3/10).\r\nCannot download a dependency: java.net.UnknownHostException: download.jetbrains.com\r\nWaiting 9.0 sec and trying again (attempt: 4/10).\r\nCannot download a dependency: java.net.UnknownHostException: download.jetbrains.com\r\n```\r\n\r\n### Expected behavior\r\nI expected `kotlin-native` to not fail to download or fetch when used in a derivation.\r\n\r\n### Notify maintainers\r\n@fabianhjr \r\n\r\n### Metadata\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.60.1-microsoft-standard-WSL2, Debian GNU/Linux, 9 (stretch)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(bree): `\"home-manager, nixpkgs\"`\r\n - nixpkgs: `/home/bree/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165794/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165792","id":1181297287,"node_id":"I_kwDOAEVQ_M5GaSqH","number":165792,"title":"Release Schedule for 22.05","user":{"login":"dasJ","id":4971975,"node_id":"MDQ6VXNlcjQ5NzE5NzU=","avatar_url":"https://avatars.githubusercontent.com/u/4971975?v=4","gravatar_id":"","url":"https://api.github.com/users/dasJ","html_url":"https://github.com/dasJ","followers_url":"https://api.github.com/users/dasJ/followers","following_url":"https://api.github.com/users/dasJ/following{/other_user}","gists_url":"https://api.github.com/users/dasJ/gists{/gist_id}","starred_url":"https://api.github.com/users/dasJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dasJ/subscriptions","organizations_url":"https://api.github.com/users/dasJ/orgs","repos_url":"https://api.github.com/users/dasJ/repos","events_url":"https://api.github.com/users/dasJ/events{/privacy}","received_events_url":"https://api.github.com/users/dasJ/received_events","type":"User","site_admin":false},"labels":[{"id":2392802829,"node_id":"MDU6TGFiZWwyMzkyODAyODI5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20release%20process","name":"6.topic: release process","color":"4cd3ba","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-25T21:45:58Z","updated_at":"2022-04-25T18:00:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"This is a GitHub issue now to make it editable which is not the case on [Discourse](https://discourse.nixos.org/t/lets-have-a-great-22-05-release-cycle/18357).\r\n\r\n|| Date | Branches Affected | Events |\r\n|-| --- | --- | --- |\r\n|:heavy_check_mark:| April, 03 | - | Ask ecosystems for desired changes, in \"Feature Freeze\" |\r\n|:heavy_check_mark:| April, 17 | `staging-next`, `staging` | Restrict breaking changes to Release Critical Packages |\r\n|| May, 01 | `staging-next`, `staging` | Restrict all breaking changes: allow only non-breaking updates and Desktop Manager changes |\r\n|| May, 07 | `master` | (Day before ZHF) merge `staging-next` into `master`, prep for ZHF |\r\n|| May, 08 | `master` | Begin ZHF, Focus on minimizing regressions in PRs targeting `master` |\r\n|| May, 15 | `master` | Merge first `staging-next` fixes into `master`; begin second `staging-next` cycle |\r\n|| May, 15 | `staging` | Unrestrict all breaking changes; new changes will not be present in `master` before branch-off |\r\n|| May, 22 | `master` | Merge second `staging-next` fix cycle |\r\n|| May, 22 | `staging-next` | Unrestrict all breaking changes; new changes will not be present in `master` before branch-off |\r\n|| May, 22 | `master`, `22.05` | Perform Branch-off, create release channels, create new beta / unstable tags |\r\n|| May, 22 | `master`, `22.05` | ZHF transitions to \"backporting\" workflow |\r\n|| May, 22 | `22.05` | Prepare for release, finish remaining issues |\r\n|| May, 30 | `22.05` | Release! Also, ZHF ends |\r\n|| June, 30 | - | Release Retrospective Meeting |","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792/reactions","total_count":38,"+1":19,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":19},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165792/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165783","id":1181209492,"node_id":"I_kwDOAEVQ_M5GZ9OU","number":165783,"title":"androidenv should replace hardcoded /bin/ls references in build-tools","user":{"login":"eliasnaur","id":524812,"node_id":"MDQ6VXNlcjUyNDgxMg==","avatar_url":"https://avatars.githubusercontent.com/u/524812?v=4","gravatar_id":"","url":"https://api.github.com/users/eliasnaur","html_url":"https://github.com/eliasnaur","followers_url":"https://api.github.com/users/eliasnaur/followers","following_url":"https://api.github.com/users/eliasnaur/following{/other_user}","gists_url":"https://api.github.com/users/eliasnaur/gists{/gist_id}","starred_url":"https://api.github.com/users/eliasnaur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/eliasnaur/subscriptions","organizations_url":"https://api.github.com/users/eliasnaur/orgs","repos_url":"https://api.github.com/users/eliasnaur/repos","events_url":"https://api.github.com/users/eliasnaur/events{/privacy}","received_events_url":"https://api.github.com/users/eliasnaur/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-25T19:50:42Z","updated_at":"2022-03-25T19:50:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Similar to https://github.com/tadfisher/android-nixpkgs/issues/33, androidenv generates Android SDKs where `d8` and `apksigner` from build-tools fails to run because of hardcoded references to `/bin/ls`:\r\n\r\n```\r\n$ nix --version\r\nnix (Nix) 2.7.0\r\n$ cat flake.nix\r\n{\r\n description = \"Gio build environment\";\r\n\r\n inputs = {\r\n nixpkgs.url = \"github:NixOS/nixpkgs\";\r\n flake-utils.url = \"github:numtide/flake-utils\";\r\n };\r\n\r\n outputs = { self, nixpkgs, flake-utils }:\r\n flake-utils.lib.eachDefaultSystem (system:\r\n let\r\n pkgs = import nixpkgs {\r\n inherit system;\r\n config.android_sdk.accept_license = true;\r\n };\r\n androidComposition = pkgs.androidenv.composeAndroidPackages {\r\n platformVersions = [ \"31\" ];\r\n abiVersions = [ \"armeabi-v7a\" \"arm64-v8a\" \"x86_64\" ];\r\n includeNDK = true;\r\n ndkVersions = [ \"22.0.7026061\" ];\r\n };\r\n in\r\n {\r\n devShell = pkgs.mkShell {\r\n buildInputs = [\r\n androidComposition.androidsdk\r\n ];\r\n };\r\n }\r\n );\r\n}\r\n$ nix develop\r\n$ rg --follow 'bin.ls' $ANDROID_SDK_ROOT/build-tools\r\n/nix/store/bqk9x92pk14d07hd1mnqw0807fm3lzg1-android-sdk-env/share/android-sdk/build-tools/31.0.0/d8\r\n21: newProg=`/bin/ls -ld \"${prog}\"`\r\n\r\n/nix/store/bqk9x92pk14d07hd1mnqw0807fm3lzg1-android-sdk-env/share/android-sdk/build-tools/31.0.0/apksigner\r\n21: newProg=`/bin/ls -ld \"${prog}\"`\r\n\r\n/nix/store/bqk9x92pk14d07hd1mnqw0807fm3lzg1-android-sdk-env/share/android-sdk/build-tools/31.0.0/mainDexClasses\r\n44: newProg=`/bin/ls -ld \"${prog}\"`\r\n```\r\n\r\nI tried to patch in\r\n\r\n```\r\n$ git diff\r\ndiff --git pkgs/development/mobile/androidenv/build-tools.nix pkgs/development/mobile/androidenv/build-tools.nix\r\nindex 536a025d15b..12448e03004 100644\r\n--- pkgs/development/mobile/androidenv/build-tools.nix\r\n+++ pkgs/development/mobile/androidenv/build-tools.nix\r\n@@ -16,6 +16,9 @@ deployAndroidPackage {\r\n\r\n wrapProgram $PWD/mainDexClasses \\\r\n --prefix PATH : ${pkgs.jdk8}/bin\r\n+\r\n+ substituteInPlace $PWD/d8 \\\r\n+ --replace \"/bin/ls\" \"${pkgs.coreutils}/bin/ls\"\r\n '';\r\n noAuditTmpdir = true; # The checker script gets confused by the build-tools path that is incorrectly identified as a reference to /build\r\n }\r\n```\r\n\r\ncombined with\r\n\r\n```\r\n$ nix develop --override-input nixpkgs /path/to/my/nixpkgs\r\n```\r\n\r\nbut that didn't have any effect on the resulting `d8` binary.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165783/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165747","id":1180532095,"node_id":"I_kwDOAEVQ_M5GXX1_","number":165747,"title":"KeePassXC version 2.6.6 -> 2.7.0","user":{"login":"ellmau","id":71695780,"node_id":"MDQ6VXNlcjcxNjk1Nzgw","avatar_url":"https://avatars.githubusercontent.com/u/71695780?v=4","gravatar_id":"","url":"https://api.github.com/users/ellmau","html_url":"https://github.com/ellmau","followers_url":"https://api.github.com/users/ellmau/followers","following_url":"https://api.github.com/users/ellmau/following{/other_user}","gists_url":"https://api.github.com/users/ellmau/gists{/gist_id}","starred_url":"https://api.github.com/users/ellmau/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ellmau/subscriptions","organizations_url":"https://api.github.com/users/ellmau/orgs","repos_url":"https://api.github.com/users/ellmau/repos","events_url":"https://api.github.com/users/ellmau/events{/privacy}","received_events_url":"https://api.github.com/users/ellmau/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-25T09:14:26Z","updated_at":"2022-03-29T14:28:33Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: keepassxc\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 2.6.6\r\ndesired version: 2.7.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @jonafato @turion \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165747/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165724","id":1180269386,"node_id":"I_kwDOAEVQ_M5GWXtK","number":165724,"title":"Binary cache opencv + gtk","user":{"login":"tobiasBora","id":2164118,"node_id":"MDQ6VXNlcjIxNjQxMTg=","avatar_url":"https://avatars.githubusercontent.com/u/2164118?v=4","gravatar_id":"","url":"https://api.github.com/users/tobiasBora","html_url":"https://github.com/tobiasBora","followers_url":"https://api.github.com/users/tobiasBora/followers","following_url":"https://api.github.com/users/tobiasBora/following{/other_user}","gists_url":"https://api.github.com/users/tobiasBora/gists{/gist_id}","starred_url":"https://api.github.com/users/tobiasBora/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tobiasBora/subscriptions","organizations_url":"https://api.github.com/users/tobiasBora/orgs","repos_url":"https://api.github.com/users/tobiasBora/repos","events_url":"https://api.github.com/users/tobiasBora/events{/privacy}","received_events_url":"https://api.github.com/users/tobiasBora/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-25T02:29:33Z","updated_at":"2022-04-07T13:38:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using the opencv library (which is as I understand the simpler way to play videos in python) we need to enable `enableGtk2 = true` for we get some errors when playing a video. Unfortunately, this library is not cached, so we need to compile it manually (which takes maybe 10mn). As I guess this library is quite popular, it would be cool to have a binary package for it.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior: start a nix shell with `shell.nix` being:\r\n```\r\n{ pkgs ? import <nixpkgs> {} }:\r\nwith pkgs;\r\npkgs.mkShell {\r\n buildInputs = [ (pkgs.python3.withPackages (ps: with ps; [numpy (opencv4.override { enableGtk2 = true; })])) ];\r\n}\r\n```\r\n\r\n### Expected behavior\r\n\r\nEverything should install quickly without build.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@jonringer @mdaiter @basvandijk\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165724/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165720","id":1180244798,"node_id":"I_kwDOAEVQ_M5GWRs-","number":165720,"title":"Packaging request: hred","user":{"login":"tejing1","id":5663576,"node_id":"MDQ6VXNlcjU2NjM1NzY=","avatar_url":"https://avatars.githubusercontent.com/u/5663576?v=4","gravatar_id":"","url":"https://api.github.com/users/tejing1","html_url":"https://github.com/tejing1","followers_url":"https://api.github.com/users/tejing1/followers","following_url":"https://api.github.com/users/tejing1/following{/other_user}","gists_url":"https://api.github.com/users/tejing1/gists{/gist_id}","starred_url":"https://api.github.com/users/tejing1/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tejing1/subscriptions","organizations_url":"https://api.github.com/users/tejing1/orgs","repos_url":"https://api.github.com/users/tejing1/repos","events_url":"https://api.github.com/users/tejing1/events{/privacy}","received_events_url":"https://api.github.com/users/tejing1/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"AndersonTorres","id":5954806,"node_id":"MDQ6VXNlcjU5NTQ4MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5954806?v=4","gravatar_id":"","url":"https://api.github.com/users/AndersonTorres","html_url":"https://github.com/AndersonTorres","followers_url":"https://api.github.com/users/AndersonTorres/followers","following_url":"https://api.github.com/users/AndersonTorres/following{/other_user}","gists_url":"https://api.github.com/users/AndersonTorres/gists{/gist_id}","starred_url":"https://api.github.com/users/AndersonTorres/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AndersonTorres/subscriptions","organizations_url":"https://api.github.com/users/AndersonTorres/orgs","repos_url":"https://api.github.com/users/AndersonTorres/repos","events_url":"https://api.github.com/users/AndersonTorres/events{/privacy}","received_events_url":"https://api.github.com/users/AndersonTorres/received_events","type":"User","site_admin":false},"assignees":[{"login":"AndersonTorres","id":5954806,"node_id":"MDQ6VXNlcjU5NTQ4MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5954806?v=4","gravatar_id":"","url":"https://api.github.com/users/AndersonTorres","html_url":"https://github.com/AndersonTorres","followers_url":"https://api.github.com/users/AndersonTorres/followers","following_url":"https://api.github.com/users/AndersonTorres/following{/other_user}","gists_url":"https://api.github.com/users/AndersonTorres/gists{/gist_id}","starred_url":"https://api.github.com/users/AndersonTorres/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AndersonTorres/subscriptions","organizations_url":"https://api.github.com/users/AndersonTorres/orgs","repos_url":"https://api.github.com/users/AndersonTorres/repos","events_url":"https://api.github.com/users/AndersonTorres/events{/privacy}","received_events_url":"https://api.github.com/users/AndersonTorres/received_events","type":"User","site_admin":false}],"milestone":null,"comments":1,"created_at":"2022-03-25T01:42:08Z","updated_at":"2022-03-27T19:01:45Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nI've been searching for a tool to extract structured data usefully from web pages which don't provide a machine-readable interface such as RSS, and I recently found `hred`. `hred` extracts data from html using a language based on css selectors, but unlike other programs such as `pup` that do the same, it outputs its matches in (fairly configurable) json rather than as a flat list, and if that's not configurable enough, it can easily be piped into `jq` for more complex processing. It also apparently handles xml.\r\n\r\nIt seems better-thought-out than other tools in the category to me, and it doesn't seem to die horribly when exposed to real-world html either, like xml-oriented things often do.\r\n\r\nI did try running `node2nix` in a local checkout, and the derivation it produced worked for me with no tweaking, so this is probably fairly trivial to package. I'm just not really familiar with how nixpkgs handles node stuff, so I'm not confident doing it myself.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/danburzo/hred\r\n* source URL: https://github.com/danburzo/hred\r\n* license: mit\r\n* platforms: anywhere node.js works\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165720/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165719","id":1180235356,"node_id":"I_kwDOAEVQ_M5GWPZc","number":165719,"title":"nvidia udev process fails","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-25T01:24:11Z","updated_at":"2022-03-30T21:53:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"```\r\nMar 24 18:20:17 porty systemd-udevd[90508]: card0: Process '/nix/store/dndi916j6yxzfzzj2sma2llhrlwahq06-bash-5.1-p16/bin/bash -c 'mknod -m 666 /dev/nvidia0 c $(grep nvidia-frontend /proc/devices | cut -d \\ -f 1) 0'' failed with exit code 1.\r\nMar 24 18:20:17 porty systemd-udevd[90533]: card0-DP-3: Process '/nix/store/dndi916j6yxzfzzj2sma2llhrlwahq06-bash-5.1-p16/bin/bash -c 'mknod -m 666 /dev/nvidia3 c $(grep nvidia-frontend /proc/devices | cut -d \\ -f 1) 3'' failed with exit code 1.\r\nMar 24 18:20:17 porty systemd-udevd[90584]: card0-DP-2: Process '/nix/store/dndi916j6yxzfzzj2sma2llhrlwahq06-bash-5.1-p16/bin/bash -c 'mknod -m 666 /dev/nvidia2 c $(grep nvidia-frontend /proc/devices | cut -d \\ -f 1) 2'' failed with exit code 1.\r\nMar 24 18:20:17 porty systemd-udevd[90508]: card0-DP-1: Process '/nix/store/dndi916j6yxzfzzj2sma2llhrlwahq06-bash-5.1-p16/bin/bash -c 'mknod -m 666 /dev/nvidia1 c $(grep nvidia-frontend /proc/devices | cut -d \\ -f 1) 1'' failed with exit code 1.\r\nMar 24 18:20:17 porty systemd-udevd[90574]: card0-HDMI-A-1: Process '/nix/store/dndi916j6yxzfzzj2sma2llhrlwahq06-bash-5.1-p16/bin/bash -c 'mknod -m 666 /dev/nvidia1 c $(grep nvidia-frontend /proc/devices | cut -d \\ -f 1) 1'' failed with exit code 1.\r\n```\r\n\r\nThis is on latest nixos unstable `commit 1ec61dd4167f04be8d05c45780818826132eea0d (nixos/nixos-unstable)`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165719/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165717","id":1180194654,"node_id":"I_kwDOAEVQ_M5GWFde","number":165717,"title":"illum - increasing brightness cycles through low values","user":{"login":"nothingmuch","id":14242,"node_id":"MDQ6VXNlcjE0MjQy","avatar_url":"https://avatars.githubusercontent.com/u/14242?v=4","gravatar_id":"","url":"https://api.github.com/users/nothingmuch","html_url":"https://github.com/nothingmuch","followers_url":"https://api.github.com/users/nothingmuch/followers","following_url":"https://api.github.com/users/nothingmuch/following{/other_user}","gists_url":"https://api.github.com/users/nothingmuch/gists{/gist_id}","starred_url":"https://api.github.com/users/nothingmuch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nothingmuch/subscriptions","organizations_url":"https://api.github.com/users/nothingmuch/orgs","repos_url":"https://api.github.com/users/nothingmuch/repos","events_url":"https://api.github.com/users/nothingmuch/events{/privacy}","received_events_url":"https://api.github.com/users/nothingmuch/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-25T00:28:42Z","updated_at":"2022-03-25T00:28:42Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen pressing the increase brightness hotkey, the value cycles through several very low settings. Decrease brightness key works normally.\r\n\r\nI can echo the right value into `/sys/class/backlight/intel_backlight/brightness` in order to be able to get back to a usable brightness.\r\n\r\nThe illum service was previously enabled and was working with sway. After switching from sway back to i3 due to stability issues, it was upgraded and I only noticed that it broke a while later so I'm not sure exactly which configuration change led to it. Honestly it could have even been broken before this switch, I don't know.\r\n\r\nConfusingly there are several versions in my nix store which all claim to be `illum-+` when given the `-V` option. I tested all of these, two of them have the issue:\r\n\r\n```\r\n> ls /nix/store/*-illum-0*/bin/illum-d\r\n/nix/store/2838q6kqsq86qwj2zrxyfc2q2cb84p65-illum-0.4/bin/illum-d\r\n/nix/store/3im2qsi69rpmchhcg7yn6gyd5bhprac2-illum-0.5/bin/illum-d # has bug\r\n/nix/store/3jhi3ab12nq3a206kn5bjxh3j44kqbg0-illum-0.4/bin/illum-d \r\n/nix/store/624vjp0zg5jfwf9pcs8jmzrg0nw1a2ny-illum-0.4/bin/illum-d\r\n/nix/store/a5ygx2j3rh8ga8vna2iqbv7szq6nzjcx-illum-0.4/bin/illum-d # has bug\r\n/nix/store/aiy4xdjvwasybig3vb4dpxcy61mqhzzv-illum-0.4/bin/illum-d\r\n```\r\n\r\nThe versions with the bug have a different output e.g.:\r\n\r\n```\r\n> sudo /nix/store/a5ygx2j3rh8ga8vna2iqbv7szq6nzjcx-illum-0.4/bin/illum-d\r\n<6>using /sys/devices/pci0000:00/0000:00:02.0/backlight/acpi_video0 as a backlight\r\n<6>using /sys/devices/pci0000:00/0000:00:02.0/drm/card0/card0-eDP-1/intel_backlight as a backlight\r\n<6>using /sys/devices/LNXSYSTM:00/LNXSYBUS:00/PNP0A08:00/LNXVIDEO:00/input/input2/event1 as an input dev\r\n<6>using /sys/devices/platform/INT33D5:00/input/input5/event5 as an input dev\r\n```\r\n\r\nand its `.drv`: \r\n[nhk9gb1sczqi2md4zq70q1b8kvh950h9-illum-0.4.drv.txt](https://github.com/NixOS/nixpkgs/files/8346463/nhk9gb1sczqi2md4zq70q1b8kvh950h9-illum-0.4.drv.txt)\r\n\r\n\r\nAs compared to the working ones, e.g.:\r\n\r\n```\r\n> sudo /nix/store/aiy4xdjvwasybig3vb4dpxcy61mqhzzv-illum-0.4/bin/illum-d\r\n<6>using event5 as an input dev\r\n<6>using event1 as an input dev\r\n```\r\n\r\nand its `.drv`: [by7wvv9mmhy8w2kj5avh9ba35dnl4jda-illum-0.4.drv.txt](https://github.com/NixOS/nixpkgs/files/8346457/by7wvv9mmhy8w2kj5avh9ba35dnl4jda-illum-0.4.drv.txt)\r\n\r\nI'm not sure how to trace back from the drvs to how it was included and in which generation of my system, so I just attached them here. Is the right thing to do to bisect nixpkgs? Illum's upstream? Not sure how to proceed.\r\n\r\n### Steps To Reproduce\r\n\r\n1. arrange for a more recent version of illum (possibly requiring my dodgy laptop to replicate)\r\n2. press increase brightness hotkey\r\n\r\n### Expected behavior\r\n\r\nLaptop screen brightness should increase until maximum value\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.15, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-21.11pre306621.439b1605227, nixos-20.09-20.09.4393.068984c00e0\"`\r\n - channels(user): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165717/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165714","id":1180166766,"node_id":"I_kwDOAEVQ_M5GV-pu","number":165714,"title":"networkd - applying links requires restart systemd-udev-trigger.service","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-24T23:38:45Z","updated_at":"2022-03-25T03:39:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOof, just lost some time to this.\r\n\r\n1. Switched to networkd.\r\n2. Add link to rename interface.\r\n3. Debug for an hour, even though it was right.\r\n\r\nOn a whim I just started restarting everything I could find. Restarting `systemd-udevd` didn't do it, but restarting `systemd-udev-trigger.service` did.\r\n\r\nMaybe we could do that automatically?\r\n\r\nThis is on latest nixos-unstable: `commit 1ec61dd4167f04be8d05c45780818826132eea0d (nixos/nixos-unstable)`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165714/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165708","id":1180136877,"node_id":"I_kwDOAEVQ_M5GV3Wt","number":165708,"title":"virtualisation.libvirtd.enable option brings up a broken virt-xml-validate","user":{"login":"renatoGarcia","id":220211,"node_id":"MDQ6VXNlcjIyMDIxMQ==","avatar_url":"https://avatars.githubusercontent.com/u/220211?v=4","gravatar_id":"","url":"https://api.github.com/users/renatoGarcia","html_url":"https://github.com/renatoGarcia","followers_url":"https://api.github.com/users/renatoGarcia/followers","following_url":"https://api.github.com/users/renatoGarcia/following{/other_user}","gists_url":"https://api.github.com/users/renatoGarcia/gists{/gist_id}","starred_url":"https://api.github.com/users/renatoGarcia/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/renatoGarcia/subscriptions","organizations_url":"https://api.github.com/users/renatoGarcia/orgs","repos_url":"https://api.github.com/users/renatoGarcia/repos","events_url":"https://api.github.com/users/renatoGarcia/events{/privacy}","received_events_url":"https://api.github.com/users/renatoGarcia/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-24T22:56:37Z","updated_at":"2022-03-24T22:56:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nIf just enabled `virtualisation.libvirtd.enable = true` on `/etc/nixos/configuration.nix`, the `virt-xml-validate` executable will be on system path, but when called it will break with error:\r\n\r\n /nix/store/kwv9550j1ip0sgm9rgh70pz5ljhh1dj1-system-path/bin/virt-xml-validate: line 129: xmllint: command not found\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable `virtualisation.libvirtd.enable = true` on `/etc/nixos/configuration.nix`\r\n2. Make sure that neither `libvirt` or `libxml2` are explicitly installed\r\n3. Create an empty or use any libvirt xml (`touch /tmp/aaa.xml`)\r\n4. Run `virt-xml-validate /tmp/aaa.xml domain`\r\n\r\n\r\n### Expected behavior\r\n\r\nI would expect that if the `virtualisation.libvirtd.enable = true` option adds `virt-xml-validate` to the system path, that program would work correctly.\r\n\r\n\r\n### Additional context\r\n\r\nThe `virt-xml-validate` executable is part of `libvirt` package. The `libvirt` package by its turn is the default value of `virtualisation.libvirtd.package`.\r\n\r\nThe `xmllint` executable is part of `libxml2` package. The `libxml2` package is in the [`buildInputs` list](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/development/libraries/libvirt/default.nix#L115) of `libvirt`. If either `libvirt` or `libxml2` packages are explicitly installed, the `xmllint` executable will be put on system path, and the bug will be gone.\r\n\r\n### Notify maintainers\r\n\r\n@fpletz @globin \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.105, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(renatofg): `\"nixpkgs-22.05pre360843.3eb07eeafb5\"`\r\n - channels(root): `\"nixos-21.11.336538.64fc73bd74f\"`\r\n - nixpkgs: `/home/renatofg/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165708/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165704","id":1180096555,"node_id":"I_kwDOAEVQ_M5GVtgr","number":165704,"title":"nixpkgs `clang` does not seem to support `-Wformat` errors","user":{"login":"albertgoncalves","id":39544913,"node_id":"MDQ6VXNlcjM5NTQ0OTEz","avatar_url":"https://avatars.githubusercontent.com/u/39544913?v=4","gravatar_id":"","url":"https://api.github.com/users/albertgoncalves","html_url":"https://github.com/albertgoncalves","followers_url":"https://api.github.com/users/albertgoncalves/followers","following_url":"https://api.github.com/users/albertgoncalves/following{/other_user}","gists_url":"https://api.github.com/users/albertgoncalves/gists{/gist_id}","starred_url":"https://api.github.com/users/albertgoncalves/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/albertgoncalves/subscriptions","organizations_url":"https://api.github.com/users/albertgoncalves/orgs","repos_url":"https://api.github.com/users/albertgoncalves/repos","events_url":"https://api.github.com/users/albertgoncalves/events{/privacy}","received_events_url":"https://api.github.com/users/albertgoncalves/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-24T21:59:40Z","updated_at":"2022-03-24T21:59:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"There is a difference in warning/error behavior when compiling identical programs with `clang` and `clang++` when installed via a `nix` shell environment.\r\n\r\nConsidering a small `.c` program:\r\n```c\r\n#include <stdio.h>\r\n\r\nint main(void) {\r\n printf(\"%hd\\n\", 1.0f);\r\n return 0;\r\n}\r\n```\r\nI would expect to see some kind of warning or error thrown due to the incorrect string formatting (`%hd` instead of `%f`).\r\n\r\nIf I enter into an environment with `llvm_14` via:\r\n```nix\r\nwith import <nixpkgs> {};\r\nmkShell.override { stdenv = llvmPackages_14.stdenv; } {\r\n buildInputs = [\r\n ];\r\n shellHook = ''\r\n '';\r\n}\r\n```\r\n```bash\r\n$ nix-shell\r\n```\r\n\r\nCompiling this program with `clang` (on `linux`) yields no warnings or errors:\r\n```bash\r\n$ which clang\r\n/nix/store/qfa5jcmmz8iv43x72z3vlvyxj3l08f98-clang-wrapper-14.0.0-rc4/bin/clang\r\n```\r\n```bash\r\n$ clang -O1 -Werror -Wall -Wformat \"-std=c11\" -o \"main_c\" \"main.c\"\r\n```\r\n\r\nYet, compiling with `clang++` does produce an error:\r\n```bash\r\n$ which clang++\r\n/nix/store/qfa5jcmmz8iv43x72z3vlvyxj3l08f98-clang-wrapper-14.0.0-rc4/bin/clang++\r\n```\r\n```bash\r\n$ cp main.c main.cpp\r\n$ clang++ -O1 -Werror -Wall -Wformat \"-std=c++11\" -o \"main_cpp\" \"main.cpp\"\r\n```\r\n```\r\nmain.cpp:4:21: error: format specifies type 'short' but the argument has type 'float' [-Werror,-Wformat]\r\n printf(\"%hd\\n\", 1.0f);\r\n ~~~ ^~~~\r\n %f\r\n1 error generated.\r\n```\r\n\r\nWhen attempting the same comparison with a locally installed version of `clang` (not via `nix`), `clang` succeeded in producing an error here. Is this a bug in the `nix packages` version of `clang`? I had originally noticed this behavior 2-3 years ago, chalked it up as a bug and figured it would be resolved down the line. Anyone have any insight what's going on here?\r\n\r\n---\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 4.15.0-142-generic, Ubuntu, 16.04.7 LTS (Xenial Xerus)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(albert): `\"nixpkgs-22.05pre360843.3eb07eeafb5\"`\r\n - nixpkgs: `/home/albert/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165704/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165682","id":1179981222,"node_id":"I_kwDOAEVQ_M5GVRWm","number":165682,"title":"RFC: Built-in tool to bundle executable with dynamic libraries","user":{"login":"elliot-midnight","id":87149454,"node_id":"MDQ6VXNlcjg3MTQ5NDU0","avatar_url":"https://avatars.githubusercontent.com/u/87149454?v=4","gravatar_id":"","url":"https://api.github.com/users/elliot-midnight","html_url":"https://github.com/elliot-midnight","followers_url":"https://api.github.com/users/elliot-midnight/followers","following_url":"https://api.github.com/users/elliot-midnight/following{/other_user}","gists_url":"https://api.github.com/users/elliot-midnight/gists{/gist_id}","starred_url":"https://api.github.com/users/elliot-midnight/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/elliot-midnight/subscriptions","organizations_url":"https://api.github.com/users/elliot-midnight/orgs","repos_url":"https://api.github.com/users/elliot-midnight/repos","events_url":"https://api.github.com/users/elliot-midnight/events{/privacy}","received_events_url":"https://api.github.com/users/elliot-midnight/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":465618943,"node_id":"MDU6TGFiZWw0NjU2MTg5NDM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20community%20feedback","name":"9.needs: community feedback","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-03-24T19:53:34Z","updated_at":"2022-04-04T14:00:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"I recently had to bundle a C++ app for distribution to macOS users who do not have Nix and do not want to build the project themselves.\r\n\r\nI came up with a quick script (found here: https://gist.github.com/elliot-midnight/90a8fb90a577bce30fc7c6fae2f31abb) that got the job done. This was simple enough that it made me curious why this isn't already built-in to nixpkgs. Or maybe it is and I couldn't find it.\r\n\r\nIf this doesn't exist, should I try to polish this up to work on Linux too and submit it? What limitations am I missing?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165682/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165670","id":1179903485,"node_id":"I_kwDOAEVQ_M5GU-X9","number":165670,"title":"GraalVM builds broken for x86_64-darwin on unstable","user":{"login":"whentze","id":6296348,"node_id":"MDQ6VXNlcjYyOTYzNDg=","avatar_url":"https://avatars.githubusercontent.com/u/6296348?v=4","gravatar_id":"","url":"https://api.github.com/users/whentze","html_url":"https://github.com/whentze","followers_url":"https://api.github.com/users/whentze/followers","following_url":"https://api.github.com/users/whentze/following{/other_user}","gists_url":"https://api.github.com/users/whentze/gists{/gist_id}","starred_url":"https://api.github.com/users/whentze/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/whentze/subscriptions","organizations_url":"https://api.github.com/users/whentze/orgs","repos_url":"https://api.github.com/users/whentze/repos","events_url":"https://api.github.com/users/whentze/events{/privacy}","received_events_url":"https://api.github.com/users/whentze/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-03-24T18:39:11Z","updated_at":"2022-04-11T20:20:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOn current nixpkgs unstable, GraalVM 11 and 17 both fail to build for darwin.\r\nSince this is a build dependency of several other packages like `babashka` and `clj-kondo`, these are also broken.\r\n\r\nWe have bisected nixpkgs and found that the regression was likely introduced in https://github.com/NixOS/nixpkgs/pull/149731\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Be a Mac\r\n2. `nix-build -A graalvm11-ce https://github.com/nixos/nixpkgs/tarball/12e48068a5aa63a3965d9a0c65409c875c5877c4`\r\n\r\n### Expected behavior\r\nThe build should succeed\r\n\r\n### Screenshots\r\nError message from the build:\r\n```\r\npatching script interpreter paths in /nix/store/mh8g4k1azqa8xx6mnlcfknckdhaybx1i-graalvm11-ce-lib\r\nTraceback (most recent call last):\r\n File \"/nix/store/0jzc88szm7fsjrhzs7jbcj4ini24sj9f-auto-patchelf.py\", line 322, in <module>\r\n with open_elf(interpreter_path) as interpreter:\r\n File \"/nix/store/3j4k5ja8zpr7v5xiyfgjwjb8qnl4iycv-python3-3.9.10/lib/python3.9/contextlib.py\", line 119, in __enter__\r\n return next(self.gen)\r\n File \"/nix/store/0jzc88szm7fsjrhzs7jbcj4ini24sj9f-auto-patchelf.py\", line 26, in open_elf\r\n yield ELFFile(stream)\r\n File \"/nix/store/0qmwd1hj38nj7dsnyhn5pxbwqv6f52m1-python3-3.9.10-env/lib/python3.9/site-packages/elftools/elf/elffile.py\", line 73, in __init__\r\n self._identify_file()\r\n File \"/nix/store/0qmwd1hj38nj7dsnyhn5pxbwqv6f52m1-python3-3.9.10-env/lib/python3.9/site-packages/elftools/elf/elffile.py\", line 482, in _identify_file\r\n elf_assert(magic == b'\\x7fELF', 'Magic number does not match')\r\n File \"/nix/store/0qmwd1hj38nj7dsnyhn5pxbwqv6f52m1-python3-3.9.10-env/lib/python3.9/site-packages/elftools/common/utils.py\", line 77, in elf_assert\r\n _assert_with_exception(cond, msg, ELFError)\r\n File \"/nix/store/0qmwd1hj38nj7dsnyhn5pxbwqv6f52m1-python3-3.9.10-env/lib/python3.9/site-packages/elftools/common/utils.py\", line 114, in _assert_with_exception\r\n raise exception_type(msg)\r\nelftools.common.exceptions.ELFError: Magic number does not match\r\n```\r\n\r\n### Additional context\r\n\r\nThe builds are failing on Hydra too:\r\n\r\nhttps://hydra.nixos.org/job/nixpkgs/trunk/graalvm11-ce.x86_64-darwin\r\nhttps://hydra.nixos.org/job/nixpkgs/trunk/graalvm17-ce.x86_64-darwin\r\n\r\n#163924 Looks like it may be related to this.\r\n\r\n### Notify maintainers\r\nAuthor of #149731:\r\n@layus\r\n\r\nGraalVM package maintainers:\r\n@bandresen\r\n@volth\r\n@hlolli\r\n@glittershark\r\n@babariviere\r\n@ericdallo\r\n@thiagokokada\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165670/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165640","id":1179681083,"node_id":"I_kwDOAEVQ_M5GUIE7","number":165640,"title":"Package request: hygen","user":{"login":"mainrs","id":5113257,"node_id":"MDQ6VXNlcjUxMTMyNTc=","avatar_url":"https://avatars.githubusercontent.com/u/5113257?v=4","gravatar_id":"","url":"https://api.github.com/users/mainrs","html_url":"https://github.com/mainrs","followers_url":"https://api.github.com/users/mainrs/followers","following_url":"https://api.github.com/users/mainrs/following{/other_user}","gists_url":"https://api.github.com/users/mainrs/gists{/gist_id}","starred_url":"https://api.github.com/users/mainrs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mainrs/subscriptions","organizations_url":"https://api.github.com/users/mainrs/orgs","repos_url":"https://api.github.com/users/mainrs/repos","events_url":"https://api.github.com/users/mainrs/events{/privacy}","received_events_url":"https://api.github.com/users/mainrs/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-24T15:30:28Z","updated_at":"2022-03-24T18:55:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n`hygen` is a template CLI that allows one to specify project-specific templates that one can invoke to generate boilerplate code.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/jondot/hygen\r\n* source URL: https://github.com/jondot/hygen\r\n* license: mit\r\n* platforms: unix, linux, darwin\r\n\r\nIs it enough to include the package here? https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/node-packages/node-packages.json \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165640/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165471","id":1178375289,"node_id":"I_kwDOAEVQ_M5GPJR5","number":165471,"title":"nixpkgs-maintainers team members notifications set to all activity","user":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":true,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-23T16:38:28Z","updated_at":"2022-03-23T16:39:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"https://discourse.nixos.org/t/incident-some-custom-notifications-for-nixpkgs-have-been-lost\r\n\r\nTo fix set the watch setting to participating\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165471/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165422","id":1177870939,"node_id":"I_kwDOAEVQ_M5GNOJb","number":165422,"title":"freedv does not build on darwin","user":{"login":"knl","id":361496,"node_id":"MDQ6VXNlcjM2MTQ5Ng==","avatar_url":"https://avatars.githubusercontent.com/u/361496?v=4","gravatar_id":"","url":"https://api.github.com/users/knl","html_url":"https://github.com/knl","followers_url":"https://api.github.com/users/knl/followers","following_url":"https://api.github.com/users/knl/following{/other_user}","gists_url":"https://api.github.com/users/knl/gists{/gist_id}","starred_url":"https://api.github.com/users/knl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/knl/subscriptions","organizations_url":"https://api.github.com/users/knl/orgs","repos_url":"https://api.github.com/users/knl/repos","events_url":"https://api.github.com/users/knl/events{/privacy}","received_events_url":"https://api.github.com/users/knl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":{"login":"Kloenk","id":12898828,"node_id":"MDQ6VXNlcjEyODk4ODI4","avatar_url":"https://avatars.githubusercontent.com/u/12898828?v=4","gravatar_id":"","url":"https://api.github.com/users/Kloenk","html_url":"https://github.com/Kloenk","followers_url":"https://api.github.com/users/Kloenk/followers","following_url":"https://api.github.com/users/Kloenk/following{/other_user}","gists_url":"https://api.github.com/users/Kloenk/gists{/gist_id}","starred_url":"https://api.github.com/users/Kloenk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Kloenk/subscriptions","organizations_url":"https://api.github.com/users/Kloenk/orgs","repos_url":"https://api.github.com/users/Kloenk/repos","events_url":"https://api.github.com/users/Kloenk/events{/privacy}","received_events_url":"https://api.github.com/users/Kloenk/received_events","type":"User","site_admin":false},"assignees":[{"login":"Kloenk","id":12898828,"node_id":"MDQ6VXNlcjEyODk4ODI4","avatar_url":"https://avatars.githubusercontent.com/u/12898828?v=4","gravatar_id":"","url":"https://api.github.com/users/Kloenk","html_url":"https://github.com/Kloenk","followers_url":"https://api.github.com/users/Kloenk/followers","following_url":"https://api.github.com/users/Kloenk/following{/other_user}","gists_url":"https://api.github.com/users/Kloenk/gists{/gist_id}","starred_url":"https://api.github.com/users/Kloenk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Kloenk/subscriptions","organizations_url":"https://api.github.com/users/Kloenk/orgs","repos_url":"https://api.github.com/users/Kloenk/repos","events_url":"https://api.github.com/users/Kloenk/events{/privacy}","received_events_url":"https://api.github.com/users/Kloenk/received_events","type":"User","site_admin":false}],"milestone":null,"comments":2,"created_at":"2022-03-23T09:47:59Z","updated_at":"2022-03-23T13:35:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nBuilding freedv on darwin fails.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n`nix-build -A freedv` \r\n\r\n### Expected behavior\r\n\r\nIt builds.\r\n\r\n### Additional context\r\n\r\nThis is the error message from the build:\r\n\r\n```\r\n[ 97%] Building CXX object src/CMakeFiles/FreeDV.dir/osx_interface.mm.o\r\n/tmp/nix-build-freedv-1.7.0.drv-0/source/src/osx_interface.mm:23:9: fatal error: 'AVFoundation/AVFoundation.h' file not found\r\n#import <AVFoundation/AVFoundation.h>\r\n ^~~~~~~~~~~~~~~~~~~~~~~~~~~~~\r\nCopying OS X content src/FreeDV.app/Contents/Resources/freedv.icns\r\n1 error generated.\r\nmake[2]: *** [src/CMakeFiles/FreeDV.dir/build.make:556: src/CMakeFiles/FreeDV.dir/osx_interface.mm.o] Error 1\r\nmake[2]: *** Waiting for unfinished jobs....\r\nmake[1]: *** [CMakeFiles/Makefile2:160: src/CMakeFiles/FreeDV.dir/all] Error 2\r\nmake: *** [Makefile:136: all] Error 2\r\nerror: builder for '/nix/store/p0zhhfw1n5fxhkzq3zxd91yr0r8ygkm5-freedv-1.7.0.drv' failed with exit code 2\r\n```\r\n\r\n### Notify maintainers\r\n\r\nSeems the maintainer doesn't exist or `mvs` is not a github name.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(nknezevi1): `\"\"`\r\n - nixpkgs: `/nix/store/f1s4icgz5zdvwgpc8kb9nr7ab46ak5wv-nixpkgs-src`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165422/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165345","id":1177458337,"node_id":"I_kwDOAEVQ_M5GLpah","number":165345,"title":"Packaging request: Authelia","user":{"login":"ettom","id":36895504,"node_id":"MDQ6VXNlcjM2ODk1NTA0","avatar_url":"https://avatars.githubusercontent.com/u/36895504?v=4","gravatar_id":"","url":"https://api.github.com/users/ettom","html_url":"https://github.com/ettom","followers_url":"https://api.github.com/users/ettom/followers","following_url":"https://api.github.com/users/ettom/following{/other_user}","gists_url":"https://api.github.com/users/ettom/gists{/gist_id}","starred_url":"https://api.github.com/users/ettom/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ettom/subscriptions","organizations_url":"https://api.github.com/users/ettom/orgs","repos_url":"https://api.github.com/users/ettom/repos","events_url":"https://api.github.com/users/ettom/events{/privacy}","received_events_url":"https://api.github.com/users/ettom/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-23T00:49:46Z","updated_at":"2022-03-23T00:49:46Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nAuthelia is an open-source authentication and authorization server providing two-factor authentication and single sign-on (SSO) for web applications.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.authelia.com/\r\n* source URL: https://github.com/authelia/authelia\r\n* license: Apache License 2.0\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165345/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165300","id":1177074153,"node_id":"I_kwDOAEVQ_M5GKLnp","number":165300,"title":"Pipewire 0.3.42 causing issues with Jabra Headset Microphone","user":{"login":"robaca","id":580474,"node_id":"MDQ6VXNlcjU4MDQ3NA==","avatar_url":"https://avatars.githubusercontent.com/u/580474?v=4","gravatar_id":"","url":"https://api.github.com/users/robaca","html_url":"https://github.com/robaca","followers_url":"https://api.github.com/users/robaca/followers","following_url":"https://api.github.com/users/robaca/following{/other_user}","gists_url":"https://api.github.com/users/robaca/gists{/gist_id}","starred_url":"https://api.github.com/users/robaca/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/robaca/subscriptions","organizations_url":"https://api.github.com/users/robaca/orgs","repos_url":"https://api.github.com/users/robaca/repos","events_url":"https://api.github.com/users/robaca/events{/privacy}","received_events_url":"https://api.github.com/users/robaca/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-22T17:19:05Z","updated_at":"2022-04-07T06:38:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nSince update to pipewire 0.3.42 in 21.11, I cannot use my Jabra headset microphone any more. It seems like a known issue fixed in 0.3.43 (https://gitlab.freedesktop.org/pipewire/pipewire/-/issues/1975). \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Activate pipewire on NixOS 0.3.42\r\n2. Connect a Jabra Evolve2 75 headset via Dongle\r\n3. In PulseAudio Mixer, the microphone does not show a sound meter and does not work.\r\n\r\n### Expected behavior\r\nJabra Microphone works like before\r\n\r\n### Screenshots\r\n\r\n\r\n### Notify maintainers\r\n@jtojnar @kranzes\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.15, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"home-manager, nixos-21.11pre333218.263ef4cc414, nixos-1909-19.09.2522.75f4ba05c63, unstable-21.11pre333180.98747f27ecf\"`\r\n - channels(carsten): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165300/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165256","id":1176609906,"node_id":"I_kwDOAEVQ_M5GIaRy","number":165256,"title":"autoResize and autoFormat should use mount options x-systemd.makefs and x-systemd.growfs instead of custom units","user":{"login":"ElvishJerricco","id":1365692,"node_id":"MDQ6VXNlcjEzNjU2OTI=","avatar_url":"https://avatars.githubusercontent.com/u/1365692?v=4","gravatar_id":"","url":"https://api.github.com/users/ElvishJerricco","html_url":"https://github.com/ElvishJerricco","followers_url":"https://api.github.com/users/ElvishJerricco/followers","following_url":"https://api.github.com/users/ElvishJerricco/following{/other_user}","gists_url":"https://api.github.com/users/ElvishJerricco/gists{/gist_id}","starred_url":"https://api.github.com/users/ElvishJerricco/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ElvishJerricco/subscriptions","organizations_url":"https://api.github.com/users/ElvishJerricco/orgs","repos_url":"https://api.github.com/users/ElvishJerricco/repos","events_url":"https://api.github.com/users/ElvishJerricco/events{/privacy}","received_events_url":"https://api.github.com/users/ElvishJerricco/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-22T10:56:16Z","updated_at":"2022-03-22T10:56:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Systemd includes code in `systemd-fstab-generator` that will format and resize file systems automatically. There's no need for our custom units.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165256/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165246","id":1176507616,"node_id":"I_kwDOAEVQ_M5GIBTg","number":165246,"title":"autogenerated Unsupported git:// github URLs causing problems","user":{"login":"tysonzero","id":5274223,"node_id":"MDQ6VXNlcjUyNzQyMjM=","avatar_url":"https://avatars.githubusercontent.com/u/5274223?v=4","gravatar_id":"","url":"https://api.github.com/users/tysonzero","html_url":"https://github.com/tysonzero","followers_url":"https://api.github.com/users/tysonzero/followers","following_url":"https://api.github.com/users/tysonzero/following{/other_user}","gists_url":"https://api.github.com/users/tysonzero/gists{/gist_id}","starred_url":"https://api.github.com/users/tysonzero/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tysonzero/subscriptions","organizations_url":"https://api.github.com/users/tysonzero/orgs","repos_url":"https://api.github.com/users/tysonzero/repos","events_url":"https://api.github.com/users/tysonzero/events{/privacy}","received_events_url":"https://api.github.com/users/tysonzero/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"assignees":[{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false}],"milestone":null,"comments":17,"created_at":"2022-03-22T09:30:22Z","updated_at":"2022-04-13T10:37:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThere are a variety of `git://` URLs in nixpkgs, and they are [no longer supported](https://github.blog/2021-09-01-improving-git-protocol-security-github/). In my specific case it is the `ghcjs-base` one that's breaking the build.\r\n\r\n### Steps To Reproduce\r\nBuild any package that uses a `git://` URL that isn't already cached.\r\nOn a fresh install, building `ghcjs-base` should do the trick:\r\n```\r\nexporting git://github.com/ghcjs/ghcjs-base (rev 85e31beab9beffc3ea91b954b61a5d04e708b8f2) into /nix/store/0fnf3zdl50j7awsv8znc3q9axlygpvla-ghcjs-base-85e31be\r\nInitialized empty Git repository in /nix/store/0fnf3zdl50j7awsv8znc3q9axlygpvla-ghcjs-base-85e31be/.git/\r\nfatal: remote error: \r\n The unauthenticated git protocol on port 9418 is no longer supported.\r\nPlease see https://github.blog/2021-09-01-improving-git-protocol-security-github/ for more information.\r\nfatal: remote error: \r\n The unauthenticated git protocol on port 9418 is no longer supported.\r\nPlease see https://github.blog/2021-09-01-improving-git-protocol-security-github/ for more information.\r\nfatal: remote error: \r\n The unauthenticated git protocol on port 9418 is no longer supported.\r\nPlease see https://github.blog/2021-09-01-improving-git-protocol-security-github/ for more information.\r\nUnable to checkout 85e31beab9beffc3ea91b954b61a5d04e708b8f2 from git://github.com/ghcjs/ghcjs-base.\r\n```\r\n\r\n### Expected behavior\r\nBuild success\r\n\r\n### Notify maintainers\r\n@ElvishJerricco @dfordivam\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.1.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246/reactions","total_count":6,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":4},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165246/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165175","id":1175963843,"node_id":"I_kwDOAEVQ_M5GF8jD","number":165175,"title":"Cassandra jvm.options have invalid defaults","user":{"login":"steinybot","id":4659562,"node_id":"MDQ6VXNlcjQ2NTk1NjI=","avatar_url":"https://avatars.githubusercontent.com/u/4659562?v=4","gravatar_id":"","url":"https://api.github.com/users/steinybot","html_url":"https://github.com/steinybot","followers_url":"https://api.github.com/users/steinybot/followers","following_url":"https://api.github.com/users/steinybot/following{/other_user}","gists_url":"https://api.github.com/users/steinybot/gists{/gist_id}","starred_url":"https://api.github.com/users/steinybot/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/steinybot/subscriptions","organizations_url":"https://api.github.com/users/steinybot/orgs","repos_url":"https://api.github.com/users/steinybot/repos","events_url":"https://api.github.com/users/steinybot/events{/privacy}","received_events_url":"https://api.github.com/users/steinybot/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-21T21:29:36Z","updated_at":"2022-03-21T21:30:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe `conf/jvm.options` that get installed with the cassandra nixpkgs have values which are invalid.\r\n\r\nIt contains:\r\n```\r\n# Per-thread stack size.\r\n-Xss256k\r\n```\r\n\r\nWhich is too small.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p cassandra`\r\n2. `cassandra -f`\r\n\r\nOutput:\r\n```\r\nThe stack size specified is too small, Specify at least 384k\r\nError: Could not create the Java Virtual Machine.\r\nError: A fatal exception has occurred. Program will exit.\r\n```\r\n\r\n### Expected behavior\r\n\r\nAll the defaults should be sufficient to start cassandra.\r\n\r\n### Screenshots\r\n\r\n### Additional context\r\n\r\nFor some options you can set `JVM_OPTS` but anything which is specified in `jvm.options` will override that as they get appended to that variable.\r\n\r\nYou can also specify `CASSANDRA_CONF` which is a bit annoying as you'll need to copy most of the files (although probably required to run anything realistic anyway).\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[nix-shell:~/src/goodcover/core/temp]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(root): `\"nixpkgs\"`\r\n - channels(jason): `\"darwin, home-manager, steinybot\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165175/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165170","id":1175932139,"node_id":"I_kwDOAEVQ_M5GF0zr","number":165170,"title":"`lomo` fails to build on Darwin","user":{"login":"austinbutler","id":354741,"node_id":"MDQ6VXNlcjM1NDc0MQ==","avatar_url":"https://avatars.githubusercontent.com/u/354741?v=4","gravatar_id":"","url":"https://api.github.com/users/austinbutler","html_url":"https://github.com/austinbutler","followers_url":"https://api.github.com/users/austinbutler/followers","following_url":"https://api.github.com/users/austinbutler/following{/other_user}","gists_url":"https://api.github.com/users/austinbutler/gists{/gist_id}","starred_url":"https://api.github.com/users/austinbutler/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/austinbutler/subscriptions","organizations_url":"https://api.github.com/users/austinbutler/orgs","repos_url":"https://api.github.com/users/austinbutler/repos","events_url":"https://api.github.com/users/austinbutler/events{/privacy}","received_events_url":"https://api.github.com/users/austinbutler/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T20:57:21Z","updated_at":"2022-03-21T23:10:53Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`lomo` fails to build on Darwin.\r\n\r\n### Steps To Reproduce\r\n\r\n1. `nix-build -A lomo`\r\n\r\n### Expected behavior\r\n\r\nBuild completes.\r\n\r\n### Additional context\r\n\r\nFailure log:\r\n```\r\nDEPRECATED: Libs must be qualified, change fipp => fipp/fipp (/private/var/folders/1s/gpt7p1x559sb7qjb_4bhq7zc75yv8y/T/nix-build-lumo-1.10.1.drv-0/lumo/deps.edn)\r\nDEPRECATED: Libs must be qualified, change fipp => fipp/fipp (deps.edn)\r\nWARNING: Implicit use of clojure.main with options is deprecated, use -M\r\njava.io.FileInputStream\r\n#'user/write-transit-json\r\n#'user/process-caches\r\nBuilding production bundle...\r\nCircular dependency: src/js/cljs.js -> src/js/repl.js -> src/js/cljs.js\r\nCircular dependency: src/js/cli.js -> src/js/cljs.js -> src/js/repl.js -> src/js/socketRepl.js -> src/js/cli.js\r\nCircular dependency: src/js/repl.js -> src/js/socketRepl.js -> src/js/repl.js\r\nCircular dependency: src/js/cljs.js -> src/js/repl.js -> src/js/socketRepl.js -> src/js/cljs.js\r\n----> framework => node\r\n----> using provided bundle target/bundle.min.js since noBundle is true\r\n----> monkey patch /private/var/folders/1s/gpt7p1x559sb7qjb_4bhq7zc75yv8y/T/nix-build-lumo-1.10.1.drv-0/lumo/tmp/node/11.13.0/node.gyp\r\n----> monkey patch /private/var/folders/1s/gpt7p1x559sb7qjb_4bhq7zc75yv8y/T/nix-build-lumo-1.10.1.drv-0/lumo/tmp/node/11.13.0/src/node.cc\r\n----> monkey patching configure file\r\n----> monkey patch /private/var/folders/1s/gpt7p1x559sb7qjb_4bhq7zc75yv8y/T/nix-build-lumo-1.10.1.drv-0/lumo/tmp/node/11.13.0/configure.py\r\n----> monkey patch /private/var/folders/1s/gpt7p1x559sb7qjb_4bhq7zc75yv8y/T/nix-build-lumo-1.10.1.drv-0/lumo/tmp/node/11.13.0/lib/internal/bootstrap/node.js\r\n----> using the after 0.12.5 method of ignoring flags.\r\n----> using the after 5.5.0 method of ignoring flags.\r\n....> ERROR: Failed to find a way to patch node.cc to ignoreFlags\r\n----> startLine = -1 | endLine = -2\r\n----> patched node.cc\r\n----> make\r\nERROR: Did not find a new enough assembler, install one or build with\r\n --openssl-no-asm.\r\n Please refer to BUILDING.md\r\nMissing or stale config.gypi, please run ./configure\r\nmake: *** [Makefile:134: config.gypi] Error 1\r\n....> ERROR: The release executable has not been generated. This indicates a failure in the build process. There is likely additional information above.\r\nbuilder for '/nix/store/9v3zzl8asnbp11pp0yl3a5n1z4zq522a-lumo-1.10.1.drv' failed with exit code 1\r\nerror: build of '/nix/store/9v3zzl8asnbp11pp0yl3a5n1z4zq522a-lumo-1.10.1.drv' failed\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@hlolli \r\n\r\n### Metadata\r\n\r\n```yaml\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.6`\r\n - channels(abutler): `\"home-manager, nixpkgs-22.05pre360843.3eb07eeafb5\"`\r\n - nixpkgs: `/Users/abutler/.nix-defexpr/channels/nixpkgs`\r\n - ```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165170/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165167","id":1175907350,"node_id":"I_kwDOAEVQ_M5GFuwW","number":165167,"title":"fwup failes to build on aarch64-darwin ","user":{"login":"mathewprokos","id":782643,"node_id":"MDQ6VXNlcjc4MjY0Mw==","avatar_url":"https://avatars.githubusercontent.com/u/782643?v=4","gravatar_id":"","url":"https://api.github.com/users/mathewprokos","html_url":"https://github.com/mathewprokos","followers_url":"https://api.github.com/users/mathewprokos/followers","following_url":"https://api.github.com/users/mathewprokos/following{/other_user}","gists_url":"https://api.github.com/users/mathewprokos/gists{/gist_id}","starred_url":"https://api.github.com/users/mathewprokos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mathewprokos/subscriptions","organizations_url":"https://api.github.com/users/mathewprokos/orgs","repos_url":"https://api.github.com/users/mathewprokos/repos","events_url":"https://api.github.com/users/mathewprokos/events{/privacy}","received_events_url":"https://api.github.com/users/mathewprokos/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T20:29:41Z","updated_at":"2022-03-21T23:10:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nfwup fails to build on aarch64-darwin because mtools fails to build on aarch64-darwin which is a dependency. However mtools is only required for testing fwup and check is disabled on darwin.\r\n\r\n### Steps To Reproduce\r\nOn a mac with aarch64 run\r\nnix-shell -p fwup\r\n\r\n### Expected behavior\r\npackage builds\r\n\r\n\r\n### Notify maintainers\r\n@georgewhewell \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 11.6`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(mathew.prokos): `\"\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165167/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165164","id":1175890828,"node_id":"I_kwDOAEVQ_M5GFquM","number":165164,"title":"Unityhub doesn't start on Arch Linux.","user":{"login":"Keyboard-Crasher","id":75228241,"node_id":"MDQ6VXNlcjc1MjI4MjQx","avatar_url":"https://avatars.githubusercontent.com/u/75228241?v=4","gravatar_id":"","url":"https://api.github.com/users/Keyboard-Crasher","html_url":"https://github.com/Keyboard-Crasher","followers_url":"https://api.github.com/users/Keyboard-Crasher/followers","following_url":"https://api.github.com/users/Keyboard-Crasher/following{/other_user}","gists_url":"https://api.github.com/users/Keyboard-Crasher/gists{/gist_id}","starred_url":"https://api.github.com/users/Keyboard-Crasher/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Keyboard-Crasher/subscriptions","organizations_url":"https://api.github.com/users/Keyboard-Crasher/orgs","repos_url":"https://api.github.com/users/Keyboard-Crasher/repos","events_url":"https://api.github.com/users/Keyboard-Crasher/events{/privacy}","received_events_url":"https://api.github.com/users/Keyboard-Crasher/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T20:13:38Z","updated_at":"2022-03-21T20:13:38Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nUnityhub doesn't start.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```console\r\n$ nix-env -iA nixpkgs.unityhub\r\n...\r\n$ unityhub\r\nGtk-Message: 21:57:14.714: Failed to load module \"canberra-gtk-module\"\r\nGtk-Message: 21:57:14.714: Failed to load module \"canberra-gtk-module\"\r\nFontconfig warning: \"/usr/share/fontconfig/conf.avail/05-reset-dirs-sample.conf\", line 6: unknown element \"reset-dirs\"\r\nChecking for update\r\nFound version 2.4.6 (url: UnityHub.AppImage)\r\nDownloading update from UnityHub.AppImage\r\nupdater cache dir: /home/user/.cache/unityhub-updater\r\n```\r\n\r\n### Expected behavior\r\nUnityhub is expected to start.\r\n\r\n### Additional context\r\nThe messages printed to console after `$ unityhub` seem to be unrelated and the exit code is 133.\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11-arch1-1, Arch Linux, noversion`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(user): `\"nixgl, nixpkgs\"`\r\n - nixpkgs: `/home/user/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165164/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165148","id":1175804871,"node_id":"I_kwDOAEVQ_M5GFVvH","number":165148,"title":"LD_PRELOAD in electron wrapper breaks unwrapped commands called by obsidian.","user":{"login":"pbsds","id":140964,"node_id":"MDQ6VXNlcjE0MDk2NA==","avatar_url":"https://avatars.githubusercontent.com/u/140964?v=4","gravatar_id":"","url":"https://api.github.com/users/pbsds","html_url":"https://github.com/pbsds","followers_url":"https://api.github.com/users/pbsds/followers","following_url":"https://api.github.com/users/pbsds/following{/other_user}","gists_url":"https://api.github.com/users/pbsds/gists{/gist_id}","starred_url":"https://api.github.com/users/pbsds/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pbsds/subscriptions","organizations_url":"https://api.github.com/users/pbsds/orgs","repos_url":"https://api.github.com/users/pbsds/repos","events_url":"https://api.github.com/users/pbsds/events{/privacy}","received_events_url":"https://api.github.com/users/pbsds/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-03-21T18:51:30Z","updated_at":"2022-03-31T10:04:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nObsidian is unable to run (non-nixpkgs) git commands, due to `$LD_PRELOAD` being prefixed with `libXScrnSaver`. \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have non-nixpkgs `git`\r\n2. open [obsidian](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/applications/misc/obsidian/default.nix#L68) from nixpkgs\r\n3. Setup [Obsidian Git](https://github.com/denolehov/obsidian-git) in obsidian\r\n4. Run the `Obsidian Git: Backup Vault` command\r\n\r\n\r\n### Expected behavior\r\nGit syncing properly\r\n\r\n\r\n### Actual behavior\r\n`git: failed on initialization`\r\n\r\n\r\n### Additional context\r\n\r\n\r\n```console\r\n$ nix-shell -p obsidian\r\n\r\n[nix-shell:~]$ head `which obsidian`\r\n#! /nix/store/bm7jr70d9ghn5cczb3q0w90apsm05p54-bash-5.1-p8/bin/bash -e\r\nexec \"/nix/store/xcrfxl4cb8s0q0w3c5qanym06vdpahw1-electron-13.6.9/bin/electron\" /nix/store/g3hg2i1m81rf68xpansw9jqpg7yk7wkr-obsidian-0.12.19/share/obsidian/app.asar \"$@\"\r\n\r\n[nix-shell:~]$ head /nix/store/xcrfxl4cb8s0q0w3c5qanym06vdpahw1-electron-13.6.9/bin/electron\r\n#! /nix/store/bm7jr70d9ghn5cczb3q0w90apsm05p54-bash-5.1-p8/bin/bash -e\r\nexport LD_PRELOAD='/nix/store/2nldwldgaiwd0zwph8sj13xdiqysdxgb-libXScrnSaver-1.2.3/lib/libXss.so.1'${LD_PRELOAD:+':'}$LD_PRELOAD\r\nexport GIO_EXTRA_MODULES='/nix/store/wsc48b6izbpm0v70wv9dryrnb0776pq1-dconf-0.40.0-lib/lib/gio/modules'${GIO_EXTRA_MODULES:+':'}$GIO_EXTRA_MODULES\r\nexport GIO_EXTRA_MODULES='/nix/store/wsc48b6izbpm0v70wv9dryrnb0776pq1-dconf-0.40.0-lib/lib/gio/modules'${GIO_EXTRA_MODULES:+':'}$GIO_EXTRA_MODULES\r\nexport GDK_PIXBUF_MODULE_FILE='/nix/store/nlpa9gavw5zszfyp50krca2iba7ymhvn-librsvg-2.52.4/lib/gdk-pixbuf-2.0/2.10.0/loaders.cache'\r\nexport XDG_DATA_DIRS='/nix/store/z2phd72675fma3nz1l4jzpignf4zycvd-gtk+3-3.24.30/share/gsettings-schemas/gtk+3-3.24.30:/nix/store/vsf6wf9g6glsdw3mkbyd0q5m1gmvcfb4-gsettings-desktop-schemas-41.0/share/gsettings-schemas/gsettings-desktop-schemas-41.0'${XDG_DATA_DIRS:+':'}$XDG_DATA_DIRS\r\nexec -a \"$0\" \"/nix/store/xcrfxl4cb8s0q0w3c5qanym06vdpahw1-electron-13.6.9/lib/electron/.electron-wrapped\" \"$@\"\r\n\r\n[nix-shell:~]$ which git\r\n/usr/bin/git\r\n\r\n[nix-shell:~]$ echo $LD_PRELOAD\r\n\r\n\r\n[nix-shell:~]$ export LD_PRELOAD='/nix/store/2nldwldgaiwd0zwph8sj13xdiqysdxgb-libXScrnSaver-1.2.3/lib/libXss.so.1'${LD_PRELOAD:+':'}$LD_PRELOAD\r\n\r\n[nix-shell:~]$ git\r\ngit: symbol lookup error: /nix/store/65hafbsx91127farbmyyv4r5ifgjdg43-glibc-2.33-117/lib/libdl.so.2: undefined symbol: _dl_catch_error_ptr, version GLIBC_PRIVATE\r\n```\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@ConradMearns @zaninime @travisbhartwell @manveru @prusnak\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.25-1-MANJARO, Manjaro Linux, noversion`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(pbsds): `\"nixpkgs-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/pbsds/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165148/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165140","id":1175733147,"node_id":"I_kwDOAEVQ_M5GFEOb","number":165140,"title":"Packaging request: realsense-viewer","user":{"login":"pbsds","id":140964,"node_id":"MDQ6VXNlcjE0MDk2NA==","avatar_url":"https://avatars.githubusercontent.com/u/140964?v=4","gravatar_id":"","url":"https://api.github.com/users/pbsds","html_url":"https://github.com/pbsds","followers_url":"https://api.github.com/users/pbsds/followers","following_url":"https://api.github.com/users/pbsds/following{/other_user}","gists_url":"https://api.github.com/users/pbsds/gists{/gist_id}","starred_url":"https://api.github.com/users/pbsds/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pbsds/subscriptions","organizations_url":"https://api.github.com/users/pbsds/orgs","repos_url":"https://api.github.com/users/pbsds/repos","events_url":"https://api.github.com/users/pbsds/events{/privacy}","received_events_url":"https://api.github.com/users/pbsds/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-21T17:46:28Z","updated_at":"2022-03-21T19:04:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\n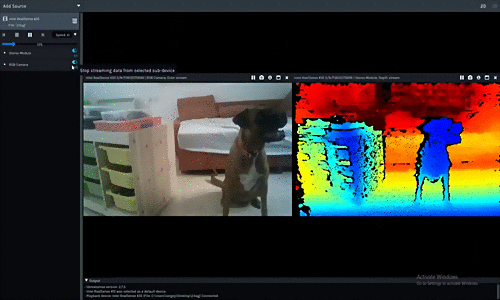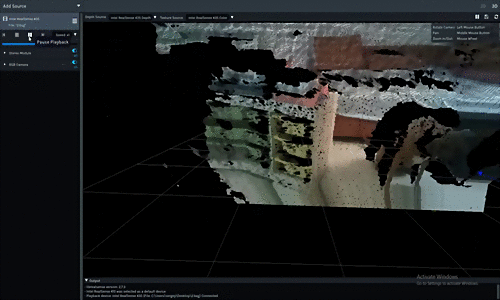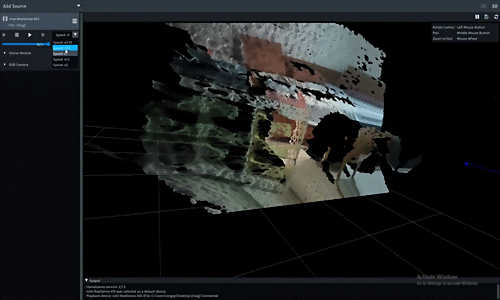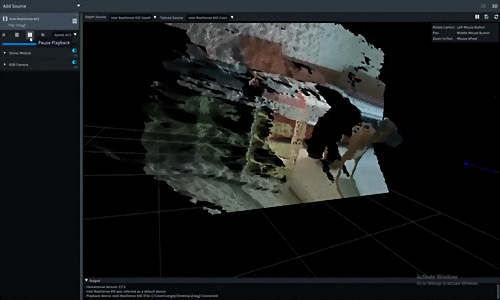\r\n\r\nRealsense-viewer is an official application for playing around with Intel® RealSense™ depth cameras (D400 series and the SR300).\r\nWe already have [librealsense](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/development/libraries/librealsense/default.nix#L72) in nixpkgs, but it does not include all of the official tools:\r\n\r\n```\r\n$ ls /nix/store/sgcm8np2ix9vjal8safbwc773b5imwid-librealsense-2.45.0/bin \r\nrs-color rs-distance rs-fw-update rs-pose-and-image rs-save-to-disk\r\nrs-convert rs-enumerate-devices rs-hello-realsense rs-pose-predict rs-terminal\r\nrs-depth rs-fw-logger rs-pose rs-record\r\n```\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/IntelRealSense/librealsense/tree/master/tools/realsense-viewer\r\n* source URL: https://github.com/IntelRealSense/librealsense/tree/master/tools/realsense-viewer \r\n* license: asl20\r\n* platforms: unix\r\n\r\n@brian-dawn :pray:","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165140/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165109","id":1175423638,"node_id":"I_kwDOAEVQ_M5GD4qW","number":165109,"title":"Test kubernetes-rbac-singlenode is broken (21.11)","user":{"login":"wamserma","id":60148,"node_id":"MDQ6VXNlcjYwMTQ4","avatar_url":"https://avatars.githubusercontent.com/u/60148?v=4","gravatar_id":"","url":"https://api.github.com/users/wamserma","html_url":"https://github.com/wamserma","followers_url":"https://api.github.com/users/wamserma/followers","following_url":"https://api.github.com/users/wamserma/following{/other_user}","gists_url":"https://api.github.com/users/wamserma/gists{/gist_id}","starred_url":"https://api.github.com/users/wamserma/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wamserma/subscriptions","organizations_url":"https://api.github.com/users/wamserma/orgs","repos_url":"https://api.github.com/users/wamserma/repos","events_url":"https://api.github.com/users/wamserma/events{/privacy}","received_events_url":"https://api.github.com/users/wamserma/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-21T13:54:42Z","updated_at":"2022-03-21T23:08:40Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nhttps://hydra.nixos.org/job/nixos/release-21.11/nixos.tests.kubernetes.rbac-single-node/all\r\n\r\nThe test started failing Jan 1st.\r\n\r\n\r\n### Notify maintainers\r\n@zowoq\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165109/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165104","id":1175328459,"node_id":"I_kwDOAEVQ_M5GDhbL","number":165104,"title":"Packaging request: Overwitch","user":{"login":"dag-h","id":16627772,"node_id":"MDQ6VXNlcjE2NjI3Nzcy","avatar_url":"https://avatars.githubusercontent.com/u/16627772?v=4","gravatar_id":"","url":"https://api.github.com/users/dag-h","html_url":"https://github.com/dag-h","followers_url":"https://api.github.com/users/dag-h/followers","following_url":"https://api.github.com/users/dag-h/following{/other_user}","gists_url":"https://api.github.com/users/dag-h/gists{/gist_id}","starred_url":"https://api.github.com/users/dag-h/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dag-h/subscriptions","organizations_url":"https://api.github.com/users/dag-h/orgs","repos_url":"https://api.github.com/users/dag-h/repos","events_url":"https://api.github.com/users/dag-h/events{/privacy}","received_events_url":"https://api.github.com/users/dag-h/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T12:41:08Z","updated_at":"2022-03-21T12:41:08Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nOverwitch is an Overbridge 2 device client for JACK (JACK Audio Connection Kit).\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/dagargo/overwitch\r\n* source URL: https://github.com/dagargo/overwitch\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165104/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165103","id":1175327323,"node_id":"I_kwDOAEVQ_M5GDhJb","number":165103,"title":"Packaging request: Elektroid","user":{"login":"dag-h","id":16627772,"node_id":"MDQ6VXNlcjE2NjI3Nzcy","avatar_url":"https://avatars.githubusercontent.com/u/16627772?v=4","gravatar_id":"","url":"https://api.github.com/users/dag-h","html_url":"https://github.com/dag-h","followers_url":"https://api.github.com/users/dag-h/followers","following_url":"https://api.github.com/users/dag-h/following{/other_user}","gists_url":"https://api.github.com/users/dag-h/gists{/gist_id}","starred_url":"https://api.github.com/users/dag-h/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dag-h/subscriptions","organizations_url":"https://api.github.com/users/dag-h/orgs","repos_url":"https://api.github.com/users/dag-h/repos","events_url":"https://api.github.com/users/dag-h/events{/privacy}","received_events_url":"https://api.github.com/users/dag-h/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T12:40:13Z","updated_at":"2022-03-21T12:40:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nElektroid is a GNU/Linux transfer application for Elektron devices.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/dagargo/elektroid\r\n* source URL: https://github.com/dagargo/elektroid\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165103/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165079","id":1175042535,"node_id":"I_kwDOAEVQ_M5GCbnn","number":165079,"title":"Qtile is missing all the ffi modules so one can't use the pulse widget","user":{"login":"leiserfg","id":2947276,"node_id":"MDQ6VXNlcjI5NDcyNzY=","avatar_url":"https://avatars.githubusercontent.com/u/2947276?v=4","gravatar_id":"","url":"https://api.github.com/users/leiserfg","html_url":"https://github.com/leiserfg","followers_url":"https://api.github.com/users/leiserfg/followers","following_url":"https://api.github.com/users/leiserfg/following{/other_user}","gists_url":"https://api.github.com/users/leiserfg/gists{/gist_id}","starred_url":"https://api.github.com/users/leiserfg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/leiserfg/subscriptions","organizations_url":"https://api.github.com/users/leiserfg/orgs","repos_url":"https://api.github.com/users/leiserfg/repos","events_url":"https://api.github.com/users/leiserfg/events{/privacy}","received_events_url":"https://api.github.com/users/leiserfg/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-21T08:18:48Z","updated_at":"2022-03-21T08:18:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\nQtile is missing all the ffi modules so one can't use the pulse widget\r\n\r\n\r\n### Steps to reproduce\r\nJust install qtile and add a \r\n```py\r\nscreens = [ \r\n Screen( \r\n top=bar.Bar([ \r\n widget.PulseVolume( )\r\n ])\r\n] \r\n```\r\nTo the config\r\n## Technical details\r\nThere is a script that has to be run as part of the packaging process\r\n<https://github.com/qtile/qtile/blob/master/scripts/ffibuild> \r\nit takes care of creating the ffi modules, not sure if that will be enough or patching \r\nhttps://github.com/qtile/qtile/blob/master/libqtile/widget/pulseaudio_ffi.py to change the paths will also be required.\r\n \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165079/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165032","id":1174716168,"node_id":"I_kwDOAEVQ_M5GBL8I","number":165032,"title":"Boot fails when importing a ZFS pool of LVM volumes with `Failed to find executable lvm: No such file or directory`","user":{"login":"jaen","id":227236,"node_id":"MDQ6VXNlcjIyNzIzNg==","avatar_url":"https://avatars.githubusercontent.com/u/227236?v=4","gravatar_id":"","url":"https://api.github.com/users/jaen","html_url":"https://github.com/jaen","followers_url":"https://api.github.com/users/jaen/followers","following_url":"https://api.github.com/users/jaen/following{/other_user}","gists_url":"https://api.github.com/users/jaen/gists{/gist_id}","starred_url":"https://api.github.com/users/jaen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jaen/subscriptions","organizations_url":"https://api.github.com/users/jaen/orgs","repos_url":"https://api.github.com/users/jaen/repos","events_url":"https://api.github.com/users/jaen/events{/privacy}","received_events_url":"https://api.github.com/users/jaen/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-20T22:53:50Z","updated_at":"2022-04-28T07:20:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nFrom some time (might coincide with lvm2 upgrade to 2.03.15, but haven't checked yet) one of my servers has problems booting – it gets stuck at ZFS import. After some debugging I have pinpointed the issue to be caused by LVM – if I go into the rescue shell and do `vgchange -ay && exit` the system boots successfully. When looking at verbose boot logs I can see the following message:\r\n```\r\nMar 20 23:05:53 ronin lvm[4242]: PV /dev/dm-12 online, VG ThunderbayCacheVolumeGroup is complete.\r\n\r\n... quite a bit of udev stuff\r\n\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: dm-12: Running command \"/run/current-system/systemd/bin/systemd-run -r --no-block --property DefaultDependencies=no --unit lvm-activate-ThunderbayCacheVolumeGroup lvm vgchange -aay --nohints ThunderbayCacheVolumeGroup\"\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: dm-12: Starting '/run/current-system/systemd/bin/systemd-run -r --no-block --property DefaultDependencies=no --unit lvm-activate-ThunderbayCacheVolumeGroup lvm vgchange -aay --nohints ThunderbayCacheVolumeGroup'\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: Successfully forked off '(spawn)' as PID 4245.\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: dm-12: '/run/current-system/systemd/bin/systemd-run -r --no-block --property DefaultDependencies=no --unit lvm-activate-ThunderbayCacheVolumeGroup lvm vgchange -aay --nohints ThunderbayCacheVolumeGroup'(err) 'Failed to find executable lvm: No such file or directory'\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: dm-12: Process '/run/current-system/systemd/bin/systemd-run -r --no-block --property DefaultDependencies=no --unit lvm-activate-ThunderbayCacheVolumeGroup lvm vgchange -aay --nohints ThunderbayCacheVolumeGroup' failed with exit code 1.\r\nMar 20 23:05:53 ronin systemd-udevd[4164]: dm-12: Command \"/run/current-system/systemd/bin/systemd-run -r --no-block --property DefaultDependencies=no --unit lvm-activate-ThunderbayCacheVolumeGroup lvm vgchange -aay --nohints ThunderbayCacheVolumeGroup\" returned 1 (error), ignoring.\r\n```\r\n\r\nAs you can see, udev fails to activate the volume group because the `lvm` seems to be missing – I can however call `vgchange` without problems from the rescue shell, so it might not be as simple as the binary not being available.\r\n\r\nIf it helps, the machine disk layout is as follow:\r\n * `ronin-storage` pool on `/dev/nvme0n1`, the device is decrypted in initrd and has `preLVM` set,\r\n * `tank` pool on 4 HDDs in a Thunderbolt enclosure with `/dev/nvme1n1` for slog/L2ARC; the devices are decrypted via crypttab.\r\n \r\nWhere LVM comes into play here is that the slog/L2ARC SSD is partitioned via LVM into three devices 2 for mirrored slogs and 1 for L2ARC (let's disregard whether it's a smart thing to do, I have done it mostly to learn how to set it up and had only one SSD to spare). This setup has worked without a hitch for a while, but has started breaking from some time.\r\n\r\nLet me know what parts of my configuration would you like me to provide or any other information that would help debugging this.\r\n\r\n### Steps To Reproduce\r\nGood question… I imagine it would be something like this:\r\n1. have ZFS pool inside LUKS devices decrypted via crypttab,\r\n2. with at least one of the devices partitioned via LVM\r\n3. try to import the pool at boot\r\n4. fail due to the LVM volumes failing to activate\r\n\r\nBut can't really test what is a minimal reproduction of this issue without having to restart server a lot and staying sane.\r\n\r\n### Expected behavior\r\nThe system should keep booting without a hitch, properly activating LVM volumes before ZFS pool import\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n╭─jaen@ronin ~\r\n╰─$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.00 MiB download, 0.00 MiB unpacked):\r\n /nix/store/rmhwi0jcya8f87gzk2jjdwv4hifmmbb4-nix-info\r\ncopying path '/nix/store/rmhwi0jcya8f87gzk2jjdwv4hifmmbb4-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.28, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220311_d532269`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165032/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010/events","html_url":"https://github.com/NixOS/nixpkgs/issues/165010","id":1174644408,"node_id":"I_kwDOAEVQ_M5GA6a4","number":165010,"title":"sfxr and sfxr-qt segfault when the gui is run","user":{"login":"fgaz","id":8182846,"node_id":"MDQ6VXNlcjgxODI4NDY=","avatar_url":"https://avatars.githubusercontent.com/u/8182846?v=4","gravatar_id":"","url":"https://api.github.com/users/fgaz","html_url":"https://github.com/fgaz","followers_url":"https://api.github.com/users/fgaz/followers","following_url":"https://api.github.com/users/fgaz/following{/other_user}","gists_url":"https://api.github.com/users/fgaz/gists{/gist_id}","starred_url":"https://api.github.com/users/fgaz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fgaz/subscriptions","organizations_url":"https://api.github.com/users/fgaz/orgs","repos_url":"https://api.github.com/users/fgaz/repos","events_url":"https://api.github.com/users/fgaz/events{/privacy}","received_events_url":"https://api.github.com/users/fgaz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"fgaz","id":8182846,"node_id":"MDQ6VXNlcjgxODI4NDY=","avatar_url":"https://avatars.githubusercontent.com/u/8182846?v=4","gravatar_id":"","url":"https://api.github.com/users/fgaz","html_url":"https://github.com/fgaz","followers_url":"https://api.github.com/users/fgaz/followers","following_url":"https://api.github.com/users/fgaz/following{/other_user}","gists_url":"https://api.github.com/users/fgaz/gists{/gist_id}","starred_url":"https://api.github.com/users/fgaz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fgaz/subscriptions","organizations_url":"https://api.github.com/users/fgaz/orgs","repos_url":"https://api.github.com/users/fgaz/repos","events_url":"https://api.github.com/users/fgaz/events{/privacy}","received_events_url":"https://api.github.com/users/fgaz/received_events","type":"User","site_admin":false},"assignees":[{"login":"fgaz","id":8182846,"node_id":"MDQ6VXNlcjgxODI4NDY=","avatar_url":"https://avatars.githubusercontent.com/u/8182846?v=4","gravatar_id":"","url":"https://api.github.com/users/fgaz","html_url":"https://github.com/fgaz","followers_url":"https://api.github.com/users/fgaz/followers","following_url":"https://api.github.com/users/fgaz/following{/other_user}","gists_url":"https://api.github.com/users/fgaz/gists{/gist_id}","starred_url":"https://api.github.com/users/fgaz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fgaz/subscriptions","organizations_url":"https://api.github.com/users/fgaz/orgs","repos_url":"https://api.github.com/users/fgaz/repos","events_url":"https://api.github.com/users/fgaz/events{/privacy}","received_events_url":"https://api.github.com/users/fgaz/received_events","type":"User","site_admin":false}],"milestone":null,"comments":4,"created_at":"2022-03-20T18:40:45Z","updated_at":"2022-03-28T07:27:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nsfxr and sfxr-qt segfault when the gui is run.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.105, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11.336515.0f85665118d\"`\r\n - channels(fgaz): `\"nixpkgs-22.05pre357729.22dc22f8ced\"`\r\n - nixpkgs: `/home/fgaz/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/165010/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164974","id":1174555897,"node_id":"I_kwDOAEVQ_M5GAkz5","number":164974,"title":"Package request: prophet","user":{"login":"rslopes","id":24928343,"node_id":"MDQ6VXNlcjI0OTI4MzQz","avatar_url":"https://avatars.githubusercontent.com/u/24928343?v=4","gravatar_id":"","url":"https://api.github.com/users/rslopes","html_url":"https://github.com/rslopes","followers_url":"https://api.github.com/users/rslopes/followers","following_url":"https://api.github.com/users/rslopes/following{/other_user}","gists_url":"https://api.github.com/users/rslopes/gists{/gist_id}","starred_url":"https://api.github.com/users/rslopes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rslopes/subscriptions","organizations_url":"https://api.github.com/users/rslopes/orgs","repos_url":"https://api.github.com/users/rslopes/repos","events_url":"https://api.github.com/users/rslopes/events{/privacy}","received_events_url":"https://api.github.com/users/rslopes/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-20T13:54:27Z","updated_at":"2022-03-20T13:54:27Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nTool for producing high quality forecasts for time series data that has multiple seasonality with linear or non-linear growth.\r\n\r\n**Metadata**\r\n* PyPI: https://pypi.org/project/prophet/\r\n* homepage URL: https://facebook.github.io/prophet/\r\n* source URL: https://github.com/facebook/prophet\r\n* license: mit\r\n* platforms: x86_64-linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164974/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164958","id":1174508021,"node_id":"I_kwDOAEVQ_M5GAZH1","number":164958,"title":"psycopg2: cross compilation fails","user":{"login":"tusj","id":1783654,"node_id":"MDQ6VXNlcjE3ODM2NTQ=","avatar_url":"https://avatars.githubusercontent.com/u/1783654?v=4","gravatar_id":"","url":"https://api.github.com/users/tusj","html_url":"https://github.com/tusj","followers_url":"https://api.github.com/users/tusj/followers","following_url":"https://api.github.com/users/tusj/following{/other_user}","gists_url":"https://api.github.com/users/tusj/gists{/gist_id}","starred_url":"https://api.github.com/users/tusj/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tusj/subscriptions","organizations_url":"https://api.github.com/users/tusj/orgs","repos_url":"https://api.github.com/users/tusj/repos","events_url":"https://api.github.com/users/tusj/events{/privacy}","received_events_url":"https://api.github.com/users/tusj/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-20T11:00:50Z","updated_at":"2022-03-20T19:15:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Cross compiling `psycopg2` currently fails. [Psycopg2](https://www.psycopg.org/docs) is a postgresql adapter for python, and therefore requires `postgresql`.\r\n\r\nThe runtime libraries for `postgresql` needs to be available for the host platform, and the binary `pg_config` from `postgresql` needs to be available for the build platform.\r\nCurrently, `postgresql` is only specified in `nativeBuildInputs`. That makes the `pg_config` binary available. However, it also makes the runtime libraries available built for build platform, not host platform. From what I understand, to make the runtime libraries for `postgresql` available for the target platform, `postgresql` should be added to `buildInputs`. However, the linking step fails because it still finds the native / build platform libraries.\r\n\r\nI'd like to fix this issue myself, but I need some pointers on the best way to proceed. I can see two ways to fix this:\r\n\r\n1. The runtime libraries for native should not be available to the linker when building for the host platform.\r\n2. In nativeBuildInputs, specify a `postgresql` package which does not include the runtime libraries.\r\n\r\nError when building: `pkgsCross.armv7l-hf-multiplatform.python39Packages.psycopg2`\r\n`/nix/store/521z5w03bmrs4d2qxpnbcqk80lvn7p4v-postgresql-13.6-lib/lib/libpq.so: file not recognized: file format not recognized`\r\nExamining the file format reveals that it is build for x86-64, the build platform.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164958/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164900","id":1174375806,"node_id":"I_kwDOAEVQ_M5F_41-","number":164900,"title":"programs.ccache.packageNames forces derivation builds even when packages are unmodified","user":{"login":"PAI5REECHO","id":96688573,"node_id":"U_kgDOBcNZvQ","avatar_url":"https://avatars.githubusercontent.com/u/96688573?v=4","gravatar_id":"","url":"https://api.github.com/users/PAI5REECHO","html_url":"https://github.com/PAI5REECHO","followers_url":"https://api.github.com/users/PAI5REECHO/followers","following_url":"https://api.github.com/users/PAI5REECHO/following{/other_user}","gists_url":"https://api.github.com/users/PAI5REECHO/gists{/gist_id}","starred_url":"https://api.github.com/users/PAI5REECHO/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PAI5REECHO/subscriptions","organizations_url":"https://api.github.com/users/PAI5REECHO/orgs","repos_url":"https://api.github.com/users/PAI5REECHO/repos","events_url":"https://api.github.com/users/PAI5REECHO/events{/privacy}","received_events_url":"https://api.github.com/users/PAI5REECHO/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-19T21:29:50Z","updated_at":"2022-03-21T20:39:01Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nAny package name listed under [`programs.ccache.packageNames`](https://search.nixos.org/options?channel=unstable&from=0&size=50&sort=relevance&type=packages&query=programs.ccache.packageNames) is built from source even if the package is unmodified or unpatched and can be pulled from a binary cache\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Put `\"qemu\"` in `programs.ccache.packageNames`\r\n2. Rebuild system\r\n3. `qemu` is built from source even though it can just be pulled from the binary cache\r\n\r\n### Expected behavior\r\nPackages that aren't modified and don't need to be built from source shouldn't be built from source even if they're listed under `programs.ccache.packageNames`.\r\n\r\n### Additional context\r\nI'm patching `qemu` but only for `virtualisation.libvirtd.qemu.package` so I'd like **that** derivation to go through `ccache`. But as far as the `qemu` needed for the default system I would like it to be pulled directly from the binary cache and **not** built from source unnecessarily.\r\n\r\n### Notify maintainers\r\n@kira-bruneau\r\n@r-burns\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220318_8ad485e`\r\n - channels(root): `\"nixos-21.05.3948.d14d83a3691, home-manager-21.05, nixos-unstable-21.11pre320334.82155ff501c\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164900/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164856","id":1174256383,"node_id":"I_kwDOAEVQ_M5F_br_","number":164856,"title":"Lutris: can't login to GOG/Humble Bundle (blank/freezed window)","user":{"login":"wyndon","id":72203260,"node_id":"MDQ6VXNlcjcyMjAzMjYw","avatar_url":"https://avatars.githubusercontent.com/u/72203260?v=4","gravatar_id":"","url":"https://api.github.com/users/wyndon","html_url":"https://github.com/wyndon","followers_url":"https://api.github.com/users/wyndon/followers","following_url":"https://api.github.com/users/wyndon/following{/other_user}","gists_url":"https://api.github.com/users/wyndon/gists{/gist_id}","starred_url":"https://api.github.com/users/wyndon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wyndon/subscriptions","organizations_url":"https://api.github.com/users/wyndon/orgs","repos_url":"https://api.github.com/users/wyndon/repos","events_url":"https://api.github.com/users/wyndon/events{/privacy}","received_events_url":"https://api.github.com/users/wyndon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-19T12:37:27Z","updated_at":"2022-03-28T21:02:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen opening the GOG login page, the window just stays blank.\r\nWith the Humble Bundle page, the window begins to load but then just freezes.\r\n\r\nIt is worth noting that even though the window is blank/freezed, you can still interact with the page itself (try to mouseover inputs and you can see that your cursor's shape is changing)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open Lutris \r\n2. Click on the \"Connect\" button next to GOG\r\n3. It just stays blank. Wait for a bit to confirm and close it\r\n4. Click on the \"Connect\" button next to Humble Bundle\r\n5. Begins to load but then it freezes.\r\n\r\n### Expected behavior\r\nLogin pages should be viewable.\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Additional context\r\nFWIW, everything working perfectly on Arch.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Chiiruno \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.27-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164856/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164775","id":1174042146,"node_id":"I_kwDOAEVQ_M5F-nYi","number":164775,"title":"magic-wormhole-transit-relay: Cannot get environment","user":{"login":"piegamesde","id":14054505,"node_id":"MDQ6VXNlcjE0MDU0NTA1","avatar_url":"https://avatars.githubusercontent.com/u/14054505?v=4","gravatar_id":"","url":"https://api.github.com/users/piegamesde","html_url":"https://github.com/piegamesde","followers_url":"https://api.github.com/users/piegamesde/followers","following_url":"https://api.github.com/users/piegamesde/following{/other_user}","gists_url":"https://api.github.com/users/piegamesde/gists{/gist_id}","starred_url":"https://api.github.com/users/piegamesde/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piegamesde/subscriptions","organizations_url":"https://api.github.com/users/piegamesde/orgs","repos_url":"https://api.github.com/users/piegamesde/repos","events_url":"https://api.github.com/users/piegamesde/events{/privacy}","received_events_url":"https://api.github.com/users/piegamesde/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-18T21:17:48Z","updated_at":"2022-03-20T19:11:56Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`nix-build -E \"with (import <nixpkgs> {}); python3.withPackages (pypkgs: with pypkgs; [magic-wormhole-transit-relay])\"`\r\n\r\n```\r\nthese derivations will be built:\r\n /nix/store/igya112v7n181600l9va1kin9rp1i9mh-python3-3.9.6-env.drv\r\nbuilding '/nix/store/igya112v7n181600l9va1kin9rp1i9mh-python3-3.9.6-env.drv'...\r\nerror: collision between `/nix/store/bm9ravdndw17dzdy963a164sgnhwzqy4-python3.9-Twisted-21.7.0/lib/python3.9/site-packages/twisted/plugins/dropin.cache' and `/nix/store/s68magn0jnr2w3dhzc48sv89inp9k9wg-python3.9-magic-wormhole-transit-relay-0.2.1/lib/python3.9/site-packages/twisted/plugins/dropin.cache'\r\nbuilder for '/nix/store/igya112v7n181600l9va1kin9rp1i9mh-python3-3.9.6-env.drv' failed with exit code 25\r\nerror: build of '/nix/store/igya112v7n181600l9va1kin9rp1i9mh-python3-3.9.6-env.drv' failed\r\n```\r\n\r\n### Expected behavior\r\nIt builds\r\n\r\n### Notify maintainers\r\n\r\n@dotlambda as the packager\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.28-1-lts, Arch Linux, noversion`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels: `\"nixpkgs-21.11.335820.521e4d7d13b, nixpkgs-unstable-22.05pre352357.98bb5b77c8c\"`\r\n - nixpkgs: `~/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164775/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164754","id":1173902457,"node_id":"I_kwDOAEVQ_M5F-FR5","number":164754,"title":"libredirect tests fail for non-sandboxed, non-NixOS builds due to system()","user":{"login":"a-m-joseph","id":54836058,"node_id":"MDQ6VXNlcjU0ODM2MDU4","avatar_url":"https://avatars.githubusercontent.com/u/54836058?v=4","gravatar_id":"","url":"https://api.github.com/users/a-m-joseph","html_url":"https://github.com/a-m-joseph","followers_url":"https://api.github.com/users/a-m-joseph/followers","following_url":"https://api.github.com/users/a-m-joseph/following{/other_user}","gists_url":"https://api.github.com/users/a-m-joseph/gists{/gist_id}","starred_url":"https://api.github.com/users/a-m-joseph/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a-m-joseph/subscriptions","organizations_url":"https://api.github.com/users/a-m-joseph/orgs","repos_url":"https://api.github.com/users/a-m-joseph/repos","events_url":"https://api.github.com/users/a-m-joseph/events{/privacy}","received_events_url":"https://api.github.com/users/a-m-joseph/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-18T18:46:22Z","updated_at":"2022-03-23T19:05:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe tests for `nix-env -iA libredirect` fail in single-user (i.e. no sandbox) nixpkgs builds on systems where `/bin/sh` comes from the host system rather than `/nix/store`. This happens because the tests use the impure `system()` call.\r\n\r\n```\r\nrunning install tests\r\nsh: symbol lookup error: /nix/store/v9j3c0rfx7hll8gan73vimlk4klh4hmi-glibc-2.33-108/lib/libdl.so.2: undefined symbol: _dl_catch_error_ptr, version GLIBC_PRIVATE\r\ntest: test.c:41: test_system: Assertion `system(TESTPATH) == 0' failed.\r\n/nix/store/cmwbb13lchz63rk5v79wx8rccjxxx55n-stdenv-linux/setup: line 1357: 23424 Aborted NIX_REDIRECTS=\"/foo/bar/test=/nix/store/0a73l706bk0gynrr5c8gqhc9n42nc30z-coreutils-9.0/bin/true:/bar/baz=$(mktemp -d)\" ./test\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Find a non-NixOS host system, install nixpkgs\r\n2. `nix-env -iA libredirect`\r\n3. Profit\r\n\r\n### Expected behavior\r\n\r\nThe `system()` tests should be skipped if an unsandboxed build environment is detected.\r\n\r\nI can't figure out how to determine, from within a derivation being built, if the build environment is sandboxed or not. If there is a reliable way to do this please let me know and I'll write the PR to close this bug.\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164754/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164694","id":1173414901,"node_id":"I_kwDOAEVQ_M5F8OP1","number":164694,"title":"Update onlyoffice to 7.0.1","user":{"login":"QuantMint","id":24614168,"node_id":"MDQ6VXNlcjI0NjE0MTY4","avatar_url":"https://avatars.githubusercontent.com/u/24614168?v=4","gravatar_id":"","url":"https://api.github.com/users/QuantMint","html_url":"https://github.com/QuantMint","followers_url":"https://api.github.com/users/QuantMint/followers","following_url":"https://api.github.com/users/QuantMint/following{/other_user}","gists_url":"https://api.github.com/users/QuantMint/gists{/gist_id}","starred_url":"https://api.github.com/users/QuantMint/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/QuantMint/subscriptions","organizations_url":"https://api.github.com/users/QuantMint/orgs","repos_url":"https://api.github.com/users/QuantMint/repos","events_url":"https://api.github.com/users/QuantMint/events{/privacy}","received_events_url":"https://api.github.com/users/QuantMint/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-18T10:10:24Z","updated_at":"2022-03-18T10:10:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: onlyoffice-bin \r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 6.3.1\r\ndesired version: 7.0.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @nh2 @GTrunSec \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164694/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164686","id":1173333237,"node_id":"I_kwDOAEVQ_M5F76T1","number":164686,"title":"haskellPackages.gi-adwaita build stuck","user":{"login":"OPNA2608","id":23431373,"node_id":"MDQ6VXNlcjIzNDMxMzcz","avatar_url":"https://avatars.githubusercontent.com/u/23431373?v=4","gravatar_id":"","url":"https://api.github.com/users/OPNA2608","html_url":"https://github.com/OPNA2608","followers_url":"https://api.github.com/users/OPNA2608/followers","following_url":"https://api.github.com/users/OPNA2608/following{/other_user}","gists_url":"https://api.github.com/users/OPNA2608/gists{/gist_id}","starred_url":"https://api.github.com/users/OPNA2608/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/OPNA2608/subscriptions","organizations_url":"https://api.github.com/users/OPNA2608/orgs","repos_url":"https://api.github.com/users/OPNA2608/repos","events_url":"https://api.github.com/users/OPNA2608/events{/privacy}","received_events_url":"https://api.github.com/users/OPNA2608/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-18T08:35:30Z","updated_at":"2022-04-12T00:11:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```console\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.246: cannot register existing type 'GtkWidget'\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.246: cannot add class private field to invalid type '<invalid>'\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.246: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\n\r\n(process:223): GLib-GObject-CRITICAL **: 08:11:14.246: g_type_add_interface_static: assertion 'G_TYPE_IS_INSTANTIATABLE (instance_type)' failed\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.246: cannot register existing type 'GtkBuildable'\r\n\r\n(process:223): GLib-GObject-CRITICAL **: 08:11:14.246: g_type_interface_add_prerequisite: assertion 'G_TYPE_IS_INTERFACE (interface_type)' failed\r\n\r\n(process:223): GLib-CRITICAL **: 08:11:14.247: g_once_init_leave: assertion 'result != 0' failed\r\n\r\n(process:223): GLib-GObject-CRITICAL **: 08:11:14.247: g_type_add_interface_static: assertion 'G_TYPE_IS_INSTANTIATABLE (instance_type)' failed\r\n\r\n(process:223): GLib-GObject-CRITICAL **: 08:11:14.247: g_type_add_interface_static: assertion 'G_TYPE_IS_INSTANTIATABLE (instance_type)' failed\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.247: cannot register existing type 'GtkWidget'\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.247: cannot add class private field to invalid type '<invalid>'\r\n\r\n(process:223): GLib-GObject-WARNING **: 08:11:14.247: cannot add private field to invalid (non-instantiatable) type '<invalid>'\r\n\r\n(process:223): GLib-GObject-CRITICAL **: 08:11:14.247: g_type_add_interface_static: assertion 'G_TYPE_IS_INSTANTIATABLE (instance_type)' failed\r\n```\r\n\r\nThen it's stuck. [Always times out on Hydra](https://hydra.nixos.org/build/168124724/nixlog/1).\r\n\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-build . -A haskellPackages.gi-adwaita`\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nBuild should pass.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\nn/a\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@NixOS/haskell ?\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n↪ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.2-xanmod1-tt, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(bt1cn): `\"unstable-22.05pre353770.23d785aa6f8\"`\r\n - channels(root): `\"nixos-21.11.336020.2128d0aa28e\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164686/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164685","id":1173289565,"node_id":"I_kwDOAEVQ_M5F7vpd","number":164685,"title":"KDE chromium based systems cannot attach files after sleep - report empty files everywhere","user":{"login":"schlichtanders","id":4255480,"node_id":"MDQ6VXNlcjQyNTU0ODA=","avatar_url":"https://avatars.githubusercontent.com/u/4255480?v=4","gravatar_id":"","url":"https://api.github.com/users/schlichtanders","html_url":"https://github.com/schlichtanders","followers_url":"https://api.github.com/users/schlichtanders/followers","following_url":"https://api.github.com/users/schlichtanders/following{/other_user}","gists_url":"https://api.github.com/users/schlichtanders/gists{/gist_id}","starred_url":"https://api.github.com/users/schlichtanders/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schlichtanders/subscriptions","organizations_url":"https://api.github.com/users/schlichtanders/orgs","repos_url":"https://api.github.com/users/schlichtanders/repos","events_url":"https://api.github.com/users/schlichtanders/events{/privacy}","received_events_url":"https://api.github.com/users/schlichtanders/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-18T07:53:16Z","updated_at":"2022-03-18T09:44:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nUsing KDE Plasma. When using chromium, chrome, brave or signal I experience the following behaviour:\r\nAfter sleep, I cannot anylonger attach files, however get everywhere the information that the files would be empty (which they are not).\r\n\r\nOn Firefox everything still works.\r\n\r\nThe key distinction seems to be that firefox uses another file-picker (looks more bare-bones) while chromium based systems use the file-picker which looks more like dolphin.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install brave on kde plasma\r\n1. Have a fresh restart of your system\r\n1. open brave\r\n1. go to somewhere where you can upload a file (e.g. on wetransfer.com)\r\n1. check that you can attach files\r\n1. press sleep\r\n1. awake the system\r\n1. try again to upload the same file - it is zero size now\r\n\r\n### Expected behavior\r\nI would so lovely if file attachment just works\r\n\r\n### Screenshots\r\noutlook error\r\n\r\n\r\n\r\n### Notify maintainers\r\n@ttuegel it seems it has something todo with KDE file pickers\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.16.10, NixOS, 21.11 (Porcupine)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.3.16`\r\n- channels(root): `\"nixos-21.11.336538.64fc73bd74f, nixos-unstable-22.05pre342264.5b091d4fbe3\"`\r\n- channels(MYUSERNAME_PLEASE_DONT_RECOMMEND_RUNNING_THINGS_WHICH_REVEAL_PRIVATE_INFORMATION): `\"nixos-21.05.1226.f77036342e2\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164685/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164648","id":1172998828,"node_id":"I_kwDOAEVQ_M5F6oqs","number":164648,"title":"Crystal fails to compile on macos","user":{"login":"charlesrocket","id":26132682,"node_id":"MDQ6VXNlcjI2MTMyNjgy","avatar_url":"https://avatars.githubusercontent.com/u/26132682?v=4","gravatar_id":"","url":"https://api.github.com/users/charlesrocket","html_url":"https://github.com/charlesrocket","followers_url":"https://api.github.com/users/charlesrocket/followers","following_url":"https://api.github.com/users/charlesrocket/following{/other_user}","gists_url":"https://api.github.com/users/charlesrocket/gists{/gist_id}","starred_url":"https://api.github.com/users/charlesrocket/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/charlesrocket/subscriptions","organizations_url":"https://api.github.com/users/charlesrocket/orgs","repos_url":"https://api.github.com/users/charlesrocket/repos","events_url":"https://api.github.com/users/charlesrocket/events{/privacy}","received_events_url":"https://api.github.com/users/charlesrocket/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"peterhoeg","id":722550,"node_id":"MDQ6VXNlcjcyMjU1MA==","avatar_url":"https://avatars.githubusercontent.com/u/722550?v=4","gravatar_id":"","url":"https://api.github.com/users/peterhoeg","html_url":"https://github.com/peterhoeg","followers_url":"https://api.github.com/users/peterhoeg/followers","following_url":"https://api.github.com/users/peterhoeg/following{/other_user}","gists_url":"https://api.github.com/users/peterhoeg/gists{/gist_id}","starred_url":"https://api.github.com/users/peterhoeg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterhoeg/subscriptions","organizations_url":"https://api.github.com/users/peterhoeg/orgs","repos_url":"https://api.github.com/users/peterhoeg/repos","events_url":"https://api.github.com/users/peterhoeg/events{/privacy}","received_events_url":"https://api.github.com/users/peterhoeg/received_events","type":"User","site_admin":false},"assignees":[{"login":"peterhoeg","id":722550,"node_id":"MDQ6VXNlcjcyMjU1MA==","avatar_url":"https://avatars.githubusercontent.com/u/722550?v=4","gravatar_id":"","url":"https://api.github.com/users/peterhoeg","html_url":"https://github.com/peterhoeg","followers_url":"https://api.github.com/users/peterhoeg/followers","following_url":"https://api.github.com/users/peterhoeg/following{/other_user}","gists_url":"https://api.github.com/users/peterhoeg/gists{/gist_id}","starred_url":"https://api.github.com/users/peterhoeg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peterhoeg/subscriptions","organizations_url":"https://api.github.com/users/peterhoeg/orgs","repos_url":"https://api.github.com/users/peterhoeg/repos","events_url":"https://api.github.com/users/peterhoeg/events{/privacy}","received_events_url":"https://api.github.com/users/peterhoeg/received_events","type":"User","site_admin":false}],"milestone":null,"comments":5,"created_at":"2022-03-17T22:45:08Z","updated_at":"2022-04-16T21:54:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n`nix-shell -p crystal2nix --run crystal2nix` on macos 21E230\r\n\r\n### Expected behavior\r\nAs described in docs\r\n\r\n### Additional context\r\n```\r\nerror: builder for '/nix/store/krfiihb7c99wk0f5ykq1xzh825yfxpym-crystal-1.0.0.drv' failed with exit code 2;\r\n last 10 log lines:\r\n > .......ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ....ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ....ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ..ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ..................ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ....ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ..ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ....ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > .........ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n > ....make: *** [Makefile:93: compiler_spec] Illegal instruction: 4\r\n For full logs, run 'nix log /nix/store/krfiihb7c99wk0f5ykq1xzh825yfxpym-crystal-1.0.0.drv'.\r\nerror: 1 dependencies of derivation '/nix/store/9z8aar3sab6ghrb7gjy02zlrmvfnrcsq-crystal-1.1.1.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/psf0s9m5gvgczlgnc75c8sh24avxdm75-crystal-1.2.2.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/f0m0llnr3am1ip33x2dqdc9a9wyg7wr3-shards-0.16.0.drv' failed to build\r\n```\r\n\r\n```\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n...ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n..ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n............ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n..ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n.ld: warning: directory not found for option '-L/nix/store/naqxf0zirwx3jcb9j3lkyzanx4my0h90-crystal-1.0.0-lib/crystal'\r\n```\r\n\r\n### Metadata\r\n```\r\nthese 2 paths will be fetched (0.01 MiB download, 0.03 MiB unpacked):\r\n /nix/store/3iqq82lf6alaiyb8k2xqyxh4dvj3dc1l-DarwinTools-1\r\n /nix/store/51jc5ig0hz78vfq7p51f7c61fp6bqavl-nix-info\r\ncopying path '/nix/store/3iqq82lf6alaiyb8k2xqyxh4dvj3dc1l-DarwinTools-1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/51jc5ig0hz78vfq7p51f7c61fp6bqavl-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n ```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164648/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164640","id":1172941321,"node_id":"I_kwDOAEVQ_M5F6aoJ","number":164640,"title":"Go-Ethereum CVE-2021-42219","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-17T21:31:27Z","updated_at":"2022-03-17T21:31:27Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"> Go-Ethereum v1.10.9 was discovered to contain an issue which allows attackers to cause a denial of service (DoS) via sending an excessive amount of messages to a node. This is caused by missing memory in the component /ethash/algorithm.go.\r\n\r\nhttps://nvd.nist.gov/vuln/detail/CVE-2021-42219\r\n\r\nNeeds to be fixed on master and release-21.11.\r\n\r\n@adisbladis @lionello @RaghavSood ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164640/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164630","id":1172807797,"node_id":"I_kwDOAEVQ_M5F56B1","number":164630,"title":"Cabal/Haskell: Importing generated path module leads to large closure","user":{"login":"m4dc4p","id":18689,"node_id":"MDQ6VXNlcjE4Njg5","avatar_url":"https://avatars.githubusercontent.com/u/18689?v=4","gravatar_id":"","url":"https://api.github.com/users/m4dc4p","html_url":"https://github.com/m4dc4p","followers_url":"https://api.github.com/users/m4dc4p/followers","following_url":"https://api.github.com/users/m4dc4p/following{/other_user}","gists_url":"https://api.github.com/users/m4dc4p/gists{/gist_id}","starred_url":"https://api.github.com/users/m4dc4p/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/m4dc4p/subscriptions","organizations_url":"https://api.github.com/users/m4dc4p/orgs","repos_url":"https://api.github.com/users/m4dc4p/repos","events_url":"https://api.github.com/users/m4dc4p/events{/privacy}","received_events_url":"https://api.github.com/users/m4dc4p/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-17T19:15:22Z","updated_at":"2022-03-18T21:11:19Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen an executable uses the \"paths\" module exported by a library (due to the `data-dir` or `data-files` directive in the library's cabal file), the closure of that executable is very large. It includes packages such as GHC and its documentation.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Clone the repo https://github.com/m4dc4p/nix-cabal-data-dir-surprise\r\n2. Run `nix-store --query -R --include-outputs $(nix-build -A app)`. \r\n3. Notice closure is small & GHC does not appear.\r\n4. Run `nix-store --query -R --include-outputs $(nix-build -A big-app)`. \r\n5. Closure has many more entries, including GHC (/nix/store/...-ghc-8.10.7) and its documentation (`/nix/store/...-ghc-8.10.7-doc`)\r\n\r\n### Expected behavior\r\n\r\nI would not expect that using the exported \"paths\" module from a library would make the closure so much larger. This is pretty impactful when building docker images. In the above repo, the docker image for `big-app` is 425MB, while the docker image for `app` is only 24M:\r\n\r\n```\r\n$ ls -lah $(nix-build -A docker-big-app)\r\n-r--r--r-- 1 justin.bailey admin 475M Dec 31 1969 /nix/store/0bvvq9sdw9bwiqbwyaidxj0wwkjmdif5-docker-image-docker-big-app.tar.gz\r\n$ ls -lah $(nix-build -A docker-app)\r\n-r--r--r-- 1 justin.bailey admin 26M Dec 31 1969 /nix/store/kbs7i25jnnlfcd0i9wxq68q3i829323m-docker-image-docker-app.tar.gz\r\n```\r\n\r\n### Additional context\r\n\r\n`app/Main.hs` conditionally imports the `Paths_library` module from the `library` package. If the module is imported and used, the closure blows up. This is due to a dependency found in the `package.conf.d` directory installed with library. \r\n\r\n```\r\n$ nix-store --query -R --include-outputs $(nix-build -A big-app) | grep ghc-8.10.7\r\n/nix/store/4ycwcc6rmyx2bchr7zbigfiyklqdkfik-ghc-8.10.7-doc\r\n/nix/store/qmcdw0bq6590082f3g6sqflqvlyvap5g-ghc-8.10.7\r\n$ nix why-depends --precise $(nix-build -A big-app) /nix/store/4ycwcc6rmyx2bchr7zbigfiyklqdkfik-ghc-8.10.7-doc\r\n/nix/store/j17x9cwaj4japr0mwk8nqvjgx7i6aysf-app-0.1.0.0\r\n└───bin/app: …rld..library_datadir./nix/store/jkndj3lpq6256xyrx2miqglllpqiv4sm-library-0.1.0.0/share/x86_64-os…\r\n → /nix/store/jkndj3lpq6256xyrx2miqglllpqiv4sm-library-0.1.0.0\r\n └───lib/ghc-8.10.7/package.conf.d/library-0.1.0.0-4DahppUPAwH8P1w4JjXODY.conf: …dock-interfaces:. /nix/store/qlcrbcy2la79hkz81wggdrwh720k7yhj-library-0.1.0.0-doc/share/doc/l…\r\n → /nix/store/qlcrbcy2la79hkz81wggdrwh720k7yhj-library-0.1.0.0-doc\r\n └───share/doc/library-0.1.0.0/html/Library.html: …> :: <a href=\"file:///nix/store/4ycwcc6rmyx2bchr7zbigfiyklqdkfik-ghc-8.10.7-doc/share/doc/ghc/ht…\r\n → /nix/store/4ycwcc6rmyx2bchr7zbigfiyklqdkfik-ghc-8.10.7-doc\r\n```\r\n\r\nThe `app` executable does not have any dependency on GHC:\r\n\r\n```\r\n$ nix-store --query -R --include-outputs $(nix-build -A app) | grep ghc-8.10.7\r\n< no output >\r\n$\r\n```\r\n\r\nNote that the `app` and `big-app` derivations compile the same source, but `big-app` passes a CPP flag so that the `Paths_library` modules gets imported and used in `app\\Main.hs`.\r\n\r\nThis bug has come up before, though not with the `data-dir` aspect, as https://github.com/NixOS/cabal2nix/issues/539 and https://github.com/NixOS/nixpkgs/issues/155924.\r\n\r\n### Notify maintainers\r\n@sternenseemann @maralorn \r\n\r\n### Metadata\r\n```\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(justin.bailey): `\"nixpkgs, nixpkgs-21.11-darwin-21.11-darwin\"`\r\n - nixpkgs: `/Users/justin.bailey/.nix-defexpr/channels/nixpkgs`\r\n - \r\n```\r\n(Current nixpkgs revision is 3e644bd62489b516292c816f70bf0052c693b3c7)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164630/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164571","id":1172212651,"node_id":"I_kwDOAEVQ_M5F3our","number":164571,"title":"Packaging request: lua-unbound","user":{"login":"Izorkin","id":26877687,"node_id":"MDQ6VXNlcjI2ODc3Njg3","avatar_url":"https://avatars.githubusercontent.com/u/26877687?v=4","gravatar_id":"","url":"https://api.github.com/users/Izorkin","html_url":"https://github.com/Izorkin","followers_url":"https://api.github.com/users/Izorkin/followers","following_url":"https://api.github.com/users/Izorkin/following{/other_user}","gists_url":"https://api.github.com/users/Izorkin/gists{/gist_id}","starred_url":"https://api.github.com/users/Izorkin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Izorkin/subscriptions","organizations_url":"https://api.github.com/users/Izorkin/orgs","repos_url":"https://api.github.com/users/Izorkin/repos","events_url":"https://api.github.com/users/Izorkin/events{/privacy}","received_events_url":"https://api.github.com/users/Izorkin/received_events","type":"User","site_admin":false},"labels":[{"id":1249449681,"node_id":"MDU6TGFiZWwxMjQ5NDQ5Njgx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20lua","name":"6.topic: lua","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-03-17T10:43:17Z","updated_at":"2022-03-18T11:47:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nTo upgrade Prosody to version 0.12.0 needed add lua-unbound.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.zash.se/luaunbound.html\r\n* source URL: https://code.zash.se/luaunbound/\r\n* license: mit\r\n* platforms: unix, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164571/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164551","id":1172069831,"node_id":"I_kwDOAEVQ_M5F3F3H","number":164551,"title":"Quicktile","user":{"login":"schlichtanders","id":4255480,"node_id":"MDQ6VXNlcjQyNTU0ODA=","avatar_url":"https://avatars.githubusercontent.com/u/4255480?v=4","gravatar_id":"","url":"https://api.github.com/users/schlichtanders","html_url":"https://github.com/schlichtanders","followers_url":"https://api.github.com/users/schlichtanders/followers","following_url":"https://api.github.com/users/schlichtanders/following{/other_user}","gists_url":"https://api.github.com/users/schlichtanders/gists{/gist_id}","starred_url":"https://api.github.com/users/schlichtanders/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/schlichtanders/subscriptions","organizations_url":"https://api.github.com/users/schlichtanders/orgs","repos_url":"https://api.github.com/users/schlichtanders/repos","events_url":"https://api.github.com/users/schlichtanders/events{/privacy}","received_events_url":"https://api.github.com/users/schlichtanders/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-17T08:23:53Z","updated_at":"2022-03-17T08:23:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nQuicktile is a window tiling add on compatible with many desktop environments.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://ssokolow.com/quicktile/\r\n* source URL: https://ssokolow.com/quicktile/\r\n* license: GPL-2.0 License\r\n* platforms: ??\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164551/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164451","id":1171197193,"node_id":"I_kwDOAEVQ_M5Fzw0J","number":164451,"title":"plasma: enable power-profiles-daemon by default","user":{"login":"SuperSamus","id":40663462,"node_id":"MDQ6VXNlcjQwNjYzNDYy","avatar_url":"https://avatars.githubusercontent.com/u/40663462?v=4","gravatar_id":"","url":"https://api.github.com/users/SuperSamus","html_url":"https://github.com/SuperSamus","followers_url":"https://api.github.com/users/SuperSamus/followers","following_url":"https://api.github.com/users/SuperSamus/following{/other_user}","gists_url":"https://api.github.com/users/SuperSamus/gists{/gist_id}","starred_url":"https://api.github.com/users/SuperSamus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/SuperSamus/subscriptions","organizations_url":"https://api.github.com/users/SuperSamus/orgs","repos_url":"https://api.github.com/users/SuperSamus/repos","events_url":"https://api.github.com/users/SuperSamus/events{/privacy}","received_events_url":"https://api.github.com/users/SuperSamus/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T15:38:00Z","updated_at":"2022-03-23T07:56:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nKDE Plasma supports the power profiles feature [since 5.23](https://pointieststick.com/2021/07/23/this-week-in-kde-power-profiles-and-a-more-polished-kickoff/), but [unlike Gnome](https://github.com/NixOS/nixpkgs/blob/master/nixos/modules/services/x11/desktop-managers/gnome.nix#L360), enabling `services.xserver.desktopManager.plasma5.enable` doesn't activate the feature by default.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `services.xserver.desktopManager.plasma5.enable = true;`\r\n2. Open Plasma;\r\n3. Click on the battery icon;\r\n4. There are no power profiles.\r\n\r\n### Expected behavior\r\nYou should see the power profiles.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164451/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164440","id":1171117501,"node_id":"I_kwDOAEVQ_M5FzdW9","number":164440,"title":"nixos/sourcehut: minio option does not do anything","user":{"login":"fgaz","id":8182846,"node_id":"MDQ6VXNlcjgxODI4NDY=","avatar_url":"https://avatars.githubusercontent.com/u/8182846?v=4","gravatar_id":"","url":"https://api.github.com/users/fgaz","html_url":"https://github.com/fgaz","followers_url":"https://api.github.com/users/fgaz/followers","following_url":"https://api.github.com/users/fgaz/following{/other_user}","gists_url":"https://api.github.com/users/fgaz/gists{/gist_id}","starred_url":"https://api.github.com/users/fgaz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fgaz/subscriptions","organizations_url":"https://api.github.com/users/fgaz/orgs","repos_url":"https://api.github.com/users/fgaz/repos","events_url":"https://api.github.com/users/fgaz/events{/privacy}","received_events_url":"https://api.github.com/users/fgaz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T14:40:22Z","updated_at":"2022-03-21T14:31:36Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSetting `services.sourcehut.minio.enable = true` does not do anything\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. enable sourcehut and a service that requires object storage, such as pages\r\n2. set `services.sourcehut.minio.enable = true` and `services.minio.enable = true`\r\n3. pages complains that object storage is not configured\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nsourcehut gets configured to use minio, like with postgresql and redis\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\nIt looks like there isn't any reference to the `minio` option in the service definition:\r\n\r\n```\r\n$ git grep minio nixos/modules/services/misc/sourcehut\r\nnixos/modules/services/misc/sourcehut/default.nix: minio = {\r\nnixos/modules/services/misc/sourcehut/default.nix: enable = mkEnableOption ''local minio integration'';\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n~~@julm (sorry)~~ @ju1m @tomberek @eadwu\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\nthe command breaks in the container I'm using, it's a nixos-unstable container\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164440/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164436","id":1171084176,"node_id":"I_kwDOAEVQ_M5FzVOQ","number":164436,"title":"libvirt: openGL does not work with Nvidia GPUs","user":{"login":"Kranzes","id":56614642,"node_id":"MDQ6VXNlcjU2NjE0NjQy","avatar_url":"https://avatars.githubusercontent.com/u/56614642?v=4","gravatar_id":"","url":"https://api.github.com/users/Kranzes","html_url":"https://github.com/Kranzes","followers_url":"https://api.github.com/users/Kranzes/followers","following_url":"https://api.github.com/users/Kranzes/following{/other_user}","gists_url":"https://api.github.com/users/Kranzes/gists{/gist_id}","starred_url":"https://api.github.com/users/Kranzes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Kranzes/subscriptions","organizations_url":"https://api.github.com/users/Kranzes/orgs","repos_url":"https://api.github.com/users/Kranzes/repos","events_url":"https://api.github.com/users/Kranzes/events{/privacy}","received_events_url":"https://api.github.com/users/Kranzes/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-16T14:14:33Z","updated_at":"2022-03-20T20:42:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThis bug has been discussed over at the discourse: https://discourse.nixos.org/t/opengl-with-libvirt-and-nvidia-driver/7177\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\nTry to create a VM with either virt-manager or virsh, with SPICE openGL enabled\r\n\r\n### Expected behavior\r\nThe expected behavior is that the VM would be created accordingly without throwing errors.\r\nNote: This does work correctly on my Intel iGPU laptop.\r\n\r\n### Error output\r\n```\r\nerror: internal error: qemu unexpectedly closed the monitor: 2022-03-16T14:11:19.539281Z qemu-system-x86_64: egl: eglGetDisplay failed\r\n2022-03-16T14:11:19.539339Z qemu-system-x86_64: Failed to initialize EGL render node for SPICE GL\r\n```\r\n\r\n### Notify maintainers\r\n@fpletz @globin\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.14, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.8.0pre20220311_d532269`\r\n - channels(root): `\"\"`\r\n - channels(kranzes): `\"\"`\r\n - nixpkgs: `/etc/nix/inputs/nixpkgs\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164436/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164424","id":1171022187,"node_id":"I_kwDOAEVQ_M5FzGFr","number":164424,"title":"`julia_17-bin` build failure on x86_64-linux as of `e517a35b`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":{"login":"7c6f434c","id":1891350,"node_id":"MDQ6VXNlcjE4OTEzNTA=","avatar_url":"https://avatars.githubusercontent.com/u/1891350?v=4","gravatar_id":"","url":"https://api.github.com/users/7c6f434c","html_url":"https://github.com/7c6f434c","followers_url":"https://api.github.com/users/7c6f434c/followers","following_url":"https://api.github.com/users/7c6f434c/following{/other_user}","gists_url":"https://api.github.com/users/7c6f434c/gists{/gist_id}","starred_url":"https://api.github.com/users/7c6f434c/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/7c6f434c/subscriptions","organizations_url":"https://api.github.com/users/7c6f434c/orgs","repos_url":"https://api.github.com/users/7c6f434c/repos","events_url":"https://api.github.com/users/7c6f434c/events{/privacy}","received_events_url":"https://api.github.com/users/7c6f434c/received_events","type":"User","site_admin":false},"assignees":[{"login":"7c6f434c","id":1891350,"node_id":"MDQ6VXNlcjE4OTEzNTA=","avatar_url":"https://avatars.githubusercontent.com/u/1891350?v=4","gravatar_id":"","url":"https://api.github.com/users/7c6f434c","html_url":"https://github.com/7c6f434c","followers_url":"https://api.github.com/users/7c6f434c/followers","following_url":"https://api.github.com/users/7c6f434c/following{/other_user}","gists_url":"https://api.github.com/users/7c6f434c/gists{/gist_id}","starred_url":"https://api.github.com/users/7c6f434c/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/7c6f434c/subscriptions","organizations_url":"https://api.github.com/users/7c6f434c/orgs","repos_url":"https://api.github.com/users/7c6f434c/repos","events_url":"https://api.github.com/users/7c6f434c/events{/privacy}","received_events_url":"https://api.github.com/users/7c6f434c/received_events","type":"User","site_admin":false}],"milestone":null,"comments":6,"created_at":"2022-03-16T13:26:04Z","updated_at":"2022-03-17T01:04:44Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"\n## Issue description\nBuild of `julia_17-bin` failed on x86_64-linux as of e517a35b9e5f309b63e26392de87ff1ebf7dcebc.\n\n[build log](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1992575351)\n\nMaintainer cc: @ninjin @7c6f434c\nOther cc: n/a\n\n### Steps to reproduce\n1. Checkout nixpkgs at commit e517a35b9e5f309b63e26392de87ff1ebf7dcebc\n2. Run `nix-build -A julia_17-bin`\n\n## Technical details\n```\n- system: `\"x86_64-linux\"`\n - host os: `Linux 5.11.0-1028-azure, Ubuntu, 20.04.4 LTS (Focal Fossa)`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.7.0`\n - nixpkgs: `/nix/store/g3600ikz01igw8sxl06nlmyawc556y3v-source`\n```\n\n## Misc.\nThis issue was automatically generated by [nixpkgs-upkeep](https://github.com/samuela/nixpkgs-upkeep).\n- [CI workflow](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1992575351) that created this issue.\n- Internal tag: 8264149597255636419\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164424/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164414","id":1170892954,"node_id":"I_kwDOAEVQ_M5Fymia","number":164414,"title":"Video Trimmer","user":{"login":"piousdeer","id":31318219,"node_id":"MDQ6VXNlcjMxMzE4MjE5","avatar_url":"https://avatars.githubusercontent.com/u/31318219?v=4","gravatar_id":"","url":"https://api.github.com/users/piousdeer","html_url":"https://github.com/piousdeer","followers_url":"https://api.github.com/users/piousdeer/followers","following_url":"https://api.github.com/users/piousdeer/following{/other_user}","gists_url":"https://api.github.com/users/piousdeer/gists{/gist_id}","starred_url":"https://api.github.com/users/piousdeer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piousdeer/subscriptions","organizations_url":"https://api.github.com/users/piousdeer/orgs","repos_url":"https://api.github.com/users/piousdeer/repos","events_url":"https://api.github.com/users/piousdeer/events{/privacy}","received_events_url":"https://api.github.com/users/piousdeer/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T11:27:22Z","updated_at":"2022-03-16T11:27:22Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nVideo Trimmer is a GTK 4 app that cuts out a fragment of a video given the start and end timestamps. The video is never re-encoded, so the process is very fast and does not reduce the video quality.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://apps.gnome.org/app/org.gnome.gitlab.YaLTeR.VideoTrimmer/\r\n* source URL: https://gitlab.gnome.org/YaLTeR/video-trimmer\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164414/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164413","id":1170883590,"node_id":"I_kwDOAEVQ_M5FykQG","number":164413,"title":"Add UnityDoorstop","user":{"login":"x10an14","id":710608,"node_id":"MDQ6VXNlcjcxMDYwOA==","avatar_url":"https://avatars.githubusercontent.com/u/710608?v=4","gravatar_id":"","url":"https://api.github.com/users/x10an14","html_url":"https://github.com/x10an14","followers_url":"https://api.github.com/users/x10an14/followers","following_url":"https://api.github.com/users/x10an14/following{/other_user}","gists_url":"https://api.github.com/users/x10an14/gists{/gist_id}","starred_url":"https://api.github.com/users/x10an14/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/x10an14/subscriptions","organizations_url":"https://api.github.com/users/x10an14/orgs","repos_url":"https://api.github.com/users/x10an14/repos","events_url":"https://api.github.com/users/x10an14/events{/privacy}","received_events_url":"https://api.github.com/users/x10an14/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T11:18:57Z","updated_at":"2022-03-16T11:18:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nCopy-paste from [current README.md](https://github.com/NeighTools/UnityDoorstop/blob/v3.4.0.0/README.md)\r\n```\r\n*Run managed code before Unity does!*\r\n\r\n# Unity Doorstop\r\nDoorstop is a tool to execute managed assemblies inside Unity as early as possible!\r\n\r\nThis repository is indented mainly for developers! \r\nDevelopers should package Doorstop into their applications for the end-users.\r\n\r\n## Features\r\n\r\n* **Runs first**: Doorstop runs its own code before Unity has an ability to do so.\r\n* **Configurable**: A very basic configuration file allows to specify your own assembly to execute!\r\n* **Public domain!** You are fully free to embed Doorstop into your application!\r\n```\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/NeighTools/UnityDoorstop.Unix\r\n* source URL: https://github.com/NeighTools/UnityDoorstop.Unix\r\n* license: Creative Commons Zero v1.0 Universal\r\n* platforms: unix, linux, darwin\r\n\r\n---\r\n**Rationale why**\r\n\r\nSeems to be leveraged by at least one (if not more) game mods/mod managers:\r\n1. https://github.com/BepInEx/BepInEx#used-libraries\r\n1. https://github.com/valheimPlus/ValheimPlus\r\n1. My own headbanging against this metaphorical wall: https://paste.sr.ht/~x10an14/b475abcde59de91290617105ba5828255e643ee6\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164413/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164393","id":1170761837,"node_id":"I_kwDOAEVQ_M5FyGht","number":164393,"title":"Add static build of z3 library","user":{"login":"Munksgaard","id":230613,"node_id":"MDQ6VXNlcjIzMDYxMw==","avatar_url":"https://avatars.githubusercontent.com/u/230613?v=4","gravatar_id":"","url":"https://api.github.com/users/Munksgaard","html_url":"https://github.com/Munksgaard","followers_url":"https://api.github.com/users/Munksgaard/followers","following_url":"https://api.github.com/users/Munksgaard/following{/other_user}","gists_url":"https://api.github.com/users/Munksgaard/gists{/gist_id}","starred_url":"https://api.github.com/users/Munksgaard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Munksgaard/subscriptions","organizations_url":"https://api.github.com/users/Munksgaard/orgs","repos_url":"https://api.github.com/users/Munksgaard/repos","events_url":"https://api.github.com/users/Munksgaard/events{/privacy}","received_events_url":"https://api.github.com/users/Munksgaard/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""},{"id":1469796342,"node_id":"MDU6TGFiZWwxNDY5Nzk2MzQy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20static","name":"6.topic: static","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T09:33:47Z","updated_at":"2022-03-21T20:20:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nMany libraries (ncurses, zlib and glibc, to name a few) have a statically compiled option, but z3 does not. z3 already has `--staticlib` and `--staticbin` flags for it's setup.py, but we don't use them.\r\n\r\nAs far as I can tell, there might be some complications regarding a statically linked c++ stdlib to link against, but I'm guessing it's solvable by someone more experienced than me.\r\n\r\nReference: https://github.com/Z3Prover/z3/blob/master/scripts/mk_util.py#L657-L658\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164393/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164357","id":1170520674,"node_id":"I_kwDOAEVQ_M5FxLpi","number":164357,"title":"Make it easier to globally disable pam auth factors for services","user":{"login":"berbiche","id":20448408,"node_id":"MDQ6VXNlcjIwNDQ4NDA4","avatar_url":"https://avatars.githubusercontent.com/u/20448408?v=4","gravatar_id":"","url":"https://api.github.com/users/berbiche","html_url":"https://github.com/berbiche","followers_url":"https://api.github.com/users/berbiche/followers","following_url":"https://api.github.com/users/berbiche/following{/other_user}","gists_url":"https://api.github.com/users/berbiche/gists{/gist_id}","starred_url":"https://api.github.com/users/berbiche/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/berbiche/subscriptions","organizations_url":"https://api.github.com/users/berbiche/orgs","repos_url":"https://api.github.com/users/berbiche/repos","events_url":"https://api.github.com/users/berbiche/events{/privacy}","received_events_url":"https://api.github.com/users/berbiche/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-16T04:17:37Z","updated_at":"2022-03-16T12:48:32Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using options such as `security.pam.u2f.enable`, all services will now be configured to allow using u2f as a mean to authenticate oneself.\r\n\r\nThis means for instance that it becomes possible to unlock your computer simply by having a u2f device plugged-in.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Set `security.pam.u2f.enable` and `security.pam.u2f.control = \"sufficient\"`.\r\n2. Lock your session.\r\n3. Unlock your session by touching your u2f key.\r\n\r\n### Expected behavior\r\n\r\nIt should be possible to disable/enable `u2fAuth` for all PAM services globally and override this value per service.\r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\n\r\nI currently \"abuse\" the type-merging feature of the module system to override the default value of `u2fAuth` and `yubicoAuth` for pam services:\r\n``` nix\r\n{ lib, ... }:\r\n\r\n{\r\n options.security.pam.services = with lib; mkOption {\r\n type = types.attrsOf (types.submodule {\r\n # Instead of overriding options.*.default, set it in the config section of the module\r\n config.u2fAuth = mkDefault false;\r\n config.yubicoAuth = mkDefault false;\r\n });\r\n };\r\n\r\n config = {\r\n # Authentication with a u2f device is sufficient for these services\r\n security.pam.services = {\r\n su.u2fAuth = true;\r\n sudo.u2fAuth = true;\r\n sshd.u2fAuth = true;\r\n polkit-1.u2fAuth = true;\r\n };\r\n };\r\n}\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@Mic92\r\n\r\nNot sure who maintains the PAM module given the history, lack of `meta.maintainers`, and a missing `CODEOWNERS` entry.\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nIrrelevant\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164357/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164287","id":1169902691,"node_id":"I_kwDOAEVQ_M5Fu0xj","number":164287,"title":"Ocaml dune and dune subpackages coherence","user":{"login":"AllanBlanchard","id":18618040,"node_id":"MDQ6VXNlcjE4NjE4MDQw","avatar_url":"https://avatars.githubusercontent.com/u/18618040?v=4","gravatar_id":"","url":"https://api.github.com/users/AllanBlanchard","html_url":"https://github.com/AllanBlanchard","followers_url":"https://api.github.com/users/AllanBlanchard/followers","following_url":"https://api.github.com/users/AllanBlanchard/following{/other_user}","gists_url":"https://api.github.com/users/AllanBlanchard/gists{/gist_id}","starred_url":"https://api.github.com/users/AllanBlanchard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AllanBlanchard/subscriptions","organizations_url":"https://api.github.com/users/AllanBlanchard/orgs","repos_url":"https://api.github.com/users/AllanBlanchard/repos","events_url":"https://api.github.com/users/AllanBlanchard/events{/privacy}","received_events_url":"https://api.github.com/users/AllanBlanchard/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null},{"id":446025054,"node_id":"MDU6TGFiZWw0NDYwMjUwNTQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20ocaml","name":"6.topic: ocaml","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-15T16:24:40Z","updated_at":"2022-03-16T14:31:27Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n\r\n- `nix search` name: dune-site\r\n - current version: 2.9.3\r\n - desired version: 3.0.3\r\n- `nix search` name: dune-private-libs\r\n - current version: 2.9.3\r\n - desired version: 3.0.3\r\n\r\nCurrently, it seems to me that there is no way to build a package that requires both Dune 3 and `dune-site`.\r\n\r\n###### Notify maintainers\r\n\r\nmaintainers: @vbgl @marsam \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164287/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164240","id":1169435190,"node_id":"I_kwDOAEVQ_M5FtCo2","number":164240,"title":"transmission on macOS fails with dyld: Library not loaded: libnatpmp.1.dylib","user":{"login":"larsr","id":182024,"node_id":"MDQ6VXNlcjE4MjAyNA==","avatar_url":"https://avatars.githubusercontent.com/u/182024?v=4","gravatar_id":"","url":"https://api.github.com/users/larsr","html_url":"https://github.com/larsr","followers_url":"https://api.github.com/users/larsr/followers","following_url":"https://api.github.com/users/larsr/following{/other_user}","gists_url":"https://api.github.com/users/larsr/gists{/gist_id}","starred_url":"https://api.github.com/users/larsr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/larsr/subscriptions","organizations_url":"https://api.github.com/users/larsr/orgs","repos_url":"https://api.github.com/users/larsr/repos","events_url":"https://api.github.com/users/larsr/events{/privacy}","received_events_url":"https://api.github.com/users/larsr/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-15T09:57:24Z","updated_at":"2022-03-22T11:16:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOn macOS (Darwin), running transmission-cli fails\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n```\r\n$ nix-shell -p transmission\r\n$ transmission-cli\r\ndyld: Library not loaded: libnatpmp.1.dylib\r\n Referenced from: /nix/store/zmbizqq1x1rs7anq9597glfls29mr7ra-transmission-3.00/bin/transmission-cli\r\n Reason: image not found\r\nAbort trap: 6\r\n```\r\n\r\n### Expected behavior\r\n\r\nThe expected behavior is to print out help text like this\r\n```\r\n$ transmission-cli\r\ntransmission-cli 3.00 (0)\r\nA fast and easy BitTorrent client\r\n\r\nUsage: transmission-cli [options] <file|url|magnet>\r\n\r\nOptions:\r\n -h --help Display this help page and exit\r\n...\r\n```\r\n\r\n\r\n### Additional context\r\n\r\nThis is not a problem due to `transmission` but rather due to how `libnatpmp` is built.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.1.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(larsr): `\"nixpkgs-22.05pre356557.74b10859829\"`\r\n - nixpkgs: `/Users/larsr/nixpkgs` \r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164240/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164161","id":1168861594,"node_id":"I_kwDOAEVQ_M5Fq2ma","number":164161,"title":"Evolution DecSync","user":{"login":"steveeJ","id":1181362,"node_id":"MDQ6VXNlcjExODEzNjI=","avatar_url":"https://avatars.githubusercontent.com/u/1181362?v=4","gravatar_id":"","url":"https://api.github.com/users/steveeJ","html_url":"https://github.com/steveeJ","followers_url":"https://api.github.com/users/steveeJ/followers","following_url":"https://api.github.com/users/steveeJ/following{/other_user}","gists_url":"https://api.github.com/users/steveeJ/gists{/gist_id}","starred_url":"https://api.github.com/users/steveeJ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/steveeJ/subscriptions","organizations_url":"https://api.github.com/users/steveeJ/orgs","repos_url":"https://api.github.com/users/steveeJ/repos","events_url":"https://api.github.com/users/steveeJ/events{/privacy}","received_events_url":"https://api.github.com/users/steveeJ/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-14T20:20:03Z","updated_at":"2022-03-14T20:21:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nDecSync for [Evolution](https://wiki.gnome.org/Apps/Evolution) is an Evolution plugin which synchronizes contacts and calendars using [DecSync](https://github.com/39aldo39/DecSync).\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/39aldo39/Evolution-DecSync\r\n* source URL: https://github.com/39aldo39/Evolution-DecSync\r\n* license: gpl2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164161/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164141","id":1168696014,"node_id":"I_kwDOAEVQ_M5FqOLO","number":164141,"title":"Separate static libraries to dev outputs automatically","user":{"login":"ilya-fedin","id":17829319,"node_id":"MDQ6VXNlcjE3ODI5MzE5","avatar_url":"https://avatars.githubusercontent.com/u/17829319?v=4","gravatar_id":"","url":"https://api.github.com/users/ilya-fedin","html_url":"https://github.com/ilya-fedin","followers_url":"https://api.github.com/users/ilya-fedin/followers","following_url":"https://api.github.com/users/ilya-fedin/following{/other_user}","gists_url":"https://api.github.com/users/ilya-fedin/gists{/gist_id}","starred_url":"https://api.github.com/users/ilya-fedin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ilya-fedin/subscriptions","organizations_url":"https://api.github.com/users/ilya-fedin/orgs","repos_url":"https://api.github.com/users/ilya-fedin/repos","events_url":"https://api.github.com/users/ilya-fedin/events{/privacy}","received_events_url":"https://api.github.com/users/ilya-fedin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-14T17:32:06Z","updated_at":"2022-03-16T13:09:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nLooking at space used by nix packages, it seems there's a lot of packages that used Nx space due to having static libraries in out/lib outputs. The first such package I found is llvm.lib used by mesa: it consumes ~300 MB while most of the space is used by static libraries that are helpful only while building something, shared libraries in the package are only around ~100 MB, so it's grown around 3x by that issue. Then, when I started looking at all static libraries in /nix/store with `find`, rav1e stands out from all other packages. Entire consumed space by rav1e is 89M, librav1e.a is 81M while librav1e.so.0.5.1 is only 3,2M. The package is around 10X bigger than if static libraries were separated and 25X bigger than if there was a lib output with only shared library.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-store -qR /run/current-system | xargs -I [] find [] -name '*.a' -exec du -h {} \\; | sort -h`\r\n\r\n### Expected behavior\r\nStatic libraries are in dev output\r\n\r\n### Additional context\r\nMy /nix/store (and `nix-store -qR /run/current-system | xargs du -csh | sort -h`) is 12GB after `nix-collect-garbage -d` and I'm trying to understand why it's so big while a similar configuration with other distros would consume a way less space...\r\n\r\n### Notify maintainers\r\n@lovek323 @7c6f434c @dtzWill @primeos for LLVM, it seems rav1e has no maintainers and I don't know who to mention for a generic solution across all the packages...\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0pre20220221_caf5172`\r\n - channels(root): `\"nixos-22.05pre338578.a2e281f5770\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164141/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164127","id":1168577414,"node_id":"I_kwDOAEVQ_M5FpxOG","number":164127,"title":"timeline: crashes on file dialog","user":{"login":"fgaz","id":8182846,"node_id":"MDQ6VXNlcjgxODI4NDY=","avatar_url":"https://avatars.githubusercontent.com/u/8182846?v=4","gravatar_id":"","url":"https://api.github.com/users/fgaz","html_url":"https://github.com/fgaz","followers_url":"https://api.github.com/users/fgaz/followers","following_url":"https://api.github.com/users/fgaz/following{/other_user}","gists_url":"https://api.github.com/users/fgaz/gists{/gist_id}","starred_url":"https://api.github.com/users/fgaz/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fgaz/subscriptions","organizations_url":"https://api.github.com/users/fgaz/orgs","repos_url":"https://api.github.com/users/fgaz/repos","events_url":"https://api.github.com/users/fgaz/events{/privacy}","received_events_url":"https://api.github.com/users/fgaz/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-03-14T15:53:26Z","updated_at":"2022-04-23T09:16:46Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"re #162503, the `timeline` package crashes with\r\n\r\n> (.timeline-wrapped:2422797): GLib-GIO-ERROR **: 17:05:40.072: No GSettings schemas are installed on the system\r\n> Trace/breakpoint trap (core dumped)\r\n\r\nwhen a file dialog is opened (eg. file -> open).\r\n\r\nThe rest of the program seems to work.\r\n\r\nI tried adding wrapGAppsHook, gsettings-desktop-schemas, and glib, but none of those fixed it.\r\n\r\nI'm running awesome wm, nixos 21.11\r\n\r\ncc @davidak","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164127/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164087","id":1168096931,"node_id":"I_kwDOAEVQ_M5Fn76j","number":164087,"title":"Package Request: YugabyteDB","user":{"login":"bouk","id":97820,"node_id":"MDQ6VXNlcjk3ODIw","avatar_url":"https://avatars.githubusercontent.com/u/97820?v=4","gravatar_id":"","url":"https://api.github.com/users/bouk","html_url":"https://github.com/bouk","followers_url":"https://api.github.com/users/bouk/followers","following_url":"https://api.github.com/users/bouk/following{/other_user}","gists_url":"https://api.github.com/users/bouk/gists{/gist_id}","starred_url":"https://api.github.com/users/bouk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bouk/subscriptions","organizations_url":"https://api.github.com/users/bouk/orgs","repos_url":"https://api.github.com/users/bouk/repos","events_url":"https://api.github.com/users/bouk/events{/privacy}","received_events_url":"https://api.github.com/users/bouk/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-14T09:20:48Z","updated_at":"2022-03-14T09:21:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\n[Yugabyte](https://www.yugabyte.com) is a 'Distributed SQL' database with a Postgresql and Cassandra-compatible API.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.yugabyte.com\r\n* source URL: https://github.com/yugabyte/yugabyte-db\r\n* license: Apache License 2.0\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164087/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164064","id":1167806053,"node_id":"I_kwDOAEVQ_M5Fm05l","number":164064,"title":"regression: tianocore/edk2 (ovmf uefi) update breaks qemu/kvm vm's","user":{"login":"lodi","id":918448,"node_id":"MDQ6VXNlcjkxODQ0OA==","avatar_url":"https://avatars.githubusercontent.com/u/918448?v=4","gravatar_id":"","url":"https://api.github.com/users/lodi","html_url":"https://github.com/lodi","followers_url":"https://api.github.com/users/lodi/followers","following_url":"https://api.github.com/users/lodi/following{/other_user}","gists_url":"https://api.github.com/users/lodi/gists{/gist_id}","starred_url":"https://api.github.com/users/lodi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lodi/subscriptions","organizations_url":"https://api.github.com/users/lodi/orgs","repos_url":"https://api.github.com/users/lodi/repos","events_url":"https://api.github.com/users/lodi/events{/privacy}","received_events_url":"https://api.github.com/users/lodi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-03-14T02:22:57Z","updated_at":"2022-04-21T20:58:47Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nCommit 9222b68380eb9195c7c87ca460fcb626d4e600ce broke my virt-manager vm's. Every vm starts, but then immediately hangs at a black screen with 100% cpu usage on 1 core. `htop` shows that thread split roughly 30/70 between kernel and virtualization. I tried leaving the vm's running for a few hours but that made no difference. I tried clearing the nvram folder, `/var/lib/libvirt/qemu/nvram/*` but that didn't help either.\r\n\r\n9222b68380eb9195c7c87ca460fcb626d4e600ce updated the OVMF UEFI firmware my vm's were using, so I bisected the [edk2](https://github.com/tianocore/edk2) source and found the offending upstream [commit](https://github.com/tianocore/edk2/commit/b8675deaa819631db2667df63f89799fe65fc906). It's something to do with TPM, and indeed I have software TPM enabled in my system config:\r\n\r\n```xml\r\n <!-- virt-manager config -->\r\n <os>\r\n <type arch=\"x86_64\" machine=\"pc-q35-5.0\">hvm</type>\r\n <loader readonly=\"yes\" type=\"rom\">/run/libvirt/nix-ovmf/OVMF_CODE.fd</loader>\r\n <nvram>/var/lib/libvirt/qemu/nvram/ubuntu_VARS.fd</nvram>\r\n </os>\r\n```\r\n\r\n```nix\r\n{\r\n virtualisation.libvirtd = {\r\n enable = true;\r\n onBoot = \"ignore\";\r\n onShutdown = \"shutdown\";\r\n\r\n qemu = {\r\n ovmf = {\r\n enable = true;\r\n package = pkgs.OVMFFull; # (1)\r\n };\r\n runAsRoot = false;\r\n swtpm.enable = true; # (2)\r\n };\r\n };\r\n}\r\n```\r\n\r\nI tried removing line 2 but that didn't change anything (the particular ubuntu vm I'm trying to boot isn't even using tpm). I also tried removing line 1 to force the system to use the `pkgs.OVMF` default, but that started throwing `qemu: could not load PC BIOS '/run/libvirt/nix-ovmf/OVMF_CODE.fd'` errors even though that file exists. I'm not sure what else I can try short of recreating the vm's from scratch.\r\n\r\n### Expected behavior\r\nVM boots into \"tianocore\" uefi logo, then proceeds to boot as normal.\r\n\r\n### Additional context\r\nRyzen 3950x\r\nAsrock X570 Taichi\r\n\r\n### Notify maintainers\r\n@alyssais \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.28, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164064/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164021","id":1167635308,"node_id":"I_kwDOAEVQ_M5FmLNs","number":164021,"title":"gnome.nautilus: No thumbnails for heic/heif files","user":{"login":"asbachb","id":1482768,"node_id":"MDQ6VXNlcjE0ODI3Njg=","avatar_url":"https://avatars.githubusercontent.com/u/1482768?v=4","gravatar_id":"","url":"https://api.github.com/users/asbachb","html_url":"https://github.com/asbachb","followers_url":"https://api.github.com/users/asbachb/followers","following_url":"https://api.github.com/users/asbachb/following{/other_user}","gists_url":"https://api.github.com/users/asbachb/gists{/gist_id}","starred_url":"https://api.github.com/users/asbachb/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/asbachb/subscriptions","organizations_url":"https://api.github.com/users/asbachb/orgs","repos_url":"https://api.github.com/users/asbachb/repos","events_url":"https://api.github.com/users/asbachb/events{/privacy}","received_events_url":"https://api.github.com/users/asbachb/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-13T16:57:38Z","updated_at":"2022-03-13T17:28:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nGnome nautilus does not generate thumbnails for heic/heif files.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Ensure thumbnails are enabled in preferences\r\n2. Open a folder containing heic files\r\n\r\n### Screenshots\r\n\r\n\r\n### Notify maintainers\r\n@hedning \r\n@jtojnar \r\n@dasj19 \r\n@maxeaubrey \r\n\r\n### Metadata\r\n```console\r\n asbachb@nixos-t14s ~ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.12, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(asbachb): `\"\"`\r\n - channels(root): `\"nixos, nixos-hardware\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164021/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019/events","html_url":"https://github.com/NixOS/nixpkgs/issues/164019","id":1167630109,"node_id":"I_kwDOAEVQ_M5FmJ8d","number":164019,"title":"Engineering apps","user":{"login":"yuuyins","id":86538850,"node_id":"MDQ6VXNlcjg2NTM4ODUw","avatar_url":"https://avatars.githubusercontent.com/u/86538850?v=4","gravatar_id":"","url":"https://api.github.com/users/yuuyins","html_url":"https://github.com/yuuyins","followers_url":"https://api.github.com/users/yuuyins/followers","following_url":"https://api.github.com/users/yuuyins/following{/other_user}","gists_url":"https://api.github.com/users/yuuyins/gists{/gist_id}","starred_url":"https://api.github.com/users/yuuyins/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yuuyins/subscriptions","organizations_url":"https://api.github.com/users/yuuyins/orgs","repos_url":"https://api.github.com/users/yuuyins/repos","events_url":"https://api.github.com/users/yuuyins/events{/privacy}","received_events_url":"https://api.github.com/users/yuuyins/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"assignees":[{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},{"login":"yuuyins","id":86538850,"node_id":"MDQ6VXNlcjg2NTM4ODUw","avatar_url":"https://avatars.githubusercontent.com/u/86538850?v=4","gravatar_id":"","url":"https://api.github.com/users/yuuyins","html_url":"https://github.com/yuuyins","followers_url":"https://api.github.com/users/yuuyins/followers","following_url":"https://api.github.com/users/yuuyins/following{/other_user}","gists_url":"https://api.github.com/users/yuuyins/gists{/gist_id}","starred_url":"https://api.github.com/users/yuuyins/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yuuyins/subscriptions","organizations_url":"https://api.github.com/users/yuuyins/orgs","repos_url":"https://api.github.com/users/yuuyins/repos","events_url":"https://api.github.com/users/yuuyins/events{/privacy}","received_events_url":"https://api.github.com/users/yuuyins/received_events","type":"User","site_admin":false}],"milestone":null,"comments":2,"created_at":"2022-03-13T16:37:52Z","updated_at":"2022-04-17T01:20:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"# Description\r\n\r\n`nixpkgs` misses many apps for engineering. My focus is software engineering, and for now mainly apps for requirements engineering and I also prioritize project management ones. They will be in `pkgs/applications/science/engineering`. This issue is mainly for stating the purpose and to keep track of the effort. Maybe I should create I separate repository for that goal. But as in https://github.com/NixOS/nixpkgs/issues/164019#issuecomment-1068711670, I really want to have it in nixpkgs as to make it easier for users to find these software, making NixOS a very good platform (or the best) for learning and practicing software engineering.\r\n\r\n- http://swebokwiki.org/Main_Page\r\n- https://ieeecs-media.computer.org/media/education/swebok/swebok-v3.pdf\r\n\r\nList of apps I’m trying and want to package\r\n\r\n# Requirements engineering\r\n\r\n## Specification/Management\r\n\r\n### rmToo <https://github.com/NixOS/nixpkgs/pull/163473>\r\n\r\n- homepage: <http://rmtoo.florath.net>\r\n- source: <https://github.com/florath/rmtoo>\r\n- license: gpl3\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n### strictdoc <https://github.com/NixOS/nixpkgs/pull/163964>\r\n\r\n- homepage: <https://strictdoc.readthedocs.io/en/stable>\r\n- source: <https://github.com/strictdoc-project/strictdoc>\r\n- license: asl20\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n### REQUS\r\n\r\n- homepage: <https://www.requs.org>\r\n- source: <https://github.com/yegor256/requs>\r\n- license: bsd3?\r\n- platforms: unix, linux, darwin\r\n\r\n### Clerq\r\n\r\n- homepage: <https://nvoynov.github.io/clerq>\r\n- source: <https://github.com/nvoynov/clerq>\r\n- license: mit\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n### OSRMT <https://github.com/NixOS/nixpkgs/pull/163400>\r\n\r\n- homepage:\r\n- source: <https://github.com/osrmt/osrmt>\r\n- license: gpl2\r\n- platforms: linux, darwin\r\n\r\n\r\n### CAIRIS\r\n\r\n- homepage: <https://cairis.org>\r\n- source: <https://github.com/cairis-platform/cairis>\r\n- license: asl20\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n\r\n\r\n### Redmine RE\r\n\r\n- homepage:\r\n- source: <https://github.com/tmerten/redmine_re>\r\n- license: gpl2\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n\r\n\r\n### Ephemeris\r\n\r\n- homepage: <https://www.ephemeris.cloud/demo>\r\n- source: <https://github.com/shuart/ephemeris>\r\n- license: mit\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n\r\n\r\n## Modeling: UML, BPMN, etc\r\n\r\n\r\n\r\n\r\n### Modelio <https://github.com/NixOS/nixpkgs/pull/154188>\r\n\r\n- homepage: <https://www.modelio.org>\r\n- source: <https://github.com/ModelioOpenSource/Modelio>\r\n- license: gpl3\r\n- platforms: unix, linux, darwin\r\n\r\n- <https://github.com/ModelioOpenSource/Modelio/wiki/Build-Modelio-Index>\r\n - <https://github.com/ModelioOpenSource/Modelio/wiki/Compile_modelio>\r\n - <https://github.com/ModelioOpenSource/Modelio/wiki/Package_modelio>\r\n\r\n\r\n\r\n\r\n### Papyrus\r\n\r\n- homepage: <https://www.eclipse.org/papyrus>\r\n- source: <https://git.eclipse.org/r/papyrus/org.eclipse.papyrus>\r\n- license: epl20\r\n- platforms: unix, linux, darwin\r\n\r\n#### Tags\r\n\r\n- <https://stackoverflow.com/questions/2107484/what-is-the-difference-between-springs-ga-rc-and-m2-releases>\r\n- <https://wiki.eclipse.org/Papyrus-RT/User/User_Guide/Papyrus-RT_RCP>\r\n\r\n#### Build\r\n\r\n- <https://wiki.eclipse.org/Papyrus/Papyrus_Developer_Guide>\r\n- <https://wiki.eclipse.org/Papyrus/Papyrus_Developer_Guide/How_To-_Code_Contributing>\r\n- <https://wiki.eclipse.org/Papyrus/Papyrus_Developer_Guide/Build_Process>\r\n \r\n git clone https://git.eclipse.org/r/papyrus/org.eclipse.papyrus\r\n\r\n#### Contact\r\n\r\n <https://www.eclipse.org/forums/index.php?t=thread&frm_id=121>\r\n\r\n\r\n\r\n\r\n### Capella\r\n\r\n- homepage: <https://www.eclipse.org/capella>\r\n- source: <https://github.com/eclipse/capella>\r\n- license: epl20\r\n- platforms: unix, linux, darwin\r\n\r\n- <https://github.com/eclipse/capella/wiki>\r\n- <https://github.com/eclipse/capella/wiki/Dependency%20versions>\r\n- <https://ci.eclipse.org/capella/>\r\n\r\n#### Build\r\n\r\n mvn clean verify -f releng/plugins/org.polarsys.capella.targets/pom.xml\r\n mvn clean install\r\n\r\n\r\n### Bonita\r\n\r\n- homepage: <https://www.bonitasoft.com>\r\n- source: <https://github.com/bonitasoft/bonita-platform>, <https://github.com/bonitasoft-community/build-bonita>\r\n- license: gpl21\r\n- platforms: unix, linux, darwin\r\n- <https://documentation.bonitasoft.com/building-community-edition-from-source>\r\n\r\n\r\n### Camunda\r\n\r\n- homepage: <https://camunda.com/products/modeler>\r\n- source: <https://github.com/camunda/camunda-modeler>\r\n- license: mit\r\n- platforms: unix, linux, darwin\r\n\r\n#### Build\r\n- https://nixos.org/manual/nixpkgs/stable/#javascript-tool-specific\r\n- https://github.com/svanderburg/node2nix\r\n- https://github.com/svanderburg/node2nix#adding-additionalglobal-npm-packages-to-a-packaging-process=\r\n- https://github.com/NixOS/nixpkgs/tree/master/pkgs/misc/base16-builder\r\n- `node2nix --supplement-input supplements.json`\r\n```\r\n[\r\n \"node-gyp\"\r\n]\r\n```\r\n\r\n# Software design\r\n\r\n## ERD\r\n\r\n### DONE brModelo <https://github.com/NixOS/nixpkgs/pull/167729> <s>https://github.com/NixOS/nixpkgs/pull/161706</s> \r\n\r\n- homepage: <https://www.sis4.com/brModelo>\r\n- source: <https://github.com/chcandido/brModelo>\r\n- license: gpl3\r\n- platforms: unix, linux, darwin\r\n\r\n## UI\r\n\r\n### Penpot\r\n\r\n- homepage: <https://penpot.app>\r\n- source: <https://github.com/penpot/penpot>\r\n- license: mpl2\r\n- platforms: unix\r\n\r\n# Project management\r\n\r\n### Zentao\r\n\r\n- homepage: <http://www.zentao.pm>\r\n- source: <https://github.com/easysoft/zentaopms>\r\n- license: <https://github.com/easysoft/zentaopms/blob/master/COPYING>\r\n- platforms: unix, linux, darwin\r\n\r\n\r\n\r\n\r\n### OpenProject\r\n\r\n- homepage: <https://www.openproject.org/>\r\n- source: <https://github.com/opf/openproject>\r\n- license: gpl3\r\n- platforms: unix, linux, darwin\r\n- <https://github.com/opf/openproject/tree/dev/nix>\r\n\r\n\r\n# Science/Research\r\n\r\n## Parsifal\r\n\r\nbased on Kitchenham guidelines for systematic reviews in software engineering\r\n\r\n- homepage: <https://parsif.al>\r\n- source: <https://github.com/vitorfs/parsifal>\r\n- license: mit\r\n- platforms: all\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/164019/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163936","id":1167440548,"node_id":"I_kwDOAEVQ_M5Flbqk","number":163936,"title":"When booting old generation, nix-env --list-generations has wrong \"current\"","user":{"login":"cyounkins","id":346185,"node_id":"MDQ6VXNlcjM0NjE4NQ==","avatar_url":"https://avatars.githubusercontent.com/u/346185?v=4","gravatar_id":"","url":"https://api.github.com/users/cyounkins","html_url":"https://github.com/cyounkins","followers_url":"https://api.github.com/users/cyounkins/followers","following_url":"https://api.github.com/users/cyounkins/following{/other_user}","gists_url":"https://api.github.com/users/cyounkins/gists{/gist_id}","starred_url":"https://api.github.com/users/cyounkins/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cyounkins/subscriptions","organizations_url":"https://api.github.com/users/cyounkins/orgs","repos_url":"https://api.github.com/users/cyounkins/repos","events_url":"https://api.github.com/users/cyounkins/events{/privacy}","received_events_url":"https://api.github.com/users/cyounkins/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-13T00:40:29Z","updated_at":"2022-03-17T01:03:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAfter selecting an older generation in the bootloader, listing system generations still indicates the latest generation as the current one.\r\n\r\n### Steps To Reproduce\r\nSelect an old generation in the bootloader. The booted system has an older kernel. The last generation is marked as \"current\".\r\n\r\n```console\r\n# uname -a\r\nLinux nixos-unstable 5.10.47 #1-NixOS SMP Wed Jun 30 13:04:24 UTC 2021 x86_64 GNU/Linux\r\n# nix-env --list-generations --profile /nix/var/nix/profiles/system\r\n 1 2021-07-10 22:14:08\r\n 2 2021-07-10 22:17:42\r\n 3 2021-07-10 22:20:26\r\n 4 2021-07-11 06:07:44\r\n 5 2022-03-12 23:46:43 (current)\r\n```\r\n\r\nReboot into the default newest generation. See the newer kernel but same output from `--list-generations`.\r\n\r\n```console\r\n# uname -a\r\nLinux nixos-unstable 5.15.27 #1-NixOS SMP Tue Mar 8 18:12:55 UTC 2022 x86_64 GNU/Linux\r\n# nix-env --list-generations --profile /nix/var/nix/profiles/system\r\n 1 2021-07-10 22:14:08\r\n 2 2021-07-10 22:17:42\r\n 3 2021-07-10 22:20:26\r\n 4 2021-07-11 06:07:44\r\n 5 2022-03-12 23:46:43 (current)\r\n```\r\n\r\n### Expected behavior\r\nI expect the booted, active generation to be marked as current.\r\n\r\n### Additional context\r\nYou can do `--switch-generation` and it will change \"current\", but obviously the kernel isn't reloaded.\r\n\r\nIf I add `nmap` to `pkgs` in `/etc/nixos/configuration.nix` and `nixos-rebuild switch`, I get generation 6. If I `--switch-generation 5`, \"current\" changes but `nmap` still exists in the path, even after re-logging. If I then boot generation 5 from the bootloader, `nmap` is not available.\r\n\r\nIt seems to me that `--switch-generation` and `--list-generations` are unusable on system generations.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.27, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0`\r\n - channels(root): `\"nixos-22.05pre359917.fcd48a5a069\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163936/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163831","id":1167276757,"node_id":"I_kwDOAEVQ_M5FkzrV","number":163831,"title":"VirtualBox won't build with extensionPack","user":{"login":"rhoriguchi","id":6047658,"node_id":"MDQ6VXNlcjYwNDc2NTg=","avatar_url":"https://avatars.githubusercontent.com/u/6047658?v=4","gravatar_id":"","url":"https://api.github.com/users/rhoriguchi","html_url":"https://github.com/rhoriguchi","followers_url":"https://api.github.com/users/rhoriguchi/followers","following_url":"https://api.github.com/users/rhoriguchi/following{/other_user}","gists_url":"https://api.github.com/users/rhoriguchi/gists{/gist_id}","starred_url":"https://api.github.com/users/rhoriguchi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rhoriguchi/subscriptions","organizations_url":"https://api.github.com/users/rhoriguchi/orgs","repos_url":"https://api.github.com/users/rhoriguchi/repos","events_url":"https://api.github.com/users/rhoriguchi/events{/privacy}","received_events_url":"https://api.github.com/users/rhoriguchi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-12T12:33:23Z","updated_at":"2022-03-22T11:37:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nCan't compile VirtualBox on `nixos-unstable` with `virtualisation.virtualbox.host.enableExtensionPack = true`.\r\n\r\n```console\r\n...\r\nThe failing command:\r\n$(QUIET)$(REDIRECT) -wo $@ -- $(SED) -f $< $(filter %.h,$^)\r\nkmk: *** Deleting file '/build/VirtualBox-6.1.30/out/linux.amd64/release/obj/Runtime/errmsgdata.h'\r\nkBuild: Generating /build/VirtualBox-6.1.30/out/linux.amd64/release/obj/Runtime/errmsgdata.h\r\nkmk: *** [/build/VirtualBox-6.1.30/src/VBox/Runtime/Makefile.kmk:3685: /build/VirtualBox-6.1.30/out/linux.amd64/release/obj/Runtime/errmsgdata.h] Segmentation fault\r\nkmk: *** Waiting for unfinished jobs....\r\nkBuild: Compiling RuntimeBldProg - /build/VirtualBox-6.1.30/src/VBox/Runtime/common/err/errinfo.cpp\r\nkBuild: Compiling RuntimeBldProg - /build/VirtualBox-6.1.30/src/VBox/Runtime/common/err/errinfolog.cpp\r\nkBuild: Compiling RuntimeBldProg - /build/VirtualBox-6.1.30/src/VBox/Runtime/common/dbg/dbgmoddwarf.cpp\r\nkmk: *** Exiting with status 2\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add these config options:\r\n```nix\r\nvirtualisation.virtualbox.host = {\r\n enable = true;\r\n enableExtensionPack = true;\r\n};\r\n```\r\n2. Build configuration\r\n\r\n### Expected behavior\r\nShould compile with no issue.\r\n\r\n### Additional context\r\nThis issue exists already a while.\r\n\r\n### Notify maintainers\r\n@svanderburg \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.96-hardened1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163831/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163830","id":1167276295,"node_id":"I_kwDOAEVQ_M5FkzkH","number":163830,"title":"srcml 0.9.5_beta outdated.","user":{"login":"armijnhemel","id":10587952,"node_id":"MDQ6VXNlcjEwNTg3OTUy","avatar_url":"https://avatars.githubusercontent.com/u/10587952?v=4","gravatar_id":"","url":"https://api.github.com/users/armijnhemel","html_url":"https://github.com/armijnhemel","followers_url":"https://api.github.com/users/armijnhemel/followers","following_url":"https://api.github.com/users/armijnhemel/following{/other_user}","gists_url":"https://api.github.com/users/armijnhemel/gists{/gist_id}","starred_url":"https://api.github.com/users/armijnhemel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/armijnhemel/subscriptions","organizations_url":"https://api.github.com/users/armijnhemel/orgs","repos_url":"https://api.github.com/users/armijnhemel/repos","events_url":"https://api.github.com/users/armijnhemel/events{/privacy}","received_events_url":"https://api.github.com/users/armijnhemel/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-12T12:30:49Z","updated_at":"2022-03-12T12:30:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [X] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [X] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: srcml\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.9.5_beta\r\ndesired version: 1.0.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @leenaars \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\nAlso, possibly move it from `version-management` to another directory, as this is clearly not a version management program. Instead, it is a code analysis program.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163830/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163768","id":1167197336,"node_id":"I_kwDOAEVQ_M5FkgSY","number":163768,"title":"warning when switching to different host","user":{"login":"jyooru","id":63786778,"node_id":"MDQ6VXNlcjYzNzg2Nzc4","avatar_url":"https://avatars.githubusercontent.com/u/63786778?v=4","gravatar_id":"","url":"https://api.github.com/users/jyooru","html_url":"https://github.com/jyooru","followers_url":"https://api.github.com/users/jyooru/followers","following_url":"https://api.github.com/users/jyooru/following{/other_user}","gists_url":"https://api.github.com/users/jyooru/gists{/gist_id}","starred_url":"https://api.github.com/users/jyooru/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jyooru/subscriptions","organizations_url":"https://api.github.com/users/jyooru/orgs","repos_url":"https://api.github.com/users/jyooru/repos","events_url":"https://api.github.com/users/jyooru/events{/privacy}","received_events_url":"https://api.github.com/users/jyooru/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-12T06:26:55Z","updated_at":"2022-03-14T11:50:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Is it possible to add a warning when switching to a system with a different hostname?\r\n\r\nToday I accidentally `nixos-rebuild switch`ed my laptop to one of my servers, and this is probably the third time I've done so...\r\n\r\nIt would be really useful if the `nixos-rebuild` script could warn the user if they are trying to switch to a completely different nixos configuration.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163768/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163760","id":1167189395,"node_id":"I_kwDOAEVQ_M5FkeWT","number":163760,"title":"Getting segmentation fault on running lxappearance","user":{"login":"wiredhikari","id":81508805,"node_id":"MDQ6VXNlcjgxNTA4ODA1","avatar_url":"https://avatars.githubusercontent.com/u/81508805?v=4","gravatar_id":"","url":"https://api.github.com/users/wiredhikari","html_url":"https://github.com/wiredhikari","followers_url":"https://api.github.com/users/wiredhikari/followers","following_url":"https://api.github.com/users/wiredhikari/following{/other_user}","gists_url":"https://api.github.com/users/wiredhikari/gists{/gist_id}","starred_url":"https://api.github.com/users/wiredhikari/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wiredhikari/subscriptions","organizations_url":"https://api.github.com/users/wiredhikari/orgs","repos_url":"https://api.github.com/users/wiredhikari/repos","events_url":"https://api.github.com/users/wiredhikari/events{/privacy}","received_events_url":"https://api.github.com/users/wiredhikari/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-12T05:45:12Z","updated_at":"2022-03-12T05:46:21Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version:\r\ndesired version:\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers:\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163760/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163739","id":1167163251,"node_id":"I_kwDOAEVQ_M5FkX9z","number":163739,"title":"cudatoolkit: cuda-memcheck broken","user":{"login":"mcwitt","id":319411,"node_id":"MDQ6VXNlcjMxOTQxMQ==","avatar_url":"https://avatars.githubusercontent.com/u/319411?v=4","gravatar_id":"","url":"https://api.github.com/users/mcwitt","html_url":"https://github.com/mcwitt","followers_url":"https://api.github.com/users/mcwitt/followers","following_url":"https://api.github.com/users/mcwitt/following{/other_user}","gists_url":"https://api.github.com/users/mcwitt/gists{/gist_id}","starred_url":"https://api.github.com/users/mcwitt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mcwitt/subscriptions","organizations_url":"https://api.github.com/users/mcwitt/orgs","repos_url":"https://api.github.com/users/mcwitt/repos","events_url":"https://api.github.com/users/mcwitt/events{/privacy}","received_events_url":"https://api.github.com/users/mcwitt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-12T03:28:59Z","updated_at":"2022-03-30T07:45:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe `cuda-memcheck` binary included with `cudatoolkit` fails to produce the expected output, instead printing `Internal error (7)`.\r\n\r\n### Steps To Reproduce\r\nThe following example (from the [cuda-memcheck docs](https://docs.nvidia.com/cuda/cuda-memcheck/index.html#example-use-of-memcheck)), when run under `cuda-memcheck`, does not produce the [expected output](https://docs.nvidia.com/cuda/cuda-memcheck/index.html#memcheck-demo-output-with-memcheck-release-build):\r\n\r\n```cuda\r\n#include <stdio.h>\r\n\r\n__device__ int x;\r\n\r\n__global__ void unaligned_kernel(void) {\r\n *(int*) ((char*)&x + 1) = 42;\r\n}\r\n\r\n__device__ void out_of_bounds_function(void) {\r\n *(int*) 0x87654320 = 42;\r\n}\r\n\r\n__global__ void out_of_bounds_kernel(void) {\r\n out_of_bounds_function();\r\n}\r\n\r\nvoid run_unaligned(void) {\r\n printf(\"Running unaligned_kernel\\n\");\r\n unaligned_kernel<<<1,1>>>();\r\n printf(\"Ran unaligned_kernel: %s\\n\",\r\n cudaGetErrorString(cudaGetLastError()));\r\n printf(\"Sync: %s\\n\", cudaGetErrorString(cudaDeviceSynchronize()));\r\n}\r\n\r\nvoid run_out_of_bounds(void) {\r\n printf(\"Running out_of_bounds_kernel\\n\");\r\n out_of_bounds_kernel<<<1,1>>>();\r\n printf(\"Ran out_of_bounds_kernel: %s\\n\",\r\n cudaGetErrorString(cudaGetLastError()));\r\n printf(\"Sync: %s\\n\", cudaGetErrorString(cudaDeviceSynchronize()));\r\n}\r\n\r\nint main() {\r\n int *devMem;\r\n\r\n printf(\"Mallocing memory\\n\");\r\n cudaMalloc((void**)&devMem, 1024);\r\n\r\n run_unaligned();\r\n run_out_of_bounds();\r\n\r\n cudaDeviceReset();\r\n cudaFree(devMem);\r\n\r\n return 0;\r\n}\r\n```\r\n\r\nTo reproduce:\r\n```console\r\n$ nix-shell --pure -p cudatoolkit_10_1 --command \"nvcc memcheck_demo.cu && LD_LIBRARY_PATH=/run/opengl-driver/lib ./a.out\"\r\nMallocing memory\r\nRunning unaligned_kernel\r\nRan unaligned_kernel: no error\r\nSync: misaligned address\r\nRunning out_of_bounds_kernel\r\nRan out_of_bounds_kernel: misaligned address\r\nSync: misaligned address\r\n```\r\n(Note: if the `LD_LIBRARY_PATH` setting is removed, this fails with `CUDA driver version is insufficient for CUDA runtime version`)\r\n\r\nThe above output is [as expected](https://docs.nvidia.com/cuda/cuda-memcheck/index.html#memcheck-demo-output). But when run under cuda-memcheck, errors are not detected and the message `Internal Error (7)` is printed:\r\n```console\r\n$ nix-shell --pure -p cudatoolkit_11_6 --command \"nvcc memcheck_demo.cu && LD_LIBRARY_PATH=/run/opengl-driver/lib cuda-memcheck a.out\"\r\n========= CUDA-MEMCHECK\r\n========= This tool is deprecated and will be removed in a future release of the CUDA toolkit\r\n========= Please use the compute-sanitizer tool as a drop-in replacement\r\nMallocing memory\r\nRunning unaligned_kernel\r\nRan unaligned_kernel: no error\r\nSync: no error\r\nRunning out_of_bounds_kernel\r\nRan out_of_bounds_kernel: no error\r\nSync: misaligned address\r\n========= Internal error (7)\r\n========= No CUDA-MEMCHECK results found\r\n```\r\n\r\nThis reproduction works for other versions of cudatoolkit I tried (e.g. 11.5, 10.1).\r\n\r\n### Expected behavior\r\nThe cuda-memcheck binary should produce the [expected output](https://docs.nvidia.com/cuda/cuda-memcheck/index.html#memcheck-demo-output-with-memcheck-release-build) when run on the example. In particular, it should not print `Internal error (7)`.\r\n\r\n### Notify maintainers\r\n[@NixOS/cuda-maintainers](https://github.com/orgs/NixOS/teams/cuda-maintainers)\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.25, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(matt): `\"\"`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163739/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163700","id":1166844270,"node_id":"I_kwDOAEVQ_M5FjKFu","number":163700,"title":"Standardize CUDA arch's/compute capabilities","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3981764947,"node_id":"LA_kwDOAEVQ_M7tVOlT","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cuda","name":"6.topic: cuda","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-11T20:34:53Z","updated_at":"2022-04-05T06:04:22Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nRight now every package builds CUDA with their own notion of CUDA architectures. As @SomeoneSerge notes in https://github.com/numtide/nixpkgs-unfree/pull/8#discussion_r824044775,\r\n\r\n> (e.g. `cudaArchList = [ \"8.6+PTX\" ];` in pytorch is `cudaCapabilities = [ \"compute_86\" ]` in jaxlib)\r\n\r\nIn order to provide a consistent experience we should probably standardize these possible options, much like how licenses and platforms are currently standardized into enum-ish concepts.\r\n\r\nIn the future perhaps we can add a nixpkgs-wide config option to set which CUDA arch you'd like things built against.\r\n\r\nOpening this issue now to track the problem, and brainstorm possible solutions.\r\n\r\ncc @NixOS/cuda-maintainers ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163700/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163684","id":1166627712,"node_id":"I_kwDOAEVQ_M5FiVOA","number":163684,"title":"Error building aarch64-unknown-linux-musl-binutils deriviation on Darwin aarch64","user":{"login":"yotam-arnac","id":97979164,"node_id":"U_kgDOBdcLHA","avatar_url":"https://avatars.githubusercontent.com/u/97979164?v=4","gravatar_id":"","url":"https://api.github.com/users/yotam-arnac","html_url":"https://github.com/yotam-arnac","followers_url":"https://api.github.com/users/yotam-arnac/followers","following_url":"https://api.github.com/users/yotam-arnac/following{/other_user}","gists_url":"https://api.github.com/users/yotam-arnac/gists{/gist_id}","starred_url":"https://api.github.com/users/yotam-arnac/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yotam-arnac/subscriptions","organizations_url":"https://api.github.com/users/yotam-arnac/orgs","repos_url":"https://api.github.com/users/yotam-arnac/repos","events_url":"https://api.github.com/users/yotam-arnac/events{/privacy}","received_events_url":"https://api.github.com/users/yotam-arnac/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-11T16:37:36Z","updated_at":"2022-03-12T17:43:08Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nError building aarch64-unknown-linux-musl-binutils on Darwin:\r\n\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n`default.nix`:\r\n```nix\r\n\r\n{ pkgs ? import (fetchTarball \"https://releases.nixos.org/nixos/unstable/nixos-22.05pre358986.062a0c5437b/nixexprs.tar.xz\") {}}:\r\nwith pkgs;\r\n\r\nmkShell {\r\n buildInputs = [pkgsCross.aarch64-multiplatform-musl.gccStdenv];\r\n}\r\n```\r\n\r\nRun `nix-shell`\r\n\r\nThe build fails with the following output:\r\n```console\r\nbuilding '/nix/store/3j50x63d4770dbphjwcab58g07lwxilk-aarch64-unknown-linux-musl-binutils-2.35.2.drv'...\r\nunpacking sources\r\nunpacking source archive /nix/store/j6z6nymw7nlfw5598wkf8f3cjksvrcy0-binutils-2.35.2.tar.bz2\r\ntar (child): lbzip2: Cannot exec: No such file or directory\r\ntar (child): Error is not recoverable: exiting now\r\ntar: Child returned status 2\r\ntar: Error is not recoverable: exiting now\r\ndo not know how to unpack source archive /nix/store/j6z6nymw7nlfw5598wkf8f3cjksvrcy0-binutils-2.35.2.tar.bz2\r\nerror: builder for '/nix/store/3j50x63d4770dbphjwcab58g07lwxilk-aarch64-unknown-linux-musl-binutils-2.35.2.drv' failed with exit code 1;\r\n last 7 log lines:\r\n > unpacking sources\r\n > unpacking source archive /nix/store/j6z6nymw7nlfw5598wkf8f3cjksvrcy0-binutils-2.35.2.tar.bz2\r\n > tar (child): lbzip2: Cannot exec: No such file or directory\r\n > tar (child): Error is not recoverable: exiting now\r\n > tar: Child returned status 2\r\n > tar: Error is not recoverable: exiting now\r\n > do not know how to unpack source archive /nix/store/j6z6nymw7nlfw5598wkf8f3cjksvrcy0-binutils-2.35.2.tar.bz2\r\n For full logs, run 'nix log /nix/store/3j50x63d4770dbphjwcab58g07lwxilk-aarch64-unknown-linux-musl-binutils-2.35.2.drv'.\r\nerror: 1 dependencies of derivation '/nix/store/mr3bv8bb057722wnbqvjl2q8jf393li5-aarch64-unknown-linux-musl-binutils-wrapper-2.35.2.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/q19xg5alzf9p9qndmayx6ag1fsc8s2v7-aarch64-unknown-linux-musl-binutils-wrapper-2.35.2.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/xc42638amw5ic50icwlqi4a9m5chww30-aarch64-unknown-linux-musl-stage-final-gcc-debug-wrapper-11.2.0.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/w9lxn612kxbh5hsy7l8khvlzlxhaxplf-stdenv-darwin.drv' failed to build\r\n```\r\n\r\n\r\n### Expected behavior\r\nThe deriviation is built.\r\n\r\n### Notify maintainers\r\n\r\n(Not sure I got the right maintainer :))\r\n@viric\r\n\r\n### Metadata\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.4.0, macOS 12.3`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(yotam): `\"nixos-21.11-21.11\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163684/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163669","id":1166381891,"node_id":"I_kwDOAEVQ_M5FhZND","number":163669,"title":"synapse will not start if services.matrix-synapse.settings.trusted_key_servers does not specify verify_keys","user":{"login":"lunik1","id":13547699,"node_id":"MDQ6VXNlcjEzNTQ3Njk5","avatar_url":"https://avatars.githubusercontent.com/u/13547699?v=4","gravatar_id":"","url":"https://api.github.com/users/lunik1","html_url":"https://github.com/lunik1","followers_url":"https://api.github.com/users/lunik1/followers","following_url":"https://api.github.com/users/lunik1/following{/other_user}","gists_url":"https://api.github.com/users/lunik1/gists{/gist_id}","starred_url":"https://api.github.com/users/lunik1/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lunik1/subscriptions","organizations_url":"https://api.github.com/users/lunik1/orgs","repos_url":"https://api.github.com/users/lunik1/repos","events_url":"https://api.github.com/users/lunik1/events{/privacy}","received_events_url":"https://api.github.com/users/lunik1/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-11T12:50:57Z","updated_at":"2022-03-12T21:00:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nNot specifying `verify_keys` in any of the `services.matrix-synapse.settings.trusted_key_servers` submodules will cause synapse to fail to start. This setting is specified as optional by usptream https://matrix-org.github.io/synapse/latest/usage/configuration/homeserver_sample_config.html.\r\n\r\nError message:\r\n```\r\n[2541475.987207] synapse_homeserver[299]: Error in configuration:\r\n[2541475.987473] synapse_homeserver[299]: Unable to parse 'trusted_key_servers': None is not of type 'object'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set `services.matrix-synapse.settings.trusted_key_servers` to e.g.\r\n```nix\r\ntrusted_key_servers = [\r\n { server_name = \"matrix.org\"; }\r\n];\r\n```\r\n2. Start the synapse service\r\n\r\n### Expected behavior\r\nSynapse should start\r\n\r\n### Additional context\r\nWorkaround: set `verify_keys` to an empty set.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Ma27 @fadenb @mguentner @Ekleog @Ralith @dandellion @sumnerevans @mweinelt \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163669/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163645","id":1165971555,"node_id":"I_kwDOAEVQ_M5Ff1Bj","number":163645,"title":"G'Mic missing from Krita","user":{"login":"aidalgol","id":2313201,"node_id":"MDQ6VXNlcjIzMTMyMDE=","avatar_url":"https://avatars.githubusercontent.com/u/2313201?v=4","gravatar_id":"","url":"https://api.github.com/users/aidalgol","html_url":"https://github.com/aidalgol","followers_url":"https://api.github.com/users/aidalgol/followers","following_url":"https://api.github.com/users/aidalgol/following{/other_user}","gists_url":"https://api.github.com/users/aidalgol/gists{/gist_id}","starred_url":"https://api.github.com/users/aidalgol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/aidalgol/subscriptions","organizations_url":"https://api.github.com/users/aidalgol/orgs","repos_url":"https://api.github.com/users/aidalgol/repos","events_url":"https://api.github.com/users/aidalgol/events{/privacy}","received_events_url":"https://api.github.com/users/aidalgol/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-11T04:00:10Z","updated_at":"2022-03-11T04:00:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nKrita 5 complains that it cannot find the G'Mic plugin.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Krita and the G'Mic plugin by adding `krita` and `gmic-qt-krita` to `environment.systemPackages` in `/etc/nixos/configuration.nix`\r\n2. Launch Krita\r\n3. Create a new image\r\n4. Select the menu item Filter→Start G'MIC-Qt\r\n5. Krita will complain, via a modal dialog, that it cannot load the plugin.\r\n6. Select the menu item Settings→Configure Krita…\r\n7. There should be a \"G’Mic plugin\" section in the left-hand sidebar, but there is not.\r\n\r\n### Expected behavior\r\nFor there to be a Krita setting to specify the path to the G'Mic plugin.\r\n\r\n### Additional context\r\nThe [Krita manual](https://docs.krita.org/en/reference_manual/preferences/g_mic_settings.html) explains the correct behaviour.\r\n\r\n### Notify maintainers\r\n@abbradar\r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.25, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(aidan): `\"nixpkgs-22.05pre355202.b66b39216b1\"`\r\n - channels(root): `\"nixos-21.11.336340.2ebb6c1e5ae, home-manager-21.11.tar.gz\"`\r\n - nixpkgs: `/home/aidan/.nix-defexpr/channels/nixpkgs\r\n ```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163645/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163643","id":1165954005,"node_id":"I_kwDOAEVQ_M5FfwvV","number":163643,"title":"Slack fails to install on Mac OS Monterey","user":{"login":"tylerlevine","id":23717670,"node_id":"MDQ6VXNlcjIzNzE3Njcw","avatar_url":"https://avatars.githubusercontent.com/u/23717670?v=4","gravatar_id":"","url":"https://api.github.com/users/tylerlevine","html_url":"https://github.com/tylerlevine","followers_url":"https://api.github.com/users/tylerlevine/followers","following_url":"https://api.github.com/users/tylerlevine/following{/other_user}","gists_url":"https://api.github.com/users/tylerlevine/gists{/gist_id}","starred_url":"https://api.github.com/users/tylerlevine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tylerlevine/subscriptions","organizations_url":"https://api.github.com/users/tylerlevine/orgs","repos_url":"https://api.github.com/users/tylerlevine/repos","events_url":"https://api.github.com/users/tylerlevine/events{/privacy}","received_events_url":"https://api.github.com/users/tylerlevine/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-11T03:20:44Z","updated_at":"2022-03-23T04:47:02Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Slack fails to install on Mac OS Monterey\r\nWhen attempting to install `slack`, installation fails with the following error:\r\n\r\n```\r\nerror: builder for '/nix/store/639ij43y08kbs7jp1x5nghg6sxzyad36-slack-4.23.0.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > unpacking sources\r\n > unpacking source archive /nix/store/1yxab68y3xf40gcia6zv3vbm7cvb0fsh-Slack-4.23.0-macOS.dmg\r\n > source root is Slack.app\r\n > patching sources\r\n > configuring\r\n > no configure script, doing nothing\r\n > building\r\n > no Makefile, doing nothing\r\n > installing\r\n > 2022-03-11 00:28:14.960 defaults[22350:333172] Unexpected argument YES; leaving defaults unchanged.\r\n For full logs, run 'nix log /nix/store/639ij43y08kbs7jp1x5nghg6sxzyad36-slack-4.23.0.drv'.\r\n```\r\n\r\nAs noted in https://github.com/NixOS/nixpkgs/pull/125051#discussion_r815383229, the call to `/usr/bin/defaults` is incorrectly using a capital B in the `-Bool` flag. It should be `-bool`.\r\n\r\nThe error coming from the `installPhase` matches the error when running the same `/usr/bin/defaults` command by itself:\r\n```\r\n/usr/bin/defaults write com.tinyspeck.slackmacgap SlackNoAutoUpdates -Bool YES\r\n2022-03-10 19:19:44.223 defaults[26087:398919] Unexpected argument YES; leaving defaults unchanged.\r\n```\r\n\r\nI searched for an existing issue which reports this, but didn't find any (aside from the comment linked earlier).\r\n\r\n### Steps To Reproduce\r\n```\r\n$ NIXPKGS_ALLOW_UNFREE=1 nix-env -iA nixpkgs.slack\r\ninstalling 'slack-4.23.0'\r\nthis derivation will be built:\r\n /nix/store/iflxk2dkbkjmdkffryqlkjsq654yy2nl-slack-4.23.0.drv\r\nthese 2 paths will be fetched (0.07 MiB download, 0.19 MiB unpacked):\r\n /nix/store/cn1kqfrayyc64vczry86a9q90yir6wvn-lzfse-1.0\r\n /nix/store/w8qn8lvm461n8g1n8zqlx25fcfdn602z-undmg-1.1.0\r\ncopying path '/nix/store/cn1kqfrayyc64vczry86a9q90yir6wvn-lzfse-1.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/w8qn8lvm461n8g1n8zqlx25fcfdn602z-undmg-1.1.0' from 'https://cache.nixos.org'...\r\nbuilding '/nix/store/iflxk2dkbkjmdkffryqlkjsq654yy2nl-slack-4.23.0.drv'...\r\nunpacking sources\r\nunpacking source archive /nix/store/1yxab68y3xf40gcia6zv3vbm7cvb0fsh-Slack-4.23.0-macOS.dmg\r\nsource root is Slack.app\r\npatching sources\r\nconfiguring\r\nno configure script, doing nothing\r\nbuilding\r\nno Makefile, doing nothing\r\ninstalling\r\n2022-03-11 03:10:56.193 defaults[26009:394028] Unexpected argument YES; leaving defaults unchanged.\r\nerror: builder for '/nix/store/iflxk2dkbkjmdkffryqlkjsq654yy2nl-slack-4.23.0.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > unpacking sources\r\n > unpacking source archive /nix/store/1yxab68y3xf40gcia6zv3vbm7cvb0fsh-Slack-4.23.0-macOS.dmg\r\n > source root is Slack.app\r\n > patching sources\r\n > configuring\r\n > no configure script, doing nothing\r\n > building\r\n > no Makefile, doing nothing\r\n > installing\r\n > 2022-03-11 03:10:56.193 defaults[26009:394028] Unexpected argument YES; leaving defaults unchanged.\r\n For full logs, run 'nix log /nix/store/iflxk2dkbkjmdkffryqlkjsq654yy2nl-slack-4.23.0.drv'.\r\n```\r\n\r\n### Expected behavior\r\nSlack is installed successfully.\r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\nN/A\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(tyler): `\"darwin\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163643/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163594","id":1165619478,"node_id":"I_kwDOAEVQ_M5FefEW","number":163594,"title":"Keepmenu","user":{"login":"stefanDeveloper","id":18898803,"node_id":"MDQ6VXNlcjE4ODk4ODAz","avatar_url":"https://avatars.githubusercontent.com/u/18898803?v=4","gravatar_id":"","url":"https://api.github.com/users/stefanDeveloper","html_url":"https://github.com/stefanDeveloper","followers_url":"https://api.github.com/users/stefanDeveloper/followers","following_url":"https://api.github.com/users/stefanDeveloper/following{/other_user}","gists_url":"https://api.github.com/users/stefanDeveloper/gists{/gist_id}","starred_url":"https://api.github.com/users/stefanDeveloper/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/stefanDeveloper/subscriptions","organizations_url":"https://api.github.com/users/stefanDeveloper/orgs","repos_url":"https://api.github.com/users/stefanDeveloper/repos","events_url":"https://api.github.com/users/stefanDeveloper/events{/privacy}","received_events_url":"https://api.github.com/users/stefanDeveloper/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-10T19:13:10Z","updated_at":"2022-03-26T14:35:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nFor i3 it is convenient to use `Dmenu` and `Rofi`, however it lacks of support for keepass databases.\r\n`Keepmenu` fully featured Dmenu/[Rofi](https://davedavenport.github.io/rofi/)/[Bemenu](https://github.com/Cloudef/bemenu) frontend for autotype and managing of Keepass databases.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/firecat53/keepmenu\r\n* source URL: https://github.com/firecat53/keepmenu\r\n* license: GPL-3.0 License \r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163594/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163590","id":1165578077,"node_id":"I_kwDOAEVQ_M5FeU9d","number":163590,"title":"mate-utils pulls inkscape to the system","user":{"login":"ilya-fedin","id":17829319,"node_id":"MDQ6VXNlcjE3ODI5MzE5","avatar_url":"https://avatars.githubusercontent.com/u/17829319?v=4","gravatar_id":"","url":"https://api.github.com/users/ilya-fedin","html_url":"https://github.com/ilya-fedin","followers_url":"https://api.github.com/users/ilya-fedin/followers","following_url":"https://api.github.com/users/ilya-fedin/following{/other_user}","gists_url":"https://api.github.com/users/ilya-fedin/gists{/gist_id}","starred_url":"https://api.github.com/users/ilya-fedin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ilya-fedin/subscriptions","organizations_url":"https://api.github.com/users/ilya-fedin/orgs","repos_url":"https://api.github.com/users/ilya-fedin/repos","events_url":"https://api.github.com/users/ilya-fedin/events{/privacy}","received_events_url":"https://api.github.com/users/ilya-fedin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-03-10T18:33:32Z","updated_at":"2022-03-10T20:45:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIt seems, inkscape is a build-only dependency of mate-utils, but wrapGAppHook makes it a runtime dependency\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install mate-utils\r\n\r\n### Expected behavior\r\nmate-utils doesn't pull inkscape\r\n\r\n### Notify maintainers\r\n@johannesloetzsch @romildo\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.8-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.7.0pre20220221_caf5172`\r\n - channels(root): `\"nixos-22.05pre338578.a2e281f5770\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163590/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163586","id":1165538623,"node_id":"I_kwDOAEVQ_M5FeLU_","number":163586,"title":"nixos manual: missing warning about firmware","user":{"login":"bgohla","id":49753283,"node_id":"MDQ6VXNlcjQ5NzUzMjgz","avatar_url":"https://avatars.githubusercontent.com/u/49753283?v=4","gravatar_id":"","url":"https://api.github.com/users/bgohla","html_url":"https://github.com/bgohla","followers_url":"https://api.github.com/users/bgohla/followers","following_url":"https://api.github.com/users/bgohla/following{/other_user}","gists_url":"https://api.github.com/users/bgohla/gists{/gist_id}","starred_url":"https://api.github.com/users/bgohla/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bgohla/subscriptions","organizations_url":"https://api.github.com/users/bgohla/orgs","repos_url":"https://api.github.com/users/bgohla/repos","events_url":"https://api.github.com/users/bgohla/events{/privacy}","received_events_url":"https://api.github.com/users/bgohla/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"assignees":[{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false}],"milestone":null,"comments":9,"created_at":"2022-03-10T17:52:00Z","updated_at":"2022-03-14T13:56:16Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"\r\nI followed the instructions in the installation section of the NixOs manual to install using the lustration method. I ended up with a bootable system, but no network access. This turned out to be due to missing firmware for my wifi card.\r\n\r\nAfter some trial and error I was able to figure out that adding\r\n```\r\n hardware.enableRedistributableFirmware = true;\r\n```\r\nto the generated `/etc/nixos/configuration.nix` is crucial for making the firmware drivers available for loading.\r\n\r\nI would submit a PR myself, but I am unsure which section it should be in, i.e., <https://nixos.org/manual/nixos/stable/index.html#sec-installing-from-other-distro> or further up.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163586/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163565","id":1165258782,"node_id":"I_kwDOAEVQ_M5FdHAe","number":163565,"title":"LXD is not using nftables","user":{"login":"Pascal-Vtx","id":75785316,"node_id":"MDQ6VXNlcjc1Nzg1MzE2","avatar_url":"https://avatars.githubusercontent.com/u/75785316?v=4","gravatar_id":"","url":"https://api.github.com/users/Pascal-Vtx","html_url":"https://github.com/Pascal-Vtx","followers_url":"https://api.github.com/users/Pascal-Vtx/followers","following_url":"https://api.github.com/users/Pascal-Vtx/following{/other_user}","gists_url":"https://api.github.com/users/Pascal-Vtx/gists{/gist_id}","starred_url":"https://api.github.com/users/Pascal-Vtx/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Pascal-Vtx/subscriptions","organizations_url":"https://api.github.com/users/Pascal-Vtx/orgs","repos_url":"https://api.github.com/users/Pascal-Vtx/repos","events_url":"https://api.github.com/users/Pascal-Vtx/events{/privacy}","received_events_url":"https://api.github.com/users/Pascal-Vtx/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-10T13:56:00Z","updated_at":"2022-03-14T10:21:28Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSince NixOS 21.11, nf_tables is used for iptables instead of xtables .\r\n\r\nLXD has two firewall drivers ( nftables and xtables ) but fails to detect nftables because the 'nft' command is missing in its environnement. As a fallback the xtables drivers is used.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. start LXD daemon with the --debug option\r\n2. check the logs for the Firewall detection messages\r\n\r\n```\r\nMar 10 11:59:07 nixos lxd[104034]: t=2022-03-10T11:59:07+0100 lvl=dbug msg=\"Firewall detected \\\"nftables\\\" incompatibility: Backend command \\\"nft\\\" missing\"\r\nMar 10 11:59:07 nixos lxd[104034]: t=2022-03-10T11:59:07+0100 lvl=dbug msg=\"Firewall detected \\\"xtables\\\" incompatibility: Backend command \\\"iptables\\\" is an nftables shim\"\r\nMar 10 11:59:07 nixos lxd[104034]: t=2022-03-10T11:59:07+0100 lvl=warn msg=\"Firewall failed to detect any compatible driver, falling back to \\\"xtables\\\" (but some features may not work as expected due to: Backend command \\\"iptables\\\" is an nftables shim)\"\r\nMar 10 11:59:07 nixos lxd[104034]: t=2022-03-10T11:59:07+0100 lvl=info msg=\"Firewall loaded driver\" driver=xtables\r\n```\r\n\r\n### Expected behavior\r\n\r\nLXD should use its nftables driver.\r\n\r\n```\r\nMar 10 12:10:38 nixos lxd[124616]: t=2022-03-10T12:10:38+0100 lvl=info msg=\"Firewall loaded driver\" driver=nftables\r\n```\r\n\r\n### Additional context\r\n\r\nI think that adding pkgs.nftables alongside iptables to the lxd wrapper should be a solution.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/8a0e1481346aeb374777aab0ea1f3fa50b934f3e/pkgs/tools/admin/lxd/default.nix#L40\r\n\r\n### Notify maintainers\r\n\r\n@fpletz \r\n@wucke13 \r\n@marsam\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.102, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336340.2ebb6c1e5ae\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163565/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163530","id":1164739870,"node_id":"I_kwDOAEVQ_M5FbIUe","number":163530,"title":"webkitgtk: Segfault when visiting specific page (possibly related to GStreamer)","user":{"login":"ninjin","id":354934,"node_id":"MDQ6VXNlcjM1NDkzNA==","avatar_url":"https://avatars.githubusercontent.com/u/354934?v=4","gravatar_id":"","url":"https://api.github.com/users/ninjin","html_url":"https://github.com/ninjin","followers_url":"https://api.github.com/users/ninjin/followers","following_url":"https://api.github.com/users/ninjin/following{/other_user}","gists_url":"https://api.github.com/users/ninjin/gists{/gist_id}","starred_url":"https://api.github.com/users/ninjin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ninjin/subscriptions","organizations_url":"https://api.github.com/users/ninjin/orgs","repos_url":"https://api.github.com/users/ninjin/repos","events_url":"https://api.github.com/users/ninjin/events{/privacy}","received_events_url":"https://api.github.com/users/ninjin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-10T04:31:14Z","updated_at":"2022-03-10T14:15:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nVisiting a specific homepage that contains audio (and most likely subtitles for said audio) causes WebKitGTK to segfault. To replicate, simply run:\r\n\r\n```console\r\n > nix-shell -p surf --run 'surf https://sive.rs/itunes'\r\n web process terminated: crashed\r\n /tmp/nix-shell-136635-0/rc: line 1: 136667 Segmentation fault (core dumped) surf https://sive.rs/itunes\r\n```\r\n\r\n### Additional context\r\n\r\nConfirmed working on Void Linux and causing a crash on Arch Linux. The latter will work if you install gst-plugins-bad, but I have tried the same on NixOS with no effect.\r\n\r\n```console\r\nMar 10 03:04:48 localhost kernel: .surf-wrapped[137046]: segfault at 570 ip 00007f55666bae94 sp 00007ffcc088f768 error 4 in libwebkit2gtk-4.0.so.37.55.9[7f5565b28000>\r\nMar 10 03:04:48 localhost kernel: Code: 84 00 00 00 00 00 48 8d 15 28 e0 31 02 48 8d 35 62 07 3b 02 31 ff e8 8b e8 a9 ff 31 c0 5b c3 0f 1f 80 00 00 00 00 48 8b 47 30>\r\nMar 10 03:04:48 localhost systemd[1]: Started Process Core Dump (PID 137103/UID 0).\r\nMar 10 03:04:49 localhost systemd-coredump[137104]: [🡕] Process 137046 (.surf-wrapped) of user 4711 dumped core.\r\n\r\n Found module linux-vdso.so.1 with build-id: 7f01a6eab4fe6ecc4ee62951c654a887e9c93c60\r\n Found module libgmp.so.10 without build-id.\r\n Found module libhogweed.so.6 without build-id.\r\n Found module libnettle.so.8 without build-id.\r\n Found module libgnutls.so.30 without build-id.\r\n Found module libgiognutls.so without build-id.\r\n Found module enchant_hspell.so without build-id.\r\n Found module libncursesw.so.6 without build-id.\r\n Found module libhunspell-1.7.so.0 without build-id.\r\n Found module enchant_hunspell.so without build-id.\r\n Found module enchant_aspell.so without build-id.\r\n Found module libudev.so.1 without build-id.\r\n Found module libuuid.so.1 without build-id.\r\n Found module libelf.so.1 with build-id: 0f60a8e8a31901ebf2128bb5e6bfd70402ddd9cd\r\n Found module libblkid.so.1 without build-id.\r\n Found module libbrotlicommon.so.1 without build-id.\r\n Found module libidn2.so.0 without build-id.\r\n Found module libunistring.so.2 without build-id.\r\n Found module libGLX.so.0 without build-id.\r\n Found module libdatrie.so.1 without build-id.\r\n Found module libjson-glib-1.0.so.0 without build-id.\r\n Found module libatspi.so.0 without build-id.\r\n Found module libdbus-1.so.3 without build-id.\r\n Found module libcap.so.2 without build-id.\r\n Found module liblz4.so.1 without build-id.\r\n Found module libzstd.so.1 without build-id.\r\n Found module liblzma.so.5 without build-id.\r\n Found module libgudev-1.0.so.0 without build-id.\r\n Found module libevdev.so.2 without build-id.\r\n Found module libICE.so.6 without build-id.\r\n Found module libSM.so.6 without build-id.\r\n Found module libaspell.so.15 without build-id.\r\n Found module libX11-xcb.so.1 without build-id.\r\n Found module liborc-0.4.so.0 without build-id.\r\n Found module libdw.so.1 with build-id: d3b425f1e6ed43ecf5df7a5cf68acbdf645d8361\r\n Found module libunwind.so.8 without build-id.\r\n Found module libexpat.so.1 without build-id.\r\n Found module libbz2.so.1 without build-id.\r\n Found module libwoff2common.so.1.0.2 without build-id.\r\n Found module libGLdispatch.so.0 without build-id.\r\n Found module libXdmcp.so.6 without build-id.\r\n Found module libXau.so.6 without build-id.\r\n Found module libpcre.so.1 without build-id.\r\n Found module libresolv.so.2 with build-id: 2290f42d057945d23e19da1c2a4038ad3a2bb317\r\n Found module libselinux.so.1 without build-id.\r\n Found module libmount.so.1 without build-id.\r\n Found module libbrotlidec.so.1 without build-id.\r\n Found module libpsl.so.5 without build-id.\r\n Found module libGL.so.1 without build-id.\r\n Found module libxcb-render.so.0 without build-id.\r\n Found module libxcb-shm.so.0 without build-id.\r\n Found module libpixman-1.so.0 with build-id: c99e1cd46146e3bc35180769096427021d346f2a\r\n Found module libgraphite2.so.3 without build-id.\r\n Found module libthai.so.0 without build-id.\r\n Found module libXinerama.so.1 without build-id.\r\n Found module libXrandr.so.2 without build-id.\r\n Found module libXcursor.so.1 without build-id.\r\n Found module libXext.so.6 without build-id.\r\n Found module libwayland-cursor.so.0 with build-id: 105e6251639db3944843a1ef4d225931a4edbd33\r\n Found module libxkbcommon.so.0 without build-id.\r\n Found module libXfixes.so.3 without build-id.\r\n Found module libtracker-sparql-3.0.so.0 without build-id.\r\n Found module libatk-bridge-2.0.so.0 without build-id.\r\n Found module libXi.so.6 without build-id.\r\n Found module libepoxy.so.0 without build-id.\r\n Found module libfribidi.so.0 without build-id.\r\n Found module libpangoft2-1.0.so.0 without build-id.\r\n Found module libgcc_s.so.1 without build-id.\r\n Found module libm.so.6 with build-id: e689d8c44e0981a60cbeb02ce80bfc33784b5946\r\n Found module libstdc++.so.6 without build-id.\r\n Found module libsystemd.so.0 without build-id.\r\n Found module libicuuc.so.70 without build-id.\r\n Found module libicui18n.so.70 without build-id.\r\n Found module libicudata.so.70 without build-id.\r\n Found module libseccomp.so.2 without build-id.\r\n Found module libmanette-0.2.so.0 without build-id.\r\n Found module libwayland-client.so.0 with build-id: 7c0f7566b764fb5f9d7778140b6bbca46ce507e9\r\n Found module libwayland-egl.so.1 with build-id: a231df0e1793b5ba43e3e088823ea4699b211f1e\r\n Found module libwayland-server.so.0 with build-id: ec40e0d92f5d5a8c8ab2f23403aaa3e538d1a1b4\r\n Found module liblcms2.so.2 without build-id.\r\n Found module libXt.so.6 without build-id.\r\n Found module libXrender.so.1 without build-id.\r\n Found module libXdamage.so.1 without build-id.\r\n Found module libXcomposite.so.1 without build-id.\r\n Found module libtasn1.so.6 without build-id.\r\n Found module libsecret-1.so.0 without build-id.\r\n Found module libgmodule-2.0.so.0 with build-id: be70d1c0aa0aec2365087e1e453bfb368706a31f\r\n Found module libenchant-2.so.2 without build-id.\r\n Found module libwebp.so.7 without build-id.\r\n Found module libwebpdemux.so.2 without build-id.\r\n Found module libopenjp2.so.7 without build-id.\r\n Found module libpng16.so.16 without build-id.\r\n Found module libjpeg.so.62 without build-id.\r\n Found module libgstfft-1.0.so.0 without build-id.\r\n Found module libgstgl-1.0.so.0 without build-id.\r\n Found module libgstvideo-1.0.so.0 without build-id.\r\n Found module libgsttag-1.0.so.0 without build-id.\r\n Found module libgstaudio-1.0.so.0 without build-id.\r\n Found module libgstpbutils-1.0.so.0 without build-id.\r\n Found module libgstreamer-1.0.so.0 without build-id.\r\n Found module libgstbase-1.0.so.0 without build-id.\r\n Found module libgstapp-1.0.so.0 without build-id.\r\n Found module libgpg-error.so.0 without build-id.\r\n Found module libharfbuzz-icu.so.0 without build-id.\r\n Found module libfreetype.so.6 without build-id.\r\n Found module libfontconfig.so.1 without build-id.\r\n Found module libwoff2dec.so.1.0.2 without build-id.\r\n Found module libGLESv2.so.2 without build-id.\r\n Found module libxslt.so.1 without build-id.\r\n Found module libsqlite3.so.0 with build-id: c75e8416550c1bbd1e4d5494e0020198301a613a\r\n Found module libxml2.so.2 without build-id.\r\n Found module libnotify.so.4 without build-id.\r\n Found module librt.so.1 with build-id: 402b3f3e14c4cd47e64a4a1a78de577fb923bb19\r\n Found module libEGL.so.1 without build-id.\r\n Found module ld-linux-x86-64.so.2 with build-id: e317665cf1fcd350c5dde8680273b9ebfda79b2e\r\n Found module libffi.so.8 without build-id.\r\n Found module libgcrypt.so.20 without build-id.\r\n Found module libpthread.so.0 with build-id: 8476567e4f6b5d1f48ca43f180475cb829fc5395\r\n Found module libdl.so.2 with build-id: bca5bcd55be4b127234c03637628eb0a57008dba\r\n Found module libxcb.so.1 without build-id.\r\n Found module libc.so.6 with build-id: 9a0f90c4bf283b50ccc2fb52a86c4c9e9e235f7b\r\n Found module libgthread-2.0.so.0 with build-id: 95f062e89e02028d56f3a22cb685bbe379981462\r\n Found module libglib-2.0.so.0 with build-id: ac1302d061e73370aaf031028e11d14c2a193bbb\r\n Found module libgobject-2.0.so.0 with build-id: 5dc61afb051a1d0ff409a2af30de521f51464dcf\r\n Found module libjavascriptcoregtk-4.0.so.18 with build-id: 5ac5b999f4d68cc938393b658894bf546b6b2467\r\n Found module libgio-2.0.so.0 with build-id: 3ccce5a13290641f0159072d201a7c0fdb337b0f\r\n Found module libsoup-2.4.so.1 without build-id.\r\n Found module libgdk_pixbuf-2.0.so.0 with build-id: 666cb6c61b9cfd9c5a4b4322c7d4a23f4a0d9437\r\n Found module libcairo.so.2 with build-id: abf7aabe83d5b846ee9940ea5d214ec275aa71a8\r\n Found module libcairo-gobject.so.2 with build-id: 44448161caf539e58baf941456090dd422a98b33\r\n Found module libatk-1.0.so.0 without build-id.\r\n Found module libharfbuzz.so.0 without build-id.\r\n Found module libpango-1.0.so.0 without build-id.\r\n Found module libpangocairo-1.0.so.0 without build-id.\r\n Found module libz.so.1 without build-id.\r\n Found module libgdk-3.so.0 with build-id: 9a54735cede5138b22b4cc2c8bb0c1fe8b538800\r\n Found module libgtk-3.so.0 with build-id: 6fc08bda77ef086c8dabe4c8a899ca7c4adfb8c7\r\n Found module libwebkit2gtk-4.0.so.37 with build-id: 5dd6508bb04640717f7bbd99cda2b5c80eeb318f\r\n Found module libp11-kit.so.0 without build-id.\r\n Found module libgck-1.so.0 without build-id.\r\n Found module libgcr-base-3.so.1 without build-id.\r\n Found module libgcr-ui-3.so.1 without build-id.\r\n Found module libX11.so.6 without build-id.\r\n Found module .surf-wrapped without build-id.\r\n Stack trace of thread 137046:\r\n #0 0x00007f55666bae94 _Z38webkitWebViewSetIsWebProcessResponsiveP14_WebKitWebViewb (libwebkit2gtk-4.0.so.37 + 0x>\r\n #1 0x00007f556668f91b _ZN16NavigationClient19processDidTerminateERN6WebKit12WebPageProxyENS0_24ProcessTerminatio>\r\n #2 0x00007f55665e6e6f _ZN6WebKit12WebPageProxy27dispatchProcessDidTerminateENS_24ProcessTerminationReasonE (libw>\r\n #3 0x00007f556661c680 _ZN6WebKit15WebProcessProxy35processDidTerminateOrFailedToLaunchENS_24ProcessTerminationRe>\r\n #4 0x00007f55664ddedb _ZN3WTF6Detail15CallableWrapperIZN3IPC10Connection18connectionDidCloseEvEUlvE_vJEE4callEv >\r\n #5 0x00007f5564892bc2 _ZN3WTF7RunLoop11performWorkEv (libjavascriptcoregtk-4.0.so.18 + 0x178bbc2)\r\n #6 0x00007f55648f5d89 _ZZN3WTF7RunLoopC4EvENUlPvE_4_FUNES1_ (libjavascriptcoregtk-4.0.so.18 + 0x17eed89)\r\n #7 0x00007f55648f675f _ZN3WTF7RunLoopUlP8_GSourcePFiPvES3_E_4_FUNES2_S5_S3_ (libjavascriptcoregtk-4.0.so.18 + 0x>\r\n #8 0x00007f5562fc89af g_main_context_dispatch (libglib-2.0.so.0 + 0x569af)\r\n #9 0x00007f5562fc8d58 g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56d58)\r\n #10 0x00007f5562fc904b g_main_loop_run (libglib-2.0.so.0 + 0x5704b)\r\n #11 0x00007f5565554235 gtk_main (libgtk-3.so.0 + 0x1fb235)\r\n #12 0x0000000000409781 main (.surf-wrapped + 0x9781)\r\n #13 0x00007f5562dbf790 __libc_start_main (libc.so.6 + 0x27790)\r\n #14 0x0000000000405d5a _start (.surf-wrapped + 0x5d5a)\r\n\r\n Stack trace of thread 137048:\r\n #0 0x00007f5562d59cf5 __futex_abstimed_wait_common64 (libpthread.so.0 + 0x14cf5)\r\n #1 0x00007f5562d53c22 pthread_cond_wait@@GLIBC_2.3.2 (libpthread.so.0 + 0xec22)\r\n #2 0x00007f555fc4873c _ZNSt18condition_variable4waitERSt11unique_lockISt5mutexE (libstdc++.so.6 + 0xd173c)\r\n #3 0x00007f55649069b9 _ZN7bmalloc9Scavenger13threadRunLoopEv (libjavascriptcoregtk-4.0.so.18 + 0x17ff9b9)\r\n #4 0x00007f5564906cc9 _ZN7bmalloc9Scavenger16threadEntryPointEPS0_ (libjavascriptcoregtk-4.0.so.18 + 0x17ffcc9)\r\n #5 0x00007f555fc4dc50 n/a (libstdc++.so.6 + 0xd6c50)\r\n #6 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #7 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137049:\r\n #0 0x00007f5562d59cf5 __futex_abstimed_wait_common64 (libpthread.so.0 + 0x14cf5)\r\n #1 0x00007f5562d53ed8 pthread_cond_timedwait@@GLIBC_2.3.2 (libpthread.so.0 + 0xeed8)\r\n #2 0x00007f55648f949b _ZN3WTF15ThreadCondition9timedWaitERNS_5MutexENS_8WallTimeE (libjavascriptcoregtk-4.0.so.1>\r\n #3 0x00007f556488fc33 _ZN3WTF10ParkingLot21parkConditionallyImplEPKvRKNS_12ScopedLambdaIFbvEEERKNS3_IFvvEEERKNS_>\r\n #4 0x00007f55648939ec _ZN3WTF5sleepENS_7SecondsE (libjavascriptcoregtk-4.0.so.18 + 0x178c9ec)\r\n #5 0x00007f5566780e8a _ZZN6WebKit21MemoryPressureMonitor5startEvENKUlvE_clEv.constprop.0 (libwebkit2gtk-4.0.so.3>\r\n #6 0x00007f55667815a9 _ZN3WTF6Detail15CallableWrapperIZN6WebKit21MemoryPressureMonitor5startEvEUlvE_vJEE4callEv >\r\n #7 0x00007f55648949c3 _ZN3WTF6Thread10entryPointEPNS0_16NewThreadContextE (libjavascriptcoregtk-4.0.so.18 + 0x17>\r\n #8 0x00007f55648f8b99 _ZN3WTFL19wtfThreadEntryPointEPv (libjavascriptcoregtk-4.0.so.18 + 0x17f1b99)\r\n #9 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #10 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137053:\r\n #0 0x00007f5562e88c89 __poll (libc.so.6 + 0xf0c89)\r\n #1 0x00007f5562fc8cee g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56cee)\r\n #2 0x00007f5562fc8e0f g_main_context_iteration (libglib-2.0.so.0 + 0x56e0f)\r\n #3 0x00007f5562fc8e61 glib_worker_main (libglib-2.0.so.0 + 0x56e61)\r\n #4 0x00007f5562ff2d7d g_thread_proxy (libglib-2.0.so.0 + 0x80d7d)\r\n #5 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #6 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137062:\r\n #0 0x00007f5562e88c89 __poll (libc.so.6 + 0xf0c89)\r\n #1 0x00007f5562fc8cee g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56cee)\r\n #2 0x00007f5562fc904b g_main_loop_run (libglib-2.0.so.0 + 0x5704b)\r\n #3 0x00007f55648f68a8 _ZN3WTF7RunLoop3runEv (libjavascriptcoregtk-4.0.so.18 + 0x17ef8a8)\r\n #4 0x00007f55648949c3 _ZN3WTF6Thread10entryPointEPNS0_16NewThreadContextE (libjavascriptcoregtk-4.0.so.18 + 0x17>\r\n #5 0x00007f55648f8b99 _ZN3WTFL19wtfThreadEntryPointEPv (libjavascriptcoregtk-4.0.so.18 + 0x17f1b99)\r\n #6 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #7 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137050:\r\n #0 0x00007f5562e88c89 __poll (libc.so.6 + 0xf0c89)\r\n #1 0x00007f5562fc8cee g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56cee)\r\n #2 0x00007f5562fc904b g_main_loop_run (libglib-2.0.so.0 + 0x5704b)\r\n #3 0x00007f55648f68a8 _ZN3WTF7RunLoop3runEv (libjavascriptcoregtk-4.0.so.18 + 0x17ef8a8)\r\n #4 0x00007f55648949c3 _ZN3WTF6Thread10entryPointEPNS0_16NewThreadContextE (libjavascriptcoregtk-4.0.so.18 + 0x17>\r\n #5 0x00007f55648f8b99 _ZN3WTFL19wtfThreadEntryPointEPv (libjavascriptcoregtk-4.0.so.18 + 0x17f1b99)\r\n #6 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #7 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137055:\r\n #0 0x00007f5562e8dac9 syscall (libc.so.6 + 0xf5ac9)\r\n #1 0x00007f556301c472 g_cond_wait_until (libglib-2.0.so.0 + 0xaa472)\r\n #2 0x00007f5562f97621 g_async_queue_pop_intern_unlocked (libglib-2.0.so.0 + 0x25621)\r\n #3 0x00007f5562ff379a g_thread_pool_thread_proxy (libglib-2.0.so.0 + 0x8179a)\r\n #4 0x00007f5562ff2d7d g_thread_proxy (libglib-2.0.so.0 + 0x80d7d)\r\n #5 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #6 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137061:\r\n #0 0x00007f5562e88c89 __poll (libc.so.6 + 0xf0c89)\r\n #1 0x00007f5562fc8cee g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56cee)\r\n #2 0x00007f5562fc904b g_main_loop_run (libglib-2.0.so.0 + 0x5704b)\r\n #3 0x00007f55648f68a8 _ZN3WTF7RunLoop3runEv (libjavascriptcoregtk-4.0.so.18 + 0x17ef8a8)\r\n #4 0x00007f55648949c3 _ZN3WTF6Thread10entryPointEPNS0_16NewThreadContextE (libjavascriptcoregtk-4.0.so.18 + 0x17>\r\n #5 0x00007f55648f8b99 _ZN3WTFL19wtfThreadEntryPointEPv (libjavascriptcoregtk-4.0.so.18 + 0x17f1b99)\r\n #6 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #7 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\n\r\n Stack trace of thread 137051:\r\n #0 0x00007f5562e88c89 __poll (libc.so.6 + 0xf0c89)\r\n #1 0x00007f5562fc8cee g_main_context_iterate.constprop.0 (libglib-2.0.so.0 + 0x56cee)\r\n #2 0x00007f5562fc904b g_main_loop_run (libglib-2.0.so.0 + 0x5704b)\r\n #3 0x00007f55648f68a8 _ZN3WTF7RunLoop3runEv (libjavascriptcoregtk-4.0.so.18 + 0x17ef8a8)\r\n #4 0x00007f55648949c3 _ZN3WTF6Thread10entryPointEPNS0_16NewThreadContextE (libjavascriptcoregtk-4.0.so.18 + 0x17>\r\n #5 0x00007f55648f8b99 _ZN3WTFL19wtfThreadEntryPointEPv (libjavascriptcoregtk-4.0.so.18 + 0x17f1b99)\r\n #6 0x00007f5562d4dd40 start_thread (libpthread.so.0 + 0x8d40)\r\n #7 0x00007f5562e9403f __clone (libc.so.6 + 0xfc03f)\r\nMar 10 03:04:49 localhost systemd[1]: systemd-coredump@31-137103-0.service: Deactivated successfully.\r\n```\r\n\r\nAlso confirmed to segfault with the current tip of `master`.\r\n\r\n### Notify maintainers\r\n\r\n@hedning, @jtojnar, @dasj19, and @maxeaubrey for WebKitGTK and @joachifm for surf (although I think surf has nothing to do with the crash from reading the code and my preliminary debugging).\r\n\r\n### Metadata\r\n\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.103, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336340.2ebb6c1e5ae, home-manager-21.11, nixos-unstable-22.05pre358986.062a0c5437b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163530/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163515","id":1164544023,"node_id":"I_kwDOAEVQ_M5FaYgX","number":163515,"title":"fluffychat: 1.3.0","user":{"login":"genofire","id":6905586,"node_id":"MDQ6VXNlcjY5MDU1ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6905586?v=4","gravatar_id":"","url":"https://api.github.com/users/genofire","html_url":"https://github.com/genofire","followers_url":"https://api.github.com/users/genofire/followers","following_url":"https://api.github.com/users/genofire/following{/other_user}","gists_url":"https://api.github.com/users/genofire/gists{/gist_id}","starred_url":"https://api.github.com/users/genofire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/genofire/subscriptions","organizations_url":"https://api.github.com/users/genofire/orgs","repos_url":"https://api.github.com/users/genofire/repos","events_url":"https://api.github.com/users/genofire/events{/privacy}","received_events_url":"https://api.github.com/users/genofire/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"mkg20001","id":7735145,"node_id":"MDQ6VXNlcjc3MzUxNDU=","avatar_url":"https://avatars.githubusercontent.com/u/7735145?v=4","gravatar_id":"","url":"https://api.github.com/users/mkg20001","html_url":"https://github.com/mkg20001","followers_url":"https://api.github.com/users/mkg20001/followers","following_url":"https://api.github.com/users/mkg20001/following{/other_user}","gists_url":"https://api.github.com/users/mkg20001/gists{/gist_id}","starred_url":"https://api.github.com/users/mkg20001/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mkg20001/subscriptions","organizations_url":"https://api.github.com/users/mkg20001/orgs","repos_url":"https://api.github.com/users/mkg20001/repos","events_url":"https://api.github.com/users/mkg20001/events{/privacy}","received_events_url":"https://api.github.com/users/mkg20001/received_events","type":"User","site_admin":false},"assignees":[{"login":"mkg20001","id":7735145,"node_id":"MDQ6VXNlcjc3MzUxNDU=","avatar_url":"https://avatars.githubusercontent.com/u/7735145?v=4","gravatar_id":"","url":"https://api.github.com/users/mkg20001","html_url":"https://github.com/mkg20001","followers_url":"https://api.github.com/users/mkg20001/followers","following_url":"https://api.github.com/users/mkg20001/following{/other_user}","gists_url":"https://api.github.com/users/mkg20001/gists{/gist_id}","starred_url":"https://api.github.com/users/mkg20001/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mkg20001/subscriptions","organizations_url":"https://api.github.com/users/mkg20001/orgs","repos_url":"https://api.github.com/users/mkg20001/repos","events_url":"https://api.github.com/users/mkg20001/events{/privacy}","received_events_url":"https://api.github.com/users/mkg20001/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-03-09T23:17:12Z","updated_at":"2022-03-09T23:25:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name:\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.2.0\r\ndesired version: 1.3.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @mkg20001\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163515/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163506","id":1164469324,"node_id":"I_kwDOAEVQ_M5FaGRM","number":163506,"title":"Package for clever-tools","user":{"login":"JalilArfaoui","id":3037833,"node_id":"MDQ6VXNlcjMwMzc4MzM=","avatar_url":"https://avatars.githubusercontent.com/u/3037833?v=4","gravatar_id":"","url":"https://api.github.com/users/JalilArfaoui","html_url":"https://github.com/JalilArfaoui","followers_url":"https://api.github.com/users/JalilArfaoui/followers","following_url":"https://api.github.com/users/JalilArfaoui/following{/other_user}","gists_url":"https://api.github.com/users/JalilArfaoui/gists{/gist_id}","starred_url":"https://api.github.com/users/JalilArfaoui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/JalilArfaoui/subscriptions","organizations_url":"https://api.github.com/users/JalilArfaoui/orgs","repos_url":"https://api.github.com/users/JalilArfaoui/repos","events_url":"https://api.github.com/users/JalilArfaoui/events{/privacy}","received_events_url":"https://api.github.com/users/JalilArfaoui/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-09T21:39:45Z","updated_at":"2022-03-09T21:39:45Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nThis is the CLI for https://www.clever-cloud.com/\r\n\r\nDerivation is already working here it seems : https://github.com/fretlink/clever-tools-nix\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.clever-cloud.com/\r\n* source URL: https://github.com/CleverCloud/clever-tools\r\n* license: Apache 2.0\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163506/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163478","id":1164239973,"node_id":"I_kwDOAEVQ_M5FZORl","number":163478,"title":"Jetbrains Gateway client support","user":{"login":"DAlperin","id":16063713,"node_id":"MDQ6VXNlcjE2MDYzNzEz","avatar_url":"https://avatars.githubusercontent.com/u/16063713?v=4","gravatar_id":"","url":"https://api.github.com/users/DAlperin","html_url":"https://github.com/DAlperin","followers_url":"https://api.github.com/users/DAlperin/followers","following_url":"https://api.github.com/users/DAlperin/following{/other_user}","gists_url":"https://api.github.com/users/DAlperin/gists{/gist_id}","starred_url":"https://api.github.com/users/DAlperin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/DAlperin/subscriptions","organizations_url":"https://api.github.com/users/DAlperin/orgs","repos_url":"https://api.github.com/users/DAlperin/repos","events_url":"https://api.github.com/users/DAlperin/events{/privacy}","received_events_url":"https://api.github.com/users/DAlperin/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-09T17:33:40Z","updated_at":"2022-04-28T23:05:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nJetbrains Gateway client allows you to connect local jetbrains editors to remote instances.\r\n\r\nI've opened a thread on the discourse to see if anyone has already packaged this somewhere: https://discourse.nixos.org/t/jetbrains-gateway-client-support-on-nixos/18108\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.jetbrains.com/remote-development/gateway/\r\n* source URL: N/A\r\n* license: unfree\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163478/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163398","id":1163353291,"node_id":"I_kwDOAEVQ_M5FV1zL","number":163398,"title":"masterpdfeditor aarch64-linux","user":{"login":"YangtseSu","id":650328,"node_id":"MDQ6VXNlcjY1MDMyOA==","avatar_url":"https://avatars.githubusercontent.com/u/650328?v=4","gravatar_id":"","url":"https://api.github.com/users/YangtseSu","html_url":"https://github.com/YangtseSu","followers_url":"https://api.github.com/users/YangtseSu/followers","following_url":"https://api.github.com/users/YangtseSu/following{/other_user}","gists_url":"https://api.github.com/users/YangtseSu/gists{/gist_id}","starred_url":"https://api.github.com/users/YangtseSu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/YangtseSu/subscriptions","organizations_url":"https://api.github.com/users/YangtseSu/orgs","repos_url":"https://api.github.com/users/YangtseSu/repos","events_url":"https://api.github.com/users/YangtseSu/events{/privacy}","received_events_url":"https://api.github.com/users/YangtseSu/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-09T00:26:06Z","updated_at":"2022-03-09T00:26:06Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nMaster PDF Editor\r\nSupport aarch64 since 5.8.33\r\n\r\n**Metadata**\r\n\r\n* homepage URL:https://code-industry.net/free-pdf-editor/\r\n* source URL:https://code-industry.net/free-pdf-editor/\r\n* license: Unfree redistributable\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163398/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163387","id":1163256346,"node_id":"I_kwDOAEVQ_M5FVeIa","number":163387,"title":"glide: (glide-player) package request: rust gstreamer CLI video player","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":333381548,"node_id":"MDU6TGFiZWwzMzMzODE1NDg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20rust","name":"6.topic: rust","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-08T23:00:17Z","updated_at":"2022-04-19T19:11:57Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\n* https://github.com/philn/glide\r\n* \"Linux/macOS media player based on GStreamer and GTK\"\r\n* gstreamer\r\n* rust\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/philn/glide\r\n* source URL: https://github.com/philn/glide\r\n* license: MIT\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163387/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163376","id":1163109673,"node_id":"I_kwDOAEVQ_M5FU6Up","number":163376,"title":"please add package for gnu/stubs-32.h","user":{"login":"FrancescoSpena","id":93486076,"node_id":"U_kgDOBZJ7_A","avatar_url":"https://avatars.githubusercontent.com/u/93486076?v=4","gravatar_id":"","url":"https://api.github.com/users/FrancescoSpena","html_url":"https://github.com/FrancescoSpena","followers_url":"https://api.github.com/users/FrancescoSpena/followers","following_url":"https://api.github.com/users/FrancescoSpena/following{/other_user}","gists_url":"https://api.github.com/users/FrancescoSpena/gists{/gist_id}","starred_url":"https://api.github.com/users/FrancescoSpena/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FrancescoSpena/subscriptions","organizations_url":"https://api.github.com/users/FrancescoSpena/orgs","repos_url":"https://api.github.com/users/FrancescoSpena/repos","events_url":"https://api.github.com/users/FrancescoSpena/events{/privacy}","received_events_url":"https://api.github.com/users/FrancescoSpena/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-03-08T20:54:54Z","updated_at":"2022-03-10T03:50:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\n\r\n**Metadata**\r\n\r\n* homepage URL:\r\n* source URL:\r\n* license: mit, bsd, gpl2+ , ...\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163376/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163363","id":1162998628,"node_id":"I_kwDOAEVQ_M5FUfNk","number":163363,"title":"Packaging request: bump version for clang-tool from 13 to 14","user":{"login":"lednakashim","id":1728530,"node_id":"MDQ6VXNlcjE3Mjg1MzA=","avatar_url":"https://avatars.githubusercontent.com/u/1728530?v=4","gravatar_id":"","url":"https://api.github.com/users/lednakashim","html_url":"https://github.com/lednakashim","followers_url":"https://api.github.com/users/lednakashim/followers","following_url":"https://api.github.com/users/lednakashim/following{/other_user}","gists_url":"https://api.github.com/users/lednakashim/gists{/gist_id}","starred_url":"https://api.github.com/users/lednakashim/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lednakashim/subscriptions","organizations_url":"https://api.github.com/users/lednakashim/orgs","repos_url":"https://api.github.com/users/lednakashim/repos","events_url":"https://api.github.com/users/lednakashim/events{/privacy}","received_events_url":"https://api.github.com/users/lednakashim/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-08T18:45:43Z","updated_at":"2022-03-08T18:45:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Looks like clang14 is available but it would be good to have a matching version of the clang-tools package (which is on the previous version)\r\n\r\nhttps://search.nixos.org/packages?channel=unstable&from=0&size=50&sort=relevance&type=packages&query=clang-tools","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163363/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163345","id":1162815336,"node_id":"I_kwDOAEVQ_M5FTydo","number":163345,"title":"nwg-shell nixos option","user":{"login":"Narice","id":31109099,"node_id":"MDQ6VXNlcjMxMTA5MDk5","avatar_url":"https://avatars.githubusercontent.com/u/31109099?v=4","gravatar_id":"","url":"https://api.github.com/users/Narice","html_url":"https://github.com/Narice","followers_url":"https://api.github.com/users/Narice/followers","following_url":"https://api.github.com/users/Narice/following{/other_user}","gists_url":"https://api.github.com/users/Narice/gists{/gist_id}","starred_url":"https://api.github.com/users/Narice/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Narice/subscriptions","organizations_url":"https://api.github.com/users/Narice/orgs","repos_url":"https://api.github.com/users/Narice/repos","events_url":"https://api.github.com/users/Narice/events{/privacy}","received_events_url":"https://api.github.com/users/Narice/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-08T15:45:14Z","updated_at":"2022-03-08T15:45:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"It would be nice to have a simple way to install the [nwg-shell](https://github.com/nwg-piotr/nwg-shell) environment on nixos.\r\nIt is from what I see so far the most advanced sway 'Desktop Environment'.\r\nIt looks straightforward, stable and consistant.\r\nSome parts are already packaged in nixpkgs which should hopefully help in creating the nixos option.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163345/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163299","id":1162471081,"node_id":"I_kwDOAEVQ_M5FSeap","number":163299,"title":"Request Xtreme Download Manager newer version","user":{"login":"bastomiadi","id":13336571,"node_id":"MDQ6VXNlcjEzMzM2NTcx","avatar_url":"https://avatars.githubusercontent.com/u/13336571?v=4","gravatar_id":"","url":"https://api.github.com/users/bastomiadi","html_url":"https://github.com/bastomiadi","followers_url":"https://api.github.com/users/bastomiadi/followers","following_url":"https://api.github.com/users/bastomiadi/following{/other_user}","gists_url":"https://api.github.com/users/bastomiadi/gists{/gist_id}","starred_url":"https://api.github.com/users/bastomiadi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bastomiadi/subscriptions","organizations_url":"https://api.github.com/users/bastomiadi/orgs","repos_url":"https://api.github.com/users/bastomiadi/repos","events_url":"https://api.github.com/users/bastomiadi/events{/privacy}","received_events_url":"https://api.github.com/users/bastomiadi/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-08T10:16:45Z","updated_at":"2022-03-08T10:21:28Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nRequest Xtreme Download Manager 2020 Version 7.2.11\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://xtremedownloadmanager.com/\r\n* source URL: https://github.com/subhra74/xdm/releases/download/7.2.11/xdm-setup-7.2.11.tar.xz\r\n* license: gpl2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163299/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163298","id":1162463554,"node_id":"I_kwDOAEVQ_M5FSclC","number":163298,"title":"nvidia drivers doesn't load with update to linux 5.16.12","user":{"login":"marius851000","id":22586596,"node_id":"MDQ6VXNlcjIyNTg2NTk2","avatar_url":"https://avatars.githubusercontent.com/u/22586596?v=4","gravatar_id":"","url":"https://api.github.com/users/marius851000","html_url":"https://github.com/marius851000","followers_url":"https://api.github.com/users/marius851000/followers","following_url":"https://api.github.com/users/marius851000/following{/other_user}","gists_url":"https://api.github.com/users/marius851000/gists{/gist_id}","starred_url":"https://api.github.com/users/marius851000/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/marius851000/subscriptions","organizations_url":"https://api.github.com/users/marius851000/orgs","repos_url":"https://api.github.com/users/marius851000/repos","events_url":"https://api.github.com/users/marius851000/events{/privacy}","received_events_url":"https://api.github.com/users/marius851000/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-08T10:09:51Z","updated_at":"2022-03-10T03:48:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use the nvidia driver\r\n2. Set ``boot.kernelPackages = pkgs.linuxPackages_latest;``\r\n3. Use nixpkgs revision ``b61740b76d45e5af5ebf21a26f917684c90244b3``\r\n4. rebuild the system, and reboot\r\n5. It will not load the graphical session\r\n\r\n### Expected behavior\r\nIt open the gdm, to ask the password and start the X11 or wayland session.\r\n\r\n### Additional context\r\nThe service ``systemd-modules-load.service`` timeout.\r\nIt normally display\r\n```\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'kvm_amd'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'bridge'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'macvlan'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'tap'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'tun'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'loop'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'ctr'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'nf_nat_ftp'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'msr'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'nvidia_uvm'\r\nmars 08 10:15:03 marius-nixos systemd-modules-load[593]: Inserted module 'nvidia_modeset'\r\nmars 08 10:15:04 marius-nixos systemd-modules-load[593]: Inserted module 'nvidia_drm'\r\nmars 08 10:15:04 marius-nixos systemd[1]: Finished Load Kernel Modules.\r\nmars 08 10:38:05 marius-nixos systemd[1]: systemd-modules-load.service: Deactivated successfully.\r\nmars 08 10:38:05 marius-nixos systemd[1]: Stopped Load Kernel Modules.\r\n```\r\n\r\nBut now fails with\r\n\r\n```\r\nmars 08 10:54:16 marius-nixos systemd-modules-load[590]: Inserted module 'kvm_amd'\r\nmars 08 10:54:16 marius-nixos systemd-modules-load[590]: Inserted module 'bridge'\r\nmars 08 10:54:16 marius-nixos systemd-modules-load[590]: Inserted module 'macvlan'\r\nmars 08 10:54:16 marius-nixos systemd-modules-load[590]: Inserted module 'tap'\r\nmars 08 10:54:16 marius-nixos systemd-modules-load[590]: Inserted module 'tun'\r\nmars 08 10:54:17 marius-nixos systemd-modules-load[590]: Inserted module 'loop'\r\nmars 08 10:54:17 marius-nixos systemd-modules-load[590]: Inserted module 'ctr'\r\nmars 08 10:54:17 marius-nixos systemd-modules-load[590]: Inserted module 'nf_nat_ftp'\r\nmars 08 10:54:17 marius-nixos systemd-modules-load[590]: Inserted module 'msr'\r\nmars 08 10:54:17 marius-nixos systemd[1]: systemd-modules-load.service: Main process exited, code=killed, status=9/KILL\r\nmars 08 10:54:17 marius-nixos systemd[1]: systemd-modules-load.service: Failed with result 'signal'.\r\nmars 08 10:54:17 marius-nixos systemd[1]: Failed to start Load Kernel Modules.\r\n```\r\n\r\nAnd so, I suspected it due to the nvidia driver, that follow the ``msr`` driver in the standard load order.\r\n\r\nBisection showed this started to happen at b61740b76d45e5af5ebf21a26f917684c90244b3 (at PR #162481)\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220221_caf5172`\r\n - channels(root): `\"\"`\r\n - channels(marius): `\"home-manager, mariusnur, mlpnur, nixos, nixpkgs, nur, ricenur\"`\r\n - nixpkgs: `/home/marius/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163298/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163294","id":1162444156,"node_id":"I_kwDOAEVQ_M5FSX18","number":163294,"title":"NVIDIA v495.x driver spamming dbus-messages","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-08T09:50:48Z","updated_at":"2022-03-27T02:39:56Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe nvidia driver is spamming this message over and over again when an OpenGL or Vulkan application is running (e.g. GNOME).\r\n\r\n```\r\nerror time=1646729515.683120 sender=org.freedesktop.DBus -> destination=:1.57 error_name=org.freedesktop.DBus.Error.ServiceUnknown reply_serial=2650\r\n string \"The name nvidia.powerd.server was not provided by any .service files\"\r\nmethod call time=1646729515.719864 sender=:1.57 -> destination=nvidia.powerd.server serial=2651 path=/nvidia/powerd/datapacket; interface=nvidia.powerd.datapacket; member=AutoflDatapacket\r\n struct {\r\n int32 4209\r\n int32 804341\r\n int64 293738006064\r\n double 1.93322e+19\r\n double 2.45137e+28\r\n double 1.66595e+31\r\n double 4.63853e-310\r\n int32 21859\r\n int32 21860\r\n }\r\n```\r\n\r\nAfter some time, the journal is also spammed with this error:\r\n\r\n```\r\ndbus-daemon[1023]: [system] Rejected: destination has a full message queue, 0 matched rules; type=\"error\", sender=\"(unset)\" ((bus)) interface=\"(unset)\" member=\"(unset)\" error name=\"org.freedesktop.DBus.Error.ServiceUnknown\" requested_reply=\"1\" destination=\":1.470\" (uid=1000 pid=220506 comm=\"/run/current-system/sw/bin/gala \" label=\"kernel\")\r\n```\r\n\r\nMaking the system unstable. My Pantheon session crashed.\r\n\r\nIt is a known issue: https://forums.developer.nvidia.com/t/bug-nvidia-v495-29-05-driver-spamming-dbus-enabled-applications-with-invalid-messages/192892\r\n\r\nIt should be fixed with 510.xx (beta) driver:\r\n\r\n>Fixed a bug which caused OpenGL and Vulkan applications to generate excessive traffic over dbus while attempting to communicate with nvidia-powerd, even though nvidia-powerd was not running.\r\n\r\nhttps://www.nvidia.com/Download/driverResults.aspx/184911/en-us\r\n\r\nOur beta version is behind stable, so i can't test the fix.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/4f0c8d0512503ff15a0894cf81eb68c536b78aac/pkgs/os-specific/linux/nvidia-x11/default.nix#L29-L34\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. use nvidia GPU and driver\r\n2. start OpenGL application\r\n3. `sudo dbus-monitor --system`\r\n\r\n### Expected behavior\r\nStable system, no errors or crashes\r\n\r\n### Additional context\r\nnvidia sucks, use amd instead\r\n\r\n### Notify maintainers\r\nThe nvidia driver has no maintainer :grimacing:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/4f0c8d0512503ff15a0894cf81eb68c536b78aac/pkgs/os-specific/linux/nvidia-x11/generic.nix#L117\r\n\r\n### Metadata\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.335443.e84444b14cc, nixos-hardware, nixos-unstable-22.05pre347947.689b76bcf36\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163294/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163263","id":1162239994,"node_id":"I_kwDOAEVQ_M5FRl_6","number":163263,"title":"Can't install `docker-compose` python package into `site-packages`","user":{"login":"erahhal","id":1174130,"node_id":"MDQ6VXNlcjExNzQxMzA=","avatar_url":"https://avatars.githubusercontent.com/u/1174130?v=4","gravatar_id":"","url":"https://api.github.com/users/erahhal","html_url":"https://github.com/erahhal","followers_url":"https://api.github.com/users/erahhal/followers","following_url":"https://api.github.com/users/erahhal/following{/other_user}","gists_url":"https://api.github.com/users/erahhal/gists{/gist_id}","starred_url":"https://api.github.com/users/erahhal/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/erahhal/subscriptions","organizations_url":"https://api.github.com/users/erahhal/orgs","repos_url":"https://api.github.com/users/erahhal/repos","events_url":"https://api.github.com/users/erahhal/events{/privacy}","received_events_url":"https://api.github.com/users/erahhal/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-08T05:33:42Z","updated_at":"2022-03-10T03:48:16Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`docker-compose` python packages is not installed as part of `site-packages`\r\n\r\n### Steps To Reproduce\r\n1. Add the following to config:\r\n```\r\nenvironment.systemPackages = [\r\n (let\r\n my-python3-packages = python3-packages: with python3-packages; [\r\n docker\r\n docker-compose\r\n pyyaml\r\n requests\r\n ];\r\n python3-with-my-packages = python3.withPackages my-python3-packages;\r\n in\r\n python3-with-my-packages)\r\n];\r\n```\r\n2. Note that all packages except `docker-compose` are in `site-packages`\r\n3. Note that python scripts can import all modules except `compose`\r\n\r\n### Expected behavior\r\n`docker-compose`'s `compose` module should be in `site-packages`\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"` \r\n - host os: `Linux 5.15.24, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes` \r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1` \r\n - nixpkgs: `/nix/store/d9wpzgyjlpw1424kw2lyilah6690fnk3-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163263/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163258","id":1162221680,"node_id":"I_kwDOAEVQ_M5FRhhw","number":163258,"title":"can't install mysql-workbench because dependency used older python","user":{"login":"bastomiadi","id":13336571,"node_id":"MDQ6VXNlcjEzMzM2NTcx","avatar_url":"https://avatars.githubusercontent.com/u/13336571?v=4","gravatar_id":"","url":"https://api.github.com/users/bastomiadi","html_url":"https://github.com/bastomiadi","followers_url":"https://api.github.com/users/bastomiadi/followers","following_url":"https://api.github.com/users/bastomiadi/following{/other_user}","gists_url":"https://api.github.com/users/bastomiadi/gists{/gist_id}","starred_url":"https://api.github.com/users/bastomiadi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bastomiadi/subscriptions","organizations_url":"https://api.github.com/users/bastomiadi/orgs","repos_url":"https://api.github.com/users/bastomiadi/repos","events_url":"https://api.github.com/users/bastomiadi/events{/privacy}","received_events_url":"https://api.github.com/users/bastomiadi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-08T05:00:50Z","updated_at":"2022-04-03T22:12:58Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nError when building mysql-workbench\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. add mysql-workbench in : sudo nano /etc/nixos/configuration.nix \r\n2. then sudo nixos-rebuild switch\r\n3. pynacl-1.4.0 must be using 3.7 python version or newer (3.9) not 2.x, check here : https://python.on-nix.com/\r\n\r\n### Expected behavior\r\nCan Install mysql-workbench in nix-system,\r\nUpdate this package for suitable using installed phyton in machine\r\n\r\n### Screenshots\r\n\r\n\r\n### Metadata\r\nbastomi@nugrohoeku:~/ > nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336340.2ebb6c1e5ae\"`\r\n - channels(bastomi): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163258/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163221","id":1162036896,"node_id":"I_kwDOAEVQ_M5FQ0ag","number":163221,"title":"Popura ポプラ: alternative Yggdrasil network client ","user":{"login":"Birdthatcantfly","id":86254368,"node_id":"MDQ6VXNlcjg2MjU0MzY4","avatar_url":"https://avatars.githubusercontent.com/u/86254368?v=4","gravatar_id":"","url":"https://api.github.com/users/Birdthatcantfly","html_url":"https://github.com/Birdthatcantfly","followers_url":"https://api.github.com/users/Birdthatcantfly/followers","following_url":"https://api.github.com/users/Birdthatcantfly/following{/other_user}","gists_url":"https://api.github.com/users/Birdthatcantfly/gists{/gist_id}","starred_url":"https://api.github.com/users/Birdthatcantfly/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Birdthatcantfly/subscriptions","organizations_url":"https://api.github.com/users/Birdthatcantfly/orgs","repos_url":"https://api.github.com/users/Birdthatcantfly/repos","events_url":"https://api.github.com/users/Birdthatcantfly/events{/privacy}","received_events_url":"https://api.github.com/users/Birdthatcantfly/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-07T23:19:19Z","updated_at":"2022-03-07T23:19:19Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nPopura, an alternative Yggdrasil network client\r\n\r\nYggdrasil Network is a peer-to-peer IPv6 network with link-local peer discovery, automatic end-to-end encryption, distributed IP address allocation, and DHT-based routing information exchange.\r\n\r\nPopura uses the same Yggdrasil core API internally, but adds some useful experimental features which the original client lacks.\r\n\r\nBy default, it works just like the original yggdrasil client, all features must be enabled manually. Popura adds new command line flags and config file sections to control those features.\r\nFeatures\r\n\r\n- Autopeering over the Internet\r\n\r\n- Built-in decentralized DNS system (meshname)\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/popura-network/Popura\r\n* source URL: https://github.com/popura-network/Popura\r\n* license: lgpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163221/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163215","id":1162016273,"node_id":"I_kwDOAEVQ_M5FQvYR","number":163215,"title":"darwin.apple_sdk.frameworks.System appears to be broken (aarch64-darwin)","user":{"login":"mikroskeem","id":3490861,"node_id":"MDQ6VXNlcjM0OTA4NjE=","avatar_url":"https://avatars.githubusercontent.com/u/3490861?v=4","gravatar_id":"","url":"https://api.github.com/users/mikroskeem","html_url":"https://github.com/mikroskeem","followers_url":"https://api.github.com/users/mikroskeem/followers","following_url":"https://api.github.com/users/mikroskeem/following{/other_user}","gists_url":"https://api.github.com/users/mikroskeem/gists{/gist_id}","starred_url":"https://api.github.com/users/mikroskeem/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mikroskeem/subscriptions","organizations_url":"https://api.github.com/users/mikroskeem/orgs","repos_url":"https://api.github.com/users/mikroskeem/repos","events_url":"https://api.github.com/users/mikroskeem/events{/privacy}","received_events_url":"https://api.github.com/users/mikroskeem/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-07T22:51:24Z","updated_at":"2022-03-10T03:47:12Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nSystem.framework System.tbd symlink is broken and causes linker to fail (on aarch64-darwin).\r\n\r\nnixpkgs rev 1fc7212a2c3992eedc6eedf498955c321ad81cc2\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n```shell\r\n$ cd /nix/store/ii0zyfqjjl10ww62735ngaxshlbrfnnn-apple-framework-System-11.0.0\r\n$ cd Library/Frameworks/System.framework\r\n$ readlink System.tbd # => Versions/Current/System.tbd\r\n$ cd Versions/Current/\r\n$ readlink System.tbd # => ../../../../../../usr/lib/libSystem.B.tbd\r\n$ realpath ../../../../../../usr/lib/libSystem.B.tbd # => realpath: ../../../../../../usr/lib/libSystem.B.tbd: No such file or directory\r\n```\r\n\r\n### Expected behavior\r\n\r\nSymlink not to be broken\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n(irrelevant, found this from flake pinned nixpkgs 1fc7212a2c3992eedc6eedf498955c321ad81cc2)\r\n\r\n```console\r\n[user@system:~]$ nix run nixpkgs#nix-info -- -m\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(mark): `\"\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/nix/store/09nmz4s952xg31z18qqc47vp7lanvdk3-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163215/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163212","id":1161997673,"node_id":"I_kwDOAEVQ_M5FQq1p","number":163212,"title":"howard-hinnant-date: CMake configuration points to `out` instead of `dev` for includes","user":{"login":"jktjkt","id":2631925,"node_id":"MDQ6VXNlcjI2MzE5MjU=","avatar_url":"https://avatars.githubusercontent.com/u/2631925?v=4","gravatar_id":"","url":"https://api.github.com/users/jktjkt","html_url":"https://github.com/jktjkt","followers_url":"https://api.github.com/users/jktjkt/followers","following_url":"https://api.github.com/users/jktjkt/following{/other_user}","gists_url":"https://api.github.com/users/jktjkt/gists{/gist_id}","starred_url":"https://api.github.com/users/jktjkt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jktjkt/subscriptions","organizations_url":"https://api.github.com/users/jktjkt/orgs","repos_url":"https://api.github.com/users/jktjkt/repos","events_url":"https://api.github.com/users/jktjkt/events{/privacy}","received_events_url":"https://api.github.com/users/jktjkt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-07T22:31:19Z","updated_at":"2022-03-07T23:16:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'm trying to use `howard-hinnant-date` from a CMake project. Its build fails because the include (`.h`) files are under a prefix which is not referenced from the installed CMake config file. Removing the `outputs = [ \"out\" \"dev\" ];` fixes this bug.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. download [`CMakeLists.txt`](https://github.com/NixOS/nixpkgs/files/8201196/CMakeLists.txt) and [`yay.cpp` (might need removing the trailing `.txt` on github)](https://github.com/NixOS/nixpkgs/files/8201201/yay.cpp.txt)\r\n2. store them into, say, `~/temp/nix-howard-date`\r\n3. get a `nix-shell -p cmake howard-hinnant-date`\r\n4. try to build via `cmake ~/temp/nix-howard-date`\r\n\r\nHere's how it fails on my NixOS:\r\n```console-session\r\n$ nix-shell -p cmake howard-hinnant-date\r\n$ rm -rf xx; mkdir xx; cd xx; cmake ~/temp/nix-howard-date\r\n-- The CXX compiler identification is GNU 10.3.0\r\n-- Detecting CXX compiler ABI info\r\n-- Detecting CXX compiler ABI info - done\r\n-- Check for working CXX compiler: /nix/store/pja9g36cy32z3d51942jqk91a6l2d5nv-gcc-wrapper-10.3.0/bin/g++ - skipped\r\n-- Detecting CXX compile features\r\n-- Detecting CXX compile features - done\r\n-- Looking for C++ include pthread.h\r\n-- Looking for C++ include pthread.h - found\r\n-- Performing Test CMAKE_HAVE_LIBC_PTHREAD\r\n-- Performing Test CMAKE_HAVE_LIBC_PTHREAD - Failed\r\n-- Looking for pthread_create in pthreads\r\n-- Looking for pthread_create in pthreads - not found\r\n-- Looking for pthread_create in pthread\r\n-- Looking for pthread_create in pthread - found\r\n-- Found Threads: TRUE \r\n-- Configuring done\r\nCMake Error at CMakeLists.txt:5 (add_executable):\r\n Cannot find source file:\r\n\r\n /nix/store/wjkxpmp3x7rg7zl6apsl6v4h6pjif3sr-howard-hinnant-date-3.0.1/include/date/date.h\r\n\r\n Tried extensions .c .C .c++ .cc .cpp .cxx .cu .mpp .m .M .mm .ixx .cppm .h\r\n .hh .h++ .hm .hpp .hxx .in .txx .f .F .for .f77 .f90 .f95 .f03 .hip .ispc\r\n\r\n\r\nCMake Error in CMakeLists.txt:\r\n Imported target \"date::date\" includes non-existent path\r\n\r\n \"/nix/store/wjkxpmp3x7rg7zl6apsl6v4h6pjif3sr-howard-hinnant-date-3.0.1/include\"\r\n\r\n in its INTERFACE_INCLUDE_DIRECTORIES. Possible reasons include:\r\n\r\n * The path was deleted, renamed, or moved to another location.\r\n\r\n * An install or uninstall procedure did not complete successfully.\r\n\r\n * The installation package was faulty and references files it does not\r\n provide.\r\n\r\n\r\n\r\n-- Generating done\r\nCMake Generate step failed. Build files cannot be regenerated correctly.\r\n```\r\n\r\nI *think* that this is similar to, e.g., #97534 and that not splitting the output into several packages will help.\r\n\r\n### Notify maintainers\r\nmaintainer: @r-burns \r\ncc: @jtojnar (is the [upstream package](https://github.com/HowardHinnant/date) using CMake properly?)\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.24, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(root): `\"nixos, nixos-21.11-21.11\"`\r\n - channels(jkt): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163212/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163206","id":1161888703,"node_id":"I_kwDOAEVQ_M5FQQO_","number":163206,"title":"Firefox - consider enabling Wayland by default","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"assignees":[{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false}],"milestone":null,"comments":3,"created_at":"2022-03-07T20:28:49Z","updated_at":"2022-03-24T02:13:18Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nref: https://www.phoronix.com/scan.php?page=news_item&px=Firefox-98.0\r\n\r\nIt sounds like:\r\n- other distros are doing it\r\n- it's about hesitancy around other bits of the user/gpu-space, where we know we're pretty up-to-date\r\n\r\nIt might also be overkill, we have `firefox-wayland`, but I'm also eager to test out the soon-to-be default path asap - I've been waiting for firefox+wayland for way, way too long.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163206/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163202","id":1161868681,"node_id":"I_kwDOAEVQ_M5FQLWJ","number":163202,"title":"ms liveshare macOS","user":{"login":"djgoku","id":105506,"node_id":"MDQ6VXNlcjEwNTUwNg==","avatar_url":"https://avatars.githubusercontent.com/u/105506?v=4","gravatar_id":"","url":"https://api.github.com/users/djgoku","html_url":"https://github.com/djgoku","followers_url":"https://api.github.com/users/djgoku/followers","following_url":"https://api.github.com/users/djgoku/following{/other_user}","gists_url":"https://api.github.com/users/djgoku/gists{/gist_id}","starred_url":"https://api.github.com/users/djgoku/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/djgoku/subscriptions","organizations_url":"https://api.github.com/users/djgoku/orgs","repos_url":"https://api.github.com/users/djgoku/repos","events_url":"https://api.github.com/users/djgoku/events{/privacy}","received_events_url":"https://api.github.com/users/djgoku/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-07T20:08:31Z","updated_at":"2022-03-10T03:47:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Support macOS/M1**\r\nCurrently live share is linux only. How would I start the process to add liveshare extension to support macOS and M1.\r\n\r\n**Metadata**\r\n\r\nThe below does not work currently:\r\n```\r\n vscodeExtensions = (with pkgs.vscode-extensions; [\r\n\r\n ]) ++ pkgs.vscode-utils.extensionsFromVscodeMarketplace [\r\n {\r\n name = \"vsliveshare\";\r\n publisher = \"ms-vsliveshare\";\r\n version = \"1.0.5418\";\r\n sha256 = \"11pnfvssn2vv975liwx5g7qm0l3l6q0lcl91hxgd0bwpkdzmnr1h\";\r\n }\r\n```\r\n\r\n* homepage URL:\r\n* source URL: https://github.com/NixOS/nixpkgs/blob/634141959076a8ab69ca2cca0f266852256d79ee/pkgs/applications/editors/vscode/extensions/ms-vsliveshare-vsliveshare/default.nix\r\n* license: mit, bsd, gpl2+ , ...\r\n* platforms: unix, linux, darwin, m1\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163202/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163191","id":1161749195,"node_id":"I_kwDOAEVQ_M5FPuLL","number":163191,"title":"Packaging request: sway-borders","user":{"login":"sei40kr","id":11665236,"node_id":"MDQ6VXNlcjExNjY1MjM2","avatar_url":"https://avatars.githubusercontent.com/u/11665236?v=4","gravatar_id":"","url":"https://api.github.com/users/sei40kr","html_url":"https://github.com/sei40kr","followers_url":"https://api.github.com/users/sei40kr/followers","following_url":"https://api.github.com/users/sei40kr/following{/other_user}","gists_url":"https://api.github.com/users/sei40kr/gists{/gist_id}","starred_url":"https://api.github.com/users/sei40kr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sei40kr/subscriptions","organizations_url":"https://api.github.com/users/sei40kr/orgs","repos_url":"https://api.github.com/users/sei40kr/repos","events_url":"https://api.github.com/users/sei40kr/events{/privacy}","received_events_url":"https://api.github.com/users/sei40kr/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-07T18:03:05Z","updated_at":"2022-03-08T14:25:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nFork of sway with some extra features, mainly related to borders.\r\n\r\n**Metadata**\r\n\r\n* homepage URL:\r\n* source URL: https://github.com/fluix-dev/sway-borders\r\n* license: mit\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163191/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163187","id":1161722070,"node_id":"I_kwDOAEVQ_M5FPnjW","number":163187,"title":"grub splashImage w/o filename ext could fail nicer","user":{"login":"mightyiam","id":635591,"node_id":"MDQ6VXNlcjYzNTU5MQ==","avatar_url":"https://avatars.githubusercontent.com/u/635591?v=4","gravatar_id":"","url":"https://api.github.com/users/mightyiam","html_url":"https://github.com/mightyiam","followers_url":"https://api.github.com/users/mightyiam/followers","following_url":"https://api.github.com/users/mightyiam/following{/other_user}","gists_url":"https://api.github.com/users/mightyiam/gists{/gist_id}","starred_url":"https://api.github.com/users/mightyiam/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mightyiam/subscriptions","organizations_url":"https://api.github.com/users/mightyiam/orgs","repos_url":"https://api.github.com/users/mightyiam/repos","events_url":"https://api.github.com/users/mightyiam/events{/privacy}","received_events_url":"https://api.github.com/users/mightyiam/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-07T17:36:56Z","updated_at":"2022-03-10T03:46:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTrying to provide a `splashImage` file that does not have a filename extension fails in the installation script.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Populate `boot.loader.grub.splashImage` with a path that lacks a filename extension.\r\n2. `nixos-rebuild switch`\r\n\r\n### Expected behavior\r\nIf it is the case that grub requires a filename extension, I'd like my build to fail with a message saying that.\r\n\r\n### Additional context\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/38639e08a03681159e1cd406b02a75b0bc9bcb15/nixos/modules/system/boot/loader/grub/install-grub.pl#L367-L390\r\n\r\n```\r\nsubstr outside of string at /nix/store/[nsixz776jams2gprxzc43ly86bgp3iz4-install-grub.pl](http://nsixz776jams2gprxzc43ly86bgp3iz4-install-grub.pl/) line 380.\r\nUse of uninitialized value in concatenation (.) or string at /nix/store/[nsixz776jams2gprxzc43ly86bgp3iz4-install-grub.pl](http://nsixz776jams2gprxzc43ly86bgp3iz4-install-grub.pl/) line 380.\r\n```\r\n\r\n### Notify maintainers\r\nNot sure who maintains this. Blame points at @samueldr, #40462.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.26, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(root): `\"nixos\"`\r\n - channels(mightyiam): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163187/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163164","id":1161569370,"node_id":"I_kwDOAEVQ_M5FPCRa","number":163164,"title":"JRE writes \"Duplicate cpuset controllers detected.\" to stdout in a FHSUserEnv","user":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-07T15:28:11Z","updated_at":"2022-03-21T17:44:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nIn a `nix-shell` sessions using `buildFHSUserEnv`, any invocation of `java` (even `java -version`) will write an error to `stdout`:\r\n\r\n```\r\n$ java -version \r\n[0.001s][warning][os,container] Duplicate cpuset controllers detected. Picking /sys/fs/cgroup/cpuset, skipping /host/sys/fs/cgroup/cpuset.\r\nopenjdk version \"17.0.1\" 2021-10-19\r\nOpenJDK Runtime Environment (build 17.0.1+12-nixos)\r\nOpenJDK 64-Bit Server VM (build 17.0.1+12-nixos, mixed mode, sharing)\r\n```\r\n\r\n(the first line goes to `stdout`, the rest to `stderr`.\r\n\r\nThis causes problems when the `stdout` is supposed to be interpreted by another tool in some pipeline.\r\n\r\n### Steps To Reproduce\r\n\r\nUse this `shell.nix`:\r\n\r\n```\r\n{ pkgs ? import <nixpkgs> {} }:\r\n\r\n(pkgs.buildFHSUserEnv {\r\n name = \"test\";\r\n\r\n targetPkgs = pkgs: [\r\n pkgs.jdk\r\n ];\r\n \r\n}).env\r\n```\r\n\r\n### Expected behavior\r\n\r\nWarnings/errors should go to `stderr`\r\n\r\n### Additional context\r\n\r\nThe 'real' bug is in OpenJDK, and it has been reported upstream as https://bugs.openjdk.java.net/browse/JDK-8270087 but closed as not reproducible. I'm pretty sure they didn't reproduce the warning at all (and consequently didn't see it get reported on `stdout` instead of `stderr`).\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.5, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos-20.03pre194293.2436c27541b\"`\r\n - nixpkgs: `/home/aengelen/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163164/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163107","id":1160952177,"node_id":"I_kwDOAEVQ_M5FMrlx","number":163107,"title":"xournalpp crashes complaining on missing icons ","user":{"login":"haizaar","id":58201,"node_id":"MDQ6VXNlcjU4MjAx","avatar_url":"https://avatars.githubusercontent.com/u/58201?v=4","gravatar_id":"","url":"https://api.github.com/users/haizaar","html_url":"https://github.com/haizaar","followers_url":"https://api.github.com/users/haizaar/followers","following_url":"https://api.github.com/users/haizaar/following{/other_user}","gists_url":"https://api.github.com/users/haizaar/gists{/gist_id}","starred_url":"https://api.github.com/users/haizaar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/haizaar/subscriptions","organizations_url":"https://api.github.com/users/haizaar/orgs","repos_url":"https://api.github.com/users/haizaar/repos","events_url":"https://api.github.com/users/haizaar/events{/privacy}","received_events_url":"https://api.github.com/users/haizaar/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-07T06:10:48Z","updated_at":"2022-04-16T04:52:44Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nGood day. I'm on NixOS unstable with KDE/Wayland.\r\nTrying to run xournalapp from nix-shell has the later crashing.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p xournalpp`\r\n2. `xournalpp`\r\n\r\nThen it crashes with:\r\n```\r\nGtk:ERROR:../gtk/gtkiconhelper.c:494:ensure_surface_for_gicon: assertion failed (error == NULL): Icon 'image-missing' not present in theme Adwaita (gtk-icon-theme-error-quark, 0)\r\nBail out! Gtk:ERROR:../gtk/gtkiconhelper.c:494:ensure_surface_for_gicon: assertion failed (error == NULL): Icon 'image-missing' not present in theme Adwaita (gtk-icon-theme-error-quark, 0)\r\n```\r\n\r\nThe full error is beflow.\r\n\r\n### Expected behavior\r\nxournalapp starting\r\n\r\n### Notify maintainers\r\n@dtzWill @Profpatsch @siraben \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.0, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(haizaar): `\"\"`\r\n - channels(root): `\"nixos-22.05pre356435.7f9b6e2babf, home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n### Full error output:\r\n```\r\n** Message: 17:08:51.411: TEXTDOMAINDIR = (null), Platform-specific locale dir = /nix/store/h1wkxdkyn2wrzgc3cwzb24bj0sy77cbm-xournalpp-1.1.1/share/xournalpp/../locale, chosen directory = /nix/store/h1wkxdkyn2wrzgc3cwzb24bj0sy77cbm-xournalpp-1.1.1/share/xournalpp/../locale\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.front.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM front\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.rear\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.center_lfe\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.side\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround51.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround21\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround51.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround21\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround40.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround40\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround51.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround41\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround51.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround50\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround51.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround51\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.surround71.0:CARD=0'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM surround71\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.iec958.0:CARD=0,AES0=4,AES1=130,AES2=0,AES3=2'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM iec958\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.iec958.0:CARD=0,AES0=4,AES1=130,AES2=0,AES3=2'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM spdif\r\nALSA lib confmisc.c:1369:(snd_func_refer) Unable to find definition 'cards.0.pcm.iec958.0:CARD=0,AES0=4,AES1=130,AES2=0,AES3=2'\r\nALSA lib conf.c:5178:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory\r\nALSA lib conf.c:5701:(snd_config_expand) Evaluate error: No such file or directory\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM spdif\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.hdmi\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.hdmi\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.modem\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.modem\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.phoneline\r\nALSA lib pcm.c:2735:(snd_pcm_open_noupdate) Unknown PCM cards.pcm.phoneline\r\n** Message: 17:08:51.635: Plugin \"MigrateFontSizes\" UI initialized\r\n\r\n** (xournalpp:5726): WARNING **: 17:08:51.676: Failed to load \"colornames.ini\" (/home/.../.config/xournalpp/colornames.ini): No such file or directory\r\n\r\n**\r\nGtk:ERROR:../gtk/gtkiconhelper.c:494:ensure_surface_for_gicon: assertion failed (error == NULL): Icon 'image-missing' not present in theme Adwaita (gtk-icon-theme-error-quark, 0)\r\nBail out! Gtk:ERROR:../gtk/gtkiconhelper.c:494:ensure_surface_for_gicon: assertion failed (error == NULL): Icon 'image-missing' not present in theme Adwaita (gtk-icon-theme-error-quark, 0)\r\n\r\n** (xournalpp:5726): WARNING **: 17:08:51.691: [Crash Handler] Crashed with signal 6\r\n\r\n** (xournalpp:5726): WARNING **: 17:08:51.691: [Crash Handler] Wrote crash log to: /home/.../.cache/xournalpp/errorlogs/errorlog.20220307-170851.log\r\n\r\n** (xournalpp:5726): WARNING **: 17:08:51.815: Trying to emergency save the current open document…\r\n\r\n** (xournalpp:5726): WARNING **: 17:08:51.816: Successfully saved document to \"/home/.../.config/xournalpp/emergencysave.xopp\"\r\n\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163107/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163080","id":1160766814,"node_id":"I_kwDOAEVQ_M5FL-Ve","number":163080,"title":"Declarative user profile pictures","user":{"login":"alyaeanyx","id":74795488,"node_id":"MDQ6VXNlcjc0Nzk1NDg4","avatar_url":"https://avatars.githubusercontent.com/u/74795488?v=4","gravatar_id":"","url":"https://api.github.com/users/alyaeanyx","html_url":"https://github.com/alyaeanyx","followers_url":"https://api.github.com/users/alyaeanyx/followers","following_url":"https://api.github.com/users/alyaeanyx/following{/other_user}","gists_url":"https://api.github.com/users/alyaeanyx/gists{/gist_id}","starred_url":"https://api.github.com/users/alyaeanyx/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alyaeanyx/subscriptions","organizations_url":"https://api.github.com/users/alyaeanyx/orgs","repos_url":"https://api.github.com/users/alyaeanyx/repos","events_url":"https://api.github.com/users/alyaeanyx/events{/privacy}","received_events_url":"https://api.github.com/users/alyaeanyx/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-07T00:35:00Z","updated_at":"2022-03-23T10:38:57Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Currently, user profile pictures as they are used in Gnome cannot be reasonably changed. The interface used for changing user icons in the Gnome system settings is unreliable (seems to only work for the preset icons). The only way to change them at all is to manually put them into `/var/lib/AccountsService/icons`.\r\n\r\nMy ideas to make declarative user icons possible are:\r\n* Patch `accountsservice` to point the user icon dir to an immutable location in `/etc`\r\n* systemd service to place user icons in `/var/lib/AccountsService/icons`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163080/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163052","id":1160693463,"node_id":"I_kwDOAEVQ_M5FLsbX","number":163052,"title":"Have IOSurface depend on Libsystem rather than XPC","user":{"login":"toonn","id":1486805,"node_id":"MDQ6VXNlcjE0ODY4MDU=","avatar_url":"https://avatars.githubusercontent.com/u/1486805?v=4","gravatar_id":"","url":"https://api.github.com/users/toonn","html_url":"https://github.com/toonn","followers_url":"https://api.github.com/users/toonn/followers","following_url":"https://api.github.com/users/toonn/following{/other_user}","gists_url":"https://api.github.com/users/toonn/gists{/gist_id}","starred_url":"https://api.github.com/users/toonn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/toonn/subscriptions","organizations_url":"https://api.github.com/users/toonn/orgs","repos_url":"https://api.github.com/users/toonn/repos","events_url":"https://api.github.com/users/toonn/events{/privacy}","received_events_url":"https://api.github.com/users/toonn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-03-06T19:22:30Z","updated_at":"2022-04-22T21:17:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe IOSurface framework as defined by the apple-source-releases depends on XPC. This causes redefinition errors because other frameworks get these definitions from Libsystem. There was an attempt to fix it in PR #161561, but this causes [build problems due to Libsystem and libc++ being incompatible currently](https://github.com/NixOS/nixpkgs/pull/161561#issuecomment-1056063573), so it was reverted in PR #162681.\r\n\r\n### Steps To Reproduce\r\nThe first problem:\r\n1. Build something that depends on Libsystem and IOSurface, like `mac-notification-sys`.\r\n\r\nThe second problem:\r\n1. Apply the patch having IOSurface depend on Libsystem rather than XPC.\r\n2. Build something depending on IOSurface and libc++, like `xcbuild`.\r\n\r\n### Expected behavior\r\nThe incompatibility between Libsystem and libc++ should be fixed so we can have IOSurface properly depend on Libsystem without causing problems.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163052/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163024","id":1160644615,"node_id":"I_kwDOAEVQ_M5FLggH","number":163024,"title":"Module Request - Kopia","user":{"login":"dit7ya","id":14034137,"node_id":"MDQ6VXNlcjE0MDM0MTM3","avatar_url":"https://avatars.githubusercontent.com/u/14034137?v=4","gravatar_id":"","url":"https://api.github.com/users/dit7ya","html_url":"https://github.com/dit7ya","followers_url":"https://api.github.com/users/dit7ya/followers","following_url":"https://api.github.com/users/dit7ya/following{/other_user}","gists_url":"https://api.github.com/users/dit7ya/gists{/gist_id}","starred_url":"https://api.github.com/users/dit7ya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dit7ya/subscriptions","organizations_url":"https://api.github.com/users/dit7ya/orgs","repos_url":"https://api.github.com/users/dit7ya/repos","events_url":"https://api.github.com/users/dit7ya/events{/privacy}","received_events_url":"https://api.github.com/users/dit7ya/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-06T15:50:40Z","updated_at":"2022-03-09T22:52:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n Cross-platform backup tool for Windows, macOS & Linux with fast, incremental backups, client-side end-to-end encryption, compression and data deduplication. CLI and GUI included. \r\n \r\n \r\n \r\n Existing Nix package - https://search.nixos.org/packages?query=kopia\r\n \r\n Would be nice to have a declarative service around like restic has.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://kopia.io/\r\n* source URL: https://github.com/kopia/kopia/\r\n* license: Apache-2.0 License \r\n* platforms: linux, darwin\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163024/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005/events","html_url":"https://github.com/NixOS/nixpkgs/issues/163005","id":1160610589,"node_id":"I_kwDOAEVQ_M5FLYMd","number":163005,"title":"Package request: cgif","user":{"login":"CoolingTool","id":62089272,"node_id":"MDQ6VXNlcjYyMDg5Mjcy","avatar_url":"https://avatars.githubusercontent.com/u/62089272?v=4","gravatar_id":"","url":"https://api.github.com/users/CoolingTool","html_url":"https://github.com/CoolingTool","followers_url":"https://api.github.com/users/CoolingTool/followers","following_url":"https://api.github.com/users/CoolingTool/following{/other_user}","gists_url":"https://api.github.com/users/CoolingTool/gists{/gist_id}","starred_url":"https://api.github.com/users/CoolingTool/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/CoolingTool/subscriptions","organizations_url":"https://api.github.com/users/CoolingTool/orgs","repos_url":"https://api.github.com/users/CoolingTool/repos","events_url":"https://api.github.com/users/CoolingTool/events{/privacy}","received_events_url":"https://api.github.com/users/CoolingTool/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-06T13:26:42Z","updated_at":"2022-03-06T13:26:42Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nGIF encoder written in C, used in libvips\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/dloebl/cgif\r\n* source URL: https://github.com/dloebl/cgif\r\n* license: mit\r\n* platforms: linux (not sure for other platforms)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/163005/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162986","id":1160560309,"node_id":"I_kwDOAEVQ_M5FLL61","number":162986,"title":"Packaging requests: nodePackages.ansible-language-server","user":{"login":"sei40kr","id":11665236,"node_id":"MDQ6VXNlcjExNjY1MjM2","avatar_url":"https://avatars.githubusercontent.com/u/11665236?v=4","gravatar_id":"","url":"https://api.github.com/users/sei40kr","html_url":"https://github.com/sei40kr","followers_url":"https://api.github.com/users/sei40kr/followers","following_url":"https://api.github.com/users/sei40kr/following{/other_user}","gists_url":"https://api.github.com/users/sei40kr/gists{/gist_id}","starred_url":"https://api.github.com/users/sei40kr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sei40kr/subscriptions","organizations_url":"https://api.github.com/users/sei40kr/orgs","repos_url":"https://api.github.com/users/sei40kr/repos","events_url":"https://api.github.com/users/sei40kr/events{/privacy}","received_events_url":"https://api.github.com/users/sei40kr/received_events","type":"User","site_admin":false},"labels":[{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-06T09:19:00Z","updated_at":"2022-03-07T09:19:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nAnsible Language Server\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://als.readthedocs.io/en/latest/\r\n* source URL: https://github.com/ansible/ansible-language-server\r\n* license: mit\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162986/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162953","id":1160490328,"node_id":"I_kwDOAEVQ_M5FK61Y","number":162953,"title":"package request: aioboto3","user":{"login":"sheenobu","id":1443459,"node_id":"MDQ6VXNlcjE0NDM0NTk=","avatar_url":"https://avatars.githubusercontent.com/u/1443459?v=4","gravatar_id":"","url":"https://api.github.com/users/sheenobu","html_url":"https://github.com/sheenobu","followers_url":"https://api.github.com/users/sheenobu/followers","following_url":"https://api.github.com/users/sheenobu/following{/other_user}","gists_url":"https://api.github.com/users/sheenobu/gists{/gist_id}","starred_url":"https://api.github.com/users/sheenobu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sheenobu/subscriptions","organizations_url":"https://api.github.com/users/sheenobu/orgs","repos_url":"https://api.github.com/users/sheenobu/repos","events_url":"https://api.github.com/users/sheenobu/events{/privacy}","received_events_url":"https://api.github.com/users/sheenobu/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-06T01:27:20Z","updated_at":"2022-03-06T01:58:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\naioboto3 is a wrapper for boto3 using aiobotocore that allows asynchronous python calls for AWS APIs.\r\n\r\nwe already have its required and optional dependencies: aiobotocore, cryptography, chalice. Don't mind doing this myself just putting in the tracking issue.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://pypi.org/project/aioboto3/\r\n* source URL: https://github.com/terrycain/aioboto3\r\n* license: Apache2\r\n* platforms: unix, linux, darwin\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162953/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162924","id":1160434646,"node_id":"I_kwDOAEVQ_M5FKtPW","number":162924,"title":"Caddy module + ACME integration gives more permissions than desired","user":{"login":"winterqt","id":78392041,"node_id":"MDQ6VXNlcjc4MzkyMDQx","avatar_url":"https://avatars.githubusercontent.com/u/78392041?v=4","gravatar_id":"","url":"https://api.github.com/users/winterqt","html_url":"https://github.com/winterqt","followers_url":"https://api.github.com/users/winterqt/followers","following_url":"https://api.github.com/users/winterqt/following{/other_user}","gists_url":"https://api.github.com/users/winterqt/gists{/gist_id}","starred_url":"https://api.github.com/users/winterqt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/winterqt/subscriptions","organizations_url":"https://api.github.com/users/winterqt/orgs","repos_url":"https://api.github.com/users/winterqt/repos","events_url":"https://api.github.com/users/winterqt/events{/privacy}","received_events_url":"https://api.github.com/users/winterqt/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-05T20:00:43Z","updated_at":"2022-03-06T03:14:56Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"(Apologies for the terrible issue title.)\r\n\r\nCurrently, the Caddy module [runs with the `acme` group as a supplemental group](https://github.com/NixOS/nixpkgs/blob/737b8e22a85e589cf0bd5187eae5f65679e1b588/nixos/modules/services/web-servers/caddy/default.nix#L311) if any ACME certs are used.\r\n\r\nThis may be undesirable for some users from a security standpoint, as it would provide the Caddy service access to all certificates.\r\n\r\nAdditionally, I believe it breaks the assertions added in b52607f43b11319edb716d65bbecbfdbf2f5b92b (which is totally my bad).\r\n\r\nI think we should make Caddy (and the other web servers) set their SupplementalGroups to include all the used certificate's (`useACMEHost` only probably, not ones created by the module directly) groups (and not the `acme` group), and remove the assertions surrounding this\r\n\r\ncc @aanderse @m1cr0man for thoughts","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162924/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162887","id":1160340551,"node_id":"I_kwDOAEVQ_M5FKWRH","number":162887,"title":"Packaging request: olympus","user":{"login":"jyooru","id":63786778,"node_id":"MDQ6VXNlcjYzNzg2Nzc4","avatar_url":"https://avatars.githubusercontent.com/u/63786778?v=4","gravatar_id":"","url":"https://api.github.com/users/jyooru","html_url":"https://github.com/jyooru","followers_url":"https://api.github.com/users/jyooru/followers","following_url":"https://api.github.com/users/jyooru/following{/other_user}","gists_url":"https://api.github.com/users/jyooru/gists{/gist_id}","starred_url":"https://api.github.com/users/jyooru/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jyooru/subscriptions","organizations_url":"https://api.github.com/users/jyooru/orgs","repos_url":"https://api.github.com/users/jyooru/repos","events_url":"https://api.github.com/users/jyooru/events{/privacy}","received_events_url":"https://api.github.com/users/jyooru/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-05T12:50:34Z","updated_at":"2022-03-05T14:29:27Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nCeleste mod manager\r\n\r\n@VergeDX I see you have it packaged in your config, could you add it to nixpkgs? I didn't want to just steal your work.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://everestapi.github.io/\r\n* source URL: https://github.com/EverestAPI/Olympus\r\n* license: MIT\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162887/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162865","id":1160288974,"node_id":"I_kwDOAEVQ_M5FKJrO","number":162865,"title":"Scarab Hollow Knight mod installer","user":{"login":"l0b0","id":168301,"node_id":"MDQ6VXNlcjE2ODMwMQ==","avatar_url":"https://avatars.githubusercontent.com/u/168301?v=4","gravatar_id":"","url":"https://api.github.com/users/l0b0","html_url":"https://github.com/l0b0","followers_url":"https://api.github.com/users/l0b0/followers","following_url":"https://api.github.com/users/l0b0/following{/other_user}","gists_url":"https://api.github.com/users/l0b0/gists{/gist_id}","starred_url":"https://api.github.com/users/l0b0/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/l0b0/subscriptions","organizations_url":"https://api.github.com/users/l0b0/orgs","repos_url":"https://api.github.com/users/l0b0/repos","events_url":"https://api.github.com/users/l0b0/events{/privacy}","received_events_url":"https://api.github.com/users/l0b0/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-05T08:49:52Z","updated_at":"2022-03-09T13:15:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nGame mod installers are often fiddly to set up, which makes them a perfect match for reproducible Nix derivations. Scarab is a cross-platform mod installer for Hollow Knight. However, the [latest ELF executable](https://github.com/fifty-six/Scarab/releases/tag/v1.10.0.0) fails to run:\r\n\r\n```console\r\n$ ./Scarab \r\nbash: ./Scarab: No such file or directory\r\n```\r\n\r\nELF description:\r\n\r\n```console\r\n$ file Scarab\r\nScarab: ELF 64-bit LSB pie executable, x86-64, version 1 (GNU/Linux), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=0d78e22dc15d366dce0f9844639a3b96ac2e139d, for GNU/Linux 2.6.32, stripped, too many notes (256)\r\n```\r\n\r\nFixing up the interpreter is not enough:\r\n\r\n```console\r\n$ nix-shell -p patchelf --run 'patchelf --set-interpreter \"$(patchelf --print-interpreter $(which mkdir))\" Scarab'\r\n$ ./Scarab \r\n./Scarab: error while loading shared libraries: libz.so.1: cannot open shared object file: No such file or directory\r\n```\r\n\r\nI also tried building the project with [some help](https://github.com/fsprojects/fantomas/issues/412#issuecomment-798774514):\r\n\r\n```console\r\nexport DOTNET_ROOT=$(dirname $(realpath $(which dotnet)))\r\n$ dotnet build\r\nMicrosoft (R) Build Engine version 17.0.0+c9eb9dd64 for .NET\r\nCopyright (C) Microsoft Corporation. All rights reserved.\r\n\r\n Determining projects to restore...\r\n Restored /home/username/dev/Scarab/Scarab.Tests/Scarab.Tests.csproj (in 328 ms).\r\n Restored /home/username/dev/Scarab/Scarab/Scarab.csproj (in 349 ms).\r\n GenerateAvaloniaResourcesTask -> Root: /home/username/dev/Scarab/Scarab, 3 resources, Output:obj/Debug/net6.0//Avalonia/resources\r\n avares -> name:/App.xaml, path: /home/username/dev/Scarab/Scarab/App.xaml, size:535, ItemSpec:App.xaml\r\n avares -> name:/Views/MainWindow.xaml, path: /home/username/dev/Scarab/Scarab/Views/MainWindow.xaml, size:298, ItemSpec:Views/MainWindow.xaml\r\n avares -> name:/Assets/omegamaggotprime.ico, path: /home/username/dev/Scarab/Scarab/Assets/omegamaggotprime.ico, size:124504, ItemSpec:Assets/omegamaggotprime.ico\r\n Scarab -> /home/username/dev/Scarab/Scarab/bin/Debug/net6.0/Scarab.dll\r\n GenerateAvaloniaResourcesTask -> Root: /home/username/dev/Scarab/Scarab.Tests, 0 resources, Output:obj/Debug/net6.0//Avalonia/resources\r\n Scarab.Tests -> /home/username/dev/Scarab/Scarab.Tests/bin/Debug/net6.0/Scarab.Tests.dll\r\n\r\nBuild succeeded.\r\n 0 Warning(s)\r\n 0 Error(s)\r\n\r\nTime Elapsed 00:00:02.51\r\n$ ./Scarab/bin/Debug/net6.0/Scarab\r\n```\r\n\r\nThe application just returns immediately with exit code 0, but creates this log:\r\n\r\n```text\r\n$ cat ModInstaller_Error_22-03-05\\ 22-20-24.log \r\nSystem.DllNotFoundException: Unable to load shared library 'libX11.so.6' or one of its dependencies. In order to help diagnose loading problems, consider setting the LD_DEBUG environment variable: liblibX11.so.6: cannot open shared object file: No such file or directory\r\n at Avalonia.X11.XLib.XInitThreads()\r\n at Avalonia.X11.AvaloniaX11Platform.Initialize(X11PlatformOptions options) in /_/src/Avalonia.X11/X11Platform.cs:line 54\r\n at Avalonia.AvaloniaX11PlatformExtensions.<>c__0`1.<UseX11>b__0_0() in /_/src/Avalonia.X11/X11Platform.cs:line 279\r\n at Avalonia.Controls.AppBuilderBase`1.Setup() in /_/src/Avalonia.Controls/AppBuilderBase.cs:line 303\r\n at Avalonia.Controls.AppBuilderBase`1.SetupWithLifetime(IApplicationLifetime lifetime) in /_/src/Avalonia.Controls/AppBuilderBase.cs:line 179\r\n at Avalonia.ClassicDesktopStyleApplicationLifetimeExtensions.StartWithClassicDesktopLifetime[T](T builder, String[] args, ShutdownMode shutdownMode) in /_/src/Avalonia.Controls/ApplicationLifetimes/ClassicDesktopStyleApplicationLifetime.cs:line 186\r\n```\r\n\r\nAt this point I'm not sure how to fix it, and less sure how to formulate the fix as a Nix expression.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/fifty-six/Scarab\r\n* source URL: https://github.com/fifty-six/Scarab\r\n* license: gpl3\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162865/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162853","id":1160261876,"node_id":"I_kwDOAEVQ_M5FKDD0","number":162853,"title":"Gitea service's option mailerPasswordFile does not work.","user":{"login":"dit7ya","id":14034137,"node_id":"MDQ6VXNlcjE0MDM0MTM3","avatar_url":"https://avatars.githubusercontent.com/u/14034137?v=4","gravatar_id":"","url":"https://api.github.com/users/dit7ya","html_url":"https://github.com/dit7ya","followers_url":"https://api.github.com/users/dit7ya/followers","following_url":"https://api.github.com/users/dit7ya/following{/other_user}","gists_url":"https://api.github.com/users/dit7ya/gists{/gist_id}","starred_url":"https://api.github.com/users/dit7ya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dit7ya/subscriptions","organizations_url":"https://api.github.com/users/dit7ya/orgs","repos_url":"https://api.github.com/users/dit7ya/repos","events_url":"https://api.github.com/users/dit7ya/events{/privacy}","received_events_url":"https://api.github.com/users/dit7ya/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-05T06:35:38Z","updated_at":"2022-03-06T03:13:31Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`services.gitea.mailerPasswordFile` has no effect - it does not set the mailer password\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable gitea service with `mailerPasswordFile` option. \r\n \r\n <details>\r\n <summary>For example, my current configuration is </summary>\r\n \r\n```nix\r\n services.gitea = {\r\n enable = true; # Enable Gitea\r\n database = {\r\n type = \"postgres\"; # Database type\r\n passwordFile = ./gitea_password;\r\n\r\n };\r\n disableRegistration = true;\r\n domain = \"redacted\"; # Domain name\r\n rootUrl = \"redacted\"; # Root web URL\r\n httpPort = 5883; # Provided unique port\r\n mailerPasswordFile = config.sops.secrets.sopsGiteaMailerPassword.path;\r\n settings = {\r\n mailer = {\r\n ENABLED = true;\r\n FROM = \"redacted@gmail.com\";\r\n HOST = \"smtp.gmail.com:587\";\r\n USER = \"redacted@gmail.com\";\r\n MAILER_TYPE = \"smtp\";\r\n IS_TLS_ENABLED = false;\r\n HELO_HOSTNAME = \"redacted\";\r\n };\r\n repository = { DEFAULT_BRANCH = \"main\"; };\r\n service = { REGISTER_EMAIL_CONFIRM = true; };\r\n ui = {\r\n DEFAULT_THEME = \"gitea\"; # Set the default theme\r\n };\r\n };\r\n };\r\n\r\n```\r\n</details>\r\n\r\n3. Rebuild and switch system.\r\n4. Check the generated config file - `sudo bat /var/lib/gitea/custom/conf/app.ini`. The field `PASSWD` under `[[mailer]]` is empty.\r\n\r\n### Expected behavior\r\nShould have the correct password in that field and work in the app as well.\r\n\r\n### Additional context\r\n\r\nI am not exactly sure but seems like this line should have the opposite predicate.\r\nhttps://github.com/NixOS/nixpkgs/blob/e3a60c19f8918c72d8fb556b52216ec8e90d6fb5/nixos/modules/services/misc/gitea.nix#L422\r\n\r\n\r\nUsing a Flakes managed NixOS config.\r\n\r\n### Notify maintainers\r\n@srhb @ma27\r\n\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.76, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162853/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162840","id":1160192841,"node_id":"I_kwDOAEVQ_M5FJyNJ","number":162840,"title":"nginx no index for virtualhost","user":{"login":"blobcode","id":47042738,"node_id":"MDQ6VXNlcjQ3MDQyNzM4","avatar_url":"https://avatars.githubusercontent.com/u/47042738?v=4","gravatar_id":"","url":"https://api.github.com/users/blobcode","html_url":"https://github.com/blobcode","followers_url":"https://api.github.com/users/blobcode/followers","following_url":"https://api.github.com/users/blobcode/following{/other_user}","gists_url":"https://api.github.com/users/blobcode/gists{/gist_id}","starred_url":"https://api.github.com/users/blobcode/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/blobcode/subscriptions","organizations_url":"https://api.github.com/users/blobcode/orgs","repos_url":"https://api.github.com/users/blobcode/repos","events_url":"https://api.github.com/users/blobcode/events{/privacy}","received_events_url":"https://api.github.com/users/blobcode/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-05T02:22:26Z","updated_at":"2022-03-05T11:34:12Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install the nginx package\r\n### Expected behavior\r\nvirtual hosts should be able to have an index assigned to them, for example\r\n```\r\nservices.nginx = {\r\nenable = true;\r\nvirtualHosts.default = {\r\n index = \"index.php\";\r\n };\r\n};\r\n```\r\nThis would result in an nginx.conf of (for example)\r\n```\r\n...\r\n server {\r\n listen 0.0.0.0:80 ;\r\n listen [::0]:80 ;\r\n server_name default ;\r\n root /nix/store/rjrbyzasdhjvv038dg3hc27j3jdc7z5v-src;\r\n index index.php;\r\n location / {\r\n ...\r\n }\r\n }\r\n...\r\n```\r\n\r\nThis is currently not possible, however is a feature of nginx normally.\r\n\r\n### Notify maintainers\r\n@erikarvstedt \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese 11 paths will be fetched (46.82 MiB download, 214.07 MiB unpacked):\r\n /nix/store/2qwnn6lizc9d119kp3zig3q19gbfm4n6-gcc-wrapper-10.3.0\r\n /nix/store/3jnlimdcwxm7a9w8dji20nr9v6lmpcwx-expand-response-params\r\n /nix/store/6r5h4h7nqx73m87j5b9sjwy2x9kyri0k-gcc-10.3.0\r\n /nix/store/977rrqjf3hfda1qbqlpp2pz22m6phczy-bash-interactive-5.1-p8-dev\r\n /nix/store/bqmg7l0jn6nhgjlfc981g1imzb6ny8xl-patchelf-0.13\r\n /nix/store/h19zwlkrp6b0hp3ypbqdcggnyarn3af6-binutils-2.35.2\r\n /nix/store/mnm45njs9m6yk0szy7lv9cbfj59n1ajv-linux-headers-5.14\r\n /nix/store/msncxcf5lgy5by9cqjyxchxd26x47d64-gnumake-4.3\r\n /nix/store/msy4nj4gscw9csc82labx0xvh7vqlfif-glibc-2.33-117-dev\r\n /nix/store/spm7d6ncyx2k5w8yl6clzynv2s4wf1kp-binutils-wrapper-2.35.2\r\n /nix/store/z7wz8q1i0j4jmfpn87wpakwma6q0k90n-stdenv-linux\r\ncopying path '/nix/store/977rrqjf3hfda1qbqlpp2pz22m6phczy-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/3jnlimdcwxm7a9w8dji20nr9v6lmpcwx-expand-response-params' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/h19zwlkrp6b0hp3ypbqdcggnyarn3af6-binutils-2.35.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/msncxcf5lgy5by9cqjyxchxd26x47d64-gnumake-4.3' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/mnm45njs9m6yk0szy7lv9cbfj59n1ajv-linux-headers-5.14' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/bqmg7l0jn6nhgjlfc981g1imzb6ny8xl-patchelf-0.13' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/msy4nj4gscw9csc82labx0xvh7vqlfif-glibc-2.33-117-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/6r5h4h7nqx73m87j5b9sjwy2x9kyri0k-gcc-10.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/spm7d6ncyx2k5w8yl6clzynv2s4wf1kp-binutils-wrapper-2.35.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2qwnn6lizc9d119kp3zig3q19gbfm4n6-gcc-wrapper-10.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/z7wz8q1i0j4jmfpn87wpakwma6q0k90n-stdenv-linux' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.102, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162840/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162693","id":1159145512,"node_id":"I_kwDOAEVQ_M5FFygo","number":162693,"title":"Invalid bubblewrap config in lutris","user":{"login":"jclangst","id":13301098,"node_id":"MDQ6VXNlcjEzMzAxMDk4","avatar_url":"https://avatars.githubusercontent.com/u/13301098?v=4","gravatar_id":"","url":"https://api.github.com/users/jclangst","html_url":"https://github.com/jclangst","followers_url":"https://api.github.com/users/jclangst/followers","following_url":"https://api.github.com/users/jclangst/following{/other_user}","gists_url":"https://api.github.com/users/jclangst/gists{/gist_id}","starred_url":"https://api.github.com/users/jclangst/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jclangst/subscriptions","organizations_url":"https://api.github.com/users/jclangst/orgs","repos_url":"https://api.github.com/users/jclangst/repos","events_url":"https://api.github.com/users/jclangst/events{/privacy}","received_events_url":"https://api.github.com/users/jclangst/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-04T01:32:46Z","updated_at":"2022-03-04T16:22:27Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nLaunching the latest Lutris package on NixOS from either the `21.11` or `unstable` channels causes the following error immediately:\r\n\r\n`bwrap: Unexpected capabilities but not setuid, old file caps config?`\r\n\r\nThis occurs prior to any GUI launching and was tested on `GNOME Shell 41.1.`\r\n\r\nNo additional logs were produced.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install lutris \r\n2. Try to launch lutris via the desktop environment or terminal\r\n3. Observe bubblewrap error\r\n\r\n### Expected behavior\r\n\r\nNo bubblewrap error should exist\r\n\r\n### Additional context\r\n\r\nUnwrapped version launches fine (but of course fails at later stages like installing games).\r\n\r\n### Notify maintainers\r\n\r\n@chiiruno\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.25, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336249.b099eaa0e01\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162693/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162687","id":1159093877,"node_id":"I_kwDOAEVQ_M5FFl51","number":162687,"title":"perlPackages.AppSqitch: 1.2.1","user":{"login":"sekunho","id":20364796,"node_id":"MDQ6VXNlcjIwMzY0Nzk2","avatar_url":"https://avatars.githubusercontent.com/u/20364796?v=4","gravatar_id":"","url":"https://api.github.com/users/sekunho","html_url":"https://github.com/sekunho","followers_url":"https://api.github.com/users/sekunho/followers","following_url":"https://api.github.com/users/sekunho/following{/other_user}","gists_url":"https://api.github.com/users/sekunho/gists{/gist_id}","starred_url":"https://api.github.com/users/sekunho/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sekunho/subscriptions","organizations_url":"https://api.github.com/users/sekunho/orgs","repos_url":"https://api.github.com/users/sekunho/repos","events_url":"https://api.github.com/users/sekunho/events{/privacy}","received_events_url":"https://api.github.com/users/sekunho/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-04T00:06:03Z","updated_at":"2022-03-04T00:06:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\nLatest version bump: https://github.com/NixOS/nixpkgs/commit/ef87b2112369292e334e360cb7ef6b01e5c15f11\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: `legacyPackages.x86_64-linux.perlPackages.AppSqitch`\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.1.0\r\ndesired version: 1.2.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: `volth` but it doesn't seem like the email is tied to a GitHub account\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162687/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162686","id":1159093652,"node_id":"I_kwDOAEVQ_M5FFl2U","number":162686,"title":"Declarative containers ignore networking.nameservers, even with privateNetwork=true","user":{"login":"delroth","id":202798,"node_id":"MDQ6VXNlcjIwMjc5OA==","avatar_url":"https://avatars.githubusercontent.com/u/202798?v=4","gravatar_id":"","url":"https://api.github.com/users/delroth","html_url":"https://github.com/delroth","followers_url":"https://api.github.com/users/delroth/followers","following_url":"https://api.github.com/users/delroth/following{/other_user}","gists_url":"https://api.github.com/users/delroth/gists{/gist_id}","starred_url":"https://api.github.com/users/delroth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/delroth/subscriptions","organizations_url":"https://api.github.com/users/delroth/orgs","repos_url":"https://api.github.com/users/delroth/repos","events_url":"https://api.github.com/users/delroth/events{/privacy}","received_events_url":"https://api.github.com/users/delroth/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1192878136,"node_id":"MDU6TGFiZWwxMTkyODc4MTM2","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.%20topic:%20nixos-container","name":"6. topic: nixos-container","color":"fef2c0","default":false,"description":"Imperative and declarative systemd-nspawn containers"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-04T00:05:42Z","updated_at":"2022-03-05T12:22:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nNixOS declarative containers have a \"feature\" that overwrites the container's `/etc/resolv.conf` at startup with the one from the host. I have doubts about that implementation in the general case, but in the case of a container configured with `privateNetwork = true;` it is beyond broken. Not only does it copy a `resolv.conf` that will in all likelihood not work (because we're in a private network namespace, with different interfaces / addressing), but it also somehow confuses `resolvconf` and makes `networking.nameservers` not do anything by default.\r\n\r\nThere is a workaround: `environment.etc.\"resolv.conf\".text = \"...\";` but that's very counter-intuitive to find, and we shouldn't require that for basic networking configuration.\r\n\r\nI'm not entirely sure how to fix this, it seems like there are two issues compounded with each other here. First, I think copying `resolv.conf` with `privateNetwork = true` just shouldn't happen, if it ever does something useful I suspect that's accidental. Second, `resolvconf` should be overwriting that host `resolv.conf` file with what has been configured in `networking.nameservers`, but it doesn't do it, and I don't yet understand why. It just decides to not touch the file and copy it verbatim.\r\n\r\n### Steps To Reproduce\r\n\r\n```\r\n containers.test = {\r\n privateNetwork = true;\r\n config = {\r\n networking.nameservers = [ \"8.8.8.8\" ];\r\n };\r\n\r\n # irrelevant to this bug\r\n autoStart = true;\r\n ephemeral = true;\r\n };\r\n```\r\n\r\n```\r\nhost# nixos-container root-login test\r\ntest# cat /etc/resolv.conf\r\n# Generated by resolvconf\r\nsearch delroth.net\r\nnameserver 127.0.0.53\r\noptions edns0 trust-ad\r\noptions edns0\r\n```\r\n\r\n### Expected behavior\r\nA declarative container can define its own DNS configuration without getting trampled over by a bash script.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nThe original implementation of the `resolv.conf` copying dates back to 2014: e620be97fe212b43ee42865dd4d3c8bba7f26fa9\r\n\r\n### Notify maintainers\r\nTagging @abbradar because I suspect from git history they might know about `resolvconf`, but that's a shot in the dark :-)\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.16-hardened1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220221_caf5172`\r\n - channels(delroth): `\"\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162686/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162665","id":1158831810,"node_id":"I_kwDOAEVQ_M5FEl7C","number":162665,"title":"thermald is broken due to use of deprecated functions","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-03T19:48:18Z","updated_at":"2022-03-04T07:45:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nsee here: https://github.com/intel/thermal_daemon/issues/340 and https://github.com/intel/thermal_daemon/pull/338\r\n\r\nI'm patching locally for now, hopefully they merge it and tag a release.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162665/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162652","id":1158666345,"node_id":"I_kwDOAEVQ_M5FD9hp","number":162652,"title":"Packaging request: nodePackages.emmet-ls","user":{"login":"sei40kr","id":11665236,"node_id":"MDQ6VXNlcjExNjY1MjM2","avatar_url":"https://avatars.githubusercontent.com/u/11665236?v=4","gravatar_id":"","url":"https://api.github.com/users/sei40kr","html_url":"https://github.com/sei40kr","followers_url":"https://api.github.com/users/sei40kr/followers","following_url":"https://api.github.com/users/sei40kr/following{/other_user}","gists_url":"https://api.github.com/users/sei40kr/gists{/gist_id}","starred_url":"https://api.github.com/users/sei40kr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sei40kr/subscriptions","organizations_url":"https://api.github.com/users/sei40kr/orgs","repos_url":"https://api.github.com/users/sei40kr/repos","events_url":"https://api.github.com/users/sei40kr/events{/privacy}","received_events_url":"https://api.github.com/users/sei40kr/received_events","type":"User","site_admin":false},"labels":[{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-03T17:04:07Z","updated_at":"2022-03-04T16:41:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nEmmet support based on LSP.\r\n\r\n**Metadata**\r\n\r\n* source URL: https://github.com/aca/emmet-ls\r\n* license: mit\r\n* platforms: all\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162652/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162618","id":1158392824,"node_id":"I_kwDOAEVQ_M5FC6v4","number":162618,"title":"CPack on Darwin can't handle CPACK_DMG_SLA_LANGUAGES (CoreServices missing)","user":{"login":"OPNA2608","id":23431373,"node_id":"MDQ6VXNlcjIzNDMxMzcz","avatar_url":"https://avatars.githubusercontent.com/u/23431373?v=4","gravatar_id":"","url":"https://api.github.com/users/OPNA2608","html_url":"https://github.com/OPNA2608","followers_url":"https://api.github.com/users/OPNA2608/followers","following_url":"https://api.github.com/users/OPNA2608/following{/other_user}","gists_url":"https://api.github.com/users/OPNA2608/gists{/gist_id}","starred_url":"https://api.github.com/users/OPNA2608/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/OPNA2608/subscriptions","organizations_url":"https://api.github.com/users/OPNA2608/orgs","repos_url":"https://api.github.com/users/OPNA2608/repos","events_url":"https://api.github.com/users/OPNA2608/events{/privacy}","received_events_url":"https://api.github.com/users/OPNA2608/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-03T13:11:50Z","updated_at":"2022-03-04T16:40:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n[Our CMake packages](https://hydra.nixos.org/build/166589797/nixlog/1) are built without `CoreServices`.\r\n\r\n> ```\r\n> -- Looking for CoreServices/CoreServices.h\r\n> -- Looking for CoreServices/CoreServices.h - not found\r\n> CMake Warning at Source/CMakeLists.txt:1127 (message):\r\n> This compiler does not appear to support\r\n> \r\n> #include <CoreServices/CoreServices.h>\r\n> \r\n> Some CPack functionality may be limited.\r\n> \r\n> See CMakeFiles/CMakeError.log for details of the failure.\r\n> ```\r\n\r\nLike the warning suggests, this leads to some missing functionalities. Trying to `cpack` a project that sets [CPACK_DMG_SLA_LANGUAGES](https://cmake.org/cmake/help/v3.23/cpack_gen/dmg.html#variable:CPACK_DMG_SLA_LANGUAGES) will throw an error about the language being unknown, because [the code that handles locale -> language & region translation requires CoreServices](https://github.com/Kitware/CMake/blob/1ca83ae2bbf9e474c46b6ea094c5035420bbfd45/Source/CPack/cmCPackDragNDropGenerator.cxx#L593-L603).\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Build a CMake project that uses CPack, the DragNDrop/Bundle generator and a license agreement + license language setting\r\ni.e. https://github.com/tildearrow/furnace\r\n```sh\r\nnix-shell -p cmake pkg-config libsndfile fmt_8 zlib darwin.apple_sdk.frameworks.{Cocoa,AudioUnit,CoreAudio,CoreServices,ForceFeedback,OpenGL,AVFoundation}\r\n# Configure with `cmake -DBUILD_GUI=ON -DSYSTEM_FMT=ON -DSYSTEM_LIBSNDFILE=ON -DSYSTEM_ZLIB=ON`\r\n```\r\n2. Run `cpack`\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nA package gets generated without errors.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n\r\n\r\n### Additional context\r\nn/a\r\n\r\n### Notify maintainers\r\n@ttuegel @lnl7\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nMac:nixpkgs puna$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-darwin\"`\r\n- host os: `Darwin 17.7.0, macOS 10.13.6`\r\n- multi-user?: `no`\r\n- sandbox: `no`\r\n- version: `nix-env (Nix) 2.5.1`\r\n- channels(puna): `\"nixpkgs-22.05pre357729.22dc22f8ced\"`\r\n- nixpkgs: `/Users/puna/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162618/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162585","id":1158029476,"node_id":"I_kwDOAEVQ_M5FBiCk","number":162585,"title":"nix bundle doesn't work together with buildFHSUserEnv","user":{"login":"luochen1990","id":2309868,"node_id":"MDQ6VXNlcjIzMDk4Njg=","avatar_url":"https://avatars.githubusercontent.com/u/2309868?v=4","gravatar_id":"","url":"https://api.github.com/users/luochen1990","html_url":"https://github.com/luochen1990","followers_url":"https://api.github.com/users/luochen1990/followers","following_url":"https://api.github.com/users/luochen1990/following{/other_user}","gists_url":"https://api.github.com/users/luochen1990/gists{/gist_id}","starred_url":"https://api.github.com/users/luochen1990/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/luochen1990/subscriptions","organizations_url":"https://api.github.com/users/luochen1990/orgs","repos_url":"https://api.github.com/users/luochen1990/repos","events_url":"https://api.github.com/users/luochen1990/events{/privacy}","received_events_url":"https://api.github.com/users/luochen1990/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-03T06:37:23Z","updated_at":"2022-03-03T06:38:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`nix bundle` doesn't work together with `buildFHSUserEnv`\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. wget [venv-py37.nix](https://gist.githubusercontent.com/luochen1990/030ddc18716e5b8b14374621be524d9a/raw/9338de1174b23747fe70cbd4b7b85f67765352d8/venv-py37.nix)\r\n2. run `nix bundle -f ./venv-py37.nix` (this might take minutes)\r\n3. run `./venv-py37`\r\n\r\n### Expected behavior\r\n\r\nEnter bash successfully.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nnothing\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.16.3-zen1, NixOS, 22.05 (Quokka)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n- channels(root): `\"n-22.05pre346355.d5dae6569ea, nixos-22.05pre346355.d5dae6569ea, nixpkgs-22.05pre346086.e5a50e8f299\"`\r\n- channels(lc): `\"n-21.11pre325514.a4bf4434570, nixos-21.11pre325514.a4bf4434570\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162585/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162562","id":1157908788,"node_id":"I_kwDOAEVQ_M5FBEk0","number":162562,"title":"Packaging Request: GameScope","user":{"login":"Krutonium","id":3945538,"node_id":"MDQ6VXNlcjM5NDU1Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/3945538?v=4","gravatar_id":"","url":"https://api.github.com/users/Krutonium","html_url":"https://github.com/Krutonium","followers_url":"https://api.github.com/users/Krutonium/followers","following_url":"https://api.github.com/users/Krutonium/following{/other_user}","gists_url":"https://api.github.com/users/Krutonium/gists{/gist_id}","starred_url":"https://api.github.com/users/Krutonium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Krutonium/subscriptions","organizations_url":"https://api.github.com/users/Krutonium/orgs","repos_url":"https://api.github.com/users/Krutonium/repos","events_url":"https://api.github.com/users/Krutonium/events{/privacy}","received_events_url":"https://api.github.com/users/Krutonium/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-03T02:52:07Z","updated_at":"2022-03-09T22:57:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nThis is the Wayland based compositor that Valve is using, that when paired with a running application, can fix minimizing and other such issues, as well as allowing AMD FSR on any application.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/Plagman/gamescope\r\n* source URL: https://github.com/Plagman/gamescope\r\n* license: BSD 2 Clause\r\n* platforms: Linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562/reactions","total_count":4,"+1":4,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162562/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162528","id":1157656303,"node_id":"I_kwDOAEVQ_M5FAG7v","number":162528,"title":"`nix flake check` fails for yarn packages","user":{"login":"mkhl","id":505,"node_id":"MDQ6VXNlcjUwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/505?v=4","gravatar_id":"","url":"https://api.github.com/users/mkhl","html_url":"https://github.com/mkhl","followers_url":"https://api.github.com/users/mkhl/followers","following_url":"https://api.github.com/users/mkhl/following{/other_user}","gists_url":"https://api.github.com/users/mkhl/gists{/gist_id}","starred_url":"https://api.github.com/users/mkhl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mkhl/subscriptions","organizations_url":"https://api.github.com/users/mkhl/orgs","repos_url":"https://api.github.com/users/mkhl/repos","events_url":"https://api.github.com/users/mkhl/events{/privacy}","received_events_url":"https://api.github.com/users/mkhl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-02T20:26:38Z","updated_at":"2022-04-10T16:57:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`nix flake check` fails for yarn packages\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. git clone https://github.com/mkhl/yarn-flake-check\r\n2. cd yarn-flake-check\r\n3. nix flake check\r\n\r\n### Expected behavior\r\nthe checks succeed\r\n\r\n### Screenshots\r\n```console\r\nerror: a 'aarch64-linux' with features {} is required to build '/nix/store/ayfxz488paiyyaiz6sbgcdvv5r063g1a-yarn.nix.drv', but I am a 'x86_64-linux' with features {benchmark, big-parallel, kvm, nixos-test}\r\n```\r\n\r\n### Additional context\r\nnone\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nmaybe @jtojnar?\r\n\r\n### Metadata\r\n\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.11-200.fc35.x86_64, Fedora Linux, 35 (Workstation Edition)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(mkhl): `\"nixpkgs\"`\r\n - nixpkgs: `/home/mkhl/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162528/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162456","id":1156449926,"node_id":"I_kwDOAEVQ_M5E7gaG","number":162456,"title":"minecraftServers questions/feedback","user":{"login":"jyooru","id":63786778,"node_id":"MDQ6VXNlcjYzNzg2Nzc4","avatar_url":"https://avatars.githubusercontent.com/u/63786778?v=4","gravatar_id":"","url":"https://api.github.com/users/jyooru","html_url":"https://github.com/jyooru","followers_url":"https://api.github.com/users/jyooru/followers","following_url":"https://api.github.com/users/jyooru/following{/other_user}","gists_url":"https://api.github.com/users/jyooru/gists{/gist_id}","starred_url":"https://api.github.com/users/jyooru/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jyooru/subscriptions","organizations_url":"https://api.github.com/users/jyooru/orgs","repos_url":"https://api.github.com/users/jyooru/repos","events_url":"https://api.github.com/users/jyooru/events{/privacy}","received_events_url":"https://api.github.com/users/jyooru/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-02T05:27:47Z","updated_at":"2022-03-11T03:38:04Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"The `minecraftServers` package set was introduced in #150197, and since then I've been working on [jyooru/nix-minecraft-servers](https://github.com/jyooru/nix-minecraft-servers). I now have packages for paper, purpur, vanilla, velocity and waterfall, and each package is generated using some JSON that is automatically updated (jyooru/nix-minecraft-servers#58 for example).\r\n\r\nI would now like to add some of these packages back into nixpkgs and also automatically update them here too.\r\n\r\nI would like some feedback from the nixpkgs community on how this should be done:\r\n\r\n- what versions should be included in nixpkgs? Right now all minor (1.17, 1.16, ...) versions are available. I think this is fine, but should I do the same for the other Minecraft servers?\r\n- when/how often should they an automated PR be created? I think weekly is fine.\r\n\r\n---\r\n\r\ncc @tomberek as you were interested in this flake\r\n\r\nAlso not sure what labels I should be adding to this issue, so please add the correct ones if I got them wrong.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162456/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162454","id":1156402664,"node_id":"I_kwDOAEVQ_M5E7U3o","number":162454,"title":"fetchFromGitHub doesn't work if there is a branch and tag with the same name","user":{"login":"glglwty","id":4530335,"node_id":"MDQ6VXNlcjQ1MzAzMzU=","avatar_url":"https://avatars.githubusercontent.com/u/4530335?v=4","gravatar_id":"","url":"https://api.github.com/users/glglwty","html_url":"https://github.com/glglwty","followers_url":"https://api.github.com/users/glglwty/followers","following_url":"https://api.github.com/users/glglwty/following{/other_user}","gists_url":"https://api.github.com/users/glglwty/gists{/gist_id}","starred_url":"https://api.github.com/users/glglwty/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/glglwty/subscriptions","organizations_url":"https://api.github.com/users/glglwty/orgs","repos_url":"https://api.github.com/users/glglwty/repos","events_url":"https://api.github.com/users/glglwty/events{/privacy}","received_events_url":"https://api.github.com/users/glglwty/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786406134,"node_id":"MDU6TGFiZWw3ODY0MDYxMzQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20fetch","name":"6.topic: fetch","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-02T04:58:04Z","updated_at":"2022-03-03T02:52:32Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen using fetchFomGithub on a repo with a branch and a tag with the same name, fetchFromGitHub fails. This happens to different packages in nixpkgs and is particularly visible if binary cache is disabled.\r\n\r\n### Steps To Reproduce\r\nFetch `alacritty` with revision directly taken from nixpkgs master:\r\n```\r\n$ nix-shell -E 'with import <nixpkgs> { }; builtins.readDir ( fetchFromGitHub {\r\n owner = \"alacritty\";\r\n repo = \"alacritty\";\r\n rev = \"v0.10.0\";\r\n sha256 = \"sha256-eVPy47T2wcsN7NxtwMoyuC6loBVXsoJjJ/2q31i3vxQ=\";\r\n }) \"\"' --show-trace --check --option substitute false\r\nbuilding '/nix/store/sclf6z8vrm00v9941jmnqd4n8yyfgawm-source.drv'...\r\n\r\ntrying https://github.com/alacritty/alacritty/archive/v0.10.0.tar.gz\r\n % Total % Received % Xferd Average Speed Time Time Time Current\r\n Dload Upload Total Spent Left Speed\r\n100 105 100 105 0 0 867 0 --:--:-- --:--:-- --:--:-- 867\r\nunpacking source archive /build/v0.10.0.tar.gz\r\ntar: This does not look like a tar archive\r\n\r\ngzip: stdin: not in gzip format\r\ntar: Child returned status 1\r\ntar: Error is not recoverable: exiting now\r\ndo not know how to unpack source archive /build/v0.10.0.tar.gz\r\nerror: builder for '/nix/store/sclf6z8vrm00v9941jmnqd4n8yyfgawm-source.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > % Total % Received % Xferd Average Speed Time Time Time Current\r\n > Dload Upload Total Spent Left Speed\r\n > 100 105 100 105 0 0 867 0 --:--:-- --:--:-- --:--:-- 867\r\n > unpacking source archive /build/v0.10.0.tar.gz\r\n > tar: This does not look like a tar archive\r\n >\r\n > gzip: stdin: not in gzip format\r\n > tar: Child returned status 1\r\n > tar: Error is not recoverable: exiting now\r\n > do not know how to unpack source archive /build/v0.10.0.tar.gz\r\n For full logs, run 'nix log /nix/store/sclf6z8vrm00v9941jmnqd4n8yyfgawm-source.drv'.\r\n\r\n … while realising the context of path '/nix/store/ylbg2llv6ggkvfj7si162p73di41m9zh-source'\r\n\r\n at «string»:1:29:\r\n\r\n 1| with import <nixpkgs> { }; builtins.readDir ( fetchFromGitHub {\r\n | ^\r\n 2| owner = \"alacritty\";\r\n```\r\n\r\n### Expected behavior\r\nnix-shell should succeed\r\n\r\n### Additional context\r\nnix document suggests fetchFromGitHub is fetching a tag not a branch. I think it should be implemented as such. \r\n\r\n### Notify maintainers\r\n@jonringer \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.8, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos\"`\r\n - channels(glglwty): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162454/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162446","id":1156308658,"node_id":"I_kwDOAEVQ_M5E696y","number":162446,"title":"OvenMediaEngine: 0.13.1","user":{"login":"genofire","id":6905586,"node_id":"MDQ6VXNlcjY5MDU1ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6905586?v=4","gravatar_id":"","url":"https://api.github.com/users/genofire","html_url":"https://github.com/genofire","followers_url":"https://api.github.com/users/genofire/followers","following_url":"https://api.github.com/users/genofire/following{/other_user}","gists_url":"https://api.github.com/users/genofire/gists{/gist_id}","starred_url":"https://api.github.com/users/genofire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/genofire/subscriptions","organizations_url":"https://api.github.com/users/genofire/orgs","repos_url":"https://api.github.com/users/genofire/repos","events_url":"https://api.github.com/users/genofire/events{/privacy}","received_events_url":"https://api.github.com/users/genofire/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-02T03:44:43Z","updated_at":"2022-03-02T03:44:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: [oven-media-engine](https://search.nixos.org/packages?channel=21.11&from=0&size=50&sort=relevance&type=packages&query=oven-media)\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.10.9-hotfix\r\ndesired version: 0.13.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @lukegb\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162446/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162435","id":1156137891,"node_id":"I_kwDOAEVQ_M5E6UOj","number":162435,"title":"Raspberry Pi 3B+ does not boot with latest kernel from 21.11","user":{"login":"terinjokes","id":273509,"node_id":"MDQ6VXNlcjI3MzUwOQ==","avatar_url":"https://avatars.githubusercontent.com/u/273509?v=4","gravatar_id":"","url":"https://api.github.com/users/terinjokes","html_url":"https://github.com/terinjokes","followers_url":"https://api.github.com/users/terinjokes/followers","following_url":"https://api.github.com/users/terinjokes/following{/other_user}","gists_url":"https://api.github.com/users/terinjokes/gists{/gist_id}","starred_url":"https://api.github.com/users/terinjokes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/terinjokes/subscriptions","organizations_url":"https://api.github.com/users/terinjokes/orgs","repos_url":"https://api.github.com/users/terinjokes/repos","events_url":"https://api.github.com/users/terinjokes/events{/privacy}","received_events_url":"https://api.github.com/users/terinjokes/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-03-02T01:32:06Z","updated_at":"2022-03-02T01:48:17Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThis is a 21.11 follow up of #142848. I was running 21.11, and upgraded today (to 5.10.102) and now my boot fails with:\r\n\r\n```\r\nMoving image from 0x80000 to 0x200000, end=3140000\r\nERROR: RD image overlaps OS image (OS=0x200000..0x3140000)\r\n[...]\r\nSCRIPT FAILED: continuing...\r\nlibfdt fdt_check_header(): FDT_ERR_BADMAGIC\r\n```\r\n\r\nPer `/etc/extlinux/extlinux.conf`, I had upgraded to `2022-03-02 00:25 - 21.11.336182.a25df4c2b79`.\r\n\r\n## Expected behavior\r\n\r\nSuccessfully boot from the SD card.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162435/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162432","id":1156057932,"node_id":"I_kwDOAEVQ_M5E6AtM","number":162432,"title":"Package adw-gtk3, a port of Gnome's GTK4 libadwaita GTK theme to GTK3","user":{"login":"berbiche","id":20448408,"node_id":"MDQ6VXNlcjIwNDQ4NDA4","avatar_url":"https://avatars.githubusercontent.com/u/20448408?v=4","gravatar_id":"","url":"https://api.github.com/users/berbiche","html_url":"https://github.com/berbiche","followers_url":"https://api.github.com/users/berbiche/followers","following_url":"https://api.github.com/users/berbiche/following{/other_user}","gists_url":"https://api.github.com/users/berbiche/gists{/gist_id}","starred_url":"https://api.github.com/users/berbiche/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/berbiche/subscriptions","organizations_url":"https://api.github.com/users/berbiche/orgs","repos_url":"https://api.github.com/users/berbiche/repos","events_url":"https://api.github.com/users/berbiche/events{/privacy}","received_events_url":"https://api.github.com/users/berbiche/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-03-02T00:41:04Z","updated_at":"2022-03-03T05:28:35Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\nadw-gtk3 is a port of Gnome's GTK4 libadwaita GTK theme to GTK3.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/lassekongo83/adw-gtk3\r\n* source URL: https://github.com/lassekongo83/adw-gtk3\r\n* license: LGPL 2.1\r\n* platforms: Linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162432/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162398","id":1155611395,"node_id":"I_kwDOAEVQ_M5E4TsD","number":162398,"title":"Disallow declaring options named `config` and `options` (and others)","user":{"login":"infinisil","id":20525370,"node_id":"MDQ6VXNlcjIwNTI1Mzcw","avatar_url":"https://avatars.githubusercontent.com/u/20525370?v=4","gravatar_id":"","url":"https://api.github.com/users/infinisil","html_url":"https://github.com/infinisil","followers_url":"https://api.github.com/users/infinisil/followers","following_url":"https://api.github.com/users/infinisil/following{/other_user}","gists_url":"https://api.github.com/users/infinisil/gists{/gist_id}","starred_url":"https://api.github.com/users/infinisil/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/infinisil/subscriptions","organizations_url":"https://api.github.com/users/infinisil/orgs","repos_url":"https://api.github.com/users/infinisil/repos","events_url":"https://api.github.com/users/infinisil/events{/privacy}","received_events_url":"https://api.github.com/users/infinisil/received_events","type":"User","site_admin":false},"labels":[{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-03-01T17:27:26Z","updated_at":"2022-03-03T15:36:26Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\nOptions being allowed to be named `config` and `options` causes problems related to module syntax. The canonical module syntax has a number of _sections_, mainly `config`, `options`, `imports`, `disabledModules` and `freeformType`, which are the only allowed top-level attributes. This might look like\r\n\r\n```nix\r\n{\r\n imports = [ ... ];\r\n options = ...;\r\n config = ...;\r\n\r\n # Not allowed\r\n foo = ...;\r\n}\r\n```\r\n\r\nBut another syntax, sometimes called shorthand syntax, is also supported, which triggers when neither `options` nor `config` is set. In this alternate syntax, setting arbitrary attributes is valid, with the semantics that they get put into the `config` section. This might look like this:\r\n\r\n```nix\r\n{\r\n imports = [ ... ];\r\n # options, config <- needs to not be defined\r\n \r\n foo = ...;\r\n}\r\n```\r\n\r\nThis is then equivalent to\r\n\r\n```nix\r\n{\r\n imports = [ ... ];\r\n config.foo = ...;\r\n}\r\n```\r\n\r\nIf you don't need any option definitions, this syntax is more convenient.\r\n\r\n---\r\n\r\nThe problem arises when you have options with names matching the section names, such as `config`, `options`, `imports`, or others. Assuming we have an option named `options`, then we can't use the convenient shorthand syntax:\r\n\r\n```nix\r\n{\r\n # Since `options` is declared, the canonical syntax is used, not the shorthand one,\r\n # making this be an option declaration, not a definition!\r\n options = ...;\r\n}\r\n```\r\n\r\nTo actually declare this option you need to use\r\n\r\n```nix\r\n{\r\n config.options = ...;\r\n}\r\n``` \r\n\r\nSimilarly, if you have an option named `config`, you can't do\r\n\r\n```nix\r\n{\r\n config = ...;\r\n}\r\n```\r\n\r\nbut instead need to write\r\n\r\n```nix\r\n{\r\n config.config = ...;\r\n}\r\n```\r\n\r\nIf options have a name matching another section name, like `imports` or `disallowedModules`, shorthand syntax also can't be used, because these attributes are interpreted as sections, not options definitions. E.g. with an option named `imports`, the following doesn't work:\r\n\r\n```nix\r\n{\r\n imports = ...;\r\n}\r\n```\r\n\r\nInstead this is needed:\r\n\r\n```nix\r\n{\r\n config.imports = ...;\r\n}\r\n```\r\n\r\n---\r\n\r\nThese same problems are also caused by submodules, except that there it's even more nuanced, because submodules declared with `types.submodule` historically have always forced the shorthand syntax by wrapping its definitions into a `config` value. This was done to prevent surprises when trying to set a `config` option. E.g. if you have an option `foo` of type `types.submodule`, which itself has a nested `config` option, then you can do this:\r\n\r\n```nix\r\n{\r\n foo.config = ...;\r\n}\r\n```\r\n\r\nInstead of having to do this:\r\n```nix\r\n{\r\n foo.config.config = ...;\r\n}\r\n```\r\n\r\nBut the flip side is that there's no way to then declare non-`config` sections. The only known hack around this is to declare values as a function, because only attribute values are wrapped under `config` (since anything else wouldn't be valid as av config value):\r\n\r\n```nix\r\n{\r\n foo = { ... }: {\r\n options = ...;\r\n };\r\n}\r\n```\r\n\r\nWith the introduction of `types.submoduleWith`, a parameter `shorthandOnlyDefinesConfig` was introduced, which controls whether this `config` wrapping is done, defaulting to it not being done (in contrast with `types.submodule`)\r\n\r\n## Suggested solution\r\n\r\nBy disallowing options to be named according to a section name, we can always know whether an attribute is a section or an option name, allowing us to avoid all these problems:\r\n- No more weird edge cases regarding shorthand syntax: Every option can be defined using shorthand syntax.\r\n- The whole `config` wrapping for `types.submodule` and `types.submoduleWith` can be removed, cleaning up code and removing the need for function hacks.\r\n- We should also change the rule of \"`options` or `config` being set implies canonical syntax\" to just \"`config` being set implies canonical syntax\". If options can't be named `options`, then there's no reason options couldn't be declared using an `options` attribute while using shorthand syntax for `config`.\r\n\r\nThe hardest part is backwards compatibility and transition, because in NixOS there are a whole bunch of options named `config` and some named `options` (and one named `imports`). Another section name that could be problematic is `key`.\r\n\r\nWe should also consider whether it's possible to rename `config` and `options` to something else. I've heard complaints in the past that these have been confusing.\r\n\r\nPing @roberth @zimbatm ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398/reactions","total_count":5,"+1":5,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162398/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162390","id":1155552033,"node_id":"I_kwDOAEVQ_M5E4FMh","number":162390,"title":"`perlPackages.XMLLibXSLT` fails on M1 Mac","user":{"login":"xave","id":8461063,"node_id":"MDQ6VXNlcjg0NjEwNjM=","avatar_url":"https://avatars.githubusercontent.com/u/8461063?v=4","gravatar_id":"","url":"https://api.github.com/users/xave","html_url":"https://github.com/xave","followers_url":"https://api.github.com/users/xave/followers","following_url":"https://api.github.com/users/xave/following{/other_user}","gists_url":"https://api.github.com/users/xave/gists{/gist_id}","starred_url":"https://api.github.com/users/xave/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/xave/subscriptions","organizations_url":"https://api.github.com/users/xave/orgs","repos_url":"https://api.github.com/users/xave/repos","events_url":"https://api.github.com/users/xave/events{/privacy}","received_events_url":"https://api.github.com/users/xave/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":1236941869,"node_id":"MDU6TGFiZWwxMjM2OTQxODY5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20TeX","name":"6.topic: TeX","color":"fef2c0","default":false,"description":"Issues regarding texlive and TeX in general"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-03-01T16:32:42Z","updated_at":"2022-03-25T20:49:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Describe the bug**\r\n\r\nRunning the command ```nix-env -iA nixpkgs.texlive.combined.scheme-full``` fails with errors on M1 Mac. \r\n\r\nSee log.\r\n\r\n**Steps To Reproduce**\r\n\r\n1. Run nix-env -iA nixpkgs.texlive.combined.scheme-full\r\n2. Failure.\r\n\r\n**Expected Behavior**\r\nA successful installation of the package.\r\n\r\n**nix-env --version output**\r\n```nix-env (Nix) 2.6.1```\r\n\r\n**Additional context**\r\n[texlive-nix-log.txt](https://github.com/NixOS/nix/files/8155234/texlive-nix-log.txt)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162390/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162387","id":1155525081,"node_id":"I_kwDOAEVQ_M5E3-nZ","number":162387,"title":"buildDotnetPackage: xbuild tool is deprecated and will be removed in future updates, use msbuild instead","user":{"login":"milahu","id":12958815,"node_id":"MDQ6VXNlcjEyOTU4ODE1","avatar_url":"https://avatars.githubusercontent.com/u/12958815?v=4","gravatar_id":"","url":"https://api.github.com/users/milahu","html_url":"https://github.com/milahu","followers_url":"https://api.github.com/users/milahu/followers","following_url":"https://api.github.com/users/milahu/following{/other_user}","gists_url":"https://api.github.com/users/milahu/gists{/gist_id}","starred_url":"https://api.github.com/users/milahu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/milahu/subscriptions","organizations_url":"https://api.github.com/users/milahu/orgs","repos_url":"https://api.github.com/users/milahu/repos","events_url":"https://api.github.com/users/milahu/events{/privacy}","received_events_url":"https://api.github.com/users/milahu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-03-01T16:08:19Z","updated_at":"2022-03-03T08:48:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"`buildDotnetPackage` is using deprecated `xcode` build tool, should use `msbuild` tool\r\n\r\n### Reproduce\r\n\r\nbuild [subtitleedit](https://github.com/SubtitleEdit/subtitleedit) with\r\n\r\n```nix\r\n/*\r\nnix-build -E 'with import <nixpkgs> { }; callPackage ./default.nix { }'\r\n*/\r\n\r\n{ lib\r\n, fetchFromGitHub\r\n, buildDotnetPackage\r\n}:\r\n\r\nbuildDotnetPackage rec {\r\n pname = \"subtitleedit\";\r\n baseName = pname; # legacy\r\n version = \"3.6.4\";\r\n src = fetchFromGitHub {\r\n owner = \"SubtitleEdit\";\r\n repo = \"subtitleedit\";\r\n rev = version;\r\n sha256 = \"5EW9qPSVbKRpWy2oR1zailECStWRYnzzGO6rxIRctN0=\";\r\n };\r\n projectFile = \"SubtitleEdit.sln\";\r\n}\r\n```\r\n\r\n> `building`\r\n> `Building dotNET packages...`\r\n> \r\n> `>>>> xbuild tool is deprecated and will be removed in future updates, use msbuild instead <<<<`\r\n>\r\n> ...\r\n>\r\n> `The default XML namespace of the project must be the MSBuild XML namespace. If the project is authored in the MSBuild 2003 format, please add xmlns=\"http://schemas.microsoft.com/developer/msbuild/2003\" to the <Project> element. If the project has been authored in the old 1.0 or 1.2 format, please convert it to MSBuild 2003 format.`\r\n\r\n\"xbuild tool is deprecated\" is just a warning\r\n\r\nthe build crashes at the \"XML namespace\" error,\r\nwhich is caused by the source file [subtitleedit/src/libse/LibSE.csproj](https://github.com/SubtitleEdit/subtitleedit/blob/master/src/libse/LibSE.csproj).\r\nthis error disappears when i use `msbuild`\r\n\r\n### Workaround\r\n\r\nin buildPhase, replace xbuild with msbuild\r\n\r\n```nix\r\n/*\r\nnix-build -E 'with import <nixpkgs> { }; callPackage ./default.nix { }'\r\n*/\r\n\r\n{ lib\r\n, fetchFromGitHub\r\n, buildDotnetPackage\r\n, msbuild\r\n}:\r\n\r\nbuildDotnetPackage rec {\r\n pname = \"subtitleedit\";\r\n baseName = pname; # legacy\r\n version = \"3.6.4\";\r\n src = fetchFromGitHub {\r\n owner = \"SubtitleEdit\";\r\n repo = \"subtitleedit\";\r\n rev = version;\r\n sha256 = \"5EW9qPSVbKRpWy2oR1zailECStWRYnzzGO6rxIRctN0=\";\r\n };\r\n projectFile = \"SubtitleEdit.sln\";\r\n buildInputs = [\r\n msbuild\r\n ];\r\n buildPhase = ''\r\n runHook preBuild\r\n msbuild ${projectFile} /p:Configuration=Release\r\n runHook postBuild\r\n '';\r\n}\r\n```\r\n\r\n### Nixpkgs files\r\n\r\nbuildDotnetPackage = [nixpkgs/pkgs/build-support/dotnet/build-dotnet-package/default.nix](https://github.com/NixOS/nixpkgs/blob/master/pkgs/build-support/dotnet/build-dotnet-package/default.nix)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.99, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-21.11pre331460.931ab058daa\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162387/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162304","id":1154847321,"node_id":"I_kwDOAEVQ_M5E1ZJZ","number":162304,"title":"SANE hangs when using brscan5 backend with certain scanners","user":{"login":"jclangst","id":13301098,"node_id":"MDQ6VXNlcjEzMzAxMDk4","avatar_url":"https://avatars.githubusercontent.com/u/13301098?v=4","gravatar_id":"","url":"https://api.github.com/users/jclangst","html_url":"https://github.com/jclangst","followers_url":"https://api.github.com/users/jclangst/followers","following_url":"https://api.github.com/users/jclangst/following{/other_user}","gists_url":"https://api.github.com/users/jclangst/gists{/gist_id}","starred_url":"https://api.github.com/users/jclangst/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jclangst/subscriptions","organizations_url":"https://api.github.com/users/jclangst/orgs","repos_url":"https://api.github.com/users/jclangst/repos","events_url":"https://api.github.com/users/jclangst/events{/privacy}","received_events_url":"https://api.github.com/users/jclangst/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-03-01T04:16:22Z","updated_at":"2022-03-04T16:19:41Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSANE hangs when reading the results of a scan using brscan5 backend and the ADS-2800 scanner. \r\n\r\nObservations:\r\n\r\n- Can find and connect to the scanner\r\n- Is able to detect when the document feeder is empty or full\r\n- Is able to initiate a scan\r\n- Appears to hang when reading the scanned bytes from the document\r\n- Same behavior observed regardless of connecting via WLAN, LAN, or USB.\r\n- Same behavior observed when using version 1.2.9 and 1.2.7 (1.2.6 from `nixos-21.11` is no longer provided on Brother's website)\r\n- Same behavior observed after disabling firewalls and ipv6\r\n- Same behavior observed after enabling + disabling `avahi` with `nssmdns` and `reflector` enabled + disabled as well\r\n- I have another scanner in my Brother printer (HL-L2395DW) which works fine under these configurations; though it connects using the sane-escl backend (`escl:http://fe80::dee9:94ff:fe1b:9728:80`)\r\n\r\n### Steps To Reproduce\r\n\r\n1. Connect an ADS-2XXX scanner from Brother to your local network or computer via USB\r\n2. Set up the following configuration:\r\n\r\n```nix\r\n # Scanning driver for Brother scanners (brother no longer provides the default version in nixpkgs)\r\n nixpkgs.overlays = [\r\n (self: super: {\r\n brscan5 = config.nix-unstable.brscan5; # Alias for nixos-unstable since broken on nixos-21.11\r\n })\r\n ];\r\n hardware.sane = {\r\n enable = true;\r\n brscan5.enable = true;\r\n };\r\n services.saned.enable = true;\r\n```\r\n\r\n3. Attempt to scan using any scanner (e.g., simplescan, `gscan2pdf`, `scanimage`, etc.)\r\n4. Program will hang after the scanner scans the documents (yes, the scanner does actually scan the documents; SANE just cannot read the results using this backend)\r\n\r\n### Expected behavior\r\n\r\nSANE is able to read the scanned bytes back rather than hang.\r\n\r\n### Logs\r\n\r\nHere is an `stace` of the a `scanimage` run when connected via USB. Notice that it appears to hang when trying to first read the results of the scanned image: https://pastebin.com/M3iU0LLU\r\n\r\nResults of `netstat -tuonp` for the saned ports:\r\n\r\n<details>\r\n\r\n```text\r\ntcp 9 0 127.0.0.1:6566 127.0.0.1:36186 CLOSE_WAIT 1/systemd off (0.00/0/0)\r\ntcp 9 0 127.0.0.1:6566 127.0.0.1:36174 CLOSE_WAIT 1/systemd off (0.00/0/0)\r\ntcp 0 0 127.0.0.1:36252 127.0.0.1:6566 ESTABLISHED 331273/scanimage off (0.00/0/0)\r\ntcp 0 0 127.0.0.1:6566 127.0.0.1:36244 ESTABLISHED 1/systemd off (0.00/0/0)\r\ntcp 0 0 127.0.0.1:36244 127.0.0.1:6566 ESTABLISHED 327271/simple-scan off (0.00/0/0)\r\ntcp 9 0 127.0.0.1:6566 127.0.0.1:36148 CLOSE_WAIT 1/systemd off (0.00/0/0)\r\ntcp 0 0 127.0.0.1:6566 127.0.0.1:36252 ESTABLISHED 1/systemd off (0.00/0/0)\r\n```\r\n</details>\r\n\r\nResults of `scanimage -L`:\r\n\r\n<details>\r\n\r\n```text\r\ndevice `v4l:/dev/video1' is a Noname HD Webcam C615 virtual device\r\ndevice `net:localhost:brother5:bus3;dev3' is a Brother ADS-2800W USB scanner\r\n```\r\n</details>\r\n\r\nResults of `brsaneconfig5 -d`\r\n<details>\r\n\r\n```text\r\nsane-find-scanner\r\n\r\n # sane-find-scanner will now attempt to detect your scanner. If the\r\n # result is different from what you expected, first make sure your\r\n # scanner is powered up and properly connected to your computer.\r\n\r\n # No SCSI scanners found. If you expected something different, make sure that\r\n # you have loaded a kernel SCSI driver for your SCSI adapter.\r\n # Also you need support for SCSI Generic (sg) in your operating system.\r\n # If using Linux, try \"modprobe sg\".\r\n\r\ncould not open USB device 0x1d6b/0x0003 at 008:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x04d9/0x4545 at 007:010: Access denied (insufficient permissions)\r\ncould not open USB device 0x046d/0xc52b at 007:009: Access denied (insufficient permissions)\r\ncould not open USB device 0x0a5c/0x21e8 at 007:008: Access denied (insufficient permissions)\r\ncould not open USB device 0x0bda/0x5411 at 007:007: Access denied (insufficient permissions)\r\ncould not open USB device 0x0556/0x0001 at 007:006: Access denied (insufficient permissions)\r\ncould not open USB device 0x046d/0x082c at 007:005: Access denied (insufficient permissions)\r\ncould not open USB device 0x0bda/0x5411 at 007:003: Access denied (insufficient permissions)\r\ncould not open USB device 0x0e8d/0x7612 at 007:002: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0002 at 007:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0003 at 006:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0002 at 005:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x174c/0x3074 at 004:002: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0003 at 004:001: Access denied (insufficient permissions)\r\nfound USB scanner (vendor=0x04f9 [Brother], product=0x03b9 [ADS-2800W]) at libusb:003:007\r\ncould not open USB device 0x174c/0x2074 at 003:002: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0002 at 003:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0003 at 002:001: Access denied (insufficient permissions)\r\ncould not open USB device 0x8087/0x0029 at 001:004: Access denied (insufficient permissions)\r\ncould not open USB device 0x0b05/0x18f3 at 001:005: Access denied (insufficient permissions)\r\ncould not open USB device 0x05e3/0x0610 at 001:003: Access denied (insufficient permissions)\r\ncould not open USB device 0x1d6b/0x0002 at 001:001: Access denied (insufficient permissions)\r\n # Your USB scanner was (probably) detected. It may or may not be supported by\r\n # SANE. Try scanimage -L and read the backend's manpage.\r\n\r\n # Not checking for parallel port scanners.\r\n\r\n # Most Scanners connected to the parallel port or other proprietary ports\r\n # can't be detected by this program.\r\n\r\n # You may want to run this program as root to find all devices. Once you\r\n # found the scanner devices, be sure to adjust access permissions as\r\n # necessary.\r\n-----------------------------\r\nls -R -all /proc/bus/usb\r\nls: cannot access '/proc/bus/usb': No such file or directory\r\n-----------------------------\r\ncat /proc/bus/usb/devices\r\ncat: /proc/bus/usb/devices: No such file or directory\r\n-----------------------------\r\nscanimage -L\r\ndevice `v4l:/dev/video1' is a Noname HD Webcam C615 virtual device\r\ndevice `net:localhost:brother5:bus3;dev3' is a Brother ADS-2800W USB scanner\r\n-----------------------------\r\n-----------------------------\r\nping\r\n```\r\n</details>\r\n\r\n### Notify maintainers\r\n\r\n@mattchrist\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.25, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336177.1622abf0e78\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162304/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162286","id":1154740650,"node_id":"I_kwDOAEVQ_M5E0_Gq","number":162286,"title":"python3Packages.torchvision: `UserWarning: Failed to load image Python extension: .../image.so`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-03-01T01:29:06Z","updated_at":"2022-03-01T21:41:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI'm getting an error trying to use torchvision:\r\n```\r\n/nix/store/nph95lnwyvrygjhjwrfxk9x9xh7klw6v-python3.9-torchvision-0.11.3/lib/python3.9/site-packages/torchvision/io/image.py:11: UserWarning: Failed to load image Python extension: /nix/store/nph95lnwyvrygjhjwrfxk9x9xh7klw6v-python3.9-torchvision-0.11.3/lib/python3.9/site-packages/torchvision/image.so: undefined symbol: _ZN5torch3jit17parseSchemaOrNameERKNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEE\r\n warn(f\"Failed to load image Python extension: {e}\")\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Checkout https://github.com/samuela/cifar10-fast at https://github.com/samuela/cifar10-fast/commit/a660ec033899d10820a1e57b480f949d6033716e.\r\n2. Follow the reproduction instructions [here](https://github.com/samuela/cifar10-fast#how-to-reproduce).\r\n3. Observe the warning/failure: \r\n```\r\n[nix-shell:~/dev/cifar10-fast]$ nixGLNvidia-510.47.03 python dawn.py\r\nDownloading datasets\r\n/nix/store/nph95lnwyvrygjhjwrfxk9x9xh7klw6v-python3.9-torchvision-0.11.3/lib/python3.9/site-packages/torchvision/io/image.py:11: UserWarning: Failed to load image Python extension: /nix/store/nph95lnwyvrygjhjwrfxk9x9xh7klw6v-python3.9-torchvision-0.11.3/lib/python3.9/site-packages/torchvision/image.so: undefined symbol: _ZN5torch3jit17parseSchemaOrNameERKNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEE\r\n warn(f\"Failed to load image Python extension: {e}\")\r\n```\r\n\r\n### Expected behavior\r\ntorchvision to run without failure.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nSee for context https://github.com/google/jax/discussions/9669.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@ericsagnes \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste hte result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.11.0-1028-aws, Ubuntu, 20.04.4 LTS (Focal Fossa)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(ubuntu): `\"home-manager, nixgl\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162286/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162260","id":1154463060,"node_id":"I_kwDOAEVQ_M5Ez7VU","number":162260,"title":"networking.interfaces.<name>.ipv4.routes makes network-addresses-<name>.service fail on boot","user":{"login":"pinpox","id":1719781,"node_id":"MDQ6VXNlcjE3MTk3ODE=","avatar_url":"https://avatars.githubusercontent.com/u/1719781?v=4","gravatar_id":"","url":"https://api.github.com/users/pinpox","html_url":"https://github.com/pinpox","followers_url":"https://api.github.com/users/pinpox/followers","following_url":"https://api.github.com/users/pinpox/following{/other_user}","gists_url":"https://api.github.com/users/pinpox/gists{/gist_id}","starred_url":"https://api.github.com/users/pinpox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pinpox/subscriptions","organizations_url":"https://api.github.com/users/pinpox/orgs","repos_url":"https://api.github.com/users/pinpox/repos","events_url":"https://api.github.com/users/pinpox/events{/privacy}","received_events_url":"https://api.github.com/users/pinpox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-02-28T19:25:25Z","updated_at":"2022-04-15T14:40:25Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nUsing this configuration to add a static route results in a failed unit during boot and no route created. Restarting the systemd unit succeeds and creates the route as intended, the problem seems to be that `network-addresses-enp0s20f0u4u1u1.service` does not wait until the network connection is ready.\r\n\r\n\r\n```nix\r\n networking.interfaces.enp0s20f0u4u1u1.ipv4.routes = [{\r\n address = \"10.88.88.0\";\r\n prefixLength = 24;\r\n via = \"192.168.2.1\";\r\n options = { metric = \"0\"; };\r\n }];\r\n```\r\n\r\n```\r\n» sudo systemctl list-units --failed\r\n UNIT LOAD ACTIVE SUB DESCRIPTION\r\n● network-addresses-enp0s20f0u4u1u1.service loaded failed failed Address configuration of enp0s20f0u4u1u1\r\n\r\n× journalctl -fu network-addresses-enp0s20f0u4u1u1.service.\r\n-- Boot 32cae321f4dd427a9d6a244f768ce21e --\r\nFeb 28 15:51:15 ahorn systemd[1]: Starting Address configuration of enp0s20f0u4u1u1...\r\nFeb 28 15:51:15 ahorn network-addresses-enp0s20f0u4u1u1-start[1315]: adding route 10.88.88.0/24... 'ip route add 10.88.88.0/24 metric 0 via 192.168.2.1 dev enp0s20f0u4u1u1' failed: Error: Nexthop has invalid gateway.\r\nFeb 28 15:51:15 ahorn systemd[1]: network-addresses-enp0s20f0u4u1u1.service: Main process exited, code=exited, status=1/FAILURE\r\nFeb 28 15:51:15 ahorn systemd[1]: network-addresses-enp0s20f0u4u1u1.service: Failed with result 'exit-code'.\r\nFeb 28 15:51:15 ahorn systemd[1]: Failed to start Address configuration of enp0s20f0u4u1u1.\r\n```\r\n\r\nRoutes before and after restarting the sytemd unit:\r\n```\r\n× route -n\r\nKernel IP routing table\r\nDestination Gateway Genmask Flags Metric Ref Use Iface\r\n0.0.0.0 192.168.2.1 0.0.0.0 UG 100 0 0 enp0s20f0u4u1u1\r\n0.0.0.0 192.168.2.1 0.0.0.0 UG 600 0 0 wlp61s0\r\n10.240.0.0 0.0.0.0 255.240.0.0 U 0 0 0 tinc.retiolum\r\n172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0\r\n172.18.0.0 0.0.0.0 255.255.0.0 U 0 0 0 br-ed7415dc9645\r\n172.19.0.0 0.0.0.0 255.255.0.0 U 0 0 0 br-c97153b7a14e\r\n192.168.2.0 0.0.0.0 255.255.255.0 U 100 0 0 enp0s20f0u4u1u1\r\n192.168.2.0 0.0.0.0 255.255.255.0 U 600 0 0 wlp61s0\r\n192.168.7.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0\r\n192.168.56.0 0.0.0.0 255.255.255.0 U 0 0 0 vboxnet0\r\n\r\n~\r\n× systemctl restart network-addresses-enp0s20f0u4u1u1.service\r\n\r\n~\r\n× route -n\r\nKernel IP routing table\r\nDestination Gateway Genmask Flags Metric Ref Use Iface\r\n0.0.0.0 192.168.2.1 0.0.0.0 UG 100 0 0 enp0s20f0u4u1u1\r\n0.0.0.0 192.168.2.1 0.0.0.0 UG 600 0 0 wlp61s0\r\n10.88.88.0 192.168.2.1 255.255.255.0 UG 0 0 0 enp0s20f0u4u1u1\r\n10.240.0.0 0.0.0.0 255.240.0.0 U 0 0 0 tinc.retiolum\r\n172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0\r\n172.18.0.0 0.0.0.0 255.255.0.0 U 0 0 0 br-ed7415dc9645\r\n172.19.0.0 0.0.0.0 255.255.0.0 U 0 0 0 br-c97153b7a14e\r\n192.168.2.0 0.0.0.0 255.255.255.0 U 100 0 0 enp0s20f0u4u1u1\r\n192.168.2.0 0.0.0.0 255.255.255.0 U 600 0 0 wlp61s0\r\n192.168.7.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0\r\n192.168.56.0 0.0.0.0 255.255.255.0 U 0 0 0 vboxnet0\r\n```\r\n\r\nThe issue can be fixed/worked around by adding:\r\n```nix \r\nsystemd.services.network-addresses-enp0s20f0u4u1u1 = { after = [ \"dhcpcd.service\" ]; };\r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add config snipped above to configuration.nix\r\n2. rebuild system\r\n3. reboot\r\n4. route -n\r\n\r\n### Expected behavior\r\nRoute is added and systemd unit does not require manual restart.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@witchof0x20 @Luflosi @symphorien @Artturin @pennae @MayNiklas \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.101, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(root): `\"\"`\r\n - channels(pinpox): `\"home-manager\"`\r\n - nixpkgs: `/nix/store/d9wpzgyjlpw1424kw2lyilah6690fnk3-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162260/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162211","id":1154034337,"node_id":"I_kwDOAEVQ_M5EySqh","number":162211,"title":"Packaging requests: TaskLite","user":{"login":"mnajib","id":2047490,"node_id":"MDQ6VXNlcjIwNDc0OTA=","avatar_url":"https://avatars.githubusercontent.com/u/2047490?v=4","gravatar_id":"","url":"https://api.github.com/users/mnajib","html_url":"https://github.com/mnajib","followers_url":"https://api.github.com/users/mnajib/followers","following_url":"https://api.github.com/users/mnajib/following{/other_user}","gists_url":"https://api.github.com/users/mnajib/gists{/gist_id}","starred_url":"https://api.github.com/users/mnajib/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mnajib/subscriptions","organizations_url":"https://api.github.com/users/mnajib/orgs","repos_url":"https://api.github.com/users/mnajib/repos","events_url":"https://api.github.com/users/mnajib/events{/privacy}","received_events_url":"https://api.github.com/users/mnajib/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-28T12:28:37Z","updated_at":"2022-03-01T04:17:52Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### TaskLite\r\n\r\n<img src=\"https://raw.githubusercontent.com/ad-si/TaskLite/master/tasklite-core/screenshots/withtag.svg\">\r\n\r\n\r\n**Project description**\r\nThe CLI task manager for power users built with Haskell and SQLite.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://tasklite.org/\r\n* source URL: https://github.com/ad-si/TaskLite\r\n* license: https://github.com/ad-si/TaskLite\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162211/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162141","id":1153552337,"node_id":"I_kwDOAEVQ_M5Ewc_R","number":162141,"title":"hplip fails to build on `aarch64-linux` for multiple reasons","user":{"login":"vikanezrimaya","id":7953163,"node_id":"MDQ6VXNlcjc5NTMxNjM=","avatar_url":"https://avatars.githubusercontent.com/u/7953163?v=4","gravatar_id":"","url":"https://api.github.com/users/vikanezrimaya","html_url":"https://github.com/vikanezrimaya","followers_url":"https://api.github.com/users/vikanezrimaya/followers","following_url":"https://api.github.com/users/vikanezrimaya/following{/other_user}","gists_url":"https://api.github.com/users/vikanezrimaya/gists{/gist_id}","starred_url":"https://api.github.com/users/vikanezrimaya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vikanezrimaya/subscriptions","organizations_url":"https://api.github.com/users/vikanezrimaya/orgs","repos_url":"https://api.github.com/users/vikanezrimaya/repos","events_url":"https://api.github.com/users/vikanezrimaya/events{/privacy}","received_events_url":"https://api.github.com/users/vikanezrimaya/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":315139041,"node_id":"MDU6TGFiZWwzMTUxMzkwNDE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20printing","name":"6.topic: printing","color":"fef2c0","default":false,"description":null},{"id":3536622080,"node_id":"LA_kwDOAEVQ_M7SzJIA","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20build%20failure","name":"0.kind: build failure","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-28T02:47:19Z","updated_at":"2022-02-28T04:23:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe recent fixes to disable `imageProcessor` in hplip didn't seem to properly work on `aarch64-linux`, making the whole package fail with a cryptic error. Additionally, due to a **dependency failure in PyQt5**, the package further refuses to build unless it's disabled.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. be an aarch64-linux user\r\n2. `nix build nixpkgs#hplip`\r\n3. watch it fail due to PyQt5 failure\r\n4. Realize that PyQt5 support can be disabled\r\n5. `nix build --impure --expr '(builtins.getFlake \"nixpkgs\").legacyPackages.aarch64-linux.hplip.override { withQt5 = false; }'`\r\n6. Watch it fail again with `-lImageProcessor`-related errors\r\n\r\n### Expected behavior\r\nhplip works\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nCurrent unstable as of writing this is `github:nixos/nixpkgs/7f9b6e2babf232412682c09e57ed666d8f84ac2d`.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\ncc @ttuegel as maintainer\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162141/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162116","id":1153389976,"node_id":"I_kwDOAEVQ_M5Ev1WY","number":162116,"title":"Packaging request: Eclipse Papyrus","user":{"login":"Jonasmadsen","id":36917429,"node_id":"MDQ6VXNlcjM2OTE3NDI5","avatar_url":"https://avatars.githubusercontent.com/u/36917429?v=4","gravatar_id":"","url":"https://api.github.com/users/Jonasmadsen","html_url":"https://github.com/Jonasmadsen","followers_url":"https://api.github.com/users/Jonasmadsen/followers","following_url":"https://api.github.com/users/Jonasmadsen/following{/other_user}","gists_url":"https://api.github.com/users/Jonasmadsen/gists{/gist_id}","starred_url":"https://api.github.com/users/Jonasmadsen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Jonasmadsen/subscriptions","organizations_url":"https://api.github.com/users/Jonasmadsen/orgs","repos_url":"https://api.github.com/users/Jonasmadsen/repos","events_url":"https://api.github.com/users/Jonasmadsen/events{/privacy}","received_events_url":"https://api.github.com/users/Jonasmadsen/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-27T20:36:05Z","updated_at":"2022-02-27T20:36:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nPapyrus is a open source Model-Based Engineering tool, build on eclipse.\r\n\r\nIt runs already directly from the folder using steam-run, however a proper package would be nice.\r\n\r\n**Metadata**\r\n\r\n* homepage URL:https://www.eclipse.org/papyrus/\r\n* source URL: https://git.eclipse.org/c/papyrus/org.eclipse.papyrus.git/\r\n* license: Eclipse Public License - v 2.0\r\n* platforms: Linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162116/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162103","id":1153336387,"node_id":"I_kwDOAEVQ_M5EvoRD","number":162103,"title":"Nheko fails to load mediaplayer plugin and cannot play videos","user":{"login":"DeeUnderscore","id":156239,"node_id":"MDQ6VXNlcjE1NjIzOQ==","avatar_url":"https://avatars.githubusercontent.com/u/156239?v=4","gravatar_id":"","url":"https://api.github.com/users/DeeUnderscore","html_url":"https://github.com/DeeUnderscore","followers_url":"https://api.github.com/users/DeeUnderscore/followers","following_url":"https://api.github.com/users/DeeUnderscore/following{/other_user}","gists_url":"https://api.github.com/users/DeeUnderscore/gists{/gist_id}","starred_url":"https://api.github.com/users/DeeUnderscore/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/DeeUnderscore/subscriptions","organizations_url":"https://api.github.com/users/DeeUnderscore/orgs","repos_url":"https://api.github.com/users/DeeUnderscore/repos","events_url":"https://api.github.com/users/DeeUnderscore/events{/privacy}","received_events_url":"https://api.github.com/users/DeeUnderscore/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-27T17:44:42Z","updated_at":"2022-02-27T17:44:42Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nNheko currently cannot play videos in app when they're posted to channels. It seems to indicate that it cannot load the relevant plugins from qtmultimedia.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start Nheko\r\n2. Try to play a video posted to any channel\r\n\r\n### Expected behavior\r\nThe video should play\r\n\r\n### Additional context\r\nStarting Nheko with `QT_DEBUG_PLUGINS=1` gives me the following logs:\r\n\r\n```\r\n[qml] [warning] QLibraryPrivate::loadPlugin failed on \"/nix/store/vy93y5glgdq0w0acmsfpvw52nmffd29n-qtmultimedia-5.15.3-bin/lib/qt-5.15.3/plugins/mediaservice/libgstmediaplayer.so\" : \"Cannot load library /nix/store/vy93y5glgdq0w0acmsfpvw52nmffd29n-qtmultimedia-5.15.3-bin/lib/qt-5.15.3/plugins/mediaservice/libgstmediaplayer.so: (/nix/store/ab5xb6va2c5xxgr2sscygx56j4jc56aq-gst-plugins-base-1.20.0/lib/libgstgl-1.0.so.0: undefined symbol: wl_proxy_marshal_flags)\" (:0, )\r\n[qml] [warning] defaultServiceProvider::requestService(): no service found for - \"org.qt-project.qt.mediaplayer\" (:0, )\r\n```\r\nI am running X, not Wayland (under Plasma).\r\n\r\n### Notify maintainers\r\n@ekleog @fpletz\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.10, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.1`\r\n - channels(d): `\"\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/nix/store/6lk1r8frx7rw1spfbfj2hi88fb853w17-source`\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162103/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162100","id":1153327925,"node_id":"I_kwDOAEVQ_M5EvmM1","number":162100,"title":"PowerTunnel - censorship circumvention proxy server","user":{"login":"piousdeer","id":31318219,"node_id":"MDQ6VXNlcjMxMzE4MjE5","avatar_url":"https://avatars.githubusercontent.com/u/31318219?v=4","gravatar_id":"","url":"https://api.github.com/users/piousdeer","html_url":"https://github.com/piousdeer","followers_url":"https://api.github.com/users/piousdeer/followers","following_url":"https://api.github.com/users/piousdeer/following{/other_user}","gists_url":"https://api.github.com/users/piousdeer/gists{/gist_id}","starred_url":"https://api.github.com/users/piousdeer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piousdeer/subscriptions","organizations_url":"https://api.github.com/users/piousdeer/orgs","repos_url":"https://api.github.com/users/piousdeer/repos","events_url":"https://api.github.com/users/piousdeer/events{/privacy}","received_events_url":"https://api.github.com/users/piousdeer/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-27T17:18:58Z","updated_at":"2022-02-27T17:18:58Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n> Simple, scalable, cross-platform and effective solution against government censorship \r\n\r\n> PowerTunnel is an extensible proxy server built on top of [LittleProxy](https://github.com/adamfisk/LittleProxy).\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/krlvm/PowerTunnel\r\n* source URL: https://github.com/krlvm/PowerTunnel\r\n* license: gpl3\r\n* platforms: unix, linux, darwin, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162100/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162064","id":1153177236,"node_id":"I_kwDOAEVQ_M5EvBaU","number":162064,"title":"libjfxwebkit.so missing in jdk in unstable channel","user":{"login":"linsui","id":36977733,"node_id":"MDQ6VXNlcjM2OTc3NzMz","avatar_url":"https://avatars.githubusercontent.com/u/36977733?v=4","gravatar_id":"","url":"https://api.github.com/users/linsui","html_url":"https://github.com/linsui","followers_url":"https://api.github.com/users/linsui/followers","following_url":"https://api.github.com/users/linsui/following{/other_user}","gists_url":"https://api.github.com/users/linsui/gists{/gist_id}","starred_url":"https://api.github.com/users/linsui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/linsui/subscriptions","organizations_url":"https://api.github.com/users/linsui/orgs","repos_url":"https://api.github.com/users/linsui/repos","events_url":"https://api.github.com/users/linsui/events{/privacy}","received_events_url":"https://api.github.com/users/linsui/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-27T10:48:42Z","updated_at":"2022-02-28T21:03:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThere is libjfxwebkit.so in openjdk 17 in 21.11 (on my system the path is `/nix/store/liziz11l6wjw4vrl45ad2255ak0n2cd8-openjdk-17.0.1+12/lib/openjdk/lib/`) while it is missed in unstable (on my system the path is `/nix/store/yirggs7jnyxbhdmk342f6an4ifkgmbgv-openjdk-17.0.1+12/lib/openjdk/lib/`).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install jdk from unstable\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@edwtjo @asbachb @bachp\r\n\r\n### Metadata\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98-hardened1, NixOS, 21.11 (Porcupine)`\r\n```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162064/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162061","id":1153142902,"node_id":"I_kwDOAEVQ_M5Eu5B2","number":162061,"title":"`pidgin` does not like `plugins` override via overlays","user":{"login":"trofi","id":226650,"node_id":"MDQ6VXNlcjIyNjY1MA==","avatar_url":"https://avatars.githubusercontent.com/u/226650?v=4","gravatar_id":"","url":"https://api.github.com/users/trofi","html_url":"https://github.com/trofi","followers_url":"https://api.github.com/users/trofi/followers","following_url":"https://api.github.com/users/trofi/following{/other_user}","gists_url":"https://api.github.com/users/trofi/gists{/gist_id}","starred_url":"https://api.github.com/users/trofi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/trofi/subscriptions","organizations_url":"https://api.github.com/users/trofi/orgs","repos_url":"https://api.github.com/users/trofi/repos","events_url":"https://api.github.com/users/trofi/events{/privacy}","received_events_url":"https://api.github.com/users/trofi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-27T10:07:56Z","updated_at":"2022-04-13T07:46:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI would prefer `pidgin` to always contain `window_merge` plugin. Here is my attempt:\r\n\r\n```\r\n$ nix build --impure --expr 'with import ./. { overlays = [(final: prev: { pidgin = prev.pidgin.override ({ plugins = [prev.pidgin-window-merge]; }); })]; }; pidgin'\r\nerror: infinite recursion encountered\r\n\r\n at //builtin/derivation.nix:19:19:\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\nBefore that I used `pidgin-with-plugins` attribute for the similar purpose.\r\n\r\nI think recursion is a manifestation of confusion of `pidgin` being an SDK for plugins (and binary itself) and `pidgin` being a wrapper around SDK, pidgin binary and plugins. Should plugins use some other attribute?\r\n\r\n### Notify maintainers\r\n\r\n@vcunat\r\n\r\nOne of the options would be to always use wrapper that embeds unwrapped pidgin:\r\n\r\n```diff\r\n--- a/pkgs/applications/networking/instant-messengers/pidgin-plugins/window-merge/default.nix\r\n+++ b/pkgs/applications/networking/instant-messengers/pidgin-plugins/window-merge/default.nix\r\n@@ -12 +12 @@ stdenv.mkDerivation rec {\r\n- buildInputs = [ pidgin ];\r\n+ buildInputs = [ pidgin.unwrapped ];\r\ndiff --git a/pkgs/applications/networking/instant-messengers/pidgin/default.nix b/pkgs/applications/networking/instant-messengers/pidgin/default.nix\r\nindex bd6febeaf9d..0e6c56bde29 100644\r\n--- a/pkgs/applications/networking/instant-messengers/pidgin/default.nix\r\n+++ b/pkgs/applications/networking/instant-messengers/pidgin/default.nix\r\n@@ -95,5 +95,4 @@ let unwrapped = stdenv.mkDerivation rec {\r\n-in if plugins == [] then unwrapped\r\n- else callPackage ./wrapper.nix {\r\n- inherit plugins;\r\n- pidgin = unwrapped;\r\n- }\r\n+in callPackage ./wrapper.nix {\r\n+ inherit plugins;\r\n+ pidgin = unwrapped;\r\n+}\r\ndiff --git a/pkgs/applications/networking/instant-messengers/pidgin/wrapper.nix b/pkgs/applications/networking/instant-messengers/pidgin/wrapper.nix\r\nindex d5641c24fb0..12c532c90df 100644\r\n--- a/pkgs/applications/networking/instant-messengers/pidgin/wrapper.nix\r\n+++ b/pkgs/applications/networking/instant-messengers/pidgin/wrapper.nix\r\n@@ -10,0 +11,3 @@ in symlinkJoin {\r\n+ passthru = {\r\n+ unwrapped = pidgin;\r\n+ };\r\n```\r\n\r\nOr alternatively expose 2 attributes:\r\n- `pidgin` (with meaning of former `pidgin-with-plugins`)\r\n- `pidgin-unwraped` (with meaning of former `pidgin` without plugins)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162061/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026/events","html_url":"https://github.com/NixOS/nixpkgs/issues/162026","id":1152438017,"node_id":"I_kwDOAEVQ_M5EsM8B","number":162026,"title":"wev fails to run on Gnome","user":{"login":"yl3dy","id":1311192,"node_id":"MDQ6VXNlcjEzMTExOTI=","avatar_url":"https://avatars.githubusercontent.com/u/1311192?v=4","gravatar_id":"","url":"https://api.github.com/users/yl3dy","html_url":"https://github.com/yl3dy","followers_url":"https://api.github.com/users/yl3dy/followers","following_url":"https://api.github.com/users/yl3dy/following{/other_user}","gists_url":"https://api.github.com/users/yl3dy/gists{/gist_id}","starred_url":"https://api.github.com/users/yl3dy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yl3dy/subscriptions","organizations_url":"https://api.github.com/users/yl3dy/orgs","repos_url":"https://api.github.com/users/yl3dy/repos","events_url":"https://api.github.com/users/yl3dy/events{/privacy}","received_events_url":"https://api.github.com/users/yl3dy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-26T22:56:59Z","updated_at":"2022-02-28T08:22:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`wev` is essentially unusable in NixOS 21.11 with Gnome 41: no keypresses are logged, no corresponding window is created.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Install wev via nix-env or globally;\r\n2. Run it with `$ wev`.\r\n\r\n### Observed behavior\r\n\r\nNo window is shown, the following error is in the terminal:\r\n\r\n wl_registry@2: error 0: invalid version for global wl_seat (18): have 5, wanted 6\r\n\r\n### Expected behavior\r\nA wev's window should appear, a log of keypresses should be in the terminal.\r\n\r\n### Additional info\r\n\r\n```console\r\n% wev -g\r\n[02: wl_registry] global: interface: 'wl_compositor', version: 4, name: 1\r\n[02: wl_registry] global: interface: 'wl_drm', version: 2, name: 2\r\n[02: wl_registry] global: interface: 'wl_shm', version: 1, name: 3\r\n[02: wl_registry] global: interface: 'wl_output', version: 2, name: 4\r\n[02: wl_registry] global: interface: 'wl_output', version: 2, name: 5\r\n[02: wl_registry] global: interface: 'zxdg_output_manager_v1', version: 3, name: 6\r\n[02: wl_registry] global: interface: 'wl_data_device_manager', version: 3, name: 7\r\n[02: wl_registry] global: interface: 'zwp_primary_selection_device_manager_v1', version: 1, name: 8\r\n[02: wl_registry] global: interface: 'gtk_primary_selection_device_manager', version: 1, name: 9\r\n[02: wl_registry] global: interface: 'wl_subcompositor', version: 1, name: 10\r\n[02: wl_registry] global: interface: 'xdg_wm_base', version: 3, name: 11\r\n[02: wl_registry] global: interface: 'zxdg_shell_v6', version: 1, name: 12\r\n[02: wl_registry] global: interface: 'wl_shell', version: 1, name: 13\r\n[02: wl_registry] global: interface: 'gtk_shell1', version: 5, name: 14\r\n[02: wl_registry] global: interface: 'wp_viewporter', version: 1, name: 15\r\n[02: wl_registry] global: interface: 'zwp_pointer_gestures_v1', version: 1, name: 16\r\n[02: wl_registry] global: interface: 'zwp_tablet_manager_v2', version: 1, name: 17\r\n[02: wl_registry] global: interface: 'wl_seat', version: 5, name: 18\r\n[02: wl_registry] global: interface: 'zwp_relative_pointer_manager_v1', version: 1, name: 19\r\n[02: wl_registry] global: interface: 'zwp_pointer_constraints_v1', version: 1, name: 20\r\n[02: wl_registry] global: interface: 'zxdg_exporter_v1', version: 1, name: 21\r\n[02: wl_registry] global: interface: 'zxdg_importer_v1', version: 1, name: 22\r\n[02: wl_registry] global: interface: 'zwp_linux_dmabuf_v1', version: 3, name: 23\r\n[02: wl_registry] global: interface: 'zwp_keyboard_shortcuts_inhibit_manager_v1', version: 1, name: 24\r\n[02: wl_registry] global: interface: 'zwp_text_input_manager_v3', version: 1, name: 25\r\n[02: wl_registry] global: interface: 'gtk_text_input_manager', version: 1, name: 26\r\n[02: wl_registry] global: interface: 'wp_presentation', version: 1, name: 27\r\n[02: wl_registry] global: interface: 'xdg_activation_v1', version: 1, name: 28\r\nwl_registry@2: error 0: invalid version for global wl_seat (18): have 5, wanted 6\r\n```\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n% nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.10, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336147.4275a321bea\"`\r\n - channels(user): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n### Maintainer pings\r\n\r\n@primeos","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/162026/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161975","id":1151808713,"node_id":"I_kwDOAEVQ_M5EpzTJ","number":161975,"title":"xpra start fails with \"parse_vt_settings: Cannot open /dev/tty0 (Permission denied)\"","user":{"login":"catern","id":5394722,"node_id":"MDQ6VXNlcjUzOTQ3MjI=","avatar_url":"https://avatars.githubusercontent.com/u/5394722?v=4","gravatar_id":"","url":"https://api.github.com/users/catern","html_url":"https://github.com/catern","followers_url":"https://api.github.com/users/catern/followers","following_url":"https://api.github.com/users/catern/following{/other_user}","gists_url":"https://api.github.com/users/catern/gists{/gist_id}","starred_url":"https://api.github.com/users/catern/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/catern/subscriptions","organizations_url":"https://api.github.com/users/catern/orgs","repos_url":"https://api.github.com/users/catern/repos","events_url":"https://api.github.com/users/catern/events{/privacy}","received_events_url":"https://api.github.com/users/catern/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-26T14:00:53Z","updated_at":"2022-03-10T04:05:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nRunning \"xpra start --daemon=no\" fails with this message:\r\n\r\n```\r\n2022-02-26 08:56:26,131 cannot use uinput for virtual devices:\r\n2022-02-26 08:56:26,131 [Errno 13] Failed to open the uinput device: Permission denied\r\n_XSERVTransSocketUNIXCreateListener: ...SocketCreateListener() failed\r\n_XSERVTransMakeAllCOTSServerListeners: server already running\r\n\r\nX.Org X Server 1.20.13\r\nX Protocol Version 11, Revision 0\r\nBuild Operating System: Nix \r\nCurrent Operating System: Linux earth 5.10.95 #1-NixOS SMP Sat Jan 29 09:26:11 UTC 2022 x86_64\r\nKernel command line: initrd=\\efi\\nixos\\9vzdn9vsrz5b4rphky4s7v1p2i72nad7-initrd-linux-5.10.95-initrd.efi init=/nix/store/a862fx7svgxbs1yngxhl8c4h2284jz95-nixos-system-earth-21.11.335733.f6ddd55d5f9/init loglevel=4\r\nBuild Date: 29 July 2021 06:48:50PM\r\n \r\nCurrent version of pixman: 0.38.4\r\n\tBefore reporting problems, check http://wiki.x.org\r\n\tto make sure that you have the latest version.\r\nMarkers: (--) probed, (**) from config file, (==) default setting,\r\n\t(++) from command line, (!!) notice, (II) informational,\r\n\t(WW) warning, (EE) error, (NI) not implemented, (??) unknown.\r\n(++) Log file: \"/run/user/1000/xpra/S2631240/Xorg.log\", Time: Sat Feb 26 08:56:26 2022\r\n(==) Using system config directory \"/nix/store/4rivhhg2ndfj26d11zr1q61grwh3yzn8-xorg-server-1.20.13/share/X11/xorg.conf.d\"\r\n(EE) \r\nFatal server error:\r\n(EE) parse_vt_settings: Cannot open /dev/tty0 (Permission denied)\r\n(EE) \r\n(EE) \r\nPlease consult the The X.Org Foundation support \r\n\t at http://wiki.x.org\r\n for help. \r\n(EE) Please also check the log file at \"/run/user/1000/xpra/S2631240/Xorg.log\" for additional information.\r\n(EE) \r\n(EE) Server terminated with error (1). Closing log file.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `xpra start --daemon=no`\r\n\r\n### Expected behavior\r\nxpra should work.\r\n\r\n### Notify maintainers\r\n@numinit @mvnetbiz @offlinehacker \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nnix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.00 MiB download, 0.00 MiB unpacked):\r\n /nix/store/q124axggd6wl6fh9508sxgkknkifrl0z-nix-info\r\ncopying path '/nix/store/q124axggd6wl6fh9508sxgkknkifrl0z-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.95, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.15`\r\n - channels(ksongnichols): `\"nixpkgs-20.09pre224406.5f14d99efed\"`\r\n - channels(sbaugh): `\"nixpkgs-22.05pre355202.b66b39216b1\"`\r\n - channels(root): `\"nixos-21.11.335733.f6ddd55d5f9, nixos-unstable-22.05pre350838.554d2d8aa25\"`\r\n - nixpkgs: `/home/sbaugh/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161975/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161928","id":1151347859,"node_id":"I_kwDOAEVQ_M5EoCyT","number":161928,"title":"MCUXpresso package","user":{"login":"lonesomebyte537","id":53977119,"node_id":"MDQ6VXNlcjUzOTc3MTE5","avatar_url":"https://avatars.githubusercontent.com/u/53977119?v=4","gravatar_id":"","url":"https://api.github.com/users/lonesomebyte537","html_url":"https://github.com/lonesomebyte537","followers_url":"https://api.github.com/users/lonesomebyte537/followers","following_url":"https://api.github.com/users/lonesomebyte537/following{/other_user}","gists_url":"https://api.github.com/users/lonesomebyte537/gists{/gist_id}","starred_url":"https://api.github.com/users/lonesomebyte537/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lonesomebyte537/subscriptions","organizations_url":"https://api.github.com/users/lonesomebyte537/orgs","repos_url":"https://api.github.com/users/lonesomebyte537/repos","events_url":"https://api.github.com/users/lonesomebyte537/events{/privacy}","received_events_url":"https://api.github.com/users/lonesomebyte537/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-26T06:54:43Z","updated_at":"2022-02-26T06:54:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**mcuxpresso ide**\r\n_Embedded firmware development suite for NXP mcu's_\r\n\r\n* homepage URL: https://www.nxp.com/design/software/development-software/mcuxpresso-software-and-tools-/mcuxpresso-integrated-development-environment-ide:MCUXpresso-IDE\r\n* source URL: https://www.nxp.com/design/software/development-software/mcuxpresso-software-and-tools-/mcuxpresso-integrated-development-environment-ide:MCUXpresso-IDE\r\n* license: ?\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161928/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161903","id":1151031859,"node_id":"I_kwDOAEVQ_M5Em1oz","number":161903,"title":"parted commands in the NixOS manual assigns same PARTLABEL \"primary\" to multiple GPT partitions","user":{"login":"nmtake","id":18096192,"node_id":"MDQ6VXNlcjE4MDk2MTky","avatar_url":"https://avatars.githubusercontent.com/u/18096192?v=4","gravatar_id":"","url":"https://api.github.com/users/nmtake","html_url":"https://github.com/nmtake","followers_url":"https://api.github.com/users/nmtake/followers","following_url":"https://api.github.com/users/nmtake/following{/other_user}","gists_url":"https://api.github.com/users/nmtake/gists{/gist_id}","starred_url":"https://api.github.com/users/nmtake/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nmtake/subscriptions","organizations_url":"https://api.github.com/users/nmtake/orgs","repos_url":"https://api.github.com/users/nmtake/repos","events_url":"https://api.github.com/users/nmtake/events{/privacy}","received_events_url":"https://api.github.com/users/nmtake/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-26T01:42:23Z","updated_at":"2022-02-26T01:42:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`parted` commands in [the NixOS manual](https://github.com/NixOS/nixpkgs/blob/e40bc2494096f0b358fd2142de976164f4068ad6/nixos/doc/manual/installation/installing.chapter.md#installation-summary-sec-installation-summary) assigns same PARTLABEL \"primary\" to multiple GPT partitions. For example, following the manual would produce\r\n\r\n```\r\n$ sudo blkid /dev/loop0p{1,2,3}\r\n/dev/loop0p1: PARTLABEL=\"primary\" PARTUUID=\"576f450e-9f3a-429f-87bc-c9fb6fb508bd\"\r\n/dev/loop0p2: PARTLABEL=\"primary\" PARTUUID=\"ba5a2c4e-0adf-4111-924e-5eeb07e89ed6\"\r\n/dev/loop0p3: PARTLABEL=\"ESP\" PARTUUID=\"12f85517-dc51-4152-a1de-c582e8b87a81\"\r\n```\r\n\r\n### Steps To Reproduce\r\n\r\nThe manual uses following parted commands for GPT partitioning (copy-pasted from the page):\r\n\r\n```\r\n# parted /dev/sda -- mklabel gpt\r\n# parted /dev/sda -- mkpart primary 512MiB -8GiB\r\n# parted /dev/sda -- mkpart primary linux-swap -8GiB 100%\r\n# parted /dev/sda -- mkpart ESP fat32 1MiB 512MiB\r\n# parted /dev/sda -- set 3 esp on\r\n```\r\n\r\nSo I ran the following commands against a loop device:\r\n\r\n```\r\n$ dd if=/dev/zero of=file.img bs=1MiB count=10000\r\n$ sudo losetup /dev/loop0 file.img\r\n\r\n$ sudo parted /dev/loop0 -- mklabel gpt\r\n$ sudo parted /dev/loop0 -- mkpart primary 512MiB -8GiB\r\n$ sudo parted /dev/loop0 -- mkpart primary linux-swap -8GiB 100%\r\n$ sudo parted /dev/loop0 -- mkpart ESP fat32 1MiB 512MiB\r\n```\r\n\r\nNow the loop device looks like:\r\n\r\n```\r\n$ sudo blkid /dev/loop0p{1,2,3}\r\n/dev/loop0p1: PARTLABEL=\"primary\" PARTUUID=\"576f450e-9f3a-429f-87bc-c9fb6fb508bd\"\r\n/dev/loop0p2: PARTLABEL=\"primary\" PARTUUID=\"ba5a2c4e-0adf-4111-924e-5eeb07e89ed6\"\r\n/dev/loop0p3: PARTLABEL=\"ESP\" PARTUUID=\"12f85517-dc51-4152-a1de-c582e8b87a81\"\r\n```\r\n\r\n### Expected behavior\r\n\r\nAssign unique and meaningful `PARTLABEL`s to the paritions.\r\n\r\n### Additional context\r\n\r\n[Arch Wiki](https://wiki.archlinux.org/title/Parted#Partition_schemes) says:\r\n\r\n> Note: Many tutorials on the web use commands which start with mkpart\r\n> primary even for GPT. They are wrong, this would set \"primary\" as the partition label.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161903/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161803","id":1150175949,"node_id":"I_kwDOAEVQ_M5EjkrN","number":161803,"title":"steam package throws bad to comprehend error on unsupported arch","user":{"login":"RonnyPfannschmidt","id":156838,"node_id":"MDQ6VXNlcjE1NjgzOA==","avatar_url":"https://avatars.githubusercontent.com/u/156838?v=4","gravatar_id":"","url":"https://api.github.com/users/RonnyPfannschmidt","html_url":"https://github.com/RonnyPfannschmidt","followers_url":"https://api.github.com/users/RonnyPfannschmidt/followers","following_url":"https://api.github.com/users/RonnyPfannschmidt/following{/other_user}","gists_url":"https://api.github.com/users/RonnyPfannschmidt/gists{/gist_id}","starred_url":"https://api.github.com/users/RonnyPfannschmidt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/RonnyPfannschmidt/subscriptions","organizations_url":"https://api.github.com/users/RonnyPfannschmidt/orgs","repos_url":"https://api.github.com/users/RonnyPfannschmidt/repos","events_url":"https://api.github.com/users/RonnyPfannschmidt/events{/privacy}","received_events_url":"https://api.github.com/users/RonnyPfannschmidt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-25T08:29:31Z","updated_at":"2022-02-26T00:44:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nwhen trying to build steam for aarch64 a bad error in another place is thrown\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behaviour:\r\n1. accident accidentally add steam on aarch64-linux\r\n\r\n```\r\n$ nixos-rebuild build --flake .#rpi \r\nbuilding the system configuration...\r\nwarning: Git tree '/home/ronny/Projects/RonnyPfannschmidt/nixos' is dirty\r\nerror: i686 Linux package set can only be used with the x86 family.\r\n```\r\n\r\nthe trace ends up somewhere in the fhs builder bubble wrap scripts\r\n\r\n### Expected behaviour\r\n(happens when trying to add sublime to the set)\r\n```\r\nPackage ‘steam...’ in /nix/store/... is not supported on ‘aarch64-linux’, refusing to evaluate.\r\n```\r\n\r\n\r\ni suspect setting platforms might work","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161803/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161741","id":1149882395,"node_id":"I_kwDOAEVQ_M5EidAb","number":161741,"title":"rambox-pro: 2.0.1","user":{"login":"definitelynobody","id":51100439,"node_id":"MDQ6VXNlcjUxMTAwNDM5","avatar_url":"https://avatars.githubusercontent.com/u/51100439?v=4","gravatar_id":"","url":"https://api.github.com/users/definitelynobody","html_url":"https://github.com/definitelynobody","followers_url":"https://api.github.com/users/definitelynobody/followers","following_url":"https://api.github.com/users/definitelynobody/following{/other_user}","gists_url":"https://api.github.com/users/definitelynobody/gists{/gist_id}","starred_url":"https://api.github.com/users/definitelynobody/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/definitelynobody/subscriptions","organizations_url":"https://api.github.com/users/definitelynobody/orgs","repos_url":"https://api.github.com/users/definitelynobody/repos","events_url":"https://api.github.com/users/definitelynobody/events{/privacy}","received_events_url":"https://api.github.com/users/definitelynobody/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-24T23:44:54Z","updated_at":"2022-04-25T09:28:01Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"New release available at https://github.com/ramboxapp/download/releases\r\n\r\n###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: rambox-pro\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.5.0\r\ndesired version: 2.0.1\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @cawilliamson\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161741/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161716","id":1149712720,"node_id":"I_kwDOAEVQ_M5EhzlQ","number":161716,"title":"fs-uae-launcher: Qt issues?","user":{"login":"ehula","id":4238154,"node_id":"MDQ6VXNlcjQyMzgxNTQ=","avatar_url":"https://avatars.githubusercontent.com/u/4238154?v=4","gravatar_id":"","url":"https://api.github.com/users/ehula","html_url":"https://github.com/ehula","followers_url":"https://api.github.com/users/ehula/followers","following_url":"https://api.github.com/users/ehula/following{/other_user}","gists_url":"https://api.github.com/users/ehula/gists{/gist_id}","starred_url":"https://api.github.com/users/ehula/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ehula/subscriptions","organizations_url":"https://api.github.com/users/ehula/orgs","repos_url":"https://api.github.com/users/ehula/repos","events_url":"https://api.github.com/users/ehula/events{/privacy}","received_events_url":"https://api.github.com/users/ehula/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-24T20:22:42Z","updated_at":"2022-02-28T19:57:07Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"I installed fs-uae-launcher from home.nix. When I run it, I get the following:\r\n\r\n```\r\n[LOGGING] Logging to /home/user/FS-UAE/Cache/Logs/fs-uae-launcher.log.txt\r\nFS-UAE Launcher 3.0.5\r\n['/nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/bin/.fs-uae-launcher-wrapped']\r\nuname_result(system='Linux', node='framework', release='5.15.4', version='#1-NixOS SMP Sun Nov 21 12:44:15 UTC 2021', machine='x86_64')\r\nTraceback (most recent call last):\r\n File \"/nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/share/fs-uae-launcher/fsgs/archive.py\", line 15, in <module>\r\n from lhafile import LhaFile\r\nModuleNotFoundError: No module named 'lhafile'\r\n[ARCHIVE] LhaFile module import problem\r\n[SETTINGS] No settings path specified\r\n[SETTINGS] Using default /home/user/FS-UAE/Data/Settings.ini\r\n[SETTINGS] File /home/user/FS-UAE/Data/Settings.ini does not exist\r\n[I18N] Initialize_locale language =\r\n[I18N] Locale is en_US\r\n[I18N] Checking /nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/bin/share/fs-uae-launcher/share-dir\r\n[I18N] Checking /nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/bin/../share/fs-uae-launcher/share-dir\r\n[I18N] bindtextdomain fs-uae-launcher: /nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/bin/../share/locale\r\n[I18N] find translations for en_US in local directory /nix/store/mdb0n6wf5psq4m2x84p9b0xavzfqgcla-fs-uae-launcher-3.0.5/bin/../share/locale\r\n[I18N] Path to mo file: None\r\n[I18N] Translations object: <gettext.NullTranslations object at 0x7fbdf62615e0>\r\nqt.qpa.plugin: Could not find the Qt platform plugin \"xcb\" in \"\"\r\nThis application failed to start because no Qt platform plugin could be initialized. Reinstalling the application may fix this problem.\r\n\r\nAborted (core dumped)\r\n```\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334247.573095944e7\"`\r\n - channels(user): `\"home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n@svanderburg @AndersonTorres ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161716/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161610","id":1148817492,"node_id":"I_kwDOAEVQ_M5EeZBU","number":161610,"title":"Second Interface (wlp3s0) does not have external connectivity. ","user":{"login":"keithy","id":193501,"node_id":"MDQ6VXNlcjE5MzUwMQ==","avatar_url":"https://avatars.githubusercontent.com/u/193501?v=4","gravatar_id":"","url":"https://api.github.com/users/keithy","html_url":"https://github.com/keithy","followers_url":"https://api.github.com/users/keithy/followers","following_url":"https://api.github.com/users/keithy/following{/other_user}","gists_url":"https://api.github.com/users/keithy/gists{/gist_id}","starred_url":"https://api.github.com/users/keithy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/keithy/subscriptions","organizations_url":"https://api.github.com/users/keithy/orgs","repos_url":"https://api.github.com/users/keithy/repos","events_url":"https://api.github.com/users/keithy/events{/privacy}","received_events_url":"https://api.github.com/users/keithy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-24T03:27:21Z","updated_at":"2022-02-25T06:04:48Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA wired connection (enp0s10) works well until a wireless connection managed by wpa_supplicant (wlp3s0) is added.\r\n\r\n1. Firstly the wireless seems to automatically get priority, \r\n2. Outward connections are blocked by the firewall on that interface.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Using the wpa_supplicant to manage a wireless interface, in addition to the existing wired interface.\r\n2. ssh router -B wlp3s0 -vvv \r\n```\r\ndebug1: Connecting to router [10.11.12.1] port 22.\r\ndebug3: set_sock_tos: set socket 3 IP_TOS 0x48\r\ndebug1: ssh_create_socket: bound to 10.11.12.6\r\n\r\n$> netstat -an | grep 10.11.12.1\r\ntcp 0 1 10.11.12.6:46339 10.11.12.1:22 SYN_SENT\r\n```\r\n### Additional context\r\nA working configuration\r\n```\r\n # prioritise wired over wireless\r\n networking.dhcpcd.extraConfig = ''\r\n\r\n interface enp0s10\r\n metric 100\r\n\r\n interface wlp3s0\r\n metric 200\r\n '';\r\n networking.firewall.enable = true;\r\n networking.firewall.interfaces.\"wlp3s0\" = { allowedTCPPorts = [22]; };\r\n networking.firewall.checkReversePath = false;\r\n```\r\n### Notify maintainers\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.22, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n ```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161610/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161570","id":1148523522,"node_id":"I_kwDOAEVQ_M5EdRQC","number":161570,"title":"strictDeps breaks libs in checkInputs","user":{"login":"symphorien","id":12595971,"node_id":"MDQ6VXNlcjEyNTk1OTcx","avatar_url":"https://avatars.githubusercontent.com/u/12595971?v=4","gravatar_id":"","url":"https://api.github.com/users/symphorien","html_url":"https://github.com/symphorien","followers_url":"https://api.github.com/users/symphorien/followers","following_url":"https://api.github.com/users/symphorien/following{/other_user}","gists_url":"https://api.github.com/users/symphorien/gists{/gist_id}","starred_url":"https://api.github.com/users/symphorien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/symphorien/subscriptions","organizations_url":"https://api.github.com/users/symphorien/orgs","repos_url":"https://api.github.com/users/symphorien/repos","events_url":"https://api.github.com/users/symphorien/events{/privacy}","received_events_url":"https://api.github.com/users/symphorien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":20,"created_at":"2022-02-23T20:06:08Z","updated_at":"2022-04-03T07:10:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\ncheckInputs are added to nativeBuildInputs but not buildInputs when doCheck is set, so libs added to checkInputs cannot be found by compilers when strictDeps is true.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/master/pkgs/stdenv/generic/make-derivation.nix#L150-L151\r\n\r\n### Steps To Reproduce\r\n\r\n```nix\r\nwith import <nixpkgs> {};\r\nstdenv.mkDerivation {\r\n name = \"whatever\";\r\n checkInputs = [ zlib ];\r\n nativeBuildInputs = [ pkg-config ];\r\n doCheck = true;\r\n strictDeps = true;\r\n buildCommand = ''\r\n pkg-config --cflags zlib\r\n touch $out\r\n '';\r\n}\r\n\r\n```\r\nWhen strictDeps is set, pkg-config fails to find zlib, whereas it finds it without strictDeps.\r\n\r\nNote: needing libs in checkInputs is very common in ocamlPackages.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161570/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161566","id":1148466912,"node_id":"I_kwDOAEVQ_M5EdDbg","number":161566,"title":"Submodules need a default value","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":549491066,"node_id":"MDU6TGFiZWw1NDk0OTEwNjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20developer%20experience","name":"6.topic: developer experience","color":"fef2c0","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-23T19:01:55Z","updated_at":"2022-02-25T18:46:03Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nUnconfigured submodules don't work unless they specify a default, which should always be `{ }` to avoid surprises.\r\n\r\n### Steps To Reproduce\r\n\r\n```\r\nnix-repl> (lib.evalModules { modules = [ ({ lib, ... }: { options.it = lib.mkOption { type = lib.types.submodule {}; }; }) ]; }).config\r\n{ it = «error: error: The option `it' is used but not defined.»; }\r\n\r\n```\r\n\r\n### Expected behavior\r\n\r\nThe module system is clever enough to figure out that modules have their own defaults and are always attrsets, making `{ }` the obvious default.\r\n\r\n### Possible implementation\r\n\r\nThis works, but it's too broad.\r\n\r\n```diff\r\ndiff --git a/lib/modules.nix b/lib/modules.nix\r\nindex e9fc1007fc2..80da5e51e36 100644\r\n--- a/lib/modules.nix\r\n+++ b/lib/modules.nix\r\n@@ -649,6 +649,8 @@ rec {\r\n if all (def: type.check def.value) defsFinal then type.merge loc defsFinal\r\n else let allInvalid = filter (def: ! type.check def.value) defsFinal;\r\n in throw \"A definition for option `${showOption loc}' is not of type `${type.description}'. Definition values:${showDefs allInvalid}\"\r\n+ else if type.emptyValue?value then\r\n+ type.emptyValue.value\r\n else\r\n # (nixos-option detects this specific error message and gives it special\r\n # handling. If changed here, please change it there too.)\r\n```\r\n\r\nPerhaps `defaultValue` should be added to types, or `emptyValue` could be renamed.\r\n\r\n### Additional context\r\n\r\nhttps://github.com/NixOS/nixops/pull/1508#issuecomment-1049093934\r\n\r\n### Notify maintainers\r\n\r\n@Infinisil\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161566/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161537","id":1148211485,"node_id":"I_kwDOAEVQ_M5EcFEd","number":161537,"title":"Packaged Kate doesn't include Nix syntax highlighting","user":{"login":"NoraCodes","id":3290365,"node_id":"MDQ6VXNlcjMyOTAzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/3290365?v=4","gravatar_id":"","url":"https://api.github.com/users/NoraCodes","html_url":"https://github.com/NoraCodes","followers_url":"https://api.github.com/users/NoraCodes/followers","following_url":"https://api.github.com/users/NoraCodes/following{/other_user}","gists_url":"https://api.github.com/users/NoraCodes/gists{/gist_id}","starred_url":"https://api.github.com/users/NoraCodes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NoraCodes/subscriptions","organizations_url":"https://api.github.com/users/NoraCodes/orgs","repos_url":"https://api.github.com/users/NoraCodes/repos","events_url":"https://api.github.com/users/NoraCodes/events{/privacy}","received_events_url":"https://api.github.com/users/NoraCodes/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-23T15:05:09Z","updated_at":"2022-02-23T22:32:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhile KDE's Kate text editor does support syntax highlighting for the Nix language, the version of Kate available in NixOS associates `.nix` files with Bash.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open Kate\r\n2. Open a `.nix` Nix language file\r\n3. Observe incorrect syntax highlighting and, if the LSP client is enabled, an error about a failure to launch the Bash language server.\r\n\r\n### Expected behavior\r\nKate installed through NixOS should probably work out of the box with the Nix language. \r\n\r\n### Additional context\r\nThe syntax file for Nix is here: https://kate-editor.org/syntax/data/syntax/nix.xml\r\n\r\n### Notify maintainers\r\n@ttuegel \r\n\r\n### Metadata\r\n\r\n```console\r\n[nora@calembel:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.96, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336103.40ef692a55b\"`\r\n - channels(nora): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161537/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161431","id":1147452572,"node_id":"I_kwDOAEVQ_M5EZLyc","number":161431,"title":"Nvidia GPU support broken in LXC/LXD","user":{"login":"sersorrel","id":9433472,"node_id":"MDQ6VXNlcjk0MzM0NzI=","avatar_url":"https://avatars.githubusercontent.com/u/9433472?v=4","gravatar_id":"","url":"https://api.github.com/users/sersorrel","html_url":"https://github.com/sersorrel","followers_url":"https://api.github.com/users/sersorrel/followers","following_url":"https://api.github.com/users/sersorrel/following{/other_user}","gists_url":"https://api.github.com/users/sersorrel/gists{/gist_id}","starred_url":"https://api.github.com/users/sersorrel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sersorrel/subscriptions","organizations_url":"https://api.github.com/users/sersorrel/orgs","repos_url":"https://api.github.com/users/sersorrel/repos","events_url":"https://api.github.com/users/sersorrel/events{/privacy}","received_events_url":"https://api.github.com/users/sersorrel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-22T22:59:25Z","updated_at":"2022-02-23T00:12:01Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nUsing `nvidia.runtime=true` with `lxc launch` makes LXC unable to create the container.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `virtualisation.lxd.enable = true;`\r\n2. `lxc launch ubuntu:20.04 mycontainer -c nvidia.runtime=true`\r\n\r\n```console\r\n$ lxc launch ubuntu:20.04 mycontainer -c nvidia.runtime=true\r\nCreating mycontainer\r\nStarting mycontainer\r\nError: Failed to run: /nix/store/dfqrhkf2vr3gqmaxn61h3gqg3np1wpdi-lxd-4.20/bin/.lxd-wrapped forkstart mycontainer /var/lib/lxd/containers /var/log/lxd/mycontainer/lxc.conf:\r\nTry `lxc info --show-log local:mycontainer` for more info\r\n\r\n$ lxc info --show-log local:mycontainer\r\nName: mycontainer\r\nStatus: STOPPED\r\nType: container\r\nArchitecture: x86_64\r\nCreated: 2022/02/22 22:45 GMT\r\nLast Used: 2022/02/22 22:45 GMT\r\n\r\nLog:\r\n\r\nlxc mycontainer 20220222224534.857 WARN cgfsng - cgroups/cgfsng.c:fchowmodat:1251 - No such file or directory - Failed to fchownat(40, memory.oom.group, 65536, 0, AT_EMPTY_PATH | AT_SYMLINK_NOFOLLOW )\r\nlxc mycontainer 20220222224534.939 ERROR conf - conf.c:run_buffer:321 - Script exited with status 1\r\nlxc mycontainer 20220222224534.939 ERROR conf - conf.c:lxc_setup:4381 - Failed to run mount hooks\r\nlxc mycontainer 20220222224534.939 ERROR start - start.c:do_start:1274 - Failed to setup container \"mycontainer\"\r\nlxc mycontainer 20220222224534.939 ERROR sync - sync.c:sync_wait:34 - An error occurred in another process (expected sequence number 4)\r\nlxc mycontainer 20220222224534.942 WARN network - network.c:lxc_delete_network_priv:3617 - Failed to rename interface with index 0 from \"eth0\" to its initial name \"veth646f7af1\"\r\nlxc mycontainer 20220222224534.942 ERROR start - start.c:__lxc_start:2068 - Failed to spawn container \"mycontainer\"\r\nlxc mycontainer 20220222224534.942 ERROR lxccontainer - lxccontainer.c:wait_on_daemonized_start:867 - Received container state \"ABORTING\" instead of \"RUNNING\"\r\nlxc mycontainer 20220222224534.942 WARN start - start.c:lxc_abort:1038 - No such process - Failed to send SIGKILL via pidfd 41 for process 8652\r\nlxc 20220222224540.235 ERROR af_unix - af_unix.c:lxc_abstract_unix_recv_fds_iov:218 - Connection reset by peer - Failed to receive response\r\nlxc 20220222224540.236 ERROR commands - commands.c:lxc_cmd_rsp_recv_fds:127 - Failed to receive file descriptors\r\n```\r\n\r\n### Expected behavior\r\nI should be able to use my GPU in LXC containers: https://blog.simos.info/running-x11-software-in-lxd-containers/\r\n\r\n### Additional context\r\nI am sick of trying to work out how to debug the problem, but if someone who understands LXC/LXD knows how to get it to actually tell me what's going wrong, I can keep trying.\r\n\r\nHere's how far I got.\r\n\r\nFirstly, you need to set $LXD_LXC_HOOK to tell LXD where the LXC hooks are (https://github.com/lxc/lxd/blob/7cf7ff1403dab27ddb3798aa5ce9c48431401e36/lxd/instance/drivers/driver_lxc.go#L1041), otherwise it will look in /usr/share/lxc/hooks, which doesn't exist, and you'll see \"The NVIDIA LXC hook couldn't be found\". I did this by adding `--set LXD_LXC_HOOK ${lxc}/share/lxc/hooks` to the `wrapProgram` invocation in lxd's postInstall.\r\n\r\nNext, you'll find that it fails because `nvidia-container-cli` isn't available, and you'll see \"The NVIDIA container tools couldn't be found\". This is in nixpkgs, but it's not exposed publicly anywhere; I get the feeling you're meant to use `mkNvidiaContainerPkg` to get at it, but because I couldn't find _any_ documentation indicating sensible values to use for `containerRuntimePath` and `configTemplate`, I just added `(callPackage /path/to/the/nixpkgs/libnvidia-container {})` to the `makeBinPath` call in the lxd derivation.\r\n\r\nThen you're basically as far as I got! I also added `config.security.wrapperDir` to $PATH, because lxc was complaining about not being able to find newuidmap and newgidmap, as well as `glibc` to the `makeBinPath` call because it seemed to want `getent`, but neither helped the fundamental problem, and I can't work out how to make LXC or LXD print any more useful debugging information (like \"the output of the hook that's failing\"...)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@fpletz @wucke13 @marsam \r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.101, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(ash): `\"home-manager-21.11, nixos-unstable-22.05pre356435.7f9b6e2babf\"`\r\n - channels(root): `\"nixos-21.11.336103.40ef692a55b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161431/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161428","id":1147440937,"node_id":"I_kwDOAEVQ_M5EZI8p","number":161428,"title":"nftables module: absorb into firewall module, rename ruleset options","user":{"login":"flokli","id":183879,"node_id":"MDQ6VXNlcjE4Mzg3OQ==","avatar_url":"https://avatars.githubusercontent.com/u/183879?v=4","gravatar_id":"","url":"https://api.github.com/users/flokli","html_url":"https://github.com/flokli","followers_url":"https://api.github.com/users/flokli/followers","following_url":"https://api.github.com/users/flokli/following{/other_user}","gists_url":"https://api.github.com/users/flokli/gists{/gist_id}","starred_url":"https://api.github.com/users/flokli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/flokli/subscriptions","organizations_url":"https://api.github.com/users/flokli/orgs","repos_url":"https://api.github.com/users/flokli/repos","events_url":"https://api.github.com/users/flokli/events{/privacy}","received_events_url":"https://api.github.com/users/flokli/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":2,"created_at":"2022-02-22T22:40:35Z","updated_at":"2022-03-28T10:05:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Problem statement\r\n\r\nRight now, we have `networking.nftables` and `networking.firewall`.\r\n\r\nHowever, at least since https://github.com/NixOS/nixpkgs/pull/81172 (which got shipped in 21.11) we kinda default to using nftables, and all `ip[6]tables`/`arptables`/`ebtables` invocations essentially only modify `nf_tables` rules under the hood.\r\n\r\nThis means, most of the things we do in the `nftables` NixOS module should also be done by default, not just if we set `networking.nftables.enable` to true:\r\n\r\n```\r\n boot.blacklistedKernelModules = [ \"ip_tables\" ];\r\n environment.systemPackages = [ pkgs.nftables ];\r\n networking.networkmanager.firewallBackend = mkDefault \"nftables\";\r\n```\r\n\r\n - It kinda makes sense to blacklist the kernel module.\r\n - We might want to have the `nft` binary in `$PATH` to be able to see and modify these rules (at least in the cases where we have `iptables` & Co. in `$PATH`).\r\n - Configuring NetworkManager to use the `nftables` backend also makes sense. [systemd-networkd already does the same](https://github.com/NixOS/nixpkgs/pull/161426).\r\n\r\n--\r\n\r\nThere's an assertion preventing us to enable both the NixOS firewall and the nftables module, as the nftables module also creates a systemd unit that tries to (exclusively) configure all `nf_tables` tables (which is dooned to fail, as there's other things inserting into it, such as systemd-networkd, and [libvirt](https://github.com/NixOS/nixpkgs/issues/88643) (through `iptables-nft`)\r\n\r\n\r\n## Proposed Fix(es)\r\n\r\n - Absorb the above three config options into the firewall module, and enable them when firewall is enabled\r\n - Move `networking.nftables.ruleset` and `networking.nftables.rulesetFile` somewhere below `networking.firewall`, with a big fat disclaimer (`lib.warn`?) stating this doesn't compose with the rest of the NixOS firewall, or other things interacting with the firewall, as it exclusively replaces everything whenever restarted.\r\n\r\ncc @fpletz @misuzu @andir ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161428/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161367","id":1146889586,"node_id":"I_kwDOAEVQ_M5EXCVy","number":161367,"title":"i2pd: no support for Yggdrasil only router configuration","user":{"login":"ne9z","id":77314501,"node_id":"MDQ6VXNlcjc3MzE0NTAx","avatar_url":"https://avatars.githubusercontent.com/u/77314501?v=4","gravatar_id":"","url":"https://api.github.com/users/ne9z","html_url":"https://github.com/ne9z","followers_url":"https://api.github.com/users/ne9z/followers","following_url":"https://api.github.com/users/ne9z/following{/other_user}","gists_url":"https://api.github.com/users/ne9z/gists{/gist_id}","starred_url":"https://api.github.com/users/ne9z/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ne9z/subscriptions","organizations_url":"https://api.github.com/users/ne9z/orgs","repos_url":"https://api.github.com/users/ne9z/repos","events_url":"https://api.github.com/users/ne9z/events{/privacy}","received_events_url":"https://api.github.com/users/ne9z/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-22T13:06:59Z","updated_at":"2022-02-27T17:31:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nNixOS has no configuration options for yggdrasil-only i2p router, as described [in documentation](https://i2pd.readthedocs.io/en/latest/tutorials/yggdrasil-only-mode/).\r\n\r\nI have configured the server as described [here](https://gist.github.com/ne9z/912773cba81fd638b8541b198f1a8479).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nSee [here](https://gist.github.com/ne9z/912773cba81fd638b8541b198f1a8479).\r\n\r\n### Expected behavior\r\nUser should be able to use i2pd with yggdrasil only.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@edwtjo\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.99, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161367/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161358","id":1146817577,"node_id":"I_kwDOAEVQ_M5EWwwp","number":161358,"title":"profile should re-read env var settings when changed","user":{"login":"wmertens","id":54934,"node_id":"MDQ6VXNlcjU0OTM0","avatar_url":"https://avatars.githubusercontent.com/u/54934?v=4","gravatar_id":"","url":"https://api.github.com/users/wmertens","html_url":"https://github.com/wmertens","followers_url":"https://api.github.com/users/wmertens/followers","following_url":"https://api.github.com/users/wmertens/following{/other_user}","gists_url":"https://api.github.com/users/wmertens/gists{/gist_id}","starred_url":"https://api.github.com/users/wmertens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wmertens/subscriptions","organizations_url":"https://api.github.com/users/wmertens/orgs","repos_url":"https://api.github.com/users/wmertens/repos","events_url":"https://api.github.com/users/wmertens/events{/privacy}","received_events_url":"https://api.github.com/users/wmertens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-22T11:55:35Z","updated_at":"2022-02-22T11:55:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nright now /etc/profile looks at `__NIXOS_SET_ENVIRONMENT_DONE=1` to determine when to read the environment variables. This is meant to avoid loading the vars in subshells.\r\n\r\nHowever, when a new system is activated, this does not reload the env vars.\r\n\r\nInstead, it should check something like `__NIXOS_SET_ENVIRONMENT_DONE=current-system-hash`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. change an env var in the config\r\n2. `nixos-rebuild switch`\r\n3. open a terminal => var unchanged\r\n\r\n### Expected behavior\r\n\r\nNew env vars available in new terminal windows\r\n\r\n### How to fix\r\n\r\n[This line](https://github.com/NixOS/nixpkgs/blob/38346f64616c3176f73ad0f20e51557ec0f3d75d/nixos/modules/config/shells-environment.nix#L197) could be set to `$out` maybe?\r\n\r\nAnd then all shells have checks like https://github.com/NixOS/nixpkgs/blob/073ca0094b916a11f42b4a82654c5d9b0c9db7eb/nixos/modules/programs/bash/bash.nix#L121 but it would be easier to move the check to the environment file instead and return early.\r\n\r\nThoughts?\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161358/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161332","id":1146587078,"node_id":"I_kwDOAEVQ_M5EV4fG","number":161332,"title":"dotnet-ef","user":{"login":"kirinnee","id":15990242,"node_id":"MDQ6VXNlcjE1OTkwMjQy","avatar_url":"https://avatars.githubusercontent.com/u/15990242?v=4","gravatar_id":"","url":"https://api.github.com/users/kirinnee","html_url":"https://github.com/kirinnee","followers_url":"https://api.github.com/users/kirinnee/followers","following_url":"https://api.github.com/users/kirinnee/following{/other_user}","gists_url":"https://api.github.com/users/kirinnee/gists{/gist_id}","starred_url":"https://api.github.com/users/kirinnee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kirinnee/subscriptions","organizations_url":"https://api.github.com/users/kirinnee/orgs","repos_url":"https://api.github.com/users/kirinnee/repos","events_url":"https://api.github.com/users/kirinnee/events{/privacy}","received_events_url":"https://api.github.com/users/kirinnee/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-22T08:15:41Z","updated_at":"2022-02-22T08:15:41Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://docs.microsoft.com/en-us/ef/core/\r\n* source URL: https://github.com/dotnet/efcore\r\n* license: MIT\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161332/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161328","id":1146560219,"node_id":"I_kwDOAEVQ_M5EVx7b","number":161328,"title":"firewall: support SSDP","user":{"login":"wmertens","id":54934,"node_id":"MDQ6VXNlcjU0OTM0","avatar_url":"https://avatars.githubusercontent.com/u/54934?v=4","gravatar_id":"","url":"https://api.github.com/users/wmertens","html_url":"https://github.com/wmertens","followers_url":"https://api.github.com/users/wmertens/followers","following_url":"https://api.github.com/users/wmertens/following{/other_user}","gists_url":"https://api.github.com/users/wmertens/gists{/gist_id}","starred_url":"https://api.github.com/users/wmertens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wmertens/subscriptions","organizations_url":"https://api.github.com/users/wmertens/orgs","repos_url":"https://api.github.com/users/wmertens/repos","events_url":"https://api.github.com/users/wmertens/events{/privacy}","received_events_url":"https://api.github.com/users/wmertens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-22T07:43:05Z","updated_at":"2022-02-22T21:56:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"I want to control my Sonos system and it's hard to configure the firewall to allow this. I propose that we add a setting like `allowSsdp` to the firewall.\r\n\r\nI currently have these rules to make it work:\r\n\r\n```nix\r\n{\r\n networking.firewall.allowedTCPPorts = [\r\n # Sonos\r\n 1400\r\n ];\r\n\r\n # support SSDP https://serverfault.com/a/911286/9166\r\n networking.firewall.extraPackages = [ pkgs.ipset ];\r\n networking.firewall.extraCommands = ''\r\n if ! ipset --quiet list upnp; then\r\n ipset create upnp hash:ip,port timeout 3\r\n fi\r\n iptables -A OUTPUT -d 239.255.255.250/32 -p udp -m udp --dport 1900 -j SET --add-set upnp src,src --exist\r\n iptables -A nixos-fw -p udp -m set --match-set upnp dst,dst -j nixos-fw-accept\r\n '';\r\n}\r\n```\r\n\r\nThis creates a 3-second memory for multicast SSDP UDP traffic that was initiated from the system, to allow UDP answers back in.\r\n\r\nThere's no nixos-fw-output chain, how about adding that? Right now the OUTPUT rule gets inserted on every firewall start, because I'm not sure how to replace exactly that rule.\r\n\r\nIs this something that could go in the firewall module, or is that too specific?\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161328/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161318","id":1146463965,"node_id":"I_kwDOAEVQ_M5EVabd","number":161318,"title":"Packaging Request for arm_now","user":{"login":"Otus9051","id":58171861,"node_id":"MDQ6VXNlcjU4MTcxODYx","avatar_url":"https://avatars.githubusercontent.com/u/58171861?v=4","gravatar_id":"","url":"https://api.github.com/users/Otus9051","html_url":"https://github.com/Otus9051","followers_url":"https://api.github.com/users/Otus9051/followers","following_url":"https://api.github.com/users/Otus9051/following{/other_user}","gists_url":"https://api.github.com/users/Otus9051/gists{/gist_id}","starred_url":"https://api.github.com/users/Otus9051/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Otus9051/subscriptions","organizations_url":"https://api.github.com/users/Otus9051/orgs","repos_url":"https://api.github.com/users/Otus9051/repos","events_url":"https://api.github.com/users/Otus9051/events{/privacy}","received_events_url":"https://api.github.com/users/Otus9051/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-22T05:12:41Z","updated_at":"2022-02-22T05:12:41Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\narm_now is a qemu powered tool that allows instant setup of virtual machines on arm cpu, mips, powerpc, nios2, x86 and more, for reverse, exploit, fuzzing and programming purpose.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/nongiach/arm_now/wiki\r\n* source URL: https://github.com/nongiach/arm_now\r\n* license: mit\r\n* platforms: linux, darwin, wsl, docker\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161318/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161224","id":1145746265,"node_id":"I_kwDOAEVQ_M5ESrNZ","number":161224,"title":"services.gnome.gnome-keyring.enable = true; needs dconf as well","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-21T12:38:41Z","updated_at":"2022-02-21T12:38:49Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen enabling `servicse.gnome.gnome-keyring`, but not `programs.dconf`. The keyring will generally not work, but without very conclusive errors. Symptoms include:\r\n\r\n* Operations involving the keyring (like unlocking your GPG key) block for 30s-1min before continuing\r\n* No keyring shows up in `gnome.seahorse`, just SSH/GPG keys\r\n* Applications using `libsecret` aren't able to store any secrets\r\n\r\n### Steps To Reproduce\r\n\r\nPut\r\n\r\n```nix\r\n services.gnome.gnome-keyring.enable = true;\r\n programs.dconf.enable = false;\r\n```\r\n\r\ninto your `configuration.nix`.\r\n\r\n### Expected behavior\r\n\r\nThe `gnome-keyring` NixOS module should enable dconf if it depends on it.\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\ncc @NixOS/gnome","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161224/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161168","id":1145354807,"node_id":"I_kwDOAEVQ_M5ERLo3","number":161168,"title":"Unable to remove the default themes and plugins from services.wordpress as well as update wordpress?","user":{"login":"zeta-00","id":50250392,"node_id":"MDQ6VXNlcjUwMjUwMzky","avatar_url":"https://avatars.githubusercontent.com/u/50250392?v=4","gravatar_id":"","url":"https://api.github.com/users/zeta-00","html_url":"https://github.com/zeta-00","followers_url":"https://api.github.com/users/zeta-00/followers","following_url":"https://api.github.com/users/zeta-00/following{/other_user}","gists_url":"https://api.github.com/users/zeta-00/gists{/gist_id}","starred_url":"https://api.github.com/users/zeta-00/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zeta-00/subscriptions","organizations_url":"https://api.github.com/users/zeta-00/orgs","repos_url":"https://api.github.com/users/zeta-00/repos","events_url":"https://api.github.com/users/zeta-00/events{/privacy}","received_events_url":"https://api.github.com/users/zeta-00/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-21T05:54:35Z","updated_at":"2022-02-21T07:11:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nGreetings,\r\n\r\nI'm using the nixos services.wordpress module to host my website and it's going great, but, the issue that I'm having has to do with the built-in themes, plugins as well as wordpress itself.\r\n\r\nWhenever I update wordpress and it's plugins, there's still red update icons that show up and message that wordpress and the built-in themes and plugins are out of date?\r\n\r\n### Steps to reproduce\r\nAttempted to manually delete the built-in themes and plugins, and updated wordpress with nix, but, the red out of date notification still persists?\r\n\r\n\r\n## Technical details\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n> nix-info -m\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(apple): `\"\"`\r\n - channels(root): `\"darwin, home-manager, nixpkgs-unstable-21.11pre311289.503209808cd, nixpkgs-21.11pre309670.253aecf69ed\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161168/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161136","id":1145190555,"node_id":"I_kwDOAEVQ_M5EQjib","number":161136,"title":"Steam not loading Nvidia Vulkan libs","user":{"login":"tfmoraes","id":351108,"node_id":"MDQ6VXNlcjM1MTEwOA==","avatar_url":"https://avatars.githubusercontent.com/u/351108?v=4","gravatar_id":"","url":"https://api.github.com/users/tfmoraes","html_url":"https://github.com/tfmoraes","followers_url":"https://api.github.com/users/tfmoraes/followers","following_url":"https://api.github.com/users/tfmoraes/following{/other_user}","gists_url":"https://api.github.com/users/tfmoraes/gists{/gist_id}","starred_url":"https://api.github.com/users/tfmoraes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tfmoraes/subscriptions","organizations_url":"https://api.github.com/users/tfmoraes/orgs","repos_url":"https://api.github.com/users/tfmoraes/repos","events_url":"https://api.github.com/users/tfmoraes/events{/privacy}","received_events_url":"https://api.github.com/users/tfmoraes/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-21T00:46:16Z","updated_at":"2022-02-21T08:49:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nAfter this PR https://github.com/NixOS/nixpkgs/pull/158276 the Steam helper is not loading the Nvidia Vulkan libs inside the Steam environment. And because of that Proton is slow.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.8, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - nixpkgs: `/etc/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161136/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161126","id":1145155969,"node_id":"I_kwDOAEVQ_M5EQbGB","number":161126,"title":"ejabberd: not compiled with sqlite support","user":{"login":"ne9z","id":77314501,"node_id":"MDQ6VXNlcjc3MzE0NTAx","avatar_url":"https://avatars.githubusercontent.com/u/77314501?v=4","gravatar_id":"","url":"https://api.github.com/users/ne9z","html_url":"https://github.com/ne9z","followers_url":"https://api.github.com/users/ne9z/followers","following_url":"https://api.github.com/users/ne9z/following{/other_user}","gists_url":"https://api.github.com/users/ne9z/gists{/gist_id}","starred_url":"https://api.github.com/users/ne9z/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ne9z/subscriptions","organizations_url":"https://api.github.com/users/ne9z/orgs","repos_url":"https://api.github.com/users/ne9z/repos","events_url":"https://api.github.com/users/ne9z/events{/privacy}","received_events_url":"https://api.github.com/users/ne9z/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-20T22:43:24Z","updated_at":"2022-02-20T23:43:04Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI would like to use ejabberd with an sqlite database, but the package in NixOS is not compiled with such support.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable ejabberd\r\n2. Use sqlite database in configuration\r\n3. Apply changes\r\n\r\n### Expected behavior\r\nThe user should be able to use sqlite as database backend.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n```\r\n2022-02-21 06:35:19.751176+08:00 [critical] <0.249.0>@ejabberd:exit_or_halt/2:145 Failed to start Erlang application 'sqlite3': no such file or directory: sqlite3.app. This usually means that ejabberd or Erlang was compiled/installed incorrectly.\r\n```\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@genofire\r\n@svanderburg\r\n@abbradar\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98-hardened1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336020.2128d0aa28e\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161126/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161122","id":1145149338,"node_id":"I_kwDOAEVQ_M5EQZea","number":161122,"title":"convert nixos manpages to commonmark","user":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-20T22:11:46Z","updated_at":"2022-02-22T14:17:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"```\r\n./nixos/doc/manual/man-configuration.xml\r\n./nixos/doc/manual/man-nixos-build-vms.xml\r\n./nixos/doc/manual/man-nixos-enter.xml\r\n./nixos/doc/manual/man-nixos-generate-config.xml\r\n./nixos/doc/manual/man-nixos-install.xml\r\n./nixos/doc/manual/man-nixos-option.xml\r\n./nixos/doc/manual/man-nixos-rebuild.xml\r\n./nixos/doc/manual/man-nixos-version.xml\r\n./nixos/doc/manual/man-pages.xml\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161122/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161072","id":1145039375,"node_id":"I_kwDOAEVQ_M5EP-oP","number":161072,"title":"```nixos-rebuild test``` with ```users.mutableUsers = false;``` erases user and root credentials permanently","user":{"login":"LHurttila","id":55827968,"node_id":"MDQ6VXNlcjU1ODI3OTY4","avatar_url":"https://avatars.githubusercontent.com/u/55827968?v=4","gravatar_id":"","url":"https://api.github.com/users/LHurttila","html_url":"https://github.com/LHurttila","followers_url":"https://api.github.com/users/LHurttila/followers","following_url":"https://api.github.com/users/LHurttila/following{/other_user}","gists_url":"https://api.github.com/users/LHurttila/gists{/gist_id}","starred_url":"https://api.github.com/users/LHurttila/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/LHurttila/subscriptions","organizations_url":"https://api.github.com/users/LHurttila/orgs","repos_url":"https://api.github.com/users/LHurttila/repos","events_url":"https://api.github.com/users/LHurttila/events{/privacy}","received_events_url":"https://api.github.com/users/LHurttila/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-02-20T14:43:30Z","updated_at":"2022-02-20T20:46:48Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nUsing ```nixos-rebuild test``` with ```users.mutableUsers = false;``` in the configuration being tested erases root and user credentials even after reboot and prevents logging in. Booting to previous generations doesn't solve the issue.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. If you want to avoid the recovery hassle below, it's probably wise to try reproducing the issue on a vm first.\r\n2. Clone https://github.com/mitchellh/nixos-config/tree/a50d0422b340067e02c78ecd273cbd97168d0755\r\n2. Read the additional context below\r\n3. Run sudo NIXPKGS_ALLOW_UNSUPPORTED_SYSTEM=1 nixos-rebuild test --flake \".#vm-intel\"\r\n\r\n### Expected behavior\r\nReboot after the command in question should return the system to exactly the same state it was before. Previous system generations should not be affected either.\r\n\r\n### Additional context\r\nI came across the issue while modifying https://github.com/mitchellh/nixos-config/tree/a50d0422b340067e02c78ecd273cbd97168d0755 for my personal use. I can't recall all the modifications but I had removed most of the vm related configuration, changed the user, removed the hashedPassword and replaced it with a plain text one for testing. \r\n\r\nThe exact command I used was ```NIXPKGS_ALLOW_UNSUPPORTED_SYSTEM=1 nixos-rebuild test --flake \".#workstation\"``` but using vm-intel here instead of workstation should make reproducing the issue simpler. If reproducing doesn't work I can post the whole modified configuration to my own repo and link it here. \r\n\r\nTbh I'm not even sure if this is a bug or a feature but if it's a feature at least a warning should be included next to ```nixos-rebuild test``` command in the Nixos manual.\r\n\r\n### Recovery\r\n1. Using eg. an install usb, run the Nixos installer (I used debug mode)\r\n2. Mount the root and boot partitions of the affected system\r\n3. Run ```sudo chroot /mnt /nix/var/nix/profiles/system/activate```\r\n4. Run ```sudo chroot /mnt /run/current-system/sw/bin/bash```\r\n5. Set root and user passwords with ```passwd```\r\n6. Run ```exit``` and ```reboot```\r\n\r\n### Notify maintainers\r\nCouldn't find `meta.maintainers` list and latest edits to https://github.com/NixOS/nixpkgs/blob/master/pkgs/os-specific/linux/nixos-rebuild/nixos-rebuild.sh don't seem relevant so I'm pinging @jonringer, @thiagokokada and @chvp. Hope you don't mind.\r\n\r\n### Metadata\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(lasse): `\"\"`\r\n - channels(root): `\"home-manager, nixos-22.05pre352272.c5051e2b5fe\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161072/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161055","id":1145008663,"node_id":"I_kwDOAEVQ_M5EP3IX","number":161055,"title":"Plasma Mobile Can Work With Pipewire Too.","user":{"login":"Obikawa","id":3336306,"node_id":"MDQ6VXNlcjMzMzYzMDY=","avatar_url":"https://avatars.githubusercontent.com/u/3336306?v=4","gravatar_id":"","url":"https://api.github.com/users/Obikawa","html_url":"https://github.com/Obikawa","followers_url":"https://api.github.com/users/Obikawa/followers","following_url":"https://api.github.com/users/Obikawa/following{/other_user}","gists_url":"https://api.github.com/users/Obikawa/gists{/gist_id}","starred_url":"https://api.github.com/users/Obikawa/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Obikawa/subscriptions","organizations_url":"https://api.github.com/users/Obikawa/orgs","repos_url":"https://api.github.com/users/Obikawa/repos","events_url":"https://api.github.com/users/Obikawa/events{/privacy}","received_events_url":"https://api.github.com/users/Obikawa/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-20T12:39:20Z","updated_at":"2022-02-22T22:59:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOption `services.xserver.desktopManager.plasma5.mobile.enable` enforces `hardware.pulseaudio.enable`, which in turn conflicts with `services.pipewire.pulse.enable`.\r\n\r\n### Steps To Reproduce\r\n\r\nEnable both `services.xserver.desktopManager.plasma5.mobile.enable` and `services.pipewire.pulse.enable`. Pipewire configuration is implied.\r\n\r\n### Expected behavior\r\n\r\nNormal rebuild.\r\n\r\n### Screenshots\r\n\r\nNot applicable.\r\n\r\n### Additional context\r\n\r\nPlasma Mobile works with Pipewire's Pulseaudio emulation just fine. I watched a couple hours of videos with EasyEffects and switched outputs with zero issues. \r\n\r\nI worked around the Pulseaudio enforcement by completely removing the requirement from `nixos/modules/services/x11/desktop-managers/plasma5.nix`.\r\n\r\nThe system is built from a configuration flake pointing to [my fork]( https://github.com/Obikawa/nixpkgs/tree/plasma-mobile-pipewire ).\r\n\r\n### Notify maintainers\r\n\r\nThe configuration file does not list maintainers, so the notification goes to the author of the new options: @samueldr .\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-info -m\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.101, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-22.05pre347947.689b76bcf36\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161055/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161049","id":1144996550,"node_id":"I_kwDOAEVQ_M5EP0LG","number":161049,"title":"`mlflow ui` raises ModuleNotFoundError","user":{"login":"YodaEmbedding","id":721196,"node_id":"MDQ6VXNlcjcyMTE5Ng==","avatar_url":"https://avatars.githubusercontent.com/u/721196?v=4","gravatar_id":"","url":"https://api.github.com/users/YodaEmbedding","html_url":"https://github.com/YodaEmbedding","followers_url":"https://api.github.com/users/YodaEmbedding/followers","following_url":"https://api.github.com/users/YodaEmbedding/following{/other_user}","gists_url":"https://api.github.com/users/YodaEmbedding/gists{/gist_id}","starred_url":"https://api.github.com/users/YodaEmbedding/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/YodaEmbedding/subscriptions","organizations_url":"https://api.github.com/users/YodaEmbedding/orgs","repos_url":"https://api.github.com/users/YodaEmbedding/repos","events_url":"https://api.github.com/users/YodaEmbedding/events{/privacy}","received_events_url":"https://api.github.com/users/YodaEmbedding/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-20T11:46:20Z","updated_at":"2022-02-21T10:57:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nRunning `mlflow ui` raises `ModuleNotFoundError: No module named 'mlflow'`.\r\n\r\nFull traceback:\r\n```console\r\n[user@system:~]$ mlflow ui\r\n[2022-02-20 03:45:47 -0800] [3321112] [INFO] Starting gunicorn 20.1.0\r\n[2022-02-20 03:45:47 -0800] [3321112] [INFO] Listening at: http://127.0.0.1:5000 (3321112)\r\n[2022-02-20 03:45:47 -0800] [3321112] [INFO] Using worker: sync\r\n[2022-02-20 03:45:47 -0800] [3321113] [INFO] Booting worker with pid: 3321113\r\n[2022-02-20 03:45:47 -0800] [3321113] [ERROR] Exception in worker process\r\nTraceback (most recent call last):\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/arbiter.py\", line 589, in spawn_worker\r\n worker.init_process()\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/workers/base.py\", line 134, in init_process\r\n self.load_wsgi()\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/workers/base.py\", line 146, in load_wsgi\r\n self.wsgi = self.app.wsgi()\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/app/base.py\", line 67, in wsgi\r\n self.callable = self.load()\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/app/wsgiapp.py\", line 58, in load\r\n return self.load_wsgiapp()\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/app/wsgiapp.py\", line 48, in load_wsgiapp\r\n return util.import_app(self.app_uri)\r\n File \"/nix/store/c556v9dcfk8xrqm19mfi82d99mgclz21-python3.9-gunicorn-20.1.0/lib/python3.9/site-packages/gunicorn/util.py\", line 359, in import_app\r\n mod = importlib.import_module(module)\r\n File \"/nix/store/2c9w4p2x6x0l64fdvcmc11app7x4xran-python3-3.9.6/lib/python3.9/importlib/__init__.py\", line 127, in import_module\r\n return _bootstrap._gcd_import(name[level:], package, level)\r\n File \"<frozen importlib._bootstrap>\", line 1030, in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 1007, in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 972, in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 228, in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap>\", line 1030, in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 1007, in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 984, in _find_and_load_unlocked\r\nModuleNotFoundError: No module named 'mlflow'\r\n[2022-02-20 03:45:47 -0800] [3321113] [INFO] Worker exiting (pid: 3321113)\r\n[2022-02-20 03:45:47 -0800] [3321112] [INFO] Shutting down: Master\r\n[2022-02-20 03:45:47 -0800] [3321112] [INFO] Reason: Worker failed to boot.\r\nRunning the mlflow server failed. Please see the logs above for details.\r\n```\r\n\r\n### Steps To Reproduce\r\nSimply install `mlflow`:\r\n```nix\r\n{\r\n description = \"simple mlflow flake\";\r\n\r\n inputs.nixpkgs-unstable.url = \"github:NixOS/nixpkgs/nixos-unstable\";\r\n\r\n outputs = { self, nixpkgs-unstable }: {\r\n\r\n defaultPackage.x86_64-linux =\r\n with import nixpkgs-unstable { system = \"x86_64-linux\"; };\r\n mkShell {\r\n packages = [\r\n python3\r\n python3Packages.mlflow\r\n ];\r\n };\r\n\r\n };\r\n}\r\n```\r\nNow run `mlflow ui` or `mlflow server`.\r\n\r\n### Expected behavior\r\nNo error.\r\n\r\n### Screenshots\r\nN/A.\r\n\r\n### Additional context\r\nTemporary workaround:\r\n```bash\r\nalias mlflow=\"python -c 'from mlflow.cli import cli; cli()'\"\r\n```\r\n\r\n### Notify maintainers\r\n@tbenst \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.96, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11.333896.a640d8394f3, nixos-unstable-22.05pre335103.6daa4a5c045\"`\r\n - channels(mulhaq): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n`flake.lock`:\r\n```json\r\n{\r\n \"nodes\": {\r\n \"nixpkgs-unstable\": {\r\n \"locked\": {\r\n \"lastModified\": 1644613700,\r\n \"narHash\": \"sha256-wLRPJclMH8vsHuFtyI78aF09lw5mbi3lMB6uiK5S2wE=\",\r\n \"owner\": \"NixOS\",\r\n \"repo\": \"nixpkgs\",\r\n \"rev\": \"23d785aa6f853e6cf3430119811c334025bbef55\",\r\n \"type\": \"github\"\r\n },\r\n \"original\": {\r\n \"owner\": \"NixOS\",\r\n \"ref\": \"nixos-unstable\",\r\n \"repo\": \"nixpkgs\",\r\n \"type\": \"github\"\r\n }\r\n },\r\n \"root\": {\r\n \"inputs\": {\r\n \"nixpkgs-unstable\": \"nixpkgs-unstable\"\r\n }\r\n }\r\n },\r\n \"root\": \"root\",\r\n \"version\": 7\r\n}\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161049/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013/events","html_url":"https://github.com/NixOS/nixpkgs/issues/161013","id":1144928061,"node_id":"I_kwDOAEVQ_M5EPjc9","number":161013,"title":"kakoune-easymotion hangs out because python isn't installed","user":{"login":"wyndon","id":72203260,"node_id":"MDQ6VXNlcjcyMjAzMjYw","avatar_url":"https://avatars.githubusercontent.com/u/72203260?v=4","gravatar_id":"","url":"https://api.github.com/users/wyndon","html_url":"https://github.com/wyndon","followers_url":"https://api.github.com/users/wyndon/followers","following_url":"https://api.github.com/users/wyndon/following{/other_user}","gists_url":"https://api.github.com/users/wyndon/gists{/gist_id}","starred_url":"https://api.github.com/users/wyndon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wyndon/subscriptions","organizations_url":"https://api.github.com/users/wyndon/orgs","repos_url":"https://api.github.com/users/wyndon/repos","events_url":"https://api.github.com/users/wyndon/events{/privacy}","received_events_url":"https://api.github.com/users/wyndon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-20T05:45:34Z","updated_at":"2022-02-20T05:45:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIf python isn't installed, the plugin hangs out when being executed and you're forced to close kakoune.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open a file with `kak`\r\n2. Try to execute `easy-motion-b`\r\n\r\n### Expected behavior\r\nEasymotion shoudn't hang out.\r\n\r\n### Notify maintainers\r\n@Flakebi @vrthra \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.19-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/store/mg64g39l6ivp6f352nx0qc11av1q7a99-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/161013/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160981","id":1144878012,"node_id":"I_kwDOAEVQ_M5EPXO8","number":160981,"title":"CodeQl can not execute java tool","user":{"login":"drestrepom","id":36453706,"node_id":"MDQ6VXNlcjM2NDUzNzA2","avatar_url":"https://avatars.githubusercontent.com/u/36453706?v=4","gravatar_id":"","url":"https://api.github.com/users/drestrepom","html_url":"https://github.com/drestrepom","followers_url":"https://api.github.com/users/drestrepom/followers","following_url":"https://api.github.com/users/drestrepom/following{/other_user}","gists_url":"https://api.github.com/users/drestrepom/gists{/gist_id}","starred_url":"https://api.github.com/users/drestrepom/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/drestrepom/subscriptions","organizations_url":"https://api.github.com/users/drestrepom/orgs","repos_url":"https://api.github.com/users/drestrepom/repos","events_url":"https://api.github.com/users/drestrepom/events{/privacy}","received_events_url":"https://api.github.com/users/drestrepom/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-20T00:08:46Z","updated_at":"2022-03-02T04:24:34Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen trying to create a database, codeql can not execute a java tool binary\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. I am using the following nix-shell\r\n```nix\r\nlet\r\n pkgs = import (fetchTarball (\"https://github.com/NixOS/nixpkgs/archive/33b225f22b9d5569494e55aad2bd24ec2a3bca4b.tar.gz\")) { };\r\nin\r\npkgs.mkShell {\r\n buildInputs = [\r\n pkgs.codeql\r\n ];\r\n}\r\n```\r\n2. `nix-shell shell.nix`\r\n3. I try to create a database for javascript project \r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.77, NixOS, 21.05pre-git (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.12`\r\n - channels(drestrepo): `\"\"`\r\n - nixpkgs: `/nix/store/x37qq91gslh2fw1s3p94vjqlpy1irqws-nixpkgsNixos-src`\r\n\r\n```console\r\n[user@system:~]$ codeql database create --language=javascript --overwrite --source-root repos/vulnerable_js_app/ javascript-database\r\nInitializing database at /home/xxxxxxx/Documents/javascript-database.\r\nRunning build command: []\r\n[2022-02-19 18:57:11] [ERROR] Spawned process exited abnormally (code 127; tried to run: [/nix/store/n4az7b05d28d1612d76lppjz77iylc67-codeql-2.8.0/codeql/javascript/tools/autobuild.sh])\r\n[2022-02-19 18:57:11] [build-stderr] env: ‘/nix/store/n4az7b05d28d1612d76lppjz77iylc67-codeql-2.8.0/codeql/tools/linux64/java/bin/java’: No such file or directory\r\nA fatal error occurred: Exit status 127 from command: [/nix/store/n4az7b05d28d1612d76lppjz77iylc67-codeql-2.8.0/codeql/javascript/tools/autobuild.sh]\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160981/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160925","id":1144801905,"node_id":"I_kwDOAEVQ_M5EPEpx","number":160925,"title":"sshd races binding to tailscale addresses.","user":{"login":"nixinator","id":66913205,"node_id":"MDQ6VXNlcjY2OTEzMjA1","avatar_url":"https://avatars.githubusercontent.com/u/66913205?v=4","gravatar_id":"","url":"https://api.github.com/users/nixinator","html_url":"https://github.com/nixinator","followers_url":"https://api.github.com/users/nixinator/followers","following_url":"https://api.github.com/users/nixinator/following{/other_user}","gists_url":"https://api.github.com/users/nixinator/gists{/gist_id}","starred_url":"https://api.github.com/users/nixinator/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nixinator/subscriptions","organizations_url":"https://api.github.com/users/nixinator/orgs","repos_url":"https://api.github.com/users/nixinator/repos","events_url":"https://api.github.com/users/nixinator/events{/privacy}","received_events_url":"https://api.github.com/users/nixinator/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-19T17:33:54Z","updated_at":"2022-02-19T17:33:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nbetween - \"rev\": \"0f316e4d72daed659233817ffe52bf08e081b5de\", (21.11) works!\r\n \"rev\": \"2128d0aa28edef51fd8fef38b132ffc0155595df\", problem!\r\n\r\nA race condition has/may been introduced when binding sshd to tailscale ip addresses exclusively.\r\n\r\nI presume that this is to do with ordering of the services, or it could be a race that i had before but not noticed.\r\n\r\nBefore i close this , anyone else seeing this problem?\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ... upgrade to \"2128d0aa28edef51fd8fef38b132ffc0155595df\r\n2. ...nixos-rebuild switch\r\n\r\n```\r\nsystemd[1]: sshd.service: Main process exited, code=exited, status=255/EXCEPTION\r\nFeb 19 17:02:05 z620 sshd[1406]: fatal: Cannot bind any address.\r\nFeb 19 17:02:05 z620 sshd[1406]: error: Bind to port 22 on 100.122.121.111 failed: Cannot assign requested address.\r\nFeb 19 17:02:05 z620 sshd[1402]: fatal: Cannot bind any address.\r\n```\r\n\r\ni'll bisect it when i get a chance.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160925/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160923","id":1144800420,"node_id":"I_kwDOAEVQ_M5EPESk","number":160923,"title":"Apps launched by xdg-open can misbehave when called from FHS envs or wrapped programs","user":{"login":"LunNova","id":782440,"node_id":"MDQ6VXNlcjc4MjQ0MA==","avatar_url":"https://avatars.githubusercontent.com/u/782440?v=4","gravatar_id":"","url":"https://api.github.com/users/LunNova","html_url":"https://github.com/LunNova","followers_url":"https://api.github.com/users/LunNova/followers","following_url":"https://api.github.com/users/LunNova/following{/other_user}","gists_url":"https://api.github.com/users/LunNova/gists{/gist_id}","starred_url":"https://api.github.com/users/LunNova/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/LunNova/subscriptions","organizations_url":"https://api.github.com/users/LunNova/orgs","repos_url":"https://api.github.com/users/LunNova/repos","events_url":"https://api.github.com/users/LunNova/events{/privacy}","received_events_url":"https://api.github.com/users/LunNova/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-02-19T17:27:50Z","updated_at":"2022-04-24T20:46:43Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nWhen calling `xdg-open` from a FHS env or wrapped app, it tries to launch the associated program directly while either having unexpected/unrelated environment variables like `LD_PRELOAD` set or worse being in an FHS env which is entirely missing some dependencies.\r\n\r\nIdeally, `xdg-open` when used in a FHS env or wrapped package would use `xdg-desktop-portal` to launch apps instead, similarly to how flatpaks use this to open other applications outside of the package.\r\n\r\nThere is partial upstream support for this but it only applies in flatpaks: \r\nhttps://github.com/freedesktop/xdg-utils/blob/1a58bc28f6844898532daf9ee1bf6da7764955a9/scripts/xdg-open.in#L250 \r\nhttps://github.com/freedesktop/xdg-utils/blob/d11b33ec7f24cfb1546f6b459611d440013bdc72/scripts/xdg-utils-common.in#L361-L363 \r\nIt also doesn't handle local files correctly.\r\n\r\nAn example script which [also handles files is here](https://github.com/LunNova/nixos-configs/blob/b6688e198ed915be798073436eef7398ce89b410/packages/xdg-open-with-portal/default.nix).\r\n\r\n### Steps To Reproduce\r\nOne example of this issue, although there are many related issues in different contexts.\r\n\r\nSteps to reproduce the behavior:\r\n1. Launch lutris under KDE\r\n2. Click a link in it or an app launched by it\r\n3. KDE thinks firefox's .desktop item isn't owned by root as it's owned by nobody in the FHS sandbox and refuses to start it\r\n\r\n### Expected behavior\r\nThe `xdg-open` package in NixOS should use `xdg-desktop-portal` to launch apps/urls/etc when possible as if it is inside a flatpak to avoid running apps in unexpected FHS envs or with unexpected env from wrappers.\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Notify maintainers\r\n@edolstra - xdg-utils maintainer entry\r\n@Atemu @illegalprime @wentasah - work on bwrap FHS envs \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.19-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-21.11.333896.a640d8394f3\"`\r\n - channels(lun): `\"\"`\r\n - nixpkgs: `/etc/nix/path/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160923/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160915","id":1144774146,"node_id":"I_kwDOAEVQ_M5EO94C","number":160915,"title":"nix profile install nixpkgs#perl => perl: warning: Setting locale failed.","user":{"login":"gerardbosch","id":30733556,"node_id":"MDQ6VXNlcjMwNzMzNTU2","avatar_url":"https://avatars.githubusercontent.com/u/30733556?v=4","gravatar_id":"","url":"https://api.github.com/users/gerardbosch","html_url":"https://github.com/gerardbosch","followers_url":"https://api.github.com/users/gerardbosch/followers","following_url":"https://api.github.com/users/gerardbosch/following{/other_user}","gists_url":"https://api.github.com/users/gerardbosch/gists{/gist_id}","starred_url":"https://api.github.com/users/gerardbosch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/gerardbosch/subscriptions","organizations_url":"https://api.github.com/users/gerardbosch/orgs","repos_url":"https://api.github.com/users/gerardbosch/repos","events_url":"https://api.github.com/users/gerardbosch/events{/privacy}","received_events_url":"https://api.github.com/users/gerardbosch/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-19T16:22:32Z","updated_at":"2022-02-19T23:10:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI install Perl with Nix with the following command:\r\n\r\n```console\r\nnix profile install nixpkgs#perl\r\n```\r\n\r\nThen, when I run `perl` there's always a warning (see below).\r\n\r\nIf I run the perl binary that comes with my distro (Ubuntu) or I install perl with Linux Homebrew, it works with no issues.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nRun perl, e.g.:\r\n```console\r\n❯ perl -e exit\r\nperl: warning: Setting locale failed.\r\nperl: warning: Please check that your locale settings:\r\n\tLANGUAGE = (unset),\r\n\tLC_ALL = (unset),\r\n\tLC_TELEPHONE = \"es_ES.UTF-8\",\r\n\tLC_MEASUREMENT = \"es_ES.UTF-8\",\r\n\tLC_NAME = \"es_ES.UTF-8\",\r\n\tLC_PAPER = \"es_ES.UTF-8\",\r\n\tLC_ADDRESS = \"es_ES.UTF-8\",\r\n\tLC_IDENTIFICATION = \"es_ES.UTF-8\",\r\n\tLC_NUMERIC = \"es_ES.UTF-8\",\r\n\tLC_TIME = \"es_ES.UTF-8\",\r\n\tLC_MONETARY = \"es_ES.UTF-8\",\r\n\tLANG = \"en_US.UTF-8\"\r\n are supported and installed on your system.\r\nperl: warning: Falling back to the standard locale (\"C\").\r\n```\r\n\r\n### Expected behavior\r\nPerl runs with no errors or warnings.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Additional context\r\n\r\nInstalled Perl version:\r\n```console\r\n❯ nix profile list | grep 'perl' \r\n28 flake:nixpkgs#legacyPackages.x86_64-linux.perl github:NixOS/nixpkgs/b66b39216b1fef2d8c33cc7a5c72d8da80b79970#legacyPackages.x86_64-linux.perl /nix/store/4i0gfyhwf63ycz5j489mgkh2nlinnvfi-perl-5.34.0\r\n```\r\n\r\nOutput of `locale`:\r\n```console\r\n❯ locale\r\nLANG=en_US.UTF-8\r\nLANGUAGE=\r\nLC_CTYPE=\"en_US.UTF-8\"\r\nLC_NUMERIC=es_ES.UTF-8\r\nLC_TIME=es_ES.UTF-8\r\nLC_COLLATE=\"en_US.UTF-8\"\r\nLC_MONETARY=es_ES.UTF-8\r\nLC_MESSAGES=\"en_US.UTF-8\"\r\nLC_PAPER=es_ES.UTF-8\r\nLC_NAME=es_ES.UTF-8\r\nLC_ADDRESS=es_ES.UTF-8\r\nLC_TELEPHONE=es_ES.UTF-8\r\nLC_MEASUREMENT=es_ES.UTF-8\r\nLC_IDENTIFICATION=es_ES.UTF-8\r\nLC_ALL=\r\n```\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.13.0-28-generic, Ubuntu, 21.10 (Impish Indri)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(gerard): `\"nixgl, nixpkgs-22.05pre337745.e7caea7700d\"`\r\n - nixpkgs: `/home/gerard/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160915/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160911","id":1144754562,"node_id":"I_kwDOAEVQ_M5EO5GC","number":160911,"title":"Package quarto-cli","user":{"login":"JonathanReeve","id":1843676,"node_id":"MDQ6VXNlcjE4NDM2NzY=","avatar_url":"https://avatars.githubusercontent.com/u/1843676?v=4","gravatar_id":"","url":"https://api.github.com/users/JonathanReeve","html_url":"https://github.com/JonathanReeve","followers_url":"https://api.github.com/users/JonathanReeve/followers","following_url":"https://api.github.com/users/JonathanReeve/following{/other_user}","gists_url":"https://api.github.com/users/JonathanReeve/gists{/gist_id}","starred_url":"https://api.github.com/users/JonathanReeve/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/JonathanReeve/subscriptions","organizations_url":"https://api.github.com/users/JonathanReeve/orgs","repos_url":"https://api.github.com/users/JonathanReeve/repos","events_url":"https://api.github.com/users/JonathanReeve/events{/privacy}","received_events_url":"https://api.github.com/users/JonathanReeve/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-19T15:32:30Z","updated_at":"2022-02-19T15:32:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n[Quarto-cli](https://github.com/quarto-dev/quarto-cli) is a CLI for Quarto, a package for scholarly publishing built on Pandoc. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://quarto.org/\r\n* source URL: https://github.com/quarto-dev/quarto-cli\r\n* license: gpl2+ \r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160911/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160874","id":1144656724,"node_id":"I_kwDOAEVQ_M5EOhNU","number":160874,"title":"codelldb inside of vscode-lldb extension doesn't work","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-02-19T10:55:21Z","updated_at":"2022-02-23T00:48:19Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nI want to use `vscode-extensions.vadimcn.vscode-lldb.adapter` (providing `codelldb`) for it's Debug Adapter support. Particularly it seems like Helix can utilize it with some early debugging support.\r\n\r\nHowever, it doesn't seem to work. After adding that to my nix shell, and entering it, and trying to run it, I get:\r\n\r\n```\r\n[cole@porty:~/code/rust-nix-template]$ codelldb\r\nError: \"\\\"/nix/store/rnqda0vmhg95ziahvl7r6y10x4xk1y6z-vscode-lldb-adapter-1.6.10/lldb/lib/liblldb.so: cannot open shared object file: No such file or directory\\\"\"\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160874/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160828","id":1144248376,"node_id":"I_kwDOAEVQ_M5EM9g4","number":160828,"title":"`mpv` is missing features on Darwin","user":{"login":"leungbk","id":29217594,"node_id":"MDQ6VXNlcjI5MjE3NTk0","avatar_url":"https://avatars.githubusercontent.com/u/29217594?v=4","gravatar_id":"","url":"https://api.github.com/users/leungbk","html_url":"https://github.com/leungbk","followers_url":"https://api.github.com/users/leungbk/followers","following_url":"https://api.github.com/users/leungbk/following{/other_user}","gists_url":"https://api.github.com/users/leungbk/gists{/gist_id}","starred_url":"https://api.github.com/users/leungbk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/leungbk/subscriptions","organizations_url":"https://api.github.com/users/leungbk/orgs","repos_url":"https://api.github.com/users/leungbk/repos","events_url":"https://api.github.com/users/leungbk/events{/privacy}","received_events_url":"https://api.github.com/users/leungbk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-19T03:18:41Z","updated_at":"2022-02-19T23:07:48Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n1. Pressing `f` to go into full-screen mode doesn't work (other keys like `q` work as normal).\r\n2. When not in full screen, the title bar and the quit/minimize/maximize buttons should not be visible under most circumstances; this is the behavior I observe when using `mpv` via Homebrew. However, a Nix-installed version of `mpv` does show the title bar and such.\r\n\r\n### Steps To Reproduce\r\n`nix-shell -p --pure mpv` on `aarch64-darwin`.\r\n\r\n### Expected behavior\r\n1. `f` should go into full-screen mode\r\n2. Title bar and friends should not generally be visible even when not in full-screen mode\r\n\r\n### Notify maintainers\r\n@marsam \r\n\r\nHe seems to be the most recent contributor to the `mpv` recipe who uses Darwin. I know he's not listed as a maintainer for `mpv`, but I don't think anybody on the maintainer list actually uses Darwin.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"darwin, home-manager-22.05pre347261.6d8215281b2, nixpkgs-22.05pre345869.46821ea01c8\"`\r\n - channels(brian): `\"darwin, home-manager-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160828/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160756","id":1143673268,"node_id":"I_kwDOAEVQ_M5EKxG0","number":160756,"title":"pkgsStatic.openssl_3_0 fails to build","user":{"login":"nioncode","id":3159451,"node_id":"MDQ6VXNlcjMxNTk0NTE=","avatar_url":"https://avatars.githubusercontent.com/u/3159451?v=4","gravatar_id":"","url":"https://api.github.com/users/nioncode","html_url":"https://github.com/nioncode","followers_url":"https://api.github.com/users/nioncode/followers","following_url":"https://api.github.com/users/nioncode/following{/other_user}","gists_url":"https://api.github.com/users/nioncode/gists{/gist_id}","starred_url":"https://api.github.com/users/nioncode/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nioncode/subscriptions","organizations_url":"https://api.github.com/users/nioncode/orgs","repos_url":"https://api.github.com/users/nioncode/repos","events_url":"https://api.github.com/users/nioncode/events{/privacy}","received_events_url":"https://api.github.com/users/nioncode/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1469796342,"node_id":"MDU6TGFiZWwxNDY5Nzk2MzQy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20static","name":"6.topic: static","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T19:52:34Z","updated_at":"2022-02-19T23:05:09Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nBuilding pkgsStatic.openssl_3_0 fails.\r\n\r\n### Steps To Reproduce\r\n`nix-build '<nixpkgs>' -A pkgsStatic.openssl_3_0`\r\n\r\nAfter a while, it fails with:\r\n```\r\n/nix/store/nxk5pcwfv32hfg62klgbzq8gcfg7zjrj-x86_64-unknown-linux-musl-binutils-2.35.2/bin/x86_64-unknown-linux-musl-ld: /nix/store/g51rj8086vryr242nsn6hh7lfdlmf9mb-x86_64-unknown-linux-musl-stage-final-gcc-10.3.0/lib/gcc/x86_64-unknown-linux-musl/10.3.0/crtbeginT.o: relocation R_X86_64_32 against hidden symbol `__TMC_END__' can not be used when making a shared object\r\n/nix/store/nxk5pcwfv32hfg62klgbzq8gcfg7zjrj-x86_64-unknown-linux-musl-binutils-2.35.2/bin/x86_64-unknown-linux-musl-ld: /nix/store/g51rj8086vryr242nsn6hh7lfdlmf9mb-x86_64-unknown-linux-musl-stage-final-gcc-10.3.0/lib/gcc/x86_64-unknown-linux-musl/10.3.0/crtend.o: relocation R_X86_64_32 against `.ctors' can not be used when making a shared object; recompile with -fPIC\r\n```\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.99, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336020.2128d0aa28e, unstable-20.09pre228384.c27e54de99d, nixos-unstable-20.09pre222244.22a3bf9fb9e\"`\r\n - channels(nion): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160756/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160745","id":1143604972,"node_id":"I_kwDOAEVQ_M5EKgbs","number":160745,"title":"\"Enforce\" better commit messages for Nixpkgs","user":{"login":"primeos","id":7537109,"node_id":"MDQ6VXNlcjc1MzcxMDk=","avatar_url":"https://avatars.githubusercontent.com/u/7537109?v=4","gravatar_id":"","url":"https://api.github.com/users/primeos","html_url":"https://github.com/primeos","followers_url":"https://api.github.com/users/primeos/followers","following_url":"https://api.github.com/users/primeos/following{/other_user}","gists_url":"https://api.github.com/users/primeos/gists{/gist_id}","starred_url":"https://api.github.com/users/primeos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/primeos/subscriptions","organizations_url":"https://api.github.com/users/primeos/orgs","repos_url":"https://api.github.com/users/primeos/repos","events_url":"https://api.github.com/users/primeos/events{/privacy}","received_events_url":"https://api.github.com/users/primeos/received_events","type":"User","site_admin":false},"labels":[{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null},{"id":335672980,"node_id":"MDU6TGFiZWwzMzU2NzI5ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20policy%20discussion","name":"6.topic: policy discussion","color":"fef2c0","default":false,"description":null},{"id":465618943,"node_id":"MDU6TGFiZWw0NjU2MTg5NDM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20community%20feedback","name":"9.needs: community feedback","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-18T19:04:20Z","updated_at":"2022-04-25T18:18:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I increasingly notice PRs with important but non-trivial changes that lack an appropriate commit message and it's getting kinda annoying to tell every author. It also often happens that the author did write a description for the PR but the commit message has only a subject and no body (a bad pattern that emerged on GitHub).\r\n\r\nIMO it'd be great if we could document the need for a good commit message more prominently.\r\n\r\nE.g., the following is already good: https://github.com/NixOS/nixpkgs/blob/3ddc71525fd0d12083620b8d2b181f62e73ffff0/CONTRIBUTING.md#writing-good-commit-messages:\r\n> In addition to writing properly formatted commit messages, it's important to include relevant information so other developers can later understand why a change was made. While this information usually can be found by digging code, mailing list/Discourse archives, pull request discussions or upstream changes, it may require a lot of work.\r\n\r\nA link to https://cbea.ms/git-commit/ or another source would also be a good addition IMO (possibly even copying \"The seven rules of a great Git commit message\").\r\nWe might also want to explicitly mention that the commit messages for non-trivial changes should have a body that explains what, why, and how.\r\n\r\nDepending on how often too brief / bad commit messages are a problem we might also want to add an item to the PR template:\r\nhttps://github.com/NixOS/nixpkgs/blob/3ddc71525fd0d12083620b8d2b181f62e73ffff0/.github/PULL_REQUEST_TEMPLATE.md. Or e.g.:\r\n```diff\r\n-- [ ] Fits [CONTRIBUTING.md](https://github.com/NixOS/nixpkgs/blob/master/CONTRIBUTING.md).\r\n+- [ ] Fits [CONTRIBUTING.md](../CONTRIBUTING.md) and has a [good commit message](../CONTRIBUTING.md#writing-good-commit-messages).\r\n```\r\n\r\n> For package version upgrades and such a one-line commit message is usually sufficient.\r\n\r\nThat is of course fine (assuming it's a trivial change that doesn't need any explanation).\r\n\r\nIt looks like the requirement for an appropriate commit message also isn't mentioned here:\r\nhttps://nixos.org/manual/nixpkgs/stable/#chap-reviewing-contributions","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745/reactions","total_count":17,"+1":10,"-1":0,"laugh":0,"hooray":5,"confused":0,"heart":2,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160745/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160735","id":1143509164,"node_id":"I_kwDOAEVQ_M5EKJCs","number":160735,"title":"Unable to start custom desktop managment sessions when X is enabled","user":{"login":"svrana","id":850665,"node_id":"MDQ6VXNlcjg1MDY2NQ==","avatar_url":"https://avatars.githubusercontent.com/u/850665?v=4","gravatar_id":"","url":"https://api.github.com/users/svrana","html_url":"https://github.com/svrana","followers_url":"https://api.github.com/users/svrana/followers","following_url":"https://api.github.com/users/svrana/following{/other_user}","gists_url":"https://api.github.com/users/svrana/gists{/gist_id}","starred_url":"https://api.github.com/users/svrana/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/svrana/subscriptions","organizations_url":"https://api.github.com/users/svrana/orgs","repos_url":"https://api.github.com/users/svrana/repos","events_url":"https://api.github.com/users/svrana/events{/privacy}","received_events_url":"https://api.github.com/users/svrana/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T18:02:02Z","updated_at":"2022-02-18T18:05:56Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWas looking into why I can not get sway to start from lightdm and noticed that the xsession script generated by services/display-managers/default.nix is not properly formatted for manually added sessions, i.e., ones specified via services.xserver.desktop-manager.session.\r\n\r\n### Steps To Reproduce\r\n\r\nThat I'm launching sway is suspect, I know, but the script is never run.\r\n\r\n```\r\nenvironment.systemPackages = with pkgs; [\r\n (\r\n pkgs.writeTextFile {\r\n name = \"start-sway\";\r\n destination = \"/bin/start-sway\";\r\n executable = true;\r\n text = ''\r\n #! ${pkgs.bash}/bin/bash\r\n systemctl --user import-environment\r\n exec systemctl --user start sway.service\r\n '';\r\n }\r\n )\r\n];\r\n\r\nprograms.sway.enable = true;\r\n\r\nservices.xserver = {\r\n enable = true;\r\n displayManager = {\r\n defaultSession = \"sway\";\r\n lightdm.enable = true;\r\n };\r\n desktopManager.session = [\r\n {\r\n name = \"sway\";\r\n start = \"start-sway\";\r\n }\r\n ];\r\n};\r\n```\r\n\r\nThe problematic portion of the generated xsession file looks like this:\r\n\r\n\r\n```bash\r\nstart-swayif [ -e $HOME/.background-image ]; then\r\n /nix/store/94alf2qzvrh65afkmi7yczxfyvai4fd4-feh-3.7.2/bin/feh --bg-scale $HOME/.background-image\r\nfi\r\n```\r\ni.e., a missing newline after my `start-sway` command prior to the background-image check added by services/x11/desktop-managers/default.nix, i.e., this code:\r\n\r\n```\r\napply = map (d: d // {\r\n manage = \"desktop\";\r\n start = d.start\r\n + optionalString (needBGCond d) ''\r\n if [ -e $HOME/.background-image ]; then\r\n ${pkgs.feh}/bin/feh --bg-${cfg.wallpaper.mode} ${optionalString cfg.wallpaper.combineScreens \"--no-xinerama\"} $HOME/.background\r\n fi\r\n '';\r\n```\r\n\r\n### Expected behavior\r\nFor my custom script to be run.\r\n\r\n### Notify maintainers\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nnixpkgs pinned to 03ec468b14067729a285c2c7cfa7b9434a04816c\r\n\r\n➜ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.84, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"\"`\r\n - channels(shaw): `\"\"`\r\n - nixpkgs: `/nix/store/g6q5v2rp0npa2xmma29xdqijk8nm1dfh-nixpkgs-src`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160735/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160719","id":1143297983,"node_id":"I_kwDOAEVQ_M5EJVe_","number":160719,"title":"Vulnerability roundup 111: xterm-370: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:50:46Z","updated_at":"2022-02-24T11:28:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=xterm&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=xterm+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24130](https://nvd.nist.gov/vuln/detail/CVE-2022-24130) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-24130\n\nxterm through Patch 370, when Sixel support is enabled, allows attackers to trigger a buffer overflow in set_sixel in graphics_sixel.c via crafted text.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @nequissimus\nCc @vrthra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160719/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160716","id":1143297780,"node_id":"I_kwDOAEVQ_M5EJVb0","number":160716,"title":"Vulnerability roundup 111: unzip-6.0: 2 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:50:40Z","updated_at":"2022-03-18T16:33:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=unzip&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=unzip+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0529](https://nvd.nist.gov/vuln/detail/CVE-2022-0529) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-0530](https://nvd.nist.gov/vuln/detail/CVE-2022-0530) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0529\n\nA flaw was found in unzip 6.0. The vulnerability occurs during the conversion of wide string to local string that leads to a heap of out-of-bound writes. This flaw allows an attacker to input a specially crafted zip file, leading to a crash or code execution.\n\n### CVE-2022-0530\n\nA flaw was found in unzip 6.0. The vulnerability occurs during the conversion of an utf-8 string to a local string that leads to a segmentation fault. This flaw allows an attacker to input a specially crafted zip file, leading to a crash or code execution.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160716/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160715","id":1143297675,"node_id":"I_kwDOAEVQ_M5EJVaL","number":160715,"title":"Vulnerability roundup 111: tensorflow-2.7.0: 56 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:50:36Z","updated_at":"2022-02-18T15:50:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=tensorflow&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=tensorflow+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23587](https://nvd.nist.gov/vuln/detail/CVE-2022-23587) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2022-21726](https://nvd.nist.gov/vuln/detail/CVE-2022-21726) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-21727](https://nvd.nist.gov/vuln/detail/CVE-2022-21727) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-21740](https://nvd.nist.gov/vuln/detail/CVE-2022-21740) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23558](https://nvd.nist.gov/vuln/detail/CVE-2022-23558) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23559](https://nvd.nist.gov/vuln/detail/CVE-2022-23559) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23560](https://nvd.nist.gov/vuln/detail/CVE-2022-23560) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23561](https://nvd.nist.gov/vuln/detail/CVE-2022-23561) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23562](https://nvd.nist.gov/vuln/detail/CVE-2022-23562) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23566](https://nvd.nist.gov/vuln/detail/CVE-2022-23566) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23573](https://nvd.nist.gov/vuln/detail/CVE-2022-23573) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-23574](https://nvd.nist.gov/vuln/detail/CVE-2022-23574) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-21728](https://nvd.nist.gov/vuln/detail/CVE-2022-21728) CVSSv3=8.1 (nixos-unstable)\n* [ ] [CVE-2022-21730](https://nvd.nist.gov/vuln/detail/CVE-2022-21730) CVSSv3=8.1 (nixos-unstable)\n* [ ] [CVE-2022-23592](https://nvd.nist.gov/vuln/detail/CVE-2022-23592) CVSSv3=8.1 (nixos-unstable)\n* [ ] [CVE-2022-23590](https://nvd.nist.gov/vuln/detail/CVE-2022-23590) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2022-23591](https://nvd.nist.gov/vuln/detail/CVE-2022-23591) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2022-23593](https://nvd.nist.gov/vuln/detail/CVE-2022-23593) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2022-21725](https://nvd.nist.gov/vuln/detail/CVE-2022-21725) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21729](https://nvd.nist.gov/vuln/detail/CVE-2022-21729) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21731](https://nvd.nist.gov/vuln/detail/CVE-2022-21731) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21732](https://nvd.nist.gov/vuln/detail/CVE-2022-21732) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21733](https://nvd.nist.gov/vuln/detail/CVE-2022-21733) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21734](https://nvd.nist.gov/vuln/detail/CVE-2022-21734) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21735](https://nvd.nist.gov/vuln/detail/CVE-2022-21735) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21736](https://nvd.nist.gov/vuln/detail/CVE-2022-21736) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21737](https://nvd.nist.gov/vuln/detail/CVE-2022-21737) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21738](https://nvd.nist.gov/vuln/detail/CVE-2022-21738) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21739](https://nvd.nist.gov/vuln/detail/CVE-2022-21739) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21741](https://nvd.nist.gov/vuln/detail/CVE-2022-21741) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23557](https://nvd.nist.gov/vuln/detail/CVE-2022-23557) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23564](https://nvd.nist.gov/vuln/detail/CVE-2022-23564) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23565](https://nvd.nist.gov/vuln/detail/CVE-2022-23565) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23567](https://nvd.nist.gov/vuln/detail/CVE-2022-23567) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23568](https://nvd.nist.gov/vuln/detail/CVE-2022-23568) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23569](https://nvd.nist.gov/vuln/detail/CVE-2022-23569) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23570](https://nvd.nist.gov/vuln/detail/CVE-2022-23570) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23571](https://nvd.nist.gov/vuln/detail/CVE-2022-23571) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23572](https://nvd.nist.gov/vuln/detail/CVE-2022-23572) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23575](https://nvd.nist.gov/vuln/detail/CVE-2022-23575) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23576](https://nvd.nist.gov/vuln/detail/CVE-2022-23576) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23577](https://nvd.nist.gov/vuln/detail/CVE-2022-23577) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23579](https://nvd.nist.gov/vuln/detail/CVE-2022-23579) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23580](https://nvd.nist.gov/vuln/detail/CVE-2022-23580) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23581](https://nvd.nist.gov/vuln/detail/CVE-2022-23581) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23582](https://nvd.nist.gov/vuln/detail/CVE-2022-23582) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23583](https://nvd.nist.gov/vuln/detail/CVE-2022-23583) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23584](https://nvd.nist.gov/vuln/detail/CVE-2022-23584) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23585](https://nvd.nist.gov/vuln/detail/CVE-2022-23585) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23586](https://nvd.nist.gov/vuln/detail/CVE-2022-23586) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23588](https://nvd.nist.gov/vuln/detail/CVE-2022-23588) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23589](https://nvd.nist.gov/vuln/detail/CVE-2022-23589) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23595](https://nvd.nist.gov/vuln/detail/CVE-2022-23595) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-23563](https://nvd.nist.gov/vuln/detail/CVE-2022-23563) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-23594](https://nvd.nist.gov/vuln/detail/CVE-2022-23594) CVSSv3=5.5 (nixos-unstable)\n* [ ] [CVE-2022-23578](https://nvd.nist.gov/vuln/detail/CVE-2022-23578) CVSSv3=4.3 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23587\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, Grappler component of TensorFlow is vulnerable to an integer overflow during cost estimation for crop and resize. Since the cropping parameters are user controlled, a malicious person can trigger undefined behavior. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21726\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `Dequantize` does not fully validate the value of `axis` and can result in heap OOB accesses. The `axis` argument can be `-1` (the default value for the optional argument) or any other positive value at most the number of dimensions of the input. Unfortunately, the upper bound is not checked and this results in reading past the end of the array containing the dimensions of the input tensor. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21727\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `Dequantize` is vulnerable to an integer overflow weakness. The `axis` argument can be `-1` (the default value for the optional argument) or any other positive value at most the number of dimensions of the input. Unfortunately, the upper bound is not checked, and, since the code computes `axis + 1`, an attacker can trigger an integer overflow. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21740\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseCountSparseOutput` is vulnerable to a heap overflow. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23558\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause an integer overflow in `TfLiteIntArrayCreate`. The `TfLiteIntArrayGetSizeInBytes` returns an `int` instead of a `size_t. An attacker can control model inputs such that `computed_size` overflows the size of `int` datatype. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23559\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause an integer overflow in embedding lookup operations. Both `embedding_size` and `lookup_size` are products of values provided by the user. Hence, a malicious user could trigger overflows in the multiplication. In certain scenarios, this can then result in heap OOB read/write. Users are advised to upgrade to a patched version.\n\n### CVE-2022-23560\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would allow limited reads and writes outside of arrays in TFLite. This exploits missing validation in the conversion from sparse tensors to dense tensors. The fix is included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range. Users are advised to upgrade as soon as possible.\n\n### CVE-2022-23561\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause a write outside of bounds of an array in TFLite. In fact, the attacker can override the linked list used by the memory allocator. This can be leveraged for an arbitrary write primitive under certain conditions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23562\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `Range` suffers from integer overflows. These can trigger undefined behavior or, in some scenarios, extremely large allocations. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23566\n\nTensorflow is an Open Source Machine Learning Framework. TensorFlow is vulnerable to a heap OOB write in `Grappler`. The `set_output` function writes to an array at the specified index. Hence, this gives a malicious user a write primitive. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23573\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `AssignOp` can result in copying uninitialized data to a new tensor. This later results in undefined behavior. The implementation has a check that the left hand side of the assignment is initialized (to minimize number of allocations), but does not check that the right hand side is also initialized. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23574\n\nTensorflow is an Open Source Machine Learning Framework. There is a typo in TensorFlow's `SpecializeType` which results in heap OOB read/write. Due to a typo, `arg` is initialized to the `i`th mutable argument in a loop where the loop index is `j`. Hence it is possible to assign to `arg` from outside the vector of arguments. Since this is a mutable proto value, it allows both read and write to outside of bounds data. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-21728\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `ReverseSequence` does not fully validate the value of `batch_dim` and can result in a heap OOB read. There is a check to make sure the value of `batch_dim` does not go over the rank of the input, but there is no check for negative values. Negative dimensions are allowed in some cases to mimic Python's negative indexing (i.e., indexing from the end of the array), however if the value is too negative then the implementation of `Dim` would access elements before the start of an array. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21730\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `FractionalAvgPoolGrad` does not consider cases where the input tensors are invalid allowing an attacker to read from outside of bounds of heap. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23592\n\nTensorflow is an Open Source Machine Learning Framework. TensorFlow's type inference can cause a heap out of bounds read as the bounds checking is done in a `DCHECK` (which is a no-op during production). An attacker can control the `input_idx` variable such that `ix` would be larger than the number of values in `node_t.args`. The fix will be included in TensorFlow 2.8.0. This is the only affected version.\n\n### CVE-2022-23590\n\nTensorflow is an Open Source Machine Learning Framework. A `GraphDef` from a TensorFlow `SavedModel` can be maliciously altered to cause a TensorFlow process to crash due to encountering a `StatusOr` value that is an error and forcibly extracting the value from it. We have patched the issue in multiple GitHub commits and these will be included in TensorFlow 2.8.0 and TensorFlow 2.7.1, as both are affected.\n\n### CVE-2022-23591\n\nTensorflow is an Open Source Machine Learning Framework. The `GraphDef` format in TensorFlow does not allow self recursive functions. The runtime assumes that this invariant is satisfied. However, a `GraphDef` containing a fragment such as the following can be consumed when loading a `SavedModel`. This would result in a stack overflow during execution as resolving each `NodeDef` means resolving the function itself and its nodes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23593\n\nTensorflow is an Open Source Machine Learning Framework. The `simplifyBroadcast` function in the MLIR-TFRT infrastructure in TensorFlow is vulnerable to a segfault (hence, denial of service), if called with scalar shapes. If all shapes are scalar, then `maxRank` is 0, so we build an empty `SmallVector`. The fix will be included in TensorFlow 2.8.0. This is the only affected version.\n\n### CVE-2022-21725\n\nTensorflow is an Open Source Machine Learning Framework. The estimator for the cost of some convolution operations can be made to execute a division by 0. The function fails to check that the stride argument is strictly positive. Hence, the fix is to add a check for the stride argument to ensure it is valid. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21729\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `UnravelIndex` is vulnerable to a division by zero caused by an integer overflow bug. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21731\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `ConcatV2` can be used to trigger a denial of service attack via a segfault caused by a type confusion. The `axis` argument is translated into `concat_dim` in the `ConcatShapeHelper` helper function. Then, a value for `min_rank` is computed based on `concat_dim`. This is then used to validate that the `values` tensor has at least the required rank. However, `WithRankAtLeast` receives the lower bound as a 64-bits value and then compares it against the maximum 32-bits integer value that could be represented. Due to the fact that `min_rank` is a 32-bits value and the value of `axis`, the `rank` argument is a negative value, so the error check is bypassed. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21732\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `ThreadPoolHandle` can be used to trigger a denial of service attack by allocating too much memory. This is because the `num_threads` argument is only checked to not be negative, but there is no upper bound on its value. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21733\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `StringNGrams` can be used to trigger a denial of service attack by causing an out of memory condition after an integer overflow. We are missing a validation on `pad_witdh` and that result in computing a negative value for `ngram_width` which is later used to allocate parts of the output. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21734\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `MapStage` is vulnerable a `CHECK`-fail if the key tensor is not a scalar. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21735\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `FractionalMaxPool` can be made to crash a TensorFlow process via a division by 0. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21736\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseTensorSliceDataset` has an undefined behavior: under certain condition it can be made to dereference a `nullptr` value. The 3 input arguments to `SparseTensorSliceDataset` represent a sparse tensor. However, there are some preconditions that these arguments must satisfy but these are not validated in the implementation. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21737\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `*Bincount` operations allows malicious users to cause denial of service by passing in arguments which would trigger a `CHECK`-fail. There are several conditions that the input arguments must satisfy. Some are not caught during shape inference and others are not caught during kernel implementation. This results in `CHECK` failures later when the output tensors get allocated. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21738\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseCountSparseOutput` can be made to crash a TensorFlow process by an integer overflow whose result is then used in a memory allocation. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21739\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `QuantizedMaxPool` has an undefined behavior where user controlled inputs can trigger a reference binding to null pointer. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21741\n\nTensorflow is an Open Source Machine Learning Framework. ### Impact An attacker can craft a TFLite model that would trigger a division by zero in the implementation of depthwise convolutions. The parameters of the convolution can be user controlled and are also used within a division operation to determine the size of the padding that needs to be added before applying the convolution. There is no check before this division that the divisor is strictly positive. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23557\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would trigger a division by zero in `BiasAndClamp` implementation. There is no check that the `bias_size` is non zero. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23564\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a resource handle tensor from protobuf, a TensorFlow process can encounter cases where a `CHECK` assertion is invalidated based on user controlled arguments. This allows attackers to cause denial of services in TensorFlow processes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23565\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can trigger denial of service via assertion failure by altering a `SavedModel` on disk such that `AttrDef`s of some operation are duplicated. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23567\n\nTensorflow is an Open Source Machine Learning Framework. The implementations of `Sparse*Cwise*` ops are vulnerable to integer overflows. These can be used to trigger large allocations (so, OOM based denial of service) or `CHECK`-fails when building new `TensorShape` objects (so, assert failures based denial of service). We are missing some validation on the shapes of the input tensors as well as directly constructing a large `TensorShape` with user-provided dimensions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23568\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `AddManySparseToTensorsMap` is vulnerable to an integer overflow which results in a `CHECK`-fail when building new `TensorShape` objects (so, an assert failure based denial of service). We are missing some validation on the shapes of the input tensors as well as directly constructing a large `TensorShape` with user-provided dimensions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23569\n\nTensorflow is an Open Source Machine Learning Framework. Multiple operations in TensorFlow can be used to trigger a denial of service via `CHECK`-fails (i.e., assertion failures). This is similar to TFSA-2021-198 and has similar fixes. We have patched the reported issues in multiple GitHub commits. It is possible that other similar instances exist in TensorFlow, we will issue fixes as these are discovered. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23570\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a tensor from protobuf, TensorFlow might do a null-dereference if attributes of some mutable arguments to some operations are missing from the proto. This is guarded by a `DCHECK`. However, `DCHECK` is a no-op in production builds and an assertion failure in debug builds. In the first case execution proceeds to the dereferencing of the null pointer, whereas in the second case it results in a crash due to the assertion failure. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-23571\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a tensor from protobuf, a TensorFlow process can encounter cases where a `CHECK` assertion is invalidated based on user controlled arguments, if the tensors have an invalid `dtype` and 0 elements or an invalid shape. This allows attackers to cause denial of services in TensorFlow processes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23572\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, TensorFlow can fail to specialize a type during shape inference. This case is covered by the `DCHECK` function however, `DCHECK` is a no-op in production builds and an assertion failure in debug builds. In the first case execution proceeds to the `ValueOrDie` line. This results in an assertion failure as `ret` contains an error `Status`, not a value. In the second case we also get a crash due to the assertion failure. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-23575\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `OpLevelCostEstimator::CalculateTensorSize` is vulnerable to an integer overflow if an attacker can create an operation which would involve a tensor with large enough number of elements. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23576\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `OpLevelCostEstimator::CalculateOutputSize` is vulnerable to an integer overflow if an attacker can create an operation which would involve tensors with large enough number of elements. We can have a large enough number of dimensions in `output_shape.dim()` or just a small number of dimensions being large enough to cause an overflow in the multiplication. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23577\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `GetInitOp` is vulnerable to a crash caused by dereferencing a null pointer. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23579\n\nTensorflow is an Open Source Machine Learning Framework. The Grappler optimizer in TensorFlow can be used to cause a denial of service by altering a `SavedModel` such that `SafeToRemoveIdentity` would trigger `CHECK` failures. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23580\n\nTensorflow is an Open Source Machine Learning Framework. During shape inference, TensorFlow can allocate a large vector based on a value from a tensor controlled by the user. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23581\n\nTensorflow is an Open Source Machine Learning Framework. The Grappler optimizer in TensorFlow can be used to cause a denial of service by altering a `SavedModel` such that `IsSimplifiableReshape` would trigger `CHECK` failures. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23582\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that `TensorByteSize` would trigger `CHECK` failures. `TensorShape` constructor throws a `CHECK`-fail if shape is partial or has a number of elements that would overflow the size of an `int`. The `PartialTensorShape` constructor instead does not cause a `CHECK`-abort if the shape is partial, which is exactly what this function needs to be able to return `-1`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23583\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that any binary op would trigger `CHECK` failures. This occurs when the protobuf part corresponding to the tensor arguments is modified such that the `dtype` no longer matches the `dtype` expected by the op. In that case, calling the templated binary operator for the binary op would receive corrupted data, due to the type confusion involved. If `Tin` and `Tout` don't match the type of data in `out` and `input_*` tensors then `flat<*>` would interpret it wrongly. In most cases, this would be a silent failure, but we have noticed scenarios where this results in a `CHECK` crash, hence a denial of service. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23584\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a use after free behavior when decoding PNG images. After `png::CommonFreeDecode(&decode)` gets called, the values of `decode.width` and `decode.height` are in an unspecified state. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23585\n\nTensorflow is an Open Source Machine Learning Framework. When decoding PNG images TensorFlow can produce a memory leak if the image is invalid. After calling `png::CommonInitDecode(..., &decode)`, the `decode` value contains allocated buffers which can only be freed by calling `png::CommonFreeDecode(&decode)`. However, several error case in the function implementation invoke the `OP_REQUIRES` macro which immediately terminates the execution of the function, without allowing for the memory free to occur. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23586\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that assertions in `function.cc` would be falsified and crash the Python interpreter. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23588\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that Grappler optimizer would attempt to build a tensor using a reference `dtype`. This would result in a crash due to a `CHECK`-fail in the `Tensor` constructor as reference types are not allowed. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23589\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, Grappler component of TensorFlow can trigger a null pointer dereference. There are 2 places where this can occur, for the same malicious alteration of a `SavedModel` file (fixing the first one would trigger the same dereference in the second place). First, during constant folding, the `GraphDef` might not have the required nodes for the binary operation. If a node is missing, the correposning `mul_*child` would be null, and the dereference in the subsequent line would be incorrect. We have a similar issue during `IsIdentityConsumingSwitch`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23595\n\nTensorflow is an Open Source Machine Learning Framework. When building an XLA compilation cache, if default settings are used, TensorFlow triggers a null pointer dereference. In the default scenario, all devices are allowed, so `flr->config_proto` is `nullptr`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23563\n\nTensorflow is an Open Source Machine Learning Framework. In multiple places, TensorFlow uses `tempfile.mktemp` to create temporary files. While this is acceptable in testing, in utilities and libraries it is dangerous as a different process can create the file between the check for the filename in `mktemp` and the actual creation of the file by a subsequent operation (a TOC/TOU type of weakness). In several instances, TensorFlow was supposed to actually create a temporary directory instead of a file. This logic bug is hidden away by the `mktemp` function usage. We have patched the issue in several commits, replacing `mktemp` with the safer `mkstemp`/`mkdtemp` functions, according to the usage pattern. Users are advised to upgrade as soon as possible.\n\n### CVE-2022-23594\n\nTensorflow is an Open Source Machine Learning Framework. The TFG dialect of TensorFlow (MLIR) makes several assumptions about the incoming `GraphDef` before converting it to the MLIR-based dialect. If an attacker changes the `SavedModel` format on disk to invalidate these assumptions and the `GraphDef` is then converted to MLIR-based IR then they can cause a crash in the Python interpreter. Under certain scenarios, heap OOB read/writes are possible. These issues have been discovered via fuzzing and it is possible that more weaknesses exist. We will patch them as they are discovered.\n\n### CVE-2022-23578\n\nTensorflow is an Open Source Machine Learning Framework. If a graph node is invalid, TensorFlow can leak memory in the implementation of `ImmutableExecutorState::Initialize`. Here, we set `item->kernel` to `nullptr` but it is a simple `OpKernel*` pointer so the memory that was previously allocated to it would leak. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @abbradar\nCc @jyp\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160715/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160714","id":1143297562,"node_id":"I_kwDOAEVQ_M5EJVYa","number":160714,"title":"Vulnerability roundup 111: tensorflow-2.4.4: 53 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:50:32Z","updated_at":"2022-02-18T15:50:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=tensorflow&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=tensorflow+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23587](https://nvd.nist.gov/vuln/detail/CVE-2022-23587) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2022-21726](https://nvd.nist.gov/vuln/detail/CVE-2022-21726) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-21727](https://nvd.nist.gov/vuln/detail/CVE-2022-21727) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-21740](https://nvd.nist.gov/vuln/detail/CVE-2022-21740) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23558](https://nvd.nist.gov/vuln/detail/CVE-2022-23558) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23559](https://nvd.nist.gov/vuln/detail/CVE-2022-23559) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23560](https://nvd.nist.gov/vuln/detail/CVE-2022-23560) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23561](https://nvd.nist.gov/vuln/detail/CVE-2022-23561) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23562](https://nvd.nist.gov/vuln/detail/CVE-2022-23562) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23566](https://nvd.nist.gov/vuln/detail/CVE-2022-23566) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23573](https://nvd.nist.gov/vuln/detail/CVE-2022-23573) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-23574](https://nvd.nist.gov/vuln/detail/CVE-2022-23574) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-21728](https://nvd.nist.gov/vuln/detail/CVE-2022-21728) CVSSv3=8.1 (nixos-21.11)\n* [ ] [CVE-2022-21730](https://nvd.nist.gov/vuln/detail/CVE-2022-21730) CVSSv3=8.1 (nixos-21.11)\n* [ ] [CVE-2022-23590](https://nvd.nist.gov/vuln/detail/CVE-2022-23590) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-23591](https://nvd.nist.gov/vuln/detail/CVE-2022-23591) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-21725](https://nvd.nist.gov/vuln/detail/CVE-2022-21725) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21729](https://nvd.nist.gov/vuln/detail/CVE-2022-21729) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21731](https://nvd.nist.gov/vuln/detail/CVE-2022-21731) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21732](https://nvd.nist.gov/vuln/detail/CVE-2022-21732) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21733](https://nvd.nist.gov/vuln/detail/CVE-2022-21733) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21734](https://nvd.nist.gov/vuln/detail/CVE-2022-21734) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21735](https://nvd.nist.gov/vuln/detail/CVE-2022-21735) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21736](https://nvd.nist.gov/vuln/detail/CVE-2022-21736) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21737](https://nvd.nist.gov/vuln/detail/CVE-2022-21737) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21738](https://nvd.nist.gov/vuln/detail/CVE-2022-21738) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21739](https://nvd.nist.gov/vuln/detail/CVE-2022-21739) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21741](https://nvd.nist.gov/vuln/detail/CVE-2022-21741) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23557](https://nvd.nist.gov/vuln/detail/CVE-2022-23557) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23564](https://nvd.nist.gov/vuln/detail/CVE-2022-23564) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23565](https://nvd.nist.gov/vuln/detail/CVE-2022-23565) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23567](https://nvd.nist.gov/vuln/detail/CVE-2022-23567) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23568](https://nvd.nist.gov/vuln/detail/CVE-2022-23568) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23569](https://nvd.nist.gov/vuln/detail/CVE-2022-23569) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23570](https://nvd.nist.gov/vuln/detail/CVE-2022-23570) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23571](https://nvd.nist.gov/vuln/detail/CVE-2022-23571) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23572](https://nvd.nist.gov/vuln/detail/CVE-2022-23572) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23575](https://nvd.nist.gov/vuln/detail/CVE-2022-23575) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23576](https://nvd.nist.gov/vuln/detail/CVE-2022-23576) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23577](https://nvd.nist.gov/vuln/detail/CVE-2022-23577) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23579](https://nvd.nist.gov/vuln/detail/CVE-2022-23579) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23580](https://nvd.nist.gov/vuln/detail/CVE-2022-23580) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23581](https://nvd.nist.gov/vuln/detail/CVE-2022-23581) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23582](https://nvd.nist.gov/vuln/detail/CVE-2022-23582) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23583](https://nvd.nist.gov/vuln/detail/CVE-2022-23583) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23584](https://nvd.nist.gov/vuln/detail/CVE-2022-23584) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23585](https://nvd.nist.gov/vuln/detail/CVE-2022-23585) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23586](https://nvd.nist.gov/vuln/detail/CVE-2022-23586) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23588](https://nvd.nist.gov/vuln/detail/CVE-2022-23588) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23589](https://nvd.nist.gov/vuln/detail/CVE-2022-23589) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23595](https://nvd.nist.gov/vuln/detail/CVE-2022-23595) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-23563](https://nvd.nist.gov/vuln/detail/CVE-2022-23563) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-23578](https://nvd.nist.gov/vuln/detail/CVE-2022-23578) CVSSv3=4.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23587\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, Grappler component of TensorFlow is vulnerable to an integer overflow during cost estimation for crop and resize. Since the cropping parameters are user controlled, a malicious person can trigger undefined behavior. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21726\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `Dequantize` does not fully validate the value of `axis` and can result in heap OOB accesses. The `axis` argument can be `-1` (the default value for the optional argument) or any other positive value at most the number of dimensions of the input. Unfortunately, the upper bound is not checked and this results in reading past the end of the array containing the dimensions of the input tensor. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21727\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `Dequantize` is vulnerable to an integer overflow weakness. The `axis` argument can be `-1` (the default value for the optional argument) or any other positive value at most the number of dimensions of the input. Unfortunately, the upper bound is not checked, and, since the code computes `axis + 1`, an attacker can trigger an integer overflow. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21740\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseCountSparseOutput` is vulnerable to a heap overflow. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23558\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause an integer overflow in `TfLiteIntArrayCreate`. The `TfLiteIntArrayGetSizeInBytes` returns an `int` instead of a `size_t. An attacker can control model inputs such that `computed_size` overflows the size of `int` datatype. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23559\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause an integer overflow in embedding lookup operations. Both `embedding_size` and `lookup_size` are products of values provided by the user. Hence, a malicious user could trigger overflows in the multiplication. In certain scenarios, this can then result in heap OOB read/write. Users are advised to upgrade to a patched version.\n\n### CVE-2022-23560\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would allow limited reads and writes outside of arrays in TFLite. This exploits missing validation in the conversion from sparse tensors to dense tensors. The fix is included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range. Users are advised to upgrade as soon as possible.\n\n### CVE-2022-23561\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would cause a write outside of bounds of an array in TFLite. In fact, the attacker can override the linked list used by the memory allocator. This can be leveraged for an arbitrary write primitive under certain conditions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23562\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `Range` suffers from integer overflows. These can trigger undefined behavior or, in some scenarios, extremely large allocations. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23566\n\nTensorflow is an Open Source Machine Learning Framework. TensorFlow is vulnerable to a heap OOB write in `Grappler`. The `set_output` function writes to an array at the specified index. Hence, this gives a malicious user a write primitive. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23573\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `AssignOp` can result in copying uninitialized data to a new tensor. This later results in undefined behavior. The implementation has a check that the left hand side of the assignment is initialized (to minimize number of allocations), but does not check that the right hand side is also initialized. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23574\n\nTensorflow is an Open Source Machine Learning Framework. There is a typo in TensorFlow's `SpecializeType` which results in heap OOB read/write. Due to a typo, `arg` is initialized to the `i`th mutable argument in a loop where the loop index is `j`. Hence it is possible to assign to `arg` from outside the vector of arguments. Since this is a mutable proto value, it allows both read and write to outside of bounds data. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-21728\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `ReverseSequence` does not fully validate the value of `batch_dim` and can result in a heap OOB read. There is a check to make sure the value of `batch_dim` does not go over the rank of the input, but there is no check for negative values. Negative dimensions are allowed in some cases to mimic Python's negative indexing (i.e., indexing from the end of the array), however if the value is too negative then the implementation of `Dim` would access elements before the start of an array. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21730\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `FractionalAvgPoolGrad` does not consider cases where the input tensors are invalid allowing an attacker to read from outside of bounds of heap. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23590\n\nTensorflow is an Open Source Machine Learning Framework. A `GraphDef` from a TensorFlow `SavedModel` can be maliciously altered to cause a TensorFlow process to crash due to encountering a `StatusOr` value that is an error and forcibly extracting the value from it. We have patched the issue in multiple GitHub commits and these will be included in TensorFlow 2.8.0 and TensorFlow 2.7.1, as both are affected.\n\n### CVE-2022-23591\n\nTensorflow is an Open Source Machine Learning Framework. The `GraphDef` format in TensorFlow does not allow self recursive functions. The runtime assumes that this invariant is satisfied. However, a `GraphDef` containing a fragment such as the following can be consumed when loading a `SavedModel`. This would result in a stack overflow during execution as resolving each `NodeDef` means resolving the function itself and its nodes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21725\n\nTensorflow is an Open Source Machine Learning Framework. The estimator for the cost of some convolution operations can be made to execute a division by 0. The function fails to check that the stride argument is strictly positive. Hence, the fix is to add a check for the stride argument to ensure it is valid. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21729\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `UnravelIndex` is vulnerable to a division by zero caused by an integer overflow bug. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21731\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of shape inference for `ConcatV2` can be used to trigger a denial of service attack via a segfault caused by a type confusion. The `axis` argument is translated into `concat_dim` in the `ConcatShapeHelper` helper function. Then, a value for `min_rank` is computed based on `concat_dim`. This is then used to validate that the `values` tensor has at least the required rank. However, `WithRankAtLeast` receives the lower bound as a 64-bits value and then compares it against the maximum 32-bits integer value that could be represented. Due to the fact that `min_rank` is a 32-bits value and the value of `axis`, the `rank` argument is a negative value, so the error check is bypassed. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21732\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `ThreadPoolHandle` can be used to trigger a denial of service attack by allocating too much memory. This is because the `num_threads` argument is only checked to not be negative, but there is no upper bound on its value. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21733\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `StringNGrams` can be used to trigger a denial of service attack by causing an out of memory condition after an integer overflow. We are missing a validation on `pad_witdh` and that result in computing a negative value for `ngram_width` which is later used to allocate parts of the output. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21734\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `MapStage` is vulnerable a `CHECK`-fail if the key tensor is not a scalar. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21735\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `FractionalMaxPool` can be made to crash a TensorFlow process via a division by 0. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21736\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseTensorSliceDataset` has an undefined behavior: under certain condition it can be made to dereference a `nullptr` value. The 3 input arguments to `SparseTensorSliceDataset` represent a sparse tensor. However, there are some preconditions that these arguments must satisfy but these are not validated in the implementation. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21737\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `*Bincount` operations allows malicious users to cause denial of service by passing in arguments which would trigger a `CHECK`-fail. There are several conditions that the input arguments must satisfy. Some are not caught during shape inference and others are not caught during kernel implementation. This results in `CHECK` failures later when the output tensors get allocated. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21738\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `SparseCountSparseOutput` can be made to crash a TensorFlow process by an integer overflow whose result is then used in a memory allocation. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21739\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `QuantizedMaxPool` has an undefined behavior where user controlled inputs can trigger a reference binding to null pointer. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-21741\n\nTensorflow is an Open Source Machine Learning Framework. ### Impact An attacker can craft a TFLite model that would trigger a division by zero in the implementation of depthwise convolutions. The parameters of the convolution can be user controlled and are also used within a division operation to determine the size of the padding that needs to be added before applying the convolution. There is no check before this division that the divisor is strictly positive. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23557\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can craft a TFLite model that would trigger a division by zero in `BiasAndClamp` implementation. There is no check that the `bias_size` is non zero. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23564\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a resource handle tensor from protobuf, a TensorFlow process can encounter cases where a `CHECK` assertion is invalidated based on user controlled arguments. This allows attackers to cause denial of services in TensorFlow processes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23565\n\nTensorflow is an Open Source Machine Learning Framework. An attacker can trigger denial of service via assertion failure by altering a `SavedModel` on disk such that `AttrDef`s of some operation are duplicated. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23567\n\nTensorflow is an Open Source Machine Learning Framework. The implementations of `Sparse*Cwise*` ops are vulnerable to integer overflows. These can be used to trigger large allocations (so, OOM based denial of service) or `CHECK`-fails when building new `TensorShape` objects (so, assert failures based denial of service). We are missing some validation on the shapes of the input tensors as well as directly constructing a large `TensorShape` with user-provided dimensions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23568\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `AddManySparseToTensorsMap` is vulnerable to an integer overflow which results in a `CHECK`-fail when building new `TensorShape` objects (so, an assert failure based denial of service). We are missing some validation on the shapes of the input tensors as well as directly constructing a large `TensorShape` with user-provided dimensions. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23569\n\nTensorflow is an Open Source Machine Learning Framework. Multiple operations in TensorFlow can be used to trigger a denial of service via `CHECK`-fails (i.e., assertion failures). This is similar to TFSA-2021-198 and has similar fixes. We have patched the reported issues in multiple GitHub commits. It is possible that other similar instances exist in TensorFlow, we will issue fixes as these are discovered. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23570\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a tensor from protobuf, TensorFlow might do a null-dereference if attributes of some mutable arguments to some operations are missing from the proto. This is guarded by a `DCHECK`. However, `DCHECK` is a no-op in production builds and an assertion failure in debug builds. In the first case execution proceeds to the dereferencing of the null pointer, whereas in the second case it results in a crash due to the assertion failure. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-23571\n\nTensorflow is an Open Source Machine Learning Framework. When decoding a tensor from protobuf, a TensorFlow process can encounter cases where a `CHECK` assertion is invalidated based on user controlled arguments, if the tensors have an invalid `dtype` and 0 elements or an invalid shape. This allows attackers to cause denial of services in TensorFlow processes. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23572\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, TensorFlow can fail to specialize a type during shape inference. This case is covered by the `DCHECK` function however, `DCHECK` is a no-op in production builds and an assertion failure in debug builds. In the first case execution proceeds to the `ValueOrDie` line. This results in an assertion failure as `ret` contains an error `Status`, not a value. In the second case we also get a crash due to the assertion failure. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, and TensorFlow 2.6.3, as these are also affected and still in supported range.\n\n### CVE-2022-23575\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `OpLevelCostEstimator::CalculateTensorSize` is vulnerable to an integer overflow if an attacker can create an operation which would involve a tensor with large enough number of elements. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23576\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `OpLevelCostEstimator::CalculateOutputSize` is vulnerable to an integer overflow if an attacker can create an operation which would involve tensors with large enough number of elements. We can have a large enough number of dimensions in `output_shape.dim()` or just a small number of dimensions being large enough to cause an overflow in the multiplication. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23577\n\nTensorflow is an Open Source Machine Learning Framework. The implementation of `GetInitOp` is vulnerable to a crash caused by dereferencing a null pointer. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23579\n\nTensorflow is an Open Source Machine Learning Framework. The Grappler optimizer in TensorFlow can be used to cause a denial of service by altering a `SavedModel` such that `SafeToRemoveIdentity` would trigger `CHECK` failures. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23580\n\nTensorflow is an Open Source Machine Learning Framework. During shape inference, TensorFlow can allocate a large vector based on a value from a tensor controlled by the user. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23581\n\nTensorflow is an Open Source Machine Learning Framework. The Grappler optimizer in TensorFlow can be used to cause a denial of service by altering a `SavedModel` such that `IsSimplifiableReshape` would trigger `CHECK` failures. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23582\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that `TensorByteSize` would trigger `CHECK` failures. `TensorShape` constructor throws a `CHECK`-fail if shape is partial or has a number of elements that would overflow the size of an `int`. The `PartialTensorShape` constructor instead does not cause a `CHECK`-abort if the shape is partial, which is exactly what this function needs to be able to return `-1`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23583\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that any binary op would trigger `CHECK` failures. This occurs when the protobuf part corresponding to the tensor arguments is modified such that the `dtype` no longer matches the `dtype` expected by the op. In that case, calling the templated binary operator for the binary op would receive corrupted data, due to the type confusion involved. If `Tin` and `Tout` don't match the type of data in `out` and `input_*` tensors then `flat<*>` would interpret it wrongly. In most cases, this would be a silent failure, but we have noticed scenarios where this results in a `CHECK` crash, hence a denial of service. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23584\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a use after free behavior when decoding PNG images. After `png::CommonFreeDecode(&decode)` gets called, the values of `decode.width` and `decode.height` are in an unspecified state. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23585\n\nTensorflow is an Open Source Machine Learning Framework. When decoding PNG images TensorFlow can produce a memory leak if the image is invalid. After calling `png::CommonInitDecode(..., &decode)`, the `decode` value contains allocated buffers which can only be freed by calling `png::CommonFreeDecode(&decode)`. However, several error case in the function implementation invoke the `OP_REQUIRES` macro which immediately terminates the execution of the function, without allowing for the memory free to occur. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23586\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that assertions in `function.cc` would be falsified and crash the Python interpreter. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23588\n\nTensorflow is an Open Source Machine Learning Framework. A malicious user can cause a denial of service by altering a `SavedModel` such that Grappler optimizer would attempt to build a tensor using a reference `dtype`. This would result in a crash due to a `CHECK`-fail in the `Tensor` constructor as reference types are not allowed. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23589\n\nTensorflow is an Open Source Machine Learning Framework. Under certain scenarios, Grappler component of TensorFlow can trigger a null pointer dereference. There are 2 places where this can occur, for the same malicious alteration of a `SavedModel` file (fixing the first one would trigger the same dereference in the second place). First, during constant folding, the `GraphDef` might not have the required nodes for the binary operation. If a node is missing, the correposning `mul_*child` would be null, and the dereference in the subsequent line would be incorrect. We have a similar issue during `IsIdentityConsumingSwitch`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23595\n\nTensorflow is an Open Source Machine Learning Framework. When building an XLA compilation cache, if default settings are used, TensorFlow triggers a null pointer dereference. In the default scenario, all devices are allowed, so `flr->config_proto` is `nullptr`. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n### CVE-2022-23563\n\nTensorflow is an Open Source Machine Learning Framework. In multiple places, TensorFlow uses `tempfile.mktemp` to create temporary files. While this is acceptable in testing, in utilities and libraries it is dangerous as a different process can create the file between the check for the filename in `mktemp` and the actual creation of the file by a subsequent operation (a TOC/TOU type of weakness). In several instances, TensorFlow was supposed to actually create a temporary directory instead of a file. This logic bug is hidden away by the `mktemp` function usage. We have patched the issue in several commits, replacing `mktemp` with the safer `mkstemp`/`mkdtemp` functions, according to the usage pattern. Users are advised to upgrade as soon as possible.\n\n### CVE-2022-23578\n\nTensorflow is an Open Source Machine Learning Framework. If a graph node is invalid, TensorFlow can leak memory in the implementation of `ImmutableExecutorState::Initialize`. Here, we set `item->kernel` to `nullptr` but it is a simple `OpKernel*` pointer so the memory that was previously allocated to it would leak. The fix will be included in TensorFlow 2.8.0. We will also cherrypick this commit on TensorFlow 2.7.1, TensorFlow 2.6.3, and TensorFlow 2.5.3, as these are also affected and still in supported range.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @abbradar\nCc @jyp\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160714/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160713","id":1143288972,"node_id":"I_kwDOAEVQ_M5EJTSM","number":160713,"title":"Vulnerability roundup 111: tcpreplay-4.3.4: 2 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:30Z","updated_at":"2022-02-24T11:32:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=tcpreplay&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=tcpreplay+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45386](https://nvd.nist.gov/vuln/detail/CVE-2021-45386) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45387](https://nvd.nist.gov/vuln/detail/CVE-2021-45387) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45386\n\ntcpreplay 4.3.4 has a Reachable Assertion in add_tree_ipv6() at tree.c\n\n### CVE-2021-45387\n\ntcpreplay 4.3.4 has a Reachable Assertion in add_tree_ipv4() at tree.c.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @proteansec\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160713/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160711","id":1143288881,"node_id":"I_kwDOAEVQ_M5EJTQx","number":160711,"title":"Vulnerability roundup 111: slic3r-1.3.0: 2 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:26Z","updated_at":"2022-02-24T11:31:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=slic3r&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=slic3r+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45846](https://nvd.nist.gov/vuln/detail/CVE-2021-45846) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45847](https://nvd.nist.gov/vuln/detail/CVE-2021-45847) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45846\n\nA flaw in the AMF parser of Slic3r libslic3r 1.3.0 allows an attacker to cause an application crash using a crafted AMF document, where a metadata tag lacks a \"type\" attribute.\n\n### CVE-2021-45847\n\nSeveral missing input validations in the 3MF parser component of Slic3r libslic3r 1.3.0 can each allow an attacker to cause an application crash using a crafted 3MF input file.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @bjornfor\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160711/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160706","id":1143288581,"node_id":"I_kwDOAEVQ_M5EJTMF","number":160706,"title":"Vulnerability roundup 111: protobuf-3.9.2: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:16Z","updated_at":"2022-02-18T15:45:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160706/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160705","id":1143288518,"node_id":"I_kwDOAEVQ_M5EJTLG","number":160705,"title":"Vulnerability roundup 111: protobuf-3.8.0: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:14Z","updated_at":"2022-02-18T15:45:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160705/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160704","id":1143288447,"node_id":"I_kwDOAEVQ_M5EJTJ_","number":160704,"title":"Vulnerability roundup 111: protobuf-3.7.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:12Z","updated_at":"2022-02-18T15:45:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160704/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160703","id":1143288386,"node_id":"I_kwDOAEVQ_M5EJTJC","number":160703,"title":"Vulnerability roundup 111: protobuf-3.6.1.3: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:10Z","updated_at":"2022-02-18T15:45:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160703/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160702","id":1143288325,"node_id":"I_kwDOAEVQ_M5EJTIF","number":160702,"title":"Vulnerability roundup 111: protobuf-3.14.0: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:08Z","updated_at":"2022-02-18T15:45:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160702/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160701","id":1143288262,"node_id":"I_kwDOAEVQ_M5EJTHG","number":160701,"title":"Vulnerability roundup 111: protobuf-3.13.0.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:06Z","updated_at":"2022-02-18T15:45:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160701/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160700","id":1143288201,"node_id":"I_kwDOAEVQ_M5EJTGJ","number":160700,"title":"Vulnerability roundup 111: protobuf-3.12.4: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:04Z","updated_at":"2022-02-18T15:45:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160700/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160699","id":1143288129,"node_id":"I_kwDOAEVQ_M5EJTFB","number":160699,"title":"Vulnerability roundup 111: protobuf-3.11.4: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:45:01Z","updated_at":"2022-02-18T15:45:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160699/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160697","id":1143280415,"node_id":"I_kwDOAEVQ_M5EJRMf","number":160697,"title":"Vulnerability roundup 111: protobuf-3.10.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:39:59Z","updated_at":"2022-02-18T15:39:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160697/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160696","id":1143280337,"node_id":"I_kwDOAEVQ_M5EJRLR","number":160696,"title":"Vulnerability roundup 111: protobuf-3.1.0: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:39:56Z","updated_at":"2022-02-18T15:39:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160696/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160695","id":1143280283,"node_id":"I_kwDOAEVQ_M5EJRKb","number":160695,"title":"Vulnerability roundup 111: protobuf-2.5.0: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:39:53Z","updated_at":"2022-02-18T15:39:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=protobuf&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=protobuf+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-22570](https://nvd.nist.gov/vuln/detail/CVE-2021-22570) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-22570\n\nNullptr dereference when a null char is present in a proto symbol. The symbol is parsed incorrectly, leading to an unchecked call into the proto file's name during generation of the resulting error message. Since the symbol is incorrectly parsed, the file is nullptr. We recommend upgrading to version 3.15.0 or greater.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160695/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160689","id":1143279894,"node_id":"I_kwDOAEVQ_M5EJREW","number":160689,"title":"Vulnerability roundup 111: open-policy-agent-0.34.0: 1 advisory [5.3]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:39:39Z","updated_at":"2022-02-18T15:39:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=open-policy-agent&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=open-policy-agent+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23628](https://nvd.nist.gov/vuln/detail/CVE-2022-23628) CVSSv3=5.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23628\n\nOPA is an open source, general-purpose policy engine. Under certain conditions, pretty-printing an abstract syntax tree (AST) that contains synthetic nodes could change the logic of some statements by reordering array literals. Example of policies impacted are those that parse and compare web paths. **All of these** three conditions have to be met to create an adverse effect: 1. An AST of Rego had to be **created programmatically** such that it ends up containing terms without a location (such as wildcard variables). 2. The AST had to be **pretty-printed** using the `github.com/open-policy-agent/opa/format` package. 3. The result of the pretty-printing had to be **parsed and evaluated again** via an OPA instance using the bundles, or the Golang packages. If any of these three conditions are not met, you are not affected. Notably, all three would be true if using **optimized bundles**, i.e. bundles created with `opa build -O=1` or higher. In that case, the optimizer would fulfil condition (1.), the result of that would be pretty-printed when writing the bundle to disk, fulfilling (2.). When the bundle was then used, we'd satisfy (3.). As a workaround users may disable optimization when creating bundles.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @06kellyjac\nCc @kalbasit\nCc @nlewo\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160689/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160687","id":1143279785,"node_id":"I_kwDOAEVQ_M5EJRCp","number":160687,"title":"Vulnerability roundup 111: navidrome-0.47.0: 1 advisory [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:39:35Z","updated_at":"2022-02-18T15:39:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=navidrome&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=navidrome+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23857](https://nvd.nist.gov/vuln/detail/CVE-2022-23857) CVSSv3=6.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23857\n\nmodel/criteria/criteria.go in Navidrome before 0.47.5 is vulnerable to SQL injection attacks when processing crafted Smart Playlists. An authenticated user could abuse this to extract arbitrary data from the database, including the user table (which contains sensitive information such as the users' encrypted passwords).\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @aciceri\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160687/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160686","id":1143279729,"node_id":"I_kwDOAEVQ_M5EJRBx","number":160686,"title":"Vulnerability roundup 111: nats-server-2.6.3: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:39:33Z","updated_at":"2022-02-18T15:39:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=nats-server&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=nats-server+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-24450](https://nvd.nist.gov/vuln/detail/CVE-2022-24450) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-24450\n\nNATS nats-server before 2.7.2 has Incorrect Access Control. Any authenticated user can obtain the privileges of the System account by misusing the \"dynamically provisioned sandbox accounts\" feature.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @swdunlop\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160686/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160684","id":1143279565,"node_id":"I_kwDOAEVQ_M5EJQ_N","number":160684,"title":"Vulnerability roundup 111: mysql-8.0.27: 69 advisories [7.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:39:26Z","updated_at":"2022-02-18T15:39:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mysql&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mysql+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21351](https://nvd.nist.gov/vuln/detail/CVE-2022-21351) CVSSv3=7.1 (nixos-unstable)\n* [ ] [CVE-2022-21363](https://nvd.nist.gov/vuln/detail/CVE-2022-21363) CVSSv3=6.6 (nixos-unstable)\n* [ ] [CVE-2022-21358](https://nvd.nist.gov/vuln/detail/CVE-2022-21358) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-21279](https://nvd.nist.gov/vuln/detail/CVE-2022-21279) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21280](https://nvd.nist.gov/vuln/detail/CVE-2022-21280) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21284](https://nvd.nist.gov/vuln/detail/CVE-2022-21284) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21285](https://nvd.nist.gov/vuln/detail/CVE-2022-21285) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21286](https://nvd.nist.gov/vuln/detail/CVE-2022-21286) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21287](https://nvd.nist.gov/vuln/detail/CVE-2022-21287) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21288](https://nvd.nist.gov/vuln/detail/CVE-2022-21288) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21289](https://nvd.nist.gov/vuln/detail/CVE-2022-21289) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21290](https://nvd.nist.gov/vuln/detail/CVE-2022-21290) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21307](https://nvd.nist.gov/vuln/detail/CVE-2022-21307) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21308](https://nvd.nist.gov/vuln/detail/CVE-2022-21308) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21309](https://nvd.nist.gov/vuln/detail/CVE-2022-21309) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21310](https://nvd.nist.gov/vuln/detail/CVE-2022-21310) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21314](https://nvd.nist.gov/vuln/detail/CVE-2022-21314) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21315](https://nvd.nist.gov/vuln/detail/CVE-2022-21315) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21316](https://nvd.nist.gov/vuln/detail/CVE-2022-21316) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21318](https://nvd.nist.gov/vuln/detail/CVE-2022-21318) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21320](https://nvd.nist.gov/vuln/detail/CVE-2022-21320) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21322](https://nvd.nist.gov/vuln/detail/CVE-2022-21322) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21326](https://nvd.nist.gov/vuln/detail/CVE-2022-21326) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21327](https://nvd.nist.gov/vuln/detail/CVE-2022-21327) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21328](https://nvd.nist.gov/vuln/detail/CVE-2022-21328) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21329](https://nvd.nist.gov/vuln/detail/CVE-2022-21329) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21330](https://nvd.nist.gov/vuln/detail/CVE-2022-21330) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21332](https://nvd.nist.gov/vuln/detail/CVE-2022-21332) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21334](https://nvd.nist.gov/vuln/detail/CVE-2022-21334) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21335](https://nvd.nist.gov/vuln/detail/CVE-2022-21335) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21336](https://nvd.nist.gov/vuln/detail/CVE-2022-21336) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21337](https://nvd.nist.gov/vuln/detail/CVE-2022-21337) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21356](https://nvd.nist.gov/vuln/detail/CVE-2022-21356) CVSSv3=6.3 (nixos-unstable)\n* [ ] [CVE-2022-21301](https://nvd.nist.gov/vuln/detail/CVE-2022-21301) CVSSv3=5.5 (nixos-unstable)\n* [ ] [CVE-2022-21367](https://nvd.nist.gov/vuln/detail/CVE-2022-21367) CVSSv3=5.5 (nixos-unstable)\n* [ ] [CVE-2022-21378](https://nvd.nist.gov/vuln/detail/CVE-2022-21378) CVSSv3=5.5 (nixos-unstable)\n* [ ] [CVE-2022-21254](https://nvd.nist.gov/vuln/detail/CVE-2022-21254) CVSSv3=5.3 (nixos-unstable)\n* [ ] [CVE-2022-21302](https://nvd.nist.gov/vuln/detail/CVE-2022-21302) CVSSv3=5.3 (nixos-unstable)\n* [ ] [CVE-2022-21253](https://nvd.nist.gov/vuln/detail/CVE-2022-21253) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21256](https://nvd.nist.gov/vuln/detail/CVE-2022-21256) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21264](https://nvd.nist.gov/vuln/detail/CVE-2022-21264) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21270](https://nvd.nist.gov/vuln/detail/CVE-2022-21270) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21303](https://nvd.nist.gov/vuln/detail/CVE-2022-21303) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21304](https://nvd.nist.gov/vuln/detail/CVE-2022-21304) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21339](https://nvd.nist.gov/vuln/detail/CVE-2022-21339) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21342](https://nvd.nist.gov/vuln/detail/CVE-2022-21342) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21344](https://nvd.nist.gov/vuln/detail/CVE-2022-21344) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21348](https://nvd.nist.gov/vuln/detail/CVE-2022-21348) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21362](https://nvd.nist.gov/vuln/detail/CVE-2022-21362) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21370](https://nvd.nist.gov/vuln/detail/CVE-2022-21370) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21374](https://nvd.nist.gov/vuln/detail/CVE-2022-21374) CVSSv3=4.9 (nixos-unstable)\n* [ ] [CVE-2022-21368](https://nvd.nist.gov/vuln/detail/CVE-2022-21368) CVSSv3=4.7 (nixos-unstable)\n* [ ] [CVE-2022-21245](https://nvd.nist.gov/vuln/detail/CVE-2022-21245) CVSSv3=4.3 (nixos-unstable)\n* [ ] [CVE-2022-21265](https://nvd.nist.gov/vuln/detail/CVE-2022-21265) CVSSv3=3.8 (nixos-unstable)\n* [ ] [CVE-2022-21311](https://nvd.nist.gov/vuln/detail/CVE-2022-21311) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21312](https://nvd.nist.gov/vuln/detail/CVE-2022-21312) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21313](https://nvd.nist.gov/vuln/detail/CVE-2022-21313) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21317](https://nvd.nist.gov/vuln/detail/CVE-2022-21317) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21319](https://nvd.nist.gov/vuln/detail/CVE-2022-21319) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21321](https://nvd.nist.gov/vuln/detail/CVE-2022-21321) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21323](https://nvd.nist.gov/vuln/detail/CVE-2022-21323) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21324](https://nvd.nist.gov/vuln/detail/CVE-2022-21324) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21325](https://nvd.nist.gov/vuln/detail/CVE-2022-21325) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21331](https://nvd.nist.gov/vuln/detail/CVE-2022-21331) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21333](https://nvd.nist.gov/vuln/detail/CVE-2022-21333) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21355](https://nvd.nist.gov/vuln/detail/CVE-2022-21355) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21357](https://nvd.nist.gov/vuln/detail/CVE-2022-21357) CVSSv3=2.9 (nixos-unstable)\n* [ ] [CVE-2022-21249](https://nvd.nist.gov/vuln/detail/CVE-2022-21249) CVSSv3=2.7 (nixos-unstable)\n* [ ] [CVE-2022-21372](https://nvd.nist.gov/vuln/detail/CVE-2022-21372) CVSSv3=2.7 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-21351\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 7.1 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21363\n\nVulnerability in the MySQL Connectors product of Oracle MySQL (component: Connector/J). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Connectors. Successful attacks of this vulnerability can result in takeover of MySQL Connectors. CVSS 3.1 Base Score 6.6 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21358\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Encryption). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21279\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21280\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21284\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21285\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21286\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21287\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21288\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21289\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21290\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21307\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21308\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21309\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21310\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21314\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21315\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21316\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with logon to the infrastructure where MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21318\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with logon to the infrastructure where MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21320\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21322\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21326\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21327\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21328\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21329\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21330\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21332\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21334\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21335\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21336\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21337\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21356\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21301\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21367\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Compiling). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21378\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21254\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21302\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21253\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21256\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Group Replication Plugin). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21264\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21270\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Federated). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21303\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Stored Procedure). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21304\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Parser). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21339\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21342\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21344\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Replication). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21348\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21362\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Information Schema). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21370\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21374\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Information Schema). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21368\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Components Services). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data as well as unauthorized read access to a subset of MySQL Server accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 4.7 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:L).\n\n### CVE-2022-21245\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 4.3 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N).\n\n### CVE-2022-21265\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 3.8 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:L).\n\n### CVE-2022-21311\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21312\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21313\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21317\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21319\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21321\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21323\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21324\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21325\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21331\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21333\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21355\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21357\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21249\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: DDL). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 2.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:L).\n\n### CVE-2022-21372\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Encryption). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 2.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:L).\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @orivej\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160684/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160683","id":1143279425,"node_id":"I_kwDOAEVQ_M5EJQ9B","number":160683,"title":"Vulnerability roundup 111: mysql-8.0.26: 72 advisories [7.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:39:21Z","updated_at":"2022-02-18T15:39:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mysql&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mysql+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21278](https://nvd.nist.gov/vuln/detail/CVE-2022-21278) CVSSv3=7.1 (nixos-21.11)\n* [ ] [CVE-2022-21351](https://nvd.nist.gov/vuln/detail/CVE-2022-21351) CVSSv3=7.1 (nixos-21.11)\n* [ ] [CVE-2022-21363](https://nvd.nist.gov/vuln/detail/CVE-2022-21363) CVSSv3=6.6 (nixos-21.11)\n* [ ] [CVE-2022-21358](https://nvd.nist.gov/vuln/detail/CVE-2022-21358) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-21279](https://nvd.nist.gov/vuln/detail/CVE-2022-21279) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21280](https://nvd.nist.gov/vuln/detail/CVE-2022-21280) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21284](https://nvd.nist.gov/vuln/detail/CVE-2022-21284) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21285](https://nvd.nist.gov/vuln/detail/CVE-2022-21285) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21286](https://nvd.nist.gov/vuln/detail/CVE-2022-21286) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21287](https://nvd.nist.gov/vuln/detail/CVE-2022-21287) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21288](https://nvd.nist.gov/vuln/detail/CVE-2022-21288) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21289](https://nvd.nist.gov/vuln/detail/CVE-2022-21289) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21290](https://nvd.nist.gov/vuln/detail/CVE-2022-21290) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21307](https://nvd.nist.gov/vuln/detail/CVE-2022-21307) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21308](https://nvd.nist.gov/vuln/detail/CVE-2022-21308) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21309](https://nvd.nist.gov/vuln/detail/CVE-2022-21309) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21310](https://nvd.nist.gov/vuln/detail/CVE-2022-21310) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21314](https://nvd.nist.gov/vuln/detail/CVE-2022-21314) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21315](https://nvd.nist.gov/vuln/detail/CVE-2022-21315) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21316](https://nvd.nist.gov/vuln/detail/CVE-2022-21316) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21318](https://nvd.nist.gov/vuln/detail/CVE-2022-21318) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21320](https://nvd.nist.gov/vuln/detail/CVE-2022-21320) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21322](https://nvd.nist.gov/vuln/detail/CVE-2022-21322) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21326](https://nvd.nist.gov/vuln/detail/CVE-2022-21326) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21327](https://nvd.nist.gov/vuln/detail/CVE-2022-21327) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21328](https://nvd.nist.gov/vuln/detail/CVE-2022-21328) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21329](https://nvd.nist.gov/vuln/detail/CVE-2022-21329) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21330](https://nvd.nist.gov/vuln/detail/CVE-2022-21330) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21332](https://nvd.nist.gov/vuln/detail/CVE-2022-21332) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21334](https://nvd.nist.gov/vuln/detail/CVE-2022-21334) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21335](https://nvd.nist.gov/vuln/detail/CVE-2022-21335) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21336](https://nvd.nist.gov/vuln/detail/CVE-2022-21336) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21337](https://nvd.nist.gov/vuln/detail/CVE-2022-21337) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21356](https://nvd.nist.gov/vuln/detail/CVE-2022-21356) CVSSv3=6.3 (nixos-21.11)\n* [ ] [CVE-2022-21352](https://nvd.nist.gov/vuln/detail/CVE-2022-21352) CVSSv3=5.9 (nixos-21.11)\n* [ ] [CVE-2022-21301](https://nvd.nist.gov/vuln/detail/CVE-2022-21301) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-21367](https://nvd.nist.gov/vuln/detail/CVE-2022-21367) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-21378](https://nvd.nist.gov/vuln/detail/CVE-2022-21378) CVSSv3=5.5 (nixos-21.11)\n* [ ] [CVE-2022-21254](https://nvd.nist.gov/vuln/detail/CVE-2022-21254) CVSSv3=5.3 (nixos-21.11)\n* [ ] [CVE-2022-21302](https://nvd.nist.gov/vuln/detail/CVE-2022-21302) CVSSv3=5.3 (nixos-21.11)\n* [ ] [CVE-2022-21253](https://nvd.nist.gov/vuln/detail/CVE-2022-21253) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21256](https://nvd.nist.gov/vuln/detail/CVE-2022-21256) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21264](https://nvd.nist.gov/vuln/detail/CVE-2022-21264) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21270](https://nvd.nist.gov/vuln/detail/CVE-2022-21270) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21297](https://nvd.nist.gov/vuln/detail/CVE-2022-21297) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21303](https://nvd.nist.gov/vuln/detail/CVE-2022-21303) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21304](https://nvd.nist.gov/vuln/detail/CVE-2022-21304) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21339](https://nvd.nist.gov/vuln/detail/CVE-2022-21339) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21342](https://nvd.nist.gov/vuln/detail/CVE-2022-21342) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21344](https://nvd.nist.gov/vuln/detail/CVE-2022-21344) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21348](https://nvd.nist.gov/vuln/detail/CVE-2022-21348) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21362](https://nvd.nist.gov/vuln/detail/CVE-2022-21362) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21370](https://nvd.nist.gov/vuln/detail/CVE-2022-21370) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21374](https://nvd.nist.gov/vuln/detail/CVE-2022-21374) CVSSv3=4.9 (nixos-21.11)\n* [ ] [CVE-2022-21368](https://nvd.nist.gov/vuln/detail/CVE-2022-21368) CVSSv3=4.7 (nixos-21.11)\n* [ ] [CVE-2022-21245](https://nvd.nist.gov/vuln/detail/CVE-2022-21245) CVSSv3=4.3 (nixos-21.11)\n* [ ] [CVE-2022-21265](https://nvd.nist.gov/vuln/detail/CVE-2022-21265) CVSSv3=3.8 (nixos-21.11)\n* [ ] [CVE-2022-21311](https://nvd.nist.gov/vuln/detail/CVE-2022-21311) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21312](https://nvd.nist.gov/vuln/detail/CVE-2022-21312) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21313](https://nvd.nist.gov/vuln/detail/CVE-2022-21313) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21317](https://nvd.nist.gov/vuln/detail/CVE-2022-21317) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21319](https://nvd.nist.gov/vuln/detail/CVE-2022-21319) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21321](https://nvd.nist.gov/vuln/detail/CVE-2022-21321) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21323](https://nvd.nist.gov/vuln/detail/CVE-2022-21323) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21324](https://nvd.nist.gov/vuln/detail/CVE-2022-21324) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21325](https://nvd.nist.gov/vuln/detail/CVE-2022-21325) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21331](https://nvd.nist.gov/vuln/detail/CVE-2022-21331) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21333](https://nvd.nist.gov/vuln/detail/CVE-2022-21333) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21355](https://nvd.nist.gov/vuln/detail/CVE-2022-21355) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21357](https://nvd.nist.gov/vuln/detail/CVE-2022-21357) CVSSv3=2.9 (nixos-21.11)\n* [ ] [CVE-2022-21249](https://nvd.nist.gov/vuln/detail/CVE-2022-21249) CVSSv3=2.7 (nixos-21.11)\n* [ ] [CVE-2022-21372](https://nvd.nist.gov/vuln/detail/CVE-2022-21372) CVSSv3=2.7 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-21278\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 7.1 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21351\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 7.1 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21363\n\nVulnerability in the MySQL Connectors product of Oracle MySQL (component: Connector/J). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Connectors. Successful attacks of this vulnerability can result in takeover of MySQL Connectors. CVSS 3.1 Base Score 6.6 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21358\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Encryption). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21279\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21280\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21284\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21285\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21286\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21287\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21288\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21289\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21290\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21307\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21308\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21309\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21310\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21314\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21315\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21316\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with logon to the infrastructure where MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21318\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with logon to the infrastructure where MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21320\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21322\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21326\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21327\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21328\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21329\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21330\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21332\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21334\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21335\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21336\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21337\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21356\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H).\n\n### CVE-2022-21352\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all MySQL Server accessible data and unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.9 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:N/I:H/A:H).\n\n### CVE-2022-21301\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21367\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Compiling). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21378\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21254\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21302\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.27 and prior. Difficult to exploit vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21253\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21256\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Group Replication Plugin). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21264\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21270\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Federated). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21297\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21303\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Stored Procedure). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21304\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Parser). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21339\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21342\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21344\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Replication). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21348\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21362\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Information Schema). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21370\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21374\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Information Schema). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21368\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Components Services). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data as well as unauthorized read access to a subset of MySQL Server accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 4.7 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:L).\n\n### CVE-2022-21245\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 4.3 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N).\n\n### CVE-2022-21265\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 3.8 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:L).\n\n### CVE-2022-21311\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21312\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21313\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21317\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21319\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21321\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21323\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21324\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21325\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21331\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21333\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21355\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21357\n\nVulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.34 and prior, 7.5.24 and prior, 7.6.20 and prior and 8.0.27 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Cluster accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 2.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:L).\n\n### CVE-2022-21249\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: DDL). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 2.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:L).\n\n### CVE-2022-21372\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Encryption). Supported versions that are affected are 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 2.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:L).\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @orivej\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160683/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160682","id":1143278377,"node_id":"I_kwDOAEVQ_M5EJQsp","number":160682,"title":"fcitx5-rime: nonexistent config file","user":{"login":"Eliot00","id":18375468,"node_id":"MDQ6VXNlcjE4Mzc1NDY4","avatar_url":"https://avatars.githubusercontent.com/u/18375468?v=4","gravatar_id":"","url":"https://api.github.com/users/Eliot00","html_url":"https://github.com/Eliot00","followers_url":"https://api.github.com/users/Eliot00/followers","following_url":"https://api.github.com/users/Eliot00/following{/other_user}","gists_url":"https://api.github.com/users/Eliot00/gists{/gist_id}","starred_url":"https://api.github.com/users/Eliot00/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Eliot00/subscriptions","organizations_url":"https://api.github.com/users/Eliot00/orgs","repos_url":"https://api.github.com/users/Eliot00/repos","events_url":"https://api.github.com/users/Eliot00/events{/privacy}","received_events_url":"https://api.github.com/users/Eliot00/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-02-18T15:38:38Z","updated_at":"2022-02-19T23:00:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. modified configuration.nix from:\r\n\r\n```nix\r\n i18n.inputMethod = {\r\n enabled = \"ibus\";\r\n ibus.engines = with pkgs.ibus-engines; [ rime ];\r\n };\r\n```\r\n\r\nto:\r\n\r\n```nix\r\n i18n.inputMethod = {\r\n enabled = \"fcitx5\";\r\n # ibus.engines = with pkgs.ibus-engines; [ rime ];\r\n fcitx5.addons = with pkgs; [ fcitx5-rime fcitx5-chinese-addons ];\r\n };\r\n```\r\n2. run `sudo nixos-rebuild boot` and `reboot`\r\n3. see error log:\r\n```console\r\nW20220218 23:20:33.091089 1615 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/user.yaml'.\r\nW20220218 23:20:33.091238 2614 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/build/default.yaml'.\r\nW20220218 23:20:33.091269 2614 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/default.yaml'.\r\nW20220218 23:20:33.091315 2614 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/build/default.yaml'.\r\nW20220218 23:20:33.091328 2614 deployment_tasks.cc:185] schema list not defined.\r\nW20220218 23:20:33.110857 1615 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/build/default.yaml'.\r\nW20220218 23:20:33.110886 1615 config_data.cc:62] nonexistent config file '/home/elliot/.local/share/fcitx5/rime/user.yaml'.\r\n```\r\n4. fcitx5-rime can't work\r\n\r\n### Expected behavior\r\n\r\nfcitx5-rime can use after config\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n\r\n@Vonfry \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.334639.9ab7d12287c\"`\r\n - channels(elliot): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160682/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160680","id":1143271861,"node_id":"I_kwDOAEVQ_M5EJPG1","number":160680,"title":"Vulnerability roundup 111: mysql-5.7.27: 6 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:34:17Z","updated_at":"2022-02-18T15:34:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mysql&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mysql+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21367](https://nvd.nist.gov/vuln/detail/CVE-2022-21367) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-21270](https://nvd.nist.gov/vuln/detail/CVE-2022-21270) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-21303](https://nvd.nist.gov/vuln/detail/CVE-2022-21303) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-21304](https://nvd.nist.gov/vuln/detail/CVE-2022-21304) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-21344](https://nvd.nist.gov/vuln/detail/CVE-2022-21344) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-21245](https://nvd.nist.gov/vuln/detail/CVE-2022-21245) CVSSv3=4.3 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-21367\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Compiling). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H).\n\n### CVE-2022-21270\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Federated). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21303\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Stored Procedure). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21304\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Parser). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21344\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Replication). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2022-21245\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 4.3 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N).\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160680/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160678","id":1143271765,"node_id":"I_kwDOAEVQ_M5EJPFV","number":160678,"title":"Vulnerability roundup 111: moodle-3.11.4: 4 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:34:12Z","updated_at":"2022-02-18T15:34:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=moodle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=moodle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0332](https://nvd.nist.gov/vuln/detail/CVE-2022-0332) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-0335](https://nvd.nist.gov/vuln/detail/CVE-2022-0335) CVSSv3=8.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-0334](https://nvd.nist.gov/vuln/detail/CVE-2022-0334) CVSSv3=4.3 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-0333](https://nvd.nist.gov/vuln/detail/CVE-2022-0333) CVSSv3=3.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0332\n\nA flaw was found in Moodle in versions 3.11 to 3.11.4. An SQL injection risk was identified in the h5p activity web service responsible for fetching user attempt data.\n\n### CVE-2022-0335\n\nA flaw was found in Moodle in versions 3.11 to 3.11.4, 3.10 to 3.10.8, 3.9 to 3.9.11 and earlier unsupported versions. The \"delete badge alignment\" functionality did not include the necessary token check to prevent a CSRF risk.\n\n### CVE-2022-0334\n\nA flaw was found in Moodle in versions 3.11 to 3.11.4, 3.10 to 3.10.8, 3.9 to 3.9.11 and earlier unsupported versions. Insufficient capability checks could lead to users accessing their grade report for courses where they did not have the required gradereport/user:view capability.\n\n### CVE-2022-0333\n\nA flaw was found in Moodle in versions 3.11 to 3.11.4, 3.10 to 3.10.8, 3.9 to 3.9.11 and earlier unsupported versions. The calendar:manageentries capability allowed managers to access or modify any calendar event, but should have been restricted from accessing user level events.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @freezeboy\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160678/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160677","id":1143271696,"node_id":"I_kwDOAEVQ_M5EJPEQ","number":160677,"title":"Vulnerability roundup 111: mongodb-3.4.24: 1 advisory [7.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:34:09Z","updated_at":"2022-02-24T11:38:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mongodb&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mongodb+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-32036](https://nvd.nist.gov/vuln/detail/CVE-2021-32036) CVSSv3=7.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-32036\n\nAn authenticated user without any specific authorizations may be able to repeatedly invoke the features command where at a high volume may lead to resource depletion or generate high lock contention. This may result in denial of service and in rare cases could result in id field collisions.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @bluescreen303\nCc @cstrahan\nCc @offlinehacker\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160677/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160676","id":1143271609,"node_id":"I_kwDOAEVQ_M5EJPC5","number":160676,"title":"Vulnerability roundup 111: micronaut-1.3.7: 1 advisory [5.3]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:34:06Z","updated_at":"2022-02-18T15:34:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=micronaut&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=micronaut+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21700](https://nvd.nist.gov/vuln/detail/CVE-2022-21700) CVSSv3=5.3 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-21700\n\nMicronaut is a JVM-based, full stack Java framework designed for building JVM web applications with support for Java, Kotlin and the Groovy language. In affected versions sending an invalid Content Type header leads to memory leak in DefaultArgumentConversionContext as this type is erroneously used in static state. ### Impact Sending an invalid Content Type header leads to memory leak in `DefaultArgumentConversionContext` as this type is erroneously used in static state. ### Patches The problem is patched in Micronaut 3.2.7 and above. ### Workarounds The default content type binder can be replaced in an existing Micronaut application to mitigate the issue: ```java package example; import java.util.List; import io.micronaut.context.annotation.Replaces; import io.micronaut.core.convert.ConversionService; import io.micronaut.http.MediaType; import io.micronaut.http.bind.DefaultRequestBinderRegistry; import io.micronaut.http.bind.binders.RequestArgumentBinder; import jakarta.inject.Singleton; @Singleton @Replaces(DefaultRequestBinderRegistry.class) class FixedRequestBinderRegistry extends DefaultRequestBinderRegistry { public FixedRequestBinderRegistry(ConversionService conversionService, List<RequestArgumentBinder> binders) { super(conversionService, binders); } @Override protected void registerDefaultConverters(ConversionService<?> conversionService) { super.registerDefaultConverters(conversionService); conversionService.addConverter(CharSequence.class, MediaType.class, charSequence -> { try { return MediaType.of(charSequence); } catch (IllegalArgumentException e) { return null; } }); } } ``` ### References Commit that introduced the vulnerability https://github.com/micronaut-projects/micronaut-core/commit/b8ec32c311689667c69ae7d9f9c3b3a8abc96fe3 ### For more information If you have any questions or comments about this advisory: * Open an issue in [Micronaut Core](https://github.com/micronaut-projects/micronaut-core/issues) * Email us at [info@micronaut.io](mailto:info@micronaut.io)\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @moaxcp\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160676/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160675","id":1143271548,"node_id":"I_kwDOAEVQ_M5EJPB8","number":160675,"title":"Vulnerability roundup 111: mattermost-5.37.5: 2 advisories [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:34:04Z","updated_at":"2022-02-18T15:34:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mattermost&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mattermost+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-37864](https://nvd.nist.gov/vuln/detail/CVE-2021-37864) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2021-37865](https://nvd.nist.gov/vuln/detail/CVE-2021-37865) CVSSv3=5.7 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-37864\n\nMattermost 6.1 and earlier fails to sufficiently validate permissions while viewing archived channels, which allows authenticated users to view contents of archived channels even when this is denied by system administrators by directly accessing the APIs.\n\n### CVE-2021-37865\n\nMattermost 6.2 and earlier fails to sufficiently process a specifically crafted GIF file when it is uploaded while drafting a post, which allows authenticated users to cause resource exhaustion while processing the file, resulting in server-side Denial of Service.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @fpletz\nCc @ryantm\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160675/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160670","id":1143271321,"node_id":"I_kwDOAEVQ_M5EJO-Z","number":160670,"title":"Vulnerability roundup 111: libsixel-1.10.3: 1 advisory [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:33:53Z","updated_at":"2022-02-18T15:33:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=libsixel&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=libsixel+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45340](https://nvd.nist.gov/vuln/detail/CVE-2021-45340) CVSSv3=6.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45340\n\nIn Libsixel prior to and including v1.10.3, a NULL pointer dereference in the stb_image.h component of libsixel allows attackers to cause a denial of service (DOS) via a crafted PICT file.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @vrthra\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160670/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160668","id":1143271215,"node_id":"I_kwDOAEVQ_M5EJO8v","number":160668,"title":"Vulnerability roundup 111: librecad-2.2.0-rc2: 2 advisories [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:33:49Z","updated_at":"2022-02-18T15:33:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=librecad&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=librecad+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45341](https://nvd.nist.gov/vuln/detail/CVE-2021-45341) CVSSv3=8.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45342](https://nvd.nist.gov/vuln/detail/CVE-2021-45342) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45341\n\nA buffer overflow vulnerability in CDataMoji of the jwwlib component of LibreCAD 2.2.0-rc3 and older allows an attacker to achieve Remote Code Execution using a crafted JWW document.\n\n### CVE-2021-45342\n\nA buffer overflow vulnerability in CDataList of the jwwlib component of LibreCAD 2.2.0-rc3 and older allows an attacker to achieve Remote Code Execution using a crafted JWW document.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @Kiwi\nCc @viric\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160668/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160667","id":1143271163,"node_id":"I_kwDOAEVQ_M5EJO77","number":160667,"title":"Vulnerability roundup 111: libde265-1.0.8: 5 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:33:47Z","updated_at":"2022-02-18T15:33:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=libde265&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=libde265+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-36409](https://nvd.nist.gov/vuln/detail/CVE-2021-36409) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-35452](https://nvd.nist.gov/vuln/detail/CVE-2021-35452) CVSSv3=6.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-36408](https://nvd.nist.gov/vuln/detail/CVE-2021-36408) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-36410](https://nvd.nist.gov/vuln/detail/CVE-2021-36410) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-36411](https://nvd.nist.gov/vuln/detail/CVE-2021-36411) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-36409\n\nThere is an Assertion `scaling_list_pred_matrix_id_delta==1' failed at sps.cc:925 in libde265 v1.0.8 when decoding file, which allows attackers to cause a Denial of Service (DoS) by running the application with a crafted file or possibly have unspecified other impact.\n\n### CVE-2021-35452\n\nAn Incorrect Access Control vulnerability exists in libde265 v1.0.8 due to a SEGV in slice.cc.\n\n### CVE-2021-36408\n\nAn issue was discovered in libde265 v1.0.8.There is a Heap-use-after-free in intrapred.h when decoding file using dec265.\n\n### CVE-2021-36410\n\nA stack-buffer-overflow exists in libde265 v1.0.8 via fallback-motion.cc in function put_epel_hv_fallback when running program dec265.\n\n### CVE-2021-36411\n\nAn issue has been found in libde265 v1.0.8 due to incorrect access control. A SEGV caused by a READ memory access in function derive_boundaryStrength of deblock.cc has occurred. The vulnerability causes a segmentation fault and application crash, which leads to remote denial of service.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @gebner\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160667/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160663","id":1143263541,"node_id":"I_kwDOAEVQ_M5EJNE1","number":160663,"title":"Vulnerability roundup 111: keycloak-15.1.0: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:28:40Z","updated_at":"2022-02-18T15:28:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=keycloak&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=keycloak+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-4133](https://nvd.nist.gov/vuln/detail/CVE-2021-4133) CVSSv3=8.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-4133\n\nA flaw was found in Keycloak in versions from 12.0.0 and before 15.1.1 which allows an attacker with any existing user account to create new default user accounts via the administrative REST API even when new user registration is disabled.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @ngerstle\nCc @talyz\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160663/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160662","id":1143263473,"node_id":"I_kwDOAEVQ_M5EJNDx","number":160662,"title":"Vulnerability roundup 111: jenkins-2.319.1: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:28:38Z","updated_at":"2022-02-18T15:28:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=jenkins&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=jenkins+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0538](https://nvd.nist.gov/vuln/detail/CVE-2022-0538) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2022-20612](https://nvd.nist.gov/vuln/detail/CVE-2022-20612) CVSSv3=4.3 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0538\n\nJenkins 2.333 and earlier, LTS 2.319.2 and earlier defines custom XStream converters that have not been updated to apply the protections for the vulnerability CVE-2021-43859 and allow unconstrained resource usage.\n\n### CVE-2022-20612\n\nA cross-site request forgery (CSRF) vulnerability in Jenkins 2.329 and earlier, LTS 2.319.1 and earlier allows attackers to trigger build of job without parameters when no security realm is set.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @coreyoconnor\nCc @earldouglas\nCc @fpletz\nCc @nequissimus\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160662/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160661","id":1143263396,"node_id":"I_kwDOAEVQ_M5EJNCk","number":160661,"title":"Vulnerability roundup 111: jenkins-2.303.3: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:28:35Z","updated_at":"2022-02-18T15:28:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=jenkins&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=jenkins+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0538](https://nvd.nist.gov/vuln/detail/CVE-2022-0538) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-20612](https://nvd.nist.gov/vuln/detail/CVE-2022-20612) CVSSv3=4.3 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0538\n\nJenkins 2.333 and earlier, LTS 2.319.2 and earlier defines custom XStream converters that have not been updated to apply the protections for the vulnerability CVE-2021-43859 and allow unconstrained resource usage.\n\n### CVE-2022-20612\n\nA cross-site request forgery (CSRF) vulnerability in Jenkins 2.329 and earlier, LTS 2.319.1 and earlier allows attackers to trigger build of job without parameters when no security realm is set.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @coreyoconnor\nCc @earldouglas\nCc @fpletz\nCc @nequissimus\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160661/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160658","id":1143263216,"node_id":"I_kwDOAEVQ_M5EJM_w","number":160658,"title":"Vulnerability roundup 111: h2-1.4.199: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:28:28Z","updated_at":"2022-02-18T15:28:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=h2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=h2+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-42392](https://nvd.nist.gov/vuln/detail/CVE-2021-42392) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2022-23221](https://nvd.nist.gov/vuln/detail/CVE-2022-23221) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-42392\n\nThe org.h2.util.JdbcUtils.getConnection method of the H2 database takes as parameters the class name of the driver and URL of the database. An attacker may pass a JNDI driver name and a URL leading to a LDAP or RMI servers, causing remote code execution. This can be exploited through various attack vectors, most notably through the H2 Console which leads to unauthenticated remote code execution.\n\n### CVE-2022-23221\n\nH2 Console before 2.1.210 allows remote attackers to execute arbitrary code via a jdbc:h2:mem JDBC URL containing the IGNORE_UNKNOWN_SETTINGS=TRUE;FORBID_CREATION=FALSE;INIT=RUNSCRIPT substring, a different vulnerability than CVE-2021-42392.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\nCc @2chilled\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160658/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160656","id":1143263117,"node_id":"I_kwDOAEVQ_M5EJM-N","number":160656,"title":"Vulnerability roundup 111: gradle-7.3.3: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:28:24Z","updated_at":"2022-02-18T15:28:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23630](https://nvd.nist.gov/vuln/detail/CVE-2022-23630) CVSSv3=7.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23630\n\nGradle is a build tool with a focus on build automation and support for multi-language development. In some cases, Gradle may skip that verification and accept a dependency that would otherwise fail the build as an untrusted external artifact. This occurs when dependency verification is disabled on one or more configurations and those configurations have common dependencies with other configurations that have dependency verification enabled. If the configuration that has dependency verification disabled is resolved first, Gradle does not verify the common dependencies for the configuration that has dependency verification enabled. Gradle 7.4 fixes that issue by validating artifacts at least once if they are present in a resolved configuration that has dependency verification active. For users who cannot update either do not use `ResolutionStrategy.disableDependencyVerification()` and do not use plugins that use that method to disable dependency verification for a single configuration or make sure resolution of configuration that disable that feature do not happen in builds that resolve configuration where the feature is enabled.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @liff\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160656/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160655","id":1143263047,"node_id":"I_kwDOAEVQ_M5EJM9H","number":160655,"title":"Vulnerability roundup 111: gradle-7.3: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":319264432,"node_id":"MDU6TGFiZWwzMTkyNjQ0MzI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20port%20to%20stable","name":"9.needs: port to stable","color":"eb6420","default":false,"description":"A PR needs a backport to the stable release."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:28:22Z","updated_at":"2022-03-25T14:03:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23630](https://nvd.nist.gov/vuln/detail/CVE-2022-23630) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23630\n\nGradle is a build tool with a focus on build automation and support for multi-language development. In some cases, Gradle may skip that verification and accept a dependency that would otherwise fail the build as an untrusted external artifact. This occurs when dependency verification is disabled on one or more configurations and those configurations have common dependencies with other configurations that have dependency verification enabled. If the configuration that has dependency verification disabled is resolved first, Gradle does not verify the common dependencies for the configuration that has dependency verification enabled. Gradle 7.4 fixes that issue by validating artifacts at least once if they are present in a resolved configuration that has dependency verification active. For users who cannot update either do not use `ResolutionStrategy.disableDependencyVerification()` and do not use plugins that use that method to disable dependency verification for a single configuration or make sure resolution of configuration that disable that feature do not happen in builds that resolve configuration where the feature is enabled.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160655/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160653","id":1143262912,"node_id":"I_kwDOAEVQ_M5EJM7A","number":160653,"title":"Vulnerability roundup 111: gradle-6.9.1: 1 advisory [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:28:16Z","updated_at":"2022-02-18T15:28:18Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23630](https://nvd.nist.gov/vuln/detail/CVE-2022-23630) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23630\n\nGradle is a build tool with a focus on build automation and support for multi-language development. In some cases, Gradle may skip that verification and accept a dependency that would otherwise fail the build as an untrusted external artifact. This occurs when dependency verification is disabled on one or more configurations and those configurations have common dependencies with other configurations that have dependency verification enabled. If the configuration that has dependency verification disabled is resolved first, Gradle does not verify the common dependencies for the configuration that has dependency verification enabled. Gradle 7.4 fixes that issue by validating artifacts at least once if they are present in a resolved configuration that has dependency verification active. For users who cannot update either do not use `ResolutionStrategy.disableDependencyVerification()` and do not use plugins that use that method to disable dependency verification for a single configuration or make sure resolution of configuration that disable that feature do not happen in builds that resolve configuration where the feature is enabled.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160653/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160651","id":1143262798,"node_id":"I_kwDOAEVQ_M5EJM5O","number":160651,"title":"Vulnerability roundup 111: go-1.17.5: 3 advisories [9.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:28:12Z","updated_at":"2022-02-18T15:28:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23806](https://nvd.nist.gov/vuln/detail/CVE-2022-23806) CVSSv3=9.1 (nixos-21.11)\n* [ ] [CVE-2022-23772](https://nvd.nist.gov/vuln/detail/CVE-2022-23772) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-23773](https://nvd.nist.gov/vuln/detail/CVE-2022-23773) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23806\n\nCurve.IsOnCurve in crypto/elliptic in Go before 1.16.14 and 1.17.x before 1.17.7 can incorrectly return true in situations with a big.Int value that is not a valid field element.\n\n### CVE-2022-23772\n\nRat.SetString in math/big in Go before 1.16.14 and 1.17.x before 1.17.7 has an overflow that can lead to Uncontrolled Memory Consumption.\n\n### CVE-2022-23773\n\ncmd/go in Go before 1.16.14 and 1.17.x before 1.17.7 can misinterpret branch names that falsely appear to be version tags. This can lead to incorrect access control if an actor is supposed to be able to create branches but not tags.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @Frostman\nCc @c00w\nCc @cstrahan\nCc @kalbasit\nCc @mdlayher\nCc @mic92\nCc @orivej\nCc @rvolosatovs\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160651/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160650","id":1143262733,"node_id":"I_kwDOAEVQ_M5EJM4N","number":160650,"title":"Vulnerability roundup 111: go-1.16.13: 3 advisories [9.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:28:10Z","updated_at":"2022-02-18T15:28:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23806](https://nvd.nist.gov/vuln/detail/CVE-2022-23806) CVSSv3=9.1 (nixos-21.11)\n* [ ] [CVE-2022-23772](https://nvd.nist.gov/vuln/detail/CVE-2022-23772) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2022-23773](https://nvd.nist.gov/vuln/detail/CVE-2022-23773) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23806\n\nCurve.IsOnCurve in crypto/elliptic in Go before 1.16.14 and 1.17.x before 1.17.7 can incorrectly return true in situations with a big.Int value that is not a valid field element.\n\n### CVE-2022-23772\n\nRat.SetString in math/big in Go before 1.16.14 and 1.17.x before 1.17.7 has an overflow that can lead to Uncontrolled Memory Consumption.\n\n### CVE-2022-23773\n\ncmd/go in Go before 1.16.14 and 1.17.x before 1.17.7 can misinterpret branch names that falsely appear to be version tags. This can lead to incorrect access control if an actor is supposed to be able to create branches but not tags.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @Frostman\nCc @c00w\nCc @cstrahan\nCc @kalbasit\nCc @mdlayher\nCc @mic92\nCc @orivej\nCc @rvolosatovs\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160650/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160648","id":1143251449,"node_id":"I_kwDOAEVQ_M5EJKH5","number":160648,"title":"Vulnerability roundup 111: glibc-2.33-59: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:21:18Z","updated_at":"2022-02-18T15:21:18Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=glibc&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=glibc+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23218](https://nvd.nist.gov/vuln/detail/CVE-2022-23218) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2022-23219](https://nvd.nist.gov/vuln/detail/CVE-2022-23219) CVSSv3=9.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2022-23218\n\nThe deprecated compatibility function svcunix_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its path argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n### CVE-2022-23219\n\nThe deprecated compatibility function clnt_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its hostname argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @edolstra\nCc @ma27\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160648/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160647","id":1143251388,"node_id":"I_kwDOAEVQ_M5EJKG8","number":160647,"title":"Vulnerability roundup 111: glibc-2.33-117: 3 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:21:16Z","updated_at":"2022-02-18T15:21:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=glibc&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=glibc+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-23218](https://nvd.nist.gov/vuln/detail/CVE-2022-23218) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2022-23219](https://nvd.nist.gov/vuln/detail/CVE-2022-23219) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2021-38604](https://nvd.nist.gov/vuln/detail/CVE-2021-38604) CVSSv3=7.5 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-23218\n\nThe deprecated compatibility function svcunix_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its path argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n### CVE-2022-23219\n\nThe deprecated compatibility function clnt_create in the sunrpc module of the GNU C Library (aka glibc) through 2.34 copies its hostname argument on the stack without validating its length, which may result in a buffer overflow, potentially resulting in a denial of service or (if an application is not built with a stack protector enabled) arbitrary code execution.\n\n### CVE-2021-38604\n\nIn librt in the GNU C Library (aka glibc) through 2.34, sysdeps/unix/sysv/linux/mq_notify.c mishandles certain NOTIFY_REMOVED data, leading to a NULL pointer dereference. NOTE: this vulnerability was introduced as a side effect of the CVE-2021-33574 fix.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @edolstra\nCc @ma27\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160647/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160645","id":1143251263,"node_id":"I_kwDOAEVQ_M5EJKE_","number":160645,"title":"Vulnerability roundup 111: gh-ost-1.1.2: 1 advisory [6.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:21:11Z","updated_at":"2022-02-24T11:44:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gh-ost&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gh-ost+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-21687](https://nvd.nist.gov/vuln/detail/CVE-2022-21687) CVSSv3=6.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-21687\n\ngh-ost is a triggerless online schema migration solution for MySQL. Versions prior to 1.1.3 are subject to an arbitrary file read vulnerability. The attacker must have access to the target host or trick an administrator into executing a malicious gh-ost command on a host running gh-ost, plus network access from host running gh-ost to the attack's malicious MySQL server. The `-database` parameter does not properly sanitize user input which can lead to arbitrary file reads.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160645/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160638","id":1143250881,"node_id":"I_kwDOAEVQ_M5EJJ_B","number":160638,"title":"Vulnerability roundup 111: calibre-web-0.6.14: 6 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:20:56Z","updated_at":"2022-02-18T15:20:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=calibre-web&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=calibre-web+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-4171](https://nvd.nist.gov/vuln/detail/CVE-2021-4171) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2022-0339](https://nvd.nist.gov/vuln/detail/CVE-2022-0339) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-4164](https://nvd.nist.gov/vuln/detail/CVE-2021-4164) CVSSv3=8.8 (nixos-unstable)\n* [ ] [CVE-2022-0273](https://nvd.nist.gov/vuln/detail/CVE-2022-0273) CVSSv3=6.5 (nixos-unstable)\n* [ ] [CVE-2022-0352](https://nvd.nist.gov/vuln/detail/CVE-2022-0352) CVSSv3=6.1 (nixos-unstable)\n* [ ] [CVE-2021-4170](https://nvd.nist.gov/vuln/detail/CVE-2021-4170) CVSSv3=5.4 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-4171\n\ncalibre-web is vulnerable to Business Logic Errors\n\n### CVE-2022-0339\n\nServer-Side Request Forgery (SSRF) in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2021-4164\n\ncalibre-web is vulnerable to Cross-Site Request Forgery (CSRF)\n\n### CVE-2022-0273\n\nImproper Access Control in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2022-0352\n\nCross-site Scripting (XSS) - Reflected in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2021-4170\n\ncalibre-web is vulnerable to Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @pborzenkov\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160638/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160637","id":1143250837,"node_id":"I_kwDOAEVQ_M5EJJ-V","number":160637,"title":"Vulnerability roundup 111: calibre-web-0.6.13: 6 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T15:20:53Z","updated_at":"2022-02-18T15:20:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=calibre-web&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=calibre-web+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-4171](https://nvd.nist.gov/vuln/detail/CVE-2021-4171) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2022-0339](https://nvd.nist.gov/vuln/detail/CVE-2022-0339) CVSSv3=9.8 (nixos-21.11)\n* [ ] [CVE-2021-4164](https://nvd.nist.gov/vuln/detail/CVE-2021-4164) CVSSv3=8.8 (nixos-21.11)\n* [ ] [CVE-2022-0273](https://nvd.nist.gov/vuln/detail/CVE-2022-0273) CVSSv3=6.5 (nixos-21.11)\n* [ ] [CVE-2022-0352](https://nvd.nist.gov/vuln/detail/CVE-2022-0352) CVSSv3=6.1 (nixos-21.11)\n* [ ] [CVE-2021-4170](https://nvd.nist.gov/vuln/detail/CVE-2021-4170) CVSSv3=5.4 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-4171\n\ncalibre-web is vulnerable to Business Logic Errors\n\n### CVE-2022-0339\n\nServer-Side Request Forgery (SSRF) in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2021-4164\n\ncalibre-web is vulnerable to Cross-Site Request Forgery (CSRF)\n\n### CVE-2022-0273\n\nImproper Access Control in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2022-0352\n\nCross-site Scripting (XSS) - Reflected in Pypi calibreweb prior to 0.6.16.\n\n### CVE-2021-4170\n\ncalibre-web is vulnerable to Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e.\n\nCc @pborzenkov\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160637/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160635","id":1143250705,"node_id":"I_kwDOAEVQ_M5EJJ8R","number":160635,"title":"Vulnerability roundup 111: SharpZipLib-0.86.0: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-18T15:20:48Z","updated_at":"2022-02-18T15:20:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=SharpZipLib&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=SharpZipLib+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-32840](https://nvd.nist.gov/vuln/detail/CVE-2021-32840) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-32840\n\nSharpZipLib (or #ziplib) is a Zip, GZip, Tar and BZip2 library. Prior to version 1.3.3, a TAR file entry `../evil.txt` may be extracted in the parent directory of `destFolder`. This leads to arbitrary file write that may lead to code execution. The vulnerability was patched in version 1.3.3.\n\n-----\nScanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160635/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160625","id":1143077490,"node_id":"I_kwDOAEVQ_M5EIfpy","number":160625,"title":"yubikey-personalization-gui fails to build","user":{"login":"permezel","id":2313876,"node_id":"MDQ6VXNlcjIzMTM4NzY=","avatar_url":"https://avatars.githubusercontent.com/u/2313876?v=4","gravatar_id":"","url":"https://api.github.com/users/permezel","html_url":"https://github.com/permezel","followers_url":"https://api.github.com/users/permezel/followers","following_url":"https://api.github.com/users/permezel/following{/other_user}","gists_url":"https://api.github.com/users/permezel/gists{/gist_id}","starred_url":"https://api.github.com/users/permezel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/permezel/subscriptions","organizations_url":"https://api.github.com/users/permezel/orgs","repos_url":"https://api.github.com/users/permezel/repos","events_url":"https://api.github.com/users/permezel/events{/privacy}","received_events_url":"https://api.github.com/users/permezel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T13:36:54Z","updated_at":"2022-02-18T13:36:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nyubikey-personalization-gui fails to build\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-env -i yubikey-personalization-gui \r\n\r\n### Expected behavior\r\nI expect the command to be built.\r\n\r\n### Screenshots\r\n```\r\nsloth% nix-env -i yubikey-personalization-gui \r\ninstalling 'yubikey-personalization-gui-3.1.25'\r\nthis derivation will be built:\r\n /nix/store/8kx880h6kd2lnllmkrc8h7vd74pah9s4-yubikey-personalization-gui-3.1.25.drv\r\nthese 175 paths will be fetched (91.03 MiB download, 458.61 MiB unpacked):\r\n /nix/store/02qcpb7w7dpnn30mjxg8vcyi0zjj2b1f-apple-framework-CoreText\r\n /nix/store/03shvkqxyfwb6rm953acq7g0mnkkacwq-pango-1.50.3\r\n /nix/store/062b4xczsd43ybd2a2l6hpzna4fbmrxa-apple-framework-QuartzCore\r\n /nix/store/06c43d6nx5rizspjycgfd44rgnh236hn-libidn2-2.3.2\r\n /nix/store/08jyx957r4flyw7qb3pw7wwcysqgrx1j-yubikey-personalization-gui-3.1.25.tar.gz\r\n /nix/store/0fs1pcz04zirhb7prg99ifasnjw37cwr-apple-framework-IOKit\r\n /nix/store/0j9y9qmc7m01bcaq2vw3griakmr2wqx0-libthai-0.1.29\r\n /nix/store/0mdsnsdq7077hp5krhciackxm95h8yzs-libxslt-1.1.34-bin\r\n /nix/store/0saadbzrwvx281s9pdzxxbpgjlc5mq9b-apple-framework-OpenCL\r\n /nix/store/0y0lm54vscg18jbfic95wyrfv47f5gmd-curl-7.81.0\r\n /nix/store/13ww2fx4bgy5l14xcw1sca031rxr3k45-apple-framework-IOSurface\r\n /nix/store/177rdkdf356m468dfyp8qyvgdlg7aj1j-libxcb-1.14\r\n /nix/store/18jrr7jjs9jf67yqrf5cvskzb5c6r1si-brotli-1.0.9-lib\r\n /nix/store/1h6b9n7iidjp8s32n9hj1vkansyvg686-libXt-1.2.1\r\n /nix/store/1jqa5w6ah7ihbvmi7wv9zxw5n2bchsrp-perl-5.34.0\r\n /nix/store/1k7as0cvf83w1my8y2197lgbq88yfysf-libXt-1.2.1-dev\r\n /nix/store/1pl0rk5zanqbd39llccs6a2ajj85y8ir-gdk-pixbuf-2.42.6-dev\r\n /nix/store/1sq4ld172h08nk3yqk67qyj0nz122pg5-rav1e-0.5.1\r\n /nix/store/23fbs10yf2k0fpa80x1c0hwhx1ayzfq4-apple-framework-Security\r\n /nix/store/2c2nhznpv9a1yyda6wd33lf78b4q3b62-gettext-0.21\r\n /nix/store/2gfy9d9k13i2wkfin1p1cajn09z21975-apple-framework-CoreData\r\n /nix/store/2ilayry6mc94lnwdz10yrijh5a69s132-openexr-2.5.7-dev\r\n /nix/store/2k7q0xz5vfws29v8s6drw47raf4qg388-libffi-3.4.2-dev\r\n /nix/store/2m0zdcng89bl3glpzcw7vflxq4ymvg5n-libunistring-0.9.10\r\n /nix/store/2xlw9hdlyj5rzwz14qjxfp742b4q4jbw-apple-framework-CoreFoundation\r\n /nix/store/303nv3mpwmm9lr97iy6fw2dv7gn11cv5-pcre2-10.39-dev\r\n /nix/store/32b9ksisxwp3msrgjz2frmbzhcc2w1mp-libssh2-1.10.0\r\n /nix/store/3drcp8a9asx5yrb1h2k69mw8d2l7vx48-libxcb-1.14-dev\r\n /nix/store/3l32af8vap5qk3qhgnpdgib5r900ayf9-apple-framework-CoreLocation\r\n /nix/store/3yvavihg1maakvh2v02qrp5nx1f7ff97-apple-framework-ModelIO\r\n /nix/store/464iky47m47zxpxf0z4m6h9sbgzs55jb-apple-framework-AudioToolbox\r\n /nix/store/48jp1fcffb29p91mr5la3saa64py1ikh-librsvg-2.52.5\r\n /nix/store/49mysix44qjlpr7xh2aj1dzjciqch9na-apple-framework-Carbon\r\n /nix/store/4f0xfvx09grhz4g3zwd9dy2gyz3dmqh6-qtbase-5.12.10-bin\r\n /nix/store/4j9lzd1iqgfxmhn08kr6q011l56l904l-libraw-0.20.2\r\n /nix/store/4klbdaavwqcgk2hp48l5rfrc42g6a032-x265-3.5\r\n /nix/store/4l7wrqah2xi0z83r7n52fm8fk57g1j50-apple-framework-Metal\r\n /nix/store/4pby6a6ddnyb0f6ry03cmmfh0cf2wcga-objc4-709.1\r\n /nix/store/4y9xjw7hhjd5wvdb2fimn3jqm060bnhw-fontconfig-2.13.94-dev\r\n /nix/store/53y4djna9lg4rghph9n4x5y7biqwlwb9-libXau-1.0.9-dev\r\n /nix/store/5g7kmwj88sqrn3lmad2jy3xp8wlwffqv-libxml2-2.9.12\r\n /nix/store/5hphscbk7qgqipd5072b2c92zd45hmcc-libICE-1.0.10-dev\r\n /nix/store/5rjp3azxhk7y68mcwd6i4drqd33kk3aw-freetype-2.11.1-dev\r\n /nix/store/5w6gxpa4qdfm51cayzby50yh9cl8wl1a-harfbuzz-3.2.0-dev\r\n /nix/store/5wwpnv10s56z3wadb7vc7yvwn727mshm-icu4c-70.1-dev\r\n /nix/store/68grnmf14wd8r60zz7iz0d53x7v7c97p-sqlite-3.37.2-bin\r\n /nix/store/6kb21xvnbhda9qq59ar1max2d004pfhk-apple-framework-ServiceManagement\r\n /nix/store/6nxp44v8vblmpkdjmw0h06p9dq8pkgr2-fontconfig-2.13.94\r\n /nix/store/6nzywbp2rg7hb3c6rmmcdvy31l9sciv4-apple-framework-ApplicationServices\r\n /nix/store/6w03y9qaxhg75w0313n1gl382i6jsnwf-pkg-config-0.29.2\r\n /nix/store/73f251a281xcz9kqbssskivamxchirpj-openexr-2.5.7-bin\r\n /nix/store/752m4pxw3rcv498h124l6hh59s523wfy-apple-framework-AudioUnit\r\n /nix/store/75g0v4c3rxz4clwsp80f514qdyq34gf9-postgresql-13.5-lib\r\n /nix/store/75kkmw2qr86m4ji9gbdxjjzm27j1spmm-apple-framework-Cocoa\r\n /nix/store/7bfplbll52571lw2gny8268wgmmb9km0-dav1d-0.9.2\r\n /nix/store/7kvf2w7gc513p44lhf24afwqb36dhddi-djvulibre-3.5.28-dev\r\n /nix/store/7p9hphzk2h89wbb1fblgx242pvk3d6ac-libXau-1.0.9\r\n /nix/store/7px6ripq5yqrgs6ca00ynbxykm5bqbdj-yubikey-personalization-1.20.0\r\n /nix/store/7rri7ys1r12hgqlppgw5vy25dk43mhcw-libusb-1.0.24\r\n /nix/store/7y60bl2ysx5gidfhpc0bl4i67dcrha09-libpng-apng-1.6.37-dev\r\n /nix/store/87szb2sqa13py3sbfv0p187qa1867sla-openexr-2.5.7\r\n /nix/store/8h6ns6g3c2cd0ljwyjjwzrcxbhh9hbq3-libjxl-0.6.1\r\n /nix/store/8v6js2md35iacyvfh26fhfz7aba0z0i5-zstd-1.5.2\r\n /nix/store/90vkbqaxld49vx42kgn4dln63fmbkyag-pcre2-10.39-bin\r\n /nix/store/911bjzmg1wvj87js00z7pnl0riggxgxw-apple-framework-DiskArbitration\r\n /nix/store/9350cblagkxjwb86nbh1whb4f8zw8504-apple-framework-AppKit\r\n /nix/store/94d4y1i7gxxpa595wizragkx42p2lbgb-dbus-1.12.20-lib\r\n /nix/store/957nfnl29rikn6nq7mmjargf37i0if2d-libyubikey-1.13\r\n /nix/store/95wmga03ljf26mycw2dfc9jqcw1j82hr-libheif-1.12.0-dev\r\n /nix/store/9g16rn376r882f6zffc5a0n2xf0cn2g0-dbus-1.12.20\r\n /nix/store/9hpjsy91av3lx0pfbqsd7qcsnl5yhrjh-apple-framework-Foundation\r\n /nix/store/9sirmb84azjl1x6imlssr4nl1vrna32h-hook\r\n /nix/store/a6pw2mpw1bi7qmkvrrqpzr40l1gkgqbq-pixman-0.38.4\r\n /nix/store/a9kv1vg7inkrc2airvp58llbw44c79b0-libtiff-4.3.0-dev\r\n /nix/store/aa4mvxgy8m5pa4sxz42hh1gna0fihn5q-libXext-1.3.4\r\n /nix/store/aj75grihmc2j5ybvc6qh7pmjjn2ympwc-xorgproto-2021.5\r\n /nix/store/awbr2wzpf4xf11n1fhmmhnhvmmzz97h3-imagemagick-7.1.0-24-dev\r\n /nix/store/bbdb06wdfdymx2k5wybjsfj2c0r8hkis-cairo-1.16.0-dev\r\n /nix/store/bx0m19wwdd1gcwb4f2cx8z8ii0c8chdn-apple-framework-OpenDirectory\r\n /nix/store/cdf2bdayqk99cd3cy4980dk8dgng7hr7-sqlite-3.37.2-dev\r\n /nix/store/cfrfg80g0wx9wx7q11v04awllfkxbzqd-cairo-1.16.0\r\n /nix/store/ckfmi0dcz15qrsj2nfwh6ijwchzkk21m-libSM-1.2.3-dev\r\n /nix/store/clv6a60f5fiahmznp8ipggh8nfnaards-openjpeg-2.4.0\r\n /nix/store/cm2xdmh4v1c70f4i0gks0mfn5ymfnhdh-lcms2-2.12-bin\r\n /nix/store/cyssq6cvdxl8vxljmm6xh9kxpjlb27kw-expat-2.4.4-dev\r\n /nix/store/d4zljaq6fv9wrqyvchxxswwvqj69np73-dbus-1.12.20-dev\r\n /nix/store/dh9gss9pid7vx3qm5ya0p9qx267d86f9-openssl-1.1.1m-dev\r\n /nix/store/dl15nx5ijygmj58rdmsjm5c6gl0p7kwl-libXdmcp-1.1.3\r\n /nix/store/f97varjrmvjphyzvfzfl7lx7dbas35qn-apple-framework-SecurityFoundation\r\n /nix/store/fi25y5nwacqfj61dd0q33sr1jd29370g-libpng-apng-1.6.37\r\n /nix/store/fml90csmdl6q40pw913178lnx9af9rk0-fontconfig-2.13.94-lib\r\n /nix/store/g08vxrq5hzgj3284zzjdfm14ifia0zn5-libheif-1.12.0-bin\r\n /nix/store/g2kslbpn3pzxq7gvwraz9s470slizh9v-hook\r\n /nix/store/g6fdlmvbm83jqf3n3a3v561bi5xx51ap-apple-framework-CoreBluetooth\r\n /nix/store/gdsh20cvk495ammlspzra426zxpm18gv-gdk-pixbuf-2.42.6\r\n /nix/store/gm9h8mha6arb0am62rylbxq4lg8292s7-glib-2.70.2-bin\r\n /nix/store/gswnlnq58llz9br77z03caaphmilar3w-lcms2-2.12\r\n /nix/store/gvwk0137cgvwanv8f86b3sr3cg185gk1-libICE-1.0.10\r\n /nix/store/hlchvx9kgr7kvkq3al5k1rn19rcdk9lw-librsvg-2.52.5-dev\r\n /nix/store/i0xai02mmy4rp7pilbh4iwa9ya6fqz5m-freetype-2.11.1\r\n /nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev\r\n /nix/store/i4sskmq8fv4p3kjx4a5n08vr95dqwygz-icu4c-70.1\r\n /nix/store/idnhm9np7crxi4vx9ks1sjvv43b91zhp-apple-framework-OpenGL\r\n /nix/store/idqs7p5dkpxir8xdx9c2vqr1gjk2ad6y-libraw-0.20.2-dev\r\n /nix/store/inz1s25yxk3ynn4v4igjif8a22nmw4wk-ilmbase-2.5.7-dev\r\n /nix/store/iqm644dw1gb8rnznw592hyz1mkwkl177-djvulibre-3.5.28\r\n /nix/store/izn7y3ny56gv35dgypzxvj48kvhf9c13-libaom-3.2.0\r\n /nix/store/j51r65k0nl3k09qd63ln9l5i5xfxi5q2-libX11-1.7.2-dev\r\n /nix/store/j57yvkdf7dq1ydy8m6qa3hhw30f5m4v0-libjpeg-turbo-2.1.2-bin\r\n /nix/store/jkri7pa119n0yrrhdpnig234kvjghaxv-liblqr-1-0.4.2\r\n /nix/store/jlz5n5hi2m5ws4biyvcdpdmvnw4m9ybh-libtiff-4.3.0\r\n /nix/store/jwppzw4kggcpx74hm7iwcg7pxgh0qzcr-apple-framework-NetFS\r\n /nix/store/k69qr6dr8hm6q1ma8f7fp5g2i9f9ipjc-pkg-config-wrapper-0.29.2\r\n /nix/store/khsaw63fi8r1dfk08s7blvcd6cqd5kkq-libSM-1.2.3\r\n /nix/store/kwzpagh7d5r2drdr9c5i179yqwcl7k5s-apple-framework-UIFoundation\r\n /nix/store/l2h3wwkb80pw3y0yc2pj9bqy5py95my1-libdeflate-1.8\r\n /nix/store/l9pjb4fxqad2mzn884xjxal6nnc69rhf-apple-framework-SystemConfiguration\r\n /nix/store/ldkfy424bzhwgny18mbr5xxvcyq6abxp-apple-framework-CoreWLAN\r\n /nix/store/lhz18lm3avhxa6n57bb97w4kp8nvaihx-qtbase-5.12.10\r\n /nix/store/lknpi15zbzbaq2m9djavykpm5s9nfca4-libkrb5-1.19.2\r\n /nix/store/lp2gac5k7qqwglrz5zhws2acy8gfpf37-libxslt-1.1.34-dev\r\n /nix/store/lsx58y1q64d9n4mvcsl2384sizh7kk93-apple-lib-xpc\r\n /nix/store/m7rv5n1yygnbgpq7bda7x810dnrk71vc-apple-framework-CoreImage\r\n /nix/store/n06c1s4b3qjn3fd3r7lxj54rnqy4d5bd-libjpeg-turbo-2.1.2\r\n /nix/store/n1ssm5qi8gdd227yxk4b3i8dv16kpi66-apple-framework-CoreMIDI\r\n /nix/store/n3pqa2mkmakh8q4z5rfhdzjjvc35qsxn-hook\r\n /nix/store/nayi7s71fj5bm35bjwh00ky29ybw0x73-fribidi-1.0.11\r\n /nix/store/nbpan0si7jqjbcgc80qcdz6w8dsm21ci-libxslt-1.1.34\r\n /nix/store/nkz4inrfv4gmm9dmigkb1868z3p9341g-apple-framework-ImageIO\r\n /nix/store/nqg3mgls2m6jxdwrvlnb0843ibmakmqn-harfbuzz-3.2.0\r\n /nix/store/nyckxqk2lnvjq8vz1i0np0s77ccff8gr-imagemagick-7.1.0-24\r\n /nix/store/p444xy948z2yvmkcjcd8zj263ivhqrrq-apple-framework-CoreGraphics\r\n /nix/store/p5dgbd3gg6c35xxa13538869mrkl02ll-xz-5.2.5-dev\r\n /nix/store/p7fyq8a8756xr92l42mqh3zb35swjdwb-hook\r\n /nix/store/pfzzbvs4pda04zbyvc41d33vdn6p069n-giflib-5.2.1\r\n /nix/store/plj93k130n0cy5gkrvs8gjn7apk9ikda-libraw-0.20.2-lib\r\n /nix/store/pr4qza8h5n03z938yc7yk9b4vj2ic48a-glib-2.70.2-dev\r\n /nix/store/pwahz3snblnhzdhcd93f5jnhkgz03adi-zlib-1.2.11-dev\r\n /nix/store/q3wv6175vqga8d7zpv6qgb64h032snbp-mariadb-connector-c-3.2.5\r\n /nix/store/q6xg7gfhsa3xkz7qgxihc04s552syh1n-djvulibre-3.5.28-bin\r\n /nix/store/q77n53fjsvjd5s5gg6cyhlki6a4ngq61-apple-framework-CoreVideo\r\n /nix/store/qd92j00gp2hb7n2fkzhcfbcanb00v5r5-potrace-1.16\r\n /nix/store/r48ysjs4xbd8g8kpac23lmrb7lm34zxh-apple-framework-Accelerate\r\n /nix/store/r814xzjqrghsv36khlg8zh4ygvmccm85-apple-framework-IOBluetooth\r\n /nix/store/rc6gn05m13b73w4srqcavaapd1i49aik-lndir-1.0.3\r\n /nix/store/rj41fyyvrzcbcf5cc8dyri6zpcalfwrn-imagemagick-7.1.0-24-doc\r\n /nix/store/rpc75vlgb05qwnzv0q54m56rj7jndzlq-openjpeg-2.4.0-dev\r\n /nix/store/rr1lrpr3dmmfjh1k5sgdsyb74g2b2rgm-nghttp2-1.43.0-lib\r\n /nix/store/ry8s7q6wk2cc9wmszrwi9q0nwd6cvmm4-libxml2-2.9.12-dev\r\n /nix/store/s3003m05bghhg4n75rklwvh1v95hc7qd-lcms2-2.12-dev\r\n /nix/store/sbycpngk4brgsxz6njkzjzwk60p2clk6-json-c-0.15\r\n /nix/store/sp6cg4avj0aw9wqb4igzpc5aha4iwxmc-hook\r\n /nix/store/sz3mdybr60zajib5xy1gw9x5hn64g767-libheif-1.12.0\r\n /nix/store/v12j89i8bynx7djgpm7h1hpvkg2zn74h-libxml2-2.9.12-bin\r\n /nix/store/v1nhay56jmmfr39k9iy1vwksacqshgar-graphite2-1.3.14\r\n /nix/store/v33nm6yj2yxkiylm3f3zvbkwfmzivvd3-apple-framework-CoreServices\r\n /nix/store/v3kjs248xzn21v2k8y0smlcl9iwvg82x-ilmbase-2.5.7\r\n /nix/store/vg4h9ywvq25k3m6c8pvrmgbk5aslmqbj-apple-framework-AGL\r\n /nix/store/vlmpfgfb4bhh62ismjwhy19xsmg0fd36-harfbuzz-3.2.0\r\n /nix/store/vpqsnyh4y0a0fmd8idrgs9d6spmyxam8-libde265-1.0.8\r\n /nix/store/vwvslyr0m538sycp387x95k1znrbbng2-apple-framework-CoreAudio\r\n /nix/store/w3j9s0jq2mp63sjh13b5mdzkxvyx597d-libX11-1.7.2\r\n /nix/store/wgxh6kc7yw56bgmdz0bi1fl8dcx9r7hn-glib-2.70.2\r\n /nix/store/x8b6i8zsf0wmf7s6j6sifirmmfd4gwrv-bzip2-1.0.6.0.2-dev\r\n /nix/store/x9cy2c7rq2ki2knhapj4zpyiyakksi8b-apple-framework-CFNetwork\r\n /nix/store/xc24nx2gczc652mn3gr7l5y4jp2881kg-libdatrie-2019-12-20-lib\r\n /nix/store/xfnr92m9b9zs8sg1cbl6gv7ig8wsw8rm-apple-framework-MetalKit\r\n /nix/store/xykmnwqdsw6i2pdgvdwmvj93yirkx60n-libwebp-1.2.1\r\n /nix/store/y86m126l3v1v5mi0b7qrv1yiqcz27ipi-libtiff-4.3.0-bin\r\n /nix/store/y8a7av55qlxm5s2d3h538pxy728dcn9l-dejavu-fonts-minimal-2.37\r\n /nix/store/ya3iah3x4m3flxgnpzzziqvls2id768w-fontconfig-2.13.94-bin\r\n /nix/store/ys9n21ak21fsrnwzgwg99cjzqgfdd502-libjpeg-turbo-2.1.2-dev\r\n /nix/store/z1kgfvxqp2jn2hw0f99hf84ma6frb2rd-cups-2.2.6-lib\r\n /nix/store/zcfdcwlbmm4hc6192lh685872n6vwrzl-libXext-1.3.4-dev\r\n /nix/store/zkpnkwqiia9gisk9xwxfxgmppi6isr8d-openssl-1.1.1m-bin\r\ncopying path '/nix/store/08jyx957r4flyw7qb3pw7wwcysqgrx1j-yubikey-personalization-gui-3.1.25.tar.gz' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/x9cy2c7rq2ki2knhapj4zpyiyakksi8b-apple-framework-CFNetwork' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/g6fdlmvbm83jqf3n3a3v561bi5xx51ap-apple-framework-CoreBluetooth' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2gfy9d9k13i2wkfin1p1cajn09z21975-apple-framework-CoreData' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2xlw9hdlyj5rzwz14qjxfp742b4q4jbw-apple-framework-CoreFoundation' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/m7rv5n1yygnbgpq7bda7x810dnrk71vc-apple-framework-CoreImage' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/3l32af8vap5qk3qhgnpdgib5r900ayf9-apple-framework-CoreLocation' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/n1ssm5qi8gdd227yxk4b3i8dv16kpi66-apple-framework-CoreMIDI' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/0fs1pcz04zirhb7prg99ifasnjw37cwr-apple-framework-IOKit' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4l7wrqah2xi0z83r7n52fm8fk57g1j50-apple-framework-Metal' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vwvslyr0m538sycp387x95k1znrbbng2-apple-framework-CoreAudio' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/911bjzmg1wvj87js00z7pnl0riggxgxw-apple-framework-DiskArbitration' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/464iky47m47zxpxf0z4m6h9sbgzs55jb-apple-framework-AudioToolbox' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/r814xzjqrghsv36khlg8zh4ygvmccm85-apple-framework-IOBluetooth' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/3yvavihg1maakvh2v02qrp5nx1f7ff97-apple-framework-ModelIO' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/jwppzw4kggcpx74hm7iwcg7pxgh0qzcr-apple-framework-NetFS' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/xfnr92m9b9zs8sg1cbl6gv7ig8wsw8rm-apple-framework-MetalKit' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/bx0m19wwdd1gcwb4f2cx8z8ii0c8chdn-apple-framework-OpenDirectory' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/idnhm9np7crxi4vx9ks1sjvv43b91zhp-apple-framework-OpenGL' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/23fbs10yf2k0fpa80x1c0hwhx1ayzfq4-apple-framework-Security' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/f97varjrmvjphyzvfzfl7lx7dbas35qn-apple-framework-SecurityFoundation' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/6kb21xvnbhda9qq59ar1max2d004pfhk-apple-framework-ServiceManagement' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/ldkfy424bzhwgny18mbr5xxvcyq6abxp-apple-framework-CoreWLAN' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/v33nm6yj2yxkiylm3f3zvbkwfmzivvd3-apple-framework-CoreServices' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/r48ysjs4xbd8g8kpac23lmrb7lm34zxh-apple-framework-Accelerate' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/l9pjb4fxqad2mzn884xjxal6nnc69rhf-apple-framework-SystemConfiguration' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/kwzpagh7d5r2drdr9c5i179yqwcl7k5s-apple-framework-UIFoundation' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/lsx58y1q64d9n4mvcsl2384sizh7kk93-apple-lib-xpc' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/18jrr7jjs9jf67yqrf5cvskzb5c6r1si-brotli-1.0.9-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/13ww2fx4bgy5l14xcw1sca031rxr3k45-apple-framework-IOSurface' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/x8b6i8zsf0wmf7s6j6sifirmmfd4gwrv-bzip2-1.0.6.0.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/p444xy948z2yvmkcjcd8zj263ivhqrrq-apple-framework-CoreGraphics' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/0saadbzrwvx281s9pdzxxbpgjlc5mq9b-apple-framework-OpenCL' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/02qcpb7w7dpnn30mjxg8vcyi0zjj2b1f-apple-framework-CoreText' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/nkz4inrfv4gmm9dmigkb1868z3p9341g-apple-framework-ImageIO' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/z1kgfvxqp2jn2hw0f99hf84ma6frb2rd-cups-2.2.6-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/6nzywbp2rg7hb3c6rmmcdvy31l9sciv4-apple-framework-ApplicationServices' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7bfplbll52571lw2gny8268wgmmb9km0-dav1d-0.9.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/q77n53fjsvjd5s5gg6cyhlki6a4ngq61-apple-framework-CoreVideo' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/y8a7av55qlxm5s2d3h538pxy728dcn9l-dejavu-fonts-minimal-2.37' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/cyssq6cvdxl8vxljmm6xh9kxpjlb27kw-expat-2.4.4-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/6nxp44v8vblmpkdjmw0h06p9dq8pkgr2-fontconfig-2.13.94' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/nayi7s71fj5bm35bjwh00ky29ybw0x73-fribidi-1.0.11' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2c2nhznpv9a1yyda6wd33lf78b4q3b62-gettext-0.21' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/pfzzbvs4pda04zbyvc41d33vdn6p069n-giflib-5.2.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/wgxh6kc7yw56bgmdz0bi1fl8dcx9r7hn-glib-2.70.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/v1nhay56jmmfr39k9iy1vwksacqshgar-graphite2-1.3.14' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gm9h8mha6arb0am62rylbxq4lg8292s7-glib-2.70.2-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/9sirmb84azjl1x6imlssr4nl1vrna32h-hook' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/n3pqa2mkmakh8q4z5rfhdzjjvc35qsxn-hook' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/i4sskmq8fv4p3kjx4a5n08vr95dqwygz-icu4c-70.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/sp6cg4avj0aw9wqb4igzpc5aha4iwxmc-hook' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/5wwpnv10s56z3wadb7vc7yvwn727mshm-icu4c-70.1-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/v3kjs248xzn21v2k8y0smlcl9iwvg82x-ilmbase-2.5.7' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/rj41fyyvrzcbcf5cc8dyri6zpcalfwrn-imagemagick-7.1.0-24-doc' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/inz1s25yxk3ynn4v4igjif8a22nmw4wk-ilmbase-2.5.7-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/sbycpngk4brgsxz6njkzjzwk60p2clk6-json-c-0.15' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gswnlnq58llz9br77z03caaphmilar3w-lcms2-2.12' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gvwk0137cgvwanv8f86b3sr3cg185gk1-libICE-1.0.10' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7p9hphzk2h89wbb1fblgx242pvk3d6ac-libXau-1.0.9' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/5hphscbk7qgqipd5072b2c92zd45hmcc-libICE-1.0.10-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/khsaw63fi8r1dfk08s7blvcd6cqd5kkq-libSM-1.2.3' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/dl15nx5ijygmj58rdmsjm5c6gl0p7kwl-libXdmcp-1.1.3' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/ckfmi0dcz15qrsj2nfwh6ijwchzkk21m-libSM-1.2.3-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/izn7y3ny56gv35dgypzxvj48kvhf9c13-libaom-3.2.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/xc24nx2gczc652mn3gr7l5y4jp2881kg-libdatrie-2019-12-20-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vpqsnyh4y0a0fmd8idrgs9d6spmyxam8-libde265-1.0.8' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/l2h3wwkb80pw3y0yc2pj9bqy5py95my1-libdeflate-1.8' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2k7q0xz5vfws29v8s6drw47raf4qg388-libffi-3.4.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/n06c1s4b3qjn3fd3r7lxj54rnqy4d5bd-libjpeg-turbo-2.1.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/lknpi15zbzbaq2m9djavykpm5s9nfca4-libkrb5-1.19.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/iqm644dw1gb8rnznw592hyz1mkwkl177-djvulibre-3.5.28' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/j57yvkdf7dq1ydy8m6qa3hhw30f5m4v0-libjpeg-turbo-2.1.2-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/fi25y5nwacqfj61dd0q33sr1jd29370g-libpng-apng-1.6.37' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/ys9n21ak21fsrnwzgwg99cjzqgfdd502-libjpeg-turbo-2.1.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/i0xai02mmy4rp7pilbh4iwa9ya6fqz5m-freetype-2.11.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/plj93k130n0cy5gkrvs8gjn7apk9ikda-libraw-0.20.2-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/fml90csmdl6q40pw913178lnx9af9rk0-fontconfig-2.13.94-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/nqg3mgls2m6jxdwrvlnb0843ibmakmqn-harfbuzz-3.2.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/ya3iah3x4m3flxgnpzzziqvls2id768w-fontconfig-2.13.94-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vlmpfgfb4bhh62ismjwhy19xsmg0fd36-harfbuzz-3.2.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/5w6gxpa4qdfm51cayzby50yh9cl8wl1a-harfbuzz-3.2.0-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4j9lzd1iqgfxmhn08kr6q011l56l904l-libraw-0.20.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/32b9ksisxwp3msrgjz2frmbzhcc2w1mp-libssh2-1.10.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/0j9y9qmc7m01bcaq2vw3griakmr2wqx0-libthai-0.1.29' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/jlz5n5hi2m5ws4biyvcdpdmvnw4m9ybh-libtiff-4.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2m0zdcng89bl3glpzcw7vflxq4ymvg5n-libunistring-0.9.10' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/q6xg7gfhsa3xkz7qgxihc04s552syh1n-djvulibre-3.5.28-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gdsh20cvk495ammlspzra426zxpm18gv-gdk-pixbuf-2.42.6' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7kvf2w7gc513p44lhf24afwqb36dhddi-djvulibre-3.5.28-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/cm2xdmh4v1c70f4i0gks0mfn5ymfnhdh-lcms2-2.12-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/06c43d6nx5rizspjycgfd44rgnh236hn-libidn2-2.3.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/y86m126l3v1v5mi0b7qrv1yiqcz27ipi-libtiff-4.3.0-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7rri7ys1r12hgqlppgw5vy25dk43mhcw-libusb-1.0.24' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/xykmnwqdsw6i2pdgvdwmvj93yirkx60n-libwebp-1.2.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/177rdkdf356m468dfyp8qyvgdlg7aj1j-libxcb-1.14' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/5g7kmwj88sqrn3lmad2jy3xp8wlwffqv-libxml2-2.9.12' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/w3j9s0jq2mp63sjh13b5mdzkxvyx597d-libX11-1.7.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/3drcp8a9asx5yrb1h2k69mw8d2l7vx48-libxcb-1.14-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/94d4y1i7gxxpa595wizragkx42p2lbgb-dbus-1.12.20-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/aa4mvxgy8m5pa4sxz42hh1gna0fihn5q-libXext-1.3.4' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/9g16rn376r882f6zffc5a0n2xf0cn2g0-dbus-1.12.20' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1h6b9n7iidjp8s32n9hj1vkansyvg686-libXt-1.2.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/d4zljaq6fv9wrqyvchxxswwvqj69np73-dbus-1.12.20-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/v12j89i8bynx7djgpm7h1hpvkg2zn74h-libxml2-2.9.12-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/nbpan0si7jqjbcgc80qcdz6w8dsm21ci-libxslt-1.1.34' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/957nfnl29rikn6nq7mmjargf37i0if2d-libyubikey-1.13' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/0mdsnsdq7077hp5krhciackxm95h8yzs-libxslt-1.1.34-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/rc6gn05m13b73w4srqcavaapd1i49aik-lndir-1.0.3' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/rr1lrpr3dmmfjh1k5sgdsyb74g2b2rgm-nghttp2-1.43.0-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4pby6a6ddnyb0f6ry03cmmfh0cf2wcga-objc4-709.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/87szb2sqa13py3sbfv0p187qa1867sla-openexr-2.5.7' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/9hpjsy91av3lx0pfbqsd7qcsnl5yhrjh-apple-framework-Foundation' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/062b4xczsd43ybd2a2l6hpzna4fbmrxa-apple-framework-QuartzCore' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/8h6ns6g3c2cd0ljwyjjwzrcxbhh9hbq3-libjxl-0.6.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/49mysix44qjlpr7xh2aj1dzjciqch9na-apple-framework-Carbon' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/73f251a281xcz9kqbssskivamxchirpj-openexr-2.5.7-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vg4h9ywvq25k3m6c8pvrmgbk5aslmqbj-apple-framework-AGL' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/752m4pxw3rcv498h124l6hh59s523wfy-apple-framework-AudioUnit' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/clv6a60f5fiahmznp8ipggh8nfnaards-openjpeg-2.4.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/9350cblagkxjwb86nbh1whb4f8zw8504-apple-framework-AppKit' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/90vkbqaxld49vx42kgn4dln63fmbkyag-pcre2-10.39-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/75kkmw2qr86m4ji9gbdxjjzm27j1spmm-apple-framework-Cocoa' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/303nv3mpwmm9lr97iy6fw2dv7gn11cv5-pcre2-10.39-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1jqa5w6ah7ihbvmi7wv9zxw5n2bchsrp-perl-5.34.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/a6pw2mpw1bi7qmkvrrqpzr40l1gkgqbq-pixman-0.38.4' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/zkpnkwqiia9gisk9xwxfxgmppi6isr8d-openssl-1.1.1m-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/cfrfg80g0wx9wx7q11v04awllfkxbzqd-cairo-1.16.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/dh9gss9pid7vx3qm5ya0p9qx267d86f9-openssl-1.1.1m-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/03shvkqxyfwb6rm953acq7g0mnkkacwq-pango-1.50.3' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/6w03y9qaxhg75w0313n1gl382i6jsnwf-pkg-config-0.29.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/48jp1fcffb29p91mr5la3saa64py1ikh-librsvg-2.52.5' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/k69qr6dr8hm6q1ma8f7fp5g2i9f9ipjc-pkg-config-wrapper-0.29.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/75g0v4c3rxz4clwsp80f514qdyq34gf9-postgresql-13.5-lib' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/qd92j00gp2hb7n2fkzhcfbcanb00v5r5-potrace-1.16' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/lhz18lm3avhxa6n57bb97w4kp8nvaihx-qtbase-5.12.10' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1sq4ld172h08nk3yqk67qyj0nz122pg5-rav1e-0.5.1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/68grnmf14wd8r60zz7iz0d53x7v7c97p-sqlite-3.37.2-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4klbdaavwqcgk2hp48l5rfrc42g6a032-x265-3.5' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/cdf2bdayqk99cd3cy4980dk8dgng7hr7-sqlite-3.37.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/sz3mdybr60zajib5xy1gw9x5hn64g767-libheif-1.12.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/aj75grihmc2j5ybvc6qh7pmjjn2ympwc-xorgproto-2021.5' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/g08vxrq5hzgj3284zzjdfm14ifia0zn5-libheif-1.12.0-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/j51r65k0nl3k09qd63ln9l5i5xfxi5q2-libX11-1.7.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/53y4djna9lg4rghph9n4x5y7biqwlwb9-libXau-1.0.9-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1k7as0cvf83w1my8y2197lgbq88yfysf-libXt-1.2.1-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/zcfdcwlbmm4hc6192lh685872n6vwrzl-libXext-1.3.4-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/95wmga03ljf26mycw2dfc9jqcw1j82hr-libheif-1.12.0-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/p5dgbd3gg6c35xxa13538869mrkl02ll-xz-5.2.5-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7px6ripq5yqrgs6ca00ynbxykm5bqbdj-yubikey-personalization-1.20.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/pwahz3snblnhzdhcd93f5jnhkgz03adi-zlib-1.2.11-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/8v6js2md35iacyvfh26fhfz7aba0z0i5-zstd-1.5.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/pr4qza8h5n03z938yc7yk9b4vj2ic48a-glib-2.70.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/0y0lm54vscg18jbfic95wyrfv47f5gmd-curl-7.81.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/jkri7pa119n0yrrhdpnig234kvjghaxv-liblqr-1-0.4.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/7y60bl2ysx5gidfhpc0bl4i67dcrha09-libpng-apng-1.6.37-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/nyckxqk2lnvjq8vz1i0np0s77ccff8gr-imagemagick-7.1.0-24' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/5rjp3azxhk7y68mcwd6i4drqd33kk3aw-freetype-2.11.1-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/a9kv1vg7inkrc2airvp58llbw44c79b0-libtiff-4.3.0-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4y9xjw7hhjd5wvdb2fimn3jqm060bnhw-fontconfig-2.13.94-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1pl0rk5zanqbd39llccs6a2ajj85y8ir-gdk-pixbuf-2.42.6-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/bbdb06wdfdymx2k5wybjsfj2c0r8hkis-cairo-1.16.0-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/s3003m05bghhg4n75rklwvh1v95hc7qd-lcms2-2.12-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/hlchvx9kgr7kvkq3al5k1rn19rcdk9lw-librsvg-2.52.5-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/idqs7p5dkpxir8xdx9c2vqr1gjk2ad6y-libraw-0.20.2-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/ry8s7q6wk2cc9wmszrwi9q0nwd6cvmm4-libxml2-2.9.12-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/q3wv6175vqga8d7zpv6qgb64h032snbp-mariadb-connector-c-3.2.5' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/lp2gac5k7qqwglrz5zhws2acy8gfpf37-libxslt-1.1.34-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2ilayry6mc94lnwdz10yrijh5a69s132-openexr-2.5.7-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/rpc75vlgb05qwnzv0q54m56rj7jndzlq-openjpeg-2.4.0-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/4f0xfvx09grhz4g3zwd9dy2gyz3dmqh6-qtbase-5.12.10-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/awbr2wzpf4xf11n1fhmmhnhvmmzz97h3-imagemagick-7.1.0-24-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/g2kslbpn3pzxq7gvwraz9s470slizh9v-hook' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/p7fyq8a8756xr92l42mqh3zb35swjdwb-hook' from 'https://cache.nixos.org'...\r\nbuilding '/nix/store/8kx880h6kd2lnllmkrc8h7vd74pah9s4-yubikey-personalization-gui-3.1.25.drv'...\r\nqmakePrePhase\r\nqtPreHook\r\nunpacking sources\r\nunpacking source archive /nix/store/08jyx957r4flyw7qb3pw7wwcysqgrx1j-yubikey-personalization-gui-3.1.25.tar.gz\r\nsource root is yubikey-personalization-gui-3.1.25\r\nsetting SOURCE_DATE_EPOCH to timestamp 1516105001 of file yubikey-personalization-gui-3.1.25/ChangeLog\r\npatching sources\r\nconfiguring\r\nQMAKEPATH=/nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev\r\nqmake PREFIX=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_OUT=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DEV=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_BIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DOC=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/share/doc/qt-5.12.10 NIX_OUTPUT_QML=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/qml NIX_OUTPUT_PLUGIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/plugins CONFIG+=release\r\nInfo: creating stash file /private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/.qmake.stash\r\n/nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev/mkspecs/features/mac/default_post.prf:5: 'xcodeSDKInfo' is not a recognized replace function.\r\nqmake: enabled parallel building\r\nbuilding\r\nbuild flags: -j12 -l12 SHELL=/nix/store/vssrny41k0mr33jclrrn67rxhbdpwrr0-bash-5.1-p12/bin/bash\r\ncd lib/ && ( test -e Makefile || /nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev/bin/qmake -o Makefile /private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/lib/lib.pro PREFIX=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_OUT=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DEV=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_BIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DOC=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/share/doc/qt-5.12.10 NIX_OUTPUT_QML=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/qml NIX_OUTPUT_PLUGIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/plugins CONFIG+=release ) && make -f Makefile \r\nProject MESSAGE: Release build\r\n/nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev/mkspecs/features/mac/default_post.prf:5: 'xcodeSDKInfo' is not a recognized replace function.\r\nmake[1]: Entering directory '/private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/lib'\r\ncompiling scanedit.cpp\r\ncompiling us-scanedit.cpp\r\ncompiling de-scanedit.cpp\r\ncompiling bepo-scanedit.cpp\r\ncompiling fr-scanedit.cpp\r\ncompiling yubikeyutil.cpp\r\nrm -f release/liblib.a\r\nar cq release/liblib.a scanedit.o us-scanedit.o de-scanedit.o bepo-scanedit.o fr-scanedit.o yubikeyutil.o\r\nranlib -s release/liblib.a\r\nmake[1]: Leaving directory '/private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/lib'\r\ncd src/ && ( test -e Makefile || /nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev/bin/qmake -o Makefile /private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/src/src.pro PREFIX=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_OUT=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DEV=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_BIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25 NIX_OUTPUT_DOC=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/share/doc/qt-5.12.10 NIX_OUTPUT_QML=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/qml NIX_OUTPUT_PLUGIN=/nix/store/gvz2hhxvh5c2s0yg3blpcabimhz0f8ka-yubikey-personalization-gui-3.1.25/lib/qt-5.12.10/plugins CONFIG+=release ) && make -f Makefile \r\nProject MESSAGE: Release build\r\nProject MESSAGE: Mac build\r\n/nix/store/i4kaf244dpjd9njyssr3yhm1fjsp44i2-qtbase-5.12.10-dev/mkspecs/features/mac/default_post.prf:5: 'xcodeSDKInfo' is not a recognized replace function.\r\nProject WARNING: Qt requires at least version 10.13 of the platform SDK, you're building against version . Please upgrade.\r\nmake[1]: Entering directory '/private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/src'\r\nuic ui/toolpage.ui\r\nuic ui/staticpage.ui\r\nuic ui/settingpage.ui\r\nuic ui/otppage.ui\r\nuic ui/oathpage.ui\r\nuic ui/mainwindow.ui\r\nuic ui/helpbox.ui\r\nuic ui/confirmbox.ui\r\nuic ui/chalresppage.ui\r\nuic ui/aboutpage.ui\r\nuic ui/diagnostics.ui\r\nuic ui/yubiaccbox.ui\r\ncompiling main.cpp\r\ncompiling ui/toolpage.cpp\r\ncompiling ui/staticpage.cpp\r\ncompiling ui/settingpage.cpp\r\ncompiling ui/otppage.cpp\r\ncompiling ui/mainwindow.cpp\r\ncompiling ui/helpbox.cpp\r\ncompiling ui/confirmbox.cpp\r\ncompiling ui/chalresppage.cpp\r\ncompiling ui/aboutpage.cpp\r\ncompiling ui/diagnostics.cpp\r\ncompiling yubikeywriter.cpp\r\nIn file included from yubikeywriter.cpp:29:\r\n./yubikeywriter.h:35:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/settingpage.cpp:30:\r\n./yubikeyfinder.h:36:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/otppage.cpp:30:\r\n./yubikeywriter.h:35:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/staticpage.cpp:30:\r\n./yubikeyfinder.h:36:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/aboutpage.cpp:32:\r\n./yubikeyfinder.h:36:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/toolpage.cpp:30:\r\n./yubikeyfinder.h:36:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nIn file included from ui/mainwindow.cpp:31:\r\n./yubikeyfinder.h:36:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\n1 error generated.\r\nmake[1]: *** [Makefile:842: ../build/release/ObjFiles/aboutpage.o] Error 1\r\nmake[1]: *** Waiting for unfinished jobs....\r\nIn file included from ui/diagnostics.cpp:32:\r\n./yubikeywriter.h:35:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\n1 error generated.\r\nmake[1]: *** [Makefile:864: ../build/release/ObjFiles/diagnostics.o] Error 1\r\n1 error generated.\r\nmake[1]: *** [Makefile:873: ../build/release/ObjFiles/yubikeywriter.o] Error 1\r\n1 error generated.\r\n1 error generated.\r\nmake[1]: *** [Makefile:760: ../build/release/ObjFiles/settingpage.o] Error 1\r\nmake[1]: *** [Makefile:806: ../build/release/ObjFiles/mainwindow.o] Error 1\r\n1 error generated.\r\nIn file included from ui/chalresppage.cpp:33:\r\n./yubikeywriter.h:35:10: fatal error: 'ykpers.h' file not found\r\n#include <ykpers.h>\r\n ^~~~~~~~~~\r\nmake[1]: *** [Makefile:730: ../build/release/ObjFiles/toolpage.o] Error 1\r\n1 error generated.\r\n1 error generated.\r\nmake[1]: *** [Makefile:772: ../build/release/ObjFiles/otppage.o] Error 1\r\nmake[1]: *** [Makefile:747: ../build/release/ObjFiles/staticpage.o] Error 1\r\n1 error generated.\r\nmake[1]: *** [Makefile:833: ../build/release/ObjFiles/chalresppage.o] Error 1\r\nmake[1]: Leaving directory '/private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/src'\r\nmake: *** [Makefile:95: sub-src-make_first-ordered] Error 2\r\nerror: builder for '/nix/store/8kx880h6kd2lnllmkrc8h7vd74pah9s4-yubikey-personalization-gui-3.1.25.drv' failed with exit code 2;\r\n last 10 log lines:\r\n > ^~~~~~~~~~\r\n > make[1]: *** [Makefile:730: ../build/release/ObjFiles/toolpage.o] Error 1\r\n > 1 error generated.\r\n > 1 error generated.\r\n > make[1]: *** [Makefile:772: ../build/release/ObjFiles/otppage.o] Error 1\r\n > make[1]: *** [Makefile:747: ../build/release/ObjFiles/staticpage.o] Error 1\r\n > 1 error generated.\r\n > make[1]: *** [Makefile:833: ../build/release/ObjFiles/chalresppage.o] Error 1\r\n > make[1]: Leaving directory '/private/tmp/nix-build-yubikey-personalization-gui-3.1.25.drv-0/yubikey-personalization-gui-3.1.25/src'\r\n > make: *** [Makefile:95: sub-src-make_first-ordered] Error 2\r\n For full logs, run 'nix log /nix/store/8kx880h6kd2lnllmkrc8h7vd74pah9s4-yubikey-personalization-gui-3.1.25.drv'.\r\nsloth% \r\n\r\n```\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nsloth% nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160625/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160599","id":1142830814,"node_id":"I_kwDOAEVQ_M5EHjbe","number":160599,"title":"KMail Renders Blank Messages","user":{"login":"Obikawa","id":3336306,"node_id":"MDQ6VXNlcjMzMzYzMDY=","avatar_url":"https://avatars.githubusercontent.com/u/3336306?v=4","gravatar_id":"","url":"https://api.github.com/users/Obikawa","html_url":"https://github.com/Obikawa","followers_url":"https://api.github.com/users/Obikawa/followers","following_url":"https://api.github.com/users/Obikawa/following{/other_user}","gists_url":"https://api.github.com/users/Obikawa/gists{/gist_id}","starred_url":"https://api.github.com/users/Obikawa/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Obikawa/subscriptions","organizations_url":"https://api.github.com/users/Obikawa/orgs","repos_url":"https://api.github.com/users/Obikawa/repos","events_url":"https://api.github.com/users/Obikawa/events{/privacy}","received_events_url":"https://api.github.com/users/Obikawa/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-18T10:51:35Z","updated_at":"2022-02-18T10:51:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Description\r\n\r\nThe title says it all. Here is the corresponding upstream bug report: [ KDE Bug Tracker ]( https://bugs.kde.org/show_bug.cgi?id=446104).\r\n\r\nThe workaround of `QT_WEBENGINE_DISABLE_WAYLAND_WORKAROUND=1` solves the problem.\r\n\r\n### Maintainers\r\n\r\n@ttuegel @vandenoever @nyanloutre","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160599/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160516","id":1142017248,"node_id":"I_kwDOAEVQ_M5EEczg","number":160516,"title":"mariadb fails to start with kernel 5.16.8 and btrfs","user":{"login":"hax404","id":1379411,"node_id":"MDQ6VXNlcjEzNzk0MTE=","avatar_url":"https://avatars.githubusercontent.com/u/1379411?v=4","gravatar_id":"","url":"https://api.github.com/users/hax404","html_url":"https://github.com/hax404","followers_url":"https://api.github.com/users/hax404/followers","following_url":"https://api.github.com/users/hax404/following{/other_user}","gists_url":"https://api.github.com/users/hax404/gists{/gist_id}","starred_url":"https://api.github.com/users/hax404/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hax404/subscriptions","organizations_url":"https://api.github.com/users/hax404/orgs","repos_url":"https://api.github.com/users/hax404/repos","events_url":"https://api.github.com/users/hax404/events{/privacy}","received_events_url":"https://api.github.com/users/hax404/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-02-17T22:53:59Z","updated_at":"2022-03-22T23:24:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nOn NixOS 21.11 Mariadb is broken with underlying btrfs and kernel 5.16.8 (`boot.kernelPackages = pkgs.linuxPackages_latest;`).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install new NixOS 21.11 on btrfs and with empty /var/lib/mysql\r\n2. ```\r\n boot.kernelPackages = pkgs.linuxPackages_latest;\r\n services.mysql = {\r\n enable = true;\r\n package = pkgs.mariadb;\r\n };\r\n ```\r\n3. `nixos-rebuild switch`\r\n4. Start of mysql hangs and never comes up.\r\n\r\n### Expected behavior\r\nMariadb starts normal.\r\n\r\n### Screenshots\r\nhttps://gist.github.com/hax404/0b4b285b16f7dcfc99db9eb18e8c7689\r\n\r\n### Known Workarounds\r\n - Don't use linuxPackages_latest, instead use kernel 5.10\r\n - `services.mysql.settings.mysqld.innodb_use_native_aio = \"OFF\";`\r\n\r\n### Additional context\r\nUsing git bisect, I found the commit https://github.com/NixOS/nixpkgs/commit/937cf30e7e7fff70b1ec6d1e8948d21aa8b24854 from PR https://github.com/NixOS/nixpkgs/pull/145117\r\n\r\nProblems with newer kernels than 5.10 are known https://mariadb.com/kb/en/mariadb-1065-release-notes/#innodb\r\n\r\nAlso tested Mariadb 10.6.7 from PR https://github.com/NixOS/nixpkgs/pull/160384\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@thoughtpolice @ajs124 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.8, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336020.2128d0aa28e\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160516/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160481","id":1141531902,"node_id":"I_kwDOAEVQ_M5ECmT-","number":160481,"title":"[Packaging request] cryptsetup-suspend","user":{"login":"onny","id":757752,"node_id":"MDQ6VXNlcjc1Nzc1Mg==","avatar_url":"https://avatars.githubusercontent.com/u/757752?v=4","gravatar_id":"","url":"https://api.github.com/users/onny","html_url":"https://github.com/onny","followers_url":"https://api.github.com/users/onny/followers","following_url":"https://api.github.com/users/onny/following{/other_user}","gists_url":"https://api.github.com/users/onny/gists{/gist_id}","starred_url":"https://api.github.com/users/onny/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/onny/subscriptions","organizations_url":"https://api.github.com/users/onny/orgs","repos_url":"https://api.github.com/users/onny/repos","events_url":"https://api.github.com/users/onny/events{/privacy}","received_events_url":"https://api.github.com/users/onny/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-17T16:00:54Z","updated_at":"2022-02-17T16:00:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n[cryptsetup-suspend](https://blog.freesources.org/posts/2020/08/cryptsetup-suspend/) is a project which enables disc encryption on suspend to ram.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://blog.freesources.org/posts/2020/08/cryptsetup-suspend/\r\n* source URL: https://salsa.debian.org/cryptsetup-team/cryptsetup/-/tree/debian/experimental\r\n* license: gpl2+\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160481/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160468","id":1141340984,"node_id":"I_kwDOAEVQ_M5EB3s4","number":160468,"title":"JetBrains JDK does not support JCEF","user":{"login":"niknetniko","id":1756811,"node_id":"MDQ6VXNlcjE3NTY4MTE=","avatar_url":"https://avatars.githubusercontent.com/u/1756811?v=4","gravatar_id":"","url":"https://api.github.com/users/niknetniko","html_url":"https://github.com/niknetniko","followers_url":"https://api.github.com/users/niknetniko/followers","following_url":"https://api.github.com/users/niknetniko/following{/other_user}","gists_url":"https://api.github.com/users/niknetniko/gists{/gist_id}","starred_url":"https://api.github.com/users/niknetniko/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/niknetniko/subscriptions","organizations_url":"https://api.github.com/users/niknetniko/orgs","repos_url":"https://api.github.com/users/niknetniko/repos","events_url":"https://api.github.com/users/niknetniko/events{/privacy}","received_events_url":"https://api.github.com/users/niknetniko/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-02-17T13:29:48Z","updated_at":"2022-04-19T19:20:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe JetBrains JDK seems to be built without JCEF support.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run something (e.g. Intellij) with the JetBrains JDK\r\n2. Expect JCEF to work.\r\n3. It doesn't.\r\n\r\n### Expected behavior\r\nJCEF should be supported.\r\n\r\n### Additional context\r\nThis is probably the cause of #143122, #109347 and #150579.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@edwtjo @petabyteboy\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(niko): `\"\"`\r\n - channels(root): `\"android, nix-ld, nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468/reactions","total_count":7,"+1":7,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160468/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160455","id":1141224879,"node_id":"I_kwDOAEVQ_M5EBbWv","number":160455,"title":"mysql-workbench: error: pynacl-1.4.0 not supported for interpreter python2.7","user":{"login":"danwdart","id":334257,"node_id":"MDQ6VXNlcjMzNDI1Nw==","avatar_url":"https://avatars.githubusercontent.com/u/334257?v=4","gravatar_id":"","url":"https://api.github.com/users/danwdart","html_url":"https://github.com/danwdart","followers_url":"https://api.github.com/users/danwdart/followers","following_url":"https://api.github.com/users/danwdart/following{/other_user}","gists_url":"https://api.github.com/users/danwdart/gists{/gist_id}","starred_url":"https://api.github.com/users/danwdart/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/danwdart/subscriptions","organizations_url":"https://api.github.com/users/danwdart/orgs","repos_url":"https://api.github.com/users/danwdart/repos","events_url":"https://api.github.com/users/danwdart/events{/privacy}","received_events_url":"https://api.github.com/users/danwdart/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-17T11:36:49Z","updated_at":"2022-03-08T15:52:12Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nError when trying to install/run mysql-workbench:\r\n```\r\nerror: pynacl-1.4.0 not supported for interpreter python2.7\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Either add to system packages or use nix-shell -p mysql-workbench\r\n2. Error shown\r\n\r\n\r\n### Expected behavior\r\nMySQL Workbench installed\r\n\r\n### Notify maintainers\r\nNot sure if @gebner or @r-ryantm or someone else?\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.21-hardened1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.336020.2128d0aa28e, unstable-21.11pre306621.439b1605227, nixpkgs-20.09\"`\r\n - channels(dwd): `\"unstable-21.11pre306621.439b1605227, home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160455/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160437","id":1141014972,"node_id":"I_kwDOAEVQ_M5EAoG8","number":160437,"title":"fcitx5: `fcitx5-with-addons` should wrap other commands","user":{"login":"sagehane","id":74805176,"node_id":"MDQ6VXNlcjc0ODA1MTc2","avatar_url":"https://avatars.githubusercontent.com/u/74805176?v=4","gravatar_id":"","url":"https://api.github.com/users/sagehane","html_url":"https://github.com/sagehane","followers_url":"https://api.github.com/users/sagehane/followers","following_url":"https://api.github.com/users/sagehane/following{/other_user}","gists_url":"https://api.github.com/users/sagehane/gists{/gist_id}","starred_url":"https://api.github.com/users/sagehane/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sagehane/subscriptions","organizations_url":"https://api.github.com/users/sagehane/orgs","repos_url":"https://api.github.com/users/sagehane/repos","events_url":"https://api.github.com/users/sagehane/events{/privacy}","received_events_url":"https://api.github.com/users/sagehane/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-02-17T08:23:52Z","updated_at":"2022-02-17T10:13:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Update:\r\n---\r\n\r\nI realized that my understanding of the \"bug\" initially described on this issue was wrong.\r\n\r\nThe issue I have is that `fcitx5-with-addons` only wraps around `fcitx5`, so other commands would be oblivious to addons on the system. See https://github.com/NixOS/nixpkgs/issues/160437#issuecomment-1042755001\r\n\r\nAn example of when this can be problematic:\r\n1. Configure Fcitx to use an IME provided by an addon, like Mozc\r\n2. Start Fcitx with `fcitx5-remote` or `fcitx5-configtool`\r\n3. Mozc won't be recognized as a valid input method, and will be deleted from your config\r\n\r\nAlso, you just won't be able to use Mozc in this scenario until you kill the Fcitx process and start it again \"properly\".\r\n\r\nOld stuff:\r\n---\r\n\r\n### Describe the bug\r\n`fcitx5`'s Addon Config Dir seems to default to `/nix/store/<fcitx5>/share/fcitx/addon` instead of `/nix/store/<fcitx5-with-addons>/share/fcitx5/addon/`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nInstall `fcitx5` by setting `i18n.inputMethod.enabled = \"fcitx5\"`\r\n\r\nThis can be confirmed by the outputs of `fcitx5-diagnose`:\r\n```\r\n$ fcitx-diagnose\r\n<omitted>\r\n# Configuration:\r\n## Fcitx Addons:\r\n1. Addon Config Dir:\r\n\r\n Found fcitx5 addon config directory: `/nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon`.\r\n<omitted>\r\n```\r\n\r\n### Expected behavior\r\nIt should instead default to `/nix/store/<fcitx5-with-addons>/share/fcitx5/addon/`, as it would break optional plugins like `fcitx5-mozc`.\r\n\r\n### Additional context\r\nContent of `fcitx5`:\r\n```sh-session\r\n$ ls -lA /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon\r\ntotal 72\r\n-r--r--r-- 2 root root 586 Jan 1 1970 classicui.conf\r\n-r--r--r-- 2 root root 399 Jan 1 1970 clipboard.conf\r\n-r--r--r-- 2 root root 271 Jan 1 1970 dbus.conf\r\n-r--r--r-- 2 root root 356 Jan 1 1970 dbusfrontend.conf\r\n-r--r--r-- 2 root root 320 Jan 1 1970 fcitx4frontend.conf\r\n-r--r--r-- 2 root root 350 Jan 1 1970 ibusfrontend.conf\r\n-r--r--r-- 2 root root 666 Jan 1 1970 imselector.conf\r\n-r--r--r-- 2 root root 358 Jan 1 1970 keyboard.conf\r\n-r--r--r-- 2 root root 480 Jan 1 1970 kimpanel.conf\r\n-r--r--r-- 2 root root 779 Jan 1 1970 notificationitem.conf\r\n-r--r--r-- 2 root root 646 Jan 1 1970 notifications.conf\r\n-r--r--r-- 2 root root 369 Jan 1 1970 quickphrase.conf\r\n-r--r--r-- 2 root root 278 Jan 1 1970 spell.conf\r\n-r--r--r-- 2 root root 817 Jan 1 1970 unicode.conf\r\n-r--r--r-- 2 root root 275 Jan 1 1970 wayland.conf\r\n-r--r--r-- 2 root root 464 Jan 1 1970 waylandim.conf\r\n-r--r--r-- 2 root root 210 Jan 1 1970 xcb.conf\r\n-r--r--r-- 2 root root 595 Jan 1 1970 xim.conf\r\n```\r\n\r\nContents of `fcitx5-with-addons` with `fcitx5-mozc` installed:\r\n```sh-session\r\n$ ls -lA /nix/store/24p7w05im9zfa29c4vl4rsmm38xb3pxs-fcitx5-with-addons-5.0.14/share/fcitx5/addon/\r\ntotal 0\r\nlrwxrwxrwx 2 root root 91 Jan 1 1970 classicui.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/classicui.conf\r\nlrwxrwxrwx 2 root root 91 Jan 1 1970 clipboard.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/clipboard.conf\r\nlrwxrwxrwx 2 root root 86 Jan 1 1970 dbus.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/dbus.conf\r\nlrwxrwxrwx 2 root root 94 Jan 1 1970 dbusfrontend.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/dbusfrontend.conf\r\nlrwxrwxrwx 2 root root 96 Jan 1 1970 fcitx4frontend.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/fcitx4frontend.conf\r\nlrwxrwxrwx 2 root root 94 Jan 1 1970 ibusfrontend.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/ibusfrontend.conf\r\nlrwxrwxrwx 2 root root 91 Jan 1 1970 imeapi.conf -> /nix/store/hzkw9j6h3zdgbnq0nxc1xwc85q7b8nkm-fcitx5-lua-5.0.6/share/fcitx5/addon/imeapi.conf\r\nlrwxrwxrwx 2 root root 92 Jan 1 1970 imselector.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/imselector.conf\r\nlrwxrwxrwx 2 root root 90 Jan 1 1970 keyboard.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/keyboard.conf\r\nlrwxrwxrwx 2 root root 90 Jan 1 1970 kimpanel.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/kimpanel.conf\r\nlrwxrwxrwx 2 root root 99 Jan 1 1970 luaaddonloader.conf -> /nix/store/hzkw9j6h3zdgbnq0nxc1xwc85q7b8nkm-fcitx5-lua-5.0.6/share/fcitx5/addon/luaaddonloader.conf\r\nlrwxrwxrwx 2 root root 98 Jan 1 1970 mozc.conf -> /nix/store/vwiaxsza9s8xmw1r1vdyjcmdmwyll07q-fcitx5-mozc-2.26.4220.102/share/fcitx5/addon/mozc.conf\r\nlrwxrwxrwx 2 root root 98 Jan 1 1970 notificationitem.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/notificationitem.conf\r\nlrwxrwxrwx 2 root root 95 Jan 1 1970 notifications.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/notifications.conf\r\nlrwxrwxrwx 2 root root 93 Jan 1 1970 quickphrase.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/quickphrase.conf\r\nlrwxrwxrwx 2 root root 87 Jan 1 1970 spell.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/spell.conf\r\nlrwxrwxrwx 2 root root 89 Jan 1 1970 unicode.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/unicode.conf\r\nlrwxrwxrwx 2 root root 89 Jan 1 1970 wayland.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/wayland.conf\r\nlrwxrwxrwx 2 root root 91 Jan 1 1970 waylandim.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/waylandim.conf\r\nlrwxrwxrwx 2 root root 85 Jan 1 1970 xcb.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/xcb.conf\r\nlrwxrwxrwx 2 root root 85 Jan 1 1970 xim.conf -> /nix/store/gzvzx5cz4s15g4dkg8vyn960v8smmkc4-fcitx5-5.0.14/share/fcitx5/addon/xim.conf\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@poscat0x04, I guess?\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(plumeus): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160437/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160427","id":1140915046,"node_id":"I_kwDOAEVQ_M5EAPtm","number":160427,"title":"`switch-to-configuration` failing because Perl built incorrectly","user":{"login":"ethnt","id":137037,"node_id":"MDQ6VXNlcjEzNzAzNw==","avatar_url":"https://avatars.githubusercontent.com/u/137037?v=4","gravatar_id":"","url":"https://api.github.com/users/ethnt","html_url":"https://github.com/ethnt","followers_url":"https://api.github.com/users/ethnt/followers","following_url":"https://api.github.com/users/ethnt/following{/other_user}","gists_url":"https://api.github.com/users/ethnt/gists{/gist_id}","starred_url":"https://api.github.com/users/ethnt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ethnt/subscriptions","organizations_url":"https://api.github.com/users/ethnt/orgs","repos_url":"https://api.github.com/users/ethnt/repos","events_url":"https://api.github.com/users/ethnt/events{/privacy}","received_events_url":"https://api.github.com/users/ethnt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-17T06:06:45Z","updated_at":"2022-02-17T08:56:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nAs far as I can tell, the `switch-to-configuration` script is not being run with Perl because the correct version of Perl was not installed.\r\n\r\nIf I run the `switch-to-configuration` script:\r\n\r\n```\r\n$ /nix/store/07cgxyc0wgd5qwwkk3afs8d9pwmxws4y-nixos-system-htpc-21.11.20220216.2128d0a/bin/switch-to-configuration\r\n/nix/store/07cgxyc0wgd5qwwkk3afs8d9pwmxws4y-nixos-system-htpc-21.11.20220216.2128d0a/bin/switch-to-configuration: line 3: use: command not found\r\n/nix/store/07cgxyc0wgd5qwwkk3afs8d9pwmxws4y-nixos-system-htpc-21.11.20220216.2128d0a/bin/switch-to-configuration: line 4: use: command not found\r\n/nix/store/07cgxyc0wgd5qwwkk3afs8d9pwmxws4y-nixos-system-htpc-21.11.20220216.2128d0a/bin/switch-to-configuration: line 5: syntax error near unexpected token `('\r\n/nix/store/07cgxyc0wgd5qwwkk3afs8d9pwmxws4y-nixos-system-htpc-21.11.20220216.2128d0a/bin/switch-to-configuration: line 5: `use File::Path qw(make_path);'\r\n```\r\n\r\nThe first line of that script is:\r\n\r\n```\r\n#! /nix/store/cwix2dqwbw4naaf8pzlgb7c9mgaxgzlv-perl-5.34.0-env/bin/perl\r\n```\r\n\r\nBut if I try to run that Perl executable, I get:\r\n\r\n```\r\n$ /nix/store/cwix2dqwbw4naaf8pzlgb7c9mgaxgzlv-perl-5.34.0-env/bin/perl --version\r\nFailed to execute process '/nix/store/cwix2dqwbw4naaf8pzlgb7c9mgaxgzlv-perl-5.34.0-env/bin/perl'. Reason:\r\nexec: unknown error (errno was 8)\r\nThe file '/nix/store/cwix2dqwbw4naaf8pzlgb7c9mgaxgzlv-perl-5.34.0-env/bin/perl' is marked as an executable but could not be run by the operating system.\r\n```\r\n\r\nIf I look and see what that executable looks like, it seems to be empty?\r\n\r\n```\r\n$ cat /nix/store/cwix2dqwbw4naaf8pzlgb7c9mgaxgzlv-perl-5.34.0-env/bin/perl\r\n$ \r\n```\r\n\r\nI'm not quite sure what's going on here.\r\n\r\n### Steps To Reproduce\r\n\r\nThis only is happening for one of my NixOS machines, not for any of the others with nearly identical configurations. They are built off of the same NixOps deployment, using the same version of nixpkgs.\r\n\r\n### Expected behavior\r\n\r\nThe `switch-to-configuration` command runs successfully.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/store/f5hg16l66fhp7qpszkn82fazh2x4pnin-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160427/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160389","id":1140686622,"node_id":"I_kwDOAEVQ_M5D_X8e","number":160389,"title":"Firejail generating invalid script when Fish is in use","user":{"login":"Krutonium","id":3945538,"node_id":"MDQ6VXNlcjM5NDU1Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/3945538?v=4","gravatar_id":"","url":"https://api.github.com/users/Krutonium","html_url":"https://github.com/Krutonium","followers_url":"https://api.github.com/users/Krutonium/followers","following_url":"https://api.github.com/users/Krutonium/following{/other_user}","gists_url":"https://api.github.com/users/Krutonium/gists{/gist_id}","starred_url":"https://api.github.com/users/Krutonium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Krutonium/subscriptions","organizations_url":"https://api.github.com/users/Krutonium/orgs","repos_url":"https://api.github.com/users/Krutonium/repos","events_url":"https://api.github.com/users/Krutonium/events{/privacy}","received_events_url":"https://api.github.com/users/Krutonium/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-02-16T23:19:03Z","updated_at":"2022-02-24T08:22:09Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen wrapping a binary using firejail, using a custom profile, the resulting generated script isn't correct.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable Firejail\r\n2. \r\n```\r\n programs.firejail.wrappedBinaries = {\r\n Discord = {\r\n executable = \"${pkgs.discord}/bin/discord\";\r\n profile = ./discord.profile;\r\n };\r\n };\r\n```\r\n3. The resulting script that's generated is \r\n```\r\n#! /nix/store/bm7jr70d9ghn5cczb3q0w90apsm05p54-bash-5.1-p8/bin/bash -e\r\nexec /run/wrappers/bin/firejail '--profile=/nix/store/jcv5yi3vb2mhf5bkfbjn1hgr0q80w71n-source/packages/discord.profile' -- /nix/store/dpmpdgz9wmlzjq0rw8l69m8n7g8vpr1l-discord-0.0.16/bin/discord \"$@\"\r\n```\r\n\r\nRunning it produces the output of \r\n\r\n```\r\nReading profile /nix/store/jcv5yi3vb2mhf5bkfbjn1hgr0q80w71n-source/packages/discord.profile\r\nParent pid 366654, child pid 366655\r\nChild process initialized in 8.79 ms\r\nfish: Unknown command: --\r\nfish: \r\n--\r\n^\r\n```\r\n(I am indeed using fish as my default interpreter)\r\n\r\n### Expected behavior\r\n\r\nDiscord should open, with the restrictions I have placed upon it.\r\n\r\n### Additional context\r\nI wrote my own script that does the same thing without the `--` and it works perfectly.\r\nYou can see it [here.](https://github.com/Krutonium/My_Unified_NixOS_Config/blob/835419d58a34ca0b996dccbb46f53a3d64daebb1/packages/discord.nix)\r\n\r\n### Notify maintainers\r\n@7c6f434c \r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.3-zen1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-21.11.335288.3ddd960a3b5, nixos-hardware\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160389/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160376","id":1140598921,"node_id":"I_kwDOAEVQ_M5D_CiJ","number":160376,"title":"paperless-ng mail-fetching broken","user":{"login":"a7p","id":112350,"node_id":"MDQ6VXNlcjExMjM1MA==","avatar_url":"https://avatars.githubusercontent.com/u/112350?v=4","gravatar_id":"","url":"https://api.github.com/users/a7p","html_url":"https://github.com/a7p","followers_url":"https://api.github.com/users/a7p/followers","following_url":"https://api.github.com/users/a7p/following{/other_user}","gists_url":"https://api.github.com/users/a7p/gists{/gist_id}","starred_url":"https://api.github.com/users/a7p/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a7p/subscriptions","organizations_url":"https://api.github.com/users/a7p/orgs","repos_url":"https://api.github.com/users/a7p/repos","events_url":"https://api.github.com/users/a7p/events{/privacy}","received_events_url":"https://api.github.com/users/a7p/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-16T21:22:10Z","updated_at":"2022-03-31T16:26:17Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nFetching email won't work.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Configure an email account + an email rule\r\n2. wait\r\n3. look at `mail.log`\r\n\r\n### Expected behavior\r\nMail get's fetched\r\n\r\n### Additional context\r\npaperless-ng's requirements pin `imap-tools==0.46.0`\r\nhttps://github.com/jonaswinkler/paperless-ng/blob/master/requirements.txt#L48\r\n\r\nThe used nixpkgs version is at 0.50.2 https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/python-modules/imap-tools/default.nix#L10\r\n\r\n`Mailbox.seen` got deprecated in 0.46 and was removed 0.47 in https://github.com/ikvk/imap_tools/blob/f070869d3d9f4f4d82ae6683bee6211a7b571eb2/docs/release_notes.rst#0470\r\n\r\n```\r\n[2022-02-16 21:09:55,267] [DEBUG] [paperless_mail] Processing mail account mail@domain.com\r\n[2022-02-16 21:09:56,172] [DEBUG] [paperless_mail] Account mail@domain.com: Processing 1 rule(s)\r\n[2022-02-16 21:09:56,176] [DEBUG] [paperless_mail] Rule mail@domain.com.Invoice-Mailbox: Selecting folder Invoices\r\n[2022-02-16 21:09:56,258] [DEBUG] [paperless_mail] Rule mail@domain.com.Invoice-Mailbox: Searching folder with criteria (SINCE 17-Jan-2022 UNSEEN)\r\n[2022-02-16 21:09:56,338] [DEBUG] [paperless_mail] Rule mail@domain.com.Invoice-Mailbox: Processed 0 matching mail(s)\r\n[2022-02-16 21:09:56,339] [DEBUG] [paperless_mail] Rule mail@domain.com.Invoice-Mailbox: Running mail actions on 0 mails\r\n[2022-02-16 21:09:56,340] [ERROR] [paperless_mail] Rule mail@domain.com.Invoice-Mailbox: Error while processing rule: Rule mail@domain.com.Invoice-Mailbox: Error while processing post-consume actions: 'MailBox' object has no attribute 'seen'\r\nTraceback (most recent call last):\r\n File \"/nix/store/65p8ahg3d8h98xvirnhb4mcczxcfz808-paperless-ng-1.5.0/lib/paperless-ng/src/paperless_mail/mail.py\", line 241, in handle_mail_rule\r\n get_rule_action(rule).post_consume(\r\n File \"/nix/store/65p8ahg3d8h98xvirnhb4mcczxcfz808-paperless-ng-1.5.0/lib/paperless-ng/src/paperless_mail/mail.py\", line 45, in post_consume\r\n M.seen(message_uids, True)\r\nAttributeError: 'MailBox' object has no attribute 'seen'\r\nDuring handling of the above exception, another exception occurred:\r\nTraceback (most recent call last):\r\n File \"/nix/store/65p8ahg3d8h98xvirnhb4mcczxcfz808-paperless-ng-1.5.0/lib/paperless-ng/src/paperless_mail/mail.py\", line 172, in handle_mail_account\r\n total_processed_files += self.handle_mail_rule(M, rule)\r\n File \"/nix/store/65p8ahg3d8h98xvirnhb4mcczxcfz808-paperless-ng-1.5.0/lib/paperless-ng/src/paperless_mail/mail.py\", line 247, in handle_mail_rule\r\n raise MailError(\r\npaperless_mail.mail.MailError: Rule mail@domain.de.de.Invoice-Mailbox: Error while processing post-consume actions: 'MailBox' object has no attribute 'seen'\r\n```\r\n\r\n### Notify maintainers\r\n@dotlambda\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.21, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335883.7adc9c14ec7\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160376/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160361","id":1140475411,"node_id":"I_kwDOAEVQ_M5D-kYT","number":160361,"title":"iotop: CONFIG_TASK_DELAY_ACCT not enabled in kernel","user":{"login":"MatthewCroughan","id":26458780,"node_id":"MDQ6VXNlcjI2NDU4Nzgw","avatar_url":"https://avatars.githubusercontent.com/u/26458780?v=4","gravatar_id":"","url":"https://api.github.com/users/MatthewCroughan","html_url":"https://github.com/MatthewCroughan","followers_url":"https://api.github.com/users/MatthewCroughan/followers","following_url":"https://api.github.com/users/MatthewCroughan/following{/other_user}","gists_url":"https://api.github.com/users/MatthewCroughan/gists{/gist_id}","starred_url":"https://api.github.com/users/MatthewCroughan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MatthewCroughan/subscriptions","organizations_url":"https://api.github.com/users/MatthewCroughan/orgs","repos_url":"https://api.github.com/users/MatthewCroughan/repos","events_url":"https://api.github.com/users/MatthewCroughan/events{/privacy}","received_events_url":"https://api.github.com/users/MatthewCroughan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":287403097,"node_id":"MDU6TGFiZWwyODc0MDMwOTc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20good-first-bug","name":"3.skill: good-first-bug","color":"f7c6c7","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-16T19:40:03Z","updated_at":"2022-04-06T18:58:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen running `iotop` on `Linux t480 5.15.21 #1-NixOS SMP Sat Feb 5 18:21:09 UTC 2022 x86_64 GNU/Linux`, it results in iotop printing the message:\r\n\r\n```\r\nCONFIG_TASK_DELAY_ACCT not enabled in kernel, cannot determine SWAPIN and IO % 107 be/4 root 0.00 B/s 0.00 B/s ?unavailable? [kstrp]\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Ensure you are running the latest Linux kernel available from Nixpkgs at the time of writing (5.15.21) \r\n2. Grab iotop (`nix-shell -p iotop`)\r\n3. See that it complains about `CONFIG_TASK_DELAY_ACCT` not being available in the kernel.\r\n\r\n### Expected behavior\r\nThe IO column should have a percentage printed. \r\n\r\n### Screenshots\r\n#### Broken\r\n\r\n#### Working\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@7c6f434c\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nuser: matthew ~ \r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.21, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"\"`\r\n - channels(matthew): `\"\"`\r\n - nixpkgs: `/nix/store/zwbw7dknw89ai257hicmwv8lhid3qb62-source`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160361/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160351","id":1140404279,"node_id":"I_kwDOAEVQ_M5D-TA3","number":160351,"title":"Home Assistant ONVIF integration","user":{"login":"felschr","id":3314323,"node_id":"MDQ6VXNlcjMzMTQzMjM=","avatar_url":"https://avatars.githubusercontent.com/u/3314323?v=4","gravatar_id":"","url":"https://api.github.com/users/felschr","html_url":"https://github.com/felschr","followers_url":"https://api.github.com/users/felschr/followers","following_url":"https://api.github.com/users/felschr/following{/other_user}","gists_url":"https://api.github.com/users/felschr/gists{/gist_id}","starred_url":"https://api.github.com/users/felschr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/felschr/subscriptions","organizations_url":"https://api.github.com/users/felschr/orgs","repos_url":"https://api.github.com/users/felschr/repos","events_url":"https://api.github.com/users/felschr/events{/privacy}","received_events_url":"https://api.github.com/users/felschr/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-16T18:29:36Z","updated_at":"2022-02-18T17:38:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nhttps://www.home-assistant.io/integrations/onvif/\r\n\r\nAt the moment some dependencies are missing:\r\nhttps://github.com/NixOS/nixpkgs/blob/535df3ed51dccffd566114dbc898d158fe394988/pkgs/servers/home-assistant/component-packages.nix#L616\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.home-assistant.io/integrations/onvif/\r\n* source URL: https://github.com/home-assistant/core/tree/dev/homeassistant/components/onvif\r\n* license: Apache-2.0 License\r\n* platforms: linux","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160351/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160323","id":1139936827,"node_id":"I_kwDOAEVQ_M5D8g47","number":160323,"title":"Cross compilation of freetype fails","user":{"login":"Cloudef","id":480330,"node_id":"MDQ6VXNlcjQ4MDMzMA==","avatar_url":"https://avatars.githubusercontent.com/u/480330?v=4","gravatar_id":"","url":"https://api.github.com/users/Cloudef","html_url":"https://github.com/Cloudef","followers_url":"https://api.github.com/users/Cloudef/followers","following_url":"https://api.github.com/users/Cloudef/following{/other_user}","gists_url":"https://api.github.com/users/Cloudef/gists{/gist_id}","starred_url":"https://api.github.com/users/Cloudef/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Cloudef/subscriptions","organizations_url":"https://api.github.com/users/Cloudef/orgs","repos_url":"https://api.github.com/users/Cloudef/repos","events_url":"https://api.github.com/users/Cloudef/events{/privacy}","received_events_url":"https://api.github.com/users/Cloudef/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-16T12:16:11Z","updated_at":"2022-03-08T16:43:22Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"First of all, sorry if this isn't right place for this, but I don't really know where else to ask.\r\n\r\nI'm using the following nix file:\r\n```nix\r\n{}:\r\n\r\nrec {\r\n # https://github.com/NixOS/nixpkgs/pull/113122\r\n tar = fetchTarball\"https://github.com/s1341/nixpkgs/archive/android_prebuilt_working.tar.gz\";\r\n pkgs = import tar {};\r\n android-i686 = import tar {\r\n crossSystem = {\r\n config = \"i686-unknown-linux-android\";\r\n rustc.config = \"i686-linux-android\";\r\n sdkVer = \"29\";\r\n ndkVer = \"21\";\r\n useAndroidPrebuilt = true;\r\n };\r\n };\r\n\r\n test = android-i686.stdenv.mkDerivation {\r\n name = \"test\";\r\n buildInputs = [ android-i686.freetype ];\r\n buildPhase = ''\r\n find ${android-i686.freetype.out}\r\n '';\r\n };\r\n }\r\n```\r\n\r\nwith `nix-build -A test` outputs:\r\n\r\n```\r\nerror: builder for '/nix/store/zihm0cxjl7p047wjzx6i6mrm49s1xzxz-bash-4.4-p23-i686-unknown-linux-android.drv' failed with exit code 2\r\nerror: 1 dependencies of derivation '/nix/store/gr25xalh7dz32zl6haw3636cp3kxhi6a-hook.drv' failed to build\r\nerror (ignored): error: cannot unlink '/tmp/nix-build-pkg-config-0.29.2-i686-unknown-linux-android.drv-0/pkg-config-0.29.2/glib': Directory not empty\r\nerror: 1 dependencies of derivation '/nix/store/2mr2jwhxz56ym4mdv9xlb2x1i6zbc5wb-freetype-2.10.4-i686-unknown-linux-android.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/rni4lz32s9igc7l332k13kj6wpx8zm1d-test-i686-unknown-linux-android.drv' failed to build\r\n```\r\n\r\nThe freetype dependency seems to bring in a hook, that tries to compile bash for the host/target platform. Is there way to avoid this. Am I doing the cross-compilation wrong here? Other dependencies seems to compile fine.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160323/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160300","id":1139751013,"node_id":"I_kwDOAEVQ_M5D7zhl","number":160300,"title":"Cannot chroot to a different CPU architecture using `boot.binfmt.emulatedSystems`","user":{"login":"chuangzhu","id":31200881,"node_id":"MDQ6VXNlcjMxMjAwODgx","avatar_url":"https://avatars.githubusercontent.com/u/31200881?v=4","gravatar_id":"","url":"https://api.github.com/users/chuangzhu","html_url":"https://github.com/chuangzhu","followers_url":"https://api.github.com/users/chuangzhu/followers","following_url":"https://api.github.com/users/chuangzhu/following{/other_user}","gists_url":"https://api.github.com/users/chuangzhu/gists{/gist_id}","starred_url":"https://api.github.com/users/chuangzhu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/chuangzhu/subscriptions","organizations_url":"https://api.github.com/users/chuangzhu/orgs","repos_url":"https://api.github.com/users/chuangzhu/repos","events_url":"https://api.github.com/users/chuangzhu/events{/privacy}","received_events_url":"https://api.github.com/users/chuangzhu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"zhaofengli","id":2189609,"node_id":"MDQ6VXNlcjIxODk2MDk=","avatar_url":"https://avatars.githubusercontent.com/u/2189609?v=4","gravatar_id":"","url":"https://api.github.com/users/zhaofengli","html_url":"https://github.com/zhaofengli","followers_url":"https://api.github.com/users/zhaofengli/followers","following_url":"https://api.github.com/users/zhaofengli/following{/other_user}","gists_url":"https://api.github.com/users/zhaofengli/gists{/gist_id}","starred_url":"https://api.github.com/users/zhaofengli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zhaofengli/subscriptions","organizations_url":"https://api.github.com/users/zhaofengli/orgs","repos_url":"https://api.github.com/users/zhaofengli/repos","events_url":"https://api.github.com/users/zhaofengli/events{/privacy}","received_events_url":"https://api.github.com/users/zhaofengli/received_events","type":"User","site_admin":false},"assignees":[{"login":"zhaofengli","id":2189609,"node_id":"MDQ6VXNlcjIxODk2MDk=","avatar_url":"https://avatars.githubusercontent.com/u/2189609?v=4","gravatar_id":"","url":"https://api.github.com/users/zhaofengli","html_url":"https://github.com/zhaofengli","followers_url":"https://api.github.com/users/zhaofengli/followers","following_url":"https://api.github.com/users/zhaofengli/following{/other_user}","gists_url":"https://api.github.com/users/zhaofengli/gists{/gist_id}","starred_url":"https://api.github.com/users/zhaofengli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zhaofengli/subscriptions","organizations_url":"https://api.github.com/users/zhaofengli/orgs","repos_url":"https://api.github.com/users/zhaofengli/repos","events_url":"https://api.github.com/users/zhaofengli/events{/privacy}","received_events_url":"https://api.github.com/users/zhaofengli/received_events","type":"User","site_admin":false}],"milestone":null,"comments":5,"created_at":"2022-02-16T09:18:17Z","updated_at":"2022-02-19T00:24:03Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nChroot to a guest system rootfs of a different CPU architecture fails. Reporting `/bin/bash: No such file or directory`.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Add `boot.binfmt.emulatedSystems = [ \"aarch64-linux\" ]` to the host's configuration and rebuild.\r\n2. Fetch the tarball of a guest system for a different arch (Gentoo arm64 here):\r\n\r\n ```shellsession\r\n [root@nixos-x86_64]# mkdir -p /mnt/gentoo-arm64 && cd /mnt/gentoo-arm64\r\n [root@nixos-x86_64]# curl -O https://bouncer.gentoo.org/fetch/root/all/releases/arm64/autobuilds/20220213T235221Z/stage3-arm64-systemd-20220213T235221Z.tar.xz\r\n ```\r\n3. Extract the tarball and try to chroot into it:\r\n\r\n ```shellsession\r\n [root@nixos-x86_64]# tar xf stage3-arm64-systemd-20220213T235221Z.tar.xz\r\n [root@nixos-x86_64]# chroot /mnt/gentoo-amd64/ /bin/bash\r\n chroot: failed to run command ‘/bin/bash’: No such file or directory\r\n [root@nixos-x86_64]# systemd-nspawn -D /mnt/gentoo-amd64 -M gentoo-amd64\r\n Spawning container gentoo-arm64 on /mnt/gentoo-arm64.\r\n Press ^] three times within 1s to kill container.\r\n execv(/bin/bash, /bin/sh) failed: No such file or directory\r\n Container gentoo-arm64 failed with error code 1.\r\n ```\r\n\r\n### Expected behavior\r\n\r\nQemu correctly interprets `/mnt/gentoo-amd64/bin/bash` and execute it.\r\n\r\n### Additional context\r\n\r\nManually executing dynamic link loader on the bash executable under the guest rootfs works\r\n\r\n```shellsession\r\n[root@nixos-x86_64]# LD_LIBRARY_PATH=/mnt/gentoo-arm64/lib64 /mnt/gentoo-arm64/lib64/ld-linux-aarch64.so.1 /mnt/gentoo-arm64/bin/bash\r\nbash-5.1# \r\n```\r\n\r\nChroot to a guest rootfs of the same arch with the host works:\r\n\r\n```shellsession\r\n[root@nixos-x86_64]# mkdir -p /mnt/gentoo-amd64 && cd /mnt/gentoo-amd64\r\n[root@nixos-x86_64]# curl -O https://bouncer.gentoo.org/fetch/root/all/releases/amd64/autobuilds/20220214T095322Z/stage3-amd64-systemd-20220214T095322Z.tar.xz\r\n[root@nixos-x86_64]# tar xf stage3-amd64-systemd-20220214T095322Z.tar.xz \r\n[root@nixos-x86_64]# systemd-nspawn -D /mnt/gentoo-amd64/ -M gentoo-amd64\r\nSpawning container gentoo-amd64 on /mnt/gentoo-amd64.\r\nPress ^] three times within 1s to kill container.\r\ngentoo-amd64 ~ # \r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@matthewbauer @shlevy @zhaofengli @polykernel @flokli\r\n\r\n### Metadata\r\n\r\n```console\r\n[root@nixos-x86_64]# nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.99, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos\"`\r\n - channels(chuang): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160300/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160289","id":1139675600,"node_id":"I_kwDOAEVQ_M5D7hHQ","number":160289,"title":"Fetching paths from cache.nixos.org can get 'stuck'","user":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":16,"created_at":"2022-02-16T08:15:53Z","updated_at":"2022-02-26T18:55:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSometimes, nix gets stuck fetching paths:\r\n\r\n```\r\n$ nix-shell -p sbt\r\nthese 2 paths will be fetched (408.08 MiB download, 694.33 MiB unpacked):\r\n /nix/store/0kg8zm25k6av8hgf177kwnp9q5j6yrf3-openjdk-17.0.1+12\r\n /nix/store/wj7x8ik896h0k9r6fk0bns21xw5c18yh-sbt-1.6.2\r\ncopying path '/nix/store/0kg8zm25k6av8hgf177kwnp9q5j6yrf3-openjdk-17.0.1+12' from 'https://cache.nixos.org'...\r\n```\r\n\r\nStalling without any network traffic.\r\n\r\nInterestingly this seems to be somehow tied to the specific path: nix can download other paths just fine, but always gets stuck on (in this case) `/nix/store/0kg8zm25k6av8hgf177kwnp9q5j6yrf3-openjdk-17.0.1+12`. \r\n\r\nIt has something to do with the system state: rebooting the machine makes it possible to fetch the path again, but killing all `nix-daemon` processes without rebooting doesn't seem to help.\r\n\r\nedit: it does seem to be something around nix-daemon though, because when rebooting I see systemd-shutdown waiting for several nix-daemon processes to shut down which takes quite a while.\r\n\r\nIf anyone can suggest ways to further diagnose the problem I'd be happy to try things out!\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.5, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos-20.03pre194293.2436c27541b\"`\r\n - nixpkgs: `/home/aengelen/nixpkgs`\r\n```\r\n\r\n(current profile is at 9f697d60e4d, nixpkgs is at 48d63e924a)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160289/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160219","id":1139226349,"node_id":"I_kwDOAEVQ_M5D5zbt","number":160219,"title":"Packaging request: webkitgtk_5_0","user":{"login":"Stunkymonkey","id":1315818,"node_id":"MDQ6VXNlcjEzMTU4MTg=","avatar_url":"https://avatars.githubusercontent.com/u/1315818?v=4","gravatar_id":"","url":"https://api.github.com/users/Stunkymonkey","html_url":"https://github.com/Stunkymonkey","followers_url":"https://api.github.com/users/Stunkymonkey/followers","following_url":"https://api.github.com/users/Stunkymonkey/following{/other_user}","gists_url":"https://api.github.com/users/Stunkymonkey/gists{/gist_id}","starred_url":"https://api.github.com/users/Stunkymonkey/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Stunkymonkey/subscriptions","organizations_url":"https://api.github.com/users/Stunkymonkey/orgs","repos_url":"https://api.github.com/users/Stunkymonkey/repos","events_url":"https://api.github.com/users/Stunkymonkey/events{/privacy}","received_events_url":"https://api.github.com/users/Stunkymonkey/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-15T21:21:38Z","updated_at":"2022-02-16T21:19:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nthere is already package `webkitgtk` and `webkitgtk_4_1`.\r\nThere is a new version `webkitgtk_5_0`, which is missing in nixpkgs. I think this comes with `gtk4`.\r\nmaybe having a look at the [arch-linux-build](https://github.com/archlinux/svntogit-packages/blob/packages/webkit2gtk-5.0/trunk/PKGBUILD) is helpfull.\r\n\r\nping to the gnome-team:\r\n@hedning, @jtojnar, @dasj19, @maxeaubrey\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://webkitgtk.org/\r\n* source URL: same as `webkitgtk`\r\n* license: bsd2\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160219/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160113","id":1138290240,"node_id":"I_kwDOAEVQ_M5D2O5A","number":160113,"title":"Tridactyl native messenger does not work.","user":{"login":"Ninlives","id":17873203,"node_id":"MDQ6VXNlcjE3ODczMjAz","avatar_url":"https://avatars.githubusercontent.com/u/17873203?v=4","gravatar_id":"","url":"https://api.github.com/users/Ninlives","html_url":"https://github.com/Ninlives","followers_url":"https://api.github.com/users/Ninlives/followers","following_url":"https://api.github.com/users/Ninlives/following{/other_user}","gists_url":"https://api.github.com/users/Ninlives/gists{/gist_id}","starred_url":"https://api.github.com/users/Ninlives/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Ninlives/subscriptions","organizations_url":"https://api.github.com/users/Ninlives/orgs","repos_url":"https://api.github.com/users/Ninlives/repos","events_url":"https://api.github.com/users/Ninlives/events{/privacy}","received_events_url":"https://api.github.com/users/Ninlives/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-15T07:25:31Z","updated_at":"2022-02-15T07:25:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI created a firefox derivation with the following snippet:\r\n```nix\r\nwrapFirefox firefox-esr-unwrapped {\r\n nixExtensions = [(fetchFirefoxAddon { name = \"tridactyl\"; url = \"...\"; sha256 = \"...\"; })];\r\n extraNativeMessagingHosts = [ tridactyl-native ];\r\n}\r\n```\r\n\r\nHowever the native messenger does not seem to work, the log says:\r\n```\r\nThis extension does not have permission to use native manifest /nix/store/z8wphgjz22divfjkkhb4yqjk0hqsa598-firefox-91.6.0esr/lib/mozilla/native-messaging-hosts/tridactyl.json\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160113/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160103","id":1138217109,"node_id":"I_kwDOAEVQ_M5D19CV","number":160103,"title":"Insufficient identifier for ruby","user":{"login":"viraptor","id":188063,"node_id":"MDQ6VXNlcjE4ODA2Mw==","avatar_url":"https://avatars.githubusercontent.com/u/188063?v=4","gravatar_id":"","url":"https://api.github.com/users/viraptor","html_url":"https://github.com/viraptor","followers_url":"https://api.github.com/users/viraptor/followers","following_url":"https://api.github.com/users/viraptor/following{/other_user}","gists_url":"https://api.github.com/users/viraptor/gists{/gist_id}","starred_url":"https://api.github.com/users/viraptor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/viraptor/subscriptions","organizations_url":"https://api.github.com/users/viraptor/orgs","repos_url":"https://api.github.com/users/viraptor/repos","events_url":"https://api.github.com/users/viraptor/events{/privacy}","received_events_url":"https://api.github.com/users/viraptor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-15T05:51:56Z","updated_at":"2022-04-27T13:51:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen building ruby, the platform identifier does not become part of the package. That means you can end up with non-runnable packages which don't rebuild automatically.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install ruby-2.7.5 and bundler on darwin-20 (or earlier) platform (check with `uname -r` or `Gem::Platform.local`)\r\n2. Upgrade system to latest (darwin-21)\r\n3. Attempt to use `bundle exec ...` in the built environment\r\n4. Get: (in this case the system upgrade was 17 -> 21)\r\n```\r\nYour bundle only supports platforms [\"arm64-darwin-21\", \"x86_64-darwin-19\", \"x86_64-darwin-20\", \"x86_64-darwin-21\", \"x86_64-linux\"] but your local platform is x86_64-darwin-17. Add the current platform to the lockfile with `bundle lock --add-platform x86_64-darwin-17` and try again. (Bundler::ProductionError)\r\n```\r\n5. Trying to `nix develop` the project after the upgrade does not see the problem and does not rebuild the dependencies.\r\n\r\n### Expected behavior\r\nDepending on ruby should cause an automatic rebuild, if the current ruby derivation was built on previous darwin version.\r\n\r\n### Additional context\r\nDoes this actually warrant making the ruby package `ruby-2.7.5-darwin-21` that's also visible as `ruby-2.7.5`?\r\n\r\n### Notify maintainers\r\n@vrthra @manveru @marsam\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(viraptor): `\"home-manager-21.11.tar.gz\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160103/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094/events","html_url":"https://github.com/NixOS/nixpkgs/issues/160094","id":1138170138,"node_id":"I_kwDOAEVQ_M5D1xka","number":160094,"title":"`python3Packages.treeo` build failure on x86_64-linux as of `a31699dc`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"ndl","id":137805,"node_id":"MDQ6VXNlcjEzNzgwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/137805?v=4","gravatar_id":"","url":"https://api.github.com/users/ndl","html_url":"https://github.com/ndl","followers_url":"https://api.github.com/users/ndl/followers","following_url":"https://api.github.com/users/ndl/following{/other_user}","gists_url":"https://api.github.com/users/ndl/gists{/gist_id}","starred_url":"https://api.github.com/users/ndl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ndl/subscriptions","organizations_url":"https://api.github.com/users/ndl/orgs","repos_url":"https://api.github.com/users/ndl/repos","events_url":"https://api.github.com/users/ndl/events{/privacy}","received_events_url":"https://api.github.com/users/ndl/received_events","type":"User","site_admin":false},"assignees":[{"login":"ndl","id":137805,"node_id":"MDQ6VXNlcjEzNzgwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/137805?v=4","gravatar_id":"","url":"https://api.github.com/users/ndl","html_url":"https://github.com/ndl","followers_url":"https://api.github.com/users/ndl/followers","following_url":"https://api.github.com/users/ndl/following{/other_user}","gists_url":"https://api.github.com/users/ndl/gists{/gist_id}","starred_url":"https://api.github.com/users/ndl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ndl/subscriptions","organizations_url":"https://api.github.com/users/ndl/orgs","repos_url":"https://api.github.com/users/ndl/repos","events_url":"https://api.github.com/users/ndl/events{/privacy}","received_events_url":"https://api.github.com/users/ndl/received_events","type":"User","site_admin":false}],"milestone":null,"comments":1,"created_at":"2022-02-15T04:34:01Z","updated_at":"2022-02-15T23:47:00Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"\n## Issue description\nBuild of `python3Packages.treeo` failed on x86_64-linux as of a31699dce9a2d5b432a41a7499e088240d1086c8.\n\n[build log](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1844166336)\n\nMaintainer cc: @ndl\nOther cc: n/a\n\n### Steps to reproduce\n1. Checkout nixpkgs at commit a31699dce9a2d5b432a41a7499e088240d1086c8\n2. Run `nix-build -A python3Packages.treeo`\n\n## Technical details\n```\n- system: `\"x86_64-linux\"`\n - host os: `Linux 5.11.0-1028-azure, Ubuntu, 20.04.3 LTS (Focal Fossa)`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.6.0`\n - nixpkgs: `/nix/store/f78jqkss0z39h2602xrrigzy6g1skpv6-source`\n```\n\n## Misc.\nThis issue was automatically generated by [nixpkgs-upkeep](https://github.com/samuela/nixpkgs-upkeep).\n- [CI workflow](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1844166336) that created this issue.\n- Internal tag: 1168056083124040910\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/160094/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159996","id":1137470491,"node_id":"I_kwDOAEVQ_M5DzGwb","number":159996,"title":"GNSS_SDR: add -DENABLE_OSMOSDR=ON to build flags","user":{"login":"Split7fire","id":13453673,"node_id":"MDQ6VXNlcjEzNDUzNjcz","avatar_url":"https://avatars.githubusercontent.com/u/13453673?v=4","gravatar_id":"","url":"https://api.github.com/users/Split7fire","html_url":"https://github.com/Split7fire","followers_url":"https://api.github.com/users/Split7fire/followers","following_url":"https://api.github.com/users/Split7fire/following{/other_user}","gists_url":"https://api.github.com/users/Split7fire/gists{/gist_id}","starred_url":"https://api.github.com/users/Split7fire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Split7fire/subscriptions","organizations_url":"https://api.github.com/users/Split7fire/orgs","repos_url":"https://api.github.com/users/Split7fire/repos","events_url":"https://api.github.com/users/Split7fire/events{/privacy}","received_events_url":"https://api.github.com/users/Split7fire/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-14T15:30:26Z","updated_at":"2022-03-21T14:09:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"While working with gnss-sdr found out that `gnss-sdr` package in nixos built without osmosdr support. Looking through [nixos packages](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/applications/radio/gnss-sdr/default.nix#L85) confirm this.\r\nCan we just add add `-DENABLE_OSMOSDR=ON` to cmakeFlags?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159996/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159981","id":1137229443,"node_id":"I_kwDOAEVQ_M5DyL6D","number":159981,"title":"Pantheon (Gala) spamming logs with assertion failures (clutter_paint_volume_set_width)","user":{"login":"kirelagin","id":451835,"node_id":"MDQ6VXNlcjQ1MTgzNQ==","avatar_url":"https://avatars.githubusercontent.com/u/451835?v=4","gravatar_id":"","url":"https://api.github.com/users/kirelagin","html_url":"https://github.com/kirelagin","followers_url":"https://api.github.com/users/kirelagin/followers","following_url":"https://api.github.com/users/kirelagin/following{/other_user}","gists_url":"https://api.github.com/users/kirelagin/gists{/gist_id}","starred_url":"https://api.github.com/users/kirelagin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kirelagin/subscriptions","organizations_url":"https://api.github.com/users/kirelagin/orgs","repos_url":"https://api.github.com/users/kirelagin/repos","events_url":"https://api.github.com/users/kirelagin/events{/privacy}","received_events_url":"https://api.github.com/users/kirelagin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1207068537,"node_id":"MDU6TGFiZWwxMjA3MDY4NTM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20pantheon","name":"6.topic: pantheon","color":"fef2c0","default":false,"description":"The Pantheon desktop environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-14T12:24:52Z","updated_at":"2022-02-14T14:11:01Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I’m running NixOS unstable, but I had the same behaviour with 21.11 (and I think maybe even 21.05).\r\n\r\nMy journal is full of this:\r\n\r\n```\r\nFeb 13 21:30:55 kirXps .gala-wrapped[2559]: clutter_paint_volume_set_width: assertion 'width >= 0.0f' failed\r\nFeb 13 21:30:55 kirXps .gala-wrapped[2559]: clutter_paint_volume_set_height: assertion 'height >= 0.0f' failed\r\n```\r\n\r\nAnd there are tens (like sometimes ~60) of these messages per second. I am not exactly sure what causes this issue, it starts to happen once I launch a “heavy” app (Firefox, Chromium, GIMP) and does not start to happen for “lighter” apps. Once it starts, it does not stop even after I exit the app, only logging out helps.\r\n\r\nThe process with pid 2559 is Gala, but I am having a hard time figuring out what is the actual code that causes this. I am actually surprised that I can’t find any reports of this given that I don’t think there is anything special about my setup, this issue is happening constantly, has been present for quite a long time, and is pretty annoying since it makes the journal unreadable and causes tons of disk writes (like, right now, journald is writing on average ~12 KB/s, so almost 1 MB/minute).\r\n\r\nI don’t understand what is special about those “large” apps that cause it yet, and I have no idea where to even start. Just wanted to create an issue to let others know that I’ll be looking into it. I’ll be grateful for any pointers.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159981/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159964","id":1137027009,"node_id":"I_kwDOAEVQ_M5DxafB","number":159964,"title":"Unable to increate ulimit nofile when using systemd","user":{"login":"bikallem","id":315907,"node_id":"MDQ6VXNlcjMxNTkwNw==","avatar_url":"https://avatars.githubusercontent.com/u/315907?v=4","gravatar_id":"","url":"https://api.github.com/users/bikallem","html_url":"https://github.com/bikallem","followers_url":"https://api.github.com/users/bikallem/followers","following_url":"https://api.github.com/users/bikallem/following{/other_user}","gists_url":"https://api.github.com/users/bikallem/gists{/gist_id}","starred_url":"https://api.github.com/users/bikallem/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bikallem/subscriptions","organizations_url":"https://api.github.com/users/bikallem/orgs","repos_url":"https://api.github.com/users/bikallem/repos","events_url":"https://api.github.com/users/bikallem/events{/privacy}","received_events_url":"https://api.github.com/users/bikallem/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-02-14T09:35:17Z","updated_at":"2022-03-02T15:30:21Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI am looking to increase the maximum no. of open file descriptors in nixos using the following\r\n\r\n```\r\nsecurity.pam.loginLimits = [\r\n {domain = \"*\";type = \"-\";item = \"nofile\";value = \"8192\";}\r\n ];\r\n```\r\n\r\nI did both `sudo nixos-rebuild switch` and `reboot` . However, I still get `1024` when I do `ulimit -a` ? Is there something that I am missing?\r\n\r\n### Steps To Reproduce\r\n1. add following lines to `/etc/nixos/configuration.nix`\r\n```\r\nsecurity.pam.loginLimits = [\r\n {domain = \"*\";type = \"-\";item = \"nofile\";value = \"8192\";}\r\n ];\r\n```\r\n2. `sudo nixos-rebuild switch`\r\n3. `ulimit -a` \r\n\r\n### Expected behavior\r\n`ulimit -a` should report 8192 but it still display 1024.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos\"`\r\n - channels(bikal): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159964/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159963","id":1137022911,"node_id":"I_kwDOAEVQ_M5DxZe_","number":159963,"title":"Packaging request: oh my posh","user":{"login":"coolshaurya","id":32027323,"node_id":"MDQ6VXNlcjMyMDI3MzIz","avatar_url":"https://avatars.githubusercontent.com/u/32027323?v=4","gravatar_id":"","url":"https://api.github.com/users/coolshaurya","html_url":"https://github.com/coolshaurya","followers_url":"https://api.github.com/users/coolshaurya/followers","following_url":"https://api.github.com/users/coolshaurya/following{/other_user}","gists_url":"https://api.github.com/users/coolshaurya/gists{/gist_id}","starred_url":"https://api.github.com/users/coolshaurya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/coolshaurya/subscriptions","organizations_url":"https://api.github.com/users/coolshaurya/orgs","repos_url":"https://api.github.com/users/coolshaurya/repos","events_url":"https://api.github.com/users/coolshaurya/events{/privacy}","received_events_url":"https://api.github.com/users/coolshaurya/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-14T09:32:07Z","updated_at":"2022-02-14T09:32:07Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nA prompt theme engine for any shell.\r\n\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://ohmyposh.dev\r\n* source URL: https://github.com/jandedobbeleer/oh-my-posh\r\n* license: GPL-3.0\r\n* platforms: MacOS and Linux (Windows too, but that's irrelevant for Nix)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159963/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159921","id":1136567787,"node_id":"I_kwDOAEVQ_M5DvqXr","number":159921,"title":"fetch-instance-ssh-keys.service on GCP with 21.11 shows failed when there is no metadata for sshKeys","user":{"login":"andre-vspry","id":54784392,"node_id":"MDQ6VXNlcjU0Nzg0Mzky","avatar_url":"https://avatars.githubusercontent.com/u/54784392?v=4","gravatar_id":"","url":"https://api.github.com/users/andre-vspry","html_url":"https://github.com/andre-vspry","followers_url":"https://api.github.com/users/andre-vspry/followers","following_url":"https://api.github.com/users/andre-vspry/following{/other_user}","gists_url":"https://api.github.com/users/andre-vspry/gists{/gist_id}","starred_url":"https://api.github.com/users/andre-vspry/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/andre-vspry/subscriptions","organizations_url":"https://api.github.com/users/andre-vspry/orgs","repos_url":"https://api.github.com/users/andre-vspry/repos","events_url":"https://api.github.com/users/andre-vspry/events{/privacy}","received_events_url":"https://api.github.com/users/andre-vspry/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-14T00:33:20Z","updated_at":"2022-02-14T00:33:20Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nfetch-instance-ssh-keys.service on GCP with 21.11 shows failed when there is no metadata for sshKeys\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n`flake.nix`\r\n```nix\r\n{\r\n description = \"gcp nixos 21.11 test\";\r\n\r\n inputs = {\r\n nixpkgs.url = github:NixOS/nixpkgs/nixos-21.11;\r\n };\r\n\r\n outputs = inputs:\r\n let\r\n system = \"x86_64-linux\";\r\n pkgs = inputs.nixpkgs.legacyPackages.${system};\r\n in\r\n {\r\n nixosConfigurations.\"gcp-21.11\" = inputs.nixpkgs.lib.nixosSystem {\r\n inherit system;\r\n\r\n modules = [\r\n ./configuration.nix\r\n ];\r\n };\r\n\r\n devShell.${system} = pkgs.mkShell {\r\n nativeBuildInputs = with pkgs; [ google-cloud-sdk jq ];\r\n\r\n PROJECT_ID = \"xxxxxx-test\";\r\n PROJECT_NUMBER = \"11111111111111\";\r\n BUCKET = \"nixos-images-xxxxxx\";\r\n REGION = \"australia-southeast1\";\r\n ZONE = \"australia-southeast1-b\";\r\n };\r\n };\r\n}\r\n```\r\n\r\n`confiuration.nix`\r\n```nix\r\n{ config, lib, pkgs, modulesPath, ... }:\r\n{\r\n imports = [\r\n (modulesPath + \"/virtualisation/google-compute-image.nix\")\r\n ];\r\n\r\n # users.users.root.openssh.authorizedKeys.keys = [\r\n # \"ecdsa-sha2-nistp256 AAAAxxxxxxxxxxxxxxxxxxxx= user\"\r\n # ];\r\n}\r\n```\r\n\r\n1. shell\r\n```sh\r\nnix develop\r\n```\r\n2. authenticate, create a bucket and give yourself object admin permissions with gcloud\r\n3. build the image\r\n```sh\r\nIMAGE=$(nix build --no-link --json '.#nixosConfigurations.\"gcp-21.11\".config.system.build.googleComputeImage' | jq -r '.[0].outputs.out' | xargs -IX find X -type f)\r\n```\r\n4. upload to bucket\r\n```sh\r\ngsutil cp \"${IMAGE}\" \"gs://${BUCKET}\"\r\n```\r\n5. create the image\r\n```sh\r\nIMAGE_NAME=$(basename \"${IMAGE}\" | cut -d- -f1-3 | tr '.' '-')\r\ngcloud compute images create \"${IMAGE_NAME}\" --project=\"${PROJECT_ID}\" --family=nixos --source-uri=https://storage.googleapis.com/${BUCKET}/$(basename \"${IMAGE}\") --storage-location=\"${REGION}\"\r\n```\r\n6. create the instance\r\n```sh\r\ngcloud compute instances create \"instance-${IMAGE_NAME}\" --project=\"${PROJECT_ID}\" --zone=\"${ZONE}\" --machine-type=n2-standard-4 --network-interface=network-tier=PREMIUM,subnet=default --no-restart-on-failure --maintenance-policy=TERMINATE --preemptible --service-account=\"${PROJECT_NUMBER}-compute@developer.gserviceaccount.com\" --scopes=https://www.googleapis.com/auth/devstorage.read_only,https://www.googleapis.com/auth/logging.write,https://www.googleapis.com/auth/monitoring.write,https://www.googleapis.com/auth/servicecontrol,https://www.googleapis.com/auth/service.management.readonly,https://www.googleapis.com/auth/trace.append --tags=allow-ssh --create-disk=\"auto-delete=yes,boot=yes,device-name=instance-${IMAGE_NAME},image=projects/${PROJECT_ID}/global/images/${IMAGE_NAME},mode=rw,size=50,type=projects/${PROJECT_ID}/zones/${ZONE}/diskTypes/pd-ssd\" --reservation-affinity=any --metadata \"enable-oslogin=TRUE\"\r\n```\r\n7. observe the logs on the console\r\n```sh\r\ngcloud compute --project=\"${PROJECT_ID}\" instances get-serial-port-output \"instance-${IMAGE_NAME}\" --zone=\"${ZONE}\" --port=1\r\n```\r\n\r\n### Expected behavior\r\nNormal boot without any failed services.\r\n\r\n### Screenshots\r\n```sh\r\nsystemctl | grep fetch\r\n```\r\n```console\r\n● fetch-instance-ssh-keys.service loaded failed failed Fetch host keys and authorized_keys for root user\r\n```\r\n\r\n```sh\r\ncurl http://metadata.google.internal/computeMetadata/v1/instance/attributes/ -H 'Metadata-Flavor: Google'\r\n```\r\n\r\nshows only `enable-oslogin` so the wget of `http://metadata.google.internal/computeMetadata/v1/instance/attributes/sshKeys` fails.\r\n\r\n\r\n```sh\r\nsudo journalctl -u fetch-instance-ssh-keys.service\r\n```\r\n```console\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[771]: Fetching authorized keys...\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[774]: --2022-02-13 23:38:09-- http://metadata.google.internal/computeMetadata/v1/instance/attributes/sshKeys\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[774]: Resolving metadata.google.internal (metadata.google.internal)... 169.254.169.254\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[774]: Connecting to metadata.google.internal (metadata.google.internal)|169.254.169.254|:80... connected.\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[774]: HTTP request sent, awaiting response... 404 Not Found\r\nFeb 13 23:38:09 localhost p2lywhlys1d4cp7w508anmc5jigxcc9l-fetch-instance-ssh-keys[774]: 2022-02-13 23:38:09 ERROR 404: Not Found.\r\nFeb 13 23:38:09 localhost systemd[1]: fetch-instance-ssh-keys.service: Main process exited, code=exited, status=8/n/a\r\nFeb 13 23:38:09 localhost systemd[1]: fetch-instance-ssh-keys.service: Failed with result 'exit-code'.\r\nFeb 13 23:38:09 localhost systemd[1]: Failed to start Fetch host keys and authorized_keys for root user.\r\n```\r\n\r\n\r\n### Additional context\r\nReferred from discussion about new agent at #150837\r\n\r\n### Notify maintainers\r\n@flokli @jonringer\r\n\r\ncc: @NinjaTrappeur @abbradar \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.98, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335883.7adc9c14ec7\"`\r\n - channels(user): `\"home-manager-21.11, unstable-22.05pre353535.48d63e924a2\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n ```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159921/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159878","id":1136281593,"node_id":"I_kwDOAEVQ_M5Dukf5","number":159878,"title":"supabase","user":{"login":"lawrencecchen","id":54008264,"node_id":"MDQ6VXNlcjU0MDA4MjY0","avatar_url":"https://avatars.githubusercontent.com/u/54008264?v=4","gravatar_id":"","url":"https://api.github.com/users/lawrencecchen","html_url":"https://github.com/lawrencecchen","followers_url":"https://api.github.com/users/lawrencecchen/followers","following_url":"https://api.github.com/users/lawrencecchen/following{/other_user}","gists_url":"https://api.github.com/users/lawrencecchen/gists{/gist_id}","starred_url":"https://api.github.com/users/lawrencecchen/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lawrencecchen/subscriptions","organizations_url":"https://api.github.com/users/lawrencecchen/orgs","repos_url":"https://api.github.com/users/lawrencecchen/repos","events_url":"https://api.github.com/users/lawrencecchen/events{/privacy}","received_events_url":"https://api.github.com/users/lawrencecchen/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-13T18:49:17Z","updated_at":"2022-02-13T18:49:17Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nAn open source firebase alternative\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://supabase.com/\r\n* source URL: https://github.com/supabase/supabase\r\n* license: MIT\r\n* platforms: docker\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159878/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159837","id":1135800164,"node_id":"I_kwDOAEVQ_M5Dsu9k","number":159837,"title":"Packaging request: OneDev","user":{"login":"wyndon","id":72203260,"node_id":"MDQ6VXNlcjcyMjAzMjYw","avatar_url":"https://avatars.githubusercontent.com/u/72203260?v=4","gravatar_id":"","url":"https://api.github.com/users/wyndon","html_url":"https://github.com/wyndon","followers_url":"https://api.github.com/users/wyndon/followers","following_url":"https://api.github.com/users/wyndon/following{/other_user}","gists_url":"https://api.github.com/users/wyndon/gists{/gist_id}","starred_url":"https://api.github.com/users/wyndon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wyndon/subscriptions","organizations_url":"https://api.github.com/users/wyndon/orgs","repos_url":"https://api.github.com/users/wyndon/repos","events_url":"https://api.github.com/users/wyndon/events{/privacy}","received_events_url":"https://api.github.com/users/wyndon/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-13T12:49:07Z","updated_at":"2022-02-13T12:49:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nOneDev is a Super Easy All-In-One DevOps Platform with Git Management, Issue Tracking, and CI/CD. Simple yet Powerful.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://code.onedev.io/projects/160\r\n* source URL: https://code.onedev.io/projects/160\r\n* license: MIT\r\n* platforms: unix","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159837/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159623","id":1134453226,"node_id":"I_kwDOAEVQ_M5DnmHq","number":159623,"title":"boot entries broken, ignoring generation 'None'","user":{"login":"orangecms","id":4245199,"node_id":"MDQ6VXNlcjQyNDUxOTk=","avatar_url":"https://avatars.githubusercontent.com/u/4245199?v=4","gravatar_id":"","url":"https://api.github.com/users/orangecms","html_url":"https://github.com/orangecms","followers_url":"https://api.github.com/users/orangecms/followers","following_url":"https://api.github.com/users/orangecms/following{/other_user}","gists_url":"https://api.github.com/users/orangecms/gists{/gist_id}","starred_url":"https://api.github.com/users/orangecms/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/orangecms/subscriptions","organizations_url":"https://api.github.com/users/orangecms/orgs","repos_url":"https://api.github.com/users/orangecms/repos","events_url":"https://api.github.com/users/orangecms/events{/privacy}","received_events_url":"https://api.github.com/users/orangecms/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-12T19:02:07Z","updated_at":"2022-02-28T07:53:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Previously filed as https://github.com/NixOS/nix/issues/6076\r\n\r\n**Describe the bug**\r\n\r\nWhen running `nix-rebuild`, it prints a bunch of `ignoring generation 'None'`.\r\n\r\nNo new boot entries are being created.\r\n\r\n**Steps To Reproduce**\r\n\r\nrun `sudo nixos-rebuild switch --upgrade`\r\n\r\n```\r\nignoring generation 'None' in the list of boot entries because of the following error:\r\n65\r\nignoring generation 'None' in the list of boot entries because of the following error:\r\n66\r\nignoring generation 'None' in the list of boot entries because of the following error:\r\n67\r\n```\r\nand so on...\r\n\r\n**Expected behavior**\r\n### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n\r\nit should create new boot entries\r\n\r\n**`nix-env --version` output**\r\n\r\n2.6.0\r\n\r\n**Additional context**\r\n\r\nin `/boot/loader/entries/`, there is a bunch of empty files like `nixos-generation-65.conf.tmp`.\r\n\r\nI figure out that `/boot/` is full by trying to write the entries manually. `nixos-upgrade` should figure that out and give feedback with advice on cleaning up kernels.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159623/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159612","id":1134410727,"node_id":"I_kwDOAEVQ_M5Dnbvn","number":159612,"title":"Current GNOME ISO exceeds Hydra output limit on Hydra ","user":{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"},{"id":253381966,"node_id":"MDU6TGFiZWwyNTMzODE5NjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20closure-size","name":"6.topic: closure-size","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":44,"created_at":"2022-02-12T18:28:54Z","updated_at":"2022-03-12T00:47:47Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe GNOME ISO job currently fails bcause it's output exceeds the configured output limit on Hydra: <https://hydra.nixos.org/build/167219646>, eventually preventing nixos-unstable from advancing.\r\n\r\nI'm not sure what caused this, ~~presumably the last staging-next rotation~~?\r\n\r\ncc @NixOS/gnome \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159612/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159569","id":1134169427,"node_id":"I_kwDOAEVQ_M5Dmg1T","number":159569,"title":"buildGoModule: Unable to override `vendorSha256` when specified as `null`","user":{"login":"ShamrockLee","id":44064051,"node_id":"MDQ6VXNlcjQ0MDY0MDUx","avatar_url":"https://avatars.githubusercontent.com/u/44064051?v=4","gravatar_id":"","url":"https://api.github.com/users/ShamrockLee","html_url":"https://github.com/ShamrockLee","followers_url":"https://api.github.com/users/ShamrockLee/followers","following_url":"https://api.github.com/users/ShamrockLee/following{/other_user}","gists_url":"https://api.github.com/users/ShamrockLee/gists{/gist_id}","starred_url":"https://api.github.com/users/ShamrockLee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ShamrockLee/subscriptions","organizations_url":"https://api.github.com/users/ShamrockLee/orgs","repos_url":"https://api.github.com/users/ShamrockLee/repos","events_url":"https://api.github.com/users/ShamrockLee/events{/privacy}","received_events_url":"https://api.github.com/users/ShamrockLee/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":337081580,"node_id":"MDU6TGFiZWwzMzcwODE1ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20golang","name":"6.topic: golang","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-12T15:14:36Z","updated_at":"2022-03-22T10:24:47Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTo package a Go module from vendored source (source with a folder named `vendor` at the project root containing stuff fetched from the packaging system of Go) using `buildGoModule`, one pass `vendorSha256` to it, making the output package's `go-module`\r\n become an empty string (`\"\"`) instead of a derivation. When someone else want to override the package to make it build from an non-vendored source, she/he needs to provide the `vendorSha256`, but trying to pass it through `overrideAttrs` attribute doesn't work, nor does passing `overrideModAttrs`.\r\n\r\nA workaround is passing the `vendorSha256`-related arguments through the parameter of the build function of the package.\r\n\r\nOverlay-style overridable mkDerivation might be (one of) the ultimate solution (#119942), but it still has a long way to go.\r\n\r\nSee #158486 and https://github.com/ShamrockLee/nixpkgs/blob/singularity-apptainer/pkgs/applications/virtualization/singularity/template.nix for an example.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Fetch `apptainer` from #158486 \r\n2. See the `apptainer.go-module` in `nix repl` or by `nix eval`, it would be `\"\"` instead of a derivation.\r\n3. Override `src` through `apptainer.overrideAttrs` to use the master branch of https://github.com/apptainer/apptainer (using flake or`fetchFromGitHub`)\r\n4. Override `vendorSha256` as `lib.fakeSha256` through `apptainer.overrideAttrs`\r\n5. See `apptainer.go-module`. A derivation is expected, but it turns out to be `\"\"`.\r\n6. As this package created by #158486 applies the workaround mentioned above, one can override `vendorSha256` using `appimage.override`. Afterward, `.go-module` should now returns a derivation.\r\n\r\n### Expected behavior\r\nThere should be a way for users to override `vendorSha256` when it is initially specified as `null`. If it isn't through `overrideAttrs`, it should be documented.\r\n\r\n\r\n\r\n<!-- ### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n-->\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@kalbasit\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.73, NixOS, 21.05.20211019.8fe3b97 (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159569/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159521","id":1133951629,"node_id":"I_kwDOAEVQ_M5DlrqN","number":159521,"title":"`python3Packages.elegy` build failure on x86_64-linux as of `19730cdb`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"ndl","id":137805,"node_id":"MDQ6VXNlcjEzNzgwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/137805?v=4","gravatar_id":"","url":"https://api.github.com/users/ndl","html_url":"https://github.com/ndl","followers_url":"https://api.github.com/users/ndl/followers","following_url":"https://api.github.com/users/ndl/following{/other_user}","gists_url":"https://api.github.com/users/ndl/gists{/gist_id}","starred_url":"https://api.github.com/users/ndl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ndl/subscriptions","organizations_url":"https://api.github.com/users/ndl/orgs","repos_url":"https://api.github.com/users/ndl/repos","events_url":"https://api.github.com/users/ndl/events{/privacy}","received_events_url":"https://api.github.com/users/ndl/received_events","type":"User","site_admin":false},"assignees":[{"login":"ndl","id":137805,"node_id":"MDQ6VXNlcjEzNzgwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/137805?v=4","gravatar_id":"","url":"https://api.github.com/users/ndl","html_url":"https://github.com/ndl","followers_url":"https://api.github.com/users/ndl/followers","following_url":"https://api.github.com/users/ndl/following{/other_user}","gists_url":"https://api.github.com/users/ndl/gists{/gist_id}","starred_url":"https://api.github.com/users/ndl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ndl/subscriptions","organizations_url":"https://api.github.com/users/ndl/orgs","repos_url":"https://api.github.com/users/ndl/repos","events_url":"https://api.github.com/users/ndl/events{/privacy}","received_events_url":"https://api.github.com/users/ndl/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-02-12T12:02:43Z","updated_at":"2022-02-13T13:46:09Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"\n## Issue description\nBuild of `python3Packages.elegy` failed on x86_64-linux as of 19730cdb79c8253582428283339ad37de7cf97dd.\n\n[build log](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1833671196)\n\nMaintainer cc: @ndl\nOther cc: n/a\n\n### Steps to reproduce\n1. Checkout nixpkgs at commit 19730cdb79c8253582428283339ad37de7cf97dd\n2. Run `nix-build -A python3Packages.elegy`\n\n## Technical details\n```\n- system: `\"x86_64-linux\"`\n - host os: `Linux 5.11.0-1028-azure, Ubuntu, 20.04.3 LTS (Focal Fossa)`\n - multi-user?: `yes`\n - sandbox: `yes`\n - version: `nix-env (Nix) 2.6.0`\n - nixpkgs: `/nix/store/f78jqkss0z39h2602xrrigzy6g1skpv6-source`\n```\n\n## Misc.\nThis issue was automatically generated by [nixpkgs-upkeep](https://github.com/samuela/nixpkgs-upkeep).\n- [CI workflow](https://github.com/samuela/nixpkgs-upkeep/actions/runs/1833671196) that created this issue.\n- Internal tag: -1708941856498551218\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159521/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159326","id":1133033573,"node_id":"I_kwDOAEVQ_M5DiLhl","number":159326,"title":"Packaging Request: bmc0/dsp","user":{"login":"X9VoiD","id":10338031,"node_id":"MDQ6VXNlcjEwMzM4MDMx","avatar_url":"https://avatars.githubusercontent.com/u/10338031?v=4","gravatar_id":"","url":"https://api.github.com/users/X9VoiD","html_url":"https://github.com/X9VoiD","followers_url":"https://api.github.com/users/X9VoiD/followers","following_url":"https://api.github.com/users/X9VoiD/following{/other_user}","gists_url":"https://api.github.com/users/X9VoiD/gists{/gist_id}","starred_url":"https://api.github.com/users/X9VoiD/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/X9VoiD/subscriptions","organizations_url":"https://api.github.com/users/X9VoiD/orgs","repos_url":"https://api.github.com/users/X9VoiD/repos","events_url":"https://api.github.com/users/X9VoiD/events{/privacy}","received_events_url":"https://api.github.com/users/X9VoiD/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-11T20:00:13Z","updated_at":"2022-02-11T20:00:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n`dsp` is an audio processing program with an interactive mode. Also has a LADSPA frontend.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/bmc0/dsp\r\n* source URL: https://github.com/bmc0/dsp\r\n* license: isc\r\n* platforms: linux","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159326/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159267","id":1132752855,"node_id":"I_kwDOAEVQ_M5DhG_X","number":159267,"title":"Discord renders a black window on Wayland","user":{"login":"Baughn","id":45811,"node_id":"MDQ6VXNlcjQ1ODEx","avatar_url":"https://avatars.githubusercontent.com/u/45811?v=4","gravatar_id":"","url":"https://api.github.com/users/Baughn","html_url":"https://github.com/Baughn","followers_url":"https://api.github.com/users/Baughn/followers","following_url":"https://api.github.com/users/Baughn/following{/other_user}","gists_url":"https://api.github.com/users/Baughn/gists{/gist_id}","starred_url":"https://api.github.com/users/Baughn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Baughn/subscriptions","organizations_url":"https://api.github.com/users/Baughn/orgs","repos_url":"https://api.github.com/users/Baughn/repos","events_url":"https://api.github.com/users/Baughn/events{/privacy}","received_events_url":"https://api.github.com/users/Baughn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-02-11T15:27:32Z","updated_at":"2022-04-29T18:40:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIf you start the standalone (Electron-based) Discord client on Wayland, though possibly only Wayland-on-Nvidia, it renders an entirely black window.\r\n\r\nThis is not nixos-specific. Various workarounds are posted around the internet; the ones that work best are to run it with --disable-gpu, or (preferrably) --use-gl=desktop. I don't know what implications would come of making the second one the default.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix run nixpkgs#discord\r\n\r\n### Expected behavior\r\nThe discord window should render. ;-)\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@ldesgoui @MP2E @devins2518\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.16-lqx2, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `relaxed`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(svein): `\"\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159267/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159179","id":1132123253,"node_id":"I_kwDOAEVQ_M5DetR1","number":159179,"title":"inkcut: crashes when picking up invalid libs from PYTHONPATH","user":{"login":"raboof","id":131856,"node_id":"MDQ6VXNlcjEzMTg1Ng==","avatar_url":"https://avatars.githubusercontent.com/u/131856?v=4","gravatar_id":"","url":"https://api.github.com/users/raboof","html_url":"https://github.com/raboof","followers_url":"https://api.github.com/users/raboof/followers","following_url":"https://api.github.com/users/raboof/following{/other_user}","gists_url":"https://api.github.com/users/raboof/gists{/gist_id}","starred_url":"https://api.github.com/users/raboof/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/raboof/subscriptions","organizations_url":"https://api.github.com/users/raboof/orgs","repos_url":"https://api.github.com/users/raboof/repos","events_url":"https://api.github.com/users/raboof/events{/privacy}","received_events_url":"https://api.github.com/users/raboof/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-11T08:58:53Z","updated_at":"2022-02-11T10:13:53Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`inkcut` currently uses Python 3.9.\r\n\r\nHowever, when running it with Python 3.10 libraries on the PYTHONPATH, it will pick those up and crash. It should probably ignore the PYTHONPATH.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p inkcut python310Packages.atom`\r\n2. `inkcut`\r\n\r\nThis gives:\r\n\r\n```\r\nLogging to /home/aengelen/.config/inkcut/logs/inkcut.txt\r\n2022-02-11 09:52:40,451 | INFO | inkcut | ========================================\r\n2022-02-11 09:52:40,451 | INFO | inkcut | Inkcut launched\r\n2022-02-11 09:52:40,451 | INFO | inkcut | Version: 2.1.3\r\n2022-02-11 09:52:40,452 | INFO | inkcut | Python: 3.9.9 (main, Nov 15 2021, 18:05:17) \r\n[GCC 10.3.0]\r\n2022-02-11 09:52:40,452 | INFO | inkcut | System: uname_result(system='Linux', node='rigter', release='5.16.3', version='#1-NixOS SMP PREEMPT Thu Jan 27 11:03:05 UTC 2022', machine='x86_64')\r\n2022-02-11 09:52:40,452 | INFO | inkcut | Executable: /nix/store/x24kxyqwqg2ln8kh9ky342kdcmhbng3h-python3-3.9.9/bin/python3.9\r\n2022-02-11 09:52:40,452 | INFO | inkcut | Args: ['/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/bin/inkcut']\r\n2022-02-11 09:52:40,469 | INFO | inkcut | Qt: 5.15.3 Api:\r\n2022-02-11 09:52:40,469 | INFO | inkcut | ========================================\r\n2022-02-11 09:52:40,473 | ERROR | inkcut | Traceback (most recent call last):\r\n File \"/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/lib/python3.9/site-packages/inkcut/app.py\", line 97, in main\r\n from inkcut.core.workbench import InkcutWorkbench\r\n File \"/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/lib/python3.9/site-packages/inkcut/core/workbench.py\", line 20, in <module>\r\n from atom.api import Str, Instance\r\n File \"/nix/store/ppk8s3dlsbsqnsl76fblwn0b9b55ph6j-python3.10-atom-0.7.0/lib/python3.10/site-packages/atom/api.py\", line 11, in <module>\r\n from .atom import AtomMeta, Atom, observe, set_default\r\n File \"/nix/store/ppk8s3dlsbsqnsl76fblwn0b9b55ph6j-python3.10-atom-0.7.0/lib/python3.10/site-packages/atom/atom.py\", line 13, in <module>\r\n from .catom import (\r\nModuleNotFoundError: No module named 'atom.catom'\r\n\r\nTraceback (most recent call last):\r\n File \"/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/bin/.inkcut-wrapped\", line 9, in <module>\r\n sys.exit(main())\r\n File \"/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/lib/python3.9/site-packages/inkcut/app.py\", line 97, in main\r\n from inkcut.core.workbench import InkcutWorkbench\r\n File \"/nix/store/ydxrj57cldsfmma0s86l57dqlmmzcbn2-inkcut-2.1.3/lib/python3.9/site-packages/inkcut/core/workbench.py\", line 20, in <module>\r\n from atom.api import Str, Instance\r\n File \"/nix/store/ppk8s3dlsbsqnsl76fblwn0b9b55ph6j-python3.10-atom-0.7.0/lib/python3.10/site-packages/atom/api.py\", line 11, in <module>\r\n from .atom import AtomMeta, Atom, observe, set_default\r\n File \"/nix/store/ppk8s3dlsbsqnsl76fblwn0b9b55ph6j-python3.10-atom-0.7.0/lib/python3.10/site-packages/atom/atom.py\", line 13, in <module>\r\n from .catom import (\r\nModuleNotFoundError: No module named 'atom.catom'\r\n```\r\n\r\nNote the /nix/store/ppk8s3dlsbsqnsl76fblwn0b9b55ph6j-python3.10-atom-0.7.0 in the stack trace: it's likely picking those up from the `PYTHONPATH` of the shell.\r\n\r\n### Expected behavior\r\n\r\nInkcut would start, ignoring the PYTHONPATH\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.3, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos-20.03pre194293.2436c27541b\"`\r\n - nixpkgs: `/home/aengelen/nixpkgs`\r\n```\r\n\r\nnixpkgs at 98bb5b77c8c6666824a4c13d23befa1e07210ef1","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159179/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159120","id":1131550964,"node_id":"I_kwDOAEVQ_M5Dchj0","number":159120,"title":"neko fails to build on aarch64-darwin (M1 macOS)","user":{"login":"boronine","id":93469,"node_id":"MDQ6VXNlcjkzNDY5","avatar_url":"https://avatars.githubusercontent.com/u/93469?v=4","gravatar_id":"","url":"https://api.github.com/users/boronine","html_url":"https://github.com/boronine","followers_url":"https://api.github.com/users/boronine/followers","following_url":"https://api.github.com/users/boronine/following{/other_user}","gists_url":"https://api.github.com/users/boronine/gists{/gist_id}","starred_url":"https://api.github.com/users/boronine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/boronine/subscriptions","organizations_url":"https://api.github.com/users/boronine/orgs","repos_url":"https://api.github.com/users/boronine/repos","events_url":"https://api.github.com/users/boronine/events{/privacy}","received_events_url":"https://api.github.com/users/boronine/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-11T02:54:28Z","updated_at":"2022-02-11T05:00:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nneko fails to build on aarch64-darwin. The error is:\r\n```\r\nerror: unknown target CPU 'armv8.3-a+crypto+sha2+aes+crc+fp16+lse+simd+ras+rdm+rcpc'\r\n```\r\n\r\naarch64-darwin support is WIP in neko: https://github.com/HaxeFoundation/neko/pull/224 Once that PR is merged and a new release of neko is made, we should be able to fix this issue by bumping the neko version in nixpkgs. This should also unblock Haxe on aarch64-darwin as that depends on neko.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```\r\nnix-shell -p neko\r\n```\r\n\r\n### Expected behavior\r\nExpecting the package to build\r\n\r\n### Notify maintainers\r\n@marcweber @locallycompact\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\nalexei@m1 hsluv % nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(alexei): `\"nixpkgs-21.11pre325289.f790fcd0bea\"`\r\n - nixpkgs: `/Users/alexei/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159120/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159106","id":1131447149,"node_id":"I_kwDOAEVQ_M5DcINt","number":159106,"title":"webbot","user":{"login":"R4Ajeti","id":19622120,"node_id":"MDQ6VXNlcjE5NjIyMTIw","avatar_url":"https://avatars.githubusercontent.com/u/19622120?v=4","gravatar_id":"","url":"https://api.github.com/users/R4Ajeti","html_url":"https://github.com/R4Ajeti","followers_url":"https://api.github.com/users/R4Ajeti/followers","following_url":"https://api.github.com/users/R4Ajeti/following{/other_user}","gists_url":"https://api.github.com/users/R4Ajeti/gists{/gist_id}","starred_url":"https://api.github.com/users/R4Ajeti/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/R4Ajeti/subscriptions","organizations_url":"https://api.github.com/users/R4Ajeti/orgs","repos_url":"https://api.github.com/users/R4Ajeti/repos","events_url":"https://api.github.com/users/R4Ajeti/events{/privacy}","received_events_url":"https://api.github.com/users/R4Ajeti/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-11T01:46:33Z","updated_at":"2022-02-11T01:46:33Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Web automation library for python for web browser automation and end to end UI testing.\r\n\r\nwebbot provides a much feature rich automation than selenium for all kinds of automation of webpage. Since the major portion of web automation is to perform actions like click and type into webpage elements , webbot automatically handles finding the right elements to perform the actions.\r\n\r\n\r\n* homepage URL: https://pypi.org/project/webbot/\r\n* source URL: https://github.com/nateshmbhat/webbot\r\n* license: mit\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159106/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159082","id":1131254523,"node_id":"I_kwDOAEVQ_M5DbZL7","number":159082,"title":"nixos-rebuild with remote target fails due to lack of valid signature","user":{"login":"felschr","id":3314323,"node_id":"MDQ6VXNlcjMzMTQzMjM=","avatar_url":"https://avatars.githubusercontent.com/u/3314323?v=4","gravatar_id":"","url":"https://api.github.com/users/felschr","html_url":"https://github.com/felschr","followers_url":"https://api.github.com/users/felschr/followers","following_url":"https://api.github.com/users/felschr/following{/other_user}","gists_url":"https://api.github.com/users/felschr/gists{/gist_id}","starred_url":"https://api.github.com/users/felschr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/felschr/subscriptions","organizations_url":"https://api.github.com/users/felschr/orgs","repos_url":"https://api.github.com/users/felschr/repos","events_url":"https://api.github.com/users/felschr/events{/privacy}","received_events_url":"https://api.github.com/users/felschr/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-10T23:42:19Z","updated_at":"2022-04-16T11:02:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nTrying to upgrade a remote machine fails with the following output:\r\n```sh\r\n$ sudo nixos-rebuild switch --flake '/etc/nixos/#felix-rpi4' --target-host user@host --use-remote-sudo\r\nbuilding the system configuration...\r\nwarning: Git tree '/etc/nixos' is dirty\r\ncopying 141 paths...\r\ncopying path '/nix/store/05rrbmrxpfmb4pj5i9wj2h6q5kbklw3z-system-shutdown' to 'ssh://user@host'...\r\nerror: cannot add path '/nix/store/05rrbmrxpfmb4pj5i9wj2h6q5kbklw3z-system-shutdown' because it lacks a valid signature\r\nerror: unexpected end-of-file\r\n```\r\n\r\n### Steps To Reproduce\r\nSee sample code above.\r\n\r\n### Expected behavior\r\nRemote deployment should succeed.\r\n\r\n### Additional context\r\nMy build system is `x86_64` and the target is `aarch64`. Both systems use flakes.\r\nI've enabled cross-compilation on the build system via `boot.binfmt.emulatedSystems = [ \"aarch64-linux\" ];`.\r\nThus far I've updated the remote machine by itself, but the rebuilds are sometimes quite slow on it (raspberry pi 4). That's why I'd like to build it on my desktop computer which is much faster.\r\n\r\n### Metadata\r\nbuild system:\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - nixpkgs: `/nix/store/zwbw7dknw89ai257hicmwv8lhid3qb62-source`\r\n```\r\n\r\ntarget system:\r\n```\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.10.52, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220127_558c4ee`\r\n - channels(root): `\"nixos-21.05pre275232.29b0d4d0b60\"`\r\n - nixpkgs: `/nix/store/pi099gbqmvjaqk6d77c9r9g08mm70w8b-source`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159082/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159066","id":1131141992,"node_id":"I_kwDOAEVQ_M5Da9to","number":159066,"title":"Add unikraft build tool","user":{"login":"chrisportela","id":505649,"node_id":"MDQ6VXNlcjUwNTY0OQ==","avatar_url":"https://avatars.githubusercontent.com/u/505649?v=4","gravatar_id":"","url":"https://api.github.com/users/chrisportela","html_url":"https://github.com/chrisportela","followers_url":"https://api.github.com/users/chrisportela/followers","following_url":"https://api.github.com/users/chrisportela/following{/other_user}","gists_url":"https://api.github.com/users/chrisportela/gists{/gist_id}","starred_url":"https://api.github.com/users/chrisportela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/chrisportela/subscriptions","organizations_url":"https://api.github.com/users/chrisportela/orgs","repos_url":"https://api.github.com/users/chrisportela/repos","events_url":"https://api.github.com/users/chrisportela/events{/privacy}","received_events_url":"https://api.github.com/users/chrisportela/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-10T22:35:13Z","updated_at":"2022-02-10T22:35:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nUnikraft is a fast, secure and open-source Unikernel Development Kit\r\n\r\nBy tailoring the operating system, libraries and configuration to the particular needs of your application, it vastly reduces virtual machine and container image sizes to a few KBs, provides blazing performance, and drastically cuts down your software stack’s attack surface.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://unikraft.org/\r\n* source URL: (unikraft itself) https://github.com/unikraft/unikraft / (kraft build tool) https://github.com/unikraft/kraft/\r\n* license: mostly bsd, some parts gpl2\r\n* platforms: linux\r\n\r\nKraft is a python3 application.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159066/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159038","id":1130961339,"node_id":"I_kwDOAEVQ_M5DaRm7","number":159038,"title":"kernel module from package chipsec missing from modprobable dir","user":{"login":"orangecms","id":4245199,"node_id":"MDQ6VXNlcjQyNDUxOTk=","avatar_url":"https://avatars.githubusercontent.com/u/4245199?v=4","gravatar_id":"","url":"https://api.github.com/users/orangecms","html_url":"https://github.com/orangecms","followers_url":"https://api.github.com/users/orangecms/followers","following_url":"https://api.github.com/users/orangecms/following{/other_user}","gists_url":"https://api.github.com/users/orangecms/gists{/gist_id}","starred_url":"https://api.github.com/users/orangecms/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/orangecms/subscriptions","organizations_url":"https://api.github.com/users/orangecms/orgs","repos_url":"https://api.github.com/users/orangecms/repos","events_url":"https://api.github.com/users/orangecms/events{/privacy}","received_events_url":"https://api.github.com/users/orangecms/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-10T21:02:15Z","updated_at":"2022-02-10T23:09:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen installing `chipsec` and adding the module to `boot.extraModulePackages`, the module with the Python libs ends up in `/run/booted-system/kernel-modules/lib/python3.9/site-packages/drivers/linux/chipsec.ko`. It's not in `/.../kernel-modules/lib/modules/...`, so `modprobe` doesn't find it.\r\n\r\n### Steps To Reproduce\r\n\r\nWhen running e.g. `sudo chipsec_util reg read RomProtect0`, it yields\r\n```\r\nERROR: Message: \"Cannot find chipsec.ko module\"\r\n```\r\n\r\nThe same message is printed when `insmod`ding manually. Does chipsec try to reload it? No clue.\r\n\r\n### Expected behavior\r\n\r\nmodule should be found\r\n\r\n### Notify maintainers\r\n\r\n@JohnAZoidberg 👋 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n\r\nSorry, too much to type, I do not log into GitHub on the machine I'm running NixOS on. Summary:\r\n\r\nnix-env 2.6.0\r\nNixOS 22.05 Quokka\r\nLinux 5.16.7 x86","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159038/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029/events","html_url":"https://github.com/NixOS/nixpkgs/issues/159029","id":1130882141,"node_id":"I_kwDOAEVQ_M5DZ-Rd","number":159029,"title":"Request to add SoundConverter package","user":{"login":"NoraCodes","id":3290365,"node_id":"MDQ6VXNlcjMyOTAzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/3290365?v=4","gravatar_id":"","url":"https://api.github.com/users/NoraCodes","html_url":"https://github.com/NoraCodes","followers_url":"https://api.github.com/users/NoraCodes/followers","following_url":"https://api.github.com/users/NoraCodes/following{/other_user}","gists_url":"https://api.github.com/users/NoraCodes/gists{/gist_id}","starred_url":"https://api.github.com/users/NoraCodes/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NoraCodes/subscriptions","organizations_url":"https://api.github.com/users/NoraCodes/orgs","repos_url":"https://api.github.com/users/NoraCodes/repos","events_url":"https://api.github.com/users/NoraCodes/events{/privacy}","received_events_url":"https://api.github.com/users/NoraCodes/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-10T20:24:00Z","updated_at":"2022-02-10T20:24:00Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**SoundConverter**\r\n_A GNOME application which provides a graphical interface for converting many audio files between formats in parallel._\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://soundconverter.org/\r\n* source URL: https://github.com/kassoulet/soundconverter (or https://launchpad.net/soundconverter/trunk )\r\n* license: gpl3\r\n* platforms: linux, gnome\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/159029/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158988","id":1130424578,"node_id":"I_kwDOAEVQ_M5DYOkC","number":158988,"title":"doas ignores environment variables set up in PAM, leading to many issues on NixOS","user":{"login":"PaulGrandperrin","id":1748936,"node_id":"MDQ6VXNlcjE3NDg5MzY=","avatar_url":"https://avatars.githubusercontent.com/u/1748936?v=4","gravatar_id":"","url":"https://api.github.com/users/PaulGrandperrin","html_url":"https://github.com/PaulGrandperrin","followers_url":"https://api.github.com/users/PaulGrandperrin/followers","following_url":"https://api.github.com/users/PaulGrandperrin/following{/other_user}","gists_url":"https://api.github.com/users/PaulGrandperrin/gists{/gist_id}","starred_url":"https://api.github.com/users/PaulGrandperrin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PaulGrandperrin/subscriptions","organizations_url":"https://api.github.com/users/PaulGrandperrin/orgs","repos_url":"https://api.github.com/users/PaulGrandperrin/repos","events_url":"https://api.github.com/users/PaulGrandperrin/events{/privacy}","received_events_url":"https://api.github.com/users/PaulGrandperrin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-10T16:31:14Z","updated_at":"2022-02-10T16:48:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## The initial weird bug\r\nI wanted to set my time locale to ISO-8601, so I did:\r\n\r\n```nix\r\ni18n.extraLocaleSettings.LC_TIME = \"en_DK.UTF-8\"; # yes, that means ISO-8601 ;-)\r\n```\r\n\r\nbut then, using `doas` to get `root` printed some warnings\r\n```\r\n$ doas -s \r\n/nix/store/4qnbxbg1v7b51vgfpmbxkv35mh1vn7bh-set-environment: line 14: warning: setlocale: LC_TIME: cannot change locale (en_DK.UTF-8): No such file or directory\r\n#\r\n```\r\n\r\nbut `date` in that root shell was using the correct locale\r\n```\r\n$ date\r\n2022-02-10T15:27:12 CET\r\n```\r\n\r\nI still investigated a bit and found that `doas date` did not use the correct locale !???\r\n```\r\n$ doas date\r\nThu Feb 10 15:30:00 CET 2022\r\n```\r\n\r\nAfter spending way too many hours troubleshooting this mystery, I finally found the root cause: https://github.com/Duncaen/OpenDoas/issues/2. It can also lead to many others difficult to understand issues..\r\n\r\n## Explanations\r\n\r\nNixOS relies on some environment variables to be set to work properly.\r\nFor example, `PATH` must include `/run/wrappers/bin` for SUID bins, `/run/current-system/sw/bin` for system bins and `/etc/profiles/per-user/$USER/bin` for user bins.\r\nWe'll come back to `PATH` later.\r\n\r\nAnother important one is `LOCALE_ARCHIVE`, which is used by Nixpkgs' [patched](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/libraries/glibc/nix-locale-archive.patch) `glibc` to find which locale archive to load.\r\nBasically, the [patch](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/libraries/glibc/nix-locale-archive.patch) first tries to lookup `LOCALE_ARCHIVE` and if unsuccessful, loads a basic archive with only the \"C/POSIX\" locale available.\r\n(more info can be found here also: https://github.com/NixOS/nixpkgs/issues/85823)\r\n\r\nTo ensure that they are set everywhere, NixOS configures PAM to include them in all new sessions:\r\nhttps://github.com/NixOS/nixpkgs/blob/nixos-21.11/nixos/modules/config/system-environment.nix#L68\r\nhttps://github.com/NixOS/nixpkgs/blob/nixos-21.11/nixos/modules/security/pam.nix#L573\r\n\r\nUnfortunately `doas` ignore those: https://github.com/Duncaen/OpenDoas/issues/2.\r\n\r\nThis makes binaries started with `doas` behave incorrectly on NixOS:\r\n- If it's a shell, the `locale-archive` will fail to load and fall back to a basic one. However, login shells also source `/etc/set-environment` which also load those variables. This doesn't solve the locale issue for the shell because the locale-archive is loaded only at startup time but it makes programs started from the shell behave correctly.\r\n- If it's a command, many variables will be missing, including `LOCALE_ARCHIVE`, the user env in `PATH` (`/etc/profiles/per-user/$USER/bin`), `NIX_PATH`, the XDG vars, `INFOPATH`, `LD_LIBRARY_PATH` and many others. Right now the `PATH` has some nix-specific paths thanks to this patch: https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/tools/security/doas/0001-add-NixOS-specific-dirs-to-safe-PATH.patch\r\n\r\nFor example, on my machine, `git` is installed through home-manager and so is in `/etc/profiles/per-user/$USER/bin`. \r\nScripts launched with `doas` will not find `git`.\r\n```\r\n$ doas ruby -e 'puts `git`' \r\nTraceback (most recent call last):\r\n\t1: from -e:1:in `<main>'\r\n-e:1:in ``': No such file or directory - git (Errno::ENOENT)\r\n\r\n$ sudo ruby -e 'puts `git`' \r\nusage: git [--version] [--help] [-C <path>] [-c <name>=<value>]\r\n [--exec-path[=<path>]] [--html-path] [--man-path] [--info-path]\r\n [-p | --paginate | -P | --no-pager] [--no-replace-objects] [--bare]\r\n [--git-dir=<path>] [--work-tree=<path>] [--namespace=<name>]\r\n [--super-prefix=<path>] [--config-env=<name>=<envvar>]\r\n <command> [<args>]\r\n...\r\n```\r\n\r\nThey'll also fail to load any locale.\r\n\r\n## Comparing with sudo\r\n\r\n```\r\n$ doas ruby -e 'ENV.each {|k,v| puts \"#{k}=#{v}\"};' \r\nDISPLAY=:0\r\nDOAS_USER=paulg\r\nHOME=/root\r\nLOGNAME=root\r\nPATH=/bin:/sbin:/usr/bin:/usr/sbin:/run/wrappers/bin:/run/current-system/sw/bin:/run/current-system/sw/sbin:/usr/local/bin:/usr/local/sbin\r\nSHELL=/run/current-system/sw/bin/fish\r\nSSH_AUTH_SOCK=/run/user/1000/keyring/ssh\r\nTERM=xterm-256color\r\nTERMINFO_DIRS=/home/paulg/.nix-profile/share/terminfo:/etc/profiles/per-user/paulg/share/terminfo:/nix/var/nix/profiles/default/share/terminfo:/run/current-system/sw/share/terminfo\r\nUSER=root\r\n```\r\n\r\n```\r\n$ sudo ruby -e 'ENV.each {|k,v| puts \"#{k}=#{v}\"};' \r\nLANG=en_US.UTF-8\r\nXAUTHORITY=/run/user/1000/.mutter-Xwaylandauth.LWUIH1\r\nPATH=/nix/store/2c9w4p2x6x0l64fdvcmc11app7x4xran-python3-3.9.6/bin:/nix/store/jqnrfnvn02lhh5qgpn6s6mlr4972fw5s-terminator-2.1.1/bin:/nix/store/7d5h782gxrvcwryzybx4jhh2fb4jpqsh-cairo-1.16.0-dev/bin:/nix/store/7rhxra449n5k56yfz25dvksj09rhmir8-freetype-2.11.0-dev/bin:/nix/store/fzl3is02f0lhqzcdx7v22wyi6d0maj4a-bzip2-1.0.6.0.2-bin/bin:/nix/store/7zsf9zcywvxvq6krgljrr7km3hsbls6s-libpng-apng-1.6.37-dev/bin:/nix/store/brl5wr9r4p1k5f57ysrivdilc4iqkf82-fontconfig-2.13.94-bin/bin:/nix/store/aa46grxlz348yf1lcqjmlxf1cz1fvnsp-expat-2.4.3-dev/bin:/nix/store/8v697gb948563iznn9g70ijbifaza34y-glib-2.70.1-dev/bin:/nix/store/7rhf667rkqhcljcyz9b9mrzjw1sh3qji-gettext-0.21/bin:/nix/store/wys2ank0vwrjf3zi751m3lcp9c6g0hxc-glib-2.70.1-bin/bin:/run/wrappers/bin:/etc/profiles/per-user/paulg/bin:/run/current-system/sw/bin:/home/paulg/.nix-profile/bin:/home/paulg/.nix-profile/bin:/nix/var/nix/profiles/default/bin\r\nTERMINFO_DIRS=/home/paulg/.nix-profile/share/terminfo:/etc/profiles/per-user/paulg/share/terminfo:/nix/var/nix/profiles/default/share/terminfo:/run/current-system/sw/share/terminfo\r\nLC_MONETARY=fr_FR.UTF-8\r\nLC_MEASUREMENT=en_DK.UTF-8\r\nLC_TIME=en_DK.UTF-8\r\nDISPLAY=:0\r\nSSH_AUTH_SOCK=/run/user/1000/keyring/ssh\r\nCOLORTERM=truecolor\r\nTERM=xterm-256color\r\nMAIL=/var/mail/root\r\nLOGNAME=root\r\nUSER=root\r\nHOME=/root\r\nSHELL=/run/current-system/sw/bin/fish\r\nSUDO_COMMAND=/etc/profiles/per-user/paulg/bin/ruby -e ENV.each {|k,v| puts \"#{k}=#{v}\"};\r\nSUDO_USER=paulg\r\nSUDO_UID=1000\r\nSUDO_GID=100\r\nGTK_PATH=/root/.nix-profile/lib/gtk-2.0:/root/.nix-profile/lib/gtk-3.0:/etc/profiles/per-user/root/lib/gtk-2.0:/etc/profiles/per-user/root/lib/gtk-3.0:/nix/var/nix/profiles/default/lib/gtk-2.0:/nix/var/nix/profiles/default/lib/gtk-3.0:/run/current-system/sw/lib/gtk-2.0:/run/current-system/sw/lib/gtk-3.0\r\nINFOPATH=/root/.nix-profile/info:/root/.nix-profile/share/info:/etc/profiles/per-user/root/info:/etc/profiles/per-user/root/share/info:/nix/var/nix/profiles/default/info:/nix/var/nix/profiles/default/share/info:/run/current-system/sw/info:/run/current-system/sw/share/info\r\nKDEDIRS=/root/.nix-profile:/etc/profiles/per-user/root:/nix/var/nix/profiles/default:/run/current-system/sw\r\nLD_LIBRARY_PATH=/nix/store/cr3mzb6gi2h94ah58yr64s0w78zsazp5-pipewire-0.3.40-jack/lib\r\nLIBEXEC_PATH=/root/.nix-profile/lib/libexec:/etc/profiles/per-user/root/lib/libexec:/nix/var/nix/profiles/default/lib/libexec:/run/current-system/sw/lib/libexec\r\nLIBVA_DRIVER_NAME=iHD\r\nLOCALE_ARCHIVE=/run/current-system/sw/lib/locale/locale-archive\r\nMOZ_PLUGIN_PATH=/root/.nix-profile/lib/mozilla/plugins:/etc/profiles/per-user/root/lib/mozilla/plugins:/nix/var/nix/profiles/default/lib/mozilla/plugins:/run/current-system/sw/lib/mozilla/plugins\r\nNAUTILUS_EXTENSION_DIR=/nix/store/nma7q20asrr2rmydxi8v3fcx077p7zwm-system-path/lib/nautilus/extensions-3.0\r\nNIX_GSETTINGS_OVERRIDES_DIR=/nix/store/56dmq50if1d3cgmrzjkqvk30967jbnf5-nixos-gsettings-desktop-schemas/share/gsettings-schemas/nixos-gsettings-overrides/glib-2.0/schemas\r\nNIX_PATH=nixpkgs=/nix/var/nix/profiles/per-user/root/channels/nixos:nixos-config=/etc/nixos/configuration.nix:/nix/var/nix/profiles/per-user/root/channels\r\nQTWEBKIT_PLUGIN_PATH=/root/.nix-profile/lib/mozilla/plugins/:/etc/profiles/per-user/root/lib/mozilla/plugins/:/nix/var/nix/profiles/default/lib/mozilla/plugins/:/run/current-system/sw/lib/mozilla/plugins/\r\nQT_PLUGIN_PATH=/root/.nix-profile/lib/qt4/plugins:/root/.nix-profile/lib/kde4/plugins:/etc/profiles/per-user/root/lib/qt4/plugins:/etc/profiles/per-user/root/lib/kde4/plugins:/nix/var/nix/profiles/default/lib/qt4/plugins:/nix/var/nix/profiles/default/lib/kde4/plugins:/run/current-system/sw/lib/qt4/plugins:/run/current-system/sw/lib/kde4/plugins\r\nTZDIR=/etc/zoneinfo\r\nVDPAU_DRIVER=va_gl\r\nXCURSOR_PATH=/root/.icons:/root/.local/share/icons:/root/.nix-profile/share/icons:/root/.nix-profile/share/pixmaps:/etc/profiles/per-user/root/share/icons:/etc/profiles/per-user/root/share/pixmaps:/nix/var/nix/profiles/default/share/icons:/nix/var/nix/profiles/default/share/pixmaps:/run/current-system/sw/share/icons:/run/current-system/sw/share/pixmaps\r\nXDG_CONFIG_DIRS=/root/.nix-profile/etc/xdg:/etc/profiles/per-user/root/etc/xdg:/nix/var/nix/profiles/default/etc/xdg:/run/current-system/sw/etc/xdg\r\nXDG_DATA_DIRS=/nix/store/mp04xqq9nbn9qkvbv2sc7qz4v7g28y89-gnome-mimeapps/share:/nix/store/8b34cja46caj1wmagvfgki9qvxsh13ql-desktops/share:/root/.nix-profile/share:/etc/profiles/per-user/root/share:/nix/var/nix/profiles/default/share:/run/current-system/sw/share\r\nXDG_DESKTOP_PORTAL_DIR=/nix/store/4av5fcs8wh753wdrcc6l1f6v26vba31l-xdg-portals/share/xdg-desktop-portal/portals\r\n```\r\n\r\n## Solutions\r\n\r\n### Fix doas\r\n\r\nThe obvious solution is to make `doas` set the vars given by PAM, just like `sudo`. I'll speak with the maintainer referring to this issue.\r\n\r\n### Work around \r\n\r\nSince we control what goes in `/etc/pam/environment `, we can also set them in `/etc/doas.conf`.\r\nIt's an eyesore and can cannot handle variable interpolation like PAM, but here's my workaround:\r\n```nix\r\n setEnv = with lib; let # because of https://github.com/Duncaen/OpenDoas/issues/2 we need to add here all variables that should have been read from PAM_env\r\n # code inspired from https://github.com/NixOS/nixpkgs/blob/nixos-21.11/nixos/modules/config/system-environment.nix#L69\r\n suffixedVariables = \r\n flip mapAttrs config.environment.profileRelativeSessionVariables (envVar: suffixes:\r\n flip concatMap config.environment.profiles (profile:\r\n map (suffix: \"${profile}${suffix}\") suffixes\r\n )\r\n );\r\n suffixedVariablesWithWrappers = (zipAttrsWith (n: concatLists)\r\n [\r\n # Make sure security wrappers are prioritized without polluting\r\n # shell environments with an extra entry. Sessions which depend on\r\n # pam for its environment will otherwise have eg. broken sudo. In\r\n # particular Gnome Shell sometimes fails to source a proper\r\n # environment from a shell.\r\n { PATH = [ config.security.wrapperDir ]; }\r\n\r\n (mapAttrs (n: toList) config.environment.sessionVariables)\r\n suffixedVariables\r\n ]\r\n );\r\n replaceEnvVars = replaceStrings [\"$HOME\" \"$USER\"] [\"/root\" \"root\"];\r\n doasVariable = k: v: ''${k}=${concatStringsSep \":\" (map replaceEnvVars (toList v))}'';\r\n\r\n in mapAttrsToList doasVariable suffixedVariablesWithWrappers;\r\n```\r\n\r\n## Inform the users?\r\n\r\nIn the meantime, I think we should update the docs to warn NixOS users of those shortcomings and workarounds.\r\nThis is especially important because those bugs are difficult to analyze, and it is very unexpected that `doas` ignores PAM env vars.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988/reactions","total_count":4,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":4,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158988/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158970","id":1130144149,"node_id":"I_kwDOAEVQ_M5DXKGV","number":158970,"title":"GitHub runner failing","user":{"login":"kirinnee","id":15990242,"node_id":"MDQ6VXNlcjE1OTkwMjQy","avatar_url":"https://avatars.githubusercontent.com/u/15990242?v=4","gravatar_id":"","url":"https://api.github.com/users/kirinnee","html_url":"https://github.com/kirinnee","followers_url":"https://api.github.com/users/kirinnee/followers","following_url":"https://api.github.com/users/kirinnee/following{/other_user}","gists_url":"https://api.github.com/users/kirinnee/gists{/gist_id}","starred_url":"https://api.github.com/users/kirinnee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kirinnee/subscriptions","organizations_url":"https://api.github.com/users/kirinnee/orgs","repos_url":"https://api.github.com/users/kirinnee/repos","events_url":"https://api.github.com/users/kirinnee/events{/privacy}","received_events_url":"https://api.github.com/users/kirinnee/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null},{"id":84668464,"node_id":"MDU6TGFiZWw4NDY2ODQ2NA==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20reporter%20feedback","name":"9.needs: reporter feedback","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-02-10T14:11:05Z","updated_at":"2022-03-25T06:51:25Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nTrying to configure GitHub runner fails\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start a shell with `github-runner`\r\n ```sh\r\n nix-shell -p github-runner\r\n ```\r\n2. Configure with `github-runner`\r\n ```sh\r\n config.sh\r\n ```\r\n\r\n### Expected behavior\r\nConfigure a Github runner\r\n\r\n### Screenshots\r\nError:\r\n```\r\ntouch: cannot touch '.env': Permission denied\r\n./env.sh: line 37: .path: Permission denied\r\n./env.sh: line 32: .env: Permission denied\r\n./env.sh: line 32: .env: Permission denied\r\nUnhandled exception. System.UnauthorizedAccessException: Access to the path '/nix/store/5mfdyxrakk7vl50szz9pfly1j53vbawr-github-runner-2.287.1/_diag' is denied.\r\n ---> System.IO.IOException: Permission denied\r\n --- End of inner exception stack trace ---\r\n at System.IO.FileSystem.CreateDirectory(String fullPath)\r\n at System.IO.Directory.CreateDirectory(String path)\r\n at GitHub.Runner.Common.HostTraceListener..ctor(String logFileDirectory, String logFilePrefix, Int32 pageSizeLimit, Int32 retentionDays)\r\n at GitHub.Runner.Common.HostContext..ctor(String hostType, String logFile)\r\n at GitHub.Runner.Listener.Program.Main(String[] args)\r\n/nix/store/5mfdyxrakk7vl50szz9pfly1j53vbawr-github-runner-2.287.1/lib/config.sh: line 81: 11937 Aborted\r\n```\r\n### Additional context\r\nUnsure if this is how the Runner is supposed to be used.\r\n\r\n### Notify maintainers\r\n@veehaitch @newAM \r\n\r\n### Metadata\r\n\r\n```console\r\nthis path will be fetched (0.00 MiB download, 0.00 MiB unpacked):\r\n /nix/store/4cx98f94l8a27rn3fgi4c54mvvivvk0z-nix-info\r\ncopying path '/nix/store/4cx98f94l8a27rn3fgi4c54mvvivvk0z-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.4.0-97-generic, Ubuntu, 20.04.3 LTS (Focal Fossa)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158970/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158947","id":1129868668,"node_id":"I_kwDOAEVQ_M5DWG18","number":158947,"title":"element-destkop-wayland: Failed to load GLES library: libGLESv2.so.2","user":{"login":"nixbitcoin","id":45737139,"node_id":"MDQ6VXNlcjQ1NzM3MTM5","avatar_url":"https://avatars.githubusercontent.com/u/45737139?v=4","gravatar_id":"","url":"https://api.github.com/users/nixbitcoin","html_url":"https://github.com/nixbitcoin","followers_url":"https://api.github.com/users/nixbitcoin/followers","following_url":"https://api.github.com/users/nixbitcoin/following{/other_user}","gists_url":"https://api.github.com/users/nixbitcoin/gists{/gist_id}","starred_url":"https://api.github.com/users/nixbitcoin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nixbitcoin/subscriptions","organizations_url":"https://api.github.com/users/nixbitcoin/orgs","repos_url":"https://api.github.com/users/nixbitcoin/repos","events_url":"https://api.github.com/users/nixbitcoin/events{/privacy}","received_events_url":"https://api.github.com/users/nixbitcoin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-10T11:15:54Z","updated_at":"2022-02-10T11:15:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nStarting `element-desktop-wayland` produces the following error message\r\n\r\n```\r\n[38:0210/110747.330884:ERROR:egl_util.cc(74)] Failed to load GLES library: libGLESv2.so.2: libGLESv2.so.2: cannot open shared object file: No such file or directory\r\n[38:0210/110747.340808:ERROR:viz_main_impl.cc(161)] Exiting GPU process due to errors during initialization\r\n[50:0210/110747.385964:ERROR:gpu_init.cc(453)] Passthrough is not supported, GL is swiftshader, ANGLE is\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install `element-desktop-wayland` package\r\n2. Run `element-desktop` from command line\r\n3. See error message in command output and witness slow performance.\r\n\r\n### Expected behavior\r\n`element-desktop-wayland` should use OpenGL under wayland and work smoothly.\r\n\r\n### Additional context\r\nProbably related to https://github.com/siraben/nixpkgs/commit/8faa4ba586c2dec935b23a166305d40044bc2c70\r\n\r\n### Notify maintainers\r\n@ma27 @fadenb @mguentner @ekleog @ralith @mjlbach @dandellion @sumnerevans @wmertens","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158947/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158892","id":1129483906,"node_id":"I_kwDOAEVQ_M5DUo6C","number":158892,"title":"Create patched versions of python packaging tools to avoid version checks","user":{"login":"jonringer","id":7673602,"node_id":"MDQ6VXNlcjc2NzM2MDI=","avatar_url":"https://avatars.githubusercontent.com/u/7673602?v=4","gravatar_id":"","url":"https://api.github.com/users/jonringer","html_url":"https://github.com/jonringer","followers_url":"https://api.github.com/users/jonringer/followers","following_url":"https://api.github.com/users/jonringer/following{/other_user}","gists_url":"https://api.github.com/users/jonringer/gists{/gist_id}","starred_url":"https://api.github.com/users/jonringer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jonringer/subscriptions","organizations_url":"https://api.github.com/users/jonringer/orgs","repos_url":"https://api.github.com/users/jonringer/repos","events_url":"https://api.github.com/users/jonringer/events{/privacy}","received_events_url":"https://api.github.com/users/jonringer/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-10T05:42:08Z","updated_at":"2022-02-10T18:29:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nVersioning within python is usually a determinate to us. Should we just modify the main packaging packages to allow for a `--skip-version-check` option?\r\n\r\ncc @FRidh @mweinelt @fabaff @dotlambda ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158892/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158827","id":1129102561,"node_id":"I_kwDOAEVQ_M5DTLzh","number":158827,"title":"KWinFT: a kwin fork focused on performance, maintance, wayland/wlroots","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-09T22:25:22Z","updated_at":"2022-02-10T17:02:07Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\n>KWinFT (KWin Fast Track) is a robust, fast and versatile yet\r\neasy to use composited window manager for the\r\n[Wayland](https://wayland.freedesktop.org/) and\r\n[X11](https://en.wikipedia.org/wiki/X_Window_System)\r\nwindowing systems on Linux.\r\n\r\n>KWinFT is intended to be used as part of a\r\n[KDE Plasma Desktop](https://kde.org/plasma-desktop/).\r\nThe [KWin](https://en.wikipedia.org/wiki/KWin)FT project is a reboot of KDE's\r\nKWin.\r\nKWinFT differentates itself from KWin in some important aspects:\r\n\r\n>KWinFT values stability and robustness.\r\n>This is achieved through upholding strict development standards\r\nand deploying modern development methods to prevent regressions and code smell.\r\nKWinFT values collaboration with competitors and and upstream partners.\r\n>We want to overcome antiquated notions on community divisions\r\nand work together on the best possible Linux graphics platform.\r\nKWinFT values the knowledge of experts but also the curiosity of beginners.\r\nWell defined and transparent decision processes enable expert knowledge to proliferate\r\nand new contributors to easily find help on their first steps.\r\n\r\n>In the last year our development focus for KWinFT was on the integration with the [wlroots library](https://gitlab.freedesktop.org/wlroots). In a single sentence our goal with this is to share underlying architecture, patterns and ideas across the Wayland ecosystem, instead of reimplementing things again and again for each and every big project while leaving smaller ones behind.\r\n\r\n\r\n\r\n**Metadata**\r\n\r\nrecent release blog post with lots of info: https://subdiff.org/blog/2022/more-wlroots-with-kwinft-524/\r\n\r\n* homepage URL: https://gitlab.com/kwinft/kwinft\r\n* source URL: https://gitlab.com/kwinft/kwinft\r\n* license: gpl2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827/reactions","total_count":3,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":3,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158827/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158809","id":1128848784,"node_id":"I_kwDOAEVQ_M5DSN2Q","number":158809,"title":"iconsur","user":{"login":"tactlessfish","id":29507110,"node_id":"MDQ6VXNlcjI5NTA3MTEw","avatar_url":"https://avatars.githubusercontent.com/u/29507110?v=4","gravatar_id":"","url":"https://api.github.com/users/tactlessfish","html_url":"https://github.com/tactlessfish","followers_url":"https://api.github.com/users/tactlessfish/followers","following_url":"https://api.github.com/users/tactlessfish/following{/other_user}","gists_url":"https://api.github.com/users/tactlessfish/gists{/gist_id}","starred_url":"https://api.github.com/users/tactlessfish/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tactlessfish/subscriptions","organizations_url":"https://api.github.com/users/tactlessfish/orgs","repos_url":"https://api.github.com/users/tactlessfish/repos","events_url":"https://api.github.com/users/tactlessfish/events{/privacy}","received_events_url":"https://api.github.com/users/tactlessfish/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-09T17:49:09Z","updated_at":"2022-02-09T21:20:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n`iconsur` is a command line tool to easily generate macOS Big Sur styled adaptive icons for third-party apps.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/rikumi/iconsur\r\n* source URL: https://github.com/rikumi/iconsur\r\n* license: MIT\r\n* platforms: darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158809/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158794","id":1128729790,"node_id":"I_kwDOAEVQ_M5DRwy-","number":158794,"title":"Error when trying to install displaylink on zen kernel","user":{"login":"macalimlim","id":5382992,"node_id":"MDQ6VXNlcjUzODI5OTI=","avatar_url":"https://avatars.githubusercontent.com/u/5382992?v=4","gravatar_id":"","url":"https://api.github.com/users/macalimlim","html_url":"https://github.com/macalimlim","followers_url":"https://api.github.com/users/macalimlim/followers","following_url":"https://api.github.com/users/macalimlim/following{/other_user}","gists_url":"https://api.github.com/users/macalimlim/gists{/gist_id}","starred_url":"https://api.github.com/users/macalimlim/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/macalimlim/subscriptions","organizations_url":"https://api.github.com/users/macalimlim/orgs","repos_url":"https://api.github.com/users/macalimlim/repos","events_url":"https://api.github.com/users/macalimlim/events{/privacy}","received_events_url":"https://api.github.com/users/macalimlim/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-09T16:02:07Z","updated_at":"2022-02-11T14:24:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nAn error is happening when I'm trying to install displaylink on a zen kernel\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Inside configuration.nix\r\n```\r\nservices.xserver.videoDrivers = [ \"displaylink\" \"modsetting\" ];\r\n```\r\n2. nix-prefetch the displaylink driver from their website\r\n3. Rebuild it\r\n```\r\n# nixos-rebuild switch\r\n```\r\n\r\n### Expected behavior\r\nGetting displaylink driver to be installed and to be used for an Asus portable monitor\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Additional context\r\nIt works fine with the vanilla kernel\r\n\r\n### Notify maintainers\r\n@nshalman \r\n@abbradar \r\n@peterhoeg \r\n@eyJhb \r\n\r\n### Metadata\r\n```console\r\n# nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.3-zen1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335820.521e4d7d13b, nixos-hardware, nixos-unstable-22.05pre351891.fbd030fb2d8\"`\r\n - nixpkgs: `/etc/.nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158794/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158779","id":1128484567,"node_id":"I_kwDOAEVQ_M5DQ07X","number":158779,"title":"Why does it output “:1” that \"echo $DISPLAY\" ?","user":{"login":"prehonor","id":10784632,"node_id":"MDQ6VXNlcjEwNzg0NjMy","avatar_url":"https://avatars.githubusercontent.com/u/10784632?v=4","gravatar_id":"","url":"https://api.github.com/users/prehonor","html_url":"https://github.com/prehonor","followers_url":"https://api.github.com/users/prehonor/followers","following_url":"https://api.github.com/users/prehonor/following{/other_user}","gists_url":"https://api.github.com/users/prehonor/gists{/gist_id}","starred_url":"https://api.github.com/users/prehonor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prehonor/subscriptions","organizations_url":"https://api.github.com/users/prehonor/orgs","repos_url":"https://api.github.com/users/prehonor/repos","events_url":"https://api.github.com/users/prehonor/events{/privacy}","received_events_url":"https://api.github.com/users/prehonor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-09T12:33:47Z","updated_at":"2022-02-09T12:33:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"I hope echo $DISPLAY output \":0\".\r\nThis is my configuration.nix:\r\nhttps://github.com/prehonor/nixos","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158779/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158764","id":1128269974,"node_id":"I_kwDOAEVQ_M5DQAiW","number":158764,"title":"vimdot not displaying graph on darwin","user":{"login":"henningphan","id":1679039,"node_id":"MDQ6VXNlcjE2NzkwMzk=","avatar_url":"https://avatars.githubusercontent.com/u/1679039?v=4","gravatar_id":"","url":"https://api.github.com/users/henningphan","html_url":"https://github.com/henningphan","followers_url":"https://api.github.com/users/henningphan/followers","following_url":"https://api.github.com/users/henningphan/following{/other_user}","gists_url":"https://api.github.com/users/henningphan/gists{/gist_id}","starred_url":"https://api.github.com/users/henningphan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/henningphan/subscriptions","organizations_url":"https://api.github.com/users/henningphan/orgs","repos_url":"https://api.github.com/users/henningphan/repos","events_url":"https://api.github.com/users/henningphan/events{/privacy}","received_events_url":"https://api.github.com/users/henningphan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-02-09T09:24:17Z","updated_at":"2022-02-18T21:11:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen using vimdot only vim starts, there is no graphical viewer of the graph\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Get a mac monterey\r\n2. nix-env -iA nixpkgs.graphviz\r\n3. vimdot\r\n\r\n### Expected behavior\r\nWhen performing the third step I expect two things, firstly vim to start, and secondly a gui window to show me the graph\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\n```\r\nhenningphan@mackan:~$ dot -Txlib noname.gv\r\nFormat: \"xlib\" not recognized. Use one of: bmp canon cmap cmapx cmapx_np dot dot_json eps fig gd gd2 gif gv imap imap_np ismap jpe jpeg jpg json json0 mp pdf pic plain plain-ext png pov ps ps2 svg svgz tga tif tiff tk vdx vml vmlz vrml wbmp webp xdot xdot1.2 xdot1.4 xdot_json\r\nhenningphan@mackan:~$\r\n```\r\n\r\nchecking the script vimdot it runs dot with an xlib flag and that seems to fail, and thats where my knowledge ends.\r\n\r\n### Notify maintainers\r\n@bjornfor @7c6f434c \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese 2 paths will be fetched (0.01 MiB download, 0.14 MiB unpacked):\r\n /nix/store/1vf7mgrsymraipkqf0pf1m0629lzxdkc-nix-info\r\n /nix/store/rqv2pkd4pj3c5r0154bl066j55g2xj6z-DarwinTools-1\r\ncopying path '/nix/store/rqv2pkd4pj3c5r0154bl066j55g2xj6z-DarwinTools-1' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1vf7mgrsymraipkqf0pf1m0629lzxdkc-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(henningphan): `\"\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158764/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158740","id":1127971463,"node_id":"I_kwDOAEVQ_M5DO3qH","number":158740,"title":"nix build ignores allowUnsupportedSystem in config.nix because it's impure","user":{"login":"sbourdeauducq","id":720864,"node_id":"MDQ6VXNlcjcyMDg2NA==","avatar_url":"https://avatars.githubusercontent.com/u/720864?v=4","gravatar_id":"","url":"https://api.github.com/users/sbourdeauducq","html_url":"https://github.com/sbourdeauducq","followers_url":"https://api.github.com/users/sbourdeauducq/followers","following_url":"https://api.github.com/users/sbourdeauducq/following{/other_user}","gists_url":"https://api.github.com/users/sbourdeauducq/gists{/gist_id}","starred_url":"https://api.github.com/users/sbourdeauducq/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sbourdeauducq/subscriptions","organizations_url":"https://api.github.com/users/sbourdeauducq/orgs","repos_url":"https://api.github.com/users/sbourdeauducq/repos","events_url":"https://api.github.com/users/sbourdeauducq/events{/privacy}","received_events_url":"https://api.github.com/users/sbourdeauducq/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":2,"created_at":"2022-02-09T02:23:19Z","updated_at":"2022-02-14T22:58:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Describe the bug**\r\n\r\nWhen attempting to build a package for an unsupported system, ``nix build`` tells you to set ``{ allowUnsupportedSystem = true; }`` in ``~/.config/nixpkgs/config.nix`` to make it go ahead anyway. But this does nothing.\r\n\r\n**Steps To Reproduce**\r\n\r\n```\r\n$ cat ~/.config/nixpkgs/config.nix\r\n{ allowUnsupportedSystem = true; }\r\n\r\n$ nix build nixpkgs#pkgsCross.mingwW64.libbfd\r\nerror: Package ‘libbfd-2.35.2’ in /nix/store/z8jqr44vdiv3sikbvgy5f1yr6k2djj97-source/pkgs/development/libraries/libbfd/default.nix:47 is not supported on ‘x86_64-windows’, refusing to evaluate.\r\n\r\n a) To temporarily allow packages that are unsupported for this system, you can use an environment variable\r\n for a single invocation of the nix tools.\r\n\r\n $ export NIXPKGS_ALLOW_UNSUPPORTED_SYSTEM=1\r\n\r\n Note: For `nix shell`, `nix build`, `nix develop` or any other Nix 2.4+\r\n (Flake) command, `--impure` must be passed in order to read this\r\n environment variable.\r\n\r\n b) For `nixos-rebuild` you can set\r\n { nixpkgs.config.allowUnsupportedSystem = true; }\r\n in configuration.nix to override this.\r\n\r\n c) For `nix-env`, `nix-build`, `nix-shell` or any other Nix command you can add\r\n { allowUnsupportedSystem = true; }\r\n to ~/.config/nixpkgs/config.nix.\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\n**Expected behavior**\r\n\r\nNix should attempt to build the package, or the error message should say that ``--impure`` must also be used in cases b) and c) (https://github.com/NixOS/nix/issues/6062#issuecomment-1032599603)\r\n\r\n**Additional context**\r\n\r\nNix 2.4.\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158740/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158665","id":1127568678,"node_id":"I_kwDOAEVQ_M5DNVUm","number":158665,"title":"Abiword crashes when something is copied","user":{"login":"ne9z","id":77314501,"node_id":"MDQ6VXNlcjc3MzE0NTAx","avatar_url":"https://avatars.githubusercontent.com/u/77314501?v=4","gravatar_id":"","url":"https://api.github.com/users/ne9z","html_url":"https://github.com/ne9z","followers_url":"https://api.github.com/users/ne9z/followers","following_url":"https://api.github.com/users/ne9z/following{/other_user}","gists_url":"https://api.github.com/users/ne9z/gists{/gist_id}","starred_url":"https://api.github.com/users/ne9z/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ne9z/subscriptions","organizations_url":"https://api.github.com/users/ne9z/orgs","repos_url":"https://api.github.com/users/ne9z/repos","events_url":"https://api.github.com/users/ne9z/events{/privacy}","received_events_url":"https://api.github.com/users/ne9z/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-08T17:47:23Z","updated_at":"2022-02-10T08:39:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nUsing sway window manager, with xwayland disabled, abiword crashes when something is copied to the clipboard.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install sway, abiword\r\n2. Disable xwayland (I don't know if this is related to the bug)\r\n3. Launch abiword\r\n4. Type \"hello\" and press Ctrl+A Ctrl+C to copy the word\r\n5. `Aborted (core dumped)`\r\n\r\n### Expected behavior\r\nShould not crash. I tested the same configuration on arch linux and everything's working perfectly\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```\r\n[:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.17, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335820.521e4d7d13b\"`\r\n - channels(yc): `\"home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158665/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158629","id":1127351815,"node_id":"I_kwDOAEVQ_M5DMgYH","number":158629,"title":"Bad UX: extraPostFetch vs postFetch","user":{"login":"Radvendii","id":1239929,"node_id":"MDQ6VXNlcjEyMzk5Mjk=","avatar_url":"https://avatars.githubusercontent.com/u/1239929?v=4","gravatar_id":"","url":"https://api.github.com/users/Radvendii","html_url":"https://github.com/Radvendii","followers_url":"https://api.github.com/users/Radvendii/followers","following_url":"https://api.github.com/users/Radvendii/following{/other_user}","gists_url":"https://api.github.com/users/Radvendii/gists{/gist_id}","starred_url":"https://api.github.com/users/Radvendii/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Radvendii/subscriptions","organizations_url":"https://api.github.com/users/Radvendii/orgs","repos_url":"https://api.github.com/users/Radvendii/repos","events_url":"https://api.github.com/users/Radvendii/events{/privacy}","received_events_url":"https://api.github.com/users/Radvendii/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":549491066,"node_id":"MDU6TGFiZWw1NDk0OTEwNjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20developer%20experience","name":"6.topic: developer experience","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false},"assignees":[{"login":"Artturin","id":56650223,"node_id":"MDQ6VXNlcjU2NjUwMjIz","avatar_url":"https://avatars.githubusercontent.com/u/56650223?v=4","gravatar_id":"","url":"https://api.github.com/users/Artturin","html_url":"https://github.com/Artturin","followers_url":"https://api.github.com/users/Artturin/followers","following_url":"https://api.github.com/users/Artturin/following{/other_user}","gists_url":"https://api.github.com/users/Artturin/gists{/gist_id}","starred_url":"https://api.github.com/users/Artturin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Artturin/subscriptions","organizations_url":"https://api.github.com/users/Artturin/orgs","repos_url":"https://api.github.com/users/Artturin/repos","events_url":"https://api.github.com/users/Artturin/events{/privacy}","received_events_url":"https://api.github.com/users/Artturin/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-02-08T14:45:04Z","updated_at":"2022-03-05T00:59:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Most fetchers have a `postFetch` attribute that runs code after the fetch occurs. Meanwhile, `fetchzip` already sets `postFetch`, and so it exposes `extraPostFetch` if you want to add something on after.\r\n\r\nThis is inconsistent UX in general, but the bigger problem is that `fetchFromGitHub` sometimes uses `fetchGit` and sometimes `fetchZip`, depending on the options you provide. This means that someone could write a `fetchFromGitHub` using `extraPostFetch`, and then come along and add a `fetchSubmodules = true;`, and all of a sudden it breaks, because now it's expecting `postFetch` instead. This seems really bad to me.\r\n\r\n### Notify maintainers\r\nnot sure who to @ since the `fetch`ers don't have maintainers listed.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629/reactions","total_count":3,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":1,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158629/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158628","id":1127338734,"node_id":"I_kwDOAEVQ_M5DMdLu","number":158628,"title":"Request for Godot Engine nix build recipe","user":{"login":"tengkuizdihar","id":22078730,"node_id":"MDQ6VXNlcjIyMDc4NzMw","avatar_url":"https://avatars.githubusercontent.com/u/22078730?v=4","gravatar_id":"","url":"https://api.github.com/users/tengkuizdihar","html_url":"https://github.com/tengkuizdihar","followers_url":"https://api.github.com/users/tengkuizdihar/followers","following_url":"https://api.github.com/users/tengkuizdihar/following{/other_user}","gists_url":"https://api.github.com/users/tengkuizdihar/gists{/gist_id}","starred_url":"https://api.github.com/users/tengkuizdihar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tengkuizdihar/subscriptions","organizations_url":"https://api.github.com/users/tengkuizdihar/orgs","repos_url":"https://api.github.com/users/tengkuizdihar/repos","events_url":"https://api.github.com/users/tengkuizdihar/events{/privacy}","received_events_url":"https://api.github.com/users/tengkuizdihar/received_events","type":"User","site_admin":false},"labels":[{"id":6314754,"node_id":"MDU6TGFiZWw2MzE0NzU0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20question","name":"0.kind: question","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-08T14:34:47Z","updated_at":"2022-02-09T21:27:30Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\nI'm requesting a recipe to build a Godot Engine project (vanilla without any gdnative) in the format of `default.nix`. I'm sorry if I'm not on the right channel to ask for this.\r\n\r\n\r\n## Technical details\r\n\r\nRight now, although Godot Engine and its template does exist in nixpkgs, I still have no idea how to use the template. As far as I've seen, people would only use Godot + Nix only for setting up their dev environments.\r\n\r\nFor added context, my recipe for default.nix is as follows,\r\n\r\n```nix\r\n{\r\n # Enable support for OpenGL/Vulkan for your drivers\r\n nixgl ? import (fetchTarball \"https://github.com/guibou/nixGL/archive/7d6bc1b21316bab6cf4a6520c2639a11c25a220e.tar.gz\") { }\r\n, # Pin the version of the nix package repository\r\n pkgs ? import (fetchTarball \"https://github.com/nixos/nixpkgs/archive/a2968d985bf46d046f67e33c313e61d310d0885a.tar.gz\") { }\r\n}:\r\npkgs.stdenv.mkDerivation {\r\n name = \"competitive-fps\";\r\n\r\n buildInputs = [\r\n # Godot Engine Editor\r\n pkgs.godot\r\n\r\n # The support for OpenGL/Vulkan\r\n nixgl.nixGLDefault\r\n ];\r\n\r\n # Alias the godot engine to use nixGL\r\n shellHook = ''\r\n alias godot=\"nixGL godot -e\"\r\n '';\r\n}\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158628/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158627","id":1127337646,"node_id":"I_kwDOAEVQ_M5DMc6u","number":158627,"title":"Merge the self-deploy and auto-upgrade modules","user":{"login":"edolstra","id":1148549,"node_id":"MDQ6VXNlcjExNDg1NDk=","avatar_url":"https://avatars.githubusercontent.com/u/1148549?v=4","gravatar_id":"","url":"https://api.github.com/users/edolstra","html_url":"https://github.com/edolstra","followers_url":"https://api.github.com/users/edolstra/followers","following_url":"https://api.github.com/users/edolstra/following{/other_user}","gists_url":"https://api.github.com/users/edolstra/gists{/gist_id}","starred_url":"https://api.github.com/users/edolstra/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/edolstra/subscriptions","organizations_url":"https://api.github.com/users/edolstra/orgs","repos_url":"https://api.github.com/users/edolstra/repos","events_url":"https://api.github.com/users/edolstra/events{/privacy}","received_events_url":"https://api.github.com/users/edolstra/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"lambdadog","id":36526063,"node_id":"MDQ6VXNlcjM2NTI2MDYz","avatar_url":"https://avatars.githubusercontent.com/u/36526063?v=4","gravatar_id":"","url":"https://api.github.com/users/lambdadog","html_url":"https://github.com/lambdadog","followers_url":"https://api.github.com/users/lambdadog/followers","following_url":"https://api.github.com/users/lambdadog/following{/other_user}","gists_url":"https://api.github.com/users/lambdadog/gists{/gist_id}","starred_url":"https://api.github.com/users/lambdadog/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lambdadog/subscriptions","organizations_url":"https://api.github.com/users/lambdadog/orgs","repos_url":"https://api.github.com/users/lambdadog/repos","events_url":"https://api.github.com/users/lambdadog/events{/privacy}","received_events_url":"https://api.github.com/users/lambdadog/received_events","type":"User","site_admin":false},"assignees":[{"login":"lambdadog","id":36526063,"node_id":"MDQ6VXNlcjM2NTI2MDYz","avatar_url":"https://avatars.githubusercontent.com/u/36526063?v=4","gravatar_id":"","url":"https://api.github.com/users/lambdadog","html_url":"https://github.com/lambdadog","followers_url":"https://api.github.com/users/lambdadog/followers","following_url":"https://api.github.com/users/lambdadog/following{/other_user}","gists_url":"https://api.github.com/users/lambdadog/gists{/gist_id}","starred_url":"https://api.github.com/users/lambdadog/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lambdadog/subscriptions","organizations_url":"https://api.github.com/users/lambdadog/orgs","repos_url":"https://api.github.com/users/lambdadog/repos","events_url":"https://api.github.com/users/lambdadog/events{/privacy}","received_events_url":"https://api.github.com/users/lambdadog/received_events","type":"User","site_admin":false}],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":1,"created_at":"2022-02-08T14:34:10Z","updated_at":"2022-02-09T01:33:45Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nPR #120940 added a service named `services.self-deploy` to automatically upgrade NixOS systems. However, this functionality already largely exists in `services.autoUpgrade`. Since we shouldn't have multiple NixOS modules that do essentially the same thing, the functionality of `services.self-deploy` should be merged into `services.autoUpgrade`.\r\n\r\n`services.autoUpgrade` can upgrade an entire configuration from a top-level flake, or it can do `nix-channel --upgrade nixpkgs` to only upgrade the Nixpkgs repo. It currently lacks the ability to fetch a non-flake configuration repo, so if we want to retain that, we should add some options to `services.autoUpgrade` for that use case.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@lambdadog\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158627/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158606","id":1127174146,"node_id":"I_kwDOAEVQ_M5DL1AC","number":158606,"title":"Systemd unit options have problematic merging, checking and defaults","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-08T12:11:15Z","updated_at":"2022-02-08T12:11:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nMerging and checking of systemd unit options is subpar, relying on non-local error-prone information. The heuristic is as follows:\r\n\r\n - If all defs are a list, emit multiple lines for each item\r\n - If no defs are a list, emit a single line for each item and require that all defs are equal\r\n\r\nThis leads to problems when the user, or any NixOS module defines a value that should have been in a list or vice versa. What's worse it that it \"just works\" in many cases, as long as the user doesn't try to set their own value. This means that such problems can remain latent for a long time.\r\n\r\nPreviously the error message was completely incomprehensible, but I'm proposing a \"fix\" for that part of the problem. \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. define a NixOS module with an `ExecStartPre = \"foo\";`\r\n2. use the module\r\n3. try to extend the `ExecStartPre` in the user configuration\r\n4. error message (should have been in a list all along)\r\n\r\n\r\n### Expected behavior\r\n\r\nSystemd options have proper merging and checking functions that just work.\r\nThe module system offers a lot to make this feasible, like\r\n - `types.coercedTo` to upgrade values to lists when appropriate\r\n - `freeformType` so proper options can be added incrementally\r\n\r\n### Additional context\r\n\r\nhttps://github.com/NixOS/nixpkgs/issues/120617 can also be solved with `freeformType`.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158606/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158600","id":1127156122,"node_id":"I_kwDOAEVQ_M5DLwma","number":158600,"title":"`ghcjs.ghcWithPackages` fails with \"error: value is a path while a set was expected\" for certain packages","user":{"login":"rzetterberg","id":766350,"node_id":"MDQ6VXNlcjc2NjM1MA==","avatar_url":"https://avatars.githubusercontent.com/u/766350?v=4","gravatar_id":"","url":"https://api.github.com/users/rzetterberg","html_url":"https://github.com/rzetterberg","followers_url":"https://api.github.com/users/rzetterberg/followers","following_url":"https://api.github.com/users/rzetterberg/following{/other_user}","gists_url":"https://api.github.com/users/rzetterberg/gists{/gist_id}","starred_url":"https://api.github.com/users/rzetterberg/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rzetterberg/subscriptions","organizations_url":"https://api.github.com/users/rzetterberg/orgs","repos_url":"https://api.github.com/users/rzetterberg/repos","events_url":"https://api.github.com/users/rzetterberg/events{/privacy}","received_events_url":"https://api.github.com/users/rzetterberg/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-02-08T11:53:36Z","updated_at":"2022-04-05T10:53:14Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen I run: \r\n\r\n```\r\nnix-shell -p 'pkgs.haskell.packages.ghcjs.ghcWithPackages (p: with p; [ reflex ])'\r\n``` \r\n\r\nI get the following error: \r\n\r\n```\r\nerror: value is a path while a set was expected\r\n\r\n at /nix/store/ivngb8kkjz9iy5ys433yf29xxn039ysl-nixos-21.11.335665.0f316e4d72d/nixos/pkgs/development/haskell-modules/lib/compose.nix:38:28:\r\n\r\n 37| */\r\n 38| overrideCabal = f: drv: (drv.override (args: args // {\r\n | ^\r\n 39| mkDerivation = drv: (args.mkDerivation drv).override f;\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\nThis problem does **not** happen if I run:\r\n\r\n```\r\nnix-shell -p 'pkgs.haskell.packages.ghcjs.ghcWithPackages (p: with p; [ base ])'\r\n```\r\n\r\nthen the compilation starts, like expected. Same thing if I provide an empty list of packages. \r\n\r\n### Notify maintainers\r\n\r\nMaintainers from haskell team: @cdepillabout, @expipiplus1, @maralorn, @sternenseemann\r\n\r\n### Metadata\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(zed): `\"\"`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158600/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158598","id":1127143302,"node_id":"I_kwDOAEVQ_M5DLteG","number":158598,"title":"`config`-driven submodules?","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-08T11:40:01Z","updated_at":"2022-03-01T00:39:31Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"\r\nThis assumes #158594 is implemented as an incremental change to the module system. I'm writing this as a separate issue to manage the scope; feel free to ignore this one.\r\n\r\nFor modules with large amounts of unset options, it is inefficient for module system evaluation to be guided by the opts, as the defs are significantly smaller value. In its early history, module system evaluation primarily traversed `config`, but presumably, this was abandoned with the introduction of defaults in options.\r\n\r\nMaking this mode of module evaluation available on an opt-in basis would allow large, frequently used submodules such as the ones in `systemd` to be modeled more efficiently, providing documentation, type checking and merging for this important part of NixOS.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Infinisil \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158598/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158594","id":1127131333,"node_id":"I_kwDOAEVQ_M5DLqjF","number":158594,"title":"RFC42-style options that default to unset, to have no attribute in `config` despite option","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-08T11:27:50Z","updated_at":"2022-02-08T11:44:26Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"When defining an option in an RFC42-style free-form settings module, say `settings.foo`, the module system always creates a `config.settings.foo` value containing the default value.\r\n\r\nSome configuration formats require that `config` definitions are omitted in order to get the default behavior. Filtering those out of the `config` is unpleasant at least and as far as I know we don't have a standard solution for it.\r\n\r\nWe could add a `mkOption` argument that has the effect of producing no default value and no `config` attribute when no definitions are present for the option.\r\n\r\nThis will allow us to simplify modules that need to elide unset options and it lowers the threshold for defining options within a settings module, improving documentation and merge semantics.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Infinisil \r\n\r\n### Additional context\r\n\r\nThis idea has come up in #112494 as well, but I'm not convinced that it isn't feasible.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158594/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158579","id":1127013698,"node_id":"I_kwDOAEVQ_M5DLN1C","number":158579,"title":"nix-perl and nix-serve fails to build","user":{"login":"pinpox","id":1719781,"node_id":"MDQ6VXNlcjE3MTk3ODE=","avatar_url":"https://avatars.githubusercontent.com/u/1719781?v=4","gravatar_id":"","url":"https://api.github.com/users/pinpox","html_url":"https://github.com/pinpox","followers_url":"https://api.github.com/users/pinpox/followers","following_url":"https://api.github.com/users/pinpox/following{/other_user}","gists_url":"https://api.github.com/users/pinpox/gists{/gist_id}","starred_url":"https://api.github.com/users/pinpox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pinpox/subscriptions","organizations_url":"https://api.github.com/users/pinpox/orgs","repos_url":"https://api.github.com/users/pinpox/repos","events_url":"https://api.github.com/users/pinpox/events{/privacy}","received_events_url":"https://api.github.com/users/pinpox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-08T09:43:03Z","updated_at":"2022-02-08T13:15:37Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nSince recenctly, enabling nix-serve breaks rebuilding the system as it's dependency nix-perl fails to build. \r\nThis is the log of the build:\r\nhttps://gist.github.com/pinpox/b5d5f4b8d20bcbe53a485f5a5752f2b4\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable nix-serve\r\n2. rebuild system\r\n\r\n\r\n### Expected behavior\r\nSystem rebuilds fine\r\n\r\n### Notify maintainers\r\n@edolstra @InternetUnexplorer @Artturin @Mic92 \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - host os: `Linux 5.10.93, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre350399.a529f0c125a\"`\r\n - nixpkgs: `/nix/store/626qldjl59n3cx00l2sd86734vdj99pk-source`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158579/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158503","id":1126410419,"node_id":"I_kwDOAEVQ_M5DI6iz","number":158503,"title":"Lazy evaluation of types of `listOf oneOf` causes option missing errors when inner types are submodules","user":{"login":"OmnipotentEntity","id":1538622,"node_id":"MDQ6VXNlcjE1Mzg2MjI=","avatar_url":"https://avatars.githubusercontent.com/u/1538622?v=4","gravatar_id":"","url":"https://api.github.com/users/OmnipotentEntity","html_url":"https://github.com/OmnipotentEntity","followers_url":"https://api.github.com/users/OmnipotentEntity/followers","following_url":"https://api.github.com/users/OmnipotentEntity/following{/other_user}","gists_url":"https://api.github.com/users/OmnipotentEntity/gists{/gist_id}","starred_url":"https://api.github.com/users/OmnipotentEntity/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/OmnipotentEntity/subscriptions","organizations_url":"https://api.github.com/users/OmnipotentEntity/orgs","repos_url":"https://api.github.com/users/OmnipotentEntity/repos","events_url":"https://api.github.com/users/OmnipotentEntity/events{/privacy}","received_events_url":"https://api.github.com/users/OmnipotentEntity/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-07T19:31:41Z","updated_at":"2022-03-01T05:37:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen attempting to write a module, I had need of a tagged type to disambiguate between a list of strings and a list of strings that contain paths, but when I created this type I ran into an issue where the module's check for stray and useless option after configuration flagged one of my inner tagged types as having an stray and undefined option.\r\n\r\n```nix\r\n# Example type:\r\nwith lib;\r\n\r\nfoo = types.submodule {\r\n options = {\r\n bar = mkOption {\r\n type = types.str;\r\n };\r\n };\r\n};\r\n\r\nbaz = types.submodule {\r\n options = {\r\n words = mkOption {\r\n quux = (types.nonEmptyListOf types.str);\r\n };\r\n };\r\n};\r\n\r\nexampleType = types.listOf (types.oneOf [ foo baz ]);\r\n```\r\n\r\nNote if `foo` is found first in the type definition list of `exampleType`, then using `[ {bar = \"/my/path\" } { quux = [ \"asdf\" ] } ]` will trigger the error \"The option `path.to.quux` does not exist.\" On the other hand if `baz` is found first in the list, then using the same data will trigger the error \"The option `path.to.bar` does not exist.\"\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a type that is similar to the code above\r\n2. Use the type in a `mkOption` definition\r\n3. Attempt to use that option\r\n\r\n### Expected behavior\r\nIt would be expected that the type would compose such that both submodules are valid and the option missing errors do not occur.\r\n\r\n### Additional context\r\nYou can find a full example of code that triggers this problem [here](https://github.com/OmnipotentEntity/nixpkgs/commit/71537c4c958e3e56afdbf4da9b3067838437f78d#diff-2aa44113e95508f50ab18ee392bd24b93c731e8a411f2b4e5541d3343bec5c01R38) (It is, however, awful, and I apologize for making you read it.)\r\n\r\nUse the following additional module to trigger it:\r\n\r\n```nix\r\n{config, pkgs, ...} : {\r\n config.environment.wordlist = {\r\n enable = true;\r\n lists = [\r\n {\r\n envVar = \"WORDLIST\";\r\n source = \"${pkgs.scowl}/share/dict/words.txt\";\r\n }\r\n {\r\n envVar = \"AUGMENTED_WORDLIST\";\r\n source = [\r\n { file = \"${pkgs.scowl}/share/dict/words.txt\"; }\r\n { words = [ \"foo\" \"bar\" \"baz\" ]; }\r\n ];\r\n }\r\n ];\r\n };\r\n}\r\n```\r\n\r\n### Notify maintainers\r\n@Infinisil @Ma27 @edolstra \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.13, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-21.05.3957.66d6ec6ed2d, nixos-unstable-21.11pre325810.2deb07f3ac4\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503/reactions","total_count":1,"+1":0,"-1":1,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158503/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158497","id":1126380931,"node_id":"I_kwDOAEVQ_M5DIzWD","number":158497,"title":"fwupd cannot update its config","user":{"login":"orangecms","id":4245199,"node_id":"MDQ6VXNlcjQyNDUxOTk=","avatar_url":"https://avatars.githubusercontent.com/u/4245199?v=4","gravatar_id":"","url":"https://api.github.com/users/orangecms","html_url":"https://github.com/orangecms","followers_url":"https://api.github.com/users/orangecms/followers","following_url":"https://api.github.com/users/orangecms/following{/other_user}","gists_url":"https://api.github.com/users/orangecms/gists{/gist_id}","starred_url":"https://api.github.com/users/orangecms/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/orangecms/subscriptions","organizations_url":"https://api.github.com/users/orangecms/orgs","repos_url":"https://api.github.com/users/orangecms/repos","events_url":"https://api.github.com/users/orangecms/events{/privacy}","received_events_url":"https://api.github.com/users/orangecms/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-07T19:05:35Z","updated_at":"2022-02-28T04:11:29Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`fwupd` has features that can be activated from its CLI, e.g., automatic upload of reports. Because Nix makes the config drop-in read-only symlinks, the config cannot be persisted.\r\n\r\n### Steps To Reproduce\r\n\r\n```\r\nsudo fwupdmgr get-updates\r\n```\r\nSay yes to uploading reports, and yes to doing so automatically in the future.\r\n\r\n### Expected behavior\r\n\r\nAn application should be able to update its config.\r\n\r\n### Additional context\r\n\r\nThis is a design question to a degree. Nix could run a daemon that watches a defined set of files for changes and tracks them, or define a replacement store etc.. I am not sure how it's done for other services such as NetworkManager.\r\n\r\n### Notify maintainers\r\n\r\n@jtojnar @maxeaubrey \r\n\r\n### Metadata\r\n\r\nN/A","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158497/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158478","id":1126121961,"node_id":"I_kwDOAEVQ_M5DH0Hp","number":158478,"title":"react-native-debugger doesn't work (missing libdrm and more)","user":{"login":"rbozan","id":7997154,"node_id":"MDQ6VXNlcjc5OTcxNTQ=","avatar_url":"https://avatars.githubusercontent.com/u/7997154?v=4","gravatar_id":"","url":"https://api.github.com/users/rbozan","html_url":"https://github.com/rbozan","followers_url":"https://api.github.com/users/rbozan/followers","following_url":"https://api.github.com/users/rbozan/following{/other_user}","gists_url":"https://api.github.com/users/rbozan/gists{/gist_id}","starred_url":"https://api.github.com/users/rbozan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rbozan/subscriptions","organizations_url":"https://api.github.com/users/rbozan/orgs","repos_url":"https://api.github.com/users/rbozan/repos","events_url":"https://api.github.com/users/rbozan/events{/privacy}","received_events_url":"https://api.github.com/users/rbozan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-07T15:11:15Z","updated_at":"2022-04-25T11:59:30Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n```\r\n/etc/nixos(master) » nix-shell -p react-native-debugger rbozan@DESKTOP-Robin\r\nthese paths will be fetched (59.17 MiB download, 224.54 MiB unpacked):\r\n /nix/store/qf0iy1n37x1g9vmszn5z4zfn05xmphdp-react-native-debugger-0.12.1\r\ncopying path '/nix/store/qf0iy1n37x1g9vmszn5z4zfn05xmphdp-react-native-debugger-0.12.1' from 'https://cache.nixos.org'...\r\nreact-native-debugger\r\n\r\n[nix-shell:/etc/nixos]$ react-native-debugger\r\nreact-native-debugger: error while loading shared libraries: libdrm.so.2: cannot open shared object file: No such file or directory\r\n```\r\n\r\n```\r\nldd /nix/store/qf0iy1n37x1g9vmszn5z4zfn05xmphdp-react-native-debugger-0.12.1/bin/react-native-debugger\r\n\tlinux-vdso.so.1 (0x00007ffe66102000)\r\n\tlibffmpeg.so => /nix/store/qf0iy1n37x1g9vmszn5z4zfn05xmphdp-react-native-debugger-0.12.1/lib/libffmpeg.so (0x00007fc8ee169000)\r\n\tlibdl.so.2 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libdl.so.2 (0x00007fc8ee164000)\r\n\tlibpthread.so.0 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libpthread.so.0 (0x00007fc8ee144000)\r\n\tlibrt.so.1 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/librt.so.1 (0x00007fc8ee139000)\r\n\tlibgobject-2.0.so.0 => /nix/store/3gblis6mvxq4lw1j1lw0rzp9d3zz1w76-glib-2.70.1/lib/libgobject-2.0.so.0 (0x00007fc8ee0de000)\r\n\tlibglib-2.0.so.0 => /nix/store/3gblis6mvxq4lw1j1lw0rzp9d3zz1w76-glib-2.70.1/lib/libglib-2.0.so.0 (0x00007fc8edfa4000)\r\n\tlibgio-2.0.so.0 => /nix/store/3gblis6mvxq4lw1j1lw0rzp9d3zz1w76-glib-2.70.1/lib/libgio-2.0.so.0 (0x00007fc8eddc8000)\r\n\tlibnss3.so => /nix/store/ykwa8l6kr783qk3zjn33qj9n12gsbz73-nss-3.73/lib/libnss3.so (0x00007fc8edc8a000)\r\n\tlibnssutil3.so => /nix/store/ykwa8l6kr783qk3zjn33qj9n12gsbz73-nss-3.73/lib/libnssutil3.so (0x00007fc8edc57000)\r\n\tlibsmime3.so => /nix/store/ykwa8l6kr783qk3zjn33qj9n12gsbz73-nss-3.73/lib/libsmime3.so (0x00007fc8edc2c000)\r\n\tlibnspr4.so => /nix/store/60yb5vj1gb1lpms3r3zw63zfb9siqcyw-nspr-4.32/lib/libnspr4.so (0x00007fc8edbe9000)\r\n\tlibatk-1.0.so.0 => /nix/store/9bdygknb508dqr27396j1q7v8j53f7qa-atk-2.36.0/lib/libatk-1.0.so.0 (0x00007fc8edbbd000)\r\n\tlibatk-bridge-2.0.so.0 => /nix/store/z3nippfnkiy4c0gcdi9y44ayszpqqfk6-at-spi2-atk-2.38.0/lib/libatk-bridge-2.0.so.0 (0x00007fc8edb85000)\r\n\tlibX11.so.6 => /nix/store/rhh49m3g22dwsajcrzws43yzmmb5j1sz-libX11-1.7.2/lib/libX11.so.6 (0x00007fc8eda40000)\r\n\tlibX11-xcb.so.1 => /nix/store/rhh49m3g22dwsajcrzws43yzmmb5j1sz-libX11-1.7.2/lib/libX11-xcb.so.1 (0x00007fc8eda3b000)\r\n\tlibxcb.so.1 => /nix/store/iswd1yqvdjjsvbsqnyz3x78bmp8dccak-libxcb-1.14/lib/libxcb.so.1 (0x00007fc8eda0f000)\r\n\tlibdbus-1.so.3 => /nix/store/pmzqwrngypx1x4m5yzbyqnh6qz8f3avj-dbus-1.12.20-lib/lib/libdbus-1.so.3 (0x00007fc8ed9b7000)\r\n\tlibgdk_pixbuf-2.0.so.0 => /nix/store/2nxwlyv24whl9fmi7i7n8cspic1ilzba-gdk-pixbuf-2.42.6/lib/libgdk_pixbuf-2.0.so.0 (0x00007fc8ed989000)\r\n\tlibgtk-3.so.0 => /nix/store/70afygp86vrskfjfgdclgjwzgy2ch3gg-gtk+3-3.24.30/lib/libgtk-3.so.0 (0x00007fc8ed1ba000)\r\n\tlibgdk-3.so.0 => /nix/store/70afygp86vrskfjfgdclgjwzgy2ch3gg-gtk+3-3.24.30/lib/libgdk-3.so.0 (0x00007fc8ed0b3000)\r\n\tlibpangocairo-1.0.so.0 => /nix/store/7x76vbd8f2n87sdm0g6v99anck2d6a5p-pango-1.48.10/lib/libpangocairo-1.0.so.0 (0x00007fc8ed0a2000)\r\n\tlibpango-1.0.so.0 => /nix/store/7x76vbd8f2n87sdm0g6v99anck2d6a5p-pango-1.48.10/lib/libpango-1.0.so.0 (0x00007fc8ed04c000)\r\n\tlibcairo.so.2 => /nix/store/m37ciz0sfip23z79qmn3zn9an8jpf0hd-cairo-1.16.0/lib/libcairo.so.2 (0x00007fc8ecf0f000)\r\n\tlibm.so.6 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libm.so.6 (0x00007fc8ecdce000)\r\n\tlibXcomposite.so.1 => /nix/store/r3fkzzbqwv3d80r124xirb1zysx6jv97-libXcomposite-0.4.5/lib/libXcomposite.so.1 (0x00007fc8ecdc9000)\r\n\tlibXdamage.so.1 => /nix/store/6jrcrdw9qsh32c0xjvkm10b41lifv05i-libXdamage-1.1.5/lib/libXdamage.so.1 (0x00007fc8ecdc4000)\r\n\tlibXext.so.6 => /nix/store/jswcdywaxfikb1dm1jx5r67mcrqqqsc1-libXext-1.3.4/lib/libXext.so.6 (0x00007fc8ecdaf000)\r\n\tlibXfixes.so.3 => /nix/store/2qb8j3lrdnfdnxflq623hirka3im8a9n-libXfixes-6.0.0/lib/libXfixes.so.3 (0x00007fc8ecda4000)\r\n\tlibXrandr.so.2 => /nix/store/0hh91566fp5j4i5zm3lzkm9rzw1xv4jz-libXrandr-1.5.2/lib/libXrandr.so.2 (0x00007fc8ecd97000)\r\n\tlibexpat.so.1 => /nix/store/if63r73rnr3xf6i25vv276cdbga2q9zn-expat-2.4.1/lib/libexpat.so.1 (0x00007fc8ecd66000)\r\n\tlibdrm.so.2 => not found\r\n\tlibxkbcommon.so.0 => not found\r\n\tlibgbm.so.1 => not found\r\n\tlibasound.so.2 => /nix/store/y6lxfmmk56mfc13h1r743xmd6idhhmnj-alsa-lib-1.2.5.1/lib/libasound.so.2 (0x00007fc8ecc5a000)\r\n\tlibcups.so.2 => /nix/store/i6g6qpllq38l9brxr9a06k237k3j92cn-cups-2.3.3op2-lib/lib/libcups.so.2 (0x00007fc8ecbd0000)\r\n\tlibatspi.so.0 => /nix/store/07mdlh09zg22fqwzwi5na2xf1avh3l7w-at-spi2-core-2.42.0/lib/libatspi.so.0 (0x00007fc8ecb94000)\r\n\tlibgcc_s.so.1 => /nix/store/rv5vk9jzy8sifdqkyl9wj8ib8hgwf2xn-gcc-10.3.0-lib/lib/libgcc_s.so.1 (0x00007fc8ecb7a000)\r\n\tlibc.so.6 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libc.so.6 (0x00007fc8ec9b5000)\r\n\t/nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/ld-linux-x86-64.so.2 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib64/ld-linux-x86-64.so.2 (0x00007fc8f6872000)\r\n\tlibffi.so.8 => /nix/store/854qgdxv2zzmral9vbyqq7sybnxx6w67-libffi-3.4.2/lib/libffi.so.8 (0x00007fc8ec9a6000)\r\n\tlibpcre.so.1 => /nix/store/dr3vpqrla3csqvd6n0b3dhnibmb3i52y-pcre-8.44/lib/libpcre.so.1 (0x00007fc8ec92d000)\r\n\tlibgmodule-2.0.so.0 => /nix/store/3gblis6mvxq4lw1j1lw0rzp9d3zz1w76-glib-2.70.1/lib/libgmodule-2.0.so.0 (0x00007fc8ec926000)\r\n\tlibz.so.1 => /nix/store/jjc6qxbjq4ghs6ibp3j1s904qp32zr3s-zlib-1.2.11/lib/libz.so.1 (0x00007fc8ec909000)\r\n\tlibmount.so.1 => /nix/store/rm4vjqxwxs3n0w1n7nnna52s0z33mav8-util-linux-2.37.2-lib/lib/libmount.so.1 (0x00007fc8ec8a7000)\r\n\tlibselinux.so.1 => /nix/store/7d1d606n9j581hhhsfk0ksxfmvjlayy6-libselinux-3.0/lib/libselinux.so.1 (0x00007fc8ec87a000)\r\n\tlibresolv.so.2 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libresolv.so.2 (0x00007fc8ec862000)\r\n\tlibplds4.so => /nix/store/60yb5vj1gb1lpms3r3zw63zfb9siqcyw-nspr-4.32/lib/libplds4.so (0x00007fc8ec85d000)\r\n\tlibplc4.so => /nix/store/60yb5vj1gb1lpms3r3zw63zfb9siqcyw-nspr-4.32/lib/libplc4.so (0x00007fc8ec856000)\r\n\tlibXau.so.6 => /nix/store/vdk0bwl7290jdsbxxyabbkfmmnck7fx2-libXau-1.0.9/lib/libXau.so.6 (0x00007fc8ec84f000)\r\n\tlibXdmcp.so.6 => /nix/store/rwj3kwaajgkll1597k81gb784sh3iyc7-libXdmcp-1.1.3/lib/libXdmcp.so.6 (0x00007fc8ec847000)\r\n\tlibsystemd.so.0 => /nix/store/zc9r3iin18bccr3sjgwsgd6snp8g9g27-systemd-249.7/lib/libsystemd.so.0 (0x00007fc8ec764000)\r\n\tlibpng16.so.16 => /nix/store/q2hpg96cfgx0lh4gygdl4y2aj5qqflfi-libpng-apng-1.6.37/lib/libpng16.so.16 (0x00007fc8ec72a000)\r\n\tlibjpeg.so.62 => /nix/store/jc8dc61kwyb6s9ijwby6db23l9szdpgl-libjpeg-turbo-2.1.2/lib/libjpeg.so.62 (0x00007fc8ec671000)\r\n\tlibharfbuzz.so.0 => /nix/store/f2lkn9mvn5xkszqln41j7n0dzgxy650b-harfbuzz-3.0.0/lib/libharfbuzz.so.0 (0x00007fc8ec57e000)\r\n\tlibpangoft2-1.0.so.0 => /nix/store/7x76vbd8f2n87sdm0g6v99anck2d6a5p-pango-1.48.10/lib/libpangoft2-1.0.so.0 (0x00007fc8ec564000)\r\n\tlibfontconfig.so.1 => /nix/store/4ssgnyxqmcw5vw96g3inmg31m1f901m9-fontconfig-2.13.94-lib/lib/libfontconfig.so.1 (0x00007fc8ec518000)\r\n\tlibfreetype.so.6 => /nix/store/bq559f84iwqj1jhklwsih67ww4j4gn1a-freetype-2.11.0/lib/libfreetype.so.6 (0x00007fc8ec44c000)\r\n\tlibfribidi.so.0 => /nix/store/5y2h8n1apwlfnz1msafcf69md6f4h4mw-fribidi-1.0.10/lib/libfribidi.so.0 (0x00007fc8ec42d000)\r\n\tlibcairo-gobject.so.2 => /nix/store/m37ciz0sfip23z79qmn3zn9an8jpf0hd-cairo-1.16.0/lib/libcairo-gobject.so.2 (0x00007fc8ec421000)\r\n\tlibepoxy.so.0 => /nix/store/pj9hysb49x9021pmkimz0k8223qqfshn-libepoxy-1.5.4/lib/libepoxy.so.0 (0x00007fc8ec2eb000)\r\n\tlibXi.so.6 => /nix/store/kv9k24xh1ma6ji273a61503mr56ac9a2-libXi-1.8/lib/libXi.so.6 (0x00007fc8ec2d7000)\r\n\tlibtracker-sparql-3.0.so.0 => /nix/store/1zrdpl9n4cisfsk2vvrbca1fadk9g8ri-tracker-3.2.1/lib/libtracker-sparql-3.0.so.0 (0x00007fc8ec1c1000)\r\n\tlibxkbcommon.so.0 => /nix/store/7rdrb8g6isprd53g7lzk3by1qln85is3-libxkbcommon-1.3.1/lib/libxkbcommon.so.0 (0x00007fc8ec17b000)\r\n\tlibwayland-client.so.0 => /nix/store/my2mp5qmyk0l56fs9c12c16r61ivkgg7-wayland-1.19.0/lib/libwayland-client.so.0 (0x00007fc8ec169000)\r\n\tlibwayland-cursor.so.0 => /nix/store/my2mp5qmyk0l56fs9c12c16r61ivkgg7-wayland-1.19.0/lib/libwayland-cursor.so.0 (0x00007fc8ec15f000)\r\n\tlibwayland-egl.so.1 => /nix/store/my2mp5qmyk0l56fs9c12c16r61ivkgg7-wayland-1.19.0/lib/libwayland-egl.so.1 (0x00007fc8ec158000)\r\n\tlibXcursor.so.1 => /nix/store/byyd0v25sr3fyzqhkdj151pcdyxndc3l-libXcursor-1.2.0/lib/libXcursor.so.1 (0x00007fc8ec14b000)\r\n\tlibXinerama.so.1 => /nix/store/pfps23xygsm6llb8kvhkjd7s71xzxvgs-libXinerama-1.1.4/lib/libXinerama.so.1 (0x00007fc8ec146000)\r\n\tlibthai.so.0 => /nix/store/8p5fp8nnzg0lzgfps09yj0lqsiqafa60-libthai-0.1.28/lib/libthai.so.0 (0x00007fc8ec13a000)\r\n\tlibpixman-1.so.0 => /nix/store/qch0midyw24vzb746xa9j4k3bjva8f4b-pixman-0.38.4/lib/libpixman-1.so.0 (0x00007fc8ec08e000)\r\n\tlibEGL.so.1 => /nix/store/8s29vfqn2agmqgxl4qba26sw7lf8511v-libglvnd-1.3.4/lib/libEGL.so.1 (0x00007fc8ec078000)\r\n\tlibxcb-shm.so.0 => /nix/store/iswd1yqvdjjsvbsqnyz3x78bmp8dccak-libxcb-1.14/lib/libxcb-shm.so.0 (0x00007fc8ec073000)\r\n\tlibxcb-render.so.0 => /nix/store/iswd1yqvdjjsvbsqnyz3x78bmp8dccak-libxcb-1.14/lib/libxcb-render.so.0 (0x00007fc8ec063000)\r\n\tlibXrender.so.1 => /nix/store/q35a27s1yk4pgazdnzhi9qb2qv7czdan-libXrender-0.9.10/lib/libXrender.so.1 (0x00007fc8ec056000)\r\n\tlibGL.so.1 => /nix/store/8s29vfqn2agmqgxl4qba26sw7lf8511v-libglvnd-1.3.4/lib/libGL.so.1 (0x00007fc8ebfc6000)\r\n\tlibavahi-common.so.3 => /nix/store/fhvkz4fs7p4csxywx8cwszx85c44lipx-avahi-0.8/lib/libavahi-common.so.3 (0x00007fc8ebfb6000)\r\n\tlibavahi-client.so.3 => /nix/store/fhvkz4fs7p4csxywx8cwszx85c44lipx-avahi-0.8/lib/libavahi-client.so.3 (0x00007fc8ebfa2000)\r\n\tlibgnutls.so.30 => /nix/store/r5g5if63q1yvbwq3g4gyfndmk6387rwp-gnutls-3.7.2/lib/libgnutls.so.30 (0x00007fc8ebd9f000)\r\n\tlibcrypt.so.1 => /nix/store/41dj1v3qz9a5kjncpkxhmq50yg9r24dn-glibc-2.33-62/lib/libcrypt.so.1 (0x00007fc8ebd63000)\r\n\tlibblkid.so.1 => /nix/store/rm4vjqxwxs3n0w1n7nnna52s0z33mav8-util-linux-2.37.2-lib/lib/libblkid.so.1 (0x00007fc8ebd0d000)\r\n\tliblzma.so.5 => /nix/store/r3fp76bzvgh1gy57xssscnr87zrjagqf-xz-5.2.5/lib/liblzma.so.5 (0x00007fc8ebce3000)\r\n\tlibzstd.so.1 => /nix/store/dmsyx31mzhrl07jjyabc5d3vgiprkqqd-zstd-1.5.0/lib/libzstd.so.1 (0x00007fc8ebbf8000)\r\n\tliblz4.so.1 => /nix/store/9bqg4pzpyyrl98bnfjgnppj4ywyvb4bi-lz4-1.9.3/lib/liblz4.so.1 (0x00007fc8ebbc4000)\r\n\tlibcap.so.2 => /nix/store/372m8f09kas0yv669jyln0iij4qb2lb6-libcap-2.49-lib/lib/libcap.so.2 (0x00007fc8ebbb9000)\r\n\tlibgcrypt.so.20 => /nix/store/0lv86s29w7pzn896z1r9672ss2frnxs2-libgcrypt-1.9.4/lib/libgcrypt.so.20 (0x00007fc8eba7d000)\r\n\tlibgraphite2.so.3 => /nix/store/y5ln9c147j7ikpaxbzr010zc706a1plh-graphite2-1.3.14/lib/libgraphite2.so.3 (0x00007fc8eba53000)\r\n\tlibbz2.so.1 => /nix/store/s3bdv799b9fsgk6rdylf1bwvdnyf7il2-bzip2-1.0.6.0.2/lib/libbz2.so.1 (0x00007fc8eba3e000)\r\n\tlibicuuc.so.70 => /nix/store/f50xdpib1rcyjxk07qa2sf1l0w7lg2n7-icu4c-70.1/lib/libicuuc.so.70 (0x00007fc8eb83e000)\r\n\tlibicui18n.so.70 => /nix/store/f50xdpib1rcyjxk07qa2sf1l0w7lg2n7-icu4c-70.1/lib/libicui18n.so.70 (0x00007fc8eb505000)\r\n\tlibsqlite3.so.0 => /nix/store/hq7f6b5xl6s585j2mk7b7d9lpb2hf04b-sqlite-3.36.0/lib/libsqlite3.so.0 (0x00007fc8eb3c0000)\r\n\tlibjson-glib-1.0.so.0 => /nix/store/81xh3ihp3wj4piymiyalw9xdd4ffaabl-json-glib-1.6.6/lib/libjson-glib-1.0.so.0 (0x00007fc8eb394000)\r\n\tlibxml2.so.2 => /nix/store/g7pq4pdfzdsmww4z8zjykfw2ywn8g2vm-libxml2-2.9.12/lib/libxml2.so.2 (0x00007fc8eb226000)\r\n\tlibdatrie.so.1 => /nix/store/r8vxnw1pinimh2xlnpigxrngifcklpjv-libdatrie-2019-12-20-lib/lib/libdatrie.so.1 (0x00007fc8eb21c000)\r\n\tlibGLdispatch.so.0 => /nix/store/8s29vfqn2agmqgxl4qba26sw7lf8511v-libglvnd-1.3.4/lib/libGLdispatch.so.0 (0x00007fc8eb161000)\r\n\tlibGLX.so.0 => /nix/store/8s29vfqn2agmqgxl4qba26sw7lf8511v-libglvnd-1.3.4/lib/libGLX.so.0 (0x00007fc8eb12c000)\r\n\tlibssp.so.0 => /nix/store/rv5vk9jzy8sifdqkyl9wj8ib8hgwf2xn-gcc-10.3.0-lib/lib/libssp.so.0 (0x00007fc8eb127000)\r\n\tlibp11-kit.so.0 => /nix/store/3x6dxf4hpqkvdh3afkdx8ll7hdhzl1rm-p11-kit-0.24.0/lib/libp11-kit.so.0 (0x00007fc8eaff0000)\r\n\tlibunistring.so.2 => /nix/store/lrhl751psj7fwfc009wqy2b62pwccnvf-libunistring-0.9.10/lib/libunistring.so.2 (0x00007fc8eae6d000)\r\n\tlibtasn1.so.6 => /nix/store/xb9lj04d6zp3zfmagkwwfzwkkh6qjkl4-libtasn1-4.17.0/lib/libtasn1.so.6 (0x00007fc8eae57000)\r\n\tlibnettle.so.8 => /nix/store/g37n6iszi0cw459fnfr72vwrlwi3g6c6-nettle-3.7.3/lib/libnettle.so.8 (0x00007fc8eae0e000)\r\n\tlibhogweed.so.6 => /nix/store/g37n6iszi0cw459fnfr72vwrlwi3g6c6-nettle-3.7.3/lib/libhogweed.so.6 (0x00007fc8eadc4000)\r\n\tlibgmp.so.10 => /nix/store/lfhpr1aq87k3czlgi29ivnh099vqsbhw-gmp-6.2.1/lib/libgmp.so.10 (0x00007fc8ead20000)\r\n\tlibgpg-error.so.0 => /nix/store/5gz368dgqksqxjag2h718aw6vi88a58c-libgpg-error-1.42/lib/libgpg-error.so.0 (0x00007fc8eacf9000)\r\n\tlibicudata.so.70 => /nix/store/f50xdpib1rcyjxk07qa2sf1l0w7lg2n7-icu4c-70.1/lib/libicudata.so.70 (0x00007fc8e90dd000)\r\n\tlibstdc++.so.6 => /nix/store/rv5vk9jzy8sifdqkyl9wj8ib8hgwf2xn-gcc-10.3.0-lib/lib/libstdc++.so.6 (0x00007fc8e8f08000)\r\n\r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335526.6c4b9f1a2fd, home-manager-21.11, nixos-unstable-22.05pre341453.ac169ec6371\"`\r\n - channels(rbozan): `\"home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158478/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158456","id":1125775087,"node_id":"I_kwDOAEVQ_M5DGfbv","number":158456,"title":"nim: `nimsuggest` can't open standard library","user":{"login":"bandithedoge","id":26331682,"node_id":"MDQ6VXNlcjI2MzMxNjgy","avatar_url":"https://avatars.githubusercontent.com/u/26331682?v=4","gravatar_id":"","url":"https://api.github.com/users/bandithedoge","html_url":"https://github.com/bandithedoge","followers_url":"https://api.github.com/users/bandithedoge/followers","following_url":"https://api.github.com/users/bandithedoge/following{/other_user}","gists_url":"https://api.github.com/users/bandithedoge/gists{/gist_id}","starred_url":"https://api.github.com/users/bandithedoge/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bandithedoge/subscriptions","organizations_url":"https://api.github.com/users/bandithedoge/orgs","repos_url":"https://api.github.com/users/bandithedoge/repos","events_url":"https://api.github.com/users/bandithedoge/events{/privacy}","received_events_url":"https://api.github.com/users/bandithedoge/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3320601120,"node_id":"MDU6TGFiZWwzMzIwNjAxMTIw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nim","name":"6.topic: nim","color":"fef2c0","default":false,"description":"Nim programing language"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-07T10:11:11Z","updated_at":"2022-03-08T07:14:23Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nRunning `nimsuggest` on any file results in the following error: `Error: cannot open '/nix/store/pa9r86v360nyv5f1bd3pbkac0jd59an8-nim-unwrapped-1.6.0/lib/system.nim'`. Looking at the store path of `nim-unwrapped`, the library files are located under `nim/lib/` instead of `lib/`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install `nim` or `nim-unwrapped`\r\n2. `nimsuggest path/to/nim/file.nim`\r\n\r\n### Expected behavior\r\n`nimsuggest` runs on the specified file\r\n\r\n### Notify maintainers\r\n@ehmry \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `relaxed`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(bandithedoge): `\"darwin, home-manager, nixpkgs-22.05pre348720.b05d2077ebe\"`\r\n - channels(root): `\"nixpkgs-22.05pre345869.46821ea01c8\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158456/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158449","id":1125648776,"node_id":"I_kwDOAEVQ_M5DGAmI","number":158449,"title":"`programs.chromium.extensions` should apply to `pkgs.ungoogled-chromium`","user":{"login":"l0b0","id":168301,"node_id":"MDQ6VXNlcjE2ODMwMQ==","avatar_url":"https://avatars.githubusercontent.com/u/168301?v=4","gravatar_id":"","url":"https://api.github.com/users/l0b0","html_url":"https://github.com/l0b0","followers_url":"https://api.github.com/users/l0b0/followers","following_url":"https://api.github.com/users/l0b0/following{/other_user}","gists_url":"https://api.github.com/users/l0b0/gists{/gist_id}","starred_url":"https://api.github.com/users/l0b0/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/l0b0/subscriptions","organizations_url":"https://api.github.com/users/l0b0/orgs","repos_url":"https://api.github.com/users/l0b0/repos","events_url":"https://api.github.com/users/l0b0/events{/privacy}","received_events_url":"https://api.github.com/users/l0b0/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-02-07T08:13:28Z","updated_at":"2022-02-10T01:52:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable Chromium with an extension:\r\n\r\n ```nix\r\n programs.chromium = {\r\n enable = true;\r\n extensions = [\r\n \"cjpalhdlnbpafiamejdnhcphjbkeiagm\" # ublock origin\r\n ];\r\n };\r\n ```\r\n2. Add `pkgs.ungoogled-chromium` to `environment.systemPackages`\r\n3. `nixos-rebuild switch`\r\n4. Run Chromium\r\n5. Go to `chrome://extensions/`\r\n\r\n### Expected behavior\r\n\r\nThe uBlock Origin extension should be listed.\r\n\r\n### Additional context\r\n\r\nSomeone described a [hacky workaround](https://discourse.nixos.org/t/howto-kinda-declaratively-install-extensions-for-ungoogled-chromium/13376) elsewhere, but I'm not sure that's a good idea.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.96, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335807.df4f1f7cc3f, home-manager-21.05\"`\r\n - channels(victor): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158449/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158436","id":1125466776,"node_id":"I_kwDOAEVQ_M5DFUKY","number":158436,"title":"Request to add LiceCap package","user":{"login":"bowbahdoe","id":5004262,"node_id":"MDQ6VXNlcjUwMDQyNjI=","avatar_url":"https://avatars.githubusercontent.com/u/5004262?v=4","gravatar_id":"","url":"https://api.github.com/users/bowbahdoe","html_url":"https://github.com/bowbahdoe","followers_url":"https://api.github.com/users/bowbahdoe/followers","following_url":"https://api.github.com/users/bowbahdoe/following{/other_user}","gists_url":"https://api.github.com/users/bowbahdoe/gists{/gist_id}","starred_url":"https://api.github.com/users/bowbahdoe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bowbahdoe/subscriptions","organizations_url":"https://api.github.com/users/bowbahdoe/orgs","repos_url":"https://api.github.com/users/bowbahdoe/repos","events_url":"https://api.github.com/users/bowbahdoe/events{/privacy}","received_events_url":"https://api.github.com/users/bowbahdoe/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-07T03:37:42Z","updated_at":"2022-02-07T03:38:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nLICEcap can capture an area of your desktop and save it directly to .GIF (for viewing in web browsers, etc) or .LCF \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.cockos.com/licecap/\r\n* source URL: [github.com/justinfrankel/licecap](https://www.github.com/justinfrankel/licecap.git)\r\n* license: gpl\r\n* platforms: windows, darwin, linux through wine\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158436/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158424","id":1125411680,"node_id":"I_kwDOAEVQ_M5DFGtg","number":158424,"title":"python3.pkgs.mailman is not a Python module","user":{"login":"dotlambda","id":6806011,"node_id":"MDQ6VXNlcjY4MDYwMTE=","avatar_url":"https://avatars.githubusercontent.com/u/6806011?v=4","gravatar_id":"","url":"https://api.github.com/users/dotlambda","html_url":"https://github.com/dotlambda","followers_url":"https://api.github.com/users/dotlambda/followers","following_url":"https://api.github.com/users/dotlambda/following{/other_user}","gists_url":"https://api.github.com/users/dotlambda/gists{/gist_id}","starred_url":"https://api.github.com/users/dotlambda/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dotlambda/subscriptions","organizations_url":"https://api.github.com/users/dotlambda/orgs","repos_url":"https://api.github.com/users/dotlambda/repos","events_url":"https://api.github.com/users/dotlambda/events{/privacy}","received_events_url":"https://api.github.com/users/dotlambda/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"globin","id":1447245,"node_id":"MDQ6VXNlcjE0NDcyNDU=","avatar_url":"https://avatars.githubusercontent.com/u/1447245?v=4","gravatar_id":"","url":"https://api.github.com/users/globin","html_url":"https://github.com/globin","followers_url":"https://api.github.com/users/globin/followers","following_url":"https://api.github.com/users/globin/following{/other_user}","gists_url":"https://api.github.com/users/globin/gists{/gist_id}","starred_url":"https://api.github.com/users/globin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/globin/subscriptions","organizations_url":"https://api.github.com/users/globin/orgs","repos_url":"https://api.github.com/users/globin/repos","events_url":"https://api.github.com/users/globin/events{/privacy}","received_events_url":"https://api.github.com/users/globin/received_events","type":"User","site_admin":false},"assignees":[{"login":"globin","id":1447245,"node_id":"MDQ6VXNlcjE0NDcyNDU=","avatar_url":"https://avatars.githubusercontent.com/u/1447245?v=4","gravatar_id":"","url":"https://api.github.com/users/globin","html_url":"https://github.com/globin","followers_url":"https://api.github.com/users/globin/followers","following_url":"https://api.github.com/users/globin/following{/other_user}","gists_url":"https://api.github.com/users/globin/gists{/gist_id}","starred_url":"https://api.github.com/users/globin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/globin/subscriptions","organizations_url":"https://api.github.com/users/globin/orgs","repos_url":"https://api.github.com/users/globin/repos","events_url":"https://api.github.com/users/globin/events{/privacy}","received_events_url":"https://api.github.com/users/globin/received_events","type":"User","site_admin":false},{"login":"alyssais","id":2768870,"node_id":"MDQ6VXNlcjI3Njg4NzA=","avatar_url":"https://avatars.githubusercontent.com/u/2768870?v=4","gravatar_id":"","url":"https://api.github.com/users/alyssais","html_url":"https://github.com/alyssais","followers_url":"https://api.github.com/users/alyssais/followers","following_url":"https://api.github.com/users/alyssais/following{/other_user}","gists_url":"https://api.github.com/users/alyssais/gists{/gist_id}","starred_url":"https://api.github.com/users/alyssais/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alyssais/subscriptions","organizations_url":"https://api.github.com/users/alyssais/orgs","repos_url":"https://api.github.com/users/alyssais/repos","events_url":"https://api.github.com/users/alyssais/events{/privacy}","received_events_url":"https://api.github.com/users/alyssais/received_events","type":"User","site_admin":false},{"login":"Ma27","id":6025220,"node_id":"MDQ6VXNlcjYwMjUyMjA=","avatar_url":"https://avatars.githubusercontent.com/u/6025220?v=4","gravatar_id":"","url":"https://api.github.com/users/Ma27","html_url":"https://github.com/Ma27","followers_url":"https://api.github.com/users/Ma27/followers","following_url":"https://api.github.com/users/Ma27/following{/other_user}","gists_url":"https://api.github.com/users/Ma27/gists{/gist_id}","starred_url":"https://api.github.com/users/Ma27/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Ma27/subscriptions","organizations_url":"https://api.github.com/users/Ma27/orgs","repos_url":"https://api.github.com/users/Ma27/repos","events_url":"https://api.github.com/users/Ma27/events{/privacy}","received_events_url":"https://api.github.com/users/Ma27/received_events","type":"User","site_admin":false}],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":2,"created_at":"2022-02-07T01:48:32Z","updated_at":"2022-03-23T20:37:01Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"`python3.pkgs.mailman` is not a Python module and `python310.pkgs.mailman` actually uses Python 3.9!???\r\nIt can also not be added to `python3Packages` with the correct Python version cause it overrides sqlalchemy.\r\nThus mailman and the packages depending on it need to be removed from `python-packages.nix`.\r\ncc @mweinelt @jonringer ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158424/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158388","id":1125292095,"node_id":"I_kwDOAEVQ_M5DEpg_","number":158388,"title":"Anki 2.1 addons not working","user":{"login":"little-dude","id":6646324,"node_id":"MDQ6VXNlcjY2NDYzMjQ=","avatar_url":"https://avatars.githubusercontent.com/u/6646324?v=4","gravatar_id":"","url":"https://api.github.com/users/little-dude","html_url":"https://github.com/little-dude","followers_url":"https://api.github.com/users/little-dude/followers","following_url":"https://api.github.com/users/little-dude/following{/other_user}","gists_url":"https://api.github.com/users/little-dude/gists{/gist_id}","starred_url":"https://api.github.com/users/little-dude/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/little-dude/subscriptions","organizations_url":"https://api.github.com/users/little-dude/orgs","repos_url":"https://api.github.com/users/little-dude/repos","events_url":"https://api.github.com/users/little-dude/events{/privacy}","received_events_url":"https://api.github.com/users/little-dude/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-06T19:23:57Z","updated_at":"2022-02-06T19:23:57Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI installed this addon https://ankiweb.net/shared/info/1508357010 via the `Tools > Addons` menu. After restarting anki, a pop-up shows the following message:\r\n\r\n```\r\nAn add-on you installed failed to load. If problems persist, please go to the Tools>Add-ons menu, and disable or delete the add-on.\r\n\r\nWhen loading 'Remaining time for Anki 21':\r\nTraceback (most recent call last):\r\n File \"/nix/store/pp2b7f9vkl8912yjx3gsd1z27nrz05mw-anki-2.1.15/lib/python3.9/site-packages/aqt/addons.py\", line 80, in loadAddons\r\n __import__(dir)\r\n File \"/home/little-dude/.local/share/Anki2/addons21/1508357010/__init__.py\", line 26, in <module>\r\n from .utils import debugLog # debug log registered here\r\n File \"/home/little-dude/.local/share/Anki2/addons21/1508357010/utils/debugLog.py\", line 2, in <module>\r\n from .JSCallable import JSCallable\r\n File \"/home/little-dude/.local/share/Anki2/addons21/1508357010/utils/JSCallable.py\", line 1, in <module>\r\n from aqt import gui_hooks\r\nImportError: cannot import name 'gui_hooks' from 'aqt' (/nix/store/pp2b7f9vkl8912yjx3gsd1z27nrz05mw-anki-2.1.15/lib/python3.9/site-packages/aqt/__init__.py)\r\n```\r\n\r\nThis other plugin fails in a similar fashion: https://ankiweb.net/shared/info/446355629\r\n\r\n```\r\nAn add-on you installed failed to load. If problems persist, please go to the Tools>Add-ons menu, and disable or delete the add-on.\r\n\r\nWhen loading 'Automatic Dark Night Mode':\r\nTraceback (most recent call last):\r\n File \"/nix/store/pp2b7f9vkl8912yjx3gsd1z27nrz05mw-anki-2.1.15/lib/python3.9/site-packages/aqt/addons.py\", line 80, in loadAddons\r\n __import__(dir)\r\n File \"/home/little-dude/.local/share/Anki2/addons21/446355629/__init__.py\", line 2, in <module>\r\n from aqt.theme import theme_manager\r\nModuleNotFoundError: No module named 'aqt.theme'\r\n```\r\n\r\n### Steps To Reproduce\r\n\r\n1. install Anki 2.1 with `nix-env -iA nixos.anki\r\n2. start Anki the \"Automatic Dark Night Mode\" plugin: click `Tools > Addons > Get Add-ons...` and enter the code `446355629`.\r\n3. restart Anki, the error message appears and the plugin doesn't work\r\n\r\n### Expected behavior\r\n\r\nNo error message when starting Anki, and the plugins work\r\n\r\n### Notify maintainers\r\n\r\n@oxij @Profpatsch \r\n\r\n### Metadata\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/nzqp5skqlczar1smnc9rppnv2nxvdlzp-bash-interactive-5.1-p12-dev\r\ncopying path '/nix/store/nzqp5skqlczar1smnc9rppnv2nxvdlzp-bash-interactive-5.1-p12-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos-22.05pre350838.554d2d8aa25\"`\r\n - channels(little-dude): `\"home-manager, nixos-22.05pre337103.581d2d6c9cd\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158388/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158371","id":1125258692,"node_id":"I_kwDOAEVQ_M5DEhXE","number":158371,"title":"Request to add JanusGraph package","user":{"login":"Givemeurcookies","id":552240,"node_id":"MDQ6VXNlcjU1MjI0MA==","avatar_url":"https://avatars.githubusercontent.com/u/552240?v=4","gravatar_id":"","url":"https://api.github.com/users/Givemeurcookies","html_url":"https://github.com/Givemeurcookies","followers_url":"https://api.github.com/users/Givemeurcookies/followers","following_url":"https://api.github.com/users/Givemeurcookies/following{/other_user}","gists_url":"https://api.github.com/users/Givemeurcookies/gists{/gist_id}","starred_url":"https://api.github.com/users/Givemeurcookies/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Givemeurcookies/subscriptions","organizations_url":"https://api.github.com/users/Givemeurcookies/orgs","repos_url":"https://api.github.com/users/Givemeurcookies/repos","events_url":"https://api.github.com/users/Givemeurcookies/events{/privacy}","received_events_url":"https://api.github.com/users/Givemeurcookies/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-06T17:07:12Z","updated_at":"2022-02-06T17:11:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nJanusGraph is a distributed, open source, massively scalable graph database. JanusGraph is a scalable graph database optimized for storing and querying graphs containing hundreds of billions of vertices and edges distributed across a multi-machine cluster.\r\n\r\nJanusGraph is a project under The Linux Foundation, and includes participants from Expero, Google, GRAKN.AI, Hortonworks, IBM and Amazon.\r\n\r\nJanusGraph is capable of both OLAP and OLTP. JanusGraph is one of the most major open source graph databases which has support for Apache Tinkerpop Gremlin.\r\n\r\nCurrently JanusGraph supports several types of backend storage databases such as Apache Cassandra, Apache HBase, Google Cloud BigTable, Oracle Berkley DB and ScyllaDB. It also has support for advanced full-text search that can optionally be enabled the following indexing databases: ElasticSearch, Apache Solr and Apache Lucene.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://janusgraph.org/\r\n* source URL: https://github.com/JanusGraph/janusgraph\r\n* license: APACHE LICENSE, VERSION 2.0\r\n* platforms: Support for unix, linux, darwin and windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158371/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158368","id":1125255064,"node_id":"I_kwDOAEVQ_M5DEgeY","number":158368,"title":"Windscribe","user":{"login":"profLake","id":58558002,"node_id":"MDQ6VXNlcjU4NTU4MDAy","avatar_url":"https://avatars.githubusercontent.com/u/58558002?v=4","gravatar_id":"","url":"https://api.github.com/users/profLake","html_url":"https://github.com/profLake","followers_url":"https://api.github.com/users/profLake/followers","following_url":"https://api.github.com/users/profLake/following{/other_user}","gists_url":"https://api.github.com/users/profLake/gists{/gist_id}","starred_url":"https://api.github.com/users/profLake/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/profLake/subscriptions","organizations_url":"https://api.github.com/users/profLake/orgs","repos_url":"https://api.github.com/users/profLake/repos","events_url":"https://api.github.com/users/profLake/events{/privacy}","received_events_url":"https://api.github.com/users/profLake/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-06T16:53:24Z","updated_at":"2022-03-02T13:39:35Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nWindscribe is a commercial VPN service provider with applications for Windows, macOS, Linux, Android, and iOS with support for routers and other platforms via custom configurations. Windscribe is based in Canada.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://windscribe.com/\r\n* source URL: https://github.com/Windscribe/desktop-v2\r\n* license: gpl2.0\r\n* platforms: linux, macos, unix, windows, android, ios, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158368/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158356","id":1125209629,"node_id":"I_kwDOAEVQ_M5DEVYd","number":158356,"title":"With nix options changes, first substituter is always cache.nixos.org","user":{"login":"rapenne-s","id":248016,"node_id":"MDQ6VXNlcjI0ODAxNg==","avatar_url":"https://avatars.githubusercontent.com/u/248016?v=4","gravatar_id":"","url":"https://api.github.com/users/rapenne-s","html_url":"https://github.com/rapenne-s","followers_url":"https://api.github.com/users/rapenne-s/followers","following_url":"https://api.github.com/users/rapenne-s/following{/other_user}","gists_url":"https://api.github.com/users/rapenne-s/gists{/gist_id}","starred_url":"https://api.github.com/users/rapenne-s/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rapenne-s/subscriptions","organizations_url":"https://api.github.com/users/rapenne-s/orgs","repos_url":"https://api.github.com/users/rapenne-s/repos","events_url":"https://api.github.com/users/rapenne-s/events{/privacy}","received_events_url":"https://api.github.com/users/rapenne-s/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-02-06T13:53:58Z","updated_at":"2022-02-12T20:32:25Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nIt seems with the move from `nix.binaryCaches` to `nix.settings.substituters`, the first substitutes server is always `https://cache.nixos.org` which defeats the use of a local caching server. \r\n\r\n`/etc/nix/nix.conf` with `nix.settings.substituters = [ \"http://10.42.42.150/\" \"https://cache.nixos.org\" ];`\r\n```\r\nsubstituters = https://cache.nixos.org/ http://10.42.42.150/ https://cache.nixos.org\r\n```\r\n\r\nIf I use mkForce to force a value with `nix.settings.substituters = pkgs.lib.mkForce [ \"http://10.42.42.150/\" \"https://cache.nixos.org\" ];` I get the following `/etc/nix/nix.conf`\r\n```\r\nsubstituters = http://10.42.42.150/ https://cache.nixos.org\r\n```\r\n\r\n### Steps To Reproduce\r\n\r\nDefine a custom substituter `nix.settings.substituters = [ \"http://10.42.42.150/\" ];` , check `grep ^substituters /etc/nix/nix.conf`, you will have `https://cache.nixos.org` first in the list.\r\n\r\n\r\n### Expected behavior\r\n\r\nIt seems `https://cache.nixos.org` is always merged first in the list, it should be merged after the user defined value.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158356/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158331","id":1125135705,"node_id":"I_kwDOAEVQ_M5DEDVZ","number":158331,"title":"darwin's stdenv bootstrap tools ship a broken libiconv.dylib","user":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-06T08:08:28Z","updated_at":"2022-02-07T23:06:05Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Follow up on #158328\r\n\r\n### Steps to reproduce\r\n\r\n```\r\nnix-build pkgs/stdenv/darwin/make-bootstrap-tools.nix -A test\r\n```\r\n\r\n```\r\nclang -idirafter /nix/store/widcf6mipqv5hazgwawj5hhj5xpykgmv-unpack/include-Libsystem --sysroot=/nix/store/widcf6mipqv5hazgwawj5hhj5xpykgmv-unpack -L/nix/store/widcf6mipqv5hazgwawj5hhj5xpykgmv-unpack/lib -L/private/tmp/nix-build-test.drv-0/libSystem-boot -Wl,-rpath,/nix/store/widcf6mipqv5hazgwawj5hhj5xpykgmv-unpack/lib -Wl,-v -g -O2 -o hello src/hello.o ./lib/libhello.a \r\n@(#)PROGRAM:ld PROJECT:ld64-530\r\nBUILD 03:37:00 Jan 17 2022\r\nconfigured to support archs: armv6 armv7 armv7s arm64 arm64e arm64_32 i386 x86_64 x86_64h armv6m armv7k armv7m armv7em (tvOS)\r\nLibrary search paths:\r\n /nix/store/widcf6mipqv5hazgwawj5hhj5xpykgmv-unpack/lib\r\n /private/tmp/nix-build-test.drv-0/libSystem-boot\r\nFramework search paths:\r\nUndefined symbols for architecture x86_64:\r\n \"_iconv\", referenced from:\r\n _mem_cd_iconv in libhello.a(striconv.o)\r\n _str_cd_iconv in libhello.a(striconv.o)\r\n (maybe you meant: _str_cd_iconv, _mem_cd_iconv , _xstr_cd_iconv , _xstr_iconv , _str_iconv , _xmem_cd_iconv )\r\n \"_iconv_close\", referenced from:\r\n _str_iconv in libhello.a(striconv.o)\r\n \"_iconv_open\", referenced from:\r\n _str_iconv in libhello.a(striconv.o)\r\nld: symbol(s) not found for architecture x86_64\r\nclang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\nmake[2]: *** [Makefile:2173: hello] Error 1\r\nmake[2]: Leaving directory '/private/tmp/nix-build-test.drv-0/hello-2.12'\r\nmake[1]: *** [Makefile:2496: all-recursive] Error 1\r\nmake[1]: Leaving directory '/private/tmp/nix-build-test.drv-0/hello-2.12'\r\nmake: *** [Makefile:1899: all] Error 2\r\n```\r\n\r\n### Problem\r\n\r\nThe library itself doesn't contain any symbols:\r\n```\r\nnm $(nix-build pkgs/stdenv/darwin/make-bootstrap-tools.nix -A build --no-out-link)/pack/lib/libiconv.dylib\r\n0000000000000fb0 T _dont_use_this\r\n U dyld_stub_binder\r\n```\r\n\r\nIt seems to rely on LC_REEXPORT_DYLIB to link to the two other libraries:\r\n```\r\notool -l $(nix-build pkgs/stdenv/darwin/make-bootstrap-tools.nix -A build --no-out-link)/pack/lib/libiconv.dylib | grep -A6 LC_REEXPORT_DYLIB\r\n cmd LC_REEXPORT_DYLIB\r\n cmdsize 56\r\n name @rpath/libiconv-nocharset.dylib (offset 24)\r\n time stamp 2 Wed Dec 31 19:00:02 1969\r\n current version 7.0.0\r\ncompatibility version 7.0.0\r\nLoad command 9\r\n cmd LC_REEXPORT_DYLIB\r\n cmdsize 56\r\n name @rpath/libcharset.1.dylib (offset 24)\r\n time stamp 2 Wed Dec 31 19:00:02 1969\r\n current version 2.0.0\r\ncompatibility version 2.0.0\r\nLoad command 10\r\n```\r\n\r\nHowever the RPATH is not set for the library (the store path can not be known in advance). But set during the test:\r\nhttps://github.com/NixOS/nixpkgs/blob/598c791f2c79c3a81921722cfe928ebcfd46f125/pkgs/stdenv/darwin/make-bootstrap-tools.nix#L332\r\nPerhaps this should use `@origin` (but would that work for linking libhello?). And/or it could be that we can get rid of libiconv from the tools.\r\n\r\nThe normal version just uses full paths:\r\n\r\n```\r\notool -l $(nix-build -A darwin.libiconv --no-out-link)/lib/libiconv.dylib | grep -A6 LC_REEXPORT_DYLIB\r\n cmd LC_REEXPORT_DYLIB\r\n cmdsize 112\r\n name /nix/store/cp7cr0c6q5cl4zxmpv21xzpaj131q9n8-libiconv-50/lib/libiconv-nocharset.dylib (offset 24)\r\n time stamp 2 Wed Dec 31 19:00:02 1969\r\n current version 7.0.0\r\ncompatibility version 7.0.0\r\nLoad command 9\r\n cmd LC_REEXPORT_DYLIB\r\n cmdsize 104\r\n name /nix/store/cp7cr0c6q5cl4zxmpv21xzpaj131q9n8-libiconv-50/lib/libcharset.1.dylib (offset 24)\r\n time stamp 2 Wed Dec 31 19:00:02 1969\r\n current version 2.0.0\r\ncompatibility version 2.0.0\r\nLoad command 10\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158331/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158284","id":1125038731,"node_id":"I_kwDOAEVQ_M5DDrqL","number":158284,"title":"gitlab-runner module re-registers too often.","user":{"login":"kevincox","id":494012,"node_id":"MDQ6VXNlcjQ5NDAxMg==","avatar_url":"https://avatars.githubusercontent.com/u/494012?v=4","gravatar_id":"","url":"https://api.github.com/users/kevincox","html_url":"https://github.com/kevincox","followers_url":"https://api.github.com/users/kevincox/followers","following_url":"https://api.github.com/users/kevincox/following{/other_user}","gists_url":"https://api.github.com/users/kevincox/gists{/gist_id}","starred_url":"https://api.github.com/users/kevincox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kevincox/subscriptions","organizations_url":"https://api.github.com/users/kevincox/orgs","repos_url":"https://api.github.com/users/kevincox/repos","events_url":"https://api.github.com/users/kevincox/events{/privacy}","received_events_url":"https://api.github.com/users/kevincox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-05T21:48:55Z","updated_at":"2022-02-06T00:44:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nRight now gitlab-runner registers itself with a hash of the config used in the name, if the config changes the name changes causing a re-registration.\r\n\r\nThis is problematic because you can configure a registered runner to be used across multiple projects, however a fresh registration will only appear in one project or group.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Change a setting such as `services.gitlab-runner.services.yourservice.environmentVariables`.\r\n2. Update your configuration.\r\n3. Notice that the runner re-registers.\r\n\r\n### Expected behavior\r\nThe runner starts using the new configuration with the same registration.\r\n\r\n### Additional context\r\n\r\nIt appears that the current design is based on https://gitlab.com/arianvp/nixos-gitlab-runner/-/blob/9126927c701aa399bd1734e7e5230c3a0010c1b7/README.md by @arianvp. I have to admit, the whole document is perplexing to me but maybe I haven't run enough runners to understand.\r\n\r\n> The current gitlab-runner module in NixOS is severely broken, as it modifies the config.toml file, which is not a configuration file, but the file that gitlab-ci uses to store internal state, and thus is modified heavily by the gitlab-runner daemon.\r\n\r\nThis seems to be the core argument of the file, but I have not found this to be true. In my history of running a (simple local docker) runner this file has not been modified. The only modification I have seen is during the initial setup. In fact a quick look at the source [shows that saveConfig is only called in service (install and configure a service), register, unregister and verify](https://sourcegraph.com/search?q=context:global+repo:%5Egitlab%5C.com/gitlab-org/gitlab-runner%24%4075b51c1+saveConfig&patternType=literal). So it is only used by setup which should be managed by NixOS, making me think that this premise is flawed. \r\n\r\n> By delegating this task to the gitlab-runner register command...\r\n\r\nThis does make writing the config file slightly easier, but it also seems to prevent updating the config without re-registering which seems to be a terrible tradeoff.\r\n\r\n> and we get automatic declarative registration and de-registration of runners.\r\n\r\nI'm not sure I understand this. [Looking at the code the registration and de-registration are manual in the setup script.](https://github.com/NixOS/nixpkgs/blob/554d2d8aa25b6e583575459c297ec23750adb6cb/nixos/modules/services/continuous-integration/gitlab-runner.nix#L30-L39) or maybe this part of the file wasn't integrated.\r\n\r\n---\r\n\r\nIf I were writing the module from scratch it would look very different. I would appreciate if we can discuss the flaws and benefits of this system.\r\n\r\n1. Generate a config file from the settings. In theory we could probably just provide an `extraConfig` option and serialize it to TOML. However it probably makes sense to retain support for the existing settings passed manually in the module.\r\n2. Use a separate \"registration config file\" which is just used for the register commands.\r\n3. Check, add and remove registrations much like today. However just use `${name}_${hostname}`. **No config hash**.\r\n4. To start the runner pull the `token` values out of the \"registration config file\" and merge them into the generated config file.\r\n\r\nPros:\r\n1. We don't rely on any default settings, we have full control over the config file.\r\n2. Updating the config doesn't require re-registration (unless you add or remove services of course).\r\n3. No config hash in the name.\r\n4. Ability for setting any value in the config file in a way that is understandable to the rest of the NixOS config (`services.gitlab-runner.services.yourservice.extraConfig.runners.docker.tls_verify = true` vs `services.gitlab-runner.services.yourservice.registrationFlags = [\"--docker-tlsverify=true\"]`)\r\n\r\nCons:\r\n1. We are assuming that:\r\n - The `token` is the only important output of registration.\r\n - That `token` never changes (for example it isn't rotated). However rotating tokens could be handled with only slightly more complexity.\r\n2. Re-registration also wipes out manual edits to Active, Protected, Max Timeout and Tags settings which has the effect of enforcing the NixOS configured values.\r\n - Ideally for existing registrations they would be updated to reflect the current values, however there appears to be no built-in gitlab-runner command for this, so this would need to be done via the API directly.\r\n - On the other hand some people may prefer to configure things such as \"Active\" in GitLab for the easy of temporarily pausing/resuming runners.\r\n3. It becomes hard to support the currently provided `registrationFlags` which is currently used to pass runner service configuration. It would probably need to be removed. \r\n\r\n### Notify maintainers\r\n@misuzu @bachp @zimbatm @globin\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158284/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158258","id":1124976061,"node_id":"I_kwDOAEVQ_M5DDcW9","number":158258,"title":"Package request: emptty","user":{"login":"StarrFox","id":43019162,"node_id":"MDQ6VXNlcjQzMDE5MTYy","avatar_url":"https://avatars.githubusercontent.com/u/43019162?v=4","gravatar_id":"","url":"https://api.github.com/users/StarrFox","html_url":"https://github.com/StarrFox","followers_url":"https://api.github.com/users/StarrFox/followers","following_url":"https://api.github.com/users/StarrFox/following{/other_user}","gists_url":"https://api.github.com/users/StarrFox/gists{/gist_id}","starred_url":"https://api.github.com/users/StarrFox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/StarrFox/subscriptions","organizations_url":"https://api.github.com/users/StarrFox/orgs","repos_url":"https://api.github.com/users/StarrFox/repos","events_url":"https://api.github.com/users/StarrFox/events{/privacy}","received_events_url":"https://api.github.com/users/StarrFox/received_events","type":"User","site_admin":false},"labels":[{"id":287403097,"node_id":"MDU6TGFiZWwyODc0MDMwOTc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20good-first-bug","name":"3.skill: good-first-bug","color":"f7c6c7","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"a-vorobiev","id":197565,"node_id":"MDQ6VXNlcjE5NzU2NQ==","avatar_url":"https://avatars.githubusercontent.com/u/197565?v=4","gravatar_id":"","url":"https://api.github.com/users/a-vorobiev","html_url":"https://github.com/a-vorobiev","followers_url":"https://api.github.com/users/a-vorobiev/followers","following_url":"https://api.github.com/users/a-vorobiev/following{/other_user}","gists_url":"https://api.github.com/users/a-vorobiev/gists{/gist_id}","starred_url":"https://api.github.com/users/a-vorobiev/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a-vorobiev/subscriptions","organizations_url":"https://api.github.com/users/a-vorobiev/orgs","repos_url":"https://api.github.com/users/a-vorobiev/repos","events_url":"https://api.github.com/users/a-vorobiev/events{/privacy}","received_events_url":"https://api.github.com/users/a-vorobiev/received_events","type":"User","site_admin":false},"assignees":[{"login":"a-vorobiev","id":197565,"node_id":"MDQ6VXNlcjE5NzU2NQ==","avatar_url":"https://avatars.githubusercontent.com/u/197565?v=4","gravatar_id":"","url":"https://api.github.com/users/a-vorobiev","html_url":"https://github.com/a-vorobiev","followers_url":"https://api.github.com/users/a-vorobiev/followers","following_url":"https://api.github.com/users/a-vorobiev/following{/other_user}","gists_url":"https://api.github.com/users/a-vorobiev/gists{/gist_id}","starred_url":"https://api.github.com/users/a-vorobiev/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/a-vorobiev/subscriptions","organizations_url":"https://api.github.com/users/a-vorobiev/orgs","repos_url":"https://api.github.com/users/a-vorobiev/repos","events_url":"https://api.github.com/users/a-vorobiev/events{/privacy}","received_events_url":"https://api.github.com/users/a-vorobiev/received_events","type":"User","site_admin":false}],"milestone":null,"comments":4,"created_at":"2022-02-05T16:52:59Z","updated_at":"2022-03-12T15:15:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nA simple to use cli display manager\r\n\r\n**Metadata**\r\n\r\n* source URL: https://github.com/tvrzna/emptty\r\n* license: MIT\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158258/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158197","id":1124818404,"node_id":"I_kwDOAEVQ_M5DC13k","number":158197,"title":"I cant use llpp to view a pdf.","user":{"login":"prehonor","id":10784632,"node_id":"MDQ6VXNlcjEwNzg0NjMy","avatar_url":"https://avatars.githubusercontent.com/u/10784632?v=4","gravatar_id":"","url":"https://api.github.com/users/prehonor","html_url":"https://github.com/prehonor","followers_url":"https://api.github.com/users/prehonor/followers","following_url":"https://api.github.com/users/prehonor/following{/other_user}","gists_url":"https://api.github.com/users/prehonor/gists{/gist_id}","starred_url":"https://api.github.com/users/prehonor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prehonor/subscriptions","organizations_url":"https://api.github.com/users/prehonor/orgs","repos_url":"https://api.github.com/users/prehonor/repos","events_url":"https://api.github.com/users/prehonor/events{/privacy}","received_events_url":"https://api.github.com/users/prehonor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-05T03:39:09Z","updated_at":"2022-02-10T15:00:31Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nllpp Pro\\ Java\\ 7\\ NIO.2.pdf \r\nFatal error: exception Failure(\"X connection failed maj=11 min=0 reason=\\\"No protocol specified\\\\n\\\"\")\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install llpp\r\n2. llpp xxx.pdf in terminal\r\n\r\n\r\n### Additional context\r\nno\r\n\r\n### Notify maintainers\r\n@pSub \r\n\r\n### Metadata\r\n\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.94, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158197/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158182","id":1124730008,"node_id":"I_kwDOAEVQ_M5DCgSY","number":158182,"title":"Dovecot utilities not usable from Nix store; must be installed in /etc","user":{"login":"chkno","id":1118859,"node_id":"MDQ6VXNlcjExMTg4NTk=","avatar_url":"https://avatars.githubusercontent.com/u/1118859?v=4","gravatar_id":"","url":"https://api.github.com/users/chkno","html_url":"https://github.com/chkno","followers_url":"https://api.github.com/users/chkno/followers","following_url":"https://api.github.com/users/chkno/following{/other_user}","gists_url":"https://api.github.com/users/chkno/gists{/gist_id}","starred_url":"https://api.github.com/users/chkno/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/chkno/subscriptions","organizations_url":"https://api.github.com/users/chkno/orgs","repos_url":"https://api.github.com/users/chkno/repos","events_url":"https://api.github.com/users/chkno/events{/privacy}","received_events_url":"https://api.github.com/users/chkno/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-05T00:08:16Z","updated_at":"2022-02-08T05:14:04Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nBasic unprivileged dovecot utility functionality requires dovecot to be installed system-wide. This makes it impossible to use dovecot utilities without administrator privileges, and makes it impossible for multiple versions of dovecot to coexist on the same machine. These are core Nix competencies & it's surprising to find them lacking for this package.\r\n\r\n\r\n### Steps To Reproduce\r\nOn a machine without dovecot installed system-wide, try to generate a password hash:\r\n```\r\n$ nix-shell -p dovecot --run \"doveadm -c /dev/null pw -p foo\"\r\ndoveadm(init): Fatal: opendir(/etc/dovecot/modules) failed: No such file or directory\r\n```\r\n\r\n\r\n### Expected behavior\r\n```\r\n$ nix-shell -p dovecot --run \"doveadm -c /dev/null pw -p foo\"\r\n{CRYPT}$2y$05$EskrTH1AHHe32GLh7nL9X.jr28KUY.F2/CzvKjfoyG1M0h/KywcCe\r\n```\r\n\r\n### Additional context\r\nThis is caused by [nixpkgs's own patch](https://github.com/NixOS/nixpkgs/blob/release-21.11/pkgs/servers/mail/dovecot/2.3.x-module_dir.patch) which modifies upstream's module-directory logic to force it to be in /etc. Just removing this patch makes things work again:\r\n\r\n```\r\n$ nix-shell -p 'dovecot.overrideAttrs (_: { patches = []; })' --run \"doveadm -c /dev/null pw -p foo\"\r\n{CRYPT}$2y$05$czS/oyWodmqA5Rq06y3iie9SyVoteHhfnPOWD1X27kfPfoxNPH3mC\r\n```\r\n\r\nThis was implemented in 2013 in 93ff42ae9c33b2f507c766ac5b2398cfd287ef30 as a way to allow combining dovecot modules from multiple derivations. Since 2013, nixpkgs has figured out much better ways to do this (eg: the various withPackages mechanisms). Dovecot's mechanism needs to be updated to these more recent, better practices.\r\n\r\n### Notify maintainers\r\nMaintainers: @fpletz @globin @ajs124\r\nAuthor of 93ff42ae9c33b2f507c766ac5b2398cfd287ef30: @rickynils","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158182/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158175","id":1124689118,"node_id":"I_kwDOAEVQ_M5DCWTe","number":158175,"title":"electron,google-chrome: Ozone/Wayland is broken","user":{"login":"primeos","id":7537109,"node_id":"MDQ6VXNlcjc1MzcxMDk=","avatar_url":"https://avatars.githubusercontent.com/u/7537109?v=4","gravatar_id":"","url":"https://api.github.com/users/primeos","html_url":"https://github.com/primeos","followers_url":"https://api.github.com/users/primeos/followers","following_url":"https://api.github.com/users/primeos/following{/other_user}","gists_url":"https://api.github.com/users/primeos/gists{/gist_id}","starred_url":"https://api.github.com/users/primeos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/primeos/subscriptions","organizations_url":"https://api.github.com/users/primeos/orgs","repos_url":"https://api.github.com/users/primeos/repos","events_url":"https://api.github.com/users/primeos/events{/privacy}","received_events_url":"https://api.github.com/users/primeos/received_events","type":"User","site_admin":false},"labels":[{"id":436938058,"node_id":"MDU6TGFiZWw0MzY5MzgwNTg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20regression","name":"0.kind: regression","color":"84b6eb","default":false,"description":"Something that worked before working no longer"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":15,"created_at":"2022-02-04T22:56:08Z","updated_at":"2022-04-26T01:46:46Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Electron: Broken since 16.0.6 (or 16.0.5): https://github.com/NixOS/nixpkgs/commit/e06082eda06ee586de17e0a060e8cd0eddd20c69\r\n- Segfaults at startup (also tested via the not yet packaged version 17.0.0).\r\n- **Actionable:** The packaging might need improvements for Ozone/Wayland support (s. Google Chrome changes - e.g. libglvnd, pciutils, and the changes for Vulkan).\r\n- Relevant upstream issue for Electron 16: https://github.com/electron/electron/issues/32436\r\n\r\nGoogle Chrome: Broken since M98(?).\r\n- Software rendering still works (and hardware rendering might be fixable via flags or Nixpkgs packaging changes).\r\n- TODO: Paste the logs (could be GPU driver dependent)\r\n\r\nThis issue lacks information but I decided to open it anyway to track those regressions. Any help would be welcome.\r\n\r\ncc @Synthetica9 (https://github.com/NixOS/nixpkgs/issues/156352)\r\ncc @travisbhartwell @manveru @prusnak (Electron maintainers)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175/reactions","total_count":5,"+1":5,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158175/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158154","id":1124543294,"node_id":"I_kwDOAEVQ_M5DBys-","number":158154,"title":"Installing Nuitka from master can't find fuse library \"(libfuse.so.x from fuse2, *not* fuse3)\"","user":{"login":"shadowrylander","id":12785394,"node_id":"MDQ6VXNlcjEyNzg1Mzk0","avatar_url":"https://avatars.githubusercontent.com/u/12785394?v=4","gravatar_id":"","url":"https://api.github.com/users/shadowrylander","html_url":"https://github.com/shadowrylander","followers_url":"https://api.github.com/users/shadowrylander/followers","following_url":"https://api.github.com/users/shadowrylander/following{/other_user}","gists_url":"https://api.github.com/users/shadowrylander/gists{/gist_id}","starred_url":"https://api.github.com/users/shadowrylander/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/shadowrylander/subscriptions","organizations_url":"https://api.github.com/users/shadowrylander/orgs","repos_url":"https://api.github.com/users/shadowrylander/repos","events_url":"https://api.github.com/users/shadowrylander/events{/privacy}","received_events_url":"https://api.github.com/users/shadowrylander/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-04T19:29:13Z","updated_at":"2022-02-09T19:59:24Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`FATAL: Error, the fuse library (libfuse.so.x from fuse2, *not* fuse3) must be installed for onefile creation to work on Linux.`\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install `Nuitka` from master `(commit: 50178beea3b05144d557cc69a285670a7ca972f8)`\r\n2. `nuitka3 --onefile --linux-onefile-icon=[path] --follow-imports [file].py`\r\n\r\n### Expected behavior\r\nI thought I'd get a binary out of this.\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.13.4, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(shadowrylander): `\"master\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158154/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158125","id":1124250120,"node_id":"I_kwDOAEVQ_M5DArII","number":158125,"title":"Packaging Request: instaloader","user":{"login":"nvmd","id":524492,"node_id":"MDQ6VXNlcjUyNDQ5Mg==","avatar_url":"https://avatars.githubusercontent.com/u/524492?v=4","gravatar_id":"","url":"https://api.github.com/users/nvmd","html_url":"https://github.com/nvmd","followers_url":"https://api.github.com/users/nvmd/followers","following_url":"https://api.github.com/users/nvmd/following{/other_user}","gists_url":"https://api.github.com/users/nvmd/gists{/gist_id}","starred_url":"https://api.github.com/users/nvmd/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nvmd/subscriptions","organizations_url":"https://api.github.com/users/nvmd/orgs","repos_url":"https://api.github.com/users/nvmd/repos","events_url":"https://api.github.com/users/nvmd/events{/privacy}","received_events_url":"https://api.github.com/users/nvmd/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-04T14:13:54Z","updated_at":"2022-02-04T15:45:20Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nInstaloader is a tool to download pictures (or videos) along with their captions and other metadata from Instagram.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://instaloader.github.io/\r\n* source URL: https://github.com/instaloader/instaloader\r\n* license: mit\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158125/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158119","id":1124217587,"node_id":"I_kwDOAEVQ_M5DAjLz","number":158119,"title":"asyncpg: 0.25.0","user":{"login":"genofire","id":6905586,"node_id":"MDQ6VXNlcjY5MDU1ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6905586?v=4","gravatar_id":"","url":"https://api.github.com/users/genofire","html_url":"https://github.com/genofire","followers_url":"https://api.github.com/users/genofire/followers","following_url":"https://api.github.com/users/genofire/following{/other_user}","gists_url":"https://api.github.com/users/genofire/gists{/gist_id}","starred_url":"https://api.github.com/users/genofire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/genofire/subscriptions","organizations_url":"https://api.github.com/users/genofire/orgs","repos_url":"https://api.github.com/users/genofire/repos","events_url":"https://api.github.com/users/genofire/events{/privacy}","received_events_url":"https://api.github.com/users/genofire/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-04T13:41:39Z","updated_at":"2022-02-05T23:54:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: asyncpg\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: v0.24.0\r\ndesired version: v0.25.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers:\r\n\r\n@eadwu \r\n\r\n###### Note for maintainers\r\nMautrix-Telegram is broken with current error:\r\n```\r\nFeb 04 14:32:29 matrix-fo mautrix-telegram[715]: hostlist_ports.append(int(hostspec_port))\r\nFeb 04 14:32:29 matrix-fo mautrix-telegram[715]: ValueError: invalid literal for int() with base 10: '1234:5678:1::2]'\r\n```\r\nit is fixed here: https://github.com/MagicStack/asyncpg/pull/845 and released in v0.25.0","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158119/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158076","id":1123774925,"node_id":"I_kwDOAEVQ_M5C-3HN","number":158076,"title":"v8 fails to build on darwin","user":{"login":"viraptor","id":188063,"node_id":"MDQ6VXNlcjE4ODA2Mw==","avatar_url":"https://avatars.githubusercontent.com/u/188063?v=4","gravatar_id":"","url":"https://api.github.com/users/viraptor","html_url":"https://github.com/viraptor","followers_url":"https://api.github.com/users/viraptor/followers","following_url":"https://api.github.com/users/viraptor/following{/other_user}","gists_url":"https://api.github.com/users/viraptor/gists{/gist_id}","starred_url":"https://api.github.com/users/viraptor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/viraptor/subscriptions","organizations_url":"https://api.github.com/users/viraptor/orgs","repos_url":"https://api.github.com/users/viraptor/repos","events_url":"https://api.github.com/users/viraptor/events{/privacy}","received_events_url":"https://api.github.com/users/viraptor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":21,"created_at":"2022-02-04T03:36:15Z","updated_at":"2022-03-02T10:40:32Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nV8 fails to build with:\r\n```\r\nIn file included from ../../src/libplatform/tracing/trace-writer.cc:14:\r\n../../src/libplatform/tracing/recorder.h:17:10: fatal error: 'os/signpost.h' file not found\r\n#include <os/signpost.h>\r\n ^~~~~~~~~~~~~~~\r\n1 error generated.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. build v8 from latest unstable (v8-9.7.106.18)\r\n\r\n### Additional context\r\n\r\nIt seems the same issue has been discussed and fixed for nodejs here https://github.com/NixOS/nixpkgs/pull/132543 so the fix for v8 should be similar.\r\n\r\n### Notify maintainers\r\n@cstrahan @proglodyte @matthewbauer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - channels(viraptor): `\"home-manager-21.11.tar.gz, unstable\"`\r\n - channels(root): `\"nixpkgs\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158076/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158046","id":1123586449,"node_id":"I_kwDOAEVQ_M5C-JGR","number":158046,"title":"Pulseaudio fails to install if override disables systemd","user":{"login":"johnrichardrinehart","id":6321578,"node_id":"MDQ6VXNlcjYzMjE1Nzg=","avatar_url":"https://avatars.githubusercontent.com/u/6321578?v=4","gravatar_id":"","url":"https://api.github.com/users/johnrichardrinehart","html_url":"https://github.com/johnrichardrinehart","followers_url":"https://api.github.com/users/johnrichardrinehart/followers","following_url":"https://api.github.com/users/johnrichardrinehart/following{/other_user}","gists_url":"https://api.github.com/users/johnrichardrinehart/gists{/gist_id}","starred_url":"https://api.github.com/users/johnrichardrinehart/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/johnrichardrinehart/subscriptions","organizations_url":"https://api.github.com/users/johnrichardrinehart/orgs","repos_url":"https://api.github.com/users/johnrichardrinehart/repos","events_url":"https://api.github.com/users/johnrichardrinehart/events{/privacy}","received_events_url":"https://api.github.com/users/johnrichardrinehart/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-03T21:45:06Z","updated_at":"2022-02-03T21:51:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nTrying to override `useSystemd` in `pulseaudio` fails.\r\n\r\n```\r\n pulseaudio = pkgs.pulseaudio.override {\r\n useSystemd = false;\r\n };\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add [the below block to a system configuration](https://github.com/johnrichardrinehart/JohnOS/blob/3a611007de2035bd96231c6c918cb39003e5c7b3/users/common.nix#L326-L328) (confirmed in `21.11` and `nixos-unstable`\r\n```\r\n pulseaudio = pkgs.pulseaudio.override {\r\n useSystemd = false;\r\n };\r\n\r\n environment.systemPackages = [ pulseaudio ];\r\n```\r\n\r\n### Expected behavior\r\n\r\nI should get a build of `pulseaudio` with all of the binary tools that I need (like `pactl`) without having the `pulseaudio` systemd service/socket that conflicts with `pipewire`.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\n\r\nYou can see a failed build of such a system [here](https://github.com/johnrichardrinehart/JohnOS/actions/runs/1791628365).\r\n\r\n### Notify maintainers\r\n\r\n@lovek323 @civodul @Mic92 @dtzWill (common people on the `git blame pkgs/servers/pulseaudio/default.nix` besides Eelco).\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.5, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.7.0pre20220202_fcb3344`\r\n - channels(root): `\"nixos-22.05.20220202.554d2d8\"`\r\n - nixpkgs: `/nix/store/pi099gbqmvjaqk6d77c9r9g08mm70w8b-source`\r\n ```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158046/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158042","id":1123554905,"node_id":"I_kwDOAEVQ_M5C-BZZ","number":158042,"title":"bootstrap linux mixes crt1 from bootstrap libc and libc.so.6 from new libc, sometimes fails linking","user":{"login":"trofi","id":226650,"node_id":"MDQ6VXNlcjIyNjY1MA==","avatar_url":"https://avatars.githubusercontent.com/u/226650?v=4","gravatar_id":"","url":"https://api.github.com/users/trofi","html_url":"https://github.com/trofi","followers_url":"https://api.github.com/users/trofi/followers","following_url":"https://api.github.com/users/trofi/following{/other_user}","gists_url":"https://api.github.com/users/trofi/gists{/gist_id}","starred_url":"https://api.github.com/users/trofi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/trofi/subscriptions","organizations_url":"https://api.github.com/users/trofi/orgs","repos_url":"https://api.github.com/users/trofi/repos","events_url":"https://api.github.com/users/trofi/events{/privacy}","received_events_url":"https://api.github.com/users/trofi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":897230915,"node_id":"MDU6TGFiZWw4OTcyMzA5MTU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20stdenv","name":"6.topic: stdenv","color":"fef2c0","default":false,"description":"Standard environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-03T21:07:57Z","updated_at":"2022-02-12T00:44:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"The best way to show the problem is to try to build current nixpkgs against glibc.2.35, patch:\r\n- ~~[0001-glibc-2.33-2.35.patch.txt](https://github.com/NixOS/nixpkgs/files/7998198/0001-glibc-2.33-2.35.patch.txt)~~ \r\n- ~~[v2-0001-glibc-2.33-2.35.patch.txt](https://github.com/NixOS/nixpkgs/files/8052200/v2-0001-glibc-2.33-2.35.patch.txt)~~\r\n- [v3-0001-glibc-2.33-2.35.patch.txt](https://github.com/NixOS/nixpkgs/files/8052388/v3-0001-glibc-2.33-2.35.patch.txt)\r\n\r\n\r\n\r\nIt fails to build simplest program as:\r\n\r\n```\r\n$ nix build -f. lv -L --max-jobs 1\r\nexpand-response-params> unpacking sources\r\nexpand-response-params> patching sources\r\nexpand-response-params> configuring\r\nexpand-response-params> no configure script, doing nothing\r\nexpand-response-params> building\r\nexpand-response-params> /nix/store/w2x0imn84ckw6y83p72rigj3h5ymmwll-binutils-2.35.2/bin/ld: /nix/store/p4s4jf7aq6v6z9iazll1aiqwb34aqxq9-bootstrap-tools/lib/crt1.o: in function `_start':\r\nexpand-response-params> /build/glibc-2.27/csu/../sysdeps/x86_64/start.S:101: undefined reference to `__libc_csu_fini'\r\nexpand-response-params> /nix/store/w2x0imn84ckw6y83p72rigj3h5ymmwll-binutils-2.35.2/bin/ld: /build/glibc-2.27/csu/../sysdeps/x86_64/start.S:102: undefined reference to `__libc_csu_init'\r\nexpand-response-params> collect2: error: ld returned 1 exit status\r\n```\r\n\r\nIf I add a bit of debugging it becomes more clear where mismatch comes from:\r\n\r\n```diff\r\n--- a/pkgs/build-support/expand-response-params/default.nix\r\n+++ b/pkgs/build-support/expand-response-params/default.nix\r\n@@ -10,7 +10,8 @@ stdenv.mkDerivation {\r\n src=$PWD\r\n '';\r\n buildPhase = ''\r\n- NIX_CC_USE_RESPONSE_FILE=0 \"$CC\" -std=c99 -O3 -o \"expand-response-params\" expand-response-params.c\r\n+ export NIX_DEBUG=1\r\n+ NIX_CC_USE_RESPONSE_FILE=0 \"$CC\" -std=c99 -O3 -o \"expand-response-params\" expand-response-params.c -Wl,--verbose\r\n '';\r\n installPhase = ''\r\n mkdir -p $prefix/bin\r\n```\r\n\r\n```\r\n$ nb --max-jobs 1 -L lv |& grep -P '(crt1|libc[.]so).*succeed'\r\nexpand-response-params> attempt to open /nix/store/i3ibpx67yncp4w4mpkf5pwvjjsd0aqln-bootstrap-tools/lib/crt1.o succeeded\r\nexpand-response-params> attempt to open /nix/store/bf7l4af8rrfy1s17af4j2az0khlp5rw0-glibc-2.35/lib/libc.so succeeded\r\nexpand-response-params> attempt to open /nix/store/bf7l4af8rrfy1s17af4j2az0khlp5rw0-glibc-2.35/lib/libc.so.6 succeeded\r\n```\r\n\r\nMy theory is that it was not visible before because until `glibc-2.35` `crt1.o` did not change much. But upstream https://sourceware.org/git/?p=glibc.git;a=commitdiff;h=035c012e32c11e84d64905efaf55e74f704d3668 change made it visible.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158042/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158031","id":1123491460,"node_id":"I_kwDOAEVQ_M5C9x6E","number":158031,"title":"nixos/test-driver: semantic keys","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-03T19:52:19Z","updated_at":"2022-02-03T19:52:19Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"This may be a bit silly, but it's also something we could totally do if we want to. Currently, we use strings for `machine.send_key`, which are directly dumped into the QEMU command line. If you mess up here (wrong name for something, etc), you get a weird and hard-to-debug failure. \r\n\r\nThe proposed change here is to add objects in scope for either all keys or only \"special\" keys, and a way to combine them (either via `-` or `.`). Example\r\n\r\n```\r\n# old:\r\nmachine.send_key(\"ctrl-alt-t\")\r\n# either:\r\nmachine.send_key(ctrl-alt-t)\r\n# or:\r\nmachine.send_key(ctrl.alt.t)\r\n```\r\n\r\nThis would allow us to fail earlier, resulting in an error when checking the script when you write something like `machine.send_key(control.alt.t)` instead of failing really late, making the debugging experience better.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158031/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158025","id":1123454015,"node_id":"I_kwDOAEVQ_M5C9ow_","number":158025,"title":"Swaylock not getting through pam check, when installed through home-manager","user":{"login":"x10an14","id":710608,"node_id":"MDQ6VXNlcjcxMDYwOA==","avatar_url":"https://avatars.githubusercontent.com/u/710608?v=4","gravatar_id":"","url":"https://api.github.com/users/x10an14","html_url":"https://github.com/x10an14","followers_url":"https://api.github.com/users/x10an14/followers","following_url":"https://api.github.com/users/x10an14/following{/other_user}","gists_url":"https://api.github.com/users/x10an14/gists{/gist_id}","starred_url":"https://api.github.com/users/x10an14/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/x10an14/subscriptions","organizations_url":"https://api.github.com/users/x10an14/orgs","repos_url":"https://api.github.com/users/x10an14/repos","events_url":"https://api.github.com/users/x10an14/events{/privacy}","received_events_url":"https://api.github.com/users/x10an14/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":20,"created_at":"2022-02-03T19:07:58Z","updated_at":"2022-03-27T04:34:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nMy `swaylock` is unable to unlock my password/sway DE.\r\n\r\n### Steps To Reproduce\r\n1. `sudo nixos-rebuild switch --flake https://git.sr.ht/~x10an14/nixos-config/commit/60d5555977ebc0cd1e6a52b1394fd362f5ba245b#`\r\n1. `home-manager switch --flake https://git.sr.ht/~x10an14/home-manager-config/commit/7d0fcfe9922a7772422d697fc2d70f79901c8c30`\r\n1. Log into sway\r\n1. `swaylock`\r\n\r\n### Expected behavior\r\nCorrect password input into `swaylock` to unlock and return user to `sway`.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nI install swaylock/swaylock-effects through home-manager.\r\nDue to https://github.com/NixOS/nixpkgs/issues/143365 I have the below enabled in my flaked nixos configuration (separate/independent flake from my hm config).\r\n```nix\r\nsecurity.pam.services.swaylock = {};\r\n```\r\n\r\nThis is what appears in the output of `sway` itself (1x per attempted unlock):\r\n```\r\n[pam.c:101] pam_authenticate failed: invalid credentials\r\n```\r\n---\r\nAs mentioned in this issue thread (https://github.com/NixOS/nixpkgs/issues/157112#issuecomment-1024250758), I had a similar issue 6 days ago.\r\nBut back then that fix referenced worked for me. And has worked until today/yesterday.\r\n\r\nIt doesn't work, even after updating to latest releases of `nixos-unstable` as shown in above flakes, and explained here: https://github.com/NixOS/nixpkgs/issues/157112#issuecomment-1029282194\r\n\r\n### Notify maintainers\r\n@gnxlxnxx @primeos \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158025/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158022","id":1123445438,"node_id":"I_kwDOAEVQ_M5C9mq-","number":158022,"title":"coreutils: can't build","user":{"login":"nyarly","id":127548,"node_id":"MDQ6VXNlcjEyNzU0OA==","avatar_url":"https://avatars.githubusercontent.com/u/127548?v=4","gravatar_id":"","url":"https://api.github.com/users/nyarly","html_url":"https://github.com/nyarly","followers_url":"https://api.github.com/users/nyarly/followers","following_url":"https://api.github.com/users/nyarly/following{/other_user}","gists_url":"https://api.github.com/users/nyarly/gists{/gist_id}","starred_url":"https://api.github.com/users/nyarly/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nyarly/subscriptions","organizations_url":"https://api.github.com/users/nyarly/orgs","repos_url":"https://api.github.com/users/nyarly/repos","events_url":"https://api.github.com/users/nyarly/events{/privacy}","received_events_url":"https://api.github.com/users/nyarly/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-02-03T18:58:03Z","updated_at":"2022-02-20T17:37:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nI cannot currently update one of my nixos systems, because it wants to build coreutils, and a test on dd fails.\r\n\r\n### Steps To Reproduce\r\n\r\nI'm advised that most users are able to fetch coreutils without building it. I'm not sure why my system want to build it, so I'm not clear how to reproduce, but `sudo nixos-rebuild switch` is sufficient on my system.\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nSystem update. coreutils needing to build shouldn't be a blocker.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n```\r\nFAIL: tests/dd/direct\r\n=====================\r\n\r\ndd: error reading 'short': Invalid argument\r\n0+0 records in\r\n0+0 records out\r\n0 bytes copied, 9.4146e-05 s, 0.0 kB/s\r\n15+1 records in\r\n15+1 records out\r\n8191 bytes (8.2 kB, 8.0 KiB) copied, 0.0179904 s, 455 kB/s\r\n16+1 records in\r\n16+1 records out\r\n8193 bytes (8.2 kB, 8.0 KiB) copied, 0.0106462 s, 770 kB/s\r\nFAIL tests/dd/direct.sh (exit status: 1)\r\n```\r\n...\r\n```\r\n============================================================================\r\nTestsuite summary for GNU coreutils 8.32\r\n============================================================================\r\n# TOTAL: 621\r\n# PASS: 464\r\n# SKIP: 156\r\n# XFAIL: 0\r\n# FAIL: 1\r\n# XPASS: 0\r\n# ERROR: 0\r\n============================================================================\r\nSee ./tests/test-suite.log\r\nPlease report to bug-coreutils@gnu.org\r\n============================================================================\r\nmake[4]: *** [Makefile:13025: tests/test-suite.log] Error 1\r\nmake[4]: Leaving directory '/build/coreutils-8.32'\r\nmake[3]: *** [Makefile:13133: check-TESTS] Error 2\r\nmake[3]: Leaving directory '/build/coreutils-8.32'\r\nmake[2]: *** [Makefile:13388: check-am] Error 2\r\nmake[2]: Leaving directory '/build/coreutils-8.32'\r\nmake[1]: *** [Makefile:12910: check-recursive] Error 1\r\nmake[1]: Leaving directory '/build/coreutils-8.32'\r\nmake: *** [Makefile:13390: check] Error 2\r\nerror: builder for '/nix/store/x2jjj1fk5j0cyldn8zmgw20cccfcc723-coreutils-8.32.drv' failed with exit code 2\r\nerror: 1 dependencies of derivation '/nix/store/l55ccwnwl37yyfzrxqaq3qlwqzdgm0hv-openssl-1.1.1l.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/q7x7skram1wzqpni4xx37xb7b69d6lwr-curl-7.76.1.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/rklkl0hm41nijshmj1b08ghr74g3gm36-scout-runtime-0.20211102.0.tar.gz.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/mqf640clr4kzadpydwdl1q05mpywjmil-steam-runtime-0.20211102.0.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/jkk12444nyy4rd3bv44r691kwk247a0n-steam-runtime-wrapped.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/kqxjp2xshs9g7g5z2fwzkr4q6js8ac0r-steam-run-usr-multi.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/vcmnk3w10hpi0crv17sp4a6fzvissjdy-steam-usr-multi.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/3858f7z906xk19la3japnhy7vkigm9ln-steam-fhs.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/30rzha4ialm99n17m12hmclf0fk8bz0g-steam-run-fhs.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/d8lkl7hz8r6c3h3yvh3qcqwxxcglbydc-steam-run.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/x97v2s07a9qgvpx0khw6b5ny52jsb0vx-steam.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/5rl2yp3x4pn89qc2551mh0r4ax768kji-steam-run.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/bw52acb5kadw0dprw54mr1i0fqqbf4a5-system-path.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/012170i9xw3qxi6d32kiqh7nkaw26h15-nixos-system-neumann-21.05.4719.0fd9ee1aa36.drv' failed to build\r\n```\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.79, NixOS, 21.05.4255.d5b65f812cd (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(root): `\"home-manager-21.05, nixos-21.05.4719.0fd9ee1aa36, nixpkgs-21.05.4719.0fd9ee1aa36\"`\r\n - channels(judson): `\"home-manager-21.05, nixpkgs-21.05.4719.0fd9ee1aa36\"`\r\n - nixpkgs: `/home/judson/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158022/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005/events","html_url":"https://github.com/NixOS/nixpkgs/issues/158005","id":1123319067,"node_id":"I_kwDOAEVQ_M5C9H0b","number":158005,"title":"nyxt-2.2.3: ERROR **: 00:27:46.959: Unable to configure xdg-desktop-portal access in the WebKit sandbox: GApplication is required.","user":{"login":"jian-lin","id":75130626,"node_id":"MDQ6VXNlcjc1MTMwNjI2","avatar_url":"https://avatars.githubusercontent.com/u/75130626?v=4","gravatar_id":"","url":"https://api.github.com/users/jian-lin","html_url":"https://github.com/jian-lin","followers_url":"https://api.github.com/users/jian-lin/followers","following_url":"https://api.github.com/users/jian-lin/following{/other_user}","gists_url":"https://api.github.com/users/jian-lin/gists{/gist_id}","starred_url":"https://api.github.com/users/jian-lin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jian-lin/subscriptions","organizations_url":"https://api.github.com/users/jian-lin/orgs","repos_url":"https://api.github.com/users/jian-lin/repos","events_url":"https://api.github.com/users/jian-lin/events{/privacy}","received_events_url":"https://api.github.com/users/jian-lin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-02-03T16:46:19Z","updated_at":"2022-04-29T13:32:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen I open (C-l) a url, nyxt hangs and this message is printed in the console:\r\n\r\n```console\r\n** (nyxt:401949): ERROR **: 00:27:46.959: Unable to configure xdg-desktop-portal access in the WebKit sandbox: GApplication is required.\r\n<WARN> [00:27:46] Warning: Error on GTK thread: The value\r\n :INVALID-CODE-OBJECT-AT-PC\r\n is not of type\r\n FUNCTION\r\n```\r\n\r\nIf I disable sandbox through `export WEBKIT_FORCE_SANDBOX=0`, no error occurs.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. open nyxt\r\n2. open a url, e.g. https://bing.com\r\n\r\n### Notify maintainers\r\n@nlewo\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-info -m\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005/reactions","total_count":3,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":2},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/158005/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157989","id":1123112618,"node_id":"I_kwDOAEVQ_M5C8Vaq","number":157989,"title":"boot.initrd.secrets omits key file and fails during initial installation","user":{"login":"ne9z","id":77314501,"node_id":"MDQ6VXNlcjc3MzE0NTAx","avatar_url":"https://avatars.githubusercontent.com/u/77314501?v=4","gravatar_id":"","url":"https://api.github.com/users/ne9z","html_url":"https://github.com/ne9z","followers_url":"https://api.github.com/users/ne9z/followers","following_url":"https://api.github.com/users/ne9z/following{/other_user}","gists_url":"https://api.github.com/users/ne9z/gists{/gist_id}","starred_url":"https://api.github.com/users/ne9z/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ne9z/subscriptions","organizations_url":"https://api.github.com/users/ne9z/orgs","repos_url":"https://api.github.com/users/ne9z/repos","events_url":"https://api.github.com/users/ne9z/events{/privacy}","received_events_url":"https://api.github.com/users/ne9z/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-03T13:52:27Z","updated_at":"2022-04-08T20:51:33Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nUnfortunately I can not pinpoint the issue, but it seems that after a `nixos-rebuild switch --upgrade` on Feb 1st, boot.initrd.secrets starts to omit a key file out of 3 key files and completely fails with a fresh system installation.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. configuration.nix contains the following lines\r\n```\r\n boot.initrd.secrets = {\r\n \"/etc/cryptkey.d/rpool_${poolUuid}-nixos-key-zfs\" = null;\r\n \"/etc/cryptkey.d/bpool_${poolUuid}-key-luks\" = null;\r\n \"/etc/cryptkey.d/${diskName}-part4-key-luks-swap\" = null;\r\n };\r\n\r\n```\r\n\r\nAll three files exist on disk.\r\n\r\n2. nixos-rebuild switch produces a initrd-secret archive that is missing the third key file.\r\n3. Fresh system installation produces the following:\r\n```\r\n+ nixos-enter --root /mnt -- /run/current-system/bin/switch-to-configuration boot\r\nsetting up /etc...\r\nupdating GRUB 2 menu...\r\nmktemp: failed to create directory via template ‘/mnt/tmp.torvrvFbQ5/initrd-secrets.XXXXXXXXXX’: No such file or directory\r\nfailed to create initrd secrets: No such file or directory\r\n+ rm -rf /mnt/tmp.torvrvFbQ5\r\n```\r\n\r\n### Expected behavior\r\nAll key files are included in generated initrd-secrets and `nixos-install --root=/mnt` does not fail.\r\n\r\n### Additional context\r\nThis issue does not exist before system update.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nThis option is declared in <nixpkgs/nixos/modules/system/boot/stage-1.nix>.\r\n\r\n@dasJ @grahamc \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.17, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335665.0f316e4d72d\"`\r\n - channels(user0): `\"home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157989/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157984","id":1123040830,"node_id":"I_kwDOAEVQ_M5C8D4-","number":157984,"title":"Packaging request: Motrix","user":{"login":"ProxyVT","id":86965169,"node_id":"MDQ6VXNlcjg2OTY1MTY5","avatar_url":"https://avatars.githubusercontent.com/u/86965169?v=4","gravatar_id":"","url":"https://api.github.com/users/ProxyVT","html_url":"https://github.com/ProxyVT","followers_url":"https://api.github.com/users/ProxyVT/followers","following_url":"https://api.github.com/users/ProxyVT/following{/other_user}","gists_url":"https://api.github.com/users/ProxyVT/gists{/gist_id}","starred_url":"https://api.github.com/users/ProxyVT/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ProxyVT/subscriptions","organizations_url":"https://api.github.com/users/ProxyVT/orgs","repos_url":"https://api.github.com/users/ProxyVT/repos","events_url":"https://api.github.com/users/ProxyVT/events{/privacy}","received_events_url":"https://api.github.com/users/ProxyVT/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"mainrs","id":5113257,"node_id":"MDQ6VXNlcjUxMTMyNTc=","avatar_url":"https://avatars.githubusercontent.com/u/5113257?v=4","gravatar_id":"","url":"https://api.github.com/users/mainrs","html_url":"https://github.com/mainrs","followers_url":"https://api.github.com/users/mainrs/followers","following_url":"https://api.github.com/users/mainrs/following{/other_user}","gists_url":"https://api.github.com/users/mainrs/gists{/gist_id}","starred_url":"https://api.github.com/users/mainrs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mainrs/subscriptions","organizations_url":"https://api.github.com/users/mainrs/orgs","repos_url":"https://api.github.com/users/mainrs/repos","events_url":"https://api.github.com/users/mainrs/events{/privacy}","received_events_url":"https://api.github.com/users/mainrs/received_events","type":"User","site_admin":false},"assignees":[{"login":"mainrs","id":5113257,"node_id":"MDQ6VXNlcjUxMTMyNTc=","avatar_url":"https://avatars.githubusercontent.com/u/5113257?v=4","gravatar_id":"","url":"https://api.github.com/users/mainrs","html_url":"https://github.com/mainrs","followers_url":"https://api.github.com/users/mainrs/followers","following_url":"https://api.github.com/users/mainrs/following{/other_user}","gists_url":"https://api.github.com/users/mainrs/gists{/gist_id}","starred_url":"https://api.github.com/users/mainrs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mainrs/subscriptions","organizations_url":"https://api.github.com/users/mainrs/orgs","repos_url":"https://api.github.com/users/mainrs/repos","events_url":"https://api.github.com/users/mainrs/events{/privacy}","received_events_url":"https://api.github.com/users/mainrs/received_events","type":"User","site_admin":false}],"milestone":null,"comments":3,"created_at":"2022-02-03T12:42:28Z","updated_at":"2022-02-26T10:49:06Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nMotrix is a full-featured download manager that supports downloading HTTP, FTP, BitTorrent, Magnet, etc.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://motrix.app\r\n* source URL: https://github.com/agalwood/Motrix\r\n* license: mit\r\n* platforms: linux, darwin, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157984/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157926","id":1122569162,"node_id":"I_kwDOAEVQ_M5C6QvK","number":157926,"title":"Wayland packages pkgconfig file in both -bin and -dev","user":{"login":"uzytkownik","id":5706,"node_id":"MDQ6VXNlcjU3MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5706?v=4","gravatar_id":"","url":"https://api.github.com/users/uzytkownik","html_url":"https://github.com/uzytkownik","followers_url":"https://api.github.com/users/uzytkownik/followers","following_url":"https://api.github.com/users/uzytkownik/following{/other_user}","gists_url":"https://api.github.com/users/uzytkownik/gists{/gist_id}","starred_url":"https://api.github.com/users/uzytkownik/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/uzytkownik/subscriptions","organizations_url":"https://api.github.com/users/uzytkownik/orgs","repos_url":"https://api.github.com/users/uzytkownik/repos","events_url":"https://api.github.com/users/uzytkownik/events{/privacy}","received_events_url":"https://api.github.com/users/uzytkownik/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-02-03T01:48:59Z","updated_at":"2022-02-07T20:31:05Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWayland package has pkgconfig file in both -bin and -dev. This causes problems with conflicts:\r\n\r\n```\r\nerror: collision between `/nix/store/k6xlv2g261xwvhg6h27h8fzrdxjh66wy-wayland-1.20.0-bin/lib/pkgconfig/wayland-scanner.pc' and `/nix/store/7lpzdf2abg0964pr7lz0l3aw3cf86z2v-wayland-1.20.0-dev/lib/pkgconfig/wayland-scanner.pc'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a dev environment with wayland\r\n\r\n### Expected behavior\r\nFile should be in -dev.\r\n\r\n### Notify maintainers\r\n@primeos @codyopel @alyssais\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre350017.efeefb2af14\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157926/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157918","id":1122501510,"node_id":"I_kwDOAEVQ_M5C6AOG","number":157918,"title":"\"sys-kernel-debug.mount\" fails when running `nixos-rebuild switch` in a Proxmox LXC","user":{"login":"adryd325","id":48024900,"node_id":"MDQ6VXNlcjQ4MDI0OTAw","avatar_url":"https://avatars.githubusercontent.com/u/48024900?v=4","gravatar_id":"","url":"https://api.github.com/users/adryd325","html_url":"https://github.com/adryd325","followers_url":"https://api.github.com/users/adryd325/followers","following_url":"https://api.github.com/users/adryd325/following{/other_user}","gists_url":"https://api.github.com/users/adryd325/gists{/gist_id}","starred_url":"https://api.github.com/users/adryd325/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/adryd325/subscriptions","organizations_url":"https://api.github.com/users/adryd325/orgs","repos_url":"https://api.github.com/users/adryd325/repos","events_url":"https://api.github.com/users/adryd325/events{/privacy}","received_events_url":"https://api.github.com/users/adryd325/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-02-02T23:45:34Z","updated_at":"2022-02-03T01:39:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\"sys-kernel-debug.mount\" fails when running `nixos-rebuild switch` in a Proxmox LXC\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a Proxmox LXC using this guide https://nixos.wiki/wiki/Proxmox_Linux_Container\r\n2. run nixos-rebuild switch after logging in as root\r\n\r\n### Expected behavior\r\nNo error about sys-kernel-debug.mount should be thrown\r\nit should be potentially disabled in containers since that stopped it from throwing the error\r\n\r\n### Screenshots\r\n```console\r\n[root@nixos:~]# nixos-rebuild switch\r\nbuilding Nix...\r\nbuilding the system configuration...\r\nactivating the configuration...\r\nsetting up /etc...\r\nreloading user units for root...\r\nsetting up tmpfiles\r\nwarning: the following units failed: sys-kernel-debug.mount\r\n\r\n× sys-kernel-debug.mount - Kernel Debug File System\r\n Loaded: loaded (/etc/systemd/system/sys-kernel-debug.mount; enabled; vendor preset: enabled)\r\n Active: failed (Result: exit-code) since Wed 2022-02-02 23:44:55 UTC; 14ms ago\r\n Where: /sys/kernel/debug\r\n What: debugfs\r\n Docs: https://www.kernel.org/doc/Documentation/filesystems/debugfs.txt\r\n https://www.freedesktop.org/wiki/Software/systemd/APIFileSystems\r\n IP: 0B in, 0B out\r\n CPU: 1ms\r\n\r\nFeb 02 23:44:55 nixos systemd[1]: Mounting Kernel Debug File System...\r\nFeb 02 23:44:55 nixos mount[2363]: mount: /sys/kernel/debug: permission denied.\r\nFeb 02 23:44:55 nixos systemd[1]: sys-kernel-debug.mount: Mount process exited, code=exited, status=32/n/a\r\nFeb 02 23:44:55 nixos systemd[1]: sys-kernel-debug.mount: Failed with result 'exit-code'.\r\nFeb 02 23:44:55 nixos systemd[1]: Failed to mount Kernel Debug File System.\r\nwarning: error(s) occurred while switching to the new configuration\r\n```\r\n\r\n### Additional context\r\nI used this build from hydra\r\nhttps://hydra.nixos.org/build/166309459\r\n\r\n### Notify maintainers\r\n@mkg20001\r\n\r\n### Metadata\r\n```console\r\n[root@nixos:~]# nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.11.22-5-pve, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335733.f6ddd55d5f9\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157918/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157893","id":1122337058,"node_id":"I_kwDOAEVQ_M5C5YEi","number":157893,"title":"Current vpnc source is no longer maintained; development has moved elsewhere","user":{"login":"dccsillag","id":15617291,"node_id":"MDQ6VXNlcjE1NjE3Mjkx","avatar_url":"https://avatars.githubusercontent.com/u/15617291?v=4","gravatar_id":"","url":"https://api.github.com/users/dccsillag","html_url":"https://github.com/dccsillag","followers_url":"https://api.github.com/users/dccsillag/followers","following_url":"https://api.github.com/users/dccsillag/following{/other_user}","gists_url":"https://api.github.com/users/dccsillag/gists{/gist_id}","starred_url":"https://api.github.com/users/dccsillag/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dccsillag/subscriptions","organizations_url":"https://api.github.com/users/dccsillag/orgs","repos_url":"https://api.github.com/users/dccsillag/repos","events_url":"https://api.github.com/users/dccsillag/events{/privacy}","received_events_url":"https://api.github.com/users/dccsillag/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-02T20:06:19Z","updated_at":"2022-02-02T20:12:08Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on github to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: vpnc\r\n<!--\r\nThe current version can be found easily with the same process than above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.5.3\r\ndesired version: also 0.5.3, but forked\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @alyssais (last person to commit on https://github.com/NixOS/nixpkgs/blob/master/pkgs/tools/networking/vpnc/default.nix, excluding merges)\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\nI first experienced issues when trying to use the already packaged `vpnc` for my institution's VPN, and things weren't working on NixOS (while they worked on my previous system running Manjaro). I eventually managed to narrow it down to the fact that, despite the version numbers being the same, the version shipped on Arch Linux is actually a fork of the one in nixpkgs, https://github.com/streambinder/vpnc.\r\n\r\nIn the fork's wiki (https://github.com/streambinder/vpnc/wiki/About), it is said:\r\n\r\n> This repository has been forked to follow the work started originally by Maurice Massar. For more information about that, please, point to VPNC original web page.\r\n>\r\n> As stated in vpnc-devel mailing-list (vpnc-devel@2017-November), this repository hasn't been started to start working actively on this project, but to passively merge security patches, fixes and features additions explicitly requested by the community.\r\n\r\nFrom what I undestood, it appears that the original code, present at https://www.unix-ag.uni-kl.de/~massar/vpnc/ is not only no longer maintained, but also contains security issues and is incompatible with some configurations. And, therefore, we should be shipping its maintained fork, https://github.com/streambinder/vpnc.\r\n\r\nIn the meantime, I was able to setup a (probably hacky) derivation for the fork, which I am using in my `configuration.nix`, and seems to work:\r\n\r\n```nix\r\n stdenv.mkDerivation rec {\r\n name = \"vpnc\";\r\n version = \"0.5.3\";\r\n src = fetchFromGitHub {\r\n owner = \"streambinder\";\r\n repo = \"vpnc\";\r\n rev = \"c8bb5371b881f8853f191c495e762f834c9def5d\";\r\n sha256 = \"1j1p83nfc2fpwczjcggsby0b44hk97ky0s6vns6md3awlbpgdn57\";\r\n fetchSubmodules = true;\r\n };\r\n\r\n buildInputs = [ pkg-config perl libgcrypt gnutls ];\r\n\r\n postPatch = ''patchShebangs src/makeman.pl'';\r\n\r\n makeFlags = [\r\n \"PREFIX=$(out)\"\r\n \"ETCDIR=$(out)/etc/vpnc\"\r\n \"SCRIPT_PATH=$(out)/etc/vpnc/vpnc-script\"\r\n ];\r\n };\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157893/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157874","id":1122233363,"node_id":"I_kwDOAEVQ_M5C4-wT","number":157874,"title":"Remove spidermonkey_78 and spidermonkey_68","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":1,"created_at":"2022-02-02T18:02:54Z","updated_at":"2022-04-07T14:52:46Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Both package have reached their end of life together with their respective firefox versions and should be removed before NixOS 22.05.\r\n\r\n- `spidermonkey_68`: https://github.com/NixOS/nixpkgs/pull/153451 \r\n- `spidermonkey_78`: EOL since 2021/11\r\n - required in polkit, but updated to mozjs-91 in https://gitlab.freedesktop.org/polkit/polkit/-/commit/a6bedfd09b7bba753de7a107dc471da0db801858\r\n\r\nhttps://endoflife.date/firefox\r\n\r\n@lostnet @abbradar @ajs124 \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157874/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157860","id":1122143474,"node_id":"I_kwDOAEVQ_M5C4ozy","number":157860,"title":"Python installed by `nixpkgs#conda` requires `libffi.so.6` which is not present.","user":{"login":"charmoniumQ","id":928570,"node_id":"MDQ6VXNlcjkyODU3MA==","avatar_url":"https://avatars.githubusercontent.com/u/928570?v=4","gravatar_id":"","url":"https://api.github.com/users/charmoniumQ","html_url":"https://github.com/charmoniumQ","followers_url":"https://api.github.com/users/charmoniumQ/followers","following_url":"https://api.github.com/users/charmoniumQ/following{/other_user}","gists_url":"https://api.github.com/users/charmoniumQ/gists{/gist_id}","starred_url":"https://api.github.com/users/charmoniumQ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/charmoniumQ/subscriptions","organizations_url":"https://api.github.com/users/charmoniumQ/orgs","repos_url":"https://api.github.com/users/charmoniumQ/repos","events_url":"https://api.github.com/users/charmoniumQ/events{/privacy}","received_events_url":"https://api.github.com/users/charmoniumQ/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-02T16:32:37Z","updated_at":"2022-02-02T16:32:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nPython installed by `nixpkgs#conda` requires `libffi.so.6` which is not present.\r\n\r\n### Steps To Reproduce\r\n```\r\n$ nix shell nixpkgs#conda --command conda-shell -c 'python -c \"import _ctypes\"'\r\nTraceback (most recent call last):\r\n File \"<string>\", line 1, in <module>\r\nImportError: libffi.so.6: cannot open shared object file: No such file or directory\r\n```\r\n\r\n### Expected behavior\r\n\r\nThe command should not error out.\r\n\r\n### Additional context\r\n\r\nNote that `nixpkgs#libffi` only provides `libffi.so.8` which is not ABI-compatible with `libffi.so.6`.\r\n\r\n### Notify maintainers\r\n\r\nConda: @jluttine @bhipple\r\n\r\nlibffi: @matthewbauer: How to get `libffi.so.6` from Nix?\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.11.0-43-generic, Ubuntu, 20.04.3 LTS (Focal Fossa)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20210503_6d2553a`\r\n - channels(sam): `\"home-manager, nixpkgs-21.11pre332093.7fad01d9d5a\"`\r\n - nixpkgs: `/home/sam/.nix-defexpr/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157860/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157803","id":1121528514,"node_id":"I_kwDOAEVQ_M5C2SrC","number":157803,"title":"sssd + AD/LDAP stopped working after update to 21.11 or unstable due to misconfigured SASL","user":{"login":"uzytkownik","id":5706,"node_id":"MDQ6VXNlcjU3MDY=","avatar_url":"https://avatars.githubusercontent.com/u/5706?v=4","gravatar_id":"","url":"https://api.github.com/users/uzytkownik","html_url":"https://github.com/uzytkownik","followers_url":"https://api.github.com/users/uzytkownik/followers","following_url":"https://api.github.com/users/uzytkownik/following{/other_user}","gists_url":"https://api.github.com/users/uzytkownik/gists{/gist_id}","starred_url":"https://api.github.com/users/uzytkownik/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/uzytkownik/subscriptions","organizations_url":"https://api.github.com/users/uzytkownik/orgs","repos_url":"https://api.github.com/users/uzytkownik/repos","events_url":"https://api.github.com/users/uzytkownik/events{/privacy}","received_events_url":"https://api.github.com/users/uzytkownik/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-02-02T05:25:33Z","updated_at":"2022-02-24T10:15:42Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nsssd + AD/LDAP stopped working after update to 21.11 or unstable due to misconfigured SASL\r\n\r\n### Steps To Reproduce\r\n1. Update from 21.05 to 21.11\r\n2. Attempt to log in\r\n\r\n### Expected behavior\r\nLog in works\r\n\r\n### Additional context\r\nErrors in logs are:\r\n```\r\nNo worthy mechs found\r\nSASL: No worthy mechs found\r\nldap_sasl_interactive_bind_s failed (-6)[Unknown authentication method]\r\nUnsable to establish connection [number]: Authentication failed\r\n```\r\n\r\n### Notify maintainers\r\n@e-user @illustris \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: \"x86_64-linux\"\r\n- host os: \"Linux 5.10.88, NixOS, 21.05.4719.0fd9ee1aa36 (Okapi)'\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version `nix-env (Nix) 2.3.16`\r\n- channels(root): `\"nixos-21.05.4719.0fd9ee1aa36\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157803/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157802","id":1121527355,"node_id":"I_kwDOAEVQ_M5C2SY7","number":157802,"title":"Getting JetBrains to natively support nix","user":{"login":"kirinnee","id":15990242,"node_id":"MDQ6VXNlcjE1OTkwMjQy","avatar_url":"https://avatars.githubusercontent.com/u/15990242?v=4","gravatar_id":"","url":"https://api.github.com/users/kirinnee","html_url":"https://github.com/kirinnee","followers_url":"https://api.github.com/users/kirinnee/followers","following_url":"https://api.github.com/users/kirinnee/following{/other_user}","gists_url":"https://api.github.com/users/kirinnee/gists{/gist_id}","starred_url":"https://api.github.com/users/kirinnee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kirinnee/subscriptions","organizations_url":"https://api.github.com/users/kirinnee/orgs","repos_url":"https://api.github.com/users/kirinnee/repos","events_url":"https://api.github.com/users/kirinnee/events{/privacy}","received_events_url":"https://api.github.com/users/kirinnee/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-02T05:23:18Z","updated_at":"2022-02-02T08:24:29Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\nI would love for JetBrains to natively support `nix`. Right now, everything other than using the IDE is jarring, such as running `remote-dev-server.sh` for Gateway development or `projector-installer` to run remote-IDEs, having DataSpell be broken, and not being able to change IDEs' PATH when the shell updates\r\n\r\nRelated Issues:\r\n- [JetBrains Gateway](https://github.com/NixOS/nixpkgs/issues/153335)\r\n- [JetBrains Projector](https://github.com/NixOS/nixpkgs/issues/138436)\r\n- [JetBrains DataSpell](https://github.com/NixOS/nixpkgs/pull/148037)\r\n\r\nI have created a YouTrack issue to request for Nix integration, I would appreciate it if our community would increase the likes to allow to show JetBrains its a high-demand feature so they would not push nix to the back of the backlog.\r\n\r\nIssue: [Jetbrains YouTrack Issue](https://youtrack.jetbrains.com/issue/CWM-5048)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157802/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157770","id":1121345030,"node_id":"I_kwDOAEVQ_M5C1l4G","number":157770,"title":"Packaging Request: python-validity","user":{"login":"scottbot95","id":2055068,"node_id":"MDQ6VXNlcjIwNTUwNjg=","avatar_url":"https://avatars.githubusercontent.com/u/2055068?v=4","gravatar_id":"","url":"https://api.github.com/users/scottbot95","html_url":"https://github.com/scottbot95","followers_url":"https://api.github.com/users/scottbot95/followers","following_url":"https://api.github.com/users/scottbot95/following{/other_user}","gists_url":"https://api.github.com/users/scottbot95/gists{/gist_id}","starred_url":"https://api.github.com/users/scottbot95/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/scottbot95/subscriptions","organizations_url":"https://api.github.com/users/scottbot95/orgs","repos_url":"https://api.github.com/users/scottbot95/repos","events_url":"https://api.github.com/users/scottbot95/events{/privacy}","received_events_url":"https://api.github.com/users/scottbot95/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-02T00:30:03Z","updated_at":"2022-02-02T00:30:03Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nValidity fingerprint sensor driver.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/uunicorn/python-validity\r\n* source URL: https://github.com/uunicorn/python-validity\r\n* license: MIT\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157770/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157769","id":1121342246,"node_id":"I_kwDOAEVQ_M5C1lMm","number":157769,"title":"Packaging Request: open-fprintd","user":{"login":"scottbot95","id":2055068,"node_id":"MDQ6VXNlcjIwNTUwNjg=","avatar_url":"https://avatars.githubusercontent.com/u/2055068?v=4","gravatar_id":"","url":"https://api.github.com/users/scottbot95","html_url":"https://github.com/scottbot95","followers_url":"https://api.github.com/users/scottbot95/followers","following_url":"https://api.github.com/users/scottbot95/following{/other_user}","gists_url":"https://api.github.com/users/scottbot95/gists{/gist_id}","starred_url":"https://api.github.com/users/scottbot95/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/scottbot95/subscriptions","organizations_url":"https://api.github.com/users/scottbot95/orgs","repos_url":"https://api.github.com/users/scottbot95/repos","events_url":"https://api.github.com/users/scottbot95/events{/privacy}","received_events_url":"https://api.github.com/users/scottbot95/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-02T00:26:15Z","updated_at":"2022-02-02T00:28:18Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nFprintd replacement which allows you to have your own backend as a standalone service.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/uunicorn/open-fprintd\r\n* source URL: https://github.com/uunicorn/open-fprintd\r\n* license: GPL2\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157769/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157757","id":1121248463,"node_id":"I_kwDOAEVQ_M5C1OTP","number":157757,"title":"git inside of a 'nix builld' sandbox is coredumping","user":{"login":"nixinator","id":66913205,"node_id":"MDQ6VXNlcjY2OTEzMjA1","avatar_url":"https://avatars.githubusercontent.com/u/66913205?v=4","gravatar_id":"","url":"https://api.github.com/users/nixinator","html_url":"https://github.com/nixinator","followers_url":"https://api.github.com/users/nixinator/followers","following_url":"https://api.github.com/users/nixinator/following{/other_user}","gists_url":"https://api.github.com/users/nixinator/gists{/gist_id}","starred_url":"https://api.github.com/users/nixinator/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nixinator/subscriptions","organizations_url":"https://api.github.com/users/nixinator/orgs","repos_url":"https://api.github.com/users/nixinator/repos","events_url":"https://api.github.com/users/nixinator/events{/privacy}","received_events_url":"https://api.github.com/users/nixinator/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-02-01T22:06:08Z","updated_at":"2022-02-01T22:06:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Describe the bug\r\n\r\ngit within various nix builds seems to be core dumping.\r\n```\r\n[611985.006979] traps: git[2813609] general protection fault ip:4ef240 sp:7fffffff7c60 error:0 in git[405000+25c000]\r\n[611985.341404] traps: git[2814122] general protection fault ip:4ef240 sp:7fffffff8160 error:0 in git[405000+25c000]\r\n[611985.693819] git[2814650]: segfault at 40 ip 0000000000624809 sp 00007fffffff6f00 error 4 in git[405000+25c000]\r\n[611985.693840] Code: e0 00 00 00 4c 89 f6 83 c3 01 e8 d2 f4 ff ff 39 5c 24 10 0f 84 80 07 00 00 49 8b 96 60 02 00 00 48 63 c3 48 8b 12 48 8b 34 c2 <8b> 4e 40 48 89 b4 24 e0 00 00 00 8d 41 6d 39 e8 0f 8e 71 ff ff ff\r\n[611986.512956] git[2815795]: segfault at 40 ip 0000000000624809 sp 00007fffffff70c0 error 4 in git[405000+25c000]\r\n[611986.512975] Code: e0 00 00 00 4c 89 f6 83 c3 01 e8 d2 f4 ff ff 39 5c 24 10 0f 84 80 07 00 00 49 8b 96 60 02 00 00 48 63 c3 48 8b 12 48 8b 34 c2 <8b> 4e 40 48 89 b4 24 e0 00 00 00 8d 41 6d 39 e8 0f 8e 71 ff ff ff\r\n```\r\n\r\nSteps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nI'm not pinpointed the exact builds which are doing this. more information can be gleamed here https://github.com/NixOS/nixpkgs/issues/154938\r\n\r\nMetadata\r\nPlease run nix-shell -p nix-info --run \"nix-info -m\" and paste the result.\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.05.20220103.88579ef (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(user): `\"nixgl, stable-21.05.4709.88579effa7e\"`\r\n - channels(root): `\"nixos-21.11pre332093.7fad01d9d5a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157757/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157755","id":1121232645,"node_id":"I_kwDOAEVQ_M5C1KcF","number":157755,"title":"snd-usb-audio fails to resume after suspend in kernel 5.16","user":{"login":"underscore-j","id":77000103,"node_id":"MDQ6VXNlcjc3MDAwMTAz","avatar_url":"https://avatars.githubusercontent.com/u/77000103?v=4","gravatar_id":"","url":"https://api.github.com/users/underscore-j","html_url":"https://github.com/underscore-j","followers_url":"https://api.github.com/users/underscore-j/followers","following_url":"https://api.github.com/users/underscore-j/following{/other_user}","gists_url":"https://api.github.com/users/underscore-j/gists{/gist_id}","starred_url":"https://api.github.com/users/underscore-j/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/underscore-j/subscriptions","organizations_url":"https://api.github.com/users/underscore-j/orgs","repos_url":"https://api.github.com/users/underscore-j/repos","events_url":"https://api.github.com/users/underscore-j/events{/privacy}","received_events_url":"https://api.github.com/users/underscore-j/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-01T21:47:35Z","updated_at":"2022-02-16T05:59:10Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nsnd-usb-audio fails with \"resume error -22\" after suspend, causing pipewire and pulseaudio to hang until the USB device is removed. It works fine after reconnecting.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have a USB sound card using this driver and use kernel 5.16 (latest).\r\n2. Suspend the system, then resume.\r\n3. Try playing music, opening pavucontrol, etc. This will not work (pavucontrol will show a \"waiting for pulseaudio\" message, playing music from youtube is stuck loading, pulsemixer doesn't have any visible behaviour and seems to hang)\r\n4. Disconnect USB sound card (optionally reconnect).\r\n5. Try playing music/ opening pavucontrol again. It should now work as expected.\r\n\r\n### Expected behavior\r\nAudio should continue working after suspend, not causing pulseaudio/pipewire to hang.\r\n\r\n### Additional context\r\nThis seems like a bug in the upstream kernel, at least I have found reports of the same problem with arch (https://bbs.archlinux.org/viewtopic.php?id=273469).\r\nHowever, the kernel bugzilla explicitly asks to report bugs to the distribution first.\r\n\r\nThe exact journalctl message is\r\n```console\r\nFeb 01 11:03:16 horseradish kernel: snd-usb-audio 5-2.6:1.0: resume error -22\r\n```\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.17, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.335665.0f316e4d72d, nixos-master, nixos-stable-21.11.335665.0f316e4d72d, nixos-unstable-22.05pre350017.efeefb2af14\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157755/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157674","id":1120539309,"node_id":"I_kwDOAEVQ_M5CyhKt","number":157674,"title":"python3Packages.zarr: Illegal instruction","user":{"login":"vcunat","id":1785925,"node_id":"MDQ6VXNlcjE3ODU5MjU=","avatar_url":"https://avatars.githubusercontent.com/u/1785925?v=4","gravatar_id":"","url":"https://api.github.com/users/vcunat","html_url":"https://github.com/vcunat","followers_url":"https://api.github.com/users/vcunat/followers","following_url":"https://api.github.com/users/vcunat/following{/other_user}","gists_url":"https://api.github.com/users/vcunat/gists{/gist_id}","starred_url":"https://api.github.com/users/vcunat/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vcunat/subscriptions","organizations_url":"https://api.github.com/users/vcunat/orgs","repos_url":"https://api.github.com/users/vcunat/repos","events_url":"https://api.github.com/users/vcunat/events{/privacy}","received_events_url":"https://api.github.com/users/vcunat/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-02-01T11:19:02Z","updated_at":"2022-03-06T08:44:45Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Right now it [failed](https://hydra.nixos.org/build/165846474) tests, probably because of getting scheduled on a bit older machine than usually.\r\nLog may get overwritten if restarted on Hydra, so here's the relevant part:\r\n<details><pre>\r\nrunning install tests\r\n============================= test session starts ==============================\r\nplatform linux -- Python 3.10.1, pytest-6.2.5, py-1.11.0, pluggy-1.0.0\r\nrootdir: /build/zarr-2.10.3, configfile: pytest.ini\r\ncollecting ... Fatal Python error: Illegal instruction\r\n\r\nCurrent thread 0x00007ffff77d8440 (most recent call first):\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap_external>\", line 1184 in exec_module\r\n File \"<frozen importlib._bootstrap>\", line 688 in _load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1006 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"/nix/store/icv204idxppknvjbpwrfqqymxbdhfqkv-python3.10-numcodecs-0.9.1/lib/python3.10/site-packages/numcodecs/shuffle.py\", line 4 in <module>\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap_external>\", line 883 in exec_module\r\n File \"<frozen importlib._bootstrap>\", line 688 in _load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1006 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"/nix/store/icv204idxppknvjbpwrfqqymxbdhfqkv-python3.10-numcodecs-0.9.1/lib/python3.10/site-packages/numcodecs/__init__.py\", line 100 in <module>\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap_external>\", line 883 in exec_module\r\n File \"<frozen importlib._bootstrap>\", line 688 in _load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1006 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"/build/zarr-2.10.3/zarr/codecs.py\", line 2 in <module>\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap_external>\", line 883 in exec_module\r\n File \"<frozen importlib._bootstrap>\", line 688 in _load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1006 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"/build/zarr-2.10.3/zarr/__init__.py\", line 2 in <module>\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap_external>\", line 883 in exec_module\r\n File \"<frozen importlib._bootstrap>\", line 688 in _load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1006 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 1050 in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap>\", line 992 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 1050 in _gcd_import\r\n File \"<frozen importlib._bootstrap>\", line 241 in _call_with_frames_removed\r\n File \"<frozen importlib._bootstrap>\", line 992 in _find_and_load_unlocked\r\n File \"<frozen importlib._bootstrap>\", line 1027 in _find_and_load\r\n File \"<frozen importlib._bootstrap>\", line 1050 in _gcd_import\r\n File \"/nix/store/fi0f5rz33byvsqlzs5hcc6l25scdlg42-python3-3.10.1/lib/python3.10/importlib/__init__.py\", line 126 in import_module\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/pathlib.py\", line 524 in import_path\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/config/__init__.py\", line 570 in _importconftest\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/config/__init__.py\", line 536 in _getconftestmodules\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 519 in gethookproxy\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 551 in _collectfile\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 702 in collect\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/runner.py\", line 341 in <lambda>\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/runner.py\", line 311 in from_call\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/runner.py\", line 341 in pytest_make_collect_report\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_callers.py\", line 39 in _multicall\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_manager.py\", line 80 in _hookexec\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_hooks.py\", line 265 in __call__\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/runner.py\", line 458 in collect_one_node\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 620 in perform_collect\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 333 in pytest_collection\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_callers.py\", line 39 in _multicall\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_manager.py\", line 80 in _hookexec\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_hooks.py\", line 265 in __call__\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 322 in _main\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 269 in wrap_session\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/main.py\", line 316 in pytest_cmdline_main\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_callers.py\", line 39 in _multicall\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_manager.py\", line 80 in _hookexec\r\n File \"/nix/store/94g90xjsfq8pk8wh67v388nw3m07bp2f-python3.10-pluggy-1.0.0/lib/python3.10/site-packages/pluggy/_hooks.py\", line 265 in __call__\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/config/__init__.py\", line 162 in main\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/lib/python3.10/site-packages/_pytest/config/__init__.py\", line 185 in console_main\r\n File \"/nix/store/kq60a6md5pm6sgyzlvqxhqxll7g6hdrj-python3.10-pytest-6.2.5/bin/.pytest-wrapped\", line 9 in <module>\r\n\r\nExtension modules: numpy.core._multiarray_umath, numpy.core._multiarray_tests, numpy.linalg.lapack_lite, numpy.linalg._umath_linalg, numpy.fft._pocketfft_internal, numpy.random._common, numpy.random.bit_generator, numpy.random._bounded_integers, numpy.random._mt19937, numpy.random.mtrand, numpy.random._philox, numpy.random._pcg64, numpy.random._sfc64, numpy.random._generator, numcodecs.compat_ext, numcodecs.blosc, numcodecs.zstd, numcodecs.lz4, numcodecs._shuffle (total: 19)\r\n/nix/store/vhdfrizjvb4p58wkidl8hmn5gnp9zbxv-stdenv-linux/setup: line 1352: 121 Illegal instruction (core dumped) pytest\r\nbuilder for '/nix/store/2pr9j3b2fzkbfmjglbsyr8anxmc2h0v6-python3.10-zarr-2.10.3.drv' failed with exit code 132\r\n</pre></details>\r\n\r\n\r\nThis looks somewhat similar to https://github.com/NixOS/nixpkgs/issues/115425 but the CPU in question here is not _that_ old (Ivy Bridge, i.e. arch < 10 years):\r\n> flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx rdtscp lm constant_tsc arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 cx16 xtpr pdcm pcid sse4_1 sse4_2 x2apic popcnt tsc_deadline_timer aes xsave avx f16c rdrand lahf_lm cpuid_fault epb pti tpr_shadow vnmi flexpriority ept vpid fsgsbase smep erms xsaveopt dtherm ida arat pln pts\r\n\r\n\r\n### Notify maintainers\r\n@costrouc","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157674/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157665","id":1120456208,"node_id":"I_kwDOAEVQ_M5CyM4Q","number":157665,"title":"pkgsStatic.libglvnd: fails to build. libtool func__fatal_error command not found","user":{"login":"ShamrockLee","id":44064051,"node_id":"MDQ6VXNlcjQ0MDY0MDUx","avatar_url":"https://avatars.githubusercontent.com/u/44064051?v=4","gravatar_id":"","url":"https://api.github.com/users/ShamrockLee","html_url":"https://github.com/ShamrockLee","followers_url":"https://api.github.com/users/ShamrockLee/followers","following_url":"https://api.github.com/users/ShamrockLee/following{/other_user}","gists_url":"https://api.github.com/users/ShamrockLee/gists{/gist_id}","starred_url":"https://api.github.com/users/ShamrockLee/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ShamrockLee/subscriptions","organizations_url":"https://api.github.com/users/ShamrockLee/orgs","repos_url":"https://api.github.com/users/ShamrockLee/repos","events_url":"https://api.github.com/users/ShamrockLee/events{/privacy}","received_events_url":"https://api.github.com/users/ShamrockLee/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1469796342,"node_id":"MDU6TGFiZWwxNDY5Nzk2MzQy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20static","name":"6.topic: static","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-02-01T10:02:24Z","updated_at":"2022-04-09T14:00:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n1. `pkgsStatic.libglvnd` fails to build\r\n2. Partial log:\r\n ```\r\n Making all in OpenGL\r\n make[3]: Entering directory '/build/source/src/OpenGL'\r\n CC libopengl_main_la-libopengl.lo\r\n CCLD libopengl_main.la\r\n x86_64-unknown-linux-musl-ar: `u' modifier ignored since `D' is the default (see `U')\r\n CCLD libOpenGL.la\r\n ../../libtool: line 2625: func__fatal_error: command not found\r\n ```\r\n where `func__fatal_error` should be a typo of `func_fatal_error`, which will show extra information about the error before exit.\r\n3. Partial content of the generated `libtool` inside the build directory kept (starting from line 2631):\r\n ```sh\r\n # func_config\r\n # -----------\r\n # Display the configuration for all the tags in this script.\r\n func_config ()\r\n {\r\n re_begincf='^# ### BEGIN LIBTOOL'\r\n re_endcf='^# ### END LIBTOOL'\r\n\r\n # Default configuration.\r\n $SED \"1,/$re_begincf CONFIG/d;/$re_endcf CONFIG/,\\$d\" < \"$progpath\"\r\n\r\n # Now print the configurations for the tags.\r\n for tagname in $taglist; do\r\n $SED -n \"/$re_begincf TAG CONFIG: $tagname\\$/,/$re_endcf TAG CONFIG: $tagname\\$/p\" < \"$progpath\"\r\n done\r\n\r\n exit $?\r\n }\r\n ```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. On the NixOS/nixpkgs source tree\r\n2. Switch to commit 78e2ef7e3dab7778d823977129e8f8902020ffe6\r\n3. Run `nix-build -A pkgsStatic.libglvnd`\r\n4. See error\r\n5. Run `nix log .#pkgsStatic.libglvnd` to see the log for flake-based Nix.\r\n\r\n### Expected behavior\r\n\r\n1. The typo in the auto-generated `libtool` be fixed, so that error message can appear.\r\n2. The build succeed.\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n\r\n### Additional context\r\n\r\nThe auto-generated file `libtool`:\r\n[libtool](https://github.com/NixOS/nixpkgs/files/7977466/libtool.txt)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@primeos\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.73, NixOS, 21.05.20211019.8fe3b97 (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157665/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157614","id":1120079210,"node_id":"I_kwDOAEVQ_M5Cww1q","number":157614,"title":"[Steam] Dota fails to launch after Jan 31 update","user":{"login":"tgharib","id":6457015,"node_id":"MDQ6VXNlcjY0NTcwMTU=","avatar_url":"https://avatars.githubusercontent.com/u/6457015?v=4","gravatar_id":"","url":"https://api.github.com/users/tgharib","html_url":"https://github.com/tgharib","followers_url":"https://api.github.com/users/tgharib/followers","following_url":"https://api.github.com/users/tgharib/following{/other_user}","gists_url":"https://api.github.com/users/tgharib/gists{/gist_id}","starred_url":"https://api.github.com/users/tgharib/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tgharib/subscriptions","organizations_url":"https://api.github.com/users/tgharib/orgs","repos_url":"https://api.github.com/users/tgharib/repos","events_url":"https://api.github.com/users/tgharib/events{/privacy}","received_events_url":"https://api.github.com/users/tgharib/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":16,"created_at":"2022-02-01T00:19:22Z","updated_at":"2022-03-21T16:39:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen launching dota from steam, it errors out with an error about `libpangoft`.\r\n\r\nDota was working yesterday. It broke today (Jan 31) after an update. I believe the update switched the game to use the soldier runtime (which runs the game inside a container). Before, I believe dota was running uncontainerized.\r\n\r\nI filed a bug report on the dota tracker: https://github.com/ValveSoftware/Dota-2/issues/2018\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Launch steam\r\n2. Launch dota\r\n\r\n### Expected behavior\r\nThe game to launch.\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nSteam installed through `programs.steam.enable = true;`.\r\n\r\n### Notify maintainers\r\n@jagajaga @jonringer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\nnix > nix-info -m\r\nwarning: Nix search path entry '/nix/var/nix/profiles/per-user/root/channels/nixos' does not exist, ignoring\r\nerror: file 'nixpkgs' was not found in the Nix search path (add it using $NIX_PATH or -I)\r\n\r\n at «string»:1:9:\r\n\r\n 1| (import <nixpkgs> {}).stdenv.hostPlatform.system\r\n | ^\r\n - system: `0`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"\"`\r\n - channels(owner): `\"\"`\r\nwarning: Nix search path entry '/nix/var/nix/profiles/per-user/root/channels/nixos' does not exist, ignoring\r\nerror: file 'nixpkgs' was not found in the Nix search path (add it using $NIX_PATH or -I)\r\n\r\n at «string»:1:1:\r\n\r\n 1| <nixpkgs>\r\n | ^\r\n - nixpkgs: `0`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157614/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157609","id":1120051441,"node_id":"I_kwDOAEVQ_M5CwqDx","number":157609,"title":"`.../vim-plugins/update.py` sometimes changes hash and nothing else","user":{"login":"malob","id":2914269,"node_id":"MDQ6VXNlcjI5MTQyNjk=","avatar_url":"https://avatars.githubusercontent.com/u/2914269?v=4","gravatar_id":"","url":"https://api.github.com/users/malob","html_url":"https://github.com/malob","followers_url":"https://api.github.com/users/malob/followers","following_url":"https://api.github.com/users/malob/following{/other_user}","gists_url":"https://api.github.com/users/malob/gists{/gist_id}","starred_url":"https://api.github.com/users/malob/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/malob/subscriptions","organizations_url":"https://api.github.com/users/malob/orgs","repos_url":"https://api.github.com/users/malob/repos","events_url":"https://api.github.com/users/malob/events{/privacy}","received_events_url":"https://api.github.com/users/malob/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-31T23:34:47Z","updated_at":"2022-02-01T00:34:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nToday when I ran `update.py` as part of #157581 and #157604, the `sha256` hash for `vim-colorschemes` was changed, but there was no update to the `rev` and `version` (which makes sense since the current `rev` in `generated.nix` is up to date).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. In the `nixpkgs` repo run `GITHUB_API_TOKEN=[token] ./pkgs/misc/vim-plugins/update.py --no-commit`\r\n2. Run `git diff` and observe that the `sha256` hash for `vim-colorschemes` was changed.\r\n```diff\r\ndiff --git a/pkgs/misc/vim-plugins/generated.nix b/pkgs/misc/vim-plugins/generated.nix\r\nindex 09fe8819a5d..de95c8d969a 100644\r\n--- a/pkgs/misc/vim-plugins/generated.nix\r\n+++ b/pkgs/misc/vim-plugins/generated.nix\r\n@@ -7680,7 +7680,7 @@ final: prev:\r\n owner = \"flazz\";\r\n repo = \"vim-colorschemes\";\r\n rev = \"fd8f122cef604330c96a6a6e434682dbdfb878c9\";\r\n- sha256 = \"1cg8q7w0vgl73aw1b9zz0zh5vw5d2pm8pm54fhfzva4azg56f416\";\r\n+ sha256 = \"0kpsf6j20fgblc8vhqn7ymr52v2d1h52vc7rbxmxfwdm80nvv3g5\";\r\n };\r\n meta.homepage = \"https://github.com/flazz/vim-colorschemes/\";\r\n };\r\n```\r\n\r\n### Expected behavior\r\nThe hash should not change if the source has not changed.\r\n\r\n### Notify maintainers\r\n @jonringer @softinio @teto @Flakebi\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n❯ nix run nixpkgs#nix-info -- -m\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.3.0, macOS 12.2`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixpkgs-21.11pre326821.509d236edf0\"`\r\n - nixpkgs: `/Users/malo/.config/nixpkgs/nixpkgs.nix`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157609/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157603","id":1120028244,"node_id":"I_kwDOAEVQ_M5CwkZU","number":157603,"title":"Disk Quotas","user":{"login":"NorfairKing","id":3521180,"node_id":"MDQ6VXNlcjM1MjExODA=","avatar_url":"https://avatars.githubusercontent.com/u/3521180?v=4","gravatar_id":"","url":"https://api.github.com/users/NorfairKing","html_url":"https://github.com/NorfairKing","followers_url":"https://api.github.com/users/NorfairKing/followers","following_url":"https://api.github.com/users/NorfairKing/following{/other_user}","gists_url":"https://api.github.com/users/NorfairKing/gists{/gist_id}","starred_url":"https://api.github.com/users/NorfairKing/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/NorfairKing/subscriptions","organizations_url":"https://api.github.com/users/NorfairKing/orgs","repos_url":"https://api.github.com/users/NorfairKing/repos","events_url":"https://api.github.com/users/NorfairKing/events{/privacy}","received_events_url":"https://api.github.com/users/NorfairKing/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-31T23:06:45Z","updated_at":"2022-03-29T14:38:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nWe would like to define disk quotas:\r\nhttps://www.linux.com/news/implementing-quotas-restrict-disk-space-usage/\r\n\r\nI can implement it, but I just want to get some feedback on the idea before I make a PR, to make sure it's a good idea.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157603/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157537","id":1119660487,"node_id":"I_kwDOAEVQ_M5CvKnH","number":157537,"title":"`/etc/wpa_supplicant.conf` should automatically be created","user":{"login":"wucke13","id":20400405,"node_id":"MDQ6VXNlcjIwNDAwNDA1","avatar_url":"https://avatars.githubusercontent.com/u/20400405?v=4","gravatar_id":"","url":"https://api.github.com/users/wucke13","html_url":"https://github.com/wucke13","followers_url":"https://api.github.com/users/wucke13/followers","following_url":"https://api.github.com/users/wucke13/following{/other_user}","gists_url":"https://api.github.com/users/wucke13/gists{/gist_id}","starred_url":"https://api.github.com/users/wucke13/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wucke13/subscriptions","organizations_url":"https://api.github.com/users/wucke13/orgs","repos_url":"https://api.github.com/users/wucke13/repos","events_url":"https://api.github.com/users/wucke13/events{/privacy}","received_events_url":"https://api.github.com/users/wucke13/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-31T16:35:58Z","updated_at":"2022-01-31T19:54:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen `networking.wireless.enable == true && allowAuxiliaryImperativeNetworks == true`, `wpa_supplicant` crashes due to a missing `/etc/wpa_supplicant.conf`. An unprivileged user is no able to fix this failure. IMHO it would be better if the file is just touched before attempting to launch `wpa_supplicant`, so that it is at least there. \r\n\r\nI'd suggest \r\n\r\n```bash\r\numask 077\r\ntouch /etc/wpa_supplicant.conf\r\nchmod 700 /etc/wpa_supplicant.conf\r\n```\r\n\r\nas `pre` action to the `wpa_supplicant` systemd service\r\n\r\n### Expected behavior\r\nThe service starts without issues\r\n\r\n### Notify maintainers\r\n@globin @rnhmjoj\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.2, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.05.3957.66d6ec6ed2d\"`\r\n - channels(zaes_wa): `\"nixpkgs-21.11.334247.573095944e7\"`\r\n - nixpkgs: `/home/my_user/.nix-defexpr/channels/nixpkgs\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157537/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157529","id":1119575472,"node_id":"I_kwDOAEVQ_M5Cu12w","number":157529,"title":"Mixxx not detecting JACK as an audio backend when PipeWire with JACK emulation is running","user":{"login":"starcraft66","id":1858154,"node_id":"MDQ6VXNlcjE4NTgxNTQ=","avatar_url":"https://avatars.githubusercontent.com/u/1858154?v=4","gravatar_id":"","url":"https://api.github.com/users/starcraft66","html_url":"https://github.com/starcraft66","followers_url":"https://api.github.com/users/starcraft66/followers","following_url":"https://api.github.com/users/starcraft66/following{/other_user}","gists_url":"https://api.github.com/users/starcraft66/gists{/gist_id}","starred_url":"https://api.github.com/users/starcraft66/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/starcraft66/subscriptions","organizations_url":"https://api.github.com/users/starcraft66/orgs","repos_url":"https://api.github.com/users/starcraft66/repos","events_url":"https://api.github.com/users/starcraft66/events{/privacy}","received_events_url":"https://api.github.com/users/starcraft66/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-31T15:24:35Z","updated_at":"2022-01-31T18:05:49Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nWhen running Pipewire with the emulated JACK server, Mixxx does not detect JACK as a suitable audio backend. Other JACK-supporting applications like Carla do so just fine. I'm unsure what could be the cause. Mixxx uses PortAudio to handle all of the communication with jack and it looks like the PortAudio in nixpkgs is up to date but something might be wrong with it? I'm also pinging PortAudio maintainers for visibilit in case, feel free to ignore if this isn't a PortAudio problem.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable `services.pipewire.enable` and `services.pipewire.jack.enable`\r\n2. Launch Mixxx and open the preferences\r\n3. Try to select JACK as an audio backend in the audio preferences\r\n\r\n### Expected behavior\r\nI expect JACK to be available in the audio preferences but only OSS and ALSA show up.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@goibhniu @bfortz @lovek323 \r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.3, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"\"`\r\n - channels(tristan): `\"\"`\r\n - nixpkgs: `/nix/store/rdglycjss277jiy7zinn982jg4q525p9-md3lc3011brc36wdc9fydj2krj9idi8m-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157529/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157525","id":1119542361,"node_id":"I_kwDOAEVQ_M5CutxZ","number":157525,"title":"Packaging request: beeware","user":{"login":"cafehaine","id":11913365,"node_id":"MDQ6VXNlcjExOTEzMzY1","avatar_url":"https://avatars.githubusercontent.com/u/11913365?v=4","gravatar_id":"","url":"https://api.github.com/users/cafehaine","html_url":"https://github.com/cafehaine","followers_url":"https://api.github.com/users/cafehaine/followers","following_url":"https://api.github.com/users/cafehaine/following{/other_user}","gists_url":"https://api.github.com/users/cafehaine/gists{/gist_id}","starred_url":"https://api.github.com/users/cafehaine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cafehaine/subscriptions","organizations_url":"https://api.github.com/users/cafehaine/orgs","repos_url":"https://api.github.com/users/cafehaine/repos","events_url":"https://api.github.com/users/cafehaine/events{/privacy}","received_events_url":"https://api.github.com/users/cafehaine/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-31T14:59:39Z","updated_at":"2022-01-31T14:59:39Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nBeeware is a set of python tools and libraries to build cross-platform applications with a native front-end.\r\nIt is mainly composed of:\r\n- briefcase: The packaging tool\r\n- toga: The ui framework\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://beeware.org/\r\n* source URL: https://github.com/beeware/\r\n* license: new bsd\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157525/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157510","id":1119330008,"node_id":"I_kwDOAEVQ_M5Ct57Y","number":157510,"title":"annotator – com.github.phase1geo.annotator.","user":{"login":"Abdillah","id":3030950,"node_id":"MDQ6VXNlcjMwMzA5NTA=","avatar_url":"https://avatars.githubusercontent.com/u/3030950?v=4","gravatar_id":"","url":"https://api.github.com/users/Abdillah","html_url":"https://github.com/Abdillah","followers_url":"https://api.github.com/users/Abdillah/followers","following_url":"https://api.github.com/users/Abdillah/following{/other_user}","gists_url":"https://api.github.com/users/Abdillah/gists{/gist_id}","starred_url":"https://api.github.com/users/Abdillah/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Abdillah/subscriptions","organizations_url":"https://api.github.com/users/Abdillah/orgs","repos_url":"https://api.github.com/users/Abdillah/repos","events_url":"https://api.github.com/users/Abdillah/events{/privacy}","received_events_url":"https://api.github.com/users/Abdillah/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-31T11:52:21Z","updated_at":"2022-01-31T11:53:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nImage crop and annotation tool built using Gtk and Vala.\r\nI think it is compatible with GNOME environment.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/phase1geo/Annotator\r\n* source URL: https://github.com/phase1geo/Annotator\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157510/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157469","id":1118820536,"node_id":"I_kwDOAEVQ_M5Cr9i4","number":157469,"title":"kitty's diff kitten does not perform syntax-highlighting","user":{"login":"leungbk","id":29217594,"node_id":"MDQ6VXNlcjI5MjE3NTk0","avatar_url":"https://avatars.githubusercontent.com/u/29217594?v=4","gravatar_id":"","url":"https://api.github.com/users/leungbk","html_url":"https://github.com/leungbk","followers_url":"https://api.github.com/users/leungbk/followers","following_url":"https://api.github.com/users/leungbk/following{/other_user}","gists_url":"https://api.github.com/users/leungbk/gists{/gist_id}","starred_url":"https://api.github.com/users/leungbk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/leungbk/subscriptions","organizations_url":"https://api.github.com/users/leungbk/orgs","repos_url":"https://api.github.com/users/leungbk/repos","events_url":"https://api.github.com/users/leungbk/events{/privacy}","received_events_url":"https://api.github.com/users/leungbk/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-31T01:08:22Z","updated_at":"2022-02-16T19:21:50Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"`kitty +kitten diff a.py b.py` outputs a split diff, but the contents aren't syntax-highlighted. The kitty documentation says `pygments` is required for syntax-highlighting to work, though simply adding `python3Packages.pygments` to the Nix recipe does not seem to be enough to produce the desired highlighting.\r\n\r\n\r\n### Notify maintainers\r\n@Luflosi \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157469/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157451","id":1118730027,"node_id":"I_kwDOAEVQ_M5Crncr","number":157451,"title":"`profiles/hardened`: setting `environment.memoryAllocator.provider`to scudo occasionally breaks sshd ","user":{"login":"al3xtjames","id":5672538,"node_id":"MDQ6VXNlcjU2NzI1Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/5672538?v=4","gravatar_id":"","url":"https://api.github.com/users/al3xtjames","html_url":"https://github.com/al3xtjames","followers_url":"https://api.github.com/users/al3xtjames/followers","following_url":"https://api.github.com/users/al3xtjames/following{/other_user}","gists_url":"https://api.github.com/users/al3xtjames/gists{/gist_id}","starred_url":"https://api.github.com/users/al3xtjames/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/al3xtjames/subscriptions","organizations_url":"https://api.github.com/users/al3xtjames/orgs","repos_url":"https://api.github.com/users/al3xtjames/repos","events_url":"https://api.github.com/users/al3xtjames/events{/privacy}","received_events_url":"https://api.github.com/users/al3xtjames/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-30T21:46:39Z","updated_at":"2022-02-24T21:43:35Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nAfter importing `profiles/hardened.nix`, I noticed that logging into my host via SSH would occasionally fail with one of the following errors:\r\n```console\r\nclient_loop: send disconnect: Broken pipe\r\n```\r\n\r\n```console\r\nConnection closed by <host IP> port 22\r\n```\r\n\r\n```console\r\nConnection reset by <host IP> port 22\r\n```\r\n\r\n`journalctl -u sshd` on the remote host showed the following error:\r\n```console\r\nfatal: privsep_preauth: preauth child terminated by signal 31\r\n```\r\n\r\nI was able to reduce this to the allocator change. Setting `environment.memoryAllocator.provider = \"scudo\";` is enough to cause these occasional sshd crashes.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add `environment.memoryAllocator.provider = \"scudo\";` to configuration.nix and switch to the new configuration on the remote host.\r\n2. Try to repeatedly connect to the host with `while true; do ssh <host> true; done`.\r\n3. Observe one of the error messages shown above.\r\n\r\n### Expected behavior\r\nSSH connections work as expected.\r\n\r\n### Additional context\r\nHere's the backtrace from a coredump:\r\n```\r\n(gdb) bt\r\n#0 0x0000de92f957e828 in syscall () from /nix/store/5z7rlpz6dsnp5fgivz24kkc19va507h7-glibc-2.33-62/lib/libc.so.6\r\n#1 0x0000de92f9b68554 in gwp_asan::AllocationMetadata::RecordAllocation(unsigned long, unsigned long) () from /nix/store/hkvgl5ka064a0c55vfwcc20li06jqg2s-malloc-provider-scudo/lib/libclang_rt.scudo-aarch64.so\r\n#2 0x0000de92f9b69150 in gwp_asan::GuardedPoolAllocator::allocate(unsigned long, unsigned long) () from /nix/store/hkvgl5ka064a0c55vfwcc20li06jqg2s-malloc-provider-scudo/lib/libclang_rt.scudo-aarch64.so\r\n#3 0x0000de92f9b56df0 in __scudo::Allocator::allocate(unsigned long, unsigned long, __scudo::AllocType, bool) () from /nix/store/hkvgl5ka064a0c55vfwcc20li06jqg2s-malloc-provider-scudo/lib/libclang_rt.scudo-aarch64.so\r\n#4 0x0000de92f9b5337c in __scudo::scudoAllocate(unsigned long, unsigned long, __scudo::AllocType) () from /nix/store/hkvgl5ka064a0c55vfwcc20li06jqg2s-malloc-provider-scudo/lib/libclang_rt.scudo-aarch64.so\r\n#5 0x0000de92f99d90ac in CRYPTO_zalloc () from /nix/store/qqk9kv2kma1iy9h8cipfhk8g5widswic-openssl-1.1.1m/lib/libcrypto.so.1.1\r\n#6 0x0000de92f99c8530 in EVP_CipherInit_ex () from /nix/store/qqk9kv2kma1iy9h8cipfhk8g5widswic-openssl-1.1.1m/lib/libcrypto.so.1.1\r\n#7 0x00000f5c1335a954 in chachapoly_new ()\r\n#8 0x00000f5c1333eb48 in cipher_init ()\r\n#9 0x00000f5c1334580c in ssh_set_newkeys ()\r\n#10 0x00000f5c1335c110 in kex_input_newkeys ()\r\n#11 0x00000f5c1334e3a4 in ssh_dispatch_run ()\r\n#12 0x00000f5c1334e47c in ssh_dispatch_run_fatal ()\r\n#13 0x00000f5c132f08a4 in main ()\r\n```\r\n\r\nAnd some output from strace:\r\n\r\n```\r\n[pid 3544] gettid() = ?\r\n[pid 3544] +++ killed by SIGSYS (core dumped) +++\r\n```\r\n\r\nAs shown in the backtrace, this `gettid` call is coming from [gwp_asan::AllocationMetadata::RecordAllocation](https://github.com/llvm/llvm-project/blob/llvmorg-13.0.0/compiler-rt/lib/gwp_asan/common.cpp#L46) ([`getThreadID` is a simple wrapper around `gettid`](https://github.com/llvm/llvm-project/blob/llvmorg-13.0.0/compiler-rt/lib/gwp_asan/platform_specific/common_posix.cpp#L20)).\r\n\r\n`gettid` is not included in OpenSSH's seccomp whitelist: https://github.com/openssh/openssh-portable/blob/V_8_8_P1/sandbox-seccomp-filter.c#L133. So this should probably be fixed upstream.\r\n\r\n### Notify maintainers\r\n@joachifm\r\n@emilazy\r\n\r\n### Metadata\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.10.94, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-21.11.334797.6979c0e49bb\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157451/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157449","id":1118702907,"node_id":"I_kwDOAEVQ_M5Crg07","number":157449,"title":"LoadCredential doesn't result in a credential file being created","user":{"login":"Pacman99","id":16345849,"node_id":"MDQ6VXNlcjE2MzQ1ODQ5","avatar_url":"https://avatars.githubusercontent.com/u/16345849?v=4","gravatar_id":"","url":"https://api.github.com/users/Pacman99","html_url":"https://github.com/Pacman99","followers_url":"https://api.github.com/users/Pacman99/followers","following_url":"https://api.github.com/users/Pacman99/following{/other_user}","gists_url":"https://api.github.com/users/Pacman99/gists{/gist_id}","starred_url":"https://api.github.com/users/Pacman99/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Pacman99/subscriptions","organizations_url":"https://api.github.com/users/Pacman99/orgs","repos_url":"https://api.github.com/users/Pacman99/repos","events_url":"https://api.github.com/users/Pacman99/events{/privacy}","received_events_url":"https://api.github.com/users/Pacman99/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-30T21:00:01Z","updated_at":"2022-02-06T15:56:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen a systemd service uses `LoadCredential` it doesn't seem to get access to that credential, and it seems like the file in `/run/credentials` doesn't even exist.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. I'm not sure what option is causing it, but I'm pretty sure it's `boot.isContainer = true`. So enable that option\r\n2. Enable a service that makes use of `LoadCredential` like keycloak or nix-serve\r\n3. The service will fail with an error that it doesn't have permissions for that file. Which I think happens because they don't have access to /run/credentials, but when inspecting that file, the file/folder where the credential should be doesn't exist.\r\n\r\n### Expected behavior\r\nSystemd should create a folder in `/run/credentials` like `nix-serve.service` with the credential file, so the service can access it.\r\n\r\n### Additional context\r\nI use vpsfree, so I've enabled the recommended options for a vpsfree server, https://gitlab.com/coffeetables/myrdd/-/blob/master/profiles/vpsadminos.nix. The rest of my server's config is in that repository.\r\n\r\nI've also filed an issue in systemd/systemd#21789, but I think it might be a nixos specific issue. It was tagged in the systemd repo as an nspawn issue.\r\n\r\nHere is log from nix-serve that i posted there:\r\n[error(1).log](https://github.com/NixOS/nixpkgs/files/7966911/error.1.log)\r\nI think this is the offending line: `Failed to mount /run/credentials/nix-serve.service (type n/a) on /run/systemd/unit-root/run/credentials/nix-serve.service (MS_BIND \"\"): No such file or directory`\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.60, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5pre20211007_844dd90`\r\n - channels(root): `\"nixos-21.05pre287333.63586475587\"`\r\n - nixpkgs: `/nix/store/q8fqyyh6l0apzm29x7syl04pdp886b2f-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157449/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157424","id":1118612555,"node_id":"I_kwDOAEVQ_M5CrKxL","number":157424,"title":"Package 'beautifulsoup4' fails to install on macOS","user":{"login":"boxmein","id":358714,"node_id":"MDQ6VXNlcjM1ODcxNA==","avatar_url":"https://avatars.githubusercontent.com/u/358714?v=4","gravatar_id":"","url":"https://api.github.com/users/boxmein","html_url":"https://github.com/boxmein","followers_url":"https://api.github.com/users/boxmein/followers","following_url":"https://api.github.com/users/boxmein/following{/other_user}","gists_url":"https://api.github.com/users/boxmein/gists{/gist_id}","starred_url":"https://api.github.com/users/boxmein/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/boxmein/subscriptions","organizations_url":"https://api.github.com/users/boxmein/orgs","repos_url":"https://api.github.com/users/boxmein/repos","events_url":"https://api.github.com/users/boxmein/events{/privacy}","received_events_url":"https://api.github.com/users/boxmein/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-30T17:25:31Z","updated_at":"2022-02-10T17:43:25Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nBeautifulsoup4 fails to install due to an error during testing:\r\n\r\n```\r\nE bs4.builder.ParserRejectedMarkup: The markup you provided was rejected by the parser. Trying a different parser or a different encoding may help.\r\nE\r\nE Original exception(s) from parser:\r\nE UnicodeDecodeError: 'utf-8' codec can't decode byte 0x91 in position 0: invalid start byte\r\nE LookupError: unknown encoding: 'b'windows-1252''\r\n\r\nbs4/__init__.py:371: ParserRejectedMarkup\r\n_________ LXMLXMLTreeBuilderSmokeTest.test_can_parse_unicode_document __________\r\n\r\nself = <bs4.tests.test_lxml.LXMLXMLTreeBuilderSmokeTest testMethod=test_can_parse_unicode_document>\r\n\r\n def test_can_parse_unicode_document(self):\r\n markup = '<?xml version=\"1.0\" encoding=\"euc-jp\"><root>Sacr\\N{LATIN SMALL LETTER E WITH ACUTE} bleu!</root>'\r\n soup = self.soup(markup)\r\n> self.assertEqual('Sacr\\xe9 bleu!', soup.root.string)\r\nE AttributeError: 'NoneType' object has no attribute 'string'\r\n\r\nbs4/testing.py:1002: AttributeError\r\n=========================== short test summary info ============================\r\nFAILED bs4/tests/test_lxml.py::LXMLTreeBuilderSmokeTest::test_real_hebrew_document\r\nFAILED bs4/tests/test_lxml.py::LXMLTreeBuilderSmokeTest::test_smart_quotes_converted_on_the_way_in\r\nFAILED bs4/tests/test_lxml.py::LXMLXMLTreeBuilderSmokeTest::test_can_parse_unicode_document\r\n======================== 3 failed, 514 passed in 1.76s =========================\r\nbuilder for '/nix/store/3rg6g9lw2xpls8gyrn5x1bv2bkjdnw64-python3.9-beautifulsoup4-4.10.0.drv' failed with exit code 1\r\nerror: build of '/nix/store/3rg6g9lw2xpls8gyrn5x1bv2bkjdnw64-python3.9-beautifulsoup4-4.10.0.drv' failed\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p python39Packages.beautifulsoup4`\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\nIt installs\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n```\r\n❯ nix doctor\r\nStore uri: daemon\r\n\r\nWarning: multiple versions of nix found in PATH.\r\n\r\n /nix/store/c43kyri67ia8mibs0id5ara7gqwlkybf-nix-2.3.16/bin\r\n /nix/store/ws2zdpdihrp28zf1pxnx1h56r81xay7j-nix-2.3.16/bin\r\n\r\n❯ nix --version\r\nnix (Nix) 2.3.16\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@domenkozar\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.1.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"darwin, home-manager, nixpkgs-21.11pre326821.509d236edf0\"`\r\n - channels(johannes): `\"darwin, home-manager, nixpkgs-22.05pre349720.5efc8ca9542\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157424/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157411","id":1118586824,"node_id":"I_kwDOAEVQ_M5CrEfI","number":157411,"title":"i18n.extraLocaleSettings does not behave as expected","user":{"login":"broccoli5","id":46381898,"node_id":"MDQ6VXNlcjQ2MzgxODk4","avatar_url":"https://avatars.githubusercontent.com/u/46381898?v=4","gravatar_id":"","url":"https://api.github.com/users/broccoli5","html_url":"https://github.com/broccoli5","followers_url":"https://api.github.com/users/broccoli5/followers","following_url":"https://api.github.com/users/broccoli5/following{/other_user}","gists_url":"https://api.github.com/users/broccoli5/gists{/gist_id}","starred_url":"https://api.github.com/users/broccoli5/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/broccoli5/subscriptions","organizations_url":"https://api.github.com/users/broccoli5/orgs","repos_url":"https://api.github.com/users/broccoli5/repos","events_url":"https://api.github.com/users/broccoli5/events{/privacy}","received_events_url":"https://api.github.com/users/broccoli5/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-30T15:46:17Z","updated_at":"2022-02-09T16:26:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Bug description\r\n`i18n.extraLocaleSettings` does not set right values for the locale settings. I have pretty weird setup because I want my system to be in en_US, but I want a sane date format so I set `LC_TIME` to en_GB, and because I'm from Czechia I set for ex. `LC_MONETARY` to cs_CZ. But when I run `locale` the locale settings are either en_US or en_GB\r\n\r\n### Steps To Reproduce\r\n1. Add these settings to `/etc/nixos/configuration.nix`\r\n```nix\r\n{\r\n # ...\r\n i18n = {\r\n defaultLocale = \"en_US.UTF-8\";\r\n extraLocaleSettings = {\r\n LC_TIME = \"en_GB.UTF-8\";\r\n LC_MONETARY = \"cs_CZ.UTF-8\";\r\n # Some other settings set to cs_CZ.UTF-8\r\n };\r\n };\r\n # ...\r\n}\r\n``` \r\n2. `sudo nixos-rebuild switch`\r\n3. reboot\r\n4. see output of `locale`\r\n\r\n### Expected behavior\r\n`i18n.extraLocaleSettings` should set the right values for the locale settings \r\n\r\n### Additional context\r\nHere is my output of `locale`:\r\n\r\n```console\r\n[user@system:~]$ locale\r\nLANG=en_US.UTF-8\r\nLC_CTYPE=\"en_US.UTF-8\"\r\nLC_NUMERIC=en_GB.UTF-8\r\nLC_TIME=en_GB.UTF-8\r\nLC_COLLATE=\"en_US.UTF-8\"\r\nLC_MONETARY=en_GB.UTF-8\r\nLC_MESSAGES=\"en_US.UTF-8\"\r\nLC_PAPER=en_GB.UTF-8\r\nLC_NAME=\"en_US.UTF-8\"\r\nLC_ADDRESS=\"en_US.UTF-8\"\r\nLC_TELEPHONE=\"en_US.UTF-8\"\r\nLC_MEASUREMENT=en_GB.UTF-8\r\nLC_IDENTIFICATION=\"en_US.UTF-8\"\r\nLC_ALL=\r\n```\r\n\r\n### Notify maintainers\r\n@edolstra (sorry if I should have tagged somebody else) \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(broccoli): `\"home-manager\"`\r\n - channels(root): `\"nixos-21.11.335526.6c4b9f1a2fd\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157411/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157398","id":1118551899,"node_id":"I_kwDOAEVQ_M5Cq79b","number":157398,"title":"buildBazelPackage has no documentation","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-30T14:25:09Z","updated_at":"2022-03-07T11:44:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nhttps://nixos.org/manual/nixpkgs/unstable/#chap-language-support has no chapter on Bazel and even looking at its [source](https://github.com/NixOS/nixpkgs/blob/master/pkgs/build-support/build-bazel-package/default.nix) does little to help \r\n\r\n### Additional context\r\nEncountered this while trying to package [mediapipe](https://github.com/NixOS/nixpkgs/pull/153255)\r\n\r\n### Notify maintainers\r\n@NixOS/bazel \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157398/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157397","id":1118550341,"node_id":"I_kwDOAEVQ_M5Cq7lF","number":157397,"title":"python3Packages.opencv should also export the wrapper packages","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-30T14:18:54Z","updated_at":"2022-01-31T15:39:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`python3Packages.opencv` only exports the `opencv` package.\r\nHowever many python packages depend on the prebuilt `opencv-python`(https://pypi.org/project/opencv-python/) or `opencv-python-headless`(https://pypi.org/project/opencv-python-headless/) pip package, as they are a drop in replacement for each other.\r\nAlso if opencv is built with the contrib extensions `opencv-contrib-python`(https://pypi.org/project/opencv-contrib-python/) should be exposed too.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Try to package a python package depending on `opencv-python` like `medialib`\r\n2. Add `opencv` to `propagatedBuildInputs`\r\n3. Build it\r\n\r\n### Expected behavior\r\nBuild succeeds without problems\r\n\r\n### Additional context\r\nI've encountered this while trying to build https://github.com/NixOS/nixpkgs/pull/153255\r\nThe suggested workaround of patching the dependant packages by removing the `opencv-python` dependency would not work if we source the package from a wheel for example.\r\n\r\nIt also duplicate works that should be done only in one place\r\n\r\n### Notify maintainers\r\n@jonringer @mdaiter @basvandijk \r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.2, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/store/8jc465d8r1mrjxb7j6wx7qc7d95frv0k-source`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157397/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157383","id":1118488629,"node_id":"I_kwDOAEVQ_M5Cqsg1","number":157383,"title":"shells-environment: Consider putting local bin paths last","user":{"login":"sagehane","id":74805176,"node_id":"MDQ6VXNlcjc0ODA1MTc2","avatar_url":"https://avatars.githubusercontent.com/u/74805176?v=4","gravatar_id":"","url":"https://api.github.com/users/sagehane","html_url":"https://github.com/sagehane","followers_url":"https://api.github.com/users/sagehane/followers","following_url":"https://api.github.com/users/sagehane/following{/other_user}","gists_url":"https://api.github.com/users/sagehane/gists{/gist_id}","starred_url":"https://api.github.com/users/sagehane/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sagehane/subscriptions","organizations_url":"https://api.github.com/users/sagehane/orgs","repos_url":"https://api.github.com/users/sagehane/repos","events_url":"https://api.github.com/users/sagehane/events{/privacy}","received_events_url":"https://api.github.com/users/sagehane/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-30T10:39:33Z","updated_at":"2022-03-02T14:11:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nNot really a bug, but a concern with the status quo.\r\n\r\n`environment.localBinPath` and `homeBinPath` sets `export PATH=\"$HOME/.local/bin:$PATH\"`, which can be used to override system binaries. (See https://github.com/NixOS/nixpkgs/blob/master/nixos/modules/config/shells-environment.nix#L209)\r\nThis seems like a footgun to me, and I guess someone with the proper permissions can put a harmful binary under `~/.local/bin/cd` and trick users into running it. (Although if they can inject a binary in your `~/.local/bin`, you certainly have other things to worry about)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nSet `enviornment.localBinPath` or `environment.homeBinPath` to `true`.\r\n\r\n### Expected behavior\r\nI think `export PATH=\"$PATH:$HOME/.local/bin\"` makes more sense. Arch certainly seems to default to this, although idk about other distros.\r\n\r\nFor now, people can set `environment.variables.PATH = \"$PATH:$HOME/.local/bin\";`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157383/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157349","id":1118395964,"node_id":"I_kwDOAEVQ_M5CqV48","number":157349,"title":"`boot.initrd.verbose` does not affect stage-2, no way to reduce output of stage-2","user":{"login":"andreoss","id":49783909,"node_id":"MDQ6VXNlcjQ5NzgzOTA5","avatar_url":"https://avatars.githubusercontent.com/u/49783909?v=4","gravatar_id":"","url":"https://api.github.com/users/andreoss","html_url":"https://github.com/andreoss","followers_url":"https://api.github.com/users/andreoss/followers","following_url":"https://api.github.com/users/andreoss/following{/other_user}","gists_url":"https://api.github.com/users/andreoss/gists{/gist_id}","starred_url":"https://api.github.com/users/andreoss/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/andreoss/subscriptions","organizations_url":"https://api.github.com/users/andreoss/orgs","repos_url":"https://api.github.com/users/andreoss/repos","events_url":"https://api.github.com/users/andreoss/events{/privacy}","received_events_url":"https://api.github.com/users/andreoss/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-30T03:34:23Z","updated_at":"2022-01-31T07:23:24Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`boot.initrd.verbose` only works for `stage-1`, not `stage-2`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set `boot.initrd.verbose = false;`\r\n2. No verbose output in stage-1\r\n3. Still verbose output in stage-2\r\n\r\n### Expected behavior\r\nStage-2 output should not be verbose. \r\n\r\n### Additional context\r\nMay be the reason for this is that `stage-2` is not exactly `initrd`,\r\nin that case maybe other parameter should affect output of stage-2 (i.e `boot.stage-2.verbose`)?\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n\r\n```console\r\n nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/fwjba5s3bxmm68m19rks3gv5fajz6d37-bash-interactive-5.1-p12-dev\r\ncopying path '/nix/store/fwjba5s3bxmm68m19rks3gv5fajz6d37-bash-interactive-5.1-p12-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.16-lqx2, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(a): `\"home-manager, nixos-22.05pre346004.5aaed40d22f, nixos-unstable-22.05pre346004.5aaed40d22f\"`\r\n - channels(root): `\"nixos-22.05pre349657.5bb20f9dc70\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157349/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157341","id":1118379748,"node_id":"I_kwDOAEVQ_M5CqR7k","number":157341,"title":"Python quart","user":{"login":"hg0428","id":45984899,"node_id":"MDQ6VXNlcjQ1OTg0ODk5","avatar_url":"https://avatars.githubusercontent.com/u/45984899?v=4","gravatar_id":"","url":"https://api.github.com/users/hg0428","html_url":"https://github.com/hg0428","followers_url":"https://api.github.com/users/hg0428/followers","following_url":"https://api.github.com/users/hg0428/following{/other_user}","gists_url":"https://api.github.com/users/hg0428/gists{/gist_id}","starred_url":"https://api.github.com/users/hg0428/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hg0428/subscriptions","organizations_url":"https://api.github.com/users/hg0428/orgs","repos_url":"https://api.github.com/users/hg0428/repos","events_url":"https://api.github.com/users/hg0428/events{/privacy}","received_events_url":"https://api.github.com/users/hg0428/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-30T01:49:07Z","updated_at":"2022-01-30T01:49:07Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://pgjones.gitlab.io/quart/\r\n* source URL: https://pgjones.gitlab.io/quart/\r\n* license: mit, bsd, gpl2+ , ...\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157341/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157325","id":1118350307,"node_id":"I_kwDOAEVQ_M5CqKvj","number":157325,"title":"`yaml-to-dhall` is not included in `dhall-json`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-29T23:14:03Z","updated_at":"2022-01-31T03:33:30Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nDhall claims to include an executable `yaml-to-dhall` ([source](https://twitter.com/dhall_lang/status/1144289285689860096?lang=en)). I'm able to find `dhall-to-yaml`, but not `yaml-to-dhall`:\r\n```\r\n❯ nix-shell -p dhall dhall-json\r\nthese paths will be fetched (1.84 MiB download, 11.15 MiB unpacked):\r\n /nix/store/5c2dzhv8bz8rabqkg12wvviwwc6ybpvx-dhall-1.39.0\r\ncopying path '/nix/store/5c2dzhv8bz8rabqkg12wvviwwc6ybpvx-dhall-1.39.0' from 'https://cache.nixos.org'...\r\n\r\n[nix-shell:~/dev/nixpkgs-upkeep]$ dhall-to-yaml --version\r\n1.7.7\r\n\r\n[nix-shell:~/dev/nixpkgs-upkeep]$ yaml-to-dhall\r\nyaml-to-dhall: command not found\r\n```\r\n\r\n### Steps To Reproduce\r\nIllustrated above. \r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nn/a\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Gabriel439 \r\n(I had a hard time tracking down how dhall/dhall-json are packaged, and was not able to find a `meta.maintainers`, but this is my best guess 🤷)\r\n\r\n### Metadata\r\n\r\n```console\r\n❯ nix-shell -p nix-info --run \"nix-info -m\" \r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.91, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335376.610d4ea2750, nix-ld\"`\r\n - channels(skainswo): `\"home-manager, nixpkgs-unstable-22.05pre343295.adf7f03d3bf\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157325/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157269","id":1118190502,"node_id":"I_kwDOAEVQ_M5Cpjum","number":157269,"title":"`swapDevices` with `randomEncryption` enabled don't work if `device` contains `:` character","user":{"login":"davidkna","id":835177,"node_id":"MDQ6VXNlcjgzNTE3Nw==","avatar_url":"https://avatars.githubusercontent.com/u/835177?v=4","gravatar_id":"","url":"https://api.github.com/users/davidkna","html_url":"https://github.com/davidkna","followers_url":"https://api.github.com/users/davidkna/followers","following_url":"https://api.github.com/users/davidkna/following{/other_user}","gists_url":"https://api.github.com/users/davidkna/gists{/gist_id}","starred_url":"https://api.github.com/users/davidkna/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidkna/subscriptions","organizations_url":"https://api.github.com/users/davidkna/orgs","repos_url":"https://api.github.com/users/davidkna/repos","events_url":"https://api.github.com/users/davidkna/events{/privacy}","received_events_url":"https://api.github.com/users/davidkna/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-29T11:21:38Z","updated_at":"2022-03-13T22:37:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nSince the last unstable update, `swapDevices` when used with a device that contain a colon like `/dev/md/host:name` or `/disk/by-id/md-uuid-00000000:00000000:00000000:00000000` with `swapDevices.*.randomEncryption = true` fail with:\r\n```\r\nerror: store path ...-unit-script-mkswap-dev-md-host:name-start contains illegal character ':'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set\r\n ```\r\n swapDevices = [{\r\n # Or any path with a colon that if tested\r\n device = \"/dev/md/disk:name\";\r\n randomEncryption.enable = true;\r\n }];\r\n```\r\n\r\n### Expected behavior\r\nColons don't leak into the script name, and device paths with a colon are supported (again) in this scenario.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.16, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(david): `\"\"`\r\n - channels(root): `\"nixos-22.05pre348581.c07b471b52b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157269/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157195","id":1117865402,"node_id":"I_kwDOAEVQ_M5CoUW6","number":157195,"title":"nixos/test-driver: non-destructively check for open ports","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-28T21:32:25Z","updated_at":"2022-01-28T21:32:25Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Currently, we use `nc -z` to check for open ports. This works, but it also connects to the port which can have an effect. Maybe it would be better to use `lsof -i:$PORT` or `netstat` to do this. ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157195/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157157","id":1117544260,"node_id":"I_kwDOAEVQ_M5CnF9E","number":157157,"title":"headless virtualbox option causes nixos-rebuild failure","user":{"login":"chreekat","id":538538,"node_id":"MDQ6VXNlcjUzODUzOA==","avatar_url":"https://avatars.githubusercontent.com/u/538538?v=4","gravatar_id":"","url":"https://api.github.com/users/chreekat","html_url":"https://github.com/chreekat","followers_url":"https://api.github.com/users/chreekat/followers","following_url":"https://api.github.com/users/chreekat/following{/other_user}","gists_url":"https://api.github.com/users/chreekat/gists{/gist_id}","starred_url":"https://api.github.com/users/chreekat/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/chreekat/subscriptions","organizations_url":"https://api.github.com/users/chreekat/orgs","repos_url":"https://api.github.com/users/chreekat/repos","events_url":"https://api.github.com/users/chreekat/events{/privacy}","received_events_url":"https://api.github.com/users/chreekat/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-28T15:39:30Z","updated_at":"2022-03-31T13:51:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nWhen I try to rebuild a system with `virtualisation.virtualbox.host.headless = true`, I get the following message during nixos-rebuild:\r\n\r\n```\r\nbuilding '/nix/store/6n0nkd1p2cpb0amb8krxrnd2s3qg16a7-ensure-all-wrappers-paths-exist.drv'...\r\nChecking that Nix store paths of all wrapped programs exist... FAIL\r\nThe path /nix/store/rsxs7kp1yx03iq6vz4yyrxpsa50w345d-virtualbox-6.1.30/libexec/virtualbox/VBoxSDL does not exist!\r\nPlease, check the value of `security.wrappers.\"VBoxSDL\".source`.\r\n```\r\n\r\nThis problem went away when I changed the option to `false`.\r\n\r\n### Steps to reproduce\r\n\r\n(Untested outside of my own system)\r\n\r\nUse the following in configuration.nix:\r\n\r\n```\r\n # For local environments\r\n virtualbox = {\r\n host.enable = true;\r\n host.headless = true;\r\n };\r\n```\r\n\r\nThen, run `nixos-rebuild test`.\r\n\r\n\r\n## Technical details\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335526.6c4b9f1a2fd\"`\r\n - channels(b): `\"unstable-21.11pre318500.51bcdc4cdaa\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157157/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157139","id":1117359476,"node_id":"I_kwDOAEVQ_M5CmY10","number":157139,"title":"Adding SonoBus to nixpkgs","user":{"login":"krissemicolon","id":41425452,"node_id":"MDQ6VXNlcjQxNDI1NDUy","avatar_url":"https://avatars.githubusercontent.com/u/41425452?v=4","gravatar_id":"","url":"https://api.github.com/users/krissemicolon","html_url":"https://github.com/krissemicolon","followers_url":"https://api.github.com/users/krissemicolon/followers","following_url":"https://api.github.com/users/krissemicolon/following{/other_user}","gists_url":"https://api.github.com/users/krissemicolon/gists{/gist_id}","starred_url":"https://api.github.com/users/krissemicolon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/krissemicolon/subscriptions","organizations_url":"https://api.github.com/users/krissemicolon/orgs","repos_url":"https://api.github.com/users/krissemicolon/repos","events_url":"https://api.github.com/users/krissemicolon/events{/privacy}","received_events_url":"https://api.github.com/users/krissemicolon/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-28T12:40:04Z","updated_at":"2022-01-28T12:40:04Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**SonoBus is a real-time network audio streaming collaboration tool.**\r\n_SonoBus is an easy to use application for streaming high-quality, low-latency peer-to-peer audio between devices over the internet or a local network._\r\n_It is really easy to use and has a nice GUI_\r\n_Also it is efficient and written in C++._\r\n\r\n**Metadata**\r\n\r\n* homepage URL: [sonobus.net](https://sonobus.net)\r\n* source URL: [github/sonosaurus/sonobus](https://github.com/sonosaurus/sonobus)\r\n* license: gplv3\r\n* platforms: windows, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157139/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157034","id":1116616664,"node_id":"I_kwDOAEVQ_M5CjjfY","number":157034,"title":"In some cases, enabling networkd will break in-initrd network","user":{"login":"flokli","id":183879,"node_id":"MDQ6VXNlcjE4Mzg3OQ==","avatar_url":"https://avatars.githubusercontent.com/u/183879?v=4","gravatar_id":"","url":"https://api.github.com/users/flokli","html_url":"https://github.com/flokli","followers_url":"https://api.github.com/users/flokli/followers","following_url":"https://api.github.com/users/flokli/following{/other_user}","gists_url":"https://api.github.com/users/flokli/gists{/gist_id}","starred_url":"https://api.github.com/users/flokli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/flokli/subscriptions","organizations_url":"https://api.github.com/users/flokli/orgs","repos_url":"https://api.github.com/users/flokli/repos","events_url":"https://api.github.com/users/flokli/events{/privacy}","received_events_url":"https://api.github.com/users/flokli/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-27T18:38:59Z","updated_at":"2022-01-27T18:39:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI'm using in-initrd ssh to unlock disks. Previously, my system config was defaulting to the scripted networking and no explicit list of interfaces to DHCP from.\r\n\r\nI enabled systemd-networkd on my server configuration, by adding the following block:\r\n\r\n```\r\n # use networkd\r\n networking.useNetworkd = true;\r\n networking.useDHCP = false;\r\n systemd.network.networks = {\r\n \"10-uplink\" = {\r\n matchConfig = {\r\n Name = \"en* eth*\";\r\n Driver = \"igb\";\r\n };\r\n networkConfig.IPv6AcceptRA = false;\r\n address = [\r\n \"xxx.xxx.xxx.xxx/32\"\r\n \"2a01:4f8:xxxx:xxxx::1/128\"\r\n ];\r\n routes = [\r\n {\r\n routeConfig = {\r\n Gateway = \"xxx.xxx.xxx.xxx\";\r\n GatewayOnLink = true;\r\n };\r\n }\r\n {\r\n routeConfig = {\r\n Gateway = \"fe80::1\";\r\n GatewayOnLink = true;\r\n };\r\n }\r\n ];\r\n };\r\n };\r\n```\r\n\r\nI switched my system to this config, verified everything came up properly, and rebooted.\r\n\r\nI noticed the in-initrd networking \"stack\" didn't come up. It didn't explicitly configure the addresses, and didn't do DHCP either.\r\n\r\nThis was a bit surprising.\r\n\r\nDigging into `nixos/modules/system/boot/initrd-network.nix`, I remembered the following two lines:\r\n\r\n```\r\n dhcpInterfaces = lib.attrNames (lib.filterAttrs (iface: v: v.useDHCP == true) (config.networking.interfaces or {}));\r\n doDhcp = config.networking.useDHCP || dhcpInterfaces != [];\r\n```\r\n\r\nEssentially, because we don't enable dhcp via the `networking.useDHCP` or `networking.interfaces.*.useDHCP` knobs, in-initrd dhcp is disabled, and as network configuration is set via `systemd.network.networks`, the in-initrd networking stack can't configure anything.\r\n\r\nAs a workaround, I dropped a dummy `networking.interfaces.enp195s0.useDHCP = true;` in my config, which is not pretty and very generic, but at least causes the in-initrd network stack to still do DHCP.\r\n\r\nI feel like we should probably log a warning if no DHCP is enabled, no addresses configured, but `boot.initrd.network.enable` set to true.\r\n\r\nIn-initrd systemd (https://github.com/NixOS/nixpkgs/issues/72401) should probably fix this as well, as we could also run networkd in there.\r\n\r\n(cc @Mic92 @kirelagin @ElvishJerricco @andir )","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157034/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157018","id":1116401355,"node_id":"I_kwDOAEVQ_M5Ciu7L","number":157018,"title":"Installing KDE Plasma overrides user defined defaultFonts","user":{"login":"AlyamanMas","id":33905034,"node_id":"MDQ6VXNlcjMzOTA1MDM0","avatar_url":"https://avatars.githubusercontent.com/u/33905034?v=4","gravatar_id":"","url":"https://api.github.com/users/AlyamanMas","html_url":"https://github.com/AlyamanMas","followers_url":"https://api.github.com/users/AlyamanMas/followers","following_url":"https://api.github.com/users/AlyamanMas/following{/other_user}","gists_url":"https://api.github.com/users/AlyamanMas/gists{/gist_id}","starred_url":"https://api.github.com/users/AlyamanMas/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AlyamanMas/subscriptions","organizations_url":"https://api.github.com/users/AlyamanMas/orgs","repos_url":"https://api.github.com/users/AlyamanMas/repos","events_url":"https://api.github.com/users/AlyamanMas/events{/privacy}","received_events_url":"https://api.github.com/users/AlyamanMas/received_events","type":"User","site_admin":false},"labels":[{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-27T15:35:21Z","updated_at":"2022-02-07T16:41:56Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"# Issue\r\nSo, I have my own custom set default fonts with `fonts.fontconfig.defaultFonts`, but since I installed plasma with `services.xserver.desktopManager.plasma5.enable = true` it has very annoyingly overridden them.\r\nI believe this should be changed as the whole point of setting `fonts.fontconfig.defaultFonts` in your configuration is to change default fonts, without anything overriding them.\r\n\r\nI have determined that the issue lies here\r\nhttps://github.com/NixOS/nixpkgs/blob/d0947df00682c44dfa65c53299b63cb52757378b/nixos/modules/services/x11/desktop-managers/plasma5.nix#L377-L382","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157018/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157011","id":1116289370,"node_id":"I_kwDOAEVQ_M5CiTla","number":157011,"title":"uTimer","user":{"login":"danielb2","id":26678,"node_id":"MDQ6VXNlcjI2Njc4","avatar_url":"https://avatars.githubusercontent.com/u/26678?v=4","gravatar_id":"","url":"https://api.github.com/users/danielb2","html_url":"https://github.com/danielb2","followers_url":"https://api.github.com/users/danielb2/followers","following_url":"https://api.github.com/users/danielb2/following{/other_user}","gists_url":"https://api.github.com/users/danielb2/gists{/gist_id}","starred_url":"https://api.github.com/users/danielb2/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/danielb2/subscriptions","organizations_url":"https://api.github.com/users/danielb2/orgs","repos_url":"https://api.github.com/users/danielb2/repos","events_url":"https://api.github.com/users/danielb2/events{/privacy}","received_events_url":"https://api.github.com/users/danielb2/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-01-27T14:33:09Z","updated_at":"2022-02-25T19:42:25Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nµTimer (\"utimer\", pronounced \"micro-timer\") is a multifunction timer (command-line only). It provides a timer (e.g. count from 0 to 4 minutes), a countdown (e.g. count from 10 minutes to 0), and a stopwatch.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://launchpad.net/utimer\r\n* source URL: https://launchpad.net/utimer/0.4/0.4/+download/utimer-0.4.tar.gz\r\n* license: GNU GPL v3\r\n* platforms: unix, linux, darwin\r\n\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157011/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157008","id":1116266021,"node_id":"I_kwDOAEVQ_M5CiN4l","number":157008,"title":"id3tool","user":{"login":"danielb2","id":26678,"node_id":"MDQ6VXNlcjI2Njc4","avatar_url":"https://avatars.githubusercontent.com/u/26678?v=4","gravatar_id":"","url":"https://api.github.com/users/danielb2","html_url":"https://github.com/danielb2","followers_url":"https://api.github.com/users/danielb2/followers","following_url":"https://api.github.com/users/danielb2/following{/other_user}","gists_url":"https://api.github.com/users/danielb2/gists{/gist_id}","starred_url":"https://api.github.com/users/danielb2/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/danielb2/subscriptions","organizations_url":"https://api.github.com/users/danielb2/orgs","repos_url":"https://api.github.com/users/danielb2/repos","events_url":"https://api.github.com/users/danielb2/events{/privacy}","received_events_url":"https://api.github.com/users/danielb2/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-27T14:14:33Z","updated_at":"2022-01-27T16:56:00Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nid3tool is a command line utility for easy manipulation of the ID3 tags present in MPEG Layer 3 audio files\r\n\r\n**Metadata**\r\n\r\n* homepage URL: http://nekohako.xware.cx/id3tool/\r\n* source URL: http://nekohako.xware.cx/id3tool/id3tool-1.2a.tar.gz\r\n* license: homegrown/free (See COPYING in source)\r\n* platforms: i386/Linux, x86/Win32\r\n\r\n\r\n**Notes**\r\n\r\nFor reference, here's the homebrew bottle: https://github.com/Homebrew/homebrew-core/blob/HEAD/Formula/id3tool.rb\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157008/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003/events","html_url":"https://github.com/NixOS/nixpkgs/issues/157003","id":1116237984,"node_id":"I_kwDOAEVQ_M5CiHCg","number":157003,"title":"Arcmenu gnome shell extension problems","user":{"login":"RDKRACZ","id":43277609,"node_id":"MDQ6VXNlcjQzMjc3NjA5","avatar_url":"https://avatars.githubusercontent.com/u/43277609?v=4","gravatar_id":"","url":"https://api.github.com/users/RDKRACZ","html_url":"https://github.com/RDKRACZ","followers_url":"https://api.github.com/users/RDKRACZ/followers","following_url":"https://api.github.com/users/RDKRACZ/following{/other_user}","gists_url":"https://api.github.com/users/RDKRACZ/gists{/gist_id}","starred_url":"https://api.github.com/users/RDKRACZ/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/RDKRACZ/subscriptions","organizations_url":"https://api.github.com/users/RDKRACZ/orgs","repos_url":"https://api.github.com/users/RDKRACZ/repos","events_url":"https://api.github.com/users/RDKRACZ/events{/privacy}","received_events_url":"https://api.github.com/users/RDKRACZ/received_events","type":"User","site_admin":false},"labels":[{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-27T13:49:52Z","updated_at":"2022-01-28T14:11:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**The provided version is too old to even be enabled with the current gnome release in Nix 21.11. The official version of Arcmenu (from https://extensions.gnome.org/extension/3628/arcmenu/) doesn't detect Gmenu for some reason.**\r\n\r\n###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on GitHub to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit https://github.com/NixOS/nixpkgs/commit/71646d4e31a95c17e38f6889bdc786779f75a14f\r\nThe \"new_version\" is the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: gnome-shell-extension-arcmenu\r\n<!--\r\nThe current version can be found easily with the same process as above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 14\r\ndesired version: 20\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: https://github.com/dkabot\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/157003/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156993","id":1116111579,"node_id":"I_kwDOAEVQ_M5ChoLb","number":156993,"title":"Add ability to specify u2f/yubico cue prompt","user":{"login":"mainrs","id":5113257,"node_id":"MDQ6VXNlcjUxMTMyNTc=","avatar_url":"https://avatars.githubusercontent.com/u/5113257?v=4","gravatar_id":"","url":"https://api.github.com/users/mainrs","html_url":"https://github.com/mainrs","followers_url":"https://api.github.com/users/mainrs/followers","following_url":"https://api.github.com/users/mainrs/following{/other_user}","gists_url":"https://api.github.com/users/mainrs/gists{/gist_id}","starred_url":"https://api.github.com/users/mainrs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mainrs/subscriptions","organizations_url":"https://api.github.com/users/mainrs/orgs","repos_url":"https://api.github.com/users/mainrs/repos","events_url":"https://api.github.com/users/mainrs/events{/privacy}","received_events_url":"https://api.github.com/users/mainrs/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-27T11:44:54Z","updated_at":"2022-01-27T16:12:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nCurrently, nixos contains modules for both u2f and yubico. u2f allows to specify that a prompt should be displayed using `cue`. `yubico` has no such option. \r\nNeither of them allows to set the prompt. It would be great if someone could add the ability to define a custom prompt as per https://man.archlinux.org/man/pam_u2f.8#OPTIONS\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156993/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156956","id":1115854724,"node_id":"I_kwDOAEVQ_M5CgpeE","number":156956,"title":"nginx: recommended-proxy-headers.conf is included both globally and when using proxy_pass","user":{"login":"bbigras","id":24027,"node_id":"MDQ6VXNlcjI0MDI3","avatar_url":"https://avatars.githubusercontent.com/u/24027?v=4","gravatar_id":"","url":"https://api.github.com/users/bbigras","html_url":"https://github.com/bbigras","followers_url":"https://api.github.com/users/bbigras/followers","following_url":"https://api.github.com/users/bbigras/following{/other_user}","gists_url":"https://api.github.com/users/bbigras/gists{/gist_id}","starred_url":"https://api.github.com/users/bbigras/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bbigras/subscriptions","organizations_url":"https://api.github.com/users/bbigras/orgs","repos_url":"https://api.github.com/users/bbigras/repos","events_url":"https://api.github.com/users/bbigras/events{/privacy}","received_events_url":"https://api.github.com/users/bbigras/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-27T07:12:16Z","updated_at":"2022-01-27T07:12:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using `recommendedProxySettings`, `recommended-proxy-headers.conf` in included in the \"global\" http block and in every location if `proxy_pass` is used.\r\n\r\nIsn't the location `include` redundant?\r\n\r\nAlso, since it's included in the `http` I cannot figure out how to override one header. I want to override `X-Forwarded-Proto`. I should be able to add a \"manual\" location using `extraConfig` but since the same header is set in the `http` block, it's only appended and causing problems. I would have to disable `recommendedProxySettings`, which I don't want to do.\r\n\r\n### Steps To Reproduce\r\n\r\n### Expected behavior\r\n\r\n### Screenshots\r\n\r\n### Additional context\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@fpletz \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.83, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre346004.5aaed40d22f, nixos-unstable-22.05pre346004.5aaed40d22f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156956/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156950","id":1115775433,"node_id":"I_kwDOAEVQ_M5CgWHJ","number":156950,"title":"Strange behaviour with GTK_USE_PORTAL=1, affects firefox, evince and gnome-desktop","user":{"login":"astrojhgu","id":2651231,"node_id":"MDQ6VXNlcjI2NTEyMzE=","avatar_url":"https://avatars.githubusercontent.com/u/2651231?v=4","gravatar_id":"","url":"https://api.github.com/users/astrojhgu","html_url":"https://github.com/astrojhgu","followers_url":"https://api.github.com/users/astrojhgu/followers","following_url":"https://api.github.com/users/astrojhgu/following{/other_user}","gists_url":"https://api.github.com/users/astrojhgu/gists{/gist_id}","starred_url":"https://api.github.com/users/astrojhgu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/astrojhgu/subscriptions","organizations_url":"https://api.github.com/users/astrojhgu/orgs","repos_url":"https://api.github.com/users/astrojhgu/repos","events_url":"https://api.github.com/users/astrojhgu/events{/privacy}","received_events_url":"https://api.github.com/users/astrojhgu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-27T04:58:41Z","updated_at":"2022-03-30T08:32:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\nWhen `xdg.portal.gtkUsePortal=true` is set, following abnormal behaviors happen:\r\n1. gnome desktop login time period becomes much longer (~30s on my x1 yoga)\r\n2. In gnome environment, Firefox failed to launch a file chooser when I press ctrl+O and complains\r\n```\r\nno such interface “org.freedesktop.portal.filechooser” on object at path /org/freedesktop/portal/desktop\r\n```\r\n3. Similar behavior happens in `evince` (still in gnome environment).\r\n\r\nAs to the `plasma` desktop, all are OK.\r\nFor gnome (wayland), it still takes a long period of time (~30s) between I enter the password and the gnome desktop is fully ready, but the filechooser can launch normally after that.\r\n\r\nIf I remove the `gtkUsePortal` setting, everything becomes OK.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. in `configuration.nix`, add `xdg.portal.gtkUsePortal=true;`\r\n2. `sudo nixos-rebuild boot`\r\n3. reboot\r\n4. login to gnome-xorg.\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n1. gnome desktop should be launch in a short period time (say 5~10 s)\r\n2. the file chooser should be launched normally.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre348581.c07b471b52b\"`\r\n - channels(astrojhgu): `\"android, nixos-21.11pre329341.9e70e9f732f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156950/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156930","id":1115644596,"node_id":"I_kwDOAEVQ_M5Cf2K0","number":156930,"title":"Improve logging when running fetchUrl","user":{"login":"busti","id":3575167,"node_id":"MDQ6VXNlcjM1NzUxNjc=","avatar_url":"https://avatars.githubusercontent.com/u/3575167?v=4","gravatar_id":"","url":"https://api.github.com/users/busti","html_url":"https://github.com/busti","followers_url":"https://api.github.com/users/busti/followers","following_url":"https://api.github.com/users/busti/following{/other_user}","gists_url":"https://api.github.com/users/busti/gists{/gist_id}","starred_url":"https://api.github.com/users/busti/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/busti/subscriptions","organizations_url":"https://api.github.com/users/busti/orgs","repos_url":"https://api.github.com/users/busti/repos","events_url":"https://api.github.com/users/busti/events{/privacy}","received_events_url":"https://api.github.com/users/busti/received_events","type":"User","site_admin":false},"labels":[{"id":786406134,"node_id":"MDU6TGFiZWw3ODY0MDYxMzQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20fetch","name":"6.topic: fetch","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-27T00:44:03Z","updated_at":"2022-01-27T07:01:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Is your feature request related to a problem? Please describe.**\r\nI'm always frustrated when ... rebuilding my system causes a download of a large file from an external source. \r\nThe main candidate for me is usually any JetBrains IDE because I add some custom packages to their paths. This usually results in the following terminal output: \r\n\r\n\r\nAs the time of writing this, I have been staring at this exact line for about 30 minutes without any indication of progress. \r\nI do not know if it failed, it might just be really slow. The problem is that I do not know how slow, if I knew I would probably get up to prepare some food, but it might finish every second, so I don't. \r\n\r\n**Describe the solution you'd like**\r\nThis looks very similar to the output of curl. \r\nWhen running in interactive mode, update the lowest line of this log to show progress. The current download bandwidth, remaining time, data already downloaded and whatnot updated every second or so would be really helpful. \r\nBut heck, I'd be happy with any indication of progress at all. Even a dot added to the last line every minute or even a single line every five minutes.\r\n\r\n**Describe alternatives you've considered**\r\nRunning curl manually and then adding the file to the store manually works, but it's equally frustrating. \r\n\r\n---\r\n\r\nThis issue was previously tracked in https://github.com/NixOS/nix/issues/5968\r\nI ported it here on suggestion by @thufschmitt \r\n> There’s actually several different fetchurls, but the one you’re referring to seems to be nixpkgs.fetchurl, which is a nixpkgs function. So maybe re-open this in the nixpkgs issue tracker","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156930/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156897","id":1115423321,"node_id":"I_kwDOAEVQ_M5CfAJZ","number":156897,"title":"ZFS boot support is broken for Virtio drives with unassigned serial numbers","user":{"login":"pshirshov","id":295225,"node_id":"MDQ6VXNlcjI5NTIyNQ==","avatar_url":"https://avatars.githubusercontent.com/u/295225?v=4","gravatar_id":"","url":"https://api.github.com/users/pshirshov","html_url":"https://github.com/pshirshov","followers_url":"https://api.github.com/users/pshirshov/followers","following_url":"https://api.github.com/users/pshirshov/following{/other_user}","gists_url":"https://api.github.com/users/pshirshov/gists{/gist_id}","starred_url":"https://api.github.com/users/pshirshov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pshirshov/subscriptions","organizations_url":"https://api.github.com/users/pshirshov/orgs","repos_url":"https://api.github.com/users/pshirshov/repos","events_url":"https://api.github.com/users/pshirshov/events{/privacy}","received_events_url":"https://api.github.com/users/pshirshov/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T19:50:55Z","updated_at":"2022-01-27T07:00:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Virtio drives w/o serial numbers aren't visible in `/dev/disk/by-id` but ZFS boot logic attempts to import zpools from `/dev/disk/by-id` only.\r\n\r\nPossibly other paths (e.g. `/dev/disk/by-path`) should be tried too.\r\n\r\nAn easy way to reproduce that would be to create a libvirt machine with one Virtio drive and unassigned serial number, install NixOS with ZFS support and try to boot.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156897/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156890","id":1115362890,"node_id":"I_kwDOAEVQ_M5CexZK","number":156890,"title":"wasm-pack attempts to build or download and run executables.","user":{"login":"kevincox","id":494012,"node_id":"MDQ6VXNlcjQ5NDAxMg==","avatar_url":"https://avatars.githubusercontent.com/u/494012?v=4","gravatar_id":"","url":"https://api.github.com/users/kevincox","html_url":"https://github.com/kevincox","followers_url":"https://api.github.com/users/kevincox/followers","following_url":"https://api.github.com/users/kevincox/following{/other_user}","gists_url":"https://api.github.com/users/kevincox/gists{/gist_id}","starred_url":"https://api.github.com/users/kevincox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kevincox/subscriptions","organizations_url":"https://api.github.com/users/kevincox/orgs","repos_url":"https://api.github.com/users/kevincox/repos","events_url":"https://api.github.com/users/kevincox/events{/privacy}","received_events_url":"https://api.github.com/users/kevincox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-26T18:43:21Z","updated_at":"2022-04-08T15:21:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nRunning wasm-pack attempts to do the following if the executables are not found on the path:\r\n\r\n- Download binaryen (for wasm-opt).\r\n- Build wasm-bindgen-cli.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Make an environment with the following packages available:\r\n - cacert\r\n - rustc\r\n - wasm-pack\r\n2. Run `wasm-pack build --target=web --release`\r\n\r\n### Expected behavior\r\nAll needed excutables should be included in wasm-pack's closure and be used locally.\r\n\r\n### Screenshots\r\n\r\n```\r\nError: failed to download from https://github.com/WebAssembly/binaryen/releases/download/version_90/binaryen-version_90-x86-linux.tar.gz\r\nTo disable `wasm-opt`, add `wasm-opt = false` to your package metadata in your `Cargo.toml`.\r\n```\r\n\r\n<pre><font color=\"#26A269\"><b> Compiling</b></font> wasm-bindgen-cli v0.2.78\r\n<font color=\"#26A269\"><b> Finished</b></font> release [optimized] target(s) in 1m 16s\r\n<font color=\"#26A269\"><b> Installing</b></font> /tmp/nix-build-ricochetrobots-wasm.drv-0/ricochetrobots/home/.cache/.wasm-pack/.wasm-bindgen-cargo-install-0.2.78/bin/wasm-bindgen\r\n<font color=\"#26A269\"><b> Installing</b></font> /tmp/nix-build-ricochetrobots-wasm.drv-0/ricochetrobots/home/.cache/.wasm-pack/.wasm-bindgen-cargo-install-0.2.78/bin/wasm-bindgen-test-runner\r\n<font color=\"#26A269\"><b> Installing</b></font> /tmp/nix-build-ricochetrobots-wasm.drv-0/ricochetrobots/home/.cache/.wasm-pack/.wasm-bindgen-cargo-install-0.2.78/bin/wasm2es6js\r\n<font color=\"#26A269\"><b> Installed</b></font> package `wasm-bindgen-cli v0.2.78` (executables `wasm-bindgen`, `wasm-bindgen-test-runner`, `wasm2es6js`)\r\n</pre>\r\n\r\n### Notify maintainers\r\n@dhl\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(kevincox): `\"\"`\r\n - channels(root): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156890/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156884","id":1115296461,"node_id":"I_kwDOAEVQ_M5CehLN","number":156884,"title":"Package pcmemtest","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-01-26T17:34:50Z","updated_at":"2022-04-07T10:57:45Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\nGPL2 licensed memory tester for x86 and x86-64 computers (rewrite of memtest86+) with support for both legacy boot and EFI.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/martinwhitaker/pcmemtest\r\n* source URL: https://github.com/martinwhitaker/pcmemtest\r\n* license: gpl2Only\r\n* platforms: all?\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156884/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156876","id":1115219410,"node_id":"I_kwDOAEVQ_M5CeOXS","number":156876,"title":"Ropper should be a python package, not python application","user":{"login":"kciredor","id":1121650,"node_id":"MDQ6VXNlcjExMjE2NTA=","avatar_url":"https://avatars.githubusercontent.com/u/1121650?v=4","gravatar_id":"","url":"https://api.github.com/users/kciredor","html_url":"https://github.com/kciredor","followers_url":"https://api.github.com/users/kciredor/followers","following_url":"https://api.github.com/users/kciredor/following{/other_user}","gists_url":"https://api.github.com/users/kciredor/gists{/gist_id}","starred_url":"https://api.github.com/users/kciredor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kciredor/subscriptions","organizations_url":"https://api.github.com/users/kciredor/orgs","repos_url":"https://api.github.com/users/kciredor/repos","events_url":"https://api.github.com/users/kciredor/events{/privacy}","received_events_url":"https://api.github.com/users/kciredor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T16:29:58Z","updated_at":"2022-01-26T17:45:11Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nRopper can be used as a CLI tool, but also as a python module. For example gef, a gdb extension does this.\r\n\r\nThe [ropper](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/python-modules/ropper/default.nix) derivation is buildPythonApplication based which makes this problematic. A good example is [goobook](https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/python-modules/goobook/default.nix) which uses buildPythonModule. For goobook, both `import goobook` from python _and_ `$ goobook` from your shell works.\r\n\r\nI have not invented this principle, it's documented here :-) https://github.com/NixOS/nixpkgs/blob/master/doc/languages-frameworks/python.section.md#topythonapplication-function-topythonapplication-function\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\nPartial of my configuration.nix:\r\n```\r\nenvironment.systemPackages = with pkgs; [\r\n (python39.withPackages(ps: with ps; [\r\n pip\r\n\r\n ropper\r\n ]))\r\n];\r\n```\r\n\r\n### Expected behavior\r\nI can `import ropper` from a python console _and_ I can run ropper from the cli because it ends up in my PATH.\r\n\r\n### Additional context\r\n(FYI, additionally, if you install it like I do using the withPackages clause, the current derivation does not add ropper to your PATH. You have to install it as a separate package like python39Packages.ropper.)\r\n\r\n### Notify maintainers\r\n@bennofs\r\n@FRidh\r\n@r-ryantm\r\n@artemist\r\n@marsam\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.0, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.335391.77aa71f66fd, nixos-hardware, nixos-unstable-22.05pre347261.6d8215281b2, nur\"`\r\n - channels(kciredor): `\"home-manager-21.11, nixos-hardware, nixos-unstable-22.05pre343944.ff377a78794, nur\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156876/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156841","id":1114929064,"node_id":"I_kwDOAEVQ_M5CdHeo","number":156841,"title":"unityhub 2.4.4","user":{"login":"Panlabek","id":58026517,"node_id":"MDQ6VXNlcjU4MDI2NTE3","avatar_url":"https://avatars.githubusercontent.com/u/58026517?v=4","gravatar_id":"","url":"https://api.github.com/users/Panlabek","html_url":"https://github.com/Panlabek","followers_url":"https://api.github.com/users/Panlabek/followers","following_url":"https://api.github.com/users/Panlabek/following{/other_user}","gists_url":"https://api.github.com/users/Panlabek/gists{/gist_id}","starred_url":"https://api.github.com/users/Panlabek/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Panlabek/subscriptions","organizations_url":"https://api.github.com/users/Panlabek/orgs","repos_url":"https://api.github.com/users/Panlabek/repos","events_url":"https://api.github.com/users/Panlabek/events{/privacy}","received_events_url":"https://api.github.com/users/Panlabek/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T11:46:10Z","updated_at":"2022-01-27T08:27:41Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n- [ X] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n\r\n- [ X] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: unityhub\r\n\r\ncurrent version: 2.3.2\r\ndesired version: 2.4.4\r\n\r\n###### Notify maintainers\r\n\r\nmaintainers: @tesq0\r\n\r\n###### Note for maintainers\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156841/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156829","id":1114860047,"node_id":"I_kwDOAEVQ_M5Cc2oP","number":156829,"title":"`swapDevices` doesn't create a proper swapfile on btrfs","user":{"login":"1sixth","id":67363572,"node_id":"MDQ6VXNlcjY3MzYzNTcy","avatar_url":"https://avatars.githubusercontent.com/u/67363572?v=4","gravatar_id":"","url":"https://api.github.com/users/1sixth","html_url":"https://github.com/1sixth","followers_url":"https://api.github.com/users/1sixth/followers","following_url":"https://api.github.com/users/1sixth/following{/other_user}","gists_url":"https://api.github.com/users/1sixth/gists{/gist_id}","starred_url":"https://api.github.com/users/1sixth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/1sixth/subscriptions","organizations_url":"https://api.github.com/users/1sixth/orgs","repos_url":"https://api.github.com/users/1sixth/repos","events_url":"https://api.github.com/users/1sixth/events{/privacy}","received_events_url":"https://api.github.com/users/1sixth/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-26T10:27:13Z","updated_at":"2022-02-10T01:50:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen using `swapDevices` to create and activate a swapfile on btrfs, it fails with messages like this:\r\n\r\n```\r\nA dependency job for swap.target failed. See 'journalctl -xe' for details.\r\nwarning: the following units failed: swapfile.swap\r\n\r\n× swapfile.swap - /swapfile\r\n Loaded: loaded (/etc/fstab; generated)\r\n Active: failed (Result: exit-code) since Wed 2022-01-26 18:15:02 CST; 23ms ago\r\n What: /swapfile\r\n Docs: man:fstab(5)\r\n man:systemd-fstab-generator(8)\r\n IP: 0B in, 0B out\r\n CPU: 2ms\r\n\r\nJan 26 18:15:02 toy systemd[1]: Activating swap /swapfile...\r\nJan 26 18:15:02 toy swapon[125673]: swapon: /swapfile: swapon failed: Invalid argument\r\nJan 26 18:15:02 toy systemd[1]: swapfile.swap: Swap process exited, code=exited, status=255/EXCEPTION\r\nJan 26 18:15:02 toy systemd[1]: swapfile.swap: Failed with result 'exit-code'.\r\nJan 26 18:15:02 toy systemd[1]: Failed to activate swap /swapfile.\r\nwarning: error(s) occurred while switching to the new configuration\r\n```\r\n\r\nThe kernel says:\r\n\r\n```\r\nJan 26 18:15:02 toy kernel: BTRFS warning (device nvme0n1p2): swapfile must not be copy-on-write\r\n```\r\n\r\nI am not very familiar with Nix, but after reading the corresponding [swap.nix](https://github.com/NixOS/nixpkgs/blob/17c61e97723ef2b10b60fd497b0e4eebe3b8655c/nixos/modules/config/swap.nix) and [btrfs manual](https://btrfs.readthedocs.io/en/latest/Swapfile.html), it seems that creating a swapfile on btrfs requires disabling copy-on-write for that file (via `chattr +C swapfile`) as well. However, `swap.nix` doesn't do it currently.\r\n\r\nBTW, manually creating the swapfile and letting NixOS activating it works fine for me.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Add `swapDevices = [{ device = \"/swapfile\"; size = 1024; }];` to `hardware-configuration.nix` (`/` is supposed to be mounted as btrfs).\r\n2. Run `sudo nixos-rebuild switch`.\r\n\r\n### Expected behavior\r\n\r\nSwapfile is created and activated without any issue.\r\n\r\n### Additional context\r\n\r\nThere is a workaround on NixOS Discourse: <https://discourse.nixos.org/t/how-do-i-set-up-a-swap-file/8323/7>.\r\n\r\n### Notify maintainers\r\n\r\n@Artturin\r\n\r\n### Metadata\r\n\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.15.11-zen1, NixOS, 22.05 (Quokka)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.5.1`\r\n- channels(root): `\"nixos-22.05pre348581.c07b471b52b, home-manager\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156829/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156814","id":1114627860,"node_id":"I_kwDOAEVQ_M5Cb98U","number":156814,"title":"`code-server` partially broken following 4.x upgrade","user":{"login":"austinbutler","id":354741,"node_id":"MDQ6VXNlcjM1NDc0MQ==","avatar_url":"https://avatars.githubusercontent.com/u/354741?v=4","gravatar_id":"","url":"https://api.github.com/users/austinbutler","html_url":"https://github.com/austinbutler","followers_url":"https://api.github.com/users/austinbutler/followers","following_url":"https://api.github.com/users/austinbutler/following{/other_user}","gists_url":"https://api.github.com/users/austinbutler/gists{/gist_id}","starred_url":"https://api.github.com/users/austinbutler/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/austinbutler/subscriptions","organizations_url":"https://api.github.com/users/austinbutler/orgs","repos_url":"https://api.github.com/users/austinbutler/repos","events_url":"https://api.github.com/users/austinbutler/events{/privacy}","received_events_url":"https://api.github.com/users/austinbutler/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T04:55:06Z","updated_at":"2022-01-26T08:48:30Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nPreviously I had a fully working setup of `code-server` 3.x. After upgrading to 4.x, it still works-ish, but many things involving extensions don't work.\r\n\r\n### Steps To Reproduce\r\n\r\n1. Add this to your `configuration.nix`:\r\n```nix\r\n{\r\n services.code-server = {\r\n auth = \"none\";\r\n enable = true;\r\n port = 8081;\r\n user = \"my_user\";\r\n };\r\n}\r\n```\r\n2. Open `http://localhost:8081`\r\n3. Open a markdown file\r\n4. CTRL+SHIFT+P, `Markdown: Open Preview`\r\n5. Observe that \"Activating Extensions\" shows up for a few second in the status bar, then disappears and nothing happens\r\n\r\nAlso affects `TypeScript: Select TypeScript Version`.\r\n\r\n### Expected behavior\r\n\r\nMarkdown preview should open or TypeScript version select dialog should pop up.\r\n\r\n### Additional context\r\n\r\nI notice in when loading in the browser, I get a 404 on `http://127.0.0.1:8081/static/stable/out/vs/workbench/services/extensions/worker/httpWebWorkerExtensionHostIframe.html?&vscodeWebWorkerExtHostId=621a0e7a-8957-44e7-a901-bdb25f146a47`. If I remove `stable/` from the URL it loads some HTML.\r\n\r\nThe console has this error: `webWorkerExtensionHost.ts:184 The Web Worker Extension Host did not start in 60s, that might be a problem.`.\r\n\r\nThe same basic setup works [in Docker](https://coder.com/docs/code-server/latest/install#docker), so it doesn't seem to be a bug with `code-server`.\r\n\r\n### Notify maintainers\r\n\r\n@dguenther @offlinehacker \r\n\r\n### Metadata\r\n\r\n```yaml\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.93, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"home-manager, nixos-22.05pre348581.c07b471b52b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156814/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156807","id":1114602488,"node_id":"I_kwDOAEVQ_M5Cb3v4","number":156807,"title":"python27Packages.scandir: test failures on aarch64-darwin","user":{"login":"abathur","id":2548365,"node_id":"MDQ6VXNlcjI1NDgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/2548365?v=4","gravatar_id":"","url":"https://api.github.com/users/abathur","html_url":"https://github.com/abathur","followers_url":"https://api.github.com/users/abathur/followers","following_url":"https://api.github.com/users/abathur/following{/other_user}","gists_url":"https://api.github.com/users/abathur/gists{/gist_id}","starred_url":"https://api.github.com/users/abathur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/abathur/subscriptions","organizations_url":"https://api.github.com/users/abathur/orgs","repos_url":"https://api.github.com/users/abathur/repos","events_url":"https://api.github.com/users/abathur/events{/privacy}","received_events_url":"https://api.github.com/users/abathur/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T04:00:49Z","updated_at":"2022-01-26T04:00:49Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I noticed ofborg was [failing](https://logs.nix.ci/?key=nixos/nixpkgs.155251&attempt_id=c5bd7269-fc6f-42a4-8a57-636461c14f3a) to build resholve (which has no short-run path off of python27) on aarch64-darwin due to test failures in scandir. \r\n\r\nI don't expect there to be much enthusiasm for the exact failure here, but I'm reporting it in case the root cause is meaningful...\r\n\r\n### Describe the bug\r\n<details>\r\n<summary>On aarch64-darwin, 1 scandir test errors and 5 fail as follows:</summary>\r\n\r\n```console\r\nSourcing python-remove-tests-dir-hook\r\nSourcing python-catch-conflicts-hook.sh\r\nSourcing python-remove-bin-bytecode-hook.sh\r\nSourcing setuptools-build-hook\r\nUsing setuptoolsBuildPhase\r\nUsing setuptoolsShellHook\r\nSourcing pip-install-hook\r\nUsing pipInstallPhase\r\nSourcing python-imports-check-hook.sh\r\nUsing pythonImportsCheckPhase\r\nSourcing setuptools-check-hook\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/s0l2vkcm04z0r64ia0xh6cn91ly8xiwr-scandir-1.10.0.tar.gz\r\nsource root is scandir-1.10.0\r\nsetting SOURCE_DATE_EPOCH to timestamp 1552154153 of file scandir-1.10.0/setup.cfg\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\n@nix { \"action\": \"setPhase\", \"phase\": \"updateAutotoolsGnuConfigScriptsPhase\" }\r\nupdateAutotoolsGnuConfigScriptsPhase\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\nno configure script, doing nothing\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nExecuting setuptoolsBuildPhase\r\n/nix/store/7nv2sjvzxccfvrca2a9i0axxhm9y3zxp-python-2.7.18/lib/python2.7/distutils/extension.py:133: UserWarning: Unknown Extension options: 'optional'\r\n warnings.warn(msg)\r\nrunning bdist_wheel\r\nrunning build\r\nrunning build_py\r\ncreating build\r\ncreating build/lib.macosx-11.0-arm64-2.7\r\ncopying scandir.py -> build/lib.macosx-11.0-arm64-2.7\r\nrunning build_ext\r\nbuilding '_scandir' extension\r\ncreating build/temp.macosx-11.0-arm64-2.7\r\nclang -I/nix/store/7nv2sjvzxccfvrca2a9i0axxhm9y3zxp-python-2.7.18/include/python2.7 -c _scandir.c -o build/temp.macosx-11.0-arm64-2.7/_scandir.o\r\nclang -bundle -undefined dynamic_lookup build/temp.macosx-11.0-arm64-2.7/_scandir.o -L/nix/store/7nv2sjvzxccfvrca2a9i0axxhm9y3zxp-python-2.7.18/lib -o build/lib.macosx-11.0-arm64-2.7/_scandir.so\r\ninstalling to build/bdist.macosx-11.0-arm64/wheel\r\nrunning install\r\nrunning install_lib\r\ncreating build/bdist.macosx-11.0-arm64\r\ncreating build/bdist.macosx-11.0-arm64/wheel\r\ncopying build/lib.macosx-11.0-arm64-2.7/_scandir.so -> build/bdist.macosx-11.0-arm64/wheel\r\ncopying build/lib.macosx-11.0-arm64-2.7/scandir.py -> build/bdist.macosx-11.0-arm64/wheel\r\nrunning install_egg_info\r\nrunning egg_info\r\nwriting scandir.egg-info/PKG-INFO\r\nwriting top-level names to scandir.egg-info/top_level.txt\r\nwriting dependency_links to scandir.egg-info/dependency_links.txt\r\nreading manifest file 'scandir.egg-info/SOURCES.txt'\r\nreading manifest template 'MANIFEST.in'\r\nwriting manifest file 'scandir.egg-info/SOURCES.txt'\r\nCopying scandir.egg-info to build/bdist.macosx-11.0-arm64/wheel/scandir-1.10.0-py2.7.egg-info\r\nrunning install_scripts\r\nadding license file \"LICENSE.txt\" (matched pattern \"LICEN[CS]E*\")\r\ncreating build/bdist.macosx-11.0-arm64/wheel/scandir-1.10.0.dist-info/WHEEL\r\ncreating 'dist/scandir-1.10.0-cp27-cp27mu-macosx_11_0_arm64.whl' and adding 'build/bdist.macosx-11.0-arm64/wheel' to it\r\nadding '_scandir.so'\r\nadding 'scandir.py'\r\nadding 'scandir-1.10.0.dist-info/LICENSE.txt'\r\nadding 'scandir-1.10.0.dist-info/METADATA'\r\nadding 'scandir-1.10.0.dist-info/WHEEL'\r\nadding 'scandir-1.10.0.dist-info/top_level.txt'\r\nadding 'scandir-1.10.0.dist-info/RECORD'\r\nremoving build/bdist.macosx-11.0-arm64/wheel\r\nFinished executing setuptoolsBuildPhase\r\n@nix { \"action\": \"setPhase\", \"phase\": \"installPhase\" }\r\ninstalling\r\nExecuting pipInstallPhase\r\n/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/dist /private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0\r\n\u001b[33mDEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality.\u001b[0m\r\nProcessing ./scandir-1.10.0-cp27-cp27mu-macosx_11_0_arm64.whl\r\nInstalling collected packages: scandir\r\nSuccessfully installed scandir-1.10.0\r\n/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0\r\nFinished executing pipInstallPhase\r\n@nix { \"action\": \"setPhase\", \"phase\": \"fixupPhase\" }\r\npost-installation fixup\r\nstrip is /nix/store/ljxsc2chsz0qr6318mpnwhc3cagcfck7-clang-wrapper-11.1.0/bin/strip\r\nstripping (with command strip and flags -S) in /nix/store/p5dfng0h9gaji94fvhlpbr2bnfv92kgq-python2.7-scandir-1.10.0/lib \r\npatching script interpreter paths in /nix/store/p5dfng0h9gaji94fvhlpbr2bnfv92kgq-python2.7-scandir-1.10.0\r\nExecuting pythonRemoveTestsDir\r\nFinished executing pythonRemoveTestsDir\r\n@nix { \"action\": \"setPhase\", \"phase\": \"installCheckPhase\" }\r\nrunning install tests\r\ntest_basic (test_scandir.TestScandirC) ... ok\r\ntest_bytes (test_scandir.TestScandirC) ... ok\r\ntest_dir_entry (test_scandir.TestScandirC) ... ok\r\ntest_file_attributes (test_scandir.TestScandirC) ... skipped 'st_file_attributes not supported'\r\ntest_path (test_scandir.TestScandirC) ... ok\r\ntest_returns_iter (test_scandir.TestScandirC) ... ok\r\ntest_stat (test_scandir.TestScandirC) ... ok\r\ntest_symlink (test_scandir.TestScandirC) ... ok\r\ntest_unicode (test_scandir.TestScandirC) ... ok\r\ntest_walk_unicode_handling (test_scandir.TestScandirC) ... ok\r\ntest_iter_returns_dir_entry (test_scandir.TestScandirDirEntry) ... ok\r\ntest_basic (test_scandir.TestScandirGeneric) ... ok\r\ntest_bytes (test_scandir.TestScandirGeneric) ... ok\r\ntest_dir_entry (test_scandir.TestScandirGeneric) ... ok\r\ntest_file_attributes (test_scandir.TestScandirGeneric) ... skipped 'st_file_attributes not supported'\r\ntest_path (test_scandir.TestScandirGeneric) ... ok\r\ntest_returns_iter (test_scandir.TestScandirGeneric) ... ok\r\ntest_stat (test_scandir.TestScandirGeneric) ... ok\r\ntest_symlink (test_scandir.TestScandirGeneric) ... ok\r\ntest_unicode (test_scandir.TestScandirGeneric) ... ok\r\ntest_walk_unicode_handling (test_scandir.TestScandirGeneric) ... ok\r\ntest_basic (test_scandir.TestScandirPython) ... FAIL\r\ntest_bytes (test_scandir.TestScandirPython) ... FAIL\r\ntest_dir_entry (test_scandir.TestScandirPython) ... ERROR\r\ntest_file_attributes (test_scandir.TestScandirPython) ... skipped 'st_file_attributes not supported'\r\ntest_path (test_scandir.TestScandirPython) ... FAIL\r\ntest_returns_iter (test_scandir.TestScandirPython) ... ok\r\ntest_stat (test_scandir.TestScandirPython) ... ok\r\ntest_symlink (test_scandir.TestScandirPython) ... FAIL\r\ntest_unicode (test_scandir.TestScandirPython) ... FAIL\r\ntest_walk_unicode_handling (test_scandir.TestScandirPython) ... ok\r\ntest_traversal (test_walk.TestWalk) ... ok\r\ntest_symlink_to_directory (test_walk.TestWalkSymlink) ... ok\r\ntest_symlink_to_file (test_walk.TestWalkSymlink) ... ok\r\n\r\n======================================================================\r\nERROR: test_dir_entry (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 113, in test_dir_entry\r\n e = entries['file1.txt']\r\nKeyError: u'file1.txt'\r\n\r\n======================================================================\r\nFAIL: test_basic (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 107, in test_basic\r\n ('linkdir', True), ('subdir', True)])\r\nAssertionError: Lists differ: [(u'', True), (u'', True), (u'... != [(u'file1.txt', False), (u'fil...\r\n\r\nFirst differing element 0:\r\n(u'', True)\r\n(u'file1.txt', False)\r\n\r\nFirst list contains 2 additional elements.\r\nFirst extra element 4:\r\n(u'', True)\r\n\r\n- [(u'', True), (u'', True), (u'', True), (u'', True), (u'', True), (u'', True)]\r\n+ [(u'file1.txt', False),\r\n+ (u'file2.txt', False),\r\n+ (u'linkdir', True),\r\n+ (u'subdir', True)]\r\n\r\n======================================================================\r\nFAIL: test_bytes (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 211, in test_bytes\r\n self.assertEqual(len(entries), 1)\r\nAssertionError: 0 != 1\r\n\r\n======================================================================\r\nFAIL: test_path (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 168, in test_path\r\n ['file1.txt', 'file2.txt', 'linkdir', 'subdir'])\r\nAssertionError: Lists differ: [u'', u'', u'', u'', u'', u''] != [u'file1.txt', u'file2.txt', u...\r\n\r\nFirst differing element 0:\r\nu''\r\nu'file1.txt'\r\n\r\nFirst list contains 2 additional elements.\r\nFirst extra element 4:\r\nu''\r\n\r\n- [u'', u'', u'', u'', u'', u'']\r\n+ [u'file1.txt', u'file2.txt', u'linkdir', u'subdir']\r\n\r\n======================================================================\r\nFAIL: test_symlink (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 183, in test_symlink\r\n ('linksubdir', False)])\r\nAssertionError: Lists differ: [(u'', False), (u'', False), (... != [(u'file1.txt', False), (u'lin...\r\n\r\nFirst differing element 0:\r\n(u'', False)\r\n(u'file1.txt', False)\r\n\r\nFirst list contains 2 additional elements.\r\nFirst extra element 4:\r\n(u'', False)\r\n\r\n- [(u'', False),\r\n+ [(u'file1.txt', False),\r\n? +++++++++\r\n\r\n+ (u'link_to_dir', True),\r\n+ (u'link_to_file', True),\r\n+ (u'linksubdir', False)]\r\n- (u'', False),\r\n- (u'', False),\r\n- (u'', False),\r\n- (u'', False),\r\n- (u'', False)]\r\n\r\n======================================================================\r\nFAIL: test_unicode (test_scandir.TestScandirPython)\r\n----------------------------------------------------------------------\r\nTraceback (most recent call last):\r\n File \"/private/tmp/nix-build-python2.7-scandir-1.10.0.drv-0/scandir-1.10.0/test/test_scandir.py\", line 229, in test_unicode\r\n self.assertEqual(len(entries), 1)\r\nAssertionError: 0 != 1\r\n\r\n----------------------------------------------------------------------\r\nRan 34 tests in 0.012s\r\n\r\nFAILED (failures=5, errors=1, skipped=3)\r\n```\r\n</details>\r\n\r\n### Additional context\r\nI don't see any similar issues upstream. I haven't yet filed anything there (but I do have a tab open to do so, if it sounds like this is intrinsic).\r\n\r\n### Notify maintainers\r\n\r\n@abbradar Just in case you've seen anything like this?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156807/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156806","id":1114601808,"node_id":"I_kwDOAEVQ_M5Cb3lQ","number":156806,"title":"neovim derivation failing on Darwin after libstdc++ dependency is added","user":{"login":"nasadorian","id":1136563,"node_id":"MDQ6VXNlcjExMzY1NjM=","avatar_url":"https://avatars.githubusercontent.com/u/1136563?v=4","gravatar_id":"","url":"https://api.github.com/users/nasadorian","html_url":"https://github.com/nasadorian","followers_url":"https://api.github.com/users/nasadorian/followers","following_url":"https://api.github.com/users/nasadorian/following{/other_user}","gists_url":"https://api.github.com/users/nasadorian/gists{/gist_id}","starred_url":"https://api.github.com/users/nasadorian/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nasadorian/subscriptions","organizations_url":"https://api.github.com/users/nasadorian/orgs","repos_url":"https://api.github.com/users/nasadorian/repos","events_url":"https://api.github.com/users/nasadorian/events{/privacy}","received_events_url":"https://api.github.com/users/nasadorian/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-26T03:59:03Z","updated_at":"2022-03-30T23:46:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nSince https://github.com/NixOS/nixpkgs/commit/abe84c21a9a45845f68eb02dcc5937ca34224dec was committed to nixpkgs-unstable, neovim is breaking upon installation.\r\n\r\n\r\nSpecifically it seems that `libstdc++` is not available, and `clang` cannot run when building neovim from source.\r\n\r\n```\r\nCMake Error at /nix/store/03rqlijjbrf595jjdz5b74a9cc1jswpr-cmake-3.22.1/share/cmake-3.22/Modules/CMakeTestCCompiler.cmake:69 (message):\r\n The C compiler\r\n\r\n \"/nix/store/fanf50m95p6848rbiyfvj008czh1iibp-clang-wrapper-11.1.0/bin/clang\"\r\n\r\n is not able to compile a simple test program.\r\n\r\n It fails with the following output:\r\n\r\n Change Dir: /tmp/nix-build-neovim-unwrapped-0.6.1.drv-0/source/build/CMakeFiles/CMakeTmp\r\n\r\n Run Build Command(s):/nix/store/askn5hm06xf8b8lmyb5r5v362lv040pk-gnumake-4.3/bin/make -f Makefile cmTC_1b8fc/fast && /nix/store/askn5hm06xf8b8lmyb5r5v362lv040pk-gnumake-4.3/bin/make -f CMakeFiles/cmTC_1b8fc.dir/build.make CMakeFiles/cmTC_1b8fc.dir/build\r\n make[1]: Entering directory '/private/tmp/nix-build-neovim-unwrapped-0.6.1.drv-0/source/build/CMakeFiles/CMakeTmp'\r\n Building C object CMakeFiles/cmTC_1b8fc.dir/testCCompiler.c.o\r\n /nix/store/fanf50m95p6848rbiyfvj008czh1iibp-clang-wrapper-11.1.0/bin/clang -MD -MT CMakeFiles/cmTC_1b8fc.dir/testCCompiler.c.o -MF CMakeFiles/cmTC_1b8fc.dir/testCCompiler.c.o.d -o CMakeFiles/cmTC_1b8fc.dir/testCCompiler.c.o -c /tmp/nix-build-neovim-unwrapped-0.6.1.drv-0/source/build/CMakeFiles/CMakeTmp/testCCompiler.c\r\n Linking C executable cmTC_1b8fc\r\n /nix/store/03rqlijjbrf595jjdz5b74a9cc1jswpr-cmake-3.22.1/bin/cmake -E cmake_link_script CMakeFiles/cmTC_1b8fc.dir/link.txt --verbose=1\r\n /nix/store/fanf50m95p6848rbiyfvj008czh1iibp-clang-wrapper-11.1.0/bin/clang -Wl,-search_paths_first -Wl,-headerpad_max_install_names CMakeFiles/cmTC_1b8fc.dir/testCCompiler.c.o -o cmTC_1b8fc\r\n ld: library not found for -lstdc++\r\n clang-11: error: linker command failed with exit code 1 (use -v to see invocation)\r\n make[1]: *** [CMakeFiles/cmTC_1b8fc.dir/build.make:100: cmTC_1b8fc] Error 1\r\n make[1]: Leaving directory '/private/tmp/nix-build-neovim-unwrapped-0.6.1.drv-0/source/build/CMakeFiles/CMakeTmp'\r\n make: *** [Makefile:127: cmTC_1b8fc/fast] Error 2\r\n\r\n CMake will not be able to correctly generate this project.\r\nCall Stack (most recent call first):\r\n CMakeLists.txt:7 (project)\r\n\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install neovim from unstable on Darwin\r\n\r\n### Expected behavior\r\nneovim should install normally without error\r\n\r\n### Notify maintainers\r\n@thornycrackers \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.10`\r\n - channels(nasadorian): `\"nixpkgs-22.05pre348596.8bd55a6a5ab, home-manager\"`\r\n - nixpkgs: `/Users/nasadorian/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806/reactions","total_count":7,"+1":7,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156806/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156785","id":1114480871,"node_id":"I_kwDOAEVQ_M5CbaDn","number":156785,"title":"Level up the test functions","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":364502399,"node_id":"MDU6TGFiZWwzNjQ1MDIzOTk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hygiene","name":"6.topic: hygiene","color":"fef2c0","default":false,"description":null},{"id":549491066,"node_id":"MDU6TGFiZWw1NDk0OTEwNjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20developer%20experience","name":"6.topic: developer experience","color":"fef2c0","default":false,"description":null},{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-26T00:00:40Z","updated_at":"2022-01-26T00:01:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\n - [ ] move generic testing functions into a separate file. (which may import other files of course)\r\n - [ ] document them in the Nixpkgs manual\r\n\r\nSome functions, off the top of my head:\r\n\r\n - [ ] testVersion\r\n - [ ] testEqualDerivation\r\n - [ ] invalidateFetcherByDrvHash\r\n - [ ] #156613 \r\n - [ ] nixosTest\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785/reactions","total_count":2,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":1,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156785/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156753","id":1114284530,"node_id":"I_kwDOAEVQ_M5CaqHy","number":156753,"title":"setting isoImage.grubTheme to null no longer works","user":{"login":"disassembler","id":651205,"node_id":"MDQ6VXNlcjY1MTIwNQ==","avatar_url":"https://avatars.githubusercontent.com/u/651205?v=4","gravatar_id":"","url":"https://api.github.com/users/disassembler","html_url":"https://github.com/disassembler","followers_url":"https://api.github.com/users/disassembler/followers","following_url":"https://api.github.com/users/disassembler/following{/other_user}","gists_url":"https://api.github.com/users/disassembler/gists{/gist_id}","starred_url":"https://api.github.com/users/disassembler/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/disassembler/subscriptions","organizations_url":"https://api.github.com/users/disassembler/orgs","repos_url":"https://api.github.com/users/disassembler/repos","events_url":"https://api.github.com/users/disassembler/events{/privacy}","received_events_url":"https://api.github.com/users/disassembler/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-25T19:34:11Z","updated_at":"2022-01-25T19:34:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nIf you set isoImage.grubTheme to null, it fails to build an ISO.\r\n\r\n### Steps To Reproduce\r\ncreate a basic configuration.nix for an installer with isoImage.grubTheme set to null\r\n\r\n```\r\nerror: cannot coerce null to a string\r\n\r\n at /nix/store/ha4ld6wd29q1igjmhjdvkvbxpxxxxbxf-source/nixos/modules/installer/cd-dvd/iso-image.nix:255:5:\r\n\r\n 254| strictDeps = true;\r\n 255| } ''\r\n | ^\r\n 256| mkdir -p $out/EFI/boot/\r\n\r\n … while evaluating the attribute 'buildCommand' of the derivation 'efi-directory'\r\n\r\n```\r\n\r\n### Expected behavior\r\nBuilds image not using theme and embedding spashImage specifried\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156753/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156700","id":1113837914,"node_id":"I_kwDOAEVQ_M5CY9Fa","number":156700,"title":"nixos/test-driver: polling_condition should be able to wait for a condition","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-25T12:36:54Z","updated_at":"2022-01-25T12:37:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Currently, `polling_condition` is generally used as follows\r\n\r\n```py\r\n@polling_condition\r\ndef some_condition():\r\n ...\r\n # Check some_condition\r\n\r\n... # Wait until that same condition holds\r\nwith some_condition:\r\n ... # Do useful work\r\n```\r\n\r\nWould propose one of the following interfaces:\r\n\r\n```py\r\n@polling_condition\r\ndef some_condition():\r\n ...\r\n # Check some_condition\r\n\r\nsome_condition.wait()\r\nwith some_condition:\r\n ... # Do useful work\r\n```\r\n\r\n```py\r\n@polling_condition\r\ndef some_condition():\r\n ...\r\n # Check some_condition\r\n\r\nwith some_condition(wait=True):\r\n ... # Do useful work\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156700/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156681","id":1113689926,"node_id":"I_kwDOAEVQ_M5CYY9G","number":156681,"title":"opencascade-occt without rapidjson breaks FreeCAD glTF export","user":{"login":"s-ol","id":1731279,"node_id":"MDQ6VXNlcjE3MzEyNzk=","avatar_url":"https://avatars.githubusercontent.com/u/1731279?v=4","gravatar_id":"","url":"https://api.github.com/users/s-ol","html_url":"https://github.com/s-ol","followers_url":"https://api.github.com/users/s-ol/followers","following_url":"https://api.github.com/users/s-ol/following{/other_user}","gists_url":"https://api.github.com/users/s-ol/gists{/gist_id}","starred_url":"https://api.github.com/users/s-ol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/s-ol/subscriptions","organizations_url":"https://api.github.com/users/s-ol/orgs","repos_url":"https://api.github.com/users/s-ol/repos","events_url":"https://api.github.com/users/s-ol/events{/privacy}","received_events_url":"https://api.github.com/users/s-ol/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-25T10:14:45Z","updated_at":"2022-01-25T10:14:45Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nThe FreeCAD glTF export is broken because the opencascade-occt dependency is configured without rapidjson support.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open freecad\r\n2. Enable Logging in Output window (Right click -> Options -> Display Message Types -> Log messages)\r\n3. Open / Select any part(s)\r\n4. Use `File -> Export` and use the `glTF` format\r\n5. Scroll down in the log window:\r\n\r\n```\r\n11:01:44 \u001b[31;1mError: glTF writer is unavailable - OCCT has been built without RapidJSON support [HAVE_RAPIDJSON undefined]\u001b[0m\r\n11:01:44 Traceback (most recent call last):\r\n File \"<string>\", line 4, in <module>\r\n<class 'OSError'>: Cannot save to file '/home/s-ol/repos/hexpad/0xCp/0xCp.gltf'\r\n```\r\n\r\n### Expected behavior\r\nThe file should be exported.\r\n\r\n### Additional context\r\nThis issue is documented in the FreeCAD forum since 2009: https://forum.freecadweb.org/viewtopic.php?f=8&t=31680&p=450917&#p450658\r\nA note can also be found in the wiki: https://wiki.freecadweb.org/glTF\r\n\r\n### Notify maintainers\r\n@amiloradovsky @gebner \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.10, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(s-ol): `\"nixos-unstable-22.05pre347947.689b76bcf36\"`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.334587.e6377ff3554\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nfreecad was installed from `nixos-unstable`.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156681/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156664","id":1113517808,"node_id":"I_kwDOAEVQ_M5CXu7w","number":156664,"title":"Flatpak exports point towards a binary in the nix store, breaking on flatpak updates.","user":{"login":"GabTheBab","id":57549136,"node_id":"MDQ6VXNlcjU3NTQ5MTM2","avatar_url":"https://avatars.githubusercontent.com/u/57549136?v=4","gravatar_id":"","url":"https://api.github.com/users/GabTheBab","html_url":"https://github.com/GabTheBab","followers_url":"https://api.github.com/users/GabTheBab/followers","following_url":"https://api.github.com/users/GabTheBab/following{/other_user}","gists_url":"https://api.github.com/users/GabTheBab/gists{/gist_id}","starred_url":"https://api.github.com/users/GabTheBab/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/GabTheBab/subscriptions","organizations_url":"https://api.github.com/users/GabTheBab/orgs","repos_url":"https://api.github.com/users/GabTheBab/repos","events_url":"https://api.github.com/users/GabTheBab/events{/privacy}","received_events_url":"https://api.github.com/users/GabTheBab/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-25T07:21:30Z","updated_at":"2022-01-25T08:47:07Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nFlatpak exports point to the nix store path of flatpak, which will break on updates. EDIT: This seems to only happen when going through gnome-software, might happen with other flatpak frontends. Using the CLI does give correct paths in exports.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install a flatpak package via gnome-software\r\n2. Look inside its desktop file, its pointing to a binary in the store\r\n\r\n### Expected behavior\r\nThere was a fix in nixpkgs to have it directly use \"flatpak run\", which doesn't seem to work when using gnome software.\r\n\r\n### Notify maintainers\r\n@jtojnar \r\n### Metadata\r\n\r\n\r\n```console\r\n➜ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12-xanmod1-tt, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156664/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156625","id":1113197559,"node_id":"I_kwDOAEVQ_M5CWgv3","number":156625,"title":"the-powder-toy segfaults on aarch64-darwin","user":{"login":"siraben","id":8219659,"node_id":"MDQ6VXNlcjgyMTk2NTk=","avatar_url":"https://avatars.githubusercontent.com/u/8219659?v=4","gravatar_id":"","url":"https://api.github.com/users/siraben","html_url":"https://github.com/siraben","followers_url":"https://api.github.com/users/siraben/followers","following_url":"https://api.github.com/users/siraben/following{/other_user}","gists_url":"https://api.github.com/users/siraben/gists{/gist_id}","starred_url":"https://api.github.com/users/siraben/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/siraben/subscriptions","organizations_url":"https://api.github.com/users/siraben/orgs","repos_url":"https://api.github.com/users/siraben/repos","events_url":"https://api.github.com/users/siraben/events{/privacy}","received_events_url":"https://api.github.com/users/siraben/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-24T22:14:34Z","updated_at":"2022-01-24T22:14:46Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nthe-powder-toy segfaults when trying to execute it on aarch64-darwin.\r\n\r\n```ShellSession\r\n$ ./result/bin/powder\r\n[1] 90495 killed ./result/bin/powder\r\n$ echo $? \r\n137\r\n```\r\n\r\n### Steps To Reproduce\r\n```ShellSession\r\n$ NIXPKGS_ALLOW_UNSUPPORTED_SYSTEM=1 nix run --impure nixpkgs#the-powder-toy\r\n```\r\n\r\n### Expected behavior\r\nIt should run and launch the game.\r\n\r\n### Notify maintainers\r\n@abbradar @siraben @NixOS/darwin-maintainers\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixpkgs-22.05pre348320.cc68710784f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156625/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156563","id":1112924469,"node_id":"I_kwDOAEVQ_M5CVeE1","number":156563,"title":"nixos/test-driver: allow easier sharing between expression and driver script","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-24T17:15:35Z","updated_at":"2022-01-24T23:46:39Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Currently, we use a lot of string interpolation to get information from the nix expression defining the test to the script running the driver. It would be nice to have a more principled way of doing this. My thought is to have a field in the driver that is written by Nix, converted to JSON, and then read by the driver script. \r\n\r\nA minimal example of how this would work:\r\n\r\n```nix\r\nimport ./make-test-python.nix ({ ... } : {\r\n machine = { ... }: { };\r\n\r\n shared = {\r\n foo = 3;\r\n };\r\n\r\n testScript =\r\n ''\r\n assert shared.foo == 3\r\n '';\r\n})\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156563/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156555","id":1112882090,"node_id":"I_kwDOAEVQ_M5CVTuq","number":156555,"title":"nixos-test-driver: use python-tesseract rather than calling tesseract from shell","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-24T16:38:16Z","updated_at":"2022-01-24T16:38:31Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"We currently call the `tesseract` program directly and parse the results, but there is a nice python wrapper around this. This gives us a lot more features (like identifying _where_ text is rather than just _which_ text it is) for a lot less work.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156555/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156506","id":1112613964,"node_id":"I_kwDOAEVQ_M5CUSRM","number":156506,"title":"redis-desktop-manager Qt packaging isn't working","user":{"login":"Tchekda","id":23559888,"node_id":"MDQ6VXNlcjIzNTU5ODg4","avatar_url":"https://avatars.githubusercontent.com/u/23559888?v=4","gravatar_id":"","url":"https://api.github.com/users/Tchekda","html_url":"https://github.com/Tchekda","followers_url":"https://api.github.com/users/Tchekda/followers","following_url":"https://api.github.com/users/Tchekda/following{/other_user}","gists_url":"https://api.github.com/users/Tchekda/gists{/gist_id}","starred_url":"https://api.github.com/users/Tchekda/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Tchekda/subscriptions","organizations_url":"https://api.github.com/users/Tchekda/orgs","repos_url":"https://api.github.com/users/Tchekda/repos","events_url":"https://api.github.com/users/Tchekda/events{/privacy}","received_events_url":"https://api.github.com/users/Tchekda/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-24T12:57:26Z","updated_at":"2022-01-27T10:42:35Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen running the command `rdm` from the [redis-desktop-manager](https://github.com/NixOS/nixpkgs/blob/master/pkgs/applications/misc/redis-desktop-manager/default.nix) package, I am getting this error : \r\n```\r\nqt.qpa.plugin: Could not find the Qt platform plugin \"xcb\" in \"\"\r\nThis application failed to start because no Qt platform plugin could be initialized. Reinstalling the application may fix this problem.\r\n\r\nfish: Job 1, 'rdm' terminated by signal SIGSEGV (Address boundary error)\r\n```\r\n\r\n### Possible solution\r\n\r\nFix the package build process to correctly wrap the app\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install or Nix-shell `redis-desktop-manager`\r\n2. Run `rdm`\r\n\r\n### Expected behavior\r\nOpen the GUI\r\n\r\n### Notify maintainers\r\n@cstrahan \r\n\r\n### Metadata\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(tchekda): `\"home-manager-21.11, nixos-21.11.334139.1bd4bbd49be, unstable-22.05pre337269.33582b3ee1d\"`\r\n - channels(root): `\"nixos-hardware, nixos-21.11.334934.8a053bc2255, home-manager-21.05\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156506/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156480","id":1112452240,"node_id":"I_kwDOAEVQ_M5CTqyQ","number":156480,"title":"fail2ban cannot send mail","user":{"login":"PhilippWoelfel","id":19400064,"node_id":"MDQ6VXNlcjE5NDAwMDY0","avatar_url":"https://avatars.githubusercontent.com/u/19400064?v=4","gravatar_id":"","url":"https://api.github.com/users/PhilippWoelfel","html_url":"https://github.com/PhilippWoelfel","followers_url":"https://api.github.com/users/PhilippWoelfel/followers","following_url":"https://api.github.com/users/PhilippWoelfel/following{/other_user}","gists_url":"https://api.github.com/users/PhilippWoelfel/gists{/gist_id}","starred_url":"https://api.github.com/users/PhilippWoelfel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PhilippWoelfel/subscriptions","organizations_url":"https://api.github.com/users/PhilippWoelfel/orgs","repos_url":"https://api.github.com/users/PhilippWoelfel/repos","events_url":"https://api.github.com/users/PhilippWoelfel/events{/privacy}","received_events_url":"https://api.github.com/users/PhilippWoelfel/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-01-24T10:27:42Z","updated_at":"2022-02-01T18:34:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nOn a system with `service.postfix` enabled, fail2ban cannot send e-mails. Using `sendmail` as an MTA produces\r\n```\r\nstderr: '/nix/store/vfai0jim0db67nk9rd7ziq29jxb5n79n-bash-5.1-p8/bin/sh: line 8: sendmail: command not found'\r\n```\r\nUsing `mail` as MTA leads to a core dump and errors such as\r\n```\r\nstderr: 'mail: cannot send message: Process exited on signal'\r\nstderr: 'mail: Cannot open file /root/dead.letter: Read-only file system'\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n1. Use the following configuration file:\r\n```nix\r\n{pkgs,config,...}:\r\n{\r\n services.postfix.enable = true;\r\n services.fail2ban = {\r\n enable = true;\r\n extraPackages = [ pkgs.mailutils ];\r\n jails.DEFAULT = ''\r\n #mta = mail\r\n destemail = noreply@fqdn.com\r\n action = %(action_mw)s\r\n '';\r\n };\r\n}\r\n```\r\n\r\n2. Execute \r\n```bash\r\nsystemctl restart fail2ban.service\r\nsystemctl status fail2ban.service\r\n```\r\n\r\n3. Repeat steps 1. and 2., uncomment line `mta = mail` in the configuration file.\r\n\r\n### Expected behavior\r\nAn e-mail is sent to `noreply@fqdn.com` when fail2ban starts.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nI've been able to get it to work using `mail` as an MTA and:\r\n```nix\r\n{\r\n systemd.services.fail2ban.serviceConfig = with pkgs; {\r\n NoNewPrivileges = lib.mkForce false;\r\n ProtectSystem = lib.mkForce null;\r\n };\r\n}\r\n```\r\nPerhaps related: https://github.com/NixOS/nixpkgs/issues/103446\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@eelco @lovek323 @fpletz \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.10.90, NixOS, 21.11 (Porcupine)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.3.16`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156480/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156430","id":1112141573,"node_id":"I_kwDOAEVQ_M5CSe8F","number":156430,"title":"buildHex function does not work when builder is provided","user":{"login":"ydlr","id":58453832,"node_id":"MDQ6VXNlcjU4NDUzODMy","avatar_url":"https://avatars.githubusercontent.com/u/58453832?v=4","gravatar_id":"","url":"https://api.github.com/users/ydlr","html_url":"https://github.com/ydlr","followers_url":"https://api.github.com/users/ydlr/followers","following_url":"https://api.github.com/users/ydlr/following{/other_user}","gists_url":"https://api.github.com/users/ydlr/gists{/gist_id}","starred_url":"https://api.github.com/users/ydlr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ydlr/subscriptions","organizations_url":"https://api.github.com/users/ydlr/orgs","repos_url":"https://api.github.com/users/ydlr/repos","events_url":"https://api.github.com/users/ydlr/events{/privacy}","received_events_url":"https://api.github.com/users/ydlr/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-24T04:06:34Z","updated_at":"2022-01-24T04:06:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen a builder is explicitly passed into buildHex, it fails to evaluate. When builder is not provided, it evaluates successfully.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a package definition that uses buildHex.\r\n2. Try to evaluate.\r\n\r\n### Expected behavior\r\nThe package definition should evaluate to a derivation.\r\n\r\n### Additional context\r\nThe following example shows a failing package with the builder explicitly provided, followed by a successful evaluation with the default builder (which is the same):\r\n\r\n```console\r\nnix-repl> with beamPackages; buildHex {\r\n builder = buildRebar3;\r\n name = \"unicode_util_compat\";\r\n version = \"0.7.0\";\r\n sha256 = \"08952lw8cjdw8w171lv8wqbrxc4rcmb3jhkrdb7n06gngpbfdvi5\";\r\n }\r\nerror: cannot coerce a set to a string\r\n\r\n at /nix/store/vx7lyj4ajzgxccc0akxchkz1swlynhjp-nixos-22.05pre342264.5b091d4fbe3/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\n\r\n 204| // (lib.optionalAttrs (attrs ? name || (attrs ? pname && attrs ? version)) {\r\n 205| name =\r\n | ^\r\n 206| let\r\n«derivation\r\nnix-repl> with beamPackages; buildHex {\r\n name = \"unicode_util_compat\";\r\n version = \"0.7.0\";\r\n sha256 = \"08952lw8cjdw8w171lv8wqbrxc4rcmb3jhkrdb7n06gngpbfdvi5\";\r\n }\r\n«derivation /nix/store/z1x28xzckl2z1lshcybrrg3zfws5kcl9-unicode_util_compat-0.7.0.drv»\r\n\r\nnix-repl> with beamPackages; buildHex {\r\n name = \"unicode_util_compat\";\r\n version = \"0.7.0\";\r\n sha256 = \"08952lw8cjdw8w171lv8wqbrxc4rcmb3jhkrdb7n06gngpbfdvi5\";\r\n }\r\n«derivation /nix/store/z1x28xzckl2z1lshcybrrg3zfws5kcl9-unicode_util_compat-0.7.0.drv»\r\n```\r\n\r\n### Notify maintainers\r\n@gleber @ericbmerritt \r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(ydlr): `\"nixos-22.05pre347261.6d8215281b2\"`\r\n - channels(root): `\"nixos-22.05pre342264.5b091d4fbe3\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156430/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156400","id":1112030971,"node_id":"I_kwDOAEVQ_M5CSD77","number":156400,"title":"NixOS modules: Secrets provided in arguments are exposed to unprivileged users","user":{"login":"TLATER","id":6654841,"node_id":"MDQ6VXNlcjY2NTQ4NDE=","avatar_url":"https://avatars.githubusercontent.com/u/6654841?v=4","gravatar_id":"","url":"https://api.github.com/users/TLATER","html_url":"https://github.com/TLATER","followers_url":"https://api.github.com/users/TLATER/followers","following_url":"https://api.github.com/users/TLATER/following{/other_user}","gists_url":"https://api.github.com/users/TLATER/gists{/gist_id}","starred_url":"https://api.github.com/users/TLATER/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/TLATER/subscriptions","organizations_url":"https://api.github.com/users/TLATER/orgs","repos_url":"https://api.github.com/users/TLATER/repos","events_url":"https://api.github.com/users/TLATER/events{/privacy}","received_events_url":"https://api.github.com/users/TLATER/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":131612005,"node_id":"MDU6TGFiZWwxMzE2MTIwMDU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20sprintable","name":"3.skill: sprintable","color":"f7c6c7","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-01-24T00:17:39Z","updated_at":"2022-04-18T10:10:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen specifying secrets via arguments, they will be exposed via `/proc/<pid>/cmdline` - this is also possible if passed indirectly via an environment variable, since the shell resolves the value. This can be trivially demonstrated like so:\r\n\r\n```console\r\ntlater ~ $ export SAMPLE_SECRET=20\r\ntlater ~ $ sleep $SAMPLE_SECRET & ps -u | grep sleep\r\n[1] 8181\r\ntlater 8181 0.0 0.0 227256 1336 pts/2 SN 21:54 0:00 sleep 20\r\n```\r\n\r\nSome modules seem to use shell scripts to feed values provided via `passwordFile` or similar to their applications at runtime (with constructs like `SECRETKEY=\"$(head -n1 ${secretKey})\"`). Often, these are then fed to `sed` to replace values in template files, or passed to `--password` arguments (which are often, but not always, arguably an upstream problem).\r\n\r\nI'm not sure how widespread exactly this is, some way to search for occurrences of this would be nice. It's difficult because not all secrets are named `passwordFile` and there would be a lot of false positives if we simply pinged all modules that have such options. It's also hard to tell when this needs an upstream fix, but at least I'd argue `passwordFile` args should not be created for modules that cannot keep the secrets from being world-readable outside the nix store either.\r\n\r\nI'd like to point out [replace-secret](https://search.nixos.org/packages?channel=21.11&show=replace-secret&from=0&size=50&sort=relevance&type=packages&query=replace-secret), which essentially exists to do this without leaking secrets.\r\n\r\nFor now, I believe at least these modules to do such things in 21.11 - I did not check if upstream have a better way of supplying secrets where applicable:\r\n\r\n- [x] `nixos/modules/services/misc/gitea.nix` (@srhb @Ma27) - #156401\r\n- [ ] `nixos/modules/services/web-servers/ttyd.nix` (@nagy @atopuzov) - tsl0922/ttyd#872\r\n- [ ] `nixos/modules/services/networking/hans.nix`\r\n- [ ] `nixos/modules/services/networking/ddclient.nix` (@felschr)\r\n \r\nThere are also some modules that use bash heredocs and `printf` (notably, `nixos/modules/config/ldap.nix`), which I believe are safe, but could probably do with some comments to point this out.\r\n\r\nI guess it will be fairly common though, since the requirement of passing secrets via files is somewhat more pronounced in NixOS, not always considered by upstreams, and leaking secrets via `ps` is an easy thing to overlook. Maybe we should consider some kind of support in `lib` for supplying secrets to applications to avoid things like this (and get more use out of systemd, which has some nice secret-passing functionality).","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156400/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156343","id":1111920228,"node_id":"I_kwDOAEVQ_M5CRo5k","number":156343,"title":"pkgsCross.mingw32.stdenv.cc provides slightly incomplete linking environment: `cannot find -lmcfgthread`","user":{"login":"trofi","id":226650,"node_id":"MDQ6VXNlcjIyNjY1MA==","avatar_url":"https://avatars.githubusercontent.com/u/226650?v=4","gravatar_id":"","url":"https://api.github.com/users/trofi","html_url":"https://github.com/trofi","followers_url":"https://api.github.com/users/trofi/followers","following_url":"https://api.github.com/users/trofi/following{/other_user}","gists_url":"https://api.github.com/users/trofi/gists{/gist_id}","starred_url":"https://api.github.com/users/trofi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/trofi/subscriptions","organizations_url":"https://api.github.com/users/trofi/orgs","repos_url":"https://api.github.com/users/trofi/repos","events_url":"https://api.github.com/users/trofi/events{/privacy}","received_events_url":"https://api.github.com/users/trofi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-23T16:33:37Z","updated_at":"2022-01-23T20:09:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"I was trying to install a few cross-compilers to be available in parallel in a single environment as `${target}-gcc`. Looks like mingw one are slightly broken currently. Here is a minimal reproducer:\r\n\r\n```c\r\n// $ cat a.c\r\nint main(){}\r\n```\r\n\r\nPorblematic attempt `mingw32`:\r\n\r\n```\r\n$ nix build -f ~/nm pkgsCross.mingw32.stdenv.cc\r\n$ ./result/bin/i686-w64-mingw32-gcc a.c -o a\r\n/nix/store/wlcxwq9ll6jprhjfn5iwv6mk5ip9g8d1-i686-w64-mingw32-binutils-2.35.2/bin/i686-w64-mingw32-ld: cannot find -lmcfgthread\r\ncollect2: error: ld returned 1 exit status\r\n```\r\n\r\nWorking `gnu32` attempt:\r\n\r\n```\r\n$ nix build -f ~/nm pkgsCross.gnu32.stdenv.cc\r\n$ ./result/bin/i686-unknown-linux-gnu-gcc a.c -o a\r\n```\r\n\r\n### Expected behavior\r\nI expect both cases of compiler to be able to link minimal `int main(){}` example without extra environment settings.\r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.16.0, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156343/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156326","id":1111894040,"node_id":"I_kwDOAEVQ_M5CRigY","number":156326,"title":"Update scons to 4.3.0","user":{"login":"QuantMint","id":24614168,"node_id":"MDQ6VXNlcjI0NjE0MTY4","avatar_url":"https://avatars.githubusercontent.com/u/24614168?v=4","gravatar_id":"","url":"https://api.github.com/users/QuantMint","html_url":"https://github.com/QuantMint","followers_url":"https://api.github.com/users/QuantMint/followers","following_url":"https://api.github.com/users/QuantMint/following{/other_user}","gists_url":"https://api.github.com/users/QuantMint/gists{/gist_id}","starred_url":"https://api.github.com/users/QuantMint/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/QuantMint/subscriptions","organizations_url":"https://api.github.com/users/QuantMint/orgs","repos_url":"https://api.github.com/users/QuantMint/repos","events_url":"https://api.github.com/users/QuantMint/events{/privacy}","received_events_url":"https://api.github.com/users/QuantMint/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-23T14:58:45Z","updated_at":"2022-01-23T15:03:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on github to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: scons\r\n<!--\r\nThe current version can be found easily with the same process than above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 4.1.0\r\ndesired version: 4.3.0\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @andir \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156326/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156312","id":1111861889,"node_id":"I_kwDOAEVQ_M5CRaqB","number":156312,"title":"lib and pkgs.lib loose sync when trying to overlay lib","user":{"login":"ony","id":11265,"node_id":"MDQ6VXNlcjExMjY1","avatar_url":"https://avatars.githubusercontent.com/u/11265?v=4","gravatar_id":"","url":"https://api.github.com/users/ony","html_url":"https://github.com/ony","followers_url":"https://api.github.com/users/ony/followers","following_url":"https://api.github.com/users/ony/following{/other_user}","gists_url":"https://api.github.com/users/ony/gists{/gist_id}","starred_url":"https://api.github.com/users/ony/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ony/subscriptions","organizations_url":"https://api.github.com/users/ony/orgs","repos_url":"https://api.github.com/users/ony/repos","events_url":"https://api.github.com/users/ony/events{/privacy}","received_events_url":"https://api.github.com/users/ony/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-01-23T12:48:46Z","updated_at":"2022-01-27T21:09:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAttempt to add overlay `lib` have effect only on `pkgs` module argument attrset and not on `lib`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Prepare dummy NixOS configuration\r\n```nix\r\n# flake.nix\r\n{\r\n outputs = { nixpkgs, ... }@inputs: with inputs; {\r\n nixosConfigurations.ony = nixpkgs.lib.nixosSystem rec {\r\n system = \"x86_64-linux\";\r\n modules = [ ./configuration.nix ];\r\n };\r\n defaultPackage.x86_64-linux = self.nixosConfigurations.ony.config.system.build.toplevel;\r\n };\r\n}\r\n```\r\n```nix\r\n{ lib, pkgs, ... }:\r\n{\r\n nixpkgs.overlays = [\r\n (final: prev: {\r\n lib = prev.lib // {\r\n licenses = prev.lib.licenses // {\r\n sspl = prev.lib.licenses.sspl // {\r\n shortName = \"sspl\"; # try to fix upper case SSPL not matching attribute\r\n };\r\n };\r\n };\r\n })\r\n ];\r\n nixpkgs.config = {\r\n # blocklistedLicenses = with lib.licenses; [ sspl ]; # => ‘SSPL’ is not an attribute of lib.licenses\r\n blocklistedLicenses = with pkgs.lib.licenses; [ sspl ]; # => ‘sspl’ is not an attribute of lib.licenses\r\n };\r\n}\r\n```\r\n2. Run `nix flake check`\r\n\r\n### Expected behavior\r\n* There should be no difference between using `lib` or `pkgs` (via `pkgs.lib`) arguments of module.\r\n* Overriding `lib` in overlay should have effect on `check-meta.nix` evaluations too. That message indicates that licenses referenced in `blocklistedLicenses` and in attrset `lib.licenses` were different even if `sspl` attribute was found. See [comment for issue with SSPL](https://github.com/NixOS/nixpkgs/issues/154031#issuecomment-1019469016).\r\n\r\n### Screenshots\r\nWhen using `lib.licenses` (no effect from overlay)\r\n```\r\nzsh% nix flake check\r\nerror: ‘SSPL’ is not an attribute of lib.licenses\r\n(use '--show-trace' to show detailed location information)\r\n```\r\nWhen using `pkgs.lib.licenses` (license do not match one referenced in `check-meta.nix`)\r\n```\r\nzsh% nix flake check\r\nerror: ‘sspl’ is not an attribute of lib.licenses\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n*(notice lower case version of `shortName`)*\r\n\r\n### Additional context\r\nWhen there is requirement for `blocklistedLicenses` to reference only licenses from `lib.licenses`, we need a way extend that attrset to allow having packages and licenses outside of main `nixpkgs` repo.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n```sh\r\nnix run nixpkgs\\#nix-info -- -m\r\n```\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11.334684.1158f346391\"`\r\n - channels(nikolay): `\"nixpkgs-unstable-21.11pre310022.14b0f20fa1f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156312/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156310","id":1111859477,"node_id":"I_kwDOAEVQ_M5CRaEV","number":156310,"title":"nixui depends on out of life node 10","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-23T12:37:50Z","updated_at":"2022-01-23T12:37:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n```\r\n; nix build github:NixOS/nixpkgs/nixos-unstable#nixui\r\ndef-matcher: command not found\r\nerror: Package ‘nodejs-10.24.1’ in /nix/store/77y898gmsx12v68zng6r00qrpxxq8fqj-source/pkgs/development/web/nodejs/v10.nix:11 is marked as insecure, refusing to evaluate.\r\n\r\n\r\n Known issues:\r\n - This NodeJS release has reached its end of life. See https://nodejs.org/en/about/releases/.\r\n\r\n You can install it anyway by allowing this package, using the\r\n following methods:\r\n\r\n a) To temporarily allow all insecure packages, you can use an environment\r\n variable for a single invocation of the nix tools:\r\n\r\n $ export NIXPKGS_ALLOW_INSECURE=1\r\n\r\n b) for `nixos-rebuild` you can add ‘nodejs-10.24.1’ to\r\n `nixpkgs.config.permittedInsecurePackages` in the configuration.nix,\r\n like so:\r\n\r\n {\r\n nixpkgs.config.permittedInsecurePackages = [\r\n \"nodejs-10.24.1\"\r\n ];\r\n }\r\n\r\n c) For `nix-env`, `nix-build`, `nix-shell` or any other Nix command you can add\r\n ‘nodejs-10.24.1’ to `permittedInsecurePackages` in\r\n ~/.config/nixpkgs/config.nix, like so:\r\n\r\n {\r\n permittedInsecurePackages = [\r\n \"nodejs-10.24.1\"\r\n ];\r\n }\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\n### Expected behavior\r\n`nixui` would install without problems\r\n\r\n### Notify maintainers\r\n@matejc \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/3c249himjn7sh3cwnapmh5qgrnmd42xg-source`\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156310/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156309","id":1111857701,"node_id":"I_kwDOAEVQ_M5CRZol","number":156309,"title":"Possible conversion of the nixpkgs manual from docbook to mdbook","user":{"login":"Sciencentistguy","id":4983935,"node_id":"MDQ6VXNlcjQ5ODM5MzU=","avatar_url":"https://avatars.githubusercontent.com/u/4983935?v=4","gravatar_id":"","url":"https://api.github.com/users/Sciencentistguy","html_url":"https://github.com/Sciencentistguy","followers_url":"https://api.github.com/users/Sciencentistguy/followers","following_url":"https://api.github.com/users/Sciencentistguy/following{/other_user}","gists_url":"https://api.github.com/users/Sciencentistguy/gists{/gist_id}","starred_url":"https://api.github.com/users/Sciencentistguy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Sciencentistguy/subscriptions","organizations_url":"https://api.github.com/users/Sciencentistguy/orgs","repos_url":"https://api.github.com/users/Sciencentistguy/repos","events_url":"https://api.github.com/users/Sciencentistguy/events{/privacy}","received_events_url":"https://api.github.com/users/Sciencentistguy/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-23T12:29:49Z","updated_at":"2022-01-23T22:47:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"[mdBook](https://github.com/rust-lang/mdBook) is a manual generator that generates paged manuals. It is what is used by the [nix manual](https://nixos.org/manual/nix/stable/), and a large number of books in the Rust community.\r\n\r\nAs opposed to the [nixpkgs manual](https://nixos.org/manual/nixpkgs/stable/), which is one monolithic page, mdBook generates paged documentation which is much easier to read.\r\n\r\nIs converting the nixpkgs documentation to mdBook desirable at this time? I certainly think that it would make the documentation more approachable and easier for beginners and advanced users alike to find what they're looking for.\r\n\r\nI would be happy to have a look at doing this myself if people think it'd be like to get merged.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156309/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156279","id":1111811899,"node_id":"I_kwDOAEVQ_M5CROc7","number":156279,"title":"Package Request: LocalToNet","user":{"login":"ghost","id":10137,"node_id":"MDQ6VXNlcjEwMTM3","avatar_url":"https://avatars.githubusercontent.com/u/10137?v=4","gravatar_id":"","url":"https://api.github.com/users/ghost","html_url":"https://github.com/ghost","followers_url":"https://api.github.com/users/ghost/followers","following_url":"https://api.github.com/users/ghost/following{/other_user}","gists_url":"https://api.github.com/users/ghost/gists{/gist_id}","starred_url":"https://api.github.com/users/ghost/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ghost/subscriptions","organizations_url":"https://api.github.com/users/ghost/orgs","repos_url":"https://api.github.com/users/ghost/repos","events_url":"https://api.github.com/users/ghost/events{/privacy}","received_events_url":"https://api.github.com/users/ghost/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-23T08:49:02Z","updated_at":"2022-01-29T06:57:44Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_LocalToNet is a reverse proxy that enables you to expose your localhost to the internet. It supports the following tunnels: HTTP/s, UDP, TCP, UDP/TCP._\r\n\r\n**Metadata**\r\n\r\n* homepage URL: [localtonet.com](https://localtonet.com)\r\n* source URL: [localtonet.com/#download](https://localtonet.com/#download)\r\n* license: Commercial/Closed source\r\n* platforms: linux, darwin, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156279/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156270","id":1111788682,"node_id":"I_kwDOAEVQ_M5CRIyK","number":156270,"title":"feature request: use Fedora's pre-signed UEFI shim to support Secure Boot systems","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-23T06:21:54Z","updated_at":"2022-04-27T00:21:39Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nMy gaming PC really wanted to upgrade to Windows 11 and now it has Secure Boot enabled and I'd prefer not to disable it.\r\n\r\nWhile I'm a bit skeptical of (what I understand of) rhboot/shim, it seems it will allow enrolling any other extra binary at boot time. This is useful for us, since we should presumably be able to just drop in the pre-built shim and then allow users to as-needed add signatures for their next stage bootloader.\r\n\r\n(now that I think about it, since the shim is already signed and will already boot anywhere the default UEFI Secure Boot signing keys are enrolled, then it doesn't really represent any risk for us to have a module to optionally deploy this and poke an EFI entry with `efibootmgr`. A would-be attacker would generally be able to side-load the shim into the ESP or boot-from-media into the shim anyway.)\r\n\r\nI'm not really sure how the shim finds it's next stage to attempt to boot though.\r\n\r\nAlso, I'm curious if you considered this @grahamc when evaluating nixos + secure boot.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156270/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156244","id":1111741446,"node_id":"I_kwDOAEVQ_M5CQ9QG","number":156244,"title":"vscode-fhs cannot be installed on aarch64-linux","user":{"login":"lithdew","id":63115601,"node_id":"MDQ6VXNlcjYzMTE1NjAx","avatar_url":"https://avatars.githubusercontent.com/u/63115601?v=4","gravatar_id":"","url":"https://api.github.com/users/lithdew","html_url":"https://github.com/lithdew","followers_url":"https://api.github.com/users/lithdew/followers","following_url":"https://api.github.com/users/lithdew/following{/other_user}","gists_url":"https://api.github.com/users/lithdew/gists{/gist_id}","starred_url":"https://api.github.com/users/lithdew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lithdew/subscriptions","organizations_url":"https://api.github.com/users/lithdew/orgs","repos_url":"https://api.github.com/users/lithdew/repos","events_url":"https://api.github.com/users/lithdew/events{/privacy}","received_events_url":"https://api.github.com/users/lithdew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-23T01:31:47Z","updated_at":"2022-01-24T20:37:27Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`vscode-fhs` and `vscode-fhsWithPackages` can not be installed on aarch64-linux.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```console\r\n# nix-shell -p vscode-fhs --show-trace\r\n```\r\n\r\n### Expected behavior\r\nThat `vscode-fhs` may be installed on aarch64-linux. The following command which install vscode without fhs works:\r\n```console\r\n# nix-shell -p vscode\r\n```\r\n\r\n### Screenshots\r\n```console\r\n# nix-shell -p vscode-fhs --show-trace\r\nerror: while evaluating the attribute 'buildInputs' of the derivation 'shell' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\nwhile evaluating the attribute 'buildCommand' of the derivation 'code' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\nwhile evaluating the attribute 'text' of the derivation 'code' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\nwhile evaluating 'bwrapCmd' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/build-support/build-fhs-userenv-bubblewrap/default.nix:100:14, called from /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/build-support/build-fhs-userenv-bubblewrap/default.nix:179:35:\r\nwhile evaluating the attribute 'buildCommand' of the derivation 'code-fhs' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\nwhile evaluating the attribute 'passAsFile' of the derivation 'code-usr-target' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\nwhile evaluating the attribute 'passAsFile' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/build-support/buildenv/default.nix:77:5:\r\nwhile evaluating the attribute 'buildCommand' of the derivation 'glibc-multi-2.33-59' at /nix/store/7l3m5xrnqsaph7463ifmwvvalpg369fm-nixos-22.05pre347735.fc4148a47fa/nixos/pkgs/stdenv/generic/make-derivation.nix:205:7:\r\ni686 Linux package set can only be used with the x86 family.\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@eadwu @Synthetica9 @maxeaubrey @bobby285271\r\n\r\n### Metadata\r\n```console\r\n# nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.15.16, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-22.05pre347735.fc4148a47fa\"`\r\n - channels(lith): `\"nixpkgs-22.05pre346530.f3d9d4bd898\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156244/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156177","id":1111627618,"node_id":"I_kwDOAEVQ_M5CQhdi","number":156177,"title":"Watchman 4.9 is 4+ years old","user":{"login":"andrewhamon","id":5134584,"node_id":"MDQ6VXNlcjUxMzQ1ODQ=","avatar_url":"https://avatars.githubusercontent.com/u/5134584?v=4","gravatar_id":"","url":"https://api.github.com/users/andrewhamon","html_url":"https://github.com/andrewhamon","followers_url":"https://api.github.com/users/andrewhamon/followers","following_url":"https://api.github.com/users/andrewhamon/following{/other_user}","gists_url":"https://api.github.com/users/andrewhamon/gists{/gist_id}","starred_url":"https://api.github.com/users/andrewhamon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/andrewhamon/subscriptions","organizations_url":"https://api.github.com/users/andrewhamon/orgs","repos_url":"https://api.github.com/users/andrewhamon/repos","events_url":"https://api.github.com/users/andrewhamon/events{/privacy}","received_events_url":"https://api.github.com/users/andrewhamon/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-22T17:13:33Z","updated_at":"2022-01-22T20:37:35Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on github to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the the current version of the package\r\n-->\r\n- [X] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [X] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: watchman\r\n<!--\r\nThe current version can be found easily with the same process than above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 4.9.0\r\ndesired version: 2022.01.17.00\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @cstrahan \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\n## Watchman is effectively versionless now\r\n[From the watchman website](https://facebook.github.io/watchman/docs/install.html#binary-downloads-for-linux-macos-and-windows-beta):\r\n\r\n> Watchman is continuously deployed as it passes our internal test validation inside Facebook and doesn’t use manually assigned or “approved” version numbers.\r\n\r\nI'm not sure what this means when it comes to packaging in nix. The version strings are basically dates now, e.g.\r\n\r\n```\r\nwatchman --version ~/flexport/flexport\r\n2022.01.17.00\r\n```\r\n\r\nI probably don't need the latest version, but switching to the homebrew installed version solved some mysterious bugs with dependent tools I was using (namely: `flow`).\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156177/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156133","id":1111262423,"node_id":"I_kwDOAEVQ_M5CPITX","number":156133,"title":"How to use Bamf in python","user":{"login":"prehonor","id":10784632,"node_id":"MDQ6VXNlcjEwNzg0NjMy","avatar_url":"https://avatars.githubusercontent.com/u/10784632?v=4","gravatar_id":"","url":"https://api.github.com/users/prehonor","html_url":"https://github.com/prehonor","followers_url":"https://api.github.com/users/prehonor/followers","following_url":"https://api.github.com/users/prehonor/following{/other_user}","gists_url":"https://api.github.com/users/prehonor/gists{/gist_id}","starred_url":"https://api.github.com/users/prehonor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prehonor/subscriptions","organizations_url":"https://api.github.com/users/prehonor/orgs","repos_url":"https://api.github.com/users/prehonor/repos","events_url":"https://api.github.com/users/prehonor/events{/privacy}","received_events_url":"https://api.github.com/users/prehonor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-22T05:13:22Z","updated_at":"2022-01-22T12:08:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"this is my code `from gi.repository import Bamf`\r\nI have instaledl pygobject and bamf, but it still says “Cannot find declaration to go to ” when mouse hang over “Bamf”","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156133/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156126","id":1111195606,"node_id":"I_kwDOAEVQ_M5CO3_W","number":156126,"title":"accelerated video playback not working - firefox nightly + libva-mesa driver","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-22T02:40:41Z","updated_at":"2022-01-28T12:11:39Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```\r\n❯ firefox \r\n\r\n(firefox:1202676): Gtk-WARNING **: 12:37:57.658: Theme file for capitaine-cursors-white has no directories\r\nlibva info: VA-API version 1.13.0\r\nlibva info: Trying to open /run/opengl-driver/lib/dri/radeonsi_drv_video.so\r\nlibva info: Trying to open /usr/lib/dri/radeonsi_drv_video.so\r\nlibva info: Trying to open /usr/lib32/dri/radeonsi_drv_video.so\r\nlibva info: Trying to open /usr/lib/x86_64-linux-gnu/dri/radeonsi_drv_video.so\r\nlibva info: Trying to open /usr/lib/i386-linux-gnu/dri/radeonsi_drv_video.so\r\nlibva info: va_openDriver() returns -1\r\n\r\n```\r\n\r\nyet:\r\n\r\n```\r\n❯ vainfo\r\nlibva info: VA-API version 1.13.0\r\nlibva info: Trying to open /run/opengl-driver/lib/dri/radeonsi_drv_video.so\r\nlibva info: Found init function __vaDriverInit_1_13\r\nlibva info: va_openDriver() returns 0\r\nvainfo: VA-API version: 1.13 (libva 2.13.0)\r\nvainfo: Driver version: Mesa Gallium driver 21.3.3 for AMD RENOIR (DRM 3.44.0, 5.16.0, LLVM 13.0.0)\r\nvainfo: Supported profile and entrypoints\r\n VAProfileMPEG2Simple :\tVAEntrypointVLD\r\n VAProfileMPEG2Main :\tVAEntrypointVLD\r\n VAProfileVC1Simple :\tVAEntrypointVLD\r\n VAProfileVC1Main :\tVAEntrypointVLD\r\n VAProfileVC1Advanced :\tVAEntrypointVLD\r\n VAProfileH264ConstrainedBaseline:\tVAEntrypointVLD\r\n VAProfileH264ConstrainedBaseline:\tVAEntrypointEncSlice\r\n VAProfileH264Main :\tVAEntrypointVLD\r\n VAProfileH264Main :\tVAEntrypointEncSlice\r\n VAProfileH264High :\tVAEntrypointVLD\r\n VAProfileH264High :\tVAEntrypointEncSlice\r\n VAProfileHEVCMain :\tVAEntrypointVLD\r\n VAProfileHEVCMain :\tVAEntrypointEncSlice\r\n VAProfileHEVCMain10 :\tVAEntrypointVLD\r\n VAProfileHEVCMain10 :\tVAEntrypointEncSlice\r\n VAProfileJPEGBaseline :\tVAEntrypointVLD\r\n VAProfileVP9Profile0 :\tVAEntrypointVLD\r\n VAProfileVP9Profile2 :\tVAEntrypointVLD\r\n VAProfileNone :\tVAEntrypointVideoProc\r\n```\r\n\r\nThis is using latest firefox nightly from `flake-firefox-nightly` but it's using the same packaging that nixpkgs's bin packaging uses. \r\n\r\nThis is with nixos-unstable current: 6d8215281b2f87a5af9ed7425a26ac575da0438f","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156126/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156121","id":1111181440,"node_id":"I_kwDOAEVQ_M5CO0iA","number":156121,"title":"systemd-boot not installing on unstable","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-22T02:02:17Z","updated_at":"2022-02-13T06:49:12Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI'm not sure if I'm doing something silly, but my `/boot` was full, so I figured I'd empty it out, set `boot.loader.systemd-boot.configurationLimit` and then re-deploy.\r\n\r\nHowever, this didn't go well (I hope the machine doesn't restart!):\r\n\r\n```\r\n+ ssh localhost 'echo \"/nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110\" | env CACHIX_SIGNING_KEY=\"eIuqcXYgSpe2wktg7fiSHuxo2Cko2lTEgxHxg2bl3YJs2snoV8xEQHht\r\n3gE6MQ3zk2K7xVw91B7gXgrFWxv8jg==\" cachix push colemickens'\r\n++ printf '\\\"%s\\\" ' sudo nix build --no-link --profile /nix/var/nix/profiles/system /nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110\r\n+ ssh 100.103.91.27 '\"sudo\" \"nix\" \"build\" \"--no-link\" \"--profile\" \"/nix/var/nix/profiles/system\" \"/nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110\" '\r\nwarning: unknown experimental feature 'ca-references'\r\n++ printf '\\\"%s\\\" ' sudo nix shell -vv /nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110 -c switch-to-configuration switch\r\n+ ssh 100.103.91.27 '\"sudo\" \"nix\" \"shell\" \"-vv\" \"/nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110\" \"-c\" \"switch-to-configuration\" \"switch\" '\r\nAll done.\r\nwarning: unknown experimental feature 'ca-references'\r\nsystemd-boot not installed in ESP.\r\nNo default/fallback boot loader installed in ESP.\r\nFailed to open \"/boot/EFI/systemd/.#systemd-bootx64.efi354fbb7c5fcf5579\" for writing: No such file or directory\r\nFailed to open \"/boot/EFI/BOOT/.#BOOTX64.EFI145e91ccf64bc344\" for writing: No such file or directory\r\ncould not find any previously installed systemd-boot, installing.\r\nTraceback (most recent call last):\r\n File \"/nix/store/f8gnqlqvsp6yhahaf0alkmqb0k4j8igb-systemd-boot\", line 305, in <module>\r\n main()\r\n File \"/nix/store/f8gnqlqvsp6yhahaf0alkmqb0k4j8igb-systemd-boot\", line 257, in main\r\n subprocess.check_call([\"/nix/store/cfhpzlarbhfw3scj91dcz5ai04ayfzik-systemd-249.7/bin/bootctl\", \"--path=/boot\", \"update\"])\r\n File \"/nix/store/dn4fwp0yx6nsa85cr20cwvdmg64xwmcy-python3-3.9.9/lib/python3.9/subprocess.py\", line 373, in check_call\r\n raise CalledProcessError(retcode, cmd)\r\nsubprocess.CalledProcessError: Command '['/nix/store/cfhpzlarbhfw3scj91dcz5ai04ayfzik-systemd-249.7/bin/bootctl', '--path=/boot', 'update']' returned non-zero exit status 1.\r\n\r\n```\r\n\r\nSo, let's remote in and try to activate the generation with `NIXOS_INSTALL_BOOTLOADER` set:\r\n\r\n```\r\ncole@jeffhyper ~\r\n❯ sudo env NIXOS_INSTALL_BOOLOADER=1 \"/nix/store/4i923igvgj0r29cif8rsgaxn89x9j4h9-nixos-system-jeffhyper-22.05.20220120.bb27110/bin/switch-to-configuration\" switch\r\nsystemd-boot not installed in ESP.\r\nNo default/fallback boot loader installed in ESP.\r\ncould not find any previously installed systemd-boot, installing.\r\nFailed to open \"/boot/EFI/systemd/.#systemd-bootx64.efi5089e392206a681c\" for writing: No such file or directory\r\nFailed to open \"/boot/EFI/BOOT/.#BOOTX64.EFI87290d639679f51f\" for writing: No such file or directory\r\nTraceback (most recent call last):\r\n File \"/nix/store/f8gnqlqvsp6yhahaf0alkmqb0k4j8igb-systemd-boot\", line 305, in <module>\r\n main()\r\n File \"/nix/store/f8gnqlqvsp6yhahaf0alkmqb0k4j8igb-systemd-boot\", line 257, in main\r\n subprocess.check_call([\"/nix/store/cfhpzlarbhfw3scj91dcz5ai04ayfzik-systemd-249.7/bin/bootctl\", \"--path=/boot\", \"update\"])\r\n File \"/nix/store/dn4fwp0yx6nsa85cr20cwvdmg64xwmcy-python3-3.9.9/lib/python3.9/subprocess.py\", line 373, in check_call\r\n raise CalledProcessError(retcode, cmd)\r\nsubprocess.CalledProcessError: Command '['/nix/store/cfhpzlarbhfw3scj91dcz5ai04ayfzik-systemd-249.7/bin/bootctl', '--path=/boot', 'update']' returned non-zero exit status 1.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use current nixos-unstable: \r\n2. These are my boot settings:\r\n```nix\r\n{ \r\n#... \r\n boot = {\r\n loader.systemd-boot.enable = true;\r\n loader.systemd-boot.configurationLimit = 3;\r\n loader.efi.canTouchEfiVariables = true;\r\n };\r\n}\r\n```\r\n\r\n### Expected behavior\r\n`systemd-boot` to be (re-)installed correctly.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156121/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156089","id":1110857946,"node_id":"I_kwDOAEVQ_M5CNlja","number":156089,"title":"cnsetuputil2 in canon-cups-ufr2 can't find /usr/share/cnsetuputil2/cnsetuputil.ui","user":{"login":"dmayle","id":67033,"node_id":"MDQ6VXNlcjY3MDMz","avatar_url":"https://avatars.githubusercontent.com/u/67033?v=4","gravatar_id":"","url":"https://api.github.com/users/dmayle","html_url":"https://github.com/dmayle","followers_url":"https://api.github.com/users/dmayle/followers","following_url":"https://api.github.com/users/dmayle/following{/other_user}","gists_url":"https://api.github.com/users/dmayle/gists{/gist_id}","starred_url":"https://api.github.com/users/dmayle/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dmayle/subscriptions","organizations_url":"https://api.github.com/users/dmayle/orgs","repos_url":"https://api.github.com/users/dmayle/repos","events_url":"https://api.github.com/users/dmayle/events{/privacy}","received_events_url":"https://api.github.com/users/dmayle/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-21T20:00:01Z","updated_at":"2022-01-21T20:00:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen trying to launch cnsetuputil2 from the canon UFR 2 driver package, it responds with an error that it is unable to locate the file cnsetuputil.ui\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install canon-cups-ufr2\r\n2. /nix/store/<PATH>/bin/cnsetuputil2\r\n\r\n### Expected behavior\r\nThe program should run\r\n\r\n### Additional context\r\nThere was a recent update to canon-cups-ufr2 to version 5.40 which introduced cnsetuputil2, but it doesn't work\r\n\r\n### Notify maintainers\r\nThere are no maintainers, and since I only have a network printer, I can't test the majority of the printers\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.91, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(douglas): `\"home-manager\"`\r\n - channels(root): `\"nixos-22.05pre346355.d5dae6569ea\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nNote, incoming PR that fixes this.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156089/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067/events","html_url":"https://github.com/NixOS/nixpkgs/issues/156067","id":1110644824,"node_id":"I_kwDOAEVQ_M5CMxhY","number":156067,"title":"mouse support in nixos/test-driver","user":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"labels":[{"id":1339304902,"node_id":"MDU6TGFiZWwxMzM5MzA0OTAy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20testing","name":"6.topic: testing","color":"fef2c0","default":false,"description":"Tooling for automated testing of packages and modules"}],"state":"open","locked":false,"assignee":{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false},"assignees":[{"login":"Synthetica9","id":7075751,"node_id":"MDQ6VXNlcjcwNzU3NTE=","avatar_url":"https://avatars.githubusercontent.com/u/7075751?v=4","gravatar_id":"","url":"https://api.github.com/users/Synthetica9","html_url":"https://github.com/Synthetica9","followers_url":"https://api.github.com/users/Synthetica9/followers","following_url":"https://api.github.com/users/Synthetica9/following{/other_user}","gists_url":"https://api.github.com/users/Synthetica9/gists{/gist_id}","starred_url":"https://api.github.com/users/Synthetica9/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Synthetica9/subscriptions","organizations_url":"https://api.github.com/users/Synthetica9/orgs","repos_url":"https://api.github.com/users/Synthetica9/repos","events_url":"https://api.github.com/users/Synthetica9/events{/privacy}","received_events_url":"https://api.github.com/users/Synthetica9/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2022-01-21T16:06:42Z","updated_at":"2022-01-21T16:07:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Currently, there is no good way to simulate mouse clicks in the NixOS test driver. Would be nice to have at least the following methods:\r\n\r\n| Proposed name | Intended function | \r\n| --- | --- |\r\n| Machine.move_mouse(x, y) | Move the mouse to coordinates |\r\n| Machine.click_mouse(buttons) | \r\n| Machine.click_text(str) | Use tesseract to identify text, for buttons and such |\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/156067/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155970","id":1109864741,"node_id":"I_kwDOAEVQ_M5CJzEl","number":155970,"title":"libmd (dependency of libbsd) fails to build on darwin","user":{"login":"davidarmstronglewis","id":6754950,"node_id":"MDQ6VXNlcjY3NTQ5NTA=","avatar_url":"https://avatars.githubusercontent.com/u/6754950?v=4","gravatar_id":"","url":"https://api.github.com/users/davidarmstronglewis","html_url":"https://github.com/davidarmstronglewis","followers_url":"https://api.github.com/users/davidarmstronglewis/followers","following_url":"https://api.github.com/users/davidarmstronglewis/following{/other_user}","gists_url":"https://api.github.com/users/davidarmstronglewis/gists{/gist_id}","starred_url":"https://api.github.com/users/davidarmstronglewis/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidarmstronglewis/subscriptions","organizations_url":"https://api.github.com/users/davidarmstronglewis/orgs","repos_url":"https://api.github.com/users/davidarmstronglewis/repos","events_url":"https://api.github.com/users/davidarmstronglewis/events{/privacy}","received_events_url":"https://api.github.com/users/davidarmstronglewis/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-20T23:28:50Z","updated_at":"2022-01-21T00:12:38Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n`libbsd`'s depency, `libmd`, does not build on Darwin (x86_64)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix repl`\r\n2. `:l <nixpkgs>`\r\n3. `:b libmd` or `:b libbsd`\r\n\r\n### Expected behavior\r\nBoth `libmd` and `libmd` should build properly.\r\n\r\n### Screenshots\r\n~~If applicable, add screenshots to help explain your problem.~~\r\n\r\n### Additional context\r\nOutput from ` nix log /nix/store/wv0vkcsbcdbws1gag8pjylsbi6mwd4kc-libmd-1.0.4.drv` after attempting to build `libmd`:\r\n\r\n```console\r\n@nix { \"action\": \"setPhase\", \"phase\": \"unpackPhase\" }\r\nunpacking sources\r\nunpacking source archive /nix/store/vmrry4cgxpa9v8mr1z3hlj25ljgp52i5-libmd-1.0.4.tar.xz\r\nsource root is libmd-1.0.4\r\nsetting SOURCE_DATE_EPOCH to timestamp 1633402044 of file libmd-1.0.4/src/sha512hl.c\r\n@nix { \"action\": \"setPhase\", \"phase\": \"patchPhase\" }\r\npatching sources\r\n@nix { \"action\": \"setPhase\", \"phase\": \"autoreconfPhase\" }\r\nautoreconfPhase\r\nautoreconf: export WARNINGS=\r\nautoreconf: Entering directory '.'\r\nautoreconf: configure.ac: not using Gettext\r\nautoreconf: running: aclocal --force -I m4\r\nautoreconf: configure.ac: tracing\r\nautoreconf: running: libtoolize --copy --force\r\nlibtoolize: putting auxiliary files in AC_CONFIG_AUX_DIR, 'build-aux'.\r\nlibtoolize: copying file 'build-aux/ltmain.sh'\r\nlibtoolize: putting macros in AC_CONFIG_MACRO_DIRS, 'm4'.\r\nlibtoolize: copying file 'm4/libtool.m4'\r\nlibtoolize: copying file 'm4/ltoptions.m4'\r\nlibtoolize: copying file 'm4/ltsugar.m4'\r\nlibtoolize: copying file 'm4/ltversion.m4'\r\nlibtoolize: copying file 'm4/lt~obsolete.m4'\r\nautoreconf: configure.ac: not using Intltool\r\nautoreconf: configure.ac: not using Gtkdoc\r\nautoreconf: running: aclocal --force -I m4\r\nautoreconf: running: /nix/store/i75sxcv3qz61w1j1drrjw5xjg1l0mps3-autoconf-2.71/bin/autoconf --force\r\nautoreconf: running: /nix/store/i75sxcv3qz61w1j1drrjw5xjg1l0mps3-autoconf-2.71/bin/autoheader --force\r\nautoreconf: running: automake --add-missing --copy --force-missing\r\nconfigure.ac:25: installing 'build-aux/compile'\r\nconfigure.ac:9: installing 'build-aux/missing'\r\nsrc/Makefile.am: installing 'build-aux/depcomp'\r\nautoreconf: Leaving directory '.'\r\n@nix { \"action\": \"setPhase\", \"phase\": \"configurePhase\" }\r\nconfiguring\r\nfixing libtool script ./build-aux/ltmain.sh\r\nconfigure flags: --disable-static --disable-dependency-tracking --prefix=/nix/store/6wsyfyrzg86jn7884pjpb71wla1kgjf1-libmd-1.0.4\r\nchecking for a BSD-compatible install... /nix/store/srv3qk2wrq058z2wwvdj02hm5jlvcj40-coreutils-9.0/bin/install -c\r\nchecking whether build environment is sane... yes\r\nchecking for a race-free mkdir -p... /nix/store/srv3qk2wrq058z2wwvdj02hm5jlvcj40-coreutils-9.0/bin/mkdir -p\r\nchecking for gawk... gawk\r\nchecking whether make sets $(MAKE)... yes\r\nchecking whether make supports nested variables... yes\r\nchecking whether make supports nested variables... (cached) yes\r\nchecking whether make supports the include directive... yes (GNU style)\r\nchecking for gcc... clang\r\nchecking whether the C compiler works... yes\r\nchecking for C compiler default output file name... a.out\r\nchecking for suffix of executables... \r\nchecking whether we are cross compiling... no\r\nchecking for suffix of object files... o\r\nchecking whether the compiler supports GNU C... yes\r\nchecking whether clang accepts -g... yes\r\nchecking for clang option to enable C11 features... none needed\r\nchecking whether clang understands -c and -o together... yes\r\nchecking dependency style of clang... none\r\nchecking for stdio.h... yes\r\nchecking for stdlib.h... yes\r\nchecking for string.h... yes\r\nchecking for inttypes.h... yes\r\nchecking for stdint.h... yes\r\nchecking for strings.h... yes\r\nchecking for sys/stat.h... yes\r\nchecking for sys/types.h... yes\r\nchecking for unistd.h... yes\r\nchecking for wchar.h... yes\r\nchecking for minix/config.h... no\r\nchecking whether it is safe to define __EXTENSIONS__... yes\r\nchecking whether _XOPEN_SOURCE should be defined... no\r\nchecking for special C compiler options needed for large files... no\r\nchecking for _FILE_OFFSET_BITS value needed for large files... no\r\nchecking the archiver (ar) interface... ar\r\nchecking build system type... x86_64-apple-darwin21.2.0\r\nchecking host system type... x86_64-apple-darwin21.2.0\r\nchecking how to print strings... printf\r\nchecking for a sed that does not truncate output... /nix/store/sr4xm8vdll6pi178fzi18dwz6zhvzimg-gnused-4.8/bin/sed\r\nchecking for grep that handles long lines and -e... /nix/store/1lfp83jaz6wsgmckpr79m5wc74hfnbdx-gnugrep-3.7/bin/grep\r\nchecking for egrep... /nix/store/1lfp83jaz6wsgmckpr79m5wc74hfnbdx-gnugrep-3.7/bin/grep -E\r\nchecking for fgrep... /nix/store/1lfp83jaz6wsgmckpr79m5wc74hfnbdx-gnugrep-3.7/bin/grep -F\r\nchecking for ld used by clang... ld\r\nchecking if the linker (ld) is GNU ld... no\r\nchecking for BSD- or MS-compatible name lister (nm)... nm\r\nchecking the name lister (nm) interface... BSD nm\r\nchecking whether ln -s works... yes\r\nchecking the maximum length of command line arguments... 786432\r\nchecking how to convert x86_64-apple-darwin21.2.0 file names to x86_64-apple-darwin21.2.0 format... func_convert_file_noop\r\nchecking how to convert x86_64-apple-darwin21.2.0 file names to toolchain format... func_convert_file_noop\r\nchecking for ld option to reload object files... -r\r\nchecking for objdump... no\r\nchecking how to recognize dependent libraries... (cached) pass_all\r\nchecking for dlltool... no\r\nchecking how to associate runtime and link libraries... printf %s\\n\r\nchecking for archiver @FILE support... no\r\nchecking for strip... strip\r\nchecking for ranlib... ranlib\r\nchecking command to parse nm output from clang object... ok\r\nchecking for sysroot... no\r\nchecking for a working dd... /nix/store/srv3qk2wrq058z2wwvdj02hm5jlvcj40-coreutils-9.0/bin/dd\r\nchecking how to truncate binary pipes... /nix/store/srv3qk2wrq058z2wwvdj02hm5jlvcj40-coreutils-9.0/bin/dd bs=4096 count=1\r\nchecking for mt... no\r\nchecking if : is a manifest tool... no\r\nchecking for dsymutil... dsymutil\r\nchecking for nmedit... no\r\nchecking for lipo... lipo\r\nchecking for otool... otool\r\nchecking for otool64... no\r\nchecking for -single_module linker flag... yes\r\nchecking for -exported_symbols_list linker flag... yes\r\nchecking for -force_load linker flag... yes\r\nchecking for dlfcn.h... yes\r\nchecking for objdir... .libs\r\nchecking if clang supports -fno-rtti -fno-exceptions... yes\r\nchecking for clang option to produce PIC... -fno-common -DPIC\r\nchecking if clang PIC flag -fno-common -DPIC works... yes\r\nchecking if clang static flag -static works... no\r\nchecking if clang supports -c -o file.o... yes\r\nchecking if clang supports -c -o file.o... (cached) yes\r\nchecking whether the clang linker (ld) supports shared libraries... yes\r\nchecking dynamic linker characteristics... darwin21.2.0 dyld\r\nchecking how to hardcode library paths into programs... immediate\r\nchecking whether stripping libraries is possible... yes\r\nchecking if libtool supports shared libraries... yes\r\nchecking whether to build shared libraries... yes\r\nchecking whether to build static libraries... no\r\nchecking for --version-script linker flag... no\r\nchecking for a sed that does not truncate output... (cached) /nix/store/sr4xm8vdll6pi178fzi18dwz6zhvzimg-gnused-4.8/bin/sed\r\nchecking for gcc... (cached) clang\r\nchecking whether the compiler supports GNU C... (cached) yes\r\nchecking whether clang accepts -g... (cached) yes\r\nchecking for clang option to enable C11 features... (cached) none needed\r\nchecking whether clang understands -c and -o together... (cached) yes\r\nchecking dependency style of clang... (cached) none\r\nchecking whether clang accepts -Wall... yes\r\nchecking whether clang accepts -Wextra... yes\r\nchecking whether clang accepts -Wbad-function-cast... yes\r\nchecking whether clang accepts -Wc99-c11-compat... no\r\nchecking whether clang accepts -Wcast-align... yes\r\nchecking whether clang accepts -Wdeclaration-after-statement... yes\r\nchecking whether clang accepts -Wdocumentation... yes\r\nchecking whether clang accepts -Wduplicated-branches... no\r\nchecking whether clang accepts -Wduplicated-cond... no\r\nchecking whether clang accepts -Wformat -Wformat-security... yes\r\nchecking whether clang accepts -Wformat=2... yes\r\nchecking whether clang accepts -Winit-self... yes\r\nchecking whether clang accepts -Wlogical-not-parentheses... yes\r\nchecking whether clang accepts -Wlogical-op... no\r\nchecking whether clang accepts -Wmissing-declarations... yes\r\nchecking whether clang accepts -Wmissing-format-attribute... yes\r\nchecking whether clang accepts -Wmissing-prototypes... yes\r\nchecking whether clang accepts -Wnested-externs... yes\r\nchecking whether clang accepts -Wno-tautological-constant-out-of-range-compare... yes\r\nchecking whether clang accepts -Wno-unused-parameter... yes\r\nchecking whether clang accepts -Wnull-dereference... yes\r\nchecking whether clang accepts -Wold-style-definition... yes\r\nchecking whether clang accepts -Wpointer-arith... yes\r\nchecking whether clang accepts -Wredundant-decls... yes\r\nchecking whether clang accepts -Wregister... yes\r\nchecking whether clang accepts -Wrestrict... no\r\nchecking whether clang accepts -Wshadow... yes\r\nchecking whether clang accepts -Wshift-negative-value... yes\r\nchecking whether clang accepts -Wsizeof-array-argument... yes\r\nchecking whether clang accepts -Wstrict-prototypes... yes\r\nchecking whether clang accepts -Wswitch-bool... yes\r\nchecking whether clang accepts -Wvla... yes\r\nchecking whether clang accepts -Wwrite-strings... yes\r\nchecking for unistd.h... (cached) yes\r\nchecking whether byte ordering is bigendian... no\r\nchecking for off_t... yes\r\nchecking for size_t... yes\r\nchecking for ssize_t... yes\r\nchecking that generated files are newer than configure... done\r\nconfigure: creating ./config.status\r\nconfig.status: creating Makefile\r\nconfig.status: creating include/Makefile\r\nconfig.status: creating man/Makefile\r\nconfig.status: creating src/Makefile\r\nconfig.status: creating src/libmd.pc\r\nconfig.status: creating test/Makefile\r\nconfig.status: creating config.h\r\nconfig.status: executing depfiles commands\r\nconfig.status: executing libtool commands\r\n@nix { \"action\": \"setPhase\", \"phase\": \"buildPhase\" }\r\nbuilding\r\nbuild flags: SHELL=/nix/store/b0q4wjdw6xwhfsqy8ab106cmhn5xrr8p-bash-5.1-p12/bin/bash\r\nmake all-recursive\r\nmake[1]: Entering directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4'\r\nMaking all in include\r\nmake[2]: Entering directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/include'\r\nmake[2]: Nothing to be done for 'all'.\r\nmake[2]: Leaving directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/include'\r\nMaking all in man\r\nmake[2]: Entering directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/man'\r\nmake[2]: Nothing to be done for 'all'.\r\nmake[2]: Leaving directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/man'\r\nMaking all in src\r\nmake[2]: Entering directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/src'\r\nmake all-am\r\nmake[3]: Entering directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/src'\r\n CC md2.lo\r\n CC md4.lo\r\n CC md5.lo\r\n CC rmd160.lo\r\n CC sha1.lo\r\n CC sha2.lo\r\n\u001b[1msha2.c:819:1: \u001b[0m\u001b[0;1;31merror: \u001b[0m\u001b[1maliases are not supported on darwin\u001b[0m\r\nlibmd_alias(SHA384Transform, SHA512Transform);\r\n\u001b[0;1;32m^\r\n\u001b[0m\u001b[1m./local-link.h:44:47: \u001b[0m\u001b[0;1;30mnote: \u001b[0mexpanded from macro 'libmd_alias'\u001b[0m\r\n extern __typeof(symbol) alias __attribute__((__alias__(#symbol)))\r\n\u001b[0;1;32m ^\r\n\u001b[0m\u001b[1msha2.c:820:1: \u001b[0m\u001b[0;1;31merror: \u001b[0m\u001b[1maliases are not supported on darwin\u001b[0m\r\nlibmd_alias(SHA384Update, SHA512Update);\r\n\u001b[0;1;32m^\r\n\u001b[0m\u001b[1m./local-link.h:44:47: \u001b[0m\u001b[0;1;30mnote: \u001b[0mexpanded from macro 'libmd_alias'\u001b[0m\r\n extern __typeof(symbol) alias __attribute__((__alias__(#symbol)))\r\n\u001b[0;1;32m ^\r\n\u001b[0m\u001b[1msha2.c:821:1: \u001b[0m\u001b[0;1;31merror: \u001b[0m\u001b[1maliases are not supported on darwin\u001b[0m\r\nlibmd_alias(SHA384Pad, SHA512Pad);\r\n\u001b[0;1;32m^\r\n\u001b[0m\u001b[1m./local-link.h:44:47: \u001b[0m\u001b[0;1;30mnote: \u001b[0mexpanded from macro 'libmd_alias'\u001b[0m\r\n extern __typeof(symbol) alias __attribute__((__alias__(#symbol)))\r\n\u001b[0;1;32m ^\r\n\u001b[0m3 errors generated.\r\nmake[3]: *** [Makefile:523: sha2.lo] Error 1\r\nmake[3]: Leaving directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/src'\r\nmake[2]: *** [Makefile:403: all] Error 2\r\nmake[2]: Leaving directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4/src'\r\nmake[1]: *** [Makefile:411: all-recursive] Error 1\r\nmake[1]: Leaving directory '/private/tmp/nix-build-libmd-1.0.4.drv-0/libmd-1.0.4'\r\nmake: *** [Makefile:343: all] Error 2\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@primeos @matthewbauer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"darwin, nixpkgs-22.05pre346086.e5a50e8f299\"`\r\n - channels(armstrong): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155970/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155947","id":1109777033,"node_id":"I_kwDOAEVQ_M5CJdqJ","number":155947,"title":"Bazel fails at runtime when building TensorFlow with custom Nix store prefix","user":{"login":"gbpdt","id":25106405,"node_id":"MDQ6VXNlcjI1MTA2NDA1","avatar_url":"https://avatars.githubusercontent.com/u/25106405?v=4","gravatar_id":"","url":"https://api.github.com/users/gbpdt","html_url":"https://github.com/gbpdt","followers_url":"https://api.github.com/users/gbpdt/followers","following_url":"https://api.github.com/users/gbpdt/following{/other_user}","gists_url":"https://api.github.com/users/gbpdt/gists{/gist_id}","starred_url":"https://api.github.com/users/gbpdt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/gbpdt/subscriptions","organizations_url":"https://api.github.com/users/gbpdt/orgs","repos_url":"https://api.github.com/users/gbpdt/repos","events_url":"https://api.github.com/users/gbpdt/events{/privacy}","received_events_url":"https://api.github.com/users/gbpdt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-20T21:20:08Z","updated_at":"2022-01-20T22:25:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWe use custom Nix store prefixes, and have found that our Nix-built Bazel 3 fails at runtime when building TensorFlow in the Nix sandbox. The error is:\r\n\r\n```\r\nFATAL: Could not find system javabase. Ensure JAVA_HOME is set, or javac is on your PATH.\r\n```\r\n\r\nThe same Bazel binary works outside the sandbox and with different Nix store prefixes (including /nix and others). This is presumably why the problem has not been noticed before.\r\n\r\nAfter some investigation, we have tracked the issue down to Bazel not finding the Nix-generated bazel-rc file in the sandbox. The bazel-rc file path is added via Nix-specific patch, and is used to override the `--server_javabase` flag to point to Java. When Bazel runs in the sandbox, the path is not included, and Bazel falls back on other logic to find the rc file (which fails), and it therefore continues with default settings and fails to find Java. Outside the sandbox the path is visible (as long as it's not GCed, I suppose!) and so Bazel works. Inspecting the bazel output store path with `nix-store -q --references` shows the bazel-rc path is missing from the broken case and present in a working case. \r\n\r\nAfter further investigation, we have found this to be caused by GCC optimisations applied to the string literal containing the path to the bazel-rc file, leading it to be truncated within the binary. Usually this does not matter since the hash part of the path (which is what Nix scans for) is intact. However in the case of one of the store prefixes we are using, the string is truncated in such a way that the hash part is missing the last two characters. This means that the dependency scan fails to find it, and the bazel-rc store path is not added as a reference to the bazel output. I have included some detail below on the optimisation which causes this failure. Note that the binary still 'knows' the full path to the bazel-rc, it's just not a contiguous ASCII string in the binary. \r\n\r\n### Steps To Reproduce\r\nSteps to demonstrate the issue with regular NixOS 21.11:\r\n1. `nix-build -A pkgs.python3Packages.bazel_3`, producing (for example) `/nix/store/01wbznph6q7dyh17nrzc0psdpriksrl4-bazel-3.7.2`\r\n2. Find the bazel-rc path\r\n ```\r\n nix-store -q --requisites /nix/store/01wbznph6q7dyh17nrzc0psdpriksrl4-bazel-3.7.2 | grep bazel-rc\r\n /nix/store/3ysisg4r89zv7ig25l2q3k3g0bjxx3k7-bazel-rc\r\n ```\r\n3. Look for the hash in the binary\r\n ```\r\n strings /nix/store/01wbznph6q7dyh17nrzc0psdpriksrl4-bazel-3.7.2/bin/bazel-3.7.2-linux-x86_64 | grep 3ysisg4r89zv7ig25l2q3k3g0bjxx3k7 \r\n src/main/cpp/blaexit_code_to_use[0:0:0:0:0:0:0:1src/main/cpp/bazel_startup_optio/nix/store/3ysisg4r89zv7ig25l2q3k3g0bjxx3k7-bazesrc/main/cpp/option_processor.cc--rc_source=clie--default_override=0:common=--emignore_all_rc_fisrc/main/cpp/rc_embedded_tools/jsrc/main/cpp/staon the command l--incompatible_enable_execution_--noincompatible_enable_executiojavalog.properti-Dcom.google.devtools.build.lib.util.LogHandlerQuerier.class=com.google.devtools.build.lib.util.SimpleLogHandleroutput_user_rootfailure_detail_ocom.google.devtools.build.lib.util.SingleLineForbatch_cpu_scheduexpand_configs_ifatal_event_bus_idle_server_taskincompatible_enable_execution_trshutdown_on_low_unlimit_coredumpwrite_command_lowindows_enable_sconnect_timeout_unix_digest_hashhost_jvm_profileinvocation_policze_util_posix.cccouldn't create Failed to write ze_util_linux.ccserver/server.stserver.starttimeCouldn't initialize byte buffer grpc.default_compression_algoritgrpc.grpclb_fallgrpc.max_receivegrpc.max_send_megrpc.resource_qugrpc.primary_usegrpc.lb_policy_ngrpc.service_con\r\n```\r\n Note the string specifying the bazel-rc path is truncated in the binary (`/nix/store/3ysisg4r89zv7ig25l2q3k3g0bjxx3k7-baze`, missing the trailing `l-rc`). In this case it doesn't cause a problem since the hash is still intact.\r\n \r\nSteps to reproduce the actual failure:\r\n1. Build a Nix with a custom prefix. `/x/yyy/zzzz` reproduces the problem (but many others do not, including some longer paths!).\r\n2. Build `pkgs.python3Packages.tensorflow` with the sandbox enabled. This fails to run bazel with the above error.\r\n3. If you inspect the bazel binary being used, searching for `/x/yyy/zzzz` using `strings` as above, you'll find the path is truncated: `/x/yyy/zzzz/store/ldg7np1ajgknzx38bhzlbdbr3z7a6d` vs `/x/yyy/zzzz/store/ldg7np1ajgknzx38bhzlbdbr3z7a6dzd-bazel-rc`. In this case, the last two characters of the hash are missing, which means the dependency scan fails to pick the dependency up.\r\n\r\nWe are hitting this problem using nixpkgs 21.05 and Nix 2.3.11, but I have verified the same issue affects Tensorflow+Bazel on NixOS 21.11 (it just doesn't cause a failure). bazel_4 is affected similarly to bazel_3.\r\n\r\nWe have a patch to manually add the dependency to work around the issue, which I'll submit in a pull request. However it should be noted that this problem could potentially affect _any_ Nix-built C++ binary with the right flags and an 'unlucky' prefix. Unfortunately we're not away of a general overall fix for this, aside from patching individual package expressions.\r\n\r\n### Expected behavior\r\nOne would expect the reference to be picked up from the path embedded in the binary, and bazel to run correctly both in and out of the sandbox.\r\n\r\n### Additional context\r\nThe following program can be used to reproduce the problem with just GCC:\r\n\r\n```\r\n#include <iostream> \r\n#include <string> \r\n \r\nstruct Foo { \r\n Foo() : x(\"/x/yyy/zzzz/store/ldg7np1ajgknzx38bhzlbdbr3z7a6dzd-bazel-rc\") {}\r\n std::string x; \r\n}; \r\n \r\nint main() \r\n{ \r\n const Foo foo; \r\n std::cout << \"FOO: \" << foo.x << std::endl; \r\n} \r\n```\r\n\r\nThe failure can be reproduced with this (using GCC 10):\r\n\r\n```\r\ng++ -std=c++17 -O2 string_test.cpp\r\nstrings a.out | grep '/x/yyy/zzzz.*bazel-rc' >/dev/null && echo succeeded || echo failed\r\n```\r\n\r\nWe investigated the generated assembler, and (briefly) the code uses SSE instructions to load 16-byte chunks of the string literal into memory (which is presumably why the string is truncated to 48 characters). The remaining characters are loaded directly as constants in the code, hence they are not contiguous with the rest of the string in the binary.\r\n\r\nThe circumstances under which GCC applies the optimisation appears to vary by version and flags, but with GCC 10 we see it using -O2 and C++17 and later. GCC 8 seems to apply it for earlier std versions. SSE instructions are presumably required (default on x86-64).\r\n\r\n### Notify maintainers\r\n@mboes @Profpatsch \r\n@NixOS/bazel","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155947/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155914","id":1109577468,"node_id":"I_kwDOAEVQ_M5CIs78","number":155914,"title":"Weird neovim runtimepath for custom runtime","user":{"login":"Garmelon","id":11077553,"node_id":"MDQ6VXNlcjExMDc3NTUz","avatar_url":"https://avatars.githubusercontent.com/u/11077553?v=4","gravatar_id":"","url":"https://api.github.com/users/Garmelon","html_url":"https://github.com/Garmelon","followers_url":"https://api.github.com/users/Garmelon/followers","following_url":"https://api.github.com/users/Garmelon/following{/other_user}","gists_url":"https://api.github.com/users/Garmelon/gists{/gist_id}","starred_url":"https://api.github.com/users/Garmelon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Garmelon/subscriptions","organizations_url":"https://api.github.com/users/Garmelon/orgs","repos_url":"https://api.github.com/users/Garmelon/repos","events_url":"https://api.github.com/users/Garmelon/events{/privacy}","received_events_url":"https://api.github.com/users/Garmelon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-20T17:29:51Z","updated_at":"2022-01-20T17:29:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nHere https://github.com/NixOS/nixpkgs/blob/b4797eaffc45f360849067549c709295f0c0c1d2/nixos/modules/programs/neovim.nix#L161 the runtimepath is set to `${runtime}/etc`, which means that this example https://github.com/NixOS/nixpkgs/blob/b4797eaffc45f360849067549c709295f0c0c1d2/nixos/modules/programs/neovim.nix#L98 doesn't work since it places the files at `${runtime}/ftplugin/c.vim`, not `${runtime}/etc/ftplugin/c.vim`.\r\n\r\nI don't know why the `/etc` is there, so I'm hesitant to submit a PR removing it.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set `programs.neovim.runtime.\"ftplugin/c.vim\".text` to make some filetype-specific changes\r\n2. `nixos-rebuild switch`\r\n3. Open a c file and observe that the changes from 1. have no effect\r\n4. Instead set `programs.neovim.runtime.\"etc/ftplugin/c.vim\".text`\r\n5. `nixos-rebuild switch`\r\n6. Open a c file and observe that the changes from 4. are now in effect\r\n\r\n### Expected behavior\r\nIn step 3, the changes from 1 are in effect.\r\n\r\nAlternatively, the documentation and example of `programs.neovim.runtime` are updated to clarify this behaviour.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@teto\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.91, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre346004.5aaed40d22f, home-manager\"`\r\n - channels(joscha): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155914/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155902","id":1109519165,"node_id":"I_kwDOAEVQ_M5CIes9","number":155902,"title":"DingTalk messenger","user":{"login":"AleXoundOS","id":464913,"node_id":"MDQ6VXNlcjQ2NDkxMw==","avatar_url":"https://avatars.githubusercontent.com/u/464913?v=4","gravatar_id":"","url":"https://api.github.com/users/AleXoundOS","html_url":"https://github.com/AleXoundOS","followers_url":"https://api.github.com/users/AleXoundOS/followers","following_url":"https://api.github.com/users/AleXoundOS/following{/other_user}","gists_url":"https://api.github.com/users/AleXoundOS/gists{/gist_id}","starred_url":"https://api.github.com/users/AleXoundOS/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AleXoundOS/subscriptions","organizations_url":"https://api.github.com/users/AleXoundOS/orgs","repos_url":"https://api.github.com/users/AleXoundOS/repos","events_url":"https://api.github.com/users/AleXoundOS/events{/privacy}","received_events_url":"https://api.github.com/users/AleXoundOS/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-20T16:33:14Z","updated_at":"2022-01-30T23:10:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n[DingTalk](https://en.wikipedia.org/wiki/DingTalk) is a messenger similar to WeChat used in many Asian countries. Some Chinese companies provide support service for their products with the help of it.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: www.dingtalk.com\r\n* source URL: https://github.com/nashaofu/dingtalk\r\n* license: [MIT](https://github.com/nashaofu/dingtalk/blob/master/LICENSE)\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155902/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155851","id":1109164093,"node_id":"I_kwDOAEVQ_M5CHIA9","number":155851,"title":"Proposing another implementation of lisp-modules","user":{"login":"Uthar","id":15697697,"node_id":"MDQ6VXNlcjE1Njk3Njk3","avatar_url":"https://avatars.githubusercontent.com/u/15697697?v=4","gravatar_id":"","url":"https://api.github.com/users/Uthar","html_url":"https://github.com/Uthar","followers_url":"https://api.github.com/users/Uthar/followers","following_url":"https://api.github.com/users/Uthar/following{/other_user}","gists_url":"https://api.github.com/users/Uthar/gists{/gist_id}","starred_url":"https://api.github.com/users/Uthar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Uthar/subscriptions","organizations_url":"https://api.github.com/users/Uthar/orgs","repos_url":"https://api.github.com/users/Uthar/repos","events_url":"https://api.github.com/users/Uthar/events{/privacy}","received_events_url":"https://api.github.com/users/Uthar/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"7c6f434c","id":1891350,"node_id":"MDQ6VXNlcjE4OTEzNTA=","avatar_url":"https://avatars.githubusercontent.com/u/1891350?v=4","gravatar_id":"","url":"https://api.github.com/users/7c6f434c","html_url":"https://github.com/7c6f434c","followers_url":"https://api.github.com/users/7c6f434c/followers","following_url":"https://api.github.com/users/7c6f434c/following{/other_user}","gists_url":"https://api.github.com/users/7c6f434c/gists{/gist_id}","starred_url":"https://api.github.com/users/7c6f434c/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/7c6f434c/subscriptions","organizations_url":"https://api.github.com/users/7c6f434c/orgs","repos_url":"https://api.github.com/users/7c6f434c/repos","events_url":"https://api.github.com/users/7c6f434c/events{/privacy}","received_events_url":"https://api.github.com/users/7c6f434c/received_events","type":"User","site_admin":false},"assignees":[{"login":"7c6f434c","id":1891350,"node_id":"MDQ6VXNlcjE4OTEzNTA=","avatar_url":"https://avatars.githubusercontent.com/u/1891350?v=4","gravatar_id":"","url":"https://api.github.com/users/7c6f434c","html_url":"https://github.com/7c6f434c","followers_url":"https://api.github.com/users/7c6f434c/followers","following_url":"https://api.github.com/users/7c6f434c/following{/other_user}","gists_url":"https://api.github.com/users/7c6f434c/gists{/gist_id}","starred_url":"https://api.github.com/users/7c6f434c/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/7c6f434c/subscriptions","organizations_url":"https://api.github.com/users/7c6f434c/orgs","repos_url":"https://api.github.com/users/7c6f434c/repos","events_url":"https://api.github.com/users/7c6f434c/events{/privacy}","received_events_url":"https://api.github.com/users/7c6f434c/received_events","type":"User","site_admin":false}],"milestone":null,"comments":52,"created_at":"2022-01-20T11:07:24Z","updated_at":"2022-04-29T20:07:01Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Hi!\r\n\r\nI made a small [nix library](https://github.com/uthar/nix-cl) (`nix-cl`), for working with ASDF and Quicklisp, which has been working great for me recently. The code is still a mess but I want to show it to you and see if it sparks interest. \r\n\r\nBasically I think it could replace the current `lisp-modules` and provide a number of benefits.\r\n\r\nIf you'd like to test it out you should use `direnv` or source `.envrc` to get the examples working. (Have to set NIX_PATH). \r\n(Also worth noting, I think that `nixpkgs` doesn't provide Clasp but it worked with my own version.)\r\n\r\nI had these problems with `lisp-modules` - please correct me if I'm wrong here:\r\n\r\n- Had to read the source to find how to run a lisp wrapper (`common-lisp.sh`) - no documentation\r\n- It leaks FASL's into `$HOME` #142604\r\n- Hard to work with Quicklisp (have to build everything ahead of time, which is slow): #150941\r\n- CFFI doesn't work on ABCL (the one library that I know of which requires a `.jar` in the `CLASSPATH`)\r\n- Can't have multiple lisps in one `nix-shell` because a lisp-with-packages is achieved by putting the libraries themselves in `buildInputs` and running the generic `common-lisp.sh`\r\n- Doesn't support ASDF systems where `.asd` is **not** in the root directory (e.g. [jzon](https://github.com/Zulu-Inuoe/jzon))\r\n\r\nWhich are improved in `nix-cl`:\r\n- Has some documentation on how to run a `${lisp}WithPackages`\r\n- `CL_SOURCE_REGISTRY`, `ASDF_OUTPUT_TRANSLATIONS` are set in a granular way, per package\r\n- It generates nix expressions for **everything** in quicklisp, which works well because of Nix's laziness. One can then just pick what they want from that.\r\n- Can declare Java libraries for ABCL\r\n- `abclWithPackages`/`cclWithPackages`/`eclWithPackages`/`sbclWithPackages` etc. makes it possible to have multiple lisps in one `nix-shell`\r\n- Works for `asd`'s not in root by using \"//\" suffix to CL_SOURCE_REGISTRY (cool feature of ASDF - [manual](https://asdf.common-lisp.dev/asdf/Shell_002dfriendly-syntax-for-configuration.html#Shell_002dfriendly-syntax-for-configuration))\r\n- Easy to package things not in quicklisp. Minimal package is `pname`,`version`,`src`.\r\n\r\nThere are issues with it still where I haven't had the need to fix them:\r\n- CLASSPATH handling assumes `/share/java/*.jar` (from `fetchMavenArtifact`)\r\n- Haven't handled the case where the manually defined packages could use the quicklisp-imported ones as dependencies (worked around by just copying the code to manual packages)\r\n- Java jars are included unnecessarily in non-java lisp wrappers\r\n- Weird prefix for libs beginning with a number (e.g. `_3d-vectors`)\r\n\r\n@7c6f434c \r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155851/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155837","id":1109090476,"node_id":"I_kwDOAEVQ_M5CG2Cs","number":155837,"title":"pcre fails to build for armv6","user":{"login":"jyooru","id":63786778,"node_id":"MDQ6VXNlcjYzNzg2Nzc4","avatar_url":"https://avatars.githubusercontent.com/u/63786778?v=4","gravatar_id":"","url":"https://api.github.com/users/jyooru","html_url":"https://github.com/jyooru","followers_url":"https://api.github.com/users/jyooru/followers","following_url":"https://api.github.com/users/jyooru/following{/other_user}","gists_url":"https://api.github.com/users/jyooru/gists{/gist_id}","starred_url":"https://api.github.com/users/jyooru/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jyooru/subscriptions","organizations_url":"https://api.github.com/users/jyooru/orgs","repos_url":"https://api.github.com/users/jyooru/repos","events_url":"https://api.github.com/users/jyooru/events{/privacy}","received_events_url":"https://api.github.com/users/jyooru/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":443329087,"node_id":"MDU6TGFiZWw0NDMzMjkwODc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20cross-compilation","name":"6.topic: cross-compilation","color":"fef2c0","default":false,"description":"Building packages on a different sort platform than than they will be run on"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-20T09:56:01Z","updated_at":"2022-03-20T13:12:33Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\npcre fails to build on armv6\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `boot.binfmt.emulatedSystems = [ \"armv6l-linux\" ];`\r\n2. Build pcre for armv6\r\n3. pcre fails to build\r\n\r\n### Expected behavior\r\nA clear and concise description of what you expected to happen.\r\n\r\npcre successfully builds\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n[Log for `9gkfna81nf7mlhndid9h57945nlw6jxq-pcre-8.45.drv`](https://hercules-ci.com/accounts/github/jyooru/derivations/%2Fnix%2Fstore%2F9gkfna81nf7mlhndid9h57945nlw6jxq-pcre-8.45.drv/log?via-job=9a68e29f-7c98-4ce3-adf8-4f54c5e8117d)\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n> If in doubt, check `git blame` for whoever last touched something.\r\n\r\n@zowoq b17d08bf5cb612620d022a53219f99c85a45974a #149736\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.90, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(joel): `\"\"`\r\n - channels(root): `\"nixos-21.05\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155837/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155822","id":1109021915,"node_id":"I_kwDOAEVQ_M5CGlTb","number":155822,"title":"add crowdsec packages (agents and bouncer)","user":{"login":"amaumene","id":2414933,"node_id":"MDQ6VXNlcjI0MTQ5MzM=","avatar_url":"https://avatars.githubusercontent.com/u/2414933?v=4","gravatar_id":"","url":"https://api.github.com/users/amaumene","html_url":"https://github.com/amaumene","followers_url":"https://api.github.com/users/amaumene/followers","following_url":"https://api.github.com/users/amaumene/following{/other_user}","gists_url":"https://api.github.com/users/amaumene/gists{/gist_id}","starred_url":"https://api.github.com/users/amaumene/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/amaumene/subscriptions","organizations_url":"https://api.github.com/users/amaumene/orgs","repos_url":"https://api.github.com/users/amaumene/repos","events_url":"https://api.github.com/users/amaumene/events{/privacy}","received_events_url":"https://api.github.com/users/amaumene/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-20T08:47:38Z","updated_at":"2022-03-02T19:21:38Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nCrowdSec - the open-source and participative IPS able to analyze visitor behavior & provide an adapted response to all kinds of attacks. It also leverages the crowd power to generate a global CTI database to protect the user network.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://crowdsec.net\r\n* source URL: https://github.com/crowdsecurity/crowdsec \r\n* license: mit\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155822/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155752","id":1108639404,"node_id":"I_kwDOAEVQ_M5CFH6s","number":155752,"title":"convert single R package DESCRIPTION into a nix derivation","user":{"login":"teto","id":886074,"node_id":"MDQ6VXNlcjg4NjA3NA==","avatar_url":"https://avatars.githubusercontent.com/u/886074?v=4","gravatar_id":"","url":"https://api.github.com/users/teto","html_url":"https://github.com/teto","followers_url":"https://api.github.com/users/teto/followers","following_url":"https://api.github.com/users/teto/following{/other_user}","gists_url":"https://api.github.com/users/teto/gists{/gist_id}","starred_url":"https://api.github.com/users/teto/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/teto/subscriptions","organizations_url":"https://api.github.com/users/teto/orgs","repos_url":"https://api.github.com/users/teto/repos","events_url":"https://api.github.com/users/teto/events{/privacy}","received_events_url":"https://api.github.com/users/teto/received_events","type":"User","site_admin":false},"labels":[{"id":3238826511,"node_id":"MDU6TGFiZWwzMjM4ODI2NTEx","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20R","name":"6.topic: R","color":"FEF2C0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-19T22:53:27Z","updated_at":"2022-01-20T17:15:25Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"## Issue description\r\n\r\n\r\npkgs/development/r-modules/generate-r-packages.R can generate R packages from a preset list of packages.\r\nI would like to convert a single R package (closed source) into a nix derivation. \r\nI dont think the previous script does it, could it be changed to do that ? For instance by passing the path to a package or a local list that contains such paths ?\r\n\r\nIt's a single package so it can be done manually but I would rather automate it to avoid adjusting it on the next update.\r\n\r\nccing the 2 latest committers @jbedo @TikhonJelvis since I dont know R. \r\n\r\n### Steps to reproduce\r\n\r\n\r\n\r\n## Technical details\r\n\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155752/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155722","id":1108567199,"node_id":"I_kwDOAEVQ_M5CE2Sf","number":155722,"title":"haskell-updates: ld.gold error with unreadable /lib on aarch64-linux aka nix-on-droid","user":{"login":"573","id":123878,"node_id":"MDQ6VXNlcjEyMzg3OA==","avatar_url":"https://avatars.githubusercontent.com/u/123878?v=4","gravatar_id":"","url":"https://api.github.com/users/573","html_url":"https://github.com/573","followers_url":"https://api.github.com/users/573/followers","following_url":"https://api.github.com/users/573/following{/other_user}","gists_url":"https://api.github.com/users/573/gists{/gist_id}","starred_url":"https://api.github.com/users/573/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/573/subscriptions","organizations_url":"https://api.github.com/users/573/orgs","repos_url":"https://api.github.com/users/573/repos","events_url":"https://api.github.com/users/573/events{/privacy}","received_events_url":"https://api.github.com/users/573/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-19T21:13:44Z","updated_at":"2022-02-05T21:29:52Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nLinking of sample project fails:\r\n>Preprocessing executable 'main' for test-0.0.0..\r\nBuilding executable 'main' for test-0.0.0..\r\nLinking /data/data/com.termux.nix/files/home/easy-hls-nix/test/dist-newstyle/build/aarch64-linux/ghc-8.10.7/test-0.0.0/x/main/build/main/main ...\r\n/nix/store/l59232a9b5dlip8yi3swyx7km3s35hzj-binutils-2.35.2/bin/ld.gold: error: /lib: can not read directory: Permission denied\r\ncollect2: error: ld returned 1 exit status\r\n `cc' failed in phase `Linker'. (Exit code: 1)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Build https://github.com/573/aarch64-linux-ld-issue155722-reproduce on master using `nix-build` or `cabal build`, in fact github-actions do that\r\n\r\n### Expected behavior\r\nSample project builds.\r\nThe linker should be called with a fallback instead of `/lib` when `/lib` exists but is not readable.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nSimilar issue https://github.com/nmattia/niv/issues/332.\r\nhttps://github.com/t184256/nix-on-droid/, the system on which this error occurs has no read permissions on `/lib`.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"aarch64-linux\"`\r\n- host os: `Linux 4.4.111-21427293`\r\n- multi-user?: `no`\r\n- sandbox: `no`\r\n- version: `nix-env (Nix) 2.3.15`\r\n- channels(nix-on-droid): `\"nix-on-droid-21.05, nixpkgs-21.05.2796.110a2c9ebbf\"`\r\n- nixpkgs: `/nix/store/h7lizyjgzjmpj4pc18jxib40s0p8lns5-e49c2d09f8dbf84c6692baef7951518ed398e0e6.tar.gz`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155722/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155706","id":1108459903,"node_id":"I_kwDOAEVQ_M5CEcF_","number":155706,"title":"mkShell broken when no nixpkgs flake or in NIX_PATH, and system's bash < 4.4","user":{"login":"bew","id":9730330,"node_id":"MDQ6VXNlcjk3MzAzMzA=","avatar_url":"https://avatars.githubusercontent.com/u/9730330?v=4","gravatar_id":"","url":"https://api.github.com/users/bew","html_url":"https://github.com/bew","followers_url":"https://api.github.com/users/bew/followers","following_url":"https://api.github.com/users/bew/following{/other_user}","gists_url":"https://api.github.com/users/bew/gists{/gist_id}","starred_url":"https://api.github.com/users/bew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bew/subscriptions","organizations_url":"https://api.github.com/users/bew/orgs","repos_url":"https://api.github.com/users/bew/repos","events_url":"https://api.github.com/users/bew/events{/privacy}","received_events_url":"https://api.github.com/users/bew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-01-19T19:09:40Z","updated_at":"2022-01-23T14:46:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nOn a non-NixOS distrib, when there is no `nixpkgs` in the flake registry or in `$NIX_PATH`, `nix-shell` falls back to the `bash` in the system.\r\n\r\nWhen the bash version is 4 (like on CentOS7), I get the error: `bash: shopt: inherit_errexit: invalid shell option name`\r\n(see reproduction steps for more)\r\n\r\nNOTE: I removed `nixpkgs` from the registry to always ensure I use my pinned version, and I have full control on where my packages comes from. No hidden global state!\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Write a simple `mkShell` invocation:\r\n\r\n In a file `foo.nix`:\r\n ```nix\r\n let\r\n nixpkgs = builtins.getFlake \"pkgs\"; # this is the name of my own nixpkgs flake, pinned appropriately\r\n pkgs = nixpkgs.legacyPackages.x86_64-linux;\r\n in pkgs.mkShell {\r\n packages = [\r\n pkgs.just\r\n ];\r\n }\r\n ```\r\n\r\n2. Running `nix-shell foo.nix` I get:\r\n ```console\r\n $ nix-shell foo.nix\r\n error: file 'nixpkgs' was not found in the Nix search path (add it using $NIX_PATH or -I)\r\n \r\n at «string»:1:9:\r\n \r\n 1| (import <nixpkgs> {}).bashInteractive\r\n | ^\r\n will use bash from your environment\r\n \r\n bash: shopt: inherit_errexit: invalid shell option name\r\n ```\r\n\r\n3. => I'm back to my initial shell, It didn't enter the nix-shell.\r\n\r\n### Expected behavior\r\nEnter the nix-shell without error!\r\n\r\n### Additional context: bash version\r\n```console\r\n$ bash --version # binary is in /usr/bin/bash\r\nGNU bash, version 4.2.46(2)-release (x86_64-redhat-linux-gnu)\r\nCopyright (C) 2011 Free Software Foundation, Inc.\r\nLicense GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>\r\n...\r\n```\r\n\r\n### Additional context: PR introducing the failing option\r\n\r\nThe `inherit_errexit` shell option was added in #139508.\r\n\r\nIt's set unconditionally:\r\nhttps://github.com/NixOS/nixpkgs/blob/82500ee3bc3f8c36a7f95bd9b8a076139ab1039d/pkgs/stdenv/generic/setup.sh#L3-L9\r\nAnd proceeds to check the bash version is >= 4 just after.\r\n\r\nMy take would be to set this option only for bash version > 4. (or whatever version this was added in)\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\n$ NIX_PATH=nixpkgs=channel:nixos-21.11 nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 3.10.0-1160.2.2.el7.x86_64, CentOS Linux, 7 (Core)`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(cloud-user): `\"legacy-nixpkgs-channel-21.05.4116.46251a79f75, nixos-20.09-20.09.1884.80666202999\"`\r\n - nixpkgs: `/nix/store/2wlj55g2gppcgr2mzsvbblsapnsqp8kd-source`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155706/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155664","id":1108274146,"node_id":"I_kwDOAEVQ_M5CDuvi","number":155664,"title":"intel-ocl download URL no longer valid","user":{"login":"rileyinman","id":37246692,"node_id":"MDQ6VXNlcjM3MjQ2Njky","avatar_url":"https://avatars.githubusercontent.com/u/37246692?v=4","gravatar_id":"","url":"https://api.github.com/users/rileyinman","html_url":"https://github.com/rileyinman","followers_url":"https://api.github.com/users/rileyinman/followers","following_url":"https://api.github.com/users/rileyinman/following{/other_user}","gists_url":"https://api.github.com/users/rileyinman/gists{/gist_id}","starred_url":"https://api.github.com/users/rileyinman/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rileyinman/subscriptions","organizations_url":"https://api.github.com/users/rileyinman/orgs","repos_url":"https://api.github.com/users/rileyinman/repos","events_url":"https://api.github.com/users/rileyinman/events{/privacy}","received_events_url":"https://api.github.com/users/rileyinman/received_events","type":"User","site_admin":false},"labels":[{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-19T15:58:29Z","updated_at":"2022-04-26T11:33:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\nWhen attempting to upgrade my system, intel-ocl returns a 403 error. Trying to download the source URL manually confirms that it no longer exists on the intel site. I'm unsure how to go about finding the new direct download URL.\r\n\r\n### Steps to reproduce\r\nAttempt to build intel-ocl.\r\n\r\n## Technical details\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335376.610d4ea2750\"`\r\n - channels(riley): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664/reactions","total_count":6,"+1":6,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155664/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155642","id":1108132295,"node_id":"I_kwDOAEVQ_M5CDMHH","number":155642,"title":"broadcom-wl-dkms","user":{"login":"johnk1917","id":96326315,"node_id":"U_kgDOBb3Sqw","avatar_url":"https://avatars.githubusercontent.com/u/96326315?v=4","gravatar_id":"","url":"https://api.github.com/users/johnk1917","html_url":"https://github.com/johnk1917","followers_url":"https://api.github.com/users/johnk1917/followers","following_url":"https://api.github.com/users/johnk1917/following{/other_user}","gists_url":"https://api.github.com/users/johnk1917/gists{/gist_id}","starred_url":"https://api.github.com/users/johnk1917/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/johnk1917/subscriptions","organizations_url":"https://api.github.com/users/johnk1917/orgs","repos_url":"https://api.github.com/users/johnk1917/repos","events_url":"https://api.github.com/users/johnk1917/events{/privacy}","received_events_url":"https://api.github.com/users/johnk1917/received_events","type":"User","site_admin":false},"labels":[{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-19T13:57:12Z","updated_at":"2022-01-21T21:54:28Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nThe broadcom-wl-dkms driver provides the wl module needed by BCM4xxx wifi chips, usually on Macbooks.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/UnitedRPMs/broadcom-wl-dkms\r\n* source URL: https://github.com/UnitedRPMs/broadcom-wl-dkms\r\n* license: mit, bsd, gpl2+ , ...\r\n* platforms: unix, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155642/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155629","id":1108072723,"node_id":"I_kwDOAEVQ_M5CC9kT","number":155629,"title":"gnupg 2.3.x update broke smartcard (Yubikey) support on Darwin","user":{"login":"mikroskeem","id":3490861,"node_id":"MDQ6VXNlcjM0OTA4NjE=","avatar_url":"https://avatars.githubusercontent.com/u/3490861?v=4","gravatar_id":"","url":"https://api.github.com/users/mikroskeem","html_url":"https://github.com/mikroskeem","followers_url":"https://api.github.com/users/mikroskeem/followers","following_url":"https://api.github.com/users/mikroskeem/following{/other_user}","gists_url":"https://api.github.com/users/mikroskeem/gists{/gist_id}","starred_url":"https://api.github.com/users/mikroskeem/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mikroskeem/subscriptions","organizations_url":"https://api.github.com/users/mikroskeem/orgs","repos_url":"https://api.github.com/users/mikroskeem/repos","events_url":"https://api.github.com/users/mikroskeem/events{/privacy}","received_events_url":"https://api.github.com/users/mikroskeem/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":10,"created_at":"2022-01-19T13:00:15Z","updated_at":"2022-03-21T23:55:27Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\ngnupg worked fine on 2.2.x; pinned nixpkgs-unstable to 0432195a4b8d68faaa7d3d4b355260a3120aeeae on my flake.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install gnupg from current nixpkgs-unstable, e.g rev d5dae6569ea9952f1ae4e727946d93a71c507821 & the usual `pkill gpg-agent`\r\n2. Try `gpg --card-status`\r\n3. See it break:\r\n\r\n```\r\n> gpg --card-status\r\ngpg: error reading symlink '/proc/curproc/file': No such file or directory\r\ngpg: selecting card failed: Operation not supported by device\r\ngpg: OpenPGP card not available: Operation not supported by device\r\n```\r\n\r\nWhen signing something, you should get pinentry asking you to insert the smartcard - re-plugging has no effect.\r\n\r\n### Expected behavior\r\n```\r\n> gpg --card-status\r\nReader ...........: Yubico YubiKey OTP FIDO CCID\r\n...\r\n```\r\n\r\n& signing work etc.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\n\r\n\r\n<details>\r\n<summary>gpg 2.3.x --version output</summary>\r\n\r\n```\r\n$ gpg --version\r\ngpg: error reading symlink '/proc/curproc/file': No such file or directory\r\ngpg (GnuPG) 2.3.3\r\nlibgcrypt 1.9.4\r\nCopyright (C) 2021 Free Software Foundation, Inc.\r\nLicense GNU GPL-3.0-or-later <https://gnu.org/licenses/gpl.html>\r\nThis is free software: you are free to change and redistribute it.\r\nThere is NO WARRANTY, to the extent permitted by law.\r\n\r\nHome: /Users/mark/.gnupg\r\nSupported algorithms:\r\nPubkey: RSA, ELG, DSA, ECDH, ECDSA, EDDSA\r\nCipher: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH,\r\n CAMELLIA128, CAMELLIA192, CAMELLIA256\r\nAEAD: EAX, OCB\r\nHash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224\r\nCompression: Uncompressed, ZIP, ZLIB, BZIP2\r\n```\r\n\r\n</details>\r\n\r\n<details>\r\n<summary>gpg 2.2.x --version output</summary>\r\n\r\n```\r\ngpg (GnuPG) 2.2.27\r\nlibgcrypt 1.9.4\r\nCopyright (C) 2021 Free Software Foundation, Inc.\r\nLicense GNU GPL-3.0-or-later <https://gnu.org/licenses/gpl.html>\r\nThis is free software: you are free to change and redistribute it.\r\nThere is NO WARRANTY, to the extent permitted by law.\r\n\r\nHome: /Users/mark/.gnupg\r\nSupported algorithms:\r\nPubkey: RSA, ELG, DSA, ECDH, ECDSA, EDDSA\r\nCipher: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH,\r\n CAMELLIA128, CAMELLIA192, CAMELLIA256\r\nHash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224\r\nCompression: Uncompressed, ZIP, ZLIB, BZIP2\r\n```\r\n\r\n</details>\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@fpletz @vrthra \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n> nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(mark): `\"\"`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/nix/store/qcyrhggzysrnsm18kxhqy47wd6bvfk99-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155629/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155581","id":1107835290,"node_id":"I_kwDOAEVQ_M5CCDma","number":155581,"title":"existing `/etc/sub*id` incorrectly updated by `nixos-rebuild switch` when `users.users.*.subUidRanges` and `users.users.*.subGidRanges` are explicitly set","user":{"login":"ppenguin","id":17690377,"node_id":"MDQ6VXNlcjE3NjkwMzc3","avatar_url":"https://avatars.githubusercontent.com/u/17690377?v=4","gravatar_id":"","url":"https://api.github.com/users/ppenguin","html_url":"https://github.com/ppenguin","followers_url":"https://api.github.com/users/ppenguin/followers","following_url":"https://api.github.com/users/ppenguin/following{/other_user}","gists_url":"https://api.github.com/users/ppenguin/gists{/gist_id}","starred_url":"https://api.github.com/users/ppenguin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ppenguin/subscriptions","organizations_url":"https://api.github.com/users/ppenguin/orgs","repos_url":"https://api.github.com/users/ppenguin/repos","events_url":"https://api.github.com/users/ppenguin/events{/privacy}","received_events_url":"https://api.github.com/users/ppenguin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-19T09:07:13Z","updated_at":"2022-01-19T09:07:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n`/etc/subuid` and `/etc/subgid` are incorrectly updated by `nixos-rebuild switch` when `users.users.*.subUidRanges` and `users.users.*.subGidRanges` are explicitly set, which leads to users having multiple entries with different values in these files after a rebuild, ultimately leading to failing `podman` execution.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. observe pre-existing `/etc/sub*id` files with IDs defined for the \"normal users\" defined in `users.users.*`\r\n2. add definitions `users.users.*.sub*idRanges` for said users to enforce explicitly defined IDs also for new users\r\n3. `sudo nixos-rebuild switch`\r\n4. observe double entries for each defined user in `/etc/sub*id` with different IDs and failing userspace execution of `podman run`\r\n\r\n### Expected behavior\r\n\r\nDeclarative definition of `users.users.*.sub*idRanges` **replaces** corresponding values in `/etc/sub*id` instead of **adding** them\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.10, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"home-manager-21.11, musnix, nixos-21.11.335331.8a70a6808c8\"`\r\n - channels(mirko): `\"home-manager-21.11\"`\r\n - channels(bjoern): `\"home-manager-21.11\"`\r\n - channels(uemit): `\"home-manager-21.11\"`\r\n - channels(jeroen): `\"home-manager-21.11, unstable-22.05pre336340.cdaa4ce25b7\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155581/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155533","id":1107426619,"node_id":"I_kwDOAEVQ_M5CAf07","number":155533,"title":"Enable SimpleDRM in the kernel config","user":{"login":"ilya-fedin","id":17829319,"node_id":"MDQ6VXNlcjE3ODI5MzE5","avatar_url":"https://avatars.githubusercontent.com/u/17829319?v=4","gravatar_id":"","url":"https://api.github.com/users/ilya-fedin","html_url":"https://github.com/ilya-fedin","followers_url":"https://api.github.com/users/ilya-fedin/followers","following_url":"https://api.github.com/users/ilya-fedin/following{/other_user}","gists_url":"https://api.github.com/users/ilya-fedin/gists{/gist_id}","starred_url":"https://api.github.com/users/ilya-fedin/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ilya-fedin/subscriptions","organizations_url":"https://api.github.com/users/ilya-fedin/orgs","repos_url":"https://api.github.com/users/ilya-fedin/repos","events_url":"https://api.github.com/users/ilya-fedin/events{/privacy}","received_events_url":"https://api.github.com/users/ilya-fedin/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-18T22:30:24Z","updated_at":"2022-01-19T00:01:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThis is more a feature request, but I can't find a template to ask a feature change in build configuration for a package.\r\nThere's a new DRM driver in the kernel that replaces the framebuffer in case there's no vendor-provided driver. I was about to create a PR, but then I found a comment in common-config.nix that I should test my change by building kernels, this is not I can do though, so I create this issue and kindly ask to test this and apply if possible.\r\n```diff\r\ndiff --git a/pkgs/os-specific/linux/kernel/common-config.nix b/pkgs/os-specific/linux/kernel/common-config.nix\r\nindex 93c6b390eb2..4fc63580fa0 100644\r\n--- a/pkgs/os-specific/linux/kernel/common-config.nix\r\n+++ b/pkgs/os-specific/linux/kernel/common-config.nix\r\n@@ -237,7 +237,8 @@ let\r\n \r\n fb = {\r\n FB = yes;\r\n- FB_EFI = yes;\r\n+ FB_SIMPLE = whenAtLeast \"5.15\" no;\r\n+ FB_EFI = mkMerge [ (whenOlder \"5.15\" yes) (whenAtLeast \"5.15\" no) ];\r\n FB_NVIDIA_I2C = yes; # Enable DDC Support\r\n FB_RIVA_I2C = yes;\r\n FB_ATY_CT = yes; # Mach64 CT/VT/GT/LT (incl. 3D RAGE) support\r\n@@ -252,11 +253,12 @@ let\r\n FRAMEBUFFER_CONSOLE_DEFERRED_TAKEOVER = whenAtLeast \"4.19\" yes;\r\n FRAMEBUFFER_CONSOLE_ROTATION = yes;\r\n FB_GEODE = mkIf (stdenv.hostPlatform.system == \"i686-linux\") yes;\r\n- # On 5.14 this conflicts with FB_SIMPLE.\r\n- DRM_SIMPLEDRM = whenAtLeast \"5.14\" no;\r\n+ SYSFB_SIMPLEFB = whenAtLeast \"5.15\" yes;\r\n };\r\n \r\n video = {\r\n+ DRM = whenAtLeast \"5.15\" yes;\r\n+ DRM_SIMPLEDRM = mkMerge [ (whenBetween \"5.14\" \"5.15\" no) (whenAtLeast \"5.15\" yes) ];\r\n # Allow specifying custom EDID on the kernel command line\r\n DRM_LOAD_EDID_FIRMWARE = yes;\r\n VGA_SWITCHEROO = yes; # Hybrid graphics support\r\n@@ -926,7 +928,8 @@ let\r\n # Many ARM SBCs hand off a pre-configured framebuffer.\r\n # This always can can be replaced by the actual native driver.\r\n # Keeping it a built-in ensures it will be used if possible.\r\n- FB_SIMPLE = yes;\r\n+ # Since 5.15, SimpleDRM replaces the simple framebuffer.\r\n+ FB_SIMPLE = whenOlder \"5.15\" yes;\r\n \r\n } // optionalAttrs (versionAtLeast version \"5.4\" && (stdenv.hostPlatform.system == \"x86_64-linux\" || stdenv.hostPlatform.system == \"aarch64-linux\")) {\r\n # Required for various hardware features on Chrome OS devices\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Boot the system\r\n\r\n### Expected behavior\r\nSimpleDRM is active in the kernel and used rather than old framebuffer drivers\r\n\r\n### Notify maintainers\r\n@TredwellGit @ma27 @nequissimus @alyssais\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"nixos-22.05pre338578.a2e281f5770\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155533/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155516","id":1107324154,"node_id":"I_kwDOAEVQ_M5CAGz6","number":155516,"title":"Remove libraries relying on `use_2to3`","user":{"login":"mweinelt","id":131599,"node_id":"MDQ6VXNlcjEzMTU5OQ==","avatar_url":"https://avatars.githubusercontent.com/u/131599?v=4","gravatar_id":"","url":"https://api.github.com/users/mweinelt","html_url":"https://github.com/mweinelt","followers_url":"https://api.github.com/users/mweinelt/followers","following_url":"https://api.github.com/users/mweinelt/following{/other_user}","gists_url":"https://api.github.com/users/mweinelt/gists{/gist_id}","starred_url":"https://api.github.com/users/mweinelt/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mweinelt/subscriptions","organizations_url":"https://api.github.com/users/mweinelt/orgs","repos_url":"https://api.github.com/users/mweinelt/repos","events_url":"https://api.github.com/users/mweinelt/events{/privacy}","received_events_url":"https://api.github.com/users/mweinelt/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-18T20:17:11Z","updated_at":"2022-02-16T15:08:34Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"`use_2to3` was an automatic translation feature provided by setuptoos to convert python2 to python3 by running 2to3 during the build phase. Projects using it are in fact python2 projects and are mostly unmaintained and should be removed.\r\n\r\nThe feature itself was removed from setuptools in version 58, which is currently on python-unstable.\r\n\r\n## Affected packages and their direct dependencies.\r\n\r\nhttps://hydra.nixos.org/eval/1738807?filter=python39&compare=1738720&full=#tabs-now-fail\r\n\r\nCheck when removed or fixed.\r\n\r\n- [x] `anyjso`\r\n - [x] `python.pkgs.carrot`\r\n- [ ] `deap`\r\n - [ ] `python.pkgs.sklearn-deap`\r\n- [x] `demjson` (https://hydra.nixos.org/build/164886968/nixlog/1)\r\n - ~~`nixops`~~\r\n- [x] `hdlparse` (https://hydra.nixos.org/build/164903277/nixlog/1)\r\n- [x] `ipy`\r\n- [ ] `jsmin`\r\n- [ ] `keepalive` (https://hydra.nixos.org/build/164889231/nixlog/1)\r\n - [ ] `python.pkgs.sparqlwrapper`\r\n- [ ] `parameterizedtestcase` (https://hydra.nixos.org/build/164898488/nixlog/1)\r\n - [ ] `python.pkgs.smart-open`\r\n- [x] `parse-type` (https://hydra.nixos.org/build/164887997/nixlog/1)\r\n - [x] `python.pkgs.behave`\r\n - [x] `python.pkgs.pytest-bdd`\r\n - [x] `python.pkgs.radish-bdd`\r\n - [x] `python.pkgs.python-docx`\r\n- [ ] `pyvcf` @scalavision \r\n- [x] `pycallgraph` (https://hydra.nixos.org/build/164891698/nixlog/1)\r\n- [ ] `nose`\r\n- [x] `nose-cover`\r\n- [ ] `s3bro`\r\n- [ ] `suds-jurko` (https://hydra.nixos.org/build/164902920/nixlog/1)\r\n - [ ] `jira_cli`\r\n - [ ] `python.pkgs.suseapi`\r\n - [ ] `python.pkgstransip`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155516/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155490","id":1107062445,"node_id":"I_kwDOAEVQ_M5B_G6t","number":155490,"title":"Sioyek","user":{"login":"foo-dogsquared","id":34962634,"node_id":"MDQ6VXNlcjM0OTYyNjM0","avatar_url":"https://avatars.githubusercontent.com/u/34962634?v=4","gravatar_id":"","url":"https://api.github.com/users/foo-dogsquared","html_url":"https://github.com/foo-dogsquared","followers_url":"https://api.github.com/users/foo-dogsquared/followers","following_url":"https://api.github.com/users/foo-dogsquared/following{/other_user}","gists_url":"https://api.github.com/users/foo-dogsquared/gists{/gist_id}","starred_url":"https://api.github.com/users/foo-dogsquared/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/foo-dogsquared/subscriptions","organizations_url":"https://api.github.com/users/foo-dogsquared/orgs","repos_url":"https://api.github.com/users/foo-dogsquared/repos","events_url":"https://api.github.com/users/foo-dogsquared/events{/privacy}","received_events_url":"https://api.github.com/users/foo-dogsquared/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-18T15:44:43Z","updated_at":"2022-01-18T15:55:47Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nA PDF reader primarily aimed at researchers.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://sioyek.info/\r\n* source URL: https://github.com/ahrm/sioyek\r\n* license: gpl3\r\n* platforms: unix, linux, darwin, windows\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155490/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155485","id":1107014607,"node_id":"I_kwDOAEVQ_M5B-7PP","number":155485,"title":"During nixos-rebuild switch --upgrade: proc-sys-fs-binfmt_misc.mount is not active, cannot reload","user":{"login":"kaldonir","id":11463279,"node_id":"MDQ6VXNlcjExNDYzMjc5","avatar_url":"https://avatars.githubusercontent.com/u/11463279?v=4","gravatar_id":"","url":"https://api.github.com/users/kaldonir","html_url":"https://github.com/kaldonir","followers_url":"https://api.github.com/users/kaldonir/followers","following_url":"https://api.github.com/users/kaldonir/following{/other_user}","gists_url":"https://api.github.com/users/kaldonir/gists{/gist_id}","starred_url":"https://api.github.com/users/kaldonir/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kaldonir/subscriptions","organizations_url":"https://api.github.com/users/kaldonir/orgs","repos_url":"https://api.github.com/users/kaldonir/repos","events_url":"https://api.github.com/users/kaldonir/events{/privacy}","received_events_url":"https://api.github.com/users/kaldonir/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-18T15:03:28Z","updated_at":"2022-02-14T14:27:52Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nWhen a system's configuration includes `boot.binfmt.emulatedSystems`, during `nixos-rebuild switch --upgrade`, I sometimes encounter the error message `proc-sys-fs-binfmt_misc.mount is not active, cannot reload`. This seems to be benign, because the system still behaves as expected after the switch. Running `nixos-rebuild switch --upgrade` again doesn't encounter this error again and simply succeeds.\r\n\r\nIn particular, the affected systems contain these settings:\r\n```\r\n boot.binfmt.emulatedSystems = [ \"aarch64-linux\" \"armv7l-linux\" ];\r\n```\r\n\r\n### Steps To Reproduce\r\n\r\nI'm not sure how to reproduce it. This sometimes happens overnight in the `nixos-upgrade` systemd service, so I suppose some package update can trigger this.\r\n\r\n### Expected behavior\r\nI'm simply running `nixos-rebuild switch --upgrade` on a stable channel, so I don't expect this to cause errors like this. \r\n\r\n### Additional context\r\n\r\nExample logs of such a failing system activation in `nixos-upgrade`:\r\n\r\n```\r\nJan 17 04:41:05 my-host nixos[57842]: switching to system configuration /nix/store/kj7g6gw08hhrwc2ahhynsj1cyvmaw7q5-nixos-system-my-host-21.11.335288.3ddd960a3b5\r\nJan 17 04:41:05 my-host nixos-upgrade-start[57842]: stopping the following units: audit.service, chronyd.service, cpufreq.service, dehydrated.timer, dehydratedNginxReload.timer, dnsmasq.service, fstrim.timer, haveged.service, kmod-static-nodes.service, mount-pstore.service, network-local-commands.service, network-setup.service, nix-gc.timer, nix-optimise.timer, nixos-upgrade.timer, nscd.service, proc-sys-fs-binfmt_misc.automount, prometheus-node-exporter.service, resolvconf.service, systemd-binfmt.service, systemd-modules-load.service, systemd-sysctl.service, systemd-tmpfiles-clean.timer, systemd-tmpfiles-setup-dev.service, systemd-udev-trigger.service, systemd-udevd-control.socket, systemd-udevd-kernel.socket, systemd-udevd.service, systemd-vconsole-setup.service\r\nJan 17 04:41:05 my-host nixos-upgrade-start[57842]: NOT restarting the following changed units: getty@tty1.service, nixos-upgrade.service, systemd-fsck@dev-disk-by\\x2duuid-9F31\\x2d596F.service, systemd-journal-flush.service, systemd-logind.service, systemd-random-seed.service, systemd-remount-fs.service, systemd-tmpfiles-setup.service, systemd-update-utmp.service, systemd-user-sessions.service\r\nJan 17 04:41:05 my-host nixos-upgrade-start[57842]: activating the configuration...\r\nJan 17 04:41:05 my-host nixos-upgrade-start[57917]: setting up /etc...\r\nJan 17 04:41:06 my-host nixos-upgrade-start[57842]: restarting systemd...\r\nJan 17 04:41:06 my-host nixos-upgrade-start[57842]: setting up tmpfiles\r\nJan 17 04:41:06 my-host nixos-upgrade-start[57842]: reloading the following units: dbus.service, dev-hugepages.mount, dev-mqueue.mount, firewall.service, proc-sys-fs-binfmt_misc.mount, reload-systemd-vconsole-setup.service, sys-fs-fuse-connections.mount, sys-kernel-config.mount, sys-kernel-debug.mount\r\nJan 17 04:41:06 my-host nixos-upgrade-start[58097]: proc-sys-fs-binfmt_misc.mount is not active, cannot reload.\r\nJan 17 04:41:06 my-host nixos-upgrade-start[57842]: restarting the following units: network-addresses-enp4s0.service, nginx.service, sshd.service, systemd-journald.service\r\nJan 17 04:41:06 my-host nixos-upgrade-start[57842]: starting the following units: audit.service, chronyd.service, cpufreq.service, dehydrated.timer, dehydratedNginxReload.timer, dnsmasq.service, fstrim.timer, haveged.service, kmod-static-nodes.service, mount-pstore.service, network-local-commands.service, network-setup.service, nix-gc.timer, nix-optimise.timer, nixos-upgrade.timer, nscd.service, proc-sys-fs-binfmt_misc.automount, prometheus-node-exporter.service, resolvconf.service, systemd-binfmt.service, systemd-modules-load.service, systemd-sysctl.service, systemd-tmpfiles-clean.timer, systemd-tmpfiles-setup-dev.service, systemd-udev-trigger.service, systemd-udevd-control.socket, systemd-udevd-kernel.socket, systemd-vconsole-setup.service\r\nJan 17 04:41:07 my-host nixos-upgrade-start[57842]: the following new units were started: systemd-tmpfiles-clean.service\r\nJan 17 04:41:07 my-host nixos[57842]: switching to system configuration /nix/store/kj7g6gw08hhrwc2ahhynsj1cyvmaw7q5-nixos-system-my-host-21.11.335288.3ddd960a3b5 failed (status 4)\r\nJan 17 04:41:07 my-host nixos-upgrade-start[51748]: warning: error(s) occurred while switching to the new configuration\r\nJan 17 04:41:07 my-host systemd[1]: nixos-upgrade.service: Main process exited, code=exited, status=1/FAILURE\r\nJan 17 04:41:07 my-host systemd[1]: nixos-upgrade.service: Failed with result 'exit-code'.\r\nJan 17 04:41:07 my-host systemd[1]: Failed to start NixOS Upgrade.\r\nJan 17 04:41:07 my-host systemd[1]: nixos-upgrade.service: Consumed 2min 5.638s CPU time, received 400.9M IP traffic, sent 1.3M IP traffic.\r\nJan 18 04:40:12 my-host systemd[1]: Starting NixOS Upgrade...\r\nJan 18 04:40:13 my-host nixos-upgrade-start[59021]: building Nix...\r\nJan 18 04:40:14 my-host nixos-upgrade-start[59021]: building the system configuration...\r\nJan 18 04:40:19 my-host nixos[59158]: switching to system configuration /nix/store/kj7g6gw08hhrwc2ahhynsj1cyvmaw7q5-nixos-system-my-host-21.11.335288.3ddd960a3b5\r\nJan 18 04:40:19 my-host nixos-upgrade-start[59158]: activating the configuration...\r\nJan 18 04:40:19 my-host nixos-upgrade-start[59214]: setting up /etc...\r\nJan 18 04:40:20 my-host nixos-upgrade-start[59158]: setting up tmpfiles\r\nJan 18 04:40:20 my-host nixos[59158]: finished switching to system configuration /nix/store/kj7g6gw08hhrwc2ahhynsj1cyvmaw7q5-nixos-system-my-host-21.11.335288.3ddd960a3b5\r\nJan 18 04:40:20 my-host systemd[1]: nixos-upgrade.service: Deactivated successfully.\r\nJan 18 04:40:20 my-host systemd[1]: Finished NixOS Upgrade.\r\nJan 18 04:40:20 my-host systemd[1]: nixos-upgrade.service: Consumed 7.802s CPU time, received 16.6K IP traffic, sent 7.3K IP traffic.\r\n```\r\n\r\nAs far as I understand it, \r\n\r\n1. `nixos-rebuild switch` first stops the `proc-sys-fs-binfmt_misc.automount` and `systemd-binfmt.service` units, and\r\n2. then tries to reload `proc-sys-fs-binfmt_misc.mount`. \r\n\r\nThe first step might affect the second one and cause it to fail, but I don't understand enough about systemd to be sure.\r\n\r\n### Notify maintainers\r\n\r\nThe module doesn't contain explicit maintainer meta data, but @matthewbauer has touched a lot of lines in this module, and @flokli was involved in some change to the way the systemd units are handled: https://github.com/NixOS/nixpkgs/commit/4e2715934e2c995554c5d70fe4eea12716425480\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.87, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-19.09.2229.d7843c8add6\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155485/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155481","id":1106988573,"node_id":"I_kwDOAEVQ_M5B-04d","number":155481,"title":"bug: syncthing-tray isn't dependent on syncthing","user":{"login":"MichaelAkvo","id":91939214,"node_id":"U_kgDOBXrhjg","avatar_url":"https://avatars.githubusercontent.com/u/91939214?v=4","gravatar_id":"","url":"https://api.github.com/users/MichaelAkvo","html_url":"https://github.com/MichaelAkvo","followers_url":"https://api.github.com/users/MichaelAkvo/followers","following_url":"https://api.github.com/users/MichaelAkvo/following{/other_user}","gists_url":"https://api.github.com/users/MichaelAkvo/gists{/gist_id}","starred_url":"https://api.github.com/users/MichaelAkvo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MichaelAkvo/subscriptions","organizations_url":"https://api.github.com/users/MichaelAkvo/orgs","repos_url":"https://api.github.com/users/MichaelAkvo/repos","events_url":"https://api.github.com/users/MichaelAkvo/events{/privacy}","received_events_url":"https://api.github.com/users/MichaelAkvo/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-18T14:40:37Z","updated_at":"2022-02-09T07:11:06Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`syncthing-tray` does have `syncthing` as a dependency, so just installing `syncthing-tray` leads to an empty tray icon.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n1. Install `syncthing-tray`\r\n2. Open tray item\r\n3. Try to open preferences\r\n\r\n### Expected behavior\r\n\r\nWhen I install `syncthing-tray`, I expect it to be usable without having to specify that \"yes, I do want syncthing too\".\r\n\r\n### Screenshots\r\n\r\nNo preferences are opened and one can't point to an external syncthing even if one wanted to.\r\n\r\n\r\n\r\n### Additional context\r\n\r\nThis is on KDE Plasma5. Haven't tested on Gnome (or whatever they call it now).\r\n\r\n### Notify maintainers\r\n\r\n@nickhu\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334814.04bd2d1a470\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155481/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155475","id":1106926441,"node_id":"I_kwDOAEVQ_M5B-ltp","number":155475,"title":"prowlarr: not working corrently without user","user":{"login":"Stunkymonkey","id":1315818,"node_id":"MDQ6VXNlcjEzMTU4MTg=","avatar_url":"https://avatars.githubusercontent.com/u/1315818?v=4","gravatar_id":"","url":"https://api.github.com/users/Stunkymonkey","html_url":"https://github.com/Stunkymonkey","followers_url":"https://api.github.com/users/Stunkymonkey/followers","following_url":"https://api.github.com/users/Stunkymonkey/following{/other_user}","gists_url":"https://api.github.com/users/Stunkymonkey/gists{/gist_id}","starred_url":"https://api.github.com/users/Stunkymonkey/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Stunkymonkey/subscriptions","organizations_url":"https://api.github.com/users/Stunkymonkey/orgs","repos_url":"https://api.github.com/users/Stunkymonkey/repos","events_url":"https://api.github.com/users/Stunkymonkey/events{/privacy}","received_events_url":"https://api.github.com/users/Stunkymonkey/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-18T13:43:52Z","updated_at":"2022-04-09T11:32:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nwhen using:\r\n```\r\nservices.prowlarr.enable = true;\r\n```\r\nthe resulting service is having multiple errors and does not work like intended:\r\n```\r\n2022-01-18 14:21:35.8|Fatal|ProwlarrErrorPipeline|Request Failed. GET /api/v1/update\r\n\r\n[v0.1.8.1231] System.Net.WebException: The SSL connection could not be established, see inner exception.: 'https://prowlarr.servarr.com/v1/update/develop/changes?version=0.1.8.1231&os=linux&arch=Arm64&runtime=netc\r\nore&runtimeVer=6.0.0&prevVersion=0.1.2.1060&active=false'\r\n ---> System.Net.WebException: The SSL connection could not be established, see inner exception.\r\n ---> System.Net.Http.HttpRequestException: The SSL connection could not be established, see inner exception.\r\n ---> System.InvalidOperationException: The home directory of the current user could not be determined.\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `services.prowlarr.enable = true;`\r\n\r\n### Expected behavior\r\nNo errors and the applications works\r\n\r\n### Possible ugly fix:\r\nadding:\r\n```\r\nusers.users.prowlarr = {\r\n isSystemUser = true;\r\n home = \"/var/lib/prowlarr\";\r\n group = \"prowlarr\";\r\n uid = 61654;\r\n};\r\nusers.groups.prowlarr.gid = 61654;\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@jdreaver\r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/vs01795cwqz8mf3fxvhh85dhwh3w9h6d-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/vs01795cwqz8mf3fxvhh85dhwh3w9h6d-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.10.52, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335288.3ddd960a3b5, nixos-unstable-22.05pre343321.78cd22c1b86\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155475/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155467","id":1106826057,"node_id":"I_kwDOAEVQ_M5B-NNJ","number":155467,"title":"NIX_DEBUG=1 causes libtool to fail to detect if -fPIC works","user":{"login":"rodarima","id":3866127,"node_id":"MDQ6VXNlcjM4NjYxMjc=","avatar_url":"https://avatars.githubusercontent.com/u/3866127?v=4","gravatar_id":"","url":"https://api.github.com/users/rodarima","html_url":"https://github.com/rodarima","followers_url":"https://api.github.com/users/rodarima/followers","following_url":"https://api.github.com/users/rodarima/following{/other_user}","gists_url":"https://api.github.com/users/rodarima/gists{/gist_id}","starred_url":"https://api.github.com/users/rodarima/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rodarima/subscriptions","organizations_url":"https://api.github.com/users/rodarima/orgs","repos_url":"https://api.github.com/users/rodarima/repos","events_url":"https://api.github.com/users/rodarima/events{/privacy}","received_events_url":"https://api.github.com/users/rodarima/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":897230915,"node_id":"MDU6TGFiZWw4OTcyMzA5MTU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20stdenv","name":"6.topic: stdenv","color":"fef2c0","default":false,"description":"Standard environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-18T12:07:56Z","updated_at":"2022-01-18T13:02:25Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"When setting the attribute NIX_DEBUG=1 of any derivation that uses libtool to build a shared library, the checks performed by libtool against the compiler report that fpic is not supported.\r\n\r\n```\r\n...\r\nchecking for dlfcn.h... yes\r\nchecking for objdir... .libs\r\nchecking if gcc supports -fno-rtti -fno-exceptions... no\r\nchecking for gcc option to produce PIC... -fPIC -DPIC\r\nchecking if gcc PIC flag -fPIC -DPIC works... no <--- see here\r\nchecking if gcc static flag -static works... no\r\nchecking if gcc supports -c -o file.o... no\r\nchecking if gcc supports -c -o file.o... (cached) no\r\nchecking if we can lock with hard links... yes\r\n...\r\n```\r\n\r\nThis is caused because libtool relies on the output of the compiler to be the same when compiling a simple test with and without `-fPIC`. As the `NIX_DEBUG=1` flag causes the compiler wrapper to print it's own arguments, the output changes and libtool interprets this change as an errror, as it could happened because the compiler emitted a warning of a not recognized flag (yes this is the actual test).\r\n\r\nI [reported the problem to libtool](https://lists.gnu.org/archive/html/bug-libtool/2022-01/msg00000.html) a few days ago, but it doesn't seem to be easy to come up with a proper solution, so in the meantime I think it should be nice if we find a workaround.\r\n\r\nTo further complicate things, most packages are compiled with the \"pic\" hardening options by default, so even if that libtool check fails, the compiler wrapper will inject `-fPIC` internally when calling the actual compiler, so magically most packages are compiled without any issue.\r\n\r\nI encountered this problem when building some custom derivations which have all hardening flags disabled, but the same behavior can be reproduced if you disable the PIC hardening with `hardeningDisable = [ \"pic\" ];` when building a library.\r\n\r\nHere is a reproducer with xorg, which uses libtool and builds a shared library:\r\n\r\n```\r\n$ nix-build -E 'with import <nixpkgs> {}; xorg.xorgserver.overrideAttrs (old:{NIX_DEBUG=1; hardeningDisable=[\"pic\"];})' -I nixpkgs=https://github.com/NixOS/nixpkgs/archive/refs/tags/21.11.tar.gz\r\n...\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/helper_exec.o: relocation R_X86_64_32 against `.rodata.str1.1' can not be used when making a shared object; recompile with -fPIC\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/helper_mem.o: relocation R_X86_64_32S against `.rodata' can not be used when making a shared object; recompile with -fPIC\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/xf86int10.o: relocation R_X86_64_32 against `.rodata.str1.1' can not be used when making a shared object; recompile with -fPIC\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/xf86x86emu.o: relocation R_X86_64_32S against hidden symbol `x_inb' can not be used when making a shared object\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/generic.o: relocation R_X86_64_32S against hidden symbol `genericMem' can not be used when making a shared object\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/x86emu.o: relocation R_X86_64_32S against `.rodata' can not be used when making a shared object; recompile with -fPIC\r\n/nix/store/js66s0xwjnzg0ggi2lq9bcvlk6x2za13-binutils-2.35.2/bin/ld: .libs/xf86x86emu.o: warning: relocation against `Int10Current' in read-only section `.text'\r\ncollect2: error: ld returned 1 exit status\r\nmake[4]: *** [Makefile:697: libint10.la] Error 1\r\nmake[4]: Leaving directory '/build/xorg-server-1.20.13/hw/xfree86/int10'\r\nmake[3]: *** [Makefile:870: all-recursive] Error 1\r\nmake[3]: Leaving directory '/build/xorg-server-1.20.13/hw/xfree86'\r\nmake[2]: *** [Makefile:679: all] Error 2\r\nmake[2]: Leaving directory '/build/xorg-server-1.20.13/hw/xfree86'\r\nmake[1]: *** [Makefile:616: all-recursive] Error 1\r\nmake[1]: Leaving directory '/build/xorg-server-1.20.13/hw'\r\nmake: *** [Makefile:819: all-recursive] Error 1\r\nbuilder for '/nix/store/1bwgh7qdn82d8avgsn3n8icd7lxwr7sk-xorg-server-1.20.13.drv' failed with exit code 2\r\nerror: build of '/nix/store/1bwgh7qdn82d8avgsn3n8icd7lxwr7sk-xorg-server-1.20.13.drv' failed\r\n\r\n```\r\n\r\nI'm not sure what is the best way to fix this problem. Maybe we can prefix the output of NIX_DEBUG with a token which is ignored by libtool. Another option may be to tell libtool that fpic is supported by setting some variable so the test is skipped. Or patch the `config.lt` file in `postConfigure`.\r\n\r\nHere is the offending test in libtool:\r\n\r\nhttps://github.com/autotools-mirror/libtool/blob/f51eddf0dbd1a3dd3119eb215d8a0b5ca451def5/m4/libtool.m4#L4883\r\n\r\n\r\n### Notify maintainers\r\n\r\nNot sure who maintains the stdenv builder. Ping @Ericson2314 @edolstra @alyssais \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result. (I added the -I flag, otherwise it fails as I dont set it by default).\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\" -I nixpkgs=https://github.com/NixOS/nixpkgs/archive/refs/tags/21.11.tar.gz\r\n - system: `0`\r\n - host os: `Linux 4.4.49-92.14-default, SLES, 12-SP2`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.10`\r\n - channels(root): `\"\"`\r\n - channels(ram): `\"\"`\r\n - nixpkgs: `0`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155467/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155458","id":1106694723,"node_id":"I_kwDOAEVQ_M5B9tJD","number":155458,"title":"libcxx: internal <version> include is found in build directory","user":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-18T09:54:25Z","updated_at":"2022-02-21T22:12:06Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"The libcxx internally includes \"version\":\r\n```\r\nsed -ne '37p' /nix/store/bb0bgspj580fghgzv9d9zvk5k9nn98d3-libcxx-11.1.0-dev/include/c++/v1/cstddef\r\n#include <version>\r\n```\r\nThis leads to a build failure when software distribution contains a file named \"version\" that ends up being included because an `-I` flag takes precedence over `-isystem`.\r\n\r\nExamples:\r\n - https://github.com/NixOS/nixpkgs/pull/153113\r\n - https://hydra.nixos.org/build/163485122\r\n - https://github.com/pysathq/pysat/pull/102\r\n - #155415\r\n - qutebrowser/qtwebengine https://github.com/NixOS/nixpkgs/pull/160252#issuecomment-1041041940\r\n - nanodbc https://github.com/NixOS/nixpkgs/pull/161196#issuecomment-1047145879","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155458/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155446","id":1106495846,"node_id":"I_kwDOAEVQ_M5B88lm","number":155446,"title":"`tmux` sessions do not show up in `who`/`users`/`last`","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-18T05:34:08Z","updated_at":"2022-01-18T05:34:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA follow up to https://discourse.nixos.org/t/tmux-sessions-do-not-show-up-in-who-users-last/14698. It seems like `/var/log/wtmp` is not getting updated when tmux sessions begin/end.\r\n\r\nRelevant links:\r\n* https://bugs.launchpad.net/ubuntu/+source/tmux/+bug/1890406\r\n* https://superuser.com/a/1501860/1286339\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `who` and note the results.\r\n2. In a different shell, open a new tmux session: `tmux`\r\n3. Without exiting tmux, run `who` again and note that the results are the same.\r\n\r\n### Expected behavior\r\nTmux user sessions to show up in `who`, `users`, and `last`, as is custom in other OSes.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nn/a\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@fpletz @tobias-hammerschmidt @malbarbo @marsam \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.87, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334578.75f3534c98a, nix-ld\"`\r\n - channels(skainswo): `\"home-manager, nixpkgs-unstable-22.05pre343295.adf7f03d3bf\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155446/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155357","id":1105687259,"node_id":"I_kwDOAEVQ_M5B53Lb","number":155357,"title":"hydra-init fails if sudo is disabled","user":{"login":"sbourdeauducq","id":720864,"node_id":"MDQ6VXNlcjcyMDg2NA==","avatar_url":"https://avatars.githubusercontent.com/u/720864?v=4","gravatar_id":"","url":"https://api.github.com/users/sbourdeauducq","html_url":"https://github.com/sbourdeauducq","followers_url":"https://api.github.com/users/sbourdeauducq/followers","following_url":"https://api.github.com/users/sbourdeauducq/following{/other_user}","gists_url":"https://api.github.com/users/sbourdeauducq/gists{/gist_id}","starred_url":"https://api.github.com/users/sbourdeauducq/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sbourdeauducq/subscriptions","organizations_url":"https://api.github.com/users/sbourdeauducq/orgs","repos_url":"https://api.github.com/users/sbourdeauducq/repos","events_url":"https://api.github.com/users/sbourdeauducq/events{/privacy}","received_events_url":"https://api.github.com/users/sbourdeauducq/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:44:22Z","updated_at":"2022-01-17T11:28:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nhydra-init (and the rest of hydra) fails if sudo is disabled.\r\n\r\n```\r\nsystemd[1]: Starting hydra-init.service...\r\nsudo[2278042]: root : unable to stat /etc/sudoers : No such file or directory ; PWD=/ ; USER=postgres ;\r\nhydra-init-pre-start[2278042]: sudo: unable to stat /etc/sudoers: No such file or directory\r\nhydra-init-pre-start[2278042]: sudo: no valid sudoers sources found, quitting\r\nhydra-init-pre-start[2278042]: sudo: error initializing audit plugin sudoers_audit\r\nsystemd[1]: hydra-init.service: Control process exited, code=exited, status=1/FAILURE\r\n```\r\n\r\n### Steps To Reproduce\r\nInstall hydra and set ``security.sudo.enable = false``\r\n\r\n### Expected behavior\r\nHydra works.\r\n\r\nNixOS 21.11","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155357/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155355","id":1105671516,"node_id":"I_kwDOAEVQ_M5B5zVc","number":155355,"title":"Vulnerability roundup 110: wasm3-0.5.0: 3 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-17T10:28:55Z","updated_at":"2022-01-25T14:16:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=wasm3&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=wasm3+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45929](https://nvd.nist.gov/vuln/detail/CVE-2021-45929) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45946](https://nvd.nist.gov/vuln/detail/CVE-2021-45946) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45947](https://nvd.nist.gov/vuln/detail/CVE-2021-45947) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45929\n\nWasm3 0.5.0 has an out-of-bounds write in CompileBlock (called from CompileElseBlock and Compile_If).\n\n### CVE-2021-45946\n\nWasm3 0.5.0 has an out-of-bounds write in CompileBlock (called from Compile_LoopOrBlock and CompileBlockStatements).\n\n### CVE-2021-45947\n\nWasm3 0.5.0 has an out-of-bounds write in Runtime_Release (called from EvaluateExpression and InitDataSegments).\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @malbarbo\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155355/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155352","id":1105671394,"node_id":"I_kwDOAEVQ_M5B5zTi","number":155352,"title":"Vulnerability roundup 110: teeworlds-0.7.5: 1 advisory [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-17T10:28:48Z","updated_at":"2022-01-18T13:22:18Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=teeworlds&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=teeworlds+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-43518](https://nvd.nist.gov/vuln/detail/CVE-2021-43518) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-43518\n\nTeeworlds up to and including 0.7.5 is vulnerable to Buffer Overflow. A map parser does not validate m_Channels value coming from a map file, leading to a buffer overflow. A malicious server may offer a specially crafted map that will overwrite client's stack causing denial of service or code execution.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @astsmtl\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155352/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155350","id":1105671304,"node_id":"I_kwDOAEVQ_M5B5zSI","number":155350,"title":"Vulnerability roundup 110: solr-8.6.3: 1 advisory [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-17T10:28:43Z","updated_at":"2022-01-26T11:42:02Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=solr&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=solr+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-44548](https://nvd.nist.gov/vuln/detail/CVE-2021-44548) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-44548\n\nAn Improper Input Validation vulnerability in DataImportHandler of Apache Solr allows an attacker to provide a Windows UNC path resulting in an SMB network call being made from the Solr host to another host on the network. If the attacker has wider access to the network, this may lead to SMB attacks, which may result in: * The exfiltration of sensitive data such as OS user hashes (NTLM/LM hashes), * In case of misconfigured systems, SMB Relay Attacks which can lead to user impersonation on SMB Shares or, in a worse-case scenario, Remote Code Execution This issue affects all Apache Solr versions prior to 8.11.1. This issue only affects Windows.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @aanderse\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155348","id":1105671246,"node_id":"I_kwDOAEVQ_M5B5zRO","number":155348,"title":"Vulnerability roundup 110: qtsvg-5.12.10: 1 advisory [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:28:39Z","updated_at":"2022-01-18T17:23:56Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=qtsvg&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=qtsvg+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45930](https://nvd.nist.gov/vuln/detail/CVE-2021-45930) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45930\n\nQt SVG in Qt 5.0.0 through 5.15.2 and 6.0.0 through 6.2.1 has an out-of-bounds write in QtPrivate::QCommonArrayOps<QPainterPath::Element>::growAppend (called from QPainterPath::addPath and QPathClipper::intersect).\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @bkchr\nCc @periklis\nCc @qknight\nCc @ttuegel\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155348/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155342","id":1105665365,"node_id":"I_kwDOAEVQ_M5B5x1V","number":155342,"title":"Vulnerability roundup 110: phoronix-test-suite-10.2.2: 1 advisory [5.4]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:23:27Z","updated_at":"2022-01-27T17:07:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=phoronix-test-suite&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=phoronix-test-suite+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0157](https://nvd.nist.gov/vuln/detail/CVE-2022-0157) CVSSv3=5.4 (nixos-21.11)\n\n## CVE details\n\n### CVE-2022-0157\n\nphoronix-test-suite is vulnerable to Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5.\n\nCc @davidak\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155342/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155338","id":1105665184,"node_id":"I_kwDOAEVQ_M5B5xyg","number":155338,"title":"Vulnerability roundup 110: mysql-5.7.27: 2 advisories [4.9]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-17T10:23:18Z","updated_at":"2022-01-17T10:23:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mysql&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mysql+in%3Apath&type=Code)\n\n* [ ] [CVE-2020-2779](https://nvd.nist.gov/vuln/detail/CVE-2020-2779) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2020-2901](https://nvd.nist.gov/vuln/detail/CVE-2020-2901) CVSSv3=4.9 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2020-2779\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 8.0.18 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.0 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n### CVE-2020-2901\n\nVulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.19 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.0 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155338/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155337","id":1105665149,"node_id":"I_kwDOAEVQ_M5B5xx9","number":155337,"title":"Vulnerability roundup 110: mruby-3.0.0: 3 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-17T10:23:16Z","updated_at":"2022-04-23T17:28:03Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mruby&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mruby+in%3Apath&type=Code)\n\n* [ ] [CVE-2022-0080](https://nvd.nist.gov/vuln/detail/CVE-2022-0080) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-4110](https://nvd.nist.gov/vuln/detail/CVE-2021-4110) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-4188](https://nvd.nist.gov/vuln/detail/CVE-2021-4188) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2022-0080\n\nmruby is vulnerable to Heap-based Buffer Overflow\n\n### CVE-2021-4110\n\nmruby is vulnerable to NULL Pointer Dereference\n\n### CVE-2021-4188\n\nmruby is vulnerable to NULL Pointer Dereference\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @nicknovitski\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155337/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155336","id":1105665111,"node_id":"I_kwDOAEVQ_M5B5xxX","number":155336,"title":"Vulnerability roundup 110: minio-2021-10-27T16-29-42Z: 1 advisory [8.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"bachp","id":333807,"node_id":"MDQ6VXNlcjMzMzgwNw==","avatar_url":"https://avatars.githubusercontent.com/u/333807?v=4","gravatar_id":"","url":"https://api.github.com/users/bachp","html_url":"https://github.com/bachp","followers_url":"https://api.github.com/users/bachp/followers","following_url":"https://api.github.com/users/bachp/following{/other_user}","gists_url":"https://api.github.com/users/bachp/gists{/gist_id}","starred_url":"https://api.github.com/users/bachp/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bachp/subscriptions","organizations_url":"https://api.github.com/users/bachp/orgs","repos_url":"https://api.github.com/users/bachp/repos","events_url":"https://api.github.com/users/bachp/events{/privacy}","received_events_url":"https://api.github.com/users/bachp/received_events","type":"User","site_admin":false},"assignees":[{"login":"bachp","id":333807,"node_id":"MDQ6VXNlcjMzMzgwNw==","avatar_url":"https://avatars.githubusercontent.com/u/333807?v=4","gravatar_id":"","url":"https://api.github.com/users/bachp","html_url":"https://github.com/bachp","followers_url":"https://api.github.com/users/bachp/followers","following_url":"https://api.github.com/users/bachp/following{/other_user}","gists_url":"https://api.github.com/users/bachp/gists{/gist_id}","starred_url":"https://api.github.com/users/bachp/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bachp/subscriptions","organizations_url":"https://api.github.com/users/bachp/orgs","repos_url":"https://api.github.com/users/bachp/repos","events_url":"https://api.github.com/users/bachp/events{/privacy}","received_events_url":"https://api.github.com/users/bachp/received_events","type":"User","site_admin":false}],"milestone":null,"comments":1,"created_at":"2022-01-17T10:23:14Z","updated_at":"2022-01-17T12:32:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=minio&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=minio+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-43858](https://nvd.nist.gov/vuln/detail/CVE-2021-43858) CVSSv3=8.8 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-43858\n\nMinIO is a Kubernetes native application for cloud storage. Prior to version `RELEASE.2021-12-27T07-23-18Z`, a malicious client can hand-craft an HTTP API call that allows for updating policy for a user and gaining higher privileges. The patch in version `RELEASE.2021-12-27T07-23-18Z` changes the accepted request body type and removes the ability to apply policy changes through this API. There is a workaround for this vulnerability: Changing passwords can be disabled by adding an explicit `Deny` rule to disable the API for users.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5.\n\nCc @bachp\nCc @edolstra\nCc @kalbasit\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155336/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155334","id":1105665025,"node_id":"I_kwDOAEVQ_M5B5xwB","number":155334,"title":"Vulnerability roundup 110: mattermost-5.37.5: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:23:09Z","updated_at":"2022-01-17T10:23:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=mattermost&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=mattermost+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-37861](https://nvd.nist.gov/vuln/detail/CVE-2021-37861) CVSSv3=7.5 (nixos-21.11)\n* [ ] [CVE-2021-37860](https://nvd.nist.gov/vuln/detail/CVE-2021-37860) CVSSv3=6.1 (nixos-21.11)\n\n## CVE details\n\n### CVE-2021-37861\n\nMattermost 6.0.2 and earlier fails to sufficiently sanitize user's password in audit logs when user creation fails.\n\n### CVE-2021-37860\n\nMattermost 5.38 and earlier fails to sufficiently sanitize clipboard contents, which allows a user-assisted attacker to inject arbitrary web script in product deployments that explicitly disable the default CSP.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5.\n\nCc @fpletz\nCc @ryantm\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155334/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155329","id":1105664821,"node_id":"I_kwDOAEVQ_M5B5xs1","number":155329,"title":"Vulnerability roundup 110: h2-1.4.199: 1 advisory [9.1]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506370,"node_id":"MDU6TGFiZWwxMjY1MDYzNzA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20work-in-progress","name":"2.status: work-in-progress","color":"e6e6e6","default":false,"description":null},{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:22:58Z","updated_at":"2022-01-28T15:44:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=h2&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=h2+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-23463](https://nvd.nist.gov/vuln/detail/CVE-2021-23463) CVSSv3=9.1 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-23463\n\nThe package com.h2database:h2 from 1.4.198 and before 2.0.202 are vulnerable to XML External Entity (XXE) Injection via the org.h2.jdbc.JdbcSQLXML class object, when it receives parsed string data from org.h2.jdbc.JdbcResultSet.getSQLXML() method. If it executes the getSource() method when the parameter is DOMSource.class it will trigger the vulnerability.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @2chilled\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155329/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155328","id":1105664784,"node_id":"I_kwDOAEVQ_M5B5xsQ","number":155328,"title":"Vulnerability roundup 110: graylog-3.3.16: 2 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:22:56Z","updated_at":"2022-01-17T10:22:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=graylog&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=graylog+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-37759](https://nvd.nist.gov/vuln/detail/CVE-2021-37759) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-37760](https://nvd.nist.gov/vuln/detail/CVE-2021-37760) CVSSv3=9.8 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-37759\n\nA Session ID leak in the DEBUG log file in Graylog before 4.1.2 allows attackers to escalate privileges (to the access level of the leaked session ID).\n\n### CVE-2021-37760\n\nA Session ID leak in the audit log in Graylog before 4.1.2 allows attackers to escalate privileges (to the access level of the leaked session ID).\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @fadenb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155328/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155327","id":1105658940,"node_id":"I_kwDOAEVQ_M5B5wQ8","number":155327,"title":"Vulnerability roundup 110: gradle-6.9.2: 4 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:17:54Z","updated_at":"2022-01-17T10:17:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gradle&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gradle+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-29428](https://nvd.nist.gov/vuln/detail/CVE-2021-29428) CVSSv3=7.8 (nixos-unstable)\n* [ ] [CVE-2021-32751](https://nvd.nist.gov/vuln/detail/CVE-2021-32751) CVSSv3=7.5 (nixos-unstable)\n* [ ] [CVE-2021-29427](https://nvd.nist.gov/vuln/detail/CVE-2021-29427) CVSSv3=7.2 (nixos-unstable)\n* [ ] [CVE-2021-29429](https://nvd.nist.gov/vuln/detail/CVE-2021-29429) CVSSv3=5.5 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-29428\n\nIn Gradle before version 7.0, on Unix-like systems, the system temporary directory can be created with open permissions that allow multiple users to create and delete files within it. Gradle builds could be vulnerable to a local privilege escalation from an attacker quickly deleting and recreating files in the system temporary directory. This vulnerability impacted builds using precompiled script plugins written in Kotlin DSL and tests for Gradle plugins written using ProjectBuilder or TestKit. If you are on Windows or modern versions of macOS, you are not vulnerable. If you are on a Unix-like operating system with the \"sticky\" bit set on your system temporary directory, you are not vulnerable. The problem has been patched and released with Gradle 7.0. As a workaround, on Unix-like operating systems, ensure that the \"sticky\" bit is set. This only allows the original user (or root) to delete a file. If you are unable to change the permissions of the system temporary directory, you can move the Java temporary directory by setting the System Property `java.io.tmpdir`. The new path needs to limit permissions to the build user only. For additional details refer to the referenced GitHub Security Advisory.\n\n### CVE-2021-32751\n\nGradle is a build tool with a focus on build automation. In versions prior to 7.2, start scripts generated by the `application` plugin and the `gradlew` script are both vulnerable to arbitrary code execution when an attacker is able to change environment variables for the user running the script. This may impact those who use `gradlew` on Unix-like systems or use the scripts generated by Gradle in thieir application on Unix-like systems. For this vulnerability to be exploitable, an attacker needs to be able to set the value of particular environment variables and have those environment variables be seen by the vulnerable scripts. This issue has been patched in Gradle 7.2 by removing the use of `eval` and requiring the use of the `bash` shell. There are a few workarounds available. For CI/CD systems using the Gradle build tool, one may ensure that untrusted users are unable to change environment variables for the user that executes `gradlew`. If one is unable to upgrade to Gradle 7.2, one may generate a new `gradlew` script with Gradle 7.2 and use it for older versions of Gradle. Fpplications using start scripts generated by Gradle, one may ensure that untrusted users are unable to change environment variables for the user that executes the start script. A vulnerable start script could be manually patched to remove the use of `eval` or the use of environment variables that affect the application's command-line. If the application is simple enough, one may be able to avoid the use of the start scripts by running the application directly with Java command.\n\n### CVE-2021-29427\n\nIn Gradle from version 5.1 and before version 7.0 there is a vulnerability which can lead to information disclosure and/or dependency poisoning. Repository content filtering is a security control Gradle introduced to help users specify what repositories are used to resolve specific dependencies. This feature was introduced in the wake of the \"A Confusing Dependency\" blog post. In some cases, Gradle may ignore content filters and search all repositories for dependencies. This only occurs when repository content filtering is used from within a `pluginManagement` block in a settings file. This may change how dependencies are resolved for Gradle plugins and build scripts. For builds that are vulnerable, there are two risks: 1) Information disclosure: Gradle could make dependency requests to repositories outside your organization and leak internal package identifiers. 2) Dependency poisoning/Dependency confusion: Gradle could download a malicious binary from a repository outside your organization due to name squatting. For a full example and more details refer to the referenced GitHub Security Advisory. The problem has been patched and released with Gradle 7.0. Users relying on this feature should upgrade their build as soon as possible. As a workaround, users may use a company repository which has the right rules for fetching packages from public repositories, or use project level repository content filtering, inside `buildscript.repositories`. This option is available since Gradle 5.1 when the feature was introduced.\n\n### CVE-2021-29429\n\nIn Gradle before version 7.0, files created with open permissions in the system temporary directory can allow an attacker to access information downloaded by Gradle. Some builds could be vulnerable to a local information disclosure. Remote files accessed through TextResourceFactory are downloaded into the system temporary directory first. Sensitive information contained in these files can be exposed to other local users on the same system. If you do not use the `TextResourceFactory` API, you are not vulnerable. As of Gradle 7.0, uses of the system temporary directory have been moved to the Gradle User Home directory. By default, this directory is restricted to the user running the build. As a workaround, set a more restrictive umask that removes read access to other users. When files are created in the system temporary directory, they will not be accessible to other users. If you are unable to change your system's umask, you can move the Java temporary directory by setting the System Property `java.io.tmpdir`. The new path needs to limit permissions to the build user only.\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @liff\nCc @lorenzleutgeb\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155327/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155326","id":1105658859,"node_id":"I_kwDOAEVQ_M5B5wPr","number":155326,"title":"Vulnerability roundup 110: gpac-1.0.1: 34 advisories [7.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-17T10:17:50Z","updated_at":"2022-01-19T09:47:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=gpac&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=gpac+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-36417](https://nvd.nist.gov/vuln/detail/CVE-2021-36417) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40568](https://nvd.nist.gov/vuln/detail/CVE-2021-40568) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40570](https://nvd.nist.gov/vuln/detail/CVE-2021-40570) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40571](https://nvd.nist.gov/vuln/detail/CVE-2021-40571) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40574](https://nvd.nist.gov/vuln/detail/CVE-2021-40574) CVSSv3=7.8 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40559](https://nvd.nist.gov/vuln/detail/CVE-2021-40559) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40562](https://nvd.nist.gov/vuln/detail/CVE-2021-40562) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40563](https://nvd.nist.gov/vuln/detail/CVE-2021-40563) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40564](https://nvd.nist.gov/vuln/detail/CVE-2021-40564) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40565](https://nvd.nist.gov/vuln/detail/CVE-2021-40565) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40566](https://nvd.nist.gov/vuln/detail/CVE-2021-40566) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40567](https://nvd.nist.gov/vuln/detail/CVE-2021-40567) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40569](https://nvd.nist.gov/vuln/detail/CVE-2021-40569) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40572](https://nvd.nist.gov/vuln/detail/CVE-2021-40572) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40573](https://nvd.nist.gov/vuln/detail/CVE-2021-40573) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40575](https://nvd.nist.gov/vuln/detail/CVE-2021-40575) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-40576](https://nvd.nist.gov/vuln/detail/CVE-2021-40576) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45288](https://nvd.nist.gov/vuln/detail/CVE-2021-45288) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45289](https://nvd.nist.gov/vuln/detail/CVE-2021-45289) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45291](https://nvd.nist.gov/vuln/detail/CVE-2021-45291) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45292](https://nvd.nist.gov/vuln/detail/CVE-2021-45292) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45831](https://nvd.nist.gov/vuln/detail/CVE-2021-45831) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46038](https://nvd.nist.gov/vuln/detail/CVE-2021-46038) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46039](https://nvd.nist.gov/vuln/detail/CVE-2021-46039) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46040](https://nvd.nist.gov/vuln/detail/CVE-2021-46040) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46041](https://nvd.nist.gov/vuln/detail/CVE-2021-46041) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46042](https://nvd.nist.gov/vuln/detail/CVE-2021-46042) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46043](https://nvd.nist.gov/vuln/detail/CVE-2021-46043) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46044](https://nvd.nist.gov/vuln/detail/CVE-2021-46044) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46045](https://nvd.nist.gov/vuln/detail/CVE-2021-46045) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46046](https://nvd.nist.gov/vuln/detail/CVE-2021-46046) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46047](https://nvd.nist.gov/vuln/detail/CVE-2021-46047) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46049](https://nvd.nist.gov/vuln/detail/CVE-2021-46049) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-46051](https://nvd.nist.gov/vuln/detail/CVE-2021-46051) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-36417\n\nA heap-based buffer overflow vulnerability exists in GPAC v1.0.1 in the gf_isom_dovi_config_get function in MP4Box, which causes a denial of service or execute arbitrary code via a crafted file.\n\n### CVE-2021-40568\n\nA buffer overflow vulnerability exists in Gpac through 1.0.1 via a malformed MP4 file in the svc_parse_slice function in av_parsers.c, which allows attackers to cause a denial of service, even code execution and escalation of privileges.\n\n### CVE-2021-40570\n\nThe binary MP4Box in Gpac 1.0.1 has a double-free vulnerability in the avc_compute_poc function in av_parsers.c, which allows attackers to cause a denial of service, even code execution and escalation of privileges.\n\n### CVE-2021-40571\n\nThe binary MP4Box in Gpac 1.0.1 has a double-free vulnerability in the ilst_box_read function in box_code_apple.c, which allows attackers to cause a denial of service, even code execution and escalation of privileges.\n\n### CVE-2021-40574\n\nThe binary MP4Box in Gpac 1.0.1 has a double-free vulnerability in the gf_text_get_utf8_line function in load_text.c, which allows attackers to cause a denial of service, even code execution and escalation of privileges.\n\n### CVE-2021-40559\n\nA null pointer deference vulnerability exists in gpac through 1.0.1 via the naludmx_parse_nal_avc function in reframe_nalu, which allows a denail of service.\n\n### CVE-2021-40562\n\nA Segmentation fault caused by a floating point exception exists in Gpac through 1.0.1 using mp4box via the naludmx_enqueue_or_dispatch function in reframe_nalu.c, which causes a denial of service.\n\n### CVE-2021-40563\n\nA Segmentation fault exists casued by null pointer dereference exists in Gpac through 1.0.1 via the naludmx_create_avc_decoder_config function in reframe_nalu.c when using mp4box, which causes a denial of service.\n\n### CVE-2021-40564\n\nA Segmentation fault caused by null pointer dereference vulnerability eists in Gpac through 1.0.2 via the avc_parse_slice function in av_parsers.c when using mp4box, which causes a denial of service.\n\n### CVE-2021-40565\n\nA Segmentation fault caused by a null pointer dereference vulnerability exists in Gpac through 1.0.1 via the gf_avc_parse_nalu function in av_parsers.c when using mp4box, which causes a denial of service.\n\n### CVE-2021-40566\n\nA Segmentation fault casued by heap use after free vulnerability exists in Gpac through 1.0.1 via the mpgviddmx_process function in reframe_mpgvid.c when using mp4box, which causes a denial of service.\n\n### CVE-2021-40567\n\nSegmentation fault vulnerability exists in Gpac through 1.0.1 via the gf_odf_size_descriptor function in desc_private.c when using mp4box, which causes a denial of service.\n\n### CVE-2021-40569\n\nThe binary MP4Box in Gpac through 1.0.1 has a double-free vulnerability in the iloc_entry_del funciton in box_code_meta.c, which allows attackers to cause a denial of service.\n\n### CVE-2021-40572\n\nThe binary MP4Box in Gpac 1.0.1 has a double-free bug in the av1dmx_finalize function in reframe_av1.c, which allows attackers to cause a denial of service.\n\n### CVE-2021-40573\n\nThe binary MP4Box in Gpac 1.0.1 has a double-free vulnerability in the gf_list_del function in list.c, which allows attackers to cause a denial of service.\n\n### CVE-2021-40575\n\nThe binary MP4Box in Gpac 1.0.1 has a null pointer dereference vulnerability in the mpgviddmx_process function in reframe_mpgvid.c, which allows attackers to cause a denial of service. This vulnerability is possibly due to an incomplete fix for CVE-2021-40566.\n\n### CVE-2021-40576\n\nThe binary MP4Box in Gpac 1.0.1 has a null pointer dereference vulnerability in the gf_isom_get_payt_count function in hint_track.c, which allows attackers to cause a denial of service.\n\n### CVE-2021-45288\n\nA Double Free vulnerability exists in filedump.c in GPAC 1.0.1, which could cause a Denail of Service via a crafted file in the MP4Box command.\n\n### CVE-2021-45289\n\nA vulnerability exists in GPAC 1.0.1 due to an omission of security-relevant Information, which could cause a Denial of Service. The program terminates with signal SIGKILL.\n\n### CVE-2021-45291\n\nThe gf_dump_setup function in GPAC 1.0.1 allows malicoius users to cause a denial of service (Invalid memory address dereference) via a crafted file in the MP4Box command.\n\n### CVE-2021-45292\n\nThe gf_isom_hint_rtp_read function in GPAC 1.0.1 allows attackers to cause a denial of service (Invalid memory address dereference) via a crafted file in the MP4Box command.\n\n### CVE-2021-45831\n\nA Null Pointer Dereference vulnerability exitgs in GPAC 1.0.1 in MP4Box via __strlen_avx2, which causes a Denial of Service.\n\n### CVE-2021-46038\n\nA Pointer Dereference vulnerability exists in GPAC 1.0.1 in unlink_chunk.isra, which causes a Denial of Service (context-dependent).\n\n### CVE-2021-46039\n\nA Pointer Dereference Vulnerabilty exists in GPAC 1.0.1 via the shift_chunk_offsets.part function, which causes a Denial of Service (context-dependent).\n\n### CVE-2021-46040\n\nA Pointer Dereference Vulnerabilty exists in GPAC 1.0.1 via the finplace_shift_moov_meta_offsets function, which causes a Denial of Servie (context-dependent).\n\n### CVE-2021-46041\n\nA Segmentation Fault Vulnerability exists in GPAC 1.0.1 via the co64_box_new function, which causes a Denial of Service.\n\n### CVE-2021-46042\n\nA Pointer Dereference Vulnerability exists in GPAC 1.0.1 via the _fseeko function, which causes a Denial of Service.\n\n### CVE-2021-46043\n\nA Pointer Dereference Vulnerability exits in GPAC 1.0.1 in the gf_list_count function, which causes a Denial of Service.\n\n### CVE-2021-46044\n\nA Pointer Dereference Vulnerabilty exists in GPAC 1.0.1via ShiftMetaOffset.isra, which causes a Denial of Service (context-dependent).\n\n### CVE-2021-46045\n\nGPAC 1.0.1 is affected by: Abort failed. The impact is: cause a denial of service (context-dependent).\n\n### CVE-2021-46046\n\nA Pointer Derefernce Vulnerbility exists GPAC 1.0.1 the gf_isom_box_size function, which could cause a Denial of Service (context-dependent).\n\n### CVE-2021-46047\n\nA Pointer Dereference Vulnerability exists in GPAC 1.0.1 via the gf_hinter_finalize function.\n\n### CVE-2021-46049\n\nA Pointer Dereference Vulnerability exists in GPAC 1.0.1 via the gf_fileio_check function, which could cause a Denial of Service.\n\n### CVE-2021-46051\n\nA Pointer Dereference Vulnerability exists in GPAC 1.0.1 via the Media_IsSelfContained function, which could cause a Denial of Service. .\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @bluescreen303\nCc @mgdelacroix\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155326/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155324","id":1105658767,"node_id":"I_kwDOAEVQ_M5B5wOP","number":155324,"title":"Vulnerability roundup 110: go-1.15.15: 2 advisories [7.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":337081580,"node_id":"MDU6TGFiZWwzMzcwODE1ODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20golang","name":"6.topic: golang","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-17T10:17:45Z","updated_at":"2022-01-31T08:36:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=go&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=go+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-44716](https://nvd.nist.gov/vuln/detail/CVE-2021-44716) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-44717](https://nvd.nist.gov/vuln/detail/CVE-2021-44717) CVSSv3=7.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-44716\n\nnet/http in Go before 1.16.12 and 1.17.x before 1.17.5 allows uncontrolled memory consumption in the header canonicalization cache via HTTP/2 requests.\n\n### CVE-2021-44717\n\nGo before 1.16.12 and 1.17.x before 1.17.5 on UNIX allows write operations to an unintended file or unintended network connection as a consequence of erroneous closing of file descriptor 0 after file-descriptor exhaustion.\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @Frostman\nCc @c00w\nCc @cstrahan\nCc @kalbasit\nCc @mdlayher\nCc @mic92\nCc @orivej\nCc @rvolosatovs\nCc @zowoq\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155324/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155319","id":1105658563,"node_id":"I_kwDOAEVQ_M5B5wLD","number":155319,"title":"Vulnerability roundup 110: ghostscript-9.53.3: 2 advisories [5.5]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:17:35Z","updated_at":"2022-01-17T10:17:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=ghostscript&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=ghostscript+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45944](https://nvd.nist.gov/vuln/detail/CVE-2021-45944) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n* [ ] [CVE-2021-45949](https://nvd.nist.gov/vuln/detail/CVE-2021-45949) CVSSv3=5.5 (nixos-21.11, nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45944\n\nGhostscript GhostPDL 9.50 through 9.53.3 has a use-after-free in sampled_data_sample (called from sampled_data_continue and interp).\n\n### CVE-2021-45949\n\nGhostscript GhostPDL 9.50 through 9.54.0 has a heap-based buffer overflow in sampled_data_finish (called from sampled_data_continue and interp).\n\n-----\nScanned versions: nixos-21.11: 3ddd960a3b5; nixos-unstable: 5aaed40d22f.\n\nCc @viric\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155319/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155317","id":1105658483,"node_id":"I_kwDOAEVQ_M5B5wJz","number":155317,"title":"Vulnerability roundup 110: dnsmasq-2.86: 7 advisories [9.8]","user":{"login":"ckauhaus","id":1448923,"node_id":"MDQ6VXNlcjE0NDg5MjM=","avatar_url":"https://avatars.githubusercontent.com/u/1448923?v=4","gravatar_id":"","url":"https://api.github.com/users/ckauhaus","html_url":"https://github.com/ckauhaus","followers_url":"https://api.github.com/users/ckauhaus/followers","following_url":"https://api.github.com/users/ckauhaus/following{/other_user}","gists_url":"https://api.github.com/users/ckauhaus/gists{/gist_id}","starred_url":"https://api.github.com/users/ckauhaus/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ckauhaus/subscriptions","organizations_url":"https://api.github.com/users/ckauhaus/orgs","repos_url":"https://api.github.com/users/ckauhaus/repos","events_url":"https://api.github.com/users/ckauhaus/events{/privacy}","received_events_url":"https://api.github.com/users/ckauhaus/received_events","type":"User","site_admin":false},"labels":[{"id":126506420,"node_id":"MDU6TGFiZWwxMjY1MDY0MjA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/1.severity:%20security","name":"1.severity: security","color":"e11d21","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-17T10:17:31Z","updated_at":"2022-01-26T10:19:04Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"[search](https://search.nix.gsc.io/?q=dnsmasq&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=dnsmasq+in%3Apath&type=Code)\n\n* [ ] [CVE-2021-45951](https://nvd.nist.gov/vuln/detail/CVE-2021-45951) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45952](https://nvd.nist.gov/vuln/detail/CVE-2021-45952) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45953](https://nvd.nist.gov/vuln/detail/CVE-2021-45953) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45954](https://nvd.nist.gov/vuln/detail/CVE-2021-45954) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45955](https://nvd.nist.gov/vuln/detail/CVE-2021-45955) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45956](https://nvd.nist.gov/vuln/detail/CVE-2021-45956) CVSSv3=9.8 (nixos-unstable)\n* [ ] [CVE-2021-45957](https://nvd.nist.gov/vuln/detail/CVE-2021-45957) CVSSv3=9.8 (nixos-unstable)\n\n## CVE details\n\n### CVE-2021-45951\n\nDnsmasq 2.86 has a heap-based buffer overflow in check_bad_address (called from check_for_bogus_wildcard and FuzzCheckForBogusWildcard).\n\n### CVE-2021-45952\n\nDnsmasq 2.86 has a heap-based buffer overflow in dhcp_reply (called from dhcp_packet and FuzzDhcp).\n\n### CVE-2021-45953\n\nDnsmasq 2.86 has a heap-based buffer overflow in extract_name (called from hash_questions and fuzz_util.c).\n\n### CVE-2021-45954\n\nDnsmasq 2.86 has a heap-based buffer overflow in extract_name (called from answer_auth and FuzzAuth).\n\n### CVE-2021-45955\n\nDnsmasq 2.86 has a heap-based buffer overflow in resize_packet (called from FuzzResizePacket and fuzz_rfc1035.c).\n\n### CVE-2021-45956\n\nDnsmasq 2.86 has a heap-based buffer overflow in print_mac (called from log_packet and dhcp_reply).\n\n### CVE-2021-45957\n\nDnsmasq 2.86 has a heap-based buffer overflow in answer_request (called from FuzzAnswerTheRequest and fuzz_rfc1035.c).\n\n-----\nScanned versions: nixos-unstable: 5aaed40d22f.\n\nCc @edolstra\nCc @fpletz\nCc @globin\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155317/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155293","id":1105294609,"node_id":"I_kwDOAEVQ_M5B4XUR","number":155293,"title":"Plasma does not pass color theme to gtk 4 apps","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-17T02:21:17Z","updated_at":"2022-01-17T21:08:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nEven through gtk 4 app recognize the `GTK_THEME=Breeze` setting, they still do not take the color theme set from the system, instead utilizing the default Breeze light color scheme\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start `plasmawayland`\r\n2. `nix-shell -I nixpkgs=channel:nixos-unstable -p gtk4.dev --run gtk4-demo`\r\n3. ` GTK_THEME=Breeze nix-shell -I nixpkgs=channel:nixos-unstable -p gtk4.dev --run gtk4-demo`\r\n\r\n### Expected behavior\r\nGTK apps are themed according to the global theme\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nGTK applications on Plasma X11 are correctly themed\r\n### Notify maintainers\r\n@NixOS/gnome @NixOS/qt-kde \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/3c249himjn7sh3cwnapmh5qgrnmd42xg-source`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155293/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155292","id":1105288484,"node_id":"I_kwDOAEVQ_M5B4V0k","number":155292,"title":"GTK_THEME is not set by plasma wayland","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-17T02:10:29Z","updated_at":"2022-01-17T17:37:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start `plasmawayland`\r\n2. `nix-shell -I nixpkgs=channel:nixos-unstable -p gtk3.dev --run gtk3-widget-factory`\r\n3. `GTK_THEME=Breeze nix-shell -I nixpkgs=channel:nixos-unstable -p gtk3.dev --run gtk3-widget-factory`\r\n### Expected behavior\r\nBreeze theme is applied to the app\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nGTK applications on Plasma X11 are correctly themed\r\n\r\n### Notify maintainers\r\n@NixOS/gnome @NixOS/qt-kde \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/3c249himjn7sh3cwnapmh5qgrnmd42xg-source`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155292/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155291","id":1105287534,"node_id":"I_kwDOAEVQ_M5B4Vlu","number":155291,"title":"Badly rendered font for gtk apps on Plasma Wayland","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2022-01-17T02:08:52Z","updated_at":"2022-03-28T18:58:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Start `plasmawayland`\r\n2. `nix-shell -I nixpkgs=channel:nixos-unstable -p gtk3.dev --run gtk3-widget-factory`\r\n\r\n### Expected behavior\r\nFont is taken from system settings and is rendered correctly\r\n\r\n### Screenshots\r\n\r\n### Additional context\r\nGTK applications on Plasma X11 are correctly themed\r\n### Notify maintainers\r\n@NixOS/gnome @NixOS/qt-kde \r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/3c249himjn7sh3cwnapmh5qgrnmd42xg-source`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155291/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155278","id":1105235457,"node_id":"I_kwDOAEVQ_M5B4I4B","number":155278,"title":"Steam: error loading libfuse.so.2","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."},{"id":1117871739,"node_id":"MDU6TGFiZWwxMTE3ODcxNzM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20upstream%20fix","name":"9.needs: upstream fix","color":"eb6420","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-17T00:28:54Z","updated_at":"2022-01-22T17:47:33Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n[SuperTux](https://store.steampowered.com/app/1572920/SuperTux/) is now available on Steam. It is packaged with AppImage, which needs FUSE to run.\r\n\r\n```\r\nOpted-in Controller Mask for AppId 1572920: 1\r\nCould not connect to X session manager: None of the authentication protocols specified are supported\r\nCould not connect to X session manager: None of the authentication protocols specified are supported\r\nCould not connect to X session manager: None of the authentication protocols specified are supported\r\nCould not connect to X session manager: None of the authentication protocols specified are supported\r\nCould not connect to X session manager: None of the authentication protocols specified are supported\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to ProcessingInstallScript with \"\"\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to SynchronizingCloud with \"\"\r\nCAPIJobRequestUserStats - Server response failed 2\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to SynchronizingControllerConfig with \"\"\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to SiteLicenseSeatCheckout with \"\"\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to CreatingProcess with \"\"\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp waiting for user response to CreatingProcess \"\"\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp continues with user response \"CreatingProcess\"\r\n/bin/sh\\0-c\\0/home/davidak/.local/share/Steam/ubuntu12_32/reaper SteamLaunch AppId=1572920 -- '/home/davidak/.local/share/Steam/steamapps/common/SuperTux/SuperTux.AppImage'\\0\r\nGame process added : AppID 1572920 \"/home/davidak/.local/share/Steam/ubuntu12_32/reaper SteamLaunch AppId=1572920 -- '/home/davidak/.local/share/Steam/steamapps/common/SuperTux/SuperTux.AppImage'\", ProcID 817562, IP 0.0.0.0:0\r\nchdir /home/davidak/.local/share/Steam/steamapps/common/SuperTux\r\nERROR: ld.so: object '/home/davidak/.local/share/Steam/ubuntu12_32/gameoverlayrenderer.so' from LD_PRELOAD cannot be preloaded (wrong ELF class: ELFCLASS32): ignored.\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to WaitingGameWindow with \"\"\r\nERROR: ld.so: object '/home/davidak/.local/share/Steam/ubuntu12_64/gameoverlayrenderer.so' from LD_PRELOAD cannot be preloaded (wrong ELF class: ELFCLASS64): ignored.\r\nERROR: ld.so: object '/home/davidak/.local/share/Steam/ubuntu12_32/gameoverlayrenderer.so' from LD_PRELOAD cannot be preloaded (wrong ELF class: ELFCLASS32): ignored.\r\nGameAction [AppID 1572920, ActionID 1] : LaunchApp changed task to Completed with \"\"\r\ndlopen(): error loading libfuse.so.2\r\n\r\nAppImages require FUSE to run. \r\nYou might still be able to extract the contents of this AppImage \r\nif you run it with the --appimage-extract option. \r\nSee https://github.com/AppImage/AppImageKit/wiki/FUSE \r\nfor more information\r\nGame process removed: AppID 1572920 \"/home/davidak/.local/share/Steam/ubuntu12_32/reaper SteamLaunch AppId=1572920 -- '/home/davidak/.local/share/Steam/steamapps/common/SuperTux/SuperTux.AppImage'\", ProcID 817562 \r\nUploaded AppInterfaceStats to Steam\r\nNo cached sticky mapping in ActivateActionSet.No cached sticky mapping in ActivateActionSet.Installing breakpad exception handler for appid(steam)/version(1639697812)\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install game\r\n2. run game\r\n3. see errors in terminal\r\n\r\n### Expected behavior\r\ngames from steam should just work\r\n\r\n### Additional context\r\n\r\nPeople which use Steam as Flatpak also have issues. The game developers might use the steam runtime instead of AppImage, which might also fix this issue. Not sure if it's worth it to add this dependency now to support other games that potentially use AppImage.\r\n\r\nhttps://www.gamingonlinux.com/2022/01/supertux-released-free-on-steam-an-open-source-classic/comment_id=217269\r\n\r\nWe can remove FUSE when not needed anymore.\r\n\r\n### Notify maintainers\r\n@jonringer\r\n\r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.335130.386234e2a61, nixos-hardware, nixos-unstable-22.05pre346004.5aaed40d22f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155278/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155274","id":1105208317,"node_id":"I_kwDOAEVQ_M5B4CP9","number":155274,"title":"kexi not building on nixos22","user":{"login":"alciono","id":8074385,"node_id":"MDQ6VXNlcjgwNzQzODU=","avatar_url":"https://avatars.githubusercontent.com/u/8074385?v=4","gravatar_id":"","url":"https://api.github.com/users/alciono","html_url":"https://github.com/alciono","followers_url":"https://api.github.com/users/alciono/followers","following_url":"https://api.github.com/users/alciono/following{/other_user}","gists_url":"https://api.github.com/users/alciono/gists{/gist_id}","starred_url":"https://api.github.com/users/alciono/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alciono/subscriptions","organizations_url":"https://api.github.com/users/alciono/orgs","repos_url":"https://api.github.com/users/alciono/repos","events_url":"https://api.github.com/users/alciono/events{/privacy}","received_events_url":"https://api.github.com/users/alciono/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-16T22:43:17Z","updated_at":"2022-01-26T10:16:16Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nkexi not building \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nixos-rebuild switch\r\n2. error message:\r\n\r\n\\-- Detecting CXX compile features - done\r\n\\-- \r\n\r\n\\-- Check for working CXX compiler: /nix/store/npm4g1zsj5yzygf6bq46pbi9fqhxisha-gcc-wrapper-10.3.0/bin/g++ - skipped\r\n\\-- Detecting CXX compile features\r\n\\-- Detecting CXX compile features - done\r\n\\-- \r\n\r\nCMake Error at CMakeLists.txt:15 (find_package):\r\n Could not find a configuration file for package \"Qt5\" that is compatible \r\n with requested version \"5.15.2\". \r\n The following configuration files were considered but not accepted: \r\n /nix/store/gszycghs77nlqa58fp1ydw2bxpy998ci-qtbase-5.14.2-dev/lib/cmake/Qt5/Qt5Config.cmake, version: 5.14.2 \r\n\\-- Configuring incomplete, errors occurred!\r\nSee also \"/build/kconfig-5.89.0/build/CMakeFiles/CMakeOutput.log\".\r\nerror: builder for '/nix/store/6ryr8drmhk9gx9a3v235mab7sq03c4pa-kconfig-5.89.0.drv' failed with exit code 1\r\nerror: 1 dependencies of derivation '/nix/store/kvqw0vp1iy0y0rdlzlh2vr60z2r1cp6s-kexi-3.2.0.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/lblcrnzacn9iblyjp3gkmlkn12r3y8s4-system-path.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/m7wzfkm5ksr5vnry306vlp3p3ar854pm-xsession-wrapper.drv' failed to build\r\nerror: 1 dependencies of derivation '/nix/store/yppskr5vfswznfsfx16bm975dmz5sfl3-nixos-system-bx26-22.05pre346004.5aaed40d22f.drv' failed to build\r\n\r\n\r\n### Expected behavior\r\nnixos-rebuild switch without errors\r\n\r\n### Notify maintainers\r\nThomas Tuegel \r\nhttps://github.com/ttuegel\r\n\r\nDavid Mell zraexy\r\nhttps://github.com/zraexy\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n /nix/store/jaa5l5g36aj1wwlmk9lqhslclmdqms3x-bash-interactive-5.1-p12-dev\r\ncopying path '/nix/store/jaa5l5g36aj1wwlmk9lqhslclmdqms3x-bash-interactive-5.1-p12-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.91, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre346004.5aaed40d22f\"`\r\n - channels(k): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155274/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155262","id":1105194378,"node_id":"I_kwDOAEVQ_M5B3-2K","number":155262,"title":"gst_all_1.gst-plugins-base fails to build on aarch64-linux via binfmt","user":{"login":"tomfitzhenry","id":61303,"node_id":"MDQ6VXNlcjYxMzAz","avatar_url":"https://avatars.githubusercontent.com/u/61303?v=4","gravatar_id":"","url":"https://api.github.com/users/tomfitzhenry","html_url":"https://github.com/tomfitzhenry","followers_url":"https://api.github.com/users/tomfitzhenry/followers","following_url":"https://api.github.com/users/tomfitzhenry/following{/other_user}","gists_url":"https://api.github.com/users/tomfitzhenry/gists{/gist_id}","starred_url":"https://api.github.com/users/tomfitzhenry/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tomfitzhenry/subscriptions","organizations_url":"https://api.github.com/users/tomfitzhenry/orgs","repos_url":"https://api.github.com/users/tomfitzhenry/repos","events_url":"https://api.github.com/users/tomfitzhenry/events{/privacy}","received_events_url":"https://api.github.com/users/tomfitzhenry/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-16T21:38:40Z","updated_at":"2022-02-08T07:45:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\ngst_all_1.gst-plugins-base fails to build when targetting aarch64-linux (emulated via binfmt). Native compilation on x86-64 works fine.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. On an x86-64 NixOS machine with `boot.binfmt.emulatedSystems = [ \"aarch64-linux\" ];`\r\n2. In a nixpkgs checkout with commit b5b0c4e1cb4c75c3f9ab38f8f9b30eea6aa7fb86\r\n2. Execute `nix-build -A gst_all_1.gst-plugins-base --option system aarch64-linux`\r\n\r\n```\r\n$ nix log /nix/store/0zb919yfyvgyn297nxvlm68m822xy5sx-gst-plugins-base-1.18.4.drv\r\n[...]\r\nERROR: can't resolve libraries to shared libraries: gsttag-1.0\r\n```\r\n\r\nFull log: https://paste.debian.net/1227319/\r\n\r\n### Expected behavior\r\nI expect the nix-build command to succeed in building gst-plugins-base.\r\n\r\n### Additional context\r\nThis builds successfully with `nix-build -A gst_all_1.gst-plugins-base` (i.e. native compilation).\r\n\r\n### Notify maintainers\r\n\r\n@matthewbauer\r\n\r\n### Metadata\r\n\r\n```\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese 2 paths will be fetched (0.07 MiB download, 0.34 MiB unpacked):\r\n /nix/store/lwcfw5vyjlzrs35k1hanv21j1q2s5c5w-stdenv-linux\r\n /nix/store/w14py6k30j21z8rnymcj8dsjcm9cxkqi-bash-interactive-5.1-p12-dev\r\ncopying path '/nix/store/w14py6k30j21z8rnymcj8dsjcm9cxkqi-bash-interactive-5.1-p12-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/lwcfw5vyjlzrs35k1hanv21j1q2s5c5w-stdenv-linux' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155262/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155168","id":1104914142,"node_id":"I_kwDOAEVQ_M5B26be","number":155168,"title":"`flex` package should provide `lex` binary","user":{"login":"WesleyAC","id":5001092,"node_id":"MDQ6VXNlcjUwMDEwOTI=","avatar_url":"https://avatars.githubusercontent.com/u/5001092?v=4","gravatar_id":"","url":"https://api.github.com/users/WesleyAC","html_url":"https://github.com/WesleyAC","followers_url":"https://api.github.com/users/WesleyAC/followers","following_url":"https://api.github.com/users/WesleyAC/following{/other_user}","gists_url":"https://api.github.com/users/WesleyAC/gists{/gist_id}","starred_url":"https://api.github.com/users/WesleyAC/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/WesleyAC/subscriptions","organizations_url":"https://api.github.com/users/WesleyAC/orgs","repos_url":"https://api.github.com/users/WesleyAC/repos","events_url":"https://api.github.com/users/WesleyAC/events{/privacy}","received_events_url":"https://api.github.com/users/WesleyAC/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-16T01:18:31Z","updated_at":"2022-01-16T10:27:20Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"On most linux distributions, `/bin/lex` is provided by the `flex` package as a symlink to `/bin/flex`. This is not the case on NixOS, which makes building some software that expects a `lex` binary difficult.\r\n\r\nNixOS should change the `flex` package to provide `/bin/lex` in addition to the `/bin/flex` and `/bin/flex++` that it currently provides.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155168/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155157","id":1104890211,"node_id":"I_kwDOAEVQ_M5B20lj","number":155157,"title":"GNOME and accountsservice are acting up","user":{"login":"TheOPtimal","id":41379516,"node_id":"MDQ6VXNlcjQxMzc5NTE2","avatar_url":"https://avatars.githubusercontent.com/u/41379516?v=4","gravatar_id":"","url":"https://api.github.com/users/TheOPtimal","html_url":"https://github.com/TheOPtimal","followers_url":"https://api.github.com/users/TheOPtimal/followers","following_url":"https://api.github.com/users/TheOPtimal/following{/other_user}","gists_url":"https://api.github.com/users/TheOPtimal/gists{/gist_id}","starred_url":"https://api.github.com/users/TheOPtimal/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/TheOPtimal/subscriptions","organizations_url":"https://api.github.com/users/TheOPtimal/orgs","repos_url":"https://api.github.com/users/TheOPtimal/repos","events_url":"https://api.github.com/users/TheOPtimal/events{/privacy}","received_events_url":"https://api.github.com/users/TheOPtimal/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-15T23:39:22Z","updated_at":"2022-03-15T07:46:55Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nGNOME is acting up - ~~system partitions like /boot and / show up in the sidebar~~, no users are detected in the users panel in GNOME Control Center, and partitions don't get automounted.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Use [my NixOS configuration](https://gitlab.com/TheOPtimal/nixos-config), this happens on both `optimal-pc` and `optimalbook` configurations\r\n2. Log in to GNOME\r\n3. Watch the mayhem unfold\r\n\r\n### Expected behavior\r\nGNOME works normally, my user shows up in GNOME Control Center and partitions are auto-mounted\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nI have traced this problem to `accountsservice` - I entered the following commands in GNOME Looking Glass (press Alt+F2 and type `lg`)\r\n\r\n```js\r\nu = imports.gi.AccountsService.UserManager.get_default().get_user(imports.gi.GLib.get_user_name())\r\n\r\nu.is_local_account()\r\nu.is_system_account()\r\n```\r\n\r\nBoth `is_local_account` and `is_system_account` returned true - I don't know how this is possible, but it could be the culprit.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n`accountsservice` maintainers:\r\n@pSub \r\nGNOME team members:\r\n@hedning\r\n@jtojnar\r\n@dasj19\r\n@maxeaubrey\r\n(Should I add `udisks2` maintainer here?)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155157/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155154","id":1104870520,"node_id":"I_kwDOAEVQ_M5B2vx4","number":155154,"title":"libredirect support for `mkstemp` family of functions","user":{"login":"risicle","id":807447,"node_id":"MDQ6VXNlcjgwNzQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/807447?v=4","gravatar_id":"","url":"https://api.github.com/users/risicle","html_url":"https://github.com/risicle","followers_url":"https://api.github.com/users/risicle/followers","following_url":"https://api.github.com/users/risicle/following{/other_user}","gists_url":"https://api.github.com/users/risicle/gists{/gist_id}","starred_url":"https://api.github.com/users/risicle/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/risicle/subscriptions","organizations_url":"https://api.github.com/users/risicle/orgs","repos_url":"https://api.github.com/users/risicle/repos","events_url":"https://api.github.com/users/risicle/events{/privacy}","received_events_url":"https://api.github.com/users/risicle/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-15T22:34:24Z","updated_at":"2022-01-16T15:52:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"It would be helpful if `libredirect` also redirected the following functions:\r\n\r\n`mkstemp` `mkostemp` `mkstemps` `mkostemps` `mkdtemp` `mktemp`\r\n\r\nShouldn't be particularly tricky, the `XXXXXX` template-suffix business can probably be ignored.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155154/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155121","id":1104753262,"node_id":"I_kwDOAEVQ_M5B2TJu","number":155121,"title":"mongodb attribute should refer to a newer version","user":{"login":"FRidh","id":2129135,"node_id":"MDQ6VXNlcjIxMjkxMzU=","avatar_url":"https://avatars.githubusercontent.com/u/2129135?v=4","gravatar_id":"","url":"https://api.github.com/users/FRidh","html_url":"https://github.com/FRidh","followers_url":"https://api.github.com/users/FRidh/followers","following_url":"https://api.github.com/users/FRidh/following{/other_user}","gists_url":"https://api.github.com/users/FRidh/gists{/gist_id}","starred_url":"https://api.github.com/users/FRidh/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/FRidh/subscriptions","organizations_url":"https://api.github.com/users/FRidh/orgs","repos_url":"https://api.github.com/users/FRidh/repos","events_url":"https://api.github.com/users/FRidh/events{/privacy}","received_events_url":"https://api.github.com/users/FRidh/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":{"url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22","html_url":"https://github.com/NixOS/nixpkgs/milestone/22","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/milestones/22/labels","id":7437265,"node_id":"MI_kwDOAEVQ_M4AcXvR","number":22,"title":"22.05","description":"","creator":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"open_issues":15,"closed_issues":18,"state":"open","created_at":"2021-11-29T07:12:03Z","updated_at":"2022-04-29T17:07:17Z","due_on":"2022-05-31T07:00:00Z","closed_at":null},"comments":4,"created_at":"2022-01-15T15:23:05Z","updated_at":"2022-01-17T06:35:31Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`mongodb` can no longer be built as it depends on old `python2` packages through and older Python 2 version of scons. Using a newer scons version is not possible.\r\n\r\n### Steps To Reproduce\r\n```\r\nnix-build -A mongodb\r\n```\r\n### Notify maintainers\r\n@bluescreen303 @offlinehacker @cstrahan @bryanasdev000 @andir @pjjw @dotlambda\r\n\r\nhttps://github.com/NixOS/nixpkgs/pull/155025#issuecomment-1013698965\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155121/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155113","id":1104721487,"node_id":"I_kwDOAEVQ_M5B2LZP","number":155113,"title":"Antora `site-generator` is missing","user":{"login":"hqurve","id":53281855,"node_id":"MDQ6VXNlcjUzMjgxODU1","avatar_url":"https://avatars.githubusercontent.com/u/53281855?v=4","gravatar_id":"","url":"https://api.github.com/users/hqurve","html_url":"https://github.com/hqurve","followers_url":"https://api.github.com/users/hqurve/followers","following_url":"https://api.github.com/users/hqurve/following{/other_user}","gists_url":"https://api.github.com/users/hqurve/gists{/gist_id}","starred_url":"https://api.github.com/users/hqurve/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/hqurve/subscriptions","organizations_url":"https://api.github.com/users/hqurve/orgs","repos_url":"https://api.github.com/users/hqurve/repos","events_url":"https://api.github.com/users/hqurve/events{/privacy}","received_events_url":"https://api.github.com/users/hqurve/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-15T13:38:31Z","updated_at":"2022-01-15T21:40:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen attempting to generate a site with antora, the following error message is displayed\r\n\r\n```\r\nFATAL (antora): Generator not found or failed to load. Try installing the '@antora/site-generator' package.\r\n```\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `antora <playbook file>`\r\n\r\n### Expected behavior\r\nAntora runs\r\n\r\n### Additional context\r\nThe package `site-generator-default` has been named to `site-generator` (see https://gitlab.com/antora/antora/-/issues/886). I have fixed this problem locally by using node2nix on a package set depending only on `@antora/antora` and `@antora/site-generator` and using the build logic at https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/tools/documentation/antora/default.nix to generate the package.\r\n\r\n~My proposed fix is to rename `@antora/site-generator-default` to `@antora/site-generator` in both the antora file and https://github.com/NixOS/nixpkgs/blob/master/pkgs/development/node-packages/node-packages.json. Sadly, node2nix takes very long on the nixpkgs, so I am requesting assistance.~\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155113/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155074","id":1104489564,"node_id":"I_kwDOAEVQ_M5B1Sxc","number":155074,"title":"Packaging request: ets","user":{"login":"cameronfyfe","id":21013281,"node_id":"MDQ6VXNlcjIxMDEzMjgx","avatar_url":"https://avatars.githubusercontent.com/u/21013281?v=4","gravatar_id":"","url":"https://api.github.com/users/cameronfyfe","html_url":"https://github.com/cameronfyfe","followers_url":"https://api.github.com/users/cameronfyfe/followers","following_url":"https://api.github.com/users/cameronfyfe/following{/other_user}","gists_url":"https://api.github.com/users/cameronfyfe/gists{/gist_id}","starred_url":"https://api.github.com/users/cameronfyfe/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cameronfyfe/subscriptions","organizations_url":"https://api.github.com/users/cameronfyfe/orgs","repos_url":"https://api.github.com/users/cameronfyfe/repos","events_url":"https://api.github.com/users/cameronfyfe/events{/privacy}","received_events_url":"https://api.github.com/users/cameronfyfe/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-15T05:58:58Z","updated_at":"2022-01-15T05:58:58Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\n`ets` is a command output timestamper similar to `ts` in moreutils. Primary advantages over `ts` are the non-conflicting command name and its handling of progress bars. See \"Comparison to moreutils ts\" section in source repo for more complete comparison.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/zmwangx/ets\r\n* source URL: https://github.com/zmwangx/ets\r\n* license: mit\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155074/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155051","id":1104187443,"node_id":"I_kwDOAEVQ_M5B0JAz","number":155051,"title":"pipewire: filter-chain: hang when specifying any filter link","user":{"login":"X9VoiD","id":10338031,"node_id":"MDQ6VXNlcjEwMzM4MDMx","avatar_url":"https://avatars.githubusercontent.com/u/10338031?v=4","gravatar_id":"","url":"https://api.github.com/users/X9VoiD","html_url":"https://github.com/X9VoiD","followers_url":"https://api.github.com/users/X9VoiD/followers","following_url":"https://api.github.com/users/X9VoiD/following{/other_user}","gists_url":"https://api.github.com/users/X9VoiD/gists{/gist_id}","starred_url":"https://api.github.com/users/X9VoiD/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/X9VoiD/subscriptions","organizations_url":"https://api.github.com/users/X9VoiD/orgs","repos_url":"https://api.github.com/users/X9VoiD/repos","events_url":"https://api.github.com/users/X9VoiD/events{/privacy}","received_events_url":"https://api.github.com/users/X9VoiD/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-14T22:46:18Z","updated_at":"2022-01-15T02:11:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nPipewire server hangs when any amount of link is specified in filter-chain.\r\n\r\nThis bug is also reported [upstream](https://gitlab.freedesktop.org/pipewire/pipewire/-/issues/1950) just in case.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Import this [pipewire.nix](https://github.com/NixOS/nixpkgs/files/7873640/pipewire.zip) (uploaded as zip since Github doesn't allow nix) to `configuration.nix`\r\n2. `sudo nixos-rebuild switch`\r\n3. Reboot, relogin, or `systemctl --user restart pipewire`\r\n\r\nThe bug doesn't happen when doing something like this: [pipewire.nix](https://github.com/NixOS/nixpkgs/files/7873651/pipewire.zip)\r\n\r\n### Expected behavior\r\nPipewire should lower the output volume by around -16db when using \"Filter Sink\" as output device. (for this minimal `pipewire.nix`. My nix where I found the bug specifies a lot more links to describe a chain of parametric EQs)\r\n\r\n### Additional context\r\nAs long as any amount of `\"links\"` is defined, pipewire will hang and consume 100% CPU time.\r\n\r\n### Notify maintainers\r\n@jtojnar \r\n@Kranzes \r\n@jansol \r\n\r\n### Metadata\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335037.e67c94a1adb\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155051/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155046","id":1104162240,"node_id":"I_kwDOAEVQ_M5B0C3A","number":155046,"title":"Plasma 5:notification buttons/textbox not working","user":{"login":"pasqui23","id":6931743,"node_id":"MDQ6VXNlcjY5MzE3NDM=","avatar_url":"https://avatars.githubusercontent.com/u/6931743?v=4","gravatar_id":"","url":"https://api.github.com/users/pasqui23","html_url":"https://github.com/pasqui23","followers_url":"https://api.github.com/users/pasqui23/followers","following_url":"https://api.github.com/users/pasqui23/following{/other_user}","gists_url":"https://api.github.com/users/pasqui23/gists{/gist_id}","starred_url":"https://api.github.com/users/pasqui23/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pasqui23/subscriptions","organizations_url":"https://api.github.com/users/pasqui23/orgs","repos_url":"https://api.github.com/users/pasqui23/repos","events_url":"https://api.github.com/users/pasqui23/events{/privacy}","received_events_url":"https://api.github.com/users/pasqui23/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-14T22:04:23Z","updated_at":"2022-04-24T21:34:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIf I get a notification with buttons I can't press those buttons to interact with it\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Recive a notification from your cell via KDE connect\r\n2. Click on a button on the notification\r\n3. See no iteraction, the notification does not even disappear\r\n\r\n### Expected behavior\r\nThe notification disappear and the described action happen\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@NixOS/qt-kde \r\n### Metadata\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/3c249himjn7sh3cwnapmh5qgrnmd42xg-source`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155046/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155044","id":1104149802,"node_id":"I_kwDOAEVQ_M5Bz_0q","number":155044,"title":"wrong and not configurable fontpath in `xwayland` used by `gdm`","user":{"login":"fedeinthemix","id":7670450,"node_id":"MDQ6VXNlcjc2NzA0NTA=","avatar_url":"https://avatars.githubusercontent.com/u/7670450?v=4","gravatar_id":"","url":"https://api.github.com/users/fedeinthemix","html_url":"https://github.com/fedeinthemix","followers_url":"https://api.github.com/users/fedeinthemix/followers","following_url":"https://api.github.com/users/fedeinthemix/following{/other_user}","gists_url":"https://api.github.com/users/fedeinthemix/gists{/gist_id}","starred_url":"https://api.github.com/users/fedeinthemix/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fedeinthemix/subscriptions","organizations_url":"https://api.github.com/users/fedeinthemix/orgs","repos_url":"https://api.github.com/users/fedeinthemix/repos","events_url":"https://api.github.com/users/fedeinthemix/events{/privacy}","received_events_url":"https://api.github.com/users/fedeinthemix/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":25,"created_at":"2022-01-14T21:44:56Z","updated_at":"2022-04-09T09:25:34Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe size and type of fonts displayed by xfig is not correct. At startup it gives the error \"Can't load font: 8x13bold, using 6x13\" and on the console\r\n\r\n```console\r\nWarning: Cannot convert string \"-*-times-medium-r-normal--16-*-*-*-*-*-*-*,-*-*-medium-r-normal--16-*-*-*-*-*-*-*,*--16-*\" to type FontSet\r\nWarning: Missing charsets in String to FontSet conversion\r\nWarning: Cannot convert string \"7x13bold\" to type FontStruct\r\nWarning: Missing charsets in String to FontSet conversion\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install and launch xfig\r\n2. insert some text\r\n\r\n### Notify maintainers\r\n@AndersonTorres \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.4, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155044/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155021","id":1103955091,"node_id":"I_kwDOAEVQ_M5BzQST","number":155021,"title":"boscaceoil: init at 2020-02-05","user":{"login":"papojari","id":81317317,"node_id":"MDQ6VXNlcjgxMzE3MzE3","avatar_url":"https://avatars.githubusercontent.com/u/81317317?v=4","gravatar_id":"","url":"https://api.github.com/users/papojari","html_url":"https://github.com/papojari","followers_url":"https://api.github.com/users/papojari/followers","following_url":"https://api.github.com/users/papojari/following{/other_user}","gists_url":"https://api.github.com/users/papojari/gists{/gist_id}","starred_url":"https://api.github.com/users/papojari/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/papojari/subscriptions","organizations_url":"https://api.github.com/users/papojari/orgs","repos_url":"https://api.github.com/users/papojari/repos","events_url":"https://api.github.com/users/papojari/events{/privacy}","received_events_url":"https://api.github.com/users/papojari/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-14T17:46:49Z","updated_at":"2022-01-14T17:46:49Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nBosca Ceoil is a tool to make music. It is very simple to use and is often used to make chiptunes.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: http://boscaceoil.net/\r\n* source URL: https://github.com/TerryCavanagh/boscaceoil\r\n* license: bsd\r\n* platforms: windows, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155021/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007/events","html_url":"https://github.com/NixOS/nixpkgs/issues/155007","id":1103639533,"node_id":"I_kwDOAEVQ_M5ByDPt","number":155007,"title":"xxHash derivation should include cmake support","user":{"login":"foolnotion","id":844222,"node_id":"MDQ6VXNlcjg0NDIyMg==","avatar_url":"https://avatars.githubusercontent.com/u/844222?v=4","gravatar_id":"","url":"https://api.github.com/users/foolnotion","html_url":"https://github.com/foolnotion","followers_url":"https://api.github.com/users/foolnotion/followers","following_url":"https://api.github.com/users/foolnotion/following{/other_user}","gists_url":"https://api.github.com/users/foolnotion/gists{/gist_id}","starred_url":"https://api.github.com/users/foolnotion/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/foolnotion/subscriptions","organizations_url":"https://api.github.com/users/foolnotion/orgs","repos_url":"https://api.github.com/users/foolnotion/repos","events_url":"https://api.github.com/users/foolnotion/events{/privacy}","received_events_url":"https://api.github.com/users/foolnotion/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-14T13:27:31Z","updated_at":"2022-01-15T11:17:30Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nCurrently the xxHash package only installs a pkg-config file, however it would be really useful if it could also install cmake support files. There are provided by upstream and are already used by e.g. vcpkg. \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install xxHash\r\n2. CMake support is missing\r\n3. \r\n\r\n### Expected behavior\r\nCmake support files are installed for xxHash.\r\n\r\n### I have made my own derivation of xxHash which looks like this:\r\n```nix\r\n{\r\n lib,\r\n stdenv,\r\n fetchFromGitHub,\r\n cmake,\r\n buildXXHSum ? false,\r\n buildSharedLibs ? true\r\n}:\r\n\r\nstdenv.mkDerivation rec {\r\n pname = \"xxhash\";\r\n version = \"0.8.1\";\r\n\r\n src = fetchFromGitHub {\r\n owner = \"Cyan4973\";\r\n repo = \"xxHash\";\r\n rev = \"v${version}\";\r\n sha256 = \"sha256-2WoYCO6QRHWrbGP2mK04/sLNTyQLOuL3urVktilAwMA=\";\r\n };\r\n\r\n nativeBuildInputs = [ cmake ];\r\n\r\n configurePhase = ''\r\n mkdir build\r\n cmake -S . -B ./build ./cmake_unofficial \\\r\n -DCMAKE_BUILD_TYPE=Release \\\r\n -DXXHASH_BUILD_XXHSUM=${if buildXXHSum then \"ON\" else \"OFF\"} \\\r\n -DBUILD_SHARED_LIBS=${if buildSharedLibs then \"ON\" else \"OFF\"} \\\r\n -DCMAKE_INSTALL_PREFIX=$out\r\n '';\r\n\r\n buildPhase = ''\r\n cmake --build build -j\r\n '';\r\n\r\n installPhase = ''\r\n cmake --install build\r\n '';\r\n\r\n meta = with lib; {\r\n description = \"Extremely fast non-cryptographic hash algorithm.\";\r\n homepage = \"https://cyan4973.github.io/xxHash/\";\r\n license = licenses.bsd2;\r\n platforms = platforms.all;\r\n };\r\n}\r\n```\r\n\r\nI think it would be good if CMake support is included with the official package. Perhaps the above could be integrated with the existing derivation.\r\n\r\n### Notify maintainers\r\n@trofi \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/155007/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154949","id":1102509396,"node_id":"I_kwDOAEVQ_M5BtvVU","number":154949,"title":"specialisations - consistent bootloader support","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-13T22:40:45Z","updated_at":"2022-02-13T11:44:35Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nFrom a quick skim of the bootloader generators and the real world systems I have around me, it appears that our 3 primary bootloader configuration generators act differently with respect to specialisations:\r\n\r\n1. Grub will output entries for specialisations, for only the most recent generation.\r\n2. Systemd-Boot will output entries for specialisations for every generation\r\n3. Extlinux does not do anything with specialisations whatsoever.\r\n\r\nI plan to hack in quick specialisation support for the extlinux generator, and I plan to add entries for specialisations for all generations.\r\n\r\nBut I wanted to open this to track, we might want to be more consistent.\r\n\r\n(Note to self, see if this work should just be moved to and done in bootspec?)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154949/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154944","id":1102464756,"node_id":"I_kwDOAEVQ_M5Btkb0","number":154944,"title":"gnomeExtensons: no desktop icons","user":{"login":"alexeymuranov","id":712698,"node_id":"MDQ6VXNlcjcxMjY5OA==","avatar_url":"https://avatars.githubusercontent.com/u/712698?v=4","gravatar_id":"","url":"https://api.github.com/users/alexeymuranov","html_url":"https://github.com/alexeymuranov","followers_url":"https://api.github.com/users/alexeymuranov/followers","following_url":"https://api.github.com/users/alexeymuranov/following{/other_user}","gists_url":"https://api.github.com/users/alexeymuranov/gists{/gist_id}","starred_url":"https://api.github.com/users/alexeymuranov/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/alexeymuranov/subscriptions","organizations_url":"https://api.github.com/users/alexeymuranov/orgs","repos_url":"https://api.github.com/users/alexeymuranov/repos","events_url":"https://api.github.com/users/alexeymuranov/events{/privacy}","received_events_url":"https://api.github.com/users/alexeymuranov/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90420949,"node_id":"MDU6TGFiZWw5MDQyMDk0OQ==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20GNOME","name":"6.topic: GNOME","color":"fef2c0","default":false,"description":"GNOME desktop environment and its underlying platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-13T22:10:06Z","updated_at":"2022-03-03T22:26:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nNo GNOME Shell Extension can enable desktop icons.\r\n\r\n### Steps To Reproduce\r\n1. Install [`gnomeExtensons.desktop-icons-neo`](https://extensions.gnome.org/extension/4337/desktop-icons-neo/) and [`gnomeExtensons.desktop-icons-ng-ding`](https://extensions.gnome.org/extension/2087/desktop-icons-ng-ding/).\r\n2. Try to enable desktop icons.\r\n\r\n### Expected behavior\r\nShould be able to enable desktop icons in GNOME Shell, one way or another.\r\n\r\n### Additional context\r\nAbout the time of NixOS 20.03, i was still able to have desktop icons using some old version of [Desktop Icons](https://extensions.gnome.org/extension/1465/desktop-icons/) extension.\r\n\r\n### Notify maintainers\r\n@piegamesde \r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.90, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(alexey): `\"\"`\r\n - channels(root): `\"nixos-21.11.335130.386234e2a61\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154944/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154939","id":1102431001,"node_id":"I_kwDOAEVQ_M5BtcMZ","number":154939,"title":"lispPackages: Just use CL_SOURCE_REGISTRY, not both CL_SOURCE_REGISTRY and asdf:initialize-source-registry","user":{"login":"remexre","id":4196789,"node_id":"MDQ6VXNlcjQxOTY3ODk=","avatar_url":"https://avatars.githubusercontent.com/u/4196789?v=4","gravatar_id":"","url":"https://api.github.com/users/remexre","html_url":"https://github.com/remexre","followers_url":"https://api.github.com/users/remexre/followers","following_url":"https://api.github.com/users/remexre/following{/other_user}","gists_url":"https://api.github.com/users/remexre/gists{/gist_id}","starred_url":"https://api.github.com/users/remexre/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/remexre/subscriptions","organizations_url":"https://api.github.com/users/remexre/orgs","repos_url":"https://api.github.com/users/remexre/repos","events_url":"https://api.github.com/users/remexre/events{/privacy}","received_events_url":"https://api.github.com/users/remexre/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":7,"created_at":"2022-01-13T21:46:57Z","updated_at":"2022-01-23T18:31:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nIn a typical package, `CL_SOURCE_REGISTRY` is initialized via `cl-wrapper-script`'s setup hook, while `NIX_LISP_ASDF_PATHS` gets set by `buildLispPackage` (`define-package.nix`), and picked up by `cl-wrapper.sh`, which uses it to construct a chunk of *code that gets evaled*, which ends up calling `(asdf:initialize-source-registry)`.\r\n\r\nThis results in systems whose build scripts call `asdf:initialize-source-registry` themselves losing all the ASDF paths!\r\n\r\n### Steps To Reproduce\r\n\r\n`example.lisp`\r\n```\r\n(asdf:initialize-source-registry\r\n '(:source-registry\r\n :inherit-configuration))\r\n(asdf:load-system \"iterate\")\r\n```\r\n\r\nin a shell with `cl-wrapper.sh` and `lispPackages.iterate`\r\n```\r\n$ cl-wrapper.sh sbcl --load example.lisp\r\n```\r\n\r\n### Expected behavior\r\n\r\n`iterate` should be loaded\r\n\r\n### Additional context\r\n\r\nASDF's behavior may be changed to make `(asdf:initialize-source-registry '(:source-registry :inherit-configuration))` a no-op in the future (changing the semantics of `:inherit-configuration`), but this bug exists for the current nixpkgs version, and the patch to make it a no-op has not been written.\r\n\r\n### Notify maintainers\r\n\r\n@7c6f434c \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.10.52, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/store/31jbhzh2pj5zsr5ip983qbknv23kf7d4-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154939/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154918","id":1102129441,"node_id":"I_kwDOAEVQ_M5BsSkh","number":154918,"title":"gzdoom (4.7.1) doesn't run due to kdialog error","user":{"login":"nixinator","id":66913205,"node_id":"MDQ6VXNlcjY2OTEzMjA1","avatar_url":"https://avatars.githubusercontent.com/u/66913205?v=4","gravatar_id":"","url":"https://api.github.com/users/nixinator","html_url":"https://github.com/nixinator","followers_url":"https://api.github.com/users/nixinator/followers","following_url":"https://api.github.com/users/nixinator/following{/other_user}","gists_url":"https://api.github.com/users/nixinator/gists{/gist_id}","starred_url":"https://api.github.com/users/nixinator/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nixinator/subscriptions","organizations_url":"https://api.github.com/users/nixinator/orgs","repos_url":"https://api.github.com/users/nixinator/repos","events_url":"https://api.github.com/users/nixinator/events{/privacy}","received_events_url":"https://api.github.com/users/nixinator/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":287403097,"node_id":"MDU6TGFiZWwyODc0MDMwOTc=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20good-first-bug","name":"3.skill: good-first-bug","color":"f7c6c7","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-13T18:17:22Z","updated_at":"2022-02-09T01:30:41Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nrunning gzdoom results in `sh: kdialog: command not found` and quits.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-shell -p gzdoom\r\n2. gzdoom\r\n\r\n\r\n### Expected behavior\r\nI enter hell and banish demons.\r\n\r\n\r\n### Additional context\r\nhttps://github.com/flathub/org.zdoom.GZDoom/issues/10\r\n\r\nmentioned here.\r\n\r\n### Notify maintainers\r\n<!--\r\n@Lassulus \r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.05.20220103.88579ef (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(user): `\"nixgl, stable-21.05.4709.88579effa7e\"`\r\n - channels(root): `\"nixos-21.11pre332093.7fad01d9d5a\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918/reactions","total_count":2,"+1":0,"-1":0,"laugh":2,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154918/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154898","id":1101924931,"node_id":"I_kwDOAEVQ_M5BrgpD","number":154898,"title":"avdmanager create avd fails with \"Probably the SDK is read-only\"","user":{"login":"cheriimoya","id":28303440,"node_id":"MDQ6VXNlcjI4MzAzNDQw","avatar_url":"https://avatars.githubusercontent.com/u/28303440?v=4","gravatar_id":"","url":"https://api.github.com/users/cheriimoya","html_url":"https://github.com/cheriimoya","followers_url":"https://api.github.com/users/cheriimoya/followers","following_url":"https://api.github.com/users/cheriimoya/following{/other_user}","gists_url":"https://api.github.com/users/cheriimoya/gists{/gist_id}","starred_url":"https://api.github.com/users/cheriimoya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cheriimoya/subscriptions","organizations_url":"https://api.github.com/users/cheriimoya/orgs","repos_url":"https://api.github.com/users/cheriimoya/repos","events_url":"https://api.github.com/users/cheriimoya/events{/privacy}","received_events_url":"https://api.github.com/users/cheriimoya/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-13T15:17:27Z","updated_at":"2022-01-27T06:52:14Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\navdmanager fails to create new avds from the command line.\r\n\r\navd = android virtual device\r\n\r\n```\r\n$ avdmanager create avd -n test -k \"system-images;android-25;google_apis;x86\"\r\n\r\nInfo: Exception while marshalling /nix/store/nqpv0wg5xcmnbkplgi1pkkyqd61wbyqp-androidsdk/libexec/android-sdk/build-tools/31.0.0/package.xml. Probably the SDK is read-only\r\nInfo: Exception while marshalling /nix/store/nqpv0wg5xcmnbkplgi1pkkyqd61wbyqp-androidsdk/libexec/android-sdk/platform-tools/package.xml. Probably the SDK is read-only\r\nInfo: Exception while marshalling /nix/store/nqpv0wg5xcmnbkplgi1pkkyqd61wbyqp-androidsdk/libexec/android-sdk/platforms/android-28/package.xml. Probably the SDK is read-only\r\nInfo: Exception while marshalling /nix/store/nqpv0wg5xcmnbkplgi1pkkyqd61wbyqp-androidsdk/libexec/android-sdk/tools/package.xml. Probably the SDK is read-only\r\nError: Package path is not valid. Valid system image paths are:ository...\r\nnull\r\n```\r\n\r\nI can provide more information if needed.\r\n\r\n### Steps To Reproduce\r\n\r\n1. install the androidsdk (a simple shell didn't work for me)\r\n ```nix\r\n {\r\n environment.systemPackages = with pkgs; [\r\n androidenv.androidPkgs_9_0.androidsdk\r\n ];\r\n nixpkgs.config.android_sdk.accept_license = true;\r\n }\r\n ```\r\n2. try to create a new avd `avdmanager create avd -n test -k \"system-images;android-25;google_apis;x86\"`\r\n3. it fails\r\n\r\n### Expected behavior\r\n\r\nThe avd gets created because the sdk/avd can write to the package.xml files _somehow_ (maybe in a temp directory?)\r\n\r\n### Additional context\r\n\r\nthe package.xml are not inside the path, so i assume the android sdk expects to be running in `~/.android/sdk` or something alike.\r\ni don't know much about the android sdk (and android in general) but i assume these files are being generated by the sdk manager on startup.\r\n\r\nhttps://developer.android.com/studio/command-line/avdmanager\r\n\r\nAnother interesting thing/workaround is, that i am able to create an avd by using android-studio.\r\nHere i can simply enter the avdmanager and create an avd.\r\nDifference here is, that android-studio downloads and stores an android sdk to `~/Android/Sdk/` with all tools running there.\r\n\r\nThere is also #19452, but i am not sure if thats connected to this issue.\r\n\r\nMaybe it is possible to simply render those files to the specified locations, but i am not that skilled with nix as of now.\r\n\r\n<details>\r\n <summary>Here is the `build-tools/32.0.0/package.xml` file from the mutable sdk location</summary>\r\n\r\n```xml\r\n<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"yes\"?><ns2:repository xmlns:ns2=\"http://schemas.android.com/repository/android/common/02\" xmlns:ns3=\"http://schemas.android.com/repository/android/common/01\" xmlns:ns4=\"http://schemas.android.com/repository/android/generic/01\" xmlns:ns5=\"http://schemas.android.com/repository/android/generic/02\" xmlns:ns6=\"http://schemas.android.com/sdk/android/repo/addon2/01\" xmlns:ns7=\"http://schemas.android.com/sdk/android/repo/addon2/02\" xmlns:ns8=\"http://schemas.android.com/sdk/android/repo/repository2/01\" xmlns:ns9=\"http://schemas.android.com/sdk/android/repo/repository2/02\" xmlns:ns10=\"http://schemas.android.com/sdk/android/repo/sys-img2/02\" xmlns:ns11=\"http://schemas.android.com/sdk/android/repo/sys-img2/01\"><license id=\"android-sdk-license\" type=\"text\">Terms and Conditions\r\n\r\nThis is the Android Software Development Kit License Agreement\r\n\r\n1. Introduction\r\n\r\n1.1 The Android Software Development Kit (referred to in the License Agreement as the \"SDK\" and specifically including the Android system files, packaged APIs, and Google APIs add-ons) is licensed to you subject to the terms of the License Agreement. The License Agreement forms a legally binding contract between you and Google in relation to your use of the SDK.\r\n\r\n1.2 \"Android\" means the Android software stack for devices, as made available under the Android Open Source Project, which is located at the following URL: http://source.android.com/, as updated from time to time.\r\n\r\n1.3 A \"compatible implementation\" means any Android device that (i) complies with the Android Compatibility Definition document, which can be found at the Android compatibility website (http://source.android.com/compatibility) and which may be updated from time to time; and (ii) successfully passes the Android Compatibility Test Suite (CTS).\r\n\r\n1.4 \"Google\" means Google Inc., a Delaware corporation with principal place of business at 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States.\r\n\r\n\r\n2. Accepting the License Agreement\r\n\r\n2.1 In order to use the SDK, you must first agree to the License Agreement. You may not use the SDK if you do not accept the License Agreement.\r\n\r\n2.2 By clicking to accept, you hereby agree to the terms of the License Agreement.\r\n\r\n2.3 You may not use the SDK and may not accept the License Agreement if you are a person barred from receiving the SDK under the laws of the United States or other countries, including the country in which you are resident or from which you use the SDK.\r\n\r\n2.4 If you are agreeing to be bound by the License Agreement on behalf of your employer or other entity, you represent and warrant that you have full legal authority to bind your employer or such entity to the License Agreement. If you do not have the requisite authority, you may not accept the License Agreement or use the SDK on behalf of your employer or other entity.\r\n\r\n\r\n3. SDK License from Google\r\n\r\n3.1 Subject to the terms of the License Agreement, Google grants you a limited, worldwide, royalty-free, non-assignable, non-exclusive, and non-sublicensable license to use the SDK solely to develop applications for compatible implementations of Android.\r\n\r\n3.2 You may not use this SDK to develop applications for other platforms (including non-compatible implementations of Android) or to develop another SDK. You are of course free to develop applications for other platforms, including non-compatible implementations of Android, provided that this SDK is not used for that purpose.\r\n\r\n3.3 You agree that Google or third parties own all legal right, title and interest in and to the SDK, including any Intellectual Property Rights that subsist in the SDK. \"Intellectual Property Rights\" means any and all rights under patent law, copyright law, trade secret law, trademark law, and any and all other proprietary rights. Google reserves all rights not expressly granted to you.\r\n\r\n3.4 You may not use the SDK for any purpose not expressly permitted by the License Agreement. Except to the extent required by applicable third party licenses, you may not copy (except for backup purposes), modify, adapt, redistribute, decompile, reverse engineer, disassemble, or create derivative works of the SDK or any part of the SDK.\r\n\r\n3.5 Use, reproduction and distribution of components of the SDK licensed under an open source software license are governed solely by the terms of that open source software license and not the License Agreement.\r\n\r\n3.6 You agree that the form and nature of the SDK that Google provides may change without prior notice to you and that future versions of the SDK may be incompatible with applications developed on previous versions of the SDK. You agree that Google may stop (permanently or temporarily) providing the SDK (or any features within the SDK) to you or to users generally at Google's sole discretion, without prior notice to you.\r\n\r\n3.7 Nothing in the License Agreement gives you a right to use any of Google's trade names, trademarks, service marks, logos, domain names, or other distinctive brand features.\r\n\r\n3.8 You agree that you will not remove, obscure, or alter any proprietary rights notices (including copyright and trademark notices) that may be affixed to or contained within the SDK.\r\n\r\n\r\n4. Use of the SDK by You\r\n\r\n4.1 Google agrees that it obtains no right, title or interest from you (or your licensors) under the License Agreement in or to any software applications that you develop using the SDK, including any intellectual property rights that subsist in those applications.\r\n\r\n4.2 You agree to use the SDK and write applications only for purposes that are permitted by (a) the License Agreement and (b) any applicable law, regulation or generally accepted practices or guidelines in the relevant jurisdictions (including any laws regarding the export of data or software to and from the United States or other relevant countries).\r\n\r\n4.3 You agree that if you use the SDK to develop applications for general public users, you will protect the privacy and legal rights of those users. If the users provide you with user names, passwords, or other login information or personal information, you must make the users aware that the information will be available to your application, and you must provide legally adequate privacy notice and protection for those users. If your application stores personal or sensitive information provided by users, it must do so securely. If the user provides your application with Google Account information, your application may only use that information to access the user's Google Account when, and for the limited purposes for which, the user has given you permission to do so.\r\n\r\n4.4 You agree that you will not engage in any activity with the SDK, including the development or distribution of an application, that interferes with, disrupts, damages, or accesses in an unauthorized manner the servers, networks, or other properties or services of any third party including, but not limited to, Google or any mobile communications carrier.\r\n\r\n4.5 You agree that you are solely responsible for (and that Google has no responsibility to you or to any third party for) any data, content, or resources that you create, transmit or display through Android and/or applications for Android, and for the consequences of your actions (including any loss or damage which Google may suffer) by doing so.\r\n\r\n4.6 You agree that you are solely responsible for (and that Google has no responsibility to you or to any third party for) any breach of your obligations under the License Agreement, any applicable third party contract or Terms of Service, or any applicable law or regulation, and for the consequences (including any loss or damage which Google or any third party may suffer) of any such breach.\r\n\r\n5. Your Developer Credentials\r\n\r\n5.1 You agree that you are responsible for maintaining the confidentiality of any developer credentials that may be issued to you by Google or which you may choose yourself and that you will be solely responsible for all applications that are developed under your developer credentials.\r\n\r\n6. Privacy and Information\r\n\r\n6.1 In order to continually innovate and improve the SDK, Google may collect certain usage statistics from the software including but not limited to a unique identifier, associated IP address, version number of the software, and information on which tools and/or services in the SDK are being used and how they are being used. Before any of this information is collected, the SDK will notify you and seek your consent. If you withhold consent, the information will not be collected.\r\n\r\n6.2 The data collected is examined in the aggregate to improve the SDK and is maintained in accordance with Google's Privacy Policy.\r\n\r\n\r\n7. Third Party Applications\r\n\r\n7.1 If you use the SDK to run applications developed by a third party or that access data, content or resources provided by a third party, you agree that Google is not responsible for those applications, data, content, or resources. You understand that all data, content or resources which you may access through such third party applications are the sole responsibility of the person from which they originated and that Google is not liable for any loss or damage that you may experience as a result of the use or access of any of those third party applications, data, content, or resources.\r\n\r\n7.2 You should be aware the data, content, and resources presented to you through such a third party application may be protected by intellectual property rights which are owned by the providers (or by other persons or companies on their behalf). You may not modify, rent, lease, loan, sell, distribute or create derivative works based on these data, content, or resources (either in whole or in part) unless you have been specifically given permission to do so by the relevant owners.\r\n\r\n7.3 You acknowledge that your use of such third party applications, data, content, or resources may be subject to separate terms between you and the relevant third party. In that case, the License Agreement does not affect your legal relationship with these third parties.\r\n\r\n\r\n8. Using Android APIs\r\n\r\n8.1 Google Data APIs\r\n\r\n8.1.1 If you use any API to retrieve data from Google, you acknowledge that the data may be protected by intellectual property rights which are owned by Google or those parties that provide the data (or by other persons or companies on their behalf). Your use of any such API may be subject to additional Terms of Service. You may not modify, rent, lease, loan, sell, distribute or create derivative works based on this data (either in whole or in part) unless allowed by the relevant Terms of Service.\r\n\r\n8.1.2 If you use any API to retrieve a user's data from Google, you acknowledge and agree that you shall retrieve data only with the user's explicit consent and only when, and for the limited purposes for which, the user has given you permission to do so. If you use the Android Recognition Service API, documented at the following URL: https://developer.android.com/reference/android/speech/RecognitionService, as updated from time to time, you acknowledge that the use of the API is subject to the Data Processing Addendum for Products where Google is a Data Processor, which is located at the following URL: https://privacy.google.com/businesses/gdprprocessorterms/, as updated from time to time. By clicking to accept, you hereby agree to the terms of the Data Processing Addendum for Products where Google is a Data Processor.\r\n\r\n\r\n9. Terminating the License Agreement\r\n\r\n9.1 The License Agreement will continue to apply until terminated by either you or Google as set out below.\r\n\r\n9.2 If you want to terminate the License Agreement, you may do so by ceasing your use of the SDK and any relevant developer credentials.\r\n\r\n9.3 Google may at any time, terminate the License Agreement with you if: (A) you have breached any provision of the License Agreement; or (B) Google is required to do so by law; or (C) the partner with whom Google offered certain parts of SDK (such as APIs) to you has terminated its relationship with Google or ceased to offer certain parts of the SDK to you; or (D) Google decides to no longer provide the SDK or certain parts of the SDK to users in the country in which you are resident or from which you use the service, or the provision of the SDK or certain SDK services to you by Google is, in Google's sole discretion, no longer commercially viable.\r\n\r\n9.4 When the License Agreement comes to an end, all of the legal rights, obligations and liabilities that you and Google have benefited from, been subject to (or which have accrued over time whilst the License Agreement has been in force) or which are expressed to continue indefinitely, shall be unaffected by this cessation, and the provisions of paragraph 14.7 shall continue to apply to such rights, obligations and liabilities indefinitely.\r\n\r\n\r\n10. DISCLAIMER OF WARRANTIES\r\n\r\n10.1 YOU EXPRESSLY UNDERSTAND AND AGREE THAT YOUR USE OF THE SDK IS AT YOUR SOLE RISK AND THAT THE SDK IS PROVIDED \"AS IS\" AND \"AS AVAILABLE\" WITHOUT WARRANTY OF ANY KIND FROM GOOGLE.\r\n\r\n10.2 YOUR USE OF THE SDK AND ANY MATERIAL DOWNLOADED OR OTHERWISE OBTAINED THROUGH THE USE OF THE SDK IS AT YOUR OWN DISCRETION AND RISK AND YOU ARE SOLELY RESPONSIBLE FOR ANY DAMAGE TO YOUR COMPUTER SYSTEM OR OTHER DEVICE OR LOSS OF DATA THAT RESULTS FROM SUCH USE.\r\n\r\n10.3 GOOGLE FURTHER EXPRESSLY DISCLAIMS ALL WARRANTIES AND CONDITIONS OF ANY KIND, WHETHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO THE IMPLIED WARRANTIES AND CONDITIONS OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.\r\n\r\n\r\n11. LIMITATION OF LIABILITY\r\n\r\n11.1 YOU EXPRESSLY UNDERSTAND AND AGREE THAT GOOGLE, ITS SUBSIDIARIES AND AFFILIATES, AND ITS LICENSORS SHALL NOT BE LIABLE TO YOU UNDER ANY THEORY OF LIABILITY FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, CONSEQUENTIAL OR EXEMPLARY DAMAGES THAT MAY BE INCURRED BY YOU, INCLUDING ANY LOSS OF DATA, WHETHER OR NOT GOOGLE OR ITS REPRESENTATIVES HAVE BEEN ADVISED OF OR SHOULD HAVE BEEN AWARE OF THE POSSIBILITY OF ANY SUCH LOSSES ARISING.\r\n\r\n\r\n12. Indemnification\r\n\r\n12.1 To the maximum extent permitted by law, you agree to defend, indemnify and hold harmless Google, its affiliates and their respective directors, officers, employees and agents from and against any and all claims, actions, suits or proceedings, as well as any and all losses, liabilities, damages, costs and expenses (including reasonable attorneys fees) arising out of or accruing from (a) your use of the SDK, (b) any application you develop on the SDK that infringes any copyright, trademark, trade secret, trade dress, patent or other intellectual property right of any person or defames any person or violates their rights of publicity or privacy, and (c) any non-compliance by you with the License Agreement.\r\n\r\n\r\n13. Changes to the License Agreement\r\n\r\n13.1 Google may make changes to the License Agreement as it distributes new versions of the SDK. When these changes are made, Google will make a new version of the License Agreement available on the website where the SDK is made available.\r\n\r\n\r\n14. General Legal Terms\r\n\r\n14.1 The License Agreement constitutes the whole legal agreement between you and Google and governs your use of the SDK (excluding any services which Google may provide to you under a separate written agreement), and completely replaces any prior agreements between you and Google in relation to the SDK.\r\n\r\n14.2 You agree that if Google does not exercise or enforce any legal right or remedy which is contained in the License Agreement (or which Google has the benefit of under any applicable law), this will not be taken to be a formal waiver of Google's rights and that those rights or remedies will still be available to Google.\r\n\r\n14.3 If any court of law, having the jurisdiction to decide on this matter, rules that any provision of the License Agreement is invalid, then that provision will be removed from the License Agreement without affecting the rest of the License Agreement. The remaining provisions of the License Agreement will continue to be valid and enforceable.\r\n\r\n14.4 You acknowledge and agree that each member of the group of companies of which Google is the parent shall be third party beneficiaries to the License Agreement and that such other companies shall be entitled to directly enforce, and rely upon, any provision of the License Agreement that confers a benefit on (or rights in favor of) them. Other than this, no other person or company shall be third party beneficiaries to the License Agreement.\r\n\r\n14.5 EXPORT RESTRICTIONS. THE SDK IS SUBJECT TO UNITED STATES EXPORT LAWS AND REGULATIONS. YOU MUST COMPLY WITH ALL DOMESTIC AND INTERNATIONAL EXPORT LAWS AND REGULATIONS THAT APPLY TO THE SDK. THESE LAWS INCLUDE RESTRICTIONS ON DESTINATIONS, END USERS AND END USE.\r\n\r\n14.6 The rights granted in the License Agreement may not be assigned or transferred by either you or Google without the prior written approval of the other party. Neither you nor Google shall be permitted to delegate their responsibilities or obligations under the License Agreement without the prior written approval of the other party.\r\n\r\n14.7 The License Agreement, and your relationship with Google under the License Agreement, shall be governed by the laws of the State of California without regard to its conflict of laws provisions. You and Google agree to submit to the exclusive jurisdiction of the courts located within the county of Santa Clara, California to resolve any legal matter arising from the License Agreement. Notwithstanding this, you agree that Google shall still be allowed to apply for injunctive remedies (or an equivalent type of urgent legal relief) in any jurisdiction.\r\n\r\n\r\nJanuary 16, 2019</license><localPackage path=\"build-tools;32.0.0\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>32</major><minor>0</minor><micro>0</micro></revision><display-name>Android SDK Build-Tools 32</display-name><uses-license ref=\"android-sdk-license\"/><dependencies><dependency path=\"tools\"/></dependencies></localPackage></ns2:repository>\r\n```\r\n\r\n</details>\r\n\r\n<details>\r\n <summary>Here is the diff between the `package.xml` file above and `platform-tools/package.xml`</summary>\r\n\r\n ```diff\r\n 141c141\r\n < January 16, 2019</license><localPackage path=\"platform-tools\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>31</major><minor>0</minor><micro>3</micro></revision><display-name>Android SDK Platform-Tools</display-name><uses-license ref=\"android-sdk-license\"/></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ---\r\n > January 16, 2019</license><localPackage path=\"build-tools;32.0.0\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>32</major><minor>0</minor><micro>0</micro></revision><display-name>Android SDK Build-Tools 32</display-name><uses-license ref=\"android-sdk-license\"/><dependencies><dependency path=\"tools\"/></dependencies></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ```\r\n</details>\r\n\r\n<details>\r\n <summary>diff build-tools/32.0.0/package.xml platforms/android-32/package.xml</summary>\r\n\r\n ```diff\r\n 141c141\r\n < January 16, 2019</license><localPackage path=\"build-tools;32.0.0\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>32</major><minor>0</minor><micro>0</micro></revision><display-name>Android SDK Build-Tools 32</display-name><uses-license ref=\"android-sdk-license\"/><dependencies><dependency path=\"tools\"/></dependencies></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ---\r\n > January 16, 2019</license><localPackage path=\"platforms;android-32\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns9:platformDetailsType\"><api-level>32</api-level><codename></codename><layoutlib api=\"15\"/></type-details><revision><major>1</major></revision><display-name>Android SDK Platform 32</display-name><uses-license ref=\"android-sdk-license\"/></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ```\r\n</details>\r\n\r\n<details>\r\n <summary>diff build-tools/32.0.0/package.xml tools/package.xml</summary>\r\n\r\n ```diff\r\n 141c141\r\n < January 16, 2019</license><localPackage path=\"build-tools;32.0.0\" obsolete=\"false\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>32</major><minor>0</minor><micro>0</micro></revision><display-name>Android SDK Build-Tools 32</display-name><uses-license ref=\"android-sdk-license\"/><dependencies><dependency path=\"tools\"/></dependencies></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ---\r\n > January 16, 2019</license><localPackage path=\"tools\" obsolete=\"true\"><type-details xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xsi:type=\"ns5:genericDetailsType\"/><revision><major>26</major><minor>1</minor><micro>1</micro></revision><display-name>Android SDK\r\n Tools</display-name><uses-license ref=\"android-sdk-license\"/><dependencies><dependency path=\"patcher;v4\"/><dependency path=\"emulator\"/><dependency path=\"platform-tools\"><min-revision><major>20</major></min-revision></dependency></dependencies></localPackage></ns2:repository>\r\n \\ No newline at end of file\r\n ```\r\n</details>\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.87, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335072.36480448d47, sops-nix, unstable-22.05pre339739.1dd151f0c0c\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154898/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154862","id":1101431512,"node_id":"I_kwDOAEVQ_M5BpoLY","number":154862,"title":"it is observed that ovs-vswitchd is crashed when restart ovs-vswitchd many times.","user":{"login":"renweichun","id":42081102,"node_id":"MDQ6VXNlcjQyMDgxMTAy","avatar_url":"https://avatars.githubusercontent.com/u/42081102?v=4","gravatar_id":"","url":"https://api.github.com/users/renweichun","html_url":"https://github.com/renweichun","followers_url":"https://api.github.com/users/renweichun/followers","following_url":"https://api.github.com/users/renweichun/following{/other_user}","gists_url":"https://api.github.com/users/renweichun/gists{/gist_id}","starred_url":"https://api.github.com/users/renweichun/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/renweichun/subscriptions","organizations_url":"https://api.github.com/users/renweichun/orgs","repos_url":"https://api.github.com/users/renweichun/repos","events_url":"https://api.github.com/users/renweichun/events{/privacy}","received_events_url":"https://api.github.com/users/renweichun/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-13T09:28:37Z","updated_at":"2022-01-13T12:47:09Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWe are using ovs 2.14.1 and dpdk 20.08 on CentOS Linux release 8.3.2011 with kernel of 5.10.44 and glibc of 2.28. When I restart ovs-vswitchd many times, it is observed that ovs-vswitchd is crashed. After some debugging I found.\r\n I have two ovs crash problems in context with DPDK. OVS process crashes when I restart ovs-vswitchd \r\n------------------------------------------------------------------------------------------------------------------------\r\nFirst stack trace:\r\n#0 ofproto_dpif_credit_table_stats (ofproto=0x3629d20, table_id=0 '\\000', n_matches=195, n_misses=0)\r\n at ofproto/ofproto-dpif.c:4350\r\n#1 0x00000000010cbcac in xlate_push_stats_entry (entry=0x7fa270030588, stats=0x7fff1ed2cac0, offloaded=<optimized out>)\r\n at ofproto/ofproto-dpif-xlate-cache.c:99\r\n#2 0x00000000010cbe7b in xlate_push_stats (xcache=<optimized out>, stats=stats@entry=0x7fff1ed2cac0,\r\n offloaded=offloaded@entry=false) at ofproto/ofproto-dpif-xlate-cache.c:181\r\n#3 0x00000000010b8e27 in push_dp_ops (udpif=udpif@entry=0x36ace90, ops=ops@entry=0x7fff1ed2cfd0, n_ops=n_ops@entry=1)\r\n at ofproto/ofproto-dpif-upcall.c:2409\r\n#4 0x00000000010b9c0e in push_dp_ops (n_ops=n_ops@entry=1, ops=0x7fff1ed2cfd0, ops@entry=0x7fff1ed2b670,\r\n udpif=udpif@entry=0x36ace90) at ofproto/ofproto-dpif-upcall.c:2441\r\n#5 push_ukey_ops (udpif=udpif@entry=0x36ace90, umap=umap@entry=0x36b2288, ops=ops@entry=0x7fff1ed2cfd0,\r\n n_ops=n_ops@entry=1) at ofproto/ofproto-dpif-upcall.c:2441\r\n#6 0x00000000010b9d8b in dp_purge_cb (aux=0x36ace90, pmd_id=25) at ofproto/ofproto-dpif-upcall.c:2870\r\n#7 0x00000000010eb476 in dp_netdev_del_pmd (dp=dp@entry=0x362b110, pmd=pmd@entry=0x7fab57cd8010) at lib/dpif-netdev.c:6555\r\n#8 0x00000000010edec7 in reconfigure_pmd_threads (dp=0x362b110) at lib/dpif-netdev.c:5175\r\n#9 reconfigure_datapath (dp=dp@entry=0x362b110) at lib/dpif-netdev.c:5266\r\n#10 0x00000000010eedbd in do_del_port (dp=0x362b110, port=0x37798f0) at lib/dpif-netdev.c:2287\r\n#11 0x00000000010ef287 in dpif_netdev_port_del (dpif=<optimized out>, port_no=27) at lib/dpif-netdev.c:2182\r\n#12 0x00000000010f935f in dpif_port_del (dpif=0x325b360, port_no=27, local_delete=local_delete@entry=false)\r\n at lib/dpif.c:631\r\n#13 0x00000000010a71b2 in port_destruct (port_=0x3781520, del=<optimized out>) at ofproto/ofproto-dpif.c:2147\r\n#14 0x00000000010935bb in ofport_destroy (port=0x3781520, del=<optimized out>) at ofproto/ofproto.c:2615\r\n#15 0x000000000109b7c0 in ofproto_destroy (p=0x371f120, del=<optimized out>) at ofproto/ofproto.c:1722\r\n#16 0x0000000001085a0e in bridge_destroy (br=0x327bf80, del=del@entry=false) at vswitchd/bridge.c:3605\r\n#17 0x000000000108a369 in bridge_exit (delete_datapath=<optimized out>) at vswitchd/bridge.c:552\r\n#18 0x0000000000573e29 in main (argc=<optimized out>, argv=<optimized out>) at vswitchd/ovs-vswitchd.c:143\r\n\r\n(gdb) info reg\r\nrax 0x0 0\r\nrbx 0x7fa270030588 140335640675720\r\nrcx 0x0 0\r\nrdx 0xc3 195\r\nrsi 0x0 0\r\nrdi 0x3629d20 56794400\r\nrbp 0x7fff1ed2cac0 0x7fff1ed2cac0\r\nrsp 0x7fff1ed2ca48 0x7fff1ed2ca48\r\nr8 0x0 0\r\nr9 0x3803e90 58736272\r\nr10 0x0 0\r\nr11 0x6 6\r\nr12 0x7fff1ed2cac0 140733710518976\r\nr13 0x70030650 1879246416\r\nr14 0x7fff1ed2cab8 140733710518968\r\nr15 0x7fff1ed2cac0 140733710518976\r\nrip 0x10a8818 0x10a8818 <ofproto_dpif_credit_table_stats+56>\r\neflags 0x10206 [ PF IF RF ]\r\ncs 0x33 51\r\nss 0x2b 43\r\nds 0x0 0\r\nes 0x0 0\r\nfs 0x0 0\r\ngs 0x0 0\r\nk0 0x0 0\r\nk1 0x0 0\r\nk2 0x0 0\r\nk3 0x0 0\r\nk4 0x0 0\r\nk5 0x0 0\r\nk6 0x0 0\r\nk7 0x0 0\r\n\r\n(gdb) disassemble 0x10a8818\r\nDump of assembler code for function ofproto_dpif_credit_table_stats:\r\n 0x00000000010a87e0 <+0>:\tmovzbl %sil,%esi\r\n 0x00000000010a87e4 <+4>:\tmov %rsi,%rax\r\n 0x00000000010a87e7 <+7>:\tshl $0x4,%rax\r\n 0x00000000010a87eb <+11>:\tsub %rsi,%rax\r\n 0x00000000010a87ee <+14>:\tshl $0x4,%rax\r\n 0x00000000010a87f2 <+18>:\tadd 0x128(%rdi),%rax\r\n 0x00000000010a87f9 <+25>:\ttest %rdx,%rdx\r\n 0x00000000010a87fc <+28>:\tjne 0x10a8818 <ofproto_dpif_credit_table_stats+56>\r\n 0x00000000010a87fe <+30>:\ttest %rcx,%rcx\r\n 0x00000000010a8801 <+33>:\tjne 0x10a8808 <ofproto_dpif_credit_table_stats+40>\r\n 0x00000000010a8803 <+35>:\tretq\r\n 0x00000000010a8804 <+36>:\tnopl 0x0(%rax)\r\n 0x00000000010a8808 <+40>:\tlock add %rcx,0xe8(%rax)\r\n 0x00000000010a8810 <+48>:\tretq\r\n 0x00000000010a8811 <+49>:\tnopl 0x0(%rax)\r\n=> 0x00000000010a8818 <+56>:\tlock add %rdx,0xe0(%rax)\r\n 0x00000000010a8820 <+64>:\tjmp 0x10a87fe <ofproto_dpif_credit_table_stats+30>\r\nEnd of assembler dump.\r\n\r\n(gdb) p *ofproto\r\n$3 = {all_ofproto_dpifs_by_name_node = {hash = 0, next = 0x3741ba0}, all_ofproto_dpifs_by_uuid_node = {hash = 57992720, next = 0x1051}, up = {hmap_node = {hash = 1163936137340, next = 0x3f0000003f},\r\n ofproto_class = 0xce2b216a, type = 0x0, name = 0x0, fallback_dpid = 0, datapath_id = 0, forward_bpdu = false, mfr_desc = 0x59fdad4700000006 <error: Cannot access memory at address 0x59fdad4700000006>,\r\n hw_desc = 0x430a8cdc868fc310 <error: Cannot access memory at address 0x430a8cdc868fc310>, sw_desc = 0x0, serial_desc = 0x7fa26009fd20 \"\", dp_desc = 0x7fa2600d23d0 \"\", frag_handling = 1611358112, ports = {\r\n buckets = 0x0, one = 0x0, mask = 369490328463343620, n = 2758902708}, port_by_name = {map = {buckets = 0x0, one = 0x7fa2600a4980, mask = 140335372699424, n = 0}}, ofp_requests = {map = {buckets = 0x0,\r\n one = 0x0, mask = 1020897070376026114, n = 0}}, alloc_port_no = 0, max_ports = 0, ofport_usage = {buckets = 0x7fa2600fce40, one = 0x0, mask = 0, n = 0}, change_seq = 0, eviction_group_timer = 0,\r\n tables = 0x0, n_tables = 0, tables_version = 0, cookies = {buckets = 0x0, one = 0x0, mask = 0, n_unique = 0}, learned_cookies = {buckets = 0xa09f639c00000004, one = 0x2b33f99c, mask = 0,\r\n n = 140335372891088}, expirable = {prev = 0x7fa260108cb0, next = 0x0}, meter_features = {max_meters = 0, band_types = 0, capabilities = 0, max_bands = 0 '\\000', max_color = 0 '\\000'}, meters = {\r\n buckets = 0x4b4c0f7a00000002, one = 0x0, mask = 0, n = 140335372886432}, slowpath_meter_id = 0, controller_meter_id = 0, connmgr = 0x0, min_mtu = 0, groups = {impl = {p = 0x0}}, n_groups = {2,\r\n 1415127537, 0, 0}, ogf = {types = 0, capabilities = 0, max_groups = {1612239072, 32674, 0, 0}, ofpacts = {0, 0, 0, 0}}, metadata_tab = {p = 0x0}, vl_mff_map = {cmap = {impl = {p = 0x0}}, mutex = {lock = {\r\n __data = {__lock = 0, __count = 0, __owner = 0, __nusers = 0, __kind = 0, __spins = 0, __elision = 0, __list = {__prev = 0x0, __next = 0x0}}, __size = '\\000' <repeats 39 times>, __align = 0},\r\n where = 0xba27fb500000004 <error: Cannot access memory at address 0xba27fb500000004>}}}, backer = 0x906958e3, uuid = {parts = {0, 0, 1610935792, 32674}}, tables_version = 140335372744048, dump_seq = 0,\r\n miss_rule = 0x0, no_packet_in_rule = 0x0, drop_frags_rule = 0xd79f750d00000006, netflow = 0xf1991026332d2be0, sflow = 0x0, ipfix = 0x7fa260043830, bundles = {buckets = 0x7fa2600a99a0, one = 0x7fa2601fd6b0,\r\n mask = 0, n = 0}, ml = 0xb9971b5200000002, ms = 0x0, has_bonded_bundles = false, lacp_enabled = false, mbridge = 0x7fa260168b50, stats_mutex = {lock = {__data = {__lock = 0, __count = 0, __owner = 0,\r\n __nusers = 0, __kind = 0, __spins = 0, __elision = 0, __list = {__prev = 0x0, __next = 0xc2d8714b00000006}}, __size = '\\000' <repeats 32 times>, \"\\006\\000\\000\\000Kq\\330\", <incomplete sequence \\302>,\r\n __align = 0}, where = 0x3bb82d338c6f5ba6 <error: Cannot access memory at address 0x3bb82d338c6f5ba6>}, stats = {rx_packets = 0, tx_packets = 140335373557152, rx_bytes = 140335373226416,\r\n tx_bytes = 140335372593392, rx_errors = 0, tx_errors = 0, rx_dropped = 8378066835995623426, tx_dropped = 0, multicast = 0, collisions = 140335373981728, rx_length_errors = 0, rx_over_errors = 0,\r\n rx_crc_errors = 0, rx_frame_errors = 0, rx_fifo_errors = 12410622260254081028, rx_missed_errors = 1186231435, tx_aborted_errors = 0, tx_carrier_errors = 140335373939168, tx_fifo_errors = 140335373424512,\r\n tx_heartbeat_errors = 0, tx_window_errors = 0, rx_1_to_64_packets = 0, rx_65_to_127_packets = 0, rx_128_to_255_packets = 0, rx_256_to_511_packets = 0, rx_512_to_1023_packets = 0,\r\n rx_1024_to_1522_packets = 0, rx_1523_to_max_packets = 0, tx_1_to_64_packets = 0, tx_65_to_127_packets = 0, tx_128_to_255_packets = 6361799859137150982, tx_256_to_511_packets = 8919369999343897625,\r\n tx_512_to_1023_packets = 0, tx_1024_to_1522_packets = 140335373711424, tx_1523_to_max_packets = 140335373447328, tx_multicast_packets = 140335373316560, rx_broadcast_packets = 0, tx_broadcast_packets = 0,\r\n rx_undersized_errors = 1507772303897788418, rx_oversize_errors = 0, rx_fragmented_errors = 0, rx_jabber_errors = 0}, stp = 0x0, stp_last_tick = 0, rstp = 0x0, rstp_last_tick = 0, ports = {map = {\r\n buckets = 0xf3c911ba00000004, one = 0xe0e96d08, mask = 0, n = 140335373890928}}, ghost_ports = {map = {buckets = 0x7fa26014ed80, one = 0x0, mask = 0, n = 0}}, port_poll_set = {map = {buckets = 0x0,\r\n one = 0x0, mask = 0, n = 0}}, port_poll_errno = 0, change_seq = 0, ams = {mutex = {lock = {__data = {__lock = 0, __count = 0, __owner = 0, __nusers = 0, __kind = 4, __spins = -26912, __elision = -18608,\r\n __list = {__prev = 0xbb62aa2c, __next = 0x0}}, __size = '\\000' <repeats 16 times>, \"\\004\\000\\000\\000\\340\\226P\\267,\\252b\\273\", '\\000' <repeats 11 times>, __align = 0}, where = 0x7fa260074160 \"\"},\r\n list = {prev = 0x7fa260125520, next = 0x0}, n = 0}, ams_seq = 0x0, ams_seqno = 3765277242901397506, is_controller_connected = false}\r\n\r\n--------------------------------------------------------------------------------------------------------------------------------------\r\nSecond stack trace:\r\n(gdb) bt\r\n#0 0xfffffac0e9000000 in ?? ()\r\n#1 0x00000000010918df in rule_destroy_cb (rule=0x3942430) at ofproto/ofproto.c:2943\r\n#2 0x0000000001175e16 in ovsrcu_call_postponed () at lib/ovs-rcu.c:348\r\n#3 0x0000000001175f04 in ovsrcu_postpone_thread (arg=<optimized out>) at lib/ovs-rcu.c:364\r\n#4 0x000000000117808d in ovsthread_wrapper (aux_=<optimized out>) at lib/ovs-thread.c:383\r\n#5 0x00007fd6f0c5a14a in start_thread () from /lib64/libpthread.so.0\r\n#6 0x00007fd6efeb3f23 in clone () from /lib64/libc.so.6\r\n(gdb) frame 1\r\n#1 0x00000000010918df in rule_destroy_cb (rule=0x3942430) at ofproto/ofproto.c:2943\r\n2943\t rule->ofproto->ofproto_class->rule_destruct(rule);\r\n(gdb) info reg\r\nrax 0x408d00 4230400\r\nrbx 0x3942430 60040240\r\nrcx 0xc11 3089\r\nrdx 0x7fd6b0000080 140560052519040\r\nrsi 0x0 0\r\nrdi 0x3942430 60040240\r\nrbp 0x7fd6b0011be0 0x7fd6b0011be0\r\nrsp 0x7fd6ecb36fb0 0x7fd6ecb36fb0\r\nr8 0x7fd6d8000924 140560723609892\r\nr9 0x7 7\r\nr10 0x2d83b96 47725462\r\nr11 0x206 518\r\nr12 0x7fd6ecb36fc0 140561070911424\r\nr13 0x7fd6ed337ebf 140561079303871\r\nr14 0x7fd6ed337f50 140561079304016\r\nr15 0x7fd6ecb37100 140561070911744\r\nrip 0x10918df 0x10918df <rule_destroy_cb+47>\r\neflags 0x10246 [ PF ZF IF RF ]\r\ncs 0x33 51\r\nss 0x2b 43\r\nds 0x0 0\r\nes 0x0 0\r\nfs 0x0 0\r\ngs 0x0 0\r\nk0 0x0 0\r\nk1 0x0 0\r\nk2 0x0 0\r\nk3 0x0 0\r\nk4 0x0 0\r\nk5 0x0 0\r\nk6 0x0 0\r\nk7 0x0 0\r\n(gdb) disassemble 0x10918df\r\nDump of assembler code for function rule_destroy_cb:\r\n 0x00000000010918b0 <+0>:\tpush %rbx\r\n 0x00000000010918b1 <+1>:\tmov %rdi,%rbx\r\n 0x00000000010918b4 <+4>:\ttestb $0x1,0xa0(%rdi)\r\n 0x00000000010918bb <+11>:\tje 0x10918cf <rule_destroy_cb+31>\r\n 0x00000000010918bd <+13>:\tcmpb $0x6,0xaa(%rdi)\r\n 0x00000000010918c4 <+20>:\tje 0x10918cf <rule_destroy_cb+31>\r\n 0x00000000010918c6 <+22>:\tcmpl $0xffff,0x18(%rdi)\r\n 0x00000000010918cd <+29>:\tjle 0x1091918 <rule_destroy_cb+104>\r\n 0x00000000010918cf <+31>:\tmov (%rbx),%rax\r\n 0x00000000010918d2 <+34>:\tmov %rbx,%rdi\r\n 0x00000000010918d5 <+37>:\tmov 0x10(%rax),%rax\r\n 0x00000000010918d9 <+41>:\tcallq *0x158(%rax)\r\n=> 0x00000000010918df <+47>:\tmov (%rbx),%rax\r\n 0x00000000010918e2 <+50>:\tmov 0x118(%rbx),%rsi\r\n 0x00000000010918e9 <+57>:\tlea 0x210(%rax),%rdi\r\n 0x00000000010918f0 <+64>:\tcallq 0x1117220 <mf_vl_mff_unref>\r\n 0x00000000010918f5 <+69>:\tmov (%rbx),%rax\r\n 0x00000000010918f8 <+72>:\tmov 0x120(%rbx),%rsi\r\n 0x00000000010918ff <+79>:\tlea 0x210(%rax),%rdi\r\n 0x0000000001091906 <+86>:\tcallq 0x1117220 <mf_vl_mff_unref>\r\n 0x000000000109190b <+91>:\tmov %rbx,%rdi\r\n 0x000000000109190e <+94>:\tpop %rbx\r\n 0x000000000109190f <+95>:\tjmpq 0x1090b50 <ofproto_rule_destroy__>\r\n 0x0000000001091914 <+100>:\tnopl 0x0(%rax)\r\n 0x0000000001091918 <+104>:\tcallq 0x1091760 <ofproto_rule_send_removed>\r\n 0x000000000109191d <+109>:\tjmp 0x10918cf <rule_destroy_cb+31>\r\nEnd of assembler dump.\r\n(gdb) p *rule\r\n$1 = {ofproto = 0x37623e0, cr = {node = {prev = 0xcccccccccccccccc, next = {p = 0x3874bc0}}, priority = 0, cls_match = {p = 0x0}, match = {{{flow = 0x38e9de0, mask = 0x38e9df0}, flows = {0x38e9de0,\r\n 0x38e9df0}}, tun_md = 0x0}}, table_id = 0 '\\000', state = RULE_REMOVED, mutex = {lock = {__data = {__lock = 0, __count = 0, __owner = 0, __nusers = 0, __kind = 2, __spins = 0, __elision = 0,\r\n __list = {__prev = 0x0, __next = 0x0}}, __size = '\\000' <repeats 16 times>, \"\\002\", '\\000' <repeats 22 times>, __align = 0}, where = 0x14ab7e8 \"<unlocked>\"}, ref_count = {count = 0},\r\n flow_cookie = 5638004435696427197, cookie_node = {hash = 3567688855, d = 0x387b8b8, s = 0x0}, flags = (unknown: 0), hard_timeout = 0, idle_timeout = 0, importance = 0, removed_reason = 2 '\\002',\r\n eviction_group = 0x0, evg_node = {idx = 0, priority = 0}, actions = 0x3889fa0, meter_list_node = {prev = 0x3942500, next = 0x3942500}, monitor_flags = (unknown: 0), add_seqno = 49, modify_seqno = 49,\r\n expirable = {prev = 0x3942528, next = 0x3942528}, created = 95441005, modified = 95441005, match_tlv_bitmap = 0, ofpacts_tlv_bitmap = 0}\r\n(gdb) p *rule->ofproto->ofproto_class->rule_destruct\r\nCannot access memory at address 0xfffffac0e9000000\r\n(gdb)\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. systemctl restart openvswitch for many times\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nThere is a ovs crash problem ,which is stack trace as above. \r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\novs-dev@openvswitch.org\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154862/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154832","id":1101015473,"node_id":"I_kwDOAEVQ_M5BoCmx","number":154832,"title":"libjxl-0.6.1 fails to build on i686 architechture in nixos-unstable","user":{"login":"llirium","id":35014749,"node_id":"MDQ6VXNlcjM1MDE0NzQ5","avatar_url":"https://avatars.githubusercontent.com/u/35014749?v=4","gravatar_id":"","url":"https://api.github.com/users/llirium","html_url":"https://github.com/llirium","followers_url":"https://api.github.com/users/llirium/followers","following_url":"https://api.github.com/users/llirium/following{/other_user}","gists_url":"https://api.github.com/users/llirium/gists{/gist_id}","starred_url":"https://api.github.com/users/llirium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/llirium/subscriptions","organizations_url":"https://api.github.com/users/llirium/orgs","repos_url":"https://api.github.com/users/llirium/repos","events_url":"https://api.github.com/users/llirium/events{/privacy}","received_events_url":"https://api.github.com/users/llirium/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-13T01:33:26Z","updated_at":"2022-04-15T10:43:36Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nlibjxl-0.6.1 fails to build on i686-based ASUS Eee PC 1000HE\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. enable lxqt and lightdm in `configuration.nix`\r\n2. `nixos-rebuild switch`\r\n\r\n### Expected behavior\r\ncompilation succeeds.\r\n\r\n### Additional context\r\nBuild log was enormous, so the log has been trimmed to show only Failed tests:\r\n[libjxl-0.6.1_build_errors_trimmed.log](https://github.com/NixOS/nixpkgs/files/7859074/libjxl-0.6.1_build_errors_trimmed.log)\r\n\r\n### Notify maintainers\r\n@nh2\r\n\r\n### Metadata\r\n - system: `\"i686-linux\"`\r\n - host os: `Linux 5.10.90, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre344851.0ecf7d41481\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154832/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154808","id":1100805365,"node_id":"I_kwDOAEVQ_M5BnPT1","number":154808,"title":"Cinnamon module conflicts with the KDE theme manager","user":{"login":"Baughn","id":45811,"node_id":"MDQ6VXNlcjQ1ODEx","avatar_url":"https://avatars.githubusercontent.com/u/45811?v=4","gravatar_id":"","url":"https://api.github.com/users/Baughn","html_url":"https://github.com/Baughn","followers_url":"https://api.github.com/users/Baughn/followers","following_url":"https://api.github.com/users/Baughn/following{/other_user}","gists_url":"https://api.github.com/users/Baughn/gists{/gist_id}","starred_url":"https://api.github.com/users/Baughn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Baughn/subscriptions","organizations_url":"https://api.github.com/users/Baughn/orgs","repos_url":"https://api.github.com/users/Baughn/repos","events_url":"https://api.github.com/users/Baughn/events{/privacy}","received_events_url":"https://api.github.com/users/Baughn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-12T21:27:56Z","updated_at":"2022-01-13T01:40:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nIf `services.xserver.cinnamon.enable` is set, then https://github.com/NixOS/nixpkgs/blob/master/nixos/modules/services/x11/desktop-managers/cinnamon.nix#L181 sets `qt5.enable`, along with some settings I presume are usable in a Cinnamon configuration. This ends up setting `QT_STYLE_OVERRIDE=adwaita`.\r\n\r\nIf KDE is also enabled then this overrides only part of the application theme. If the user then also selects a 'dark' style such as adwaita-dark, then the result is light grey text on a light grey background. For foreground windows this renders their text entirely invisible.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable cinnamon & plasma5.\r\n2. Launch plasma5, and select Breeze Dark.\r\n3. Run any of a number of applications, for instance Spectacle.\r\n\r\n### Expected behavior\r\nThemes should be consistent, or at least text should be readable. Alternately, there should be an assert to prevent this scenario.\r\n\r\n### Screenshots\r\nhttps://usercontent.irccloud-cdn.com/file/aqvj3AcZ/image.png\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@mkg20001 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `relaxed`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154808/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154789","id":1100656644,"node_id":"I_kwDOAEVQ_M5BmrAE","number":154789,"title":"Packaging request: armorpaint","user":{"login":"Shou","id":819413,"node_id":"MDQ6VXNlcjgxOTQxMw==","avatar_url":"https://avatars.githubusercontent.com/u/819413?v=4","gravatar_id":"","url":"https://api.github.com/users/Shou","html_url":"https://github.com/Shou","followers_url":"https://api.github.com/users/Shou/followers","following_url":"https://api.github.com/users/Shou/following{/other_user}","gists_url":"https://api.github.com/users/Shou/gists{/gist_id}","starred_url":"https://api.github.com/users/Shou/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Shou/subscriptions","organizations_url":"https://api.github.com/users/Shou/orgs","repos_url":"https://api.github.com/users/Shou/repos","events_url":"https://api.github.com/users/Shou/events{/privacy}","received_events_url":"https://api.github.com/users/Shou/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-12T18:24:41Z","updated_at":"2022-01-12T20:23:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n3D PBR Texture Painting Software\r\n\r\nI've already written a Nixpkg derivation[1] that seems to work okay, but it needs a maintainer and some cleaning up.\r\n\r\n[1] https://github.com/Shou/nixos-configuration/blob/7ef312ba6886f8ce11ef3f114ebe9416251074d8/pkgs/armorpaint/default.nix\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://armorpaint.org/\r\n* source URL: https://github.com/armory3d/armorpaint\r\n* license: zlib/libpng\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154789/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154774","id":1100502047,"node_id":"I_kwDOAEVQ_M5BmFQf","number":154774,"title":"[RFC] PHP should be compiled with ZTS or not ?","user":{"login":"drupol","id":252042,"node_id":"MDQ6VXNlcjI1MjA0Mg==","avatar_url":"https://avatars.githubusercontent.com/u/252042?v=4","gravatar_id":"","url":"https://api.github.com/users/drupol","html_url":"https://github.com/drupol","followers_url":"https://api.github.com/users/drupol/followers","following_url":"https://api.github.com/users/drupol/following{/other_user}","gists_url":"https://api.github.com/users/drupol/gists{/gist_id}","starred_url":"https://api.github.com/users/drupol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/drupol/subscriptions","organizations_url":"https://api.github.com/users/drupol/orgs","repos_url":"https://api.github.com/users/drupol/repos","events_url":"https://api.github.com/users/drupol/events{/privacy}","received_events_url":"https://api.github.com/users/drupol/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-01-12T15:52:31Z","updated_at":"2022-01-23T14:25:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Hi,\r\n\r\nI'm opening this RFC hoping to gather comments from the Apache and PHP maintainers.\r\n\r\nWe know that there are two ways to compile the PHP interpreter (_yeah there are many others but in this thread, only those flags are relevant_):\r\n* `NTS`: Non-Thread Safe\r\n* `ZTS`: Zend-Thread Safe\r\n\r\nMe, as a PHP developer, I remember these rules:\r\n\r\n* When PHP is meant to be used with `mod_php` in Apache -> it's better to use `ZTS`\r\n* When PHP is meant to used with CGI/FASTCGI/Nginx/CommandLine -> It's better `NTS`\r\n\r\nThe default PHP in Nixos is built with `ZTS` and I think it should be `NTS`. `NTS` is also the default in many other distributions.\r\n\r\nWhat's your point of view about that?\r\n\r\nRelevant links:\r\n* https://externals.io/message/65332\r\n* https://github.com/oerdnj/deb.sury.org/issues/1419\r\n* https://github.com/fossar/nix-phps/issues/63\r\n\r\nCC:\r\n* Apache maintainers: @lovek323\r\n* PHP maintainers: @aanderse @etu @globin @ma27 @talyz ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154774/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154772","id":1100467407,"node_id":"I_kwDOAEVQ_M5Bl8zP","number":154772,"title":"Packaging request: wldash","user":{"login":"coolshaurya","id":32027323,"node_id":"MDQ6VXNlcjMyMDI3MzIz","avatar_url":"https://avatars.githubusercontent.com/u/32027323?v=4","gravatar_id":"","url":"https://api.github.com/users/coolshaurya","html_url":"https://github.com/coolshaurya","followers_url":"https://api.github.com/users/coolshaurya/followers","following_url":"https://api.github.com/users/coolshaurya/following{/other_user}","gists_url":"https://api.github.com/users/coolshaurya/gists{/gist_id}","starred_url":"https://api.github.com/users/coolshaurya/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/coolshaurya/subscriptions","organizations_url":"https://api.github.com/users/coolshaurya/orgs","repos_url":"https://api.github.com/users/coolshaurya/repos","events_url":"https://api.github.com/users/coolshaurya/events{/privacy}","received_events_url":"https://api.github.com/users/coolshaurya/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-12T15:21:41Z","updated_at":"2022-01-12T23:56:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n\r\nA dashboard/launcher/control-panel thing for Wayland.\r\n\r\n\r\n\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/kennylevinsen/wldash\r\n* source URL: https://github.com/kennylevinsen/wldash\r\n* license: GPL 3.0\r\n* platforms: linux, only wayland, only wlroots compositors\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154772/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154762","id":1100355519,"node_id":"I_kwDOAEVQ_M5Blhe_","number":154762,"title":"dhall-toml","user":{"login":"mainrs","id":5113257,"node_id":"MDQ6VXNlcjUxMTMyNTc=","avatar_url":"https://avatars.githubusercontent.com/u/5113257?v=4","gravatar_id":"","url":"https://api.github.com/users/mainrs","html_url":"https://github.com/mainrs","followers_url":"https://api.github.com/users/mainrs/followers","following_url":"https://api.github.com/users/mainrs/following{/other_user}","gists_url":"https://api.github.com/users/mainrs/gists{/gist_id}","starred_url":"https://api.github.com/users/mainrs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mainrs/subscriptions","organizations_url":"https://api.github.com/users/mainrs/orgs","repos_url":"https://api.github.com/users/mainrs/repos","events_url":"https://api.github.com/users/mainrs/events{/privacy}","received_events_url":"https://api.github.com/users/mainrs/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-12T13:39:29Z","updated_at":"2022-01-12T16:45:55Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nA CLI that converts dhall expressions to toml.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/dhall-lang/dhall-haskell\r\n* source URL: https://github.com/dhall-lang/dhall-haskell/tree/master/dhall-toml\r\n* license: bsd\r\n* platforms: unix, linux, darwin\r\n* maintainers: @Gabriel439 \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154762/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154761","id":1100345564,"node_id":"I_kwDOAEVQ_M5BlfDc","number":154761,"title":"manpages: empty $out/bin","user":{"login":"KAction","id":44864956,"node_id":"MDQ6VXNlcjQ0ODY0OTU2","avatar_url":"https://avatars.githubusercontent.com/u/44864956?v=4","gravatar_id":"","url":"https://api.github.com/users/KAction","html_url":"https://github.com/KAction","followers_url":"https://api.github.com/users/KAction/followers","following_url":"https://api.github.com/users/KAction/following{/other_user}","gists_url":"https://api.github.com/users/KAction/gists{/gist_id}","starred_url":"https://api.github.com/users/KAction/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/KAction/subscriptions","organizations_url":"https://api.github.com/users/KAction/orgs","repos_url":"https://api.github.com/users/KAction/repos","events_url":"https://api.github.com/users/KAction/events{/privacy}","received_events_url":"https://api.github.com/users/KAction/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-12T13:30:39Z","updated_at":"2022-01-17T20:23:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"```\n$ nix-build -A manpages\n/nix/store/l74pj6cxz94yc1lmwkm4c36nkpw6yj0b-man-pages-5.13\n$ ls ./result/\nbin\nshare\n$ ls -a ./result/bin/\n.\n..\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154761/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154754","id":1100274583,"node_id":"I_kwDOAEVQ_M5BlNuX","number":154754,"title":"python.interpreter on inline scripts using python for python packages","user":{"login":"lucasew","id":15693688,"node_id":"MDQ6VXNlcjE1NjkzNjg4","avatar_url":"https://avatars.githubusercontent.com/u/15693688?v=4","gravatar_id":"","url":"https://api.github.com/users/lucasew","html_url":"https://github.com/lucasew","followers_url":"https://api.github.com/users/lucasew/followers","following_url":"https://api.github.com/users/lucasew/following{/other_user}","gists_url":"https://api.github.com/users/lucasew/gists{/gist_id}","starred_url":"https://api.github.com/users/lucasew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lucasew/subscriptions","organizations_url":"https://api.github.com/users/lucasew/orgs","repos_url":"https://api.github.com/users/lucasew/repos","events_url":"https://api.github.com/users/lucasew/events{/privacy}","received_events_url":"https://api.github.com/users/lucasew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-12T12:18:47Z","updated_at":"2022-01-13T01:35:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhile working on #153896 I received [this review](https://github.com/NixOS/nixpkgs/pull/153896#discussion_r782340298) from @jonringer about the python interpreter used and then checked on other packages. There are some of them that got merged without this detail, even PRs authored by me.\r\n\r\nI plan this as a tracking issue, I might send a PR fixing the occurences\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Clone nixpkgs\r\n2. cd into `pkgs/development/python-modules`\r\n3. with ripgrep, run `rg 'python '`\r\n4. Look for likely occurences\r\n\r\n### Expected behavior\r\nPython calls using `${python.interpreter}` instead of plain `python`\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nWhen I realized this the branch I am working on was based on `568e0bc498ee51fdd88e1e94089de05f2fdbd18b`\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/store/ydkfjk5v61jw0xvlzxcsfw7x59shzp4y-source`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154754/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154737","id":1100144600,"node_id":"I_kwDOAEVQ_M5Bkt_Y","number":154737,"title":"Support pluggable ethernet devices (avoid \"Timed out while waiting for device\")","user":{"login":"rien","id":3226995,"node_id":"MDQ6VXNlcjMyMjY5OTU=","avatar_url":"https://avatars.githubusercontent.com/u/3226995?v=4","gravatar_id":"","url":"https://api.github.com/users/rien","html_url":"https://github.com/rien","followers_url":"https://api.github.com/users/rien/followers","following_url":"https://api.github.com/users/rien/following{/other_user}","gists_url":"https://api.github.com/users/rien/gists{/gist_id}","starred_url":"https://api.github.com/users/rien/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rien/subscriptions","organizations_url":"https://api.github.com/users/rien/orgs","repos_url":"https://api.github.com/users/rien/repos","events_url":"https://api.github.com/users/rien/events{/privacy}","received_events_url":"https://api.github.com/users/rien/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-12T10:10:55Z","updated_at":"2022-01-13T01:35:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI have configured a pluggable ethernet device (from a dock) on my NixOS system with `networking.interfaces.enp0s13f0u1u4.useDHCP = true`. When I boot without the dock plugged in, it now waits 1m30s for the ethernet device to appear (which won't happen) and then proceed booting normally. \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Configure a pluggable or non-existing ethernet device\r\n2. Boot without the device \r\n3. Systemd will show a message: `Waiting for a start job for device ...`\r\n4. After 1m30s, systemd will time out logging `Timed out waiting for device /sys/subsystem/net/devices/enp0s13f0u1u4`\r\n5. The boot completes succesfully\r\n\r\n### Expected behavior\r\n\r\nIf the pluggable ethernet device is not present when booting, systemd should not needlessly delay the booting process by waiting on the device to appear.\r\n\r\nThis should probably not be the default behavior however, since some systems depend on an ethernet connection to be present. We probably want an option to set `networking.interfaces.<name>.pluggable = true;` to enable skipping the device at boot time.\r\n\r\n### Additional context\r\nI am using a Dell XPS 13 with a dock.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@symphorien, @Artturin, @rnhmjoj\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(rien): `\"\"`\r\n - nixpkgs: `/etc/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154737/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154690","id":1099759287,"node_id":"I_kwDOAEVQ_M5BjP63","number":154690,"title":"ncmpcpp fails to display non latin symbols","user":{"login":"Sciencentistguy","id":4983935,"node_id":"MDQ6VXNlcjQ5ODM5MzU=","avatar_url":"https://avatars.githubusercontent.com/u/4983935?v=4","gravatar_id":"","url":"https://api.github.com/users/Sciencentistguy","html_url":"https://github.com/Sciencentistguy","followers_url":"https://api.github.com/users/Sciencentistguy/followers","following_url":"https://api.github.com/users/Sciencentistguy/following{/other_user}","gists_url":"https://api.github.com/users/Sciencentistguy/gists{/gist_id}","starred_url":"https://api.github.com/users/Sciencentistguy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Sciencentistguy/subscriptions","organizations_url":"https://api.github.com/users/Sciencentistguy/orgs","repos_url":"https://api.github.com/users/Sciencentistguy/repos","events_url":"https://api.github.com/users/Sciencentistguy/events{/privacy}","received_events_url":"https://api.github.com/users/Sciencentistguy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-12T00:53:38Z","updated_at":"2022-01-18T13:16:01Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nncmpcpp fails to display (at least) Japanese and Cyrillic characters in song titles or file names.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have a non-latin script character in a song title\r\n2. It doesn't display properly\r\n\r\n### Expected behavior\r\nIt should display the characters correctly\r\n\r\n### Screenshots\r\nLeft is a system-wide ncmpcpp installed with pacman, displaying the correct behavior. Right is the broken nix version\r\n\r\n\r\n\r\n\r\n\r\n\r\n### Additional context\r\nI am running nix on Arch linux.\r\n\r\n### Notify maintainers\r\n@jfrankenau @k0ral @lovek323 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12-arch1-1, Arch Linux, noversion`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixgl, nixpkgs-22.05pre344883.27d2fe1e69d\"`\r\n - channels(jamie): `\"nixpkgs-21.11pre329302.d14ae62671f\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154690/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154626","id":1099484947,"node_id":"I_kwDOAEVQ_M5BiM8T","number":154626,"title":"npm package: speccy ","user":{"login":"cixel","id":3770250,"node_id":"MDQ6VXNlcjM3NzAyNTA=","avatar_url":"https://avatars.githubusercontent.com/u/3770250?v=4","gravatar_id":"","url":"https://api.github.com/users/cixel","html_url":"https://github.com/cixel","followers_url":"https://api.github.com/users/cixel/followers","following_url":"https://api.github.com/users/cixel/following{/other_user}","gists_url":"https://api.github.com/users/cixel/gists{/gist_id}","starred_url":"https://api.github.com/users/cixel/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cixel/subscriptions","organizations_url":"https://api.github.com/users/cixel/orgs","repos_url":"https://api.github.com/users/cixel/repos","events_url":"https://api.github.com/users/cixel/events{/privacy}","received_events_url":"https://api.github.com/users/cixel/received_events","type":"User","site_admin":false},"labels":[{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-11T18:18:36Z","updated_at":"2022-01-12T06:00:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n[speccy](https://www.npmjs.com/package/speccy) is a tool for working with OpenAPI 3.0 specs. It includes a linter, and an html docs viewer.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://speccy.io/ (the project lists this as the home page, but it's been dead for a couple of months now at least)\r\n* source URL: https://github.com/wework/speccy\r\n* license: MIT\r\n* platforms: I've only used on **darwin**, but this is a node.js project and a cursory glance does not indicate it has any OS dependencies, so it's likely to work elsewhere.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154626/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154613","id":1099438446,"node_id":"I_kwDOAEVQ_M5BiBlu","number":154613,"title":"cdemu: missing Dbus service (regression)","user":{"login":"vvs-","id":5171934,"node_id":"MDQ6VXNlcjUxNzE5MzQ=","avatar_url":"https://avatars.githubusercontent.com/u/5171934?v=4","gravatar_id":"","url":"https://api.github.com/users/vvs-","html_url":"https://github.com/vvs-","followers_url":"https://api.github.com/users/vvs-/followers","following_url":"https://api.github.com/users/vvs-/following{/other_user}","gists_url":"https://api.github.com/users/vvs-/gists{/gist_id}","starred_url":"https://api.github.com/users/vvs-/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vvs-/subscriptions","organizations_url":"https://api.github.com/users/vvs-/orgs","repos_url":"https://api.github.com/users/vvs-/repos","events_url":"https://api.github.com/users/vvs-/events{/privacy}","received_events_url":"https://api.github.com/users/vvs-/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-11T17:26:37Z","updated_at":"2022-01-23T21:16:31Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nThere is no Dbus service file in the derivation outputs. This prevents `cdemu-daemon` from starting on demand. It works if it was started manually beforehand.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. run `cdemu status`\r\n\r\n### Expected behavior\r\nThere should be a message about device slot 0 not loaded. But instead there is an error: `ERROR: Failed to acquire daemon interface version (this most likely means your daemon is out-of-date): g-dbus-error-quark: GDBus.Error:org.freedesktop.DBus.Error.ServiceUnknown: The name net.sf.cdemu.CDEmuDaemon was not provided by any .service files (2)`\r\n\r\n### Additional context\r\nThis is a regression from at least NixOS 20.09 where this file was present. Apparently some `nixpkgs` defaults were changed since then.\r\n\r\n### Notify maintainers\r\n@bendlas\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154613/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154555","id":1099152841,"node_id":"I_kwDOAEVQ_M5Bg73J","number":154555,"title":"split2flac: broken (but not developed anymore, remove?)","user":{"login":"dschrempf","id":5596239,"node_id":"MDQ6VXNlcjU1OTYyMzk=","avatar_url":"https://avatars.githubusercontent.com/u/5596239?v=4","gravatar_id":"","url":"https://api.github.com/users/dschrempf","html_url":"https://github.com/dschrempf","followers_url":"https://api.github.com/users/dschrempf/followers","following_url":"https://api.github.com/users/dschrempf/following{/other_user}","gists_url":"https://api.github.com/users/dschrempf/gists{/gist_id}","starred_url":"https://api.github.com/users/dschrempf/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dschrempf/subscriptions","organizations_url":"https://api.github.com/users/dschrempf/orgs","repos_url":"https://api.github.com/users/dschrempf/repos","events_url":"https://api.github.com/users/dschrempf/events{/privacy}","received_events_url":"https://api.github.com/users/dschrempf/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290122996,"node_id":"MDU6TGFiZWwyOTAxMjI5OTY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20clean-up","name":"9.needs: clean-up","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-11T13:29:07Z","updated_at":"2022-01-13T18:15:31Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`split2flac` fails to compile on `nixos-unstable` because of a broken Python 2 dependency (`pytest-forked`).\r\n\r\n### Additional context\r\nAccording to the github home page, `split2flac` is not anymore developed and replaced by `unflac`, see https://git.sr.ht/~ft/unflac,\r\n\r\n### Notify maintainers\r\n@jfrankenau","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154555/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154544","id":1099111575,"node_id":"I_kwDOAEVQ_M5BgxyX","number":154544,"title":"New maintainer needed for assh","user":{"login":"zzamboni","id":32876,"node_id":"MDQ6VXNlcjMyODc2","avatar_url":"https://avatars.githubusercontent.com/u/32876?v=4","gravatar_id":"","url":"https://api.github.com/users/zzamboni","html_url":"https://github.com/zzamboni","followers_url":"https://api.github.com/users/zzamboni/followers","following_url":"https://api.github.com/users/zzamboni/following{/other_user}","gists_url":"https://api.github.com/users/zzamboni/gists{/gist_id}","starred_url":"https://api.github.com/users/zzamboni/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/zzamboni/subscriptions","organizations_url":"https://api.github.com/users/zzamboni/orgs","repos_url":"https://api.github.com/users/zzamboni/repos","events_url":"https://api.github.com/users/zzamboni/events{/privacy}","received_events_url":"https://api.github.com/users/zzamboni/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-11T12:47:28Z","updated_at":"2022-01-11T12:47:28Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"## Issue description\r\n\r\nI originally contributed the [assh](https://github.com/NixOS/nixpkgs/blob/master/pkgs/tools/networking/assh/default.nix) package some time ago, but I no longer use Nix, so I should not be listed as the maintainer anymore.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154544/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154492","id":1098935355,"node_id":"I_kwDOAEVQ_M5BgGw7","number":154492,"title":"DPDK building fails on arm64","user":{"login":"xin3liang","id":6204206,"node_id":"MDQ6VXNlcjYyMDQyMDY=","avatar_url":"https://avatars.githubusercontent.com/u/6204206?v=4","gravatar_id":"","url":"https://api.github.com/users/xin3liang","html_url":"https://github.com/xin3liang","followers_url":"https://api.github.com/users/xin3liang/followers","following_url":"https://api.github.com/users/xin3liang/following{/other_user}","gists_url":"https://api.github.com/users/xin3liang/gists{/gist_id}","starred_url":"https://api.github.com/users/xin3liang/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/xin3liang/subscriptions","organizations_url":"https://api.github.com/users/xin3liang/orgs","repos_url":"https://api.github.com/users/xin3liang/repos","events_url":"https://api.github.com/users/xin3liang/events{/privacy}","received_events_url":"https://api.github.com/users/xin3liang/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-11T09:59:51Z","updated_at":"2022-01-14T02:38:12Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nDPDK building fails on arm64.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ``$ nix-build -A dpdk``\r\n\r\n### Expected behavior\r\nBuild success\r\n\r\n### Additional context\r\n```console\r\n$ nix-build -A dpdk\r\n...\r\nCompiler for C supports arguments -Wno-missing-field-initializers: YES\r\nProgram /build/dpdk-21.02/config/arm/armv8_machine.py found: YES (/build/dpdk-21.02/config/arm/armv8_machine.py)\r\n\r\nconfig/arm/meson.build:445:4: ERROR: Problem encountered: Error when getting Arm Implementer ID and part number.\r\n\r\nA full log can be found at /build/dpdk-21.02/build/meson-logs/meson-log.txt\r\nerror: builder for '/nix/store/mincq33z7w6dhvilqmv0h1nhf59qg9na-dpdk-21.02.drv' failed with exit code 1\r\n```\r\n\r\nconfig/arm/meson.build reelate code\r\n```\r\n437 detect_vendor = find_program(join_paths(meson.current_source_dir(),\r\n438 'armv8_machine.py'))\r\n439 cmd = run_command(detect_vendor.path())\r\n440 if cmd.returncode() == 0\r\n441 cmd_output = cmd.stdout().to_lower().strip().split(' ')\r\n442 implementer_id = cmd_output[0]\r\n443 part_number = cmd_output[3]\r\n444 else\r\n445 error('Error when getting Arm Implementer ID and part number.')\r\n446 endif\r\n```\r\n\r\nFile armv8_machine.py\r\n```\r\n 1 #!/usr/bin/env python3\r\n 2 # SPDX-License-Identifier: BSD-3-Clause\r\n 3 # Copyright(c) 2017 Cavium, Inc\r\n 4\r\n 5 ident = []\r\n 6 fname = '/sys/devices/system/cpu/cpu0/regs/identification/midr_el1'\r\n 7 with open(fname) as f:\r\n 8 content = f.read()\r\n 9\r\n 10 midr_el1 = (int(content.rstrip('\\n'), 16))\r\n 11\r\n 12 ident.append(hex((midr_el1 >> 24) & 0xFF)) # Implementer\r\n 13 ident.append(hex((midr_el1 >> 20) & 0xF)) # Variant\r\n 14 ident.append(hex((midr_el1 >> 16) & 0XF)) # Architecture\r\n 15 ident.append(hex((midr_el1 >> 4) & 0xFFF)) # Primary Part number\r\n 16 ident.append(hex(midr_el1 & 0xF)) # Revision\r\n 17\r\n 18 print(' '.join(ident))\r\n```\r\n```console\r\n$ /nix/store/9akqxpvd20pc527zx8r0p2zy42kaj33m-source/dpdk/config/arm/armv8_machine.py\r\n0x43 0x1 0xf 0xaf 0x1\r\n$ echo $?\r\n0\r\n\r\n```\r\n\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n...\r\n - system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.4.0-90-generic, Ubuntu, 20.04.2 LTS (Focal Fossa)`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(ubuntu): `\"nixpkgs-22.05pre345162.81f05d871fa\"`\r\n - nixpkgs: `/home/ubuntu/.nix-defexpr/channels/nixpkgs`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154492/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154479","id":1098857725,"node_id":"I_kwDOAEVQ_M5Bfzz9","number":154479,"title":"steamrt copy of libcurl-gnutls.so.4 segfaults when used in steam fhs-env","user":{"login":"anund","id":1087544,"node_id":"MDQ6VXNlcjEwODc1NDQ=","avatar_url":"https://avatars.githubusercontent.com/u/1087544?v=4","gravatar_id":"","url":"https://api.github.com/users/anund","html_url":"https://github.com/anund","followers_url":"https://api.github.com/users/anund/followers","following_url":"https://api.github.com/users/anund/following{/other_user}","gists_url":"https://api.github.com/users/anund/gists{/gist_id}","starred_url":"https://api.github.com/users/anund/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/anund/subscriptions","organizations_url":"https://api.github.com/users/anund/orgs","repos_url":"https://api.github.com/users/anund/repos","events_url":"https://api.github.com/users/anund/events{/privacy}","received_events_url":"https://api.github.com/users/anund/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-01-11T08:40:31Z","updated_at":"2022-01-13T07:23:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nAttempting to launch the linux version of the steam game 'The Eternal Castle [REMASTERED]' results in a crash and the message 'Segmentation fault (core dumped)'. A gdb back trace contains the following: \r\n```\r\nThread 1 \"TheEternalCastl\" received signal SIGSEGV, Segmentation fault.\r\n0x00007ffff7d9eb00 in curl_multi_remove_handle () from /steamrt/amd64/usr/lib/x86_64-linux-gnu/libcurl-gnutls.so.4\r\n(gdb) backtrace\r\n#0 0x00007ffff7d9eb00 in curl_multi_remove_handle () from /steamrt/amd64/usr/lib/x86_64-linux-gnu/libcurl-gnutls.so.4\r\n#1 0x0000000001445946 in ?? ()\r\n#2 0x00000000016a9e7f in ?? ()\r\n#3 0x000000000159b4fe in ?? ()\r\n#4 0x000000000159b8ef in ?? ()\r\n#5 0x0000000001406b52 in ?? ()\r\n#6 0x00007ffff6e19780 in __libc_start_main () from /lib64/libc.so.6\r\n#7 0x000000000040a1f5 in ?? ()\r\n#8 0x00007fffffffbab8 in ?? ()\r\n#9 0x000000000000001c in ?? ()\r\n#10 0x0000000000000001 in ?? ()\r\n#11 0x00007fffffffc0e5 in ?? ()\r\n#12 0x0000000000000000 in ?? ()\r\n(gdb) quit\r\n```\r\n\r\nSteam uses a custom override to define curl in the fhs-env [here](https://github.com/NixOS/nixpkgs/blob/master/pkgs/games/steam/fhsenv.nix#L189) (and [appimage-run](https://github.com/NixOS/nixpkgs/blob/master/pkgs/build-support/appimage/default.nix#L109)). This compiles curl against `gnutls` and requires additional [libraries](https://github.com/NixOS/nixpkgs/blob/master/pkgs/tools/networking/curl/default.nix#L130-L134) at runtime. Since curl is being overridden as a one-liner only the `.bin` output is being passed by default leaving `libcurl-gnutls.so*` out of the built fhs-env.\r\n\r\nWork around then becomes.\r\n```\r\n nixpkgs.config.packageOverrides = let\r\n curlWithGnuTls = (pkgs.curl.override { \r\n gnutlsSupport = true; \r\n opensslSupport = false; \r\n });\r\n in pkgs: {\r\n steam = pkgs.steam.override {\r\n extraPkgs = pkgs: with pkgs; [\r\n # The Eternal Castle [REMASTERED]\r\n curlWithGnuTls # curl as already defined by steam \r\n curlWithGnuTls.out # missing /lib contents\r\n ];\r\n };\r\n };\r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Launch 'The Eternal Castle [REMASTERED]' via the linux release (not the proton compatibility mode which can also fix the issue)\r\n2. See seg fault + crash\r\n\r\n### Expected behavior\r\nGame launches\r\n\r\n### Additional context\r\nThis is likely a problem for fhsenv wrappers (affecting steam and appimage) or an issue with ether the way curl is packaged (affecting ~6 packages).\r\n\r\n### Notify maintainers\r\n@jagajaga (steam maintainer). Steam likely needs two dependencies added to fhs-env to allow curl + gnutls to function.\r\n@ShamrockLee (appimage maintainer). Appimage may? need similar dependency changes as it also uses `curl.override...` to use gnutls\r\nCurl maintainer maybe interested if curl.override needs to be catered for differently in the curl package.\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 22.05 (Quokka)`\r\n```\r\n\r\nAdditional details:\r\n<details>\r\n <summary>Incorrect workaround</summary>\r\n\r\nhttps://steamcommunity.com/app/751780/discussions/1/1639787494965532434/ Suggests this sort of failure for a different game was a packaging issue on Arch. Suggested fix in that case involved pulling the instance of curl packaged by debian and changing LD_LIBRARY_PATH to use it instead. That results in \r\n```\r\n./TheEternalCastle: error while loading shared libraries: libssh2.so.1: cannot open shared object file: No such file or directory\r\n```\r\nSo still missing a dependency.\r\n\r\nWhat's the full set of deps needed if we swap in the debian version of libcurl?\r\n\r\nLooking at the way curl builds suggests at least `gnutls` needs to be present to set the correct flag value https://github.com/NixOS/nixpkgs/blob/master/pkgs/tools/networking/curl/default.nix#L100 so it probably also needs to be present in the fhsenv for steam. Adding this fixes the segfault and results in the same shared lib issue as the debian version.\r\n\r\nAdding both `gnutls` and `libssh2` successfully allows the game to launch. Workaround is then the following:\r\nDownload the debian version of libcurl via link in the steam issue. Move it to `.../steamapps/common/The Eternal Castle...`\r\nAdd the deps that copy of libcurl expects to the steam-fhs as follows:\r\n```\r\n nixpkgs.config.packageOverrides = pkgs: {\r\n steam = pkgs.steam.override {\r\n extraPkgs = pkgs: with pkgs; [\r\n gnutls\r\n libssh2\r\n ];\r\n };\r\n };\r\n```\r\n</details>\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154479/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154456","id":1098763763,"node_id":"I_kwDOAEVQ_M5Bfc3z","number":154456,"title":"request: vscode-extensions.rust-lang.rust","user":{"login":"waynevanson","id":29592214,"node_id":"MDQ6VXNlcjI5NTkyMjE0","avatar_url":"https://avatars.githubusercontent.com/u/29592214?v=4","gravatar_id":"","url":"https://api.github.com/users/waynevanson","html_url":"https://github.com/waynevanson","followers_url":"https://api.github.com/users/waynevanson/followers","following_url":"https://api.github.com/users/waynevanson/following{/other_user}","gists_url":"https://api.github.com/users/waynevanson/gists{/gist_id}","starred_url":"https://api.github.com/users/waynevanson/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/waynevanson/subscriptions","organizations_url":"https://api.github.com/users/waynevanson/orgs","repos_url":"https://api.github.com/users/waynevanson/repos","events_url":"https://api.github.com/users/waynevanson/events{/privacy}","received_events_url":"https://api.github.com/users/waynevanson/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-11T06:50:16Z","updated_at":"2022-01-11T06:50:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nRust extension for Visual Studio Code\r\n\r\n**Metadata**\r\n* homepage URL: https://marketplace.visualstudio.com/items?itemName=rust-lang.rust\r\n* source URL: https://github.com/rust-lang/vscode-rust\r\n* license: mit\r\n* platforms: linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154456/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154437","id":1098679470,"node_id":"I_kwDOAEVQ_M5BfISu","number":154437,"title":"mautrix python module incorrectly advertises python 3.7 support","user":{"login":"pavlukivan","id":9590981,"node_id":"MDQ6VXNlcjk1OTA5ODE=","avatar_url":"https://avatars.githubusercontent.com/u/9590981?v=4","gravatar_id":"","url":"https://api.github.com/users/pavlukivan","html_url":"https://github.com/pavlukivan","followers_url":"https://api.github.com/users/pavlukivan/followers","following_url":"https://api.github.com/users/pavlukivan/following{/other_user}","gists_url":"https://api.github.com/users/pavlukivan/gists{/gist_id}","starred_url":"https://api.github.com/users/pavlukivan/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pavlukivan/subscriptions","organizations_url":"https://api.github.com/users/pavlukivan/orgs","repos_url":"https://api.github.com/users/pavlukivan/repos","events_url":"https://api.github.com/users/pavlukivan/events{/privacy}","received_events_url":"https://api.github.com/users/pavlukivan/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-11T05:49:14Z","updated_at":"2022-01-13T09:12:22Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"`mautrix` on py3.7 requires `typing_extensions` module ([source](https://github.com/mautrix/python/blob/master/requirements.txt)). `typing_extensions` isn't currently packaged for nix, so `mautrix` won't work on py3.7. It should either be packaged and added as an conditional dependency, or minimal version should be changed to py3.8.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154437/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154344","id":1098426043,"node_id":"I_kwDOAEVQ_M5BeKa7","number":154344,"title":"systemd.mounts.*.before/after do not work","user":{"login":"kjeremy","id":4325700,"node_id":"MDQ6VXNlcjQzMjU3MDA=","avatar_url":"https://avatars.githubusercontent.com/u/4325700?v=4","gravatar_id":"","url":"https://api.github.com/users/kjeremy","html_url":"https://github.com/kjeremy","followers_url":"https://api.github.com/users/kjeremy/followers","following_url":"https://api.github.com/users/kjeremy/following{/other_user}","gists_url":"https://api.github.com/users/kjeremy/gists{/gist_id}","starred_url":"https://api.github.com/users/kjeremy/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kjeremy/subscriptions","organizations_url":"https://api.github.com/users/kjeremy/orgs","repos_url":"https://api.github.com/users/kjeremy/repos","events_url":"https://api.github.com/users/kjeremy/events{/privacy}","received_events_url":"https://api.github.com/users/kjeremy/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T21:53:54Z","updated_at":"2022-01-11T16:59:22Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```nix\r\nsystemd.mounts = [\r\n {\r\n #...\r\n before = [ \"foo.service\" ];\r\n after = [ \"bar.service\" ];\r\n }\r\n];\r\n```\r\n\r\nDoes not add the `before` or `after` to the unit section of the file. `unitConfig.Before/After` work.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. ...\r\n2. ...\r\n3. ...\r\n\r\n### Expected behavior\r\nbefore/after should be in the [Unit] section of the file.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Artturin \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.90, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"nixos\"`\r\n - channels(jkolb): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154344/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154314","id":1098246112,"node_id":"I_kwDOAEVQ_M5Bdefg","number":154314,"title":"znap","user":{"login":"Sepero","id":1575546,"node_id":"MDQ6VXNlcjE1NzU1NDY=","avatar_url":"https://avatars.githubusercontent.com/u/1575546?v=4","gravatar_id":"","url":"https://api.github.com/users/Sepero","html_url":"https://github.com/Sepero","followers_url":"https://api.github.com/users/Sepero/followers","following_url":"https://api.github.com/users/Sepero/following{/other_user}","gists_url":"https://api.github.com/users/Sepero/gists{/gist_id}","starred_url":"https://api.github.com/users/Sepero/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Sepero/subscriptions","organizations_url":"https://api.github.com/users/Sepero/orgs","repos_url":"https://api.github.com/users/Sepero/repos","events_url":"https://api.github.com/users/Sepero/events{/privacy}","received_events_url":"https://api.github.com/users/Sepero/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T18:39:25Z","updated_at":"2022-01-10T18:39:25Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"Znap is the light-weight Git repo manager for Zsh tailored to managing Zsh plugins and dotfiles.\r\n\r\n* homepage URL: https://github.com/marlonrichert/zsh-snap\r\n* source URL: https://github.com/marlonrichert/zsh-snap\r\n* license: mit\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154314/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154300","id":1098105408,"node_id":"I_kwDOAEVQ_M5Bc8JA","number":154300,"title":"Should I PR 100 typo fixes?","user":{"login":"fetsorn","id":12858105,"node_id":"MDQ6VXNlcjEyODU4MTA1","avatar_url":"https://avatars.githubusercontent.com/u/12858105?v=4","gravatar_id":"","url":"https://api.github.com/users/fetsorn","html_url":"https://github.com/fetsorn","followers_url":"https://api.github.com/users/fetsorn/followers","following_url":"https://api.github.com/users/fetsorn/following{/other_user}","gists_url":"https://api.github.com/users/fetsorn/gists{/gist_id}","starred_url":"https://api.github.com/users/fetsorn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fetsorn/subscriptions","organizations_url":"https://api.github.com/users/fetsorn/orgs","repos_url":"https://api.github.com/users/fetsorn/repos","events_url":"https://api.github.com/users/fetsorn/events{/privacy}","received_events_url":"https://api.github.com/users/fetsorn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-10T16:29:27Z","updated_at":"2022-01-11T20:27:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"I went through nixpkgs/master with ripgrep and found a hundred typos in about 50 packages.\r\nMost are in the comments - some in nix files, some in patch files and other package files. Some are in package descriptions. And a couple are in top-level plain text files and docs.\r\nI don't want to trouble the maintainers unnecessarily, so asking here beforehand.\r\nWould a PR with fixes be likely to be accepted? Would one be useful? If so, is it better to submit one or separate PRs? e.g by package or by descriptions/comments/files/docs?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154300/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154292","id":1098011887,"node_id":"I_kwDOAEVQ_M5BclTv","number":154292,"title":"throw vs assert in packages","user":{"login":"Profpatsch","id":3153638,"node_id":"MDQ6VXNlcjMxNTM2Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/3153638?v=4","gravatar_id":"","url":"https://api.github.com/users/Profpatsch","html_url":"https://github.com/Profpatsch","followers_url":"https://api.github.com/users/Profpatsch/followers","following_url":"https://api.github.com/users/Profpatsch/following{/other_user}","gists_url":"https://api.github.com/users/Profpatsch/gists{/gist_id}","starred_url":"https://api.github.com/users/Profpatsch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Profpatsch/subscriptions","organizations_url":"https://api.github.com/users/Profpatsch/orgs","repos_url":"https://api.github.com/users/Profpatsch/repos","events_url":"https://api.github.com/users/Profpatsch/events{/privacy}","received_events_url":"https://api.github.com/users/Profpatsch/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"assignees":[{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},{"login":"Profpatsch","id":3153638,"node_id":"MDQ6VXNlcjMxNTM2Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/3153638?v=4","gravatar_id":"","url":"https://api.github.com/users/Profpatsch","html_url":"https://github.com/Profpatsch","followers_url":"https://api.github.com/users/Profpatsch/followers","following_url":"https://api.github.com/users/Profpatsch/following{/other_user}","gists_url":"https://api.github.com/users/Profpatsch/gists{/gist_id}","starred_url":"https://api.github.com/users/Profpatsch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Profpatsch/subscriptions","organizations_url":"https://api.github.com/users/Profpatsch/orgs","repos_url":"https://api.github.com/users/Profpatsch/repos","events_url":"https://api.github.com/users/Profpatsch/events{/privacy}","received_events_url":"https://api.github.com/users/Profpatsch/received_events","type":"User","site_admin":false},{"login":"sternenseemann","id":3154475,"node_id":"MDQ6VXNlcjMxNTQ0NzU=","avatar_url":"https://avatars.githubusercontent.com/u/3154475?v=4","gravatar_id":"","url":"https://api.github.com/users/sternenseemann","html_url":"https://github.com/sternenseemann","followers_url":"https://api.github.com/users/sternenseemann/followers","following_url":"https://api.github.com/users/sternenseemann/following{/other_user}","gists_url":"https://api.github.com/users/sternenseemann/gists{/gist_id}","starred_url":"https://api.github.com/users/sternenseemann/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sternenseemann/subscriptions","organizations_url":"https://api.github.com/users/sternenseemann/orgs","repos_url":"https://api.github.com/users/sternenseemann/repos","events_url":"https://api.github.com/users/sternenseemann/events{/privacy}","received_events_url":"https://api.github.com/users/sternenseemann/received_events","type":"User","site_admin":false}],"milestone":null,"comments":7,"created_at":"2022-01-10T15:09:18Z","updated_at":"2022-01-17T18:35:08Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"@roberth I feel like we are moving in two different directions here, and we should standardize on one of them.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/92b09d4735639fa4ee7fb550aa9e48b64d3e0d88/pkgs/tools/networking/connman/connman.nix#L52-L53\r\n\r\n^ this was the way most packages wrote assertions so far, and `lib.asserts` was just a slight improvement over `assert`.\r\n\r\nThe new approach is different and diverges from the previous best practice.\r\n\r\n_Originally posted by @Profpatsch in https://github.com/NixOS/nixpkgs/issues/153740#issuecomment-1008961355_\r\n\r\ncc @roberth","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":1,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154292/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154283","id":1097892695,"node_id":"I_kwDOAEVQ_M5BcINX","number":154283,"title":"ruby: documentation is missing","user":{"login":"csabahenk","id":43937,"node_id":"MDQ6VXNlcjQzOTM3","avatar_url":"https://avatars.githubusercontent.com/u/43937?v=4","gravatar_id":"","url":"https://api.github.com/users/csabahenk","html_url":"https://github.com/csabahenk","followers_url":"https://api.github.com/users/csabahenk/followers","following_url":"https://api.github.com/users/csabahenk/following{/other_user}","gists_url":"https://api.github.com/users/csabahenk/gists{/gist_id}","starred_url":"https://api.github.com/users/csabahenk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/csabahenk/subscriptions","organizations_url":"https://api.github.com/users/csabahenk/orgs","repos_url":"https://api.github.com/users/csabahenk/repos","events_url":"https://api.github.com/users/csabahenk/events{/privacy}","received_events_url":"https://api.github.com/users/csabahenk/received_events","type":"User","site_admin":false},"labels":[{"id":343457371,"node_id":"MDU6TGFiZWwzNDM0NTczNzE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20ruby","name":"6.topic: ruby","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-10T13:18:49Z","updated_at":"2022-04-19T20:47:51Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nThe _*.ri_ documentation is not generated (or shipped) with the build, so _ri(1)_, the standard doc cli for Ruby, is not displaying the documentation for core / stdlib APIs. (Nb. Ruby has a _docSupport_ opion, which is `true` by default.) This is true for all versions shipped by nixpkgs.\r\n\r\n## Steps to reproduce\r\n\r\nActual:\r\n\r\n```\r\n$ ri Hash\r\nNothing known about Hash\r\n```\r\n\r\nExpected:\r\n\r\n```\r\n$ ri Hash\r\n= Hash < Object \r\n \r\n------------------------------------------------------------------------\r\n= Includes:\r\nEnumerable (from ruby core)\r\n\r\n(from ruby core) \r\n------------------------------------------------------------------------\r\nA Hash maps each of its unique keys to a specific value.\r\n...\r\n```\r\n\r\n## Technical details\r\n\r\n```\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335037.e67c94a1adb\"`\r\n - channels(csaba): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nThe posix path for the Ruby _*.ri_ files is _/usr/share/ri/\\<ruby version\\>/system_ (eg. documentation of the `Hash` class, that was looked for in the above example, should reside at _/usr/share/ri/\\<ruby version\\>/system/Hash/cdesc-Hash.ri_). _/usr/share/ri_ does not exist in the Nix ruby packages.\r\n\r\nI checked for the effect of the _docSupport_ option; only difference I see is that if it's enabled, the _/usr/share/ruby/doc_ directory is created, otherwise it's not (and it's left empty even in the former case). I don't know of any reliance of the Ruby ecosystem on _/usr/share/ruby/doc_ (all I know is that some distros chose to place some package miscellany in it, like _LICENSE_). Documentation in Ruby world means _*.ri_.\r\n\r\nI tried to locate _*.ri_ files via nix-index / nix-locate (maybe they are slated to some other package?), but even that does not give anything either.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154283/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154277","id":1097805157,"node_id":"I_kwDOAEVQ_M5Bby1l","number":154277,"title":"mipsel-linux stdenv does not evaluate from flake","user":{"login":"ehmry","id":537775,"node_id":"MDQ6VXNlcjUzNzc3NQ==","avatar_url":"https://avatars.githubusercontent.com/u/537775?v=4","gravatar_id":"","url":"https://api.github.com/users/ehmry","html_url":"https://github.com/ehmry","followers_url":"https://api.github.com/users/ehmry/followers","following_url":"https://api.github.com/users/ehmry/following{/other_user}","gists_url":"https://api.github.com/users/ehmry/gists{/gist_id}","starred_url":"https://api.github.com/users/ehmry/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ehmry/subscriptions","organizations_url":"https://api.github.com/users/ehmry/orgs","repos_url":"https://api.github.com/users/ehmry/repos","events_url":"https://api.github.com/users/ehmry/events{/privacy}","received_events_url":"https://api.github.com/users/ehmry/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":2476856759,"node_id":"MDU6TGFiZWwyNDc2ODU2NzU5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20exotic","name":"6.topic: exotic","color":"fef2c0","default":false,"description":"Exotic hardware or software platform"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T11:51:14Z","updated_at":"2022-01-10T11:56:21Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe flake output `legacyPackages.mipsel-linux.stdenv` does not eval. It would be preferable if it did, because then flakes could map over all the outputs of the Nixpkgs flake, like this:\r\n```\r\n{ self, nixpkgs }: {\r\n overlay = final: prev: { };\r\n legacyPackages = nixpkgs.lib.attrsets.mapAttrs\r\n (sys: pkgs: pkgs.extend self.overlay)\r\n nixpkgs.legacyPackages;\r\n}\r\n```\r\n\r\nError message is `error: attribute 'busybox' missing` from [pkgs/stdenv/linux/bootstrap-tools/default.nix:6](https://github.com/NixOS/nixpkgs/blob/b426ea250c498a995d97b03907fde9ef592e6b9f/pkgs/stdenv/linux/bootstrap-tools/default.nix#L6).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix build nixpkgs#legacyPackages.mipsel-linux.stdenv`\r\n\r\n### Expected behavior\r\nA cleaner error, a broken package, or no `mipsel` in `flake.nix`.\r\n\r\n### Notify maintainers\r\n\r\n@viric \r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154277/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154273","id":1097785448,"node_id":"I_kwDOAEVQ_M5BbuBo","number":154273,"title":"First letter of host key filename dropped in initrd-ssh when using path instead of string","user":{"login":"kosmonavtika","id":53181303,"node_id":"MDQ6VXNlcjUzMTgxMzAz","avatar_url":"https://avatars.githubusercontent.com/u/53181303?v=4","gravatar_id":"","url":"https://api.github.com/users/kosmonavtika","html_url":"https://github.com/kosmonavtika","followers_url":"https://api.github.com/users/kosmonavtika/followers","following_url":"https://api.github.com/users/kosmonavtika/following{/other_user}","gists_url":"https://api.github.com/users/kosmonavtika/gists{/gist_id}","starred_url":"https://api.github.com/users/kosmonavtika/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kosmonavtika/subscriptions","organizations_url":"https://api.github.com/users/kosmonavtika/orgs","repos_url":"https://api.github.com/users/kosmonavtika/repos","events_url":"https://api.github.com/users/kosmonavtika/events{/privacy}","received_events_url":"https://api.github.com/users/kosmonavtika/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T11:28:23Z","updated_at":"2022-01-10T11:30:43Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen trying to use add host keys to initrd for SSH using a path, `initrd-ssh.nix` will drop the first character in the filename (in the example below, the `i` in `initrd_host_rsa_key` and `initrd_host_ed25519_key`). \r\n\r\n```\r\nhostKeys = [\r\n \"/etc/ssh/initrd_host_rsa_key\"\r\n \"/etc/ssh/initrd_host_ed25519_key\"\r\n];\r\n```\r\n\r\nThis will cause SSH in initrd to fail, because it will be looking for `/etc/ssh/nitrd_host_rsa_key` which doesn't exist.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Configure initrd SSH with host keys provided as paths and not as strings\r\n2. Reboot system\r\n3. initrd will be looking for the wrong file, i.e. `/etc/ssh/nitrd_host_rsa_key`\r\n\r\n### Expected behavior\r\nThe expected behavior is that initrd doesn't drop the first character of the host key filename.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nThe problematic line seems to be this one: https://github.com/NixOS/nixpkgs/commit/d930466b7728e5515991cb73c060fc3f32bdc001#diff-2ceb0271cb3e52ffed8acd3a5f29b63999489c31245680733ea4ef66df0712c3R104. \r\n\r\n### Notify maintainers\r\n@emilazy \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (0.06 MiB download, 0.30 MiB unpacked):\r\n /nix/store/gd7ihraqqpginv5cmhgk347nfn2iiqkj-bash-interactive-5.1-p8-dev\r\ncopying path '/nix/store/gd7ihraqqpginv5cmhgk347nfn2iiqkj-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.12-hardened1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.335119.79c7b6a353e\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154273/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154270","id":1097722128,"node_id":"I_kwDOAEVQ_M5BbekQ","number":154270,"title":"[Packaging request] Bluemail","user":{"login":"onny","id":757752,"node_id":"MDQ6VXNlcjc1Nzc1Mg==","avatar_url":"https://avatars.githubusercontent.com/u/757752?v=4","gravatar_id":"","url":"https://api.github.com/users/onny","html_url":"https://github.com/onny","followers_url":"https://api.github.com/users/onny/followers","following_url":"https://api.github.com/users/onny/following{/other_user}","gists_url":"https://api.github.com/users/onny/gists{/gist_id}","starred_url":"https://api.github.com/users/onny/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/onny/subscriptions","organizations_url":"https://api.github.com/users/onny/orgs","repos_url":"https://api.github.com/users/onny/repos","events_url":"https://api.github.com/users/onny/events{/privacy}","received_events_url":"https://api.github.com/users/onny/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T10:40:57Z","updated_at":"2022-01-10T10:40:57Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nBluemail is a graphical mail client for the desktop. Also includes a calendar with Exchange and iCal support.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://bluemail.me/\r\n* source URL: -\r\n* license: nonfree\r\n* platforms: unix","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154270/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154260","id":1097537756,"node_id":"I_kwDOAEVQ_M5Baxjc","number":154260,"title":"nix-serve: cannot determine user’s home directory","user":{"login":"eigengrau","id":4939947,"node_id":"MDQ6VXNlcjQ5Mzk5NDc=","avatar_url":"https://avatars.githubusercontent.com/u/4939947?v=4","gravatar_id":"","url":"https://api.github.com/users/eigengrau","html_url":"https://github.com/eigengrau","followers_url":"https://api.github.com/users/eigengrau/followers","following_url":"https://api.github.com/users/eigengrau/following{/other_user}","gists_url":"https://api.github.com/users/eigengrau/gists{/gist_id}","starred_url":"https://api.github.com/users/eigengrau/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/eigengrau/subscriptions","organizations_url":"https://api.github.com/users/eigengrau/orgs","repos_url":"https://api.github.com/users/eigengrau/repos","events_url":"https://api.github.com/users/eigengrau/events{/privacy}","received_events_url":"https://api.github.com/users/eigengrau/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-10T07:23:21Z","updated_at":"2022-02-04T09:22:24Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen using the nix-serve module, nix-serve responds with an internal server error when any .narinfo resource is requested.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `services.nix-serve.enable = true`\r\n2. `nix-build '<nixpkgs>' -A hello`\r\n2. `curl http://localhost:5000/bn2zlzs294rkxxjvx7153akgbwxpzi96.narinfo`\r\n3. Observe that the server returns HTTP 500\r\n4. Observe that nix-serve logs `cannot determine user's home directory at /nix/store/70q6vzakmlvxgxk8qaw3ljp4r8adh4pj-nix-serve-0.2-e4675e3/libexec/nix-serve/nix-serve.psgi line 26.`\r\n\r\n### Expected behavior\r\nnix-serve should return the requested narinfo.\r\n\r\n### Additional context\r\nThis appears to be related to the use of a systemd dynamic user in the service configuration. nix-serve (or rather the Nix Perl-module it pulls in) appears to expect that `HOME` is set. When setting `systemd.services.nix-serve.environment.HOME = \"/\";`, the problem no longer manifests.\r\n\r\n### Notify maintainers\r\n@Mic92 \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-21.05.4255.d5b65f812cd\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154260/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154234","id":1097425227,"node_id":"I_kwDOAEVQ_M5BaWFL","number":154234,"title":"[Package Request] MultiQC","user":{"login":"spencerking","id":6580486,"node_id":"MDQ6VXNlcjY1ODA0ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6580486?v=4","gravatar_id":"","url":"https://api.github.com/users/spencerking","html_url":"https://github.com/spencerking","followers_url":"https://api.github.com/users/spencerking/followers","following_url":"https://api.github.com/users/spencerking/following{/other_user}","gists_url":"https://api.github.com/users/spencerking/gists{/gist_id}","starred_url":"https://api.github.com/users/spencerking/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/spencerking/subscriptions","organizations_url":"https://api.github.com/users/spencerking/orgs","repos_url":"https://api.github.com/users/spencerking/repos","events_url":"https://api.github.com/users/spencerking/events{/privacy}","received_events_url":"https://api.github.com/users/spencerking/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T03:46:11Z","updated_at":"2022-01-10T03:46:11Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nAggregate results from bioinformatics analyses across many samples into a single report\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://multiqc.info\r\n* source URL: https://github.com/ewels/MultiQC\r\n* license: GPL 3.0\r\n* platforms: unix\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154234/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154217","id":1097385731,"node_id":"I_kwDOAEVQ_M5BaMcD","number":154217,"title":"[Package Request] guacamole-server","user":{"login":"ilovefornite797","id":89365682,"node_id":"MDQ6VXNlcjg5MzY1Njgy","avatar_url":"https://avatars.githubusercontent.com/u/89365682?v=4","gravatar_id":"","url":"https://api.github.com/users/ilovefornite797","html_url":"https://github.com/ilovefornite797","followers_url":"https://api.github.com/users/ilovefornite797/followers","following_url":"https://api.github.com/users/ilovefornite797/following{/other_user}","gists_url":"https://api.github.com/users/ilovefornite797/gists{/gist_id}","starred_url":"https://api.github.com/users/ilovefornite797/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ilovefornite797/subscriptions","organizations_url":"https://api.github.com/users/ilovefornite797/orgs","repos_url":"https://api.github.com/users/ilovefornite797/repos","events_url":"https://api.github.com/users/ilovefornite797/events{/privacy}","received_events_url":"https://api.github.com/users/ilovefornite797/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-10T02:09:53Z","updated_at":"2022-01-10T02:09:53Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Apache guacamole-server**\r\n_Remote desktop access via web browser_\r\n\r\n**Metadata**\r\n\r\n* homepage URL: [https://guacamole.apache.org/](https://guacamole.apache.org/)\r\n* source URL: [https://dlcdn.apache.org/guacamole/1.4.0/source/guacamole-server-1.4.0.tar.gz](https://dlcdn.apache.org/guacamole/1.4.0/source/guacamole-server-1.4.0.tar.gz)\r\n* license: apache 2.0\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154217/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154203","id":1097328687,"node_id":"I_kwDOAEVQ_M5BZ-gv","number":154203,"title":"`cc <file> -o /dev/null` fails on aarch64-darwin","user":{"login":"abathur","id":2548365,"node_id":"MDQ6VXNlcjI1NDgzNjU=","avatar_url":"https://avatars.githubusercontent.com/u/2548365?v=4","gravatar_id":"","url":"https://api.github.com/users/abathur","html_url":"https://github.com/abathur","followers_url":"https://api.github.com/users/abathur/followers","following_url":"https://api.github.com/users/abathur/following{/other_user}","gists_url":"https://api.github.com/users/abathur/gists{/gist_id}","starred_url":"https://api.github.com/users/abathur/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/abathur/subscriptions","organizations_url":"https://api.github.com/users/abathur/orgs","repos_url":"https://api.github.com/users/abathur/repos","events_url":"https://api.github.com/users/abathur/events{/privacy}","received_events_url":"https://api.github.com/users/abathur/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-09T23:18:45Z","updated_at":"2022-01-16T19:08:20Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"I noticed [OfBorg failing to build](https://github.com/NixOS/nixpkgs/pull/154190/checks?check_run_id=4755232149) oil-dev on aarch64-darwin.\r\n\r\nIt's failing on a [~sanity-check](https://github.com/oilshell/oil/blob/8fbc09bb3254cee944b0450f640e268c2f627bec/configure#L158-L160) Oil's `configure` script is performing. I think I've successfully boiled the failing check down to a nix-shell oneliner that works on x86_64-darwin but fails on aarch64-darwin as below:\r\n\r\n```console\r\n$ nix-shell -p stdenv --command 'cc -o /dev/null -x c <(echo \"int main(void){ return 0; }\"); echo $?'\r\nlibc++abi: terminating with uncaught exception of type SigTool::NotAMachOFileException: std::exception\r\n/nix/store/r2pg5y3iyvsdx996iqynm4b414blbwpc-post-link-sign-hook: line 2: 95193 Abort trap: 6 CODESIGN_ALLOCATE=codesign_allocate /nix/store/pil07xvm57xbiczfqqj0cmrycwimapr5-sigtool-0.1.2/bin/codesign -f -s - \"$linkerOutput\"\r\nclang-11: error: linker command failed with exit code 134 (use -v to see invocation)\r\n134\r\n```\r\n\r\nI'm not really familiar with anything at this level, but dropping `-o /dev/null` causes the invocation to work, and it seems plausible that the post-link-sign-hook trying to codesign /dev/null could cause trouble.\r\n\r\nI don't know what the appropriate fix is, but I see where `/dev/null` would get picked up and set to `$linkerOutput`: https://github.com/NixOS/nixpkgs/blob/538a698388eb5ab1209c658e9223fa81ae255a6f/pkgs/build-support/bintools-wrapper/ld-wrapper.sh#L165-L181\r\n\r\n@thefloweringash \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154203/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154202","id":1097327163,"node_id":"I_kwDOAEVQ_M5BZ-I7","number":154202,"title":"rpi-eeprom is out of date","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-09T23:11:38Z","updated_at":"2022-01-09T23:22:18Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"As far as I can tell, rpi isn't tagging their releases, but they drop releases in their firmware/stable dir:\r\n\r\nhttps://github.com/raspberrypi/rpi-eeprom/tree/master/firmware/stable\r\n\r\nFor example, it seems there was a newest, latest release in dec 2021.\r\n\r\ncc: @superherointj ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154202/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154178","id":1097278231,"node_id":"I_kwDOAEVQ_M5BZyMX","number":154178,"title":"`lib.types.*.check`: return a message","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314752,"node_id":"MDU6TGFiZWw2MzE0NzUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20enhancement","name":"0.kind: enhancement","color":"84b6eb","default":false,"description":null},{"id":421758032,"node_id":"MDU6TGFiZWw0MjE3NTgwMzI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20user%20experience","name":"6.topic: user experience","color":"fef2c0","default":false,"description":null},{"id":549491066,"node_id":"MDU6TGFiZWw1NDk0OTEwNjY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20developer%20experience","name":"6.topic: developer experience","color":"fef2c0","default":false,"description":null},{"id":1919438524,"node_id":"MDU6TGFiZWwxOTE5NDM4NTI0","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20module%20system","name":"6.topic: module system","color":"fef2c0","default":false,"description":"About NixOS module system internals"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-09T19:14:40Z","updated_at":"2022-01-10T09:54:33Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n\r\nWe can improve type error messages by returning a string instead of `false`.\r\n\r\nThe module system can improve its error messages with these strings.\r\n\r\nOther users of `types` can benefit from this too, for example validating configuration parameters in Nixpkgs, such as #153740\r\n\r\nTo implement this without breaking anything, we can make this variation of the type checking function optional.\r\n\r\nSo we'll keep the `check : any -> bool` attribute on types, add `getErrorMessage : any -> nullOr str` and add helper functions that are compatible with old / out-of-tree types.\r\n\r\nOne helper would be `getTypeErrorMessage: type -> a -> nullOr str` which returns a generic message like `\"value is not of type ${type.description}\"`.\r\n\r\nAnother helper could be `validate : type -> a -> a` which uses `getTypeErrorMessage` to throw an error message as appropriate. It could also transform the value; supporting the `coerceTo` type.\r\n\r\nWe could deprecate the `check` attr at some point, by logging when `lib.types.*.check` is used.\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154178/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154173","id":1097268983,"node_id":"I_kwDOAEVQ_M5BZv73","number":154173,"title":"Package request: dbxfs","user":{"login":"mausch","id":95194,"node_id":"MDQ6VXNlcjk1MTk0","avatar_url":"https://avatars.githubusercontent.com/u/95194?v=4","gravatar_id":"","url":"https://api.github.com/users/mausch","html_url":"https://github.com/mausch","followers_url":"https://api.github.com/users/mausch/followers","following_url":"https://api.github.com/users/mausch/following{/other_user}","gists_url":"https://api.github.com/users/mausch/gists{/gist_id}","starred_url":"https://api.github.com/users/mausch/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mausch/subscriptions","organizations_url":"https://api.github.com/users/mausch/orgs","repos_url":"https://api.github.com/users/mausch/repos","events_url":"https://api.github.com/users/mausch/events{/privacy}","received_events_url":"https://api.github.com/users/mausch/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-09T18:32:33Z","updated_at":"2022-01-09T18:32:33Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nUser-space file system for Dropbox\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://thelig.ht/code/dbxfs/\r\n* source URL: https://thelig.ht/code/dbxfs/\r\n* license: GPLv3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154173/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154163","id":1097250494,"node_id":"I_kwDOAEVQ_M5BZra-","number":154163,"title":"Building a NixOS system with the linux_rpi* kernels fails with `Module ... not found in directory`","user":{"login":"pstn","id":1329940,"node_id":"MDQ6VXNlcjEzMjk5NDA=","avatar_url":"https://avatars.githubusercontent.com/u/1329940?v=4","gravatar_id":"","url":"https://api.github.com/users/pstn","html_url":"https://github.com/pstn","followers_url":"https://api.github.com/users/pstn/followers","following_url":"https://api.github.com/users/pstn/following{/other_user}","gists_url":"https://api.github.com/users/pstn/gists{/gist_id}","starred_url":"https://api.github.com/users/pstn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pstn/subscriptions","organizations_url":"https://api.github.com/users/pstn/orgs","repos_url":"https://api.github.com/users/pstn/repos","events_url":"https://api.github.com/users/pstn/events{/privacy}","received_events_url":"https://api.github.com/users/pstn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":185850329,"node_id":"MDU6TGFiZWwxODU4NTAzMjk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20kernel","name":"6.topic: kernel","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-09T17:10:29Z","updated_at":"2022-04-21T14:54:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nBuilding a sd-image for the raspberry-pi 4 fails with\r\n`modprobe: FATAL: Module sun4i-drm not found in directory /nix/store/azccsmgqmvhy8vmdr1f4rcpf1rbxvgx5-linux-5.10.52-1.20210805-modules/lib/modules/5.10.52`\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\nrun `nix-build '<nixpkgs/nixos>' -A config.system.build.sdImage -I nixos-config=./minimal.nix --argstr system aarch64-linux`\r\n\r\nwith `minimal.nix` being:\r\n```\r\n{ config, pkgs, lib, ... }:\r\n{\r\n\r\n imports = [\r\n <nixpkgs/nixos/modules/installer/sd-card/sd-image-aarch64-installer.nix>\r\n ];\r\n boot = {\r\n kernelPackages = pkgs.linuxPackages_rpi4;\r\n };\r\n}\r\n```\r\n\r\n### Expected behavior\r\nAn image is being produced\r\n\r\n### Additional context\r\n[Seems like it is this issue](https://github.com/NixOS/nixpkgs/issues/111683#issuecomment-968435872)\r\n\r\n### Notify maintainers\r\n@samueldr \r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n- host os: `Linux 5.15.11, NixOS, 22.05 (Quokka)`\r\n- multi-user?: `yes`\r\n- sandbox: `yes`\r\n- version: `nix-env (Nix) 2.5.1`\r\n- channels(philipp): `\"\"`\r\n- channels(root): `\"home-manager, nixos, nixos-hardware\"`\r\n- nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154163/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154150","id":1097224706,"node_id":"I_kwDOAEVQ_M5BZlIC","number":154150,"title":"shotcut: GLib-GIO-ERROR: Settings schema 'org.gtk.Settings.ColorChooser' is not installed","user":{"login":"akho","id":104951,"node_id":"MDQ6VXNlcjEwNDk1MQ==","avatar_url":"https://avatars.githubusercontent.com/u/104951?v=4","gravatar_id":"","url":"https://api.github.com/users/akho","html_url":"https://github.com/akho","followers_url":"https://api.github.com/users/akho/followers","following_url":"https://api.github.com/users/akho/following{/other_user}","gists_url":"https://api.github.com/users/akho/gists{/gist_id}","starred_url":"https://api.github.com/users/akho/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/akho/subscriptions","organizations_url":"https://api.github.com/users/akho/orgs","repos_url":"https://api.github.com/users/akho/repos","events_url":"https://api.github.com/users/akho/events{/privacy}","received_events_url":"https://api.github.com/users/akho/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-09T15:26:14Z","updated_at":"2022-01-09T20:32:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nShotcut crashes when opening color chooser dialogs.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Open Shotcut\r\n2. Try to open a color chooser (e.g., in a text frame)\r\n3. Shotcut crashes with \r\n\r\n```\r\n(shotcut:319447): GLib-GIO-ERROR **: 17:30:56.289: Settings schema 'org.gtk.Settings.ColorChooser' is not installed\r\nfish: Job 1, 'shotcut' terminated by signal SIGTRAP (Trace or breakpoint trap)\r\n```\r\n\r\n### Expected behavior\r\nNo crash\r\n\r\n### Additional context\r\nThe package is missing `wrapGAppsHook`. A bit strange that it’s required, given that shotcut is a Qt application, but adding the right folder to `XDG_DATA_DIRS` helps as a workaround.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@goibhniu @woffs @peti\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-info -m\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-21.11.335072.36480448d47, nixos-hardware\"`\r\n - channels(akho): `\"home-manager\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154150/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154132","id":1097184310,"node_id":"I_kwDOAEVQ_M5BZbQ2","number":154132,"title":"NixOS does not boot with WQHD (1440p) displays in default configuration on amdgpu","user":{"login":"joepie91","id":1663259,"node_id":"MDQ6VXNlcjE2NjMyNTk=","avatar_url":"https://avatars.githubusercontent.com/u/1663259?v=4","gravatar_id":"","url":"https://api.github.com/users/joepie91","html_url":"https://github.com/joepie91","followers_url":"https://api.github.com/users/joepie91/followers","following_url":"https://api.github.com/users/joepie91/following{/other_user}","gists_url":"https://api.github.com/users/joepie91/gists{/gist_id}","starred_url":"https://api.github.com/users/joepie91/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/joepie91/subscriptions","organizations_url":"https://api.github.com/users/joepie91/orgs","repos_url":"https://api.github.com/users/joepie91/repos","events_url":"https://api.github.com/users/joepie91/events{/privacy}","received_events_url":"https://api.github.com/users/joepie91/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-09T12:34:16Z","updated_at":"2022-01-20T12:47:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI've recently switched out my old Full HD (1080p) monitors connected over HDMI, for new WQHD (1440p) monitors connected over DisplayPort. This worked fine out of the box on Windows. However, I could not boot into NixOS; during the boot process, presumably during KMS, the screen would blank completely with no way to get graphics back.\r\n\r\nAfter some searching around, I ran into [this thread](https://forum.manjaro.org/t/can-not-boot-when-using-a-3440x1440-monitor/61456), which describes a similar issue, with roughly the same journalctl output as I had. It mentions that the problem can be resolved by doing early KMS; in the case of NixOS, this turned out to involve setting `boot.initrd.kernelModules = [ \"amdgpu\" ];`, which solved the issue and let the system boot correctly.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have an existing install (using amdgpu) with 1080p monitors over HDMI?\r\n2. Replace the monitors with 1440p monitors over DisplayPort.\r\n3. Try to boot, run into a blank screen.\r\n\r\n### Expected behavior\r\nThe system should boot correctly after switching out the monitors, without requiring further manual configuration.\r\n\r\n### Screenshots\r\nn/a, the screen is blank :)\r\n\r\n### Additional context\r\nThe issue could be resolved on a NixOS level by automatically adding `amdgpu` to `boot.initrd.kernelModules`, at least when the `amdgpu` driver is being used. I don't know whether this has any undesirable tradeoffs.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(sven): `\"\"`\r\n - channels(root): `\"nixos-21.11.335005.c6019d8efb5\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154132/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154128","id":1097175610,"node_id":"I_kwDOAEVQ_M5BZZI6","number":154128,"title":"suid wrapper architecture should be documented","user":{"login":"flokli","id":183879,"node_id":"MDQ6VXNlcjE4Mzg3OQ==","avatar_url":"https://avatars.githubusercontent.com/u/183879?v=4","gravatar_id":"","url":"https://api.github.com/users/flokli","html_url":"https://github.com/flokli","followers_url":"https://api.github.com/users/flokli/followers","following_url":"https://api.github.com/users/flokli/following{/other_user}","gists_url":"https://api.github.com/users/flokli/gists{/gist_id}","starred_url":"https://api.github.com/users/flokli/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/flokli/subscriptions","organizations_url":"https://api.github.com/users/flokli/orgs","repos_url":"https://api.github.com/users/flokli/repos","events_url":"https://api.github.com/users/flokli/events{/privacy}","received_events_url":"https://api.github.com/users/flokli/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-09T11:51:53Z","updated_at":"2022-01-09T11:52:00Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"People are often confused about some binaries only working as root.\r\n\r\nThis is because Nix (rightfully) doesn't ship suid binaries in the Nix store, but all that is handled through the `security.wrappers` infrastructure. We should document that more cleanly somewhere, so people searching for suid in the docs can find an explanation.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154128/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154123","id":1097155301,"node_id":"I_kwDOAEVQ_M5BZULl","number":154123,"title":"Safe and readable ExecStart for systemd proposal","user":{"login":"roberth","id":496447,"node_id":"MDQ6VXNlcjQ5NjQ0Nw==","avatar_url":"https://avatars.githubusercontent.com/u/496447?v=4","gravatar_id":"","url":"https://api.github.com/users/roberth","html_url":"https://github.com/roberth","followers_url":"https://api.github.com/users/roberth/followers","following_url":"https://api.github.com/users/roberth/following{/other_user}","gists_url":"https://api.github.com/users/roberth/gists{/gist_id}","starred_url":"https://api.github.com/users/roberth/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/roberth/subscriptions","organizations_url":"https://api.github.com/users/roberth/orgs","repos_url":"https://api.github.com/users/roberth/repos","events_url":"https://api.github.com/users/roberth/events{/privacy}","received_events_url":"https://api.github.com/users/roberth/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-01-09T10:08:06Z","updated_at":"2022-01-09T13:22:16Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n`ExecStart` is hard to read and write.\r\n - Cryptic prefixes\r\n - Surprising escaping (ref unescaping: #154113, although perhaps a clean slate is preferable https://github.com/NixOS/nixpkgs/pull/154113#discussion_r780763630)\r\n\r\n`script` is only suitable for a subset of use cases. (#135557, maybe other problems?)\r\n - No prefixes\r\n - No substitutions whatsoever\r\n - Only `ExecStart`\r\n\r\n### Expected behavior\r\n\r\n - Uphold the rule that a string is a string unless explicitly requested to be modified.\r\n - Use module system `enum`s instead of cryptic prefixes (or perhaps add a `bool` if a prefix can always be combined etc; haven't fully dissected those)\r\n - Manage expectations: these aren't bash statements\r\n\r\nIt might look like this:\r\n\r\n```nix\r\nsystemd.services.foo = {\r\n execStarts = [ # plural; it's a list\r\n { mode = \"privileged\"; # `+` prefix; TODO need to research exactly how prefixes combine\r\n exe = \"echoAll\";\r\n args = [ \"$a\" { substitute = \"%i\"; } ]; # escaped by default. not escaped when in { substitute = x; }\r\n }\r\n ]\r\n}\r\n```\r\n\r\nMaybe even s/args/argv. More explicit, but also cryptic if you don't know C.\r\n\r\n### Additional context\r\n\r\n`man systemd.service` (Exec* family of fields)\r\n`man systemd.unit` (substitutions)\r\n\r\n### Notify maintainers\r\n\r\n@NixOS/systemd\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154123/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072/events","html_url":"https://github.com/NixOS/nixpkgs/issues/154072","id":1097063394,"node_id":"I_kwDOAEVQ_M5BY9vi","number":154072,"title":"Markdown blockquotes does not work in documentation","user":{"login":"davidak","id":91113,"node_id":"MDQ6VXNlcjkxMTEz","avatar_url":"https://avatars.githubusercontent.com/u/91113?v=4","gravatar_id":"","url":"https://api.github.com/users/davidak","html_url":"https://github.com/davidak","followers_url":"https://api.github.com/users/davidak/followers","following_url":"https://api.github.com/users/davidak/following{/other_user}","gists_url":"https://api.github.com/users/davidak/gists{/gist_id}","starred_url":"https://api.github.com/users/davidak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/davidak/subscriptions","organizations_url":"https://api.github.com/users/davidak/orgs","repos_url":"https://api.github.com/users/davidak/repos","events_url":"https://api.github.com/users/davidak/events{/privacy}","received_events_url":"https://api.github.com/users/davidak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":1540529485,"node_id":"MDU6TGFiZWwxNTQwNTI5NDg1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20documentation%20source","name":"6.topic: documentation source","color":"fef2c0","default":false,"description":"Meta-discussion about documentation and its workflow"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-08T23:56:42Z","updated_at":"2022-01-08T23:56:42Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. add something with quotes to the docs like\r\n\r\n```\r\n> This\r\n> is a\r\n> Test\r\n```\r\n\r\n2. build docs like described in https://nixos.org/manual/nixpkgs/stable/#chap-contributing\r\n3. see broken result\r\n\r\n\r\n\r\n\r\n### Expected behavior\r\nFull support of Markdown (CommonMark)\r\n\r\nhttps://spec.commonmark.org/0.30/#block-quotes\r\n\r\n### Additional context\r\nI used code block as workaround.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/154072/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153983","id":1096894537,"node_id":"I_kwDOAEVQ_M5BYUhJ","number":153983,"title":"Dolphin file manager doesn't create PDF and DJVU thumbnails","user":{"login":"johkneisl","id":97337894,"node_id":"U_kgDOBc1CJg","avatar_url":"https://avatars.githubusercontent.com/u/97337894?v=4","gravatar_id":"","url":"https://api.github.com/users/johkneisl","html_url":"https://github.com/johkneisl","followers_url":"https://api.github.com/users/johkneisl/followers","following_url":"https://api.github.com/users/johkneisl/following{/other_user}","gists_url":"https://api.github.com/users/johkneisl/gists{/gist_id}","starred_url":"https://api.github.com/users/johkneisl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/johkneisl/subscriptions","organizations_url":"https://api.github.com/users/johkneisl/orgs","repos_url":"https://api.github.com/users/johkneisl/repos","events_url":"https://api.github.com/users/johkneisl/events{/privacy}","received_events_url":"https://api.github.com/users/johkneisl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-08T10:32:39Z","updated_at":"2022-04-21T13:31:55Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nKDE's file manager Dolphin doesn't create thumbnails of PDF files, despite being configured to do so and libsForQt5.kdegraphics-thumbnailers being installed. Thumbnails for images, videos, directories, and text files are created as expected.\r\n\r\n### Steps To Reproduce\r\n1. Install Dolphin and kdegraphics-thumbnailer on NixOS\r\n2. Open Dolphin -> Configure Dolphin... -> Previews -> Select \"PostScript, PDF and DVI Files\" and \"DjVu Files\".\r\nSet \"No Limit\" for previews and save.\r\n3. Open Dolphin, set View -> Show Previews.\r\n\r\n### Expected behavior\r\nThumbnails of PDF files are created.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n\r\n\r\n### Additional context\r\nWhen I create a new user on my system, I can reproduce the problem.\r\nPDF thumbnails can be created with either Nautilus+evince installed or Thunar+Tumbler installed.\r\nThose thumbnails are not picked up by Dolphin, but by some other apps, such as index-fm.\r\nPotentially relevant entry in the systemd journal:\r\n krunner[19796]: kf.kio.slaves.thumbnail.djvu: QProcess::FailedToStart \"\"\r\nInstalling several further KDE packages, following a working configuration by another user [here](https://gitlab.com/liketechnik/nixos-files/-/blob/master/profiles/graphical/default.nix#L27) doesn't resolve the problem. \r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.89, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre343944.ff377a78794\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153983/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153944","id":1096828024,"node_id":"I_kwDOAEVQ_M5BYER4","number":153944,"title":"openmw-tes3mp: 0.7.1 -> 0.7.0-alpha","user":{"login":"nixdaemon","id":33565694,"node_id":"MDQ6VXNlcjMzNTY1Njk0","avatar_url":"https://avatars.githubusercontent.com/u/33565694?v=4","gravatar_id":"","url":"https://api.github.com/users/nixdaemon","html_url":"https://github.com/nixdaemon","followers_url":"https://api.github.com/users/nixdaemon/followers","following_url":"https://api.github.com/users/nixdaemon/following{/other_user}","gists_url":"https://api.github.com/users/nixdaemon/gists{/gist_id}","starred_url":"https://api.github.com/users/nixdaemon/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nixdaemon/subscriptions","organizations_url":"https://api.github.com/users/nixdaemon/orgs","repos_url":"https://api.github.com/users/nixdaemon/repos","events_url":"https://api.github.com/users/nixdaemon/events{/privacy}","received_events_url":"https://api.github.com/users/nixdaemon/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-08T04:12:49Z","updated_at":"2022-04-11T02:30:18Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nthe latest version of [openmw-tes3mp](https://github.com/NixOS/nixpkgs/blob/nixos-21.11/pkgs/games/openmw/tes3mp.nix) in nixpkgs does not match the release version people use to host TES3MP servers ( 0.7.0-alpha). as a result, when someone tries to connect, they are kicked because their client's version doesn't match the server version.\r\n\r\n### Steps To Reproduce\r\nsteps to reproduce the behavior:\r\n1. install openmw-tes3mp (this will require data files from the game The Elder Scrolls III: Morrowind)\r\n2. connect to a server ( I have a server up that is hosted at https://bottom.rs )\r\n3. watch yourself get kicked\r\n\r\n### Expected behavior\r\nthe packaged version of TES3MP should connect to a server without an issue\r\n\r\n### Additional Content\r\nthe 0.7.0-alpha builds are advertised by the TES3MP community and it's developers as stable builds, listed here: https://github.com/TES3MP/openmw-tes3mp/releases/tag/0.7.0-alpha and that 0.7.1 is a dev build that is not meant for general use, usually with breaking features and additions that are still being tested out.\r\n\r\nthis is my first time filing a bug in this repo and i am not sure if this is the right place","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153944/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153884","id":1096544141,"node_id":"I_kwDOAEVQ_M5BW--N","number":153884,"title":"Imagemagick default system font","user":{"login":"twhitehead","id":787843,"node_id":"MDQ6VXNlcjc4Nzg0Mw==","avatar_url":"https://avatars.githubusercontent.com/u/787843?v=4","gravatar_id":"","url":"https://api.github.com/users/twhitehead","html_url":"https://github.com/twhitehead","followers_url":"https://api.github.com/users/twhitehead/followers","following_url":"https://api.github.com/users/twhitehead/following{/other_user}","gists_url":"https://api.github.com/users/twhitehead/gists{/gist_id}","starred_url":"https://api.github.com/users/twhitehead/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/twhitehead/subscriptions","organizations_url":"https://api.github.com/users/twhitehead/orgs","repos_url":"https://api.github.com/users/twhitehead/repos","events_url":"https://api.github.com/users/twhitehead/events{/privacy}","received_events_url":"https://api.github.com/users/twhitehead/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-07T18:02:58Z","updated_at":"2022-03-12T19:34:38Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nImagemagick defaults to `helvetica` as [described here](https://github.com/ImageMagick/ImageMagick/issues/2905#issuecomment-737533598) unless a default system font is put into the `policy.xml` file. This breaks applications like `montage` even if you don't use fonts.\r\n\r\n### Steps To Reproduce\r\n\r\nAssuming you have two png images called `1.png` and `2.png` that you want to combine into a single output `1and2.png` file\r\n\r\n```\r\n$ nix run nixos.imagemagick\r\n$ montage 1.png 2.png 1and2.png && echo OK || echo FAILED\r\nmontage: unable to read font `helvetica' @ error/annotate.c/RenderFreetype/1425.\r\nFAILED\r\n```\r\n### Expected behavior\r\n\r\nWould be great if there a valid default font could be patched into the `etc/ImageMagick-7/policy.xml` file as [described here](https://github.com/ImageMagick/ImageMagick/issues/2905#issuecomment-737536775) so this would just work.\r\n\r\n### Notify maintainers\r\n\r\n@erictapen @dotlambda \r\n\r\n### Metadata\r\n\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.48, NixOS, 21.05.1510.a165aeceda9 (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.12`\r\n - channels(root): `\"nixos-21.05.1510.a165aeceda9\"`\r\n - channels(tyson): `\"unstable-22.05pre339888.81cef6b70fb\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884/reactions","total_count":3,"+1":3,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153884/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153841","id":1096288046,"node_id":"I_kwDOAEVQ_M5BWAcu","number":153841,"title":"Package request for rofi-rbw","user":{"login":"farzin-az","id":82333104,"node_id":"MDQ6VXNlcjgyMzMzMTA0","avatar_url":"https://avatars.githubusercontent.com/u/82333104?v=4","gravatar_id":"","url":"https://api.github.com/users/farzin-az","html_url":"https://github.com/farzin-az","followers_url":"https://api.github.com/users/farzin-az/followers","following_url":"https://api.github.com/users/farzin-az/following{/other_user}","gists_url":"https://api.github.com/users/farzin-az/gists{/gist_id}","starred_url":"https://api.github.com/users/farzin-az/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/farzin-az/subscriptions","organizations_url":"https://api.github.com/users/farzin-az/orgs","repos_url":"https://api.github.com/users/farzin-az/repos","events_url":"https://api.github.com/users/farzin-az/events{/privacy}","received_events_url":"https://api.github.com/users/farzin-az/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-07T12:46:55Z","updated_at":"2022-01-24T22:15:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\nrofi-rbw is a rofi client for rbw. Many rofi scripts have already been packaged but this rather new script is not. Though, it is possible to install it from pip, some applications don't recognize the binary.\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/fdw/rofi-rbw\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153841/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153793","id":1095905659,"node_id":"I_kwDOAEVQ_M5BUjF7","number":153793,"title":"Incorrect use of -frandom-seed","user":{"login":"TravisWhitaker","id":1310395,"node_id":"MDQ6VXNlcjEzMTAzOTU=","avatar_url":"https://avatars.githubusercontent.com/u/1310395?v=4","gravatar_id":"","url":"https://api.github.com/users/TravisWhitaker","html_url":"https://github.com/TravisWhitaker","followers_url":"https://api.github.com/users/TravisWhitaker/followers","following_url":"https://api.github.com/users/TravisWhitaker/following{/other_user}","gists_url":"https://api.github.com/users/TravisWhitaker/gists{/gist_id}","starred_url":"https://api.github.com/users/TravisWhitaker/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/TravisWhitaker/subscriptions","organizations_url":"https://api.github.com/users/TravisWhitaker/orgs","repos_url":"https://api.github.com/users/TravisWhitaker/repos","events_url":"https://api.github.com/users/TravisWhitaker/events{/privacy}","received_events_url":"https://api.github.com/users/TravisWhitaker/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null},{"id":897230915,"node_id":"MDU6TGFiZWw4OTcyMzA5MTU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20stdenv","name":"6.topic: stdenv","color":"fef2c0","default":false,"description":"Standard environment"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-07T01:54:10Z","updated_at":"2022-01-07T03:51:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"In `pkgs/build-support/setup-hooks/reproducible-builds.sh` we add a fixed random seed based on the package out path. However, the GCC manual states that, if -frandom-seed is used, it must be different for each translation unit. I suspect that this is because the seed is added to e.g. anonymous static object code symbol names, so that duplicate static objects in different translation units end up with unique names in the final object code. We are AFAIU breaking this rule by using the same seed for every $CC call in a given package.\r\n\r\nWe're probably getting away with this because:\r\n- GCC adds enough other unique information to each use site of the random seed to make things work. If GCC is doing this on purpose, its manual should be updated.\r\n- One has to do some very specific and unlikely thing to cause breakage with repeated random seeds, and by sheer luck no one has noticed any breakage in Nixpkgs yet.\r\n\r\nFWIW I only noticed this because a colleague ran in to https://github.com/NixOS/nixpkgs/issues/109033 and pointed out the relevant GCC manual section to me. ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153793/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153783","id":1095853545,"node_id":"I_kwDOAEVQ_M5BUWXp","number":153783,"title":"python3Packages.cairocffi: segmentation fault on aarch64-darwin","user":{"login":"PartemImperium","id":88595311,"node_id":"MDQ6VXNlcjg4NTk1MzEx","avatar_url":"https://avatars.githubusercontent.com/u/88595311?v=4","gravatar_id":"","url":"https://api.github.com/users/PartemImperium","html_url":"https://github.com/PartemImperium","followers_url":"https://api.github.com/users/PartemImperium/followers","following_url":"https://api.github.com/users/PartemImperium/following{/other_user}","gists_url":"https://api.github.com/users/PartemImperium/gists{/gist_id}","starred_url":"https://api.github.com/users/PartemImperium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PartemImperium/subscriptions","organizations_url":"https://api.github.com/users/PartemImperium/orgs","repos_url":"https://api.github.com/users/PartemImperium/repos","events_url":"https://api.github.com/users/PartemImperium/events{/privacy}","received_events_url":"https://api.github.com/users/PartemImperium/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-07T00:28:52Z","updated_at":"2022-01-17T01:03:52Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\ncairosvg does not build on a m1 mac.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add python39Packages.cairosvg to home-manager or any method of building a nix package\r\n\r\n### Expected behavior\r\nThe app builds and can be run.\r\n\r\n### Additional context\r\nIf I install have it build as \"x86_64-darwin\" it builds just fine and works. It is just aarch64-darwin that does not work.\r\n\r\nBelow is part of the build output when the error starts.\r\n\r\nplatform darwin -- Python 3.9.6, pytest-6.2.5, py-1.10.0, pluggy-1.0.0\r\nrootdir: /nix/store/7l8c4hl7jykb44yay3m9x1zsgp159fig-python3.9-cairocffi-1.2.0/lib/python3.9/site-packages\r\ncollected 52 items / 1 skipped / 51 selected \r\n\r\n../../../../nix/store/7l8c4hl7jykb44yay3m9x1zsgp159fig-python3.9-cairocffi-1.2.0/lib/python3.9/site-packages/cairocffi/test_cairo.py . [ 1%]\r\n.FF...FF..FFFFFFFFFFF......FF................ [ 88%]\r\n../../../../nix/store/7l8c4hl7jykb44yay3m9x1zsgp159fig-python3.9-cairocffi-1.2.0/lib/python3.9/site-packages/cairocffi/test_numpy.py F [ 90%]\r\n [ 90%]\r\n../../../../nix/store/7l8c4hl7jykb44yay3m9x1zsgp159fig-python3.9-cairocffi-1.2.0/lib/python3.9/site-packages/cairocffi/test_pixbuf.py Fatal Python error: Segmentation fault\r\n\r\n### Notify maintainers\r\n@SuperSandro2000 \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.1.0, macOS 12.0.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(myUser): `\"darwin, home-manager, nixpkgs-22.05pre340506.5c37ad87222\"`\r\n - channels(root): `\"darwin, home-manager, nixpkgs-22.05pre335173.56cbe42f166\"`\r\n - nixpkgs: `/Users/myUser/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153783/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153763","id":1095665287,"node_id":"I_kwDOAEVQ_M5BToaH","number":153763,"title":"Manyverse","user":{"login":"spencerhadley","id":4071593,"node_id":"MDQ6VXNlcjQwNzE1OTM=","avatar_url":"https://avatars.githubusercontent.com/u/4071593?v=4","gravatar_id":"","url":"https://api.github.com/users/spencerhadley","html_url":"https://github.com/spencerhadley","followers_url":"https://api.github.com/users/spencerhadley/followers","following_url":"https://api.github.com/users/spencerhadley/following{/other_user}","gists_url":"https://api.github.com/users/spencerhadley/gists{/gist_id}","starred_url":"https://api.github.com/users/spencerhadley/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/spencerhadley/subscriptions","organizations_url":"https://api.github.com/users/spencerhadley/orgs","repos_url":"https://api.github.com/users/spencerhadley/repos","events_url":"https://api.github.com/users/spencerhadley/events{/privacy}","received_events_url":"https://api.github.com/users/spencerhadley/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":{"login":"fabianhjr","id":303897,"node_id":"MDQ6VXNlcjMwMzg5Nw==","avatar_url":"https://avatars.githubusercontent.com/u/303897?v=4","gravatar_id":"","url":"https://api.github.com/users/fabianhjr","html_url":"https://github.com/fabianhjr","followers_url":"https://api.github.com/users/fabianhjr/followers","following_url":"https://api.github.com/users/fabianhjr/following{/other_user}","gists_url":"https://api.github.com/users/fabianhjr/gists{/gist_id}","starred_url":"https://api.github.com/users/fabianhjr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fabianhjr/subscriptions","organizations_url":"https://api.github.com/users/fabianhjr/orgs","repos_url":"https://api.github.com/users/fabianhjr/repos","events_url":"https://api.github.com/users/fabianhjr/events{/privacy}","received_events_url":"https://api.github.com/users/fabianhjr/received_events","type":"User","site_admin":false},"assignees":[{"login":"fabianhjr","id":303897,"node_id":"MDQ6VXNlcjMwMzg5Nw==","avatar_url":"https://avatars.githubusercontent.com/u/303897?v=4","gravatar_id":"","url":"https://api.github.com/users/fabianhjr","html_url":"https://github.com/fabianhjr","followers_url":"https://api.github.com/users/fabianhjr/followers","following_url":"https://api.github.com/users/fabianhjr/following{/other_user}","gists_url":"https://api.github.com/users/fabianhjr/gists{/gist_id}","starred_url":"https://api.github.com/users/fabianhjr/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/fabianhjr/subscriptions","organizations_url":"https://api.github.com/users/fabianhjr/orgs","repos_url":"https://api.github.com/users/fabianhjr/repos","events_url":"https://api.github.com/users/fabianhjr/events{/privacy}","received_events_url":"https://api.github.com/users/fabianhjr/received_events","type":"User","site_admin":false}],"milestone":null,"comments":2,"created_at":"2022-01-06T20:22:48Z","updated_at":"2022-04-30T06:10:05Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nManyverse is a cross-platform app for the ScuttleButt network\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.manyver.se/\r\n* source URL: https://gitlab.com/staltz/manyverse\r\n* license: none?\r\n* platforms: Linux, MacOS, Windows, iOS, Android\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153763/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153759","id":1095614226,"node_id":"I_kwDOAEVQ_M5BTb8S","number":153759,"title":"pkgsLLVM.llvmPackages.stdenv does not work: fatal error: 'cstdio' file not found","user":{"login":"trofi","id":226650,"node_id":"MDQ6VXNlcjIyNjY1MA==","avatar_url":"https://avatars.githubusercontent.com/u/226650?v=4","gravatar_id":"","url":"https://api.github.com/users/trofi","html_url":"https://github.com/trofi","followers_url":"https://api.github.com/users/trofi/followers","following_url":"https://api.github.com/users/trofi/following{/other_user}","gists_url":"https://api.github.com/users/trofi/gists{/gist_id}","starred_url":"https://api.github.com/users/trofi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/trofi/subscriptions","organizations_url":"https://api.github.com/users/trofi/orgs","repos_url":"https://api.github.com/users/trofi/repos","events_url":"https://api.github.com/users/trofi/events{/privacy}","received_events_url":"https://api.github.com/users/trofi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-06T19:13:14Z","updated_at":"2022-03-26T10:31:29Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"`pkgsLLVM` should provide `libc++` headers, but it does not. I initially observed it on `pkgsLLVM.mold` which uses `llvmPackages_latest.stdenv`.\r\n\r\nHere is the one-liner reproducer:\r\n\r\ngood:\r\n\r\n```\r\n$ nix build --impure --expr 'with import ./. {}; llvmPackages.stdenv.mkDerivation { name = \"d\"; unpackPhase = \"srcs=foo.cc; echo \\\"#include <cstdio>\\\" > $srcs\"; buildPhase = \"$CXX -c $srcs -o $out\"; installPhase= \" \"; }' -L\r\n\r\nd> unpacking sources\r\nd> patching sources\r\nd> configuring\r\nd> no configure script, doing nothing\r\nd> building\r\nd> installing\r\nd> post-installation fixup\r\nd> shrinking RPATHs of ELF executables and libraries in /nix/store/dw557ng62rbvnhw5jmqll3xlkz4z79qq-d\r\nd> shrinking /nix/store/dw557ng62rbvnhw5jmqll3xlkz4z79qq-d\r\nd> patchelf: wrong ELF type\r\nd> strip is /nix/store/185kz4r9brb1lay70w025287l11lb5y0-clang-wrapper-7.1.0/bin/strip\r\nd> patching script interpreter paths in /nix/store/dw557ng62rbvnhw5jmqll3xlkz4z79qq-d\r\nd> checking for references to /build/ in /nix/store/dw557ng62rbvnhw5jmqll3xlkz4z79qq-d...\r\nd> patchelf: wrong ELF type\r\n```\r\n\r\nbad:\r\n\r\n```\r\n$ nix build --impure --expr 'with import ./. {}; pkgsLLVM.llvmPackages.stdenv.mkDerivation { name = \"d\"; unpackPhase = \"srcs=foo.cc; echo \\\"#include <cstdio>\\\" > $srcs\"; buildPhase = \"$CXX -c $srcs -o $out\"; installPhase= \" \"; }' -L\r\n\r\nd-x86_64-unknown-linux-gnu> unpacking sources\r\nd-x86_64-unknown-linux-gnu> patching sources\r\nd-x86_64-unknown-linux-gnu> configuring\r\nd-x86_64-unknown-linux-gnu> no configure script, doing nothing\r\nd-x86_64-unknown-linux-gnu> building\r\nd-x86_64-unknown-linux-gnu> foo.cc:1:10: fatal error: 'cstdio' file not found\r\nd-x86_64-unknown-linux-gnu> #include <cstdio>\r\nd-x86_64-unknown-linux-gnu> ^~~~~~~~\r\n```\r\n\r\nNote: `<cstdio>` is not in the visible path.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153759/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153697","id":1095100787,"node_id":"I_kwDOAEVQ_M5BRelz","number":153697,"title":"Mobilizon","user":{"login":"genofire","id":6905586,"node_id":"MDQ6VXNlcjY5MDU1ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6905586?v=4","gravatar_id":"","url":"https://api.github.com/users/genofire","html_url":"https://github.com/genofire","followers_url":"https://api.github.com/users/genofire/followers","following_url":"https://api.github.com/users/genofire/following{/other_user}","gists_url":"https://api.github.com/users/genofire/gists{/gist_id}","starred_url":"https://api.github.com/users/genofire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/genofire/subscriptions","organizations_url":"https://api.github.com/users/genofire/orgs","repos_url":"https://api.github.com/users/genofire/repos","events_url":"https://api.github.com/users/genofire/events{/privacy}","received_events_url":"https://api.github.com/users/genofire/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-06T08:52:58Z","updated_at":"2022-01-06T11:13:54Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nGather, organize and mobilize yourselves with a convivial, ethical, and emancipating tool.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://joinmobilizon.org\r\n* source URL: https://framagit.org/framasoft/mobilizon/\r\n* license: agpl3\r\n* platforms: unix, linux, darwin, \r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153697/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153693","id":1095076978,"node_id":"I_kwDOAEVQ_M5BRYxy","number":153693,"title":"`buildFHSUserEnv` doesn't works with nix-shell shebang `-i` pattern","user":{"login":"luochen1990","id":2309868,"node_id":"MDQ6VXNlcjIzMDk4Njg=","avatar_url":"https://avatars.githubusercontent.com/u/2309868?v=4","gravatar_id":"","url":"https://api.github.com/users/luochen1990","html_url":"https://github.com/luochen1990","followers_url":"https://api.github.com/users/luochen1990/followers","following_url":"https://api.github.com/users/luochen1990/following{/other_user}","gists_url":"https://api.github.com/users/luochen1990/gists{/gist_id}","starred_url":"https://api.github.com/users/luochen1990/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/luochen1990/subscriptions","organizations_url":"https://api.github.com/users/luochen1990/orgs","repos_url":"https://api.github.com/users/luochen1990/repos","events_url":"https://api.github.com/users/luochen1990/events{/privacy}","received_events_url":"https://api.github.com/users/luochen1990/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-06T08:19:43Z","updated_at":"2022-01-31T06:13:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe man page of `nix-shell` described a usage like\r\n\r\n```shell\r\n#! /usr/bin/env nix-shell\r\n#! nix-shell deps.nix -i python\r\n```\r\n\r\nBut this pattern doesn't work when `deps.nix` uses `buildFHSUserEnv`.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Create a file named `script.sh` with following content:\r\n```python\r\n#! /usr/bin/env nix-shell\r\n#! nix-shell deps.nix -i sh\r\npython3 --version\r\n```\r\n2. Create a file named `deps.nix` with following content:\r\n```nix\r\n{ pkgs ? import <nixpkgs> {} }:\r\n\r\n(pkgs.buildFHSUserEnv {\r\n name = \"devbox\";\r\n targetPkgs = pkgs: (with pkgs; [\r\n python38\r\n python38Packages.pip\r\n python38Packages.virtualenv\r\n pythonManylinuxPackages.manylinux2014Package\r\n ]);\r\n runScript = \"bash\";\r\n}).env\r\n```\r\n3. Execute `chmod +x ./script.sh && ./script.sh`\r\n\r\n### Expected behavior\r\n\r\nExecute `./script.sh` prints the correct python version info which is `python3.8` or similar things\r\n\r\n### Got\r\n\r\nExecute `./script.sh` enters bash without printting anything\r\n\r\n### Metadata\r\n\r\n```\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.5-zen1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(root): `\"n-22.05pre343321.78cd22c1b86, nixos-22.05pre343321.78cd22c1b86, nixpkgs-22.05pre343295.adf7f03d3bf\"`\r\n - channels(lc): `\"n-21.11pre325514.a4bf4434570, nixos-21.11pre325514.a4bf4434570\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153693/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153689","id":1095044691,"node_id":"I_kwDOAEVQ_M5BRQ5T","number":153689,"title":"services.restic: Add option for starting restic backup after systemd unit completes","user":{"login":"jdheyburn","id":34041368,"node_id":"MDQ6VXNlcjM0MDQxMzY4","avatar_url":"https://avatars.githubusercontent.com/u/34041368?v=4","gravatar_id":"","url":"https://api.github.com/users/jdheyburn","html_url":"https://github.com/jdheyburn","followers_url":"https://api.github.com/users/jdheyburn/followers","following_url":"https://api.github.com/users/jdheyburn/following{/other_user}","gists_url":"https://api.github.com/users/jdheyburn/gists{/gist_id}","starred_url":"https://api.github.com/users/jdheyburn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jdheyburn/subscriptions","organizations_url":"https://api.github.com/users/jdheyburn/orgs","repos_url":"https://api.github.com/users/jdheyburn/repos","events_url":"https://api.github.com/users/jdheyburn/events{/privacy}","received_events_url":"https://api.github.com/users/jdheyburn/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-06T07:28:14Z","updated_at":"2022-01-07T01:13:20Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\nLooking to see if anyone else in restic community sees value in allowing for an option in the config to invoke a restic backup After the conclusion of another service.\r\n\r\nExample use case: chaining restic backups sequentially so as to not overload the OS or other resources.\r\n\r\n```nix\r\n services.restic.backups.my-backup = {\r\n # removed for brevity\r\n serviceConfig = {\r\n after = [ \"some-other-service.service\" ];\r\n };\r\n };\r\n```\r\n\r\n### Steps to reproduce\r\nN/A\r\n\r\n\r\n## Technical details\r\n\r\nN/A\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153689/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153666","id":1094870499,"node_id":"I_kwDOAEVQ_M5BQmXj","number":153666,"title":"Packaging Request: Remnants of the Precursors","user":{"login":"jtrees","id":5802758,"node_id":"MDQ6VXNlcjU4MDI3NTg=","avatar_url":"https://avatars.githubusercontent.com/u/5802758?v=4","gravatar_id":"","url":"https://api.github.com/users/jtrees","html_url":"https://github.com/jtrees","followers_url":"https://api.github.com/users/jtrees/followers","following_url":"https://api.github.com/users/jtrees/following{/other_user}","gists_url":"https://api.github.com/users/jtrees/gists{/gist_id}","starred_url":"https://api.github.com/users/jtrees/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jtrees/subscriptions","organizations_url":"https://api.github.com/users/jtrees/orgs","repos_url":"https://api.github.com/users/jtrees/repos","events_url":"https://api.github.com/users/jtrees/events{/privacy}","received_events_url":"https://api.github.com/users/jtrees/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-06T01:03:31Z","updated_at":"2022-01-06T01:03:31Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nRemnants of the Precursors is an open-source modernization of the 1993 classic \"Master of Orion\" written in Java.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://rayfowler.itch.io/remnants-of-the-precursors\r\n* source URL: https://github.com/rayfowler/rotp-public\r\n* licenses: various, primarily gpl3 (details [here](https://github.com/rayfowler/rotp-public/blob/master/LICENSE))\r\n* platforms: linux*\r\n\r\n\\* It (most likely) runs on many platforms, but I am specifically interested in linux support.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153666/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153659","id":1094833893,"node_id":"I_kwDOAEVQ_M5BQdbl","number":153659,"title":"Junction: Application chooser","user":{"login":"Birdthatcantfly","id":86254368,"node_id":"MDQ6VXNlcjg2MjU0MzY4","avatar_url":"https://avatars.githubusercontent.com/u/86254368?v=4","gravatar_id":"","url":"https://api.github.com/users/Birdthatcantfly","html_url":"https://github.com/Birdthatcantfly","followers_url":"https://api.github.com/users/Birdthatcantfly/followers","following_url":"https://api.github.com/users/Birdthatcantfly/following{/other_user}","gists_url":"https://api.github.com/users/Birdthatcantfly/gists{/gist_id}","starred_url":"https://api.github.com/users/Birdthatcantfly/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Birdthatcantfly/subscriptions","organizations_url":"https://api.github.com/users/Birdthatcantfly/orgs","repos_url":"https://api.github.com/users/Birdthatcantfly/repos","events_url":"https://api.github.com/users/Birdthatcantfly/events{/privacy}","received_events_url":"https://api.github.com/users/Birdthatcantfly/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-05T23:44:14Z","updated_at":"2022-01-05T23:44:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nJunction lets you choose the application to open files and links.\r\n\r\nJunction will pop up automatically when you open a link in a desktop application. Use the mouse or keyboard navigation to choose the application to open the link or file with. \r\n\r\n**Metadata**\r\n* homepage URL: https://apps.gnome.org/ru/app/re.sonny.Junction/\r\n* source URL: https://github.com/sonnyp/Junction\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153659/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153657","id":1094828476,"node_id":"I_kwDOAEVQ_M5BQcG8","number":153657,"title":"Maui Shell: convergent shell for desktops, tablets, and phones.","user":{"login":"Birdthatcantfly","id":86254368,"node_id":"MDQ6VXNlcjg2MjU0MzY4","avatar_url":"https://avatars.githubusercontent.com/u/86254368?v=4","gravatar_id":"","url":"https://api.github.com/users/Birdthatcantfly","html_url":"https://github.com/Birdthatcantfly","followers_url":"https://api.github.com/users/Birdthatcantfly/followers","following_url":"https://api.github.com/users/Birdthatcantfly/following{/other_user}","gists_url":"https://api.github.com/users/Birdthatcantfly/gists{/gist_id}","starred_url":"https://api.github.com/users/Birdthatcantfly/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Birdthatcantfly/subscriptions","organizations_url":"https://api.github.com/users/Birdthatcantfly/orgs","repos_url":"https://api.github.com/users/Birdthatcantfly/repos","events_url":"https://api.github.com/users/Birdthatcantfly/events{/privacy}","received_events_url":"https://api.github.com/users/Birdthatcantfly/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-05T23:31:29Z","updated_at":"2022-01-05T23:31:29Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nMaui Shell is a convergent shell for desktops, tablets, and phones.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://nxos.org/english/nxd/\r\n* source URL: https://github.com/Nitrux/maui-shell\r\n* license: lgpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153657/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153577","id":1094104844,"node_id":"I_kwDOAEVQ_M5BNrcM","number":153577,"title":"Stats","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2022-01-05T08:33:44Z","updated_at":"2022-01-10T08:58:38Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\n\r\nStats is a macOS app that displays system statistics such as CPU usage or power draw in the menu bar\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/exelban/stats\r\n* source URL: https://github.com/exelban/stats\r\n* license: mit\r\n* platforms: darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153577/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153537","id":1093905572,"node_id":"I_kwDOAEVQ_M5BM6yk","number":153537,"title":"Balena Etcher is broken","user":{"login":"gbtb","id":37017396,"node_id":"MDQ6VXNlcjM3MDE3Mzk2","avatar_url":"https://avatars.githubusercontent.com/u/37017396?v=4","gravatar_id":"","url":"https://api.github.com/users/gbtb","html_url":"https://github.com/gbtb","followers_url":"https://api.github.com/users/gbtb/followers","following_url":"https://api.github.com/users/gbtb/following{/other_user}","gists_url":"https://api.github.com/users/gbtb/gists{/gist_id}","starred_url":"https://api.github.com/users/gbtb/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/gbtb/subscriptions","organizations_url":"https://api.github.com/users/gbtb/orgs","repos_url":"https://api.github.com/users/gbtb/repos","events_url":"https://api.github.com/users/gbtb/events{/privacy}","received_events_url":"https://api.github.com/users/gbtb/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-05T01:59:51Z","updated_at":"2022-02-08T21:32:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nBalena etcher app starts with blank white screen\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install etcher 1.6.0 from unstable nixpkgs\r\n2. Run app\r\n3. ...\r\n\r\n### Expected behavior\r\nIt should open UI with buttons etc...\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nLogs in devtools of etcher:\r\n```\r\nindex.css:1 Failed to load resource: net::ERR_FILE_NOT_FOUND\r\ngui.js:7117 Uncaught TypeError: Cannot read properties of undefined (reading 'app')\r\n at appPath (gui.js:7117)\r\n at Object.exports.CODE_TO_ERRNO.E2BIG (gui.js:7119)\r\n at __webpack_require__ (gui.js:72085)\r\n at Object.__webpack_modules__.constructor (gui.js:5691)\r\n at __webpack_require__ (gui.js:72085)\r\n at Object.__webpack_modules__.DiskWrapper.DiskWrapper (gui.js:5686)\r\n at __webpack_require__ (gui.js:72085)\r\n at Object.<anonymous> (gui.js:5587)\r\n at __webpack_require__ (gui.js:72085)\r\n at Object.defineProperty.value (gui.js:5401)\r\n```\r\n\r\nLogs in terminal:\r\n```\r\n[Axios v1.6.0] Transitional option 'clarifyTimeoutError' has been deprecated since v1.0.0 and will be removed in the near future\r\n[Axios v1.6.0] Transitional option 'forcedJSONParsing' has been deprecated since v1.0.0 and will be removed in the near future\r\n[Axios v1.6.0] Transitional option 'silentJSONParsing' has been deprecated since v1.0.0 and will be removed in the near future\r\n(node:14552) electron: The default of nativeWindowOpen is deprecated and will be changing from false to true in Electron 15. See https://github.com/electron/electron/issues/28511 for more information.\r\n(Use `electron --trace-warnings ...` to show where the warning was created)\r\nready-to-show: 1.119s\r\n(node:14552) Warning: No such label 'ready-to-show' for console.timeEnd()\r\n```\r\n\r\n### Notify maintainers\r\n@Shou \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"home-manager-21.05, nixos-22.05pre342264.5b091d4fbe3, unstable-22.05pre340506.5c37ad87222\"`\r\n - channels(artem): `\"home-manager-21.05, nixos-22.05pre340506.5c37ad87222\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537/reactions","total_count":17,"+1":17,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153537/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153528","id":1093842140,"node_id":"I_kwDOAEVQ_M5BMrTc","number":153528,"title":"webkitgtk: broken on i686","user":{"login":"vvs-","id":5171934,"node_id":"MDQ6VXNlcjUxNzE5MzQ=","avatar_url":"https://avatars.githubusercontent.com/u/5171934?v=4","gravatar_id":"","url":"https://api.github.com/users/vvs-","html_url":"https://github.com/vvs-","followers_url":"https://api.github.com/users/vvs-/followers","following_url":"https://api.github.com/users/vvs-/following{/other_user}","gists_url":"https://api.github.com/users/vvs-/gists{/gist_id}","starred_url":"https://api.github.com/users/vvs-/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/vvs-/subscriptions","organizations_url":"https://api.github.com/users/vvs-/orgs","repos_url":"https://api.github.com/users/vvs-/repos","events_url":"https://api.github.com/users/vvs-/events{/privacy}","received_events_url":"https://api.github.com/users/vvs-/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T23:42:20Z","updated_at":"2022-01-04T23:42:20Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI think it should be marked as broken to avoid frustrating other people. This package is impossible to build without more than 4G address space due to linker memory exhaustion. It can be built only on 64-bit hosts (the same as Firefox).\r\n\r\nAnd that permanently breaks Gnome 3 on i686. It was possible to build it in the past using local modifications, though.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153528/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153512","id":1093730887,"node_id":"I_kwDOAEVQ_M5BMQJH","number":153512,"title":"[Packaging request] NocoDB","user":{"login":"onny","id":757752,"node_id":"MDQ6VXNlcjc1Nzc1Mg==","avatar_url":"https://avatars.githubusercontent.com/u/757752?v=4","gravatar_id":"","url":"https://api.github.com/users/onny","html_url":"https://github.com/onny","followers_url":"https://api.github.com/users/onny/followers","following_url":"https://api.github.com/users/onny/following{/other_user}","gists_url":"https://api.github.com/users/onny/gists{/gist_id}","starred_url":"https://api.github.com/users/onny/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/onny/subscriptions","organizations_url":"https://api.github.com/users/onny/orgs","repos_url":"https://api.github.com/users/onny/repos","events_url":"https://api.github.com/users/onny/events{/privacy}","received_events_url":"https://api.github.com/users/onny/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T20:32:09Z","updated_at":"2022-01-04T20:32:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n[NocoDB](https://nocodb.com/) is an [Airtable](https://www.airtable.com/) alternative, similar to [Baserow](https://baserow.io/). A web application for displaying and managing database information.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://nocodb.com\r\n* source URL: https://github.com/nocodb/nocodb\r\n* license: agpl3\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153512/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153495","id":1093619123,"node_id":"I_kwDOAEVQ_M5BL02z","number":153495,"title":"Pretix","user":{"login":"genofire","id":6905586,"node_id":"MDQ6VXNlcjY5MDU1ODY=","avatar_url":"https://avatars.githubusercontent.com/u/6905586?v=4","gravatar_id":"","url":"https://api.github.com/users/genofire","html_url":"https://github.com/genofire","followers_url":"https://api.github.com/users/genofire/followers","following_url":"https://api.github.com/users/genofire/following{/other_user}","gists_url":"https://api.github.com/users/genofire/gists{/gist_id}","starred_url":"https://api.github.com/users/genofire/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/genofire/subscriptions","organizations_url":"https://api.github.com/users/genofire/orgs","repos_url":"https://api.github.com/users/genofire/repos","events_url":"https://api.github.com/users/genofire/events{/privacy}","received_events_url":"https://api.github.com/users/genofire/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-04T17:54:01Z","updated_at":"2022-02-26T13:50:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nTicket shop application for conferences, festivals, concerts, tech events, shows, exhibitions, workshops, barcamps, etc. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://pretix.eu/\r\n* source URL: https://github.com/pretix/pretix/\r\n* license: AGPLv3 (with specials)\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153495/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153494","id":1093611030,"node_id":"I_kwDOAEVQ_M5BLy4W","number":153494,"title":"Package/module request: linkding","user":{"login":"peperunas","id":6033387,"node_id":"MDQ6VXNlcjYwMzMzODc=","avatar_url":"https://avatars.githubusercontent.com/u/6033387?v=4","gravatar_id":"","url":"https://api.github.com/users/peperunas","html_url":"https://github.com/peperunas","followers_url":"https://api.github.com/users/peperunas/followers","following_url":"https://api.github.com/users/peperunas/following{/other_user}","gists_url":"https://api.github.com/users/peperunas/gists{/gist_id}","starred_url":"https://api.github.com/users/peperunas/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peperunas/subscriptions","organizations_url":"https://api.github.com/users/peperunas/orgs","repos_url":"https://api.github.com/users/peperunas/repos","events_url":"https://api.github.com/users/peperunas/events{/privacy}","received_events_url":"https://api.github.com/users/peperunas/received_events","type":"User","site_admin":false},"labels":[{"id":290122483,"node_id":"MDU6TGFiZWwyOTAxMjI0ODM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(new)","name":"9.needs: package (new)","color":"eb6420","default":false,"description":null},{"id":290122569,"node_id":"MDU6TGFiZWwyOTAxMjI1Njk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20module%20(new)","name":"9.needs: module (new)","color":"eb6420","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T17:42:51Z","updated_at":"2022-01-04T23:55:35Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n Self-hosted bookmark service \r\n\r\n**Metadata**\r\n\r\n* source URL: https://github.com/sissbruecker/linkding\r\n* license: mit\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153494/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153490","id":1093585397,"node_id":"I_kwDOAEVQ_M5BLsn1","number":153490,"title":"Package/module request: Ghostfolio","user":{"login":"peperunas","id":6033387,"node_id":"MDQ6VXNlcjYwMzMzODc=","avatar_url":"https://avatars.githubusercontent.com/u/6033387?v=4","gravatar_id":"","url":"https://api.github.com/users/peperunas","html_url":"https://github.com/peperunas","followers_url":"https://api.github.com/users/peperunas/followers","following_url":"https://api.github.com/users/peperunas/following{/other_user}","gists_url":"https://api.github.com/users/peperunas/gists{/gist_id}","starred_url":"https://api.github.com/users/peperunas/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/peperunas/subscriptions","organizations_url":"https://api.github.com/users/peperunas/orgs","repos_url":"https://api.github.com/users/peperunas/repos","events_url":"https://api.github.com/users/peperunas/events{/privacy}","received_events_url":"https://api.github.com/users/peperunas/received_events","type":"User","site_admin":false},"labels":[{"id":290122483,"node_id":"MDU6TGFiZWwyOTAxMjI0ODM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(new)","name":"9.needs: package (new)","color":"eb6420","default":false,"description":null},{"id":290122569,"node_id":"MDU6TGFiZWwyOTAxMjI1Njk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20module%20(new)","name":"9.needs: module (new)","color":"eb6420","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T17:09:46Z","updated_at":"2022-01-04T23:55:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nOpen Source Wealth Management Software made for Humans \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://ghostfol.io\r\n* source URL: https://github.com/ghostfolio/ghostfolio\r\n* license: agpl3\r\n* platforms: linux","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153490/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153467","id":1093297971,"node_id":"I_kwDOAEVQ_M5BKmcz","number":153467,"title":"speechd reports no voices for festival lite","user":{"login":"jtojnar","id":705123,"node_id":"MDQ6VXNlcjcwNTEyMw==","avatar_url":"https://avatars.githubusercontent.com/u/705123?v=4","gravatar_id":"","url":"https://api.github.com/users/jtojnar","html_url":"https://github.com/jtojnar","followers_url":"https://api.github.com/users/jtojnar/followers","following_url":"https://api.github.com/users/jtojnar/following{/other_user}","gists_url":"https://api.github.com/users/jtojnar/gists{/gist_id}","starred_url":"https://api.github.com/users/jtojnar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jtojnar/subscriptions","organizations_url":"https://api.github.com/users/jtojnar/orgs","repos_url":"https://api.github.com/users/jtojnar/repos","events_url":"https://api.github.com/users/jtojnar/events{/privacy}","received_events_url":"https://api.github.com/users/jtojnar/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T12:17:08Z","updated_at":"2022-01-04T12:17:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"As noted in https://github.com/NixOS/nixpkgs/issues/78880#issuecomment-1004742345, `flite` backend lists no voices:\r\n\r\n```ShellSession\r\n$ env $(nix-build -A speechd --no-out-link)/bin/spd-say -o flite -L\r\n NAME LANGUAGE VARIANT\r\n```\r\n\r\neven though\r\n\r\n```ShellSession\r\n$ env $(nix-build -A speechd --no-out-link)/bin/spd-say 'Hello word! I am testing the speech dispatcher output modules.' -o flite\r\n```\r\n\r\nspeaks just fine.\r\n\r\nThis prevents Firefox’s narrate feature from working when speechd is configured to use flite backend.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153467/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153444","id":1093072488,"node_id":"I_kwDOAEVQ_M5BJvZo","number":153444,"title":"Inkscape does not do anything in aarch64-darwin.","user":{"login":"PartemImperium","id":88595311,"node_id":"MDQ6VXNlcjg4NTk1MzEx","avatar_url":"https://avatars.githubusercontent.com/u/88595311?v=4","gravatar_id":"","url":"https://api.github.com/users/PartemImperium","html_url":"https://github.com/PartemImperium","followers_url":"https://api.github.com/users/PartemImperium/followers","following_url":"https://api.github.com/users/PartemImperium/following{/other_user}","gists_url":"https://api.github.com/users/PartemImperium/gists{/gist_id}","starred_url":"https://api.github.com/users/PartemImperium/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/PartemImperium/subscriptions","organizations_url":"https://api.github.com/users/PartemImperium/orgs","repos_url":"https://api.github.com/users/PartemImperium/repos","events_url":"https://api.github.com/users/PartemImperium/events{/privacy}","received_events_url":"https://api.github.com/users/PartemImperium/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-04T07:10:57Z","updated_at":"2022-01-09T03:36:57Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen launching inkscape from command line the executable is started and it shows up in command + tab but no window shows up and wont quit unless force quit. If I install it as intel darwin (x86_64-darwin) either on an actual intel mac or through rosetta on a m1 it works just fine.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add inkscape to home-manager or any method of building inkscape\r\n2. Run inkscape in the command line (\"inkscape\")\r\n\r\n\r\n### Expected behavior\r\nThe app opens and is functional\r\n\r\n### Screenshots\r\n\r\n\r\n### Additional context\r\nThere is not any errors in the console (that are not also there when running the x86 version that works) but would be happy to share any log files that exist. I just dont know where they are to include here.\r\n\r\n### Notify maintainers\r\n@jtojnar \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.1.0, macOS 12.0.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(myUser): `\"darwin, home-manager, nixpkgs-22.05pre340506.5c37ad87222\"`\r\n - channels(root): `\"darwin, home-manager, nixpkgs-22.05pre335173.56cbe42f166\"`\r\n - nixpkgs: `/Users/myUser/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153444/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153429","id":1092981227,"node_id":"I_kwDOAEVQ_M5BJZHr","number":153429,"title":"Kavita comics/manga reader","user":{"login":"amaumene","id":2414933,"node_id":"MDQ6VXNlcjI0MTQ5MzM=","avatar_url":"https://avatars.githubusercontent.com/u/2414933?v=4","gravatar_id":"","url":"https://api.github.com/users/amaumene","html_url":"https://github.com/amaumene","followers_url":"https://api.github.com/users/amaumene/followers","following_url":"https://api.github.com/users/amaumene/following{/other_user}","gists_url":"https://api.github.com/users/amaumene/gists{/gist_id}","starred_url":"https://api.github.com/users/amaumene/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/amaumene/subscriptions","organizations_url":"https://api.github.com/users/amaumene/orgs","repos_url":"https://api.github.com/users/amaumene/repos","events_url":"https://api.github.com/users/amaumene/events{/privacy}","received_events_url":"https://api.github.com/users/amaumene/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-04T03:34:37Z","updated_at":"2022-01-04T03:34:37Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nLighting fast with a slick design, Kavita is a rocket fueled self-hosted digital library which supports a vast array of file formats. Install to start reading and share your server with your friends.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://www.kavitareader.com\r\n* source URL: https://github.com/Kareadita/Kavita\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153429/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153369","id":1092734081,"node_id":"I_kwDOAEVQ_M5BIcyB","number":153369,"title":"Evaluation-time checking of systemd units","user":{"login":"nh2","id":399535,"node_id":"MDQ6VXNlcjM5OTUzNQ==","avatar_url":"https://avatars.githubusercontent.com/u/399535?v=4","gravatar_id":"","url":"https://api.github.com/users/nh2","html_url":"https://github.com/nh2","followers_url":"https://api.github.com/users/nh2/followers","following_url":"https://api.github.com/users/nh2/following{/other_user}","gists_url":"https://api.github.com/users/nh2/gists{/gist_id}","starred_url":"https://api.github.com/users/nh2/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nh2/subscriptions","organizations_url":"https://api.github.com/users/nh2/orgs","repos_url":"https://api.github.com/users/nh2/repos","events_url":"https://api.github.com/users/nh2/events{/privacy}","received_events_url":"https://api.github.com/users/nh2/received_events","type":"User","site_admin":false},"labels":[{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":8,"created_at":"2022-01-03T18:44:46Z","updated_at":"2022-01-04T19:59:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"This ticket describes a way how we can make writing systemd dependencies much safer, but I need help with making its implementation better.\r\n\r\n---\r\n\r\nIn my deployments we have many NixOS modules with systemd units that depend on each other.\r\n\r\nWhen expressing dependencies, It is easy to make mistakes that are only noticed at runtime, e.g. in\r\n\r\n```nix\r\nafter = [ \"nginx.service\" ];\r\n```\r\n\r\nyou may forget to enable the nginx module, or make a typo, or have a new NixOS release rename the service so things will break in production.\r\n\r\nI have written an evaluation-time check like this:\r\n\r\n```nix\r\nafter = [ (ensureUnitExists config \"nginx.service\") ];\r\n```\r\n\r\nthat will complain if that unit does not exist on the machine.\r\n\r\nIt is implemented like this:\r\n\r\n```nix\r\n # Asserts that a systemd unit (like `nginx.service`) exists; then retuns it.\r\n ensureUnitExists = config: unitName:\r\n if builtins.hasAttr unitName config.systemd.units\r\n then unitName\r\n else abort \"Unit named '${unitName}' does not exist on host '${config.networking.hostName}'\";\r\n```\r\n\r\nTo do that, I had to modify nixpkgs like this:\r\n\r\n```diff\r\nniklas@ares ~/src/benaco-review/nix-channel/nixpkgs (git)-[remotes/origin/benaco-nixos-21.11] % git --no-pager show 724ff860e9a2477202efe2c6f7fb8a0d7f5545f8\r\ncommit 724ff860e9a2477202efe2c6f7fb8a0d7f5545f8\r\nAuthor: Niklas Hambüchen <mail@nh2.me>\r\nDate: Thu Nov 4 02:19:59 2021 +0000\r\n\r\n nixos/systemd: Add `unitName` attribute.\r\n \r\n Allows writing expressions like:\r\n \r\n systemd.services.nginx.after = [ \"${config.systemd.services.redis.unitName}.service\" ];\r\n \r\n which fail loudly at evaluation time when a unit name is mis-spelled\r\n or not declared for other reasons.\r\n\r\ndiff --git a/nixos/modules/system/boot/systemd-unit-options.nix b/nixos/modules/system/boot/systemd-unit-options.nix\r\nindex 4154389b2ce..f586215aec8 100644\r\n--- a/nixos/modules/system/boot/systemd-unit-options.nix\r\n+++ b/nixos/modules/system/boot/systemd-unit-options.nix\r\n@@ -96,6 +96,14 @@ in rec {\r\n \r\n commonUnitOptions = sharedOptions // {\r\n \r\n+ unitName = mkOption {\r\n+ type = types.str;\r\n+ default = config._module.args.name;\r\n+ description = ''\r\n+ Name of the unit, without suffix like \".service\"\r\n+ '';\r\n+ };\r\n+\r\n description = mkOption {\r\n default = \"\";\r\n type = types.str;\r\n```\r\n\r\nIt works, but the `config._module.args.name` magic has one drawback:\r\n\r\nIt generates NixOS manual/options rebuilds, which take long.\r\n\r\nIs there a better way we can do this?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153369/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153362","id":1092696855,"node_id":"I_kwDOAEVQ_M5BITsX","number":153362,"title":"Reference to undefined variable in systemd-boot","user":{"login":"d4hines","id":25231383,"node_id":"MDQ6VXNlcjI1MjMxMzgz","avatar_url":"https://avatars.githubusercontent.com/u/25231383?v=4","gravatar_id":"","url":"https://api.github.com/users/d4hines","html_url":"https://github.com/d4hines","followers_url":"https://api.github.com/users/d4hines/followers","following_url":"https://api.github.com/users/d4hines/following{/other_user}","gists_url":"https://api.github.com/users/d4hines/gists{/gist_id}","starred_url":"https://api.github.com/users/d4hines/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/d4hines/subscriptions","organizations_url":"https://api.github.com/users/d4hines/orgs","repos_url":"https://api.github.com/users/d4hines/repos","events_url":"https://api.github.com/users/d4hines/events{/privacy}","received_events_url":"https://api.github.com/users/d4hines/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":2636554152,"node_id":"MDU6TGFiZWwyNjM2NTU0MTUy","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20systemd","name":"6.topic: systemd","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-03T17:43:30Z","updated_at":"2022-01-04T21:15:05Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI believe there's an error in https://github.com/NixOS/nixpkgs/blob/master/nixos/modules/system/boot/loader/systemd-boot/systemd-boot-builder.py#L284: `profile` is referenced but is not in scope. This caused `nixos-rebuild switch` to fail for me.\r\n\r\n### Steps To Reproduce\r\n\r\nI don't have clear reproduction steps :( however, I can tell you what happened:\r\n\r\nI was installing the `esy` package from the https://github.com/anmonteiro/nix-overlays flake into my NixOS system flake. The `nixos-rebuild switch` failed because one of the dependency packages failed to build.\r\n\r\nGoing forward, all calls to `nixos-rebuild switch` failed with an error coming from the above systemd-boot script. I looked at the script, noticed the missing variable, remounted `/nix/store` as read/write, removed the reference to the missing variable, and `nixos-rebuild switch` works again. However, I still print the error caught:\r\n```\r\n[Errno 2] No such file or directory: '/nix/store/sq4mr090vgprxfh8x3hamhfz1hlwsr3p-pem-0.2.4-doc/kernel'\r\n```\r\nIt seems that this was the root error, which bubbled up and was caught by the error handler linked, only there's a bug in the handler code.\r\n\r\nI don't know what caused my initial error - the first package to fail to build was https://gitlab.com/nomadic-labs/lwt-exit and I'm guessing there is either some unexpected non-determinism in the test or something peculiar about my system. I'm not sure how that broke my whole NixOS system, but I'm guessing there was some necessary cleanup that was prevented but the bug I've described. \r\n\r\n### Expected behavior\r\n\r\nThe script should keep going as intended. Printing out the generation number (which _is_ in scope) would be a helpful clue from which to track down the error. \r\n\r\n### Screenshots\r\nN/A\r\n\r\n### Additional context\r\nMy system flake is here https://github.com/d4hines/beth/tree/nixos. Not much has changed between the occurrence of the error and now. \r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\nwarning: Nix search path entry '/nix/var/nix/profiles/per-user/root/channels/nixos' does not exist, ignoring\r\nwarning: Nix search path entry '/nix/var/nix/profiles/per-user/root/channels' does not exist, ignoring\r\nerror: file 'nixpkgs' was not found in the Nix search path (add it using $NIX_PATH or -I)\r\n\r\n at «string»:1:25:\r\n\r\n 1| {...}@args: with import <nixpkgs> args; (pkgs.runCommandCC or pkgs.runCommand) \"shell\" { buildInputs = [ (nix-info) ]; } \"\"\r\n | \r\n```\r\n\r\n(Obviously there's a problem with this output. I hypothesize the reason NIX_PATH is missing has something to do with installing NixOS from a flake via the method described in https://nixos.org/manual/nixos/stable/index.html#sec-installing-from-other-distro. This may or may not be related to the initial cause of my error, but regardless, I think I've still found a real bug in the above python systemd-boot script).","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153362/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153350","id":1092617094,"node_id":"I_kwDOAEVQ_M5BIAOG","number":153350,"title":"The `programs.unity3d.enable` option enables chromium suid sandboxing","user":{"login":"Munksgaard","id":230613,"node_id":"MDQ6VXNlcjIzMDYxMw==","avatar_url":"https://avatars.githubusercontent.com/u/230613?v=4","gravatar_id":"","url":"https://api.github.com/users/Munksgaard","html_url":"https://github.com/Munksgaard","followers_url":"https://api.github.com/users/Munksgaard/followers","following_url":"https://api.github.com/users/Munksgaard/following{/other_user}","gists_url":"https://api.github.com/users/Munksgaard/gists{/gist_id}","starred_url":"https://api.github.com/users/Munksgaard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Munksgaard/subscriptions","organizations_url":"https://api.github.com/users/Munksgaard/orgs","repos_url":"https://api.github.com/users/Munksgaard/repos","events_url":"https://api.github.com/users/Munksgaard/events{/privacy}","received_events_url":"https://api.github.com/users/Munksgaard/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-03T15:47:35Z","updated_at":"2022-01-04T10:37:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Is that really intended? It doesn't seem like the chromium suid sandboxing setting has anything to do with unity, and it certainly doesn't \"enable\" unity3d, as far as I can tell. The change was introduced two years ago with seemingly no explanation: https://github.com/NixOS/nixpkgs/commit/4ee3e8b21dfeaf236b86a0c109953dd809a77e64","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153343","id":1092580675,"node_id":"I_kwDOAEVQ_M5BH3VD","number":153343,"title":"ccache doesn't work for linux kernel","user":{"login":"WesleyAC","id":5001092,"node_id":"MDQ6VXNlcjUwMDEwOTI=","avatar_url":"https://avatars.githubusercontent.com/u/5001092?v=4","gravatar_id":"","url":"https://api.github.com/users/WesleyAC","html_url":"https://github.com/WesleyAC","followers_url":"https://api.github.com/users/WesleyAC/followers","following_url":"https://api.github.com/users/WesleyAC/following{/other_user}","gists_url":"https://api.github.com/users/WesleyAC/gists{/gist_id}","starred_url":"https://api.github.com/users/WesleyAC/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/WesleyAC/subscriptions","organizations_url":"https://api.github.com/users/WesleyAC/orgs","repos_url":"https://api.github.com/users/WesleyAC/repos","events_url":"https://api.github.com/users/WesleyAC/events{/privacy}","received_events_url":"https://api.github.com/users/WesleyAC/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2022-01-03T14:59:55Z","updated_at":"2022-01-25T19:28:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI am trying to use ccache to compile the linux kernel with the following config:\r\n\r\n```\r\n programs.ccache.enable = true;\r\n programs.ccache.packageNames = [ \"linuxPackages_latest\" ];\r\n nix.sandboxPaths = [ config.programs.ccache.cacheDir ];\r\n boot.kernelPackages = pkgs.linuxPackages_latest;\r\n```\r\n\r\nBut I get the following error:\r\n\r\n```\r\nerror: attribute 'override' missing, at /nix/var/nix/profiles/per-user/root/channels/nixos/nixos/modules/programs/ccache.nix:55:54\r\n```\r\n\r\n### Steps To Reproduce\r\n\r\n1. Use the four lines above in `/etc/nixos/configuration.nix`\r\n2. Run `nixos-rebuild switch`\r\n\r\n### Expected behavior\r\n\r\nKernel is built using ccache.\r\n\r\n### Additional context\r\n\r\n#62121 may be related?\r\n\r\n### Notify maintainers\r\n\r\nNot sure who this belongs to :(\r\n\r\n### Metadata\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334247.573095944e7\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153343/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153335","id":1092554362,"node_id":"I_kwDOAEVQ_M5BHw56","number":153335,"title":"Request: JetBrains `remote-dev-server`","user":{"login":"lorenzleutgeb","id":542154,"node_id":"MDQ6VXNlcjU0MjE1NA==","avatar_url":"https://avatars.githubusercontent.com/u/542154?v=4","gravatar_id":"","url":"https://api.github.com/users/lorenzleutgeb","html_url":"https://github.com/lorenzleutgeb","followers_url":"https://api.github.com/users/lorenzleutgeb/followers","following_url":"https://api.github.com/users/lorenzleutgeb/following{/other_user}","gists_url":"https://api.github.com/users/lorenzleutgeb/gists{/gist_id}","starred_url":"https://api.github.com/users/lorenzleutgeb/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lorenzleutgeb/subscriptions","organizations_url":"https://api.github.com/users/lorenzleutgeb/orgs","repos_url":"https://api.github.com/users/lorenzleutgeb/repos","events_url":"https://api.github.com/users/lorenzleutgeb/events{/privacy}","received_events_url":"https://api.github.com/users/lorenzleutgeb/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":16,"created_at":"2022-01-03T14:23:12Z","updated_at":"2022-04-09T15:29:47Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"JetBrains IDE products support \"Remote Development\" via a headless process running on the \"server\". They call this an \"IDE backend\" and the script to run it is named `remote-dev-server.sh`, see https://www.jetbrains.com/help/idea/2021.3/remote-development-overview.html#server_to_client\r\n\r\nI did not manage to get this running with IDEA:\r\n\r\n```\r\n% /nix/store/3ljqlkcarzxpxzsilhcnm71d1kdmsxgc-idea-ultimate-2021.3/idea-ultimate-2021.3/bin/remote-dev-server.sh status $PWD\r\nIDE config directory: /home/lorenz/.config/JetBrains/RemoteDev-IU/[REDACTED]\r\nIDE system directory: /var/run/user/1000/.cache/JetBrains/RemoteDev-IU/[REDACTED]\r\ncp: cannot stat '/nix/store/3ljqlkcarzxpxzsilhcnm71d1kdmsxgc-idea-ultimate-2021.3/idea-ultimate-2021.3/jbr': No such file or directory\r\n```\r\n\r\nIt appears to me that the version packaged in Nipxkgs does not include JBR, see https://github.com/NixOS/nixpkgs/blob/75a86ab9f5691930f79de6c72e9f80eb280cf2dd/pkgs/applications/editors/jetbrains/default.nix#L310\r\n\r\nIt would be nice to get this feature working.\r\n\r\nMaintainers: @edwtjo @gytis-ivaskevicius","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335/reactions","total_count":11,"+1":11,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153335/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153298","id":1092243412,"node_id":"I_kwDOAEVQ_M5BGk_U","number":153298,"title":"pkgs.mkShell: NIX_ENFORCE_PURITY is set during shellHook, but not afterwards","user":{"login":"bergkvist","id":410028,"node_id":"MDQ6VXNlcjQxMDAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/410028?v=4","gravatar_id":"","url":"https://api.github.com/users/bergkvist","html_url":"https://github.com/bergkvist","followers_url":"https://api.github.com/users/bergkvist/followers","following_url":"https://api.github.com/users/bergkvist/following{/other_user}","gists_url":"https://api.github.com/users/bergkvist/gists{/gist_id}","starred_url":"https://api.github.com/users/bergkvist/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/bergkvist/subscriptions","organizations_url":"https://api.github.com/users/bergkvist/orgs","repos_url":"https://api.github.com/users/bergkvist/repos","events_url":"https://api.github.com/users/bergkvist/events{/privacy}","received_events_url":"https://api.github.com/users/bergkvist/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-03T05:51:16Z","updated_at":"2022-01-03T13:16:53Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`$NIX_ENFORCE_PURITY` is set during invocation of shellHook, but when running commands in the resulting shell - `$NIX_ENFORCE_PURITY` is no longer set. This means that a gcc/ld command that works inside the shell might fail inside the shellHook when moving it here instead of typing it manually (https://github.com/NixOS/nixpkgs/issues/24660). This led to a lot of confusion for me.\r\n\r\n### Steps To Reproduce\r\n```nix\r\n{ pkgs ? import <nixpkgs> {} }:\r\npkgs.mkShell {\r\n shellHook = ''\r\n echo \"NIX_ENFORCE_PURITY=$NIX_ENFORCE_PURITY\"\r\n '';\r\n}\r\n```\r\n\r\n<img width=\"640\" alt=\"image\" src=\"https://user-images.githubusercontent.com/410028/147901948-b96c4930-d196-4eb8-bdc1-6286b13cbede.png\">\r\n\r\n### Expected behavior\r\nThe same environment variables are set both when running the shellHook and running commands in the resulting shell.\r\n\r\nIt probably makes sense for NIX_ENFORCE_PURITY to not be set inside shellHook.\r\n\r\n### Additional context\r\nI'm trying to automate the production of python wheels with shared library dependencies shipped inside the wheels. These wheels can't know anything about nix or the nix store to maximize portability. Using nix-shell with shellHook seemed like my best shot for running commands in an impure way, while still being able to take advantage of nixpkgs providing all my build-time dependencies.\r\n\r\nI got stuck for an hour or so here in confusion because of this issue.\r\n\r\n### Notify maintainers\r\n@zimbatm @roberth @Mic92 @fzakaria @nh2\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[tobias:~/repos/python-env/abc123]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.84-1-MANJARO, Manjaro Linux, noversion`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(tobias): `\"nixpkgs-22.05pre340506.5c37ad87222, nixpkgs-afdb5675a18-21.11pre293818.afdb5675a18, pkgs-22.05pre339892.7ac6901f5e3, pkgs-afdb5675a18-21.11pre293818.afdb5675a18\"`\r\n - nixpkgs: `/home/tobias/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153298/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153288","id":1092163237,"node_id":"I_kwDOAEVQ_M5BGRal","number":153288,"title":"No way to disable the at-least-one-priviledged-user check","user":{"login":"chkno","id":1118859,"node_id":"MDQ6VXNlcjExMTg4NTk=","avatar_url":"https://avatars.githubusercontent.com/u/1118859?v=4","gravatar_id":"","url":"https://api.github.com/users/chkno","html_url":"https://github.com/chkno","followers_url":"https://api.github.com/users/chkno/followers","following_url":"https://api.github.com/users/chkno/following{/other_user}","gists_url":"https://api.github.com/users/chkno/gists{/gist_id}","starred_url":"https://api.github.com/users/chkno/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/chkno/subscriptions","organizations_url":"https://api.github.com/users/chkno/orgs","repos_url":"https://api.github.com/users/chkno/repos","events_url":"https://api.github.com/users/chkno/events{/privacy}","received_events_url":"https://api.github.com/users/chkno/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-03T01:34:39Z","updated_at":"2022-01-03T01:34:39Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nThere is no way to intentionally build a NixOS system with no privileged access when `users.mutableUsers=false`. Sometimes this is desired. For example:\r\n * VM images often have no need for either mutableUsers or admin access.\r\n * NixOS tests hardly ever need mutableUsers or admin access.\r\n\r\nThis is a fine check to have in place by default, but it needs an escape hatch.\r\n\r\nIn fact, #93451 already required this escape hatch, and so it just added itself directly to this check as a special case. But editing the source of nixos/modules/config/users-groups.nix from user configuration with [the whole-module copy/paste + disabledModules escape hatch](https://nixos.org/manual/nixos/stable/#sec-replace-modules) is unpleasant.\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n```\r\n$ nix repl <<< 'with import <nixpkgs> {}; (nixos ({modulesPath, ...}: { imports = [ (modulesPath + \"/virtualisation/qemu-vm.nix\")]; users.mutableUsers = false; })).toplevel'\r\n\r\nerror: \r\nFailed assertions:\r\n- Neither the root account nor any wheel user has a password or SSH authorized key.\r\nYou must set one to prevent being locked out of your system.\r\n```\r\n\r\n### Expected behavior\r\n```\r\n$ nix repl <<< 'with import <nixpkgs> {}; (nixos ({modulesPath, ...}: { imports = [ (modulesPath + \"/virtualisation/qemu-vm.nix\")]; users.mutableUsers = false; users.requirePrivilegedUser = false; })).toplevel'\r\n\r\n«derivation /nix/store/0123456789abcdefghijklmnopqrstuv-nixos-system-nixos-22.05pre-git.drv»\r\n```\r\n\r\n### Additional context\r\n6e767657951788775451859f1c36d4eb0230581c Added this check\r\n#5329 and #7308: Original discussion of this check\r\n#93451 exempted Google OS Login from this check (@edef1c)\r\n#91238 fixed this check for special hashes\r\n#22082 and #95130: Discussion about making this check stronger / more nuanced","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153288/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153251","id":1092090540,"node_id":"I_kwDOAEVQ_M5BF_qs","number":153251,"title":"smplayer-skins","user":{"login":"farzin-az","id":82333104,"node_id":"MDQ6VXNlcjgyMzMzMTA0","avatar_url":"https://avatars.githubusercontent.com/u/82333104?v=4","gravatar_id":"","url":"https://api.github.com/users/farzin-az","html_url":"https://github.com/farzin-az","followers_url":"https://api.github.com/users/farzin-az/followers","following_url":"https://api.github.com/users/farzin-az/following{/other_user}","gists_url":"https://api.github.com/users/farzin-az/gists{/gist_id}","starred_url":"https://api.github.com/users/farzin-az/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/farzin-az/subscriptions","organizations_url":"https://api.github.com/users/farzin-az/orgs","repos_url":"https://api.github.com/users/farzin-az/repos","events_url":"https://api.github.com/users/farzin-az/events{/privacy}","received_events_url":"https://api.github.com/users/farzin-az/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2022-01-02T20:02:46Z","updated_at":"2022-01-05T15:09:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_describe the project a little_\r\nsmplayer has a diverse set of skins (themes). In other distros there is a package smplayer-skins which contains all the skins for the app. There is none in NixOS. Since I'm new to NixOS I don´t know how to package them so I make a package request.\r\n\r\n* homepage URL: https://www.smplayer.info/","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153251/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153238","id":1092076680,"node_id":"I_kwDOAEVQ_M5BF8SI","number":153238,"title":"Fwupd can use a bump from 1.7.2 to 1.7.3 to support StarBook Mk V","user":{"login":"kciredor","id":1121650,"node_id":"MDQ6VXNlcjExMjE2NTA=","avatar_url":"https://avatars.githubusercontent.com/u/1121650?v=4","gravatar_id":"","url":"https://api.github.com/users/kciredor","html_url":"https://github.com/kciredor","followers_url":"https://api.github.com/users/kciredor/followers","following_url":"https://api.github.com/users/kciredor/following{/other_user}","gists_url":"https://api.github.com/users/kciredor/gists{/gist_id}","starred_url":"https://api.github.com/users/kciredor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kciredor/subscriptions","organizations_url":"https://api.github.com/users/kciredor/orgs","repos_url":"https://api.github.com/users/kciredor/repos","events_url":"https://api.github.com/users/kciredor/events{/privacy}","received_events_url":"https://api.github.com/users/kciredor/received_events","type":"User","site_admin":false},"labels":[{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-02T18:42:17Z","updated_at":"2022-03-15T18:32:15Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on github to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: fwupd (unsure if dependency fwupd-efi needs a bump as well)\r\n<!--\r\nThe current version can be found easily with the same process than above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 1.7.2\r\ndesired version: 1.7.3\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @jtojnar\r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\nThanks for (hopefully) picking this up. The latest minor contains Star Labs patches allowing for fwupd to update Coreboot firmware on StarBook Mk V laptops.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153238/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153142","id":1091924831,"node_id":"I_kwDOAEVQ_M5BFXNf","number":153142,"title":"caddy: Allow raw JSON configs","user":{"login":"dwf","id":60206,"node_id":"MDQ6VXNlcjYwMjA2","avatar_url":"https://avatars.githubusercontent.com/u/60206?v=4","gravatar_id":"","url":"https://api.github.com/users/dwf","html_url":"https://github.com/dwf","followers_url":"https://api.github.com/users/dwf/followers","following_url":"https://api.github.com/users/dwf/following{/other_user}","gists_url":"https://api.github.com/users/dwf/gists{/gist_id}","starred_url":"https://api.github.com/users/dwf/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dwf/subscriptions","organizations_url":"https://api.github.com/users/dwf/orgs","repos_url":"https://api.github.com/users/dwf/repos","events_url":"https://api.github.com/users/dwf/events{/privacy}","received_events_url":"https://api.github.com/users/dwf/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-02T00:50:40Z","updated_at":"2022-01-02T15:06:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nThe current `services.caddy` definition does not allow one to provide a `configFile` in simple JSON, Caddy V2's native config format, because `adapter` is required. \"json5\" or \"jsonc\" adapters currently don't work in stable (probably missing plugins), but an adapter shouldn't be necessary.\r\n\r\nOne way forward would be to simply omit the `--adapter` argument if `cfg.adapter` is set to the empty string.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Try to specify a JSON file as `services.caddy.configFile`.\r\n\r\n### Expected behavior\r\nIt should be possible to specify raw JSON, natively processed by Caddy, as the configFile.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@Br1ght0ne\r\n\r\n### Metadata\r\n\r\n(N.B. this is still a problem in master, and my patch is against master)\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334139.1bd4bbd49be\"`\r\n - channels(dwf): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\noutput here\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153142/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153102","id":1091887469,"node_id":"I_kwDOAEVQ_M5BFOFt","number":153102,"title":"Genymotion package issues related to download and run","user":{"login":"mkmodrzew","id":12850581,"node_id":"MDQ6VXNlcjEyODUwNTgx","avatar_url":"https://avatars.githubusercontent.com/u/12850581?v=4","gravatar_id":"","url":"https://api.github.com/users/mkmodrzew","html_url":"https://github.com/mkmodrzew","followers_url":"https://api.github.com/users/mkmodrzew/followers","following_url":"https://api.github.com/users/mkmodrzew/following{/other_user}","gists_url":"https://api.github.com/users/mkmodrzew/gists{/gist_id}","starred_url":"https://api.github.com/users/mkmodrzew/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mkmodrzew/subscriptions","organizations_url":"https://api.github.com/users/mkmodrzew/orgs","repos_url":"https://api.github.com/users/mkmodrzew/repos","events_url":"https://api.github.com/users/mkmodrzew/events{/privacy}","received_events_url":"https://api.github.com/users/mkmodrzew/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-01T20:36:04Z","updated_at":"2022-01-01T20:36:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI'll try to describe two issues related to single packages, because I tried to solve problem on my own and I was partially successful, but couldn't move it to the working finish. \r\nFirst: trying to install genymotion fails with \r\n``` console\r\ntrying https://dl.genymotion.com/releases/genymotion-3.2.1/genymotion-3.2.1-linux_x64.bin\r\n % Total % Received % Xferd Average Speed Time Time Time Current\r\n Dload Upload Total Spent Left Speed\r\n 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0\r\ncurl: (22) The requested URL returned error: 403\r\nerror: cannot download genymotion-3.2.1-linux_x64.bin from any mirror\r\n```\r\n\r\nSecond: after replacing url address with local package, running `nixos-rebuild`, and running `genymotion` program failed with output:\r\n```console\r\nLogging activities to file: /home/michal/.Genymobile/genymotion.log\r\n2022-01-01T21:16:36+01:00 [Genymotion:22898] [fatal] Failed to load the component: qrc:/Launchpad/main.qml:10 Type ApplicationWindow unavailable\r\nfile:///nix/store/c87z3gm1f3rbcpk5j3xn0fx64y0w7lcf-qtquickcontrols2-5.15.3-bin/lib/qt-5.15.3/qml/QtQuick/Controls.2/Material/qmldir:-1 plugin cannot be loaded for module \"QtQuick.Controls.Material\": The plugin '/nix/store/c87z3gm1f3rbcpk5j3xn0fx64y0w7lcf-qtquickcontrols2-5.15.3-bin/lib/qt-5.15.3/qml/QtQuick/Controls.2/Material/libqtquickcontrols2materialstyleplugin.so' uses incompatible Qt library. (5.15.0) [release]\r\n\r\nAborted (core dumped)\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add `genymotion` to `environment.systemPackages` list in `/etc/nixos/configuration.nix` \r\n2. Run `sudo nixos-rebuild switch --upgrade`\r\n--- after successfully replacement url with local\r\n3. Run `genymotion`\r\n\r\n### Expected behavior\r\nWorking `genymotion` program \r\n\r\n### Notify maintainers\r\n@puffnfresh \r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.88, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334934.8a053bc2255\"`\r\n - channels(michal): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153102/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153083","id":1091848224,"node_id":"I_kwDOAEVQ_M5BFEgg","number":153083,"title":"Document interaction between `initialPassword` and `initialHashedPassword`","user":{"login":"nh2","id":399535,"node_id":"MDQ6VXNlcjM5OTUzNQ==","avatar_url":"https://avatars.githubusercontent.com/u/399535?v=4","gravatar_id":"","url":"https://api.github.com/users/nh2","html_url":"https://github.com/nh2","followers_url":"https://api.github.com/users/nh2/followers","following_url":"https://api.github.com/users/nh2/following{/other_user}","gists_url":"https://api.github.com/users/nh2/gists{/gist_id}","starred_url":"https://api.github.com/users/nh2/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/nh2/subscriptions","organizations_url":"https://api.github.com/users/nh2/orgs","repos_url":"https://api.github.com/users/nh2/repos","events_url":"https://api.github.com/users/nh2/events{/privacy}","received_events_url":"https://api.github.com/users/nh2/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":289925828,"node_id":"MDU6TGFiZWwyODk5MjU4Mjg=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20documentation","name":"9.needs: documentation","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2022-01-01T16:40:51Z","updated_at":"2022-01-06T17:31:16Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"The docs of [`initialPassword`](https://search.nixos.org/options?channel=21.11&show=users.users.%3Cname%3E.initialPassword&from=0&size=50&sort=relevance&type=packages&query=initialPassword) / [`initialHashedPassword`](https://search.nixos.org/options?channel=21.11&show=users.users.%3Cname%3E.initialHashedPassword&from=0&size=50&sort=relevance&type=packages&query=initialHashedPassword) are written as if they didn't know the other option existed.\r\n\r\n* [ ] The docs should explain how they interact, and which one wins if both are set.\r\n * From an initial read over the code; both are mingled into `users-groups.json` [here](https://github.com/NixOS/nixpkgs/blob/8a053bc2255659c5ca52706b9e12e76a8f50dbdd/nixos/modules/config/users-groups.nix#L416-L423) and then a Perl script [`update-users-groups.pl`](https://github.com/NixOS/nixpkgs/blob/8a053bc2255659c5ca52706b9e12e76a8f50dbdd/nixos/modules/config/users-groups.nix#L572) runs, which seems to prefer `initialPassword` over `initialHashedPassword` [here](https://github.com/NixOS/nixpkgs/blob/8a053bc2255659c5ca52706b9e12e76a8f50dbdd/nixos/modules/config/update-users-groups.pl#L218-L222), without a comment on why this order makes sense or is preferred.\r\n * They were originally introduced simultaneously by @edolstra in https://github.com/NixOS/nixpkgs/commit/1b53a3fcb7d6f1f31c4178131d8dff2177c81060\r\n* [ ] The docs should mention the ability to set the password to `\"!\"`, as was once documented e.g. [here](https://github.com/NixOS/nixpkgs/commit/0b92ad02c87b9eff8dbc45cc4221289d737d29a6) and [still appears possible](https://github.com/NixOS/nixpkgs/blob/8a053bc2255659c5ca52706b9e12e76a8f50dbdd/nixos/modules/config/users-groups.nix#L16-L23). It should be explained whether thta's exactly the same as setting it to `null`, or whether there are differences.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153083/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153078","id":1091838665,"node_id":"I_kwDOAEVQ_M5BFCLJ","number":153078,"title":"`reanimate-svg` Haskell package is broken due to failing tests","user":{"login":"srid","id":3998,"node_id":"MDQ6VXNlcjM5OTg=","avatar_url":"https://avatars.githubusercontent.com/u/3998?v=4","gravatar_id":"","url":"https://api.github.com/users/srid","html_url":"https://github.com/srid","followers_url":"https://api.github.com/users/srid/followers","following_url":"https://api.github.com/users/srid/following{/other_user}","gists_url":"https://api.github.com/users/srid/gists{/gist_id}","starred_url":"https://api.github.com/users/srid/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/srid/subscriptions","organizations_url":"https://api.github.com/users/srid/orgs","repos_url":"https://api.github.com/users/srid/repos","events_url":"https://api.github.com/users/srid/events{/privacy}","received_events_url":"https://api.github.com/users/srid/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2022-01-01T15:37:36Z","updated_at":"2022-01-22T03:10:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nThe `reanimate-svg` package, which is transitively used by https://reanimate.github.io, fails to build in latest Nixpkgs. Reproducible on both macOS and Linux.\r\n\r\n### Steps To Reproduce\r\n\r\nRun `bin/run` or `nix build` on https://github.com/srid/anima/tree/14896ecd098706f4ae4d0850d0a39e1b270ff408\r\n\r\n### Screenshots\r\n<img width=\"968\" alt=\"image\" src=\"https://user-images.githubusercontent.com/3998/147854118-aa89c74b-f03d-48f0-aa0e-8a961a6c23a9.png\">\r\n\r\n\r\n### Additional context\r\n\r\n```\r\nerror: builder for '/nix/store/6daxcs1kr7cchqn7js047vgf33ngjxgj-reanimate-svg-0.13.0.1.drv' failed with exit code 1;\r\n last 10 log lines:\r\n > Exception: rsvg-convert: startProcess: posix_spawnp: illegal operation (Inappropriate ioctl for device) (expected failure)\r\n > types-dom-svgstringlist-01-f: FAIL (expected)\r\n > Exception: rsvg-convert: startProcess: posix_spawnp: illegal operation (Inappropriate ioctl for device) (expected failure)\r\n > types-dom-svgtransformable-01-f: FAIL (expected)\r\n > Exception: rsvg-convert: startProcess: posix_spawnp: illegal operation (Inappropriate ioctl for device) (expected failure)\r\n >\r\n > 252 out of 504 tests failed (0.53s)\r\n > Test suite w3c-spec: FAIL\r\n > Test suite logged to: dist/test/reanimate-svg-0.13.0.1-w3c-spec.log\r\n > 0 of 1 test suites (0 of 1 test cases) passed.\r\n For full logs, run 'nix log /nix/store/6daxcs1kr7cchqn7js047vgf33ngjxgj-reanimate-svg-0.13.0.1.drv'.\r\n```\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n```\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(srid): `\"darwin\"`\r\n - channels(root): `\"nixpkgs-21.11pre333180.98747f27ecf\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153078/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153057","id":1091776663,"node_id":"I_kwDOAEVQ_M5BEzCX","number":153057,"title":"Add BuildRoot","user":{"login":"mollthecoder","id":63081316,"node_id":"MDQ6VXNlcjYzMDgxMzE2","avatar_url":"https://avatars.githubusercontent.com/u/63081316?v=4","gravatar_id":"","url":"https://api.github.com/users/mollthecoder","html_url":"https://github.com/mollthecoder","followers_url":"https://api.github.com/users/mollthecoder/followers","following_url":"https://api.github.com/users/mollthecoder/following{/other_user}","gists_url":"https://api.github.com/users/mollthecoder/gists{/gist_id}","starred_url":"https://api.github.com/users/mollthecoder/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/mollthecoder/subscriptions","organizations_url":"https://api.github.com/users/mollthecoder/orgs","repos_url":"https://api.github.com/users/mollthecoder/repos","events_url":"https://api.github.com/users/mollthecoder/events{/privacy}","received_events_url":"https://api.github.com/users/mollthecoder/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2022-01-01T09:05:21Z","updated_at":"2022-01-01T09:05:21Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n_Buildroot is a simple, efficient and easy-to-use tool to generate embedded Linux systems through cross-compilation._\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://buildroot.org/\r\n* source URL: https://git.buildroot.net/buildroot/ with an alternate mirror on Github https://github.com/buildroot/buildroot\r\n* license: mit, bsd, gpl2+ , ... version 2 or later of the GNU General Public License\r\n* platforms: unix, linux, darwin, ... Linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153057/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020/events","html_url":"https://github.com/NixOS/nixpkgs/issues/153020","id":1091712284,"node_id":"I_kwDOAEVQ_M5BEjUc","number":153020,"title":"PyQtChart please","user":{"login":"prehonor","id":10784632,"node_id":"MDQ6VXNlcjEwNzg0NjMy","avatar_url":"https://avatars.githubusercontent.com/u/10784632?v=4","gravatar_id":"","url":"https://api.github.com/users/prehonor","html_url":"https://github.com/prehonor","followers_url":"https://api.github.com/users/prehonor/followers","following_url":"https://api.github.com/users/prehonor/following{/other_user}","gists_url":"https://api.github.com/users/prehonor/gists{/gist_id}","starred_url":"https://api.github.com/users/prehonor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prehonor/subscriptions","organizations_url":"https://api.github.com/users/prehonor/orgs","repos_url":"https://api.github.com/users/prehonor/repos","events_url":"https://api.github.com/users/prehonor/events{/privacy}","received_events_url":"https://api.github.com/users/prehonor/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2022-01-01T01:46:11Z","updated_at":"2022-01-15T15:34:13Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nPyQtChart is a set of Python bindings for The Qt Company’s Qt Charts library. The bindings sit on top of PyQt5 and are implemented as a single module.\r\n\r\n**Metadata**\r\n\r\n* homepage URL:https://www.riverbankcomputing.com/software/pyqtchart/\r\n* source URL:https://pypi.org/project/PyQtChart/#files\r\n* license: GPL v3\r\n* platforms: unix, linux, darwin\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/153020/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152986","id":1091652809,"node_id":"I_kwDOAEVQ_M5BEUzJ","number":152986,"title":"Plasma5 and i3, better integration of window managers and desktop managers","user":{"login":"not7cd","id":4332632,"node_id":"MDQ6VXNlcjQzMzI2MzI=","avatar_url":"https://avatars.githubusercontent.com/u/4332632?v=4","gravatar_id":"","url":"https://api.github.com/users/not7cd","html_url":"https://github.com/not7cd","followers_url":"https://api.github.com/users/not7cd/followers","following_url":"https://api.github.com/users/not7cd/following{/other_user}","gists_url":"https://api.github.com/users/not7cd/gists{/gist_id}","starred_url":"https://api.github.com/users/not7cd/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/not7cd/subscriptions","organizations_url":"https://api.github.com/users/not7cd/orgs","repos_url":"https://api.github.com/users/not7cd/repos","events_url":"https://api.github.com/users/not7cd/events{/privacy}","received_events_url":"https://api.github.com/users/not7cd/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-31T19:17:02Z","updated_at":"2021-12-31T22:37:14Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"As I wanted to run i3wm within Plasma5 DE, I came to [this solution](https://discourse.nixos.org/t/how-can-i-use-i3-as-the-windowmanager-for-plasma5/6231/3?u=not7cd).\r\n\r\nAfter enabling both `plasma5`and `i3` nixos generates session profiles. One of them is `plasma5+i3`, but the config is quite naive, as it doesn't respect how plasma5 expects window manager to be supplied. Only one of them starts, and they don't integrate at all. This session is generated by this script.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/06edb74413eb4e4ac56921ef2c038d8f106b15df/nixos/modules/services/x11/display-managers/default.nix\r\n\r\nHere is a custom session that enables more proper behavior, at lest in my opinion, and according to previously mentioned solution. \r\n```\r\nservices.xserver.displayManager = {\r\n sddm.enable = true;\r\n defaultSession = \"plasma5+i3+whatever\";\r\n session = [\r\n {\r\n manage = \"desktop\";\r\n name = \"plasma5+i3+whatever\";\r\n start = ''exec env KDEWM=${pkgs.i3-gaps}/bin/i3 ${pkgs.plasma-workspace}/bin/startplasma-x11'';\r\n }\r\n ];\r\n};\r\n```\r\n\r\nI currently would propose to, whenever config for plasma5 is generated:\r\n1. Don't `exec` window manager executable before desktop manager\r\n2. Set `env KDEWM=$PATH_TO_WM_EXECUTABLE` before executing startplasma-x11","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152986/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152761","id":1091232163,"node_id":"I_kwDOAEVQ_M5BCuGj","number":152761,"title":"nwg-launchers: no icons shown","user":{"login":"asbachb","id":1482768,"node_id":"MDQ6VXNlcjE0ODI3Njg=","avatar_url":"https://avatars.githubusercontent.com/u/1482768?v=4","gravatar_id":"","url":"https://api.github.com/users/asbachb","html_url":"https://github.com/asbachb","followers_url":"https://api.github.com/users/asbachb/followers","following_url":"https://api.github.com/users/asbachb/following{/other_user}","gists_url":"https://api.github.com/users/asbachb/gists{/gist_id}","starred_url":"https://api.github.com/users/asbachb/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/asbachb/subscriptions","organizations_url":"https://api.github.com/users/asbachb/orgs","repos_url":"https://api.github.com/users/asbachb/repos","events_url":"https://api.github.com/users/asbachb/events{/privacy}","received_events_url":"https://api.github.com/users/asbachb/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2021-12-30T17:46:45Z","updated_at":"2022-01-26T18:48:51Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\n\r\nWindow Manager: `sway`\r\n\r\n`configuration.nix`:\r\n```\r\n [...]\r\n programs.sway.enable = true;\r\n programs.sway.extraPackages = with pkgs; [\r\n [...]\r\n gnome3.adwaita-icon-theme\r\n nwg-launchers\r\n ];\r\n programs.sway.wrapperFeatures.gtk = true;\r\n```\r\n\r\n### Expected behavior\r\nShow icons.\r\n\r\n### Screenshots\r\n\r\n\r\n### Notify maintainers\r\n@bbigras @Artturin \r\n\r\n### Metadata\r\n```console\r\n asbachb@nixos-t14s ~ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(asbachb): `\"\"`\r\n - channels(root): `\"nixos-22.05pre341453.ac169ec6371, nixos-hardware\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n\r\n### Additional context\r\n```console\r\nasbachb@nixos-t14s ~ nwggrid\r\nINFO: wm: sway\r\nINFO: Locale: en\r\nINFO: Using css file '\"/home/asbachb/.config/nwg-launchers/nwggrid/style.css\"'\r\nERROR: Failed to load icon 'vlc': Icon 'vlc' not present in theme Adwaita\r\nERROR: Failed to load icon 'vlc': Failed to open file “/usr/share/pixmaps/vlc”: No such file or directory\r\nfalling back to placeholder\r\nERROR: Failed to load icon 'org.gnome.Evince': Icon 'org.gnome.Evince' not present in theme Adwaita\r\nERROR: Failed to load icon 'org.gnome.Evince': Failed to open file “/usr/share/pixmaps/org.gnome.Evince”: No such file or directory\r\nfalling back to placeholder\r\nERROR: Failed to load icon 'firefox': Icon 'firefox' not present in theme Adwaita\r\nERROR: Failed to load icon 'firefox': Failed to open file “/usr/share/pixmaps/firefox”: No such file or directory\r\nfalling back to placeholder\r\nERROR: Failed to load icon 'gparted': Icon 'gparted' not present in theme Adwaita\r\nERROR: Failed to load icon 'gparted': Failed to open file “/usr/share/pixmaps/gparted”: No such file or directory\r\n```\r\n\r\nIcon Loading in nwg_launcher: https://github.com/nwg-piotr/nwg-launchers/blob/4dde40e2a0d82ae87a262e0c2babd22e309d28bf/common/nwg_classes.cc#L243-L263","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152761/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152649","id":1090937395,"node_id":"I_kwDOAEVQ_M5BBmIz","number":152649,"title":"`lib.showOption` doesn't quote attributes with periods","user":{"login":"lilyball","id":714,"node_id":"MDQ6VXNlcjcxNA==","avatar_url":"https://avatars.githubusercontent.com/u/714?v=4","gravatar_id":"","url":"https://api.github.com/users/lilyball","html_url":"https://github.com/lilyball","followers_url":"https://api.github.com/users/lilyball/followers","following_url":"https://api.github.com/users/lilyball/following{/other_user}","gists_url":"https://api.github.com/users/lilyball/gists{/gist_id}","starred_url":"https://api.github.com/users/lilyball/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lilyball/subscriptions","organizations_url":"https://api.github.com/users/lilyball/orgs","repos_url":"https://api.github.com/users/lilyball/repos","events_url":"https://api.github.com/users/lilyball/events{/privacy}","received_events_url":"https://api.github.com/users/lilyball/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-30T07:57:01Z","updated_at":"2022-03-01T20:10:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`lib.showOption` doesn't quote attributes containing periods, so the output is identical for e.g. `[ \"a.b\" ]` and `[ \"a\" \"b\" ]`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `lib.showOption [ \"a\" \"b.c\" \"d\" ]`\r\n\r\n### Expected behavior\r\nIt should return `''a.\"b.c\".d''`. Instead it returns `''a.b.c.d''`.\r\n\r\n### Additional context\r\nIt also doesn't include quotes for components containing other non-attribute-valid chars such as spaces. This is more of an aesthetic issue as `a.b c.d` is unambiguous, though it bothers me. Not quoting components containing periods is a correctness issue.\r\n\r\nRight now it calls `lib.strings.escapeNixString` and checks if the output is identical to `\"${part}\"`. It does have comments explaining that it allows options starting with digits, as well as placeholders like `*` and `<name>`. This means it can't just use `lib.strings.escapeNixIdentifier`. But it could still be a bit smarter about this, inlining `lib.strings.escapeNixIdentifier` and then modifying the regex to allow these additional values.\r\n\r\nMy suggestion for such a regex is something like `\"([^[:punct:][:space:]]|['_<>*-])+\"`. This way most punctuation and all whitespace will cause quoting but it will still allow `*` and `<name>`. Alternatively it could be more conservative and only quote for spaces and periods, but it seems more reasonable to me to quote for arbitrary punctuation as well.\r\n\r\n### Notify maintainers\r\n@jtojnar @grahamc @LnL7 @Infinisil\r\n\r\n### Metadata\r\n\r\n```console\r\n❯ nix run nixpkgs#nix-info -- -m\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `relaxed`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(lily): `\"darwin, home-manager\"`\r\n - channels(root): `\"nixpkgs-21.11pre330171.92204897f3d\"`\r\n - nixpkgs: `/etc/nix/inputs/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152649/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152645","id":1090902203,"node_id":"I_kwDOAEVQ_M5BBdi7","number":152645,"title":"google-chrome-stable hangs at startup in gnome due to gnome-keyring","user":{"login":"jsravn","id":522123,"node_id":"MDQ6VXNlcjUyMjEyMw==","avatar_url":"https://avatars.githubusercontent.com/u/522123?v=4","gravatar_id":"","url":"https://api.github.com/users/jsravn","html_url":"https://github.com/jsravn","followers_url":"https://api.github.com/users/jsravn/followers","following_url":"https://api.github.com/users/jsravn/following{/other_user}","gists_url":"https://api.github.com/users/jsravn/gists{/gist_id}","starred_url":"https://api.github.com/users/jsravn/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jsravn/subscriptions","organizations_url":"https://api.github.com/users/jsravn/orgs","repos_url":"https://api.github.com/users/jsravn/repos","events_url":"https://api.github.com/users/jsravn/events{/privacy}","received_events_url":"https://api.github.com/users/jsravn/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-30T06:20:58Z","updated_at":"2022-02-18T00:21:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen using Gnome, google-chrome-stable randomly hangs at startup. Using the flag `--password-store=basic` makes chrome always start up successfully.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install Gnome\r\n2. Run google-chrome-stable (possibly with a google login/profile)\r\n3. Observe a hang\r\n\r\n### Expected behavior\r\nIt should always start up. I first noticed this behavior in 21.05, had no issues in 20.09. Took me a while to figure out what was causing it.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nSeems to be reported elsewhere, such as here: https://bbs.archlinux.org/viewtopic.php?id=270871\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, nixos-21.11.334921.8588b14a397, nixos-unstable-22.05pre341453.ac169ec6371, nixpkgs-unstable-22.05pre340506.5c37ad87222\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152645/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152641","id":1090890244,"node_id":"I_kwDOAEVQ_M5BBaoE","number":152641,"title":"`nixos-rebuild dry-build` with flakes enabled required root","user":{"login":"psydvl","id":43755002,"node_id":"MDQ6VXNlcjQzNzU1MDAy","avatar_url":"https://avatars.githubusercontent.com/u/43755002?v=4","gravatar_id":"","url":"https://api.github.com/users/psydvl","html_url":"https://github.com/psydvl","followers_url":"https://api.github.com/users/psydvl/followers","following_url":"https://api.github.com/users/psydvl/following{/other_user}","gists_url":"https://api.github.com/users/psydvl/gists{/gist_id}","starred_url":"https://api.github.com/users/psydvl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/psydvl/subscriptions","organizations_url":"https://api.github.com/users/psydvl/orgs","repos_url":"https://api.github.com/users/psydvl/repos","events_url":"https://api.github.com/users/psydvl/events{/privacy}","received_events_url":"https://api.github.com/users/psydvl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-30T05:44:19Z","updated_at":"2022-01-01T21:46:02Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n``` console\r\n$ nixos-rebuild dry-build\r\nwarning: updating lock file '/etc/nixos/flake.lock':\r\n• Added input 'nixos-unstable':\r\n 'github:NixOS/nixpkgs/ac169ec6371f0d835542db654a65e0f2feb07838' (2021-12-26)\r\n• Updated input 'nixpkgs':\r\n 'github:NixOS/nixpkgs/5c37ad87222cfc1ec36d6cd1364514a9efc2f7f2' (2021-12-25)\r\n → 'github:NixOS/nixpkgs/8588b14a397e045692d0a87192810b6dddf53003' (2021-12-29)\r\nerror: opening file '/etc/nixos/flake.lock': Permission denied\r\n(use '--show-trace' to show detailed location information)\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable flake and create `flake.nix` file with any inputs for your NixOS\r\n2. Try dry build\r\n\r\n### Expected behavior\r\nNo root access required for dry build, because it's for testing and shouldn't override nothing\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.3-zen1, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11.334797.6979c0e49bb, nixos-unstable-22.05pre340469.cb372c3b888\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152641/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152622","id":1090746592,"node_id":"I_kwDOAEVQ_M5BA3jg","number":152622,"title":"Cannot enable bluetooth from KDE settings","user":{"login":"niknetniko","id":1756811,"node_id":"MDQ6VXNlcjE3NTY4MTE=","avatar_url":"https://avatars.githubusercontent.com/u/1756811?v=4","gravatar_id":"","url":"https://api.github.com/users/niknetniko","html_url":"https://github.com/niknetniko","followers_url":"https://api.github.com/users/niknetniko/followers","following_url":"https://api.github.com/users/niknetniko/following{/other_user}","gists_url":"https://api.github.com/users/niknetniko/gists{/gist_id}","starred_url":"https://api.github.com/users/niknetniko/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/niknetniko/subscriptions","organizations_url":"https://api.github.com/users/niknetniko/orgs","repos_url":"https://api.github.com/users/niknetniko/repos","events_url":"https://api.github.com/users/niknetniko/events{/privacy}","received_events_url":"https://api.github.com/users/niknetniko/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-29T20:59:47Z","updated_at":"2022-03-05T10:55:59Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen bluetooth is disabled, I cannot enable it from the KDE settings.\r\nI can, however, enable it using blueman. Afterwards, I can manage using KDE settings fine, but I have to enable using blueman first.\r\n\r\n(I'm pretty new to linux/nixos, so excuse me if the wrong terms are used here)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Have bluetooth disabled.\r\n2. Go to KDE system settings (or launch `kcmshell5 bluetooth`)\r\n3. Press the button to enable bluetooth\r\n\r\n### Expected behavior\r\nBluetooth should be enabled, just like with blueman.\r\n\r\n### Additional context\r\nWhen running from the console, this error is printed:\r\n\r\n```console\r\n$ kcmshell5 bluetooth\r\nkf.kirigami: Units.devicePixelRatio is deprecated (since 5.86 ): This returns 1 when using Qt HiDPI scaling.\r\nfile:///nix/store/sknfvzd3wd7kqwxkcy55ijq8l0waqsb3-bluedevil-5.23.4/share/kpackage/kcms/kcm_bluetooth/contents/ui/Bluetooth.qml:83:13: QML InlineMessage: Cannot anchor to an item that isn't a parent or sibling.\r\nkf.bluezqt: Cannot open /dev/rfkill for writing!\r\n```\r\n\r\nWhen in this state, `rfkill` lists:\r\n\r\n```console\r\n$ rfkill\r\nID TYPE DEVICE SOFT HARD\r\n 0 wlan dell-wifi unblocked unblocked\r\n 1 bluetooth dell-bluetooth blocked unblocked\r\n 2 wlan phy0 unblocked unblocked\r\n```\r\n\r\nHowever, once I turned on bluetooth using blueman, I can manage it from the KDE settings just fine.\r\nThe same error is printed though, so I'm not sure what's happening.\r\n\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@ttuegel @nyanloutre (sorry if not the correct maintainers, unsure where the issue is exactly)\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(niko): `\"\"`\r\n - channels(root): `\"nixos-22.05pre341453.ac169ec6371, android, nix-ld\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nI'm on nixos-unstable, Plasma 5.23.4, KDE Frameworks 5.87.0, QT 5.13.3","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152622/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152615","id":1090718399,"node_id":"I_kwDOAEVQ_M5BAwq_","number":152615,"title":"Breaking change from 21.05 to 21.11: filesystem topology requirements","user":{"login":"jeaye","id":1057635,"node_id":"MDQ6VXNlcjEwNTc2MzU=","avatar_url":"https://avatars.githubusercontent.com/u/1057635?v=4","gravatar_id":"","url":"https://api.github.com/users/jeaye","html_url":"https://github.com/jeaye","followers_url":"https://api.github.com/users/jeaye/followers","following_url":"https://api.github.com/users/jeaye/following{/other_user}","gists_url":"https://api.github.com/users/jeaye/gists{/gist_id}","starred_url":"https://api.github.com/users/jeaye/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jeaye/subscriptions","organizations_url":"https://api.github.com/users/jeaye/orgs","repos_url":"https://api.github.com/users/jeaye/repos","events_url":"https://api.github.com/users/jeaye/events{/privacy}","received_events_url":"https://api.github.com/users/jeaye/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-29T19:49:51Z","updated_at":"2022-02-12T13:26:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI am running NixOS on a Digital Ocean droplet, which used nixos-in-place to turn a Debian machine into a NixOS machine. DO requires that the root of the filesystem still be a \"normal\" Debian distro, since it injects files in there for things like configuring network interfaces. To work around this, nixos-in-place installs NixOS to `/nixos` and then creates a bind mount on boot such that `/` becomes `/nixos`. This has worked for 5 years and 21.11 breaks it.\r\n\r\nNote, this breakage was not noted in the release notes for 21.11. It may be unintentional.\r\n\r\n### Steps To Reproduce\r\nThis is the config which nixos-in-place creates:\r\n\r\n```nix\r\n{ config, pkgs, ... }:\r\n{\r\n boot.kernelParams = [\"boot.shell_on_fail\"];\r\n boot.loader.grub.device = \"/dev/vda\";\r\n boot.loader.grub.storePath = \"/nixos/nix/store\";\r\n boot.initrd.supportedFilesystems = [ \"ext4\" ];\r\n boot.initrd.postDeviceCommands = ''\r\n mkdir -p /mnt-root/old-root ;\r\n mount -t ext4 /dev/vda1 /mnt-root/old-root ;\r\n '';\r\n fileSystems = {\r\n \"/\" = {\r\n device = \"/old-root/nixos\";\r\n fsType = \"none\";\r\n \"options\" = [ \"bind\" ];\r\n };\r\n \"/old-root\" = {\r\n device = \"/dev/vda1\";\r\n fsType = \"ext4\";\r\n };\r\n };\r\n \r\n ## Digital Ocean networking setup; manage interfaces manually\r\n networking.useDHCP = false;\r\n\r\n systemd.services.setup-network = {\r\n wantedBy = [ \"multi-user.target\" ];\r\n after = [ \"network-pre.target\" ];\r\n path = [ pkgs.gawk pkgs.iproute pkgs.openresolv ];\r\n serviceConfig = {\r\n ExecStart = \"${pkgs.bash}/bin/bash /etc/nixos-in-place/setup-network\";\r\n };\r\n };\r\n}\r\n```\r\nWhen I try to upgrade to 21.11, I see this:\r\n\r\n```bash\r\n[root@nixums:/etc/nixos]# nix-channel --add https://nixos.org/channels/nixos-21.11-small nixos\r\n[root@nixums:/etc/nixos]# nixos-rebuild switch --upgrade\r\n...\r\nbuilding Nix...\r\nbuilding the system configuration...\r\nerror: \r\nFailed assertions:\r\n- The ‘fileSystems’ option can't be topologically sorted: mountpoint dependency path / -> /old-root loops to /\r\n```\r\n\r\n#### Depends\r\nNote that I've found a recent change to add a `depends` attribute: https://github.com/NixOS/nixpkgs/pull/86967\r\nI've tried adding that to the `/` mount, like so:\r\n\r\n```nix\r\n fileSystems = {\r\n \"/\" = {\r\n device = \"/old-root/nixos\";\r\n fsType = \"none\";\r\n \"options\" = [ \"bind\" ];\r\n depends = [ \"/old-root\" ];\r\n };\r\n \"/old-root\" = {\r\n device = \"/dev/vda1\";\r\n fsType = \"ext4\";\r\n };\r\n };\r\n```\r\n\r\nIt had no effect.\r\n\r\n### Expected behavior\r\nI would expect this behavior to remain as it has for all previous versions.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\nHard to say. The blame on this error shows it, and the surrounding code, is quite old: https://github.com/NixOS/nixpkgs/blame/0699530f08290f34c532beedd66046825d9756fa/nixos/modules/tasks/filesystems.nix#L230\r\nPerhaps @dotlambda \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[root@nixums:/etc/nixos]# nix-shell -p nix-info --run \"nix-info -m\"\r\nthese paths will be fetched (49.20 MiB download, 227.57 MiB unpacked):\r\n /nix/store/12z1nc5fmif2z7wian28n55j61acbmny-glibc-2.33-59-dev\r\n /nix/store/1mhhdzc1x7z8xm0jqmgi0fisc9ibx9q8-bash-interactive-5.1-p8-info\r\n /nix/store/2ah5bynj7yb45vzqlga3dhvpi1lrawg4-glibc-2.33-59-bin\r\n /nix/store/79zvzq15mga6bgk5phnmw0fd2pnpim9v-bash-interactive-5.1-p8\r\n /nix/store/dzlbars3xgx3jh2hkldwavy0crkg328h-readline-8.1p0\r\n /nix/store/fh3cdchz3x43znd5sahi2fy0fz3pwqj9-expand-response-params\r\n /nix/store/gd7ihraqqpginv5cmhgk347nfn2iiqkj-bash-interactive-5.1-p8-dev\r\n /nix/store/gkzmfpb04ddb7phzj8g9sl6saxzprssg-gcc-wrapper-10.3.0\r\n /nix/store/jjv2lgwg9a5wg88xaa195fa47r6skfiz-ncurses-6.2\r\n /nix/store/k8qjik2a44ljdx48lmin2byz77ssrngk-stdenv-linux\r\n /nix/store/kb6iwp7acy1wibygx7phvpd24z2nqn03-bash-interactive-5.1-p8-man\r\n /nix/store/mrqrvina0lfgrvdzfyri7sw9vxy6pyms-gcc-10.3.0\r\n /nix/store/qypk3gzaf4p5bhzmyzjmlycs8v2sdw2h-nix-info\r\n /nix/store/rbqplhv2s539liymkvm3zbjj9lvgzpd5-binutils-2.35.2\r\n /nix/store/vafyy0lx82py8403bvkaki34i5bpin2n-linux-headers-5.14\r\n /nix/store/xa3xdjy1pifx8nwcxd75jmsx9n6jch97-bash-interactive-5.1-p8-doc\r\n /nix/store/z3fj7lv606mcdllhg0q7d98lpgc7b21z-binutils-wrapper-2.35.2\r\ncopying path '/nix/store/xa3xdjy1pifx8nwcxd75jmsx9n6jch97-bash-interactive-5.1-p8-doc' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/1mhhdzc1x7z8xm0jqmgi0fisc9ibx9q8-bash-interactive-5.1-p8-info' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/kb6iwp7acy1wibygx7phvpd24z2nqn03-bash-interactive-5.1-p8-man' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/rbqplhv2s539liymkvm3zbjj9lvgzpd5-binutils-2.35.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/fh3cdchz3x43znd5sahi2fy0fz3pwqj9-expand-response-params' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/2ah5bynj7yb45vzqlga3dhvpi1lrawg4-glibc-2.33-59-bin' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/vafyy0lx82py8403bvkaki34i5bpin2n-linux-headers-5.14' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/jjv2lgwg9a5wg88xaa195fa47r6skfiz-ncurses-6.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/12z1nc5fmif2z7wian28n55j61acbmny-glibc-2.33-59-dev' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/qypk3gzaf4p5bhzmyzjmlycs8v2sdw2h-nix-info' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/z3fj7lv606mcdllhg0q7d98lpgc7b21z-binutils-wrapper-2.35.2' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/mrqrvina0lfgrvdzfyri7sw9vxy6pyms-gcc-10.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/dzlbars3xgx3jh2hkldwavy0crkg328h-readline-8.1p0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gkzmfpb04ddb7phzj8g9sl6saxzprssg-gcc-wrapper-10.3.0' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/79zvzq15mga6bgk5phnmw0fd2pnpim9v-bash-interactive-5.1-p8' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/k8qjik2a44ljdx48lmin2byz77ssrngk-stdenv-linux' from 'https://cache.nixos.org'...\r\ncopying path '/nix/store/gd7ihraqqpginv5cmhgk347nfn2iiqkj-bash-interactive-5.1-p8-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.87, NixOS, 21.05.4666.7bca80140fc (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"nixos-21.11.334917.e101dc111ac, unstable-21.11pre295280.fa0326ce523\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152615/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152607","id":1090652487,"node_id":"I_kwDOAEVQ_M5BAglH","number":152607,"title":"Add Freelan","user":{"login":"aidalgol","id":2313201,"node_id":"MDQ6VXNlcjIzMTMyMDE=","avatar_url":"https://avatars.githubusercontent.com/u/2313201?v=4","gravatar_id":"","url":"https://api.github.com/users/aidalgol","html_url":"https://github.com/aidalgol","followers_url":"https://api.github.com/users/aidalgol/followers","following_url":"https://api.github.com/users/aidalgol/following{/other_user}","gists_url":"https://api.github.com/users/aidalgol/gists{/gist_id}","starred_url":"https://api.github.com/users/aidalgol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/aidalgol/subscriptions","organizations_url":"https://api.github.com/users/aidalgol/orgs","repos_url":"https://api.github.com/users/aidalgol/repos","events_url":"https://api.github.com/users/aidalgol/events{/privacy}","received_events_url":"https://api.github.com/users/aidalgol/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-29T17:19:07Z","updated_at":"2021-12-29T17:19:07Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nFreelan is a simple-to-use, peer-to-peer VPN system. One of its advantages over other VPN software is that it is a layer 2 VPN, making it possible to run LAN games that use broadcast addressing.\r\n\r\n**Metadata**\r\n* homepage URL: http://freelan.org/\r\n* source URL: https://github.com/freelan-developers/freelan\r\n* license: GPL 3 or later with OpenSSL exception\r\n* platforms: Linux, maybe Darwin?\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152607/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152592","id":1090586174,"node_id":"I_kwDOAEVQ_M5BAQY-","number":152592,"title":"Can't mount iphone","user":{"login":"tobiasBora","id":2164118,"node_id":"MDQ6VXNlcjIxNjQxMTg=","avatar_url":"https://avatars.githubusercontent.com/u/2164118?v=4","gravatar_id":"","url":"https://api.github.com/users/tobiasBora","html_url":"https://github.com/tobiasBora","followers_url":"https://api.github.com/users/tobiasBora/followers","following_url":"https://api.github.com/users/tobiasBora/following{/other_user}","gists_url":"https://api.github.com/users/tobiasBora/gists{/gist_id}","starred_url":"https://api.github.com/users/tobiasBora/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tobiasBora/subscriptions","organizations_url":"https://api.github.com/users/tobiasBora/orgs","repos_url":"https://api.github.com/users/tobiasBora/repos","events_url":"https://api.github.com/users/tobiasBora/events{/privacy}","received_events_url":"https://api.github.com/users/tobiasBora/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1025428533,"node_id":"MDU6TGFiZWwxMDI1NDI4NTMz","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20hardware","name":"6.topic: hardware","color":"fef2c0","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2021-12-29T15:16:58Z","updated_at":"2021-12-30T12:42:46Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI'm trying to mount the Iphone of a friend on NixOs, but I can't manage to do it. I tried to follow the wiki instructions, and also to install ifuse, but nothing mounts in Dolphin or nautilus, and `ifuse` does not find the device:\r\n\r\n\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior. First, add in your configuration:\r\n```\r\n{ config, pkgs, lib, ... }:\r\n{\r\n # Read iphones (see also ifuse?) https://nixos.wiki/wiki/IOS\r\n services.usbmuxd.enable = true;\r\n environment.systemPackages = with pkgs; [\r\n ifuse # I tried to add that\r\n libimobiledevice\r\n ];\r\n}\r\n```\r\n\r\nThen, dolphin shows nothing in the left pannel, and ifuse gives this error:\r\n```\r\n$ mkdir /tmp/iphone/\r\n$ sudo ifuse /tmp/iphone/\r\nERROR: No device found!\r\nIs the device properly connected?\r\nIf it is make sure that your user has permissions to access the raw USB device.\r\nIf you're still having issues try unplugging the device and reconnecting it.\r\n```\r\n\r\nThe very first time I plugged the phone I needed to type a password on the Iphone to allow the computer to access it, but then nothing happened.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152592/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152506","id":1090146849,"node_id":"I_kwDOAEVQ_M5A-lIh","number":152506,"title":"libreoffice has implicit dependencies on grep, sed and coreutils","user":{"login":"KAction","id":44864956,"node_id":"MDQ6VXNlcjQ0ODY0OTU2","avatar_url":"https://avatars.githubusercontent.com/u/44864956?v=4","gravatar_id":"","url":"https://api.github.com/users/KAction","html_url":"https://github.com/KAction","followers_url":"https://api.github.com/users/KAction/followers","following_url":"https://api.github.com/users/KAction/following{/other_user}","gists_url":"https://api.github.com/users/KAction/gists{/gist_id}","starred_url":"https://api.github.com/users/KAction/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/KAction/subscriptions","organizations_url":"https://api.github.com/users/KAction/orgs","repos_url":"https://api.github.com/users/KAction/repos","events_url":"https://api.github.com/users/KAction/events{/privacy}","received_events_url":"https://api.github.com/users/KAction/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-28T21:57:48Z","updated_at":"2021-12-28T21:57:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n```\r\n$ git log --format=%H -1\r\neaeea6e9337b93d2acb7c2aa27e3f4617408375a\r\n$ nix-build -A libreoffice\r\n/nix/store/g33sl8d7ja46skl3515rwjwcwp5jz3fy-libreoffice-7.1.8.1\r\n$ ./result/bin/libreoffice --help > /dev/null\r\n$ /usr/bin/env -i ./result/bin/libreoffice --help > /dev/null\r\n./result/bin/libreoffice: line 5: uname: command not found\r\n./result/bin/libreoffice: line 5: grep: command not found\r\n./result/bin/libreoffice: line 28: basename: command not found\r\n./result/bin/libreoffice: line 28: /nix/store/h76ql0ka27mdlfs5rv4jfz5wvbwvskp9-libreoffice-7.1.8.1/bin/: Is a directory\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152506/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152423","id":1089661824,"node_id":"I_kwDOAEVQ_M5A8uuA","number":152423,"title":"ledger-live-desktop does not start","user":{"login":"grnnja","id":31556469,"node_id":"MDQ6VXNlcjMxNTU2NDY5","avatar_url":"https://avatars.githubusercontent.com/u/31556469?v=4","gravatar_id":"","url":"https://api.github.com/users/grnnja","html_url":"https://github.com/grnnja","followers_url":"https://api.github.com/users/grnnja/followers","following_url":"https://api.github.com/users/grnnja/following{/other_user}","gists_url":"https://api.github.com/users/grnnja/gists{/gist_id}","starred_url":"https://api.github.com/users/grnnja/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/grnnja/subscriptions","organizations_url":"https://api.github.com/users/grnnja/orgs","repos_url":"https://api.github.com/users/grnnja/repos","events_url":"https://api.github.com/users/grnnja/events{/privacy}","received_events_url":"https://api.github.com/users/grnnja/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-28T07:08:06Z","updated_at":"2021-12-28T07:08:06Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nledger-live-desktop hangs and does not open a window\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install ledger-live-desktop\r\n2. launch in terminal\r\n\r\n### Expected behavior\r\nledger-live-desktop opens a new window with the program in it.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nthis gets printed in the terminal:\r\n```Ledger Live 2.36.3\r\ninit\r\nChecking for update\r\nspawned internal process 97\r\nUpdate for version 2.36.3 is not available (latest version: 2.36.3, downgrade is disallowed).\r\n```\r\nand the program hangs and does not open a window.\r\nI'm on wayland (sway) if that's relevant.\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@andresilva @thedavidmeister @nyanloutre @RaghavSood @th0rgal\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n```\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.11, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.6.0pre20211217_6e6e998`\r\n - channels(root): `\"nixos\"`\r\n - channels(prem): `\"nixos-22.05pre335501.c71f061c68b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152423/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152406","id":1089542948,"node_id":"I_kwDOAEVQ_M5A8Rsk","number":152406,"title":"`pgmanage.service` defines a package option, but does not use it in the service definition.","user":{"login":"MarcFontaine","id":1433367,"node_id":"MDQ6VXNlcjE0MzMzNjc=","avatar_url":"https://avatars.githubusercontent.com/u/1433367?v=4","gravatar_id":"","url":"https://api.github.com/users/MarcFontaine","html_url":"https://github.com/MarcFontaine","followers_url":"https://api.github.com/users/MarcFontaine/followers","following_url":"https://api.github.com/users/MarcFontaine/following{/other_user}","gists_url":"https://api.github.com/users/MarcFontaine/gists{/gist_id}","starred_url":"https://api.github.com/users/MarcFontaine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MarcFontaine/subscriptions","organizations_url":"https://api.github.com/users/MarcFontaine/orgs","repos_url":"https://api.github.com/users/MarcFontaine/repos","events_url":"https://api.github.com/users/MarcFontaine/events{/privacy}","received_events_url":"https://api.github.com/users/MarcFontaine/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":290122605,"node_id":"MDU6TGFiZWwyOTAxMjI2MDU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20module%20(update)","name":"9.needs: module (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":{"login":"MarcFontaine","id":1433367,"node_id":"MDQ6VXNlcjE0MzMzNjc=","avatar_url":"https://avatars.githubusercontent.com/u/1433367?v=4","gravatar_id":"","url":"https://api.github.com/users/MarcFontaine","html_url":"https://github.com/MarcFontaine","followers_url":"https://api.github.com/users/MarcFontaine/followers","following_url":"https://api.github.com/users/MarcFontaine/following{/other_user}","gists_url":"https://api.github.com/users/MarcFontaine/gists{/gist_id}","starred_url":"https://api.github.com/users/MarcFontaine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MarcFontaine/subscriptions","organizations_url":"https://api.github.com/users/MarcFontaine/orgs","repos_url":"https://api.github.com/users/MarcFontaine/repos","events_url":"https://api.github.com/users/MarcFontaine/events{/privacy}","received_events_url":"https://api.github.com/users/MarcFontaine/received_events","type":"User","site_admin":false},"assignees":[{"login":"MarcFontaine","id":1433367,"node_id":"MDQ6VXNlcjE0MzMzNjc=","avatar_url":"https://avatars.githubusercontent.com/u/1433367?v=4","gravatar_id":"","url":"https://api.github.com/users/MarcFontaine","html_url":"https://github.com/MarcFontaine","followers_url":"https://api.github.com/users/MarcFontaine/followers","following_url":"https://api.github.com/users/MarcFontaine/following{/other_user}","gists_url":"https://api.github.com/users/MarcFontaine/gists{/gist_id}","starred_url":"https://api.github.com/users/MarcFontaine/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/MarcFontaine/subscriptions","organizations_url":"https://api.github.com/users/MarcFontaine/orgs","repos_url":"https://api.github.com/users/MarcFontaine/repos","events_url":"https://api.github.com/users/MarcFontaine/events{/privacy}","received_events_url":"https://api.github.com/users/MarcFontaine/received_events","type":"User","site_admin":false}],"milestone":null,"comments":0,"created_at":"2021-12-28T00:59:20Z","updated_at":"2021-12-28T00:59:20Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`pgmanage.service` defines a package option, but does not use it in the service definition.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/be5272250926e352427b3c62c6066a95c6592375/nixos/modules/services/databases/pgmanage.nix#L190\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Set an alternative package to use\r\n2. Rebuild system\r\n3. Setting is ignored\r\n\r\n### Expected behavior\r\nAs there is an option to set an alternative package, this setting should be honored. \r\n\r\n### Additional context\r\nThe current version of pkgs.pgmanage is broken, which was the motivation to actually use the package option.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152406/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152404","id":1089532101,"node_id":"I_kwDOAEVQ_M5A8PDF","number":152404,"title":"Failure to build pkgsMusl.libredirect","user":{"login":"KAction","id":44864956,"node_id":"MDQ6VXNlcjQ0ODY0OTU2","avatar_url":"https://avatars.githubusercontent.com/u/44864956?v=4","gravatar_id":"","url":"https://api.github.com/users/KAction","html_url":"https://github.com/KAction","followers_url":"https://api.github.com/users/KAction/followers","following_url":"https://api.github.com/users/KAction/following{/other_user}","gists_url":"https://api.github.com/users/KAction/gists{/gist_id}","starred_url":"https://api.github.com/users/KAction/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/KAction/subscriptions","organizations_url":"https://api.github.com/users/KAction/orgs","repos_url":"https://api.github.com/users/KAction/repos","events_url":"https://api.github.com/users/KAction/events{/privacy}","received_events_url":"https://api.github.com/users/KAction/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-28T00:14:40Z","updated_at":"2021-12-28T00:14:40Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"Attribute `pkgsMusl.libredirect` fails to build:\n\n```\n$ uname -a\nLinux (none) 5.15.7 #1 SMP Sat Dec 11 21:04:53 UTC 2021 x86_64 GNU/Linux\n$ git log --format='%ci %H' -1\n2021-12-26 15:50:06 -0500 28e6997f6f7c6b31fe7f341de3eb0aab1872262a\n$ nix-instantiate -A pkgsMusl.libredirect\n[...]\n\u001b[01m\u001b[Klibredirect.c:166:17:\u001b[m\u001b[K \u001b[01;31m\u001b[Kerror: \u001b[m\u001b[Kredefinition of ‘\u001b[01m\u001b[Kfopen\u001b[m\u001b[K’\n 166 | WRAPPER(FILE *, \u001b[01;31m\u001b[Kfopen64\u001b[m\u001b[K)(const char * path, const char * mode)\n | \u001b[01;31m\u001b[K^~~~~~~\u001b[m\u001b[K\n\u001b[01m\u001b[Klibredirect.c:28:34:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[Kin definition of macro ‘\u001b[01m\u001b[KWRAPPER\u001b[m\u001b[K’\n 28 | #define WRAPPER(ret, name) ret \u001b[01;36m\u001b[Kname\u001b[m\u001b[K\n | \u001b[01;36m\u001b[K^~~~\u001b[m\u001b[K\nIn file included from \u001b[01m\u001b[Klibredirect.c:2\u001b[m\u001b[K:\n\u001b[01m\u001b[K/nix/store/mlijpwqjym7x7ch81jzmb85n3s1s5l9r-musl-1.2.2-dev/include/stdio.h:68:7:\u001b[m\u001b[K \u001b[01;36m\u001b[Knote: \u001b[m\u001b[Kprevious definition of ‘\u001b[01m\u001b[Kfopen\u001b[m\u001b[K’ was here\n 68 | FILE *\u001b[01;36m\u001b[Kfopen\u001b[m\u001b[K(const char *__restrict, const char *__restrict);\n | \u001b[01;36m\u001b[K^~~~~\u001b[m\u001b[K\n```\n\nFull build log is available here: https://gist.github.com/5b1c00e9c3d7b8d3cdc2a2ca40536670\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152404/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152293","id":1088865660,"node_id":"I_kwDOAEVQ_M5A5sV8","number":152293,"title":"Difference between plasma-integration, kwayland-integration and plasma-browser integration?","user":{"login":"LoveIsGrief","id":2829538,"node_id":"MDQ6VXNlcjI4Mjk1Mzg=","avatar_url":"https://avatars.githubusercontent.com/u/2829538?v=4","gravatar_id":"","url":"https://api.github.com/users/LoveIsGrief","html_url":"https://github.com/LoveIsGrief","followers_url":"https://api.github.com/users/LoveIsGrief/followers","following_url":"https://api.github.com/users/LoveIsGrief/following{/other_user}","gists_url":"https://api.github.com/users/LoveIsGrief/gists{/gist_id}","starred_url":"https://api.github.com/users/LoveIsGrief/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/LoveIsGrief/subscriptions","organizations_url":"https://api.github.com/users/LoveIsGrief/orgs","repos_url":"https://api.github.com/users/LoveIsGrief/repos","events_url":"https://api.github.com/users/LoveIsGrief/events{/privacy}","received_events_url":"https://api.github.com/users/LoveIsGrief/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-26T23:41:45Z","updated_at":"2021-12-26T23:41:45Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"## Issue description\r\n\r\nWhen searching on https://search.nixos.org for \"plasma integration\" there are 2 different packages : `plasma-integration` and `plasma-browser-integration`. Looking further [in the repo](https://github.com/NixOS/nixpkgs/tree/master/pkgs/desktops/plasma-5) to try and find a distinction, there's additionally a [`kwayland-integration`](https://github.com/NixOS/nixpkgs/blob/master/pkgs/desktops/plasma-5/kwayland-integration.nix). To make matters even more confusing [`plasma-integration/default.nix`](https://github.com/NixOS/nixpkgs/blob/master/pkgs/desktops/plasma-5/plasma-integration/default.nix) requires `kwayland`\r\n\r\nWhat are all these packages? Are they related? Aliases? Copies?\r\n\r\n@ttuegel @bkchr would probably know more.\r\n\r\nI don't know if `mkDerivation` allows adding a description, but that or a comment in the `.nix` files would be greatly appreciated.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152293/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152284","id":1088853668,"node_id":"I_kwDOAEVQ_M5A5pak","number":152284,"title":"kalendar: Segmentation fault on startup","user":{"login":"pinpox","id":1719781,"node_id":"MDQ6VXNlcjE3MTk3ODE=","avatar_url":"https://avatars.githubusercontent.com/u/1719781?v=4","gravatar_id":"","url":"https://api.github.com/users/pinpox","html_url":"https://github.com/pinpox","followers_url":"https://api.github.com/users/pinpox/followers","following_url":"https://api.github.com/users/pinpox/following{/other_user}","gists_url":"https://api.github.com/users/pinpox/gists{/gist_id}","starred_url":"https://api.github.com/users/pinpox/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/pinpox/subscriptions","organizations_url":"https://api.github.com/users/pinpox/orgs","repos_url":"https://api.github.com/users/pinpox/repos","events_url":"https://api.github.com/users/pinpox/events{/privacy}","received_events_url":"https://api.github.com/users/pinpox/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-26T22:13:01Z","updated_at":"2022-01-31T09:58:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nThe application `kalendar` segfaults on startup.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-shell -p kalendar\r\n2. kalendar\r\n\r\n\r\n### Expected behavior\r\nApplication starts\r\n\r\n\r\n\r\n### Additional context\r\n```\r\n~ via ❄ impure (shell)\r\n» kalendar\r\norg.kde.pim.akonadicore: Unable to execute akonadi_control, falling back to D-Bus auto-launch\r\norg.kde.pim.akonadicore: Unable to execute akonadi_control, falling back to D-Bus auto-launch\r\norg.kde.pim.akonadicore: Unable to execute akonadi_control, falling back to D-Bus auto-launch\r\nkf.kirigami: Warning: Theme implementations should use Kirigami.BasicThemeDefinition for its root item\r\nkf.kirigami: Failed to find a Kirigami platform plugin\r\nqrc:/ScheduleView.qml:47: TypeError: Cannot read property 'item' of null\r\nqrc:/ScheduleView.qml:77: TypeError: Cannot read property 'firstDayOfMonth' of null\r\nqrc:/DatePicker.qml:27: TypeError: Cannot read property 'startDate' of null\r\nzsh: segmentation fault (core dumped) kalendar\r\n```\r\n### Notify maintainers\r\n@chuangzhu \r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.87, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"\"`\r\n - channels(pinpox): `\"home-manager\"`\r\n - nixpkgs: `/nix/store/293cqgx8pcmkcn9mx5ln6i9nwvxv274r-source````\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152284/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152270","id":1088834961,"node_id":"I_kwDOAEVQ_M5A5k2R","number":152270,"title":"Problem with RDRAND on AMD Ryzen","user":{"login":"lagunoff","id":11205014,"node_id":"MDQ6VXNlcjExMjA1MDE0","avatar_url":"https://avatars.githubusercontent.com/u/11205014?v=4","gravatar_id":"","url":"https://api.github.com/users/lagunoff","html_url":"https://github.com/lagunoff","followers_url":"https://api.github.com/users/lagunoff/followers","following_url":"https://api.github.com/users/lagunoff/following{/other_user}","gists_url":"https://api.github.com/users/lagunoff/gists{/gist_id}","starred_url":"https://api.github.com/users/lagunoff/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lagunoff/subscriptions","organizations_url":"https://api.github.com/users/lagunoff/orgs","repos_url":"https://api.github.com/users/lagunoff/repos","events_url":"https://api.github.com/users/lagunoff/events{/privacy}","received_events_url":"https://api.github.com/users/lagunoff/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-26T19:57:39Z","updated_at":"2022-01-10T00:27:26Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nWhen I try to upgrade the system from nixos-20.09 it won't start with following error:\r\n```\r\nterminate called after throwing an instance of 'std::runtime_error'\r\n what(): random_device: rdrand failed\r\n```\r\nSame thing if I try to install something from unstable (`https://nixos.org/channels/nixos-unstable`) . \r\n```console\r\n$ nix-channel --list\r\nnixos https://nixos.org/channels/nixos-20.09\r\nunstable https://nixos.org/channels/nixos-unstable\r\n$ nix-env -iA unstable.tdesktop\r\n$ telegram-desktop\r\nterminate called after throwing an instance of 'std::runtime_error'\r\n what(): random_device: rdrand failed\r\n[1] 28708 abort (core dumped) telegram-desktop\r\n```\r\nCurrently running `nixos-20.09` on `AMD Ryzen 9 5950X` it seems nixos-20.09 is the last release that can work with Ryzen processors \r\n\r\n### Steps To Reproduce\r\n1. Running nixos-20.09 on AMD Ryzen try to upgrade it to nixos-21.11\r\n2. It won't upgrade showing this error message:\r\n```console\r\nbuilding Nix...\r\nbuilding the system configuration...\r\nterminate called after throwing an instance of 'std::runtime_error'\r\n what(): random_device: rdrand fail\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152270/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152257","id":1088814116,"node_id":"I_kwDOAEVQ_M5A5fwk","number":152257,"title":"mediathekview: libnotify missing?","user":{"login":"Moredread","id":100848,"node_id":"MDQ6VXNlcjEwMDg0OA==","avatar_url":"https://avatars.githubusercontent.com/u/100848?v=4","gravatar_id":"","url":"https://api.github.com/users/Moredread","html_url":"https://github.com/Moredread","followers_url":"https://api.github.com/users/Moredread/followers","following_url":"https://api.github.com/users/Moredread/following{/other_user}","gists_url":"https://api.github.com/users/Moredread/gists{/gist_id}","starred_url":"https://api.github.com/users/Moredread/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Moredread/subscriptions","organizations_url":"https://api.github.com/users/Moredread/orgs","repos_url":"https://api.github.com/users/Moredread/repos","events_url":"https://api.github.com/users/Moredread/events{/privacy}","received_events_url":"https://api.github.com/users/Moredread/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-26T17:34:38Z","updated_at":"2021-12-26T17:35:44Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nRunning mediathekview produces the following error:\r\n\r\n```\r\n...\r\n. failed to initialize libNotify\r\njava.lang.UnsatisfiedLinkError: Unable to load library 'libnotify.so.4':\r\nlibnotify.so.4: cannot open shared object file: No such file or directory\r\nlibnotify.so.4: cannot open shared object file: No such file or directory\r\n...\r\n```\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.80, NixOS, 21.05.4349.09650059d7f (Okapi)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(root): `\"home-manager-21.11, lorri, mozilla-overlay, nixos-21.11.334797.6979c0e49bb, nixos-hardware, nixos-unstable-22.05pre340324.eac07edbd20, nixpkgs-21.11.334797.6979c0e49bb, nur\"`\r\n - channels(addy): `\"home-manager-21.11, lorri, mozilla-overlay, nixos-21.11.334797.6979c0e49bb, nixos-hardware, nixos-unstable-22.05pre340324.eac07edbd20, nixpkgs-21.11.334797.6979c0e49bb, nur\"`\r\n - nixpkgs: `/home/addy/.nix-defexpr/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152257/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152254","id":1088811176,"node_id":"I_kwDOAEVQ_M5A5fCo","number":152254,"title":"prusa-slicer: cli build (maybe SuperSlicer aswell)","user":{"login":"Moredread","id":100848,"node_id":"MDQ6VXNlcjEwMDg0OA==","avatar_url":"https://avatars.githubusercontent.com/u/100848?v=4","gravatar_id":"","url":"https://api.github.com/users/Moredread","html_url":"https://github.com/Moredread","followers_url":"https://api.github.com/users/Moredread/followers","following_url":"https://api.github.com/users/Moredread/following{/other_user}","gists_url":"https://api.github.com/users/Moredread/gists{/gist_id}","starred_url":"https://api.github.com/users/Moredread/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Moredread/subscriptions","organizations_url":"https://api.github.com/users/Moredread/orgs","repos_url":"https://api.github.com/users/Moredread/repos","events_url":"https://api.github.com/users/Moredread/events{/privacy}","received_events_url":"https://api.github.com/users/Moredread/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-26T17:14:50Z","updated_at":"2021-12-26T17:14:50Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\n\r\nPrusa-slicer supports building without a GUI. Needs work to move GUI only options behind build flag.\r\n\r\nMight also apply to other slic3r forks.\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152254/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152201","id":1088725010,"node_id":"I_kwDOAEVQ_M5A5KAS","number":152201,"title":"Add node package highlight.js","user":{"login":"McSinyx","id":13689192,"node_id":"MDQ6VXNlcjEzNjg5MTky","avatar_url":"https://avatars.githubusercontent.com/u/13689192?v=4","gravatar_id":"","url":"https://api.github.com/users/McSinyx","html_url":"https://github.com/McSinyx","followers_url":"https://api.github.com/users/McSinyx/followers","following_url":"https://api.github.com/users/McSinyx/following{/other_user}","gists_url":"https://api.github.com/users/McSinyx/gists{/gist_id}","starred_url":"https://api.github.com/users/McSinyx/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/McSinyx/subscriptions","organizations_url":"https://api.github.com/users/McSinyx/orgs","repos_url":"https://api.github.com/users/McSinyx/repos","events_url":"https://api.github.com/users/McSinyx/events{/privacy}","received_events_url":"https://api.github.com/users/McSinyx/received_events","type":"User","site_admin":false},"labels":[{"id":923362382,"node_id":"MDU6TGFiZWw5MjMzNjIzODI=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nodejs","name":"6.topic: nodejs","color":"fef2c0","default":false,"description":""},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-26T08:39:47Z","updated_at":"2022-01-29T23:16:16Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Project description\r\n\r\nHighlight.js is a syntax highlighter written in JavaScript. It works in the browser as well as on the server. It can work with pretty much any markup, doesn’t depend on any other frameworks, and has automatic language detection.\r\n\r\n### Metadata\r\n\r\n* Homepage URL: https://highlightjs.readthedocs.io\r\n* Source URL: (npm)\r\n* License: BSD 3-Clause\r\n* Platforms: any\r\n\r\nI tried to add it myself but on my (poor) connection after 4 hours `pkgs/development/node-packages/generate.sh` still hasn't finished, so it would be rather difficult for me to keep up with conflicts etc.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152201/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152161","id":1088676669,"node_id":"I_kwDOAEVQ_M5A4-M9","number":152161,"title":"insync-v3 server doesn't seem to start","user":{"login":"ajmasia","id":23419327,"node_id":"MDQ6VXNlcjIzNDE5MzI3","avatar_url":"https://avatars.githubusercontent.com/u/23419327?v=4","gravatar_id":"","url":"https://api.github.com/users/ajmasia","html_url":"https://github.com/ajmasia","followers_url":"https://api.github.com/users/ajmasia/followers","following_url":"https://api.github.com/users/ajmasia/following{/other_user}","gists_url":"https://api.github.com/users/ajmasia/gists{/gist_id}","starred_url":"https://api.github.com/users/ajmasia/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ajmasia/subscriptions","organizations_url":"https://api.github.com/users/ajmasia/orgs","repos_url":"https://api.github.com/users/ajmasia/repos","events_url":"https://api.github.com/users/ajmasia/events{/privacy}","received_events_url":"https://api.github.com/users/ajmasia/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-26T00:41:36Z","updated_at":"2022-01-16T09:25:40Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nI've installed insync-v3 and when run `insync start && insync show`, I get this message `Insync doesn't seem to be running. Start it first`\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `insync start`\r\n2. `insync show`\r\n\r\nMy sytem config:\r\n\r\n```bash\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(ajmasia): `\"nixpkgs-unstable-22.05pre339357.3e4c1337b93\"`\r\n - channels(root): `\"nixos-21.11.334247.573095944e7\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n ```\r\n### Notify maintainers\r\n@siraben @benley ","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152161/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152155","id":1088668703,"node_id":"I_kwDOAEVQ_M5A48Qf","number":152155,"title":"Feature Request: boot.loader.systemd-boot.mirroredBoots","user":{"login":"aidalgol","id":2313201,"node_id":"MDQ6VXNlcjIzMTMyMDE=","avatar_url":"https://avatars.githubusercontent.com/u/2313201?v=4","gravatar_id":"","url":"https://api.github.com/users/aidalgol","html_url":"https://github.com/aidalgol","followers_url":"https://api.github.com/users/aidalgol/followers","following_url":"https://api.github.com/users/aidalgol/following{/other_user}","gists_url":"https://api.github.com/users/aidalgol/gists{/gist_id}","starred_url":"https://api.github.com/users/aidalgol/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/aidalgol/subscriptions","organizations_url":"https://api.github.com/users/aidalgol/orgs","repos_url":"https://api.github.com/users/aidalgol/repos","events_url":"https://api.github.com/users/aidalgol/events{/privacy}","received_events_url":"https://api.github.com/users/aidalgol/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-25T23:26:58Z","updated_at":"2021-12-26T17:40:55Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"I am installing NixOS on ZFS mirror pool (with two disks), with an EFI partition on each disk.\r\n```\r\nNumber Start End Size File system Name Flags\r\n 3 1049kB 537MB 536MB fat32 ESP boot, esp\r\n 1 537MB 45.1GB 44.6GB primary\r\n 2 45.1GB 53.7GB 8589MB linux-swap(v1) primary swap\r\n```\r\nWith GRUB, I could use the `boot.loader.grub.mirroredBoots` option, but I would prefer to use `systemd-boot`, so I am manually syncing the EFI partition on disk 1 to disk 2 after making changes. It would be nice to have an equivalent to this option for `systemd-boot`.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152155/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152109","id":1088624635,"node_id":"I_kwDOAEVQ_M5A4xf7","number":152109,"title":"allow for defininig libvirt vms","user":{"login":"cherusk","id":10729954,"node_id":"MDQ6VXNlcjEwNzI5OTU0","avatar_url":"https://avatars.githubusercontent.com/u/10729954?v=4","gravatar_id":"","url":"https://api.github.com/users/cherusk","html_url":"https://github.com/cherusk","followers_url":"https://api.github.com/users/cherusk/followers","following_url":"https://api.github.com/users/cherusk/following{/other_user}","gists_url":"https://api.github.com/users/cherusk/gists{/gist_id}","starred_url":"https://api.github.com/users/cherusk/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cherusk/subscriptions","organizations_url":"https://api.github.com/users/cherusk/orgs","repos_url":"https://api.github.com/users/cherusk/repos","events_url":"https://api.github.com/users/cherusk/events{/privacy}","received_events_url":"https://api.github.com/users/cherusk/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null},{"id":1192878136,"node_id":"MDU6TGFiZWwxMTkyODc4MTM2","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.%20topic:%20nixos-container","name":"6. topic: nixos-container","color":"fef2c0","default":false,"description":"Imperative and declarative systemd-nspawn containers"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-25T16:24:54Z","updated_at":"2022-02-02T07:39:30Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nNixpkgs has already https://github.com/NixOS/nixpkgs/blob/master/nixos/modules/virtualisation/qemu-vm.nix\r\nand also there is the https://www.mankier.com/8/nixos-build-vms# nixos-build-vms tool.\r\n\r\nYet, wouldn't it be great to allow for defining libvirt vms as done for oci-containers or qemu-vms or other virtualisation technologies? Is there are reason around why it's not done?\r\n\r\n* platforms: unix, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152109/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152103","id":1088619170,"node_id":"I_kwDOAEVQ_M5A4wKi","number":152103,"title":"sw_vers on the host and sw_vers from `darwin.DarwinTools` return different results when run on `macos-11`","user":{"login":"cpcloud","id":417981,"node_id":"MDQ6VXNlcjQxNzk4MQ==","avatar_url":"https://avatars.githubusercontent.com/u/417981?v=4","gravatar_id":"","url":"https://api.github.com/users/cpcloud","html_url":"https://github.com/cpcloud","followers_url":"https://api.github.com/users/cpcloud/followers","following_url":"https://api.github.com/users/cpcloud/following{/other_user}","gists_url":"https://api.github.com/users/cpcloud/gists{/gist_id}","starred_url":"https://api.github.com/users/cpcloud/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cpcloud/subscriptions","organizations_url":"https://api.github.com/users/cpcloud/orgs","repos_url":"https://api.github.com/users/cpcloud/repos","events_url":"https://api.github.com/users/cpcloud/events{/privacy}","received_events_url":"https://api.github.com/users/cpcloud/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-25T15:37:08Z","updated_at":"2021-12-30T11:34:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Run `/usr/bin/sw_vers`\r\n2. Run `nix shell -f '<nixpkgs>' darwin.DarwinTools -c sw_vers\r\n\r\n### Expected behavior\r\n\r\nI expect the output of these two commands to be the same if running on the same host\r\n\r\n### Screenshots\r\n\r\nhttps://github.com/cpcloud/numbsql/runs/4632305086?check_suite_focus=true#step:5:11\r\n\r\nis a CI run where both results are printed out\r\n\r\n\r\n\r\n### Notify maintainers\r\n@matthewbauer\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 10.16`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/store/80lb3j2qn31cxnyazikmvlb39vkp7k21-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152103/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152060","id":1088544238,"node_id":"I_kwDOAEVQ_M5A4d3u","number":152060,"title":"OpenCL error with mesa","user":{"login":"kotatsuyaki","id":17219127,"node_id":"MDQ6VXNlcjE3MjE5MTI3","avatar_url":"https://avatars.githubusercontent.com/u/17219127?v=4","gravatar_id":"","url":"https://api.github.com/users/kotatsuyaki","html_url":"https://github.com/kotatsuyaki","followers_url":"https://api.github.com/users/kotatsuyaki/followers","following_url":"https://api.github.com/users/kotatsuyaki/following{/other_user}","gists_url":"https://api.github.com/users/kotatsuyaki/gists{/gist_id}","starred_url":"https://api.github.com/users/kotatsuyaki/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kotatsuyaki/subscriptions","organizations_url":"https://api.github.com/users/kotatsuyaki/orgs","repos_url":"https://api.github.com/users/kotatsuyaki/repos","events_url":"https://api.github.com/users/kotatsuyaki/events{/privacy}","received_events_url":"https://api.github.com/users/kotatsuyaki/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-25T04:33:11Z","updated_at":"2021-12-25T04:38:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI got this error message when running `clinfo`, as well as OpenCL hello-world programs with mesa (restored in #136402), and it fails to compile OpenCL kernels.\r\n\r\n```\r\n<built-in>:1:10: fatal error: 'clc/clc.h' file not found\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable OpenCL by setting `hardware.opengl.extraPackages = [ pkgs.mesa.opencl ];`.\r\n2. Run `clinfo`. The error message shows up.\r\n\r\n### Expected behavior\r\nThe error shoudn't be shown, and compiling OpenCL kernels should work.\r\n\r\n### Additional context\r\nIt seems that it tried to find that file, but the path is ill-formatted. See the repeated path `/nix/store/d902ifqzwfld7mjw3vxgy08l87055whr-libclc-11.0.1//nix/store/d902ifqzwfld7mjw3vxgy08l87055whr-libclc-11.0.1/include` in the strace below.\r\n\r\n<details>\r\n <summary>strace output</summary>\r\n\r\n```\r\n$ strace ./hello 2>&1 | rg clc\r\nnewfstatat(AT_FDCWD, \"/nix/store/d902ifqzwfld7mjw3vxgy08l87055whr-libclc-11.0.1//nix/store/d902ifqzwfld7mjw3vxgy08l87055whr-libclc-11.0.1/include\", 0x7ffe2a5cf060, 0) = -1 ENOENT (No such file or directory)\r\nopenat(AT_FDCWD, \"/nix/store/d902ifqzwfld7mjw3vxgy08l87055whr-libclc-11.0.1/share/clc/polaris10-amdgcn-mesa-mesa3d.bc\", O_RDONLY|O_CLOEXEC) = 8\r\nnewfstatat(AT_FDCWD, \"./clc\", 0x7ffe2a5cde50, 0) = -1 ENOENT (No such file or directory)\r\nwrite(2, \"<built-in>:1:10: fatal error: 'c\"..., 57<built-in>:1:10: fatal error: 'clc/clc.h' file not found\r\n```\r\n</details>\r\n\r\nThe path is hardcoded in `libMesaOpenCL.so.1`.\r\n\r\n<details>\r\n <summary>xxd output</summary>\r\n\r\n```\r\n$ xxd -d /run/opengl-driver/lib/libMesaOpenCL.so.1 | rg libclc-11 -C 8\r\n31535136: 6c69 622f 6c69 622f 636c 616e 672f 3133 lib/lib/clang/13\r\n31535152: 2e30 2e30 2f69 6e63 6c75 6465 0000 0000 .0.0/include....\r\n31535168: 2f6e 6978 2f73 746f 7265 2f64 3930 3269 /nix/store/d902i\r\n31535184: 6671 7a77 666c 6437 6d6a 7733 7678 6779 fqzwfld7mjw3vxgy\r\n31535200: 3038 6c38 3730 3535 7768 722d 6c69 6263 08l87055whr-libc\r\n31535216: 6c63 2d31 312e 302e 312f 2f6e 6978 2f73 lc-11.0.1//nix/s\r\n31535232: 746f 7265 2f64 3930 3269 6671 7a77 666c tore/d902ifqzwfl\r\n31535248: 6437 6d6a 7733 7678 6779 3038 6c38 3730 d7mjw3vxgy08l870\r\n31535264: 3535 7768 722d 6c69 6263 6c63 2d31 312e 55whr-libclc-11.\r\n31535280: 302e 312f 696e 636c 7564 652f 0000 0000 0.1/include/....\r\n31535296: 636c 5f63 6c61 6e67 5f73 746f 7261 6765 cl_clang_storage\r\n31535312: 5f63 6c61 7373 5f73 7065 6369 6669 6572 _class_specifier\r\n31535328: 7300 0000 0000 0000 2f6e 6978 2f73 746f s......./nix/sto\r\n31535344: 7265 2f64 3930 3269 6671 7a77 666c 6437 re/d902ifqzwfld7\r\n31535360: 6d6a 7733 7678 6779 3038 6c38 3730 3535 mjw3vxgy08l87055\r\n31535376: 7768 722d 6c69 6263 6c63 2d31 312e 302e whr-libclc-11.0.\r\n31535392: 312f 7368 6172 652f 636c 632f 006b 6572 1/share/clc/.ker\r\n31535408: 6e65 6c5f 6172 675f 7479 7065 002e 6c6c nel_arg_type..ll\r\n31535424: 002e 6173 6d00 0000 0000 0000 0000 0000 ..asm...........\r\n31535440: 5374 3139 5f53 705f 6d61 6b65 5f73 6861 St19_Sp_make_sha\r\n31535456: 7265 645f 7461 6700 0000 0000 0000 0000 red_tag.........\r\n31535472: 0000 0000 0000 0000 0000 0000 0000 0000 ................\r\n31535488: 2a5a 4e31 325f 474c 4f42 414c 5f5f 4e5f *ZN12_GLOBAL__N_\r\n31535504: 3138 6f70 7469 6d69 7a65 4552 4e34 6c6c 18optimizeERN4ll\r\n```\r\n</details>\r\n\r\nThe wrong include directory is the `LIBCLC_INCLUDEDIR` [added by clover here](https://gitlab.freedesktop.org/mesa/mesa/-/blob/main/src/gallium/frontends/clover/llvm/invocation.cpp#L297), which is generated by [this meson script](https://gitlab.freedesktop.org/mesa/mesa/-/blob/main/src/gallium/frontends/clover/meson.build#L30). I'm not knowledgeable enough to fix it, but I think this is close to the root of the problem.\r\n\r\n### Notify maintainers\r\n@primeos @vcunat \r\n\r\n### Metadata\r\nI'm using flakes on nixos-21.11. The command `nix-shell -p nix-info --run \"nix-info -m\"` fails so it's not included.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152060/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056/events","html_url":"https://github.com/NixOS/nixpkgs/issues/152056","id":1088540563,"node_id":"I_kwDOAEVQ_M5A4c-T","number":152056,"title":"`jemalloc` build fails on aarch64-darwin","user":{"login":"samuela","id":226872,"node_id":"MDQ6VXNlcjIyNjg3Mg==","avatar_url":"https://avatars.githubusercontent.com/u/226872?v=4","gravatar_id":"","url":"https://api.github.com/users/samuela","html_url":"https://github.com/samuela","followers_url":"https://api.github.com/users/samuela/followers","following_url":"https://api.github.com/users/samuela/following{/other_user}","gists_url":"https://api.github.com/users/samuela/gists{/gist_id}","starred_url":"https://api.github.com/users/samuela/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/samuela/subscriptions","organizations_url":"https://api.github.com/users/samuela/orgs","repos_url":"https://api.github.com/users/samuela/repos","events_url":"https://api.github.com/users/samuela/events{/privacy}","received_events_url":"https://api.github.com/users/samuela/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2021-12-25T03:52:10Z","updated_at":"2021-12-30T17:49:33Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n`python3Packages.tensorflow` does not build aarch64-darwin as of eac07edbd20ed4908b98790ba299250b5527ecdf.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Check out eac07edbd20ed4908b98790ba299250b5527ecdf.\r\n2. `nix-build -A python3Packages.tensorflow` on aarch64-darwin\r\n\r\n### Expected behavior\r\nThe build to succeed or the package to be marked as broken.\r\n\r\n### Screenshots\r\nn/a\r\n\r\n### Additional context\r\nFull build log: https://gist.github.com/samuela/42e5da41bb7a2e32842bd3de3777fced\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@jyp @abbradar @ndl @veprbl @danieldk @timokau \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(samuelainsworth): `\"darwin, home-manager, nixpkgs-21.11pre330734.5cb226a06c4\"`\r\n - channels(root): `\"nixpkgs-21.11pre330734.5cb226a06c4\"`\r\n - nixpkgs: `/Users/samuelainsworth/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/152056/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151994","id":1088290843,"node_id":"I_kwDOAEVQ_M5A3gAb","number":151994,"title":"ethminer-free no longer works with rocm","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2021-12-24T10:08:52Z","updated_at":"2021-12-24T13:58:54Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nCaused by https://github.com/NixOS/nixpkgs/pull/150767\r\n\r\nNot sure whether this is an upstream issue or ours.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix-shell -p ethminer-free --command 'ethminer --list-devices'`\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n@Flakebi","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151994/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151978","id":1088210806,"node_id":"I_kwDOAEVQ_M5A3Md2","number":151978,"title":"fish shell: can't cross-compile","user":{"login":"rembo10","id":801525,"node_id":"MDQ6VXNlcjgwMTUyNQ==","avatar_url":"https://avatars.githubusercontent.com/u/801525?v=4","gravatar_id":"","url":"https://api.github.com/users/rembo10","html_url":"https://github.com/rembo10","followers_url":"https://api.github.com/users/rembo10/followers","following_url":"https://api.github.com/users/rembo10/following{/other_user}","gists_url":"https://api.github.com/users/rembo10/gists{/gist_id}","starred_url":"https://api.github.com/users/rembo10/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/rembo10/subscriptions","organizations_url":"https://api.github.com/users/rembo10/orgs","repos_url":"https://api.github.com/users/rembo10/repos","events_url":"https://api.github.com/users/rembo10/events{/privacy}","received_events_url":"https://api.github.com/users/rembo10/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-24T07:33:07Z","updated_at":"2021-12-28T02:36:43Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nTrying to cross compile fish for armv7l-linux on x86_64-linux, I was running into an error where cmake was trying to use the host platform's uname (and gettext), instead of the build platform's versions. Checking the env-vars in the failed build directory, I saw that CMAKE_PREFIX_PATH was populated with all of the host platform's dependencies. From the [cmake docs:](https://cmake.org/cmake/help/latest/variable/CMAKE_PREFIX_PATH.html), the CMAKE_PREFIX_PATH is a:\r\n\r\n```\r\nSemicolon-separated list of directories specifying installation prefixes to be searched by the find_package(),\r\nfind_program(), find_library(), find_file(), and find_path() commands. Each command will add appropriate\r\nsubdirectories (like bin, lib, or include) as specified in its own documentation.\r\n```\r\n\r\nCommenting out the addCMakeParams() in the cmake [setup-hook.sh](https://github.com/NixOS/nixpkgs/blob/ab93217a2b74a1c36bc892c14f44ee5959c33f12/pkgs/development/tools/build-managers/cmake/setup-hook.sh#L2) fixes the issue, and all my other cmake dependencies seem to build fine (EDIT: other packages, e.g. aws-c-cal failed to build), but I'm not sure if this is the optimal solution, it's just something that happened to work.\r\n\r\nIt's a little above my pay grade and I don't really feel comfortable messing with something that might affect so many packages, so maybe someone can take a look? \r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix build nixpkgs#pkgsCross.armv7l-hf-multiplatform.fish\r\n(although maybe it's better to try with another cmake package since fish seems to bring in a whole nixos system? EDIT: although I made a [patch to fix that](https://github.com/NixOS/nixpkgs/pull/152025))\r\n\r\n### Expected behavior\r\ncmake should use the build host's binaries when building\r\n\r\n### Additional context\r\nI was able to cross compile fish on my machine at one point, but when I tried to build it in github actions, it was failing. I set sandbox = true in my nix.conf, and then I started getting the error on my machine as well (although now even with that setting disabled it still happens?)\r\n\r\nI saw this in the failed build dir's CMakeSystem.cmake:\r\n```\r\nset(CMAKE_HOST_SYSTEM \"Linux-/nix/store/gngmkdfmqz7plxckwdj3n5gyyai4nsqn-coreutils-armv7l-unknown-linux-gnueabihf-9.0/bin/uname: line 1: syntax error: unexpected word (expecting \")\")\")\r\nset(CMAKE_HOST_SYSTEM_NAME \"Linux\")\r\nset(CMAKE_HOST_SYSTEM_VERSION \"/nix/store/gngmkdfmqz7plxckwdj3n5gyyai4nsqn-coreutils-armv7l-unknown-linux-gnueabihf-9.0/bin/uname: line 1: syntax error: unexpected word (expecting \")\")\")\r\nset(CMAKE_HOST_SYSTEM_PROCESSOR \"unknown\")\r\n```\r\n\r\n\r\n### Notify maintainers\r\n@ttuegel @LnL7\r\n\r\n### Metadata\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151978/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151916","id":1088010867,"node_id":"I_kwDOAEVQ_M5A2bpz","number":151916,"title":"Singularity install (non-nixOS) fails to run example container","user":{"login":"cfhammill","id":7467038,"node_id":"MDQ6VXNlcjc0NjcwMzg=","avatar_url":"https://avatars.githubusercontent.com/u/7467038?v=4","gravatar_id":"","url":"https://api.github.com/users/cfhammill","html_url":"https://github.com/cfhammill","followers_url":"https://api.github.com/users/cfhammill/followers","following_url":"https://api.github.com/users/cfhammill/following{/other_user}","gists_url":"https://api.github.com/users/cfhammill/gists{/gist_id}","starred_url":"https://api.github.com/users/cfhammill/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/cfhammill/subscriptions","organizations_url":"https://api.github.com/users/cfhammill/orgs","repos_url":"https://api.github.com/users/cfhammill/repos","events_url":"https://api.github.com/users/cfhammill/events{/privacy}","received_events_url":"https://api.github.com/users/cfhammill/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":256301533,"node_id":"MDU6TGFiZWwyNTYzMDE1MzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20non-nixos","name":"6.topic: non-nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-23T21:56:15Z","updated_at":"2022-01-06T05:18:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI successfully installed singularity on a non-nixOS linux system, then I went to try a demonstration container, a small alpine linux container\r\n\r\nhttps://cloud.sylabs.io/library/_container/5baba5e594feb900016ea41c\r\n\r\nI tried to open the container with \r\n\r\n```\r\nsingularity run alpine-container bash\r\n```\r\n\r\nbut failed to run the container, citing conflicting glibc versions\r\n\r\n```\r\nsingularity run alpine-container bash\r\nINFO: Converting SIF file to temporary sandbox...\r\nFATAL: while extracting alpine-container: root filesystem extraction failed: extract command failed: /nix/store/10lpzbif47sl14z6cjr5mn7vq1w5c9p4-singularity-3.8.5/bin/singularity: /lib/x86_64\r\n-linux-gnu/libc.so.6: version `GLIBC_2.33' not found (required by /nix/store/10lpzbif47sl14z6cjr5mn7vq1w5c9p4-singularity-3.8.5/bin/singularity)\r\n/nix/store/10lpzbif47sl14z6cjr5mn7vq1w5c9p4-singularity-3.8.5/bin/singularity: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.32' not found (required by /nix/store/10lpzbif47sl14z6cjr5mn7vq1\r\nw5c9p4-singularity-3.8.5/bin/singularity)\r\n: exit status 1\r\n```\r\n\r\nI tried to fix with `LD_PRELOAD`, but that can only fix one of the two versions, for some reason it appears to require both GLIBC_2.33 and 2.32.\r\n\r\n### Steps To Reproduce\r\n1. Be on a non-nixOS system\r\n1. Download the container from sylabs cloud (I did manually for some networking reasons)\r\nhttps://cloud.sylabs.io/library/_container/5baba5e594feb900016ea41c and named it alpine-container\r\n1. nix-shell -p singularity\r\n1. singularity run alpine-container bash\r\n\r\n\r\n### Expected behavior\r\n\r\nShould start a shell inside the container\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n\r\n@jbedo (hi!)\r\n\r\n### Metadata\r\n\r\n```console\r\nnix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 4.15.0-117-generic, Ubuntu, 18.04.5 LTS (Bionic Beaver)`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(chris): `\"nixpkgs-22.05pre340162.0c408a087b4\"`\r\n - nixpkgs: `/home/chris/.nix-defexpr/channels/nixpkgs`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151916/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151908","id":1087979061,"node_id":"I_kwDOAEVQ_M5A2T41","number":151908,"title":"`bazel_4` incorrect arch set for aarch64-darwin","user":{"login":"jacobfoard","id":13523222,"node_id":"MDQ6VXNlcjEzNTIzMjIy","avatar_url":"https://avatars.githubusercontent.com/u/13523222?v=4","gravatar_id":"","url":"https://api.github.com/users/jacobfoard","html_url":"https://github.com/jacobfoard","followers_url":"https://api.github.com/users/jacobfoard/followers","following_url":"https://api.github.com/users/jacobfoard/following{/other_user}","gists_url":"https://api.github.com/users/jacobfoard/gists{/gist_id}","starred_url":"https://api.github.com/users/jacobfoard/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jacobfoard/subscriptions","organizations_url":"https://api.github.com/users/jacobfoard/orgs","repos_url":"https://api.github.com/users/jacobfoard/repos","events_url":"https://api.github.com/users/jacobfoard/events{/privacy}","received_events_url":"https://api.github.com/users/jacobfoard/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-23T20:35:39Z","updated_at":"2022-03-14T18:06:48Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nWhen using a `.bazelversion` file with the current `bazel_4`, you get a message like: \r\n```\r\nbazel build //...\r\nERROR: The project you're trying to build requires Bazel 4.2.1 (specified in /local/project/path/.bazelversion), but it wasn't found in /nix/store/lh5cn9cmqvj6iry3i4k02vi5vyvcy58w-bazel-4.2.2/bin.\r\n\r\nBazel binaries for all official releases can be downloaded from here:\r\n https://github.com/bazelbuild/bazel/releases\r\n\r\nPlease put the downloaded Bazel binary into this location:\r\n /nix/store/lh5cn9cmqvj6iry3i4k02vi5vyvcy58w-bazel-4.2.2/bin/bazel-4.2.1-darwin-arm64\r\n```\r\n\r\na quick `ls` in that store path shows that the bin is suffixed with `aarch64` instead of `arm64`\r\n\r\n```\r\n /bin/ls -l /nix/store/lh5cn9cmqvj6iry3i4k02vi5vyvcy58w-bazel-4.2.2/bin/\r\ntotal 62776\r\n-r-xr-xr-x 1 root nixbld 8734 Dec 31 1969 bazel\r\n-r-xr-xr-x 1 root nixbld 32123374 Dec 31 1969 bazel-4.2.2-darwin-aarch64\r\n-r-xr-xr-x 1 root nixbld 240 Dec 31 1969 bazel-execlog\r\n```\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Add a `.bazelversion` file to an existing bazel project\r\n2. Attempt to use `bazel_4` \r\n\r\n### Expected behavior\r\nBuild should work and continue forward without error\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nOnce I remove the `.bazelversion` file, it works fine. \r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n @NixOS/bazel\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - nixpkgs: `/nix/store/2l43ycb2hl1pv05bifdvjf352x0g6sg8-lgfhg4n6445yizgf0xjirb4bc4j86fr9-source`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151908/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151874","id":1087537953,"node_id":"I_kwDOAEVQ_M5A0oMh","number":151874,"title":"qt-5 should not depend on llvmPackages_5 (?)","user":{"login":"dnadlinger","id":19335,"node_id":"MDQ6VXNlcjE5MzM1","avatar_url":"https://avatars.githubusercontent.com/u/19335?v=4","gravatar_id":"","url":"https://api.github.com/users/dnadlinger","html_url":"https://github.com/dnadlinger","followers_url":"https://api.github.com/users/dnadlinger/followers","following_url":"https://api.github.com/users/dnadlinger/following{/other_user}","gists_url":"https://api.github.com/users/dnadlinger/gists{/gist_id}","starred_url":"https://api.github.com/users/dnadlinger/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/dnadlinger/subscriptions","organizations_url":"https://api.github.com/users/dnadlinger/orgs","repos_url":"https://api.github.com/users/dnadlinger/repos","events_url":"https://api.github.com/users/dnadlinger/events{/privacy}","received_events_url":"https://api.github.com/users/dnadlinger/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":137715073,"node_id":"MDU6TGFiZWwxMzc3MTUwNzM=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20qt/kde","name":"6.topic: qt/kde","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-23T09:33:14Z","updated_at":"2021-12-23T19:25:53Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe Qt 5 derivations depend specifically on LLVM 5.0 when the stdenv cc is Clang:\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/41513de1fd8947ef9ad6af465a20b564dc84b6f0/pkgs/development/libraries/qt-5/5.15/default.nix#L28\r\n\r\nThis is an ancient version, which is the first hard blocker for Qt on aarch64-darwin, where compiler-rt from that version doesn't build.\r\n\r\nIs there a reason for requiring this old version?\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. `nix --system aarch64-darwin nixpkgs#qt515.qtsvg\r\n2. Note broken package warning for compiler-rt from llvmPackages_5.\r\n\r\n### Expected behavior\r\nI'm not sure why that `stdenvActual` sleight is necessary, but presumably, this should at least be `llvmPackages.stdenv`, such that `llvmPackages_11` is used on aarch64?\r\n\r\nI've had a quick go at building a patched Qt 5.15 for aarch64, and while there are some fundamental toolchain issues to sort out still (even with the 5.15 aarch64 patch from Homebrew), sorting out the dependencies is at least a first step.\r\n\r\nMarking Qt 5 itself as broken would also give much more intelligible error messages than compiler-rt-5 somewhere deep in the dependency tree of a project.\r\n\r\n### Notify maintainers\r\n@qknight @ttuegel @periklis @bkchr @veprbl\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(dpn): `\"\"`\r\n - channels(root): `\"nixpkgs-22.05pre338661.3c52ea8c921\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151874/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151841","id":1087224872,"node_id":"I_kwDOAEVQ_M5Azbwo","number":151841,"title":"`vifm` help page is broken","user":{"login":"ambroisie","id":12465195,"node_id":"MDQ6VXNlcjEyNDY1MTk1","avatar_url":"https://avatars.githubusercontent.com/u/12465195?v=4","gravatar_id":"","url":"https://api.github.com/users/ambroisie","html_url":"https://github.com/ambroisie","followers_url":"https://api.github.com/users/ambroisie/followers","following_url":"https://api.github.com/users/ambroisie/following{/other_user}","gists_url":"https://api.github.com/users/ambroisie/gists{/gist_id}","starred_url":"https://api.github.com/users/ambroisie/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ambroisie/subscriptions","organizations_url":"https://api.github.com/users/ambroisie/orgs","repos_url":"https://api.github.com/users/ambroisie/repos","events_url":"https://api.github.com/users/ambroisie/events{/privacy}","received_events_url":"https://api.github.com/users/ambroisie/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-22T22:14:34Z","updated_at":"2022-02-11T15:09:12Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nTyping `:help` in `vifm` (with `vim` or `neovim` installed) leads to the following error in `vim`:\r\n\r\n```\r\nError detected while processing command line: \r\nE149: Sorry, no help for vifm-app.txt \r\n```\r\n\r\n### Steps To Reproduce\r\n1. Add `vifm` or `vifm-full` to your system packages\r\n2. Add `vim` or `neovim` to your system packages\r\n3. Open `vifm`\r\n4. Type `:help`\r\n\r\n### Expected behavior\r\n\r\nI would expect the documentation to be readable.\r\n\r\n### Screenshots\r\nIf applicable, add screenshots to help explain your problem.\r\n\r\n### Additional context\r\nAdd any other context about the problem here.\r\n\r\n### Notify maintainers\r\n@7c6f434c \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.81, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-21.11pre293089.1c2986bbb80\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841/reactions","total_count":1,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":1},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151841/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151816","id":1087128954,"node_id":"I_kwDOAEVQ_M5AzEV6","number":151816,"title":"XQuartz does not display anything on screen","user":{"login":"ayushkarnawat","id":12387834,"node_id":"MDQ6VXNlcjEyMzg3ODM0","avatar_url":"https://avatars.githubusercontent.com/u/12387834?v=4","gravatar_id":"","url":"https://api.github.com/users/ayushkarnawat","html_url":"https://github.com/ayushkarnawat","followers_url":"https://api.github.com/users/ayushkarnawat/followers","following_url":"https://api.github.com/users/ayushkarnawat/following{/other_user}","gists_url":"https://api.github.com/users/ayushkarnawat/gists{/gist_id}","starred_url":"https://api.github.com/users/ayushkarnawat/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/ayushkarnawat/subscriptions","organizations_url":"https://api.github.com/users/ayushkarnawat/orgs","repos_url":"https://api.github.com/users/ayushkarnawat/repos","events_url":"https://api.github.com/users/ayushkarnawat/events{/privacy}","received_events_url":"https://api.github.com/users/ayushkarnawat/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-22T19:35:18Z","updated_at":"2022-02-02T13:47:11Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n<!-- A clear and concise description of what the bug is. -->\r\n\r\nWhen attempting to run any GUI application that depends on X11/XQuartz, the X11 server seem to startup, but no graphics are displayed locally. Running just the XQuartz binary (via the commandline `XQuartz`), results in the XQuartz app opening, but then immediately crashing with an error message \"Failed to activate core devices.\"\r\n\r\n<!--\r\nAttempting to change the `DISPLAY` environment variable to `:0` or `localhost:0`\r\nor `localhost:0.0` results a `Error: Can't open display: localhost:0`.\r\n-->\r\n\r\n### Steps To Reproduce\r\n<!-- Steps to reproduce the behavior: -->\r\n\r\n1. Create and activate a `nix-shell` environment with a (relatively new) version of nixpkgs:\r\n\r\n```nix\r\n# shell.nix\r\n{ nixpkgs ? import (\r\n fetchTarball {\r\n name = \"nixpkgs-21.08\";\r\n url = \"https://github.com/nixos/nixpkgs/archive/\" +\r\n \"fbafeb7ad5dd6196fcc5d84264e1706653a62f81.tar.gz\";\r\n sha256 = \"1kvx8j1z0xwfqjh33l3plhjc6dkjdg5md6zg667abdi06sg9w8pk\";\r\n }) {}\r\n}:\r\n\r\nwith nixpkgs;\r\n\r\nmkShell {\r\n buildInputs = [\r\n llvmPackages_12.clang\r\n xorg.xeyes\r\n xquartz # for darwin only\r\n ];\r\n # Automate process of extracting correct paths to binaries. This (somewhat)\r\n # hacky approach works despite the fact that there might be multiple different\r\n # versions of the pkg of interest, as each version has its own unique hash.\r\n shellHook = ''\r\n clang_dir=$(ls -l /nix/store/ | grep ${llvmPackages_12.clang.pname + \"-\" +\r\n llvmPackages_12.clang.version} | grep '^d' | awk '/ / {print $NF}')\r\n export PATH=\"/nix/store/$clang_dir/bin:$PATH\"\r\n '';\r\n}\r\n```\r\n\r\n2. Run `xquartz-install` to install xquartz as per the [instructions](https://github.com/NixOS/nixpkgs/blob/dd2d0191a046bc79f36d3682e8532e0e729608d1/pkgs/servers/x11/xquartz/default.nix)\r\n\r\n3. Ensure that the DISPLAY environment variable is now set (note: you may need to logout for it to be set).\r\n\r\n```console\r\n$ echo $DISPLAY\r\n/private/tmp/com.apple.launchd.pahMNJkiNX/org.nixos.xquartz:0\r\n```\r\n\r\n4. Run `xeyes` from the command line. The process hangs here, and no graphics are displayed.\r\n\r\n### Expected behavior\r\n<!-- A clear and concise description of what you expected to happen. -->\r\nThe application runs without error and displays the requested objects in a new Window on screen.\r\n\r\n### Screenshots\r\n<!-- If applicable, add screenshots to help explain your problem. -->\r\nN.A., but can attach if it helps.\r\n\r\n### Additional context\r\n\r\nNOTE: This pertains to and tested on darwin-based systems. Attempting to install/use XQuartz with `nix-env` results in the same problems. However, when using XQuartz downloaded via the disk installer `.dmg`, all applications work well, e.g. the graphics are displayed properly.\r\n\r\n### Notify maintainers\r\n\r\n@cstrahan\r\n\r\n### Metadata\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-darwin\"`\r\n - host os: `Darwin 20.6.0, macOS 10.16`\r\n - multi-user?: `no`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.8`\r\n - channels: `\"darwin-20.09pre246307.9b8530e3721, nixpkgs-21.03pre250093.0da76dab4c2\"`\r\n - nixpkgs: `$HOME/.nix-defexpr/channels/nixpkgs`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151816/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151803","id":1087076953,"node_id":"I_kwDOAEVQ_M5Ay3pZ","number":151803,"title":"meld on Mac M1 is broken.","user":{"login":"sequencer","id":5791019,"node_id":"MDQ6VXNlcjU3OTEwMTk=","avatar_url":"https://avatars.githubusercontent.com/u/5791019?v=4","gravatar_id":"","url":"https://api.github.com/users/sequencer","html_url":"https://github.com/sequencer","followers_url":"https://api.github.com/users/sequencer/followers","following_url":"https://api.github.com/users/sequencer/following{/other_user}","gists_url":"https://api.github.com/users/sequencer/gists{/gist_id}","starred_url":"https://api.github.com/users/sequencer/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/sequencer/subscriptions","organizations_url":"https://api.github.com/users/sequencer/orgs","repos_url":"https://api.github.com/users/sequencer/repos","events_url":"https://api.github.com/users/sequencer/events{/privacy}","received_events_url":"https://api.github.com/users/sequencer/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-22T18:27:45Z","updated_at":"2021-12-22T18:27:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nrun `meld` from zsh+tmux on M1 MacBook Air 16G, log below: \r\n```\r\n-------------------------------------\r\nTranslated Report (Full Report Below)\r\n-------------------------------------\r\n\r\nProcess: python3.9 [49102]\r\nPath: /Volumes/VOLUME/*/python3\r\nIdentifier: python3.9\r\nVersion: ???\r\nCode Type: ARM-64 (Native)\r\nParent Process: zsh [28956]\r\nResponsible: Alfred [4406]\r\nUser ID: 501\r\n\r\nDate/Time: 2021-12-23 02:23:33.1763 +0800\r\nOS Version: macOS 12.2 (21D5025f)\r\nReport Version: 12\r\nAnonymous UUID: BBEEA9DD-326D-6FE8-9435-4F6AFAEDE56B\r\n\r\nSleep/Wake UUID: BF3A4700-04FD-475B-BF5E-44EBE49410D8\r\n\r\nTime Awake Since Boot: 93000 seconds\r\nTime Since Wake: 48543 seconds\r\n\r\nSystem Integrity Protection: enabled\r\n\r\nCrashed Thread: 0 Dispatch queue: com.apple.main-thread\r\n\r\nException Type: EXC_BAD_ACCESS (SIGSEGV)\r\nException Codes: KERN_INVALID_ADDRESS at 0xa940421110fe0018 -> 0x0000421110fe0018 (possible pointer authentication failure)\r\nException Codes: 0x0000000000000001, 0xa940421110fe0018\r\nException Note: EXC_CORPSE_NOTIFY\r\n\r\nTermination Reason: Namespace SIGNAL, Code 11 Segmentation fault: 11\r\nTerminating Process: exc handler [49102]\r\n\r\nVM Region Info: 0x421110fe0018 is not in any region. Bytes after previous region: 72160030621721 Bytes before following region: 32912049307624\r\n REGION TYPE START - END [ VSIZE] PRT/MAX SHRMOD REGION DETAIL\r\n commpage (reserved) 1000000000-7000000000 [384.0G] ---/--- SM=NUL ...(unallocated)\r\n---> GAP OF 0x5f9000000000 BYTES\r\n MALLOC_NANO 600000000000-600008000000 [128.0M] rw-/rwx SM=PRV \r\n\r\nThread 0 Crashed:: Dispatch queue: com.apple.main-thread\r\n0 ??? \t 0x105ad2530 g_callable_info_free_closure + 20\r\n1 ??? \t 0x105a89924 _pygi_invoke_closure_free + 28\r\n2 ??? \t 0x105a89924 _pygi_invoke_closure_free + 28\r\n3 ??? \t 0x10a01bc8c gtk_combo_box_destroy + 100\r\n4 ??? \t 0x105b0d750 g_closure_invoke + 200\r\n5 ??? \t 0x105b238d0 signal_emit_unlocked_R + 2416\r\n6 ??? \t 0x105b24434 g_signal_emit_valist + 2548\r\n7 ??? \t 0x105b24748 g_signal_emit + 44\r\n8 ??? \t 0x10a279dd8 gtk_widget_dispose + 128\r\n9 ??? \t 0x105b12ef4 g_object_unref + 232\r\n10 ??? \t 0x10a098214 set_extra_widget + 72\r\n11 ??? \t 0x105b14a6c object_set_property + 316\r\n12 ??? \t 0x105b146b0 g_object_setv + 168\r\n13 ??? \t 0x105b154dc g_object_set_property + 48\r\n14 ??? \t 0x105b14a6c object_set_property + 316\r\n15 ??? \t 0x105b146b0 g_object_setv + 168\r\n16 ??? \t 0x105b154dc g_object_set_property + 48\r\n17 ??? \t 0x105a8adbc pygi_set_property_value + 984\r\n18 ??? \t 0x105a72580 PyGProps_setattro + 336\r\n19 ??? \t 0x105521e80 PyObject_SetAttr + 148\r\n20 ??? \t 0x1055ad348 _PyEval_EvalFrameDefault + 13492\r\n21 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n22 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n23 ??? \t 0x1054dd7c0 method_vectorcall + 396\r\n24 ??? \t 0x105a8b39c pygi_signal_closure_marshal + 860\r\n25 ??? \t 0x105b0d750 g_closure_invoke + 200\r\n26 ??? \t 0x105b236a8 signal_emit_unlocked_R + 1864\r\n27 ??? \t 0x105b24434 g_signal_emit_valist + 2548\r\n28 ??? \t 0x105b24748 g_signal_emit + 44\r\n29 ??? \t 0x105b17d48 g_object_dispatch_properties_changed + 80\r\n30 ??? \t 0x105b13838 g_object_notify_queue_thaw + 264\r\n31 ??? \t 0x105b146cc g_object_setv + 196\r\n32 ??? \t 0x105b154dc g_object_set_property + 48\r\n33 ??? \t 0x10a0872c4 gtk_file_chooser_button_set_property + 416\r\n34 ??? \t 0x105b14a6c object_set_property + 316\r\n35 ??? \t 0x105b14cfc g_object_set_valist + 392\r\n36 ??? \t 0x105b153c8 g_object_set + 76\r\n37 ??? \t 0x10a0870b0 gtk_file_chooser_button_constructed + 1428\r\n38 ??? \t 0x105b141c0 g_object_new_internal + 264\r\n39 ??? \t 0x105b14578 g_object_newv + 264\r\n40 ??? \t 0x109fd9718 _gtk_builder_construct + 676\r\n41 ??? \t 0x109fdfcb8 builder_construct + 92\r\n42 ??? \t 0x109fdf8c0 end_element + 1052\r\n43 ??? \t 0x105c2e3d0 emit_end_element + 244\r\n44 ??? \t 0x105c2dd00 g_markup_parse_context_parse + 5988\r\n45 ??? \t 0x109fde090 _gtk_builder_parser_parse_buffer + 248\r\n46 ??? \t 0x109fda934 gtk_builder_extend_with_template + 368\r\n47 ??? \t 0x10a2789f4 gtk_widget_init_template + 212\r\n48 ??? \t 0x105a3404c ffi_call_SYSV + 76\r\n49 ??? \t 0x105a318cc ffi_call_int + 1208\r\n50 ??? \t 0x105a8bd84 pygi_invoke_c_callable + 1984\r\n51 ??? \t 0x105a8cf00 pygi_function_cache_invoke + 68\r\n52 ??? \t 0x1054dacc0 _PyObject_MakeTpCall + 360\r\n53 ??? \t 0x1055b2490 call_function + 516\r\n54 ??? \t 0x1055afd3c _PyEval_EvalFrameDefault + 24232\r\n55 ??? \t 0x1054db534 function_code_fastcall + 116\r\n56 ??? \t 0x1055b242c call_function + 416\r\n57 ??? \t 0x1055afd3c _PyEval_EvalFrameDefault + 24232\r\n58 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n59 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n60 ??? \t 0x1054dd750 method_vectorcall + 284\r\n61 ??? \t 0x1054db994 _PyObject_CallFunctionVa + 136\r\n62 ??? \t 0x1054dc0fc _PyObject_CallMethod_SizeT + 112\r\n63 ??? \t 0x105a7ba10 pygobject__g_instance_init + 196\r\n64 ??? \t 0x105b2641c g_type_create_instance + 520\r\n65 ??? \t 0x105b14100 g_object_new_internal + 72\r\n66 ??? \t 0x105b13b2c g_object_new_with_properties + 352\r\n67 ??? \t 0x105a7844c pygobject_constructv + 80\r\n68 ??? \t 0x105a72240 pygobject_init + 292\r\n69 ??? \t 0x10553ea4c wrap_init + 20\r\n70 ??? \t 0x1054dacc0 _PyObject_MakeTpCall + 360\r\n71 ??? \t 0x1055b2490 call_function + 516\r\n72 ??? \t 0x1055afcc0 _PyEval_EvalFrameDefault + 24108\r\n73 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n74 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n75 ??? \t 0x1054daab0 _PyObject_FastCallDictTstate + 312\r\n76 ??? \t 0x1054db840 _PyObject_Call_Prepend + 148\r\n77 ??? \t 0x10553e960 slot_tp_init + 216\r\n78 ??? \t 0x105535774 type_call + 352\r\n79 ??? \t 0x1054dacc0 _PyObject_MakeTpCall + 360\r\n80 ??? \t 0x1055b2490 call_function + 516\r\n81 ??? \t 0x1055afd3c _PyEval_EvalFrameDefault + 24232\r\n82 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n83 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n84 ??? \t 0x1055b242c call_function + 416\r\n85 ??? \t 0x1055afc9c _PyEval_EvalFrameDefault + 24072\r\n86 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n87 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n88 ??? \t 0x105a894f0 _pygi_closure_handle + 816\r\n89 ??? \t 0x105a31d84 ffi_closure_SYSV_inner + 1040\r\n90 ??? \t 0x105a341d4 ffi_closure_SYSV + 52\r\n91 ??? \t 0x10617291c _g_cclosure_marshal_INT__OBJECTv + 120\r\n92 ??? \t 0x105b0d968 _g_closure_invoke_va + 212\r\n93 ??? \t 0x105b23e3c g_signal_emit_valist + 1020\r\n94 ??? \t 0x105b24748 g_signal_emit + 44\r\n95 ??? \t 0x1061cbb34 g_application_call_command_line + 124\r\n96 ??? \t 0x1061cd968 g_application_real_local_command_line + 1464\r\n97 ??? \t 0x1061cb878 g_application_run + 408\r\n98 ??? \t 0x105a3404c ffi_call_SYSV + 76\r\n99 ??? \t 0x105a318cc ffi_call_int + 1208\r\n100 ??? \t 0x105a8bd84 pygi_invoke_c_callable + 1984\r\n101 ??? \t 0x105a8cf00 pygi_function_cache_invoke + 68\r\n102 ??? \t 0x1054db2e0 _PyObject_Call + 172\r\n103 ??? \t 0x1055affb8 _PyEval_EvalFrameDefault + 24868\r\n104 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n105 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n106 ??? \t 0x1055b242c call_function + 416\r\n107 ??? \t 0x1055afc9c _PyEval_EvalFrameDefault + 24072\r\n108 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n109 ??? \t 0x1054db4b4 _PyFunction_Vectorcall + 256\r\n110 ??? \t 0x1055b242c call_function + 416\r\n111 ??? \t 0x1055afd3c _PyEval_EvalFrameDefault + 24232\r\n112 ??? \t 0x1054db534 function_code_fastcall + 116\r\n113 ??? \t 0x1055b242c call_function + 416\r\n114 ??? \t 0x1055afd3c _PyEval_EvalFrameDefault + 24232\r\n115 ??? \t 0x1055b3424 _PyEval_EvalCode + 3196\r\n116 ??? \t 0x1055a9dcc PyEval_EvalCode + 80\r\n117 ??? \t 0x1055f4204 pyrun_file + 304\r\n118 ??? \t 0x1055f211c PyRun_SimpleFileExFlags + 660\r\n119 ??? \t 0x10560fbd0 Py_RunMain + 1724\r\n120 ??? \t 0x1056100e0 pymain_main + 340\r\n121 ??? \t 0x10561016c Py_BytesMain + 56\r\n122 dyld \t 0x104fe10f4 start + 520\r\n\r\nThread 1:\r\n0 libsystem_pthread.dylib \t 0x197078010 start_wqthread + 0\r\n\r\nThread 2:\r\n0 libsystem_pthread.dylib \t 0x197078010 start_wqthread + 0\r\n\r\nThread 3:\r\n0 libsystem_pthread.dylib \t 0x197078010 start_wqthread + 0\r\n\r\nThread 4:: gmain\r\n0 libsystem_kernel.dylib \t 0x197049ad0 poll + 8\r\n1 ??? \t 0x105c291e8 g_main_context_iterate + 444\r\n2 ??? \t 0x105c29324 g_main_context_iteration + 112\r\n3 ??? \t 0x105c2b5a8 glib_worker_main + 48\r\n4 ??? \t 0x105c529ac g_thread_proxy + 68\r\n5 libsystem_pthread.dylib \t 0x19707d240 _pthread_start + 148\r\n6 libsystem_pthread.dylib \t 0x197078024 thread_start + 8\r\n\r\nThread 5:: pool-spawner\r\n0 libsystem_kernel.dylib \t 0x1970450c0 __psynch_cvwait + 8\r\n1 libsystem_pthread.dylib \t 0x19707d808 _pthread_cond_wait + 1228\r\n2 ??? \t 0x105c7b788 g_cond_wait + 44\r\n3 ??? \t 0x105bf5788 g_async_queue_pop_intern_unlocked + 144\r\n4 ??? \t 0x105c53050 g_thread_pool_spawn_thread + 88\r\n5 ??? \t 0x105c529ac g_thread_proxy + 68\r\n6 libsystem_pthread.dylib \t 0x19707d240 _pthread_start + 148\r\n7 libsystem_pthread.dylib \t 0x197078024 thread_start + 8\r\n\r\nThread 6:: pool-org.gnome.\r\n0 libsystem_kernel.dylib \t 0x1970450c0 __psynch_cvwait + 8\r\n1 libsystem_pthread.dylib \t 0x19707d834 _pthread_cond_wait + 1272\r\n2 ??? \t 0x105c7b9a0 g_cond_wait_until + 144\r\n3 ??? \t 0x105bf57ac g_async_queue_pop_intern_unlocked + 180\r\n4 ??? \t 0x105c53d8c g_thread_pool_thread_proxy + 172\r\n5 ??? \t 0x105c529ac g_thread_proxy + 68\r\n6 libsystem_pthread.dylib \t 0x19707d240 _pthread_start + 148\r\n7 libsystem_pthread.dylib \t 0x197078024 thread_start + 8\r\n\r\nThread 7:: pool-org.gnome.\r\n0 libsystem_kernel.dylib \t 0x1970450c0 __psynch_cvwait + 8\r\n1 libsystem_pthread.dylib \t 0x19707d834 _pthread_cond_wait + 1272\r\n2 ??? \t 0x105c7b9a0 g_cond_wait_until + 144\r\n3 ??? \t 0x105bf57ac g_async_queue_pop_intern_unlocked + 180\r\n4 ??? \t 0x105c53d8c g_thread_pool_thread_proxy + 172\r\n5 ??? \t 0x105c529ac g_thread_proxy + 68\r\n6 libsystem_pthread.dylib \t 0x19707d240 _pthread_start + 148\r\n7 libsystem_pthread.dylib \t 0x197078024 thread_start + 8\r\n\r\n\r\nThread 0 crashed with ARM Thread State (64-bit):\r\n x0: 0x000000013b330190 x1: 0x0000000106aa4430 x2: 0x0000000000000008 x3: 0x0000000000000000\r\n x4: 0x0000000000000000 x5: 0x0000000000000002 x6: 0x0000600002a95200 x7: 0x0000000109fa01cc\r\n x8: 0xa940421110fe0010 x9: 0x0000000000000002 x10: 0x0000000000000000 x11: 0x0000000000000002\r\n x12: 0x000000000000001e x13: 0x0000000000000066 x14: 0x0000000000000066 x15: 0x0000000000000000\r\n x16: 0x0000000105ad251c x17: 0x00000001f13881b8 x18: 0x0000000000000000 x19: 0x0000000106aa4430\r\n x20: 0x000000013b62eff0 x21: 0x000000016af2e420 x22: 0x0000000000000001 x23: 0x0000000000000000\r\n x24: 0x0000000000000098 x25: 0x0000000000000002 x26: 0x0000000105b0de58 x27: 0x0000000000000000\r\n x28: 0x0000000000000000 fp: 0x000000016af2e270 lr: 0x0000000105a89924\r\n sp: 0x000000016af2e260 pc: 0x0000000105ad2530 cpsr: 0x60001000\r\n far: 0xa940421110fe0018 esr: 0x92000004 (Data Abort) byte read Translation fault\r\n\r\nBinary Images:\r\n 0x0 - 0xffffffffffffffff ??? (*) <00000000-0000-0000-0000-000000000000> ???\r\n 0x104fdc000 - 0x10503bfff dyld (*) <6c3fc6e6-ee27-3ad4-82fd-73e4b990bb02> /usr/lib/dyld\r\n 0x197076000 - 0x197082fff libsystem_pthread.dylib (*) <61ee3110-0816-31e9-84bb-6a4fe8548658> /usr/lib/system/libsystem_pthread.dylib\r\n 0x197040000 - 0x197075fff libsystem_kernel.dylib (*) <b2f21b34-f3f3-3a01-8537-dcd2cc36d2da> /usr/lib/system/libsystem_kernel.dylib\r\n\r\nExternal Modification Summary:\r\n Calls made by other processes targeting this process:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n Calls made by this process:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n Calls made by all processes on this machine:\r\n task_for_pid: 0\r\n thread_create: 0\r\n thread_set_state: 0\r\n\r\nVM Region Summary:\r\nReadOnly portion of Libraries: Total=799.2M resident=0K(0%) swapped_out_or_unallocated=799.2M(100%)\r\nWritable regions: Total=976.1M written=0K(0%) resident=0K(0%) swapped_out=0K(0%) unallocated=976.1M(100%)\r\n\r\n VIRTUAL REGION \r\nREGION TYPE SIZE COUNT (non-coalesced) \r\n=========== ======= ======= \r\nActivity Tracing 256K 1 \r\nColorSync 464K 23 \r\nCoreGraphics 48K 3 \r\nKernel Alloc Once 32K 1 \r\nMALLOC 210.2M 28 \r\nMALLOC guard page 96K 5 \r\nMALLOC_MEDIUM (reserved) 360.0M 3 reserved VM address space (unallocated)\r\nMALLOC_NANO (reserved) 384.0M 1 reserved VM address space (unallocated)\r\nSTACK GUARD 56.1M 8 \r\nStack 11.7M 8 \r\nVM_ALLOCATE 1.0G 43 \r\n__AUTH 1766K 143 \r\n__AUTH_CONST 9132K 283 \r\n__DATA 9373K 336 \r\n__DATA_CONST 10.8M 348 \r\n__DATA_DIRTY 593K 99 \r\n__FONT_DATA 4K 1 \r\n__LINKEDIT 581.1M 68 \r\n__OBJC_CONST 1223K 117 \r\n__OBJC_RO 82.0M 1 \r\n__OBJC_RW 3104K 1 \r\n__TEXT 218.1M 364 \r\n__UNICODE 588K 1 \r\ndyld private memory 1024K 1 \r\nmapped file 63.5M 33 \r\nshared memory 1408K 14 \r\n=========== ======= ======= \r\nTOTAL 3.0G 1934 \r\nTOTAL, minus reserved VM space 2.2G 1934 \r\n```\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. nix-env -I meld\r\n2. meld\r\n3. broken\r\n\r\n### Expected behavior\r\nrun\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - host os: `Darwin 21.3.0, macOS 12.2`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - channels(sequencer): `\"nixpkgs-22.05pre339739.1dd151f0c0c\"`\r\n - channels(root): `\"nixpkgs-21.11pre325327.30f73c6493b\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151803/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151784","id":1086996193,"node_id":"I_kwDOAEVQ_M5Ayj7h","number":151784,"title":"'Teamviewer' terminated by Segmentation fault (core dumped)","user":{"login":"khrj","id":44947946,"node_id":"MDQ6VXNlcjQ0OTQ3OTQ2","avatar_url":"https://avatars.githubusercontent.com/u/44947946?v=4","gravatar_id":"","url":"https://api.github.com/users/khrj","html_url":"https://github.com/khrj","followers_url":"https://api.github.com/users/khrj/followers","following_url":"https://api.github.com/users/khrj/following{/other_user}","gists_url":"https://api.github.com/users/khrj/gists{/gist_id}","starred_url":"https://api.github.com/users/khrj/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/khrj/subscriptions","organizations_url":"https://api.github.com/users/khrj/orgs","repos_url":"https://api.github.com/users/khrj/repos","events_url":"https://api.github.com/users/khrj/events{/privacy}","received_events_url":"https://api.github.com/users/khrj/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":16,"created_at":"2021-12-22T16:35:37Z","updated_at":"2022-04-22T12:32:10Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nTeamviewer exits with \"Segmentation fault (core dumped)\" about 20 seconds after connecting remotely from a device (server is NixOS, client is macOS)\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Launch teamviewer\r\n2. Connect to NixOS using a remote computer\r\n3. Teamviewer exits on NixOS machine with `Segmentation fault (core dumped)`\r\n\r\n### Expected behavior\r\nTeamviewer doesn't quit after 20 seconds of remote access\r\n\r\n### Screenshots\r\n\r\n\r\n\r\n### Additional context\r\nPossibly fixed in next minor version 15.25.5 (unstable is on 15.24.5)\r\n\r\n### Notify maintainers\r\n@jagajaga\r\n@jraygauthier\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n- system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.84, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-21.05.4481.c5f1ee98224\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos\r\n ```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute: teamviewer\r\n# a list of nixos modules affected by the problem\r\nmodule: teamviewer\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151784/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151772","id":1086933140,"node_id":"I_kwDOAEVQ_M5AyUiU","number":151772,"title":"Idea: add new `using` attribute for package declared override","user":{"login":"psydvl","id":43755002,"node_id":"MDQ6VXNlcjQzNzU1MDAy","avatar_url":"https://avatars.githubusercontent.com/u/43755002?v=4","gravatar_id":"","url":"https://api.github.com/users/psydvl","html_url":"https://github.com/psydvl","followers_url":"https://api.github.com/users/psydvl/followers","following_url":"https://api.github.com/users/psydvl/following{/other_user}","gists_url":"https://api.github.com/users/psydvl/gists{/gist_id}","starred_url":"https://api.github.com/users/psydvl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/psydvl/subscriptions","organizations_url":"https://api.github.com/users/psydvl/orgs","repos_url":"https://api.github.com/users/psydvl/repos","events_url":"https://api.github.com/users/psydvl/events{/privacy}","received_events_url":"https://api.github.com/users/psydvl/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-22T15:23:37Z","updated_at":"2022-01-16T13:32:45Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"For now there are multiple versions for some packages, also no strong naming rules\r\nWith `using` attribute we can solve some naming problems, packages over flood (as I see it), multiple version support etc.\r\n\r\nThere are already override attribute, but it's only overriding, while using `using` we can create predeclared some options.\r\nAnd on `search.nixos.org` we can show package available options instead of big list of package renaming.\r\n\r\n<details>\r\n<summary>How, I think, `using` structure may look like for firefox package in draft:</summary>\r\n\r\nNB: It's still very draft.\r\n\r\n__default.nix__\r\n```\r\n{ .......... }:\r\nuse {\r\n\tusage = {\r\n\t\tversion = mkOption {\r\n\t\t\ttype = lib.types.enum [ \"default\", “esr”, “beta”, “nightly” ];\r\n\t\t};\r\n\t\ttype = mkOption {\r\n\t\t\ttype = lib.types.enum [ \"default\", “devedition” ]\r\n\t\t};\r\n\t\tbinary = mkOption {\r\n\t\t\tdefault = false;\r\n\t\t\ttype = bool;\r\n\t\t};\r\n\t\twayland = mkOption {\r\n\t\t\tdefault = usage.global.wayland;\r\n\t\t\ttype = bool;\r\n\t\t};\r\n\t};\r\n}@use:\r\nlet\r\n\tresult = import versions.nix { use.type, use.version, use.binary };\r\n\tversion = result.version;\r\n\tsha256 = result.sha256;\r\n\tsrc = if use.binary\r\n\t\tthen import binary.nix { inherit version sha256; }\r\n\t\telse import source.nix { inherit version sha256; };\r\nin\r\n#....\r\n```\r\n\r\n__versions.nix__\r\n```\r\n{ type, version, binary }:\r\nlet\r\n\tversions = {\r\n\t\t“default” = {\r\n\t\t\t“default” = {\r\n\t\t\t\tversion = “96.1.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“esr” = {\r\n\t\t\t\tversion = “91.5.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“beta” = {\r\n\t\t\t\tversion = “97.0beta”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“nightly” = {\r\n\t\t\t\tversion = “98.0a1”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t};\r\n\t\t“devedition” = {\r\n\t\t\t“default” = {\r\n\t\t\t\tversion = “96.1.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t};\r\n\t};\r\n\tversions-bin = {\r\n\t\t“default” = {\r\n\t\t\t“default” = {\r\n\t\t\t\tversion = “96.1.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“esr” = {\r\n\t\t\t\tversion = “91.5.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“beta” = {\r\n\t\t\t\tversion = “97.0beta”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t\t“nightly” = {\r\n\t\t\t\tversion = “98.0a1”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t};\r\n\t\t“devedition” = {\r\n\t\t\t“default” = {\r\n\t\t\t\tversion = “96.1.0”;\r\n\t\t\t\tsha256 = “AAAA..AA”;\r\n\t\t\t};\r\n\t\t};\r\n\t};\r\nin\r\n{\r\n\tversion = if binary\r\n\t\tthen versions-bin.type.version.version\r\n\t\tthen versions.type.version.version;\r\n\tsha256 = if binary\r\n\t\tthen versions-bin.type.version.sha256\r\n\t\tthen versions.type.version.sha256;\r\n}\r\n```\r\n\r\n__configuration.nix__\r\n```\r\nfirefox.using {\r\n\tversion = “esr”;\r\n\tbinary = true;\r\n\twayland = true;\r\n}\r\n```\r\n\r\n</details>\r\n\r\nHow it can work:\r\n1. linux kernel\r\n\t- Before `linuxKernel.kernels.linux_4_9`, `linuxKernel.kernels.linux_zen`\r\n\t- After `linuxKernel.kernels.using { version = “4.9”; }`, `linuxKernel.kernels.using { type = “zen”; }`\r\n2. Firefox\r\n\t- Before `firefox`, `firefox-esr-wayland`, `firefox-beta-bin`, `firefox-devedition-bin`\r\n\t\t<details>\r\n\t\t<summary>On search all available variants listed</summary>\r\n\t\t\r\n\t\t\r\n\t\t\r\n\t\t</details>\r\n\t- After\r\n\t\t`firefox` no changes per using default state\r\n\t\t```\r\n\t\tfirefox.using {\r\n\t\t\tversion = \"esr\"; # default - \"latest\" == latest stable, other variants: \"94.0\", \"beta\", \"dev\"\r\n\t\t\twayland = true;\r\n\t\t}\r\n\t\t```\r\n\t\t```\r\n\t\tfirefox.using {\r\n\t\t\tversion = \"beta\";\r\n\t\t\tbinary = true;\r\n\t\t}\r\n\t\t```\r\n\t\t```\r\n\t\tfirefox.using {\r\n\t\t\ttype = \"devedition\";\r\n\t\t\tbinary = true;\r\n\t\t}\r\n\t\t```\r\n\t\t<details>\r\n\t\t<summary>On search only `firefox` showing, with `using` options list `\"version\", \"type\", \"wayland\", \"binary\"` with on-click explanation</summary>\r\n\t\t\r\n\t\t\r\n\t\t\r\n\t\t</details>\r\n3. Meson\r\n\t- Before `meson`, `meson_0_60`\r\n\t- After\r\n\t\t`meson.using { version = \"0.57\" }` - which eqivalent for latest version in `[0.57.0, 0.58.0)`\r\n\t\t`meson.using { version = \"0.60\" }`\r\n4. ffmpeg\r\n\t- `ffmpeg`, `ffmpeg_3`, `ffmpeg-full`\r\n\t- `ffmpeg`\r\n\t\t`ffmpeg.using { version = \"3\" }`\r\n\t\t`ffmpeg.using { type = \"full\" # [\"default\", \"full\", \"minimal\", \"selective\"] }`\r\n\t\tExtra option:\r\n\t\t```\r\n\t\tffmpeg.using {\r\n\t\t\ttype = \"selective\"; # as idea only, not sure anyone really need this part\r\n\t\t\textra = [\r\n\t\t\t\talsa-lib \r\n\t\t\t\tfrei0r\r\n\t\t\t\tlibmfx\r\n\t\t\t];\r\n\t\t}\r\n\t\t```\r\n5. `libreoffice`: `version`: [\"still\", \"fresh\"], `qt`: bool\r\n6. `thinderbird`: `binary`: bool\r\n7. `xonotic`: `type`: [\"sdl\", \"glx\"]\r\n8. etc.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151772/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151729","id":1086664766,"node_id":"I_kwDOAEVQ_M5AxTA-","number":151729,"title":"wpa_supplicant not able to associate with home wifi using default authProtocols list","user":{"login":"tfc","id":29044,"node_id":"MDQ6VXNlcjI5MDQ0","avatar_url":"https://avatars.githubusercontent.com/u/29044?v=4","gravatar_id":"","url":"https://api.github.com/users/tfc","html_url":"https://github.com/tfc","followers_url":"https://api.github.com/users/tfc/followers","following_url":"https://api.github.com/users/tfc/following{/other_user}","gists_url":"https://api.github.com/users/tfc/gists{/gist_id}","starred_url":"https://api.github.com/users/tfc/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/tfc/subscriptions","organizations_url":"https://api.github.com/users/tfc/orgs","repos_url":"https://api.github.com/users/tfc/repos","events_url":"https://api.github.com/users/tfc/events{/privacy}","received_events_url":"https://api.github.com/users/tfc/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2021-12-22T10:11:57Z","updated_at":"2022-01-13T12:36:21Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI have a network config like this at home:\r\n\r\n```nix\r\n networking.wireless = {\r\n enable = true;\r\n interfaces = [ \"wlp3s0\" ];\r\n networks = {\r\n \"mySSID\" = { psk = \"mypassword\"; };\r\n ...\r\n };\r\n };\r\n```\r\n\r\nOn latest nixos, my laptop (a Lenovo x250) is completely unable to associate with the network due to authentication faults.\r\n\r\nBy leaving out the `key_mgmt` out of the wpa_supplicant config like this, i get it to work:\r\n\r\n```\r\ndiff --git a/nixos/modules/services/networking/wpa_supplicant.nix b/nixos/modules/services/networking/wpa_supplicant.nix\r\nindex 07dec8ea718..0684737aef6 100644\r\n--- a/nixos/modules/services/networking/wpa_supplicant.nix\r\n+++ b/nixos/modules/services/networking/wpa_supplicant.nix\r\n@@ -44,10 +44,12 @@ let\r\n \r\n options = [\r\n \"ssid=${quote ssid}\"\r\n- (if pskString != null || opts.auth != null\r\n- then \"key_mgmt=${concatStringsSep \" \" opts.authProtocols}\"\r\n- else \"key_mgmt=NONE\")\r\n- ] ++ optional opts.hidden \"scan_ssid=1\"\r\n+ ] ++ optional (opts.authProtocols != null) (\r\n+ if pskString != null || opts.auth != null\r\n+ then\"key_mgmt=${concatStringsSep \" \" opts.authProtocols}\"\r\n+ else \"key_mgmt=NONE\"\r\n+ )\r\n+ ++ optional opts.hidden \"scan_ssid=1\"\r\n ++ optional (pskString != null) \"psk=${pskString}\"\r\n ++ optionals (opts.auth != null) (filter (x: x != \"\") (splitString \"\\n\" opts.auth))\r\n ++ optional (opts.priority != null) \"priority=${toString opts.priority}\"\r\n@@ -253,19 +255,14 @@ in {\r\n };\r\n \r\n authProtocols = mkOption {\r\n- default = [\r\n- # WPA2 and WPA3\r\n- \"WPA-PSK\" \"WPA-EAP\" \"SAE\"\r\n- # 802.11r variants of the above\r\n- \"FT-PSK\" \"FT-EAP\" \"FT-SAE\"\r\n- ];\r\n+ default = null;\r\n # The list can be obtained by running this command\r\n # awk '\r\n # /^# key_mgmt: /{ run=1 }\r\n # /^#$/{ run=0 }\r\n # /^# [A-Z0-9-]{2,}/{ if(run){printf(\"\\\"%s\\\"\\n\", $2)} }\r\n # ' /run/current-system/sw/share/doc/wpa_supplicant/wpa_supplicant.conf.example\r\n- type = types.listOf (types.enum [\r\n+ type = types.nullOr (types.listOf (types.enum [\r\n \"WPA-PSK\"\r\n \"WPA-EAP\"\r\n \"IEEE8021X\"\r\n@@ -287,7 +284,7 @@ in {\r\n \"FT-FILS-SHA384\"\r\n \"OWE\"\r\n \"DPP\"\r\n- ]);\r\n+ ]));\r\n description = ''\r\n The list of authentication protocols accepted by this network.\r\n This corresponds to the <literal>key_mgmt</literal> option in wpa_supplicant.\r\n```\r\n\r\n### Notify maintainers\r\n\r\n@rnhmjoj \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.10, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(tfc): `\"\"`\r\n - channels(root): `\"nixos-21.11.334639.9ab7d12287c, home-manager-21.11\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151729/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151720","id":1086623172,"node_id":"I_kwDOAEVQ_M5AxI3E","number":151720,"title":"mono fails to build on aarch64-darwin","user":{"login":"prusnak","id":42201,"node_id":"MDQ6VXNlcjQyMjAx","avatar_url":"https://avatars.githubusercontent.com/u/42201?v=4","gravatar_id":"","url":"https://api.github.com/users/prusnak","html_url":"https://github.com/prusnak","followers_url":"https://api.github.com/users/prusnak/followers","following_url":"https://api.github.com/users/prusnak/following{/other_user}","gists_url":"https://api.github.com/users/prusnak/gists{/gist_id}","starred_url":"https://api.github.com/users/prusnak/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prusnak/subscriptions","organizations_url":"https://api.github.com/users/prusnak/orgs","repos_url":"https://api.github.com/users/prusnak/repos","events_url":"https://api.github.com/users/prusnak/events{/privacy}","received_events_url":"https://api.github.com/users/prusnak/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":5,"created_at":"2021-12-22T09:24:01Z","updated_at":"2022-02-03T09:51:15Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Build ends up with\r\n\r\n```\r\nif test -w /private/tmp/nix-build-mono-6.12.0.122.drv-1/mono-6.12.0.122/mcs; then :; else chmod -R +w /private/tmp/nix-build-mono-6.12.0.122.drv-1/mono-6.12.0.122/mcs; fi\r\ncd /private/tmp/nix-build-mono-6.12.0.122.drv-1/mono-6.12.0.122/mcs && make --no-print-directory -s NO_DIR_CHECK=1 PROFILES='binary_reference_assemblies net_4_x xbuild_12 xbuild_14 ' CC='clang' all-profiles\r\nmkdir -p -- build/deps\r\n/nix/store/7aqi1cxp0q594zl71c8fpkv7zjnzf6rw-bash-5.1-p12/bin/bash: line 1: mono: command not found\r\nmake[6]: *** [build/profiles/build.make:134: build/deps/basic-profile-check.exe] Error 127\r\n*** The runtime 'mono' doesn't appear to be usable.\r\n*** Trying the 'monolite-macos/1A5E0066-58DC-428A-B21C-0AD6CDAE2789' directory.\r\nmake[8]: *** [build/profiles/build.make:134: build/deps/basic-profile-check.exe] Segmentation fault: 11\r\n*** The contents of your 'monolite-macos/1A5E0066-58DC-428A-B21C-0AD6CDAE2789' directory may be out-of-date\r\n*** You may want to try 'make get-monolite-latest'\r\nmake[8]: *** [build/profiles/build.make:117: do-profile-check-monolite] Error 1\r\nmake[7]: *** [build/profiles/build.make:93: do-profile-check] Error 2\r\nmake[6]: *** [build/profiles/build.make:129: do-profile-check-monolite] Error 2\r\nmake[5]: *** [build/profiles/build.make:93: do-profile-check] Error 2\r\nmake[4]: *** [Makefile:58: profile-do--build--all] Error 2\r\nmake[3]: *** [Makefile:54: profiles-do--all] Error 2\r\nmake[2]: *** [Makefile:706: all-mcs] Error 2\r\nmake[2]: Leaving directory '/private/tmp/nix-build-mono-6.12.0.122.drv-1/mono-6.12.0.122/runtime'\r\nmake[1]: *** [Makefile:601: all-recursive] Error 1\r\nmake[1]: Leaving directory '/private/tmp/nix-build-mono-6.12.0.122.drv-1/mono-6.12.0.122'\r\nmake: *** [Makefile:529: all] Error 2\r\nerror: builder for '/nix/store/63g0r6i4gililac2ai7fnvac7b4kc1l8-mono-6.12.0.122.drv' failed with exit code 2\r\n```\r\n\r\nFull log: https://logs.nix.ci/?key=nixos/nixpkgs.151468&attempt_id=199e4e63-2c40-469e-8fe5-d8e8b73b5043","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151720/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151696","id":1086510162,"node_id":"I_kwDOAEVQ_M5AwtRS","number":151696,"title":"Recent dhcpcd update breaks dhcpcd if Graphene's hardened_malloc is used","user":{"login":"artemislena","id":51862164,"node_id":"MDQ6VXNlcjUxODYyMTY0","avatar_url":"https://avatars.githubusercontent.com/u/51862164?v=4","gravatar_id":"","url":"https://api.github.com/users/artemislena","html_url":"https://github.com/artemislena","followers_url":"https://api.github.com/users/artemislena/followers","following_url":"https://api.github.com/users/artemislena/following{/other_user}","gists_url":"https://api.github.com/users/artemislena/gists{/gist_id}","starred_url":"https://api.github.com/users/artemislena/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/artemislena/subscriptions","organizations_url":"https://api.github.com/users/artemislena/orgs","repos_url":"https://api.github.com/users/artemislena/repos","events_url":"https://api.github.com/users/artemislena/events{/privacy}","received_events_url":"https://api.github.com/users/artemislena/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":11,"created_at":"2021-12-22T06:52:24Z","updated_at":"2022-01-30T18:07:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nThe recent PR by @pennae https://github.com/NixOS/nixpkgs/pull/147516 seems to break DHCP, for us at least.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\nDon't know, honestly, as it seems to work for other people, and we had a fairly standard, autogenerated network connection…\r\n\r\n### Expected behavior\r\nAn IP address should get assigned through DHCP and network connection should work.\r\n\r\n### Additional context\r\nI'm pretty sure it's a dhcpd issue as the rollback that fixed it always said it was removing the user and group dhcpcd.\r\nAlso see Matrix messages https://matrix.to/#/!KqkRjyTEzAGRiZFBYT:nixos.org/$GKwDPNm053wj5ELWYcG6XEI4i0oX6vV2na_d8_ze1eY?via=nixos.org&via=matrix.org&via=tchncs.de to https://matrix.to/#/!KqkRjyTEzAGRiZFBYT:nixos.org/$WlpEmq-yEjBTF_7mgzHr3uhU8Iq0NkA2GMBqyyc2RRU?via=nixos.org&via=matrix.org&via=tchncs.de (in the Nix/NixOS Matrix room).\r\nAlso check https://codeberg.org/artemislena/nixos-server-configs if you think it might be an issue with our configuration… Note: Networking in general isn't broken, as networkd works…\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@edolstra @fpletz \r\n\r\n### Metadata\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n- system: `\"aarch64-linux\"`\r\n - host os: `Linux 5.10.87-hardened1, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.1`\r\n - channels(root): `\"nixos-22.05pre339875.9e1b85b91fe\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nSorry, unsure what to put below…\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151696/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151659","id":1086336110,"node_id":"I_kwDOAEVQ_M5AwCxu","number":151659,"title":"python-language-server-0.36.2 not supported for interpreter python3.9 on Nixos 21.11?","user":{"login":"prehonor","id":10784632,"node_id":"MDQ6VXNlcjEwNzg0NjMy","avatar_url":"https://avatars.githubusercontent.com/u/10784632?v=4","gravatar_id":"","url":"https://api.github.com/users/prehonor","html_url":"https://github.com/prehonor","followers_url":"https://api.github.com/users/prehonor/followers","following_url":"https://api.github.com/users/prehonor/following{/other_user}","gists_url":"https://api.github.com/users/prehonor/gists{/gist_id}","starred_url":"https://api.github.com/users/prehonor/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/prehonor/subscriptions","organizations_url":"https://api.github.com/users/prehonor/orgs","repos_url":"https://api.github.com/users/prehonor/repos","events_url":"https://api.github.com/users/prehonor/events{/privacy}","received_events_url":"https://api.github.com/users/prehonor/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2021-12-22T00:26:46Z","updated_at":"2021-12-31T05:24:54Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"add spyder and nixos-rebuild,\r\nI got this error \r\nerror: python-language-server-0.36.2 not supported for interpreter python3.9\r\n(use '--show-trace' to show detailed location information)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151659/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151597","id":1086004244,"node_id":"I_kwDOAEVQ_M5AuxwU","number":151597,"title":"`sssctl` can't find the `memberof` module ","user":{"login":"wucke13","id":20400405,"node_id":"MDQ6VXNlcjIwNDAwNDA1","avatar_url":"https://avatars.githubusercontent.com/u/20400405?v=4","gravatar_id":"","url":"https://api.github.com/users/wucke13","html_url":"https://github.com/wucke13","followers_url":"https://api.github.com/users/wucke13/followers","following_url":"https://api.github.com/users/wucke13/following{/other_user}","gists_url":"https://api.github.com/users/wucke13/gists{/gist_id}","starred_url":"https://api.github.com/users/wucke13/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wucke13/subscriptions","organizations_url":"https://api.github.com/users/wucke13/orgs","repos_url":"https://api.github.com/users/wucke13/repos","events_url":"https://api.github.com/users/wucke13/events{/privacy}","received_events_url":"https://api.github.com/users/wucke13/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2021-12-21T16:23:54Z","updated_at":"2022-01-04T15:45:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThis started with the update from 21.05 to 21.11.\r\n\r\nWhen I execute `sudo sssctl domain-status`, I get the following error:\r\n\r\n```\r\n[sssd] [ldb] (0x0010): WARNING: Module [memberof] not found - do you need to set LDB_MODULES_PATH?\r\n[sssd] [ldb] (0x0010): Unable to load modules for /var/lib/sss/db/cache_<MY.DOMAIN>.ldb: (null)\r\n[sssd] [sss_tool_route] (0x0010): Command initialization failed [5] Input/output error\r\n```\r\n\r\nFurther on, SSSD doesn't work in our setup, neither login nor `getent passwd` works on any ad supplied user. The following message is in the log:\r\n\r\n```\r\nThere is no server that can be written into kdc info file.\r\n```\r\n\r\nSo far I believe, both issues are related, e.g. not only the `sssctl` tool but `sssd` itself have issue opening the `.ldb` file due to the missing module.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install a complicated AD setup\r\n2. Run `sssctl domain-status`\r\n\r\n### Expected behavior\r\nNo error message appears\r\n\r\n### Notify maintainers\r\n\r\n@bbigras\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.14.21, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151597/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151564","id":1085769883,"node_id":"I_kwDOAEVQ_M5At4ib","number":151564,"title":"package-request: oomox","user":{"login":"AnzenKodo","id":50282743,"node_id":"MDQ6VXNlcjUwMjgyNzQz","avatar_url":"https://avatars.githubusercontent.com/u/50282743?v=4","gravatar_id":"","url":"https://api.github.com/users/AnzenKodo","html_url":"https://github.com/AnzenKodo","followers_url":"https://api.github.com/users/AnzenKodo/followers","following_url":"https://api.github.com/users/AnzenKodo/following{/other_user}","gists_url":"https://api.github.com/users/AnzenKodo/gists{/gist_id}","starred_url":"https://api.github.com/users/AnzenKodo/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/AnzenKodo/subscriptions","organizations_url":"https://api.github.com/users/AnzenKodo/orgs","repos_url":"https://api.github.com/users/AnzenKodo/repos","events_url":"https://api.github.com/users/AnzenKodo/events{/privacy}","received_events_url":"https://api.github.com/users/AnzenKodo/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-21T12:14:06Z","updated_at":"2021-12-21T12:14:06Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nGraphical application for generating different color variations of a Materia and Oomox themes (GTK2, GTK3 and others), Archdroid, Gnome-Colors, Numix, Papirus, Suru++ icons, and terminal palette.\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/themix-project/oomox\r\n* source URL: https://github.com/themix-project/oomox\r\n* license: gpl3\r\n* platforms: linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151564/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151550","id":1085736448,"node_id":"I_kwDOAEVQ_M5AtwYA","number":151550,"title":"Navidrome: fails to connect to last.fm with DNS lookup failures","user":{"login":"antifuchs","id":11864,"node_id":"MDQ6VXNlcjExODY0","avatar_url":"https://avatars.githubusercontent.com/u/11864?v=4","gravatar_id":"","url":"https://api.github.com/users/antifuchs","html_url":"https://github.com/antifuchs","followers_url":"https://api.github.com/users/antifuchs/followers","following_url":"https://api.github.com/users/antifuchs/following{/other_user}","gists_url":"https://api.github.com/users/antifuchs/gists{/gist_id}","starred_url":"https://api.github.com/users/antifuchs/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/antifuchs/subscriptions","organizations_url":"https://api.github.com/users/antifuchs/orgs","repos_url":"https://api.github.com/users/antifuchs/repos","events_url":"https://api.github.com/users/antifuchs/events{/privacy}","received_events_url":"https://api.github.com/users/antifuchs/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-21T11:32:50Z","updated_at":"2021-12-31T21:41:19Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI'm trying to connect navidrome to last.fm, and it fails in a way that makes me suspect the non-cgo DNS lookup method that haunts other golang tools, as well:\r\n\r\n```\r\ntime=\"2021-12-21T11:06:12Z\" level=error msg=\"Could not fetch LastFM session key\" error=\"Get \\\"https://ws.audioscrobbler.com/2.0/?api_key=<xxx>&api_sig=<xxx>&format=json&method=auth.getSession&token=<xxx>\\\": dial tcp: lookup ws.audioscrobbler.com on [::1]:53: read udp [::1]:55341->[::1]:53: read: connection refused\" requestId=bonnetmaker/daMWUeL5JW-000657 token=<xxx> userId=<xxx>\r\n```\r\n\r\nI am not running a DNS server locally, nor are the various DNS resolution knobs set to `[::1]:53`. I'm able to resolve `ws.audioscrobbler.com` on the machine running navidrome on the commandline.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. install navidrome\r\n2. visit `<navidrome_install_url>/app/#/personal` and select \"Scrobble to last.fm\"\r\n3. on last.fm, login with your account & select \"connect app\".\r\n4. error message is displayed in the browser, and the above message is logged by navidrome.\r\n\r\n### Expected behavior\r\n\r\nnavidrome should be able to resolve `ws.audioscrobbler.com`.\r\n\r\n### Additional context\r\n\r\nI have two suspicions:\r\n\r\n* One is that this might be a \"pure go\" dns resolution problem: https://github.com/golang/go/issues/21906 seems to be a classic of the genre\r\n* The other is that there is some systemd isolation knob that's turned on in the navidrome service.\r\n\r\n### Notify maintainers\r\n\r\n@aciceri\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.77, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixos-20.09.2331.7d57790bc12\"`\r\n - nixpkgs: `/nix/store/4g24bds0a05p0vj87jzp3v4yy9nywpf2-source`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute: navidrome\r\n# a list of nixos modules affected by the problem\r\nmodule: services.navidrome\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151550/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151548","id":1085733719,"node_id":"I_kwDOAEVQ_M5AtvtX","number":151548,"title":"nixos-rebuild offline","user":{"login":"piegamesde","id":14054505,"node_id":"MDQ6VXNlcjE0MDU0NTA1","avatar_url":"https://avatars.githubusercontent.com/u/14054505?v=4","gravatar_id":"","url":"https://api.github.com/users/piegamesde","html_url":"https://github.com/piegamesde","followers_url":"https://api.github.com/users/piegamesde/followers","following_url":"https://api.github.com/users/piegamesde/following{/other_user}","gists_url":"https://api.github.com/users/piegamesde/gists{/gist_id}","starred_url":"https://api.github.com/users/piegamesde/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piegamesde/subscriptions","organizations_url":"https://api.github.com/users/piegamesde/orgs","repos_url":"https://api.github.com/users/piegamesde/repos","events_url":"https://api.github.com/users/piegamesde/events{/privacy}","received_events_url":"https://api.github.com/users/piegamesde/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-21T11:29:29Z","updated_at":"2022-04-11T10:11:11Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"**Is your feature request related to a problem? Please describe.**\r\nThere are a lot of issues around building nix derivations in offline mode, when no dependencies need to be fetched: https://github.com/NixOS/nix/issues/1985 https://github.com/NixOS/nix/issues/2715 https://github.com/NixOS/nix/issues/1195.\r\n\r\nAs far as I can tell, all the fixes are only concerned with `nix-build` and `nix build`. None of them seem to mention `nixos-rebuild`, so I'm opening this issue.\r\n\r\n**Describe the solution you'd like**\r\nIf the internet connection fails, but none is actually needed, then the build should not fail.\r\n\r\n**Describe alternatives you've considered**\r\nA `nixos-rebuild --offline` flag\r\n\r\n**Additional context**\r\nWorkaround: `nixos-rebuild switch --option substitute false` [source](https://discourse.nixos.org/t/rebuild-nixos-offline/3679/4?u=piegames)\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548/reactions","total_count":5,"+1":5,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151548/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151534","id":1085689065,"node_id":"I_kwDOAEVQ_M5Atkzp","number":151534,"title":"hydra jobs should more predictably import nixpkgs so that cache hits collide with flake imports","user":{"login":"colemickens","id":327028,"node_id":"MDQ6VXNlcjMyNzAyOA==","avatar_url":"https://avatars.githubusercontent.com/u/327028?v=4","gravatar_id":"","url":"https://api.github.com/users/colemickens","html_url":"https://github.com/colemickens","followers_url":"https://api.github.com/users/colemickens/followers","following_url":"https://api.github.com/users/colemickens/following{/other_user}","gists_url":"https://api.github.com/users/colemickens/gists{/gist_id}","starred_url":"https://api.github.com/users/colemickens/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/colemickens/subscriptions","organizations_url":"https://api.github.com/users/colemickens/orgs","repos_url":"https://api.github.com/users/colemickens/repos","events_url":"https://api.github.com/users/colemickens/events{/privacy}","received_events_url":"https://api.github.com/users/colemickens/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-21T10:40:34Z","updated_at":"2021-12-21T11:44:44Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nI'd like to mirror the hydra netboot builds that are pushed to the public nixos cache by referencing their derivation, but it's proving to be hard.\r\n\r\nWhen I look at hydra's reproduce script, it's... calling `nix-build` with a bunch of args including a meticulous nixpkgs that I'm not even sure I can reproduce properly in pure eval mode.\r\n\r\nex:\r\n\r\n```\r\n\r\nif ! [ -d \"$inputDir\" ]; then\r\n info \"fetching Git input ‘nixpkgs’ from ‘https://github.com/NixOS/nixpkgs.git’ (commit d87b72206aadebe6722944f541f55d33fd7046fb)...\"\r\n requireCommand git\r\n inputDirTmp=\"$inputDir.tmp\"\r\n rm -rf \"$inputDirTmp\"\r\n mkdir -p \"$inputDirTmp\"\r\n git clone 'https://github.com/NixOS/nixpkgs.git' \"$inputDirTmp\"\r\n (cd \"$inputDirTmp\" && git checkout 'd87b72206aadebe6722944f541f55d33fd7046fb')\r\n revCount=\"$(cd \"$inputDirTmp\" && (git rev-list 'd87b72206aadebe6722944f541f55d33fd7046fb' | wc -l))\"\r\n rm -rf \"$inputDirTmp/.git\"\r\n mv \"$inputDirTmp\" \"$inputDir\"\r\n echo -n $revCount > \"$tmpDir/nixpkgs/rev-count\"\r\nelse\r\n revCount=\"$(cat \"$tmpDir/nixpkgs/rev-count\")\"\r\nfi\r\n\r\nargs+=(--arg 'nixpkgs' \"{ outPath = $inputDir; rev = \\\"d87b72206aadebe6722944f541f55d33fd7046fb\\\"; shortRev = \\\"d87b722\\\"; revCount = $revCount; }\")\r\n```\r\n\r\nCan we simplify / unify this somehow so that this is less of an issue. Alternatively maybe someone has the right syntax to get the same exact derivation to build from pure eval Nix? I guess I could emulate that exact set of steps in shell, but... 👀 flakes...\r\n\r\nOr maybe just have another set of derivations that use flake compat to ensure we're just building the way flakes users would build for maximum hits?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151534/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151524","id":1085573351,"node_id":"I_kwDOAEVQ_M5AtIjn","number":151524,"title":"Standardize \"Mavenization\" for all Gradle Builds","user":{"login":"lorenzleutgeb","id":542154,"node_id":"MDQ6VXNlcjU0MjE1NA==","avatar_url":"https://avatars.githubusercontent.com/u/542154?v=4","gravatar_id":"","url":"https://api.github.com/users/lorenzleutgeb","html_url":"https://github.com/lorenzleutgeb","followers_url":"https://api.github.com/users/lorenzleutgeb/followers","following_url":"https://api.github.com/users/lorenzleutgeb/following{/other_user}","gists_url":"https://api.github.com/users/lorenzleutgeb/gists{/gist_id}","starred_url":"https://api.github.com/users/lorenzleutgeb/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/lorenzleutgeb/subscriptions","organizations_url":"https://api.github.com/users/lorenzleutgeb/orgs","repos_url":"https://api.github.com/users/lorenzleutgeb/repos","events_url":"https://api.github.com/users/lorenzleutgeb/events{/privacy}","received_events_url":"https://api.github.com/users/lorenzleutgeb/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":3104166337,"node_id":"MDU6TGFiZWwzMTA0MTY2MzM3","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20java","name":"6.topic: java","color":"fef2c0","default":false,"description":"Including JDK, tooling, other languages, other VMs"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-21T08:37:20Z","updated_at":"2021-12-23T13:05:44Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"When you search for [\"mavenize\" (6 hits)](https://github.com/NixOS/nixpkgs/search?q=mavenize) or [\"mavenizes\" (8 hits)](https://github.com/NixOS/nixpkgs/search?q=mavenizes) in Nixpkgs you'll find duplicated code.\r\n\r\nIt's usually something like\r\n\r\n```\r\nfind $GRADLE_USER_HOME/caches/modules-2 -type f -regex '.*\\.\\(jar\\|pom\\)' \\\r\n | perl -pe 's#(.*/([^/]+)/([^/]+)/([^/]+)/[0-9a-f]{30,40}/([^/\\s]+))$# ($x = $2) =~ tr|\\.|/|; \"install -Dm444 $1 \\$out/$x/$3/$4/$5\" #e' \\\r\n | sh\r\n```\r\n\r\nbut there are some variations. \"Mavenizing\" a Gradle cache should be standardized accross Nixpkgs.","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524/reactions","total_count":1,"+1":1,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151524/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151515","id":1085509516,"node_id":"I_kwDOAEVQ_M5As4-M","number":151515,"title":"coconut.vim","user":{"login":"drperceptron","id":92106371,"node_id":"U_kgDOBX1ugw","avatar_url":"https://avatars.githubusercontent.com/u/92106371?v=4","gravatar_id":"","url":"https://api.github.com/users/drperceptron","html_url":"https://github.com/drperceptron","followers_url":"https://api.github.com/users/drperceptron/followers","following_url":"https://api.github.com/users/drperceptron/following{/other_user}","gists_url":"https://api.github.com/users/drperceptron/gists{/gist_id}","starred_url":"https://api.github.com/users/drperceptron/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/drperceptron/subscriptions","organizations_url":"https://api.github.com/users/drperceptron/orgs","repos_url":"https://api.github.com/users/drperceptron/repos","events_url":"https://api.github.com/users/drperceptron/events{/privacy}","received_events_url":"https://api.github.com/users/drperceptron/received_events","type":"User","site_admin":false},"labels":[{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null},{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-21T07:11:02Z","updated_at":"2022-01-08T09:18:39Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"**Project description**\r\nVim syntax highlight and indent definition for Coconut\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://github.com/manicmaniac/coconut.vim\r\n* source URL: https://github.com/manicmaniac/coconut.vim\r\n* license: none\r\n* platforms: vim","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151515/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151507","id":1085445611,"node_id":"I_kwDOAEVQ_M5AspXr","number":151507,"title":"LXD cloud-init support is broken","user":{"login":"kstenerud","id":245857,"node_id":"MDQ6VXNlcjI0NTg1Nw==","avatar_url":"https://avatars.githubusercontent.com/u/245857?v=4","gravatar_id":"","url":"https://api.github.com/users/kstenerud","html_url":"https://github.com/kstenerud","followers_url":"https://api.github.com/users/kstenerud/followers","following_url":"https://api.github.com/users/kstenerud/following{/other_user}","gists_url":"https://api.github.com/users/kstenerud/gists{/gist_id}","starred_url":"https://api.github.com/users/kstenerud/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/kstenerud/subscriptions","organizations_url":"https://api.github.com/users/kstenerud/orgs","repos_url":"https://api.github.com/users/kstenerud/repos","events_url":"https://api.github.com/users/kstenerud/events{/privacy}","received_events_url":"https://api.github.com/users/kstenerud/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-21T05:14:31Z","updated_at":"2021-12-21T05:44:05Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nCloud-init never completes when creating a container via LXD in NixOS. It seems to get stuck right at the beginning because no commands get executed.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Enable lxd (virtualisation.lxd.enable = true) and add yourself to the lxd group\r\n2. Run the following from a shell:\r\n\r\n```\r\ncat << EOF >config.yml\r\n#cloud-config\r\nruncmd:\r\n - touch /run/cloud-config-did-run\r\nEOF\r\n\r\nlxc launch ubuntu: x --config=user.user-data=\"$(cat config.yml)\"\r\nlxc exec x -- bash -c \"cloud-init status --wait\"\r\n```\r\n\r\n### Expected behavior\r\nIt launches a container, prints a few dots to the screen and exits, after which one can see a file `cloud-config-did-run` in `/run` inside the container (this is what happens if run on an Ubuntu host).\r\n\r\n### Actual behavior\r\n`cloud-init status --wait` never completes, even after 30 minutes. It just fills the entire screen with dots as it waits to complete, and the file never gets created in `/run`. In fact, no cloud-init directives get run at all (I'm just using `runcmd` as a quick example).\r\n\r\n### Additional context\r\nComparing to Ubuntu's behaviour:\r\n\r\n#### /var/log/cloud-init-output.log\r\n\r\nBoth start the same but on an Ubuntu host the container has the following at the end of the log whereas on a Nixos host it does not:\r\n\r\n```\r\nCloud-init v. 21.4-0ubuntu1~20.04.1 running 'modules:config' at Tue, 21 Dec 2021 04:36:00 +0000. Up 16.37 seconds.\r\nCloud-init v. 21.4-0ubuntu1~20.04.1 running 'modules:final' at Tue, 21 Dec 2021 04:36:01 +0000. Up 17.41 seconds.\r\nci-info: no authorized SSH keys fingerprints found for user ubuntu.\r\nCloud-init v. 21.4-0ubuntu1~20.04.1 finished at Tue, 21 Dec 2021 04:36:01 +0000. Datasource DataSourceNoCloud [seed=/var/lib/cloud/seed/nocloud-net][dsmode=net]. Up 17.64 seconds\r\n```\r\n\r\n#### /var/log/cloud-init.log\r\n\r\nOn a Nixos host the log file ends here (on an Ubuntu host there are another 200 or so lines afterwards):\r\n```\r\n2021-12-21 04:41:25,312 - main.py[DEBUG]: Ran 15 modules with 0 failures\r\n2021-12-21 04:41:25,313 - atomic_helper.py[DEBUG]: Atomically writing to file /var/lib/cloud/data/status.json (via temporary file /var/lib/cloud/data/tmprkhv1111) - w: [644] 568 bytes/chars\r\n2021-12-21 04:41:25,313 - util.py[DEBUG]: Reading from /proc/uptime (quiet=False)\r\n2021-12-21 04:41:25,314 - util.py[DEBUG]: Read 20 bytes from /proc/uptime\r\n2021-12-21 04:41:25,314 - util.py[DEBUG]: cloud-init mode 'init' took 1.577 seconds (1.58)\r\n2021-12-21 04:41:25,314 - handlers.py[DEBUG]: finish: init-network: SUCCESS: searching for network datasources\r\n```\r\n\r\n### Notify maintainers\r\n@Mic92\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\n\r\n```console\r\n[karl@nas:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.05 MiB download, 0.28 MiB unpacked):\r\n /nix/store/wzach25vwapl3sa6f7gylqank3jhhsin-bash-interactive-4.4-p23-dev\r\ncopying path '/nix/store/wzach25vwapl3sa6f7gylqank3jhhsin-bash-interactive-4.4-p23-dev' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.84, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151507/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151475","id":1085271234,"node_id":"I_kwDOAEVQ_M5Ar-zC","number":151475,"title":"separateDebugInfo causes impurity (ca-derivations)","user":{"login":"Mindavi","id":9799623,"node_id":"MDQ6VXNlcjk3OTk2MjM=","avatar_url":"https://avatars.githubusercontent.com/u/9799623?v=4","gravatar_id":"","url":"https://api.github.com/users/Mindavi","html_url":"https://github.com/Mindavi","followers_url":"https://api.github.com/users/Mindavi/followers","following_url":"https://api.github.com/users/Mindavi/following{/other_user}","gists_url":"https://api.github.com/users/Mindavi/gists{/gist_id}","starred_url":"https://api.github.com/users/Mindavi/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Mindavi/subscriptions","organizations_url":"https://api.github.com/users/Mindavi/orgs","repos_url":"https://api.github.com/users/Mindavi/repos","events_url":"https://api.github.com/users/Mindavi/events{/privacy}","received_events_url":"https://api.github.com/users/Mindavi/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":6,"created_at":"2021-12-20T22:53:05Z","updated_at":"2021-12-21T16:46:41Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nNote that this bug is specific for content-addressed derivations. When input-addressed, it's a given that introducing env vars that don't do anything will give a different output.\r\n\r\nDue to separateDebugInfo inserting a build-id based on the (input-addressed) paths that are used, enabling that option makes a package (that's built using the nixUnstable ca-derivations feature) non-reproducible based on the environment.\r\n\r\nE.g. if an environment variable (that isn't used in the build) is set, this causes the build-id to change and thus also the content-addressed package.\r\n\r\nA way to resolve this is to not make the build-id based on the contents (+ the path, presumably), but to set it manually to a value (maybe a sha256 of _only_ the contents?). I'm not 100% sure how that should work, but it does not seem too hard to implement.\r\n\r\nThis is related to https://github.com/NixOS/nix/issues/5220 as well. Hydra is probably doing something it shouldn't, but regardless this should be fixed too.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n\r\n1. Enable the `ca-derivations` experimental feature.\r\n1. Download this zip with a reproducer: [content-address-unreproducible-debug-info.zip](https://github.com/NixOS/nixpkgs/files/7748305/content-address-unreproducible-debug-info.zip)\r\n1. `nix-shell -p diffoscope --run \"diffoscope $(nix-build 1.nix) $(nix-build 2.nix)\"`\r\n1. Observe different Build ID (and store paths).\r\n\r\n### Expected behavior\r\n\r\nBuild is reproducible and produces the same hash when unrelated environment variables are introduced, even with enableDebugInfo on (in content-addressed mode).\r\n\r\n### Additional context\r\n\r\nResolving this will improve reproducibility of _important_ derivations, since the ones with enableDebugInfo are typically very low-level core libraries.\r\n\r\nSince the Build ID is dependent on the input-addressed path, any change in stdenv / dependencies may cause the build to give a different result, even though the only difference is the Build ID. I _think_ this is undesirable.\r\n\r\n### Notify maintainers\r\n\r\n@regnat -> so you're aware of this issue before rolling out ca-derivations in nixpkgs. Thanks for the great work you've done and are doing!\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.5.0pre20211206_d1aaa7e`\r\n - channels(root): `\"nixos-22.05pre335103.6daa4a5c045, nixpkgs-22.05pre335103.6daa4a5c045\"`\r\n - channels(rick): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151475/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151469","id":1085251557,"node_id":"I_kwDOAEVQ_M5Ar5_l","number":151469,"title":"Regressions due to a boost bump","user":{"login":"veprbl","id":245573,"node_id":"MDQ6VXNlcjI0NTU3Mw==","avatar_url":"https://avatars.githubusercontent.com/u/245573?v=4","gravatar_id":"","url":"https://api.github.com/users/veprbl","html_url":"https://github.com/veprbl","followers_url":"https://api.github.com/users/veprbl/followers","following_url":"https://api.github.com/users/veprbl/following{/other_user}","gists_url":"https://api.github.com/users/veprbl/gists{/gist_id}","starred_url":"https://api.github.com/users/veprbl/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/veprbl/subscriptions","organizations_url":"https://api.github.com/users/veprbl/orgs","repos_url":"https://api.github.com/users/veprbl/repos","events_url":"https://api.github.com/users/veprbl/events{/privacy}","received_events_url":"https://api.github.com/users/veprbl/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":131612005,"node_id":"MDU6TGFiZWwxMzE2MTIwMDU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/3.skill:%20sprintable","name":"3.skill: sprintable","color":"f7c6c7","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2021-12-20T22:17:31Z","updated_at":"2022-02-21T07:14:03Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"The default boost version has been bumped from 1.69 (or 1.75) to 1.77. This is a notice for maintainers that **the following packages are now failing to build**:\r\n\r\n - [ ] [libpointmatcher](https://hydra.nixos.org/job/nixpkgs/staging-next/libpointmatcher.x86_64-linux) @cryptix\r\n - [ ] [masari](https://hydra.nixos.org/job/nixpkgs/staging-next/masari.x86_64-linux) @fpletz\r\n - [ ] [libtorrent-rasterbar-1_1_x](https://hydra.nixos.org/job/nixpkgs/staging-next/libtorrent-rasterbar-1_1_x.x86_64-linux) @phreedom\r\n - [x] [monotone](https://hydra.nixos.org/job/nixpkgs/staging-next/monotone.x86_64-linux) @7c6f434c #152208\r\n - [x] [arc_unpacker](https://hydra.nixos.org/job/nixpkgs/staging-next/arc_unpacker.x86_64-linux) @midchildan #152370\r\n - [x] [swiften](https://hydra.nixos.org/job/nixpkgs/staging-next/swiften.x86_64-linux) @Twey https://github.com/NixOS/nixpkgs/pull/152145\r\n - [ ] [pivxd](https://hydra.nixos.org/job/nixpkgs/staging-next/pivxd.x86_64-linux) @wucke13\r\n - [x] [cpp-netlib](https://hydra.nixos.org/job/nixpkgs/staging-next/cpp-netlib.x86_64-linux) - #151202\r\n - [ ] [particl-core](https://hydra.nixos.org/job/nixpkgs/staging-next/particl-core.x86_64-linux) @demyanrogozhin\r\n - [x] [nova-filters](https://hydra.nixos.org/job/nixpkgs/staging-next/nova-filters.x86_64-linux) @magnetophon #151732\r\n - [x] [powerdns](https://hydra.nixos.org/job/nixpkgs/staging-next/powerdns.x86_64-linux) @mic92 @disassembler - #151202\r\n - [ ] [uhd3_5](https://hydra.nixos.org/job/nixpkgs/staging-next/uhd3_5.x86_64-linux) @bjornfor @fpletz @tomberek\r\n - [ ] [namecoind](https://hydra.nixos.org/job/nixpkgs/staging-next/namecoind.x86_64-linux) @infinisil\r\n - [x] [libbitcoin](https://hydra.nixos.org/job/nixpkgs/staging-next/libbitcoin.x86_64-linux) - #151202\r\n - [x] [ndn-tools](https://hydra.nixos.org/job/nixpkgs/staging-next/ndn-tools.x86_64-linux) @bertof #152721\r\n - [x] [nfd](https://hydra.nixos.org/job/nixpkgs/staging-next/nfd.x86_64-linux) @bertof #152721\r\n - [x] [rethinkdb](https://hydra.nixos.org/job/nixpkgs/staging-next/rethinkdb.x86_64-linux) @thoughtpolice @bluescreen303 https://github.com/NixOS/nixpkgs/pull/153639\r\n - [ ] [litecoind](https://hydra.nixos.org/job/nixpkgs/staging-next/litecoind.x86_64-linux) @offlinehacker\r\n - [x] [wt3](https://hydra.nixos.org/job/nixpkgs/staging-next/wt3.x86_64-linux) @juliendehos @willibutz #152128\r\n - [x] [mozart2](https://hydra.nixos.org/job/nixpkgs/staging-next/mozart2.x86_64-linux) @layus #151576\r\n - [x] [librecad](https://hydra.nixos.org/job/nixpkgs/staging-next/librecad.x86_64-linux) @Kiwi @viric - #151202\r\n - [x] [ycmd](https://hydra.nixos.org/job/nixpkgs/staging-next/ycmd.x86_64-linux) @rasendubi @cstrahan @lnl7 597743cf9c62c21ec55a6d2ad64cdf062f117aaa\r\n - [ ] [namecoin](https://hydra.nixos.org/job/nixpkgs/staging-next/namecoin.x86_64-linux) @infinisil\r\n - [ ] [emulationstation](https://hydra.nixos.org/job/nixpkgs/staging-next/emulationstation.x86_64-linux) @edwtjo\r\n - [x] [python39Packages.graph-tool](https://hydra.nixos.org/job/nixpkgs/staging-next/python39Packages.graph-tool.x86_64-linux) @joelmo #151638\r\n - [ ] [opendungeons](https://hydra.nixos.org/job/nixpkgs/staging-next/opendungeons.x86_64-linux) \r\n - [ ] [litecoin](https://hydra.nixos.org/job/nixpkgs/staging-next/litecoin.x86_64-linux) @offlinehacker\r\n - [x] [colobot](https://hydra.nixos.org/job/nixpkgs/staging-next/colobot.x86_64-linux) @freezeboy #153130\r\n - [x] [snapcast](https://hydra.nixos.org/job/nixpkgs/staging-next/snapcast.x86_64-linux) @fpletz\r\n - [x] [gnuradio3_8Packages.gnuradio](https://hydra.nixos.org/job/nixpkgs/staging-next/gnuradio3_8Packages.gnuradio.x86_64-linux) @doronbehar @bjornfor @fpletz #151864\r\n - [x] [sourcetrail](https://hydra.nixos.org/job/nixpkgs/staging-next/sourcetrail.x86_64-linux) @midchildan #152375\r\n - [ ] [dashpay](https://hydra.nixos.org/job/nixpkgs/staging-next/dashpay.x86_64-linux) \r\n - [x] [digikam](https://hydra.nixos.org/job/nixpkgs/staging-next/digikam.x86_64-linux) - https://github.com/NixOS/nixpkgs/pull/151388\r\n - [x] [gnuradio3_8Minimal](https://hydra.nixos.org/job/nixpkgs/staging-next/gnuradio3_8Minimal.x86_64-linux) @doronbehar @bjornfor @fpletz\r\n - [x] [freecad](https://hydra.nixos.org/job/nixpkgs/staging-next/freecad.x86_64-linux) @viric @gebner @AndersonTorres #151741\r\n - [x] [opentoonz](https://hydra.nixos.org/job/nixpkgs/staging-next/opentoonz.x86_64-linux) @chkno #151500\r\n - [x] [sdrangel](https://hydra.nixos.org/job/nixpkgs/staging-next/sdrangel.x86_64-linux) @Alkeryn https://github.com/NixOS/nixpkgs/pull/153316\r\n - [x] [pokerth-server](https://hydra.nixos.org/job/nixpkgs/staging-next/pokerth-server.x86_64-linux) @obadz @yegortimoshenko #157088\r\n - [x] [python39Packages.roboschool](https://hydra.nixos.org/job/nixpkgs/staging-next/python39Packages.roboschool.x86_64-linux) @timokau - #154998\r\n - [x] [python39Packages.scikit-survival](https://hydra.nixos.org/job/nixpkgs/staging-next/python39Packages.scikit-survival.x86_64-linux)\r\n - [x] [foundationdb61](https://hydra.nixos.org/job/nixpkgs/staging-next/foundationdb61.x86_64-linux) @thoughtpolice #157967\r\n - [x] [pokerth](https://hydra.nixos.org/job/nixpkgs/staging-next/pokerth.x86_64-linux) @obadz @yegortimoshenko #157088\r\n - [x] [python38Packages.graph-tool](https://hydra.nixos.org/job/nixpkgs/staging-next/python38Packages.graph-tool.x86_64-linux) @joelmo - https://github.com/NixOS/nixpkgs/pull/151638\r\n - [x] [python38Packages.roboschool](https://hydra.nixos.org/job/nixpkgs/staging-next/python38Packages.roboschool.x86_64-linux) @timokau - #154998\r\n - [x] [bombono](https://hydra.nixos.org/job/nixpkgs/staging-next/bombono.x86_64-linux) @symphorien #151574\r\n - [x] [musikcube](https://hydra.nixos.org/job/nixpkgs/staging-next/musikcube.x86_64-linux) @aanderse\r\n - [x] [gplates](https://hydra.nixos.org/job/nixpkgs/staging-next/gplates.x86_64-linux) - https://github.com/NixOS/nixpkgs/pull/151505\r\n - [x] [mapnik](https://hydra.nixos.org/job/nixpkgs/staging-next/mapnik.x86_64-linux) @hrdinka @erictapen - #151202\r\n - [ ] [pivx](https://hydra.nixos.org/job/nixpkgs/staging-next/pivx.x86_64-linux) @wucke13\r\n - [x] [mirtk](https://hydra.nixos.org/job/nixpkgs/staging-next/mirtk.x86_64-linux) @bcdarwin #151596\r\n - [x] [slic3r](https://hydra.nixos.org/job/nixpkgs/staging-next/slic3r.x86_64-linux) @bjornfor #153276\r\n - [x] [arrayfire](https://hydra.nixos.org/job/nixpkgs/staging-next/arrayfire.x86_64-linux) @chessai\r\n - [x] [ethminer-free](https://hydra.nixos.org/job/nixpkgs/staging-next/ethminer-free.x86_64-linux) @Atemu #151989\r\n - [x] cryfs #152817\r\n\r\nA typical fix would involve pinning the package to a specific version (e.g. see #151202)","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469/reactions","total_count":11,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":8,"rocket":0,"eyes":3},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151469/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151464","id":1085218261,"node_id":"I_kwDOAEVQ_M5Arx3V","number":151464,"title":"Package Request: OpenSearch","user":{"login":"afics","id":948407,"node_id":"MDQ6VXNlcjk0ODQwNw==","avatar_url":"https://avatars.githubusercontent.com/u/948407?v=4","gravatar_id":"","url":"https://api.github.com/users/afics","html_url":"https://github.com/afics","followers_url":"https://api.github.com/users/afics/followers","following_url":"https://api.github.com/users/afics/following{/other_user}","gists_url":"https://api.github.com/users/afics/gists{/gist_id}","starred_url":"https://api.github.com/users/afics/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/afics/subscriptions","organizations_url":"https://api.github.com/users/afics/orgs","repos_url":"https://api.github.com/users/afics/repos","events_url":"https://api.github.com/users/afics/events{/privacy}","received_events_url":"https://api.github.com/users/afics/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-20T21:26:55Z","updated_at":"2021-12-20T21:26:55Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\nElasticsearch Fork\r\n\r\nVia homepage:\r\n> OpenSearch is a community-driven, open source search and analytics suite derived from Apache 2.0 licensed Elasticsearch 7.10.2 & Kibana 7.10.2. It consists of a search engine daemon, OpenSearch, and a visualization and user interface, OpenSearch Dashboards. OpenSearch enables people to easily ingest, secure, search, aggregate, view, and analyze data. \r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://opensearch.org/\r\n* source URL: https://github.com/opensearch-project/OpenSearch\r\n* license: apache-2.0\r\n* platforms: unix, linux, darwin, ...\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464/reactions","total_count":9,"+1":9,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151464/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151428","id":1084935560,"node_id":"I_kwDOAEVQ_M5Aqs2I","number":151428,"title":"Build pyradio with `requests` and `dnspython`","user":{"login":"j-steinbach","id":69524139,"node_id":"MDQ6VXNlcjY5NTI0MTM5","avatar_url":"https://avatars.githubusercontent.com/u/69524139?v=4","gravatar_id":"","url":"https://api.github.com/users/j-steinbach","html_url":"https://github.com/j-steinbach","followers_url":"https://api.github.com/users/j-steinbach/followers","following_url":"https://api.github.com/users/j-steinbach/following{/other_user}","gists_url":"https://api.github.com/users/j-steinbach/gists{/gist_id}","starred_url":"https://api.github.com/users/j-steinbach/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/j-steinbach/subscriptions","organizations_url":"https://api.github.com/users/j-steinbach/orgs","repos_url":"https://api.github.com/users/j-steinbach/repos","events_url":"https://api.github.com/users/j-steinbach/events{/privacy}","received_events_url":"https://api.github.com/users/j-steinbach/received_events","type":"User","site_admin":false},"labels":[{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null},{"id":290122561,"node_id":"MDU6TGFiZWwyOTAxMjI1NjE=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20package%20(update)","name":"9.needs: package (update)","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-20T15:44:18Z","updated_at":"2021-12-21T15:07:36Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"###### Checklist\r\n\r\n<!-- Note that these are hard requirements -->\r\n\r\n<!--\r\nYou can use the \"Go to file\" functionality on github to find the package\r\nThen you can go to the history for this package\r\nFind the latest \"package_name: old_version -> new_version\" commit\r\nThe \"new_version\" is the the current version of the package\r\n-->\r\n- [x] Checked the [nixpkgs master branch](https://github.com/NixOS/nixpkgs)\r\n<!--\r\nType the name of your package and try to find an open pull request for the package\r\nIf you find an open pull request, you can review it!\r\nThere's a high chance that you'll have the new version right away while helping the community!\r\n-->\r\n- [x] Checked the [nixpkgs pull requests](https://github.com/NixOS/nixpkgs/pulls)\r\n\r\n###### Project name\r\n`nix search` name: pyradio\r\n<!--\r\nThe current version can be found easily with the same process than above for checking the master branch\r\nIf an open PR is present for the package, take this version as the current one and link to the PR\r\n-->\r\ncurrent version: 0.8.9\r\ndesired version: 0.8.9 built with `requests'; see [readme](https://github.com/coderholic/pyradio#packaging-pyradio)\r\n\r\n###### Notify maintainers\r\n<!--\r\nSearch your package here: https://search.nixos.org/packages?channel=unstable\r\nIf no maintainer is listed for your package, tag the person that last updated the package\r\n-->\r\n\r\nmaintainers: @contrun \r\n\r\n###### Note for maintainers\r\n\r\nPlease tag this issue in your PR.\r\n\r\n\r\n----\r\n\r\nI tried my hand on building this myself, but maybe someone experienced can take a look?\r\n\r\n```nix\r\nwith import <nixpkgs> {};\r\n#{ lib, python3Packages, fetchFromGitHub }:\r\n\r\npython3Packages.buildPythonApplication rec {\r\n pname = \"pyradio\";\r\n version = \"0.8.9.9\";\r\n\r\n src = fetchFromGitHub {\r\n owner = \"coderholic\";\r\n repo = pname;\r\n rev = version;\r\n sha256 = \"04asw5alkkf2q5iixswarj6ddb0y4a6ixm7cckl6204jiyxpv6kc\";\r\n };\r\n\r\n propagatedBuildInputs = with python39Packages; [\r\n dnspython\r\n requests\r\n ];\r\n\r\n prePatch = ''\r\n\t sed -i 's/distro = None/distro = NixOS/' pyradio/config\r\n\t ''; \r\n\r\n checkPhase = ''\r\n $out/bin/pyradio --help\r\n '';\r\n\r\n meta = with lib; {\r\n homepage = \"http://www.coderholic.com/pyradio/\";\r\n description = \"Curses based internet radio player\";\r\n license = licenses.mit;\r\n maintainers = with maintainers; [ contrun ];\r\n };\r\n}\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151428/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151422","id":1084868003,"node_id":"I_kwDOAEVQ_M5AqcWj","number":151422,"title":"go-neb's `secretFile` support changes the semantics of the template options","user":{"login":"grahamc","id":76716,"node_id":"MDQ6VXNlcjc2NzE2","avatar_url":"https://avatars.githubusercontent.com/u/76716?v=4","gravatar_id":"","url":"https://api.github.com/users/grahamc","html_url":"https://github.com/grahamc","followers_url":"https://api.github.com/users/grahamc/followers","following_url":"https://api.github.com/users/grahamc/following{/other_user}","gists_url":"https://api.github.com/users/grahamc/gists{/gist_id}","starred_url":"https://api.github.com/users/grahamc/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/grahamc/subscriptions","organizations_url":"https://api.github.com/users/grahamc/orgs","repos_url":"https://api.github.com/users/grahamc/repos","events_url":"https://api.github.com/users/grahamc/events{/privacy}","received_events_url":"https://api.github.com/users/grahamc/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-20T14:40:37Z","updated_at":"2022-02-25T14:13:47Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nThe syntax inside templates is different depending on if secretFile is used or not, this makes the templates non-portable and produces confusing results.\r\n\r\nFor example, without a secret file the template in this config is valid:\r\n\r\n```nix\r\n{\r\n services.go-neb = {\r\n config = {\r\n clients = [\r\n {\r\n UserId = \"@bot:nixos.org\";\r\n AccessToken = \"SomeAccessToken\";\r\n HomeServerUrl = \"https://nixos.ems.host\";\r\n Sync = true;\r\n AutoJoinRooms = true;\r\n DisplayName = \"Bot\";\r\n }\r\n ];\r\n services = [\r\n {\r\n ID = \"alertmanager_service\";\r\n Type = \"alertmanager\";\r\n UserId = \"@bot:nixos.org\";\r\n Config.rooms.\"!QLQqibtFaVtDgurUAE:nixos.org\" = {\r\n html_template = ''\r\n {{range .Alerts -}}\r\n {{ $severity := index .Labels \"severity\" }}\r\n <b>{{ $severity }}</b>\r\n {{end -}}\r\n '';\r\n msg_type = \"m.text\";\r\n };\r\n }\r\n ];\r\n };\r\n };\r\n}\r\n```\r\n\r\nHowever, after adding a `secretFile` we get startup errors:\r\n\r\n```\r\nhtml template is invalid: template: htmlTemplate:2: unexpected \\\":=\\\" in command\"\r\n```\r\n\r\nWhat is happening? In the rendered config, `$severity` has been replaced with an empty string:\r\n\r\n```\r\nhtml_template: \"{{range .Alerts -}}\\n {{ := index .Labels \\\"severity\\\"\\...\r\n```\r\n\r\nTo fix this, I must change `$severity` to `$$severity`. However, `$$severity` is not valid if I _don't_ specify a secretFile.\r\n\r\n### Expected behavior\r\n\r\nThe templates I provide should be valid whether or not I provide a `secretFile`.\r\n\r\n### Notify maintainers\r\n\r\ncc @Mic92, @mweinelt \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.84, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20210810_a6ba313`\r\n - nixpkgs: `/nix/store/33zzxrj3kzlyv22qm3p7a703dp69cshd-source`\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n- services.go-neb\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151422/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151372","id":1084213018,"node_id":"I_kwDOAEVQ_M5An8ca","number":151372,"title":"NixOS install iso: allow to boot system from grub menu","user":{"login":"piegamesde","id":14054505,"node_id":"MDQ6VXNlcjE0MDU0NTA1","avatar_url":"https://avatars.githubusercontent.com/u/14054505?v=4","gravatar_id":"","url":"https://api.github.com/users/piegamesde","html_url":"https://github.com/piegamesde","followers_url":"https://api.github.com/users/piegamesde/followers","following_url":"https://api.github.com/users/piegamesde/following{/other_user}","gists_url":"https://api.github.com/users/piegamesde/gists{/gist_id}","starred_url":"https://api.github.com/users/piegamesde/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/piegamesde/subscriptions","organizations_url":"https://api.github.com/users/piegamesde/orgs","repos_url":"https://api.github.com/users/piegamesde/repos","events_url":"https://api.github.com/users/piegamesde/events{/privacy}","received_events_url":"https://api.github.com/users/piegamesde/received_events","type":"User","site_admin":false},"labels":[{"id":60265212,"node_id":"MDU6TGFiZWw2MDI2NTIxMg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20nixos","name":"6.topic: nixos","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":3,"created_at":"2021-12-19T22:58:18Z","updated_at":"2022-03-22T04:10:58Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"Usually, distro installers have an entry to their boot menu so that one can boot the system. Although one can always do that by using an earlier boot menu, this sometimes is really convenient.\r\n\r\nAn alternative would be a \"reboot to system\" command on the ISO, but I don't know how technically feasible this is.\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151372/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151367","id":1084196270,"node_id":"I_kwDOAEVQ_M5An4Wu","number":151367,"title":"scan-build from libclang unable to find ccc-analyzer","user":{"login":"jtojnar","id":705123,"node_id":"MDQ6VXNlcjcwNTEyMw==","avatar_url":"https://avatars.githubusercontent.com/u/705123?v=4","gravatar_id":"","url":"https://api.github.com/users/jtojnar","html_url":"https://github.com/jtojnar","followers_url":"https://api.github.com/users/jtojnar/followers","following_url":"https://api.github.com/users/jtojnar/following{/other_user}","gists_url":"https://api.github.com/users/jtojnar/gists{/gist_id}","starred_url":"https://api.github.com/users/jtojnar/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/jtojnar/subscriptions","organizations_url":"https://api.github.com/users/jtojnar/orgs","repos_url":"https://api.github.com/users/jtojnar/repos","events_url":"https://api.github.com/users/jtojnar/events{/privacy}","received_events_url":"https://api.github.com/users/jtojnar/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-19T21:32:38Z","updated_at":"2021-12-19T23:02:37Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n`scan-build` program from `libclang` looks for `ccc-analyzer` in `../libexec` but it is installed into a different output.\r\n\r\n### Steps To Reproduce\r\n```\r\n$ nix-build -A libclang.all\r\n$ result/bin/scan-build -o /tmp/foo echo\r\nscan-build: 'ccc-analyzer' does not exist at '/nix/store/54fwpd1lsgr1kadg9989cvafqkzfsqm8-clang-7.1.0/bin/ccc-analyzer'\r\n```\r\n\r\n### Expected behaviour\r\n`scan-build` should find `ccc-analyzer`.\r\n\r\n### Additional context\r\n\r\nIt works with `scan-build` from `clang-analyzer`:\r\n\r\n```\r\n$ nix-build -A clang-analyzer\r\n$ result/bin/scan-build -o /tmp/foo echo\r\nscan-build: Using '/nix/store/52w8z9p8m5idz4fsh9y1znmms59da8ba-clang-wrapper-13.0.0/bin/clang' for static analysis\r\n[…]\r\n```\r\n\r\nThis is bug is especially annoying because when it is first on `PATH`, it shadows the working program.\r\n\r\n### Possible solutions\r\n- Remove `scan-build` from `libclang` so it has a canonical home in `clang-analyzer`.\r\n- Patch [scan-build code](https://github.com/llvm/llvm-project/blob/555eacf75f21cd1dfc6363d73ad187b730349543/clang/tools/scan-build/bin/scan-build#L1898-L1899) to point to `lib` output.\r\n- Move `ccc-analyzer` to `out` output.\r\n\r\n### Notify maintainers\r\ncc @lovek323 @7c6f434c @dtzWill @primeos (libclang)\r\ncc @thoughtpolice @Mic92 (clang-analyzer)\r\n\r\n### Metadata\r\nNixpkgs a2e281f5770247855b85d70c43454ba5bff34613\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute: libclang\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151367/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151359","id":1084176726,"node_id":"I_kwDOAEVQ_M5AnzlW","number":151359,"title":"Why does the sdImage builder compress the ext4 image regardless of `sdImage.compressImage`?","user":{"login":"wucke13","id":20400405,"node_id":"MDQ6VXNlcjIwNDAwNDA1","avatar_url":"https://avatars.githubusercontent.com/u/20400405?v=4","gravatar_id":"","url":"https://api.github.com/users/wucke13","html_url":"https://github.com/wucke13","followers_url":"https://api.github.com/users/wucke13/followers","following_url":"https://api.github.com/users/wucke13/following{/other_user}","gists_url":"https://api.github.com/users/wucke13/gists{/gist_id}","starred_url":"https://api.github.com/users/wucke13/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/wucke13/subscriptions","organizations_url":"https://api.github.com/users/wucke13/orgs","repos_url":"https://api.github.com/users/wucke13/repos","events_url":"https://api.github.com/users/wucke13/events{/privacy}","received_events_url":"https://api.github.com/users/wucke13/received_events","type":"User","site_admin":false},"labels":[],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2021-12-19T19:47:52Z","updated_at":"2021-12-21T16:55:25Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"This is particular wasteful when using binfmt emulation to build images for `aarch64`. I'd much prefer if the `build.sdImage` derivations args would allow me to opt out of any unnecessary compression.\r\n\r\nhttps://github.com/NixOS/nixpkgs/blob/ae969de2bbf871583109d10f812d854ae8d4a878/nixos/modules/installer/sd-card/sd-image.nix#L21","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151359/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151350","id":1084154647,"node_id":"I_kwDOAEVQ_M5AnuMX","number":151350,"title":"vimPlugins.vim-colorschemes have hash mismatch","user":{"login":"KAction","id":44864956,"node_id":"MDQ6VXNlcjQ0ODY0OTU2","avatar_url":"https://avatars.githubusercontent.com/u/44864956?v=4","gravatar_id":"","url":"https://api.github.com/users/KAction","html_url":"https://github.com/KAction","followers_url":"https://api.github.com/users/KAction/followers","following_url":"https://api.github.com/users/KAction/following{/other_user}","gists_url":"https://api.github.com/users/KAction/gists{/gist_id}","starred_url":"https://api.github.com/users/KAction/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/KAction/subscriptions","organizations_url":"https://api.github.com/users/KAction/orgs","repos_url":"https://api.github.com/users/KAction/repos","events_url":"https://api.github.com/users/KAction/events{/privacy}","received_events_url":"https://api.github.com/users/KAction/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null},{"id":344191335,"node_id":"MDU6TGFiZWwzNDQxOTEzMzU=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20vim","name":"6.topic: vim","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-19T17:51:08Z","updated_at":"2021-12-23T00:14:13Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Steps To Reproduce\n\n```\n:; nix-build -A vimPlugins.vim-colorschemes\nthese 2 derivations will be built:\n /nix/store/03k8iyms9hadvk2a8csalqhnlr3s7nb3-source.drv\n /nix/store/8ifriy2q0mymvs2iip7pwmziqqd3iqyg-vimplugin-vim-colorschemes-2020-05\n-15.drv\nbuilding '/nix/store/03k8iyms9hadvk2a8csalqhnlr3s7nb3-source.drv'...\n\n\ntrying https://github.com/flazz/vim-colorschemes/archive/fd8f122cef604330c96a6a6\ne434682dbdfb878c9.tar.gz\ntrying https://github.com/flazz/vim-colorschemes/archive/fd8f122cef604330c96a6a6\ne434682dbdfb878c9.tar.gz\n % Total % Received % Xferd Average Speed Time Time Time Current\n % Total % Received % Xferd Average Speed Time Time Time Current\n Dload Upload Total Spent Left Speed\n Dload Upload Total Spent Left Speed\n100 164 100 164 0 0 1197 0 --:--:-- --:--:-- --:--:-- 1205\n100 164 100 164 0 0 1197 0 --:--:-- --:--:-- --:--:-- 1205\n100 1216k 0 1216k 0 0 1547k 0 --:--:-- --:--:-- --:--:-- 2826k\n100 1216k 0 1216k 0 0 1547k 0 --:--:-- --:--:-- --:--:-- 2826k\nunpacking source archive /build/fd8f122cef604330c96a6a6e434682dbdfb878c9.tar.gz\nunpacking source archive /build/fd8f122cef604330c96a6a6e434682dbdfb878c9.tar.gz\nhash mismatch in fixed-output derivation '/nix/store/2r0hrjgnhb8nyf5zh0gn8xwyqxa\nzrg9f-source':\n wanted: sha256:0kpsf6j20fgblc8vhqn7ymr52v2d1h52vc7rbxmxfwdm80nvv3g5\n got: sha256:1cg8q7w0vgl73aw1b9zz0zh5vw5d2pm8pm54fhfzva4azg56f416\ncannot build derivation '/nix/store/8ifriy2q0mymvs2iip7pwmziqqd3iqyg-vimplugin-v\nim-colorschemes-2020-05-15.drv': 1 dependencies couldn't be built\nerror: build of '/nix/store/8ifriy2q0mymvs2iip7pwmziqqd3iqyg-vimplugin-vim-color\nschemes-2020-05-15.drv' failed\n```\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151350/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151347","id":1084148742,"node_id":"I_kwDOAEVQ_M5AnswG","number":151347,"title":"haskellPackages not deterministic","user":{"login":"Atemu","id":18599032,"node_id":"MDQ6VXNlcjE4NTk5MDMy","avatar_url":"https://avatars.githubusercontent.com/u/18599032?v=4","gravatar_id":"","url":"https://api.github.com/users/Atemu","html_url":"https://github.com/Atemu","followers_url":"https://api.github.com/users/Atemu/followers","following_url":"https://api.github.com/users/Atemu/following{/other_user}","gists_url":"https://api.github.com/users/Atemu/gists{/gist_id}","starred_url":"https://api.github.com/users/Atemu/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Atemu/subscriptions","organizations_url":"https://api.github.com/users/Atemu/orgs","repos_url":"https://api.github.com/users/Atemu/repos","events_url":"https://api.github.com/users/Atemu/events{/privacy}","received_events_url":"https://api.github.com/users/Atemu/received_events","type":"User","site_admin":false},"labels":[{"id":99513706,"node_id":"MDU6TGFiZWw5OTUxMzcwNg==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20haskell","name":"6.topic: haskell","color":"fef2c0","default":false,"description":null},{"id":290143264,"node_id":"MDU6TGFiZWwyOTAxNDMyNjQ=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20reproducible%20builds","name":"6.topic: reproducible builds","color":"fef2c0","default":false,"description":null},{"id":885133080,"node_id":"MDU6TGFiZWw4ODUxMzMwODA=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/2.status:%20wait-for-upstream","name":"2.status: wait-for-upstream","color":"e6e6e6","default":false,"description":"Waiting for upstream fix (or their other action)."}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":4,"created_at":"2021-12-19T17:21:57Z","updated_at":"2021-12-22T09:29:55Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"### Describe the bug\r\nA clear and concise description of what the bug is.\r\n\r\nIn the [GNOME ISO r13y report](https://r13y.com/iso_gnome/index.html) you can see a ton of haskellPackages that are not deterministic.\r\n\r\nJudging by [this](https://r13y.com/iso_gnome/diff/1f1b657ccb977b5f8a4e1178cbbb7dfdf01d9ab5ff6f930de4dd0449d7b538bf-cfb7e0739a0812cdd560b8c849354f9c6737e9be0cb42c520ec922a48723fc1d.html), it looks like label names are somehow a bit random sometimes?","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151347/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151338","id":1084135971,"node_id":"I_kwDOAEVQ_M5Anpoj","number":151338,"title":"Building nixpkgs.icoutils on darwin fails","user":{"login":"HerrSpace","id":224042,"node_id":"MDQ6VXNlcjIyNDA0Mg==","avatar_url":"https://avatars.githubusercontent.com/u/224042?v=4","gravatar_id":"","url":"https://api.github.com/users/HerrSpace","html_url":"https://github.com/HerrSpace","followers_url":"https://api.github.com/users/HerrSpace/followers","following_url":"https://api.github.com/users/HerrSpace/following{/other_user}","gists_url":"https://api.github.com/users/HerrSpace/gists{/gist_id}","starred_url":"https://api.github.com/users/HerrSpace/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/HerrSpace/subscriptions","organizations_url":"https://api.github.com/users/HerrSpace/orgs","repos_url":"https://api.github.com/users/HerrSpace/repos","events_url":"https://api.github.com/users/HerrSpace/events{/privacy}","received_events_url":"https://api.github.com/users/HerrSpace/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-19T16:21:53Z","updated_at":"2021-12-19T17:00:45Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\nBuilding nixpkgs.icoutils on arm64 darwin fails with the following error:\r\n`/nix/store/ypqm9riz1gr599jdv9sh45g1wfknnqsj-libSystem-11.0.0/include/stdlib.h:181:5: error: 'TARGET_OS_IPHONE' is not defined, evaluates to 0 [-Werror,-Wundef-prefix=TARGET_OS_]`\r\n\r\nHaven't reproed, but [looks also broken on AMD64](https://hydra.nixos.org/job/nixos/trunk-combined/nixpkgs.icoutils.x86_64-darwin).\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Try to build it with something like `nix-build ~/repos/upstream/nixpkgs -A icoutils`\r\n2. Get the error above. [Full build log here](https://gist.github.com/HerrSpace/982beec8915e207b485c745539ad979c#file-gistfile1-txt-L1738)\r\n\r\n### Expected behavior\r\nThe build should succeed.\r\n\r\n### Additional context\r\n- It seems to me like TARGET_OS_IPHONE is defined [here in Libsystem](https://github.com/NixOS/nixpkgs/blob/master/pkgs/os-specific/darwin/apple-source-releases/Libsystem/default.nix#L71)\r\n- It's unclear to me how to reference Libsystem properly from icoutils.\r\n\r\n### Notify maintainers\r\n- Maybe the Libsystem maintainers can enlighten me here :) @copumpkin @gridaphobe \r\n- Also @matthewbauer who [marked icoutils as supported by darwin here](https://github.com/NixOS/nixpkgs/commit/fe9b9e7f38999ca219ad9e6b4cf6447320ec9b70)\r\n\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(root): `\"nixpkgs-22.05pre339191.e1f9e754a40\"`\r\n - channels(space): `\"\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute: nixpkgs.ghidra-bin\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338/reactions","total_count":2,"+1":2,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151338/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151336","id":1084134759,"node_id":"I_kwDOAEVQ_M5AnpVn","number":151336,"title":"systemd-boot update touches EFI variables when told not to","user":{"login":"Informatic","id":1131102,"node_id":"MDQ6VXNlcjExMzExMDI=","avatar_url":"https://avatars.githubusercontent.com/u/1131102?v=4","gravatar_id":"","url":"https://api.github.com/users/Informatic","html_url":"https://github.com/Informatic","followers_url":"https://api.github.com/users/Informatic/followers","following_url":"https://api.github.com/users/Informatic/following{/other_user}","gists_url":"https://api.github.com/users/Informatic/gists{/gist_id}","starred_url":"https://api.github.com/users/Informatic/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/Informatic/subscriptions","organizations_url":"https://api.github.com/users/Informatic/orgs","repos_url":"https://api.github.com/users/Informatic/repos","events_url":"https://api.github.com/users/Informatic/events{/privacy}","received_events_url":"https://api.github.com/users/Informatic/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":1,"created_at":"2021-12-19T16:16:12Z","updated_at":"2022-01-31T18:17:23Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"### Describe the bug\r\nDuring systemd-boot update step `bootctl` attempts to touch EFI variables, even when `boot.loader.efi.canTouchEfiVariables` is set to `false`.\r\n\r\n### Steps To Reproduce\r\nSteps to reproduce the behavior:\r\n1. Install NixOS 21.05 with systemd-boot and `boot.loader.efi.canTouchEfiVariables = false;`\r\n2. Upgrade to NixOS 21.11 (fa8aa7ff5995d539aabc6f6a009dfcc1e3fd33a8)\r\n3. Configuration switch fails with:\r\n```\r\nCopied \"/nix/store/rgjrn2vl55pyxahfggvbdgl5g0xn0an1-systemd-249.5/lib/systemd/boot/efi/systemd-bootx64.efi\" to \"/boot/EFI/systemd/systemd-bootx64.efi\".\r\nCopied \"/nix/store/rgjrn2vl55pyxahfggvbdgl5g0xn0an1-systemd-249.5/lib/systemd/boot/efi/systemd-bootx64.efi\" to \"/boot/EFI/BOOT/BOOTX64.EFI\".\r\nupdating systemd-boot from (247) to (249.5)\r\nFailed to create EFI Boot variable entry: Input/output error\r\nTraceback (most recent call last):\r\n File \"/nix/store/5f69p1syxlsfyxxb54zs1gc59ngf2cxz-systemd-boot\", line 314, in <module>\r\n main()\r\n File \"/nix/store/5f69p1syxlsfyxxb54zs1gc59ngf2cxz-systemd-boot\", line 267, in main\r\n subprocess.check_call([\"/nix/store/rgjrn2vl55pyxahfggvbdgl5g0xn0an1-systemd-249.5/bin/bootctl\", \"--path=/boot\", \"update\"])\r\n File \"/nix/store/wl02plhc6zf84m6x9984l42wnnnbly5m-python3-3.9.6/lib/python3.9/subprocess.py\", line 373, in check_call\r\n raise CalledProcessError(retcode, cmd)\r\nsubprocess.CalledProcessError: Command '['/nix/store/rgjrn2vl55pyxahfggvbdgl5g0xn0an1-systemd-249.5/bin/bootctl', '--path=/boot', 'update']' returned non-zero exit status 1.\r\n```\r\nAn error is just an indication of update trying to touch EFI variables. (I have EFI vars touching disabled on that system because of some unrelated firmware breakage)\r\nManually running `bootctl --path=/boot update --no-variables` properly finishes, further switches work fine.\r\n\r\n### Expected behavior\r\nsystemd-boot update should not touch EFI variables during upgrade.\r\n\r\n### Notify maintainers\r\n@andir @flokli @kloenk\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.10.64, NixOS, 21.11 (Porcupine)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.3.16`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151336/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151311","id":1084108717,"node_id":"I_kwDOAEVQ_M5Ani-t","number":151311,"title":"Remove wlroots_0_14 (tracking issue)","user":{"login":"primeos","id":7537109,"node_id":"MDQ6VXNlcjc1MzcxMDk=","avatar_url":"https://avatars.githubusercontent.com/u/7537109?v=4","gravatar_id":"","url":"https://api.github.com/users/primeos","html_url":"https://github.com/primeos","followers_url":"https://api.github.com/users/primeos/followers","following_url":"https://api.github.com/users/primeos/following{/other_user}","gists_url":"https://api.github.com/users/primeos/gists{/gist_id}","starred_url":"https://api.github.com/users/primeos/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/primeos/subscriptions","organizations_url":"https://api.github.com/users/primeos/orgs","repos_url":"https://api.github.com/users/primeos/repos","events_url":"https://api.github.com/users/primeos/events{/privacy}","received_events_url":"https://api.github.com/users/primeos/received_events","type":"User","site_admin":false},"labels":[{"id":290122996,"node_id":"MDU6TGFiZWwyOTAxMjI5OTY=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/9.needs:%20clean-up","name":"9.needs: clean-up","color":"eb6420","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-19T14:19:32Z","updated_at":"2022-02-04T20:46:09Z","closed_at":null,"author_association":"MEMBER","active_lock_reason":null,"body":"~~Note: This is WIP / only a draft. https://github.com/NixOS/nixpkgs/pull/151234 isn't even merged yet.~~\r\n\r\nThe affected packages should switch to the latest wlroots release when possible (usually a new upstream release). There's no hurry (everything is still in `staging`) but let's use this issue to track the current progress.\r\n\r\nPackages:\r\n- [ ] cage (https://github.com/Hjdskes/cage/pull/197)\r\n- [ ] cagebreak (no patches yet: https://github.com/project-repo/cagebreak/tree/development)\r\n- [x] dwl (https://github.com/djpohly/dwl/tree/wlroots-next; **released**: https://github.com/djpohly/dwl/releases/tag/v0.2.2): https://github.com/NixOS/nixpkgs/pull/157593\r\n- [ ] hikari (https://hub.darcs.net/raichoo/hikari/patch/1dbeab7561c1f86815cbacdbbd4a8a8b2ec13b3e)\r\n- [x] labwc (https://github.com/labwc/labwc/commit/c9312edf0b05162b49032828837370e168a010d8; https://github.com/labwc/labwc/issues/121): https://github.com/NixOS/nixpkgs/pull/157065\r\n- [x] python3.8-pywlroots python3.9-pywlroots (https://github.com/flacjacket/pywlroots/issues/52 and https://github.com/flacjacket/pywlroots/pull/51; **released**: https://github.com/flacjacket/pywlroots/releases/tag/v0.15.0): https://github.com/NixOS/nixpkgs/pull/156671\r\n - [x] qtile (https://github.com/qtile/qtile; only depends on pywlroots): https://github.com/NixOS/nixpkgs/pull/156671\r\n- [x] river (**released**: https://github.com/riverwm/river/releases/tag/v0.1.1): https://github.com/NixOS/nixpkgs/pull/156086\r\n- [x] sway sway-unwrapped (https://github.com/swaywm/sway/commit/c53ef023850fcdc4b3dfeee2992cdaa7f0cee1ac; https://github.com/swaywm/sway/issues/6729): https://github.com/NixOS/nixpkgs/pull/151902\r\n - nwg-panel (only depends on Sway)\r\n - [x] waybar (https://github.com/Alexays/Waybar; depends on wlroots and Sway)\r\n- [ ] waybox-unstable (unmaintained: https://github.com/wizbright/waybox/issues/27)\r\n- [ ] wayfire wayfire wcm wcm wf-shell (https://github.com/WayfireWM/wayfire/commit/c690ad8d699978ec5f9fe2925a661a104c479e8a and https://github.com/WayfireWM/wayfire/issues/1386)\r\n- [ ] wio (basically unmaintained)\r\n- [ ] phoc (https://gitlab.gnome.org/World/Phosh/phoc/-/merge_requests/284)\r\n\r\nNo changes required / unaffected:\r\n- [x] fnott (https://codeberg.org/dnkl/fnott)\r\n- [x] qt-video-wlr (unmaintained?: https://github.com/xdavidwu/qt-video-wlr)\r\n- [x] wlroots tinywl\r\n\r\nPrevious issue: https://github.com/NixOS/nixpkgs/issues/118838","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151311/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151244","id":1083963122,"node_id":"I_kwDOAEVQ_M5Am_by","number":151244,"title":"Package request: GDLauncher","user":{"login":"l4ssc","id":72284051,"node_id":"MDQ6VXNlcjcyMjg0MDUx","avatar_url":"https://avatars.githubusercontent.com/u/72284051?v=4","gravatar_id":"","url":"https://api.github.com/users/l4ssc","html_url":"https://github.com/l4ssc","followers_url":"https://api.github.com/users/l4ssc/followers","following_url":"https://api.github.com/users/l4ssc/following{/other_user}","gists_url":"https://api.github.com/users/l4ssc/gists{/gist_id}","starred_url":"https://api.github.com/users/l4ssc/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/l4ssc/subscriptions","organizations_url":"https://api.github.com/users/l4ssc/orgs","repos_url":"https://api.github.com/users/l4ssc/repos","events_url":"https://api.github.com/users/l4ssc/events{/privacy}","received_events_url":"https://api.github.com/users/l4ssc/received_events","type":"User","site_admin":false},"labels":[{"id":1455363239,"node_id":"MDU6TGFiZWwxNDU1MzYzMjM5","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20packaging%20request","name":"0.kind: packaging request","color":"84b6eb","default":false,"description":""}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-18T23:06:49Z","updated_at":"2021-12-18T23:06:49Z","closed_at":null,"author_association":"NONE","active_lock_reason":null,"body":"**Project description**\r\n> GDLauncher is a custom open-source Minecraft launcher written from the ground up in electron/react. Its main goal is to make it easy and enjoyable to manage different Minecraft versions and install forge/fabric, bringing the playing and modding experience to the next level!\r\n\r\n**Metadata**\r\n\r\n* homepage URL: https://gdevs.io\r\n* source URL: https://github.com/gorilla-devs/GDLauncher\r\n* license: GPLv3, [LICENSE](https://github.com/gorilla-devs/GDLauncher/blob/master/LICENSE)\r\n* platforms: darwin, linux\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244/reactions","total_count":7,"+1":7,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151244/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151223","id":1083881703,"node_id":"I_kwDOAEVQ_M5Amrjn","number":151223,"title":"Idris2: compiled executables are broken on Mac","user":{"login":"srid","id":3998,"node_id":"MDQ6VXNlcjM5OTg=","avatar_url":"https://avatars.githubusercontent.com/u/3998?v=4","gravatar_id":"","url":"https://api.github.com/users/srid","html_url":"https://github.com/srid","followers_url":"https://api.github.com/users/srid/followers","following_url":"https://api.github.com/users/srid/following{/other_user}","gists_url":"https://api.github.com/users/srid/gists{/gist_id}","starred_url":"https://api.github.com/users/srid/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/srid/subscriptions","organizations_url":"https://api.github.com/users/srid/orgs","repos_url":"https://api.github.com/users/srid/repos","events_url":"https://api.github.com/users/srid/events{/privacy}","received_events_url":"https://api.github.com/users/srid/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":90308187,"node_id":"MDU6TGFiZWw5MDMwODE4Nw==","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20darwin","name":"6.topic: darwin","color":"fef2c0","default":false,"description":"Running or building packages on Darwin"}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":9,"created_at":"2021-12-18T17:53:51Z","updated_at":"2021-12-30T00:59:08Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\n\r\n\r\nOn M1 Mac with Idris2 installed via rosetta packages, the compiler generated executables cannot be executed:\r\n\r\n```\r\n[nix-shell:~/code/idris-template]$ idris2 hello.idr -x main\r\nException: (while loading libidris2_support.dylib) dlopen(libidris2_support.dylib, 0x0002): tried: '/nix/store/lxfslviarb3h6a2fa9ndwcv37j4dmjls-swift-corefoundation/Library/Frameworks/libidris2_support.dylib' (no such file), '/nix/store/lxfslviarb3h6a2fa9ndwcv37j4dmjls-swift-corefoundation/Library/Frameworks/libidris2_support.dylib' (no such file), 'libidris2_support.dylib' (no such file), '/usr/local/lib/libidris2_support.dylib' (no such file), '/usr/lib/libidris2_support.dylib' (no such file), '/Users/srid/code/idris-template/libidris2_support.dylib' (no such file), '/usr/local/lib/libidris2_support.dylib' (no such file), '/usr/lib/libidris2_support.dylib' (no such file)\r\n```\r\n\r\nalso,\r\n\r\n```\r\n[nix-shell:~/code/idris-template]$ idris2 hello.idr -o hello\r\n\r\n[nix-shell:~/code/idris-template]$ ./build/exec/hello\r\nException: (while loading libidris2_support.dylib) dlopen(libidris2_support.dylib, 0x0002): tried: '/nix/store/lxfslviarb3h6a2fa9ndwcv37j4dmjls-swift-corefoundation/Library/Frameworks/libidris2_support.dylib' (no such file), '/nix/store/lxfslviarb3h6a2fa9ndwcv37j4dmjls-swift-corefoundation/Library/Frameworks/libidris2_support.dylib' (no such file), 'libidris2_support.dylib' (no such file), '/usr/local/lib/libidris2_support.dylib' (no such file), '/usr/lib/libidris2_support.dylib' (no such file), '/Users/srid/code/idris-template/libidris2_support.dylib' (no such file), '/usr/local/lib/libidris2_support.dylib' (no such file), '/usr/lib/libidris2_support.dylib' (no such file)\r\n\r\n[nix-shell:~/code/idris-template]$ \r\n```\r\n\r\n### Steps To Reproduce\r\n\r\nOn a M1 Mac, run `nix develop -c make` in https://github.com/srid/idris-template/tree/c76e6086012fc1d48b25ddb484f0fa23fe429c57\r\n\r\n\r\n### Notify maintainers\r\n\r\n@fabianhjr @wchresta\r\n\r\n### Metadata\r\n\r\n```\r\n❯ nix-shell -p nix-info --run \"nix-info -m\"\r\n - system: `\"aarch64-darwin\"`\r\n - host os: `Darwin 21.2.0, macOS 12.1`\r\n - multi-user?: `yes`\r\n - sandbox: `no`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(srid): `\"darwin\"`\r\n - channels(root): `\"nixpkgs-21.11pre333180.98747f27ecf\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixpkgs`\r\n ```\r\n\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151223/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151197","id":1083845839,"node_id":"I_kwDOAEVQ_M5AmizP","number":151197,"title":"shiboken has broken pkgconfig file","user":{"login":"yshui","id":366851,"node_id":"MDQ6VXNlcjM2Njg1MQ==","avatar_url":"https://avatars.githubusercontent.com/u/366851?v=4","gravatar_id":"","url":"https://api.github.com/users/yshui","html_url":"https://github.com/yshui","followers_url":"https://api.github.com/users/yshui/followers","following_url":"https://api.github.com/users/yshui/following{/other_user}","gists_url":"https://api.github.com/users/yshui/gists{/gist_id}","starred_url":"https://api.github.com/users/yshui/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/yshui/subscriptions","organizations_url":"https://api.github.com/users/yshui/orgs","repos_url":"https://api.github.com/users/yshui/repos","events_url":"https://api.github.com/users/yshui/events{/privacy}","received_events_url":"https://api.github.com/users/yshui/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":9820195,"node_id":"MDU6TGFiZWw5ODIwMTk1","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20python","name":"6.topic: python","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":0,"created_at":"2021-12-18T14:37:58Z","updated_at":"2021-12-19T11:49:09Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nshiboken's pkgconfig file lists a directory as a library:\r\n\r\n```\r\nLibs: /nix/store/k0z9n599k02hab8qjjp3ljw065iwjcvg-python3-3.9.6/lib -L${libdir} -lshiboken.cpython-39-x86_64-linux-gnu\r\n```\r\n\r\nThis originates from setting PYTHON3_LIBRARY to a directory instead of the library during build.\r\n\r\n### Notify maintainers\r\n@jnetod @jonringer \r\n\r\n### Metadata\r\nPlease run `nix-shell -p nix-info --run \"nix-info -m\"` and paste the result.\r\n\r\n```console\r\n[user@system:~]$ nix-shell -p nix-info --run \"nix-info -m\"\r\nthis path will be fetched (0.00 MiB download, 0.00 MiB unpacked):\r\n /nix/store/rc7i07hxpz6h2a892x7pyzm0z6pw4gs4-nix-info\r\ncopying path '/nix/store/rc7i07hxpz6h2a892x7pyzm0z6pw4gs4-nix-info' from 'https://cache.nixos.org'...\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.7-zen-local+, Arch Linux, noversion`\r\n - multi-user?: `no`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4`\r\n - channels(shui): `\"nixpkgs-22.05pre338928.45a3f9d7725\"`\r\n - nixpkgs: `/home/shui/.nix-defexpr/channels/nixpkgs`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\n# a list of nixpkgs attributes affected by the problem\r\nattribute:\r\n# a list of nixos modules affected by the problem\r\nmodule:\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151197/timeline","performed_via_github_app":null},{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194","repository_url":"https://api.github.com/repos/NixOS/nixpkgs","labels_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194/labels{/name}","comments_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194/comments","events_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194/events","html_url":"https://github.com/NixOS/nixpkgs/issues/151194","id":1083839259,"node_id":"I_kwDOAEVQ_M5AmhMb","number":151194,"title":"Steam/Proton: Proton Fails to Load OpenGL","user":{"login":"seandheath","id":6528011,"node_id":"MDQ6VXNlcjY1MjgwMTE=","avatar_url":"https://avatars.githubusercontent.com/u/6528011?v=4","gravatar_id":"","url":"https://api.github.com/users/seandheath","html_url":"https://github.com/seandheath","followers_url":"https://api.github.com/users/seandheath/followers","following_url":"https://api.github.com/users/seandheath/following{/other_user}","gists_url":"https://api.github.com/users/seandheath/gists{/gist_id}","starred_url":"https://api.github.com/users/seandheath/starred{/owner}{/repo}","subscriptions_url":"https://api.github.com/users/seandheath/subscriptions","organizations_url":"https://api.github.com/users/seandheath/orgs","repos_url":"https://api.github.com/users/seandheath/repos","events_url":"https://api.github.com/users/seandheath/events{/privacy}","received_events_url":"https://api.github.com/users/seandheath/received_events","type":"User","site_admin":false},"labels":[{"id":6314750,"node_id":"MDU6TGFiZWw2MzE0NzUw","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/0.kind:%20bug","name":"0.kind: bug","color":"84b6eb","default":false,"description":null},{"id":786634609,"node_id":"MDU6TGFiZWw3ODY2MzQ2MDk=","url":"https://api.github.com/repos/NixOS/nixpkgs/labels/6.topic:%20steam","name":"6.topic: steam","color":"fef2c0","default":false,"description":null}],"state":"open","locked":false,"assignee":null,"assignees":[],"milestone":null,"comments":2,"created_at":"2021-12-18T14:01:55Z","updated_at":"2021-12-20T22:46:27Z","closed_at":null,"author_association":"CONTRIBUTOR","active_lock_reason":null,"body":"### Describe the bug\r\nI'm trying to launch Noita using Proton on Steam. The client attempts to launch the game but it immediately crashes.\r\n\r\nThe Proton log shows the following error:\r\n\r\n```\r\n290.182:010c:0110:err:wgl:X11DRV_WineGL_InitOpenglInfo couldn't initialize OpenGL, expect problems\r\n```\r\nI have OpenGL and my CPU configured as follows:\r\n```\r\n boot.kernel.sysctl = {\r\n \"dev.i915.perf_stream_paranoid\" = 0;\r\n };\r\n boot.kernelParams = [ \"i915.enable_psr=0\" ];\r\n boot.kernelPackages = pkgs.linuxPackages_latest;\r\n hardware.opengl = {\r\n enable = true;\r\n driSupport = true;\r\n driSupport32Bit = true;\r\n extraPackages = with pkgs; [\r\n libva\r\n vaapiIntel\r\n vaapiVdpau\r\n libvdpau-va-gl\r\n intel-media-driver\r\n ];\r\n extraPackages32 = with pkgs.pkgsi686Linux; [\r\n libva\r\n vaapiIntel\r\n vaapiVdpau\r\n libvdpau-va-gl\r\n ];\r\n };\r\n```\r\n\r\nI've tried both 21.05 stable and nixpkgs-unstable. I've tested mesa using the following:\r\n\r\n```\r\nnix run nixpkgs#glxinfo\r\nnix run nixpkgs#pkgsi686Linux.glxinfo\r\n```\r\n and both appear to be functioning normally.\r\n\r\nI set the launch configuration for the game to use OpenGL 4.6 (as indicated by glxinfo) using the following game specific launch parameters:\r\n\r\n```\r\nMESA_GL_VERSION_OVERRIDE=4.6 MESA_GLSL_VERSION_OVERRIDE=460 PROTON_LOG=1 %command%\r\n```\r\n\r\nI have tried pipewire and pulseaudio. I've enabled 32 bit support for both.\r\n\r\nI have attempted to enable steam-native per instructions on the NixOS wiki.\r\n\r\nI have tried using Proton GE (installed using protonup) as well as Proton Experimental and Proton 5.13.\r\n\r\nI still get the error. I'm not sure what else to try or how else to debug this.\r\n\r\n### Steps To Reproduce\r\n\r\nSteps to reproduce the behavior:\r\n\r\n1. Enable steam using `programs.steam.enable = true;`\r\n2. Enable steam compatibility layer for non-linux games in the settings menu\r\n3. Install Noita\r\n4. Launch Noita in the steam client \r\n\r\n### Expected behavior\r\nThe game should open and run normally.\r\n\r\n### Additional context\r\n\r\n I share the majority of my configuration between my AMD/Nvidia desktop and my Intel laptop and the game opens and runs correctly on the AMD/Nvidia machine.\r\n\r\n### Notify maintainers\r\n<!--\r\nPlease @ people who are in the `meta.maintainers` list of the offending package or module.\r\nIf in doubt, check `git blame` for whoever last touched something.\r\n-->\r\n@jagajaga @jonringer\r\n\r\n### Metadata\r\n\r\n```console\r\n - system: `\"x86_64-linux\"`\r\n - host os: `Linux 5.15.7, NixOS, 22.05 (Quokka)`\r\n - multi-user?: `yes`\r\n - sandbox: `yes`\r\n - version: `nix-env (Nix) 2.4pre20211006_53e4794`\r\n - channels(root): `\"nixos-21.05.4394.2553aee74fe, nixos-hardware\"`\r\n - channels(user): `\"home-manager-21.05, nixos-unstable-21.11pre328987.c935f5e0add\"`\r\n - nixpkgs: `/nix/var/nix/profiles/per-user/root/channels/nixos`\r\n```\r\n\r\nMaintainer information:\r\n```yaml\r\nmodule:\r\nsteam\r\n```\r\n","reactions":{"url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194/reactions","total_count":0,"+1":0,"-1":0,"laugh":0,"hooray":0,"confused":0,"heart":0,"rocket":0,"eyes":0},"timeline_url":"https://api.github.com/repos/NixOS/nixpkgs/issues/151194/timeline","performed_via_github_app":null}]
|